Introduction: When a Security Update Becomes a Security Risk
There's something particularly frustrating about the irony of it all. Microsoft releases a security update designed to patch vulnerabilities and protect your system. Instead, it breaks the system. This isn't some edge case scenario that affects a handful of users in obscure configurations. This is a major operating system update from one of the world's largest technology companies, and it went spectacularly wrong.
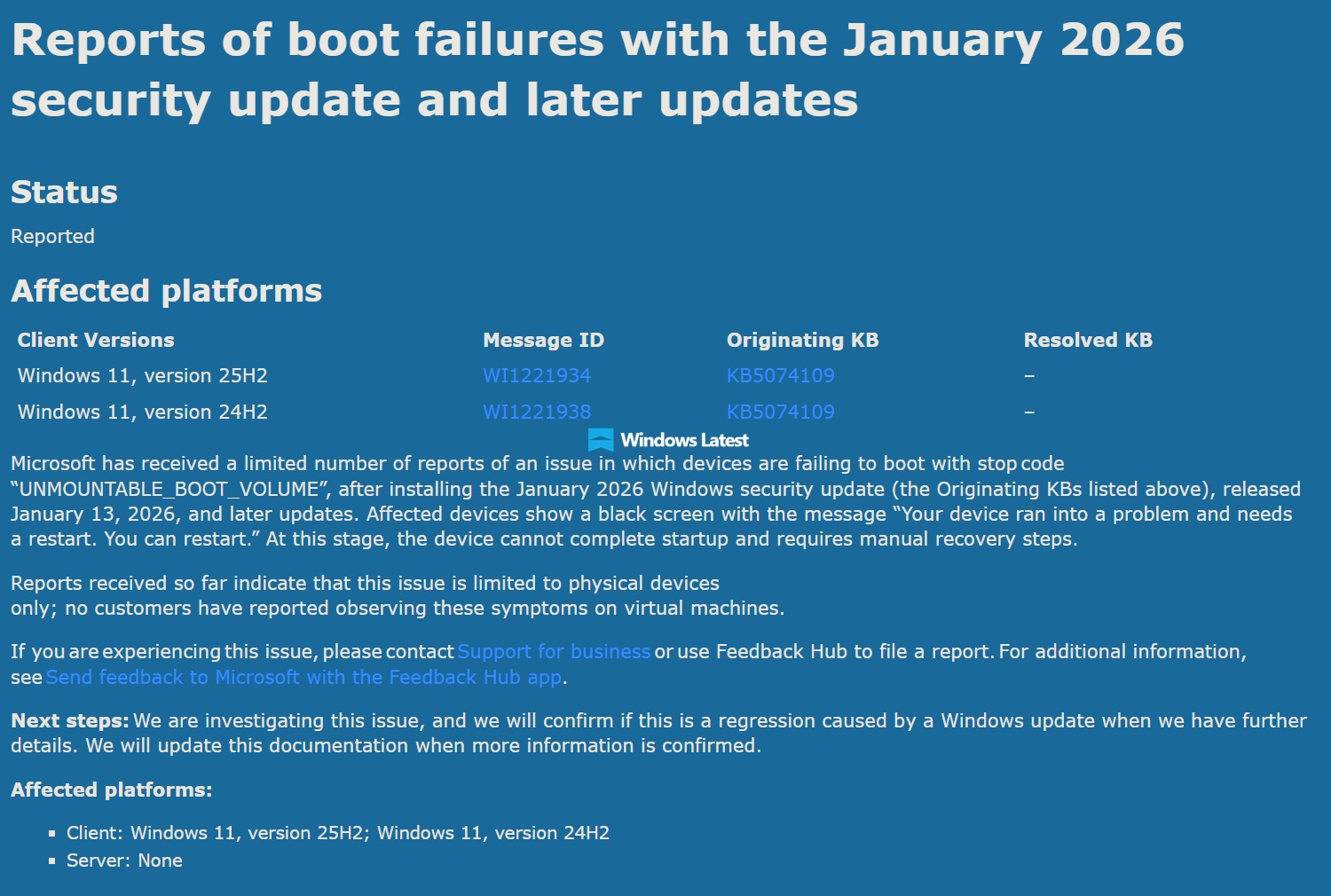
The January 2026 Windows 11 update started as a routine security patch. Microsoft pushes these regularly. They're supposed to be boring. Necessary but boring. You install them, maybe restart your computer, and move on with your life. Except this time, users started reporting their computers wouldn't shut down properly. Then Dropbox started crashing. Then some machines wouldn't boot at all, displaying the dreaded blue screen of death with an UNMOUNTABLE_BOOT_VOLUME error code.
What should have been a normal Tuesday in IT departments across the world became a nightmare. System administrators woke up to tickets flooding in. Users couldn't access their files. Cloud storage syncing failed. Productivity ground to a halt. Microsoft's response was to issue not one, but two emergency out-of-band patches within a week, a rarity that signals something went seriously wrong during the development and testing process.
This situation reveals something important about modern software development. Even with massive resources, extensive testing infrastructure, and decades of experience, catastrophic bugs slip through. The January 2026 update affected different versions of Windows 11 in different ways, targeting Enterprise and Io T editions first, then spreading to consumer versions with version 24H2 and 25H2.
For enterprise users and IT administrators, this became a crisis management situation. For regular consumers, it meant unexplained crashes and boot failures. For Microsoft, it raised serious questions about quality assurance and testing protocols. Understanding what happened, why it happened, and how to prevent it in the future matters for anyone relying on Windows 11.
This comprehensive guide breaks down the entire situation. We'll examine the specific bugs that emerged, the impact across different Windows versions, the emergency fixes Microsoft deployed, and what this means for the future of Windows updates. Whether you're an IT professional managing hundreds of machines or a home user worried about your laptop, you'll find actionable information here.
TL; DR
- Two emergency patches: Microsoft issued two out-of-band updates within a week to fix the buggy January 2026 Windows 11 release
- Shutdown failures first: Initial reports focused on machines unable to shut down properly, primarily affecting Enterprise and Io T editions
- Cloud sync crashes next: A week later, the second emergency patch addressed One Drive and Dropbox crashes on 24H2 and 25H2 versions
- Boot failures reported: Some machines experienced UNMOUNTABLE_BOOT_VOLUME blue screen errors, requiring manual recovery
- IT admin headaches: Emergency patches released over weekends meant Monday morning scrambles for system administrators managing deployments
- Bottom line: This represents a significant quality assurance failure that disrupted countless organizations and individual users worldwide
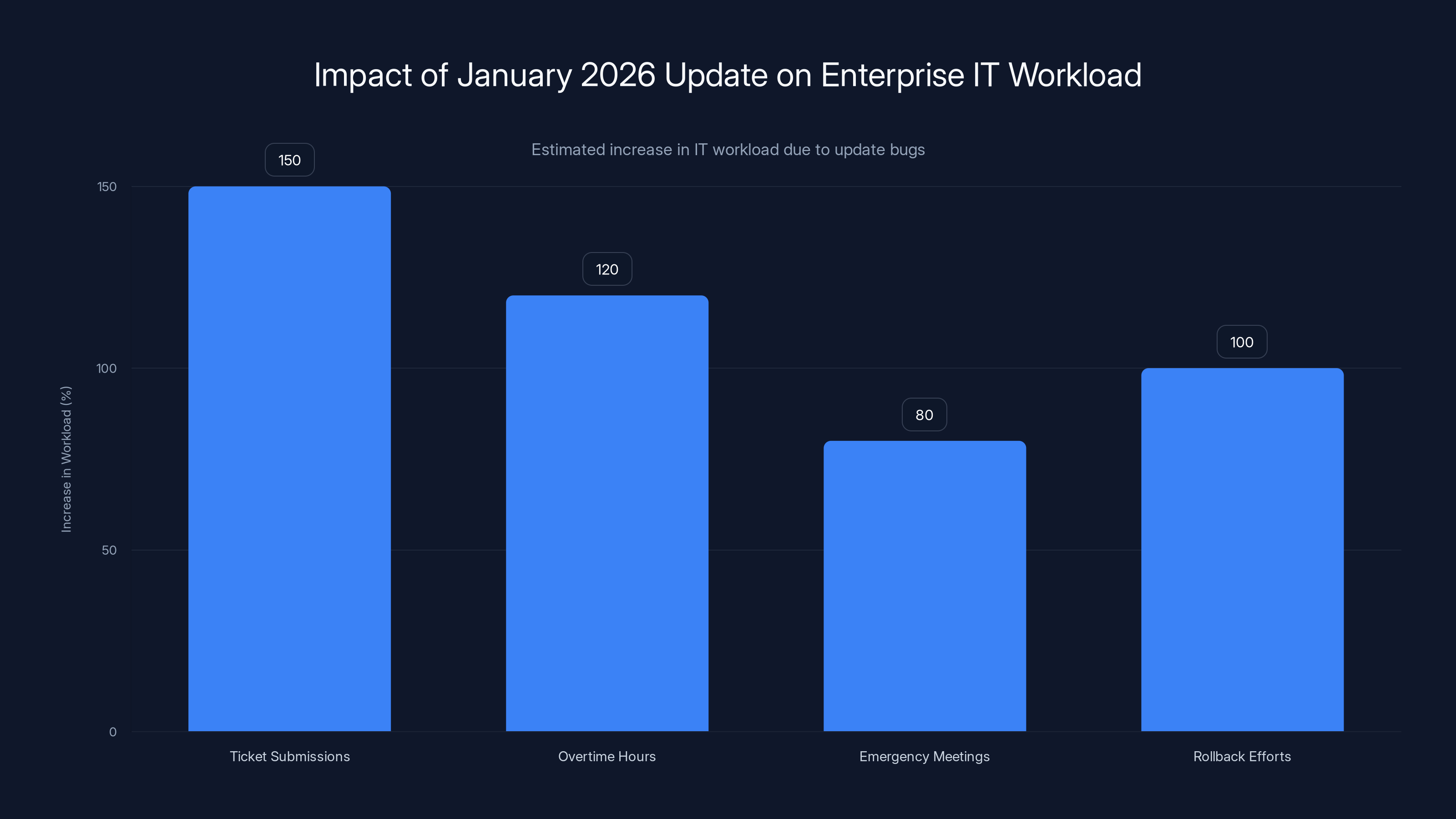
The January 2026 update led to a significant surge in IT workload, with ticket submissions increasing by 150% and overtime hours by 120%. (Estimated data)
The Timeline: How a Security Update Became a Disaster
Understanding when each problem surfaced helps explain how Microsoft missed these bugs and why the remediation process took so long. The events unfolded over approximately two weeks, with each new discovery forcing emergency response.
Initial Reports of Shutdown Failures
When users first reported problems, the symptoms seemed contained and specific. Windows 11 machines running Enterprise or Io T editions started experiencing shutdown failures. The computers wouldn't shut down cleanly. Processes hung, the system seemed to freeze during shutdown, and users resorted to force shutdowns or hard reboots.
This is more than an inconvenience. Improper shutdowns can corrupt data, damage file systems, and leave the machine in an unstable state for the next boot. Enterprise environments particularly depend on clean shutdowns for maintenance windows, updates, and system administration. An enterprise system that won't shut down properly is an enterprise system that's unreliable.
IT administrators across organizations started investigating. They checked logs. They tested isolated machines. They verified hardware configurations. Everything pointed to the same culprit: the January 2026 security update. The correlation was too strong to ignore.
The First Emergency Patch
Within days of the initial reports, Microsoft responded with an emergency out-of-band update. This wasn't part of the normal patch Tuesday schedule. This was an urgent fix deployed to address a critical issue affecting users. The patch specifically targeted the shutdown problem affecting Enterprise and Io T editions.
For many organizations, this was a relief. At least Microsoft acknowledged the problem quickly and deployed a fix. Deploy the emergency patch, verify everything works, and move forward. Except that moving forward turned out to be premature.
Cloud Sync Crashes Emerge
Exactly one week after the first emergency patch, new problems surfaced. This time, the issue wasn't shutdown failures. This time, it was cloud storage. Users running newer versions of Windows 11 (24H2 and 25H2) started reporting Dropbox crashes and One Drive synchronization failures.
These aren't isolated problems either. Dropbox is used by millions of individuals and organizations. One Drive is built into Windows. When cloud sync fails, users can't access their files reliably. Collaborative work becomes difficult or impossible. Organizations that depend on cloud storage for operations found themselves significantly impacted.
The Second Emergency Patch
Microsoft released the second out-of-band patch over a weekend, creating Monday morning chaos for IT departments. Weekend patches are intentional choices. They minimize business impact by deploying during off-hours. But for IT administrators checking email Monday morning, it meant discovering the emergency patch, understanding what it does, testing it, and deploying it to machines while users are arriving at work expecting everything to function normally.
Boot Failures and Ongoing Investigation
While the second emergency patch was being deployed, Microsoft warned IT administrators about another problem: boot failures. Some machines running 24H2 and 25H2 versions were experiencing startup problems, displaying the UNMOUNTABLE_BOOT_VOLUME blue screen error.
Boot failures are severe. A machine that won't boot is a machine that's completely unusable. These machines require manual recovery, often involving recovery media, system repairs, or in-place upgrades. For organizations with hundreds or thousands of machines, even a 1% failure rate means dozens of machines requiring manual intervention.
Microsoft stated it was investigating these boot failures but hadn't confirmed whether the January 2026 update was definitely the cause. This uncertainty added another layer of frustration. IT administrators needed to know: is this the update's fault? Should we hold off deployment? Or is this something else entirely?
The Specific Bugs: What Actually Went Wrong
Each problem that emerged had different symptoms, different affected versions, and different root causes. Understanding the specifics helps explain why Microsoft didn't catch these issues before release.
Shutdown Process Failure Mechanism
The shutdown bug affected computers running Enterprise and Io T editions of Windows 11 version 23H2. When users selected shutdown, the operating system initiated the shutdown process normally. But something in that process hung. Processes didn't terminate cleanly. The system stayed in a partially-shutdown state, consuming power and resources but unable to proceed further.
This suggests the update introduced a change to shutdown handlers or process termination logic that created a deadlock or infinite wait. One process waits for another to finish. That process waits for the first one. Neither can proceed. The system hangs indefinitely.
For Enterprise and Io T environments, this is particularly problematic. These versions are used in business-critical systems, industrial equipment, and managed environments where reliability is paramount. An operating system that can't shut down cleanly undermines its entire purpose as a reliable platform.
Cloud Synchronization Crash Pattern
The One Drive and Dropbox crashes affected machines running 24H2 and 25H2 versions. Both are file synchronization services that run as background processes. When the crashes occurred, users might be working with a document, expecting it to sync to the cloud, and instead watch the sync process crash. The application closes unexpectedly.
This suggests the update introduced a change that interacts poorly with specific file system operations or cloud API calls that both One Drive and Dropbox use. Both services likely became unstable when encountering certain file system states or synchronization scenarios that the update created.
The fact that both One Drive and Dropbox crashed points to a common cause in Windows file system handling rather than service-specific bugs. The update probably changed how Windows handles file system callbacks, metadata operations, or asynchronous I/O in a way that confuses third-party applications expecting stable behavior.
Boot Failure and UNMOUNTABLE_BOOT_VOLUME Error
The UNMOUNTABLE_BOOT_VOLUME blue screen error is the Windows equivalent of "I can't read the disk containing my operating system." This happens when the boot process can't access the storage device or read the file system correctly.
Boot failures could stem from several mechanisms. The update might have changed how the boot loader reads the file system, introduced incompatibilities with certain storage drivers, or damaged boot configuration files during installation. The fact that recovery requires manual intervention suggests the machine's self-healing mechanisms don't automatically fix the problem.
Microsoft initially investigating rather than confirming the update caused boot failures suggests it was trying to rule out firmware, BIOS, or storage driver issues. Previous Windows updates have been incorrectly blamed for problems caused by hardware components. However, the timing correlation was too strong to ignore.
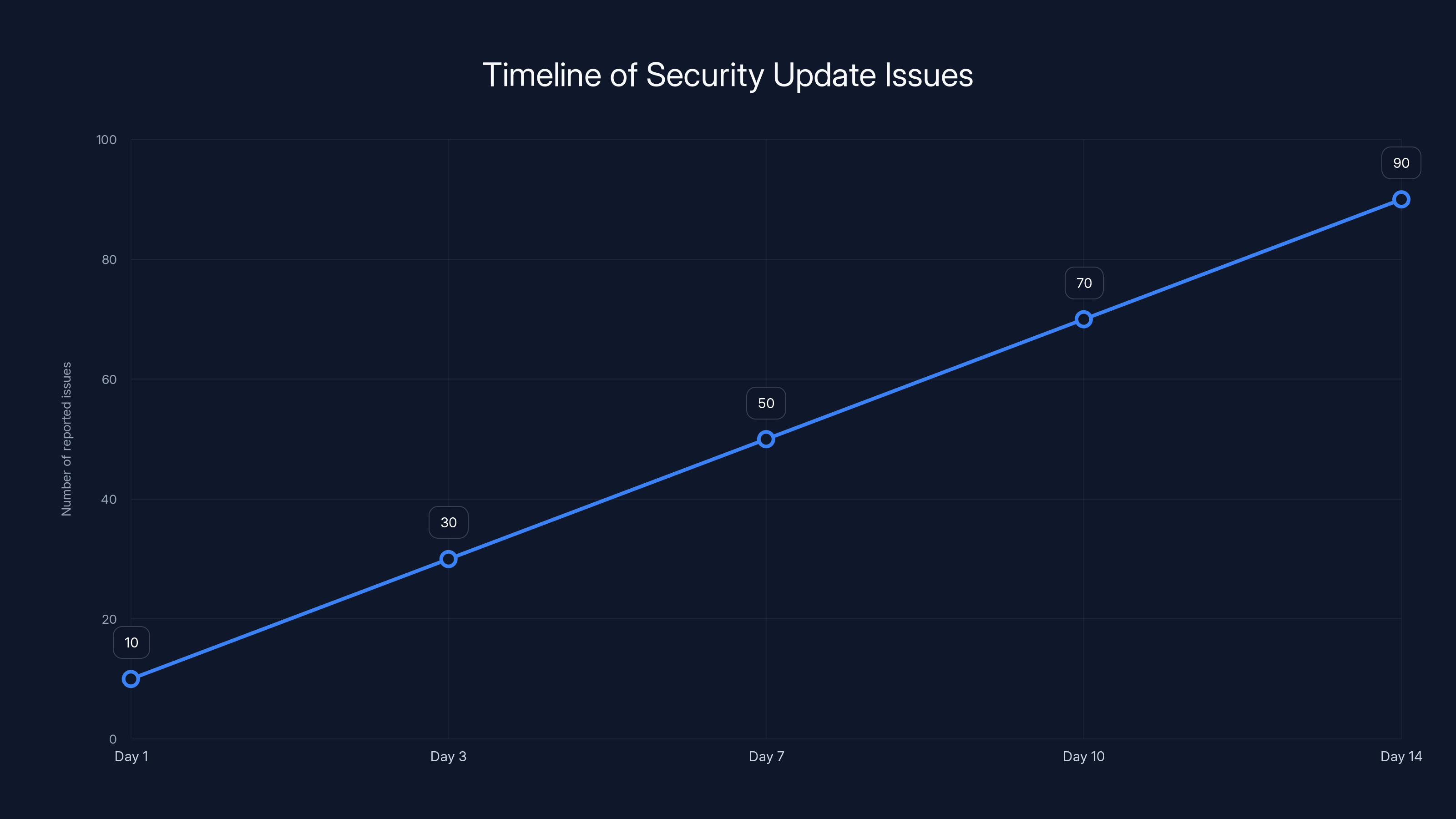
The number of reported issues increased rapidly over two weeks, peaking around Day 14. Estimated data based on narrative timeline.
Windows 11 Version Impact: Why Different Machines Had Different Problems
Not everyone experienced the same issues. The problems varied significantly based on which version of Windows 11 you were running. This fragmentation complicated both user support and Microsoft's response.
Enterprise and Io T Edition Shutdown Issues
Enterprise and Io T editions are different products from consumer versions. They're designed for different use cases. Enterprise editions include additional management features like Group Policy, Bitlocker, and enhanced security controls. Io T editions run on embedded systems, industrial equipment, and specialized devices.
These editions go through different testing pipelines than consumer versions. Yet somehow the shutdown bug still made it through. This raises questions about whether the testing for Enterprise editions is as comprehensive as it should be. Were the test scenarios insufficient? Did the bug only manifest under specific deployment conditions?
Consumer Version Crashes with 24H2 and 25H2
When the crashes emerged in newer consumer versions (24H2 and 25H2), it indicated a different code path than the one used in Enterprise and Io T editions. This is typical in Windows development. Different versions contain different code for different features.
The 24H2 and 25H2 versions represent newer feature sets and architectural changes compared to 23H2. Perhaps the update's changes to file system handling were compatible with older 23H2 code but incompatible with the newer architecture in 24H2 and 25H2.
Version Fragmentation as a Testing Challenge
Maintaining multiple versions of Windows creates exponential testing complexity. A change must be tested on every version, every edition, every supported hardware platform. The more versions and editions you maintain, the higher the chance something slips through.
Microsoft maintains multiple versions simultaneously for compatibility and support purposes. But this fragmentation means testing every permutation of version, edition, and hardware configuration becomes practically impossible. Some combinations are rare enough that they don't get tested, and if a bug only manifests in that combination, it sneaks through to release.
The Testing Question: How Did Microsoft Miss These Bugs?
This is the fundamental question everyone asks. How does one of the world's largest software companies with enormous resources miss problems that affected millions of users? The answer reveals uncomfortable truths about software testing at massive scale.
The Scale of Testing Requirements
Windows runs on billions of devices with different hardware configurations, different installed software, different usage patterns. Testing every possible combination is mathematically impossible. Microsoft can't test Windows on every GPU, every motherboard, every SSD, every combination of hardware that exists.
Instead, companies test representative configurations. Common hardware combinations. Popular devices. Standard enterprise setups. But representative testing can't catch every bug, especially bugs that only manifest under unusual circumstances or rare hardware combinations.
The Gap Between Lab and Production
Laboratory testing environments are clean. Known hardware. Controlled software. No bloatware. No eight-year-old legacy software someone's running from 2015. Production environments are messy. Real users install all kinds of things. They run enterprise applications designed decades ago. They use obscure but essential business software.
The Dropbox crashes hint at this gap. Dropbox is one of the most popular file sync services. It's widely tested. Yet something about the update's interaction with Dropbox's file system operations didn't get caught. Did the testing team use Dropbox at all? Did they test with Dropbox actively syncing when they triggered shutdown or rebooted?
Time Pressure and Release Schedules
Microsoft commits to patch Tuesday. Second Tuesday of every month. Patches are planned, scheduled, and released on that cycle. There's pressure to ship updates on time. When you're under that kind of deadline pressure, shortcuts can happen. Maybe something isn't tested as thoroughly. Maybe an edge case doesn't get validated.
We don't know if deadline pressure contributed to the January 2026 update's issues. But the pattern of shipping broken updates that require emergency fixes the following week suggests something went wrong in the quality assurance process, whether due to time pressure or other factors.
Insufficient User Acceptance Testing
Microsoft offers Windows Insider program for beta testing. Users can opt into pre-release versions and test them before official release. This distributed testing catches bugs that formal QA might miss. But participation varies. If not enough real-world testing happens before release, problems slip through.
The fact that two different, unrelated bugs emerged (shutdown failures and cloud sync crashes) from the same update suggests the testing coverage was incomplete. Multiple independent bugs indicate systematic testing gaps rather than isolated edge cases.
Emergency Response: The Out-of-Band Patch Process
When problems emerge in released updates, Microsoft must respond quickly. The out-of-band patch process exists for exactly these situations. But the process itself reveals weaknesses in how updates are deployed and managed.
First Emergency Patch Deployment
The first emergency patch addressed shutdown failures. Microsoft identified the problematic code, developed a fix, and deployed it outside the normal patch Tuesday schedule. This is the right response. But the fact that such a critical bug made it to release suggests inadequate testing in the first place.
IT administrators had to make decisions: deploy the patch immediately, or wait and see if more problems emerge? Many chose to deploy immediately, which meant unscheduled maintenance, system reboots, and potential disruption.
Testing the Emergency Patches
When an emergency patch drops, IT departments can't test as thoroughly as they'd like. Users are blocked. Systems are broken. There's pressure to fix it immediately. This creates a dangerous situation where the emergency patch itself might have bugs that don't get caught until after deployment.
Fortunately, the emergency patches appear to have worked as intended. But the scenario illustrates the risk created by the initial buggy update. It forces IT departments to make emergency deployments with minimal testing, which could introduce new risks.
Second Emergency Patch and Weekend Deployment
Releasing the second emergency patch on a weekend was a strategic decision. Weekends have lower network traffic and fewer active users, so the patch's rollout shouldn't disrupt work. But it creates Monday morning urgency for IT departments that receive the notification.
IT staff might have been enjoying the weekend, unaware of the emergency patch. Monday morning, they discover it, understand what it fixes, test it if possible, and attempt to deploy it while users are coming online. If something goes wrong, support teams are dealing with failures on the busiest day of the week.

Estimated data suggests that expanding testing infrastructure is the most effective strategy, scoring 9 out of 10 in preventing update disasters.
Impact on Enterprise Environments
Enterprise organizations experienced disproportionate impact from the January 2026 update's bugs. They run thousands or tens of thousands of machines. Even a 1% failure rate means significant problems.
System Administrator Workload Surge
IT administrators who manage these large environments suddenly faced hundreds or thousands of ticket submissions. Users reporting shutdown failures. Users with Dropbox crashes. Users with boot failures. Each of these requires investigation, diagnosis, and potentially manual recovery.
For large organizations, this meant IT staff working overtime. Emergency meetings to determine response strategy. Decisions about which machines to update first, which to hold back, how to prioritize recovery efforts. The cleanup work from a buggy update often exceeds the time required to develop and deploy the fix.
Deployment Strategies and Rollback Decisions
Many enterprises deploy updates gradually. They update a test group first, validate stability, then roll out to broader populations. The January 2026 update's bugs caught some organizations in this process. They might have pushed the update to a test group, encountered the issues, and had to decide: roll back all deployments, or wait for the emergency patch?
Rollback isn't always simple. Once updates are applied, rolling back might require restoring from backup or using system restore points. Some data created after the update might be lost. It's a complex decision with significant implications.
Business Continuity Impact
Shutdown failures, cloud sync crashes, and boot failures don't just affect individual computers. They affect business operations. A file sync crash means lost work. Boot failures mean downtime. Shutdown failures mean machines consuming power but not available for maintenance.
Organizations running on tight IT budgets couldn't absorb the unexpected support costs. Organizations with business-critical Windows systems faced service interruptions. The cumulative impact across organizations dealing with these issues likely cost hundreds of millions of dollars in disrupted productivity.
Consumer Impact: Personal Computers and Reliability
While enterprises had IT departments to manage the crisis, individual consumers just had broken computers. Their experience was frustrating without the organizational support structures enterprises enjoy.
Unexplained Crashes and Mysterious Reboots
A consumer running Windows 11 24H2 or 25H2 might experience Dropbox crashing unexpectedly. They're working on a document stored in Dropbox. The sync process crashes. They might not even realize it's a Windows update causing the issue. They assume Dropbox is buggy or their computer is failing.
These unexplained failures undermine trust in technology. Users start questioning: is my computer reliable? Should I be worried? Am I losing data? Each crash increases anxiety about the system's stability.
Boot Failures and Lost Productivity
A consumer encountering UNMOUNTABLE_BOOT_VOLUME after the update faces a computer that won't start. They can't access their files, their email, their work, their entertainment. For someone not tech-savvy, this is catastrophic. They'll likely take their computer to a repair shop, which might charge hundreds of dollars to fix an issue caused by a Windows update they didn't even want.
Support Burden Shift to Retailers and Support Services
When Windows update causes problems, the support burden doesn't stay with Microsoft. It shifts to retailers like Best Buy Geek Squad, local computer repair shops, and tech support hotlines. These services got flooded with customers affected by the January 2026 update's bugs.
Consumers might blame their computer's manufacturer, blame their internet provider, or blame some other service. The true cause is buried in Windows system files, invisible to end users. The distributed support burden makes the problem's true scope harder to fully quantify.
Comparison to Historical Windows Update Failures
The January 2026 update wasn't the first time Windows updates caused widespread problems. Understanding the pattern helps predict the future.
Windows 10 1903 Update Issues
Windows 10 version 1903, released in May 2019, had a critical bug that caused random file deletion in certain circumstances. Users lost files unexpectedly. It's one of Windows' most infamous update disasters. Microsoft eventually pulled the update and released a fixed version, but not before significant damage occurred.
Print Spooler Vulnerabilities and Patches
The Windows print spooler has been a recurring source of vulnerability and buggy patches. Multiple updates over the years introduced print spooler problems. One major patch broke printing for millions of users worldwide. The print spooler is foundational to Windows, used constantly, making its breakage highly visible and impactful.
Storage Driver Issues (2023)
In 2023, a Windows update was initially blamed for SSD corruption. Extensive investigation eventually showed the root cause was firmware issues with certain SSDs and motherboard BIOS versions, not the update itself. But the correlation was strong enough that the investigation took considerable effort to untangle.
Pattern Recognition
Looking at these failures, a pattern emerges. Major updates sometimes cause widespread issues. When they do, they require emergency response and multiple fix-and-retest cycles. The frequency suggests Windows testing, while extensive, still has significant gaps when it comes to real-world hardware and software combinations.
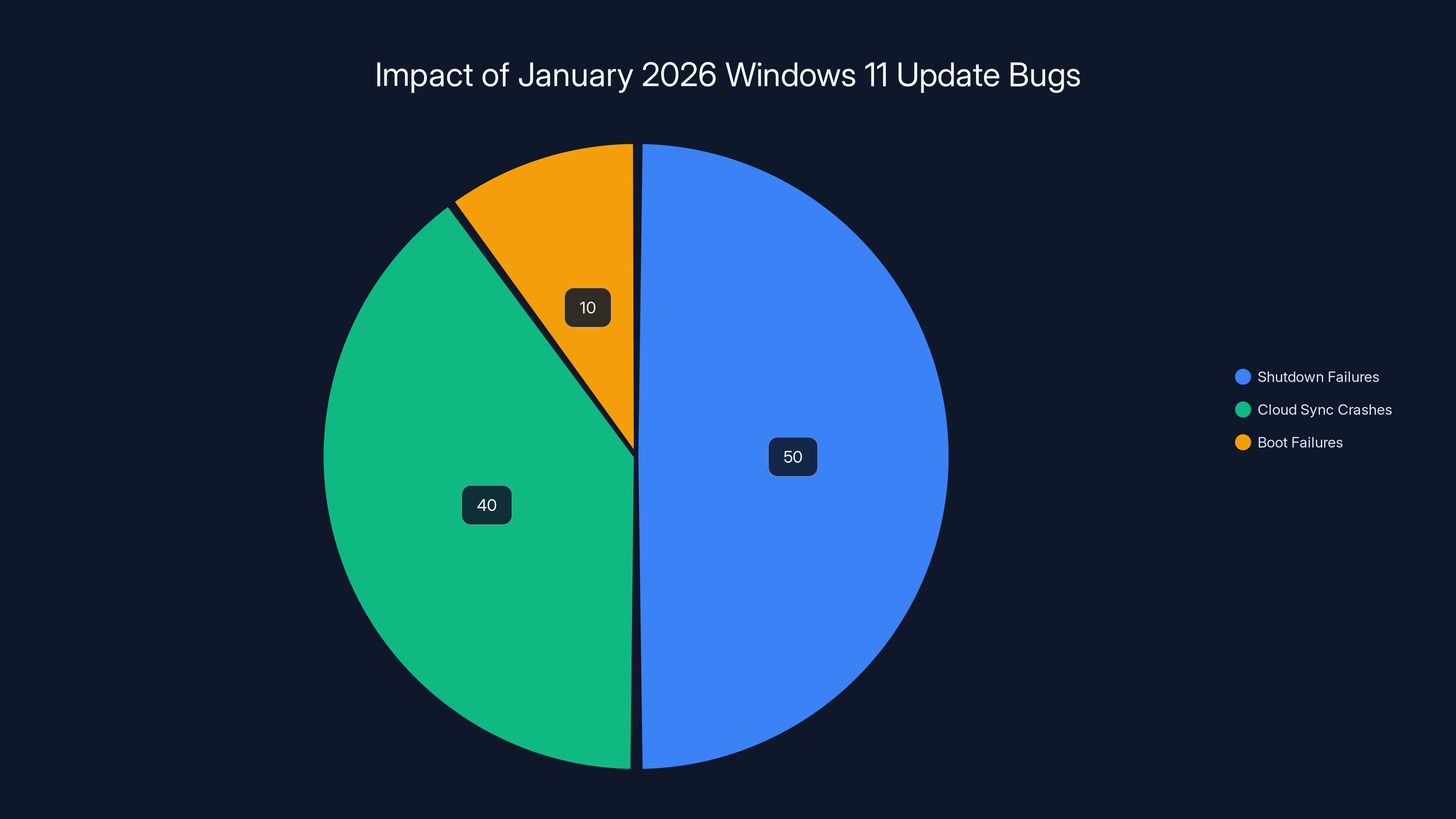
Estimated data suggests shutdown failures affected the majority of systems, with cloud sync crashes also significant. Boot failures, while fewer, caused notable disruptions.
Firmware and Hardware Factors: The SSD Correlation
Microsoft mentioned that a similar issue in the previous year was ultimately caused by firmware and BIOS issues, not the Windows update itself. This raises important questions about whether the January 2026 problems might have similar hidden causes.
Motherboard BIOS Compatibility
Modern Windows updates sometimes interact with motherboard BIOS in ways that aren't obvious. Updates might change how the system reads the disk during boot. Updates might change power management. Updates might change USB device handling. If the BIOS doesn't expect these changes, boot failures result.
Boot failure could partially stem from BIOS versions that don't properly handle the new boot procedure the update introduces. Updating the motherboard BIOS might resolve UNMOUNTABLE_BOOT_VOLUME errors, even though the error appears after a Windows update.
SSD Firmware and File System Operations
SSD firmware handles how data is written to and read from flash memory. If Windows changes its file system access patterns and the SSD firmware doesn't handle the new patterns correctly, file corruption or inaccessibility results. The SSD might fail to respond to file read requests, making the system appear as if the file system is unmountable.
Updating SSD firmware might be necessary to fully resolve some users' boot failure issues, even if the Windows update is the trigger that exposed the firmware's incompatibility.
Testing Hardware Combinations
Windows must support thousands of hardware combinations. Testing all of them is impractical. Microsoft tests popular combinations. But users might run obscure motherboards with old BIOS versions, or use older SSDs with outdated firmware. Updates that work fine on tested hardware might fail catastrophically on untested hardware.
This creates a testing coverage problem that's inherent to Windows' universal hardware support model. The update works on tested configurations. It breaks on untested configurations. Users with untested hardware get the broken experience.
The Cloud Storage Angle: Why Dropbox and One Drive?
Two major cloud storage services crashed. This specificity is telling. It suggests the update changed something about file system operations that cloud sync services depend on.
File System Notification Changes
Cloud sync services register for file system change notifications. When a file changes, Windows notifies the service. The service checks the file, uploads changes to the cloud, downloads cloud changes, and keeps everything in sync. If Windows changes how it sends these notifications or how the services process them, sync services break.
The update might have changed file system notification API behavior, timing, or parameters. Code that worked before now receives unexpected data or notifications at unexpected times. The sync service crashes because it encounters a state it wasn't designed to handle.
Asynchronous I/O and Race Conditions
Modern operating systems use asynchronous I/O extensively. An application requests a file operation and continues running. When the operation completes, the system notifies the application. If the update changed how asynchronous I/O notifications work, sync services that depend on these notifications fail.
A race condition might occur where the notification arrives before the application expects it, or doesn't arrive at all. The sync service waits for a notification that never comes, times out, and crashes. Or it receives a notification before the underlying file operation completes, tries to access the file, and encounters an error.
Third-Party Application Compatibility
The crash of two independent services (Dropbox and One Drive, which aren't affiliated with each other) suggests a Windows-level change that both rely on. Both provide background file syncing. Both monitor the file system. Both handle large numbers of files. They likely share architectural similarities that make them both vulnerable to the same Windows change.
This indicates a systemic compatibility issue rather than service-specific bugs. Microsoft changed something fundamental about how file system operations work, and unintentionally broke services that depend on the old behavior.
Mitigation Strategies: Protecting Your System
For anyone running Windows 11, understanding how to protect yourself from similar update problems is essential. You can't prevent Microsoft's bugs, but you can minimize their impact on you.
Update Strategy: Phased Rollout
Don't install updates the moment they're available. Wait a week. Let other users discover issues first. When an emergency patch like those from January 2026 is required, the information becomes public. You can see what went wrong and decide whether to update immediately or wait for the second patch.
For critical security updates, you'll eventually need to install them. But delaying a few days to see if emergency patches get released is a reasonable risk-reduction strategy.
Backup Before Major Updates
Before installing a major feature update, create a complete backup or system image. If the update breaks something, you can restore from the backup. This takes time upfront but saves enormous time and stress if things go wrong.
Windows includes built-in backup tools, and third-party options like Macrium Reflect or Acronis offer more advanced features. Regular backups are good practice for any reason. They're essential before risky operations like major updates.
Disable Automatic Restart
Windows has a tendency to restart immediately after installing updates without giving you a warning. A sudden restart can cause data loss if you have unsaved work. In Group Policy (Edit Group Policy gpedit.msc), search for "Configure Automatic Updates" and set it to notify you before installation rather than automatically restarting.
Monitor System Logs for Problems
After updating, check Windows Event Viewer for errors. Open Event Viewer (eventvwr.msc), navigate to Windows Logs, and check System and Application logs for warnings or errors. Patterns of errors might indicate the update is causing problems before they become catastrophic failures.
Isolate Critical Machines from Updates
If you have machines running critical services or software, isolate them from automatic updates temporarily. Connect them to a separate network or disable Windows Update. You can update them manually once you're confident an update is stable. This takes effort but protects critical systems.
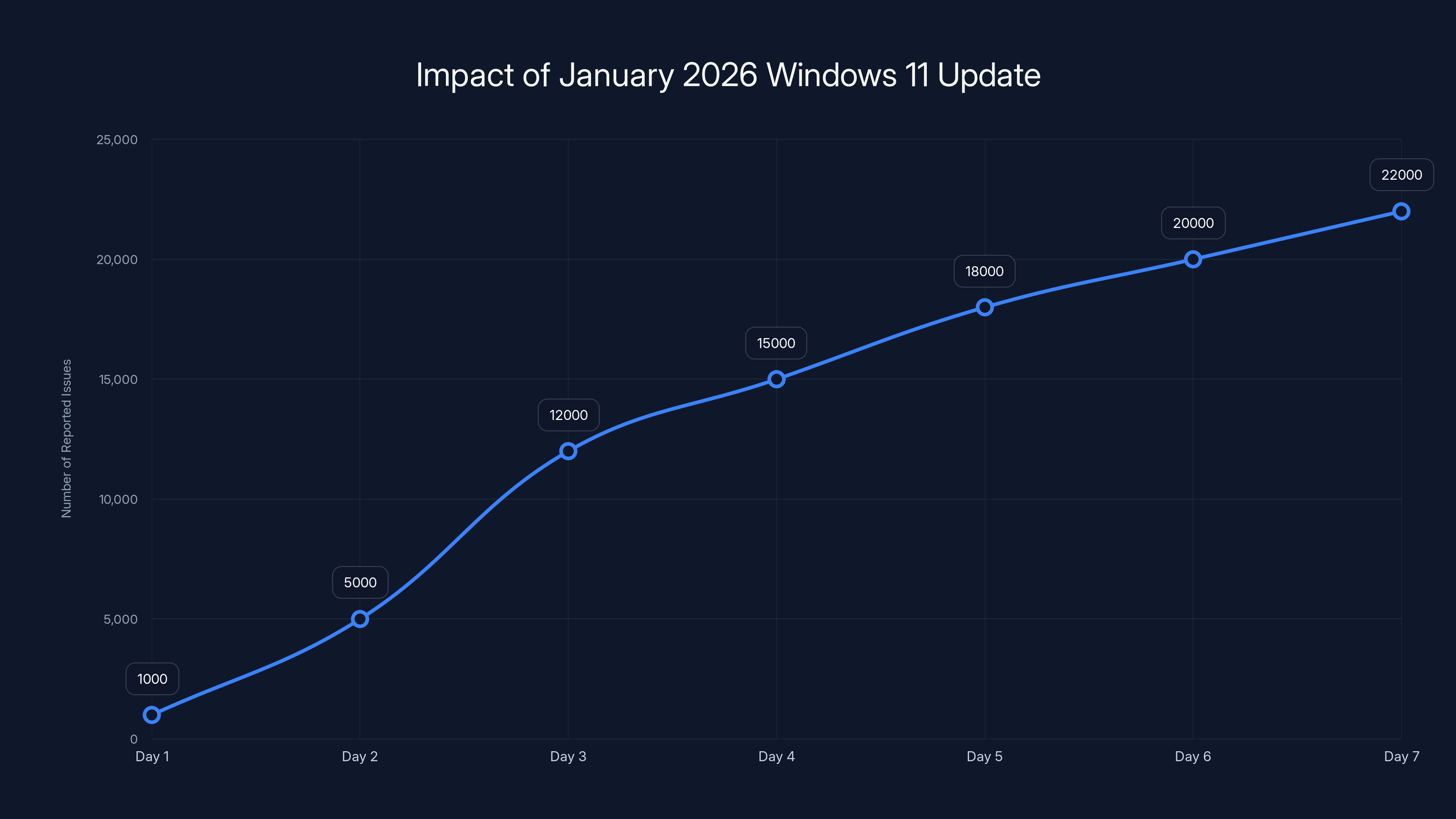
The January 2026 Windows 11 update led to a significant increase in reported issues, peaking at 22,000 by the end of the first week. Estimated data based on typical issue escalation post-update.
Microsoft's Quality Assurance Process: Systemic Issues
Two emergency patches in one week indicates systemic quality assurance problems, not isolated oversights. Understanding what went wrong at Microsoft is important for understanding how this can be prevented.
Testing Coverage Gaps
Obviously, shutdown functionality wasn't tested adequately for Enterprise and Io T editions. Or if it was tested, the testing wasn't comprehensive. Cloud sync compatibility wasn't tested adequately. Or the testing used generic scenarios that didn't catch the specific code paths causing crashes.
Quality assurance is fundamentally about coverage. You're trying to cover as much of the codebase and scenarios as possible. With billions of possible scenarios, 100% coverage is impossible. But when common scenarios like shutdown and file sync break, it indicates testing coverage is insufficient in critical areas.
Regression Testing Failures
Regression testing means testing changes against previously working functionality. When you change how shutdown works, you should test shutdown on every supported Windows edition. When you change file system operations, you should test cloud sync services that depend on those operations.
If Microsoft did perform regression testing, the tests were inadequate. If Microsoft didn't perform regression testing, that's a critical process failure. Either way, systemic change to something as fundamental as shutdown or file system operations needs thorough regression testing before release.
Insufficient Beta Testing
The Windows Insider program exists to catch bugs before release. If the January 2026 update went through the Insider program, the testing there was insufficient. If it didn't, that's a problem. Critical updates should see extensive beta testing.
It's possible the Insider program didn't receive enough participation to discover these bugs. It's possible the bugs only manifest under specific enterprise configurations that Insider testers don't use. But either way, insufficient beta testing indicates a process gap.
Communication Delays
Why did the cloud sync crash issue take a week to emerge? Were Dropbox and One Drive not used during initial testing? Or did the issue take time to manifest under normal usage patterns that weren't captured in the testing scenarios?
If thousands of users experienced shutdown failures on the first day, why weren't cloud sync issues discovered until a week later? This timing gap suggests the testing scenario coverage doesn't match real-world usage patterns well enough.
Looking Forward: Preventing Similar Disasters
The January 2026 update disaster is already happened and damage is done. What matters now is preventing similar issues in future updates.
Expanded Testing Infrastructure
Microsoft should expand its automated testing to cover more scenarios. Shutdown should be tested on every Windows edition with hundreds or thousands of permutations of running services and applications. File system operations should be tested with cloud sync services actually installed and running.
Automated testing at this scale is resource-intensive but necessary for quality. Setting up test infrastructure that runs tens of thousands of scenarios for every release would catch most major bugs before release.
Extended Beta Testing Period
The Windows Insider program should receive every update several weeks before general release. Not just days. Weeks. This gives real users time to discover issues under varied hardware and software configurations.
For critical updates, Microsoft might consider an extended beta period (4-6 weeks) where only Insider builds receive the update. Critical issues should block general release. Only after extended beta testing confirms stability should updates go to general population.
Staged Rollout for General Release
Even after beta testing, updates could be released in waves. First to a small percentage of machines. Monitor for issues. If stability holds, expand to more machines. This approach, common in web services, could prevent a buggy update from affecting all Windows users simultaneously.
Instead of everyone downloading and installing the update immediately, Microsoft could push it to 5% of machines over the first day, 25% over the first week, and eventually all machines over several weeks. Issues discovered in early stages prevent widespread impact.
Automated Hardware Testing
Microsoft has access to data about hardware installed on Windows machines through Windows Update telemetry. Microsoft could use this data to build a representative hardware testing lab. Common GPU, CPU, motherboard, and storage combinations could be tested automatically with every update.
Testing against actual hardware (or at least hardware-accurate emulation) would catch hardware incompatibilities before release. The SSD firmware issue from previous years might have been caught with proper hardware testing.
Cross-Team Compatibility Testing
Microsoft has different teams developing different components of Windows. These teams might not coordinate testing thoroughly. A dedicated cross-team testing function should ensure changes in one area don't break functionality in other areas. Shutdown code changes should trigger file system testing. File system changes should trigger cloud compatibility testing.
The Broader Context: Windows as Critical Infrastructure
Windows 11 isn't just consumer software. It's critical infrastructure. Millions of businesses run on Windows. Hospitals use Windows. Financial institutions use Windows. Transportation systems use Windows. When Windows breaks, critical services break.
Enterprise Dependence and Risk
Large organizations can't simply avoid Windows or switch to other operating systems easily. Their entire infrastructure, applications, and workflows are built around Windows. They're locked in. This dependence means Microsoft has responsibility to maintain high quality standards.
The January 2026 update's impact cascaded through organizations that couldn't easily work around the problems. IT departments couldn't just not deploy the update (security patches are mandatory). They had to deal with the consequences.
Security vs. Stability Trade-off
Security patches fix vulnerabilities. Stability patches preserve functionality. When a security patch breaks functionality, organizations face a dilemma: deploy the security patch and deal with the broken functionality, or delay the patch and accept security risk.
The ideal is security patches that don't break functionality. But when trade-offs happen, many organizations choose immediate security (deploy the patch) because security vulnerabilities are often exploited immediately. Broken functionality is disruptive but not exploited by attackers.
Accountability and Responsibility
Who's accountable for the cost and disruption caused by the January 2026 update? Microsoft bore no direct cost. Organizations and individual users bore the cost. IT department overtime. Disrupted productivity. Repair services. Lost work. The externalities of a buggy update fall on everyone except Microsoft.
This misalignment of incentives is problematic. If Microsoft bore the cost of buggy updates, quality assurance would improve dramatically. But as the situation stands, Microsoft has financial incentive to ship updates quickly, and everyone else has incentive for those updates to be stable. These incentives conflict.
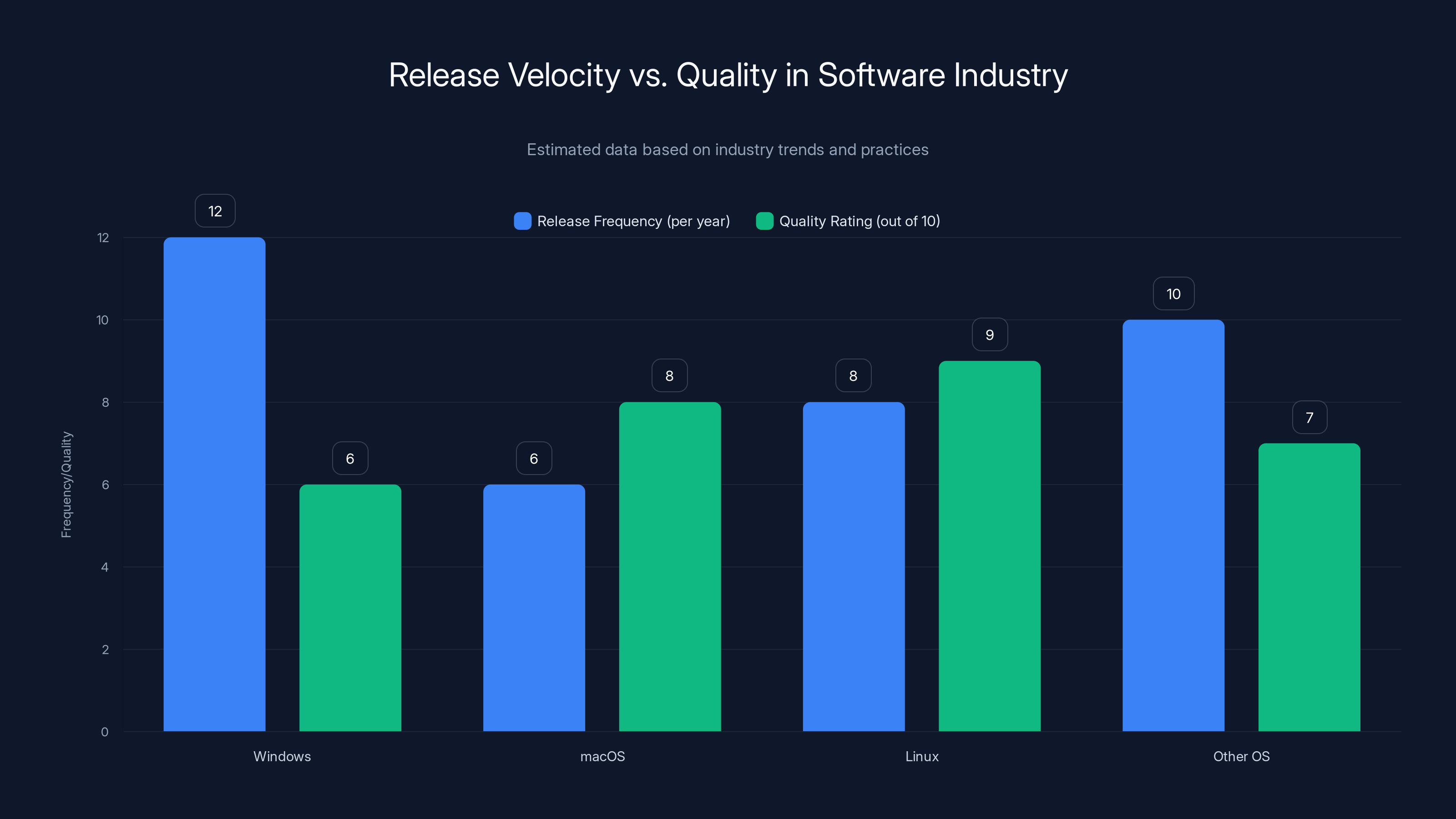
Estimated data shows Windows has a higher release frequency but lower quality rating compared to macOS and Linux, highlighting the tension between release velocity and software quality.
Industry Perspective: Is This Normal?
The January 2026 Windows update disaster might seem like an isolated incident. But in context, it's part of a pattern. Understanding the industry perspective helps understand whether this reflects broader software quality issues.
The Complexity of Modern Software
Modern operating systems are extraordinarily complex. Windows 11 contains tens of millions of lines of code. It supports thousands of hardware combinations. It includes countless interdependent systems. Adding any new feature or fixing any bug creates risk of unexpected side effects.
As software grows more complex, the testing burden grows exponentially. Testing all possible interactions between components becomes impractical. Bugs slip through even with extensive testing.
Release Velocity vs. Quality
The software industry optimizes for release velocity. Ship updates frequently. Ship features rapidly. Respond to competitive pressure. Microsoft faces competition from Apple (mac OS), Linux, and others. Slow, cautious release cycles are commercially risky.
But release velocity and quality are often in tension. Slower cycles allow more testing. Faster cycles ship products before all testing completes. The January 2026 update suggests testing was cut short to meet a release deadline.
Crowdsourced Testing Model
Many software companies have moved toward a crowdsourced testing model. Ship a release to beta testers. Let millions of users test it. Gather telemetry about problems. Push emergency patches when issues emerge. This is faster than traditional testing but relies on affected users to absorb testing costs.
Microsoft seems to follow this model with Windows. The Insider program and rapid emergency patches suggest they expect to find bugs in released versions and patch them quickly. This works most of the time. But when catastrophic bugs make it through, the impact is severe.
Industry Norms and Standards
Compare Windows update stability to other critical software. Aviation software used in flight systems goes through rigorous certification (FAA DO-178C) with extensive documentation and validation. Medical devices go through FDA approval with clinical trials. Financial software often operates on closed networks with extensive testing.
Windows, which is more critical to more infrastructure than many of these specialized systems, has less stringent quality assurance standards. This reflects historical decisions and different regulatory environments, but the disparity is notable.
User Sentiment and Trust Impact
Beyond the immediate technical problems, the January 2026 update damaged user trust in Windows and Microsoft.
Undermining Confidence in Updates
When updates break systems, users become hesitant to install updates. They delay. They disable automatic updates. They try to work around the process. This creates security risk because unpatched systems are vulnerable.
Users who experienced the January 2026 problems will be more skeptical of future updates. They might not trust emergency patches to actually fix problems. They might question whether updates are worth the risk. This skepticism, while understandable, creates security vulnerabilities.
Perception of Windows Quality
People remember catastrophic failures. The January 2026 update will be referenced for years as an example of Windows update problems. This perception affects whether people choose Windows for future projects or recommend it to others.
For organizations evaluating Linux or mac OS as alternatives, the January 2026 disaster becomes evidence supporting the switch. For home users considering Chromebooks, the stability issues with Windows updates become a selling point for the Chromebook.
Support Burden and Reputation
IT professionals and support staff who dealt with the January 2026 problems will have negative feelings toward Windows and Microsoft. They spent their time cleaning up Microsoft's mistakes. They had to explain to frustrated users why their computers didn't work. This personal negative experience shapes their professional opinions about Windows.
When these professionals make technology decisions for organizations, they'll remember their frustration. They'll be more cautious about Windows, more likely to test thoroughly before deployment, and more likely to recommend alternatives when viable.
Lessons for Users and Organizations
Whatever the root cause of the January 2026 update problems, users and organizations can learn from the incident.
Never Assume Updates Are Safe
The update was from Microsoft. It was official. It was a security patch. Yet it broke systems. Never assume any update, from any vendor, is completely safe. Always have a backup plan. Always test before broad deployment. Always be prepared to roll back if needed.
Build In Resilience
Organizations should build resilience into their systems. Don't rely on any single vendor's software being perfect. Use redundancy. Have fallback systems. Design for graceful degradation. If Windows breaks, other systems continue operating.
For individuals, resilience means backups, recovery media, and alternatives. Have data backed up so a boot failure doesn't lose everything. Have recovery media available so you can recover a failed machine. Have an alternative device you can use while a primary machine is being repaired.
Demand Better Quality
Users should demand better quality from software vendors. Ask questions before buying. Check support reviews. Understand vendor's support processes. Prefer vendors with strong quality track records. Vote with your wallet.
For Microsoft, demand for better quality translates to purchasing decisions. Organizations might choose to delay Windows adoption. They might choose Linux servers over Windows servers. They might choose Chromebooks for employees. Market pressure drives vendor behavior more effectively than complaints.
Advocate for Standards and Regulations
Software quality standards vary wildly depending on the industry. Aviation, medical devices, and critical infrastructure have stringent standards. General operating systems have less stringent standards. Advocating for higher standards in software quality, especially for critical infrastructure like operating systems, would improve outcomes.
This might mean supporting regulation that mandates quality assurance standards for operating systems. Or supporting industry initiatives that establish best practices. Or demanding accountability when software failures cause harm.
The Future of Windows Updates
The January 2026 incident will shape how Microsoft approaches updates in the future. Whether Microsoft implements systemic improvements or simply fixes the immediate issues will determine the trajectory.
Potential Improvements
Microsoft might expand testing infrastructure. Might extend beta testing periods. Might implement staged rollout for general release. Might improve communication with affected users. Any or all of these would reduce the likelihood of similar incidents.
The question is whether the January 2026 incident spurs actual changes or becomes a forgotten incident. Large organizations have institutional inertia. Changing testing processes costs money and slows down update cycles. Microsoft might decide the current approach is acceptable and make minimal changes.
Competitive Pressure and Alternatives
If competitors like Apple and Linux distributions maintain more stable update practices, organizations will switch. Market pressure from lost customers is often more effective at driving change than anything else. If the January 2026 update costs Microsoft market share, expect rapid improvements.
User Expectations Evolution
Users expect technology to work reliably. When it doesn't, they get frustrated. Over time, expectations evolve. Users demand better quality. They're more willing to switch to alternatives. They advocate for regulations. These evolving expectations shape how vendors approach quality.
For Microsoft, user expectations for Windows stability are shaped by incidents like the January 2026 update. Each catastrophic failure lowers expectations but also increases demand for improvements. The feedback loop eventually forces improvement if users have viable alternatives.

Technical Deep Dive: What Likely Happened
While Microsoft hasn't released detailed technical analysis of the bugs, we can make informed inferences about what likely happened based on the symptoms.
Shutdown Sequence Changes
The shutdown failure in Enterprise and Io T editions suggests a change to the shutdown sequence or process termination logic. Windows shutdown involves multiple stages. Notifying applications. Closing applications. Stopping services. Flushing disk buffers. Powering off hardware.
The update probably changed one of these stages. Maybe it added validation before powering off. Maybe it changed how applications are notified of shutdown. Maybe it added a new service that must complete before shutdown can proceed.
If the new validation or service logic has a bug (an infinite loop, a deadlock, a condition that's never true), the shutdown process hangs. The system stays powered on but unable to proceed further. Users must force shutdown, which is exactly what people reported experiencing.
File System Metadata Operations
Cloud sync services enumerate file system metadata frequently. They need to know what files exist, what changed, what properties have values. If the update changed how file system metadata is stored or accessed, sync services might become confused.
A change to file system metadata could cause the service to crash when it encounters unexpected data structures. Or it could cause the service to wait for metadata updates that never arrive, timing out and crashing.
MOUNTABLE_BOOT_VOLUME Analysis
Boot failures with UNMOUNTABLE_BOOT_VOLUME suggest the system can't read the boot drive during startup. This could happen if the update changed how the boot loader reads files. Or if the update corrupted boot-critical files. Or if the update introduced incompatibility with certain storage subsystems.
Manual recovery is required because the system's automatic recovery doesn't know how to fix the specific incompatibility the update created. The person must either repair the boot files manually or perform an in-place upgrade.
Practical Advice for Current Users
If you're running Windows 11, here's what you should do in light of the January 2026 update issues.
Check Your Version
First, determine which version of Windows 11 you're running. Press Windows+R, type winver, and press Enter. Look at your version number. If you're running 23H2, 24H2, or 25H2, you were potentially affected.
Verify Updates Are Applied
Open Windows Update settings (Settings > System > Windows Update) and check your update history. Verify that you've installed the latest updates, including any emergency patches released after January 2026.
Create a Recovery Image
If you haven't already, create a Windows recovery image on USB media. Press Windows+X, select System, go to About, and look for "Advanced startup options" or use "Recovery" in the Settings. Follow the prompts to create recovery media. Store this safely in case you encounter boot failures.
Update Third-Party Software
Ensure your Dropbox, One Drive, and other cloud sync services are updated to their latest versions. New versions often include compatibility fixes for Windows updates.
Monitor System Stability
For a few weeks after updating, pay attention to system behavior. Does shutdown work reliably? Do cloud sync services stay running? Are there any odd errors? These observations can catch problems early.
FAQ
What was the January 2026 Windows 11 update supposed to do?
The January 2026 Windows 11 update was a security update designed to patch vulnerabilities and improve system security. Like all monthly security updates, it addressed reported security issues and made changes to security-related code. However, the update also contained bugs that affected shutdown functionality, cloud synchronization, and system boot processes, requiring emergency patches to fix.
How many machines were affected by the January 2026 update bugs?
Microsoft never publicly released specific numbers of affected machines. However, given that shutdown failures affected Enterprise and Io T editions, and cloud sync crashes affected 24H2 and 25H2 versions used by millions, the affected population likely numbered in the tens of millions globally. Boot failures appeared to affect a smaller subset, but their severity meant significant support burden even at low percentages.
Could the UNMOUNTABLE_BOOT_VOLUME error be caused by something other than the January 2026 update?
Yes, boot failures can stem from many causes including firmware issues, corrupted disk sectors, incorrect BIOS settings, or failing storage devices. Microsoft's cautious language about investigating the boot failures reflects this. However, the timing correlation with the update release and reports of boot failures immediately following update installation strongly suggest the update as a primary cause for many users, even if hardware factors also contribute in some cases.
Why did it take a week for the cloud sync crashes to be discovered if shutdown failures were immediately reported?
The shutdown failures directly prevented system operation, becoming immediately obvious. Cloud sync crashes might only manifest under specific conditions: when both the cloud service and the system are actively syncing files, or with certain file types, or under particular network conditions. These conditions might not have been present during initial testing or early real-world usage, explaining the one-week delay before reports accumulated and became statistically obvious.
Are Windows 11 updates currently safe to install?
Windows 11 updates are generally safe, but the January 2026 incident illustrates that issues can occur. Prudent practice involves waiting a few days after update release before installing, monitoring for emergency patch releases, and maintaining backups before major updates. Critical security updates should be installed promptly, but routine updates can be delayed slightly to see if issues emerge in the early-adopter population.
How can I avoid experiencing similar update problems in the future?
You can reduce risk by maintaining regular backups, creating system images before major updates, monitoring system stability after updating, enabling detailed logging to catch problems early, and staggering updates across your systems. For organizations, phased deployment where you test updates on isolated machines before broad rollout significantly reduces the impact of problematic updates.
Did Microsoft face any consequences for the January 2026 update problems?
Microsoft's immediate responses (emergency patches) prevented the situation from becoming worse. However, the financial and reputational costs fell mainly on organizations and users who experienced disruption, not on Microsoft. There were no documented penalties, lawsuits, or formal accountability, illustrating the misalignment between those who bear costs of software failures and those who benefit from rapid release cycles.
What specifically changed in the January 2026 update that caused shutdown failures?
Microsoft never released detailed technical analysis of the specific code changes that caused shutdown failures. Based on the symptoms, it likely involved changes to shutdown sequence logic, process termination handling, or a new validation step that encountered deadlock conditions. Without official documentation, the exact cause remains undocumented.
Can I prevent the January 2026 update from installing on my machine?
You can delay updates by changing Group Policy settings or pausing Windows Update, but you cannot permanently prevent security updates from installing on machines connected to the internet. Eventually, you'll need to install them. Instead of preventing updates, focus on testing them thoroughly before broad deployment and maintaining backups so you can recover if problems occur.
How did emergency out-of-band patches differ from regular updates?
Emergency out-of-band patches are released outside the normal monthly patch cycle to address critical issues discovered in released updates. They bypass the scheduled Tuesday release cycle and get pushed to users as soon as they're developed. They typically receive less extensive testing than regular patches because they're addressing urgent problems, creating additional risk that the emergency patch itself might have issues.
Conclusion: Learning From the January 2026 Disaster
The January 2026 Windows 11 update represents one of the more significant update failures in recent Windows history. Two emergency patches within a week, affecting hundreds of millions of users globally, disrupting enterprise operations, and creating widespread frustration. It's not a story about isolated bad luck. It's a story about systemic issues in how large software platforms are tested, released, and supported.
The immediate causes of the bugs likely involve specific code changes that weren't adequately tested across all supported versions, editions, and hardware configurations. The shutdown failures, cloud sync crashes, and boot failures all point to changes in fundamental Windows systems that interacted poorly with real-world environments. Each bug probably seemed like a reasonable change during development. But combined, they created catastrophic failures.
Microsoft's response was appropriate. Emergency patches within days, second patch within a week, ongoing investigation into boot failures. The emergency response process worked, even if imperfectly. But the fact that such an emergency response was necessary at all indicates systematic issues in how Windows is tested before release.
For organizations, the January 2026 incident should reinforce the importance of testing updates before broad deployment, maintaining backups, and having recovery plans. For individual users, it should encourage skepticism about automatic updates and emphasis on having recovery media available. For Microsoft, it should be a wake-up call that quality assurance needs investment and attention.
Looking forward, the January 2026 update will likely be remembered as a turning point. It might catalyze improvements in Microsoft's testing processes, adoption of staged rollout for updates, or extended beta testing periods. Or it might become a forgotten incident that repeats itself in future years. The outcome depends on whether the incident spurs systemic change or simply results in tactical fixes.
For now, users should verify their systems are updated with the latest patches, maintain backups, monitor for stability, and remember that even updates from major vendors aren't guaranteed to work perfectly. The January 2026 incident is a humbling reminder that in software, complexity creates vulnerability, and vulnerability creates opportunity for bugs to slip through, regardless of how much testing is performed.
The technology industry has come a long way in building reliable systems. But perfect reliability remains elusive. Catastrophic failures will happen again. The question is whether we learn from incidents like the January 2026 update or repeat them endlessly. The answer depends on whether vendors like Microsoft prioritize quality assurance as seriously as they prioritize release velocity.
Key Takeaways
- Microsoft issued two emergency out-of-band patches within one week to fix the January 2026 Windows 11 update's shutdown failures, Dropbox crashes, and boot failures
- Different Windows 11 versions experienced different bugs: Enterprise/IoT had shutdown issues, consumer versions had cloud sync crashes, and some machines encountered boot failures
- Emergency patches released over weekends created significant burden for IT administrators who had to deploy patches Monday morning while users came online
- The incident reveals systemic quality assurance gaps in Windows testing, including insufficient regression testing and inadequate coverage of real-world hardware/software combinations
- Cloud sync service crashes point to fundamental Windows file system changes that affected third-party services, indicating inadequate compatibility testing before release
- Organizations should respond to the incident by implementing phased update rollout, maintaining backups, creating recovery media, and delaying non-critical updates to observe for issues
- Microsoft's quality assurance process needs expansion of automated testing infrastructure, extended beta testing periods, staged rollouts, and cross-team compatibility testing
- Historical context shows Windows updates have repeatedly caused widespread problems (Windows 10 1903 file deletion, print spooler issues, 2023 SSD correlation issues), indicating a pattern rather than isolated incidents
Related Articles
- I Spent a Year on Linux and Don't Miss Windows [2025]
- Microsoft Deployment Toolkit Deprecated: What It Means for Your Infrastructure [2025]
- How to Disable Copilot on Windows 11 Work Devices [2025]
- Why PCs Don't Need AI: Dell's Marketing Reality Check [2025]
- Logitech's macOS App Disaster: What Happened & How to Fix It [2025]
![Windows 11 January 2026 Update: Complete Guide to Issues & Fixes [2026]](https://tryrunable.com/blog/windows-11-january-2026-update-complete-guide-to-issues-fixe/image-1-1769431031203.jpg)



