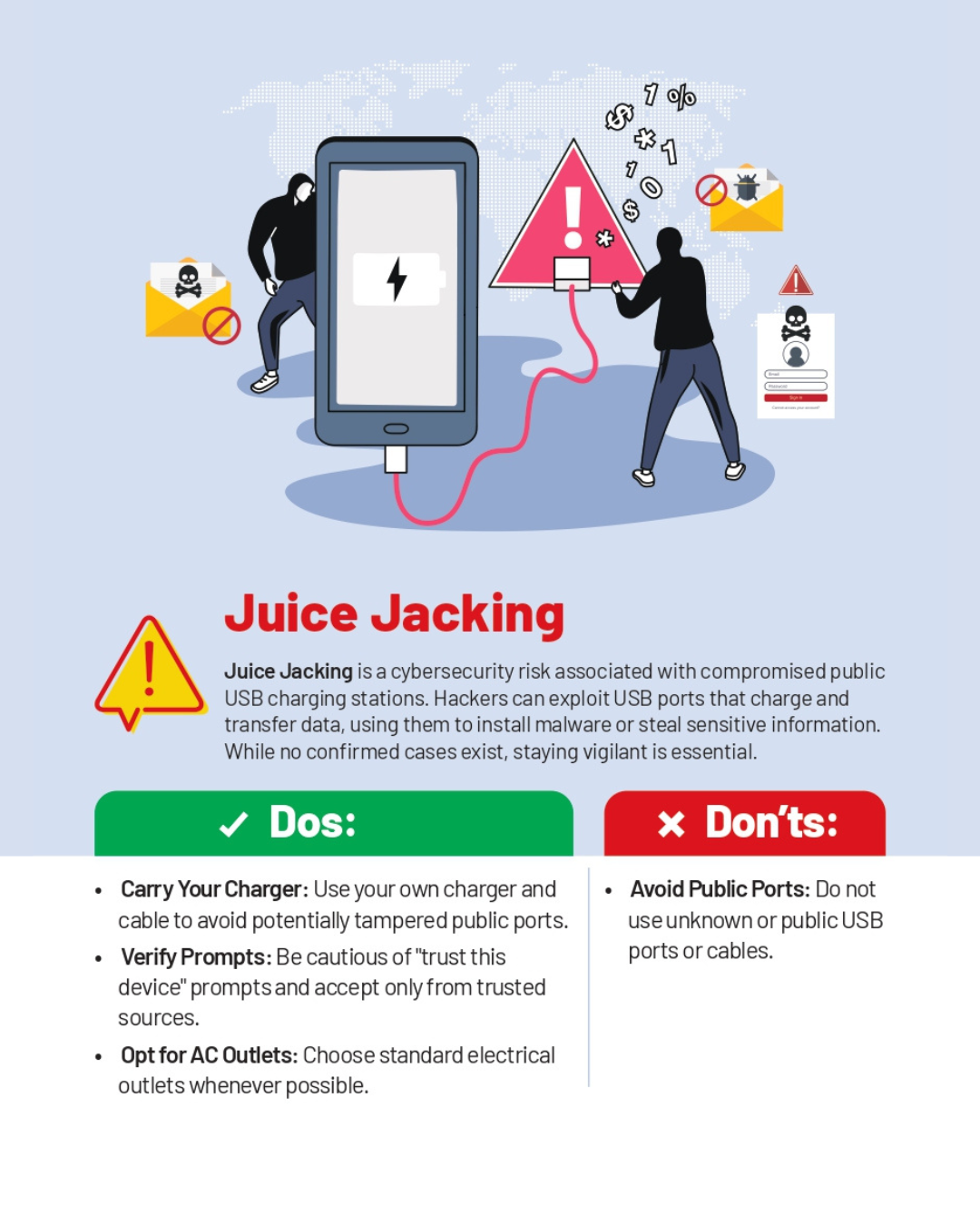
Introduction: The Hidden Danger Lurking in Airport Charging Stations
You're at the airport. Your phone's battery is dying. You spot a USB charging station and think, "Perfect." You plug in your phone and relax. But what if that innocent-looking cable just became a gateway to your personal data?
This isn't paranoia. It's a real security concern called "juice jacking," and it's become increasingly sophisticated as our devices store more sensitive information. The concept is simple but terrifying: a compromised charging cable or station can simultaneously charge your device while stealing passwords, photos, banking credentials, and more. According to Travel + Leisure, juice jacking is a growing concern as public charging stations become more prevalent.
Here's what makes this threat so insidious: you can't see it happening. Your phone charges normally. You have no visual indicator that malicious software is crawling through your files. By the time you notice something's wrong—unusual account activity, unauthorized transactions—the damage is already done.
The term "juice jacking" emerged around 2011, but experts agree the threat landscape has evolved dramatically. Modern attacks are more targeted, more subtle, and increasingly difficult to detect. In 2025, as we rely on public charging infrastructure more than ever, understanding this threat isn't optional anymore—it's essential.
What makes this topic urgent right now? Several factors converge: the proliferation of public USB charging ports in hotels, airports, transit stations, and shopping centers; the increasing sophistication of malware designed specifically for data exfiltration; and the fact that many users remain completely unaware this threat exists. You might think your iPhone or Android device is secure by default. Spoiler alert: it's not invulnerable to a determined attacker with physical access to your charging port.
In this deep dive, we'll explore exactly how juice jacking works, examine the real-world risks versus hype, and provide you with actionable strategies to protect your device. We'll look at what security researchers have discovered, what major tech companies are doing about it, and most importantly, what you should do right now to keep your data safe.
TL; DR
- Juice jacking is real: Compromised charging cables and stations can steal data while charging your phone through USB data transfer protocols.
- The attack surface is expanding: Public charging infrastructure in airports, hotels, and transit systems represents a growing vulnerability that most users ignore.
- Prevention is practical: USB data blockers, portable chargers, and awareness of risky charging locations can eliminate most juice jacking risks.
- Your device isn't automatically safe: Both iOS and Android devices can be compromised, though the technical requirements differ between platforms.
- Bottom line: Treat public charging ports like you treat public Wi-Fi—as potentially unsafe until proven otherwise.

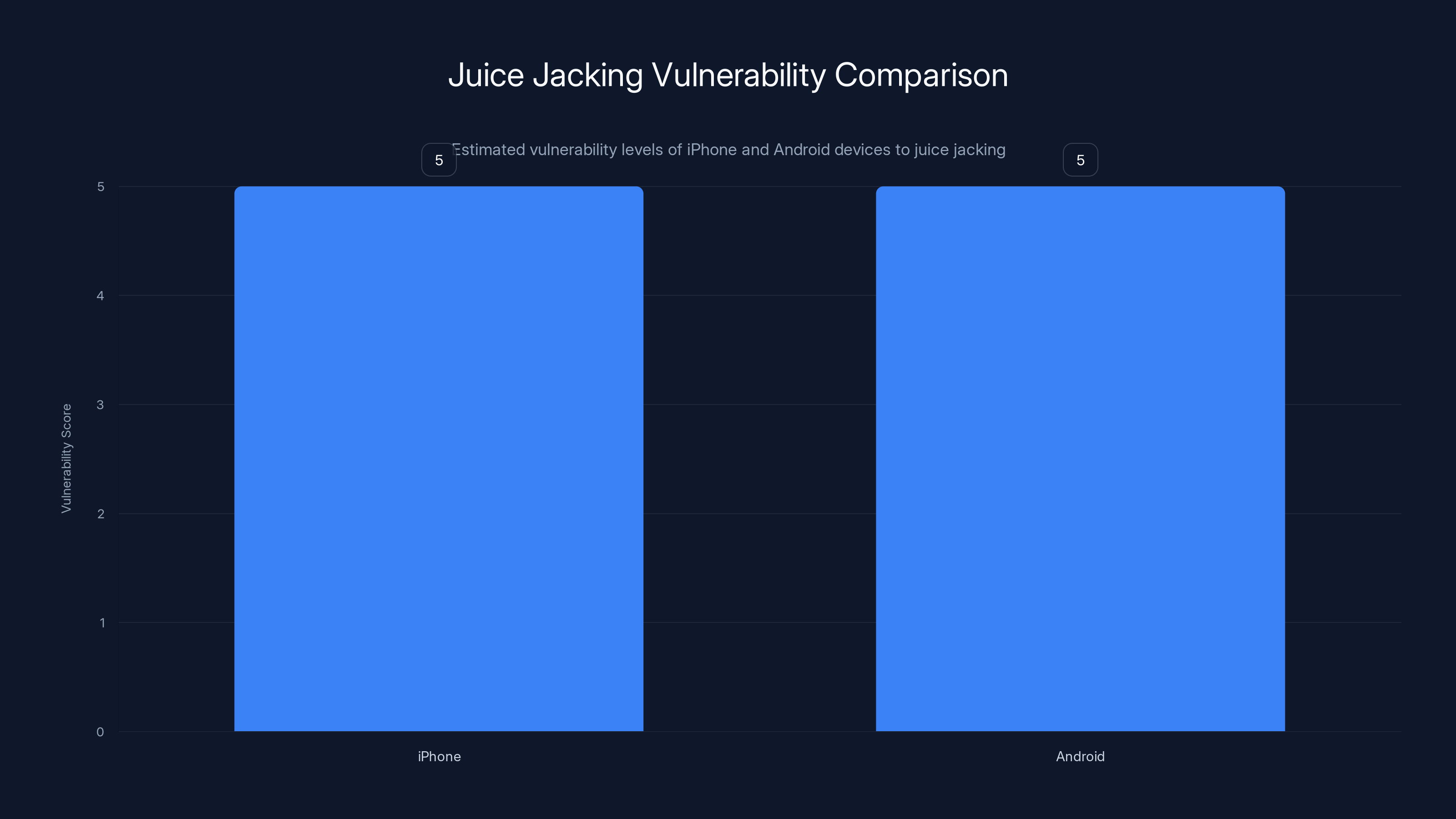
Both iPhone and Android devices have similar vulnerability levels to juice jacking due to different security features and attack vectors. Estimated data.
What Is Juice Jacking? Understanding the Attack Vector
Juice jacking is the practice of installing malware on public USB charging stations or distributing compromised charging cables that intercept data transmission between your device and the charger. The name combines "juice" (slang for battery charge) with "jacking" (hijacking your data). It's catchy, memorable, and unfortunately, very real. Travel + Leisure explains that this threat is particularly concerning due to its subtlety and effectiveness.
Here's how it works on a technical level: USB connections operate on two separate channels simultaneously. One channel handles power delivery—the actual charging function. The other channel handles data communication. When you plug your iPhone into your computer, both channels activate. The data channel allows your computer to access your photos, contacts, and other information. The same thing happens with public charging stations.
A modified USB cable or compromised charging port intercepts this data channel while the power channel operates normally. Your phone has no way of distinguishing a legitimate charger from a malicious one based on the physical connection alone. It simply recognizes a charging port and attempts to establish communication. If that communication is coming from a compromised device controlled by an attacker, your data is vulnerable.
The sophistication varies dramatically. A basic attack might use a simple USB-to-Ethernet adapter to intercept basic network traffic. More sophisticated attacks employ actual malware that installs on your device, providing persistent access long after you've left the charging station. The most advanced versions use SSL stripping to decrypt encrypted connections, allowing attackers to capture passwords even from secure websites.
What's particularly troubling is that you get a legitimate charging experience. Your battery percentage increases. Your phone doesn't crash or malfunction. The attack happens silently in the background while you scroll through your email or watch videos.
The attack vector has multiple entry points. The most common are USB-A or USB-C ports in public spaces where anyone can modify or replace them. But it extends beyond just cables. Some attacks involve modifying the charging station itself, replacing internal components with malicious hardware that captures data from every device charged on that station. Others involve distributing free charging cables that look legitimate but contain hidden hardware designed to intercept data.
One critical detail: juice jacking requires either physical access to modify the hardware or the ability to replace legitimate cables entirely. An attacker can't remotely convert a standard charging cable into a malicious one. They need to physically install the malicious hardware. This is both good news and bad news. Good news: it's not a wireless vulnerability that can affect you across a room. Bad news: attackers have plenty of opportunity to install compromised equipment in high-traffic areas where nobody notices or cares about cable conditions.

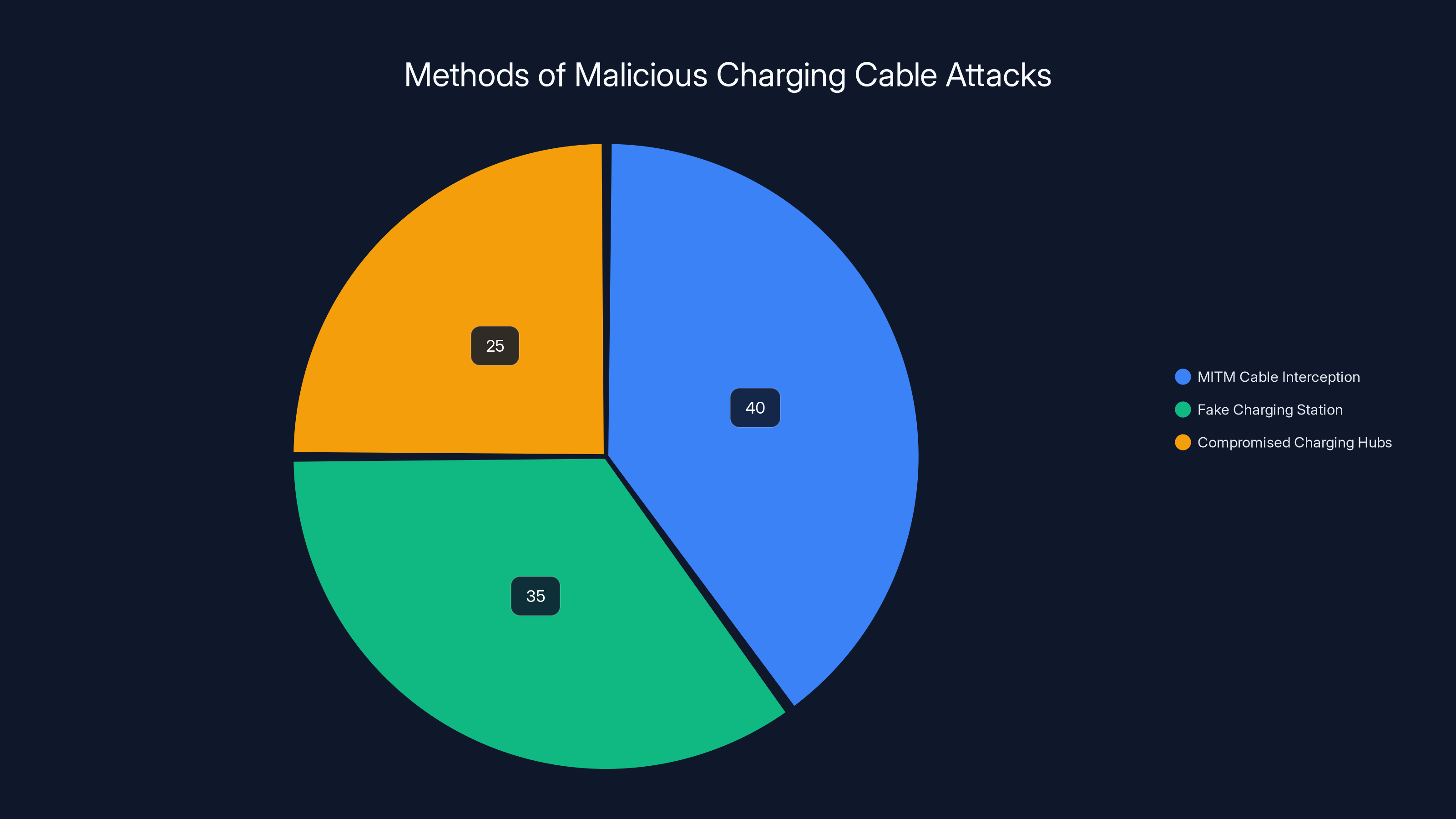
Estimated data shows that MITM cable interception is the most common method, followed by fake charging stations and compromised hubs.
How Malicious Charging Cables Actually Work
Understanding the mechanics of a juice jacking cable reveals just how practical this attack really is. It's not some theoretical vulnerability discussed only in academic papers—it's a threat that requires relatively simple tools and can be implemented by people without deep programming expertise.
A basic malicious USB cable operates using one of several approaches. The simplest method involves a Man-in-the-Middle (MITM) attack architecture. Inside the cable, between the USB connector and the internal wiring, attackers install a small circuit board or microcontroller. This device sits between your phone and the charging port. It passes through power delivery unchanged, ensuring your phone charges normally. But on the data lines, it intercepts every communication packet.
This interception can accomplish several things. The most basic version simply sniffs the data passing through—capturing unencrypted passwords, authentication tokens, and file transfers. A more sophisticated version uses an actual miniature computer embedded in the cable. These "smart" cables can run their own software, establish their own network connections, and even modify data before passing it on.
The second major approach involves hardware that doesn't technically go inside the cable itself. Attackers create a fake charging station that looks identical to a legitimate one. The station contains a computer running software specifically designed to exploit the USB protocol. When you plug in your device, the station software probes your phone looking for vulnerabilities. Modern devices have some protections against this—they don't automatically enter data transfer mode when connected to an unknown device. But these protections have workarounds, and security researchers have demonstrated exploits for both iOS and Android that bypass these safeguards.
A third method involves compromised charging hubs. These look like normal multi-port charging stations where multiple people can charge simultaneously. But hidden inside is a small computer connected to a cellular or Wi-Fi module that exfiltrates captured data. An attacker sets up such a station in a hotel lobby or airport lounge, and over the course of days, it captures data from hundreds of phones.
What makes these cables particularly dangerous is their invisibility. A malicious USB cable looks virtually identical to a legitimate one. The only way to detect it physically is to open it up and examine the internals—something nobody does. You can't scan it for malware. You can't run an antivirus check on the cable itself. Once it's plugged in, you're trusting it implicitly.
The cost barrier is also remarkably low. A microcontroller capable of conducting juice jacking attacks costs less than $20. The cables themselves cost a few dollars each. An attacker could manufacture dozens of malicious cables for the price of a single phone. This makes the economics of the attack very attractive for criminals—they invest minimal money and time but potentially compromise dozens or hundreds of devices.
What's particularly clever is that these cables work with standard operating systems. Attackers don't need proprietary software or extensive technical knowledge about iOS or Android internals. The USB protocol itself is the vulnerability. It was designed in an era when the primary concern was simply standardizing the physical and electrical specifications for device connectivity. Security came later—and it never fully caught up to the protocol's fundamental design.
iOS vs. Android: Which Devices Are Most Vulnerable?
The vulnerability landscape differs significantly between Apple's iOS and Google's Android. Both operating systems have implemented protections against unauthorized data access, but both have also faced compromises to those protections.
Apple's approach centers on the "Trust" dialog. When you connect an iPhone to a computer or unknown USB device, iOS displays a prompt asking whether you want to "Trust" this device. This trust prompt is supposed to prevent unauthorized data access—you can't access iPhone files without the user explicitly granting permission. In theory, this is an excellent defense. In practice, it has limitations.
First, research has shown that iPhones in certain states—particularly when locked or during the initial setup process—may allow data transfer before the trust dialog appears. Security researchers have demonstrated exploits that extract data from iPhones without the user ever seeing a trust prompt. The FORCEDENTRY vulnerability, discovered in 2021, allowed attackers to install spyware on iPhones through a malicious USB accessory without requiring user interaction.
Second, the trust prompt relies on user awareness and proper response. If you're tired, distracted, or simply don't understand what the prompt is asking, you might grant trust to a malicious device. This is particularly true for international travelers or users unfamiliar with the iOS interface.
Third, the trust prompt only protects data access. It doesn't prevent the installation of actual malware or the exploitation of low-level vulnerabilities in the charging hardware itself. A sophisticated attack might bypass the trust prompt entirely by exploiting memory corruption vulnerabilities or other iOS security gaps.
Android's approach is more heterogeneous because different manufacturers implement security differently. By default, Android's USB Debugging mode must be explicitly enabled before a computer can access device data. Like iOS, Android displays a dialog asking you to allow USB debugging from an unknown computer. However, Android also has vulnerabilities that allow attackers to enable USB Debugging remotely or bypass it entirely.
The Stagefright vulnerability (discovered in 2015) and subsequent vulnerabilities have shown that malicious USB devices can exploit media processing flaws to execute arbitrary code on Android devices. These exploits happen at the operating system level, bypassing the user trust prompts entirely. An attacker doesn't need your permission to install malware if they can exploit a kernel vulnerability.
Additionally, Android's fragmentation creates inconsistent security. A vulnerability patched in Android 13 on a Pixel phone might remain unpatched on a Samsung Galaxy running the same Android version, because Samsung uses its own custom firmware layer. This means some Android devices are significantly more vulnerable than others, depending on the manufacturer and update frequency.
There's a paradox here: iOS's more locked-down architecture theoretically provides better protection against unauthorized modifications. You can't sideload apps, you can't modify system files, and you can't disable security features. But that doesn't make iPhones completely invulnerable to juice jacking. Attackers simply need to exploit vulnerabilities at deeper levels of the operating system, using privilege escalation exploits that only Apple's engineers typically discover.
Android, being more open, provides more attack surface area. But it also allows faster deployment of security fixes by third-party vendors, and tech-savvy users have more tools to protect themselves.
The practical reality: both iPhone and Android devices are vulnerable to juice jacking. The specific attack vectors differ, but the end result is the same. Neither operating system can guarantee that plugging into an unknown USB device is completely safe.
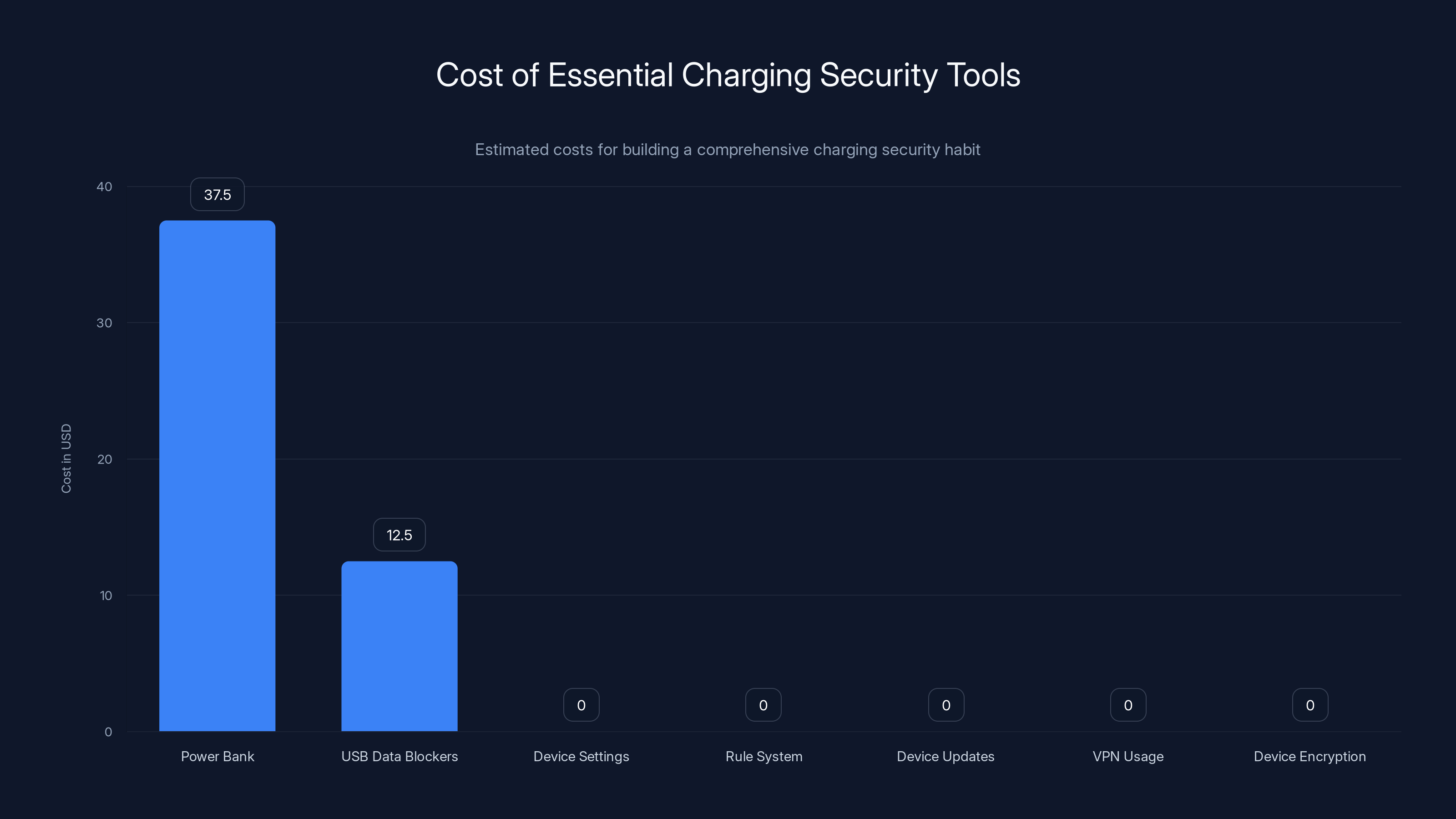
The primary costs in building a charging security habit are for a power bank and USB data blockers. Other measures are free but require regular maintenance and discipline. Estimated data.
The Real vs. Hyped Threat: What Security Experts Actually Say
Part of understanding juice jacking requires distinguishing between the theoretical threat and the actual, documented risk in the real world. This distinction matters because it determines how urgently you need to change your behavior.
Security researchers have definitively proven that juice jacking attacks are technically possible. Numerous proof-of-concept demonstrations at security conferences like Black Hat and DEF CON have shown working exploits against both iOS and Android devices. These aren't theoretical exercises—they're functional attacks that could work in the real world. This settles the "is it possible" question: yes, absolutely.
But is it actually happening at scale? That's where the evidence becomes murkier. Law enforcement and cybersecurity firms have not reported widespread juice jacking incidents. The FBI and Secret Service have not issued major alerts about juice jacking-related data breaches. No major corporations have reported that their data was compromised through juice jacking attacks at public charging stations.
This doesn't mean it's not happening at all. Targeted juice jacking against high-value individuals—executives, politicians, journalists—could occur and remain undetected. Criminals might be running small-scale operations in certain geographic areas without attracting attention. Some breaches attributed to other causes might actually have involved juice jacking, but investigators wouldn't recognize it without specific evidence.
However, the absence of widespread documented incidents suggests one of two things: either the attack is far less common than security theater would imply, or it's happening but remaining mostly undetected. Neither scenario is comforting.
Major security firms including Kaspersky, McAfee, and Sophos have all released statements about juice jacking risks. These statements validate the technical feasibility but typically stop short of claiming it's a primary threat vector. Instead, they classify it as a "low probability but high impact" risk—something unlikely to happen to any individual user, but devastating if it does happen.
What experts universally agree on: juice jacking is significantly less likely than other data theft vectors. Your data is far more likely to be compromised through phishing emails, weak passwords, or insecure Wi-Fi networks than through a malicious charging cable. The effort required to conduct juice jacking attacks is substantial compared to the payoff. Attackers can target far more people far more easily through other methods.
Yet this low-probability, high-impact nature is precisely why security professionals recommend basic protections. The cost of defending against juice jacking is minimal—often just a USB data blocker that costs a few dollars. The benefit of preventing even one successful attack that exposes sensitive data is enormous.
Several factors influence the apparent gap between theoretical risk and actual incidents. First, many juice jacking attacks might target individuals who never realize they've been compromised. Your data might be stolen, analyzed, and found uninteresting. No alerts. No detection. Second, victims often blame other causes—maybe your identity theft came from a data breach you never heard about, not from that charging station three weeks ago. Third, criminals using juice jacking for targeted espionage would keep it secret, avoiding the kind of public incidents that make news headlines.
The security community's consensus seems to be: treat juice jacking like car theft prevention. You don't assume you'll be targeted specifically, but you lock your car anyway because the cost is minimal and the consequences of being wrong are severe.

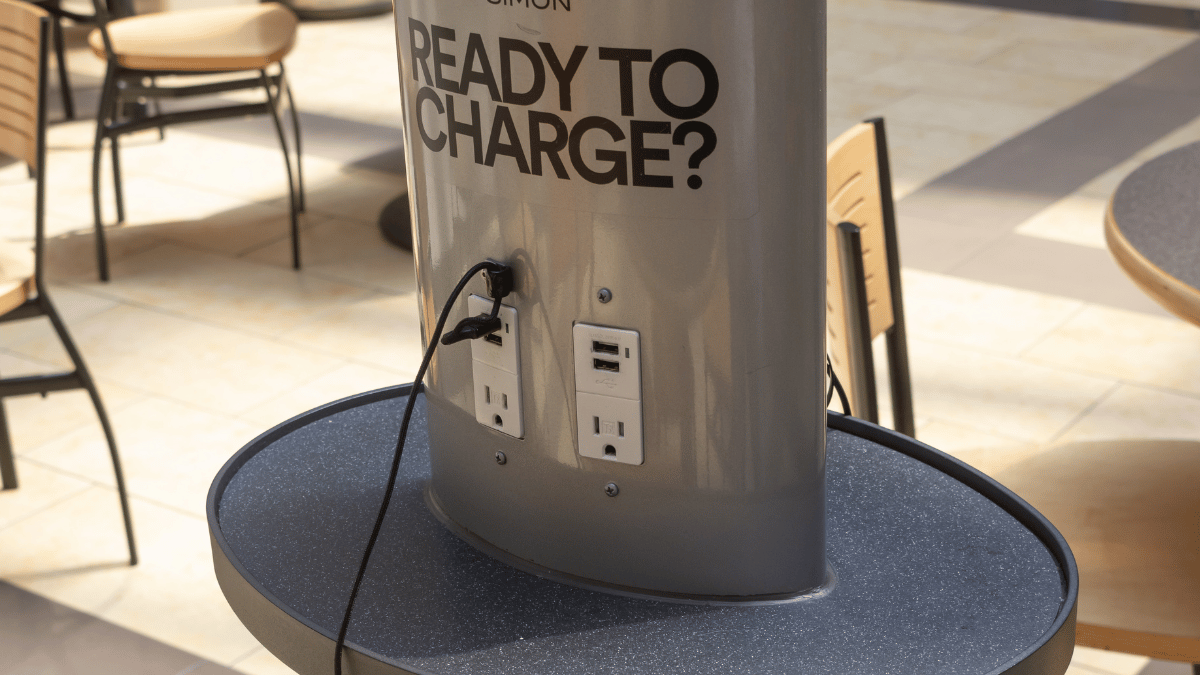
Public Charging Infrastructure: Where the Risk Is Highest
Not all public charging locations present equal risk. Understanding which environments are higher-risk helps you make intelligent decisions about when to use public charging and when to avoid it.
Airports represent the highest-risk environment. Airports have several characteristics that make them attractive targets for juice jacking attacks. First, they have dense concentrations of people from diverse geographic areas, many of whom are stressed and distracted. Second, airports have numerous public charging stations, many installed and maintained by third parties rather than airport security. Third, travelers often have valuable devices containing passwords, banking information, and access to important accounts. An attacker who compromises one traveler's phone might gain access to corporate networks, financial accounts, or other high-value targets.
Hotels present a similar risk profile. Business travelers charge phones in hotel rooms using potentially compromised cables, or they use public charging stations in hotel lobbies where attackers could have installed malicious equipment. The difference from airports is that hotel charging infrastructure might remain unchanged for longer periods, allowing attackers to establish semi-permanent installations.
Public transportation systems—trains, buses, subways—are increasingly adding USB charging ports to seats and stations. These are often difficult to monitor and easy to compromise. The advantage for attackers is high foot traffic with people staying in place long enough for data transfer. The disadvantage is that the port is public, and visible tampering might be noticed. Still, many people use these chargers without hesitation.
Cafes and restaurants with built-in charging ports present lower risk than airports, simply because foot traffic is lower and attackers would compromise fewer devices. However, some upscale hotels have partnered with charging stations that replace traditional outlets at restaurant tables. These could potentially be compromised.
Workplaces typically present lower risk because IT departments maintain charging infrastructure and people are less likely to plug into unknown devices. However, shared office charging stations could theoretically be compromised by insiders with malicious intent.
Retail stores and shopping centers increasingly offer USB charging as an amenity. These are relatively low-risk because retail environments have security cameras and rapid turnover of staff means a long-term compromise would be harder to maintain. However, they're not impossible to target.
Private charging devices—your own cables and chargers at home—present no juice jacking risk unless someone physically broke into your home and modified your equipment. If you purchased cables from legitimate retailers, they're safe.
The key insight: high-risk locations share characteristics of being transit points where people charge for short periods and then leave, making detection of compromise unlikely, combined with weak security infrastructure and high concentrations of desirable targets.

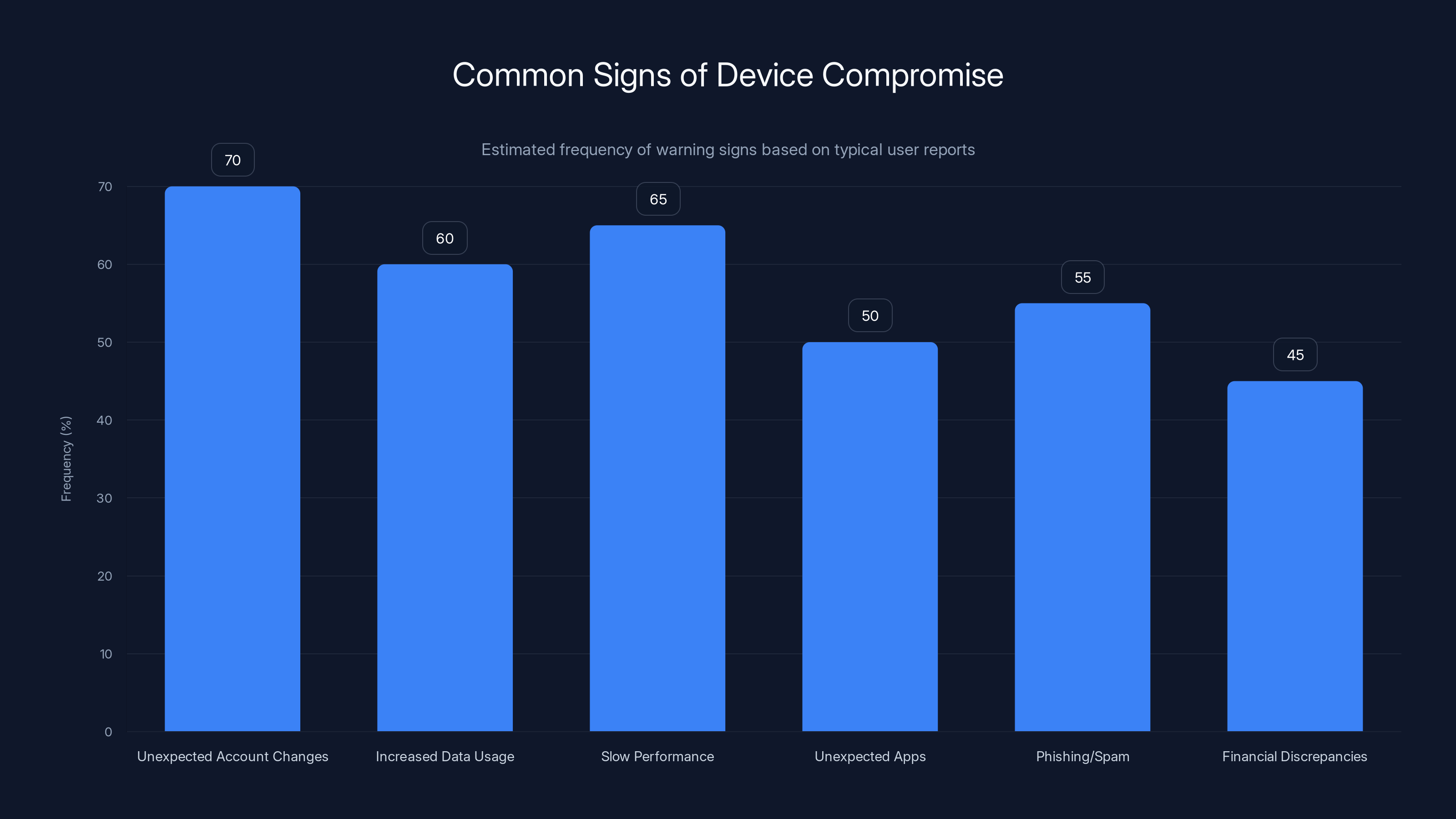
Unexpected account changes and slow device performance are the most common signs of device compromise. Estimated data based on typical user reports.
USB Data Blockers: Your First Line of Defense
A USB data blocker is a simple physical device that allows power transmission while blocking data transmission. It's a small adapter that sits between your device and the charging cable, interrupting the data lines while allowing the power lines to function normally.
These devices work through simple electrical design. A standard USB cable has four wires: two for power (positive and ground) and two for data (D+ and D-). A USB data blocker allows current to flow through the power wires while physically disconnecting or interrupting the data wires. Your device still receives power. No data transfer is possible, even if the charging station is actively trying to exploit your device.
The practical effect: you've eliminated the entire juice jacking attack vector. An attacker with a malicious charging cable can no longer access your data because the data lines are disconnected. Your device cannot be compromised through malware installation because there's no communication channel through which the malware could be delivered.
USB data blockers are absurdly cheap. Quality ones cost between
The downside to data blockers: they completely prevent legitimate data transfer. If you want to charge your phone and sync files simultaneously, a data blocker makes that impossible. This is rarely an issue for public charging situations—you're just topping up your battery, not syncing your entire phone library. But if you have a legitimate need to charge and transfer data from a public USB port, you'd need to remove the data blocker, defeating its protection temporarily.
Some people worry that data blockers might prevent their phone from being recognized as a legitimate device by the charging port. Modern USB specifications actually make this a non-issue. The charging port doesn't need to identify your phone—it simply needs to deliver power according to the USB Power Delivery protocol. Data blockers are completely transparent to the power delivery side of the equation.
How to choose a quality USB data blocker: look for models that are clearly labeled with their supported connector types and power specifications. Avoid the absolute cheapest options on large marketplace platforms—these might be poorly manufactured and could actually damage your charging port. Reviews are helpful, but the signal-to-noise ratio is low because reviewers are often just confirming that the device fits their cable.
A practical approach: buy several USB data blockers. Keep one on your main charging cable, one in your travel bag, and one in your backpack or purse. Because they're inexpensive, losing one is not a tragedy. Because they're effective, they provide genuine peace of mind when charging in public.
Portable Chargers: The Safest Charging Option
If USB data blockers are your first line of defense, portable chargers are your strategic withdrawal to a safer position entirely. Instead of using any public USB infrastructure, you bring your own power source.
Portable chargers (power banks) are increasingly inexpensive and practical. A modest 10,000 mAh portable charger costs around
The security advantage is absolute. When you charge your phone from a power bank, your device only communicates with the power bank—not with airport infrastructure, hotel systems, or any potentially compromised external charging port. The power bank itself isn't connected to the internet. It's not running any suspicious software. It's simply a battery in a case with USB ports.
What about charging the power bank itself? If you charge your power bank from your own personal outlet at home or at a trusted workplace, you've completely isolated yourself from public charging infrastructure. The only way someone could compromise your phone would be if they installed malicious hardware on your personal chargers at home—a much harder target for attackers.
The practical workflow becomes: charge your power bank at home before traveling. When you're away, charge your phone exclusively from the power bank. When you return home, charge the power bank from your safe personal outlets. This approach essentially eliminates the juice jacking risk entirely.
Why don't more people use this approach? Part of it is awareness—many travelers don't realize how affordable power banks have become. Part of it is convenience—you need to remember to charge the power bank itself. And part of it is pure habit—people are accustomed to using any charging port they find.
Power banks have limitations worth acknowledging. They take up space in your luggage. They add weight to your travel bag. If you forget to charge the power bank before traveling, it does you no good. And if you've completely drained your power bank and your phone battery is also dead, you're stuck without power unless you can find a traditional outlet.
But for intentional travelers, for people who charge their phones frequently, for anyone who carries sensitive information on their device, a quality power bank is a worthwhile investment. It solves multiple problems beyond just juice jacking—you get more flexible charging that doesn't depend on finding a public port, and you reduce your exposure to all public charging risks, not just juice jacking specifically.
When selecting a power bank, look for models with trusted brands, good safety certifications (like CE or FCC certification), and reviews from verified purchasers. Cheap power banks can overheat or even catch fire in rare cases. A slightly more expensive, reputable brand is worth the difference.
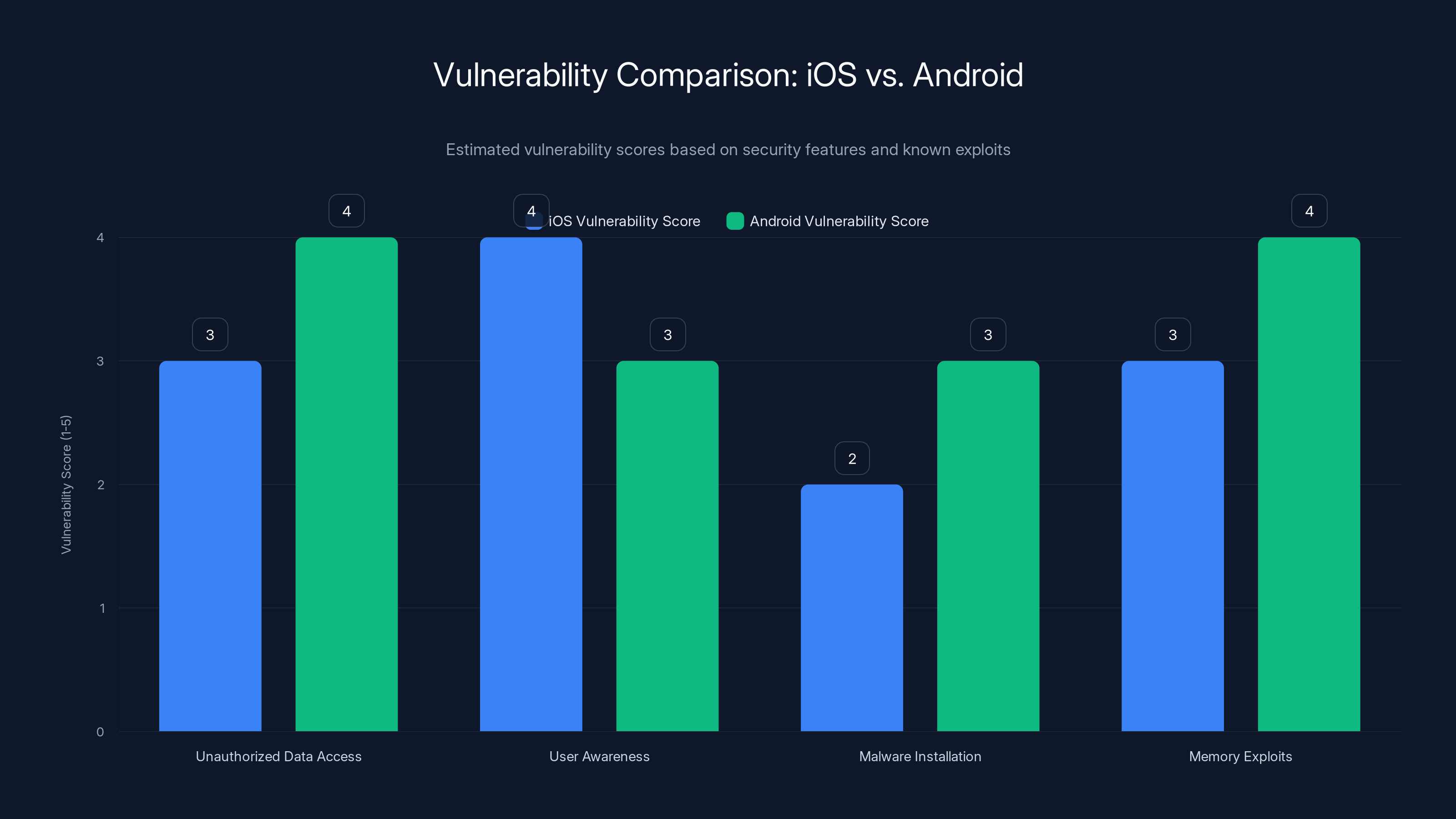
iOS and Android both face vulnerabilities, but their exposure varies by aspect. iOS scores lower in malware installation due to stricter app controls, while Android's diverse implementations lead to higher scores in unauthorized data access. (Estimated data)
Device Settings and OS-Level Protections
Beyond physical solutions, your device's operating system provides several settings that reduce juice jacking vulnerability. They're not perfect, but they're free and worth enabling.
On iOS:
The Trust settings dialog is your primary defense. When you connect to an unfamiliar USB device, iOS prompts you to establish trust. Simply refusing to tap "Trust" prevents the device from accessing your data. However, this protection is weaker than most users realize. In certain circumstances—particularly when the phone is locked or during setup—this dialog might not appear, or attackers might exploit deeper vulnerabilities to bypass it.
A secondary protection: Disable automatic Wi-Fi password sharing. When you connect to an unknown device, iOS sometimes shares Wi-Fi credentials automatically to speed up setup. Disabling this in Settings > Privacy prevents your device from volunteering sensitive information.
Enable USB Restricted Mode if you're running iOS 15.1 or later. This setting, activated in Settings > Face ID & Passcode, requires your face or fingerprint to unlock USB access even when your iPhone is already unlocked. This prevents attackers from quickly extracting data if they gain physical access to your unlocked phone.
On Android:
Disable USB Debugging by default. Verify that USB Debugging (Settings > Developer Options > USB Debugging) is actually disabled. On some devices, it might be enabled by default or by third-party software.
Enable the "Require authorization" toggle in Developer Options. This makes your phone require explicit authorization before allowing any USB connection. Even if someone connects your phone to a computer, they can't access data without your permission.
Use a screen lock. A passcode, fingerprint, or facial recognition makes extracting data significantly harder. Without unlocking your phone, an attacker's options are limited.
On both platforms:
Keep your operating system updated. iOS and Android security updates frequently patch vulnerabilities that could be exploited through malicious USB devices. An older device with unpatched vulnerabilities is far more susceptible to juice jacking attacks than a current device with the latest security updates.
Disable automatic Wi-Fi connection to open networks. Some Wi-Fi networks in public spaces are actually created by attackers to capture your data. Preventing your phone from automatically connecting reduces this risk.
Use a VPN when you must access sensitive data in public. While a VPN doesn't specifically protect against juice jacking, it does encrypt your data traffic, making it useless to an attacker even if they manage to intercept it.
These settings aren't perfect. A sophisticated attacker with specialized exploit code might be able to bypass some of them. But for the vast majority of potential threats, enabling these protections significantly reduces your vulnerability.

Traveling Internationally: Special Considerations
International travel increases your juice jacking risk for several reasons. First, you're away from your normal environment for extended periods. Second, international airports and hotels might have weaker security standards than major facilities in your home country. Third, you might be unfamiliar with the charging infrastructure or unable to distinguish legitimate charging ports from suspicious ones.
International travelers face the additional complication of different USB standards. Some countries still use older USB-A connectors, while others have predominantly moved to USB-C. You might need to use adapter cables, increasing the number of devices between your phone and the actual charging port—each one a potential attack vector.
Specific recommendations for international travel:
Bring your own charging cables from home. You know your personal cables are legitimate. Using unfamiliar cables from foreign hotels or tourist shops increases your risk. Pack extra cables in your luggage so you always have a trusted option.
Invest in a compact voltage converter. Most international hotels provide USB charging ports that are safe, but they're not always available. Having your own power adapter allows you to charge from regular electrical outlets instead of relying on public USB infrastructure. This adds a pound or two to your luggage but eliminates an entire category of risk.
Research your destination. Before traveling, look up the charging infrastructure in your destination city. Major hotels and airports in developed countries typically have safe charging infrastructure. Budget hotels or street-level charging stations in less developed areas might represent higher risk.
Avoid charging public devices or shared family devices from public USB ports. If you're traveling with family members or colleagues, prevent them from using public USB charging ports. Once one device on a shared network is compromised, attackers might be able to access other devices on that network.
Be extra cautious with work devices. If you're traveling with a company laptop or phone containing corporate data, use only your personal power bank or USB data blockers. The risk of compromising corporate systems is far higher than the inconvenience of carrying extra charging equipment.
Consider establishing a rule: never charge from an unknown USB port while traveling. Make it a habit so strict that you don't even consider the possibility. This eliminates the decision entirely.

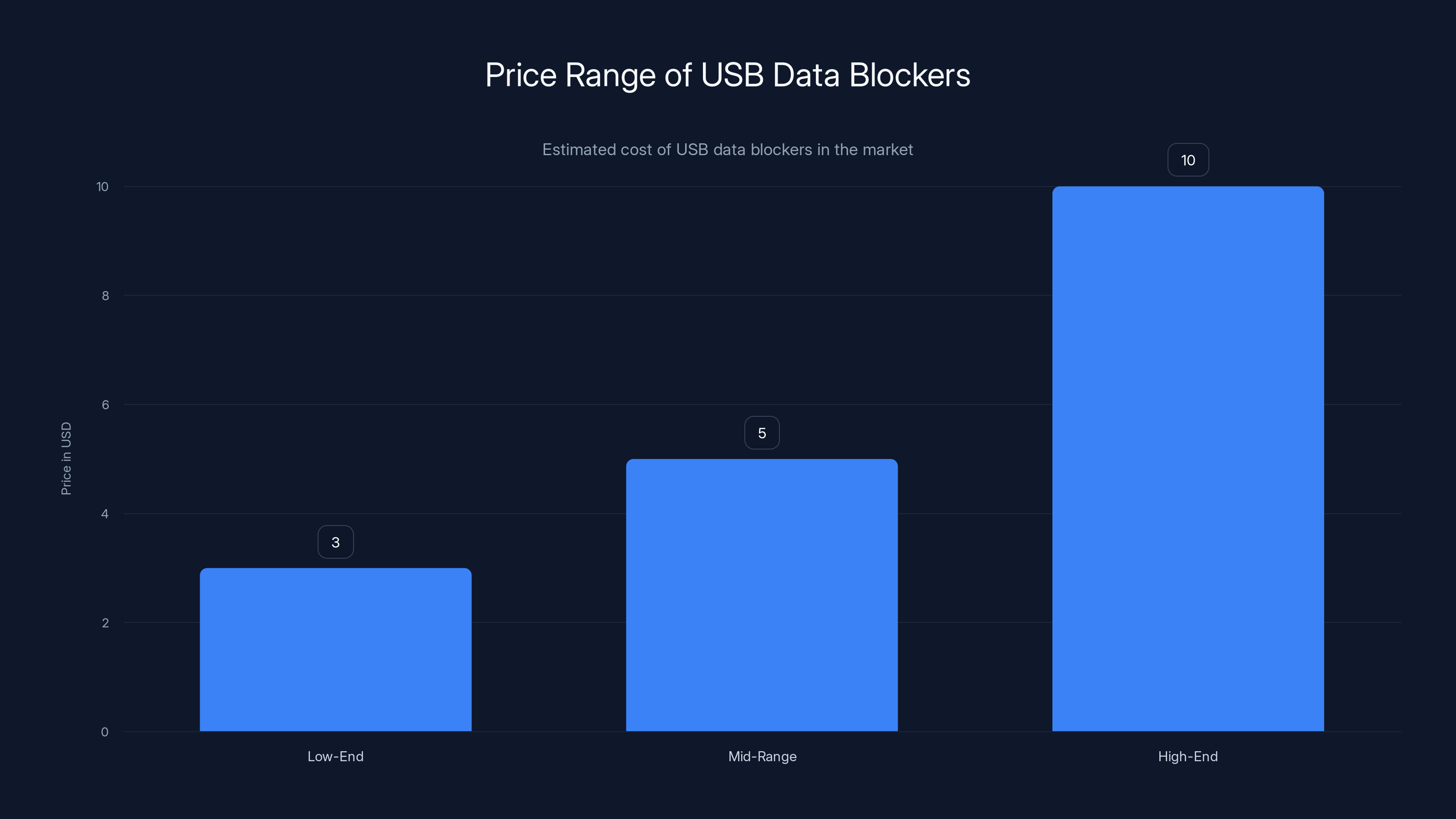
USB data blockers are affordable, with prices ranging from
What Attackers Actually Want From Your Phone
Understanding what attackers seek through juice jacking helps you assess your personal risk. Not all data is equally valuable to attackers, and understanding the hierarchy of targets helps you prioritize your protective measures.
Financial credentials are the primary target. Access to banking apps, payment systems, and financial accounts allows immediate theft of money. An attacker who successfully extracts your online banking password can transfer funds before you notice the breach. Payment app credentials (Venmo, PayPal, Square Cash) allow sending money to the attacker's accounts. Cryptocurrency wallet credentials are even more valuable because the transfers are permanent and untraceable.
Social media credentials are secondary targets. Access to your Facebook, Instagram, Twitter, or TikTok accounts allows the attacker to impersonate you, damage your reputation, or use your account to spread malware to your followers. While not directly profitable, account hijacking is popular because it's easy to monetize—selling access to high-follower accounts is a brisk business.
Email credentials are extremely valuable. Your email account is often the master key to all your other accounts. With email access, an attacker can initiate password resets for banking, social media, and other services. Your email also contains sensitive information: receipts, private communications, backup codes for authentication systems.
Health and personal data has emerging value. The medical records, mental health information, and intimate personal communications stored on your phone can be used for blackmail, identity theft, or sold to health insurance brokers. The value here is growing as hackers develop better tools to extract and monetize this data.
Corporate data is the highest-value target. If you're traveling with work devices, attackers particularly want access to corporate emails, documents, and credentials. A single compromised work device could give attackers access to entire corporate networks, making that device worth far more than a personal consumer phone.
Location history and movement patterns reveal where you go, who you meet, and when you're home or away. This information can be used for physical targeting—burglars knowing when you're away, or worse, stalkers tracking your movements.
Understanding this hierarchy helps you prioritize protective measures. The most valuable data on your device is worth protecting seriously. If you carry sensitive work information or financial credentials, your risk level is higher, and you should take stronger protective measures.
Personal phones used primarily for social media and casual browsing are lower-value targets, meaning the risk, while still real, is lower in magnitude.
The Evolution of Charging Security: What Companies Are Doing
Major technology companies are gradually improving charging security, though progress is slower than many security experts would prefer.
Apple's implementation of USB Restricted Mode (available since iOS 12, enhanced in iOS 15.1) makes it harder for USB accessories to access data on locked iPhones. By requiring biometric authentication for any USB data access on locked phones, Apple increased the barrier for attackers.
Google has been less aggressive but has included similar protections in Android. The Restricted USB mode available on some Android devices prevents data transfer without explicit authorization. However, Google's power to enforce this is limited because dozens of manufacturers create Android devices with varying levels of security implementation.
Third-party manufacturers are slowly adding security features to charging accessories. Some advanced USB hubs now include security features that prevent unauthorized data access. Some charging cables have built-in authentication systems. However, these are still niche products not widely adopted.
The bigger picture: the USB Power Delivery specification itself hasn't adequately addressed security concerns. The spec focuses on safely delivering higher power levels without overheating or damaging devices, but it doesn't comprehensively address the data security risks we've discussed. Updating this specification would require consensus from dozens of manufacturers, a process that typically takes years.
What this means practically: you can't rely on your device or charging infrastructure automatically protecting you. You need to take deliberate protective steps yourself. Manufacturers are improving, but not fast enough to entirely eliminate the threat in the near term.
Building a Comprehensive Charging Security Habit
The most effective protection against juice jacking isn't any single tool—it's a comprehensive habit that addresses multiple vectors simultaneously.
Your charging security system should include:
-
A personal power bank that you charge exclusively from home outlets. This becomes your primary charging method during travel, eliminating reliance on public USB infrastructure entirely. Cost:
50 for a quality bank that lasts years. -
USB data blockers in strategic locations. One on your main charging cable at home, one in your travel bag, one in your backpack. These serve as backup protection if you must use public charging. Cost:
20 for multiple blockers. -
Intentional device settings reviewed every time you update your OS. USB Debugging disabled, Trust settings enabled, Restricted USB Mode enabled on iPhone. These are free but require active maintenance.
-
A rule system where you consciously avoid certain charging locations. Decide that you won't charge from unmanned USB ports, and stick to that rule even when inconvenient. This costs nothing but requires discipline.
-
Regular device updates ensuring your operating system has the latest security patches that defend against known vulnerabilities. This requires checking your update settings quarterly and installing updates promptly.
-
VPN usage when you must access sensitive data on public networks, even though you're charging from your power bank. This provides defense-in-depth against multiple threat vectors.
-
Device encryption enabled on your phone. Most modern phones encrypt data by default, but verify this is enabled in your security settings. This means that even if an attacker successfully accesses your device, the data stored on it remains unreadable without your password.
This system isn't overwhelming. Most of it is one-time setup. The main ongoing effort is remembering to charge your power bank before traveling and habitually refusing to use suspicious public charging ports. Both become automatic with practice.

Detecting If Your Device Has Been Compromised
Because juice jacking attacks can happen silently, it's worth understanding the warning signs that might indicate your device has been compromised.
Warning signs that your device might have been targeted by juice jacking:
Unexpected changes to your accounts. If you notice unauthorized login attempts, account access from locations you weren't in, or settings changes you didn't make, your device might have been compromised. Check your bank account activity, email login history, and social media access logs regularly.
Increased data usage. If your data plan suddenly shows massive usage that you didn't cause, an attacker might be exfiltrating data from your device. Review your cellular data statistics.
Unusually slow device performance. Malware running in the background consumes processing power and battery. If your device is suddenly slow or your battery drains faster than normal, investigate the cause.
Unexpected apps or modifications. Regularly review your installed apps. If applications appear that you didn't install, that's suspicious. Also check if your home screen has been reorganized or if default apps have changed.
Phishing or spam you weren't previously receiving. Compromised devices are often used to send spam messages. If you start receiving bounce-back messages about emails you didn't send, or your contacts report receiving messages from you that you didn't write, you've been compromised.
Unexpected bill increases or financial discrepancies. The most direct sign of juice jacking is when attackers use your extracted credentials to steal money or make unauthorized purchases. Check all financial accounts monthly.
What to do if you suspect compromise:
First, don't panic. Suspect compromise doesn't equal confirmed compromise. Change all your important passwords from a different device. Change your banking passwords, email password, and any sensitive account credentials while using a computer you're certain is clean.
Enable two-factor authentication on all accounts if you haven't already. This prevents attackers from accessing your accounts even with your passwords.
Run a security scan using your device's built-in security tools or a reputable mobile antivirus app. Note that antivirus detection on phones isn't perfect—sophisticated malware might remain hidden—but it can catch common threats.
Consider a factory reset of your device, which wipes all data and settings and reinstalls the operating system cleanly. This is the most reliable way to remove any malware. Backup your device before resetting, then selectively restore apps and data rather than restoring everything. This allows you to avoid restoring any malicious software that might have been on your device.
Monitor your accounts closely for the next several months. Attackers might have copies of your data and could attempt unauthorized access weeks after the initial compromise.

Future Threats: The Evolution of Charging Vulnerabilities
Juice jacking as we understand it today is likely to evolve. Understanding future threat landscapes helps you stay ahead of emerging risks.
Wireless charging vulnerabilities are an emerging concern. As more phones adopt wireless charging, the question becomes: can attackers exploit wireless charging to extract data? The answer is probably yes, though the technical requirements are different. Wireless charging coils create electromagnetic fields that, in theory, could be exploited to exfiltrate data or install malware. However, this remains largely theoretical—no practical wireless charging attacks have been widely documented yet.
IoT device networks will increasingly include charging infrastructure. As public charging stations become "smart" devices connected to networks for management and monitoring, they introduce additional security vulnerabilities. These systems might have poor security practices, allowing remote attackers to compromise the charging station without physical access.
5G integration in charging infrastructure could introduce network-based attacks. If charging stations use cellular networks to communicate with management systems, compromised or spoofed cellular connections could be used to deliver malware or intercept data.
Advanced biometric integration might eventually make USB data transfer impossible without explicit biometric authentication, but this technology is years away from widespread implementation.
The most likely near-term threat remains the one we've already discussed: physical juice jacking through compromised cables and charging stations. But the landscape will evolve, requiring continued vigilance and adaptation of protective strategies.

What You Should Do Right Now
Rather than leaving you with abstract information, here are concrete actions you can take in the next 24 hours to improve your charging security:
Immediate actions (next 30 minutes):
Review your iOS or Android security settings using the recommendations in this article. Verify that USB Debugging is disabled on Android, that Trust settings are properly configured on iOS, and that USB Restricted Mode is enabled if available.
Order or purchase USB data blockers if you don't already own them. Amazon and similar retailers deliver them within 2 days. The investment is minimal, and the peace of mind is substantial.
Short-term actions (next week):
Purchase a quality power bank if you travel frequently. Research models with good reviews and appropriate capacity for your needs. A 10,000-20,000 mAh bank provides excellent value.
Establish a conscious rule about public charging. Decide right now that you won't charge from suspicious public USB ports. Write this rule down or share it with friends to reinforce the commitment.
Medium-term actions (next month):
Enable two-factor authentication on your most important accounts if you haven't already. This protects you not just from juice jacking but from multiple threat vectors.
Enable full device encryption if it's not already enabled. Most modern phones encrypt by default, but verify this in your security settings.
Ongoing actions (ongoing):
Update your operating system promptly when updates become available. Security patches matter, and delaying updates leaves you exposed to known vulnerabilities.
Review your account activity monthly. Check your bank account login history, email access logs, and financial transaction history to catch any unauthorized access early.
Reinforce your charging security habits with family members and friends. Share what you've learned so they can protect themselves as well.
FAQ
What exactly is juice jacking?
Juice jacking is an attack where a compromised USB charging cable or station simultaneously charges your phone while stealing data through the USB connection. The attacker intercepts the data lines in the USB connection, allowing them to extract passwords, photos, banking credentials, and other sensitive information while your device charges normally.
Is juice jacking really happening, or is it just a security scare?
Juice jacking has been proven technically feasible through numerous demonstrations by security researchers at conferences like Black Hat and DEF CON. However, documented incidents of actual juice jacking attacks compromising individuals are rare compared to the volume of warnings about it. The threat is real and possible, but it's not currently widespread, making it a low-probability, high-impact risk that's worth protecting against without being paranoid about it.
How can attackers get malicious cables into public charging stations?
Attackers can either replace existing cables with malicious ones they've installed themselves, or they can install malicious hardware inside public charging stations. Some attacks involve distributing USB cables that look legitimate but contain hidden malicious circuitry. Physical access is required, which limits the scale of attacks but doesn't eliminate the possibility, especially in high-traffic areas where tampering might go unnoticed.
Which is more vulnerable—iPhone or Android?
Both iPhone and Android devices are vulnerable to juice jacking, but the attack vectors differ. iPhones have protections like the Trust dialog and USB Restricted Mode, but older research has shown ways to bypass these. Android devices have USB Debugging protections, but the wide variation in Android implementations across different manufacturers creates inconsistent security levels. Neither platform is inherently safer from juice jacking than the other.
Will a USB data blocker prevent all data theft from a public charging port?
A USB data blocker prevents data transmission by physically disconnecting the data lines while allowing power to flow. This eliminates the primary juice jacking attack vector. However, it doesn't protect against other possible attacks involving exploitation of power-related vulnerabilities or devices at deeper operating system levels. For practical purposes, a USB data blocker stops the vast majority of juice jacking attacks, though no single device provides 100% protection against all possible threats.
How much does juice jacking protection actually cost?
Basic protection is extremely affordable. USB data blockers cost
Can my antivirus app detect juice jacking attacks?
Antivirus apps on phones focus on detecting installed malware, not on preventing data theft through USB connections. If juice jacking successfully installs malware on your device, your antivirus might eventually detect it, but only after the malicious access has already occurred. Prevention through physical protection (USB data blockers or power banks) is far more effective than attempting detection after an attack happens.
What should I do if I've been using public USB chargers and I'm worried I've been compromised?
Start by changing your important passwords from a different device you're certain is secure. Change your banking passwords, email password, and any sensitive account passwords. Enable two-factor authentication if you haven't already. Monitor your financial accounts and email access logs for unauthorized activity. If you notice signs of actual compromise, perform a factory reset of your phone to remove any potential malware. Consider running your phone's built-in security scan, though sophisticated malware might evade detection.
Is it safe to use USB charging ports in public places like cafes or airports?
Using public USB charging ports carries measurable risk of juice jacking, even if the actual probability of being targeted is low. The safer alternatives—portable power banks or wall outlets with your own charger—carry no juice jacking risk. If you must use public USB ports, use a USB data blocker to block data transmission. Better yet, use a portable charger or find a wall outlet instead.
Will future phones have built-in protections against juice jacking?
Phone manufacturers are gradually adding protections like USB Restricted Mode, but progress is slow and not all manufacturers implement comprehensive protections. The USB Power Delivery specification itself would need updating to fully address security concerns, a process involving consensus from dozens of manufacturers. For the foreseeable future, users will need to take deliberate protective steps rather than relying on automatic protections in the device itself.

Conclusion: Taking Control of Your Charging Security
Juice jacking might sound like an obscure threat buried in security conferences, but it represents a genuine vulnerability in how we charge our increasingly important devices. Unlike many cybersecurity threats that require sophisticated hacking skills or social engineering, juice jacking is straightforward: someone physically compromises the charging infrastructure, and your data is at risk.
The good news is that protecting yourself costs almost nothing and takes minimal effort. A USB data blocker for
But more important than any specific tool is developing a security mindset about public charging. Treat USB ports like you treat public Wi-Fi networks. Don't assume they're safe. Don't plug in your device without thinking about the risks. Build habits that protect you not through paranoia but through simple, practical caution.
The threat landscape for mobile devices continues evolving. New vulnerabilities emerge, old ones are patched, and attackers find novel approaches to compromise devices and steal data. But the fundamental principle remains constant: taking responsibility for your own security, rather than assuming your devices and the infrastructure around them will protect you automatically.
Your personal information—your banking credentials, your private communications, your health data, your location history—has real value. It's worth protecting with more than hope. It's worth protecting with actual, practical measures that you implement yourself.
Start with just one action today: purchase a USB data blocker or resolve to never charge from a public USB port again without a physical protection method. That single action, maintained as a habit, provides real security. Build from there with the other recommendations in this article. In a few weeks, you'll have comprehensive protection against juice jacking, and you'll have peace of mind knowing your data is safer when you travel.
Charging your phone is a necessary part of modern life. Making that charging secure is now your responsibility to handle.

Key Takeaways
- Juice jacking is a proven technical threat where compromised USB cables or charging stations steal data while charging your phone through the USB data lines
- The actual documented frequency of juice jacking attacks remains low despite widespread security warnings, but the potential impact on any individual victim is severe
- USB data blockers (25-50) are the most practical and affordable protection methods that eliminate juice jacking risk entirely
- Public charging locations like airports, hotels, and transportation hubs represent higher-risk environments where attackers are more likely to install malicious equipment
- Both iOS and Android devices are vulnerable through different technical mechanisms; neither platform provides complete automatic protection against juice jacking attacks
![Juice Jacking: How to Protect Your Phone from Public Charging Threats [2025]](https://tryrunable.com/blog/juice-jacking-how-to-protect-your-phone-from-public-charging/image-1-1766947338175.jpg)




