Nord VPN Teams Up With Crowd Strike: What This Partnership Actually Means
Here's something that happened quietly in the VPN world, but it's actually pretty significant. Nord VPN didn't just add another feature. They partnered with Crowd Strike, one of the most respected names in enterprise cybersecurity, to bring institutional-grade threat intelligence straight into your consumer VPN.
Now, I'll be honest. VPN partnerships sound boring until you understand what's actually happening under the hood. Crowd Strike's threat research team sees attacks across millions of endpoints. They track malware families, ransomware campaigns, and zero-days in real time. That intelligence—the stuff enterprises pay six figures for—is now feeding into Nord VPN's Threat Protection Pro suite.
Why does this matter to you? Because the threat landscape has completely changed. You're not just protecting yourself against generic viruses anymore. Modern attacks are targeted, intelligent, and evolving hourly. Most consumer VPN users have no idea what they're actually facing. Nord VPN and Crowd Strike are trying to fix that.
This partnership represents something I haven't seen much of: a consumer security tool getting real enterprise-level visibility. Let's dig into what changed, why it matters, and whether you should actually care.
Understanding the Crowd Strike-Nord VPN Integration
What Crowd Strike Actually Does
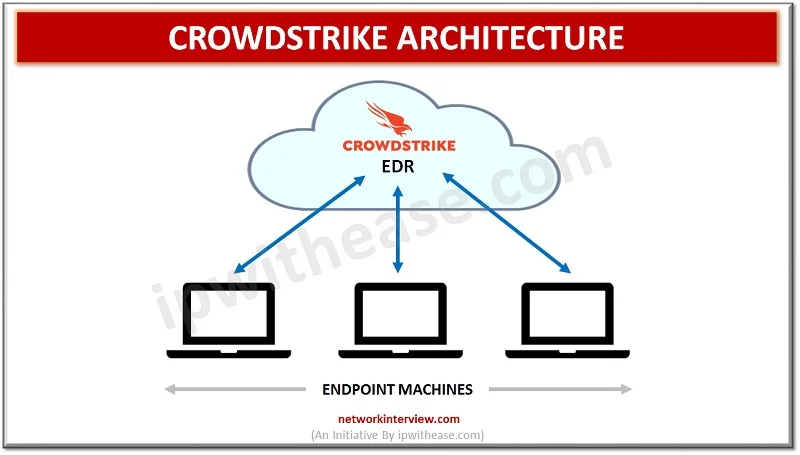
Crowd Strike's Falcon platform isn't your standard antivirus. It's an endpoint detection and response (EDR) system that enterprises deploy across entire networks. Think of it as having a security analyst watching every single computer, every connection, every file execution, 24/7.
The company's Threat Graph processes intelligence from 26 million endpoints. When something suspicious happens on one machine, the AI correlates it against patterns from millions of others. If someone's trying a new attack technique, Falcon spots it across the network before most companies even know they're compromised.
This is institutional knowledge. Enterprise threat intelligence. The kind of data that took Crowd Strike years and billions in research to compile.
How This Intelligence Gets Into Your VPN
Nord VPN's integration taps into Crowd Strike's threat data, but not in the way you might think. Nord VPN isn't running full EDR on consumer devices. That would be overkill and would destroy battery life on mobile.
Instead, they're using Crowd Strike's threat intelligence feeds. Specifically, they're getting access to real-time data about known malicious IPs, phishing domains, and malware signatures. When you connect to Nord VPN, the service checks your traffic against this intelligence.
The system works bidirectionally too. If Nord VPN detects something suspicious happening through its infrastructure, it can contribute that signal back to Crowd Strike's global threat picture. It's not a one-way feed of information.
Why Threat Protection Pro Was Already Useful
Nord VPN's Threat Protection feature existed before the Crowd Strike deal. But here's the reality: it was using threat databases from third-party sources. Good ones, sure, but not in real time.
The problem with static databases is obvious. A phishing domain gets registered at 2 AM. By the time it shows up in a threat feed at 3 AM, thousands of people have already fallen for it. The lag between discovery and distribution matters.
With Crowd Strike's integration, the detection gets dramatically faster. The latency between discovery and your device knowing about a threat shrinks from hours to minutes. In the security world, that's the difference between stopping an attack and becoming a victim.
Security researcher Alex Stamos has talked about this problem for years. Consumer devices are the weakest link in network security, but they don't have access to enterprise threat intelligence. This partnership narrows that gap significantly.
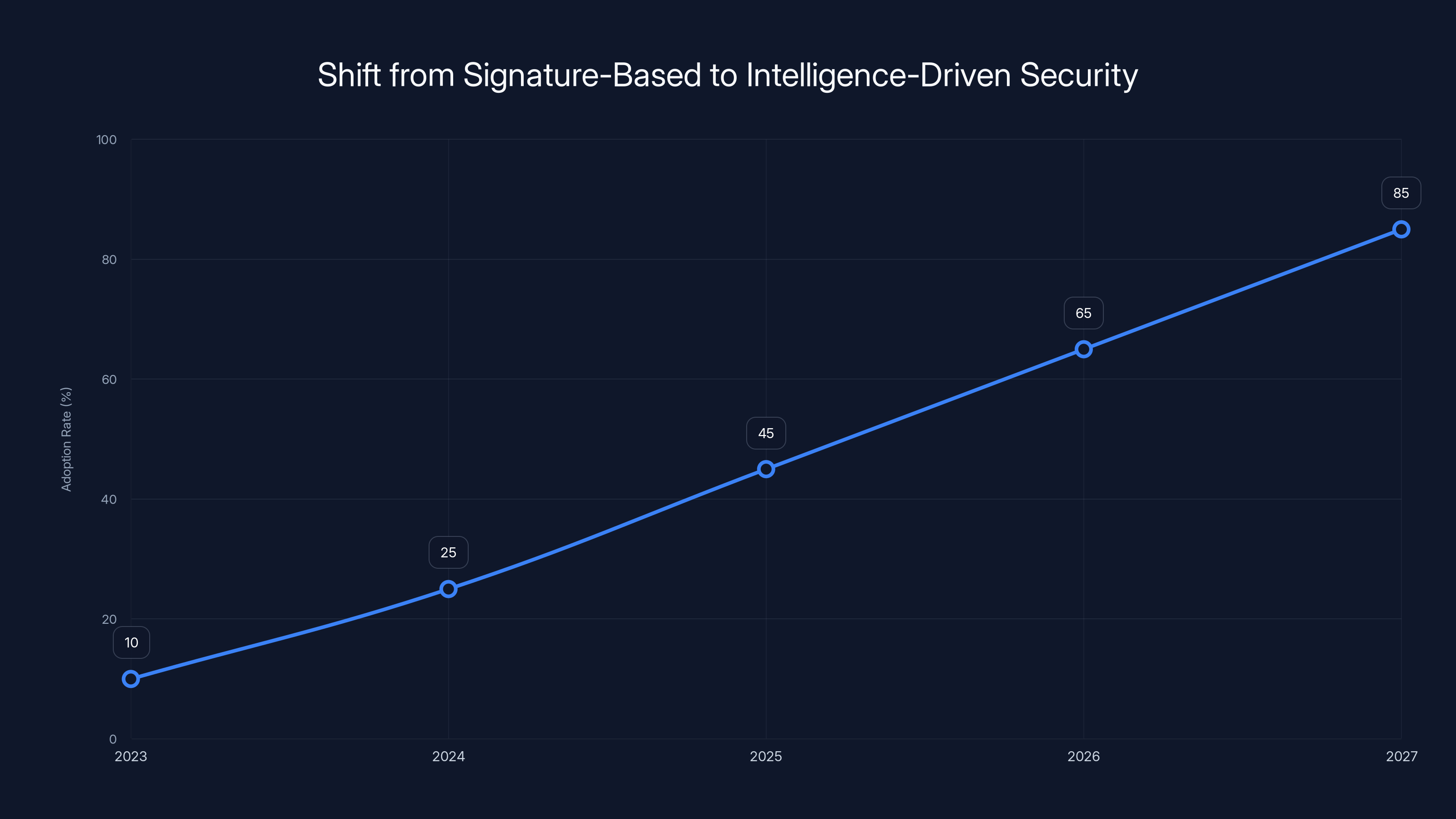
Estimated data shows a significant increase in the adoption of intelligence-driven security in consumer products, reaching 85% by 2027. This trend reflects a shift from traditional signature-based methods.
The Technical Architecture Behind the Partnership
How Real-Time Threat Detection Works
Let's get specific about what's happening technically. When you visit a website with Threat Protection Pro enabled, Nord VPN doesn't just let traffic through. It performs several checks simultaneously.
First, it checks the domain against Crowd Strike's phishing database. This isn't just a list of known bad domains. Crowd Strike's system uses behavioral analysis to detect brand-new phishing sites that mimic legitimate services. They look at SSL certificate patterns, domain registration metadata, and page structure to identify fraudulent sites in minutes.
Second, if you're downloading a file, Nord VPN scans it against malware signatures. But again, it's not comparing against a static list. Crowd Strike's threat intelligence includes zero-day signatures—patterns for attacks that haven't been publicly disclosed yet. Enterprises using Falcon often detect breaches months before public disclosure.
Third, there's IP reputation checking. Crowd Strike tracks which IP addresses are actively involved in attacks. If traffic is coming from or going to a known command-and-control server, Threat Protection Pro blocks it.
The Data Architecture
All of this happens without sending your personal browsing data to Crowd Strike or Nord VPN. This was crucial for the partnership agreement. Here's why: you're connecting to a VPN to hide your activities. The last thing you'd want is to trade privacy to one company (your ISP) for privacy risk to another company (Nord VPN or Crowd Strike).
The architecture solves this through what's called "zero-knowledge" threat detection. Your device gets a local copy of the threat database. When you visit a site, the check happens locally on your device. Only if something is flagged as malicious does Nord VPN learn about it—and even then, it learns the URL or domain, not your identity or context.
Think of it like this: every device has a reference book of "bad places." When you try to go somewhere, your device checks the book first. Only if the destination is in the book does anyone else get notified.
Performance Implications
Here's the concern most people have: won't this slow everything down? Real-time threat checking sounds computationally expensive.
The answer is nuanced. Yes, there's some overhead. You're running additional checks on every domain you visit. But we're talking about 5-15 milliseconds added latency per request. That's barely perceptible.
Nord VPN has optimized this through local processing and smart caching. If you visit the same 50 domains daily (which most people do), those are cached as "safe" after the first check. The subsequent checks take microseconds.
On older devices or slower networks, you might notice something. On modern hardware with standard internet speeds, it's transparent.
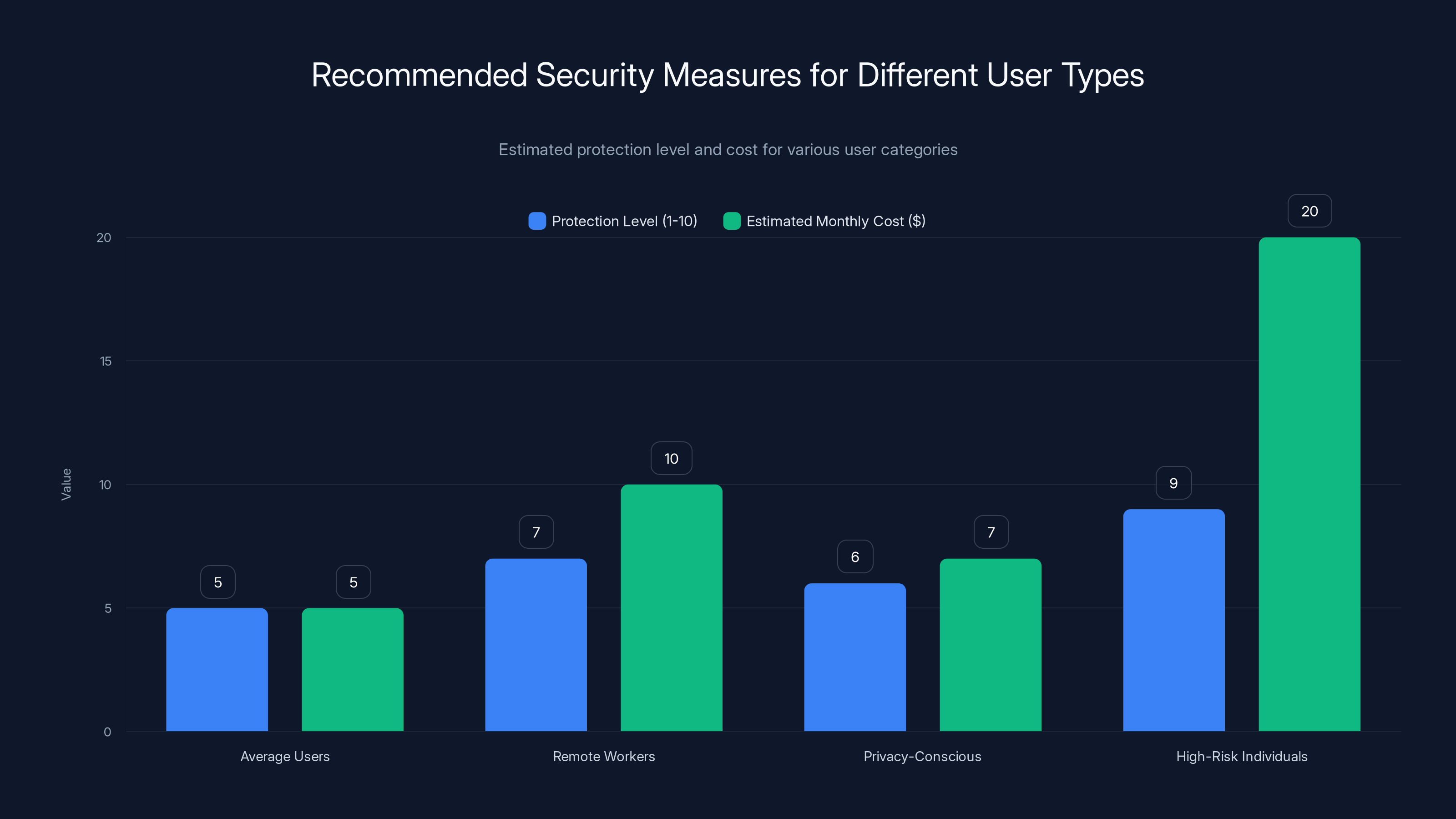
Different user types require varying levels of security measures and incur different costs. High-risk individuals need the most comprehensive protection, while average users can manage with basic measures. (Estimated data)
What Changed in Threat Protection Pro After the Crowd Strike Partnership
New Detection Capabilities
Before Crowd Strike, Nord VPN's threat detection was decent but not exceptional. After the partnership, several new capabilities appeared:
Zero-day malware detection is the biggest one. Crowd Strike's Falcon platform detects attacks using behavioral analysis, not just signature matching. If malware is doing something suspicious—unusual system calls, privilege escalation attempts, lateral movement—Falcon catches it even if the malware is brand new.
Advanced phishing detection improved dramatically. Crowd Strike uses machine learning to identify phishing sites that haven't been reported yet. Most phishing detection uses URL databases. Crowd Strike looks at the actual page content, certificate metadata, and behavioral patterns. This catches phishing kits—tools used to create dozens of identical phishing sites—much earlier.
Ransomware-specific detection is another addition. Crowd Strike's team has analyzed hundreds of ransomware campaigns. They know which IP addresses are known to be part of ransomware infrastructure. If your device tries to connect to one of these IPs, Threat Protection Pro blocks it before the ransomware can phone home to its command server.
Cryptojacking prevention also made the list. Cryptojacking—malware that hijacks your CPU to mine cryptocurrency—is getting more common. Crowd Strike detects the specific behavior patterns of mining malware, even if it's a new variant.
Frequency of Threat Database Updates
This is where the real advantage shows. Before the partnership, threat databases updated weekly or daily at best. With Crowd Strike's integration, updates happen continuously throughout the day.
Crowd Strike's team works on a 24/7 rotation. When they discover a new threat—a phishing campaign, a malware sample, a command-and-control server—they can push that intelligence to the database immediately. Within minutes, Nord VPN clients get the update.
For consumers, this means you're protected against threats hours before they hit the news. Most people only learn about a major phishing campaign after it's already affected thousands. With this partnership, you're defended before it becomes a news story.

Pricing, Plans, and What You Actually Get
Where Threat Protection Pro Fits in Nord VPN's Lineup
Nord VPN's pricing structure has multiple tiers, and Threat Protection Pro is included differently depending on which plan you choose.
On the basic Standard plan, you get the VPN tunnel. That's it. You're anonymizing your traffic and encrypting your connection. That's valuable, but it doesn't protect against malware or phishing.
On the Plus plan (around $5.99/month when discounted), Threat Protection is included. You get the VPN tunnel plus real-time malware and phishing detection. This is where the Crowd Strike partnership adds value.
On the Premium plan (around $11.99/month), you get everything Plus offers, plus additional features like Threat Protection Pro, which includes the deep Crowd Strike integration.
I know what you're thinking: that seems expensive. Fair. But context matters. You're paying for enterprise-grade threat intelligence that would cost your company thousands per year. The retail price of Crowd Strike Falcon starts at enterprise scale only.
What's Included in Each Tier
Threat Protection (Plus plan) includes:
- Basic malware and phishing detection
- IP reputation filtering
- Known-malware blocking
- Limited threat intelligence
Threat Protection Pro (Premium plan) adds:
- Advanced zero-day detection
- Behavioral malware analysis
- Full Crowd Strike threat intelligence feed
- Ransomware-specific detection
- Cryptojacking prevention
- Priority threat response
- Real-time domain reputation updates
The difference isn't marginal. The Pro tier is where the Crowd Strike partnership actually shines. The basic tier is fine for casual users. The Pro tier is for people who take their security seriously.
Free Alternatives and How They Compare
You're probably wondering if you can get this elsewhere for free. Short answer: not really.
Windows Defender is free and decent. It catches known malware through signature matching and some behavioral analysis. But it doesn't have access to Crowd Strike's threat intelligence. It won't catch brand-new phishing campaigns. It's reactive, not proactive.
Chrome and Firefox have built-in phishing detection. They're pretty good actually. But they only protect browsing, not other traffic. If you're using email, messaging apps, or torrenting, they're not helping.
The free version of Malwarebytes catches malware on your device. But again, it's not connected to real-time threat intelligence. It won't prevent you from visiting a phishing site that was registered this morning.
None of these options have the institutional intelligence that Crowd Strike brings. You're not getting enterprise-grade threat detection for free. That was never realistic.
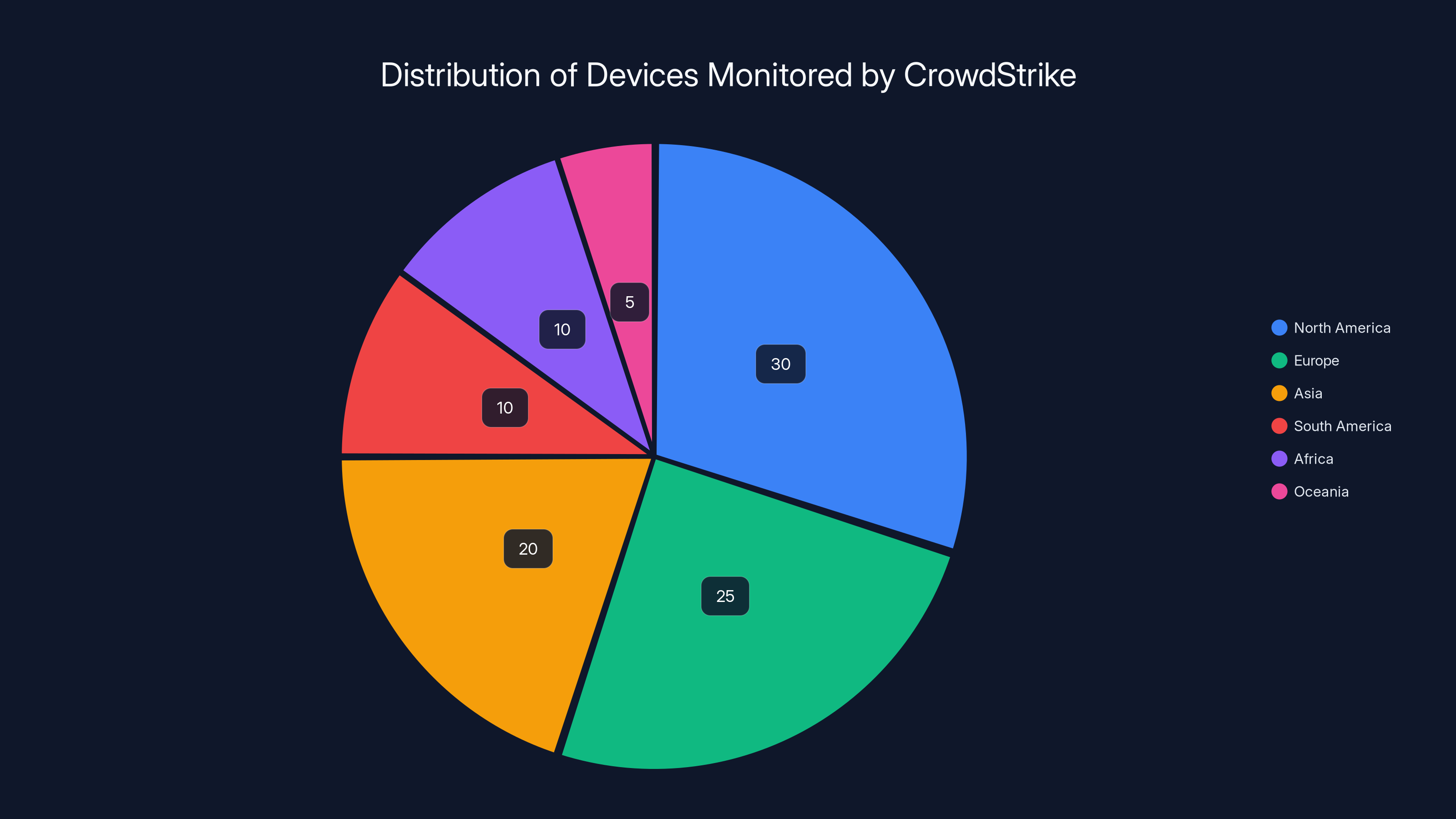
CrowdStrike monitors 26 million devices globally, with the highest concentration in North America and Europe. Estimated data.
Real-World Impact: How This Changes Your Actual Security
Phishing Attack Prevention in Practice
Let's ground this in reality. Last year, a major phishing campaign targeted users of a popular cryptocurrency exchange. Attackers registered domain names that were one character off from the real site. They set up replicas of the login page.
Most users' default protections—Chrome's phishing detection, Windows Defender—missed these sites because they were brand new. The attackers had them live for 6 hours before reporting took them down.
With Threat Protection Pro, what would happen? Crowd Strike's analysts would have flagged these domains within minutes. Not hours. Minutes. They track phishing kit distribution, recognize the patterns of these fake domains, and add them to the threat intelligence feed immediately.
If you were connected to Nord VPN during those 6 hours, your browser would have shown a warning before you could even type your password. The attack would have been completely neutralized against you.
This happens regularly. Crowd Strike's team publishes case studies showing how they prevented breaches before they started. When they integrate that intelligence into your VPN, you benefit from that same speed.
Malware Infection Prevention
Here's a scenario that actually happened: a user downloaded what they thought was a legitimate software tool from a sketchy download site. It was actually malware bundled with a legitimate installer.
Most antivirus software wouldn't have caught this because the installer itself was legitimate. The malware was hiding inside. By the time the user's antivirus detected it, the malware had already executed and installed itself.
With Crowd Strike's behavioral analysis—which Threat Protection Pro now includes—the malware would be flagged the moment it tried to execute. Crowd Strike's system would recognize the specific behaviors: attempting to write to system directories without permission, trying to establish persistence, reaching out to known command servers.
Even if the malware was brand new, these behaviors would trigger detection. You'd be protected against an attack that traditional antivirus would miss.
Ransomware Infrastructure Blocking
Ransomware attacks have two phases. First, the malware infects your system and encrypts your files. Second, it contacts a command server to pay the ransom.
Most people focus on preventing the first phase. But Crowd Strike's partnership adds defense for the second phase. Even if ransomware somehow makes it onto your system, it can't contact its home base. The connection gets blocked.
This matters because ransomware can be dormant. It infects your system, stays quiet for days or weeks, then activates. During that dormancy, Threat Protection Pro is watching for suspicious behavior.
When the ransomware wakes up and tries to contact its command server, the connection is blocked. The attack fails. You never even know it was there.
The Privacy Considerations: What's Actually Being Tracked
How Nord VPN Handles Your Data With Crowd Strike Intelligence
I need to be direct here because this is where a lot of people get nervous. You're connecting to a VPN to hide your activity. Now there's another company—Crowd Strike—in the picture. What's being shared?
The good news: Nord VPN's no-logs policy still applies. They're not logging your browsing history. They're not sending your visited sites to Crowd Strike. Everything is processed locally on your device.
When a threat is detected, only the threat signature gets reported back. If you visit a malicious domain, Nord VPN learns the domain is malicious from your report, but they don't learn that it was you who visited it. Your IP address is not logged. Your device is not identified.
Crowd Strike never sees your personal data. They see threat intelligence from the aggregate detection patterns. Thousands of Nord VPN users visiting malicious domains generates signal, but no personal information is transmitted.
Here's how you can verify this: download Nord VPN's privacy policy and search for "Crowd Strike." They disclose exactly what data is shared. It's minimal. Domain-level threat intelligence and nothing more.
What You're Trading and What You're Gaining
Let's be honest about the trade-off. You're giving Nord VPN and Crowd Strike access to real-time threat detection data from your device. That's slightly more data than a traditional VPN service would see.
What you're gaining is protection against threats that would otherwise infect you. You're trading minimal metadata for actual security.
Whether that trade is worth it depends on your threat model. If you're just casually browsing the web, the risk of infection is low. If you handle sensitive information—work documents, financial data, personal communications—the risk is much higher.
For most people, it's a good trade. For privacy maximalists who reject any data sharing, it's not.
Compliance and Data Residency
One detail that matters for certain users: where is threat intelligence data stored and processed?
Nord VPN operates servers globally, but their infrastructure is primarily in privacy-friendly jurisdictions. Data residency matters if you're in a regulated industry or high-risk country.
Crowd Strike's threat intelligence is centralized in the United States. This is important if you're concerned about US government access to your threat data. Under FISA Section 702 and similar laws, US-based companies are compelled to share certain data with intelligence agencies.
This doesn't mean your personal browsing data is being shared with the NSA. But threat metadata from millions of devices does get aggregated, and that aggregate data could theoretically be requested by US authorities.
If you're in a jurisdiction where this is a concern, you need to know this. It's not a dealbreaker for most users, but it's worth understanding.

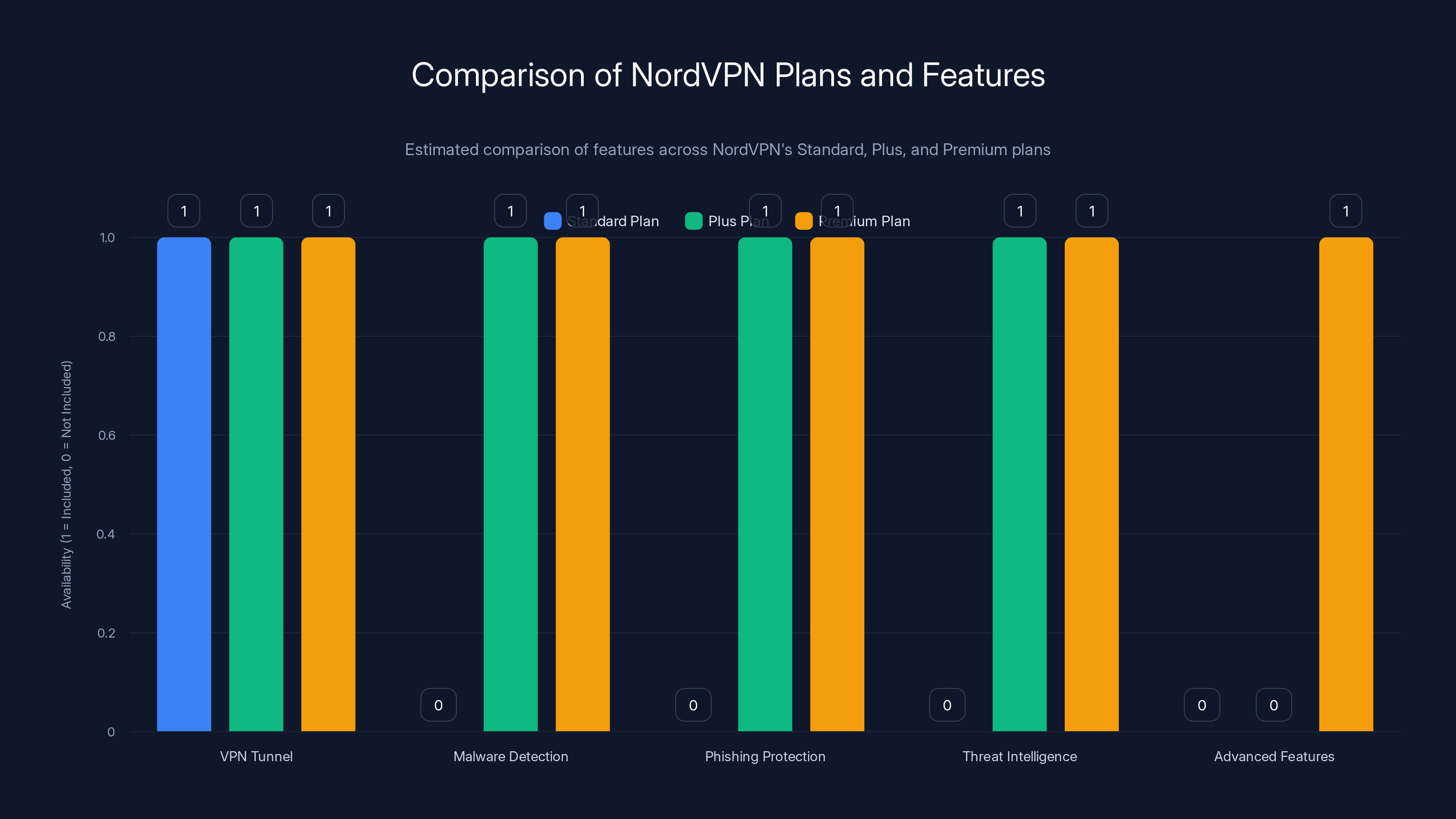
The Premium plan offers the most comprehensive security features, including advanced threat intelligence and protection, compared to the Standard and Plus plans. Estimated data based on feature descriptions.
Comparing This to Other VPN Security Features
How Threat Protection Pro Stacks Against Competitors
Nord VPN isn't the only VPN with threat protection. Let's look at how this partnership actually improves their position.
Express VPN has a feature called "Threat Manager" that filters malware. But it's not integrated with enterprise threat intelligence. It's using third-party threat feeds, not real-time institutional intelligence.
Surfshark includes malware protection. Again, it's competent but not connected to institutional threat intelligence. It's good enough for basic protection but not best-in-class.
Proton VPN focuses primarily on privacy and doesn't have built-in malware detection at all. That's a different philosophy—they believe the VPN alone should handle security.
The Crowd Strike partnership puts Nord VPN ahead in the threat detection arms race. None of the other consumer VPNs have access to institutional-grade threat intelligence. None of them are getting real-time detection data from an endpoint security platform that monitors 26 million devices.
This isn't marketing fluff. This is a genuine technical advantage.
Comparing to Traditional Antivirus
You might be wondering: why use a VPN's threat protection when you already have antivirus?
Good question. Antivirus is your local defense. It scans files, checks executables, monitors system behavior. But it's reactive. It catches threats after they arrive on your system.
Threat Protection Pro is your network-level defense. It stops threats before they reach your system. If you try to visit a malicious domain, it blocks the connection. If you try to download infected files, it stops the download.
They're complementary. Antivirus catches what gets through. Threat Protection Pro prevents things from getting through in the first place.
Having both is better than having either alone. The VPN-based detection is faster because it works at the network level. But local antivirus has deeper visibility into your system.
For best protection, run both. Nord VPN Threat Protection Pro + a good antivirus (like Kaspersky, Bitdefender, or Norton). Don't rely on one defense layer.
Implementation and Getting Started
How to Enable and Use Threat Protection Pro
Setting this up is straightforward. If you're on Nord VPN's Premium plan, Threat Protection Pro is already included.
On Windows or mac OS:
- Open the Nord VPN app
- Click Settings (usually bottom-left or in the menu)
- Find "Threat Protection Pro" toggle
- Enable it
- The feature is now active across all your internet traffic
On i Phone or Android:
- Open the Nord VPN app
- Tap Settings (usually a gear icon)
- Scroll to Threat Protection
- Toggle it on
- You may be asked to enable a VPN profile; allow this
Once enabled, Threat Protection Pro works automatically. You don't need to do anything else. It runs in the background, checking traffic in real time.
Best Practices for Using Threat Protection Effectively
Having the feature enabled is step one. Using it effectively requires a few practices:
Keep it enabled everywhere. Don't just turn it on when you're on public Wi-Fi. Threats exist on your home network too. Keep Threat Protection Pro active 24/7.
Still verify before clicking. This tool prevents most phishing attacks, but it's not perfect. If something feels off about an email or website, trust your gut. Hover over links to see where they actually go.
Keep Nord VPN updated. The threat databases update automatically, but the app itself needs regular updates too. Check the app store monthly for new versions.
Complement with strong passwords. Even if Threat Protection Pro prevents you from visiting a phishing site, weak passwords create risk elsewhere. Use a password manager like 1 Password or Dashlane.
Monitor your accounts. If you do accidentally download malware, you want to catch account compromise quickly. Set up alerts on your important accounts. Check Have I Been Pwned monthly.
Troubleshooting Common Issues
Sometimes Threat Protection Pro blocks legitimate sites. This is rare, but it happens. What do you do?
First, check if it's actually blocked. The app will usually show a notification if something is blocked. Read it carefully. If it says the domain is malicious, trust it. False positives are uncommon.
If you genuinely believe it's a false positive, you can whitelist the domain. Go to Settings > Threat Protection > Manage Exceptions and add the domain.
Be careful with whitelisting though. This is how you can accidentally expose yourself. Only whitelist domains you genuinely trust.
If Threat Protection Pro is slowing your connection significantly (you'd notice this—sites taking noticeably longer to load), you can disable it temporarily. But understand that you're reducing your protection surface.
For mobile users, if battery drain increases significantly after enabling Threat Protection Pro, that's worth noting. It shouldn't drain much battery, but older devices might feel the impact. Consider disabling it on older phones.

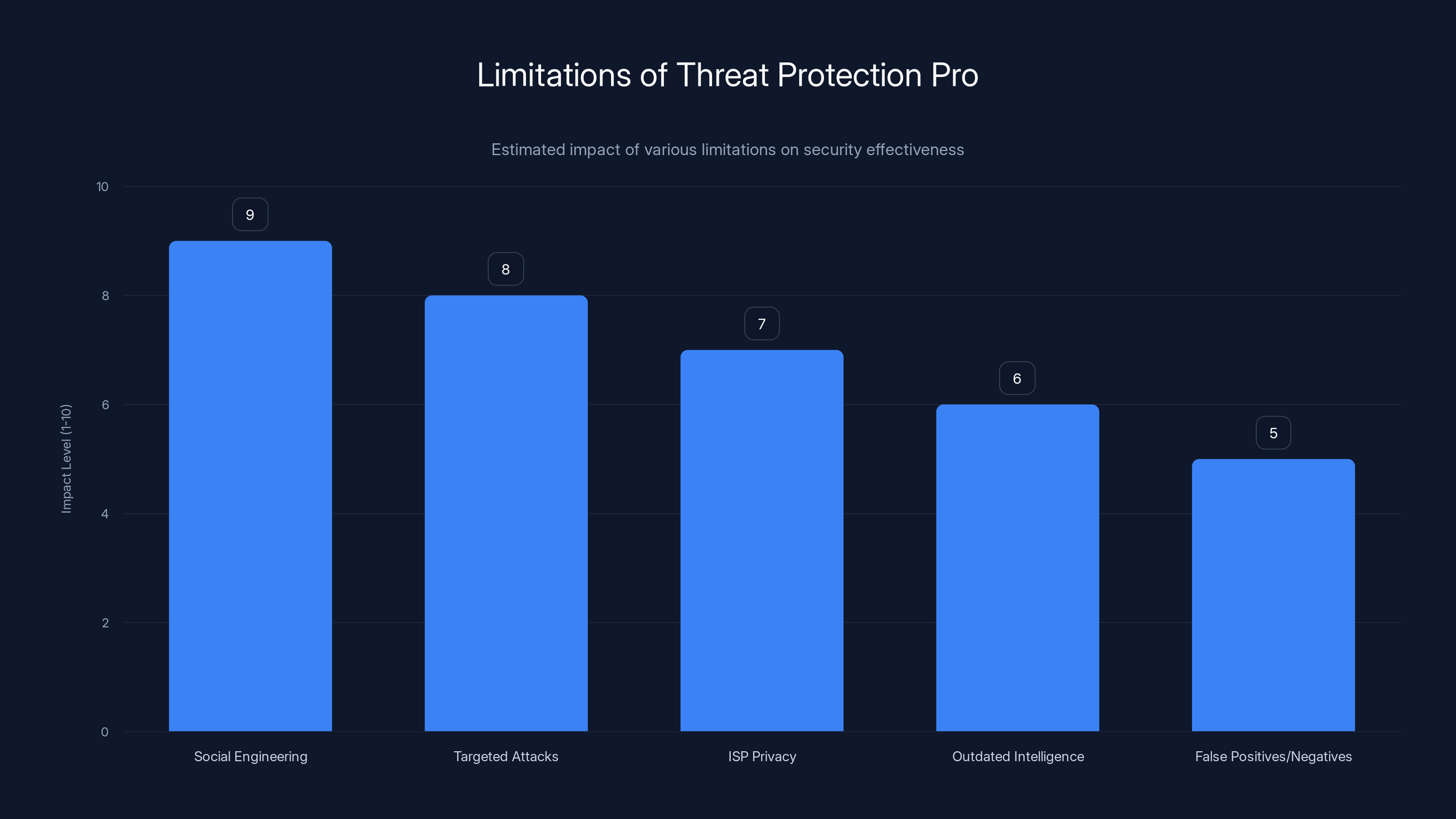
Estimated data shows that social engineering and targeted attacks have the highest impact on security effectiveness, highlighting areas where Threat Protection Pro is less effective.
The Broader Context: Enterprise Security Going Consumer
Why This Partnership Matters for the Industry
This partnership represents something bigger than just Nord VPN and Crowd Strike. It's a sign of enterprise security moving downstream to consumer products.
For decades, enterprise and consumer security were separate worlds. Enterprises had access to institutional-grade threat intelligence and tools. Consumers had basic antivirus software from 10 years ago.
That gap has been widening, which actually increased consumer risk. As attackers became more sophisticated, consumer protections stayed static.
This partnership starts to close that gap. It shows that enterprise threat intelligence can be adapted for consumer use without creating privacy nightmares.
If this works well, you'll see more partnerships like it. Consumers might eventually have access to threat detection that would have been unthinkable a few years ago.
The Emerging Trend of Intelligence-Driven Security
For the past 20 years, security was signature-based. Your antivirus had a database of known malware signatures. If something matched, it was blocked.
This approach works if you're always behind on threats. But modern attacks move too fast for signatures. New malware variants emerge constantly. Zero-days exploit unknown vulnerabilities.
The new approach is intelligence-driven security. You don't just rely on signatures. You monitor for behaviors that indicate an attack. You track threat actors and their infrastructure. You use machine learning to identify patterns.
This is what Crowd Strike does. This is what the partnership brings to Nord VPN.
Over the next 5 years, intelligence-driven security will become the norm. VPNs, antivirus, firewalls—all of them will shift from signature-based to intelligence-based detection.
Companies like Palo Alto Networks, Mandiant, and Trend Micro are already there. This partnership puts Nord VPN in that category for consumer-grade protection.
How This Changes the VPN Market
For years, VPNs competed on speed, server count, and pricing. Nord VPN had more servers. Express VPN was faster. Surfshark was cheaper.
Those metrics still matter, but they're no longer differentiators. Every good VPN is fast enough. Every VPN has servers everywhere.
Now the competition shifts to security features. Nord VPN just moved ahead in that category significantly.
The question is: will other VPNs respond with their own partnerships? Will Express VPN partner with Elastic or Splunk for threat intelligence? Will Surfshark partner with a threat intelligence provider?
If they want to remain competitive, they'll have to. Nord VPN just raised the bar for what a VPN should include.

Potential Limitations and Honest Assessment
What Threat Protection Pro Can't Do
Let's be clear about the limits. This feature is powerful, but it's not a silver bullet.
It can't prevent social engineering. If an attacker tricks you into revealing your password, no amount of threat detection helps. You've voluntarily given them access.
It can't protect against targeted attacks on your accounts. If someone guesses your password, Threat Protection Pro doesn't matter. Use strong, unique passwords.
It doesn't protect your privacy from ISPs. Threat Protection Pro blocks malicious destinations. But your ISP still sees that you're using Nord VPN. If you need privacy from your ISP, the VPN tunnel is what provides that, not threat detection.
It requires updates. Threat Protection Pro depends on current threat intelligence. If your database is three weeks out of date, new threats won't be detected. Keep Nord VPN updated.
It has false positives and false negatives. No security system is perfect. Sometimes legitimate sites get flagged. Sometimes malware slips through. It dramatically reduces your risk, but doesn't eliminate it.
Performance Trade-offs
There's always a trade-off between security and performance. Threat Protection Pro adds overhead.
On modern devices with fast internet, you won't notice. On older devices or slow connections, you might see slight delays.
If performance is critical—you're a gamer with 10ms latency requirements—you might want to disable threat detection for gaming sessions. For everything else, keep it enabled.
The Corporate Dependency Question
Here's a question worth asking: what if Nord VPN or Crowd Strike go out of business? What if their services are compromised?
Nord VPN is owned by Norton Life Lock, a $4 billion company. They're not going anywhere.
Crowd Strike is even bigger. They have a $50+ billion market cap. They're one of the most critical security companies in the world.
But tech companies fail. They get breached. Management makes decisions that harm users. You should never assume any company is permanent or trustworthy forever.
This is why you shouldn't rely on any single company for your security. Use Threat Protection Pro, but also use antivirus, strong passwords, 2FA, and good security practices.
Geographic Limitations
Threat Protection Pro works globally, but there are some nuances.
In countries with strict internet censorship (China, Russia, parts of the Middle East), threat intelligence feeds might be throttled or blocked. You might not get real-time updates.
In countries with strict surveillance laws, you need to know that threat data is being stored somewhere. I mentioned earlier that Crowd Strike's infrastructure is primarily in the US. That matters if you're concerned about government access.
For most users in most countries, these concerns are theoretical. But they're worth knowing about.

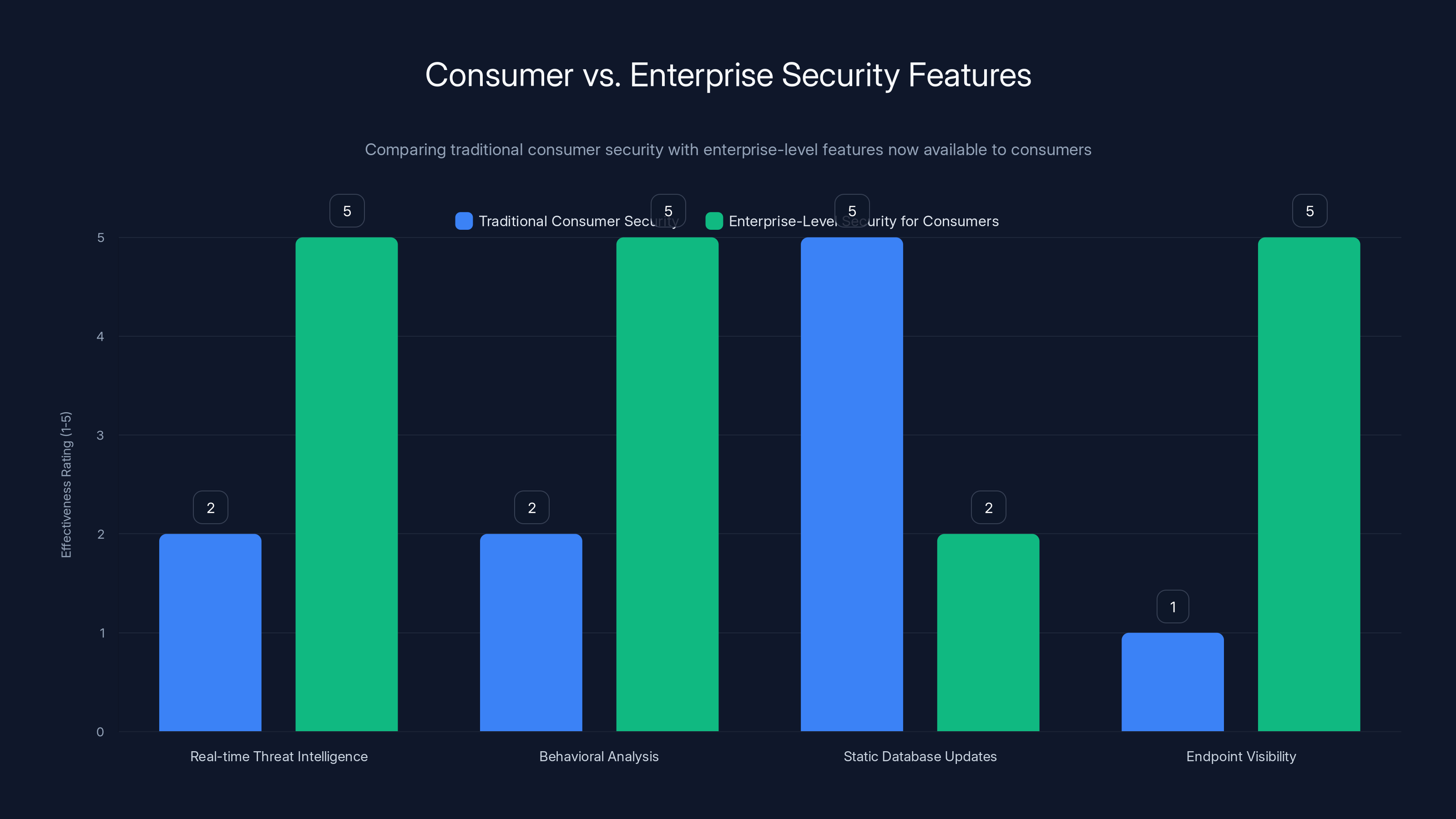
Estimated data shows that enterprise-level security features now available to consumers significantly enhance protection compared to traditional consumer security methods.
Practical Scenarios: When This Actually Saves You
Scenario 1: A Targeted Phishing Campaign
You receive an email that looks like it's from your bank. The domain looks perfect: slight variation of the real domain. The email is personalized with your actual account number.
Without Threat Protection Pro, you might not notice the domain is fake. You click the link and enter your login credentials. The attacker now has your account.
With Threat Protection Pro, when you click the link, your device checks the domain against Crowd Strike's threat intelligence. It's flagged as a known phishing domain. Your browser shows a warning before you can type anything.
The attack is prevented before it succeeds. This happens to millions of people daily. With this protection, you're not one of them.
Scenario 2: Drive-by Download Malware
You visit a news website. Without your knowledge, the site has been compromised. It's serving malware through an ad network.
Normally, you'd download the malware when you load the page. Your antivirus might catch it, or it might execute before detection.
With Threat Protection Pro, when the malware tries to download, your device recognizes the source IP as a known malware distribution point. The download is blocked before it reaches your device.
You never even know the attack happened. You finish reading the news. The website served an ad, and that ad was automatically blocked.
Scenario 3: Command-and-Control Callback
You download what you think is legitimate software. It's actually malware bundled with legitimate software.
The malware installs and runs. It tries to contact its command-and-control server to receive instructions.
Traditional antivirus might not catch the malware because it's new. But Threat Protection Pro blocks the connection to the C&C server. The malware can't communicate with its operators.
Without command instructions, the malware becomes inert. It can't encrypt your files, steal your data, or spread. It's sitting on your system but unable to do anything.
Meanwhile, your antivirus is still scanning. Eventually it finds the malware and removes it. But even if it takes days, the malware can't do harm because it can't communicate.
Scenario 4: Ransomware Lateral Movement
A ransomware actor gains access to your computer through a vulnerability. Before you notice, ransomware starts spreading through your network to file servers, backup systems, and connected devices.
But Threat Protection Pro is monitoring all outbound connections. When the ransomware tries to reach its infrastructure, the connection is blocked.
Without the ability to phone home, the ransom note can't be delivered. The attack is incomplete. Your files aren't encrypted because the malware couldn't establish control.
This is actually more valuable than direct malware detection. Even if ransomware somehow executes, it's useless without external command and control.

Looking Forward: The Future of VPN-Based Threat Protection
Coming Enhancements
This partnership is version 1.0. Future versions will likely include:
Machine learning-based detection that identifies new malware based on behavioral patterns, not just known signatures. The more data Crowd Strike collects, the better their models become.
Cross-device threat correlation that recognizes when one of your devices is compromised and protects your other devices. If your phone gets infected, your laptop gets notified.
Threat actor attribution that identifies which group is attacking you. Some attacks are opportunistic. Others are targeted. Knowing the difference helps you respond appropriately.
Incident response integration that automatically collects forensic data when an attack is detected. If you're breached, Nord VPN could provide evidence to law enforcement or insurance.
Industry-specific threat intelligence that customizes detection based on your profession. A financial analyst gets different threat detection than a teacher.
These features are technically feasible right now. They'll likely appear within 12-24 months.
Competitive Pressure and Market Response
Nord VPN just forced the VPN market to evolve. If other VPNs want to remain relevant, they need similar partnerships.
This benefits consumers. Competition drives innovation. Over the next year, expect to see threat intelligence partnerships announced by other VPN providers.
The VPN market might consolidate around three or four major players, all with institutional-grade threat intelligence. Smaller VPNs without these partnerships might become irrelevant.
Regulatory Considerations
As VPNs become more sophisticated security tools, they'll face more regulatory scrutiny.
Regulators in Europe (GDPR), the US (various state privacy laws), and other regions are asking: what data is being collected? How is it stored? Who has access?
Nord VPN and Crowd Strike have already navigated these questions, but as the partnership matures, new questions will emerge.
Expect to see legislation requiring VPN providers to disclose exactly how threat intelligence works and what data is shared.
For consumers, this is good. More transparency means less chance of abuse.

Actionable Recommendations for Different User Types
For Average Internet Users
If you browse the web casually, check email, and use social media, you need basic protection. Nord VPN Plus with standard Threat Protection is sufficient. It costs about $5/month and provides solid malware and phishing protection.
You don't need Threat Protection Pro. The basic version handles most threats. Save the extra cost.
But do enable it. And keep your browser and OS updated. Those two things together handle 95% of consumer risk.
For Remote Workers and Business Users
If you work from home, handle company data, or access sensitive systems, upgrade to Threat Protection Pro. The extra cost is minimal compared to the risk of a compromise.
Also use a password manager and enable 2FA everywhere. Your company is probably monitoring your security posture anyway.
Consider using a corporate VPN in addition to Nord VPN. Defense in depth matters when you're handling business data.
For Privacy-Conscious Users
If privacy is your primary concern, understand that Threat Protection Pro involves some data sharing. It's minimal and handled carefully, but it's there.
If you want to completely eliminate any data sharing, disable Threat Protection Pro and rely on your OS and antivirus for protection. You'll be less protected against modern threats, but your privacy surface is smaller.
Alternatively, use Threat Protection Pro but route critical activities through a separate system that doesn't have it enabled. Use it for casual browsing, disable it for accessing sensitive accounts.
For High-Risk Individuals
If you're a journalist, activist, political opponent, or someone with genuine adversaries, you need enterprise-grade protection across all layers.
Nord VPN Premium with Threat Protection Pro is baseline. But also invest in:
- A proper endpoint security solution (Kaspersky, Bitdefender)
- Hardware security keys for 2FA
- Air-gapped systems for your most sensitive work
- Regular security audits
High-risk individuals need professionals helping them. This is beyond consumer VPN features.

FAQ
What exactly is the partnership between Nord VPN and Crowd Strike?
Nord VPN integrated Crowd Strike's threat intelligence feeds into its Threat Protection Pro feature. This gives Nord VPN access to real-time malware signatures, phishing databases, and IP reputation data from an enterprise endpoint detection platform that monitors 26 million devices globally. Nord VPN customers using Premium plans now get protection powered by Crowd Strike's institutional-grade threat intelligence.
How does Threat Protection Pro differ from regular antivirus?
Antivirus works locally on your device, scanning files and monitoring system behavior after threats arrive. Threat Protection Pro works at the network level, blocking connections to malicious destinations before your device can be infected. They're complementary: antivirus catches threats after arrival, VPN threat protection prevents them from arriving in the first place. Using both together provides defense-in-depth.
Will Threat Protection Pro slow down my internet connection?
The performance impact is minimal—typically 5-15 milliseconds of latency per request. On modern devices with standard internet speeds, it's imperceptible. Older devices or slow networks might notice slight delays. Nord VPN optimizes this through local caching of threat data and only transmitting threat signatures, not full data packets. Most users see no noticeable speed difference.
Is my browsing data being shared with Crowd Strike?
No. Threat Protection Pro uses zero-knowledge architecture. Your device performs threat checks locally before anything is shared. Only threat intelligence—threat signatures, malicious domain indicators—flows from Nord VPN and Crowd Strike. Your personal browsing history, IP address, and device identity are never shared. If a threat is detected, the threat signature is logged, but not your identity or context.
What does Threat Protection Pro cost, and is it worth it?
Threat Protection Pro is included with Nord VPN's Premium plan, which costs around
Can Threat Protection Pro be bypassed by sophisticated attackers?
Yes, no security system is perfect. Sophisticated threat actors use multiple techniques to evade detection, including zero-days, custom malware, and living-off-the-land tactics. Threat Protection Pro significantly reduces risk but doesn't eliminate it. It's most effective against automated, wide-scale attacks (ransomware, phishing, malware botnets) and least effective against highly targeted attacks from well-resourced threat actors.
Does Threat Protection Pro work on all devices and platforms?
Yes, Threat Protection Pro works on Windows, mac OS, i OS, and Android. Enablement is the same across all platforms through the Nord VPN app settings. Mobile implementations may have slight variations depending on OS restrictions (i OS blocks some deep system monitoring), but core functionality is available everywhere. Some older or low-spec devices might experience battery drain or performance impacts.
What happens if Threat Protection Pro incorrectly blocks a legitimate website?
This is rare but can happen. The app will show a notification if something is blocked. You can review what was blocked and whitelist specific domains in your app settings (Settings > Threat Protection > Manage Exceptions). Be cautious about whitelisting—only whitelist sites you genuinely trust. False negatives (missed threats) are more concerning than false positives (blocked legitimate sites).
How frequently are threat databases updated?
Threat databases update continuously throughout the day. Crowd Strike's threat intelligence team operates 24/7 and pushes updates to the database as new threats are discovered. This means your Nord VPN client gets updated threat intelligence multiple times per day, sometimes multiple times per hour during active campaigns. The latency between threat discovery and your protection being updated is typically minutes, not hours.
Should I use Threat Protection Pro in addition to my antivirus?
Absolutely. They protect against different attack phases. Antivirus catches malware after it arrives on your system. Threat Protection Pro prevents malware from arriving in the first place. Using both creates layered defense. If malware slips past Threat Protection Pro (which is rare), antivirus catches it. If your antivirus misses something, Threat Protection Pro blocks the command-and-control communication.
Is Nord VPN Premium with Threat Protection Pro necessary, or can I use the free tier?
Free tier is rare for Nord VPN—they don't offer much free functionality. The basic free option is their 7-day trial. For ongoing use, you need a paid plan. Nord VPN Plus (

Conclusion: A Watershed Moment for Consumer Security
This partnership between Nord VPN and Crowd Strike marks something significant, even if it doesn't feel like a big deal on the surface.
For 20 years, enterprise and consumer security operated in separate worlds. Enterprises had access to real-time threat intelligence, behavioral analysis, and institutional knowledge. Consumers had antivirus software that relied on static databases updated weekly.
That divide has been shrinking for a few years, but this partnership accelerates it. Consumers can now access threat detection that's powered by visibility into 26 million endpoints. The same intelligence that protects Fortune 500 companies is now protecting individual internet users.
Does this mean you're suddenly completely safe? No. Security is never about absolute safety. It's about reducing risk to acceptable levels. This partnership reduces risk significantly.
What's particularly clever is that Nord VPN didn't try to build their own enterprise threat intelligence. That would take years and billions of dollars. Instead, they partnered with someone who already had it. Now they're distributing it to millions of consumers.
This is the future of consumer security: less reliance on static signatures, more reliance on institutional intelligence and behavioral analysis. More real-time detection, less lag between threat discovery and protection.
If you're using Nord VPN, enable Threat Protection Pro. The cost is minimal compared to the protection it provides. If you're using another VPN, ask them when they're bringing similar capabilities to market.
The security landscape is evolving. This partnership shows what evolution looks like.
Security isn't a set-and-forget thing anymore. It's an arms race. The good news is that for the first time, individual consumers are getting access to the same weapons that enterprises use.
That's progress worth paying attention to.

Key Takeaways
- NordVPN integrated CrowdStrike's threat intelligence to power Threat Protection Pro with real-time detection from 26 million endpoints
- The partnership bridges the gap between enterprise and consumer security—institutional-grade threat data is now available to everyday users
- Threat Protection Pro works at network level to block malicious connections before they reach your device, complementing traditional antivirus
- Premium plan includes Threat Protection Pro with zero-knowledge architecture—your browsing data isn't shared, only threat signatures
- This partnership represents a broader industry trend of intelligence-driven security replacing static signature-based detection
Related Articles
- ExpressVPN Pricing Deals: Save on the Cheapest VPN [2025]
- How Hackers Are Using AI: The Threats Reshaping Cybersecurity [2025]
- Surfshark VPN 87% Off: Complete Deal Analysis & VPN Buyer's Guide [2025]
- Proton VPN 70% Off Deal: Is This Two-Year Plan Worth It? [2025]
- Windows 11 Notepad Security Flaw: What You Need to Know [2025]
- ExpressVPN 81% Off Deal: Complete 2025 Guide [Updated]
![NordVPN & CrowdStrike Partnership: Enterprise Security for Everyone [2025]](https://tryrunable.com/blog/nordvpn-crowdstrike-partnership-enterprise-security-for-ever/image-1-1770981112148.jpg)



