How to Check if Your VPN Is Working [2025]
You installed a VPN, hit connect, and now you're assuming you're protected. But here's the thing: most people have no idea whether their VPN is actually doing its job. The app says "connected." The interface shows a green checkmark. But is your data really encrypted? Is your real IP address actually hidden? Or is the VPN silently leaking your identity through a backdoor you don't even know exists?
I've tested this scenario more times than I'd like to admit. A VPN app claims it's working perfectly while DNS requests are sailing straight to your ISP unencrypted. Web RTC vulnerabilities are exposing your real IP address. IPv6 leaks are happening in the background. And you're sitting there thinking you're anonymous when you're actually broadcasting your location to anyone paying attention.
The gap between a VPN that appears to work and one that actually protects your privacy is razor-thin. And closing that gap requires understanding what can go wrong, then running the right tests to catch problems before they compromise your security.
In this guide, I'm going to walk you through seven different verification methods. Each one checks for a different failure point. Some catch obvious problems. Others expose subtle vulnerabilities you'd never notice without the right tools. By the time you're done, you'll know exactly whether your VPN is doing what it promised.
TL; DR
- Check basic connection status first: Most VPN apps display connection status with indicators like "Connected" and server location, but this is only the first step
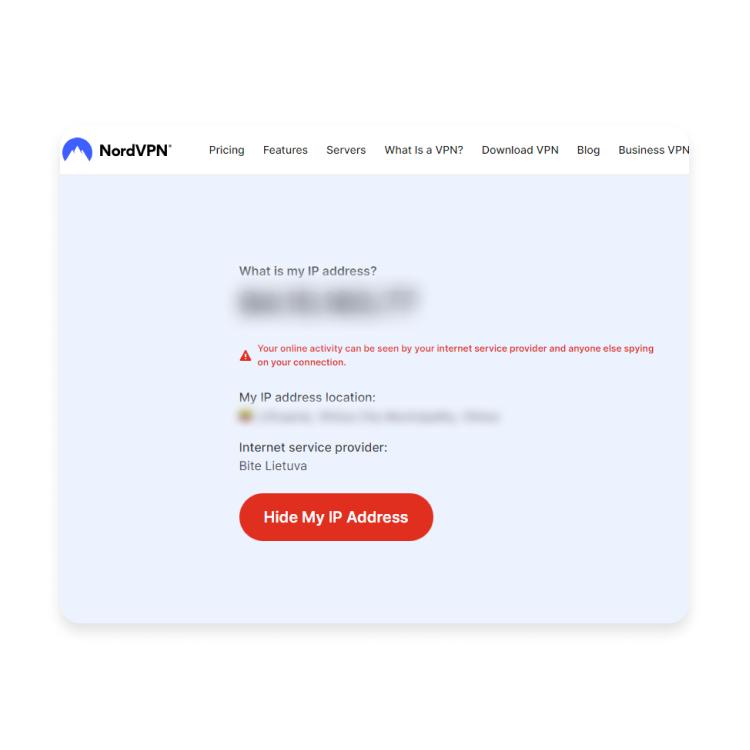
- Your IP address must change: Use whatismyipaddress.com to confirm your visible IP matches your VPN's server location, not your true ISP location
- DNS leaks expose your ISP: Test with dnsleaktest.com to ensure all DNS queries route through your VPN, never directly to your ISP
- Web RTC vulnerabilities leak real IP: Run Web RTC leak tests on ipleak.net to prevent browser exploits from bypassing your VPN tunnel
- IPv6 can undermine encryption: Disable IPv6 in your browser settings or verify no IPv6 leaks appear in leak tests
- Fix problems systematically: Start with reconnecting, then try different servers, VPN protocols, clear DNS cache, and restart devices
- Bottom line: A working VPN requires passing all seven tests, not just showing "connected" in the app
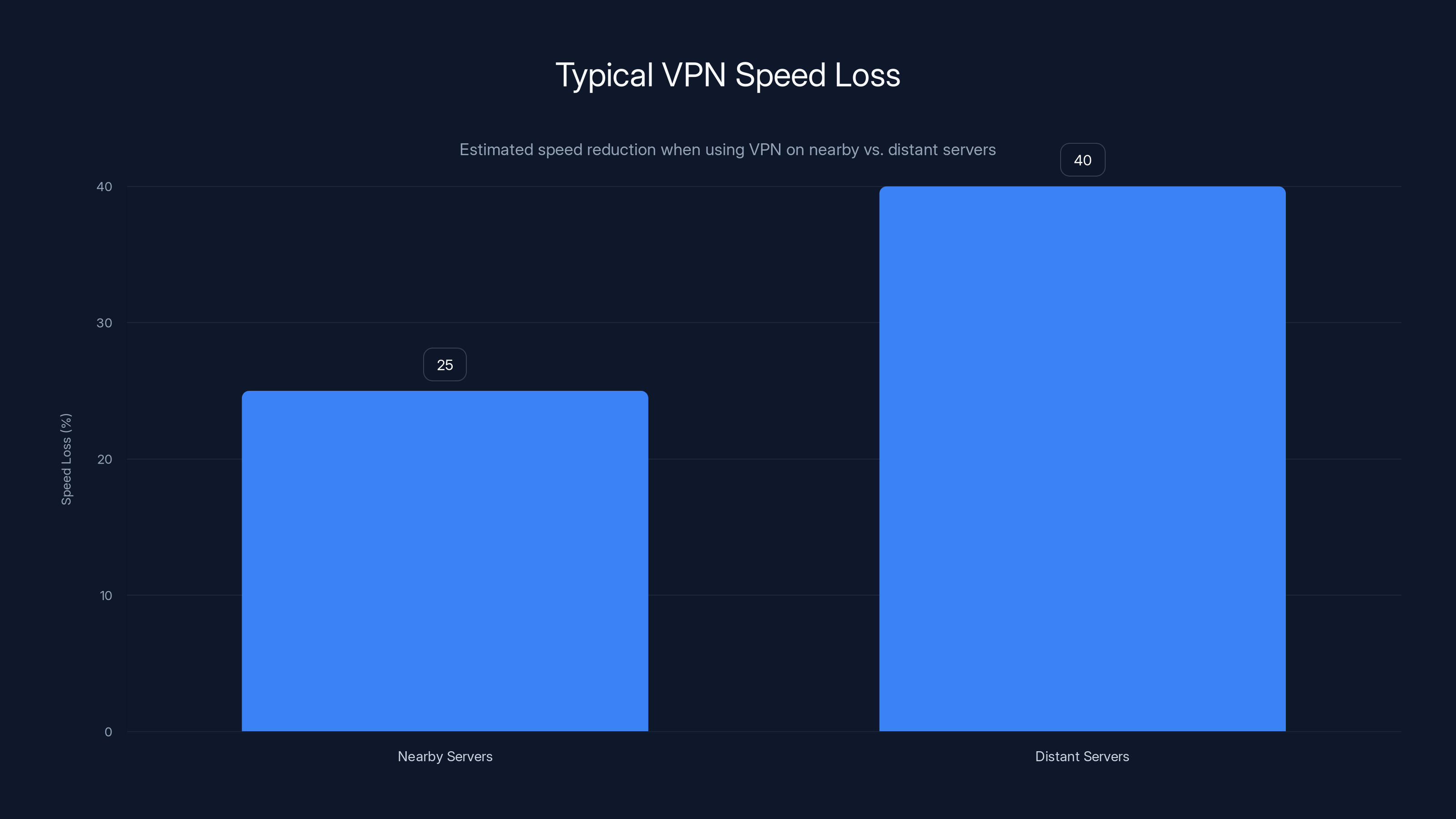
Using a VPN typically results in a 20-30% speed reduction for nearby servers and 30-50% for distant servers. Estimated data.
Step 1: Verify Your VPN App Is Actually Connected
Before running any technical tests, start with the simplest check: is your VPN actually turned on?
I know this sounds obvious, but you'd be surprised how often people forget this basic step. You open the app, browse through settings, pick a server, maybe configure some preferences, then close the window thinking you're done. Except you never actually hit the connect button. The app sits idle in the background while your traffic flows completely unencrypted.
This happens more often than you'd think, especially with mobile apps. You tap the VPN icon, the screen changes, and your brain assumes everything's working. But many VPN interfaces show the same screen whether connected or disconnected. The visual feedback isn't always obvious.
To verify you're actually connected, open your VPN app on your desktop or phone. Look for these telltale signs:
Connection indicators to look for:
- A green circle, green button, or green status light
- The word "Connected" displayed prominently
- The server location you selected showing as active
- A connection timer indicating how long you've been connected
- A toggle switch clearly in the "on" position
Different VPN providers design their apps differently. Cyber Ghost uses a massive connect button that turns green. Proton VPN displays "Connected" with a server location. Surfshark shows a power icon that illuminates when active.
The key is understanding your specific app's visual language. Some apps also show a system notification or icon in your taskbar when connected. Check there too.
For mobile users on iOS, the VPN status appears in your settings under VPN in the Settings app, showing "Connected" next to your VPN provider's name. Android displays a VPN icon in your notification bar at the top of your screen when connected. In both cases, a missing indicator means the VPN isn't active.
Once you've confirmed your VPN is actually connected, proceed to the remaining tests. Everything that follows assumes your VPN is in active "connected" status.
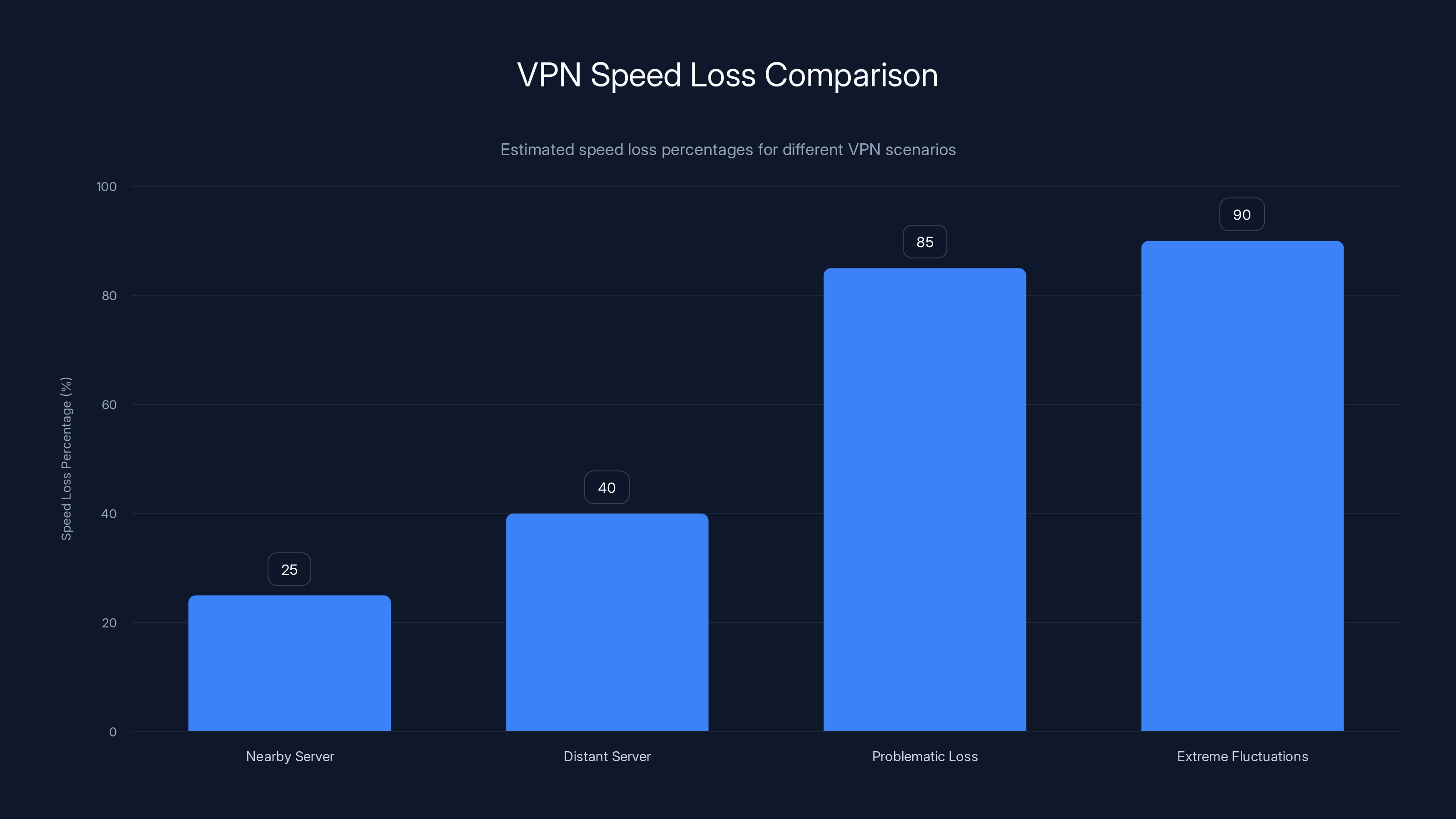
Estimated data shows typical speed loss percentages: 20-30% for nearby servers, 30-50% for distant servers, and problematic losses at 80%+.
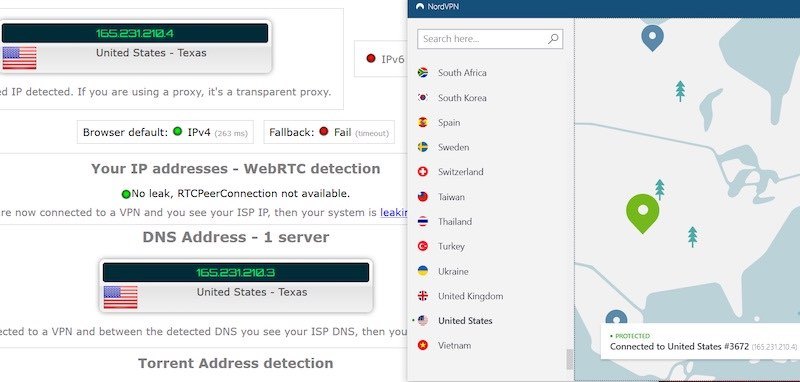
Step 2: Test Your IP Address Change
The most fundamental job of any VPN is changing your IP address. Your IP address is your digital fingerprint on the internet. It reveals your approximate location, identifies your internet service provider, and connects your online activities directly to you and your home or office.
A VPN's primary function is replacing your real IP address with one belonging to the VPN's server. If this isn't happening, nothing else matters. Your VPN is either completely broken or pretending to work while doing absolutely nothing.
Testing for IP address changes is straightforward. You need a baseline measurement of your real IP, then compare it against your VPN IP.
Here's the exact process:
- Disconnect your VPN completely and write down or screenshot everything from an IP checking tool
- Visit whatismyipaddress.com or ipleak.net and note your IP address, ISP name, and geographic location
- Write this down: Include the specific IPv4 address, the city where your ISP reports the connection originated, and the ISP provider name
- Connect to your VPN and remember which server location you selected
- Return to the same IP checking tool and refresh the page
- Compare the results: Your new IP should be completely different from step 2, and should match (approximately) the server location you connected to
What you're looking for is a complete IP address change. Not a partial change. Not a similar-looking IP. A fundamentally different IP address that maps to a different geographic location and different ISP.
What a successful test looks like:
- Without VPN: IP 73.45.120.88, ISP: Comcast, Location: Philadelphia, Pennsylvania
- With VPN (connected to Netherlands): IP 89.200.52.114, ISP: NL-Data, Location: Amsterdam, Netherlands
Notice the IP is completely different, the ISP is different, and the location is different. That's what you want to see.
What a failed test looks like:
- Without VPN: IP 73.45.120.88, ISP: Comcast, Location: Philadelphia, Pennsylvania
- With VPN: IP 73.45.120.88, ISP: Comcast, Location: Philadelphia, Pennsylvania
If your IP doesn't change, your VPN isn't working at all. This is a critical failure.
Troubleshooting IP address failures:
If your IP isn't changing, try these fixes in order:
-
Disconnect and reconnect: Wait 10 seconds after disconnecting, then connect again. Sometimes a failed handshake just needs a retry.
-
Try a different server location: Your current server might be overloaded or misconfigured. Switch to a different location and test again.
-
Switch VPN protocols: Most VPN apps let you change protocols (OpenVPN, WireGuard, IKEv2, etc.). Try a different one. Sometimes certain protocols fail on certain networks.
-
Clear your system cache: Your operating system might be caching the old connection. On Windows, open Command Prompt and run
ipconfig /flushdns. On Mac, open Terminal and runsudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder. -
Restart your device: A full reboot clears all active connections and caches. Restart your computer or phone completely.
-
Check your firewall or antivirus: Some security software blocks VPN connections. Temporarily disable it to test.
-
Try a fresh installation: Uninstall the VPN app completely, restart your device, then download and install a fresh copy.
If none of these work, contact the VPN provider's support team. An IP address that doesn't change indicates a fundamental connectivity problem.
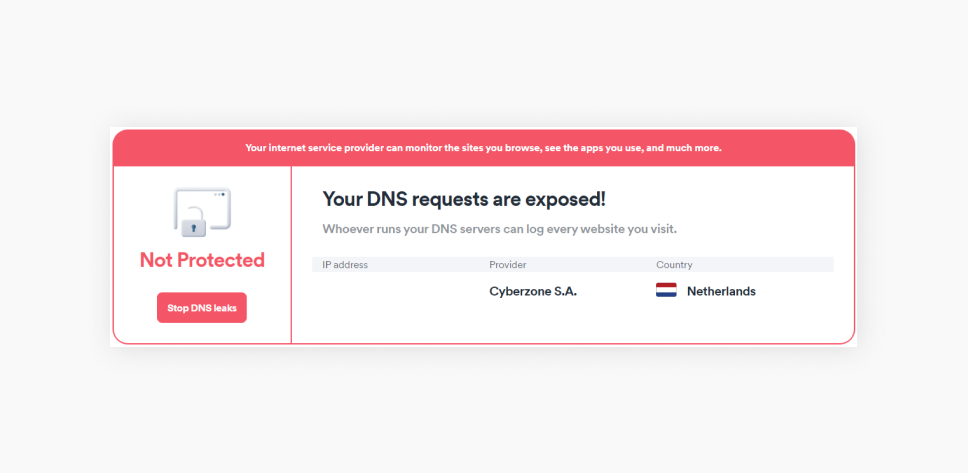
Step 3: Check for DNS Leaks
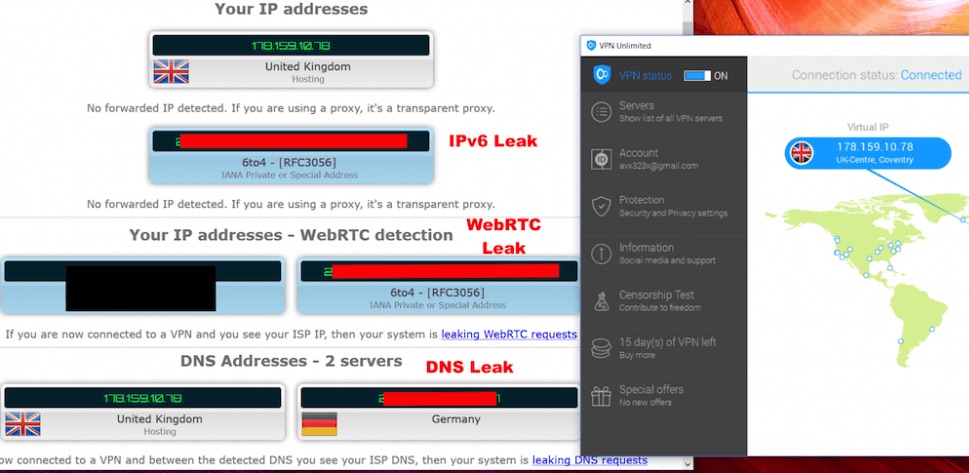
DNS leaks represent one of the most common ways VPNs fail while appearing to work perfectly.
Here's what's happening: When you type a website address into your browser (like example.com), your device needs to convert that human-readable domain name into an IP address. This lookup process is called a DNS query, and it gets sent to a DNS server.
Normally, your ISP provides your DNS servers by default. When you use a VPN, those DNS requests should be encrypted and routed through the VPN's servers. But sometimes they aren't. Sometimes your device bypasses the VPN entirely and sends DNS queries directly to your ISP's DNS servers.
When this happens, your ISP sees every single website you're trying to visit. The VPN hides your IP address, but your ISP knows exactly what websites you're accessing. This is a critical privacy leak.
A DNS leak test checks whether your DNS queries are being intercepted by your ISP or properly routed through your VPN.
Here's how to test for DNS leaks:
- Ensure your VPN is connected to a specific server
- Visit dnsleaktest.com (the most reliable DNS leak test)
- Click "Standard test" to run a basic DNS leak check
- Wait for results: The test sends several DNS queries and identifies which servers resolve them
- Examine the results: You should see only your VPN provider's DNS servers listed
- Look for your ISP name: If you see your ISP (like "Comcast" or "Verizon"), you have a DNS leak
What a passing test shows:
- All DNS servers belong to your VPN provider
- No mention of your ISP
- All locations match your selected VPN server location
What a failing test shows:
- Your ISP name appears in the results
- You see DNS servers you didn't specify
- Locations don't match your VPN's server location
DNS leak fixes:
If you detect DNS leaks, try these solutions:
-
Enable DNS leak protection: Most VPN apps have a setting for "DNS leak protection" or "DNS protection." Enable it in your VPN settings and test again.
-
Try a different VPN protocol: Some protocols are more prone to DNS leaks. Switch to OpenVPN or WireGuard and test again.
-
Disable IPv6 in your browser: IPv6 DNS leaks sometimes appear as regular DNS leaks. See Step 5 for IPv6 disabling instructions.
-
Clear your DNS cache: Follow the cache-clearing instructions from Step 2.
-
Try a different DNS server within your VPN: Some VPN apps let you specify which DNS servers to use. Try switching to your VPN's alternative DNS option.
-
Restart your router: Unplug your router for 30 seconds, plug it back in, reconnect to VPN, and test again.
Persistent DNS leaks indicate either a configuration problem in your VPN settings or a bug in your VPN app. Contact the provider's support team if problems continue.

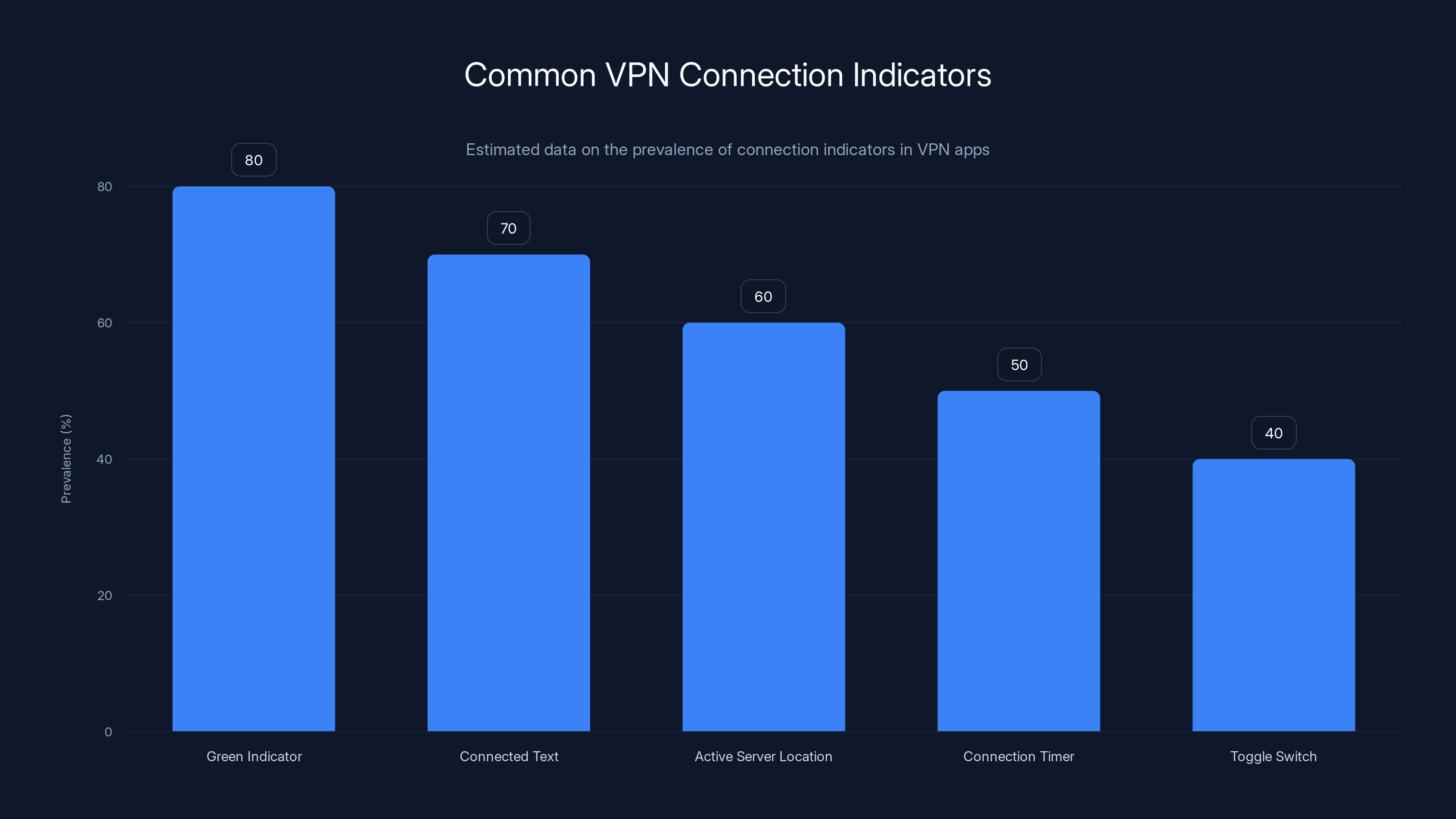
Estimated data suggests that green indicators and 'Connected' text are the most common signs of a VPN connection. Estimated data.
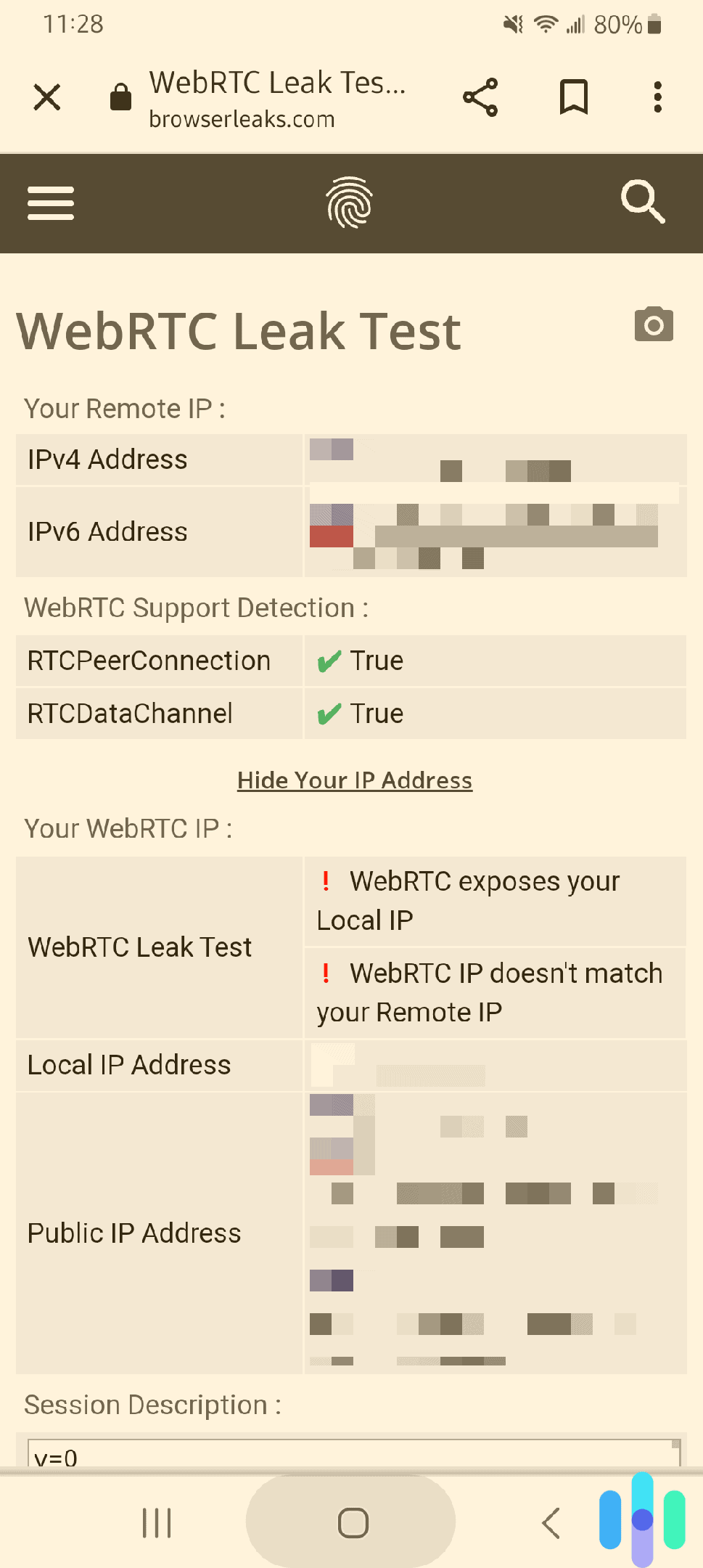
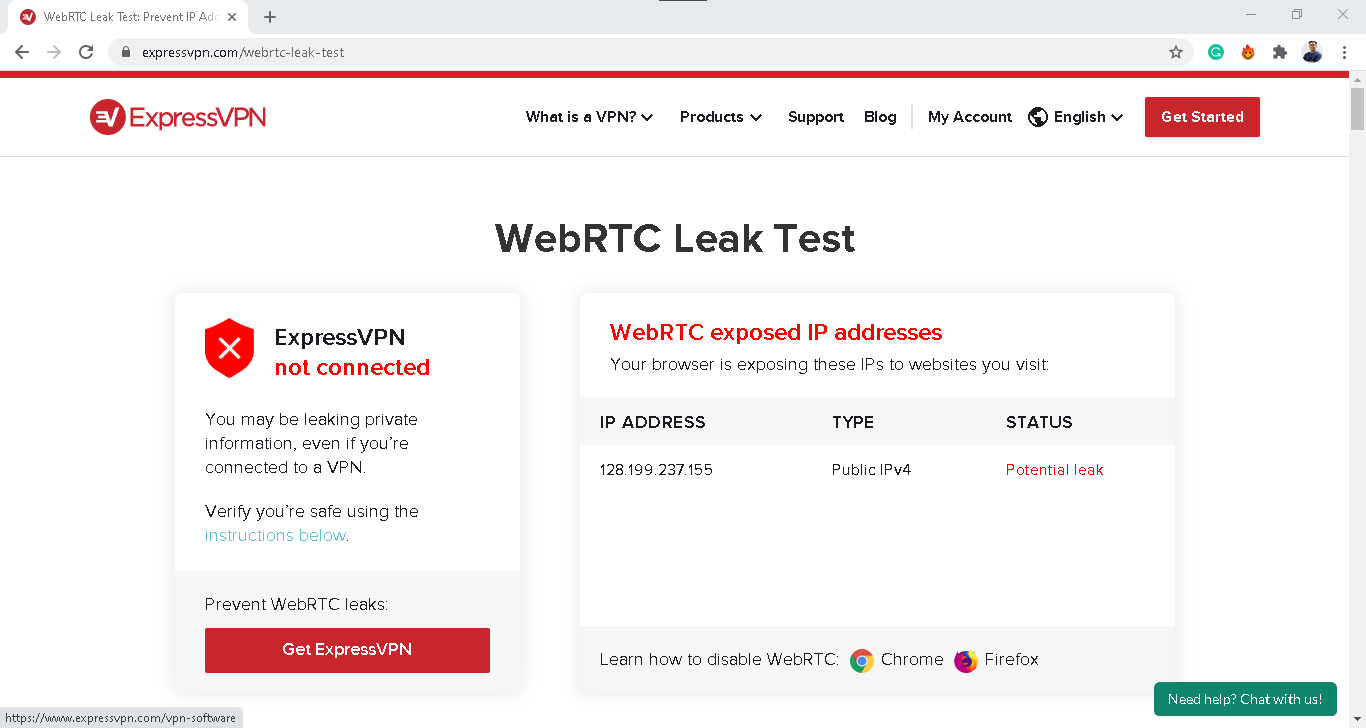
Step 4: Run a Web RTC Leak Test
Web RTC (Web Real-Time Communication) is a technology that lets web browsers communicate directly with each other. It powers video calls, voice chats, screen sharing, and peer-to-peer video streaming.
But Web RTC creates a privacy vulnerability. Browsers can leak your real IP address through Web RTC connections, even while a VPN is actively hiding it. This happens because Web RTC can communicate directly with remote servers without going through your VPN tunnel.
Imagine your VPN successfully routing all your web traffic through an encrypted tunnel. You're invisible online. But then a website uses Web RTC to establish a direct connection to its servers, and your browser automatically provides your real IP address as part of the connection setup. You're suddenly exposed.
Web RTC leaks are particularly problematic because they're invisible. Your VPN shows connected. Your IP test passes. But your real IP is being leaked constantly in the background.
How to test for Web RTC leaks:
- Ensure your VPN is connected to a specific server location
- Visit ipleak.net and scroll down to the "Web RTC Leak Test" section
- The test runs automatically: It attempts to detect your real IP through Web RTC
- Check the results: You should see only your VPN's IP address listed
- Look for your real IP: If your actual IP appears (the one from Step 2), you have a Web RTC leak
What a passing test shows:
- Only your VPN server's IP address
- No mention of your real ISP or location
- All IPs match the VPN server you selected
What a failing test shows:
- Your real IP address appears in the results
- A different ISP than your VPN provider
- Your actual geographic location (before you connected to the VPN)
Web RTC leak fixes:
-
Disable Web RTC in your browser: This is the most effective fix
- Chrome/Edge: Install a Web RTC leak prevention extension from the Chrome Web Store
- Firefox: Type
about:configin the address bar, search formedia.peerconnection.enabled, and toggle it to "false" - Safari: Web RTC control is built into settings under "Privacy"
-
Use your VPN's leak protection feature: Many VPN apps have "Web RTC leak protection" built in. Enable it and test again.
-
Try a different VPN protocol: Some protocols handle Web RTC better than others. Switch to WireGuard if available.
-
Use a dedicated Web RTC blocker: Browser extensions like "Web RTC Leak Prevent" (Chrome) or "IP Leak Protection" (Firefox) add extra safeguards.
-
Switch browsers temporarily: Test whether the leak happens in all browsers or just one. Some browsers are more vulnerable than others.
Web RTC leaks aren't always the VPN provider's fault. They're often browser vulnerabilities. Using both VPN and browser-level protections is your best defense.

Step 5: Detect IPv6 Leaks
IPv6 is the newer version of internet protocol technology, designed to replace the older IPv4 system. Most of the internet still runs on IPv4 (the IP addresses that look like 192.168.1.1 or 73.45.120.88). But IPv6 addresses (which look like 2001:0db8:85a3:0000:0000:8a2e:0370:7334) are becoming increasingly common.
Here's the problem: Many VPNs are optimized for IPv4 but don't properly handle IPv6 traffic. If your device is connected to an IPv6 network, your real IPv6 address might leak straight out of the VPN tunnel, potentially revealing your identity even though your IPv4 address is properly hidden.
You could pass all the IPv4 tests and still be exposing your real address through IPv6. This is a subtle but critical vulnerability.
How to test for IPv6 leaks:
- Connect to your VPN to a specific server
- Visit ipleak.net and scroll to the IPv6 Leak Test section
- Check your IPv6 address: The test shows whether you have an IPv6 address assigned
- Verify the origin: If an IPv6 address appears, it should belong to your VPN provider, not your ISP
- Compare locations: The IPv6 address should map to your selected VPN server location, not your actual location
What a passing test shows:
- No IPv6 address detected (if your ISP doesn't provide IPv6), or
- IPv6 address belongs to your VPN provider
- IPv6 location matches your VPN server, not your real location
What a failing test shows:
- Your real IPv6 address appears
- IPv6 address maps to your actual ISP and location
- Different ISP than your VPN provider
IPv6 leak fixes:
-
Disable IPv6 in Windows:
- Open Settings > Network & Internet > Status
- Click "Advanced network settings"
- Scroll down to "Advanced network settings"
- Click "More network adapter options"
- Right-click your network connection and select "Properties"
- Uncheck "Internet Protocol Version 6 (TCP/IPv6)"
- Click OK
-
Disable IPv6 on Mac:
- Open System Preferences > Network
- Select your active connection
- Click "Advanced..."
- Go to the "TCP/IP" tab
- In the "IPv6 Configuration" dropdown, select "Off"
- Click OK
-
Disable IPv6 in your browser:
- Most browsers don't have a direct IPv6 toggle
- Install a browser extension like "IPv6 Leak Shield"
- Or configure at the OS level (above)
-
Enable IPv6 leak protection in your VPN: Many VPN apps now have built-in IPv6 leak protection. Check your VPN settings.
-
Try a different VPN server: Some servers handle IPv6 better than others. Switch locations and test again.
IPv6 leaks are less common than DNS or Web RTC leaks, but they're potentially more damaging because fewer people know to test for them.

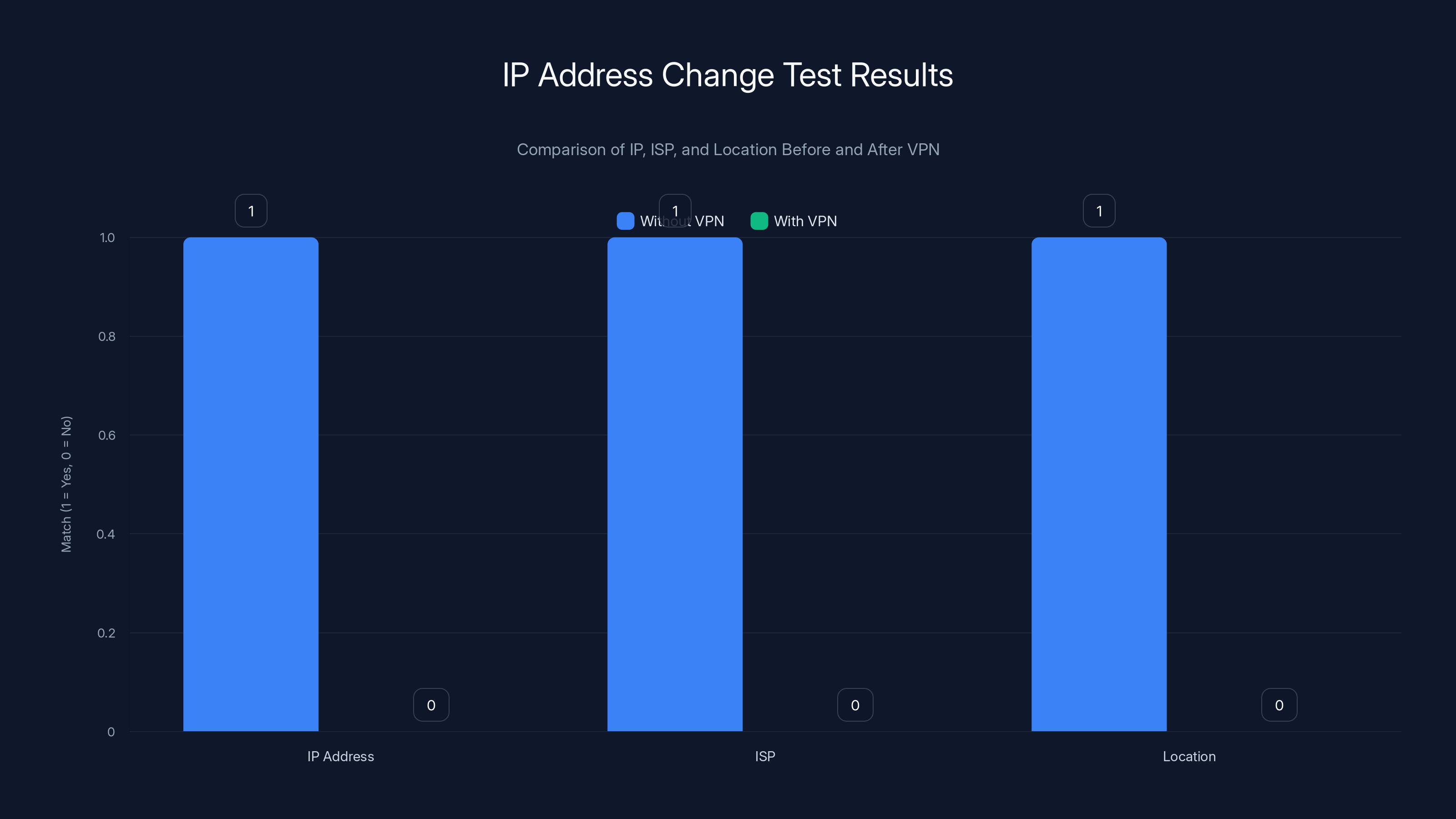
A successful VPN test shows a complete change in IP address, ISP, and location. Estimated data used for illustration.
Step 6: Verify Your Server Location Accuracy
Just because your VPN shows you're connected to a server in one location doesn't mean you actually are. VPN servers can be misconfigured, mislabeled, or spoofed.
A test that appears to show success (a different IP address) might actually be connecting you to a completely different location than advertised. If you think you're in France but actually connected to France's servers that are physically hosted in Russia, your privacy assumptions are wrong.
Verifying server location accuracy involves cross-referencing multiple data points.
How to verify server location:
- Connect to a VPN server in a specific location (note the location name)
- Go to whatismyipaddress.com and check the geographic location
- Note the reported city and country: This should match (approximately) your selected VPN location
- Cross-reference with an IP geolocation tool: Try ip-lookup.net or ipinfo.io for a second opinion
- Check the ISP name: It should match your VPN provider, not a different provider
Location accuracy matters because some countries have strict data laws. If you think you're connecting through a Swiss server (known for strong privacy laws) but you're actually connecting through a German server (different regulations), your assumptions about data protection are wrong.
What accurate server location shows:
- City and country match your selected VPN location (within reasonable margin)
- ISP belongs to your VPN provider
- Coordinates on the map show the correct country
- Multiple geolocation tools agree on the location
What inaccurate location shows:
- Reported city is 500+ miles from your selected location
- Different ISP than expected
- Map coordinates show a different country
- Geolocation tools disagree significantly
If you consistently see inaccurate server locations, contact your VPN provider. Some servers are mislabeled or misconfigured, and they should know about it.
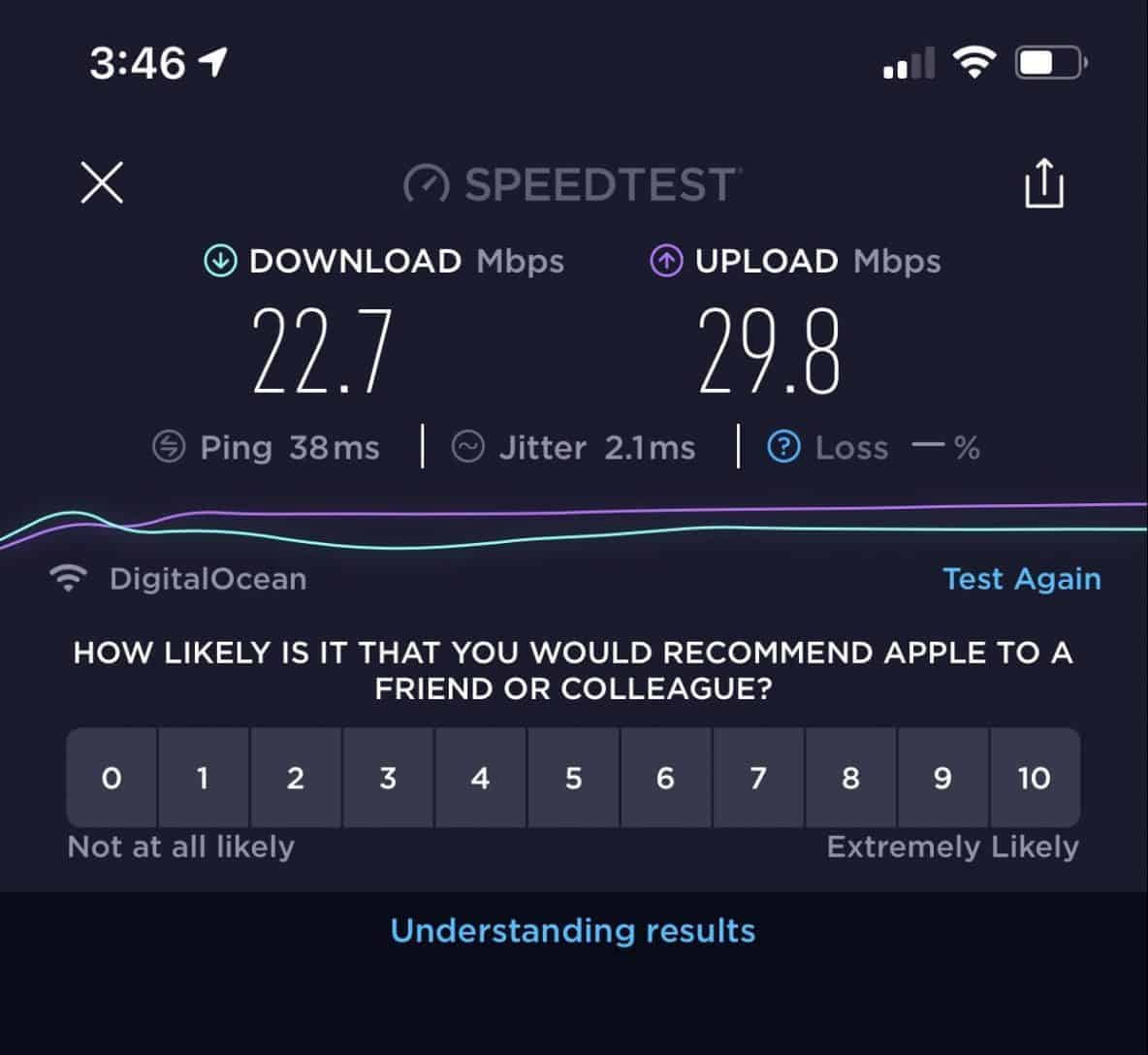
Step 7: Check for Bandwidth Throttling and Speed Loss
While not technically a "leak," extreme speed loss or throttling can indicate that your VPN isn't working properly. It might be leaking traffic, routing inefficiently, or experiencing server problems.
A properly functioning VPN typically causes some speed loss (usually 20-30% is acceptable). But if you're losing 80-90% of your speed, something's wrong.
How to test VPN speed:
- Disconnect from your VPN completely
- Run a speed test at speedtest.net or fast.com
- Note your baseline speed: Write down your download speed and upload speed
- Connect to your VPN on your normal server
- Run the same speed test again from the same website
- Compare the results: Calculate the percentage of speed loss
Formula for speed loss calculation:
For example:
- Baseline speed without VPN: 100 Mbps
- Speed with VPN: 70 Mbps
- Speed loss: (100 - 70) / 100 × 100 = 30% loss (normal and acceptable)
What normal speed loss looks like:
- 20-30% loss on nearby servers
- 30-50% loss on distant servers
- Consistent speeds each time you test
What problematic speed loss looks like:
- 80%+ loss consistently
- Extreme fluctuations (50 Mbps one test, 5 Mbps the next)
- Speeds improving dramatically when disconnected from VPN
- Timeout errors or failed connections
Troubleshooting speed problems:
-
Try a different server location: Distant servers are slower. Test a nearby one.
-
Switch VPN protocols: Some protocols are faster than others. WireGuard is typically fastest.
-
Restart your connection: Disconnect, wait 10 seconds, reconnect.
-
Check your internet connection: Run a speed test on regular internet. If it's slow, the VPN isn't the problem.
-
Disable VPN split tunneling: Some VPN apps route only certain traffic through the VPN. This can affect speeds inconsistently.
-
Restart your router: Unplug for 30 seconds and restart.
-
Try a wired connection: WiFi speed loss is normal. Test with Ethernet cable if possible.
Extreme, consistent speed loss might indicate server overload or a problem with your VPN provider. If issues persist, contact support.
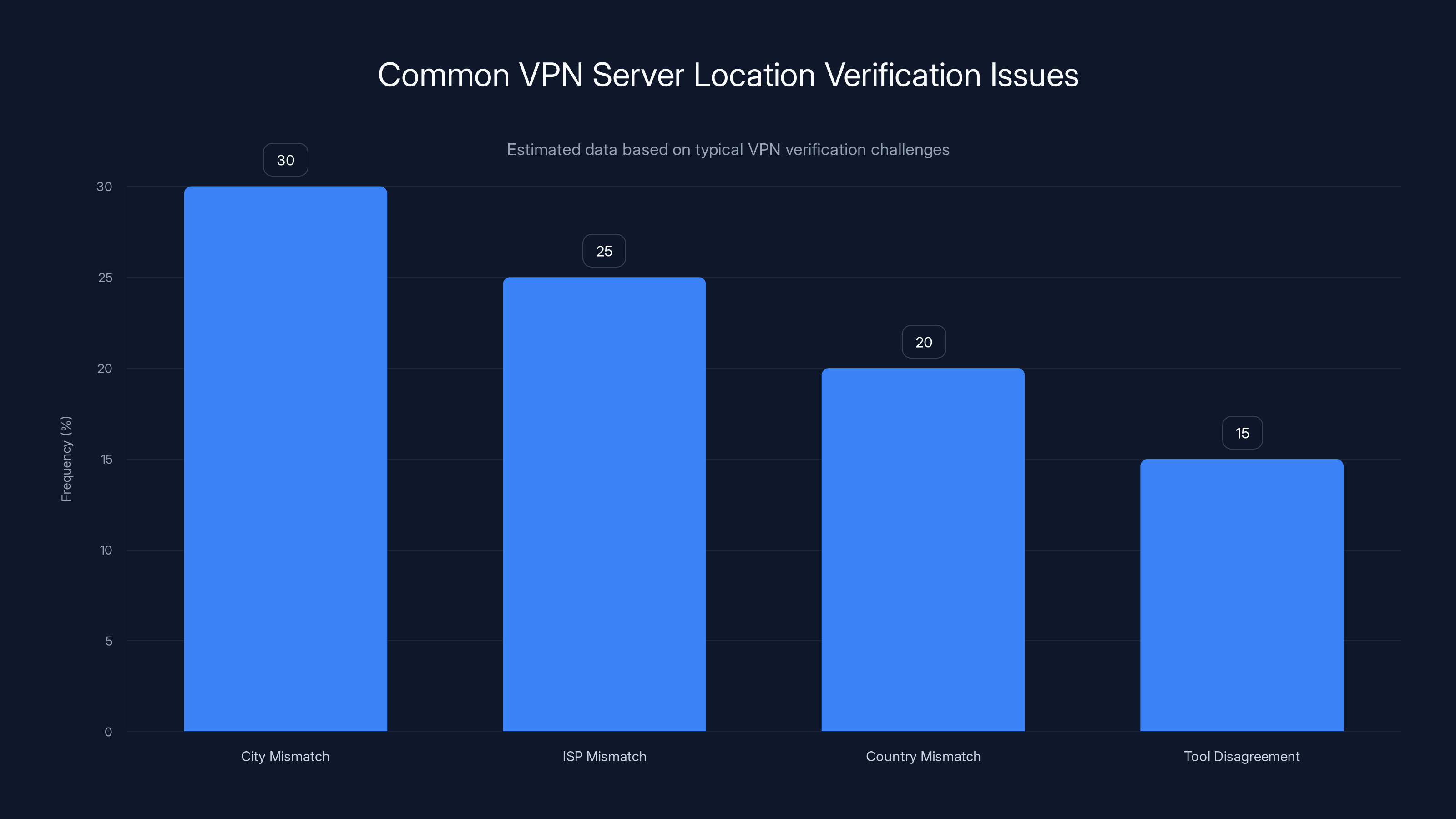
Estimated data shows city mismatch is the most common issue when verifying VPN server locations, followed by ISP mismatches.
Step 8: Review VPN App Logs for Connection Errors
Most VPN apps record detailed logs of every connection attempt, disconnection, error message, and reconnection. These logs are goldmines of diagnostic information.
If your VPN is failing sporadically, the logs will show exactly when and why. Connection refused. Timeout error. Protocol failure. Authentication error. The logs tell the real story your VPN app's UI might be hiding.
How to access VPN logs:
The process varies by provider. Here are common locations:
Windows:
- Most VPN apps store logs in
C:\Users\[Your Username]\AppData\Local\[VPN Provider Name] - Some store in
C:\Program Files\[VPN Provider Name]\logs - Check your VPN app's settings or help documentation
Mac:
- Logs typically live in
~/Library/Logs/[VPN Provider Name] - Or
~/Library/Application Support/[VPN Provider Name]/logs - Open Finder, press Cmd+Shift+G, paste the path above
iOS:
- Most apps don't expose logs directly
- Check Settings > Privacy > VPN for connection status
- Contact app support for detailed logs
Android:
- Some apps store logs in the app's internal storage
- You may need to enable "debug mode" or "advanced logging" in settings
- Or contact app support to retrieve logs
What to look for in logs:
- Repeated connection failures: Indicates server problems or configuration issues
- Authentication errors: Your account credentials might be wrong or compromised
- Timeout errors: Your connection is unstable or the server is unreachable
- Disconnection events: Logs should show when and why you disconnected
- Protocol errors: Indicates the VPN protocol isn't working properly
- Reconnection attempts: Good VPN apps automatically reconnect. Logs should show this working
If logs show repeated errors, take screenshots and send them to your VPN provider's support team. They can interpret the specific error codes and tell you what's wrong.

Step 9: Test VPN Behavior Under Various Network Conditions
A VPN that works perfectly on your home WiFi might fail when you switch to mobile data, coffee shop WiFi, or corporate networks. Different networks have different conditions, and your VPN needs to handle all of them.
Test on different networks:
- Your home WiFi: Run all the tests (IP change, DNS leak, Web RTC, IPv6) on your normal home internet
- Mobile data (4G/5G): Connect through your phone's cellular data and rerun tests
- Public WiFi: Go to a coffee shop, library, or airport and test on their WiFi
- Corporate network: If applicable, test on your workplace network
- Hotspot from another device: Create a mobile hotspot and test through it
Each network type has different characteristics. Some block certain ports. Some have aggressive traffic monitoring. Some limit bandwidth. Your VPN needs to work through all of them.
Document your findings:
Create a simple table showing which tests pass or fail on each network:
| Network Type | IP Change | DNS Leak | Web RTC Leak | Speed | Connection Stability |
|---|---|---|---|---|---|
| Home WiFi | Pass | Pass | Pass | 70 Mbps | Stable |
| Mobile 4G | Pass | Pass | Fail | 15 Mbps | Occasional drops |
| Public WiFi | Pass | Pass | Pass | 8 Mbps | Unstable |
| Corporate | Fail | Fail | N/A | 0 Mbps | Connection blocked |
If your VPN fails on certain network types, you know where the problem is. Corporate networks, for example, might block all VPN traffic entirely (it's your company's choice). Public WiFi might have compatibility issues with certain protocols.
Identifying which networks cause problems helps you decide whether to troubleshoot or use different solutions on those networks.
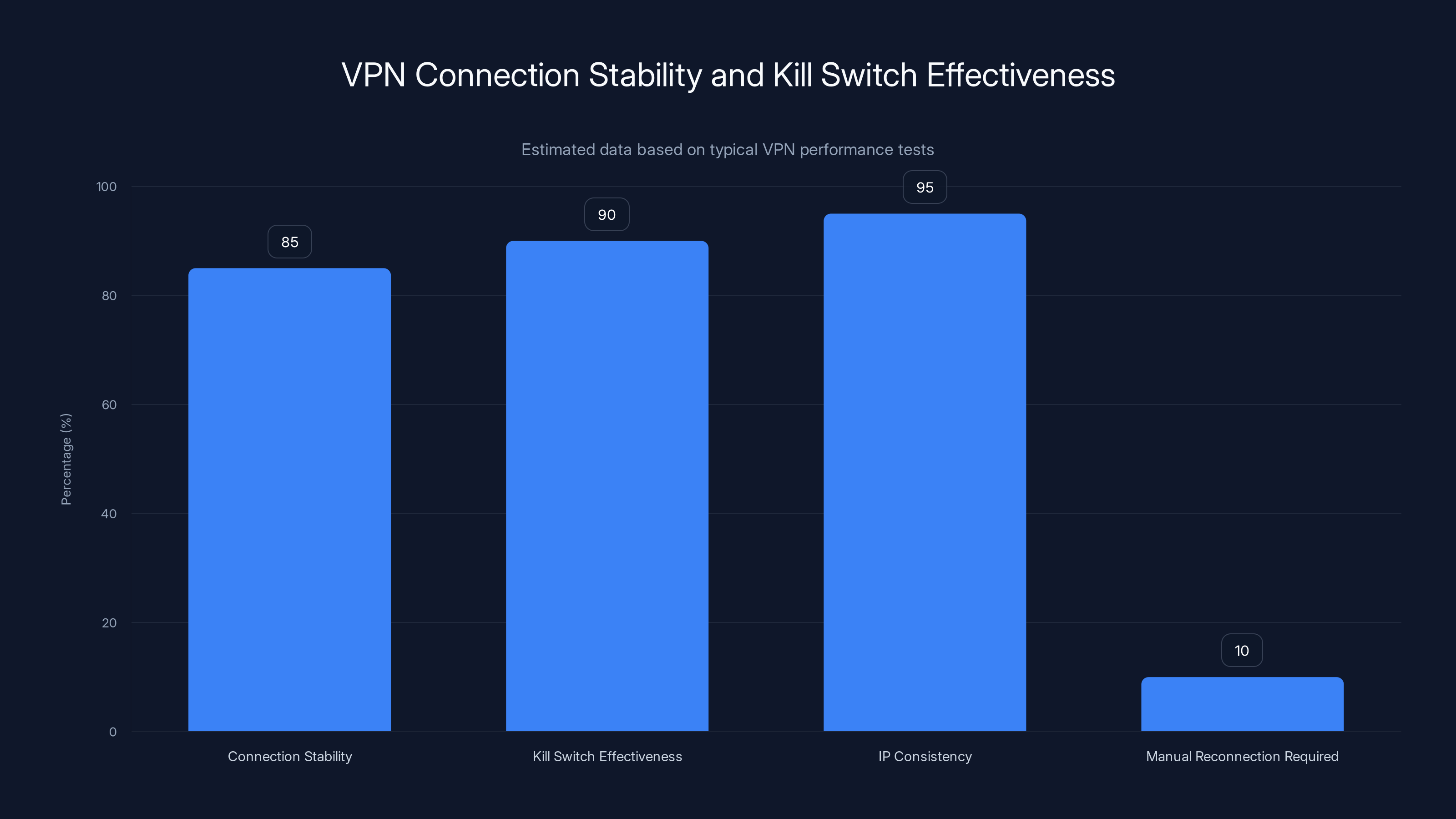
Estimated data shows that most VPNs maintain high connection stability and effective kill switch functionality, though a small percentage may require manual reconnection.
Step 10: Monitor Connection Stability and Reconnection Behavior
A VPN that connects once but disconnects unexpectedly is worse than no VPN at all. At least you'd know you're unprotected. But a VPN that silently disconnects makes you think you're protected when you aren't.
The best VPNs include "kill switch" functionality that automatically blocks internet access if the VPN disconnects. You're either connected to the VPN or your internet is off. There's no window where you're unencrypted.
How to test connection stability:
- Connect to your VPN and note the time
- Run the IP check test to confirm you're connected
- Leave the connection running for 24 hours: Don't touch anything, let it run
- Periodically check your connection status: Every 4-6 hours, verify you're still connected
- Run the IP check test again at the 24-hour mark
What you're looking for is consistent connection over extended periods. The IP should remain unchanged. Connection status should show "connected" the entire time.
Monitor for:
- Unexpected disconnections
- IP address changes (should stay the same while connected to same server)
- Dropped packets or timeouts
- Connection dropouts that require manual reconnection
Test the kill switch:
If your VPN has a kill switch:
- Ensure kill switch is enabled in your VPN settings
- Connect to your VPN and verify connection
- Run an IP address test to confirm you're protected
- Manually disconnect the VPN using the VPN app's disconnect button
- Try to browse the internet: Your connection should be blocked entirely
- Check your IP address: The test should fail or hang (internet is blocked)
- Reconnect the VPN and verify internet access is restored
A properly functioning kill switch prevents any unencrypted internet activity from reaching the internet while VPN is disconnected.
Advanced Testing: Checking for DNS Hijacking and Potential Man-in-the-Middle Attacks
Beyond basic leak tests, there are more sophisticated vulnerabilities you might want to check for.
DNS hijacking occurs when someone intercepts your DNS requests and provides false IP addresses, redirecting you to malicious websites that look legitimate. A compromised DNS could send you to a fake bank website, fake email client, or fake social media platform.
Man-in-the-middle (MITM) attacks involve someone positioning themselves between your device and your VPN server, intercepting encrypted traffic. While difficult with modern encryption, it's theoretically possible on certain networks.
How to detect DNS hijacking:
- Visit dnsleaktest.com and run a DNS hijack test
- Check for modified responses: The test sends requests to known domains and checks if responses have been altered
- Look for unexpected IP addresses: Domains should resolve to their legitimate IP addresses, not different ones
MITM attack indicators:
- Certificate errors: Your browser warns about untrusted SSL certificates while connected to VPN
- HTTPS failures: Encrypted websites fail to load or show security warnings
- Unexpected redirects: Websites redirect to unexpected locations
- Speed patterns: Consistent and unusual speed drops suggest traffic inspection
These advanced attacks are rare on consumer networks but more common on corporate networks or hostile WiFi environments. If you suspect these issues, contact your VPN provider or security professional.
Common VPN Testing Mistakes to Avoid
Most people test their VPNs incorrectly, leading to false conclusions about whether they work.
Mistake 1: Testing without actually connecting Running IP tests while thinking you're connected to a VPN, but you're actually disconnected. Always verify connection status before testing.
Mistake 2: Testing in browser cache Browsers cache IP geolocation results. The same IP address tested twice might show different results because of cached data. Clear your browser cache or use a private/incognito window.
Mistake 3: Assuming one passing test means everything works Passing the IP address test doesn't mean you're not leaking through DNS, Web RTC, or IPv6. You need to pass all tests.
Mistake 4: Testing on only one server location VPN providers have hundreds of servers. One working server doesn't guarantee all servers work. Test multiple locations.
Mistake 5: Comparing speeds incorrectly Speed tests are highly variable and depend on current internet traffic. Compare speeds consistently (same time of day, same test site, multiple runs).
Mistake 6: Ignoring browser extensions Browser extensions can interfere with VPN testing or bypass your VPN entirely. Disable all extensions before critical tests.
Mistake 7: Not understanding what "leaking" means Seeing your ISP in DNS results doesn't automatically mean you're compromised. It might be a cached result or false positive. Repeat tests to confirm.
Mistake 8: Testing on different devices and assuming results are the same Different devices (laptop, phone, tablet) may have different VPN configurations. Test on the specific device you care about.
What to Do If Your VPN Is Failing Tests
If your VPN fails one or more tests, here's your systematic troubleshooting roadmap:
For IP address not changing:
- Reconnect to VPN (wait 10 seconds between disconnect and reconnect)
- Try a different server location
- Switch VPN protocols
- Clear DNS cache (Windows:
ipconfig /flushdns, Mac:sudo dscacheutil -flushcache) - Restart VPN app
- Restart your device
- Restart your router
- Reinstall VPN app
- Contact support if unresolved
For DNS leaks:
- Enable DNS leak protection in VPN settings
- Try different VPN protocol
- Disable IPv6 in browser
- Clear DNS cache
- Try different DNS server option in VPN app
- Restart router
- Contact support if unresolved
For Web RTC leaks:
- Disable Web RTC in browser settings (varies by browser)
- Install Web RTC leak prevention extension
- Enable Web RTC protection in VPN app
- Try different VPN protocol
- Switch browsers to test
- Contact support if unresolved
For IPv6 leaks:
- Disable IPv6 at operating system level
- Disable IPv6 in browser
- Enable IPv6 leak protection in VPN app
- Try different server location
- Restart device
- Contact support if unresolved
For speed issues:
- Try server location closer to your actual location
- Switch VPN protocol
- Check your baseline internet speed (disconnect from VPN)
- Test at different time of day
- Use wired connection instead of WiFi
- Disable split tunneling if enabled
- Restart router
- Contact support if unresolved
If problems persist after these steps, your VPN provider's support team is your next step. Provide them with:
- Screenshots of failed tests
- Your VPN version number
- Your operating system and version
- The specific server location you were connected to
- Timestamp of when the problem occurred
- Anything you already tried
Good support teams can interpret these details and solve problems quickly.
Automated VPN Testing Tools and Services
Instead of manually running tests each time, several automated tools can perform comprehensive VPN verification.
Recommended testing services:
ipleak.net: Comprehensive leak testing covering DNS, Web RTC, IPv6, and location verification. Free. My personal go-to for quick checks.
dnsleaktest.com: Specialized DNS leak testing with detailed reports. Free. Best for DNS-specific diagnosis.
browserleaks.com: Browser-specific leak testing including Web RTC, canvas fingerprinting, and more. Free. Great for understanding browser-based vulnerabilities.
vpnpro.com/vpn-test: Automated all-in-one VPN testing tool with pass/fail results. Free.
speedtest.net: Gold standard speed testing. Free. Essential for measuring VPN performance impact.
whoer.net: Russian-based comprehensive privacy checker combining IP, DNS, Web RTC, and browser tests. Free.
These tools automate the manual testing I've described. Running tests monthly keeps you informed about whether your VPN continues to work as expected.
Final Recommendations for Maximum VPN Verification Confidence
To truly ensure your VPN is working as intended, implement this comprehensive testing protocol:
Initial setup (one-time):
- Run all five core tests (IP, DNS, Web RTC, IPv6, speed)
- Test on multiple server locations
- Test on multiple networks (home, mobile, public WiFi)
- Document baseline results
Monthly verification:
- Repeat core tests on your primary server location
- Run automated test via ipleak.net or whoer.net
- Test speed and verify acceptable performance
- Review VPN app logs for error patterns
Quarterly deep-dive:
- Test all five core tests across multiple server locations
- Test on different networks
- Review connection stability over extended period
- Update your documentation
Annual review:
- Complete comprehensive testing of all features
- Re-evaluate whether current VPN meets your needs
- Compare against new VPN options and features
- Update VPN if better alternatives exist
This protocol takes roughly 30 minutes per month and gives you complete confidence that your VPN is protecting your privacy as promised.
A working VPN is the foundation of online privacy. But a non-working VPN is worse than no VPN at all, because you think you're protected when you aren't. Knowing how to verify your VPN's functionality is absolutely essential.
You've now got everything you need to test your VPN comprehensively. Start with the IP address test. If that passes, move through DNS, Web RTC, and IPv6. If everything works, you're genuinely protected. If something fails, you now know exactly how to fix it.
Don't assume. Don't guess. Test. Verify. Confirm. Your privacy depends on it.

FAQ
What is a VPN and why do I need to verify it's working?
A VPN (Virtual Private Network) encrypts your internet traffic and routes it through a remote server, hiding your real IP address and location. Verification is critical because a VPN that claims to work might actually be leaking your identity through DNS requests, Web RTC vulnerabilities, or IPv6 addresses while appearing to function normally. Without testing, you could believe you're protected when you're actually fully exposed.
How often should I test if my VPN is working?
At minimum, test your VPN once per month to ensure it continues functioning properly. More frequent testing (weekly) is valuable if you rely on your VPN for sensitive activities like accessing financial accounts or handling confidential work. After any changes to your system, network, VPN protocol, or server location, run a quick test to confirm continued functionality.
Can a VPN be working for some types of traffic but not others?
Yes, absolutely. Your VPN might successfully hide your IPv4 address while leaking your IPv6 address. DNS queries might bypass the VPN while web traffic goes through it. Web RTC might leak your real IP while everything else is encrypted. This is why running multiple different tests is essential. A single passing test doesn't guarantee complete protection.
What does it mean if I see my ISP in my DNS leak test?
It means DNS requests are reaching your ISP's DNS servers instead of routing through your VPN's encrypted tunnel. Your ISP can see every website you're trying to visit, which is a critical privacy leak. This requires fixing through VPN settings adjustments, DNS leak protection features, or potential app reinstallation.
Is it normal for my internet to be slower when using a VPN?
Yes, some speed loss is normal and expected. A 20-30% decrease on nearby servers or 30-50% on distant servers is typical. Speed loss happens because traffic travels through an additional server (your VPN) before reaching its destination. However, if you're losing 80%+ of your speed consistently, something is wrong with either the VPN or that specific server.
Should I disable IPv6 to avoid IPv6 leaks?
Disabling IPv6 at the operating system level is the most reliable way to prevent IPv6 leaks, but it's not always necessary. Many modern VPNs handle IPv6 properly. Start by testing for IPv6 leaks. If no leaks are detected, leave IPv6 enabled. If leaks appear, then disable it. Check whether your VPN provider has built-in IPv6 leak protection before disabling the protocol system-wide.
What's the difference between a DNS leak and a Web RTC leak?
A DNS leak occurs when DNS queries (website address lookups) bypass your VPN and reach your ISP's servers directly. A Web RTC leak happens when web browser real-time communication technology exposes your real IP address through direct browser-to-server connections. DNS leaks reveal which websites you're visiting. Web RTC leaks reveal your actual IP address. Both are serious privacy problems but have different causes and fixes.
If my VPN is leaking, does that mean the VPN provider is malicious?
Not necessarily. VPN leaks can result from misconfigured servers, bugs in the app, incompatibilities with your operating system or browser, or network-level issues. Some leaks (like IPv6) aren't always the provider's fault. Most reputable providers fix leaks quickly once they're reported. Always contact your provider if you detect leaks rather than immediately assuming malicious intent.
Can I trust the IP address checking websites to give accurate results?
Generally yes, but verify with multiple sources. Different IP checking websites sometimes have cached or slightly inaccurate data. Visit three different IP checkers (whatismyipaddress.com, ipleak.net, ipinfo.io) and compare results. If all three show the same IP address and location, you can trust the results. If they differ significantly, wait a few minutes and try again, as DNS propagation delays sometimes cause temporary inconsistencies.
What should I do if my VPN passes all tests but I still feel my privacy is compromised?
First, double-check your test results for accuracy. Then consider whether your privacy concerns might be coming from other sources: browser fingerprinting, tracking pixels, cookies, device identifiers, or app-level tracking. A VPN protects your IP address and ISP visibility but doesn't prevent websites from identifying you through other methods. Consider supplementary privacy tools like browser extensions for tracking prevention or ad blockers.
Is a free VPN testing reliable, or should I pay for professional VPN auditing?
Free VPN testing through ipleak.net, dnsleaktest.com, and similar services is highly reliable for detecting the major leak categories (DNS, Web RTC, IPv6). Professional VPN audits are valuable if you need documentation for compliance purposes or suspect sophisticated attacks. For personal privacy verification, free tools are sufficient and provide the same quality of results as paid options.
Key Takeaways
Your VPN might not be doing what it's supposed to do. Without testing, you won't know until it's too late. Run the tests covered in this guide. Pass all of them before trusting your VPN with sensitive activities.

![How to Check if Your VPN Is Working [2025]](https://tryrunable.com/blog/how-to-check-if-your-vpn-is-working-2025/image-1-1769002764257.jpg)



