Encrypt Your Windows PC Without Sharing Keys With Microsoft [2025]
Here's a question that probably hasn't kept you up at night until now: where does Microsoft keep your disk encryption keys? If you're running Windows 11 with a Microsoft account and haven't explicitly opted out, the answer is their servers. And if law enforcement shows up with a warrant, Microsoft will hand them over.
This isn't speculation. In early 2025, the FBI served Microsoft with a warrant for BitLocker recovery keys tied to several laptops in connection with a fraud investigation involving Guam's COVID-19 unemployment assistance program. Microsoft complied. A company spokesperson later acknowledged handling around 20 similar requests per year from government authorities, as reported by TechPowerUp.
Now, before you panic and think your privacy is completely compromised, understand this: BitLocker encryption itself is genuinely strong. The encryption protecting your actual data isn't the weak link. The problem is where Microsoft stores your recovery key, which could theoretically give someone access to unlock your entire drive. It's the digital equivalent of storing your house keys with a third party.
But here's the good news. If you want true disk encryption where you and only you control the keys, Windows actually gives you that option. It's not buried in some obscure registry hack or third-party tool. It's built right in. You just need to know where to look and what to do. This guide walks you through the entire process, step by step.
TL; DR
- Windows 11 Home version won't let you control encryption keys, only Pro and higher editions give you that control, as detailed by PCMag.
- Your recovery key can be stored locally on a USB drive, printed out, or saved as a text file instead of uploading to Microsoft.
- You'll need to decrypt and re-encrypt your drive if it's already been encrypted with a Microsoft account, which takes 1-2 hours depending on drive size.
- BitLocker is the encryption tool you're using, whether you realize it or not, and it's been part of Windows for nearly two decades.
- Recovery keys are non-negotiable in case hardware changes trigger re-authentication, so save yours somewhere physically safe.
Understanding BitLocker and Why Your Recovery Key Matters
BitLocker isn't new. It's been around since Windows Vista, nearly two decades ago. But for most of that time, it was something only Windows Pro users could turn on manually. You had to go into Settings, find the right option, and choose to encrypt your drive. Most people didn't bother.
Microsoft changed that calculus starting with Windows 8, but it really became standard with Windows 11. Now, if you sign into Windows 11 Home or Pro with a Microsoft account, the operating system automatically encrypts your disk using BitLocker. No prompt. No opt-in dialog. It just happens in the background.
The automatic encryption is actually a good thing. It means everyone gets the protection of full-disk encryption by default, not just the technically sophisticated. But there's a catch built into that convenience.
When Windows automatically encrypts your drive, it also automatically uploads your recovery key to Microsoft's servers. Why? Because of hardware changes. If you replace your CPU, upgrade your motherboard, or make other significant hardware modifications, Windows will sometimes treat the system as a different computer. Your BitLocker key might stop working. Without a recovery key stored somewhere accessible, you'd be locked out of your own data.
So storing the recovery key makes sense from a practical standpoint. The problem is where it's stored. When you upload it to Microsoft, you're not giving the company the ability to decrypt your data directly. BitLocker uses a strong encryption algorithm. The real key protecting your data stays on your drive. But the recovery key—think of it as a master bypass—could theoretically allow someone with legal authority to unlock everything, as highlighted by HackRead.
The difference between the Home and Pro versions of Windows becomes crucial here. Home edition simply doesn't let you manage this process. You can't choose where your recovery key goes. You can't decide not to encrypt. You can't back up the key locally. Pro edition, by contrast, gives you complete control. You can encrypt or decrypt whenever you want. You can save your recovery key anywhere. You're in charge.
This distinction exists because Microsoft views Pro as the "business and advanced users" edition. Presumably, they thought privacy-conscious professionals might actually care about this stuff. They were right, as noted by Windows Central.
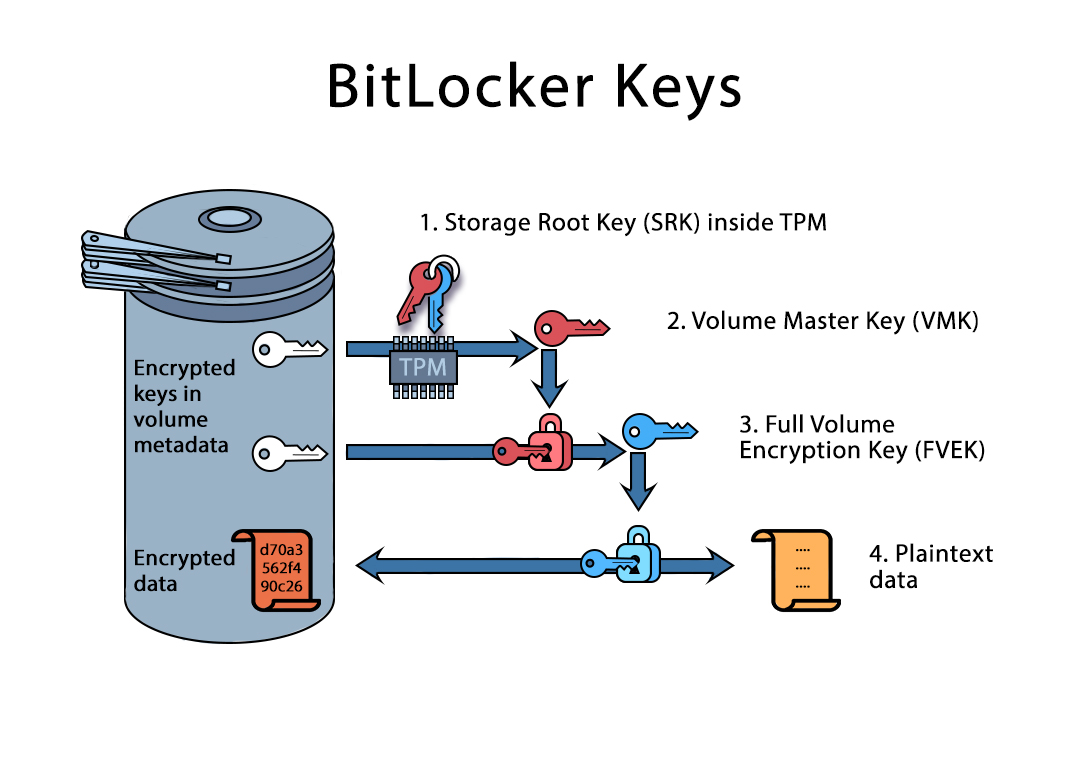
Why Storing Keys With Microsoft Became a Privacy Concern
Technically, Microsoft isn't being unusual or nefarious by complying with warrants. That's what companies do when served with legal paperwork. Apple, Google, Amazon, and most other tech companies operate the same way. When law enforcement shows up with a warrant, they comply. It's the law.
But there's a context worth understanding. The political environment in the United States has shifted notably since 2024. The Trump administration has signaled increased interest in investigating journalists, political opponents, and various other targets. The FBI has become more active in certain investigations. Encryption backdoors and key access have become live political issues.
For journalists especially, the ability to protect their sources and communications is essential. For activists, political organizers, and others who face potential government scrutiny, having encryption keys stored in Microsoft's servers represents a genuine risk. If a warrant gets served—even a questionable one—Microsoft will hand over your recovery key. The company isn't going to fight it in court on your behalf, as discussed in Forbes.
Apple has made much of the fact that it stores device encryption keys using additional encryption that allegedly makes them inaccessible even to Apple. The company claims it can't hand over the keys even if served with a warrant, because they don't actually have them in a form they could decrypt. Whether that's technically accurate is debated, but the point stands: some companies at least present the option of genuinely inaccessible keys.
Microsoft's approach is more straightforward. Your recovery key exists on their servers in a form they can access. They will hand it over if legally required. That's the trade-off for the convenience of automatic encryption and cloud-based recovery, as noted by HotHardware.
For many people, that trade-off is fine. Most of us aren't targets of federal investigations. But if you want actual privacy—not just assume privacy—you need to store your recovery key yourself.

Windows 11 Pro vs. Home: Why Edition Matters More Than You Think
This is the hardest requirement of the whole process, and it's not technical. It's financial. You need Windows 11 Pro, not Home. This isn't optional. Home edition simply doesn't have the settings you need.
Home edition can use BitLocker, but only in a limited way. When you're signed in with a Microsoft account, encryption happens automatically and your recovery key goes to Microsoft's servers. End of story. You don't get options. You don't get settings. There's no way to change where the recovery key goes. Home edition wasn't designed with privacy-conscious users in mind.
Pro edition gives you full control. You can turn BitLocker on or off. You can choose where your recovery key is stored. You can manage the encryption settings completely. If you want to encrypt your drive without uploading your key to Microsoft, you absolutely must have Pro, as explained by WebProNews.
So how do you get Pro? Microsoft offers a direct upgrade through the Microsoft Store for
There are also third-party key resellers online offering Windows 11 Pro keys for significantly less. Some of these are legitimate resellers with authorization from Microsoft. Others... are more questionable. A key from Stack Commerce or other authorized partners might cost
The honest answer is that if you can afford it, spending the $99 for Microsoft's official upgrade is the safest option. If that's genuinely not feasible, third-party resellers are a thing, but understand the risks. Sometimes these keys get revoked. Sometimes they're from invalid sources. You could end up buying something that doesn't work.
Once you have a valid Pro key, the upgrade process itself is painless. Open Settings. Go to System, then Activation. Click on the option to upgrade your edition of Windows. Enter your product key. Confirm. Your computer will restart. Within minutes, you'll be running Windows 11 Pro.
You won't need to reinstall anything. Your apps stay. Your files stay. Your settings stay. It's not like switching operating systems. It's like unlocking features that were already there.
Checking Your Current Encryption Status Before You Begin
Before you actually do anything, you need to know what state your drive is in. Is it already encrypted? If so, is your recovery key stored with Microsoft? These are important questions because they determine your next steps.
If you've been running Windows 11 with a Microsoft account and haven't explicitly opted out of encryption, your drive is almost certainly already encrypted. BitLocker is running in the background, doing its job. Your recovery key is almost certainly on Microsoft's servers. You'll need to decrypt and then re-encrypt to change that.
If you've been running Windows 11 without a Microsoft account, you might not have any encryption enabled. You'll be able to skip the decryption step and go straight to enabling BitLocker with your own recovery key storage.
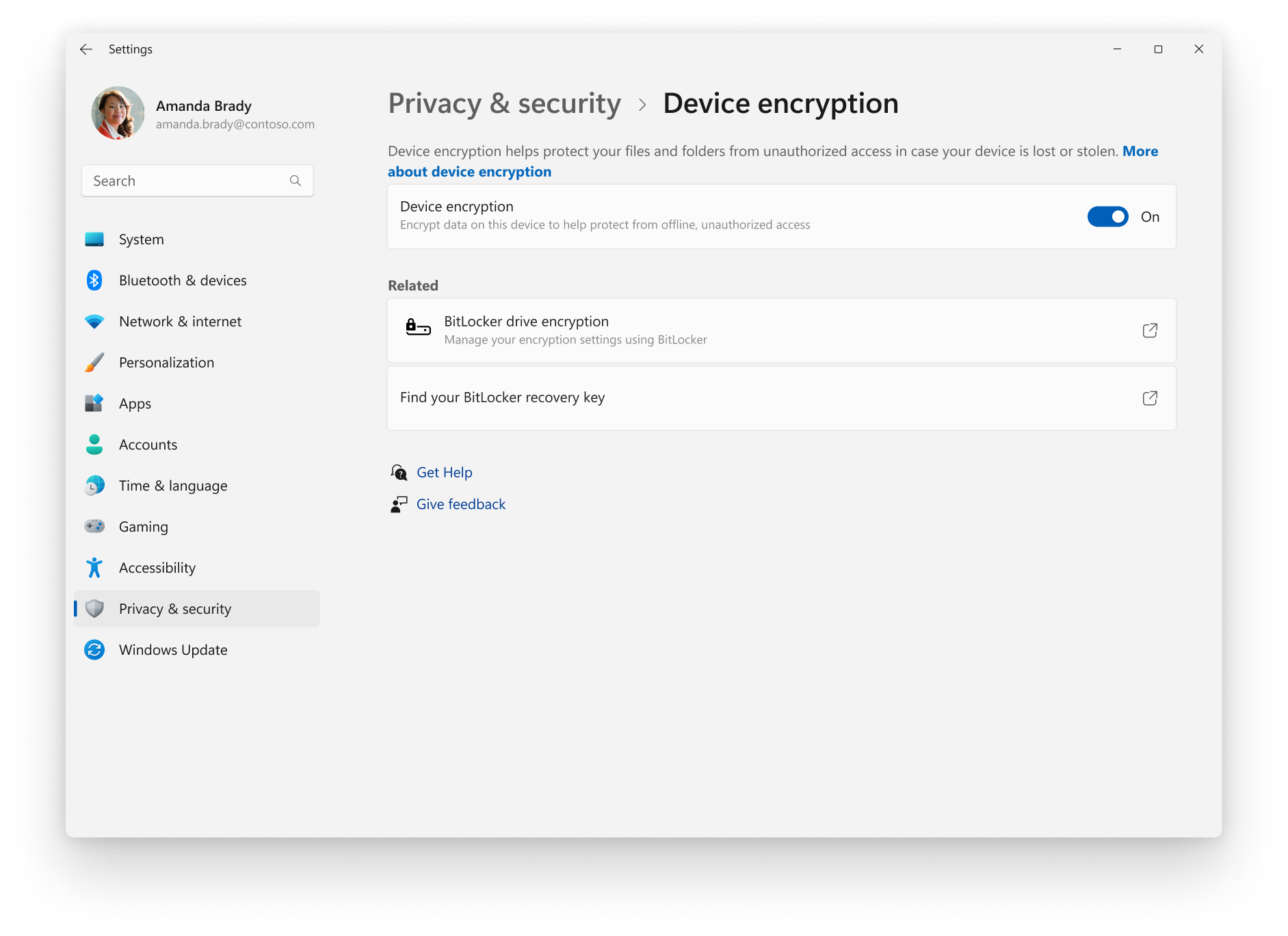
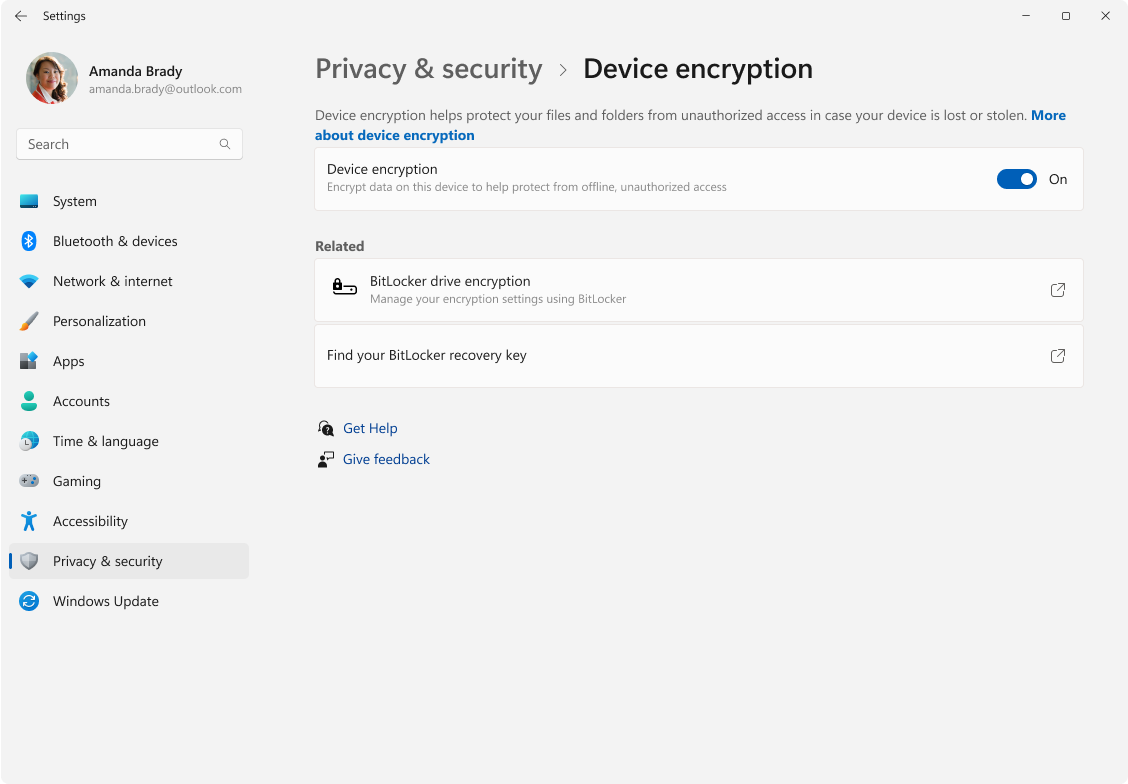
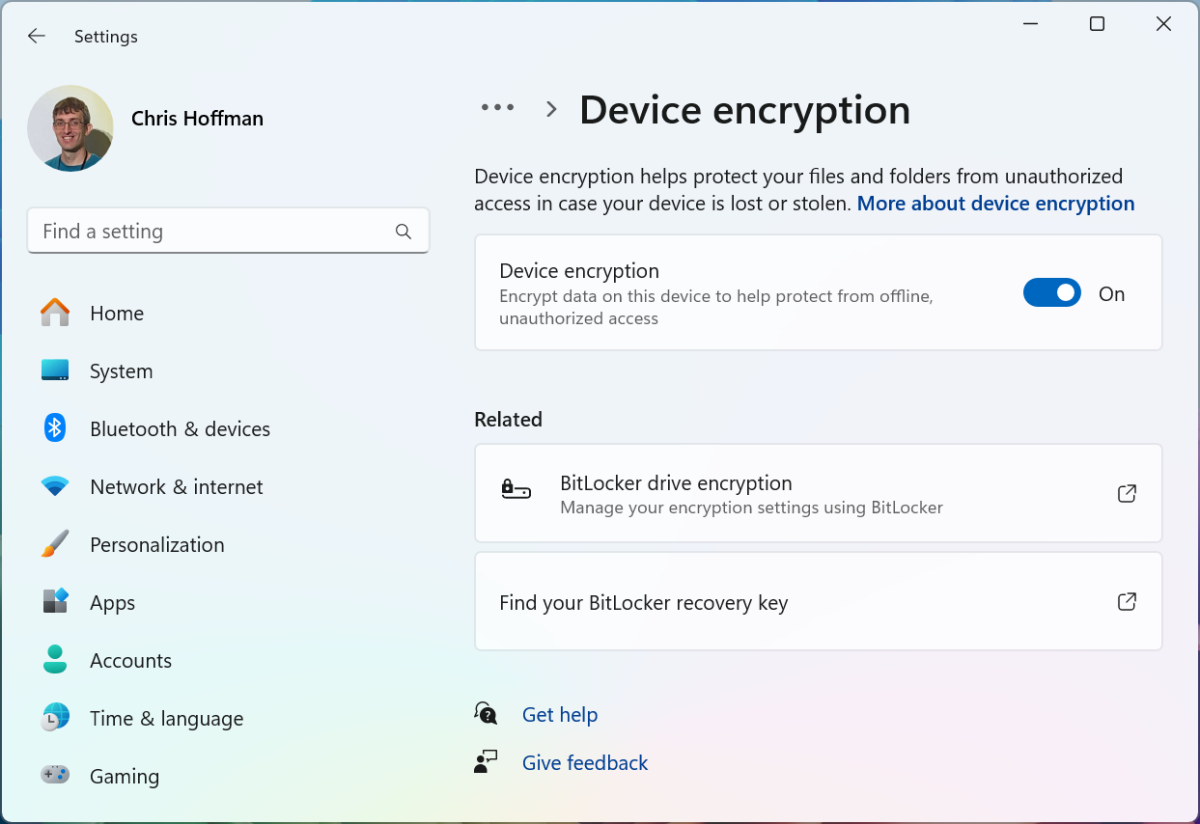
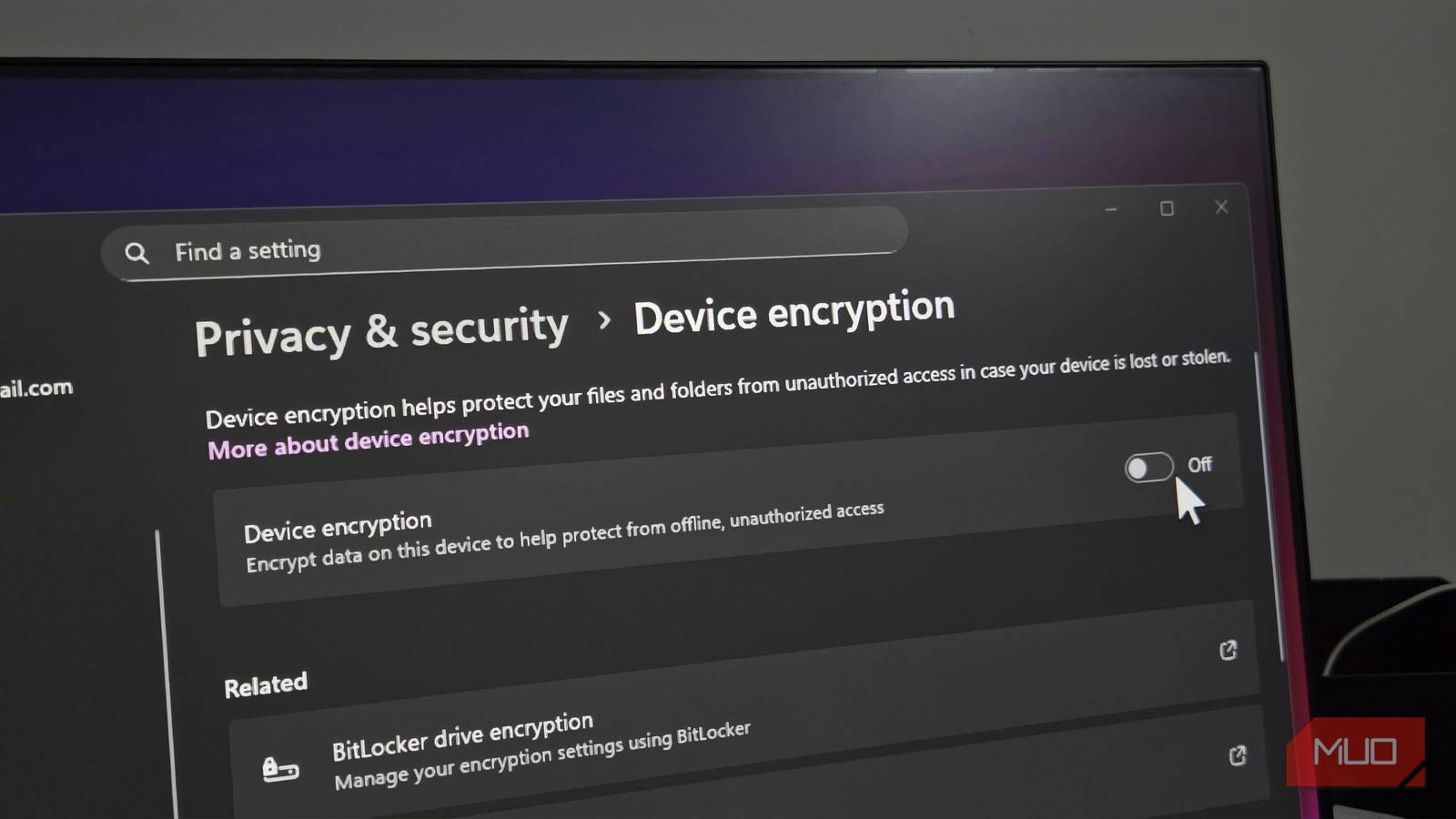
To check, open Settings. Navigate to Privacy & Security. Look for Device encryption. You'll see a toggle switch. If it's ON, your drive is encrypted. If it's OFF, you're not encrypted (though you might still have BitLocker available through a different settings path).
Next to the encryption status, you should see your recovery key information. If it says your key is backed up to your Microsoft account, that's the situation we're fixing. If it says your key is not backed up, that's actually already good—though it also means if something goes wrong with your drive, you could be locked out. Ideally, you want a recovery key stored somewhere safe, just not with Microsoft.
Take a screenshot of this screen or write down what it says. Having a record of your current encryption status is helpful for troubleshooting if anything goes wrong.
Decrypting Your Drive: Why This Takes So Long
If your drive is already encrypted with your recovery key stored on Microsoft's servers, you need to decrypt it first before re-encrypting with your own recovery key backup. This is the most time-consuming part of the entire process.
Why can't you just change the recovery key in place? Because of how BitLocker works. When encryption is enabled with a recovery key backed up to Microsoft, that configuration is baked into your drive. Changing it requires actually decrypting the entire drive and then re-encrypting it with new settings.
How long does this take? That depends on two things: the size of your drive and the speed of your storage. A 256GB SSD on a modern computer might take 30 to 45 minutes. A 1TB or larger drive could take several hours. A mechanical hard drive could take even longer. The process runs in the background, but it does consume resources, so your computer will be noticeably slower while it's happening.
Microsoft's documentation says it "may take a while." That's technically accurate but hilariously vague. Realistically, plan on at least 1-2 hours depending on your hardware. Don't start this process if you need your computer for work in the next few hours.
During decryption, your drive is vulnerable. It's not encrypted. If something goes catastrophically wrong—a power loss, a system crash—you could lose data. This is extremely unlikely on modern hardware, but it's technically possible. Make sure your computer is plugged in and not about to run out of battery. Don't unplug it. Don't restart it. Just let it finish.
You can check the progress by going back into Settings > Privacy & Security > Device encryption. The toggle will be OFF, and Windows will show you a percentage of how much of the drive has been decrypted. Sometimes it says "waiting for background activity to complete." That's fine. It'll get there.
Once decryption is complete, you'll get a notification. Your drive will now be unencrypted. Don't panic. You're about to re-encrypt it immediately with your own recovery key. You're not leaving your drive unencrypted.

The Path to BitLocker Settings: Why Windows Still Uses Vista-Era Controls
Once your drive is fully decrypted, you need to re-enable encryption. This is where things get slightly weird, because Windows still routes you through some genuinely ancient control panels.
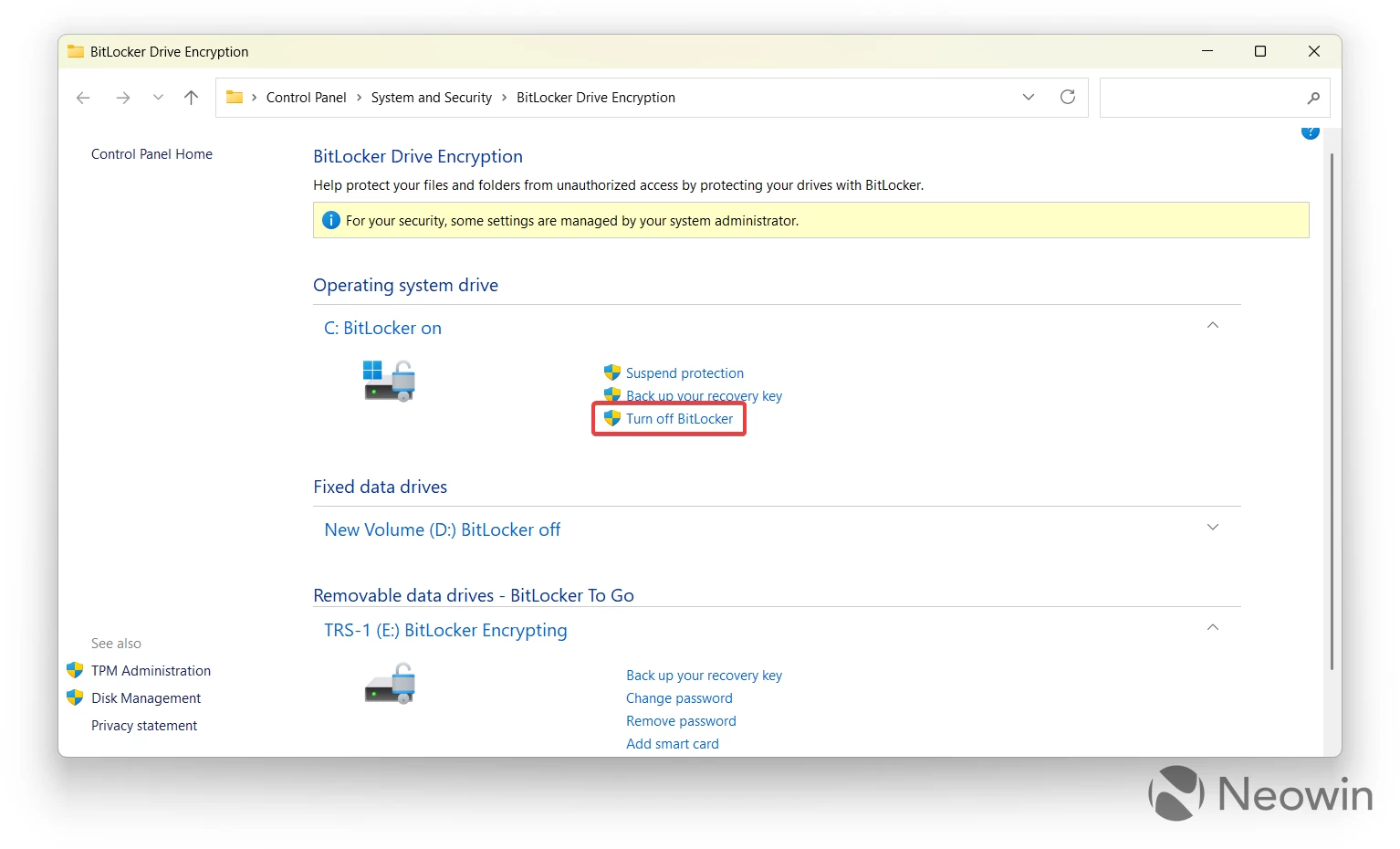
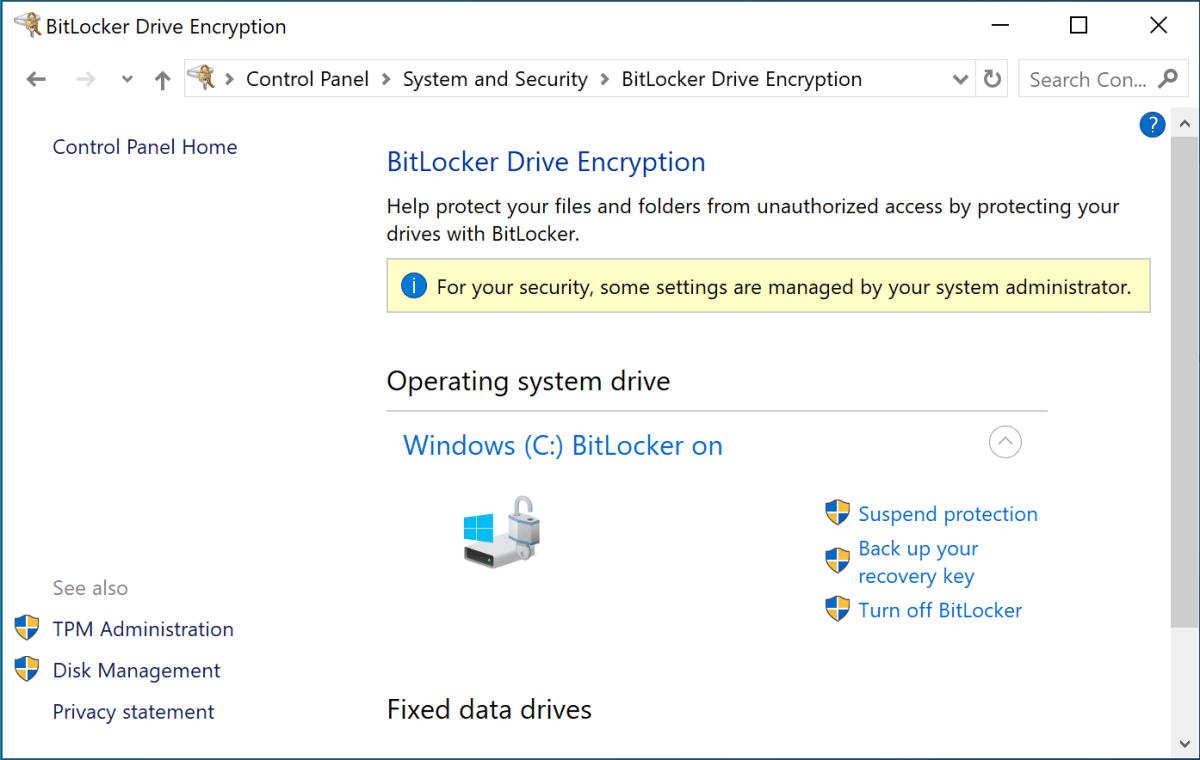
Go back to Settings. Privacy & Security. Device encryption. Now the toggle is OFF. But you'll notice there's another option in the same screen: "BitLocker drive encryption." This is a button (though it's styled as a link) that says "Manage BitLocker." Click it.
What you'll see next is jarring if you're used to the modern Windows 11 interface. The Settings app closes and a Control Panel window opens. This is the BitLocker settings panel from Windows Vista. It hasn't been substantially updated in nearly 20 years. The styling is ancient. The interface is clunky. But it works, and it gives you access to the granular encryption settings you actually need.
Microsoft has never bothered to modernize this interface. It exists in Windows 11 because removing it would break existing tools and workflows. So here it sits, a relic from the Windows Vista era, running alongside the sleek new Settings app. It's a perfect example of how even massive operating systems accumulate technical debt.
The BitLocker Management window shows you all your drives. You'll see your C: drive (your main Windows partition) and possibly other internal drives if you have them. External drives won't show up here, only internal ones.
Next to each drive, you'll see a "Turn on BitLocker" option. Click it for your C: drive. This starts the encryption wizard that will let you choose where to store your recovery key.
Choosing Your Recovery Key Storage Method
This is the whole reason you've been following along. This is where you actually get to choose something other than "store it with Microsoft."
When you click to turn on BitLocker, you'll get a wizard with several options for your recovery key:
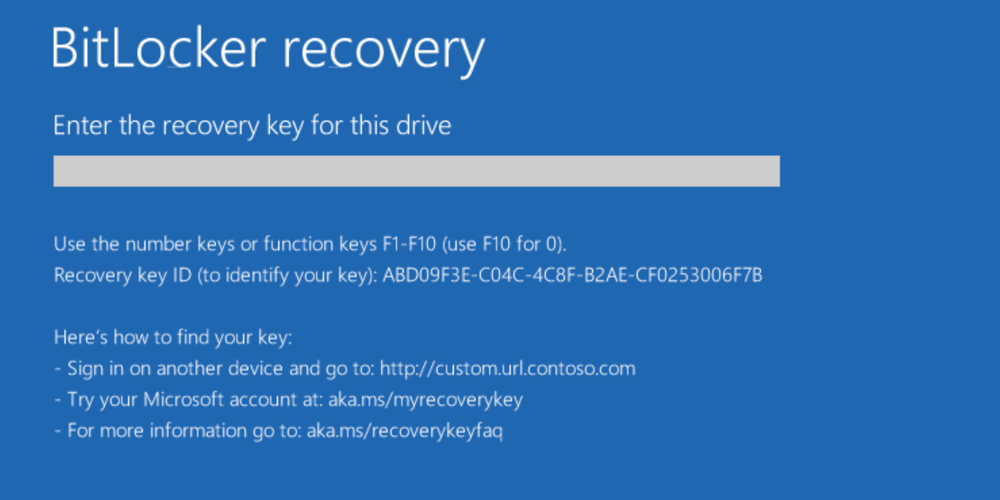
Print the recovery key: You can print it out right then and there. Windows generates a unique 48-character code (usually presented in 6 groups of 8 characters). You print this, you put it in a safe, you're done. This is genuinely secure. A piece of paper in your safe can't be hacked by anyone with a warrant. It also can't be accessed if your house burns down. This is the nuclear option of recovery key storage.
Save it to a file: You can save your recovery key as a text file on a USB drive, an external drive, or another location. This is actually the most practical option for most people. You save the 48-character key to a file, put that file on a USB drive, label it clearly ("BitLocker Recovery Key - [Date]"), and store it somewhere safe. Not on your computer. Not in your cloud storage. On a physical device that you control.
Save it to your Microsoft account: This is the default option, and it's what you're trying to avoid. You'll see this option, but don't click it.
Save it to an Azure AD account: If you use a work or organizational Microsoft account tied to Azure Active Directory, you can save it there instead of your personal account. This is still not ideal if you're trying to avoid Microsoft, but it's at least not sending it to Microsoft's consumer cloud.
Choose one of the first two options. Print your recovery key or save it to a USB drive. Actually do this, not "I'll do it later." Right now. You'll want that recovery key in your possession before you finish the encryption setup.
One important thing: after you create the recovery key, Windows will ask you to confirm you've saved it somewhere. Don't lie about this. If you say you've saved it but you haven't, and then something goes wrong with your drive, you'll be locked out of your own computer. The recovery key is your lifeline. Treat it seriously.
The Re-Encryption Process and What to Expect
Once you've confirmed your recovery key storage, Windows will start the actual re-encryption. You'll get a progress bar, and it'll tell you this will take a while (again with that vague language).
Unlike the decryption process, re-encryption can happen while you use your computer. You can work, browse, do normal things. The process will run in the background. It's just slower. Your system will be noticeably less responsive. Programs will take longer to open. Files will take longer to access. This is normal and expected.
Because of these performance implications, the best time to do this is overnight or when you don't need your computer. Start it before bed, let it run for several hours, and you'll wake up with a fully encrypted drive.
You can check the progress by going back into the BitLocker settings and looking at the drive status. It'll show you a percentage. Sometimes the percentage seems stuck for a while. That's fine. It's still working. The operating system is doing other things too, so sometimes the background encryption work gets paused momentarily.
During this process, don't restart your computer. Don't put it to sleep (well, sleep is fine, encryption continues). Don't unplug it. Just let it work.
Once encryption is complete, you'll notice the performance returns to normal. Your drive is now encrypted, and your recovery key is stored wherever you chose to store it. Not with Microsoft. You control it.
Verifying Your Encryption Status and Recovery Key
After re-encryption completes, you want to verify that everything worked as intended. Go back to Settings > Privacy & Security > Device encryption. The toggle should now be ON. That's good. Your drive is encrypted.
Now look at the recovery key information. Where does it say your key is backed up? It should say something like "stored on a removable drive" or "backed up as a file" or similar. It should NOT say "saved to your Microsoft account." If it does, something went wrong. You'd need to go through the decryption and re-encryption process again.
If the storage location is correct, you're done. Seriously, that's it. Your drive is encrypted, your recovery key is stored locally, and you've got privacy control back.
The only remaining task is to keep that recovery key safe. Put it somewhere secure. Some people laminate their printed recovery key. Some people store it in a safe deposit box at a bank. Some people keep a USB drive with the recovery key in a secure location separate from their computer. The exact method doesn't matter. What matters is that it's somewhere you can access it if needed, but somewhere that's not going to get lost or damaged.
Write down the date you created the recovery key. Write down what computer it's for (if you have multiple). Put this information with the key itself. Future you will be grateful.

What If You Have Multiple Internal Drives?
If your computer has multiple internal drives—not external drives, but actual separate drives physically installed in your computer—you can encrypt each one separately with BitLocker. The process is identical to what we've described, just repeated for each drive.
Go back to the BitLocker Management panel. You'll see all your internal drives listed. For each one you want to encrypt, click "Turn on BitLocker" and go through the recovery key process. You can use the same recovery key for multiple drives or different keys for each one. Technically, different keys are more secure (if one key is compromised, only one drive is at risk), but one recovery key that works for all drives is more convenient.
You'll need to make this choice for each drive. And yes, encryption happens sequentially. You can only encrypt one drive at a time. If you have three drives, you're looking at 3-6 hours of total encryption time depending on drive sizes and speeds.
Hardware Changes and BitLocker Suspension
Here's something important to understand: if you make certain hardware changes to your computer, BitLocker will suspend or require re-authentication.
The specific changes that trigger this vary, but common ones include upgrading your CPU, replacing your motherboard, or significantly changing your system configuration. Windows does this as a security measure. The idea is that someone physically stealing your hard drive can't just plug it into another computer and access it (without your recovery key or password).
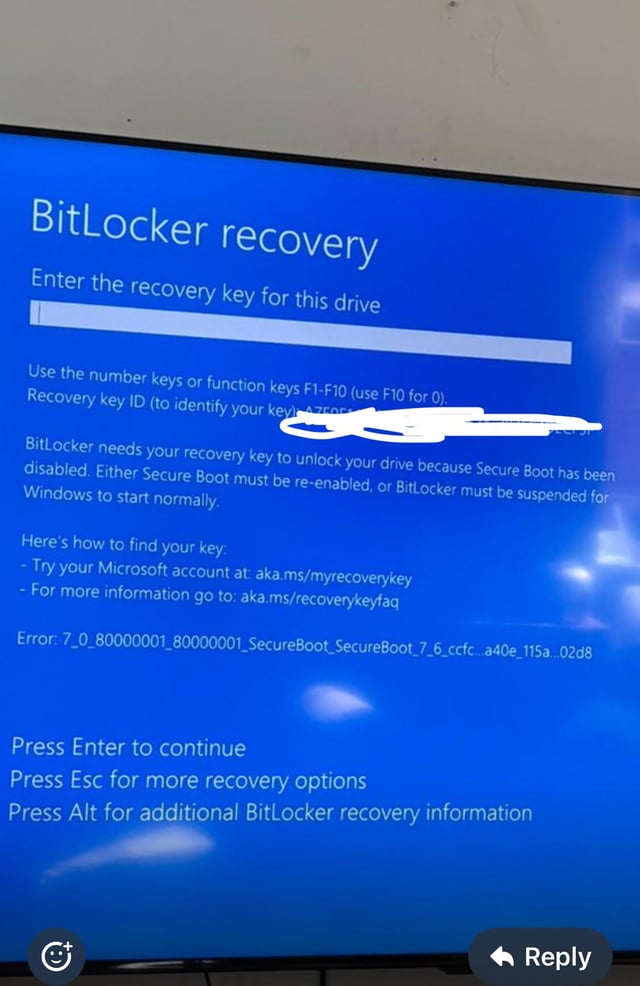
When BitLocker detects that the system it's running on has changed significantly, it requires you to provide the recovery key before Windows will boot. This is exactly what your recovery key is for. You provide it, Windows verifies you have the correct key, and you get access to your drive on the new system configuration.
This is why having that recovery key is so important. If you lose it and your hardware changes, you're genuinely locked out. Your data is still there, encrypted and safe, but you can't access it without the key.
Microsoft's solution for people who kept their recovery key on their servers was that they could always recover it. You go to account.microsoft.com, log in, and retrieve your recovery key even if your computer isn't working. Without that option, your recovery key is solely your responsibility.
So please, keep that recovery key safe.
Temporary Suspension of BitLocker
There's also a temporary suspension feature. If you know you're going to make hardware changes and you want BitLocker to not trigger its security checks during the process, you can temporarily suspend BitLocker.
Go into the BitLocker settings, find your drive, and look for the "Suspend protection" option. This tells BitLocker: "Hey, I know I'm about to make some hardware changes. Don't freak out." BitLocker stops enforcing its checks for a period of time (usually until the next restart), allowing you to make your hardware changes without triggering the recovery key requirement.
Once you've made your hardware changes and your system is stable, you can resume BitLocker protection. BitLocker will turn back on and resume its normal security checks.
This is useful if you're upgrading components but want to avoid the hassle of providing your recovery key multiple times during the upgrade process. Just suspend before you start, make your upgrades, resume when you're done.
What About Older Versions of Windows?
If you're still running Windows 10 Pro, this same process works. BitLocker is available in Windows 10 Pro just like it is in Windows 11 Pro. The settings paths are slightly different (it might be in Control Panel rather than the Settings app), but the options and functionality are the same.
Windows 10 Home edition has the same limitation as Windows 11 Home: you can't manage BitLocker settings yourself. If you want to upgrade Windows 10 Home to Pro, Microsoft charges $99 just like Windows 11. The same third-party reseller options exist.
If you're running Windows 7, Windows 8, or anything older than Windows 10, you're out of luck. BitLocker is still there if you're on Pro edition, but it's less user-friendly and the recovery key management isn't as straightforward. The honest answer is that if you're on Windows 7 or earlier and you care about this, you should probably upgrade your operating system anyway. Windows 7 especially is genuinely insecure at this point.
Alternative Encryption Tools if You Want Third-Party Options
This entire article has focused on BitLocker because it's free, built in, and frankly, quite good. But if you're the type who doesn't trust Microsoft even with local key storage, you do have alternatives.
VeraCrypt is an open-source full-disk encryption tool. It's free, well-respected by security professionals, and completely independent of Microsoft. You encrypt your drive, you manage your keys, nobody else gets involved. The downside is that it's less integrated into Windows and it's significantly less user-friendly than BitLocker.
DiskCryptor is another open-source option, similar in philosophy to VeraCrypt.
BitLocker with TPM disabled is actually another option if you want to use BitLocker but remove its dependency on your system's TPM (Trusted Platform Module). This requires some technical knowledge and command-line work, but it's possible.
The trade-off with all of these alternatives is integration and ease of use. BitLocker is built into Windows. Your recovery works smoothly. Your hardware changes are handled gracefully. Third-party tools work, but they require more manual management.
For most people, BitLocker with local recovery key storage is the right answer. It gives you the security and privacy you want without sacrificing ease of use.
The Ongoing Debate: Privacy, Law Enforcement, and Encryption
Zoom out for a moment. Why does this matter? Why does the location of a recovery key create such a difference?
Because of the broader encryption debate happening at government, corporate, and social levels. Law enforcement agencies worldwide have been arguing that strong encryption prevents them from investigating crimes. They want backdoors. They want government access to encryption keys. They want the ability to unlock devices with court orders.
Privacy advocates and security experts argue that backdoors in encryption benefit criminals and authoritarian governments far more than they benefit legitimate law enforcement. A backdoor doesn't just work for the good guys. If it exists, it can be exploited.
Microsoft's approach to BitLocker sits in the middle. The encryption itself is strong. No backdoor exists. But the recovery key can be accessed with a warrant. It's not quite as restrictive as a true backdoor (which would allow access without the recovery key), but it's not as private as having no key stored with any third party.
Other companies have taken different approaches. Apple claims (credibly, based on what security researchers have found) that some of its encryption keys are stored in ways even Apple can't access. End-to-end encrypted messaging services like Signal simply don't store the keys on any server.
The point is this: if privacy matters to you, you need to be intentional about it. Privacy doesn't happen by default in most software and services. It happens when you opt in, configure things correctly, and make conscious choices.
Storing your BitLocker recovery key locally instead of uploading it to Microsoft is one of those intentional choices. It's not a perfect solution. It's not a guarantee that someone won't find a way to access your drive. But it removes one specific vector of access: the ability for Microsoft to hand over your recovery key on demand.
For many people, that's sufficient. For others, it's not enough, and they'll pursue additional security measures. Either way, understanding that the choice exists is the first step.
Troubleshooting Common Issues
What if something goes wrong? What if decryption fails? What if BitLocker won't re-enable?
Decryption seems stuck: Sometimes Windows pauses the background decryption task while doing other work. It's genuinely still happening, just slowly. If the percentage hasn't changed in several hours, try restarting your computer. This sometimes kicks the process back into gear.
BitLocker won't turn on: Make sure you actually have Windows Pro, not Home. Make sure Device encryption is actually OFF before trying to turn on BitLocker. Sometimes Windows gets confused if both settings are enabled simultaneously.
You're prompted for recovery key on startup: This might happen if BitLocker thinks your system has changed significantly, or if there's been a failure during encryption. You'll need your recovery key to boot. If you don't have it, you're locked out. If you do have it, provide it and Windows will boot normally.
Performance is terrible during encryption: Yes, this is expected. Encrypting an entire drive is computationally intensive. Your system will be slow. This is normal.
You forgot where you saved your recovery key: If it's on a USB drive, go through your drives and look for the file. If you printed it, check your printer's output tray and your desk. If you saved it in a folder and forgot, search your computer for files containing your recovery key code (if you remember any of it). This is why organizing and labeling your recovery key matters.
Making BitLocker a Regular Part of Your Security Routine
Once BitLocker is enabled with your recovery key backed up locally, you should make certain things part of your regular security practice.
Every time you create a new recovery key (which happens when you suspend and resume BitLocker, or if you regenerate keys), save the new key to a secure location. Organize your old keys so you know which key goes with which point in time. If you ever have to actually use a recovery key, you want to use the correct one for your current drive state.
If you have that USB drive with your recovery key, keep it in a safe place but check on it occasionally. USB drives can fail. The data can degrade over time, especially in poor storage conditions. Periodically verify that your recovery key file is still readable.
If you have a printed recovery key, store it in a way that protects it from moisture, heat, and physical damage. A laminated copy in a safe is ideal. A copy stuffed in a drawer next to food and beverages is not.
Consider what happens if your house burns down or you move. Your recovery key needs to travel with you or be accessible from wherever you are. If your laptop gets stolen and you have a recovery key locked in a safe in a house that burns down, that recovery key is useless.
These aren't sexy considerations. But they're important when you're managing the keys to your encrypted drives.
The Future of Encryption in Windows
Microsoft isn't done with BitLocker. The company continues to develop the feature, adding TPM integration to improve security, expanding support to Home editions (though still without key management), and integrating it more deeply with Windows 11's security features.
What's unlikely to change is the fundamental choice: if you want to use automatic, seamless disk encryption without any manual key management, you accept that your recovery key gets backed up to Microsoft's servers. If you want complete key control, you opt into the manual process we've described.
This trade-off between convenience and control is unlikely to shift. It's actually how most of the tech industry operates. Easier usually means less control. More control usually means more complexity. The two things rarely come together perfectly.
Microsoft is betting that most users will accept the convenience trade-off. And statistically, they're probably right. Most Windows users don't care where their recovery key is stored. Most people never change hardware significantly enough to trigger BitLocker's recovery key requirement. Most people never face a warrant for their encryption keys.
But for people who do care, or who do face these situations, or who simply want to sleep better at night knowing their encryption keys aren't in someone else's database, this process exists. It's built in, it's free, and it works.
FAQ
What exactly is BitLocker recovery key storage and why does it matter?
Your BitLocker recovery key is a 48-character code that can unlock your encrypted drive if the normal decryption fails or if Windows detects significant hardware changes. If Microsoft stores this key on their servers, they can potentially hand it over to law enforcement with a warrant, effectively giving authorities access to unlock your drive. Storing it locally means you control the only copy, eliminating this specific surveillance vector.
Can I use Windows 11 Home edition to store recovery keys locally?
No. Windows 11 Home edition doesn't give you any control over BitLocker encryption settings. It automatically encrypts your drive if you're signed in with a Microsoft account, and the recovery key automatically goes to Microsoft's servers with no options to change it. You must upgrade to Windows 11 Pro ($99 from Microsoft) or use a Windows Pro product key to get this functionality.
How long does it actually take to decrypt and re-encrypt a drive?
The time depends on your drive size and storage speed. A 256GB SSD typically takes 30 to 45 minutes for decryption and a similar amount of time for re-encryption. A 1TB drive could take 2 to 4 hours for each process. Mechanical hard drives take significantly longer. Plan on 3 to 8 hours total, and don't restart your computer during this time. Start the process before bed or during a period when you don't need your computer.
What should I do if I lose my recovery key?
If your recovery key is lost and your system hardware changes, you'll be locked out of your drive. You cannot recover a locally-stored recovery key without the physical file or printout. This is why it's critical to store your recovery key in multiple locations (printed copy, USB backup, etc.) and in a secure place. If you truly lose it and get locked out, you'll need to contact Microsoft support or use Windows' recovery options, though your data recovery options will be severely limited.
Can I use the same recovery key for multiple drives?
Technically yes, you can use the same recovery key code for multiple drives during encryption setup. However, each drive can be configured with a different recovery key, which provides better security (if one key is compromised, only one drive is at risk). Most people opt for one recovery key per system for simplicity, but understand that this means a single compromised key could unlock multiple drives.
What happens if I make hardware changes after encryption?
If you replace major components like your CPU or motherboard, Windows recognizes the system configuration has changed and will require you to provide your recovery key before allowing normal boot. This is a security feature to prevent stolen drives from being accessed on different systems. You simply provide your recovery key when prompted, and Windows verifies it, then boots normally. If you know you'll be making hardware changes, you can temporarily suspend BitLocker protection through Settings, make your changes, then resume protection.
Is BitLocker encryption actually secure, or does it have known vulnerabilities?
BitLocker uses AES-128 or AES-256 encryption (depending on your configuration) and is considered cryptographically sound. There are no known practical attacks against the encryption algorithm itself. The security concerns aren't about BitLocker's encryption being weak—it's strong—but about where the recovery key is stored and who can access it. Local recovery key storage doesn't change BitLocker's encryption strength; it just removes Microsoft as a third party that could access your key.
Should I also use third-party encryption tools like VeraCrypt?
If your primary concern is keeping Microsoft out of the equation entirely, third-party tools like VeraCrypt provide that. However, they're less integrated with Windows, require more manual management, and are generally less user-friendly. For most people concerned about recovery key access, using BitLocker with local key storage provides an excellent balance of security and usability. Use third-party tools only if you have specific advanced requirements or ideological objections to using Microsoft's tools.
Bottom Line: Privacy Is a Choice, Not a Default
Here's the hard truth nobody likes hearing: privacy on Windows requires opt-in. It requires knowledge. It requires action. If you do nothing and just use Windows the way Microsoft sets it up, you're implicitly accepting that your encryption recovery key goes to Microsoft's servers. No judgment—most people are fine with that trade-off.
But if you're not fine with it, if you want to encrypt your drive without Microsoft holding your recovery key, you can. You've got a path. You need Windows Pro (not cheap, but necessary). You need to manually decrypt and re-encrypt your drive (takes time, but doable). You need to keep your recovery key safe (requires responsibility, but it's just a file or a piece of paper).
The good news is it works. The encryption is strong. The process is free once you've bought Windows Pro. And you end up with a system where you control the keys to your own data, and nobody—not Microsoft, not law enforcement without a recovery key in hand—can unlock your drive without it.
That's real privacy. Not theoretical privacy, not "trust us we don't actually look at your data" privacy. Real, actual privacy where the technical reality matches the promise. It takes some work to get there, but it's entirely possible with Windows 11 Pro.
Start with the edition check. See if you're actually running Pro. If not, plan your upgrade. Then set aside a few hours when you don't need your computer, follow the steps we've outlined, and take control of your own encryption. Future you—especially future you facing unexpected questions from authorities—will be grateful.
Privacy isn't given. It's taken. And this is one of the most straightforward ways to take it back.

Key Takeaways
- Windows 11 Home edition automatically encrypts drives but forces recovery keys to Microsoft servers; Windows Pro gives you full control.
- Decryption and re-encryption of existing encrypted drives takes 1-2 hours per step depending on drive size, but is necessary to change recovery key storage.
- Recovery keys can be stored as printed copies, USB drive files, or in Microsoft's servers, but only local storage prevents company access with warrants.
- FBI and law enforcement agencies make 15-30 BitLocker recovery key requests annually to Microsoft, emphasizing the real surveillance implications of cloud-stored keys.
- Proper recovery key management requires multiple secure backups since losing the key means potential permanent data lockout if hardware changes trigger re-authentication.
![Encrypt Your Windows PC Without Sharing Keys With Microsoft [2025]](https://tryrunable.com/blog/encrypt-your-windows-pc-without-sharing-keys-with-microsoft-/image-1-1769452633587.jpg)



