The Bitfinex Heist That Shook Crypto: How a $5.2 Billion Theft Changed Everything
Imagine someone breaking into the vault of one of the world's largest cryptocurrency exchanges and walking out with 120,000 bitcoin. That's not a hypothetical—it actually happened in August 2016 at Bitfinex, a cryptocurrency platform based in Hong Kong. The theft amounted to roughly $71 million at the time, but those stolen coins are now worth billions in today's market. What made this crime particularly remarkable wasn't just the scale or the value. It was the years-long cat-and-mouse game that followed, the sophisticated money laundering schemes designed to hide the loot, and ultimately, the early release of the mastermind thanks to presidential legislation.
Ilya Lichtenstein was the technical architect behind one of the biggest cryptocurrency thefts in history. For years, he successfully evaded detection while he and his wife, Heather "Razzlekhan" Morgan, moved stolen bitcoin through an intricate web of darknet markets, cryptocurrency mixers, fake identities, and complex wallet chains. Their operation was methodical, careful, and designed to blend legitimate financial activity with criminal proceeds. But in January 2022, federal agents showed up at their door with arrest warrants. What happened next would expose not just their crimes, but also the vulnerabilities in how we track cryptocurrency transactions and the evolving nature of digital currency crime.
In early 2025, Lichtenstein walked out of prison early. He credited President Donald Trump's First Step Act, a 2018 criminal justice reform law designed to reduce incarceration and encourage rehabilitation. His release sparked intense debate about criminal justice reform, cryptocurrency security, and whether early release sends the right message to the tech industry. Some viewed it as a triumph of rehabilitative justice. Others saw it as a slap in the face to the victims and the law enforcement professionals who spent years tracking down one of the biggest digital heists ever.
This isn't just a story about a clever hacker or a broken security system. It's about how cryptocurrency's perceived anonymity created opportunities for crime, how law enforcement adapted to catch criminals in the digital age, and what happens when someone convicted of one of the biggest financial crimes in history gets a second chance. Let's dig into what really happened, how they pulled it off, and why this case matters for cybersecurity and criminal justice.
TL; DR
- The Bitfinex hack in 2016 resulted in the theft of 120,000 bitcoin, worth roughly $5.2 billion at current market prices, making it one of the largest cryptocurrency thefts ever recorded
- Ilya Lichtenstein spent nearly 6 years in prison after pleading guilty to conspiracy to commit money laundering and was released early in 2025 under the First Step Act criminal justice reform law
- The duo used sophisticated money laundering techniques including darknet markets, cryptocurrency mixers, and fake identities to hide stolen funds across multiple blockchain networks
- Federal investigators traced the crypto through blockchain analysis, demonstrating that digital currencies aren't truly anonymous and that advanced forensic techniques can recover stolen digital assets
- The First Step Act allows eligible prisoners to earn time credits for good behavior and program participation, reducing sentences by years and enabling early release for qualifying inmates
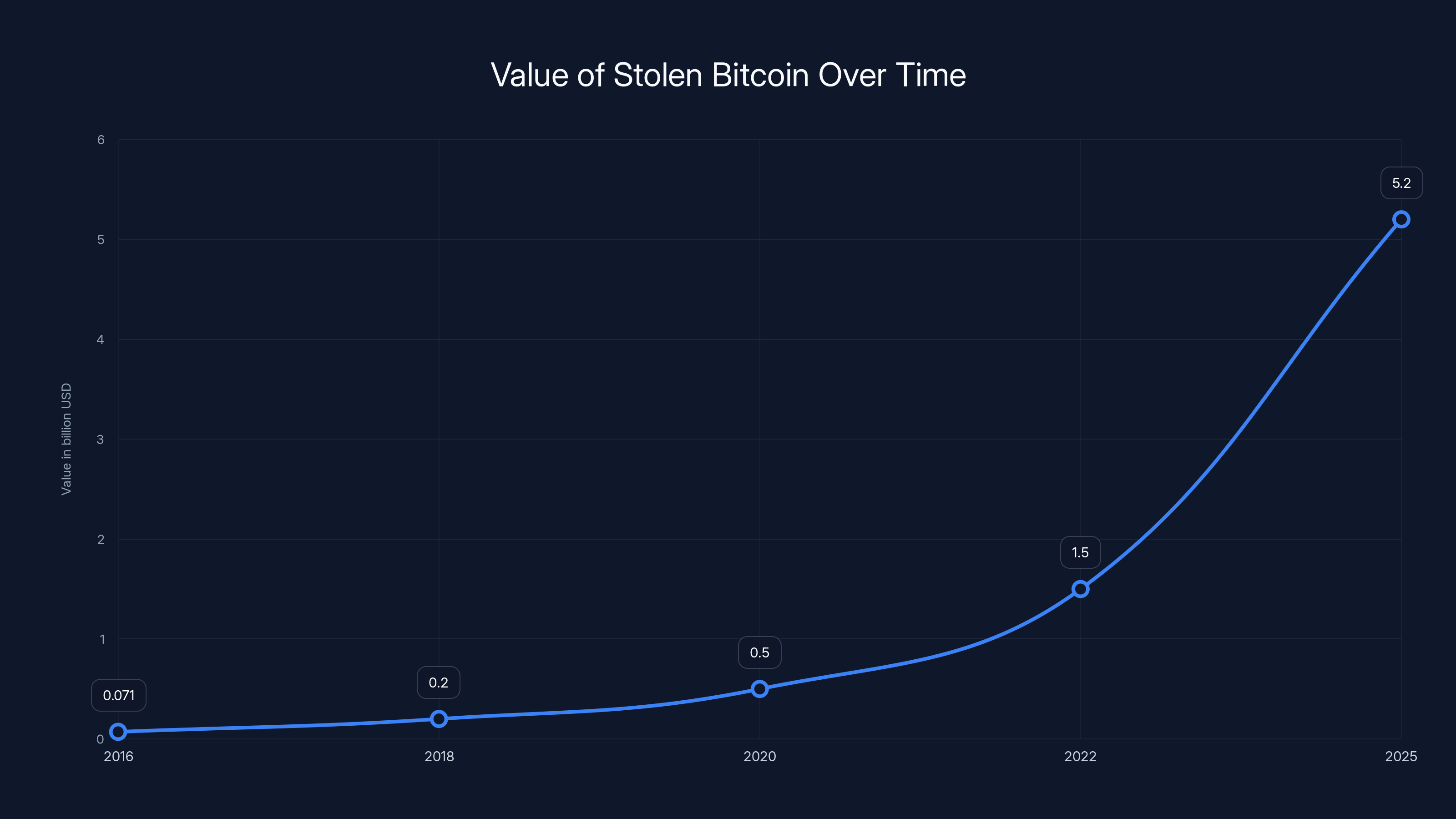
The value of the stolen bitcoin from the Bitfinex hack increased dramatically from
Understanding the 2016 Bitfinex Hack: How 120,000 Bitcoin Disappeared
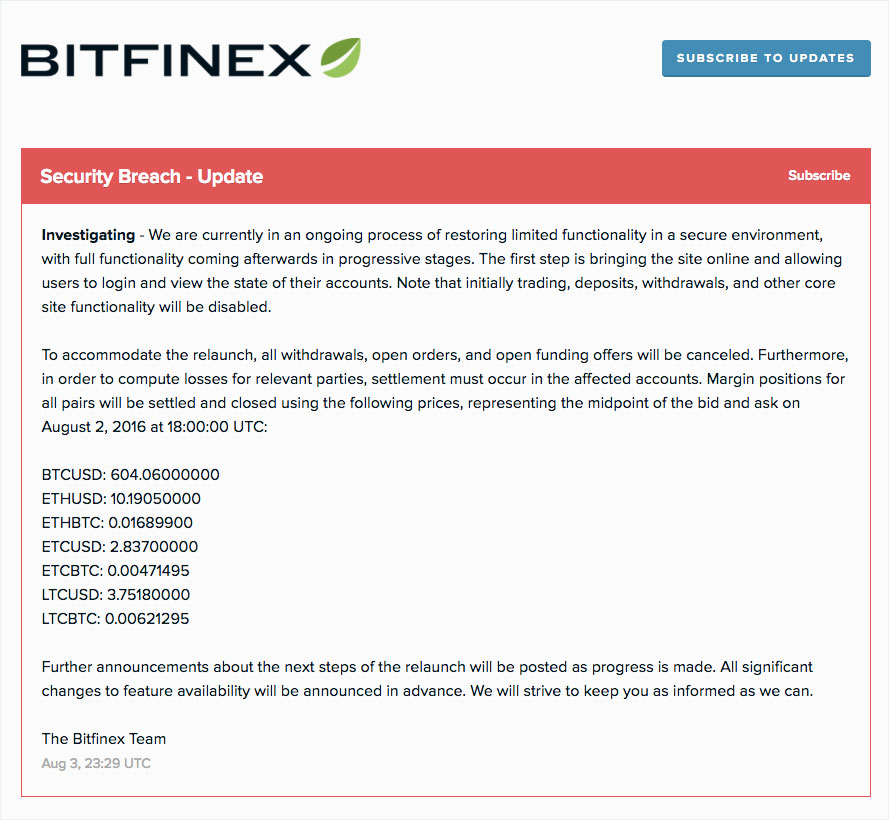
Bitfinex was one of the largest cryptocurrency exchanges in the world back in 2016. The platform allowed users to buy, sell, and trade cryptocurrencies, primarily bitcoin and ethereum. It handled millions of dollars in daily transactions and attracted traders from around the globe who wanted exposure to cryptocurrency markets. Like most exchanges, Bitfinex held cryptocurrency in digital wallets for its users, storing the private keys needed to access those funds. If security was breached, those keys could be stolen, and the cryptocurrency could be transferred instantly to attackers' wallets. There's no chargebacks in crypto, no fraud insurance, no way to reverse transactions. Once coins are stolen and moved, they're gone.
On August 2, 2016, hackers exploited a vulnerability in Bitfinex's security infrastructure. The attack was sophisticated—it wasn't a random phishing attempt or a brute-force password cracking scenario. Someone gained unauthorized access to the exchange's internal systems and wallet infrastructure. In the chaos that followed, approximately 119,756 bitcoin were stolen directly from Bitfinex's hot wallet, the online storage system connected to the internet where the exchange kept cryptocurrency for active trading. Users' accounts were also compromised. The exchange immediately shut down trading to prevent further theft, but the damage was done.
At the time, 120,000 bitcoin was worth approximately
Bitfinex eventually compensated affected users through a combination of their own insurance funds and recovery efforts. The exchange implemented security improvements and continued operating, but the hack became one of the defining moments in cryptocurrency history. It demonstrated that even established, relatively well-funded exchanges could suffer massive security breaches. It showed the cryptocurrency industry that if you're going to hold digital assets, security can't be an afterthought.
The immediate aftermath was chaotic. Users demanded answers about how the breach happened. Investigators began tracking the stolen coins across the blockchain. And somewhere, someone with deep technical knowledge of cryptocurrency, wallets, and financial systems was starting to move that bitcoin, knowing that law enforcement would eventually be hunting for it.
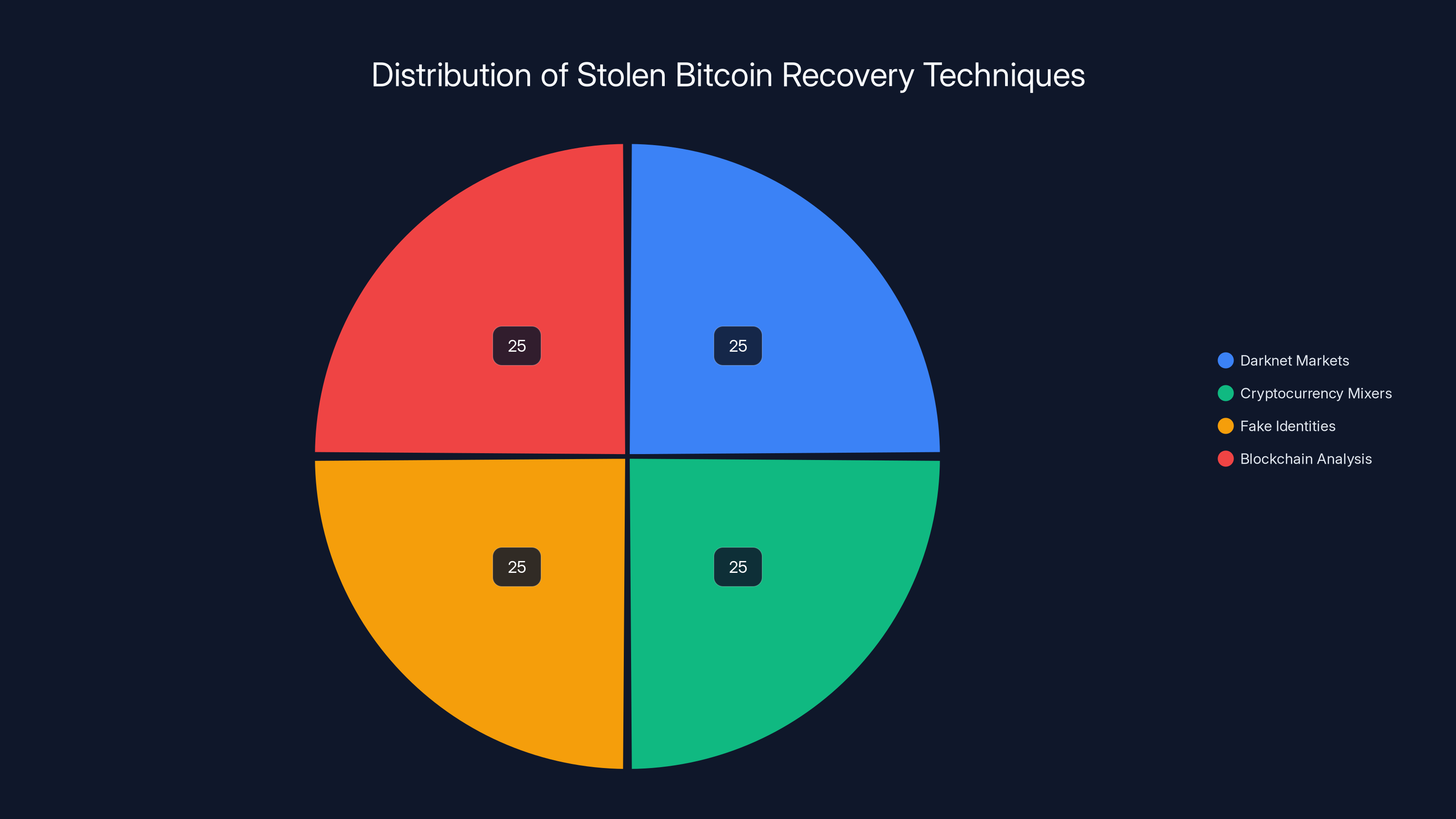
Estimated data showing equal reliance on various techniques to trace and recover stolen Bitcoin, highlighting the complexity of the investigation.
Who Is Ilya Lichtenstein? The Technical Mind Behind the Heist
Ilya Lichtenstein is a Russian-born U. S. citizen with a background in computer science and cryptocurrency. He wasn't a stereotypical career criminal with a long rap sheet. He was technically skilled, deeply knowledgeable about how cryptocurrency works, and comfortable operating in the dark corners of the digital ecosystem. This expertise made him dangerous, because he understood not just how to access systems, but how to hide stolen digital assets once he had them.
Lichtenstein was born in Russia but immigrated to the United States, eventually becoming a U. S. citizen. He developed significant expertise in software development and cryptocurrency technology. Unlike street criminals who operate through physical force or basic fraud, Lichtenstein's tools were keyboards, code, and an understanding of financial systems. He could read technical documentation, identify vulnerabilities in security architecture, and exploit them methodically.
What's particularly notable about Lichtenstein is that he seemed to understand that stealing cryptocurrency is only half the battle. The real challenge is moving it without getting caught. Digital currencies exist on public blockchains, which means every transaction is theoretically traceable. Every wallet address, every transfer, every exchange interaction leaves a footprint. This is fundamentally different from stealing physical cash, where you can physically hide the money and it's impossible to trace. With cryptocurrency, the record of the theft is permanent and public. You need a sophisticated plan to move the coins in ways that obscure your ownership, hide the connection to the original theft, and eventually convert them to fiat currency without triggering alarms.
This is where Lichtenstein's technical expertise became his most valuable tool. He wasn't just the guy who broke in to Bitfinex. He was the architect of the entire laundering operation that followed. Federal investigators would later describe him as the "technical architect" of both the hack and the subsequent money laundering conspiracy. That means he designed the systems, understood the processes, and directed how stolen funds were moved, mixed, and hidden.
Lichtenstein worked alongside his wife, Heather Morgan, who would become known in the media as "Razzlekhan," a reference to her social media persona. She portrayed herself as a tech entrepreneur and social media influencer. Together, they formed an unlikely partnership. Lichtenstein handled the technical side of moving and mixing the cryptocurrency. Morgan seemed to handle more operational and social aspects. What unified them was their commitment to keeping the stolen bitcoin hidden for years while they figured out what to do with it.
The Money Laundering Operation: How They Hidden $5.2 Billion in Bitcoin
Once Lichtenstein had the stolen bitcoin, the real challenge began. How do you move 120,000 bitcoin without law enforcement noticing? The answer requires understanding cryptocurrency mixing, darknet markets, and identity obfuscation.
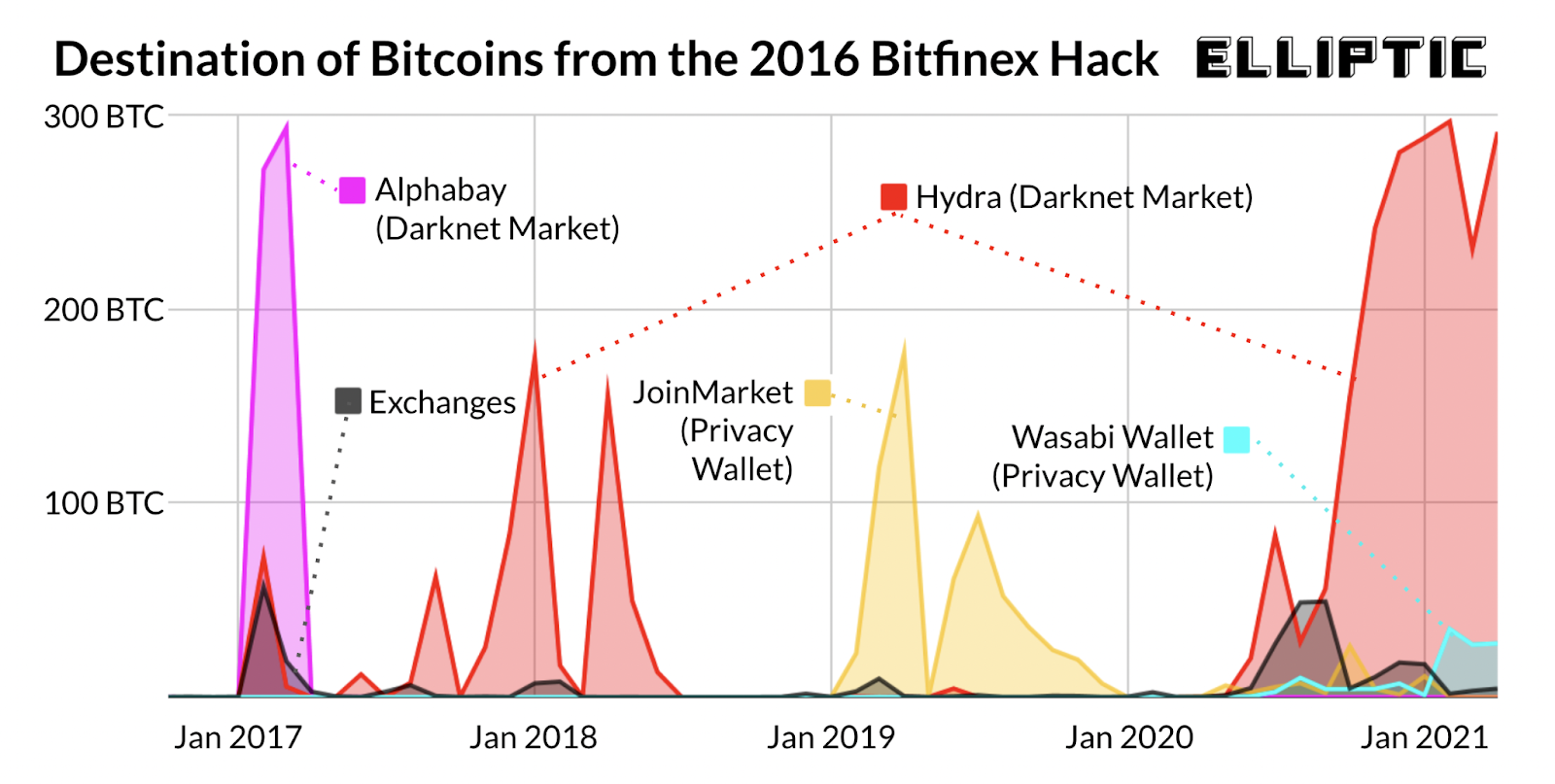
The first tactic was using cryptocurrency mixers, sometimes called "tumblers." These are services that take cryptocurrency from multiple sources, pool them together, and redistribute them in new combinations. The theory is that if you send bitcoin to a mixer, and 1,000 other people send bitcoin to the same mixer at roughly the same time, when the mixed coins come back out, there's no clear link between the original coins and the coins you receive. In practice, mixers provide some obfuscation, but they're not perfect. If you send exactly 100 bitcoin in and receive exactly 100 bitcoin back a few hours later, blockchain analysts can sometimes establish the connection through timing and amount analysis.
Lichtenstein didn't rely solely on mixers. Instead, he used them as one layer in a multi-layered approach. He would move coins through mixers, then to darknet marketplaces, then to different wallets, then to other mixing services, and back again. The goal was to create so many hops that tracing the original coins back to the Bitfinex theft became computationally difficult and analytically impossible.
Darknet markets played a key role. These are websites accessible only through special software like Tor, which anonymizes internet traffic. Darknet markets facilitate the buying and selling of both legal and illegal goods. Lichtenstein and Morgan would move stolen bitcoin through these marketplaces, sometimes participating in transactions with other users to further obscure the source of the coins. Every transaction added another layer of complexity to the chain.
They also used fake identities and multiple accounts. Rather than using one wallet address controlled by one person, they created numerous wallet addresses, some associated with fictional identities, some tied to compromised accounts, some linked to legitimate-seeming business entities. The effect was to create a web of interconnected wallets that made it difficult to determine who actually controlled any single address.
One particularly clever tactic involved using the stolen bitcoin to purchase other cryptocurrencies. Bitcoin is the most recognizable cryptocurrency, but there are thousands of alternatives. By converting stolen bitcoin to ethereum, monero, or other coins, they could further obscure the trail. Ethereum, for instance, operates on a different blockchain with different analytics tools. Moving coins from one blockchain to another creates friction that slows down investigators.
They also attempted to move coins through legitimate exchanges, though this is where their operation eventually became vulnerable. Exchanges have gotten better at understanding cryptocurrency flows. They use blockchain analysis companies to identify suspicious patterns. If someone suddenly tries to exchange 1,000 bitcoin for fiat currency without proper identification documents or legitimate explanation for the source, exchanges now have sophisticated systems to flag that activity.
For nearly six years, the operation worked. From 2016 to 2022, Lichtenstein and Morgan successfully moved significant portions of the stolen bitcoin without being caught. They didn't attempt to cash out all of it at once. They were patient, methodical, and careful. This patience itself was a security measure. Attempting to liquidate all 120,000 bitcoin simultaneously would have triggered massive alarms across the cryptocurrency ecosystem. By moving slowly, they kept the operation under the radar.

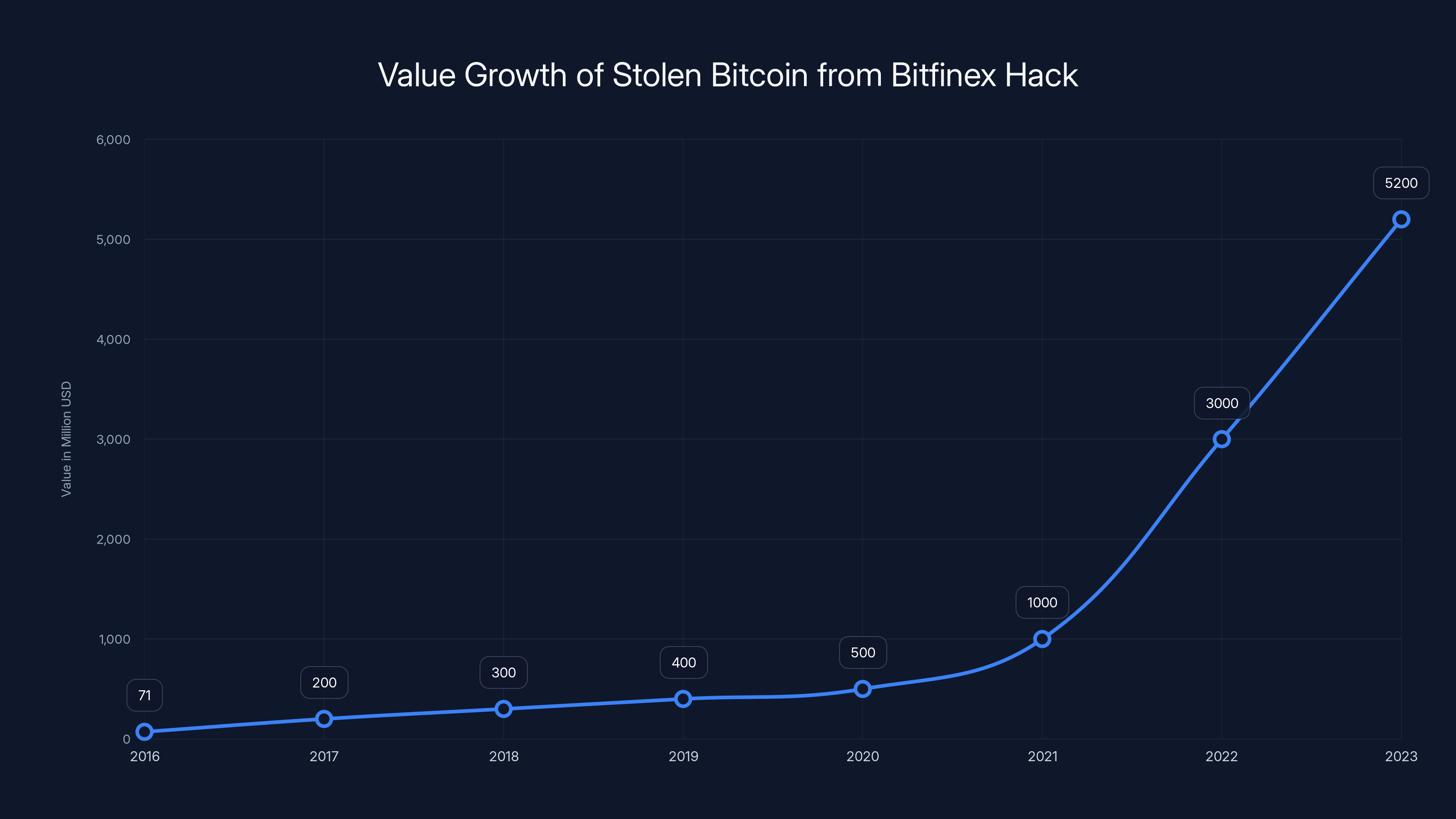
The value of the stolen 120,000 bitcoins from the Bitfinex hack increased from
The Investigation: How Law Enforcement Caught Them
Federal investigators didn't solve this case through luck. They solved it through combination of traditional detective work, advanced blockchain analysis, and human error.
The key breakthrough came when investigators identified specific wallet addresses associated with the stolen bitcoin. This required analyzing the public blockchain and identifying patterns. When the Bitfinex hack occurred, the stolen coins were moved to specific addresses. Blockchain analysts could see those transactions clearly on the public ledger. From there, investigators could trace where those coins flowed next, what exchanges they interacted with, and what patterns emerged.
One particularly valuable tool was blockchain analysis software. Companies like Chainalysis, Elliptic, and others developed sophisticated tools that can trace cryptocurrency transactions across multiple blockchains. These tools can identify patterns, flag suspicious activities, and help connect wallet addresses to real-world identities. When Lichtenstein and Morgan moved stolen coins through exchanges, even partial exchanges or conversions, these tools could detect the activity.
Law enforcement also benefited from customer identification requirements (KYC) at major exchanges. When someone tries to exchange a large amount of cryptocurrency for fiat currency or transfer it off an exchange, reputable platforms require identity verification. If Lichtenstein or Morgan attempted to convert stolen bitcoin to dollars and deposit it in a bank account, they would need to verify their identity. Any attempted transaction would create a record linking their personal identity to the stolen coins.
Investigators also conducted traditional surveillance and intelligence gathering. They monitored darknet marketplaces, tracked suspicious accounts, and analyzed financial patterns. When you're moving billions of dollars in stolen assets, you leave traces. You interact with other people in the cryptocurrency ecosystem. You engage in transactions. Each interaction creates data points that investigators can analyze.
The breakthrough came when investigators were able to connect Heather Morgan and Ilya Lichtenstein to specific wallet addresses. Once that connection was established, federal agents had probable cause to conduct a search warrant. In January 2022, they showed up at Lichtenstein and Morgan's residence with arrest warrants. They found evidence of the money laundering operation, cryptocurrency wallets under their control, and documentation of transactions.
What's particularly interesting is that investigators recovered a significant portion of the stolen bitcoin. Not all of it, but a meaningful amount. This recovery demonstrates that despite the sophistication of their operation, law enforcement had become skilled enough at tracking cryptocurrency to catch them and recover stolen assets. It's a vindication of blockchain analysis technology and a warning to anyone thinking about stealing cryptocurrency. You can hide it for a while, but advanced forensic techniques and patient detective work can eventually trace it back to you.

The Legal Case: From Arrest to Guilty Plea
When federal agents arrested Lichtenstein and Morgan in January 2022, they faced serious charges. The allegations included wire fraud, conspiracy to commit money laundering, and related financial crimes. These aren't minor charges. Wire fraud alone can carry sentences of up to 20 years. Money laundering conspiracies can add decades. The potential exposure was substantial.
Lichtenstein eventually pleaded guilty to conspiracy to commit money laundering. This is significant. By accepting a guilty plea, he avoided going to trial. Trials are unpredictable. A jury could convict him on every charge, or they could acquit him on some. By pleading guilty, he accepted responsibility, but he also negotiated a sentencing agreement with prosecutors. Instead of facing 20-plus years, he received a 5-year sentence.
Heather Morgan, his wife, faced charges as well but received a lighter sentence of 18 months, apparently reflecting a different role in the conspiracy or more cooperation with prosecutors.
When Lichtenstein was sentenced in November 2023, the court acknowledged the seriousness of the crime. The judge noted the scale of the theft, the sophistication of the money laundering operation, and the years of criminal activity. However, the judge also considered mitigating factors, including Lichtenstein's acceptance of responsibility through his guilty plea, his lack of prior criminal history, and other personal circumstances.
The sentence itself reflected both punishment and the federal guidelines for similar crimes. A 5-year sentence for stealing
What happened next, however, would prove more controversial.

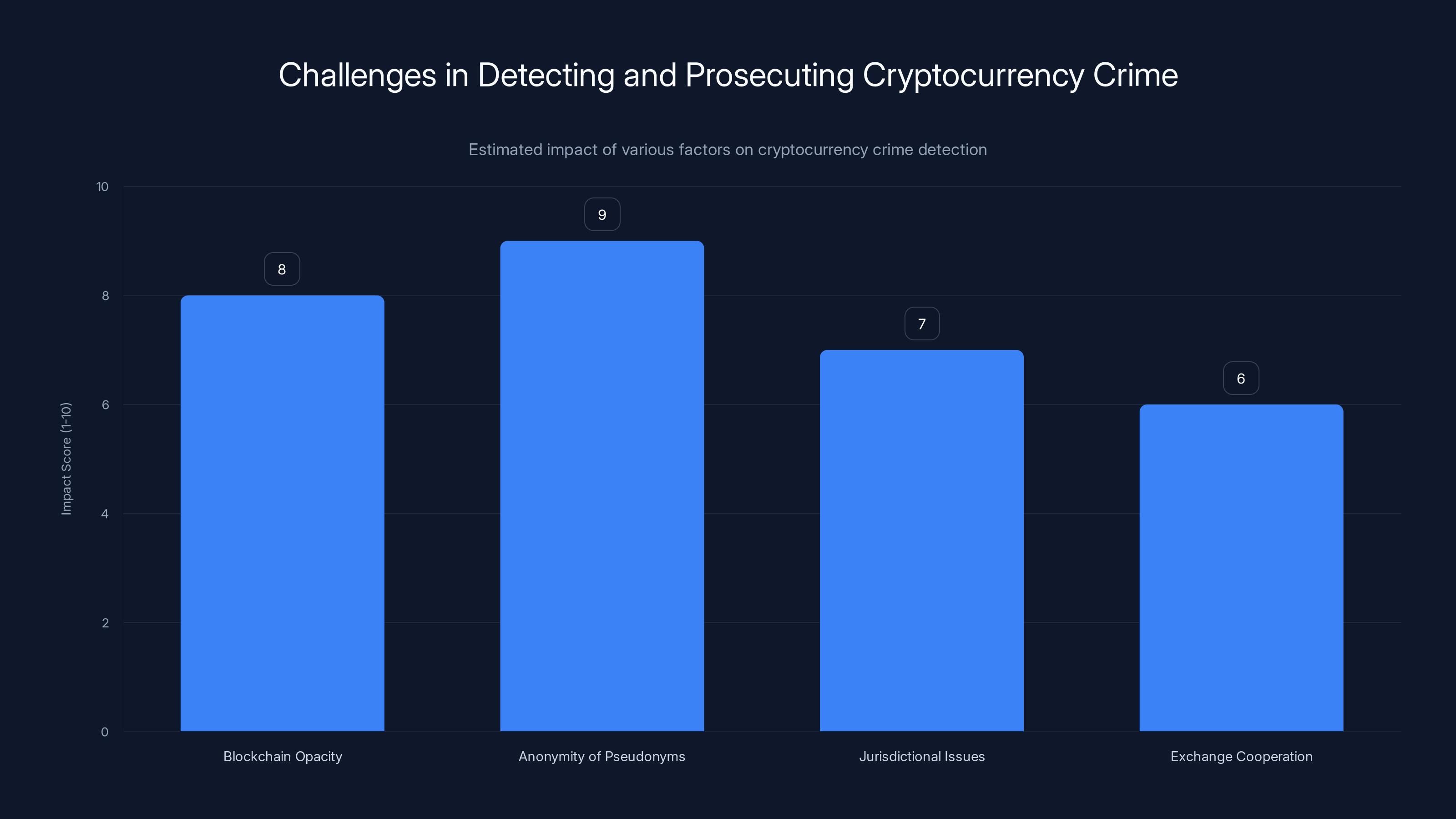
Anonymity of pseudonyms and blockchain opacity are the most significant challenges in detecting and prosecuting cryptocurrency crime. Estimated data.
Understanding the First Step Act: Criminal Justice Reform in Practice
The First Step Act is a federal law passed in December 2018 with bipartisan support. The legislation was designed to reform the federal criminal justice system by reducing incarceration, encouraging rehabilitation, and giving eligible prisoners opportunities to shorten their sentences.
At its core, the First Step Act is based on the philosophy that incarceration alone doesn't necessarily prevent crime or rehabilitate offenders. Instead, the law creates mechanisms for prisoners to demonstrate that they're making positive changes and deserve a reduced sentence. Specifically, the Act allows eligible federal prisoners to earn Time Credits for Good Behavior and Program Participation.
How do these Time Credits work? Federal prisoners can participate in various approved programs, including:
- Educational programs: GED classes, vocational training, college courses
- Job training: Apprenticeships, skills training, professional certification programs
- Substance abuse treatment: Drug and alcohol rehabilitation programs
- Mental health treatment: Counseling and psychological services
- Good conduct: Simply following prison rules, avoiding disciplinary infractions
When prisoners participate in these programs and demonstrate good behavior, they can earn Time Credits. These credits can accumulate to meaningfully reduce a sentence. Instead of serving five years, a prisoner who earns sufficient credits might serve three years, or even less, depending on the amount of credits earned and how the sentencing judge authorized them to be used.
The philosophy behind this approach is sensible. If a prisoner spends their time in prison getting educated, learning a trade, addressing substance abuse issues, and following rules, they're arguably more likely to succeed after release than someone who simply sits in a cell counting down the days. The First Step Act creates incentives for prisoners to engage in self-improvement.
For Lichtenstein specifically, he would have been eligible to participate in educational and job training programs while in federal custody. If he earned sufficient Time Credits and met the other requirements of the law, he could apply for sentence reduction. A judge would review his application, consider the nature of his crime, his behavior while incarcerated, his participation in programs, and other factors, then decide whether to grant sentence reduction.
In February 2025, Lichtenstein was released early from federal prison, reportedly after serving approximately 2.7 years of his 5-year sentence. He credited President Trump's administration and the First Step Act for his early release. In a post on X (formerly Twitter), he wrote: "Thanks to President Trump's First Step Act, I have been released from prison early. I remain committed to making a positive impact in cybersecurity as soon as I can. To the supporters, thank you for everything. To the haters, I look forward to proving you wrong."
His wife, Morgan, was also released early and celebrated the reunion with a post of her own, saying: "The best New Years present I could get was finally having my husband home after 4 years of being apart."

The Controversy: Was Early Release Appropriate?
The early release of Ilya Lichtenstein sparked significant debate in cybersecurity, law enforcement, and criminal justice communities.
Supporters of the early release argue that the First Step Act is working as intended. Lichtenstein served time, presumably participated in educational and rehabilitation programs, demonstrated good behavior, and earned the credits to support early release. He accepted responsibility through his guilty plea rather than forcing prosecutors to prove the case. His wife was also released, and both have an opportunity to reintegrate into society. From this perspective, the criminal justice system should focus on rehabilitation rather than pure punishment, especially for non-violent offenders. Lichtenstein's crime, while serious, was primarily financial in nature. He didn't physically harm anyone. If he's genuinely committed to changing his behavior, as he claims, early release gives him an opportunity to prove it.
Critics of the early release counter that Lichtenstein's crime was extraordinarily serious, even if non-violent. He stole billions of dollars in cryptocurrency (in current value). The operation was sophisticated and required years of sustained criminal effort. He lived with the proceeds of his crime for six years before being caught. The victims of the Bitfinex hack lost significant funds, and recovery was only partial. Releasing Lichtenstein early, from this perspective, sends the wrong message. It suggests that even massive financial crimes can result in relatively short sentences if the offender cooperates and participates in prison programs. For victims and law enforcement professionals, early release feels like a diminishment of the seriousness of the crime.
There's also the question of what Lichtenstein intends to do after release. He wrote that he wants to "make a positive impact in cybersecurity." He's got deep technical knowledge of cryptocurrency, security systems, and money laundering techniques. Will he use those skills for legitimate cybersecurity work, or could he potentially return to criminal activity? Even if his stated intentions are genuine, questions about trust and rehabilitation linger.

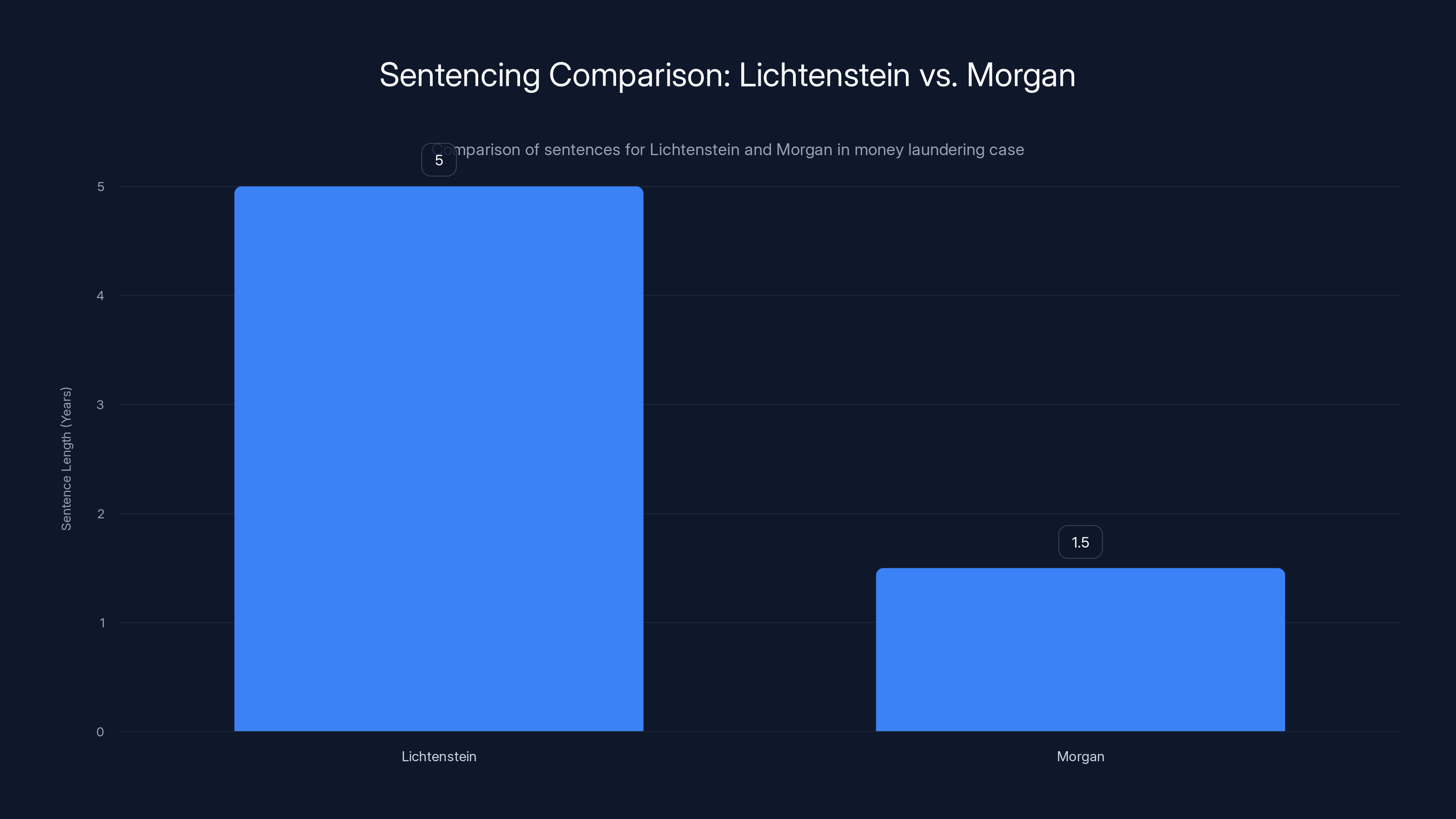
Lichtenstein received a 5-year sentence, while Morgan received an 18-month sentence, reflecting different roles and cooperation levels in the conspiracy.
Why Cryptocurrency Crime Remains So Difficult to Detect and Prosecute
The Bitfinex hack and the subsequent investigation reveal significant challenges in detecting and prosecuting cryptocurrency crime. Understanding these challenges helps explain both why Lichtenstein was able to hide for so long and why his case ultimately succeeded.
Blockchain opacity vs. blockchain transparency creates a paradox. While all Bitcoin transactions are recorded on a public ledger, determining who actually controls any given wallet address is extremely difficult. A wallet address is just a long string of characters. It could belong to one person, or multiple people could have access to a private key. If the person controlling the wallet uses cryptocurrency mixers, darknet marketplaces, and multiple wallet addresses, tracing the original coins to the current location becomes computationally complex and analytically difficult.
The anonymity of pseudonyms is another challenge. You can create a wallet address and begin conducting transactions with zero personal identification. Unlike traditional banks, which require proof of identity and maintain customer records, cryptocurrency wallets can be created instantly and anonymously. This anonymity is one of Bitcoin's core features, but it's also a significant tool for criminals.
International jurisdictional issues complicate enforcement. Cryptocurrency transactions can move across countries instantly. A wallet controller in Russia can send funds to an exchange in Singapore, which transfers them to a wallet in Switzerland, which moves them to a darknet marketplace with servers distributed across multiple countries. Each jurisdictional boundary creates challenges for law enforcement cooperation and evidence gathering.
Exchange cooperation and oversight varies significantly. Some exchanges have sophisticated compliance programs, blockchain analysis tools, and legitimate suspicion reporting systems. Others, particularly smaller exchanges or those operating in less regulated jurisdictions, may have minimal compliance infrastructure. This patchwork of oversight creates opportunities for criminals to use less-regulated exchanges to convert cryptocurrency to fiat currency.
Technological limitations in blockchain analysis exist despite advances. Current tools are powerful, but they're not perfect. Sophisticated actors can potentially remain below detection thresholds if they're patient enough and careful enough. The Bitfinex case succeeded partly because Lichtenstein eventually made moves that triggered investigation, but other criminals might avoid such triggers indefinitely.
Despite these challenges, law enforcement capabilities have improved significantly. The combination of blockchain analysis tools, international cooperation agreements, exchange compliance requirements, and traditional investigative techniques has made it substantially harder for criminals to hide cryptocurrency theft. The Bitfinex case is instructive precisely because it demonstrates that sophisticated money laundering operations can eventually be caught.

Recovering Stolen Cryptocurrency: Progress and Challenges
One of the remarkable aspects of the Bitfinex hack investigation was the recovery of stolen bitcoin. Federal law enforcement and Bitfinex itself worked to identify and recover portions of the stolen funds. The recovery process illustrates both the possibilities and limitations of modern cryptocurrency forensics.
When investigators identified wallet addresses containing stolen bitcoin, they could theoretically freeze or seize those addresses if they controlled the private keys. However, in practice, many stolen coins had been moved to wallets not controlled by law enforcement. Some coins were in wallets controlled by Lichtenstein and Morgan, which could be seized. But other coins had been moved to other parties, sometimes in legitimate transactions through exchanges, sometimes through other criminal enterprises that had purchased stolen bitcoin themselves.
Bitfinex's own recovery efforts involved a combination of legal action, negotiation with exchanges, and compensation of affected users. The exchange didn't recover 100% of stolen funds, but they did recover meaningful amounts and used a combination of recovered assets and their own insurance to compensate affected users.
The broader lesson here is that even when stolen cryptocurrency is successfully seized by authorities, questions remain about who has a legal claim to the assets. The original users whose accounts were compromised? The exchange itself? The federal government? Multiple parties can have legitimate claims. Resolution often requires litigation and negotiation.
For future cryptocurrency crime victims, improved security practices are critical. Exchanges are implementing hardware security modules, multi-signature wallet requirements, offline cold storage for assets not needed for immediate trading, and robust access control systems. These measures make it harder for attackers to steal large amounts of cryptocurrency, though they don't eliminate risk entirely.

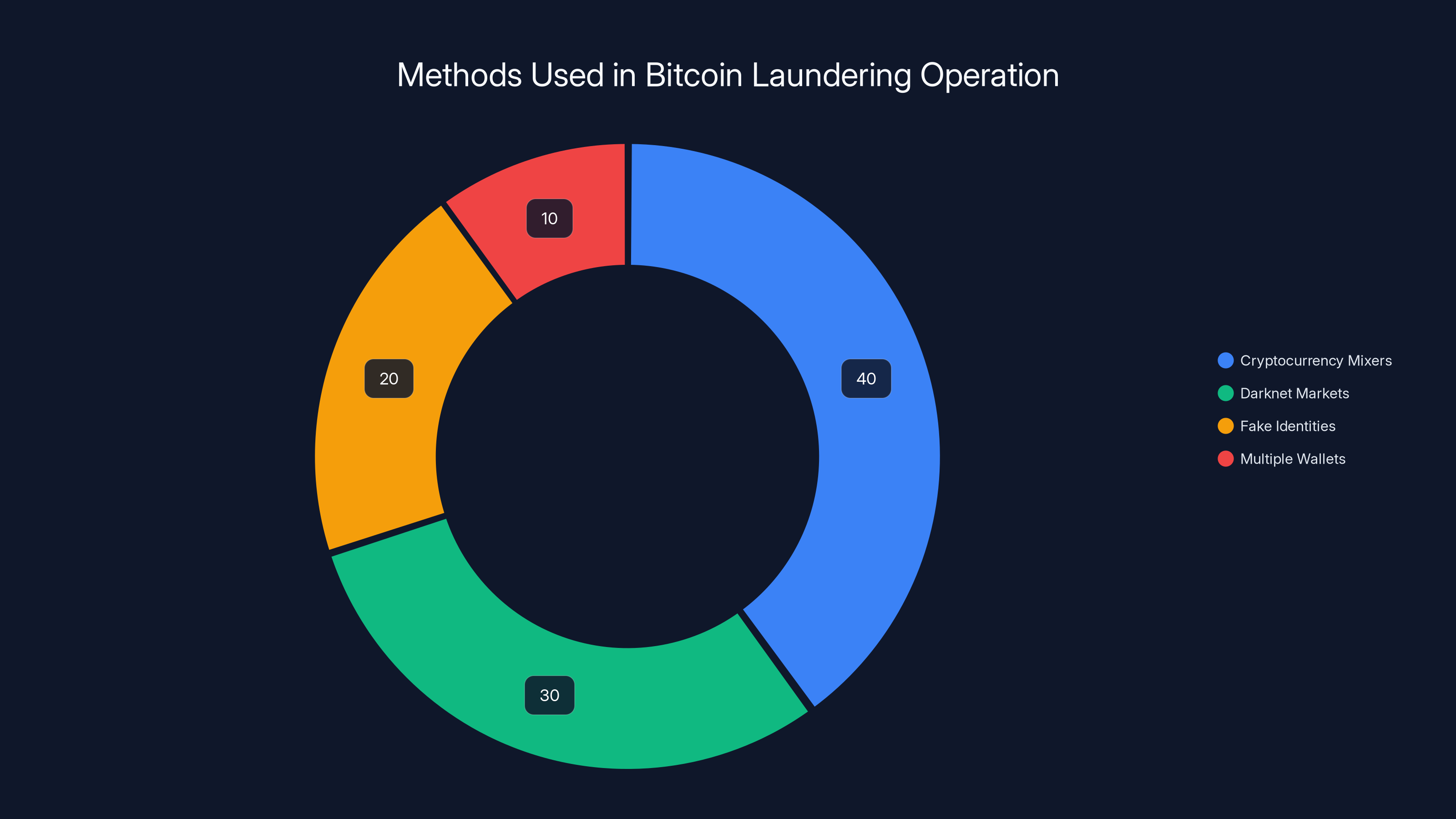
Estimated data shows that cryptocurrency mixers were the most used method, accounting for 40% of the laundering operation, followed by darknet markets at 30%.
The Broader Context: How This Case Changed Cryptocurrency Security
The Bitfinex hack occurred in 2016, when cryptocurrency security practices and regulatory oversight were in their infancy. Exchanges were still learning how to protect digital assets. There was minimal regulatory guidance, limited industry standards, and many security mistakes were still being made by even the largest players.
Today, the cryptocurrency industry has matured significantly. Exchanges implement security practices that were rare in 2016. Regulatory frameworks have been established in many jurisdictions. Industry security standards have been developed. The Bitfinex hack is now viewed as a foundational moment that drove security improvements across the ecosystem.
Key security improvements since 2016 include:
- Hardware security modules (HSMs) for key storage
- Cold storage strategies where most assets are kept offline
- Multi-signature requirements where multiple private keys are needed to authorize large transactions
- Regular security audits and penetration testing
- Insurance programs to protect users against theft
- Compliance officer positions and regulatory expertise
- Blockchain analysis tools integrated into exchange operations
- Improved access controls limiting employee access to sensitive systems
Bitfinex itself, despite being the victim of one of the largest cryptocurrency thefts ever, continued operating and implemented significant security improvements. The exchange now operates with what security professionals consider industry-leading security practices. Other exchanges learned from the Bitfinex experience and implemented similar protections proactively.
However, security is an ongoing challenge. Even with advanced security measures, vulnerabilities continue to emerge. Exchange hacks still occur, though typically at smaller scales and with better recovery processes than the original Bitfinex theft.

Criminal Justice Reform: Success Story or Soft on Crime?
The early release of Ilya Lichtenstein has become a focal point in the broader debate about criminal justice reform in the United States.
Proponents of criminal justice reform point to Lichtenstein's case as evidence that the system can work. He committed a serious crime, accepted responsibility, served his time while presumably improving himself through programs, and earned credits toward early release. The system incentivized good behavior and rehabilitation. From this perspective, there's nothing problematic about his early release. The First Step Act is functioning as intended. It's giving people second chances based on demonstrated reform.
Critics, particularly those focused on white-collar crime enforcement and cryptocurrency regulation, worry that early release for serious financial crimes sends the wrong message. It potentially makes financial crime less risky. If you steal billions of dollars and cooperate with authorities, you might serve only 2-3 years instead of 5+. From the perspective of deterrence, this seems light. It might not be enough to deter sophisticated criminals from committing serious financial crimes.
There's also a question about whether the First Step Act was intended for someone like Lichtenstein. The law was originally designed to address concerns about mass incarceration, particularly as it affects lower-income and minority communities. It's designed to give people who've served time an opportunity to get education and job training so they can reintegrate successfully into society. Lichtenstein, by contrast, is a highly educated technical professional who presumably already has marketable skills. Did he really need job training and educational programs to succeed after release?
These are legitimate policy questions without easy answers. Different people will evaluate the appropriateness of his early release differently based on their values regarding punishment, rehabilitation, deterrence, and justice.

What Lichtenstein's Release Means for Cryptocurrency Security Going Forward
Now that Lichtenstein is released, there are practical questions about what he'll do next and what his case means for cryptocurrency security.
Lichtenstein claimed in his statement that he wants to "make a positive impact in cybersecurity." This could be genuine. Many reformed criminals have gone on to use their knowledge for legitimate purposes. There's a field called "ethical hacking" or "bug bounty" work, where security professionals are hired to find vulnerabilities in systems and report them to the owners. Lichtenstein's deep knowledge of cryptocurrency security, wallet management, and attack vectors could potentially be valuable in this field.
On the other hand, his statement might be pure public relations. After six years in federal prison, claiming you want to contribute positively to cybersecurity is certainly better optics than saying you want to exploit cryptocurrency systems again. It's impossible to know his true intentions without observing his behavior after release.
From a policy perspective, the case highlights the ongoing need for improvements in cryptocurrency security, regulation, and law enforcement coordination. The gap between offense and defense in cryptocurrency crime is narrowing, but gaps still exist. Future thefts might be prevented through better security practices and regulatory requirements.
The case also underscores the value of blockchain analysis technology and international law enforcement cooperation. The fact that Lichtenstein was eventually caught demonstrates that sophisticated money laundering operations can be traced and prosecuted. This should theoretically deter future criminals, though the scale of cryptocurrency theft hasn't decreased since 2016.
The Future of Cryptocurrency Crime: What the Bitfinex Case Teaches Us
Looking forward, the Bitfinex hack and its aftermath offer several lessons for the future of cryptocurrency crime and security.
First, cryptocurrency theft will likely continue as long as cryptocurrency exists and holds significant value. The economics are too attractive for criminals. Billions of dollars are stored in cryptocurrency form. If there's a 0.1% chance of stealing it and a 10% chance of getting caught, the risk-reward calculation might still favor attempting the theft from a criminal's perspective.
Second, law enforcement capabilities will continue to improve. Blockchain analysis technology is advancing. International cooperation agreements are strengthening. Regulatory frameworks are maturing. This means cryptocurrency theft is becoming increasingly risky for perpetrators. The days of stealing large amounts of cryptocurrency and remaining undetected indefinitely are largely over.
Third, security practices in the cryptocurrency industry must continue to evolve. While exchanges have improved significantly since 2016, new types of attacks emerge. Criminals are creative and persistent. Security must be a continuous process, not a one-time implementation.
Fourth, regulatory clarity and oversight are essential. The more that cryptocurrency exchanges and service providers are regulated, the more their compliance obligations force them to implement security measures and prevent money laundering. Some jurisdictions have embraced cryptocurrency regulation while others resist it. Those that regulate effectively will likely see fewer theft incidents and better victim recovery.
Finally, the case demonstrates that even sophisticated criminals can be caught. Lichtenstein was educated, technically skilled, and operating in a sphere where anonymity is theoretically possible. He still got caught. This suggests that for most criminals, detection is not a matter of if but when. Patience, good investigative work, and advanced forensic techniques eventually prevail.

FAQ
What exactly did Ilya Lichtenstein steal in the Bitfinex hack?
Lichtenstein stole approximately 119,756 bitcoin from Bitfinex in August 2016. At the time of the theft, this bitcoin was worth roughly
How did Lichtenstein move the stolen bitcoin without being detected for six years?
Lichtenstein used a sophisticated multi-layered approach to hide the stolen cryptocurrency. He employed cryptocurrency mixers (services that pool and redistribute coins to obscure their origin), moved coins through darknet marketplaces, used fake identities and multiple wallet addresses, converted stolen bitcoin to other cryptocurrencies like ethereum to further obscure the trail, and broke up large transfers into smaller amounts. This complexity created a web of transactions that delayed detection, though federal investigators eventually traced the coins back to him through blockchain analysis, traditional investigative work, and cooperation from cryptocurrency exchanges.
What is the First Step Act and how did it result in Lichtenstein's early release?
The First Step Act is a 2018 federal law designed to reform the criminal justice system by giving eligible prisoners opportunities to earn Time Credits through good behavior and program participation. These credits can be applied toward sentence reduction. Lichtenstein, after serving approximately 2.7 years of his 5-year sentence, earned enough credits through educational and rehabilitation programs to qualify for early release. A federal judge approved his sentence reduction, resulting in his release in February 2025.
Was Lichtenstein's early release controversial?
Yes, his early release sparked significant debate. Supporters of criminal justice reform argue that the First Step Act is working as intended, giving people who demonstrate rehabilitation a second chance. Critics counter that Lichtenstein's crime was extraordinarily serious—involving billions of dollars in stolen cryptocurrency—and that early release sends the wrong message about white-collar crime. They worry it insufficiently deters future financial crime. The disagreement reflects broader tensions in criminal justice policy between punishment and rehabilitation approaches.
How do cryptocurrency mixers work, and are they legal?
Cryptocurrency mixers are services that combine cryptocurrency from many sources, scramble it, and redistribute it. The theory is that mixing breaks the link between a wallet sending coins and the wallet receiving them. Mixers are legal in most jurisdictions when used for legitimate privacy reasons, but they're also commonly used by criminals to hide the origins of stolen funds. Many mixers don't conduct proper identity verification, making them attractive for money laundering. Some countries and exchanges have increased restrictions on mixer usage in response to criminal activity.
What improvements have been made to cryptocurrency exchange security since the 2016 Bitfinex hack?
Bitfinex and the broader cryptocurrency industry have implemented numerous security improvements since 2016. These include hardware security modules for key storage, cold storage strategies where most assets are kept offline, multi-signature requirements where multiple private keys are needed to authorize transactions, regular security audits, insurance programs, blockchain analysis tools to detect suspicious activity, improved access controls, and compliance officer positions. These measures make large-scale theft significantly more difficult than it was in 2016, though security remains an ongoing challenge.
What happened to the stolen bitcoin from the Bitfinex hack?
Federal investigators and Bitfinex itself worked to identify and recover portions of the stolen bitcoin. Not all coins were recovered—some were spent by Lichtenstein and Morgan, some were moved to third parties, and some remain in wallets. However, law enforcement recovered meaningful amounts through tracing blockchain transactions and seizing wallets they identified. Bitfinex compensated affected users through a combination of recovered assets and the exchange's own resources. The case demonstrates both the possibilities and limitations of recovering stolen cryptocurrency.
Is Ilya Lichtenstein likely to commit crimes again after his release?
No one can definitively predict future behavior, but several factors suggest lower recidivism risk compared to some other criminals. Lichtenstein is well-educated, technically skilled, and presumably employable in legitimate sectors like cybersecurity. His stated intention to work in cybersecurity could provide legitimate income sufficient to make returning to crime economically irrational. However, his previous crime demonstrated sophistication and access to advanced technical knowledge, so genuine concern about potential recidivism remains reasonable. Monitoring and oversight would be prudent.
How do federal investigators trace cryptocurrency transactions to real-world identities?
Federal investigators use multiple techniques in combination. They employ blockchain analysis software that identifies patterns and flags suspicious activity. They subpoena exchanges to identify customers associated with wallet addresses that interact with their platforms. They conduct traditional surveillance and financial investigation. They examine public information about cryptocurrency transactions, wallet movements, and market interactions. They cooperate internationally with law enforcement in other countries. They analyze metadata from darknet transactions. While criminals can add obfuscation layers, sophisticated investigation eventually traces most significant cryptocurrency movements back to real-world actors.
What does the Bitfinex case tell us about the future of cryptocurrency?
The case demonstrates that despite cryptocurrency's theoretical anonymity, law enforcement has developed effective tools for tracing major thefts and prosecuting perpetrators. This is likely to make large-scale cryptocurrency crime increasingly risky and therefore less attractive. However, it also shows that substantial gaps remain—smaller thefts, more sophisticated obfuscation, and operations in less-regulated jurisdictions might still succeed. The case underscores the importance of continued security improvements, regulatory development, and international cooperation in managing cryptocurrency crime.

Conclusion: Justice, Rehabilitation, and the Future of Financial Crime
The story of Ilya Lichtenstein—from sophisticated cryptocurrency thief to released felon—encapsulates several competing narratives about crime, punishment, rehabilitation, and justice in the modern era. On one level, it's a remarkable criminal caper, with sophisticated money laundering techniques, years of evasion, and ultimately, capture through persistent investigation. On another level, it's a case study in criminal justice reform and whether rehabilitative approaches to incarceration are appropriate even for serious financial crime.
What's indisputable is that Lichtenstein committed one of the largest single-incident cryptocurrency thefts in history. He and his wife spent nearly six years moving and hiding stolen bitcoin worth billions of dollars. They used sophisticated techniques that, while ultimately unsuccessful in evading detection, nonetheless demonstrate the complexity of modern financial crime. Yet he also accepted responsibility through a guilty plea, presumably participated in educational and rehabilitation programs while incarcerated, and earned enough behavioral credits to qualify for early release under federal law.
For the cryptocurrency industry, the Bitfinex hack has been a net positive despite the immediate harm. It drove security improvements across the sector. It accelerated the development of blockchain analysis tools. It demonstrated that law enforcement could track and prosecute cryptocurrency crime even when it's technically sophisticated. It led to regulatory frameworks that, while sometimes controversial, provide oversight and consumer protection. The industry has matured significantly since 2016, and the Bitfinex hack was a major catalyst for that maturation.
For the broader criminal justice system, Lichtenstein's early release reflects the ongoing debate about how to balance punishment, rehabilitation, and deterrence. Different stakeholders will evaluate the appropriateness of his release differently. Advocates for criminal justice reform will view it as a success story. Those focused on white-collar crime deterrence will worry about insufficient consequences. What's clear is that the First Step Act creates real opportunities for sentence reduction, and Lichtenstein took advantage of those opportunities.
Moving forward, several principles seem evident. First, that cryptocurrency crime, while sophisticated, is increasingly detectable and prosecutable. This should theoretically deter future theft. Second, that security practices must continually evolve to stay ahead of emerging threats. Third, that regulatory frameworks and industry standards matter—they force adoption of protective measures that would otherwise be optional. Fourth, that international cooperation is essential in an ecosystem where crimes cross jurisdictional boundaries instantly.
Ilya Lichtenstein is now a free man, released to reintegrate into society with an opportunity to prove that he can contribute positively rather than engage in crime. Whether he'll seize that opportunity or squander it remains to be seen. What's certain is that his case has become a landmark in the history of cryptocurrency crime, a pivotal moment when law enforcement caught a sophisticated criminal, recovered stolen assets, prosecuted successfully, and ultimately granted a second chance through rehabilitative justice. For some, that's a triumph of the criminal justice system. For others, it's a cautionary tale about the consequences of financial crime becoming insufficiently serious. The debate will continue, shaped by cases like his and the values that different communities bring to questions of justice, punishment, and rehabilitation.

Key Takeaways
- Ilya Lichtenstein stole 120,000 bitcoin (5.2B today) from Bitfinex in 2016 and spent six years hiding the funds through mixers, darknet markets, and fake identities before his arrest in 2022
- Federal investigators used blockchain analysis, exchange cooperation, and traditional detective work to trace the stolen cryptocurrency across multiple wallets and ultimately prosecute Lichtenstein successfully
- The First Step Act, a 2018 criminal justice reform law, allows federal prisoners to earn sentence reduction credits through education, job training, good behavior, and rehabilitation program participation
- Lichtenstein's early release in 2025 sparked controversy about whether white-collar financial crime carries sufficient consequences and whether rehabilitation deserves priority over deterrence for serious offenders
- The Bitfinex hack drove significant security improvements across the cryptocurrency industry, including cold storage, multi-signature requirements, hardware security modules, and blockchain analysis tools that make large-scale theft substantially more difficult
![Crypto Thief Ilya Lichtenstein Released Early: Inside the Bitfinex Hack [2025]](https://tryrunable.com/blog/crypto-thief-ilya-lichtenstein-released-early-inside-the-bit/image-1-1767638215260.jpg)



