Brightspeed Data Breach Investigation: What Happened & What's Next [2025]
When a major broadband provider gets hit with a data breach, it's not just a corporate problem anymore. It's your problem. Your name, email, phone number, and potentially partial payment information could be in the hands of cybercriminals. That's exactly what happened to Brightspeed, one of the largest fiber broadband companies operating across the United States.
Last weekend, a hacking group calling itself the Crimson Collective announced on Telegram that they'd stolen personally identifiable information (PII) on over one million Brightspeed customers. The group made a bold claim: they had access to names, emails, phone numbers, postal addresses, user account information, payment history, and partial payment card details. And they weren't subtle about it.
"If anyone has someone working at Bright Speed, tell them to read their mails fast! We have in our hands over 1m+ residential user PII's," the group announced, threatening to release samples if the company didn't respond to their demands.
Here's the thing: Brightspeed hasn't confirmed the breach yet. The company is "investigating reports of a cybersecurity event," according to their statement to security researchers. But that investigation window is critical. For millions of Americans relying on Brightspeed for internet service, the uncertainty is almost worse than confirmation.
This breach matters because it reveals vulnerabilities in the infrastructure that connects millions of American homes and businesses. It also raises serious questions about how major telecom companies protect customer data, what happens when they fail to do so, and what you should do if you're affected.
TL; DR
- The Breach: Crimson Collective claims to have stolen PII on 1M+ Brightspeed customers, including names, emails, phone numbers, and partial payment data
- What Brightspeed Says: The company is investigating but hasn't confirmed the breach or provided customer notifications
- Affected Data: Names, emails, phone numbers, postal addresses, user account info, payment history, and partial payment card data
- Who's Affected: Anyone with an active or recent Brightspeed account across 20 states
- What to Do: Monitor credit reports, enable fraud alerts, consider credit freezes, and change passwords
Paying a ransom might seem cost-effective at
Who Is Brightspeed and Why Does This Matter?
Brightspeed isn't some obscure regional ISP. The company operates one of the largest fiber broadband networks in the United States. Based in Charlotte, North Carolina, Brightspeed was formed in 2022 when Apollo Global Management acquired local exchange assets from Lumen Technologies. Since then, the company has rapidly expanded its footprint across the country.
Today, Brightspeed operates high-speed fiber broadband and traditional internet services across 20 states in the Midwest, Southeast, and Mid-Atlantic regions. The company has passed over two million homes and businesses with fiber infrastructure. That's significant infrastructure. That's significant scale. Their stated goal is to reach over five million locations and serve approximately 7.3 million premises in their service territory.
We're talking about a company generating around $1 billion in annual revenue, backed by multibillion-dollar capital investments and government grant funding. This isn't a startup. This isn't a small regional player. This is a major telecommunications infrastructure provider.
When a company of this size experiences a data breach, it affects millions of people across multiple states. It's not just about the immediate data loss. It's about the downstream consequences: identity theft, fraudulent charges, spam, phishing attacks, and worse.
The company provides broadband to residential and business customers, which means the breach potentially affected both consumer and business accounts. If you're a small business owner in one of Brightspeed's service areas and your business account info was compromised, that's a different level of problem than residential data theft.

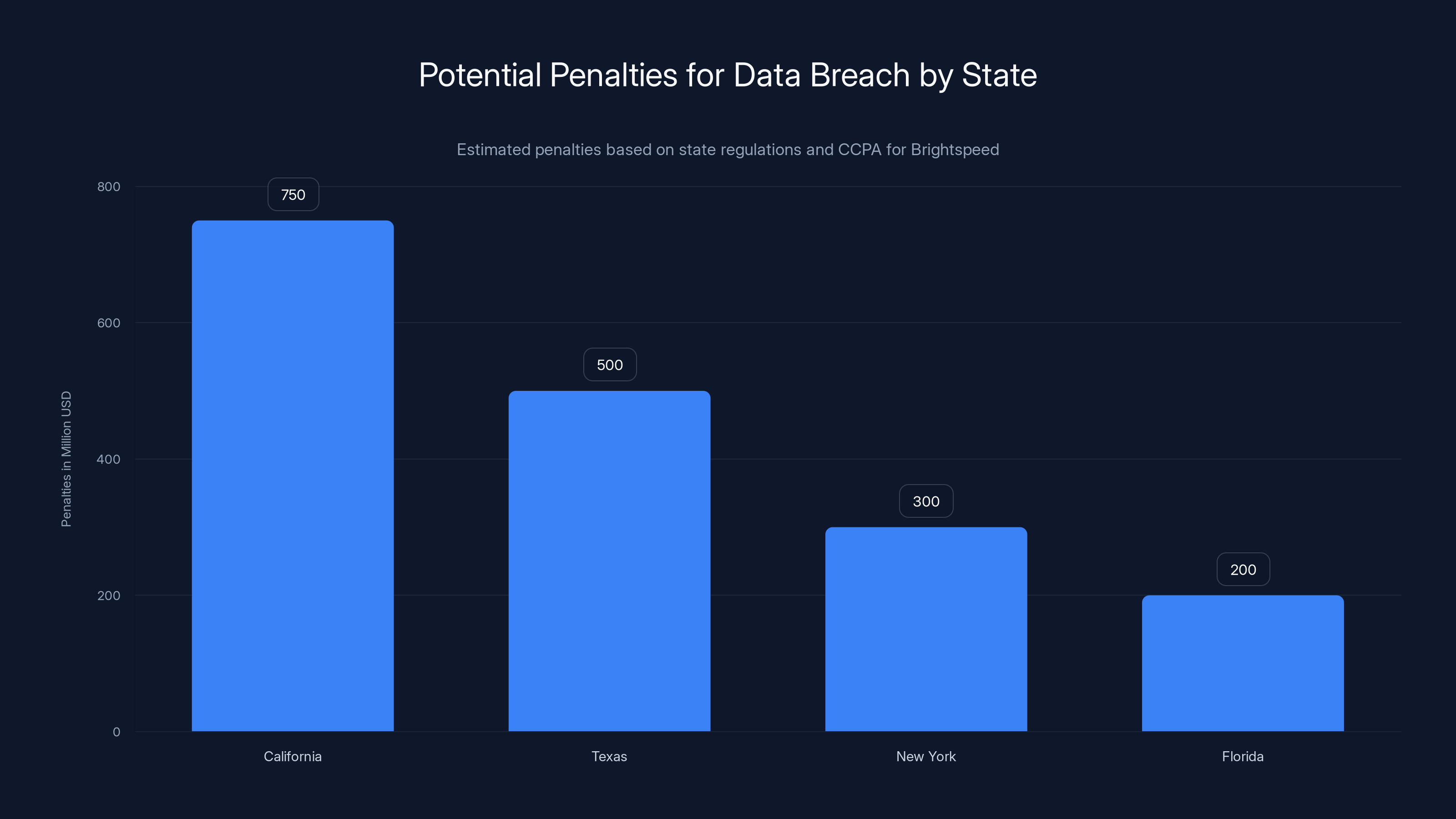
Estimated data shows California has the highest potential penalties due to CCPA, reaching up to $750 million, highlighting the significant financial risk of data breaches.
The Crimson Collective: Who Are They?
Understanding the threat actor behind this breach is important. The Crimson Collective is a relatively new name in the cybercriminal landscape, but the group demonstrates sophisticated operational security and technical capability.
The group announced the breach on Telegram, a messaging platform popular among cybercriminals because of its encryption and privacy features. They posted to a public channel, which is a common tactic for threat actors who want to build reputation, attract customers, or negotiate with targets.
The fact that they specifically mentioned releasing "samples" on a deadline is significant. This is extortion language. They're saying: "Prove you have what you claim, then negotiate." This is standard operating procedure for extortion-driven data theft operations. The group is essentially running a business model: steal data, threaten to release it, negotiate payment, then either release or delete the data depending on the outcome.
Crimson Collective's tactics suggest they're not amateur hackers working out of a bedroom. The operation to steal PII on over one million customers requires either direct database access, compromised credentials, or exploitation of a significant vulnerability. That's not trivial. That requires technical sophistication.
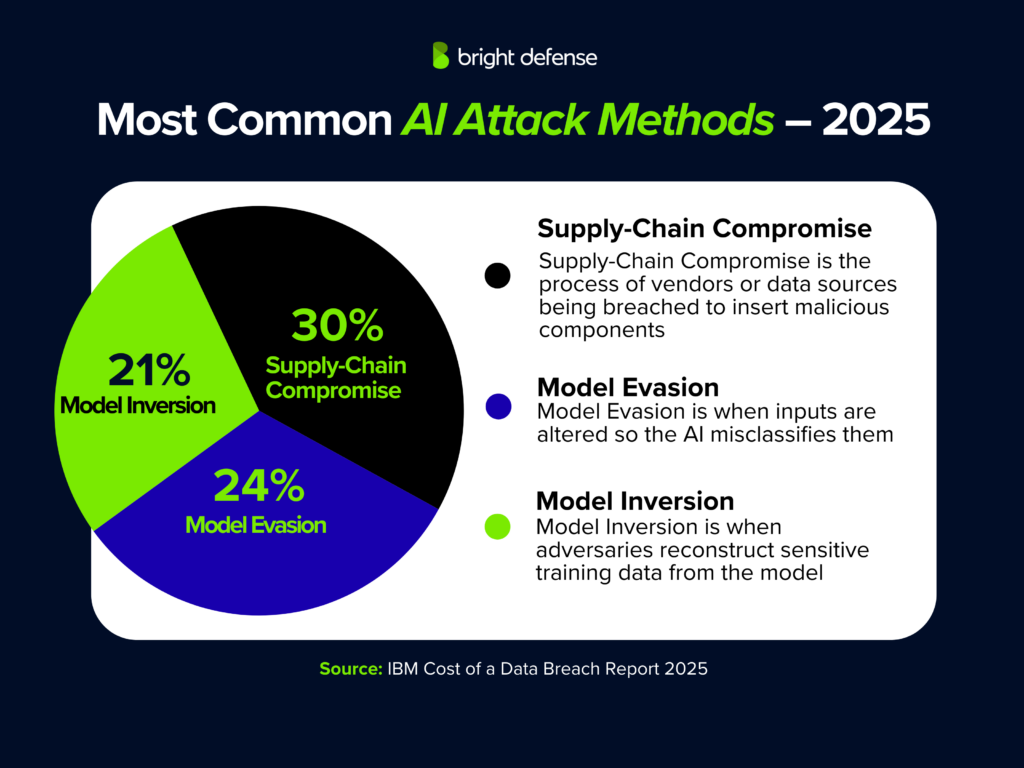
We don't know yet how they got in. Was it a vulnerability in Brightspeed's systems? Compromised employee credentials? Supply chain attack? Third-party vendor with access? Until Brightspeed completes its investigation, we're operating in the dark.
What we do know is that Crimson Collective exists within an ecosystem of organized cybercrime. They likely operate from a jurisdiction with limited cybercrime enforcement, possibly Eastern Europe or Southeast Asia based on typical threat actor patterns. They probably have experience in extortion, data sales, and leveraging stolen information.

What Data Was Actually Stolen?
The Crimson Collective's claims are specific. They say they have access to: names, email addresses, phone numbers, postal addresses, user account information (linked to session/user IDs), payment history, partial payment card information, and appointment/order records.
Let's break this down. We're not talking about encrypted passwords here. We're talking about personally identifiable information that directly ties to real people in the real world.
Names and email addresses are the foundation of identity theft. These are the easiest data points to use for phishing, spam, and impersonation. Someone with your name and email can sign up for accounts in your name, reset passwords on your existing accounts, or simply spam you with malicious emails.
Phone numbers are particularly valuable in the modern threat landscape. Your phone number is often used as a secondary authentication factor. It's used for SMS-based two-factor authentication, password resets, and account recovery. In the wrong hands, a phone number can be used for SIM swap attacks, where a criminal convinces a cell carrier to port your number to a device they control.
Postal addresses enable mail interception and fraud. Someone with your address can intercept account notifications, billing information, and correspondence that could expose you to additional theft.
User account information linked to session IDs is serious. This suggests the attackers got more than just a customer database dump. Session IDs and user account identifiers suggest they may have accessed active account information, authentication tokens, or system identifiers that could be used to access accounts.
Payment history tells a story about your financial situation. Who you've paid, how much, and when. This data can be used for targeted phishing, fraud prediction, and financial crime.
Partial payment card information is the key phrase here. "Partial" means not the full 16-digit number. But even partial card numbers, combined with other data, can be used for fraud. And partial card data in combination with names, dates, and other information can be used to guess or derive full card numbers.
The fact that it's partial and not full card data suggests either Brightspeed had some level of payment card encryption in place, or the attackers couldn't extract the complete card numbers. That's one small win in an otherwise devastating breach.
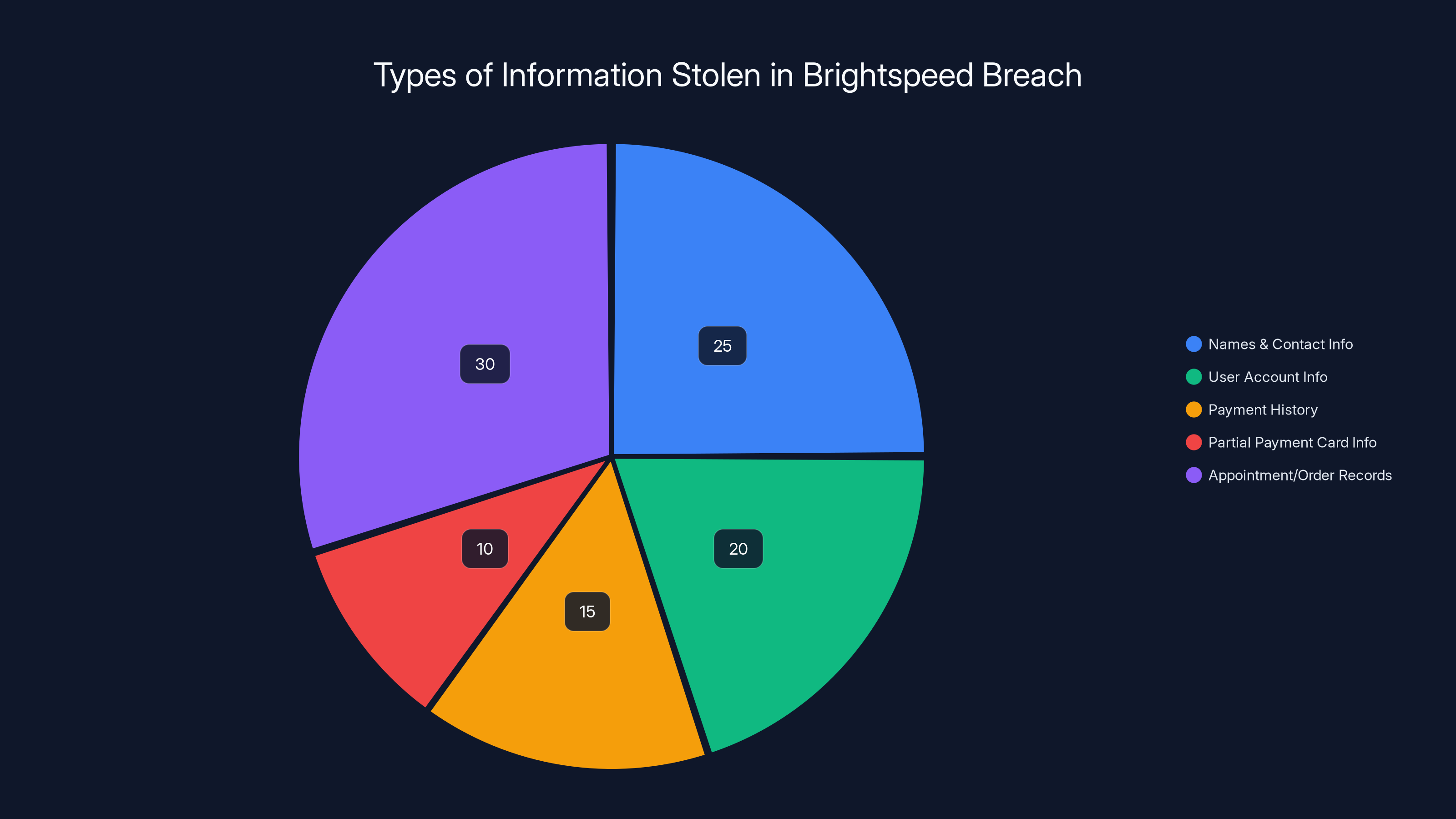
The breach exposed various types of personal information, with appointment/order records being the most affected. Estimated data based on typical breach patterns.
Brightspeed's Response (and Non-Response)
As of the investigation's launch, Brightspeed has not confirmed the breach publicly. There's no post on their website. No notification email to affected customers. No press release. Nothing. The company's statement to cybersecurity media outlets was measured and cautious: "We take the security of our networks and protection of our customers' and employees' information seriously and are rigorous in securing our networks and monitoring threats. We are currently investigating reports of a cybersecurity event. As we learn more, we will keep our customers, employees and authorities informed."
That's corporate speak for "We're not admitting anything yet, but we're looking into it."
This approach makes sense from a legal standpoint. Brightspeed's lawyers probably told them not to confirm anything until they understand the scope. Confirmation triggers legal liability. It triggers regulatory obligations. It triggers potential litigation from affected customers. The company is protected (at least temporarily) by the phrase "investigating reports."
But here's the problem: millions of customers don't know if they're affected. They don't know to monitor their credit. They don't know to freeze their accounts. They don't know to change their passwords. They're left in the dark while the company figures out what happened.
This is where the regulatory framework becomes important. Most states require that companies notify affected individuals of data breaches "without unreasonable delay." The clock is ticking for Brightspeed. They can't investigate forever. At some point, they need to either confirm the breach or deny it.
The threat of the Crimson Collective releasing sample data on Monday night also puts pressure on this timeline. If the group releases convincing evidence, Brightspeed's options narrow. They'll be forced to confirm or face a credibility crisis.
What should Brightspeed be doing right now? First, they should preserve evidence. Forensic investigators should be analyzing logs, access patterns, and system changes. Second, they should identify exactly which customer data was accessed. Third, they should notify affected individuals immediately. Fourth, they should work with law enforcement and regulatory agencies.
Instead, we're getting silence and an investigation.
How Did the Breach Happen? The Technical Questions
We don't have confirmed information about how Crimson Collective got access to Brightspeed's customer data. But we can analyze the most likely scenarios based on typical breach patterns.
Scenario 1: Vulnerable Web Application
Broadband providers typically maintain web portals where customers can view bills, manage accounts, and report issues. If Brightspeed's customer portal has a vulnerability like SQL injection, cross-site scripting, or insecure direct object references, an attacker could potentially access the underlying database.
SQL injection is particularly dangerous. An attacker crafts a malicious SQL query that tricks the application into executing unintended database commands. If Brightspeed's developers didn't properly sanitize user inputs or use parameterized queries, an attacker could dump the entire customer database.
This scenario is plausible because customer portals are often complex, often built quickly, and often not subject to the same security scrutiny as core banking or payment systems.
Scenario 2: Compromised Employee Credentials
Another common attack vector is phishing or credential theft targeting Brightspeed employees. An employee with database access gets tricked into revealing their password, or their laptop gets compromised with malware that captures their credentials.
Once an attacker has legitimate employee credentials, they can log into internal systems with the trust that the company's perimeter security has already granted. This is often called the "trusted insider" problem. The attacker looks like an authorized user to the system.
Broadband companies employ thousands of people. Even with security awareness training, some percentage will fall for phishing. It only takes one successful compromise of one privileged account.
Scenario 3: Third-Party Vendor Compromise
Brightspeed likely uses third-party vendors for various services: billing systems, customer service platforms, data analytics, IT support. If any of these vendors are compromised, and if they have access to Brightspeed's customer database, the attack surface expands significantly.
This scenario is particularly concerning because the victim company (Brightspeed) may not even know about the vulnerability. They're relying on their vendors to maintain security.
Scenario 4: API or Integration Exploitation
Modern broadband companies integrate with many systems. Payment processors, mapping services, Io T device platforms, third-party analytics. Each integration represents an attack surface. If an API is misconfigured, uses weak authentication, or exposes sensitive data, attackers can exploit it.
The fact that attackers accessed user account information linked to session IDs suggests they may have gotten into an authentication or session management system. This could indicate API exploitation.
Scenario 5: Supply Chain Attack
Less common but increasingly observed: attackers compromise a company that supplies software or services to Brightspeed. They inject malicious code into a software update or supply malicious infrastructure. Brightspeed installs or uses the compromised software, and the attacker gains access.
This scenario is hard to defend against because the threat comes from trusted suppliers.
Without Brightspeed's forensic analysis, we're speculating. But these scenarios represent the most likely paths to a million-customer database compromise.

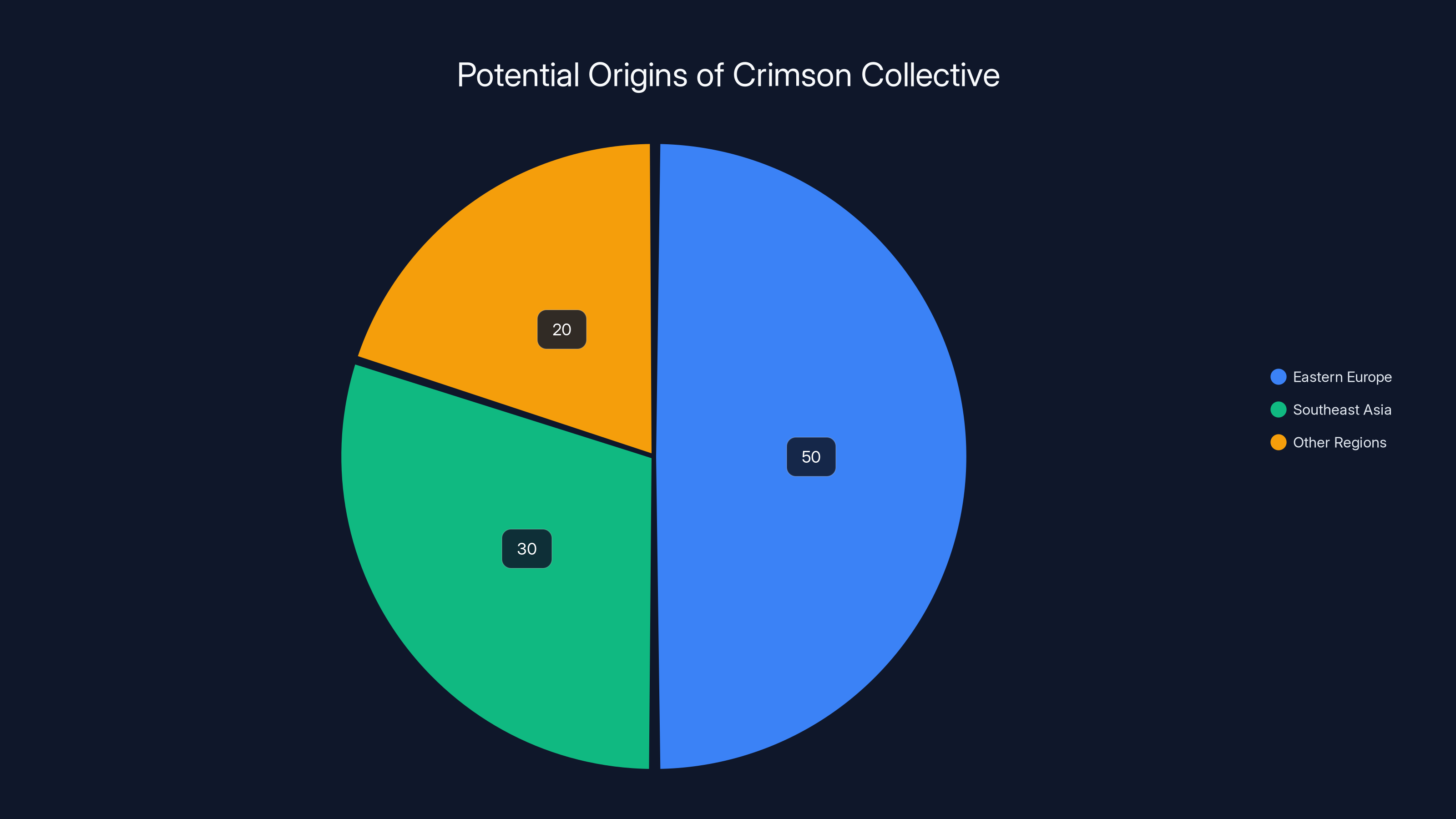
Estimated data suggests that Eastern Europe and Southeast Asia are likely origins for the Crimson Collective, given typical cybercriminal patterns.
The Timeline: Extortion Threats and Investigation Windows
The Crimson Collective gave Brightspeed a specific timeline. They announced the breach on a weekend, threatened to release samples "Monday night," and said they were "letting them some time first to answer to us." This is textbook extortion.
Here's how this typically plays out:
Day 1-2: Threat actor announces breach, makes initial contact/threat
Day 3-5: Threat actor releases proof (sample data) to establish credibility
Day 5-30: Negotiation period. Threat actor and victim discuss price, payment method, proof of deletion
Day 30+: Either payment is made and data is supposedly deleted, or data is released to the public or sold on dark web marketplaces
Brightspeed is currently in day 1-2. They have a narrow window to decide: do they negotiate? Do they refuse? Do they bring in law enforcement?
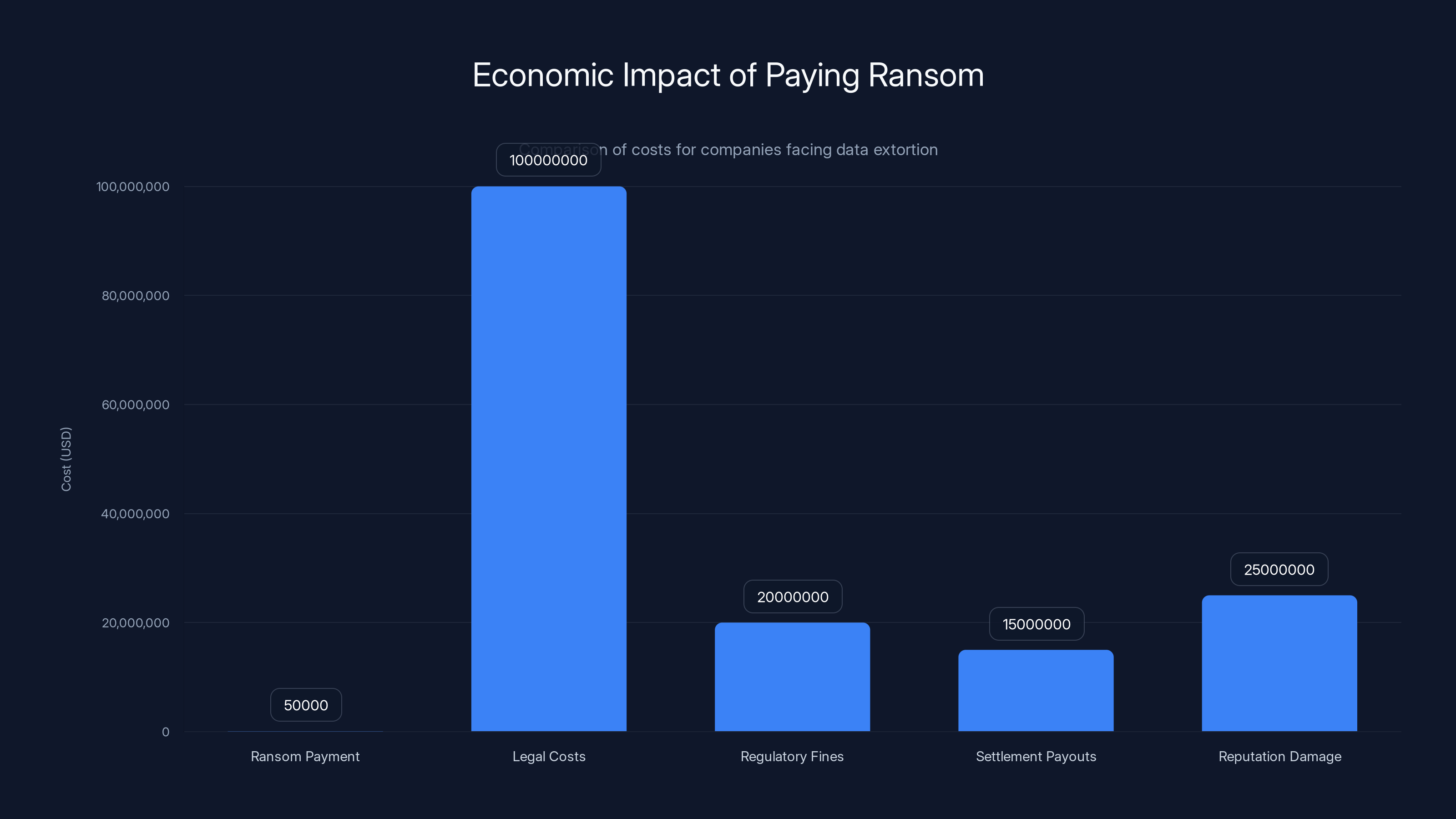
Negotiating with extortionists is generally discouraged by law enforcement, but companies do it anyway. The FBI's position is that paying ransom fuels future attacks. But from Brightspeed's perspective, paying $50,000 to delete stolen data might cost less than the damage from exposure.
The problem with this calculation is that there's no guarantee the threat actor will actually delete the data. They could take the money and release it anyway. Or they could sell it multiple times to different buyers. Trust is not part of this equation.
The realistic timeline suggests Brightspeed will either confirm the breach this week, or wait until they have more information. Either way, customers need to act now.

Regulatory and Legal Implications
When a major data breach happens involving US customers, multiple regulatory frameworks kick into gear.
State Breach Notification Laws
Every US state has a breach notification law. The specifics vary, but they generally require companies to notify affected individuals of breaches "without unreasonable delay" or "in the most expedient time possible." Some states require notification within 30 days. Others are more flexible.
Brightspeed operates in 20 states, so they need to comply with 20 different state laws. That's complex. Some states (like California) have stricter requirements and bigger penalties. California's Consumer Privacy Act (CCPA) allows for civil penalties up to
Those numbers get regulators' attention. The California Attorney General has a team dedicated to data breach enforcement. They're watching.
FTC Safeguards Rule
Telecommunications companies are regulated under the FTC's Safeguards Rule, which requires "reasonable" security measures to protect customer information. The FTC will likely investigate whether Brightspeed's security was actually reasonable. If they find it wasn't, they can impose significant penalties and demand security improvements.
SEC Disclosure Requirements
Brightspeed is likely privately held, but if they have public shareholders or bonds, they may need to disclose material information about the breach. Data breaches involving millions of customers can affect company valuation and financial health.
Criminal Investigation
The FBI and other law enforcement agencies will likely investigate. The Computer Fraud and Abuse Act makes it illegal to access computer systems without authorization. Extortion related to stolen data is also a federal crime. If authorities can identify and prosecute the Crimson Collective members, they face federal charges.
The challenge is jurisdictional. If the threat actors are operating from outside the US, extradition becomes difficult. But the FBI has ways of applying pressure through international law enforcement cooperation.
Class Action Litigation
Affected customers will likely sue. The lawsuits will claim negligence, breach of fiduciary duty, and violations of various consumer protection laws. Class actions often result in settlements that include compensation, free credit monitoring, and injunctions requiring the company to improve security.
For Brightspeed, this means legal fees, settlement costs, and management distraction. The actual dollar amount can be substantial.

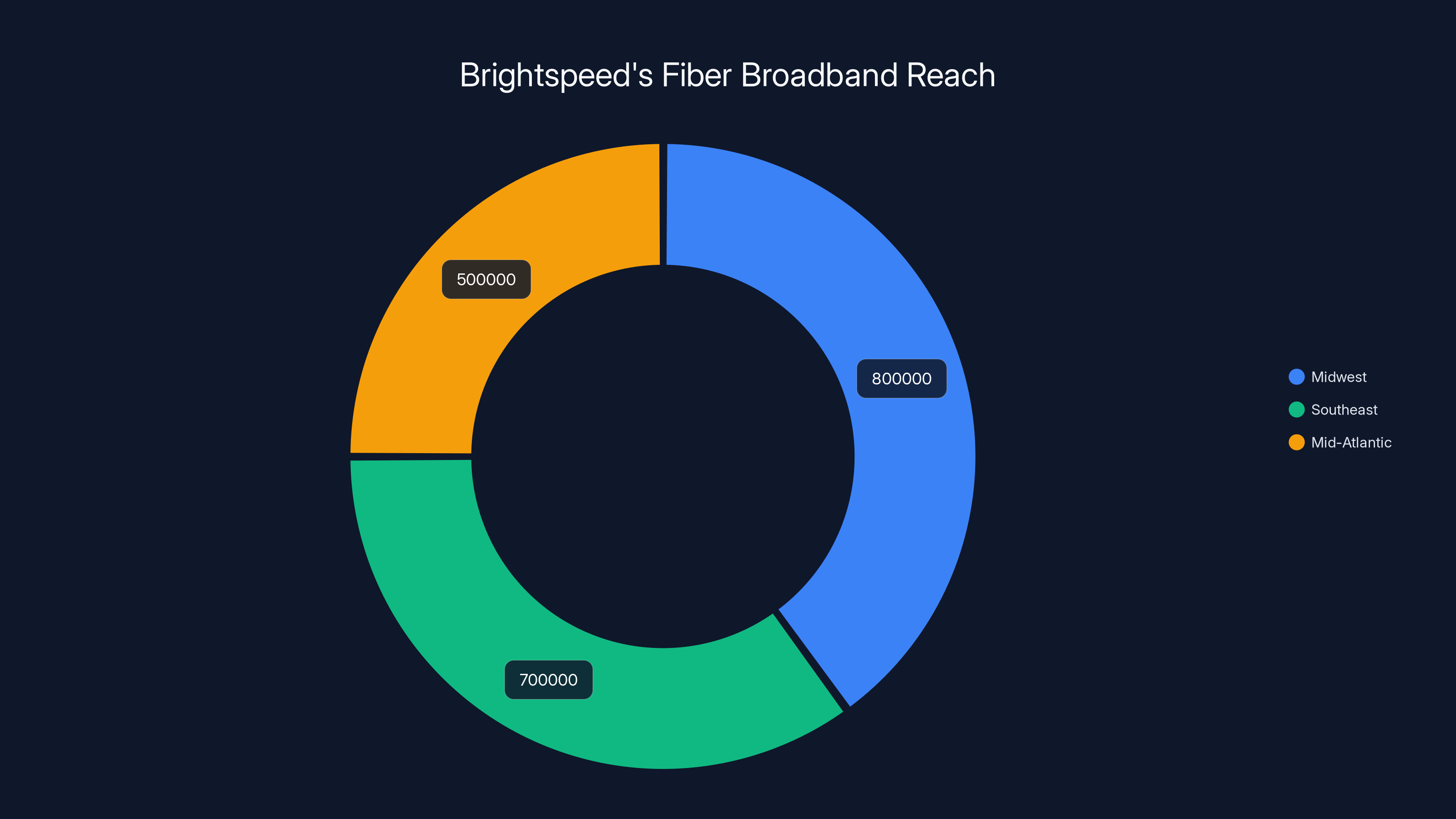
Brightspeed's fiber network reaches over two million locations, with significant presence in the Midwest, Southeast, and Mid-Atlantic regions. Estimated data.
What About Your Personal Data? The Risk Analysis
If you're a Brightspeed customer, your data is potentially exposed. But "potentially exposed" doesn't mean "definitely compromised." Here's the risk breakdown.
Immediate Risks
Your name and email address being in the hands of cybercriminals means you're likely to receive phishing emails. These won't be generic spam. They'll be targeted: "Click here to update your Brightspeed account." They'll look legitimate because they know you're actually a Brightspeed customer.
Your phone number means you could get phishing texts (smishing) or voice calls claiming to be from Brightspeed.
Your postal address means you could receive physical mail attempting to redirect your service or collect money. This is rare but it happens.
Medium-Term Risks
Your email, name, and phone number are valuable on dark web marketplaces. Cybercriminals buy lists of email addresses and phone numbers to use in mass phishing campaigns, credential-stuffing attacks, or SIM swap attempts.
Your payment history could be used for targeted fraud. If criminals know what services you pay for, they can create more convincing phishing attempts.
Your session ID and account information could potentially be used to access your account directly if the credentials aren't changed.
Long-Term Risks
Identity theft. Someone with your name, email, phone number, postal address, and partial payment information could potentially open accounts in your name, apply for credit, or commit other identity fraud.
The good news: the breach happened. It happened in the past. The Crimson Collective already has the data. The risk isn't that they'll steal it—they already did. The risk is what they'll do with it now.
Risk Mitigation Actions (in order of importance)
-
Change your Brightspeed password immediately - Use a strong, unique password. This prevents attackers from using stolen credentials to access your account. The password should be at least 16 characters with mixed case, numbers, and symbols.
-
Check your credit reports - Visit annualcreditreport.com and pull your reports from all three bureaus (Equifax, Experian, Trans Union). Look for unfamiliar accounts or inquiries. You get one free report per bureau per year.
-
Set fraud alerts - Contact one of the three credit bureaus and request an initial fraud alert. This requires creditors to verify your identity before opening new accounts. It lasts one year and can be renewed.
-
Consider a credit freeze - A security freeze locks your credit report so that new accounts can't be opened without your consent. It's the most effective protection against identity theft but adds friction when you want to apply for credit. It's free and you can temporarily unfreeze it when needed.
-
Monitor your financial accounts - Check your bank accounts, credit cards, and payment services regularly. Set up alerts for new transactions or login attempts.
-
Watch for phishing - Be suspicious of emails or texts claiming to be from Brightspeed. Hover over links before clicking to see the actual URL. Legitimate companies won't ask for passwords via email.
-
Consider identity theft protection - Services like Lifelock, Identity Force, or others monitor your credit and personal information for suspicious activity. These are optional but useful for high-risk breaches.
The investment of time here is maybe 30 minutes total. The value is protecting yourself from years of potential fraud.

The Broader Implications: Broadband Security Infrastructure
This breach exposes a wider problem in the broadband industry. Internet service providers sit at a critical chokepoint in our digital infrastructure. They connect millions of homes and businesses to the internet. They have visibility into traffic patterns. They have access to customer personal information. And apparently, some of them don't protect that data adequately.
Broadband providers aren't typically thought of as security companies. They're infrastructure providers. But their security has downstream effects on entire ecosystems.
Consider: if attackers have access to Brightspeed's network infrastructure, what else could they do? Could they intercept traffic? Could they target specific customers for deeper attacks? Could they conduct man-in-the-middle attacks?
We don't have evidence that this particular breach extended beyond the customer database. But the capability to breach a million-customer database suggests significant access to Brightspeed's systems.
For context, this isn't the first major US broadband provider breach. Previous breaches have affected AT&T, Comcast, Verizon, Charter, and others. The pattern is consistent: massive data exposure, delayed response, eventual settlement.
This suggests either:
- The security requirements for broadband infrastructure are inadequate
- The enforcement of security requirements is insufficient
- The business incentives don't justify the investment in security
Probably all three.
Regulators are slowly waking up to this problem. The FTC has been more aggressive with enforcement. Congress is considering privacy and security legislation. But the pace of change is glacial compared to the pace of attacks.
For customers, the lesson is clear: assume your ISP will be breached at some point. Plan accordingly.

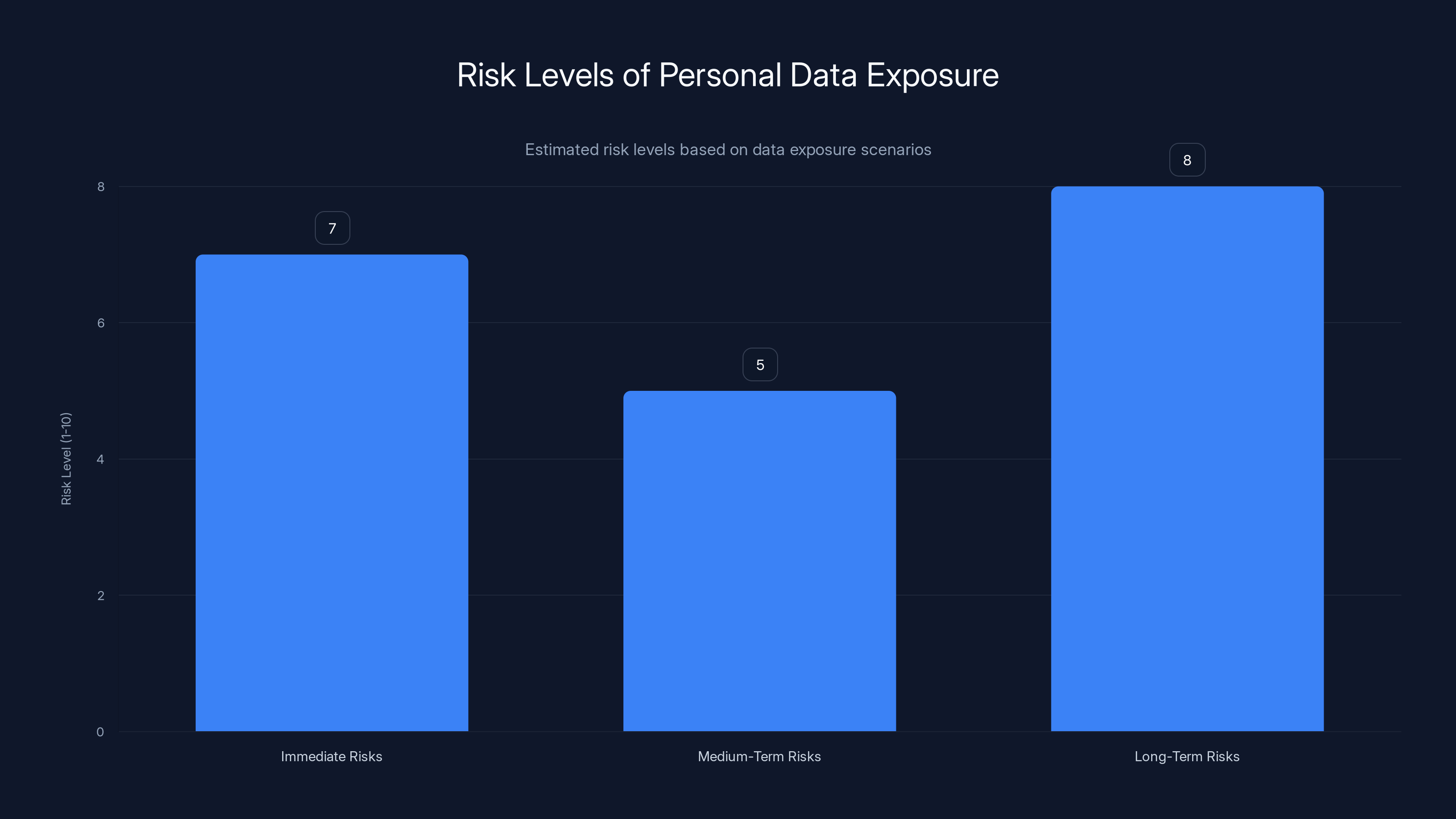
Immediate risks are high due to targeted phishing, while long-term risks are highest due to potential identity theft. Estimated data based on typical exposure scenarios.
Similar Breaches: This Isn't New
Brightspeed's breach is significant, but it's not an anomaly. Major US broadband provider breaches have become almost routine.
AT&T Mobility Data Breach (2023-2024)
AT&T disclosed that attackers accessed data belonging to millions of customers. The breach exposed phone numbers, email addresses, and account information. Initially, AT&T claimed only a small subset was affected. Later reports suggested the scope was larger. AT&T faced criticism for slow disclosure and inadequate initial notifications.
Comcast Xfinity Customer Data Breach (2023)
Comcast disclosed that attackers accessed customer data through compromised credentials. The breach exposed account numbers, payment information, and personal details. Comcast required affected customers to reset passwords and offered credit monitoring.
Previous Broadband Breaches
Verizon, Charter, Century Link, and other major providers have all experienced significant data breaches. The pattern is consistent: large-scale data exposure, credentials compromised through phishing or exploitation, delayed disclosure, eventual settlement with regulators and customers.
What this pattern tells us: data breach risk is endemic to the industry. It's not a matter of if, but when. Companies are investing in security, but apparently not enough.
The common thread in these breaches is that customer data is stored, and storing data at scale creates risk. The more data you have, the bigger the target. The longer you store it, the longer the window for compromise.
Broadband providers could reduce risk by minimizing data retention. But that conflicts with business interests like billing, marketing, and service provisioning.
So we get breaches.

What Should Brightspeed Do? A Roadmap for Recovery
Assuming Brightspeed wants to actually solve this problem (rather than just manage the PR crisis), here's what they should do:
Immediate (Days 1-7)
- Complete forensic investigation to confirm breach scope
- Notify all affected customers with clear, specific information about what was exposed
- Provide free credit monitoring and identity theft protection for at least three years
- Set up a dedicated breach response phone line with knowledgeable staff
- Preserve evidence for law enforcement investigation
Short-term (Weeks 2-4)
- Publish a public statement with confirmed breach details and timeline
- Implement multi-factor authentication for customer accounts
- Conduct security audit of all systems that access customer data
- Review and strengthen access controls for employees and vendors
- Engage third-party security firm to validate remediation efforts
Medium-term (Months 2-6)
- Implement data minimization: only collect and store data that's necessary
- Encrypt sensitive customer data at rest and in transit
- Implement comprehensive logging and monitoring of data access
- Develop incident response plan with clear communication procedures
- Increase security awareness training for all employees
Long-term (6+ months)
- Modernize infrastructure and replace legacy systems that can't be adequately secured
- Implement zero-trust security architecture
- Establish ongoing security testing and vulnerability management program
- Maintain transparency with customers about security measures
- Invest in security at a level proportionate to the business risk
Will Brightspeed do all of this? Probably not. Companies typically do the minimum required by law and then move on. But the security-conscious option is clear.

The Extortion Economics: Why Paying the Ransom is a Bad Idea
The Crimson Collective has made their business model clear: steal data, threaten to release it, extort money, repeat. From a purely economic perspective, understanding why this works reveals why it's so hard to stop.
The Math
Let's say the Crimson Collective is targeting 10 similar-sized companies per year. They successfully steal data from 8 of them. They demand
Their costs are low: maybe a few servers, VPN services, credentials to purchase from dark web marketplaces, and time. Total costs might be $20,000 per year.
Return on investment: 1,900%. That's better than almost any legitimate business.
Now multiply this by thousands of groups conducting similar operations, and you understand why data extortion is a growth industry.
From Brightspeed's perspective, the calculation looks different. The company could potentially pay
But here's where the economics get interesting: if Brightspeed pays, they're signaling to other criminal groups that they're a payable target. Future groups will target them knowing they might be willing to pay. By refusing to pay, Brightspeed reduces future targeting.
Furthermore, there's no guarantee the payment results in data deletion. The criminals could take the money and still release the data. Or they could sell it multiple times to different buyers.
Law Enforcement Perspective
The FBI, Secret Service, and international law enforcement agencies are increasingly aggressive about prosecuting extortion and ransomware cases. They've had some notable successes: recovering ransomware payments, indicting threat actors, and disrupting criminal infrastructure.
But enforcement is limited by jurisdictional challenges. If the Crimson Collective is operating from a country with limited extradition treaties, prosecution becomes difficult.
The Real Solution
Paying or not paying doesn't solve the underlying problem: the data is compromised. The only real solution is prevention: better security, faster detection, faster response, and better data minimization practices.
Until the cost of a breach exceeds the benefit to criminals, the crimes will continue.
Looking Forward: What Happens Next?
The Brightspeed breach will likely follow this timeline:
Week 1: Continued speculation, sample data possibly released by Crimson Collective, Brightspeed continues investigation
Week 2-3: Brightspeed either confirms the breach with specifics, or issues a more detailed statement about their findings
Week 4: Customer notifications go out (required by law), free credit monitoring is offered, lawsuits are filed
Months 2-6: Negotiations with regulators, settlement discussions, implementation of security improvements
6-12 months: Class action settlement, regulatory fine announced, executives potentially departing
12+ months: Life moves on, but the data is still out there, probably being sold on dark web marketplaces
The optimistic scenario: Brightspeed's investigation finds a single root cause (a vulnerable system), they patch it, implement better monitoring, and actually improve security. The pessimistic scenario: they find nothing definitive, implement the minimum required improvements, and wait for the next breach.
History suggests the pessimistic scenario is more likely.
For customers, the takeaway is simple: this is the new normal. Major broadband providers will be breached. Your data will be exposed at some point. You should assume this and plan accordingly.
That means maintaining good credit security hygiene: monitoring reports, using unique passwords, enabling 2FA where possible, watching for suspicious activity.
It also means realizing that some risks are outside your control. Brightspeed is responsible for protecting your data. If they fail, there's not much you can do except protect yourself from the downstream consequences.

The Bigger Picture: Telecom Security in 2025
Brightspeed's breach is part of a larger trend in telecommunications security. The industry is under unprecedented attack pressure from multiple threat actors with varying motivations.
Nation-State Actors: Governments are interested in telecommunications infrastructure because it provides access to communications, metadata, and downstream systems. The recent discovery of Chinese hacking groups infiltrating US telecom infrastructure shows this is an active, ongoing threat.
Financially Motivated Criminals: Groups like Crimson Collective are pure profit-seeking. They steal data and extort money. They operate like businesses, with division of labor and professional practices.
Hacktivists and Thrill-Seekers: Some attacks are motivated by politics, ideology, or simply the challenge. These tend to be less sophisticated but can still cause damage.
Insiders: Disgruntled employees or former employees with access to systems represent ongoing risk. Some of the biggest breaches have insider involvement.
For telecommunications companies, the challenge is defending against all four threat categories simultaneously while maintaining infrastructure uptime and service quality.
The broader implication: telecommunications infrastructure is critical to modern life. Internet access enables work, education, healthcare, commerce, and communication. When telecom companies are breached, the impact cascades through society.
This argues for stronger regulation, higher security standards, and better enforcement. But it also argues for individual vigilance. You can't rely solely on companies to protect your data.

FAQ
What is Brightspeed and why is the breach significant?
Brightspeed is one of the largest fiber broadband providers in the United States, operating across 20 states in the Midwest, Southeast, and Mid-Atlantic regions. The company serves millions of residential and business customers with fiber and traditional internet services. The breach is significant because it potentially exposed personally identifiable information for over one million customers, affecting a major piece of US telecommunications infrastructure.
How did the Crimson Collective breach Brightspeed's systems?
The exact attack method hasn't been officially confirmed by Brightspeed, but likely scenarios include exploitation of a vulnerable web application, compromise of employee credentials through phishing, unauthorized access through a third-party vendor, or exploitation of an API or integration. Forensic analysis is ongoing to determine the specific attack vector. The scope of access (over one million customer records) suggests either direct database access or exploitation of a significant system vulnerability.
What personal information was stolen in the breach?
According to the Crimson Collective's claims, the stolen data includes: names, email addresses, phone numbers, postal addresses, user account information linked to session IDs, payment history, partial payment card information (not full card numbers), and appointment/order records. The partial nature of payment card data suggests some level of encryption or access restriction was in place, but other highly sensitive information was fully exposed.
What should I do if I'm a Brightspeed customer?
Immediate actions include: (1) change your Brightspeed account password immediately, (2) check your credit reports at annualcreditreport.com for unauthorized accounts, (3) place a fraud alert with the credit bureaus, (4) consider a credit freeze, (5) monitor your financial accounts for suspicious activity, (6) watch for phishing emails or texts claiming to be from Brightspeed, and (7) consider identity theft protection services. You should also watch for official notification from Brightspeed about the breach and what additional protections they're offering.
Is my payment card information at risk?
Partially. The Crimson Collective claims to have partial payment card information, not full card numbers. While partial card data is less useful than full card numbers, in combination with other personal information (name, email, address), it could potentially be used for fraud or sold to other criminals. You should monitor your credit card statements carefully and consider requesting new cards from your issuer if you're concerned. Contact your bank or credit card company if you see any suspicious charges.
When will Brightspeed officially confirm the breach and notify customers?
Brightspeed is currently investigating and hasn't officially confirmed the breach. However, US federal law and state regulations require companies to notify affected individuals without unreasonable delay, typically within 30 days of discovery. Expect an official notification within the next few weeks. The timeline depends on how quickly Brightspeed completes its forensic investigation and determines the exact scope of the breach.
What are the risks of the Crimson Collective releasing the stolen data?
If the data is released publicly or sold to other criminals, the risks increase significantly. Your personal information becomes available to thousands of threat actors who can use it for phishing, identity theft, fraud, SIM swapping, or simply spam. The longer-term risk is that your data enters the dark web criminal marketplace and remains available for years. This is why monitoring your credit and accounts is so important.
Is Brightspeed breaking any laws?
If the breach is confirmed, Brightspeed may have violated federal regulations (FTC Safeguards Rule, HIPAA if any health data was involved), state breach notification laws in 20 different states, and potentially consumer protection laws. The company will likely face regulatory investigation and potential fines. Affected customers may also file civil lawsuits against the company for negligence and failure to adequately protect personal information. However, proving what laws were violated depends on the details of Brightspeed's security practices.
How do I know if I'm affected by the breach?
You're potentially affected if you have an active or recent Brightspeed account. The Crimson Collective claims to have data on over one million customers. Not all Brightspeed customers are necessarily affected (the breach may be geographically or temporally limited), but assuming the claims are accurate, a significant portion of the company's customer base is at risk. Brightspeed's official notification will specify which accounts are affected based on their forensic findings.
Should I switch to a different broadband provider?
That depends on your situation. The breach at Brightspeed reflects broader security challenges across the telecommunications industry. Other major providers (AT&T, Comcast, Verizon, Charter) have also experienced significant breaches. A single breach isn't necessarily a reason to switch, especially if switching isn't practical in your area (many regions have limited broadband options). However, if you have alternatives and security is a priority, it's reasonable to research competitors' security track records.
What You Need to Know: Final Takeaways
Brightspeed's breach affects millions of Americans across 20 states. The personally identifiable information exposed—names, emails, phone numbers, addresses, account information, and partial payment data—is valuable to cybercriminals and represents a significant identity theft risk.
What makes this breach particularly serious is that the company hasn't fully confirmed it yet, leaving customers without clear guidance on what to do. While Brightspeed investigates, the Crimson Collective has issued ultimatums and threatened to release sample data. This creates pressure on both sides: Brightspeed to complete their investigation quickly, and affected customers to take protective measures.
The good news: you have actionable steps you can take right now. Change your password, check your credit, set fraud alerts, monitor your accounts. These aren't complex steps, but they're essential.
The bigger picture: this breach is part of a trend. Telecommunications companies are increasingly targeted by sophisticated threat actors. Major breaches have become routine. If you're in the broadband industry, you should assume you'll be breached at some point. That doesn't mean giving up on security. It means being realistic about risk and planning accordingly.
Brightspeed has questions to answer. How did the breach happen? What exactly was accessed? When will customers be notified? Will the company take meaningful steps to prevent future breaches? Or will they implement minimum-required security improvements and hope for the best?
For now, we're waiting. Waiting for Brightspeed's investigation. Waiting for Crimson Collective's threatened sample release. Waiting for official customer notifications. Waiting to see if this becomes yet another telecom breach that fades from headlines after a few weeks of news coverage, a regulatory settlement, and a collective forgetting by the public.
In the meantime, protect yourself. Because Brightspeed certainly didn't.

Key Takeaways
- Brightspeed, operating fiber broadband across 20 states, is investigating a breach affecting 1M+ customers involving stolen names, emails, phone numbers, addresses, account info, and partial payment data
- The Crimson Collective hacking group announced the breach and threatened to release sample data, using standard extortion tactics demanding ransom to prevent public release
- Affected data can be used for identity theft, phishing attacks, SIM swapping, fraud, and account takeovers, making immediate protective action essential for customers
- Regulatory requirements mandate customer notification within 30 days of breach discovery, and Brightspeed faces potential legal liability and regulatory fines from state attorneys general and the FTC
- Customers should immediately change passwords, check credit reports, place fraud alerts, consider credit freezes, monitor accounts, and watch for phishing attempts
![Brightspeed Data Breach Investigation: What Happened & What's Next [2025]](https://tryrunable.com/blog/brightspeed-data-breach-investigation-what-happened-what-s-n/image-1-1767733730007.jpg)



