Federal Cybersecurity Crisis: Why Government Digital Defense Is Collapsing
Something's broken in how America defends itself online. Not the code, not the technology, not the strategies. The people. And right now, things are falling apart faster than anyone predicted.
For the better part of a decade, the federal government was playing perpetual catch-up on cybersecurity. Agencies were running systems that belonged in a museum. Patches weren't being applied. Vulnerabilities sat open like doors with broken locks. It was a slow, grinding disaster, the kind that makes security experts wake up at 3 AM in a cold sweat. But somewhere around 2018 to 2023, something shifted. The Cybersecurity and Infrastructure Security Agency (CISA) started establishing actual standards. Minimum protections began rolling out. Progress was messy and frustratingly incremental, but it was happening.
Then 2025 arrived, and the momentum died.
The numbers are brutal. CISA lost roughly 1,000 employees, wiping out more than a third of its entire workforce. Not through normal attrition. Through deliberate, calculated cuts. Other critical agencies absorbed similar hits. The cybersecurity experts, the incident responders, the engineers who actually know how to defend the networks that run the country—many of them are either gone or on their way out. Gene Dodaro, the retiring Comptroller General of the United States, told Congress in December that he was genuinely worried. "I think we'll live to regret it," he said about the staffing reductions. That's not hyperbole from a partisan. That's a career civil servant watching a house fire and being told to stop bringing water.
What makes this crisis different from the normal government dysfunction is the timing and the consequences. This isn't about an agency running inefficiently. This is about the networks that run power grids, water systems, financial infrastructure, and military communications becoming increasingly vulnerable. And it's happening while state-sponsored hackers are getting bolder, more sophisticated, and more aggressive.
Here's what you need to know about what's actually happening, why it matters, and what the real fallout could look like.
TL; DR
- CISA lost 1,000+ employees: More than 33% workforce reduction through deliberate cuts in 2025, severely hampering cybersecurity operations
- Government shutdown exposed gaps: Multi-week shutdown disrupted monitoring, broke contractor relationships, and created blind spots in critical infrastructure defense
- Brain drain accelerating: Specialized cybersecurity talent fleeing government, taking institutional knowledge that takes years to rebuild
- Critical vulnerabilities emerging: Congressional Budget Office hacked during shutdown; multiple agencies facing backlog and reduced defensive capabilities
- No rapid recovery path: Current staffing plans insufficient; rebuilding institutional knowledge and expertise takes 3-5 years minimum
- Bottom line: Federal cybersecurity capabilities are actively degrading while threats intensify, creating unprecedented national security risk

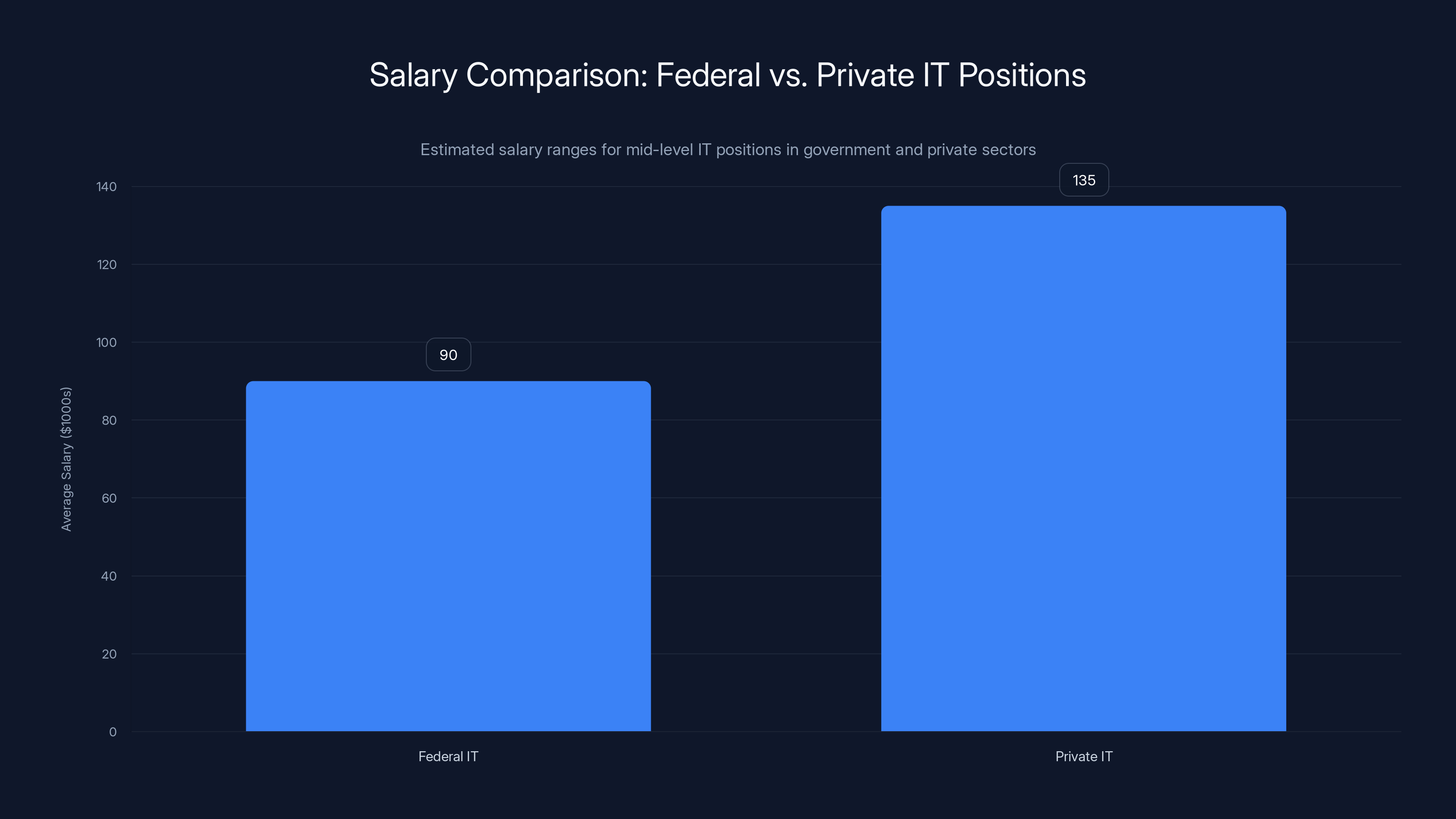
Federal IT professionals earn significantly less than their private sector counterparts, with a 30-50% pay gap driving talent migration. Estimated data.
The Unraveling of CISA's Cybersecurity Mission
CISA wasn't perfect when it was fully staffed, but it was working. The agency, created in 2018 as a branch of the Department of Homeland Security, had spent the early 2020s building something that actually resembled a coherent national cybersecurity effort. After years of watching private companies suffer breaches and federal agencies deal with catastrophic hacks, CISA was finally becoming the thing we needed: a central authority that could identify threats, coordinate responses, and push agencies toward basic security hygiene.
By 2023, CISA was issuing binding directives. Agencies had to meet certain standards. Vulnerabilities had to be patched by specific dates. There were actual teeth to the guidance. It wasn't revolutionary, but it was revolutionary compared to what came before, which was essentially nothing.
Then the cuts began. The stated reason was anger over CISA's election security work. The Trump administration viewed the agency's 2020 and 2024 election security efforts as political opposition and decided to use staffing reductions as retaliation. Whatever your political views on election security, the practical effect was the same: roughly 1,000 people walked out the door.
Acting CISA director Madhu Gottumukkala acknowledged the damage in a November memo to staff. He noted the agency had hit "a pivotal moment" but was "hampered by an approximately 40 percent vacancy rate across key mission areas." Think about that number. Forty percent of critical positions sitting empty. That's not a shortage. That's operational paralysis.
The agency claims it's accelerating innovation and directing resources efficiently. But that's what organizations always say when they're in crisis mode. The truth is simpler and more damaging: fewer people means fewer threat investigations, fewer coordination meetings with critical infrastructure operators, fewer security reviews, fewer incident responses. You can't compress years of cybersecurity expertise into faster workflows just by being more motivated.
Government Shutdowns as Cybersecurity Disasters
Government shutdowns are treated like bureaucratic inconveniences, something Congress needs to sort out so federal employees can get back to work. But if you actually think about what a shutdown does to cybersecurity, it's terrifying.
During the weeks-long shutdown in fall 2024, hundreds of thousands of federal employees were furloughed. Cybersecurity analysts went home. Incident responders stopped responding. The people monitoring networks for intrusions were gone. It's like removing half the firefighters from a city and hoping nothing catches fire for a few weeks.
There were actual consequences. The Congressional Budget Office, which was still operating on a skeleton crew, got hacked. A suspected foreign actor infiltrated the agency. The incident wasn't massive in scope—the CBO contained it relatively quickly—but it illustrated the point perfectly. While the government was essentially shut down, someone was actively probing federal networks.
Beyond the direct security impact, the shutdown created institutional damage that will echo for years. Cybersecurity consultants who were contractors for federal agencies had to find other work when the funding dried up. These aren't generic IT contractors who can find jobs easily. They're specialists who understand specific government systems, threat models unique to federal networks, and institutional relationships that took years to build. Many of them didn't come back. Why would they? The government has proven it can't even keep the lights on reliably.
Amelie Koran, a former chief enterprise security architect for the Department of Interior, noted that the shutdown likely disrupted or ended relationships with specialized contractors, and that the limited continuing resolution Congress passed meant "no new contracts and extensions or options are probably being done, which will cascade to next year and beyond." That's not just a budget problem. That's institutional degradation.
The shutdown also created a massive backlog that won't clear for years. Federal IT workers were already overloaded. Patches that should have been deployed during the shutdown weren't. Vulnerability assessments got postponed. Security training got deferred. Every week of downtime adds months to the recovery timeline.

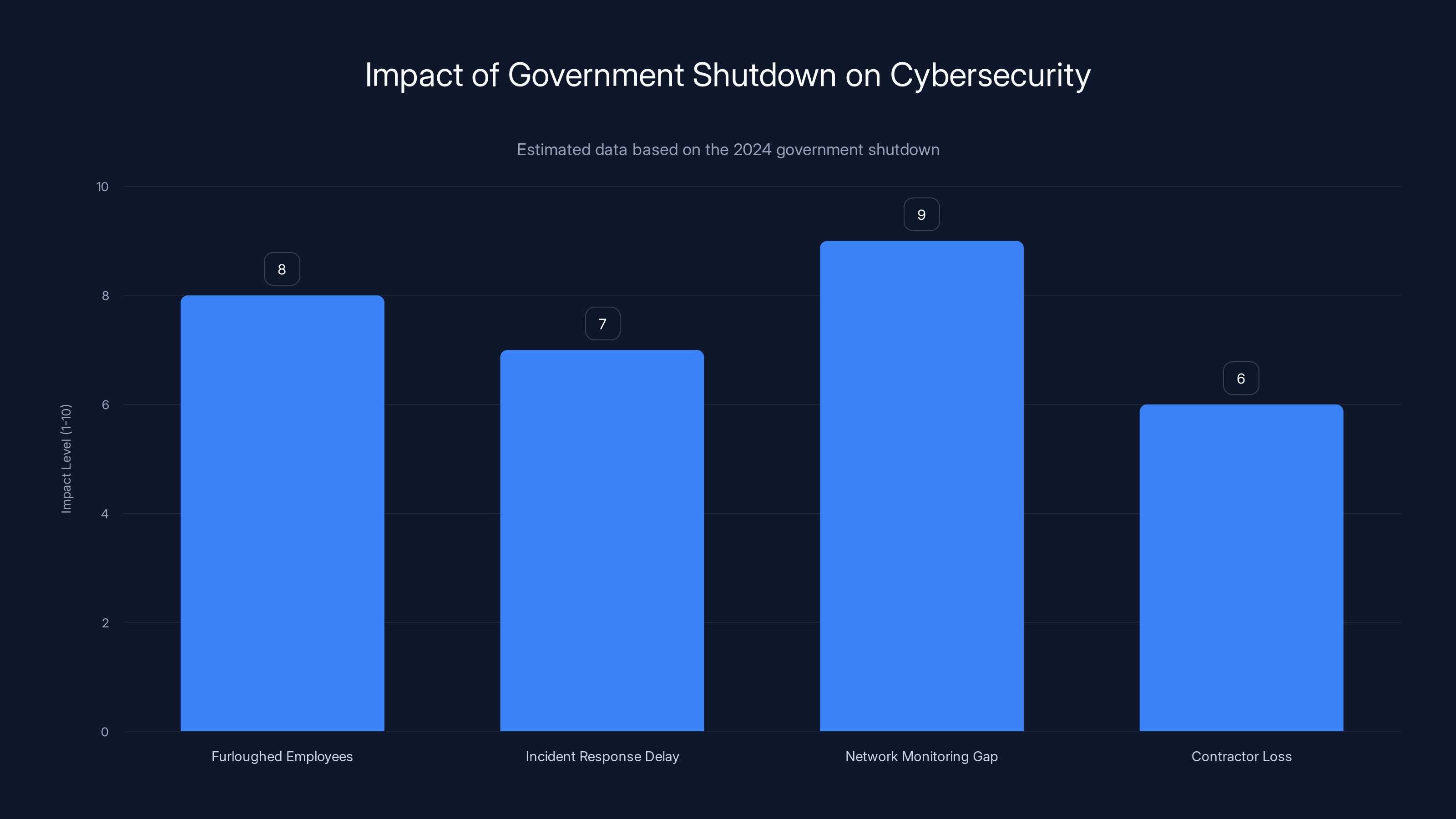
The 2024 government shutdown significantly impacted cybersecurity, with high levels of vulnerability due to furloughed employees and network monitoring gaps. Estimated data.
The Brain Drain Problem: Institutional Knowledge Walking Out the Door
Cybersecurity expertise isn't fungible. You can't just hire someone with a certification and have them understand the intricacies of defending federal networks. A CISA analyst who's spent five years understanding how a specific adversary group operates, what their TTPs (tactics, techniques, and procedures) are, and how to detect their activity is irreplaceable. Not because they're uniquely talented, but because that knowledge exists only in their head and their case files.
When CISA lost 1,000 people, much of that knowledge walked out the door. Jake Williams, a former NSA hacker and current VP of R&D at Hunter Strategy, puts it bluntly: "When, not if, we have a major cybersecurity incident within the federal government, we can't simply staff up with additional cybersecurity resources after the fact and expect the same outcomes we would get from long-tenured staff."
The problem is exponential. A new hire needs training. That training comes from someone with experience. But many of those experienced people are gone. The people who would have been training the next generation of federal cybersecurity analysts are scattered across private industry, making significantly more money and dealing with far less bureaucracy. The federal government can't compete on salary, benefits, or work environment. So it loses.
Government cybersecurity jobs have historically been viewed as stepping stones. You spend a few years gaining experience, then jump to a private sector role that pays 30 to 50 percent more. That's always been true, but the recent cuts have made it worse. Now there's also job instability. Why commit to a government role when staffing reductions could happen tomorrow?
The rebuilding timeline is measured in years, not months. It takes 18 to 24 months to get someone competent in a specialized cybersecurity role. That's assuming they have prior experience. If you're building entry-level staff, add another year. Multiply that by the 1,000 people CISA lost, and you're looking at years of reduced capability even if hiring magically resumed tomorrow at full capacity.
Why This Matters: The Threat Environment Is Escalating
If government cybersecurity staffing was declining while the threat environment was stable, that would be bad but manageable. But the opposite is happening. Threats are intensifying while defenses are weakening. That's the actual nightmare scenario.
State-sponsored actors are getting bolder. China's sophisticated enough that it's conducting multi-year espionage campaigns against federal networks, slowly building access and exfiltrating data. Russia has demonstrated the ability to compromise critical infrastructure, water treatment systems, and energy grids. Iran is conducting aggressive reconnaissance against U.S. defense and government targets. And now you're telling those actors that the people defending against them are being removed from their positions?
Take the SolarWinds hack in 2020. That breach was conducted by Russian intelligence and affected dozens of federal agencies. It took months to understand the scope. It cost billions to remediate. Now imagine that happening while government cybersecurity operations are 40 percent understaffed. The response would be slower. The detection would take longer. The remediation would be incomplete because there simply aren't enough people to handle it.
The OPM breach in 2015, where China stole millions of security clearance files, was catastrophic at the time. But the post-breach investigations and remediation efforts required specialized teams of federal cybersecurity experts working around the clock. Those same experts are now either retired or working in private industry. The institutional knowledge is gone.
The calculus for attackers is getting better. The return on investment for conducting sophisticated operations against federal networks is increasing because detection and response capabilities are declining. That's not speculation. That's basic threat modeling.

Critical Infrastructure: The Real Vulnerability
CISA's mission isn't just about protecting government networks, though that's important. The agency is responsible for critical infrastructure security, which means the networks that run power grids, water treatment plants, hospitals, financial systems, and telecommunications networks.
When CISA is fully staffed, it conducts threat assessments on critical infrastructure, works with operators to identify vulnerabilities, and coordinates incident response when attacks occur. With 40 percent of key positions vacant, that work slows down dramatically.
Consider what happened in Ukraine when Russia conducted cyberattacks against Ukrainian power grids. Coordinated sophistication. Multiple attack vectors. The grid went dark. Power plants were damaged. The lesson? Critical infrastructure is vulnerable to determined state actors with sufficient resources and patience. And the people responsible for defending similar infrastructure in the U.S. are being sent home.
The threat isn't hypothetical. It's active. Iranian hackers have been probing U.S. water treatment facilities. Russian actors have been mapping access points to energy infrastructure. Chinese intelligence has been conducting reconnaissance on defense contractor networks. These aren't sophisticated attacks yet. They're reconnaissance. But the reconnaissance phase is where vulnerabilities are identified, and the capabilities phase is coming.
When it comes, CISA will be under-resourced to respond. That's not a guess. That's inevitable arithmetic.
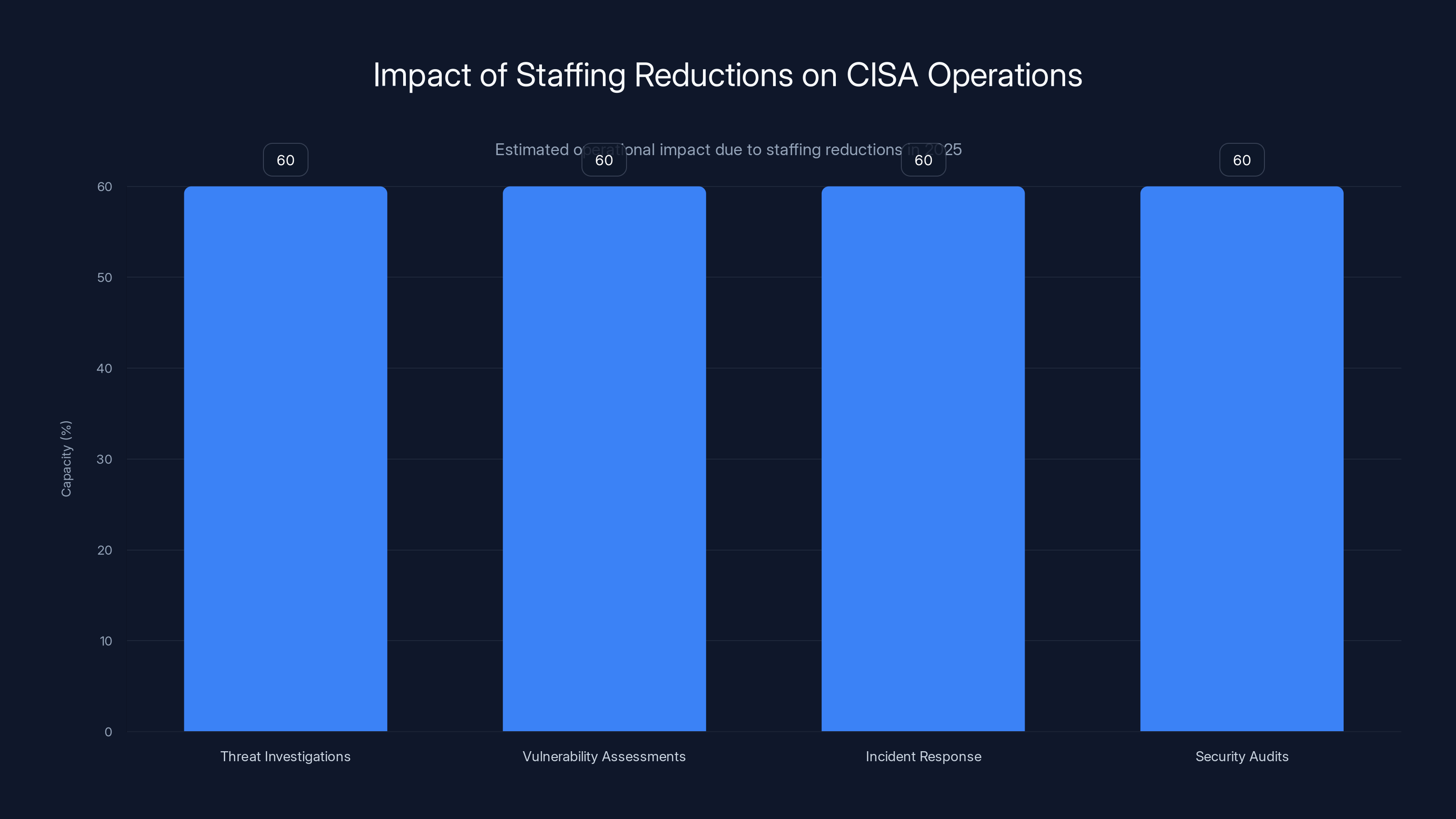
CISA's operational capacity dropped to 60% in key areas due to a 40% workforce reduction in 2025. Estimated data.
The SolarWinds Precedent: How Bad Can It Really Get?
To understand why the current situation is so concerning, you need to understand what SolarWinds actually was and what it would look like if something similar happened today.
In late 2020, security researchers discovered that Russian foreign intelligence had compromised SolarWinds, a software company whose products are used throughout the federal government and critical infrastructure. The attackers inserted malicious code into a legitimate software update. Federal agencies and private companies installed the update. The backdoor was installed. Russian intelligence now had access.
The scope was staggering. Treasury Department. Homeland Security. Commerce Department. Energy Department. Dozens of agencies. Many remained compromised for months before detection and remediation. The investigation took years. The cost ran into billions. The damage to national security is still being assessed.
Here's the critical part: responding to SolarWinds required hundreds of specialized cybersecurity personnel. Forensic analysts. Threat hunters. Incident responders. Infrastructure specialists. People who understood specific federal systems and could identify what was actually taken or compromised. It was the kind of all-hands-on-deck response that required institutions like CISA to be fully staffed and fully engaged.
Imagine SolarWinds 2.0 happening right now. Same sophistication. Same scope. But CISA is 40 percent understaffed. The response would be slower. The investigation would be incomplete. The remediation would take longer. And all of that translates to more damage to national security.
This isn't theoretical. Former officials and current experts are specifically worried about this scenario. A major breach happening during a period of reduced capacity. And you can't just staff up after the fact. By then, the damage is done.
The Staffing Cuts: Motivation and Consequences
Understanding why CISA was cut is important for understanding how bad the situation is. The cuts weren't driven by budget constraints. CISA's budget wasn't slashed. The cuts were driven by political ideology. The Trump administration viewed CISA's election security work as political opposition and responded by reducing the agency's workforce.
You can have whatever political views you want about election security. That's a legitimate policy debate. But the consequence of using staffing reductions as a political cudgel against a national security agency is that your national security gets worse. That's not a political statement. That's cause and effect.
Acting director Gottumukkala acknowledged in his memo that the staffing cuts are forcing the agency into survival mode. The agency is now focused on immediate operational priorities, which means the longer-term projects that actually improve federal cybersecurity posture are getting deferred. Threat research programs are being cut. Vulnerability assessment initiatives are being paused. Training and development for new staff is being postponed.
The White House claimed the agency is "accelerating innovation" and "directing resources where they yield the greatest return." That's the standard response from any organization in crisis mode. But anyone who works in cybersecurity understands what's really happening: the agency is triaging. They're focusing on the emergencies happening right now because they don't have the capacity to do anything else.
The stated plan is to rebuild in 2026. But rebuilding doesn't mean getting back to where CISA was in early 2025. It means hiring new people, training them, integrating them into teams, and slowly rebuilding institutional knowledge. That's a five-year project, minimum. Even if hiring accelerates significantly, CISA will be operating at reduced capacity for years.
The Government IT Workforce Crisis: Structural Problems
CISA's staffing problems are part of a larger structural problem in federal IT. The people who work in government cybersecurity and IT are chronically underpaid, overworked, and underappreciated. A federal IT salary for a mid-level position might be
One former national security official who spoke to journalists about the shutdown's impact said something that captures the systemic problem: "Federal IT workers, they are good jobs, there's not enough resources for the issues that they have to deal with. It's always underfunded. They always have to catch up."
That's been true for decades. But it's accelerating. The most talented people leave. The mid-career people who might have stayed are reconsidering. The entry-level people who would have been trained are looking for other jobs. The institutional knowledge is being systematically drained from federal cybersecurity organizations.
The sad part is that government IT could be genuinely interesting work. You're defending networks that actually matter. You're protecting critical infrastructure. You're working on problems that affect national security. But nobody stays for the mission if they're making 40 percent less than they could in private industry.

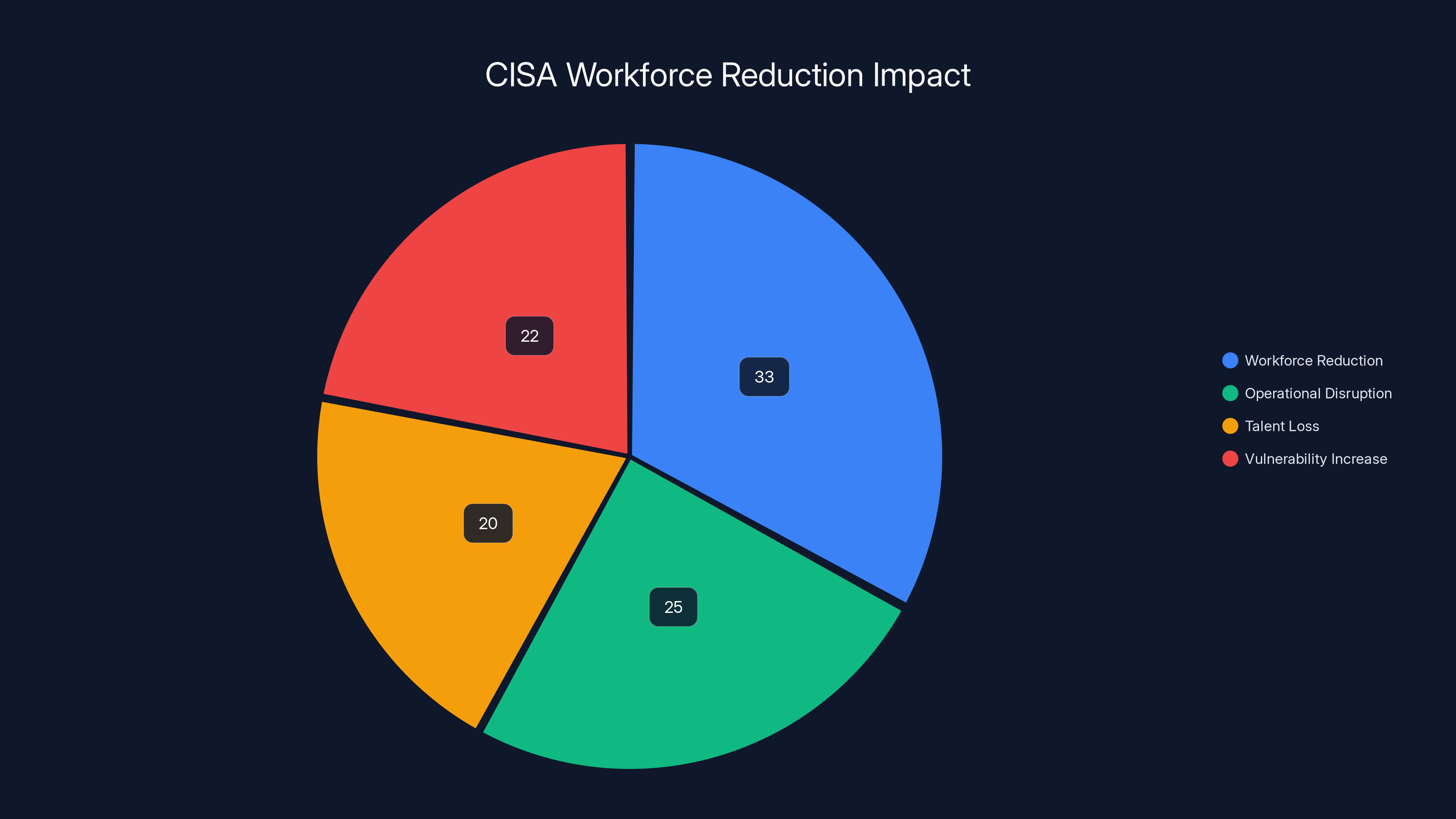
Estimated data shows a significant 33% workforce reduction at CISA, with operational disruption and talent loss also contributing to increased vulnerabilities.
The Ripple Effects: Contractors and Specialized Expertise
Federal cybersecurity operations depend heavily on contractors. These aren't the massive consulting firms doing strategy work. These are specialized boutique firms and individuals who understand specific government systems and provide deep expertise that federal employees can't always develop internally.
During the government shutdown, contracts were frozen. Contractors went without payment. Many of them found other work. The government eventually paid the back pay, but the damage was done. Contractors who were deep in the middle of incident investigations or vulnerability assessments had to step away. The work stopped. They came back to new assignments or, often, to no assignment at all.
Amelie Koran's point about the continuing resolution is crucial. The CR (continuing resolution) that reopened the government after the shutdown was limited in scope. No new contracts. No extensions of existing contracts. No options being exercised on contract vehicles. That means specialized contractors can't be brought on for new projects. The capability that was already limited just became more limited.
This cascades. A contractor who was planning to train a federal team on new threat intelligence analysis techniques can't because there's no contract vehicle to bring them in. A specialized firm that was supposed to conduct security assessments of federal networks has to wait until funding clears. The timeline for every improvement initiative slips by months.
Contractors also represent institutional knowledge outside government. They work across multiple agencies, see patterns that single-agency employees might miss, and bring expertise that takes government employees years to develop. When the contractor relationships break down because of repeated shutdowns and frozen contracts, that knowledge leaves the system.
Vulnerability Management: The Backlog Crisis
One of CISA's core functions is identifying vulnerabilities in federal systems and pushing agencies to patch them. It sounds simple, but it's actually complex. There are millions of software packages, firmware updates, and system configurations. New vulnerabilities are discovered daily. Some are critical. Most are moderate. The job is prioritizing which vulnerabilities matter most and making sure agencies actually patch them by specific deadlines.
With staffing at 60 percent capacity, that function is operating in crisis mode. Patch management falls behind. The backlog of unpatched systems grows. Each unpatched system is a potential entry point for an attacker. Multiply that across the entire federal government, across thousands of agencies and offices, and you're creating a landscape that's increasingly vulnerable to exploitation.
This isn't academic. When an attacker wants to breach a federal agency, they start by identifying unpatched systems. That's always their first move. An agency with a massive backlog of unpatched vulnerabilities is an easy target. And right now, due to staffing constraints and the shutdown's disruptions, the federal government's backlog is substantial and growing.

The 2024 Breach Timeline: A Warning
The incidents that have already occurred in 2024 and early 2025 are warning signs. The Congressional Budget Office breach during the shutdown wasn't the most damaging breach in history, but it happened during a period when the government's defenses were deliberately reduced. That's the trend line. That's where this is headed.
Each incident that occurs while staffing is reduced takes longer to detect, takes longer to investigate, and causes more damage because the incident response capability is constrained. The first major breach that occurs at full scale while CISA is 40 percent understaffed will be significantly worse than if it had occurred when CISA was fully staffed.
The intelligence community and the cybersecurity experts who actually track these threats are worried. They're not worried about something that might happen in five years. They're worried about something that could happen next month. That's a different kind of concern.
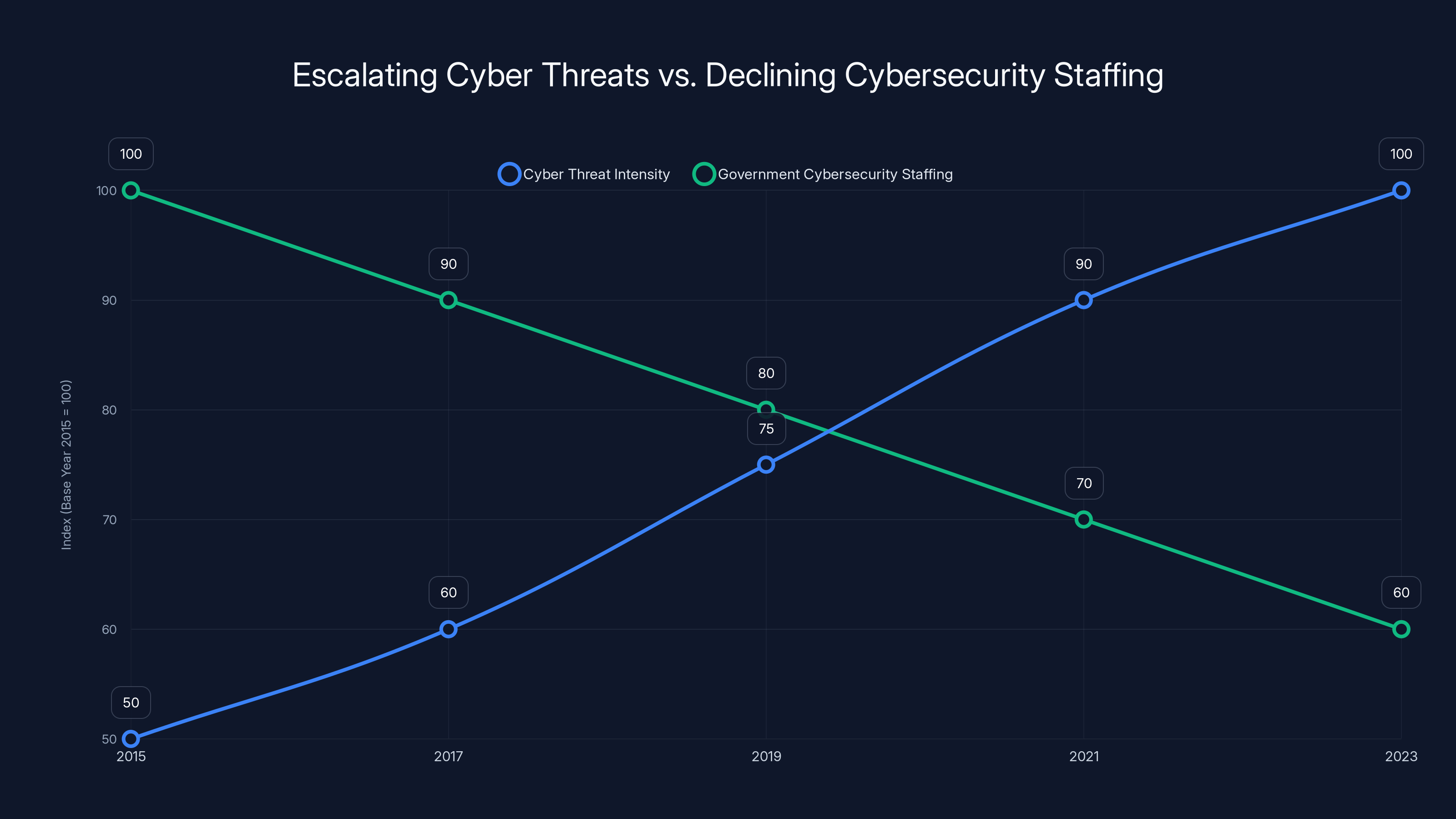
The chart illustrates the growing intensity of cyber threats against the backdrop of declining government cybersecurity staffing from 2015 to 2023. Estimated data shows a critical gap forming, highlighting the increasing risk of cyber incidents.
The Rebuilding Timeline: Why Recovery Will Take Years
Okay, so the staffing gets restored tomorrow. Hiring accelerates. Budget flows. New analysts join CISA. How long until the agency is back to full capability?
Years. Realistically, three to five years minimum.
Here's the math: A mid-level cybersecurity analyst takes 18 to 24 months to become truly productive in a federal role. That's assuming they already have background in cybersecurity. If you're hiring entry-level, add another year. So each new hire represents a 2 to 3-year investment before they're contributing at the level that veteran employee was.
Multiply that by 1,000 people. Even if CISA could hire 1,000 people in a year (which is unrealistic because the hiring process in government takes months), you're looking at a decade for the organization to return to pre-cut performance levels. More realistically, if CISA hires 300 people per year over the next few years, you're looking at 2029 or 2030 before the organization has the staffing levels it had in 2024.
Meanwhile, the threat environment isn't pausing. Attackers aren't waiting for CISA to rebuild. They're probing, accessing, and establishing footholds in federal networks right now. The longer CISA operates understaffed, the more time adversaries have to establish persistent access that will take years to discover and eradicate.
This is the real threat. Not a single catastrophic breach. But the slow, steady degradation of defensive capability while threats continue to escalate.

What Federal Agencies Are Actually Doing Right Now
Across federal agencies, the response to staffing cuts and reduced budgets is predictable. They're prioritizing immediate crises over long-term improvements. Patch management is being focused on the most critical systems only. Threat hunting is being reduced to defensive response only. Security assessments are being postponed. Training is being deferred.
Some agencies are doing better than others. The Department of Defense, with its own cybersecurity budget and specialized expertise, is managing better than smaller agencies. But even DoD is feeling the pressure. The National Security Agency has its own cybersecurity operations, so they have some redundancy. But agencies like Interior, Commerce, and others are basically running on fumes.
What's not happening is innovation, improvement, or forward progress. Federal cybersecurity has shifted from slowly getting better to actively getting worse. That's a qualitative change in trajectory that matters a lot.
The Expert Consensus: This Is Serious
Gene Dodaro, the retiring Comptroller General, is worried enough to tell Congress directly. Jake Williams, a former NSA hacker, is explicitly worried about backsliding. Amélie Koran, a former Department of Interior security architect, is warning about cascading contract impacts. These aren't people who exaggerate threats. These are people who have spent careers in national security and cybersecurity.
Their consensus is clear: federal cybersecurity capability is degrading. It's not a temporary dip. It's structural. And the longer it goes on, the more damage it causes.
You don't have to take their word for it. You can look at the numbers. 1,000 people cut. 40 percent vacancy rates in critical areas. Multi-week shutdown disrupting operations. Contractor relationships broken. Vulnerability backlogs growing. That's the factual situation. The question is what consequences that produces.

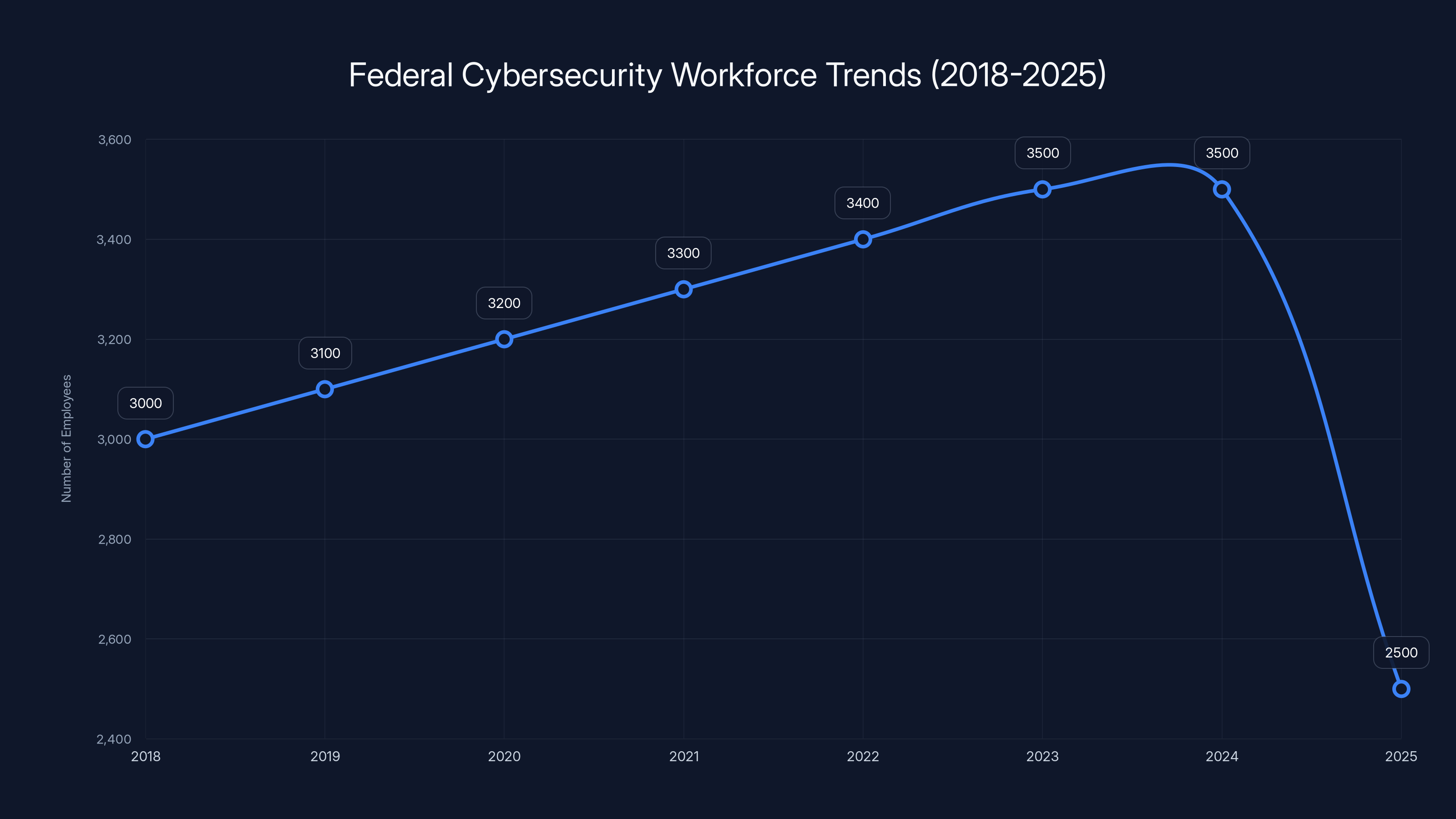
CISA's workforce grew steadily from 2018 to 2023 but faced a sharp decline in 2025 due to significant staffing cuts. Estimated data reflects the impact on cybersecurity capabilities.
The National Security Implications
Here's the thing that's hard to talk about because it involves classified information and specific capabilities: the federal government has specific cybersecurity priorities that go beyond routine operations. There are networks that are monitored for specific threats related to active military operations, intelligence collection, and national security. Staffing cuts at CISA affect the broader ecosystem that supports those operations.
When CISA has to cut corners on threat hunting and vulnerability assessment, it means the baseline is getting weaker. That baseline weakness makes it harder to distinguish normal activity from actual attacks. It makes it easier for sophisticated attackers to hide. It reduces the ability to detect intrusions before they cause damage.
The military, intelligence agencies, and defense contractors are increasingly concerned about Chinese and Russian intelligence capabilities targeting U.S. networks. The timing of staffing cuts at the exact moment when those threats are accelerating is poor, to put it mildly.
There are operational security implications that can't be discussed in detail. But the principle is simple: when your defensive capability is reduced while threats are increasing, your vulnerability to those threats increases. That's just math.
What Needs to Happen: The Recovery Path
If we're being serious about federal cybersecurity, here's what actually needs to happen:
Immediate staffing restoration: CISA needs to be authorized to rehire quickly. This isn't a budget question. The budget is available. This is an authorization and prioritization question.
Contractor stability: The government needs to ensure that specialized contractors can continue their work without constant interruptions from shutdowns and frozen contracts. This probably means multi-year contract vehicles that survive CRs.
Federal IT compensation: The federal government needs to address the structural salary disparity that drives talent away from government roles. You can't compete with private industry on work environment or mission, so you have to compete on compensation.
Long-term planning: Cybersecurity strategy needs to extend beyond annual budget cycles. Multi-year initiatives need to be protected from political disruption.
Critical infrastructure focus: CISA's critical infrastructure security work needs to be resourced at higher levels. The stakes are too high to skimp here.
None of this is technically complicated. It's all about political will and budgeting priorities. But it requires recognizing that federal cybersecurity isn't an administrative function that can be cut without consequences. It's a critical national security capability.

The Private Sector Opportunity and Risk
As federal government cybersecurity capability declines, two things happen. First, the most talented people move to private industry, where they make more money and deal with fewer politics. Second, private companies filling the gap end up with outsized importance in national security.
Some of this is appropriate. Private companies do have sophisticated cybersecurity capabilities. But there's a risk when critical infrastructure defense gets outsourced too far. The private sector isn't going to do this work for free. They're going to do it for profit. And when budgets are constrained, corners get cut.
There's also an opportunity for private companies to actually solve this problem. Companies like those offering AI-powered security automation, threat intelligence platforms, and incident response tools can potentially help federal agencies do more with fewer people. But that only works if agencies have the budget to invest in tools and the expertise to implement them effectively. And right now, they don't have either.
The irony is that better tooling could help federal cybersecurity operate more effectively with constrained staffing. But implementing new tools requires the expertise you're losing due to staffing cuts. It's a catch-22.
The Broader Lesson: Why National Security Can't Be Treated as a Budget Item
The underlying problem is that cybersecurity is treated as a budget line item that can be adjusted based on political priorities or fiscal concerns. But national security isn't divisible that way. You can't be 60 percent defended against sophisticated cyberattacks. You can't have 40 percent fewer incident responders and hope for the best.
When you make staffing cuts in cybersecurity, you're not saving money. You're spending it in a different way. You're spending it on dealing with breaches that you could have prevented with better security. You're spending it on remediating damage that you could have mitigated with faster incident response. You're spending it on rebuilding systems that were compromised because of unpatched vulnerabilities.
Every dollar spent on cybersecurity prevention is worth roughly five dollars in incident response and remediation. That's been consistent across decades of incident data. So cutting cybersecurity spending isn't cost reduction. It's false economy that makes the bill bigger down the road.
The current situation at CISA is the clearest possible example of that false economy. The cuts were made for political reasons. The costs will be paid in terms of national security capability, infrastructure vulnerability, and financial damage from incidents that could have been prevented.

Looking Ahead: 2025 and Beyond
The next few years are going to be difficult for federal cybersecurity. CISA will gradually rebuild, but it will operate below full capacity for years. The threat environment will continue to intensify. Attackers will take advantage of the opportunity window that's opened.
Specific predictions: Expect more incidents affecting federal agencies and critical infrastructure. Some of them will be relatively minor. Some will be significant. At least one will be major enough to force a national conversation about cybersecurity resources. That incident will happen before CISA has fully rebuilt its capacity.
The longer-term question is whether the political system will learn the lesson. Will federal cybersecurity be properly funded and resourced going forward? Or will this happen again in a few years when budget pressures return or political priorities shift?
Based on history, the answer is probably the latter. Federal cybersecurity will get attention after a major incident, will be properly resourced for a few years, and then will face cuts again when other priorities emerge. That's the cycle we've seen repeatedly.
What would actually solve this problem is treating federal cybersecurity as a non-negotiable national security priority, the way we treat defense spending or intelligence budgets. Not something that gets cut based on political disagreements with a specific agency.
FAQ
What is CISA and why does it matter?
The Cybersecurity and Infrastructure Security Agency is a division of the Department of Homeland Security responsible for improving cybersecurity across the federal government and protecting critical infrastructure like power grids, water systems, and financial networks. CISA establishes minimum security standards, coordinates incident response when breaches occur, and works with private companies to identify and remediate vulnerabilities. When CISA functions effectively, the entire nation's cybersecurity posture improves because federal agencies set the baseline that trickles down to contractors, vendors, and critical infrastructure operators.
How did CISA lose 1,000 employees and what does that mean operationally?
CISA lost approximately 1,000 employees (more than one-third of its workforce) through deliberate staffing reductions ordered by the Trump administration in 2025, primarily in response to the agency's election security work. Operationally, this means CISA has roughly 40 percent vacancy rates in critical mission areas, significantly reducing the agency's ability to conduct threat investigations, vulnerability assessments, incident response coordination, and security audits. With fewer analysts, threat hunting capacity drops, patch management backlogs grow, and the time to detect and respond to breaches increases substantially.
What is the impact of government shutdowns on cybersecurity?
During government shutdowns, federal cybersecurity personnel are furloughed, meaning network monitoring stops, incident response teams aren't working, and threat analysis pauses. This creates blind spots where attackers can operate undetected. Additionally, contractors providing specialized expertise have to find other work, relationships are disrupted, and when the government reopens, the backlog of deferred security work takes months to clear. The 2024 shutdown even resulted in a confirmed breach of the Congressional Budget Office, demonstrating that attackers actively exploit the reduced defenses during shutdown periods.
Why is the brain drain from federal cybersecurity such a big problem?
Cybersecurity expertise is highly specialized and institutional. An analyst with five years of experience understanding specific threat actors, their tactics, and how to detect them can't be easily replaced. When experienced staff leave government, they take years of institutional knowledge with them. The rebuilding timeline is measured in years, not months. Even if hiring accelerates immediately, it will take 3-5 years minimum for federal cybersecurity agencies to return to pre-cut capacity. Meanwhile, threats continue to escalate and adversaries take advantage of the degraded defenses.
What was the SolarWinds breach and why is it relevant to current concerns?
SolarWinds was a 2020 breach where Russian foreign intelligence compromised a software company and used legitimate software updates to distribute malware across dozens of federal agencies including the Treasury, Homeland Security, and Energy departments. The breach took months to detect and years to fully remediate, requiring hundreds of specialized cybersecurity personnel working around the clock. Experts are concerned that a similar breach occurring today, while federal cybersecurity agencies are understaffed by 40 percent, would result in slower detection, incomplete investigation, and more extensive damage to national security.
How long will it take federal cybersecurity to recover from current staffing cuts?
Realistically, 3-5 years minimum, even with aggressive hiring and budget restoration. A new cybersecurity analyst typically requires 18-24 months to become fully productive in a federal role, and that's assuming they already have prior cybersecurity experience. Multiply that timeline across the 1,000 people CISA lost, and you're looking at years of reduced capacity even in the best-case scenario. Meanwhile, the threat environment isn't pausing, allowing attackers to establish persistent access during the window of degraded defenses.
What is the relationship between staffing cuts and critical infrastructure vulnerability?
CISA is responsible for protecting critical infrastructure including power grids, water treatment plants, and hospitals. With 40 percent of critical positions vacant, the agency can't conduct as many security assessments, threat evaluations, or vulnerability reviews with infrastructure operators. This means critical infrastructure operators are operating with less federal support and guidance precisely when sophisticated nation-state actors are escalating reconnaissance and attack planning against those same targets. The timing creates a dangerous window of reduced defensive capability.
What should the federal government do to address cybersecurity staffing crisis?
Immediate priorities include authorizing rapid rehiring at CISA, stabilizing contractor relationships through multi-year contract vehicles that survive government shutdowns, addressing the salary disparity that causes talent to migrate to private industry, and protecting multi-year cybersecurity initiatives from political disruption. The federal government also needs to implement better tooling and automation to help staff operate more effectively with constrained resources. These are all solvable problems, but they require treating federal cybersecurity as a non-negotiable national security priority rather than a budget line item subject to routine cuts.

The Hard Truth About Federal Cybersecurity
The situation is serious and it's going to get worse before it gets better. A fully staffed federal cybersecurity apparatus is already playing catch-up against sophisticated nation-state threats. A 60 percent-staffed federal cybersecurity apparatus is falling behind. And that's exactly where we are right now.
The incidents that will come over the next few years—and they will come—will provide the political ammunition to properly fund federal cybersecurity again. But that's an expensive, painful way to learn a lesson we should have learned years ago. The time to invest in cybersecurity is before you need it, not after you've been breached and millions of Americans have had their data stolen.
The good news is that none of this is irreversible if you're willing to invest the resources and the political capital. The bad news is that the window for preventing the worst outcomes is closing. Every month of understaffing is another month where vulnerabilities aren't being patched, where threats aren't being hunted, where relationships with critical infrastructure operators are degrading.
If you work in government cybersecurity, you're probably stressed and considering leaving. That's rational. The private sector is hiring aggressively and paying better. But if you do leave, document your knowledge. Write down the processes, the threat models, the key relationships. Make that knowledge portable so it doesn't disappear from the system.
If you work in critical infrastructure, now is the time to ensure your own cybersecurity practices are as strong as possible. Don't assume government agencies will detect intrusions targeting you. Assume you're on your own. Build your monitoring, your threat hunting, and your incident response capabilities independently.
If you work in private sector cybersecurity, understand that the degradation of federal cybersecurity affects your operational environment. The threats are going to be more sophisticated and more successful because federal defenses are weaker. Plan accordingly.
And if you work in politics or policy, understand that every budget cut to federal cybersecurity comes due later, multiplied. The math is harsh, but the principle is simple: you can pay for cybersecurity now, or you can pay for breach response and remediation later. The later option is always more expensive.
The current trajectory isn't sustainable. It's going to change, either through conscious policy decision or through a crisis response to a major incident. The question isn't whether federal cybersecurity will be properly resourced. The question is whether that happens before or after something really bad occurs.
Right now, it looks like it's going to be the latter. And that's the biggest threat of all.
Key Takeaways
- CISA lost 1,000+ employees (33% of workforce) through political staffing cuts, creating 40% vacancy rates in critical mission areas
- Multi-week government shutdown disrupted cybersecurity monitoring, broke contractor relationships, and confirmed breaches occur during reduced defenses
- Brain drain to private sector compounds staffing shortages: rebuilding specialized expertise takes 3-5+ years minimum
- Federal cybersecurity capability is declining while nation-state threats escalate, creating dangerous window of vulnerability
- Current staffing levels are insufficient to prevent, detect, and respond to major incidents like a potential SolarWinds 2.0 breach
![Federal Cybersecurity Crisis: Why Government Digital Defense Is Collapsing [2025]](https://tryrunable.com/blog/federal-cybersecurity-crisis-why-government-digital-defense-/image-1-1767180993427.jpg)



