How a Single Expired Certificate Broke Thousands of Logitech Mice on macOS
It's the kind of thing that makes you question how software even works. One minute, your $99 Logitech MX Master 4 is functioning perfectly. The next, the scroll wheel's direction reverses itself. Extra buttons stop responding. The Logi Options Plus app won't even open. You restart. You reinstall. Nothing works.
Turns out, it wasn't a bug. It wasn't malware. It was something far more mundane: Logitech simply forgot to renew a certificate.
This is the story of how a single administrative oversight cascaded into a technical disaster affecting thousands of macOS users, what certificate validation actually is and why Apple enforces it so strictly, how this exposed a critical vulnerability in how we deploy software, and what it teaches us about the fragility of modern computing infrastructure.
If you're a Logitech user running macOS, you probably experienced this firsthand. If you didn't, you're about to understand why this type of failure is more common than you'd think, and why companies need better systems to catch these problems before they ship to customers.
Let's break down exactly what happened, why macOS users were hit so much harder than Windows users, and what this incident reveals about software development practices in 2025.
TL; DR
- The Problem: Logitech's Logi Options Plus and G Hub apps stopped working on macOS after an embedded developer certificate expired
- Why macOS Only: Apple's security model requires valid Developer ID certificates to run applications; Windows lacks this enforcement mechanism
- The Impact: Users lost access to customized button mappings, scroll wheel settings, and advanced mouse gestures
- The Fix: Logitech released a manual patch requiring users to download and install it themselves, since the auto-updater also relied on the expired certificate
- The Lesson: This incident highlights dangerous gaps in software deployment pipelines and why certificate management needs to be automated

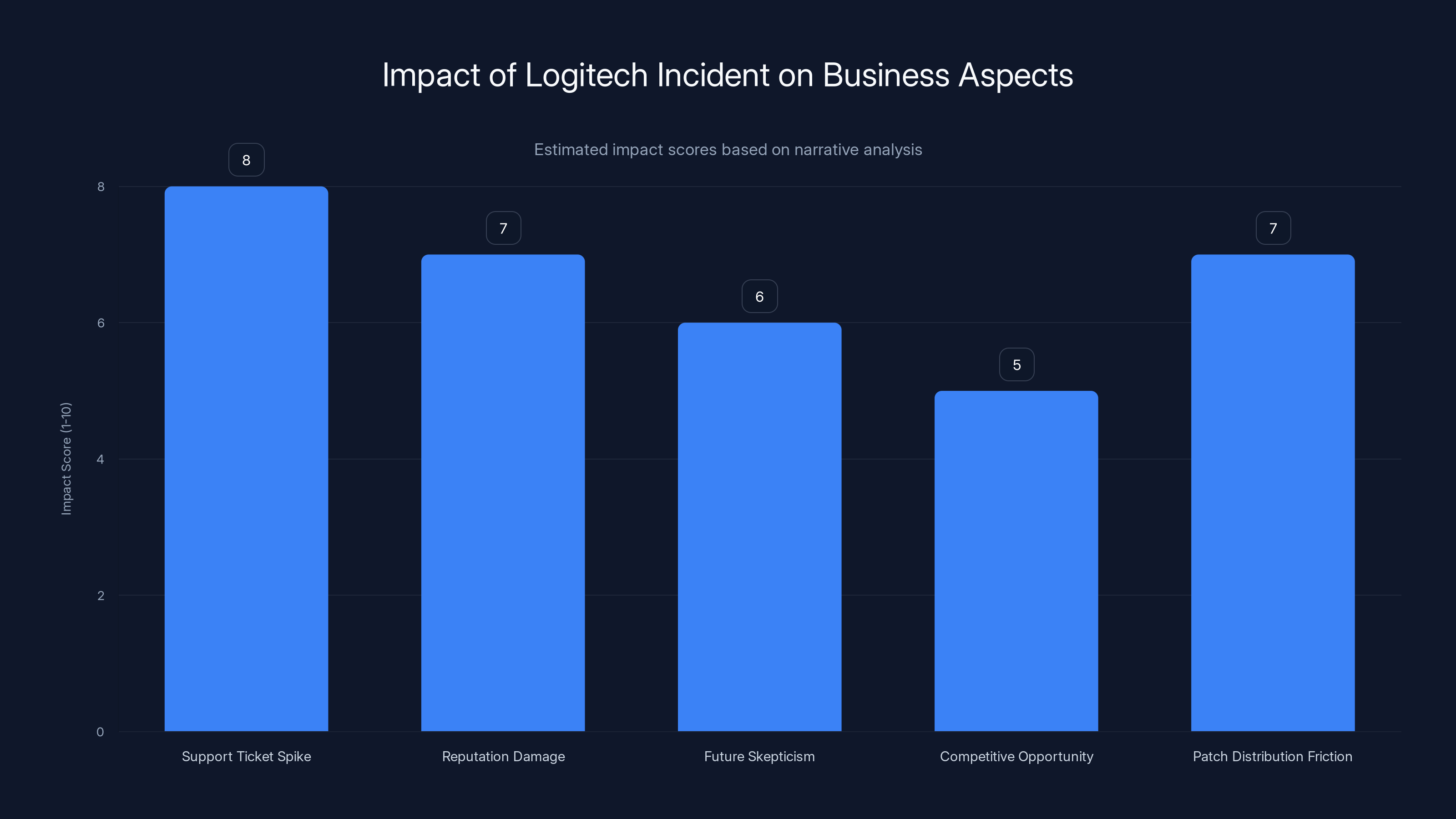
Estimated data shows that the support ticket spike had the highest impact, followed by reputation damage and patch distribution friction. Estimated data.
What Actually Went Wrong: The Certificate Chain
To understand how a single certificate caused such widespread chaos, you need to understand what certificates actually do in the software world.
When Apple released macOS with stricter security requirements, they implemented what's called "code signing." This is a cryptographic process where developers digitally sign their applications using a private key provided by Apple. When you launch an app on macOS, the operating system checks this signature against Apple's public key. If the signature is valid and the certificate hasn't expired, the app runs. If either condition fails, macOS throws up a roadblock.
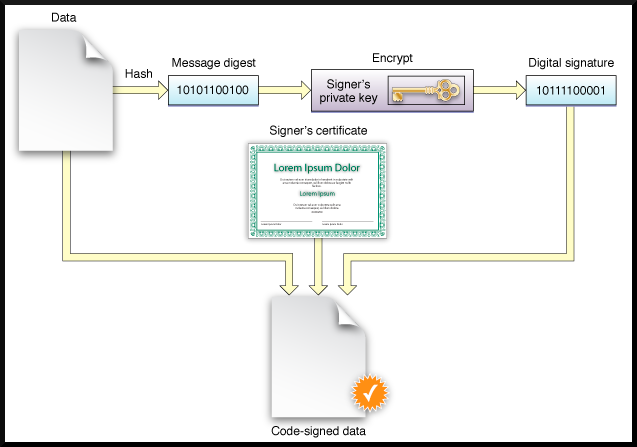
Logitech's developers embedded a Developer ID certificate directly into both Logi Options Plus and G Hub applications. This certificate acts like a digital passport. It tells macOS, "This code came from Logitech, and they're responsible for it. They've been verified by Apple."
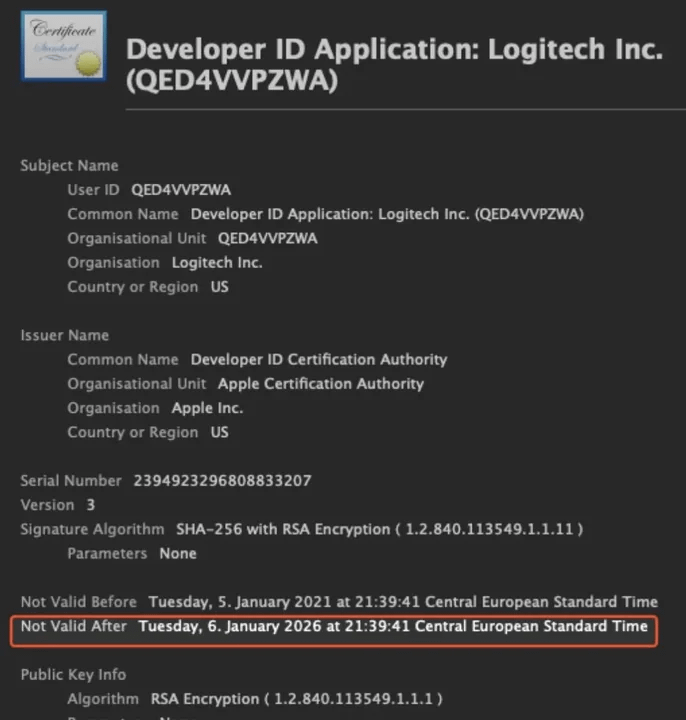
The certificate had an expiration date. And Logitech's team didn't renew it before that date arrived.
When the expiration date passed, macOS saw the signature as invalid. Not suspicious. Not outdated. Invalid. The operating system treated the expired certificate the same way it would treat an unsigned app or one signed by an untrusted developer. It refused to run it.
But here's the critical part: the in-app updater that would normally fix this problem also relied on the same expired certificate to function. This created a catch-22. Users couldn't open the app to update it because the app wouldn't run. And the app wouldn't run because the certificate was expired.
Why Windows Users Weren't Affected
This is where it gets interesting. Windows users running the exact same version of Logitech's G Hub software experienced zero issues.
The reason comes down to fundamental differences in how Windows and macOS approach application security. Windows doesn't require valid code signatures to run most applications. It has security mechanisms like Smart Screen and UAC (User Account Control), but these don't rely on mandatory certificate validation the way macOS does.
Microsoft's approach is more permissive. The operating system trusts the user to decide whether to run software. It can warn users, but it generally won't refuse to launch an unsigned or expired-certificate application.
macOS takes the opposite philosophy. Apple enforces certificate validation at the kernel level. If a certificate is expired or invalid, the app doesn't run. Full stop.
This design decision has real security benefits. It's one reason why macOS experiences fewer widespread malware incidents than Windows. But it also creates scenarios like this one, where a simple administrative mistake can instantly brick thousands of applications across the install base.
Windows users effectively got a free pass because the security model doesn't mandate the same level of certificate enforcement. Logitech's mistake became an exclusively macOS problem.
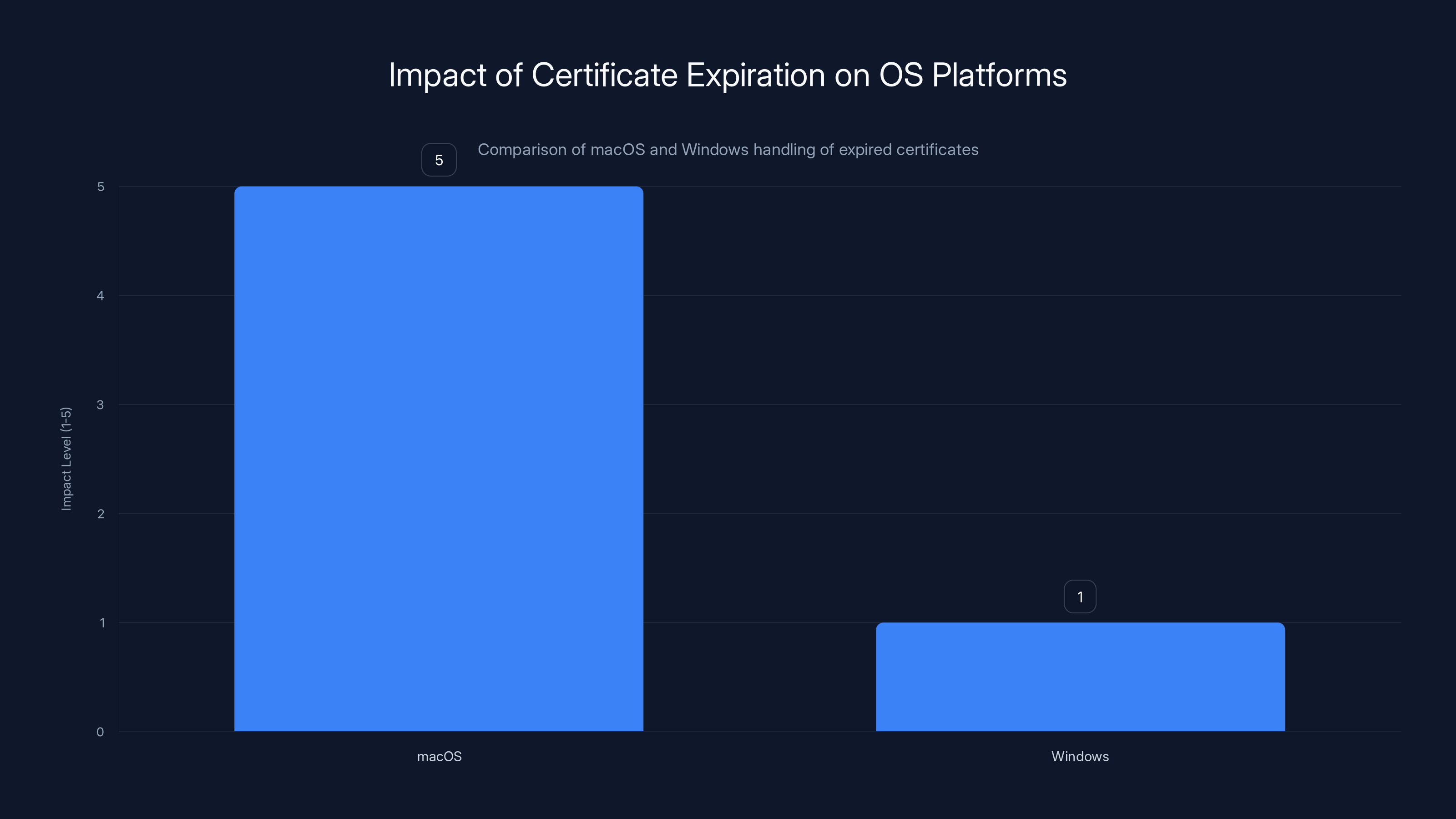
macOS enforces strict certificate validation, leading to a high impact when certificates expire, unlike Windows. (Estimated data)
The Incident Timeline: From Oversight to Acknowledgment
Based on user reports and Logitech's public statements, here's what appears to have happened:
Before January 2025: Logitech had a Developer ID certificate embedded in Logi Options Plus and G Hub. This certificate was valid and renewed periodically. At some point, Logitech's IT or DevOps team missed the renewal window.
Early January 2025: Users on Reddit began reporting issues. The Logi Options Plus app crashed on launch. The scroll direction inverted unexpectedly. Extra mouse buttons became unresponsive. Users tried restarting their Macs. They uninstalled and reinstalled the software. Nothing worked.
One Reddit user described opening the app and watching it enter a boot loop. The app would start loading, fail, and restart immediately. This repeated endlessly until they force-quit it.
Same Day: Multiple affected users identified the root cause by examining system logs and security settings. macOS was blocking the application due to an invalid code signature. The developer certificate had expired.
Within 24 Hours: Logitech acknowledged the issue publicly. A company spokesperson, identified as ATXsantucci on Reddit, posted a candid response: "We dropped the ball here. This is an inexcusable mistake. We're extremely sorry for the inconvenience caused."
This level of directness from a corporate representative is rare. Most companies issue carefully worded statements through PR departments. Logitech's person-to-person apology on Reddit suggested this was recognized internally as a serious failure.
Hours Later: Logitech released a patch. But the patch came with a caveat: it had to be installed manually. Users couldn't use the automatic update mechanism within the app because, remember, the app wouldn't run at all.
Users had to download the patch from Logitech's support page, manually run an installer, and then the app would work again. This added friction during a period when Logitech's reputation was already damaged.
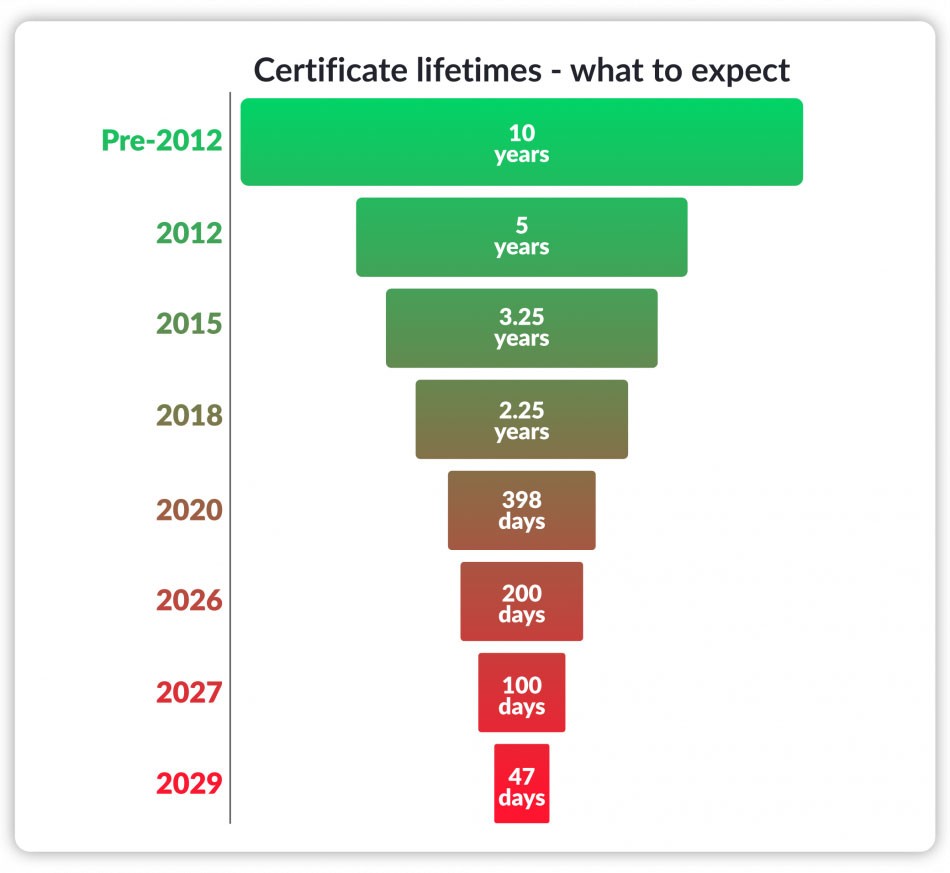
How the Manual Patch Actually Fixed the Problem
Logitech's patch worked by including a new, valid Developer ID certificate that hadn't expired yet.
When you downloaded the patch file and ran the installer, it overwrote the old application bundle with a fresh one signed using the new certificate. Assuming that new certificate is managed properly and renewed before its expiration date, the app would continue working normally.
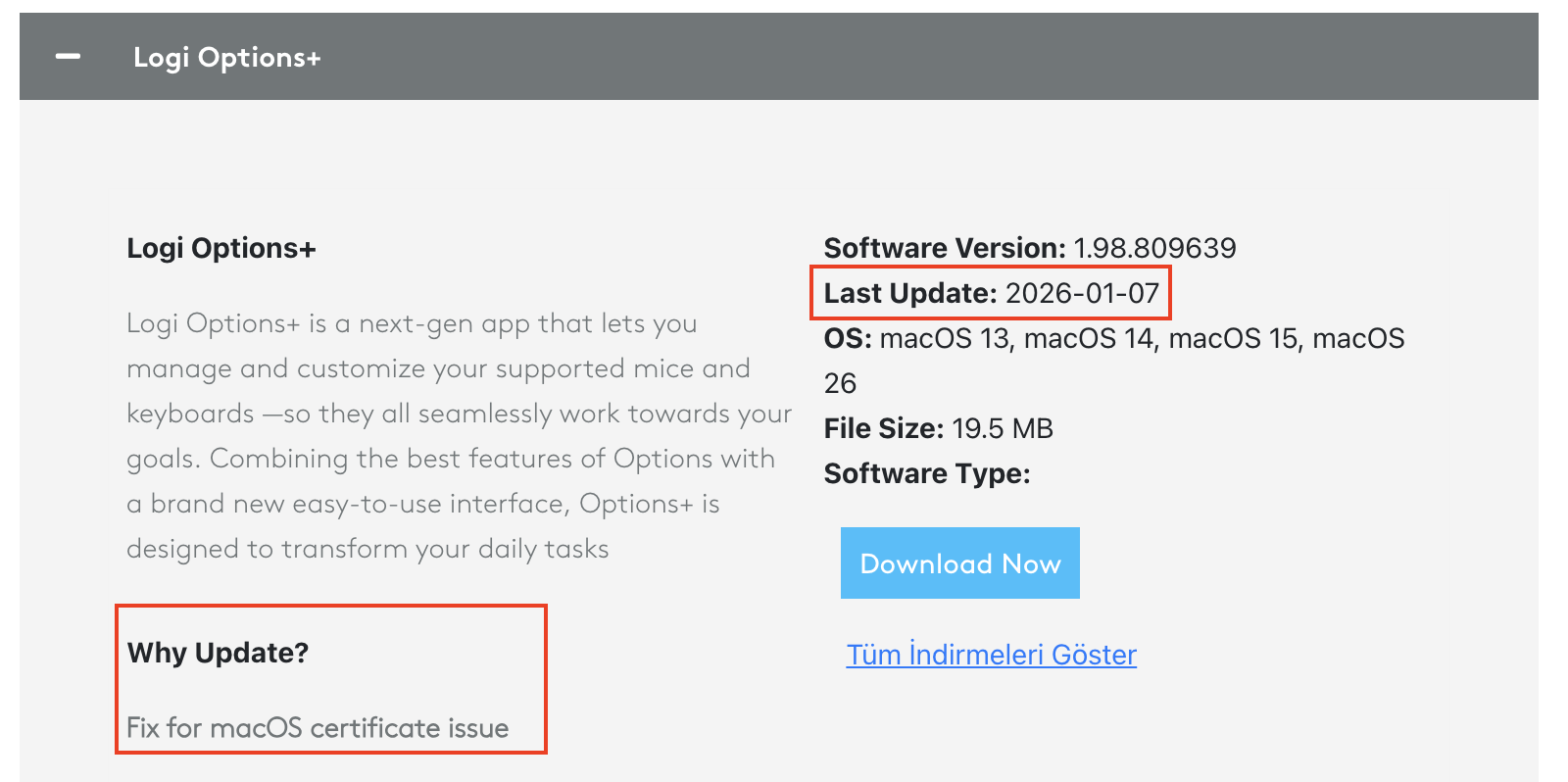
The patch was released for macOS versions 13 (Ventura), 14 (Sonoma), 15 (Sequoia), and 16 (Tahoe). Logitech noted that older versions of macOS would receive a patch "at a later time," suggesting they needed to rebuild and test the application for those older OS versions separately.
Once installed, Logitech stated that "device settings, customizations, and profiles for impacted users will remain intact." This was important reassurance. Users wouldn't lose their carefully configured button mappings and scroll settings after applying the fix.
The Broader Pattern: Why This Keeps Happening
This incident wasn't unique to Logitech. Similar certificate expiration issues have affected other major software companies.
In 2023, a security certificate expiration caused issues for another major tech company's software distribution. In 2024, multiple incidents occurred where developers missed certificate renewal deadlines, resulting in temporary service disruptions.
The pattern suggests a systemic problem: certificate management is treated as boring infrastructure work rather than as a critical operational dependency.
Here's why these oversights happen:
Decentralized Ownership: Certificate renewal responsibilities often live in infrastructure or DevOps teams, but the actual certificate might be managed by a different group. This fragmentation creates gaps.
No Automated Reminders: Many organizations still rely on manual calendar reminders rather than automated systems that alert teams when certificates are approaching expiration.
Certificates Aren't Sexy: Engineering teams prioritize new features and bug fixes. Certificate renewal is unsexy operational maintenance. It gets deprioritized until it breaks something.
Legacy Systems: Older software might have certificates embedded in ways that are hard to update without rebuilding and redeploying the entire application.
Multiple Certificates: Enterprise software often has dozens or hundreds of certificates across different systems and deployments. Tracking all of them manually is error-prone.
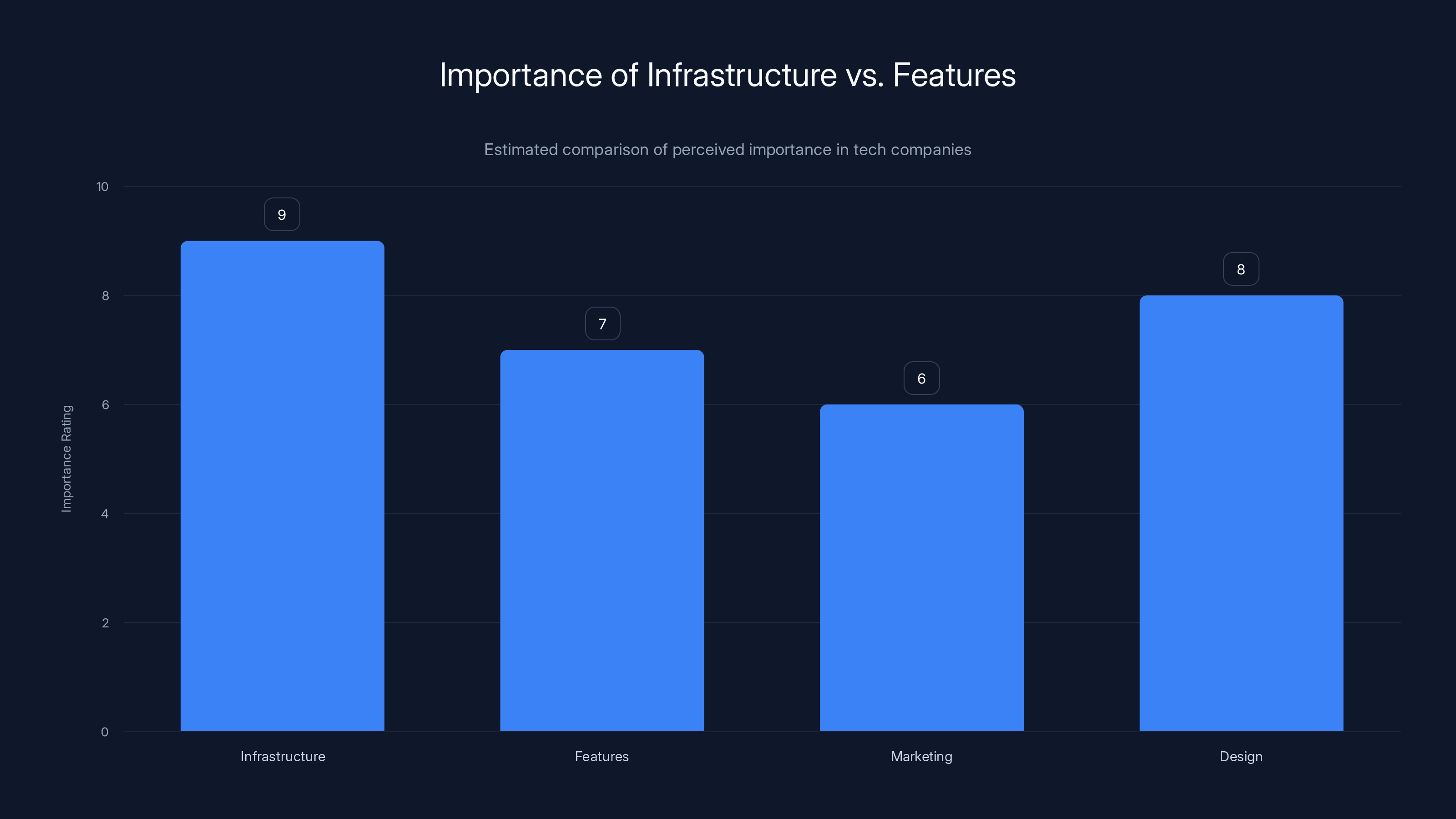
Infrastructure and operational discipline are rated higher in importance than features and marketing in tech companies. Estimated data.
Apple's Security Model and Why It's Both a Feature and a Liability
Apple's strict code-signing requirements exist for good reasons. They prevent malware from running on macOS. They make it harder for attackers to distribute compromised software. They ensure that if someone claims to have installed an app from Apple's official sources, it really came from there.
But this security model has a dark side: it's unforgiving. There's no "warning" stage. There's no grace period. If a certificate is expired, the app is blocked, period.
Compare this to other security mechanisms. A password can be changed. A firewall rule can be updated. But a code signature is permanent once the software is distributed. The only way to fix an expired certificate is to rebuild the app with a new certificate and ask every user to update it.
At scale, this becomes a logistical nightmare. Logitech had to rebuild Logi Options Plus and G Hub for multiple macOS versions. They had to notify users about the availability of a patch. They had to field support requests from confused users who didn't understand why their mouse stopped working.
The security benefit—preventing unsigned or maliciously signed code from running—is legitimate. But the implementation creates a scenario where a single administrative mistake can bring down an application ecosystem instantly.
Windows' more permissive approach has security drawbacks, but it's more resilient to certificate management failures. macOS' strict approach is more secure overall, but brittle when things go wrong.
The Impact on End Users: What Actually Broke
For affected Logitech users, the impact was immediate and annoying.
Customization Loss: Logitech mice come with advanced customization features. The MX Master 4, for example, has a programmable thumb wheel that can be configured to perform different actions in different applications. When Logi Options Plus failed, users lost access to this customization layer. The hardware still functioned, but it reverted to default behavior.
Scroll Direction Issues: Some users reported that scroll direction inverted unexpectedly. If you configured scrolling to move up when you scroll up (natural scrolling), it suddenly reversed. This isn't just annoying; it breaks muscle memory.
Button Mapping Failure: Extra buttons programmed for specific actions stopped working. Users who mapped buttons for productivity macros or gaming controls found those buttons inert.
Application Instability: The Logi Options Plus app itself wouldn't launch, leaving users with no way to reconfigure their devices or troubleshoot problems.
No Automatic Recovery: Users couldn't simply wait for an auto-update to fix the problem. They had to actively download a patch, locate the installer, and manually run it. For less technical users, this became a support burden.
The severity of the impact depended on how heavily a user relied on customization. Someone using a Logitech mouse for basic pointing and clicking would barely notice. Someone using advanced features or gaming macros would have their workflow disrupted.
Logitech's guarantee that "device settings, customizations, and profiles for impacted users will remain intact" after installing the patch was a smart move. Users didn't have to reconfigure everything from scratch.
The Root Cause: Certificate Management Failures
This incident exposes a critical gap in how enterprise software is deployed and maintained.
Most large software companies have implemented continuous integration and continuous deployment (CI/CD) pipelines. These are automated systems that build, test, and deploy software changes rapidly. But certificate management often lives outside these automated systems.
Why? Because certificates are usually treated as secrets that shouldn't be checked into version control. They're stored separately, often in manual configuration files or password managers. This separation makes sense from a security perspective, but it creates operational blind spots.
When certificate renewal falls through the cracks, there's no automated system to catch it. The certificate just expires silently. The software continues to build and deploy with the old certificate embedded. Everything appears normal until the certificate's expiration date passes and macOS suddenly blocks execution.
The fix requires implementing automated certificate management systems that:
- Monitor Certificate Status: Check expiration dates automatically
- Alert Early: Send notifications well before expiration
- Automate Renewal: Renew certificates programmatically when possible
- Test Thoroughly: Verify that renewed certificates work before deploying
- Track Everything: Maintain a centralized inventory of all certificates in use
Large companies like Amazon and Google have already implemented these systems because they've been bitten by certificate management failures before. But it's clear that Logitech hadn't implemented the same level of rigor.
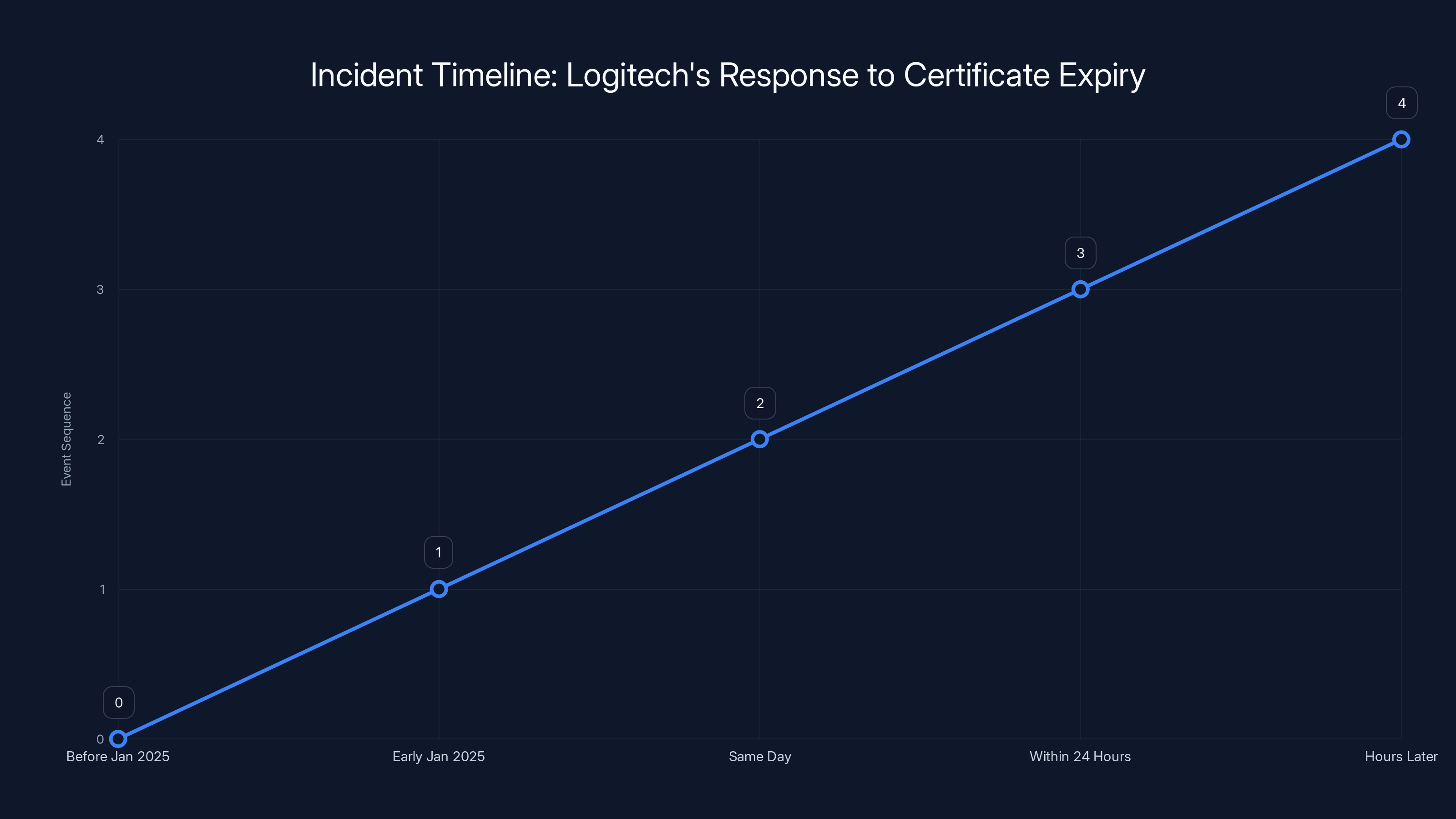
The timeline shows the progression from oversight to acknowledgment and resolution, highlighting Logitech's swift response within hours of user reports. Estimated data.
Comparing macOS Failures to Windows: A Tale of Two Security Models
The stark difference between macOS and Windows outcomes in this incident is worth examining in detail.
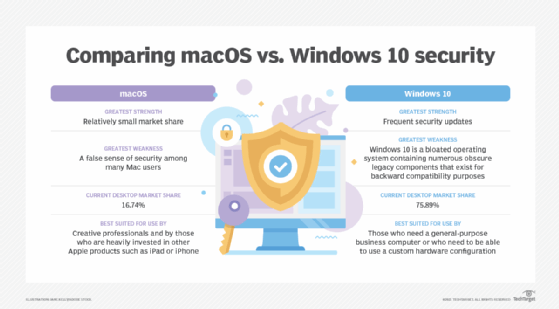
macOS Security Model:
- Code signing is mandatory
- Expired certificates block execution
- No grace period
- Affects all applications with embedded certificates
- Results in immediate, widespread user impact
Windows Security Model:
- Code signing is optional for most applications
- Unsigned applications run with warnings
- No certificate validation at the kernel level
- Legacy compatibility takes priority
- Results in fewer catastrophic failures, but potentially lower security overall
Where's the optimum? Probably somewhere between these two extremes.
Apple's strict approach provides better security. It's harder to distribute malware on macOS because applications must be properly signed. But it creates brittleness. A certificate management failure becomes an application failure.
Windows' permissive approach is more forgiving of certificate issues, but it's also more vulnerable to malware distribution and compromised software.
There are ways to thread this needle. For example, a system could:
- Enforce code signing on new installations
- Allow a grace period after expiration (24 to 48 hours) before blocking
- Provide more detailed error messages explaining why an app is blocked
- Offer a way for end users to temporarily disable code signing for debugging
Apple hasn't implemented these refinements, likely because they prioritize security over user convenience.
How to Prevent Certificate Expiration Disasters
If you're responsible for managing software that ships with embedded certificates, here's how to build systems that prevent this problem:
1. Centralized Certificate Inventory
Maintain a single source of truth for all certificates in your organization. This should include:
- Certificate name and purpose
- Expiration date
- Which applications or services use it
- Who owns it (which team is responsible for renewal)
- When it was last renewed
2. Automated Monitoring
Implement systems that check certificate expiration dates automatically. Tools like cert-manager can do this. Set up alerts at multiple intervals:
- 180 days before expiration (strategic planning phase)
- 90 days before expiration (engineering team prepares)
- 30 days before expiration (work begins)
- 14 days before expiration (urgent)
- 7 days before expiration (critical)
3. Automated Renewal
Where possible, automate the renewal process. Let's Encrypt pioneered automated certificate renewal for web certificates. Similar approaches can work for code-signing certificates.
4. Build Pipeline Integration
Add certificate validation to your continuous integration pipeline. If a certificate will expire within 90 days of the build date, fail the build and alert the team. Don't allow deployments with soon-to-expire certificates.
5. Staging and Testing
Before deploying any certificate renewal, test it in a staging environment. Verify that:
- The new certificate is valid
- Applications signed with the new certificate work correctly
- The transition from old to new certificate is seamless
6. Documentation and Ownership
Make sure certificate management responsibility is explicitly assigned. Include it in runbooks and on-call documentation. If no one owns it, no one will prioritize it.
7. Regular Audits
Every quarter, audit all certificates in production. Verify that each one is tracked, monitored, and assigned to an owner.
The Business Impact: Damage Control and Customer Trust
Beyond the technical issues, this incident had real business consequences for Logitech.
Support Ticket Spike: Thousands of users reporting the same problem overwhelmed Logitech's support channels. Even though the fix was straightforward once identified, every affected user needed assistance.
Reputation Damage: Logitech's quick public acknowledgment and apology helped, but the damage was done. Users experienced unexpected failure of a premium product they'd paid $99+ for. That sticks.
Future Skepticism: Users might be more hesitant to rely on Logitech's software ecosystem in the future. They now know that even Logitech can have critical failures.
Competitive Opportunity: Competitors selling alternative mouse solutions could use this incident in marketing. "Our mouse didn't break because we manage our infrastructure better."
Patch Distribution Friction: The need for manual patching added friction. Some users didn't notice the fix was available. Others had trouble installing it. This extended the duration of the incident.
The positive aspect of Logitech's response—direct acknowledgment and a quick fix—probably limited long-term damage. A company that had been defensive or slow to respond would have faced much worse fallout.
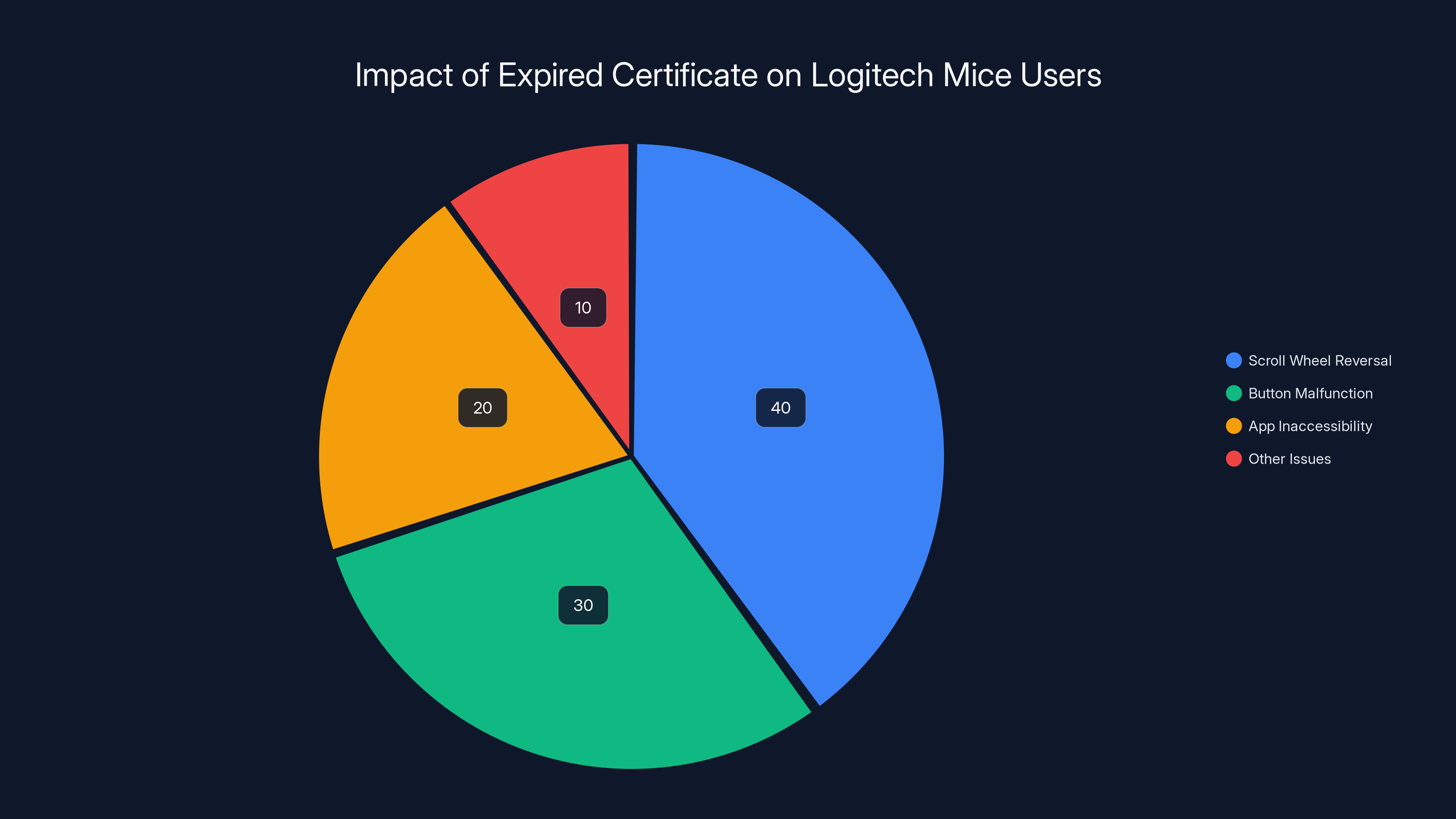
Estimated data shows that scroll wheel reversal was the most common issue, affecting 40% of users, followed by button malfunctions and app inaccessibility.
What This Reveals About Modern Software Complexity
This incident is a window into the fragility of modern software systems.
A single administrative task—renewing a certificate—has been embedded so deeply into the macOS security model that a failure in that task instantly breaks applications across hundreds of thousands of machines.
This is an example of what engineers call "tight coupling." The application's functionality is tightly coupled to certificate validity. There's no separation of concerns, no fallback mechanism, no graceful degradation.
In well-architected systems, you'd expect:
- Fallback validation methods if the primary certificate is invalid
- A grace period during which expired certificates still work
- Clear user communication if a certificate issue is detected
- Automatic remediation mechanisms
But real-world systems often prioritize security and simplicity over resilience. Apple chose to make macOS instantly block unsigned or improperly signed applications rather than provide fallback mechanisms.
This decision has security benefits—it's harder to exploit—but operational costs.
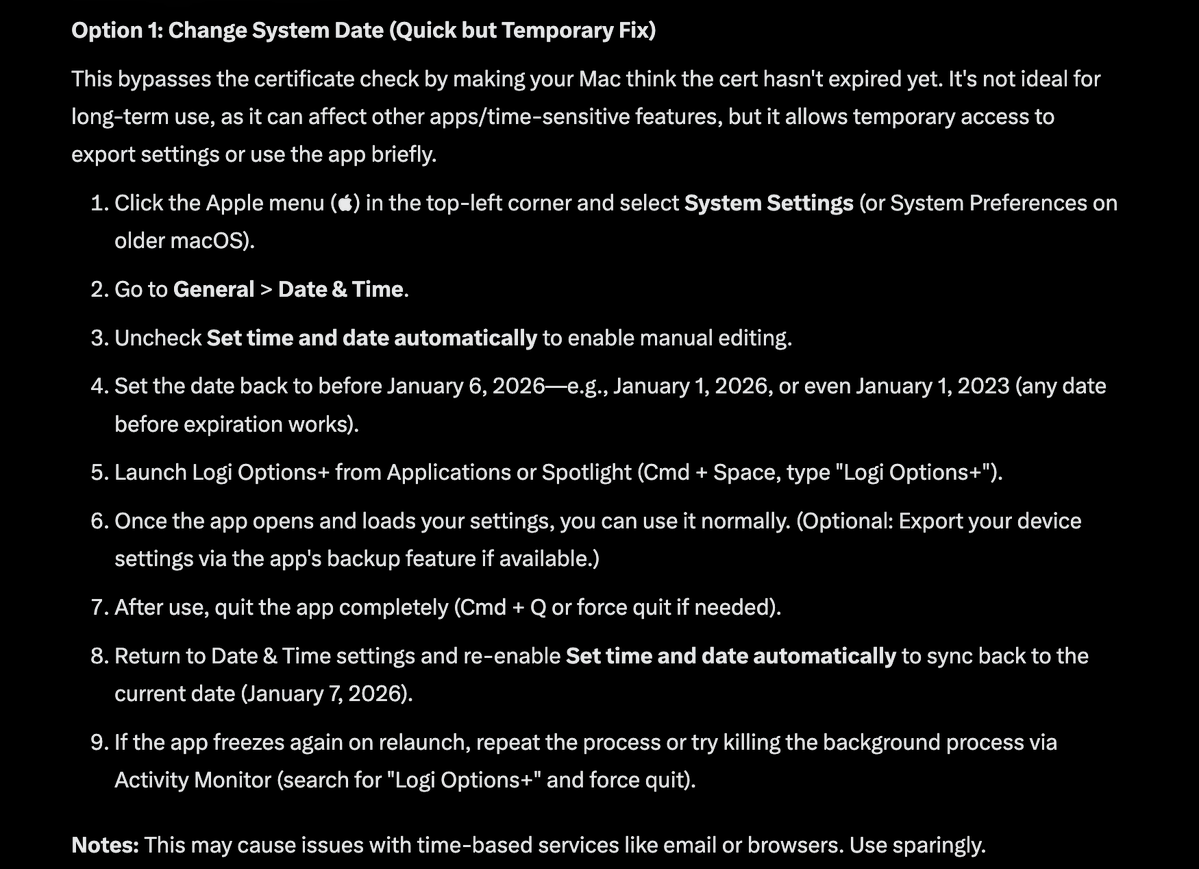
Lessons for Organizations Running Production Systems
If you manage production software, especially software distributed to end users, here's what to learn from Logitech's experience:
1. Certificate Management is Critical Infrastructure
Treat it with the same care you'd give to database backups or security keys. It deserves dedicated monitoring, automation, and ownership.
2. Single Points of Failure Are Everywhere
One expired certificate broke multiple applications and affected thousands of users. Look for similar critical dependencies in your systems. What else could bring down your application ecosystem?
3. Security and Convenience Are in Tension
macOS enforces strict security by requiring valid certificates. This is good for security, bad for operational convenience. Accept that tradeoffs exist and plan accordingly.
4. Manual Processes Don't Scale
Relying on someone to remember to renew a certificate doesn't scale. Automate everything you can.
5. User Communication Matters
Logitech's public acknowledgment and apology on Reddit helped minimize reputational damage. Be honest when things go wrong.
6. Patch Distribution Must Be Robust
If an issue breaks the in-app updater, you need an alternative distribution mechanism. Logitech had to provide a manual download. Having a plan for this ahead of time would have been better.

The Technical Deep Dive: How macOS Code Signing Works
For those interested in the technical details, here's how Apple's code-signing mechanism works under the hood:
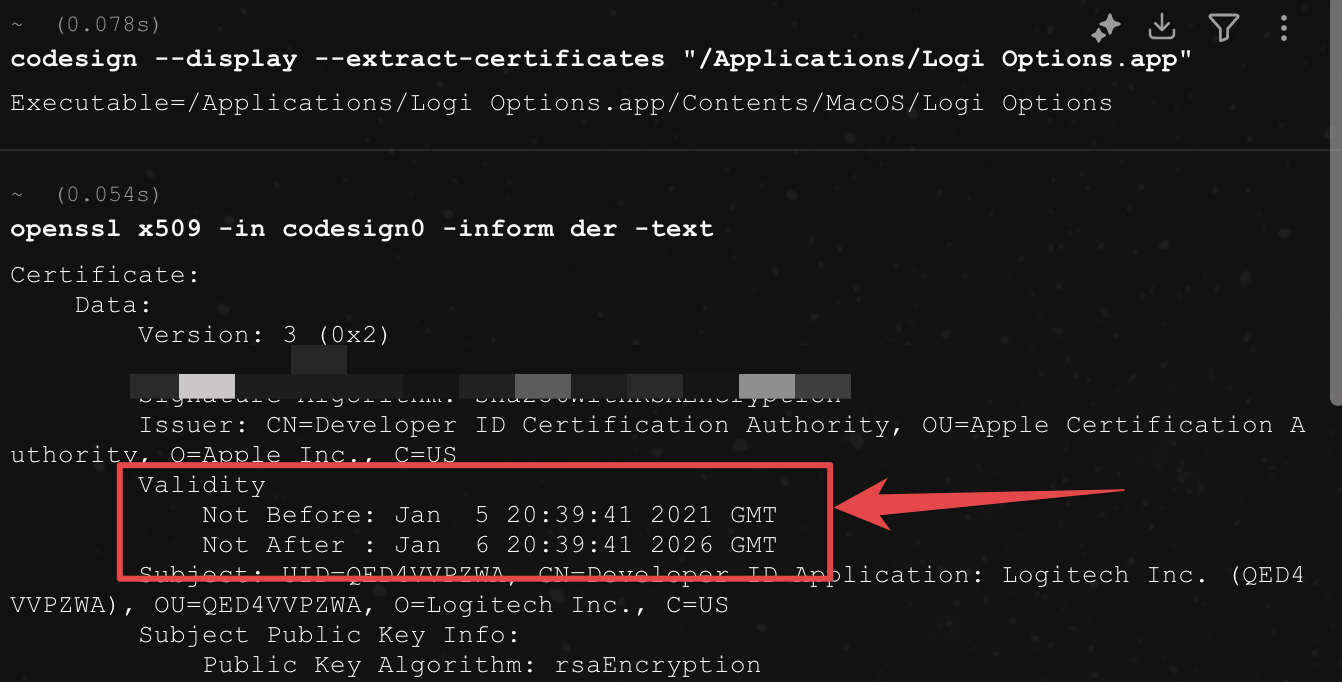
When a developer builds an application on macOS, they use a tool called codesign to sign the application bundle. This tool takes the application's code, computes a cryptographic hash, and signs that hash with the developer's private key.
The signature, along with the public certificate, is embedded in the application bundle. When a user launches the application, macOS extracts the signature and certificate, uses the public key to verify the signature, and checks whether the certificate is valid (not revoked, not expired, issued by a trusted authority).
If all checks pass, macOS runs the application. If any check fails, macOS blocks execution and displays an error message.
Logitech's certificate had expired. When users tried to launch the app, macOS extracted the expired certificate, saw that it had passed its expiration date, and refused to run the application. This wasn't due to a bug in the application itself; it was purely a certificate validity check failing.
The codesign tool itself is part of Xcode, Apple's development framework. To sign an application with a renewed certificate, Logitech would have needed to:
- Obtain a new Developer ID certificate from Apple Developer
- Add the new certificate to their code-signing configuration
- Rebuild the application
- Re-sign the rebuilt application with the new certificate
- Test the signed application to ensure it works
- Distribute it to users
Steps 2-5 should be automated in a CI/CD pipeline, but step 1 requires human action (requesting the certificate from Apple). Step 6 requires users to update, which can be automatic or manual depending on how the application handles updates.
Logitech implemented step 6 as manual because their automatic update mechanism also relied on the invalid certificate. This was a smart failsafe: they couldn't trust the broken update system to deliver a fix, so they had users download it directly.

Predictions: How the Industry Will Respond
Based on historical patterns after high-profile infrastructure failures, we can predict how the industry will respond:
1. Increased Automation: More companies will invest in automated certificate management systems. This incident demonstrated the risks of manual processes.
2. Better Alerting: Expect to see more sophisticated certificate monitoring tools that provide early warnings well before expiration.
3. Industry Standards: Organizations like the Cloud Native Computing Foundation might develop standards for certificate management and distribution.
4. Educational Focus: This incident will appear in engineering courses and conference talks as a case study in infrastructure failure.
5. Tool Evolution: The tools and platforms used for code signing and certificate management will likely add more safeguards and automation.
6. Cultural Shift: Certificate management will become recognized as a critical operational responsibility rather than a routine maintenance task.
Within Logitech specifically, we can expect they'll implement comprehensive certificate management systems to prevent recurrence.

FAQ
What caused Logitech mice to stop working on macOS?
Logitech's Logi Options Plus and G Hub applications relied on an embedded Developer ID certificate to run on macOS. When this certificate expired, macOS blocked the applications from launching, causing users to lose access to customization features like custom button mappings and scroll settings. The issue only affected macOS because Apple enforces certificate validation at the kernel level, while Windows does not.
Why did only macOS users experience the problem?
macOS requires all applications to have valid code-signing certificates to execute. If a certificate is expired or invalid, the operating system refuses to run the application. Windows doesn't enforce this requirement as strictly, so Windows users running the same software had no issues. This reflects a fundamental difference in security philosophies between the two operating systems.
How did Logitech fix the problem?
Logitech released a patch that included a fresh, valid Developer ID certificate. Users had to manually download and install this patch because the broken application's automatic update system also relied on the expired certificate. Once the patch was installed, users regained access to all customization features, and Logitech confirmed that stored settings and profiles remained intact.
What is a developer certificate and why does it matter?
A developer certificate is a cryptographic credential issued by Apple that authenticates the developer and allows code signing. When an application is signed with a valid certificate, macOS trusts it enough to execute. The certificate includes an expiration date, and Apple requires developers to renew these certificates periodically. An expired certificate signals to macOS that the application should not be trusted to run.
How can organizations prevent certificate expiration issues?
Companies should implement automated certificate monitoring systems that track expiration dates, send alerts at regular intervals (90 days, 60 days, 30 days, and 14 days before expiration), and integrate certificate checks into their CI/CD pipelines. Automating the renewal process where possible and maintaining a centralized inventory of all certificates in use can also prevent oversights.
What does this incident reveal about software security and reliability?
This incident illustrates the tension between security and resilience. While Apple's strict code-signing requirements make macOS more secure against malware, they also create brittle failure modes where a single administrative mistake can affect thousands of users. It highlights the need for better automated certificate management and the risks of having single points of failure in critical systems.
Should users be concerned about Logitech's software reliability going forward?
Logitech handled the situation well by quickly acknowledging the mistake, issuing a public apology, and releasing a fix within hours. However, this incident demonstrates that infrastructure failures can happen at any company. Users should feel more confident after seeing how Logitech responded, though the incident does raise questions about their certificate management processes.
What's the difference between macOS and Windows code-signing requirements?
macOS mandates code signing with valid certificates and enforces this at the kernel level; unsigned or invalid-certificate applications cannot run. Windows treats code signing as optional and relies more on user choice and Smart Screen warnings. macOS's approach is more secure against malware but less forgiving of certificate management mistakes.
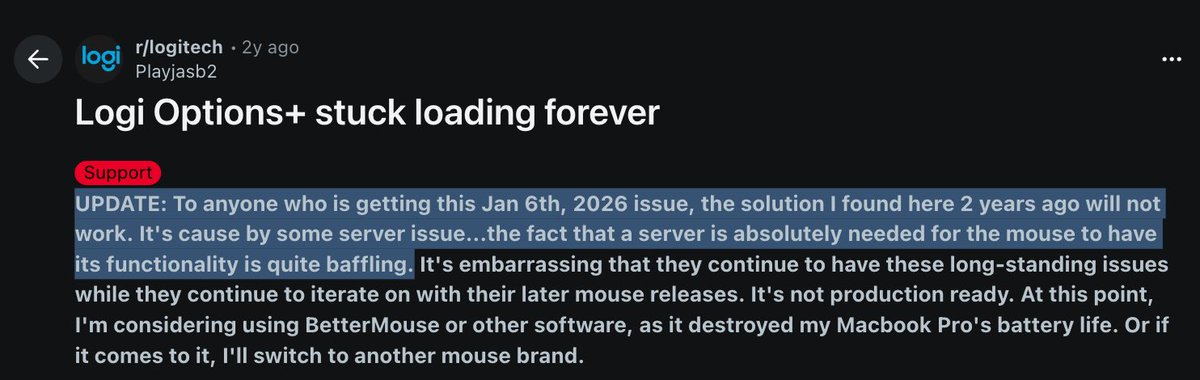
The Bottom Line: Infrastructure Matters More Than You Think
Logitech's certificate expiration incident seems trivial on the surface. A company forgot to renew a certificate. Users experienced temporary inconvenience. A fix was released. Problem solved.
But beneath the surface, this incident reveals something profound about modern software: infrastructure and operational discipline matter more than features or marketing.
A company can design the best mouse in the world, implement cutting-edge customization features, and deliver exceptional hardware. But if they can't manage their software deployment pipeline correctly, all of that excellence becomes worthless the moment something goes wrong.
This is why major tech companies spend so much effort on DevOps, infrastructure automation, and operational reliability. They've learned—sometimes painfully, as Logitech just did—that what kills companies isn't bad features; it's bad operations.
For Logitech users, the takeaway is simple: check for that patch and install it if you haven't already. Your customized mouse settings are waiting to be reclaimed.
For software engineers and infrastructure teams, the takeaway is more significant: treat certificate management like the critical infrastructure it is. Implement monitoring, automate renewals, add checks to your CI/CD pipeline, and make sure someone owns the responsibility. A single administrative task—done consistently and on schedule—can prevent disasters that affect millions of users.
The irony is that preventing this type of failure is actually easier than fixing it after the fact. A few hours of upfront work to set up automated certificate management would have saved Logitech—and thousands of users—hours of frustration.
That's the real lesson here.

Key Takeaways
- Logitech forgot to renew a Developer ID certificate, causing Logi Options Plus and G Hub to fail on macOS due to Apple's strict code-signing enforcement
- Only macOS users were affected because Apple requires valid certificates to execute applications, while Windows does not enforce this requirement
- The expired certificate also broke the automatic update system, requiring Logitech to release a manual patch that users had to download and install separately
- This incident exposes critical gaps in certificate management practices and the need for automated monitoring, renewal alerts, and CI/CD pipeline integration
- Organizations can prevent similar failures by implementing centralized certificate inventories, automated monitoring at 180, 90, 30, and 14-day intervals, and automated renewal where possible
Related Articles
- Razer Wolverine V3 Pro Controller Review & Best Price Guide [2025]
- Sony WF-1000XM6 Earbuds: Release Date, Pricing & Specs [2025]
- Best Earbuds & Headphones at CES 2026 [2025]
- Ninja Crispi Air Fryer: Complete Guide to Features, Price & Reviews [2025]
- Samsung Galaxy S26 Launch Date & Price Predictions [2025]
- Best Cat Toys & Interactive Enrichment for 2025
![Logitech Certificate Expiration Broke macOS Mice: What Happened [2025]](https://tryrunable.com/blog/logitech-certificate-expiration-broke-macos-mice-what-happen/image-1-1767789486694.jpg)



