Logitech's macOS Certificate Disaster: A Deep Dive Into What Went Wrong
Imagine waking up on a Monday morning, firing up your Mac, and discovering that all your carefully configured Logitech keyboard and mouse settings have vanished. Your custom shortcuts are gone. Your device-specific profiles disappeared. The apps that manage everything? They won't even launch.
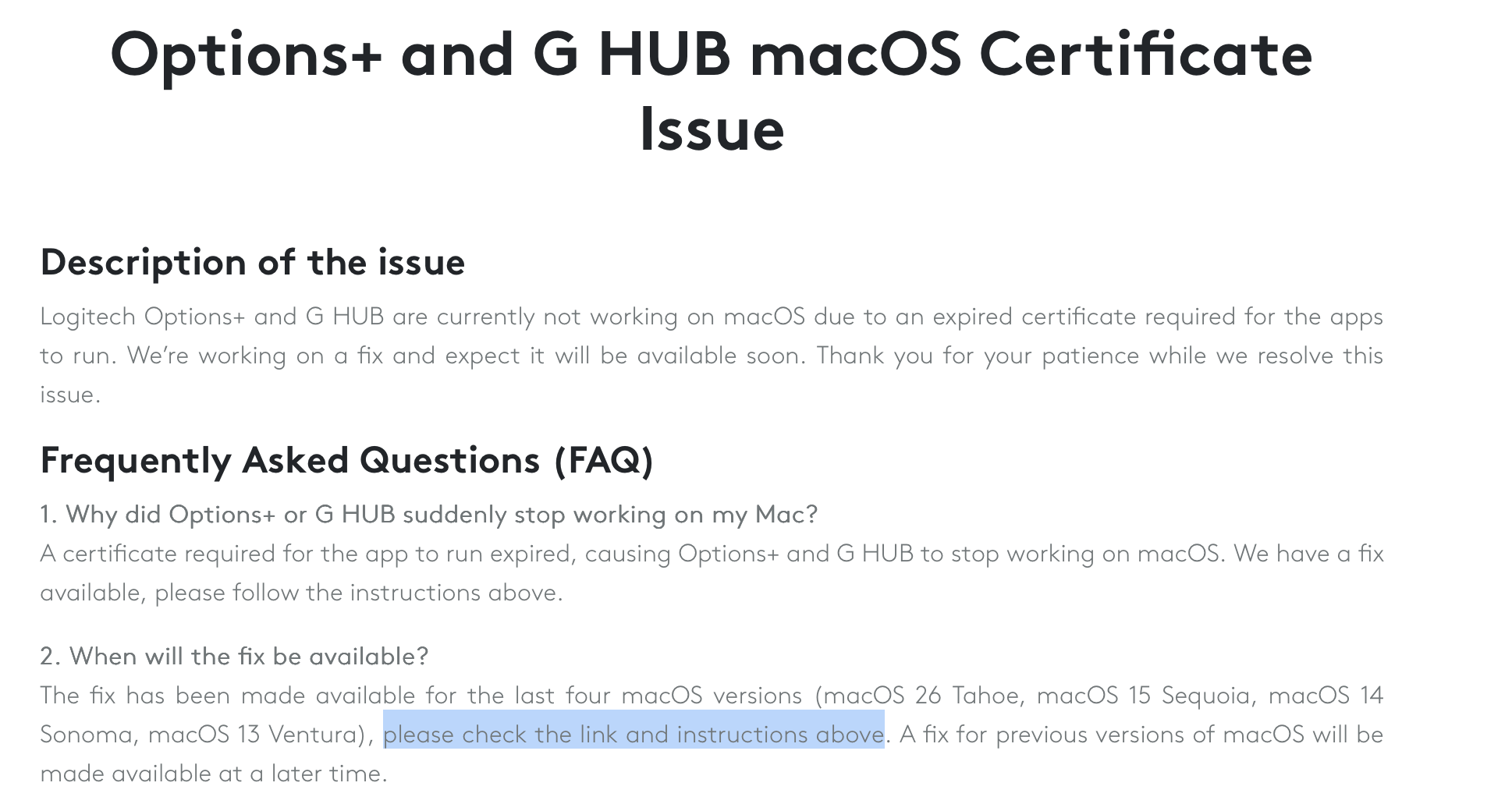
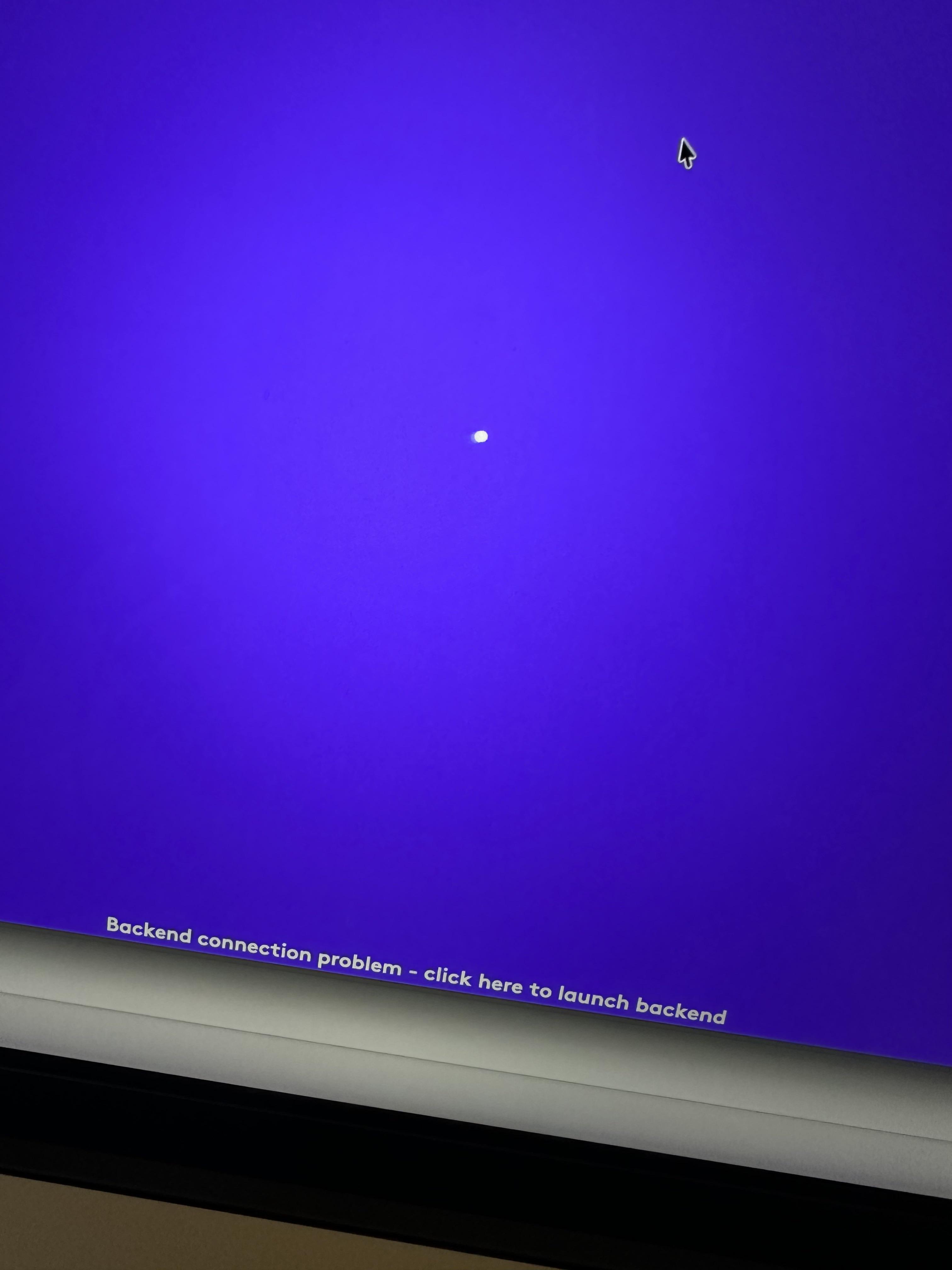
This isn't hypothetical. It happened to thousands of Mac users in January 2025, and the reason was startlingly simple: a security certificate expired. According to MacRumors, Logitech's Logi Options+ and G Hub applications for macOS suddenly went dark across the platform, refusing to start and reverting every customized setting back to factory defaults. For power users who'd spent hours configuring their Logitech peripherals, it felt like sabotage. For IT departments managing fleets of devices, it was a nightmare.
The kicker? Even though Logitech released a fix within days, there was no automatic way to deploy it. Users had to manually download and install patches themselves because the very mechanism that handles automatic updates was broken by the same expired certificate.
This incident exposes something critical about modern software: how fragile the foundation can be, and how a single overlooked detail in certificate management can cascade into widespread disruption. It's also a masterclass in what happens when security infrastructure meets poor operational oversight.
TL; DR
- What Happened: Logitech's security certificate for inter-process communication expired on January 13, 2025, immediately breaking Logi Options+ and G Hub on macOS.
- The Impact: Users couldn't launch the apps, lost all custom settings, and reverted to default configurations with no way to recover preferences.
- The Complication: The expired certificate broke the app's built-in auto-updater, so users couldn't fix the problem automatically and needed manual patches.
- The Fix: Logitech released patches requiring manual installation, with support for macOS 13, 14, 15, and 26, while older OS versions faced extended downtime.
- The Lesson: Certificate management remains one of the most overlooked but critical aspects of software infrastructure, and its failures cascade unpredictably.
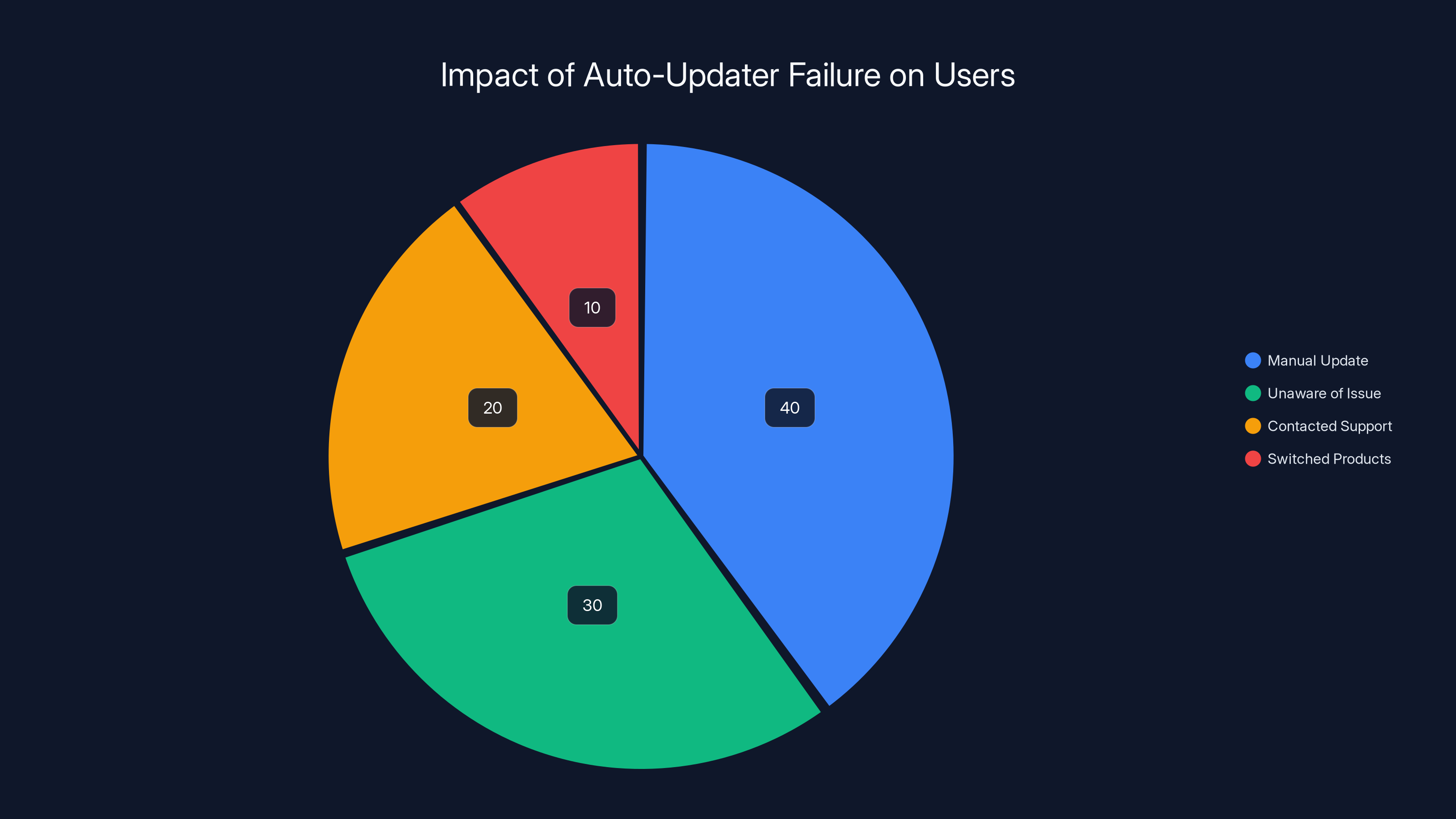
Estimated data shows that 40% of users manually updated, while 30% remained unaware of the issue, highlighting the operational challenges of manual updates.
Understanding the Certificate Failure: What Actually Broke
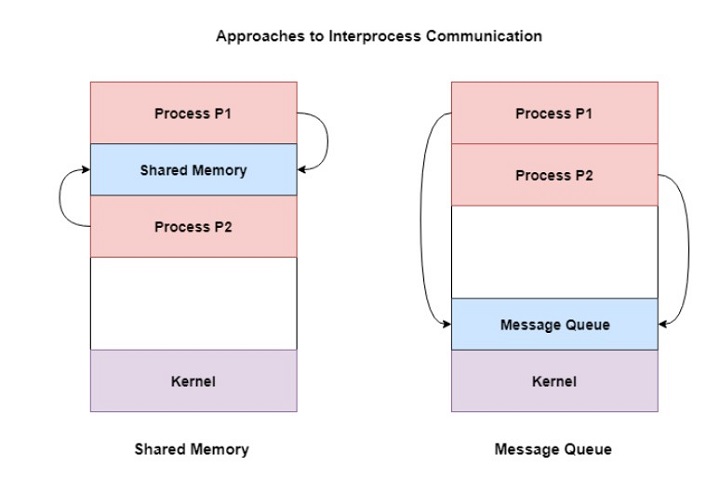
To understand why this failure was so catastrophic, you need to understand what the expired certificate actually did. This wasn't a public-facing SSL certificate for a website. This was an internal security certificate used for inter-process communication (IPC) between different components of Logitech's applications.
Inter-process communication is how different parts of a single application talk to each other securely. When you launch Logi Options+, multiple processes spin up behind the scenes. They need to communicate with each other safely and verify that they're actually legitimate components of the same application, not malicious code trying to hijack the communication channel. That's where the certificate comes in.
The certificate serves as a cryptographic handshake. It says, "I am a legitimate part of Logitech's software, and I have the right to talk to other components." Without it, the verification fails. The processes can't confirm each other's legitimacy, so the entire application refuses to start. This is actually a good security practice. Apple's macOS has increasingly strict requirements about code signing and verification, especially as security concerns have grown. Logitech implemented this correctly in principle. The only problem: they didn't manage the certificate's lifecycle.
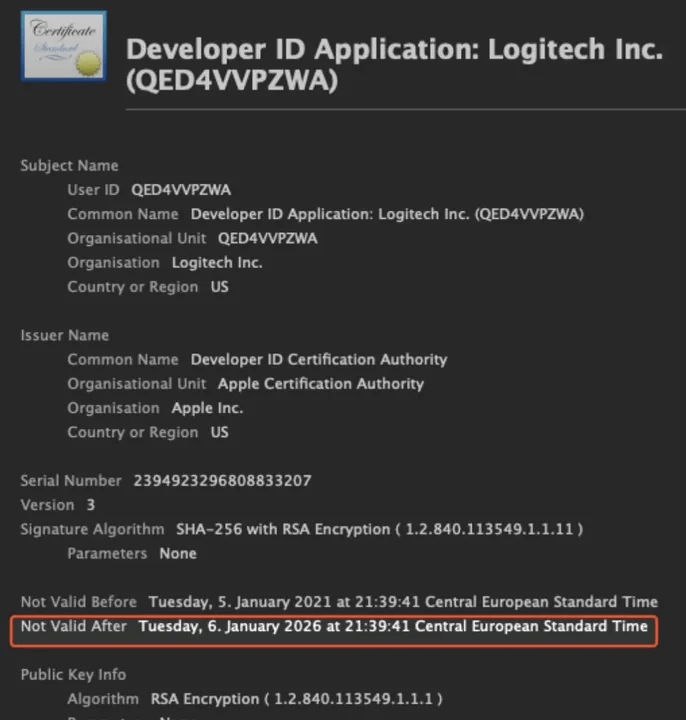
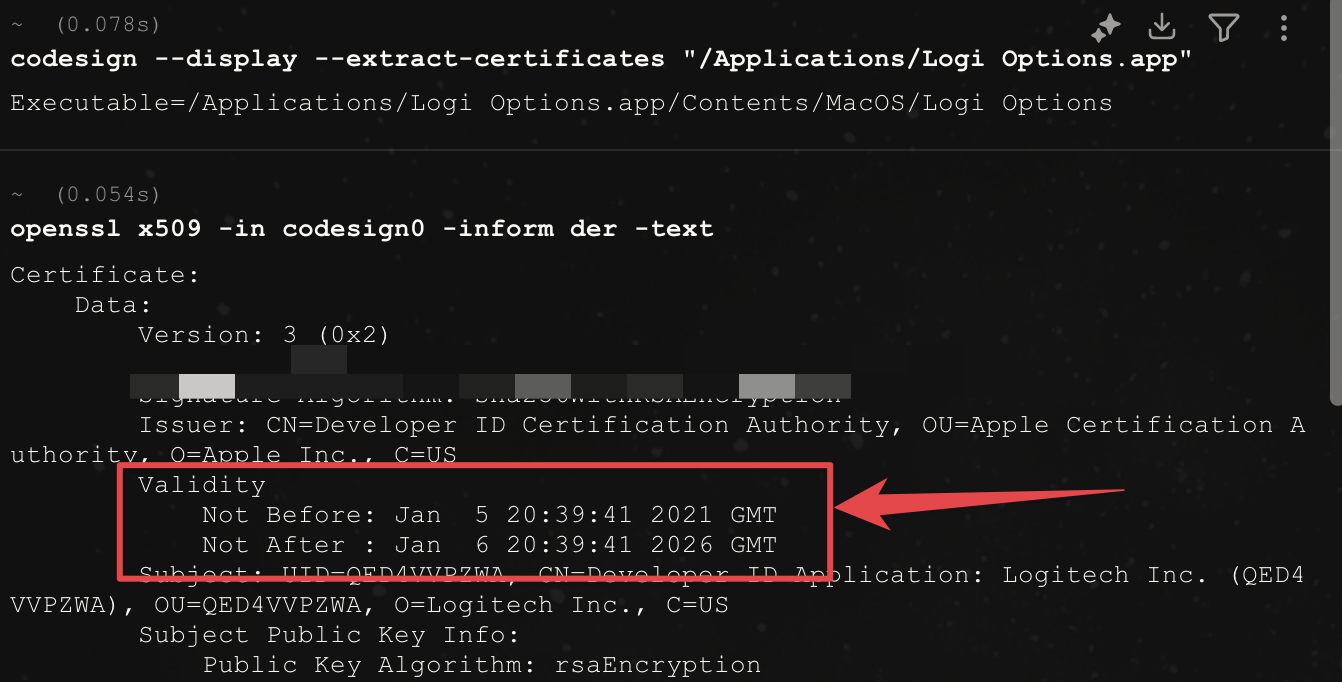
Certificates have expiration dates for a reason. They force organizations to regularly update their cryptographic keys, improving security by requiring periodic rotation. A certificate that lasts forever is a security liability. If someone steals the private key, they can use it indefinitely. With regular expiration, the theft window is limited. But this security benefit only works if the organization actually manages the renewal process. Logitech's certificate expired on January 13, 2025, and somehow it wasn't renewed before that date.
Joe Santucci, Logitech's Head of Global Marketing, acknowledged the failure directly in Reddit posts: "The certificate that expired is used to secure inter-process communications and the expiration results in the software not being able to start successfully." He didn't mince words about the severity: "We dropped the ball here. This is an inexcusable mistake. We're extremely sorry for the inconvenience caused."
That's refreshingly honest, but honesty doesn't solve the immediate problem for users whose devices are now unusable.
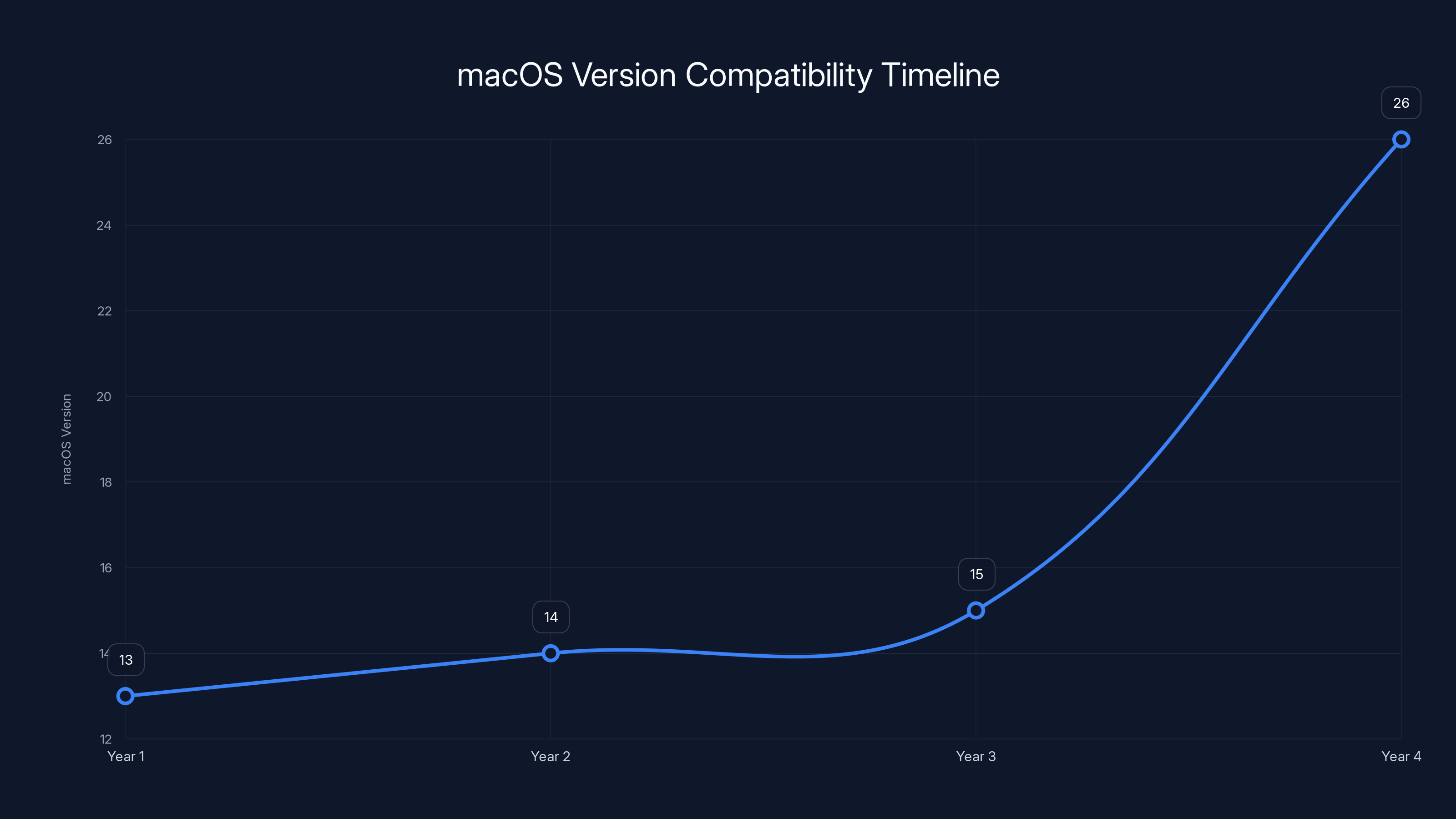
Logitech's support spans four macOS versions over four years, highlighting good support but also the challenge of version fragmentation. Estimated data.
The Cascade Effect: Why the Auto-Updater Failed Too
Here's where the failure became even more problematic: the same expired certificate that prevented the apps from launching also prevented them from updating themselves. Logitech's built-in auto-update mechanism relies on the same inter-process communication infrastructure that the certificate protects. When the certificate expired, the updater couldn't verify that it was talking to a legitimate part of the application, so it failed too.
This created a catch-22. The app was broken. The app couldn't be fixed automatically because the mechanism that handles automatic fixes was also broken by the same root cause. Software architectures sometimes have these nested dependencies that aren't obvious until something breaks. You might design the update system to use the same security infrastructure as the main application to minimize code duplication and maintain consistency. That's good engineering in normal circumstances. But it means a single point of failure takes down the entire system.
For end users, this meant the only path forward was manual intervention. You couldn't just wait for a background update to fix things. You had to:
- Recognize that the problem existed (not obvious if you didn't follow tech news)
- Find the patch from Logitech's support pages
- Download it manually
- Run the installer
- Restart the app
For a consumer product with millions of users, requiring manual fixes for a widespread problem is operationally expensive. It drives up support costs, increases frustration, and leaves many users unaware a fix exists at all.
Logitech's apps, however, aren't distributed through the App Store. They're downloaded directly from Logitech's website, which means they rely on their own update mechanisms. And those mechanisms had just become nonfunctional.
The Settings Problem: Lost Customizations and Data Recovery
When the apps stopped running, users didn't just lose access to customization features. They lost the settings themselves. All the profiles you'd created, the keystroke assignments you'd mapped, the device-specific configurations you'd built up over months or years, the lighting preferences, the button remapping—all of it disappeared and reverted to factory defaults.
This raises an important question: where were these settings stored? When a Logitech user configured their keyboard or mouse, those settings were typically stored in one of two places: either in a local file on the Mac (usually in the user's home directory), or synced to Logitech's cloud services if the user had an account.
The problem was that during the outage, users couldn't access the app to retrieve or restore those settings. Even if the data was intact on disk or in the cloud, there was no interface to access it. Worse, some users who were trying to troubleshoot the problem followed the classic IT troubleshooting playbook: uninstall and reinstall the app. In doing so, they inadvertently deleted the local settings files.
Logitech's FAQ acknowledged this scenario: "Some users, prior to installing the patch, as part of troubleshooting, often uninstall/reinstall the app trying to get it to work and lose settings. So we recommend only using the patch installer."
This is a critical point. Logitech's recommended fix explicitly tells users not to uninstall the app because uninstalling deletes the settings files. But the uninstall-reinstall process is the most common troubleshooting step for app problems. Many users would naturally try this and permanently lose their data.
The patch itself doesn't recover deleted data. If you'd uninstalled the app while troubleshooting, your settings are gone permanently. If you'd never uninstalled, and you simply installed the patch, your settings should be restored. This introduced a lottery element to the outage experience. Users who happened to follow the wrong troubleshooting steps suffered permanent data loss, while those who waited or used the patch immediately lost nothing.
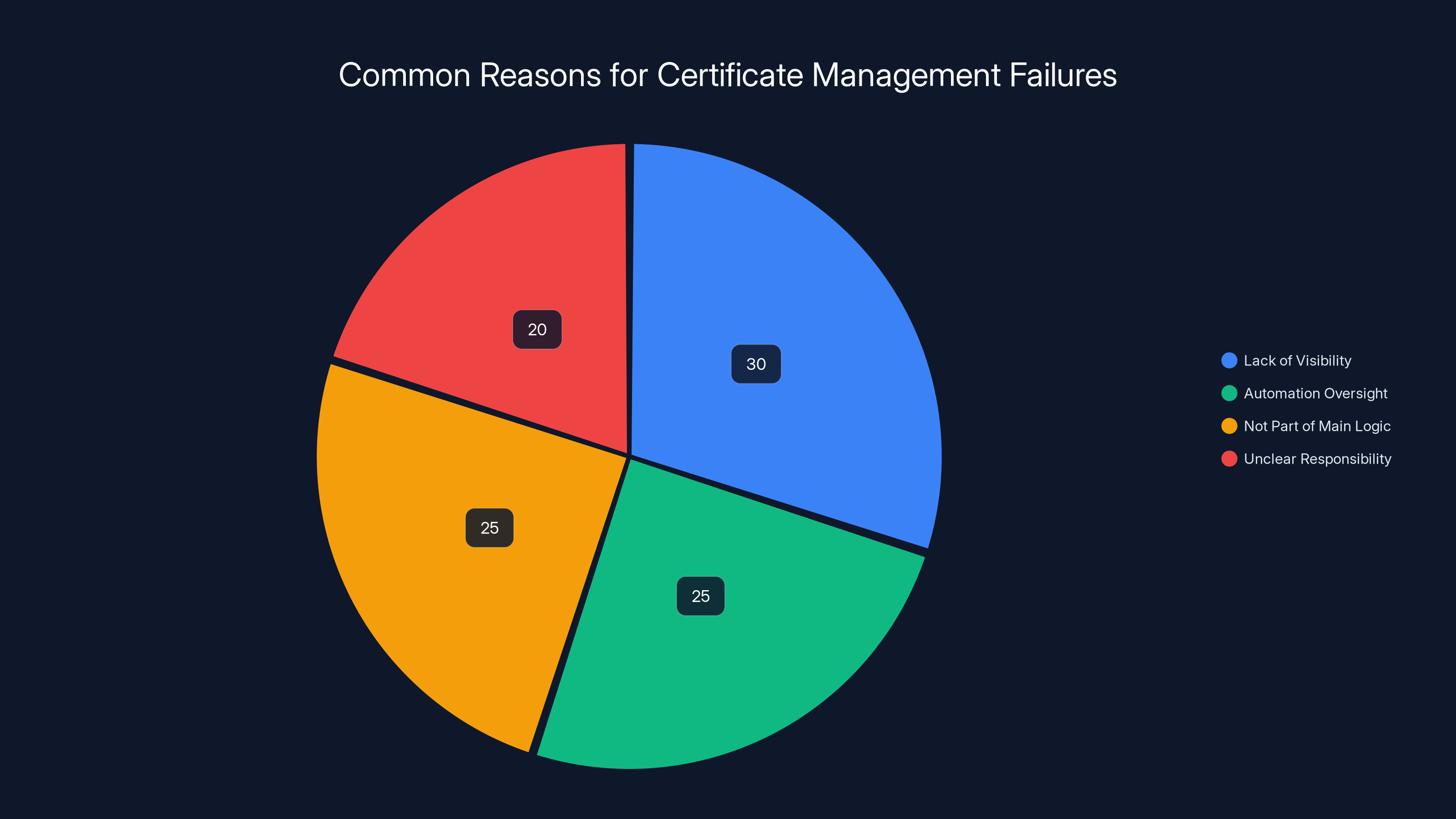
Estimated data shows that lack of visibility and automation oversight are leading causes of certificate management failures, each contributing significantly to the issue.
macOS Version Compatibility: A Timeline of Uncertainty
Logitech's patches were made available for macOS versions 13 (Ventura), 14 (Sonoma), 15 (Sequoia), and 26 (Tahoe). That's a four-year span of operating system versions, which is actually pretty good support. But users running older versions of macOS were told that fixes "will be made available at a later time," which is corporate-speak for "we're not sure we'll fix this."
Logitech did add a note that if you're running an older macOS and you can update to version 14 or later, you should, because Apple only supports the last four OS versions with security patches and Safari updates. An unsupported OS is a security liability.
This raises an important pattern in modern software: version fragmentation. When you're supporting multiple major versions of an operating system, you multiply your testing burden, your maintenance work, and the likelihood of bugs creeping into each branch. There's economic pressure to drop support for older OS versions. It costs money to maintain compatibility, and the number of users on truly ancient systems is usually small. But that leaves those users in a bad position when something breaks.
Why Certificate Management Gets Overlooked
One of the most interesting aspects of this failure is how mundane the root cause was. It's not a complex security vulnerability. It's not a subtle logic error in the code. It's not a race condition that only manifests under specific hardware configurations. It's just a calendar date that someone forgot to prepare for.
This happens more often than you'd think. Certificate expiration failures have been responsible for widespread outages in the tech industry before. In 2015, Comcast accidentally broke a major HTTPS certificate. In 2017, a single expired certificate nearly broke portions of the internet. In 2020, multiple security vendors' certificates expired simultaneously, breaking their ability to function.
Why does certificate management fail so frequently? Several reasons:
It's not visible until it breaks. A certificate works perfectly until the exact moment it expires. There's no degradation, no warnings in production, no slow performance that tips you off something's wrong. It just stops working suddenly.
It's easy to automate away and then forget. Many organizations implement automated certificate renewal systems and then assume the problem is solved permanently. But when the renewal system itself breaks or when you switch certificate authorities or when you move the cert to a different server and forget to set up renewal there, nobody notices until the customer impact is severe.
It's not part of the main application logic. When a core feature breaks, developers notice immediately because they test it regularly. Certificate management is infrastructure. It's the foundation that makes everything work, but it's not the main feature. Developers don't interact with it daily, so it's easy for it to slip through the cracks.
Responsibility is unclear. Is certificate management the DevOps team's job? The security team's? The infrastructure team? When multiple teams could own a process, it's easy for it to fall through the cracks between them.
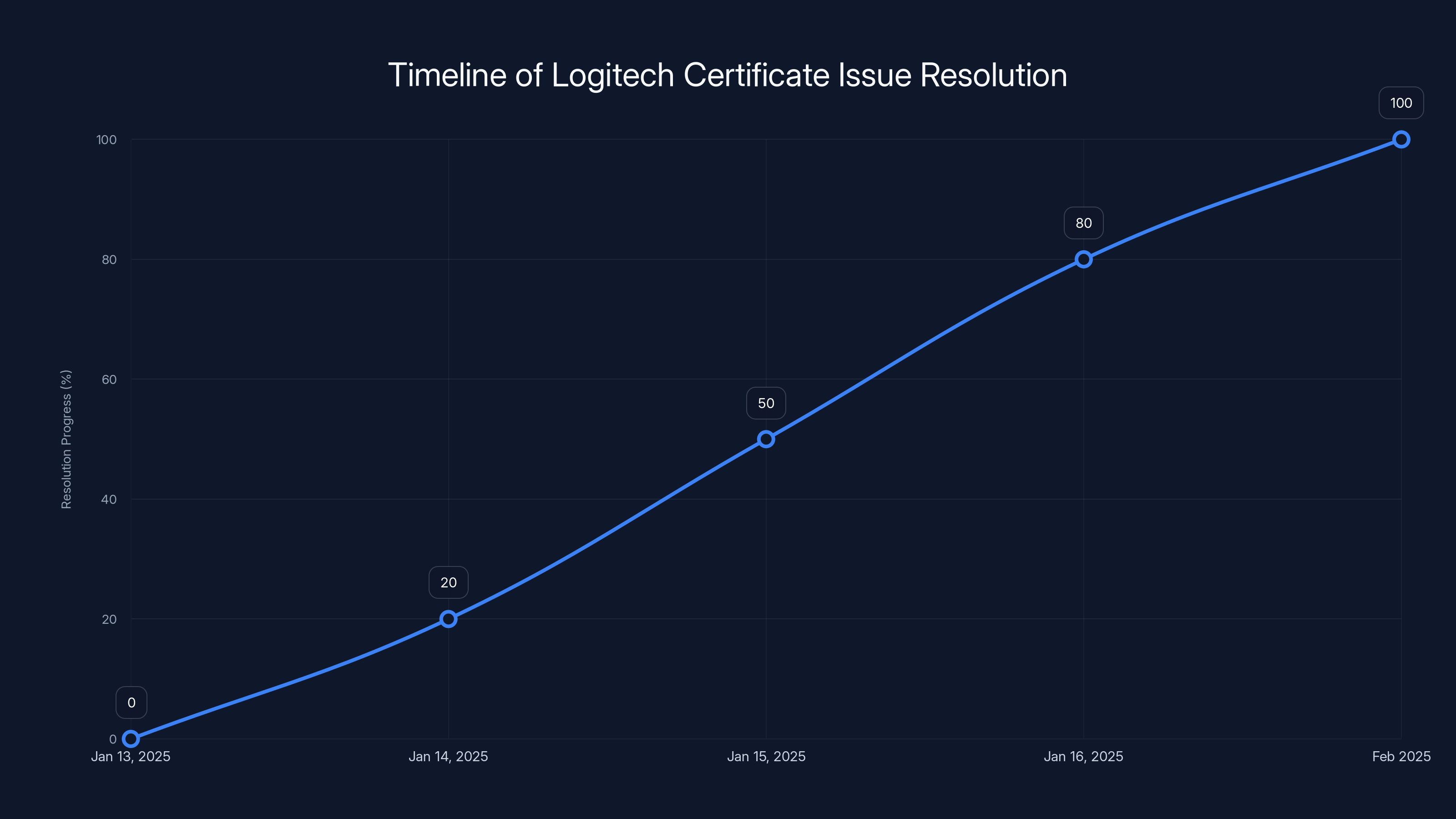
The resolution of the Logitech certificate issue progressed rapidly after the problem was identified, with most users resolving the issue within a few days. However, some users experienced delays due to lack of information or unsupported systems. Estimated data.
The Patch Distribution Problem: Why Manual Installation Is Necessary
Modern apps ideally update themselves silently in the background. You turn on your Mac, you get a notification that an update is available, you click a button, and the update installs while you work. Or even better, the app checks for updates in the background and installs them without asking.
Logitech couldn't implement this solution because the auto-update mechanism was the secondary victim of the certificate expiration. The certificate didn't just break app launching; it broke the internal security verification that the updater relies on.
So Logitech had two choices:
Option One: Release a patch that requires manual installation. Users download the patch, run it, and the problem is solved. The downside is that not all users will install it. Some won't know about it. Some will forget. The company ends up supporting a divided user base where some are on the working version and some are still broken.
Option Two: Release an entirely new version of the application that bypasses the problem by not shipping with the expired certificate. This would be a fresh download from scratch, which defeats the purpose of a patch and requires even more manual user action.
Logitech chose Option One, which is the pragmatic choice. The alternative would be worse.
But this exposes a fundamental problem with applications that aren't distributed through app stores. Without a centralized distribution mechanism that can force updates, you can never guarantee that your users are on the fixed version. Some users won't update for weeks or months. Some might never update at all.
This is part of why Apple strongly pushed developers toward the App Store in the first place. When you distribute through Apple's infrastructure, Apple can ensure that users are kept up-to-date. When you distribute directly to users, you're relying on their behavior to fix problems.
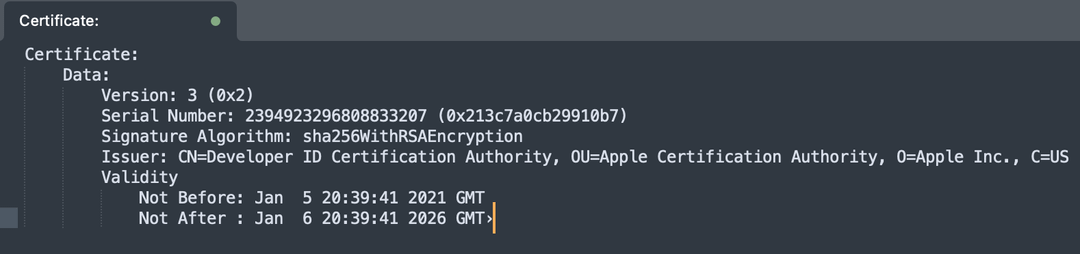
Timeline: From Working to Broken to Partially Fixed
Let's reconstruct the timeline of events:
Sometime in the past: Logitech obtains a security certificate for inter-process communication in their macOS applications. The certificate is valid for a certain period, probably one to three years.
January 13, 2025 (approximately): The certificate expires. Automatically, without any user action, the certificate becomes invalid for cryptographic purposes. This is by design.
January 13, 2025 (morning, user time): Users start trying to launch Logi Options+ or G Hub and find that the apps won't start. No error message. No helpful notification. The app just fails to launch, and the user has no idea why.
January 13-14, 2025: Users start posting on Reddit, in tech forums, and on Logitech's support pages asking what happened. Some users start trying to troubleshoot by uninstalling and reinstalling, which deletes their settings.
January 14-15, 2025: Logitech's support team realizes the scope of the issue. They identify the root cause (the expired certificate) and begin preparing patches.
January 15-16, 2025: Patches are released. Logitech publishes documentation explaining the problem and directing users to manually download and install the patch.
January 16 onwards: Users gradually learn about the patches and install them. Settings are restored for those who didn't uninstall during troubleshooting. The incident is largely resolved, though some users are still affected due to settings loss from troubleshooting or because they use unsupported macOS versions.
The total duration of the outage was roughly 2-3 days for users who found and installed the patch quickly, but potentially weeks or months for users who didn't know about the issue or who delay updating.

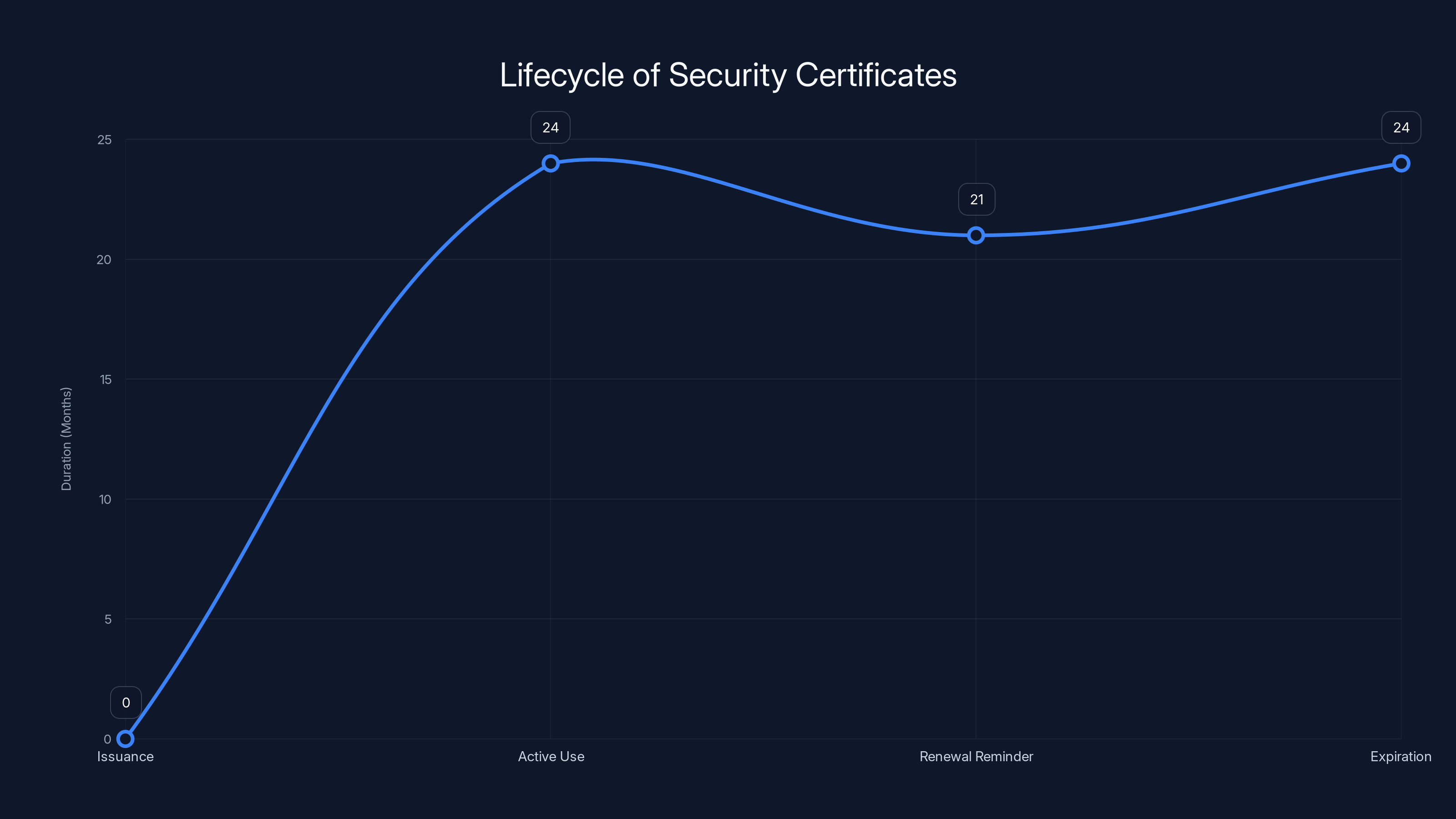
Certificates typically have a lifecycle of 24 months, with renewal reminders starting 3 months before expiration. Estimated data.
The Technical Root Cause: Certificate Lifecycle Management
Logitech made a mistake in their certificate lifecycle management. This is a process that should have been automated or heavily monitored. Here's what should have happened:
Monitoring: A system should have been in place to check certificate expiration dates against the current date. When a certificate is less than 90 days from expiration, alerts should have been triggered to the relevant team.
Renewal: Long before the expiration date, the certificate should have been renewed and the new certificate deployed to all systems that use it. This could have been automated entirely.
Testing: After deployment, the new certificate should have been tested in a staging environment to ensure the applications still function correctly.
Verification: A verification process should have confirmed that the old certificate was successfully replaced and that all systems were using the new one.
Apparently, Logitech's process broke down somewhere in this chain. Maybe the renewal was forgotten. Maybe it was renewed, but deployment to the macOS app bundle was missed. Maybe the alert was generated but not acted upon.
The technical implementation itself is probably fine. The issue is operational. In software, operational failures—the human and process-level mistakes—are often the root cause of the biggest outages.

Impact on Different User Groups
This incident affected different users in different ways:
Professional Users and Teams: For offices using Logitech keyboards and mice, this could have affected productivity. If the organization had many Macs, this could have impacted dozens or hundreds of computers simultaneously. IT departments had to decide whether to let support tickets pile up or manually patch each system.
Power Users with Complex Configurations: Users who'd spent hours building sophisticated macros and keyboard shortcuts lost all that work. The restoration of settings depended on whether they'd uninstalled the app during troubleshooting.
Casual Users: Most users probably reverted to using the default device settings and didn't even notice the problem was fixed. The default settings are functional; they're just not personalized.
Users with Unsupported macOS Versions: Those on older macOS versions were left without a clear timeline for a fix. Some were effectively locked out of using their Logitech software indefinitely.
Cloud-Synced Users: If you had a Logitech account and had settings synced to the cloud, you had a better chance of recovery because the settings data existed in multiple locations. Users with purely local configurations were more vulnerable to permanent data loss.
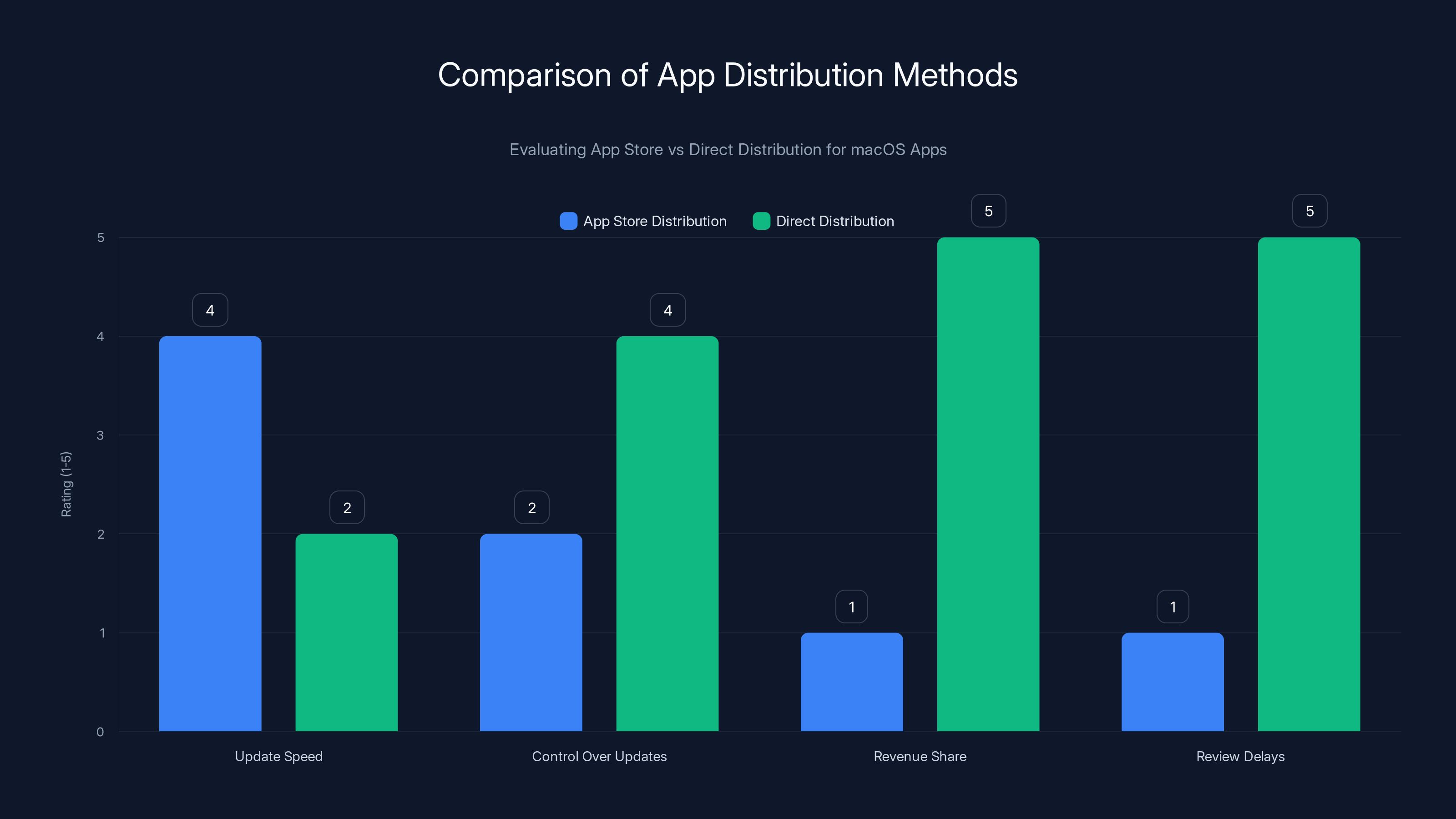
App Store distribution offers faster updates but less control, while direct distribution provides more control but requires maintaining update infrastructure. Estimated data.
Comparing to Other Recent Software Failures
Logitech's certificate expiration isn't unprecedented. Let's look at how similar failures have played out in the industry:
Crowd Strike's July 2024 Outage: A bad content update was pushed out and broke systems globally. The difference here is that Crowd Strike's auto-update mechanism worked perfectly—too perfectly. It automatically pushed the broken update to every system before anyone could catch it. Logitech's inability to auto-update meant the problem was more localized, but the manual fix required more user effort.
Facebook/Instagram Outages: When Facebook's certificate infrastructure failed briefly in the past, their global reach meant that hundreds of millions of users were affected for hours. Logitech's impact was smaller because they're a smaller company with a smaller user base, but the underlying problem was similar.
Wells Fargo Mobile Banking Certificate Issues: In 2020, Wells Fargo's mobile banking app broke temporarily due to certificate issues. The bank had to issue emergency patches and public communications to get users back online.
The pattern is clear: certificate management failures are systemic across the industry. They're not unique to Logitech, and they're not sophisticated attacks or hacks. They're the result of operational oversights.
The macOS Ecosystem and App Distribution
One reason this incident had such a broad impact is that Logitech's apps are distributed outside the macOS App Store. This gives Logitech more control over their application distribution, but it also means they're responsible for their own update mechanisms.
If Logi Options+ and G Hub were distributed through the App Store, Apple would have handled the update distribution. Apple's servers would have pushed the fix to users' devices automatically, and the outage would have been largely contained to the initial 24-48 hours before most users received the auto-update.
But App Store distribution comes with trade-offs too. Apple takes a 30% cut of revenue (though these are free apps, so that's not relevant). Apple reviews apps more strictly, which can slow down releases. Developers have less control over the user experience and update timing.
For Logitech, distributing directly to users probably felt like the right choice. They avoided App Store review delays and kept more control. But it meant they also had to maintain their own update infrastructure, which is where the failure occurred.
This is a classic trade-off in software distribution: centralization makes updates easier but reduces control, while decentralization gives developers control but makes updates harder.
Lessons for Software Infrastructure Teams
If you manage software infrastructure, Logitech's failure offers several important lessons:
Automate Certificate Management: Don't rely on calendar reminders or email alerts. Use automated systems that renew certificates before they expire. Services like Let's Encrypt have made this much easier, and similar systems exist for internal certificates.
Monitor All Certificates: You need visibility into every certificate your systems use. This includes public certificates, internal certificates, self-signed certificates, everything. A comprehensive audit should be done at least annually.
Test Thoroughly After Certificate Updates: When you renew a certificate, test the affected applications in a staging environment before deploying to production. Don't assume the renewal will work.
Decouple Update Mechanisms from Security Infrastructure: If your auto-update system depends on the same security infrastructure as your main application, you've created a single point of failure. Consider whether you can make your update mechanism more independent and resilient.
Document the Certificate Lifecycle: Every certificate should have documentation that clearly states when it was issued, when it expires, where it's used, and how it's renewed. This prevents future teams from being confused about the certificate's status.
Have a Contingency Plan: Even with automation, things can go wrong. Have a documented procedure for manually deploying critical updates or patches when the automated system fails.
What Users Can Do to Protect Themselves
As a user, there are steps you can take to minimize your vulnerability to similar incidents:
Keep Applications Updated: Install patches and updates when they're available. They often fix not just new features but critical infrastructure problems like certificate issues.
Use App Store Distribution When Possible: For applications available on the macOS App Store, prefer the App Store version. Apple's infrastructure ensures you get updates automatically.
Backup Your Settings: For applications that manage complex configurations (like Logitech's), periodically export your settings to a file. If something breaks, you can restore your configuration manually.
Follow Multiple News Sources: Tech incidents like this are often covered by tech media. Following sources like Ars Technica, The Verge, or other tech news outlets means you'll hear about major problems faster than waiting for official company communications.
Monitor Support Pages: If you use a product, occasionally check the company's support pages for known issues. Many companies post notices about outages or problems without sending email notifications.
Keep Your Operating System Updated: Logitech provided patches for the four most recent macOS versions because Apple only supports those versions with security updates. Keeping your OS current helps ensure you're on a supported version.
The Bigger Picture: Software Fragility
Logitech's certificate failure is a small incident in the grand scheme of internet infrastructure. No servers were hacked. No critical data was exposed. No lives were endangered. For most users, the problem was fixed within hours or days.
But it reveals something uncomfortable about modern software: how fragile it can be. A single expired certificate broke not just one app, but multiple apps from a major company simultaneously. And that same certificate also broke the mechanism that would normally fix such problems.
This kind of cascading failure is becoming more common as software becomes more complex and interconnected. Every system depends on dozens of other systems. Every application depends on multiple pieces of infrastructure working correctly. The more complex the system, the more ways it can fail.
The good news is that this kind of failure is largely preventable through careful operational practices. Automated monitoring, automated renewal, automated testing, and clear documentation can prevent certificate expiration issues entirely.
The bad news is that many companies treat infrastructure as an afterthought, focusing their energy and budget on feature development instead. Infrastructure is boring. It doesn't make for exciting product announcements. It doesn't drive user growth. So it often gets deprioritized.
Until a certificate expires.
How Logitech's Response Compares
One positive aspect of Logitech's handling was their transparency. Rather than staying silent or issuing vague statements, Logitech acknowledged the problem directly. Joe Santucci's comments on Reddit weren't defensiveness; they were straightforward admissions that the company made a mistake.
Compare this to how some companies handle similar failures: they issue carefully worded corporate statements that never quite admit fault, blame external factors, or remain silent and hope the issue is forgotten.
Logitech's approach was refreshing and probably helped maintain some user trust despite the failure. People are often forgiving of mistakes if the company is honest about what happened and works to fix it quickly.
That said, there were still complications. The requirement for manual patching, the data loss for users who troubleshot incorrectly, and the lack of fixes for older macOS versions all represent gaps in the response. A perfect response would have:
- Released a fix within hours (Logitech was within roughly 24-48 hours, which is reasonable)
- Ensured the fix could be deployed automatically (this was impossible due to the nature of the failure)
- Protected user settings from accidental loss (this could have been mitigated with better documentation)
- Provided a timeline for supporting older macOS versions (instead of "later")
None of these gaps were catastrophic, but they added friction to the recovery process.
Industry-Wide Certificate Management Failures
This isn't the first time certificates have caused widespread outages, and it won't be the last. The industry has seen similar failures repeatedly:
2015: Comcast Certificate Failure - A misconfigured certificate caused massive connectivity issues for Comcast customers.
2017: Global Cert-Based Outages - Multiple incidents where certificate mismanagement affected large portions of the internet.
2020: Antivirus Software Certificate Issues - Several security vendors' certificates expired, breaking their ability to function properly.
2023: CDN Certificate Problems - Content delivery network issues caused by certificate mismanagement affected thousands of websites.
The repeatability of this pattern suggests that the industry hasn't learned the lesson. Certificate management remains one of the weakest points in software infrastructure, despite being one of the most important.
What's notable is that the solutions already exist. Automated certificate renewal services, monitoring systems, and deployment automation are all mature technologies. The problem isn't technical; it's organizational. Companies aren't prioritizing certificate management because nothing bad happens until something catastrophic breaks.

What This Means for the Future of Software Reliability
As software becomes more critical to business operations, the cost of these kinds of failures increases. Logitech's incident was inconvenient for users, but the broader pattern points toward a future where infrastructure reliability becomes a competitive advantage.
Companies that invest in robust certificate management, comprehensive monitoring, and mature automation will have fewer surprises. Companies that treat infrastructure as a necessary evil will continue experiencing these failures.
For users, the lesson is becoming clearer: the reliability of the software you depend on depends heavily on the operational practices of the company that makes it. Transparency about those practices (or lack thereof) is valuable information when choosing between competing products.
The future likely involves better tools for certificate management. Some companies are already moving toward certificate abstraction layers and automatic renewal systems that are harder to screw up. But these systems will only help if companies actually use them.
FAQ
What exactly is a security certificate and why does it matter?
A security certificate is a digital credential that uses encryption to verify the identity and legitimacy of software components or servers. In Logitech's case, their certificate was used to verify that different parts of the application could safely communicate with each other. When the certificate expired, the application couldn't verify its own components, so it refused to run. Certificates expire deliberately to force regular renewal and improve security.
Why couldn't Logitech fix this problem automatically for all users?
The same expired certificate that prevented the apps from launching also prevented the automatic update mechanism from working. This created a catch-22 where the infrastructure that would normally deliver the fix was also broken by the same root cause. Users had to manually download and install patches because the application couldn't trust itself enough to run the auto-updater.
Will my Logitech settings come back after I install the patch?
Your settings should be restored if you install the patch without first uninstalling the app. However, if you uninstalled Logi Options+ or G Hub while troubleshooting the problem, your settings files were deleted and cannot be recovered by the patch. Logitech specifically warned against this because reinstalling and then patching is the safest approach.
Why did this happen to only macOS and not Windows?
The incident was specific to Logitech's macOS applications. While it's possible similar issues could happen on Windows, this particular failure affected macOS because that's where the expired certificate was used. Logitech likely uses different certificate infrastructure on Windows, or the certificate hadn't expired there yet.
What macOS versions were affected and what about older systems?
Logitech provided patches for macOS 13 (Ventura), 14 (Sonoma), 15 (Sequoia), and 26 (Tahoe). Users running older macOS versions were told that fixes would come later. However, Apple only supports the four most recent OS versions with security updates, so running an older macOS version carries broader security risks.
How long was the outage and how many users were affected?
The outage lasted roughly 2-3 days for users who quickly found and installed the patch, but potentially much longer for users who didn't know about the problem or delayed updating. The exact number of affected users isn't public, but Logitech has millions of macOS users worldwide, and the incident trended on social media and tech forums, suggesting hundreds of thousands if not millions were impacted.
Could this have been prevented?
Yes, entirely. Automated certificate renewal systems that are standard industry practice would have prevented this problem. Logitech had the technology and resources to implement such automation. The failure was operational, not technical. The certificate should have been renewed automatically weeks or months before it expired.
What should I do to prevent this from affecting me again in the future?
Keep your applications updated promptly when patches are released. Consider using the macOS App Store version of applications when available, since Apple handles updates automatically. Back up your application settings periodically if the app supports configuration export. Follow tech news sources to learn about widespread issues quickly. And consider filing feedback with companies about the importance of robust update infrastructure.
Why is automatic updating so important?
Automatic updates remove the dependency on users to remember to install patches. Without automatic updates, companies can't guarantee that users are running the fixed version. Some users won't update for weeks or months, leaving them vulnerable. With automatic updates managed by platforms like the App Store, fixes can be deployed to nearly all users within hours.
What does this incident say about software reliability?
It highlights that seemingly small infrastructure problems—like certificate management—can cascade into widespread failures. Modern software depends on many interconnected systems, and failures in foundational infrastructure can break everything built on top of it. Companies that invest in monitoring, automation, and operational excellence are less likely to suffer these kinds of failures.
Conclusion: Learning From Infrastructure Failures
Logitech's certificate expiration failure was in many ways a mundane incident. It wasn't a sophisticated security breach. It wasn't a complex logic error. It wasn't even a system running out of resources or having performance problems. A date on a calendar passed, and a certificate became invalid.
Yet that simple fact cascaded into widespread disruption for thousands of users. Apps wouldn't launch. Settings disappeared. Support tickets piled up. Users had to manually intervene to fix a problem they didn't cause.
What makes this incident instructive is that it's so preventable. The technology to automatically manage certificate renewal exists. The monitoring systems to alert before expiration exist. The procedures to test after renewal exist. Logitech had access to all of these tools. The failure was purely operational.
This pattern repeats throughout the tech industry. Systems fail not because the technology isn't good enough, but because operational discipline is lacking. Someone didn't set up the automation. Someone didn't respond to an alert. Someone didn't test after updating. Someone didn't document the process.
For companies building software, the lesson is clear: invest in infrastructure and operations as seriously as you invest in features. The coolest new feature becomes worthless if your certificate management is so poor that the application stops working.
For users, the lesson is more nuanced. You should understand that the reliability of the software you depend on reflects the operational maturity of the company that makes it. Companies that are transparent about how they handle infrastructure, that proactively communicate about problems, and that fix issues quickly are companies you can trust more.
Logitech's response—while not perfect—was reasonably good by industry standards. They acknowledged the problem, identified the root cause, and released fixes relatively quickly. They were transparent about what happened.
But the incident also serves as a reminder that software infrastructure remains fragile, that operational failures are surprisingly common, and that simple preventive measures can make the difference between an outage and no incident at all.
The next time you hear about a major software failure, look past the technical details. Usually, you'll find a more mundane root cause: something that was forgotten, something that wasn't automated, something that seemed like it would be handled but fell through the cracks.
That's not the fault of technology. That's the fault of human organization and process discipline. And unlike technical problems, which require expertise to solve, organizational problems are solvable with commitment and structure.
Logitech will probably implement better certificate management processes now. They'll likely automate their renewal systems and add more comprehensive monitoring. Not because the technology is new—it's not—but because the failure forced them to prioritize something that was easy to ignore when it was working fine.
That's the expensive lesson of infrastructure failures: sometimes you don't learn about problems until they break in production, affecting real users and damaging trust.
The question for other companies is whether they'll wait for their own certificate to expire, or whether they'll invest in preventing that failure proactively.
Key Takeaways
- An expired security certificate used for inter-process communication broke both Logi Options+ and G Hub on macOS, preventing apps from launching and reverting all user customizations to factory defaults.
- The same expired certificate also broke the automatic update mechanism, forcing users to manually download and install patches instead of receiving automatic fixes.
- Users who uninstalled the app while troubleshooting permanently lost their custom settings because the patch couldn't recover deleted data files.
- Patches were released for the four most recent macOS versions within 24-48 hours, but older operating system versions faced delayed support.
- This incident highlights how operational failures in certificate management remain surprisingly common across the software industry despite mature automation tools being available.
![Logitech macOS Certificate Crisis: How One Mistake Broke Thousands of Apps [2025]](https://tryrunable.com/blog/logitech-macos-certificate-crisis-how-one-mistake-broke-thou/image-1-1767811089580.jpg)



