Critical Infrastructure Breach: Engineering Firm Hack Exposes US Utilities [2025]
When a cybercriminal walks away with 800+ files containing transmission line maps, LiDAR data, and substation locations from three major US utilities, it's not just a data breach. It's a wake-up call about how fragile our electrical grid actually is. According to The Register, this breach highlights significant vulnerabilities in the infrastructure.
This isn't some hypothetical nightmare scenario from a security conference. Last week, hackers posted on a dark web forum claiming they'd successfully stolen sensitive operational data from Pickett and Associates, a Florida-based engineering firm that does critical work for utilities across the United States. The stolen files included detailed infrastructure maps, high-resolution aerial photography, vegetation data, and design specifications that could be used for reconnaissance, sabotage planning, or targeted attacks. The Cybersecurity Dive reported that such breaches are part of a growing trend of targeting critical infrastructure.
Three names you've probably heard of were mentioned: Duke Energy, Tampa Electric Company, and American Electric Power. These aren't startups or regional providers. These are utilities that power millions of homes and businesses across the country. The attackers are demanding 6.5 bitcoin (roughly $600,000) for the data. And here's what really concerns security experts: this appears to be part of a coordinated campaign targeting critical infrastructure globally. The same threat actors are also selling stolen data from Germany's Enerparc AG, a renewable energy company. This suggests it's not random targeting. It's deliberate, methodical, and focused, as noted by Industrial Cyber.
Let me walk you through what happened, why it matters, and what it means for the future of infrastructure security in America.
What Exactly Was Stolen?
The files in question aren't just generic spreadsheets or employee contact lists. They're operational engineering data that reveals how critical infrastructure is physically laid out and managed. According to The Register, the stolen data includes over 800 raw LiDAR point cloud files in .las format. LiDAR (Light Detection and Ranging) is a remote sensing technology that creates precise 3D maps of terrain and structures. These files contain detailed elevation data, vegetation mapping, and structural features across transmission corridors. For someone planning an attack, this is gold. You can see exactly where power lines run, how they're supported, what trees are nearby that could be cut to cause outages, and where substations are located.
The data also allegedly includes full coverage of transmission line corridors and substations with specialized mapping layers. We're talking about bare earth models, vegetation data, conductor information, and structural details. When combined, this information creates a complete picture of critical infrastructure vulnerability. High-resolution orthophotos in .ecw format were part of the haul as well. These are essentially extremely detailed aerial photographs of infrastructure areas. Combined with LiDAR data, they provide visual confirmation of what the point clouds show, making reconnaissance faster and more reliable for potential attackers.
MicroStation design files and PTC settings found their way into the criminals' hands too. These aren't just pretty diagrams. They're the actual engineering specifications used for infrastructure planning, maintenance, and upgrades. They contain the technical details of how systems are designed to function and fail over. Large vegetation feature files in .xyz format rounded out the theft. Vegetation management is critical for utility operations. It prevents tree-related outages, which are among the most common causes of power failures. Knowing exactly where vegetation poses risks helps attackers plan which areas to target for maximum disruption.
Pickett and Associates specializes in exactly this type of work. The company provides surveying, aerial mapping, LiDAR services, transmission and distribution design, and project management for utilities. Their clients include investor-owned utilities, municipalities, electric cooperatives, and mining operations. So the firm has legitimate access to this data. The problem is, it didn't stay legitimate.

Nation-state actors are the most likely buyers of the $600,000 infrastructure data, given their resources and strategic interests. Estimated data.
Why This Matters: The Critical Infrastructure Angle
Here's what keeps energy security professionals up at night: operational technology (OT) networks that control our power grid are increasingly connected to IT systems, creating vulnerabilities. But before you even get to hacking into SCADA systems or breaching control centers, having detailed maps of where infrastructure lives is half the battle. With the stolen data, a bad actor could conduct sophisticated reconnaissance without ever touching a computer system. They could identify critical choke points where taking out a few transmission lines would cascade into widespread outages. They could find substations that are geographically isolated, making emergency response slower. They could locate vegetation risks and plan to exploit them. They could identify where infrastructure overlaps with vulnerable populations who depend on steady power for medical equipment.
This isn't theoretical. The Department of Energy and FBI have repeatedly warned about adversarial nations and criminal groups targeting US critical infrastructure. China, Russia, and Iran have all been caught probing energy sector networks. Ransomware groups like LockBit and BlackCat have specifically targeted utilities. Foreign entities actively seek information about American infrastructure to understand vulnerabilities and plan future operations. The SC World reported on similar coordinated campaigns targeting critical infrastructure.
The data theft from Pickett and Associates reveals something else troubling: even third-party service providers, which often have weaker security than the utilities themselves, are becoming targets. Utilities hire firms like Pickett to do specialized work because those companies have expertise utilities don't develop in-house. But that means sensitive data gets distributed across the supply chain, multiplying the places where breaches can happen.
The timing of this breach is also worth noting. The US power grid is under strain. Demand for electricity is rising due to data centers, AI infrastructure, and industrial growth. The grid is also aging in many regions, with infrastructure built in the 1960s and 70s still in use. Renewable energy integration adds complexity to grid management. In this environment of stress and transition, losing detailed operational knowledge about infrastructure to criminals is particularly dangerous.

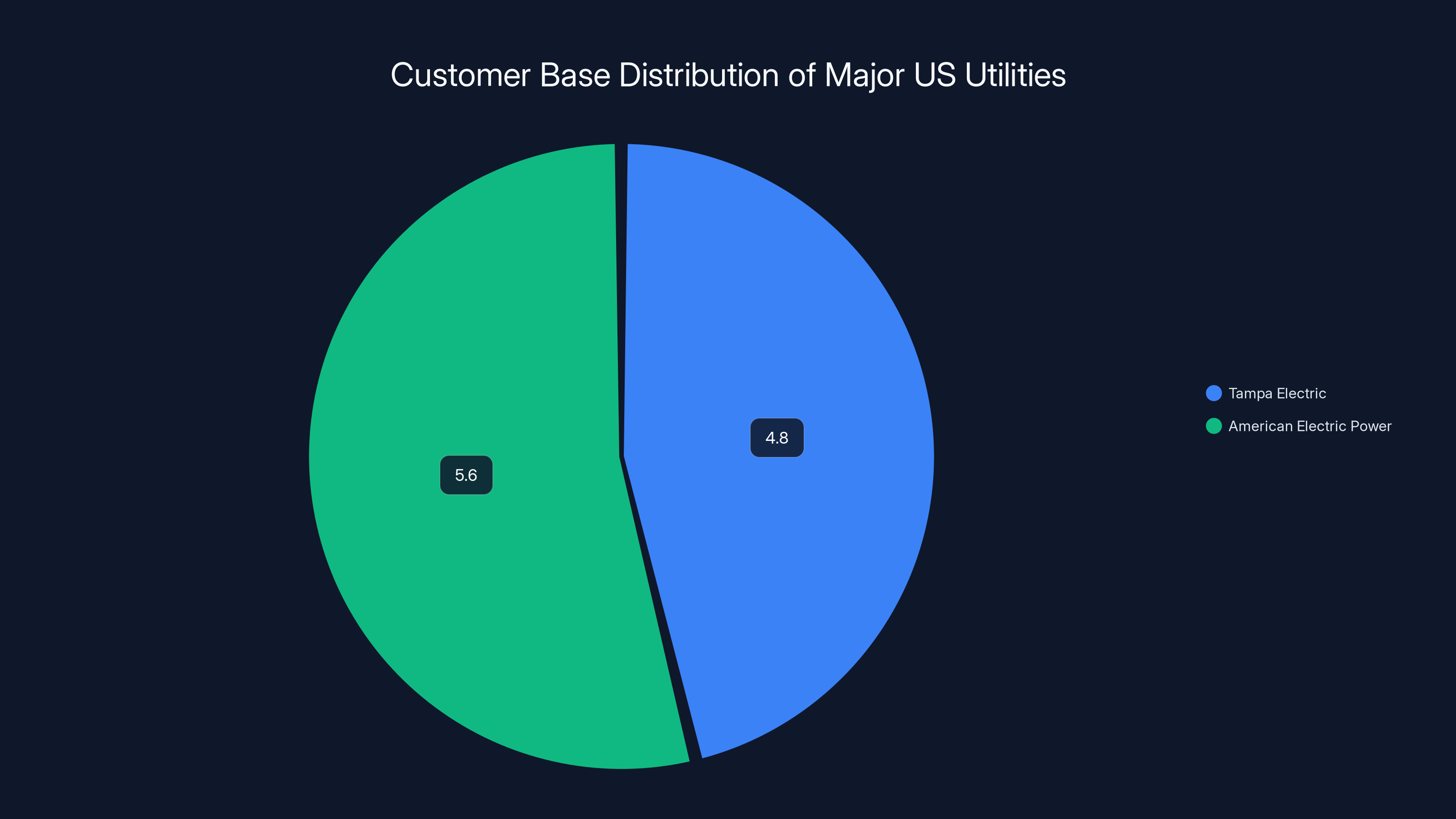
American Electric Power serves a larger customer base (5.6 million) compared to Tampa Electric (4.8 million), highlighting its broader reach in the US energy sector.
The Threat Actors: Organized, Focused, Global
Who did this? The threat actors haven't revealed their full identity, which is typical in these situations. Operating on dark web forums anonymously is the standard playbook. But what we can infer about them is important. They're organized enough to breach a company that should have some security measures in place. They're technically sophisticated enough to exfiltrate hundreds of large files without getting detected immediately. They understand the value of what they stole well enough to price it at $600,000 in bitcoin. And they're patient enough to develop a business model around selling this data.
Most significantly, they're focused on critical infrastructure. The fact that they're simultaneously selling data from Germany's Enerparc AG indicates this isn't random cybercriminals looking for credit card numbers or personal information. This is infrastructure targeting. Either it's being done by nation-state actors collecting intelligence, criminal groups building a portfolio to sell to interested parties (including potentially hostile governments), or some combination of both. The Jefferson County website provides insights into the vulnerabilities of infrastructure to such threats.
Historically, when we've seen infrastructure data being sold on dark web forums, there have been connections to state-sponsored activity. Russian APT groups have been caught targeting utilities. Chinese APT groups have conducted extensive reconnaissance of US infrastructure. Iranian groups have attempted direct attacks on energy companies. Whether this current situation involves state sponsorship or is purely criminal remains unknown, but the pattern of targeting and the nature of the data suggest serious intent.
Duke Energy's Response and Investigation
When The Register reached out to Duke Energy (the utility mentioned in the breach claims that actually acknowledged the incident), the company provided a carefully worded statement: "With threats evolving every day, Duke Energy's highly skilled cyber security team works diligently to protect our businesses, systems and information technology assets and responds quickly if a cyber incident occurs. We are taking the necessary actions to investigate this claim."
This response tells us several things. First, Duke Energy isn't denying the breach happened. They're investigating it. Second, they're characterizing it as a claim that needs investigation, which is appropriate since the company hadn't independently confirmed the theft at the time of reporting. What's notable is what Duke Energy isn't saying. They haven't provided a timeline of when the breach was discovered. They haven't said whether they plan to notify regulators or customers. They haven't disclosed the scope of data they believe was compromised. They haven't announced any operational changes related to the incident. This measured response is both prudent (don't say anything that could complicate matters) and frustrating (the public remains largely in the dark).
Federal Energy Regulatory Commission (FERC) rules require utilities to report cyber incidents that affect the bulk power system, but the timeline for reporting can be lengthy, and the details disclosed are limited. The Department of Energy also has incident reporting requirements, but again, there's discretion about what gets disclosed publicly.
Duke Energy's investigation is happening in parallel with potential law enforcement involvement. The FBI likely has knowledge of this breach given the critical infrastructure angle. But coordinating between corporate security teams, law enforcement, and regulators is slow, messy, and deliberately opaque to preserve investigative value.
What we know from past similar incidents is that Duke Energy will likely discover more details as their investigation proceeds. They may find that the attackers had access longer than initially thought. They may find that data beyond what the threat actors claimed was stolen is actually missing. They may discover that other utilities were also compromised and didn't realize it. Or, they may conclude that the threat actors' claims are exaggerated or partially false.

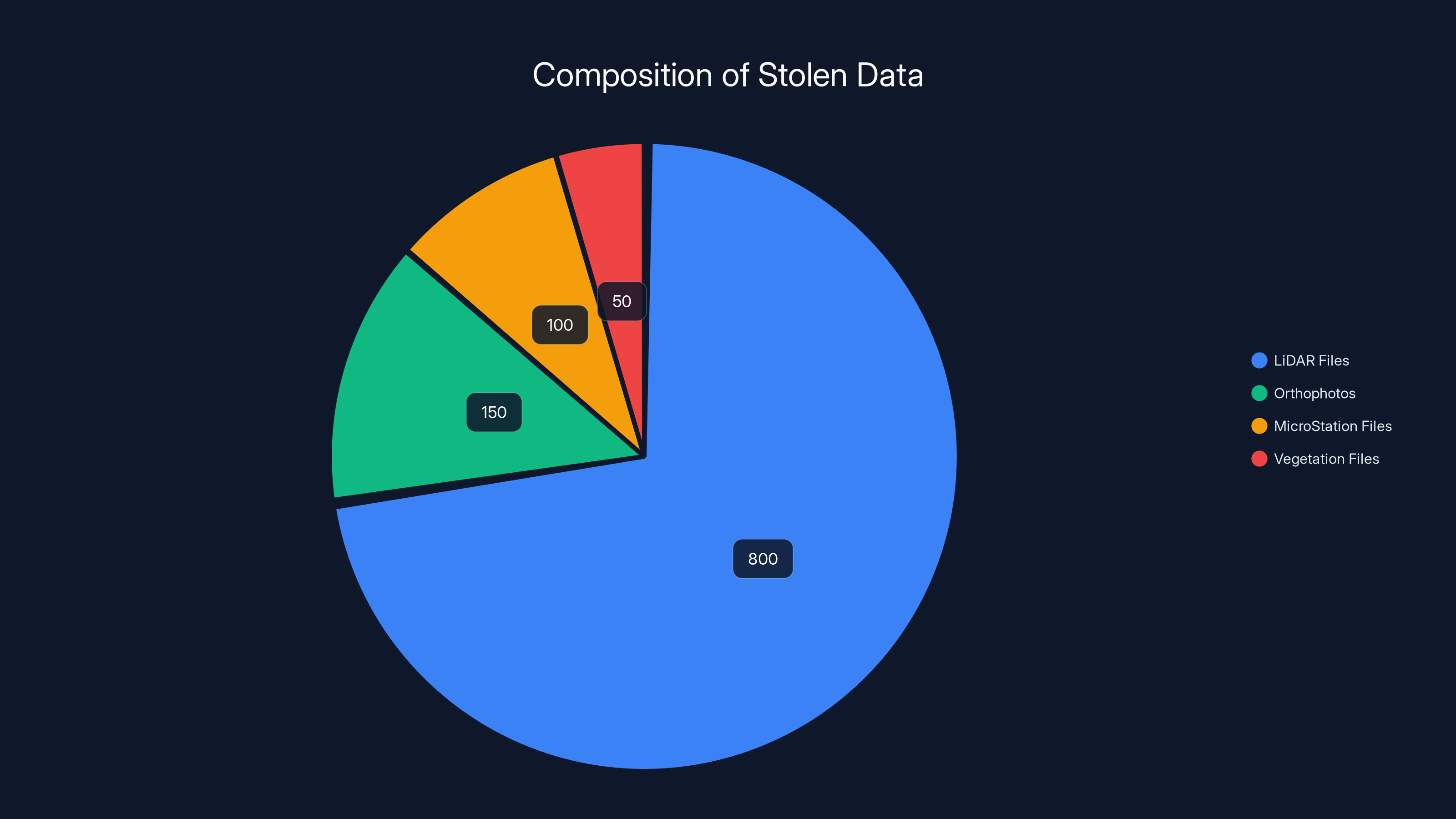
The majority of the stolen data consists of over 800 LiDAR files, highlighting the focus on detailed 3D mapping and structural data. Estimated data.
Tampa Electric and American Electric Power: What We Know
Tampa Electric Company and American Electric Power are the other two utilities mentioned in the threat actors' claims. Unlike Duke Energy, neither company has publicly acknowledged investigating the breach. Tampa Electric is a subsidiary of TECO Energy and serves approximately 4.8 million customers across Florida and Georgia. American Electric Power is one of the largest utilities in the country, serving 5.6 million customers across 11 states. Both are major players in the US energy sector.
Neither company has issued public statements about potential data theft related to Pickett and Associates. This doesn't necessarily mean they weren't targeted or that they don't believe the claims are legitimate. It may simply mean they're following a standard incident response playbook: investigate quietly, don't comment publicly until you have facts, consult with legal counsel before disclosure, coordinate with regulators.
However, this silence also creates uncertainty. Are these companies unaware they're mentioned in the breach? Have they investigated and determined the claims are false? Are they investigating but haven't finished? Without confirmation or denial, customers and stakeholders are left guessing about whether their utility was actually compromised.
For both Tampa Electric and American Electric Power, the financial and reputational implications are significant. If they were truly compromised, customers may question the company's security practices. Regulators may impose requirements for enhanced security measures. Competitors may use the incident in marketing material. Insurance costs may increase.

The Global Picture: Enerparc AG and Coordinated Targeting
What elevates this breach from a US utilities problem to a geopolitical concern is the fact that the same threat actors are also selling data stolen from Enerparc AG, a German renewable energy company. Enerparc specializes in solar and wind power projects, particularly rooftop solar installations and utility-scale renewable energy systems. Like Pickett and Associates, Enerparc has detailed knowledge of where critical infrastructure is located. Solar and wind installations represent the future of energy generation, and mapping where these systems exist is strategically valuable information.
The correlation between targeting Pickett and Associates and Enerparc AG suggests this is part of a coordinated campaign to collect infrastructure intelligence globally. It's not random. The threat actors identified two companies that hold detailed information about critical infrastructure across two major developed economies, compromised both, and are now monetizing the data. This pattern is consistent with what we know about advanced persistent threat (APT) groups and criminal organizations that specialize in infrastructure targeting. They build expertise in understanding the energy sector. They develop techniques for identifying and accessing companies with relevant information. They build networks of buyers for the data they steal (potentially including governments, military organizations, or other criminal groups).
From a strategic perspective, having detailed maps of US and German energy infrastructure is valuable for multiple purposes: planning military operations that could involve critical infrastructure damage, identifying vulnerabilities for corporate espionage, understanding energy security risks to exploit during conflicts, or simply having a library of infrastructure information for future reference.
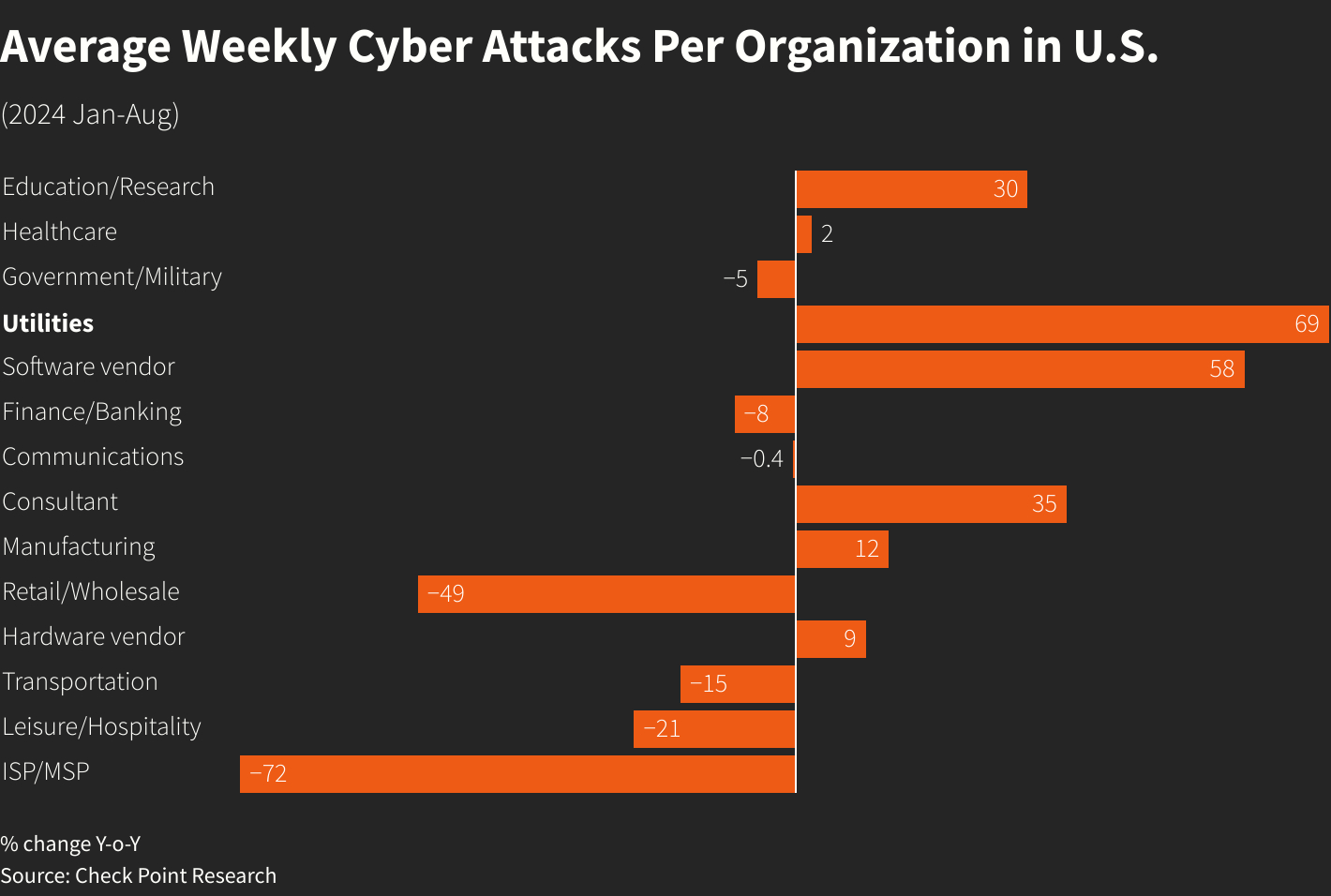
Tree-related outages account for approximately 35% of power interruptions in the United States. Equipment failure and weather events are also significant contributors. (Estimated data)
How the Attack Likely Happened
We don't have official details about how the attackers gained access to Pickett and Associates' systems, but we can make educated guesses based on how similar breaches typically occur. Most likely scenario: compromised credentials. Someone at Pickett and Associates had access to file servers containing the LiDAR data and design files. That person's credentials (username and password) were compromised. This could have happened through phishing (a fake email attempting to steal login credentials), credential stuffing (trying passwords from other breaches), brute force attacks against weak passwords, or malware that captured keystrokes.
Once the attackers had valid credentials, they could log into Pickett and Associates' systems like any legitimate user. They could browse file servers, identify the data of interest, and exfiltrate it. If the company's security monitoring was weak, the attackers could move slowly and carefully, extracting files over time to avoid triggering alerts. Alternative scenario: exploited vulnerability. Pickett and Associates might have had a web-facing application (a portal for uploading project data, for example) with an unpatched security vulnerability. The attackers could have exploited that vulnerability to gain initial access, then escalated privileges to access more sensitive data.
Another possibility: supply chain compromise. Maybe the attackers didn't directly compromise Pickett and Associates, but instead compromised a third party that had access to their data or systems. For example, a cloud service provider that Pickett uses, or a security firm that monitors their networks, or even a hardware vendor. What's clear is that the attackers got what they wanted: 800+ files containing detailed infrastructure data. Whether they obtained this in a single sophisticated attack or through a series of smaller incursions we don't know. What matters is the data got out, and it's now for sale.

The $600,000 Question: Who's the Buyer?
The threat actors are selling the stolen data for 6.5 bitcoin, which at current prices is approximately
Who actually has $600,000 for intelligence data and motivation to buy it? The list is short and concerning: nation-state intelligence agencies, military organizations, wealthy criminal syndicates with specific operational goals, or state-backed criminal groups operating with government funding. Let's think through the possibilities:
Nation-state actors: China, Russia, Iran, and North Korea have all demonstrated interest in US critical infrastructure. Each country benefits from having detailed maps of American energy infrastructure. For espionage purposes, this data is valuable. For operational planning in a hypothetical conflict, it's invaluable. State actors have budgets that make $600,000 seem trivial. They might pay it through proxies or shell companies to avoid direct attribution.
Criminal organizations with specific targets: Highly sophisticated criminal groups might want infrastructure data for planned attacks. If a group intended to conduct a major ransomware attack on a utility, having detailed operational knowledge beforehand would increase their chances of success. A $600,000 investment could lead to multi-million dollar ransoms.
Terrorists or extremist groups: Extremist organizations with anti-government or anti-infrastructure motivations might want to study vulnerabilities in critical infrastructure. However, most extremist groups lack $600,000 in funding and typically operate differently than well-organized criminal groups.
The most likely scenario is state-sponsored or state-backed buyers. This is how sophisticated infrastructure targeting campaigns work. Intelligence agencies identify valuable targets, either directly compromise them or purchase stolen data, and build their operational knowledge over time.

Estimated data distribution shows a significant portion of the stolen files were transmission line maps and design specifications, highlighting potential risks for targeted attacks. Estimated data.
Regulatory Response and What Happens Next
Here's where federal regulation comes in. The Federal Energy Regulatory Commission (FERC) has authority over the bulk power system, and utilities are required to comply with various cybersecurity standards. The most relevant is the Critical Infrastructure Protection (CIP) standards. CIP standards require utilities to maintain incident response plans, conduct security assessments, implement access controls, monitor for suspicious activity, and respond to incidents. Specifically, CIP-005 requires utilities to protect Electronic Security Perimeter (ESP) systems, which are the computers and networks that control critical functions.
But here's the complication: the data stolen from Pickett and Associates isn't from the utilities' critical systems themselves. It's from a third-party engineering firm that maintains detailed information about utility infrastructure. While FERC's standards require utilities to manage third-party risks, the responsibility for actually securing third-party data is murky. Utilities contract with firms like Pickett and Associates precisely because those companies have specialized expertise. The data those firms hold is incredibly sensitive and valuable. But utilities don't necessarily have direct control over how those firms secure their data. If Pickett had weak security practices (single-factor authentication, unpatched systems, poor network segmentation), the utilities weren't responsible for fixing those issues, even though they benefited from Pickett's services.
This gap in accountability is a persistent problem in infrastructure security. The supply chain is only as secure as the weakest link. If Pickett and Associates was compromised, all of its customers (the utilities) are potentially exposed to the consequences.
Expect several regulatory responses:
-
FERC and the Department of Energy will likely investigate whether utilities were properly managing their third-party risk related to companies like Pickett and Associates.
-
Utilities may be required to conduct security audits of their third-party service providers, implement additional monitoring, and establish contracts with specific security requirements.
-
The Electricity Subsector Coordinating Council (ESCC), which brings together industry representatives and government agencies, will likely issue guidance about managing similar risks.
-
Congress may introduce new legislation mandating enhanced third-party risk management for critical infrastructure.
Beyond federal regulation, individual states that have utility regulatory agencies (most do) may impose additional requirements. And utilities themselves, eager to avoid further breaches, will likely invest in better vendor security management.

The Pickett and Associates Response
Pickett and Associates initially declined to comment on the hackers' claims. The company issued a brief statement saying it doesn't comment on such matters. This silence is understandable from a public relations perspective. Confirming a breach opens the company to lawsuits from affected utilities, regulatory investigation, and damage to its reputation. Not confirming the breach leaves the company in a gray area where the hack is widely believed but not officially acknowledged.
However, silence also signals uncertainty and lack of transparency. In 2025, companies that are breached face expectations of rapid, honest communication. The old playbook of staying quiet isn't working anymore. Customers, regulators, and stakeholders expect companies to acknowledge incidents, explain what happened, detail what was taken, and explain what they're doing to prevent recurrence.
For Pickett and Associates, the company faces significant liability. The utilities that hired them are likely reviewing their contracts with Pickett to understand what obligations the engineering firm had regarding data security. If Pickett failed to implement reasonable security measures, the utilities may pursue damages. The company will also face scrutiny about its incident response. Did they detect the intrusion on their own, or did a third party alert them? How long did the attackers have access to their systems? Did they exfiltrate data from customer project files, or also from internal systems? Did any customer data (names, addresses, contact information) get compromised along with the infrastructure data?
Pickett and Associates also faces employee and customer retention challenges. Employees may worry about working for a company that was breached. Customers may evaluate whether to continue using Pickett's services or switch to competitors with stronger security reputations.
Realistically, Pickett and Associates will eventually conduct an independent security audit (law firms and insurers will demand it), share findings with affected utilities and regulators, implement security improvements, and attempt to rebuild trust. Whether the company survives this incident intact or faces bankruptcy remains to be seen. Much depends on how many utilities decide to stop using their services and seek alternatives.

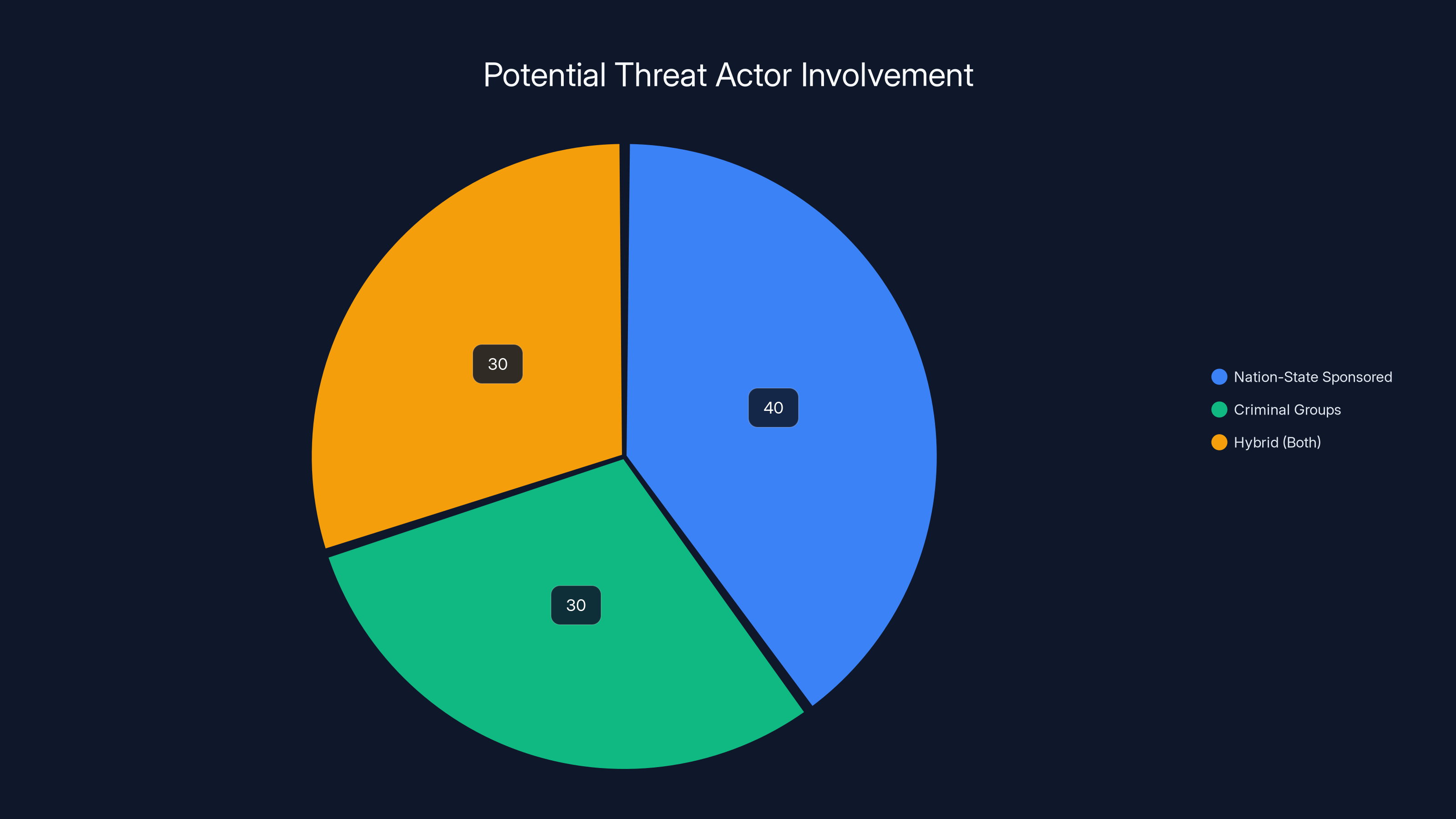
Estimated data suggests a significant portion of threat actors targeting critical infrastructure may involve nation-state sponsorship, with others being criminal groups or a hybrid of both.
Lessons for Critical Infrastructure Security
This breach reveals several persistent vulnerabilities in how the US approaches critical infrastructure security.
First, third-party risk management is broken. Utilities outsource specialized work like surveying, mapping, and design to companies like Pickett and Associates. Those third parties accumulate sensitive data. But utilities don't have direct oversight of those companies' security practices and often don't have contractual requirements for specific security standards. The supply chain security problem is real and growing as organizations increasingly depend on third-party service providers.
Second, sensitive data is too accessible. The fact that 800+ files containing detailed infrastructure information could be exfiltrated by attackers suggests weak data access controls. Ideally, such sensitive information would be stored in secure environments with additional authentication requirements, compartmentalized access based on job role, and advanced monitoring for unusual access patterns.
Third, incident detection and response capabilities vary widely. We don't know how long the attackers had access to Pickett and Associates' systems before being discovered (if they were even detected by the company itself). Some companies have sophisticated security operations centers with real-time threat monitoring. Others don't have dedicated security staff. The gap between best-in-class and worst-in-class infrastructure security is enormous.
Fourth, regulations lag behind threats. FERC's CIP standards are reasonable but reactive. They're updated in response to past breaches, not in anticipation of future ones. By the time regulations are implemented, adversaries have often already moved to new attack techniques.
Fifth, data classification and retention practices need improvement. Does Pickett and Associates actually need to retain 800+ files of detailed historical LiDAR data from completed projects? Or could they archive older data in more secure offline storage, limiting what's available on internet-accessible systems? Many companies keep data far longer than operationally necessary.

The Broader Context: Infrastructure Under Siege
This breach doesn't exist in isolation. It's part of a pattern of increasing targeting of US and allied critical infrastructure by sophisticated adversaries. In recent years, we've seen:
- Russian APT groups conducting extensive reconnaissance of US electric grid infrastructure
- Chinese APT groups stealing detailed information about US oil and gas companies
- Iranian cyber units attempting to breach utility networks
- Ransomware gangs launching attacks against water utilities and energy companies
- Nation-states conducting exercises involving shutting down power in other countries' infrastructure
Each incident reveals vulnerabilities. Each stolen database of infrastructure information provides adversaries with better knowledge for planning future operations. Each successful extortion payment funds more sophisticated attacks. The Pickett and Associates breach fits into this troubling trend. It's not an isolated incident. It's evidence that critical infrastructure continues to be attractive to sophisticated threat actors, and the security defenses protecting that infrastructure remain insufficient.
What's particularly concerning is the information asymmetry. Utilities and the government know more about threats than the public. Briefings to Congress about infrastructure vulnerabilities are often classified. Details about attacks are withheld from the public. This means regular people lack understanding of just how vulnerable critical infrastructure actually is. If the public truly understood the risks, there would likely be far more pressure for investment in infrastructure security.

What Needs to Happen: A Road Map
Addressing these vulnerabilities requires action at multiple levels.
At the utility level: Implement zero-trust network architecture (never trust, always verify), conduct regular security audits of critical systems, establish security requirements for third-party service providers, implement data loss prevention tools, provide regular security training to employees, and invest in security operations centers that can detect intrusions in real time.
At the federal level: Strengthen FERC's Critical Infrastructure Protection standards with more specific requirements for third-party risk management, mandate security assessments by independent auditors, establish incident reporting requirements that balance transparency with investigation needs, and fund research into emerging threats to infrastructure.
At the industry level: Utilities should share threat intelligence more freely with competitors and the government, establish security consortiums to collectively fund better security research and tools, and develop security standards that exceed regulatory minimums.
At the vendor level: Companies like Pickett and Associates need to implement security practices appropriate to the sensitivity of data they handle, even if those practices go beyond what regulatory requirements mandate. Security should be a competitive differentiator and an area where companies invest to differentiate from competitors.

The Cryptocurrency Payment Problem
One detail worth exploring: the attackers want payment in bitcoin. This is standard for ransomware gangs and data extortionists, but it highlights a persistent problem in law enforcement response to cybercrime. Bitcoin transactions are theoretically traceable. Every transaction is recorded on the blockchain, permanently and publicly. Yet tracking bitcoin payments from criminal extortion is difficult because intermediaries (mixing services, exchanges) exist that obscure the trail. A buyer could send bitcoin to the criminals, who immediately move it through mixing services, and then either cash it out through legitimate exchanges in countries with weak anti-money-laundering enforcement, or use it to purchase goods and services anonymously.
The US government has increasingly focused on cryptocurrency regulation and tracking. The Treasury Department's Financial Crimes Enforcement Network (FinCEN) has issued guidance on cryptocurrency reporting requirements. The SEC has moved toward cryptocurrency regulations. Law enforcement has successfully traced and seized some criminal cryptocurrency holdings. But the current system is still cat-and-mouse. If sophisticated criminal groups or nation-states want to use cryptocurrency for ransom or extortion payments while obscuring their identity, they have tools and techniques to do so. The buyers of this infrastructure data, if they choose to pay in bitcoin, can likely protect their identity reasonably well, though it's not foolproof.
This is one reason why the infrastructure breach is so troubling. Even if law enforcement identifies who purchases the stolen data, taking enforcement action against a state actor is diplomatically complex. Taking action against a non-state criminal group may take months or years. In the meantime, the data is in hostile hands, being used for reconnaissance, analysis, and operational planning.

Preparing Your Organization for Similar Threats
If you work in critical infrastructure or are responsible for information security at a utilities company or related organization, this breach offers practical lessons.
Conduct a data audit: Identify all sensitive data your organization holds. Where is it stored? Who has access? How is access monitored? Is sensitive data properly classified and labeled? Do employees understand what data is sensitive and why it must be protected?
Evaluate third-party risk: Review all service providers and vendors who have access to sensitive data. Do contracts specify security requirements? Have you conducted security audits of these third parties? Do you have visibility into their security practices, incident history, and employee training?
Implement access controls: Use the principle of least privilege. Employees should only have access to data they need for their specific jobs. Access should be logged and periodically reviewed. Elevated access (to sensitive files or systems) should require additional authentication, ideally including multi-factor authentication.
Monitor for data exfiltration: Implement data loss prevention tools that monitor for unusual patterns of data access and transfer. If someone suddenly downloads hundreds of large files when they normally download zero, that's suspicious. If data is transferred to unusual locations or outside your network, that warrants investigation.
Have an incident response plan: Who is responsible for different aspects of incident response? What's the process for detecting, investigating, and responding to breaches? How quickly can you isolate compromised systems? How do you communicate with affected parties? Have you practiced your incident response plan?
Invest in threat detection: Sophisticated attacks often take weeks or months to execute. Early detection can limit the damage. Invest in security monitoring tools that can detect suspicious behavior: unusual login times, access from unexpected locations, unusual data transfers, suspicious process execution.
Stay informed about threats: Subscribe to information from CISA (Cybersecurity and Infrastructure Security Agency), your industry sector's information sharing organization, and threat intelligence services. Understanding what threats are currently active in your industry helps you prioritize defenses.

What This Means for Energy Consumers
Let's bring this back to the individual level. If you're a customer of Duke Energy, Tampa Electric, or American Electric Power, what does this breach mean for you? Directly, very little. The stolen data is operational infrastructure information, not customer account data, billing information, or personal information. You're not at risk of identity theft because your Social Security number wasn't stolen. Your power bills won't change because some files with elevation maps were exfiltrated.
Indirectly, the implications are more concerning. If the stolen data is used by adversaries to understand vulnerabilities in the power grid, that increases the risk of infrastructure attacks that could cause outages. If the data is used to plan more sophisticated attacks on utilities, that could lead to widespread power disruptions affecting millions of people.
The most vulnerable populations are those that depend on continuous power: hospitals with life-support systems, people using medical equipment at home, elderly people relying on air conditioning or heating, water treatment facilities needing power to deliver clean water.
What should consumers do? Stay informed about utility security through official utility channels. Support investment in grid modernization and security. If your utility has a resilience program for vulnerable populations, use it. Have backup plans for extended outages: backup power for essential devices, stored water, first aid kits, and communication devices.
Unfortunately, individual consumers have limited ability to affect critical infrastructure security. That responsibility falls on utilities and government. But being aware of the risks and supporting policies that enhance security is the appropriate consumer response.

The Investigation: Where It Stands and Where It's Heading
As of now, Duke Energy has confirmed it's investigating the breach claims. Law enforcement agencies (FBI, CISA, potentially others) are likely also investigating. The Department of Energy may conduct a separate assessment.
Expect these investigation activities:
Timeline reconstruction: Investigators will work to determine when the attackers first gained access to Pickett and Associates' systems, how long they maintained access, and when the data was exfiltrated. This involves analyzing logs from Pickett's systems, interview employees, and reconstruction of network activity.
Scope determination: Beyond the 800+ files mentioned by the threat actors, investigators will try to determine if additional data was stolen. Companies often discover that attacks were larger than initially apparent.
Attribution: Law enforcement will attempt to identify who conducted the attack. This involves analyzing the attackers' techniques, tools, and patterns, comparing them to known threat groups, and attempting to trace cryptocurrency payments.
Impact assessment: For each utility mentioned, investigators will assess what data was actually stolen and what the potential impact is. This involves reviewing the stolen files and evaluating what operational risks they create.
The investigation timeline is typically measured in months or years. It's rare that attackers are identified and prosecuted quickly. Sometimes attribution is never made public. Sometimes investigations conclude that state actors were responsible but there's no public announcement because of diplomatic implications.
For now, expect Duke Energy and other utilities to provide minimal public updates. Security investigations are typically conducted confidentially to preserve investigative value and avoid tipping off attackers about what law enforcement knows.

Looking Ahead: Future Vulnerabilities
If this breach teaches us anything, it's that similar breaches will happen again. The question isn't if, but when and where. Future risks include:
Water utilities: These face similar vulnerabilities to power utilities. They contract with engineering firms that maintain detailed maps of water infrastructure. If that data is stolen, it could enable attacks on water systems that millions depend on for drinking water.
Transportation infrastructure: Roads, bridges, and public transit systems are critical. Detailed maps of these systems could enable terrorist attacks or infrastructure sabotage.
Telecommunications networks: The backbone of modern communications, including backbone networks that carry internet and phone traffic, could be targeted similarly.
Healthcare infrastructure: Hospitals and healthcare networks depend on power, water, and communications. Attacks on these systems indirectly attack healthcare.
Data centers: The cloud infrastructure that modern businesses depend on is increasingly geographically concentrated. Maps and information about data center locations and vulnerabilities are sought after.
Each of these sectors has third-party service providers holding sensitive operational data. Each is vulnerable to similar compromise. And each would have significant consequences if critical infrastructure was damaged.

FAQ
What is critical infrastructure and why does it matter?
Critical infrastructure includes the physical systems and networks essential for society to function: power grids, water systems, telecommunications networks, transportation systems, and financial systems. These systems are so fundamental that disruptions cause cascading failures affecting hundreds of millions of people. A prolonged power outage in a major city could cause deaths, economic losses in the billions, and widespread chaos.
How do attackers typically breach companies like Pickett and Associates?
Attackers use multiple methods including phishing emails to steal login credentials, exploiting unpatched security vulnerabilities in web applications, purchasing compromised credentials from data breach marketplaces, conducting brute force attacks against weak passwords, and social engineering to trick employees into providing access. Once inside, they move laterally through networks to find sensitive data and exfiltrate it.
Why is LiDAR data so valuable to attackers?
LiDAR creates precise 3D maps showing terrain, vegetation, and structures. For infrastructure, it reveals exactly where power lines are located, how they're supported, what vegetation exists nearby that could be cut to cause outages, and structural details that could help plan attacks. Combined with other data, LiDAR maps provide operational intelligence that adversaries use for reconnaissance and attack planning.
What does FERC do to protect critical infrastructure?
FERC enforces the Critical Infrastructure Protection (CIP) standards that require utilities to implement cybersecurity measures including access controls, incident response plans, security monitoring, and regular assessments. FERC also coordinates with other agencies like the Department of Energy and works with the Electricity Subsector Coordinating Council to share threat information and develop security guidance for utilities.
Could this data be used to cause a power outage?
The data itself doesn't directly cause outages, but it provides valuable intelligence for planning attacks. An attacker with infrastructure maps could identify critical choke points where removing a few transmission lines would cause cascading failures affecting millions. They could target substations that are geographically isolated where emergency response is slower. They could identify vegetation risks and exploit them. The data significantly increases the sophistication and effectiveness of infrastructure attacks.
What should utilities do differently to prevent similar breaches?
Utilities should implement zero-trust network architecture, conduct regular security audits of critical systems and third-party vendors, establish specific security requirements for service providers, implement data loss prevention tools, provide security training to employees, maintain 24/7 security operations centers, and conduct regular incident response drills. They should also limit how long sensitive data is retained and compartmentalize access to reduce the impact if data is stolen.
How is bitcoin used in cybercrime and can payments be traced?
Attackers request payment in bitcoin because it enables relatively anonymous transactions compared to traditional banking. However, bitcoin transactions are permanently recorded on the public blockchain, making them theoretically traceable. Criminals use mixing services and exchanges in countries with weak anti-money-laundering enforcement to obscure the trail. Law enforcement has become better at tracking cryptocurrency but determined adversaries can still hide their tracks reasonably well.
What happens when utilities are breached?
Utilities typically conduct internal investigations to determine the scope of the breach, work with law enforcement if a crime occurred, notify regulators as required by FERC rules, potentially notify customers if personal information was exposed, implement security improvements to prevent recurrence, and may face lawsuits from affected parties. Public communication is usually limited until investigation is complete because disclosing details could complicate law enforcement efforts.

The Critical Reality: It's Not If, But When
The Pickett and Associates breach isn't a unique incident. It's a symptom of systemic vulnerabilities in how America approaches critical infrastructure security. We have utilities that run on systems designed in the 1970s. We have infrastructure that depends on third-party service providers with inconsistent security practices. We have regulatory frameworks that are reactive, not proactive. We have adversaries—nation-states and criminal organizations—actively targeting these systems for economic, political, and military advantage.
The breach also highlights how information asymmetry creates false confidence. Most Americans don't realize how close we've come to major infrastructure disruptions, how often attackers probe our systems, how much sophisticated nations know about our infrastructure vulnerabilities. Regulatory agencies know more than the public. Utilities know more than regulators. Intelligence agencies know more than utilities.
This knowledge gap means society underinvests in infrastructure security. If people truly understood how vulnerable the power grid is, there would be massive political pressure for hardening. Instead, critical infrastructure security remains an afterthought, underfunded and understaffed.
What this breach really shows is that we need a fundamental rethinking of how critical infrastructure is protected. It's not enough to follow regulations written a decade ago. It's not enough to hope attackers don't target your specific organization. It's not enough to assume your service providers have adequate security.
We need defense in depth: multiple layers of security so if one layer fails, others catch the attack. We need threat intelligence sharing so organizations learn from each other's incidents. We need investment in security talent because there's a shortage of skilled cybersecurity professionals. We need to remove perverse incentives that encourage organizations to hide breaches rather than transparently reporting them. And we need to accept that some attacks will succeed, so resilience and rapid recovery matter as much as prevention.
The Pickett and Associates breach is a wake-up call. Whether we heed it or continue sleepwalking toward a major infrastructure disaster remains to be seen.
Key Takeaways
- Pickett and Associates, a Florida-based engineering firm, has been breached with 800+ sensitive files stolen from major US utilities including Duke Energy, Tampa Electric, and American Electric Power
- The stolen data includes LiDAR point clouds, transmission corridor maps, orthophotos, and design files valued at approximately $600,000 and now for sale on dark web forums
- Third-party service provider vulnerabilities represent a critical weak point in infrastructure security, as utilities outsource specialized work without full oversight of vendor security practices
- Similar threats are targeting critical infrastructure globally, with the same threat actors also selling stolen data from Germany's Enerparc AG, suggesting coordinated nation-state or organized crime operations
- Effective response requires strengthening FERC standards, implementing zero-trust security architecture, improving incident detection and response capabilities, and treating infrastructure security as a competitive differentiator
![Critical Infrastructure Breach: Engineering Firm Hack Exposes US Utilities [2025]](https://tryrunable.com/blog/critical-infrastructure-breach-engineering-firm-hack-exposes/image-1-1767645670582.jpg)



