Introduction: Why Post-Quantum Encryption Isn't Enough
You've probably heard the term "post-quantum encryption" thrown around lately. It sounds like a silver bullet for cybersecurity, right? The reality is messier and way more interesting.
Here's the thing: post-quantum encryption gets one job done. It protects your data against quantum computers that don't exist yet. But that's where the story actually begins, not ends.
Last May, Nord VPN rolled out post-quantum encryption across all its apps. Sounds great. But then the company's leadership started talking about something less flashy but far more critical: cryptographic agility. That's the ability to swap encryption methods quickly, continuously, and without breaking user experience.
Why does this matter? Because the cybersecurity landscape doesn't stand still. Vulnerabilities emerge. New attack vectors appear. Standards evolve. A VPN service that locked itself into a single encryption method—even a quantum-resistant one—would be painting itself into a corner.
The companies leading security in 2025 aren't just implementing the latest cryptographic standards. They're building flexible systems that can adapt as threats evolve. They're thinking about "cryptographic agility" the way cloud architects think about scalability or DevOps teams think about deployment speed.
This article breaks down what post-quantum encryption actually does, why it's not the end of the security story, and how organizations are preparing for a future where cryptographic methods might need to change mid-stream. We'll explore the technical foundations, the real-world implications, the industry challenges, and the tools (including Runable) that help teams automate security workflows.
By the end, you'll understand why the smartest security teams are thinking beyond "secure encryption" to "secure, adaptable encryption."
TL; DR
- Post-quantum encryption protects against future quantum threats but represents just one layer of modern security architecture
- Cryptographic agility is the real innovation, allowing systems to swap encryption methods without service interruption
- Nord VPN's 2026 roadmap focuses on building certification frameworks and industry standards for quantum-safe VPN practices
- NIST finalized post-quantum cryptography standards in 2024, giving organizations concrete algorithms to implement
- Legacy encryption methods are becoming liabilities, not assets, as security standards shift toward hybrid and quantum-resistant approaches

Post-quantum algorithms like ML-KEM and lattice-based methods offer higher security and performance compared to traditional RSA and ECDSA. Estimated data.
What Is Post-Quantum Encryption? The Foundation
Post-quantum encryption isn't some exotic future tech. It's a specific category of cryptographic algorithms designed to resist attacks from both classical computers and theoretical quantum computers.
Let's be precise about what's happening. Current encryption—RSA, ECDSA, and similar systems—relies on mathematical problems that are "hard" for classical computers to solve. Factoring huge numbers, computing discrete logarithms, solving elliptic curve problems. With current hardware, these would take billions of years.
But quantum computers operate differently. They use quantum bits (qubits) that exist in superposition, allowing them to explore multiple solutions simultaneously. Algorithms like Shor's algorithm could theoretically crack today's encryption in hours or days.
Post-quantum cryptography uses different mathematical foundations. Instead of factorization or discrete logarithms, algorithms like ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism) rely on the hardness of lattice problems. These remain difficult even for quantum computers.
The key insight: we don't have practical quantum computers yet. IBM's latest quantum systems have a few hundred qubits, but they're error-prone and require extreme cooling. A cryptographically relevant quantum computer would need millions of stable qubits.
But here's why organizations care now. If adversaries are storing encrypted data today with the intent to decrypt it later—"harvest now, decrypt later" attacks—they could use future quantum computers against today's communications. Your encrypted emails, your VPN traffic, your financial transactions from 2024 could become readable in 2035.
Nord VPN's implementation uses lattice-based algorithms combined with their existing encryption. When you connect, your device performs a handshake that uses post-quantum math. From the user's perspective? Nothing changes. The connection happens faster than it did two years ago, actually.
The U.S. government took this seriously. NIST finalized post-quantum cryptography standards in August 2024, after nearly a decade of evaluation. This wasn't a "nice to have." It was a recognition that quantum threat timelines are uncertain, and preparation takes years.
The Quantum Computing Timeline: How Real Is the Threat?
Let's address the elephant in the room. Quantum computers that can break encryption don't exist. So why panic?
Because cryptographic transitions take forever. SSL/TLS rollouts took years. IPv6 adoption has been happening for 25 years and still isn't universal. Moving every encrypted system on earth to quantum-resistant algorithms? That's a multi-decade project.
Estimates vary wildly. Some security experts predict cryptographically relevant quantum computers could appear between 2030-2040. Others say 2050+. The timeline depends on breakthroughs we haven't had yet.
But here's what we know with certainty: the attackers aren't waiting for quantum computers. They're preparing now.
Imagine you're a nation-state intelligence agency. You have the capability to intercept encrypted communications globally. You know quantum computers will eventually exist. Do you: (A) ignore these communications, or (B) store them and wait for decryption capabilities?
Obviously B. This means traffic from today that appears secure could become readable in 15 years. Financial data, health information, trade secrets, diplomatic cables—all at risk.
For most individuals, this seems abstract. For banks, healthcare systems, governments, and enterprises managing sensitive data with long shelf lives? It's an existential risk.
Major banks and financial institutions started implementing quantum-safe measures years ago. Why? Because a stolen encryption key for a classified document in 2024 could be weaponized in 2040. By that time, the person leaking it might be retired, but the damage persists.
Nord VPN's push toward post-quantum encryption isn't about paranoia. It's about acknowledging that data has lifetime value measured in decades, not months.
The math on this is straightforward. Let's say there's a 10% chance a cryptographically relevant quantum computer emerges in the next 15 years. The cost of preparing now (implementing new algorithms, testing systems) might be $1M for an enterprise. The cost of not preparing, if quantum computers arrive and your data gets compromised? Potentially billions in liability, reputation damage, and regulatory fines.

Implementing quantum-safe encryption incurs costs now, but potential breach costs are significantly higher, making early investment economically sensible. Estimated data.
Post-Quantum Encryption ≠ Complete Security
Here's where the narrative gets important. Post-quantum encryption is a necessary condition for future-proof security, but it's not sufficient.
Think of it this way: you've got a vault with quantum-resistant locks. Impressive. But what about the hinges? The walls? The people who have keys?
Nord VPN's leadership gets this. They've been public about the fact that post-quantum encryption alone doesn't solve every security problem. This is refreshingly honest in an industry that loves silver bullets.
Consider what post-quantum encryption doesn't protect against:
Side-channel attacks: These exploit the physical implementation of encryption, not the math. Timing attacks, power analysis, acoustic cryptanalysis. A brilliant quantum-resistant algorithm can still leak information through how fast it runs or how much power it uses.
Key management failures: Quantum-resistant encryption keys still need secure storage, rotation, and handling. If you lose the keys, the encryption is useless. If you reuse keys, patterns emerge. If keys are compromised at the source, the math doesn't matter.
Protocol vulnerabilities: The encryption algorithm is one component. How it's used matters enormously. Weak random number generation, poor authentication, insecure key exchange protocols—these can undermine even perfect encryption.
Zero-day exploits: New vulnerabilities in encryption implementations appear regularly. OpenSSL, GnuTLS, and similar libraries have had critical flaws discovered years after deployment. Post-quantum algorithms will be implemented in code, and code has bugs.
Legal/regulatory requirements: Some jurisdictions have specific encryption requirements. A system might be mathematically secure but legally non-compliant.
This is why Nord VPN isn't just deploying post-quantum encryption and calling it done. The company is thinking about the entire ecosystem—certification, standards, testing, validation.
Cryptographic Agility: The Real Innovation
Post-quantum encryption is the what. Cryptographic agility is the how.
Here's the scenario: it's 2027. Researchers discover a weakness in one of the NIST-approved post-quantum algorithms. Not a critical break, but enough to recommend moving to a different algorithm. What happens?
Companies with rigid cryptographic architectures have a problem. They've baked one algorithm into firmware, protocols, and infrastructure. Changing it requires updates, testing, rollouts, potential compatibility issues.
Companies with cryptographic agility? They flip a switch. New connections use the updated algorithm. Existing connections gradually migrate.
Cryptographic agility means several things:
Algorithm negotiation: When two systems connect, they talk about which encryption to use. Like how HTTPS clients and servers negotiate TLS versions and cipher suites. If both support multiple quantum-resistant algorithms, they pick the best one.
Hybrid encryption: Running multiple encryption schemes simultaneously. Your VPN connection might use classical RSA for some purposes and lattice-based encryption for others. If one breaks, you're not completely exposed.
Version management: Being able to support old and new encryption side-by-side during transitions. Users on outdated apps still connect, but new apps get better security.
Runtime switching: Changing encryption parameters without restarting connections. Imagine a VPN that periodically renegotiates its encryption, introducing new keys and algorithms continuously. An attacker intercepting traffic would see constantly shifting cryptographic methods.
Nord VPN's roadmap for 2026 explicitly includes "cryptographic agility frameworks." This is significant because it suggests the company is thinking architecturally, not just tactically.
From a technical standpoint, implementing cryptographic agility is hard. It requires:
- Modular encryption implementations that can be swapped in and out
- Protocol negotiations that support multiple algorithms
- Testing pipelines that validate compatibility across versions
- Documentation clear enough that developers understand which algorithms are safe in which contexts
- Monitoring systems that detect when algorithms are failing in the field
For a VPN service, it's even harder because you have millions of clients across different devices, operating systems, and app versions. Changing encryption globally could break older clients if not handled carefully.
But this is exactly where forward-thinking companies are headed. Security isn't a fixed target anymore. It's a moving one.
The companies building systems with cryptographic agility now will have a massive advantage when (not if) cryptographic standards shift. They'll adapt. Others will scramble.
NIST's Post-Quantum Cryptography Standards: What Was Approved?
For years, the cryptographic community debated which algorithms could best resist quantum attacks. NIST's Post-Quantum Cryptography project ran a competition. Researchers worldwide submitted algorithms. NIST evaluated them against real-world attack scenarios.
In August 2024, NIST finalized its recommendations. Three algorithms got the green light:
ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism): This is the workhorse. It's based on lattice problems—specifically, the Learning With Errors problem. The math: you've got a matrix of numbers, and you're hiding a secret by adding small errors. Recovering the secret requires solving the lattice problem, which even quantum computers struggle with. ML-KEM comes in three variants with different security levels. Performance is excellent—key establishment happens in microseconds on modern hardware.
ML-DSA (Module-Lattice-Based Digital Signature Algorithm): Digital signatures prove you created a message without revealing your private key. ML-DSA does this using lattice math. Signature sizes are larger than classical DSA, but still practical. Trust infrastructure—certificate authorities, code signing, authentication protocols—all rely on digital signatures. Having a quantum-resistant alternative is crucial.
SLH-DSA (Stateless Hash-Based Digital Signature Algorithm): This one's interesting. It's not lattice-based; it uses hash functions. Hash functions are already considered quantum-resistant (quantum computers only provide a square-root speedup). SLH-DSA generates signatures by hashing repeatedly. The downside: signatures are large (about 4KB). The upside: security is based on a very well-understood mathematical problem.
NIST also identified four other algorithms for standardization in the near future, including Kyber and Dilithium variants for different use cases.
Why lattice-based algorithms? Several reasons:
- Performance: They're fast. Key generation, encryption, decryption—all happen with acceptable overhead.
- Security: The underlying problems (Learning With Errors, Module Learning With Errors) are mathematically well-studied. No known attacks, even from quantum computers.
- Compatibility: Lattice algorithms work with existing infrastructure. You don't need to rebuild the entire internet; you just swap the cryptographic primitives.
- Flexibility: You can tune parameters to trade off security and performance. Higher security = larger keys and slower operations, but the scaling is predictable.
Nord VPN's implementation uses lattice-based encryption from this NIST-approved set. This wasn't a guess. NIST spent over a decade validating these algorithms against theoretical and practical attacks.
The significance: organizations can now implement post-quantum encryption with confidence they're using vetted, battle-hardened algorithms. Not experimental stuff. Not proprietary solutions. Open standards that have survived intense scrutiny.
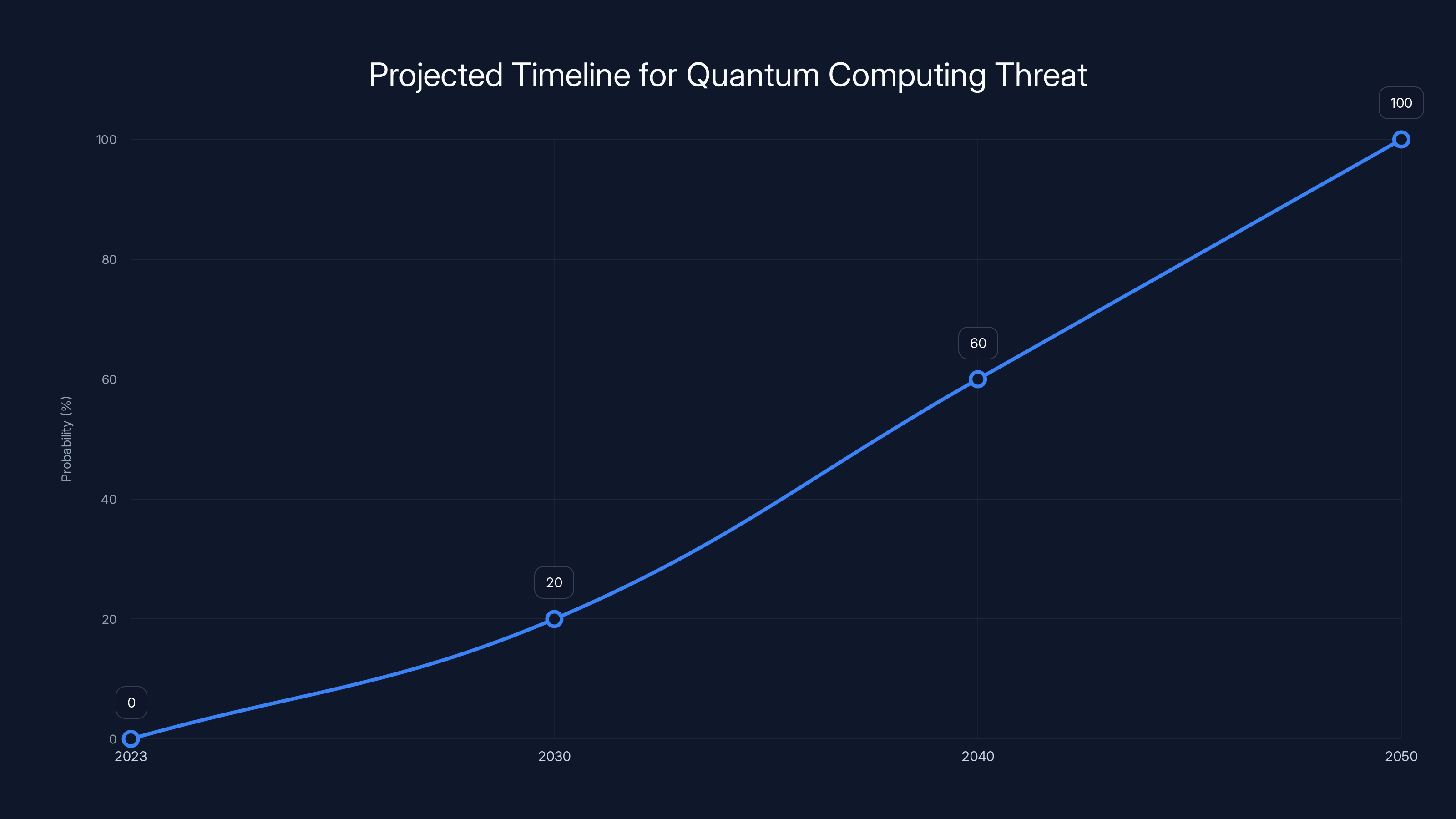
Estimated data shows increasing probability of cryptographically relevant quantum computers emerging between 2030 and 2050.
How VPNs Implement Post-Quantum Encryption
Let's get technical. How does a VPN service actually deploy post-quantum encryption?
Start with the handshake. When you launch a VPN app and connect to a server, several things happen:
1. Client-Server Negotiation: Your device says, "I support post-quantum encryption via ML-KEM and classical RSA." The server responds, "Great, I support both too. Let's use ML-KEM." This negotiation happens over an unencrypted channel, but it doesn't matter because it's only deciding which encryption to use, not revealing secrets.
2. Key Establishment: The server generates an ML-KEM key pair (public and private keys). The public key is sent to your device. Your device generates a random secret, encrypts it with the server's ML-KEM public key, and sends the ciphertext back. Both sides now share a secret that only they can decrypt. This happens in milliseconds.
3. Session Key Derivation: The shared secret from ML-KEM is run through a hash function to derive actual encryption keys. A client-to-server key, a server-to-client key, and keys for authentication and integrity checking.
4. Tunnel Encryption: All your traffic—browsing, streaming, torrenting—is encrypted with these keys and passed through the VPN tunnel.
5. Rekeying: Periodically (typically every hour or after a certain amount of data), new keys are negotiated and the process repeats. This limits how much data an attacker can intercept even if they break one key.
What's different from classical VPN encryption? Mainly the math in step 2. Instead of RSA or ECDH (elliptic curve Diffie-Hellman), you're using ML-KEM. The security properties are different—resistant to quantum attack—but the overall architecture is identical.
Performance impact? Surprisingly minimal. ML-KEM is actually faster than RSA key establishment because lattice operations are less computationally expensive. Bandwidth impact? Minimal. ML-KEM public keys are a few kilobytes; RSA keys are similar sizes.
Nord VPN's implementation handles backwards compatibility intelligently. Older app versions that don't support post-quantum encryption still work, but they negotiate classical encryption. New apps default to quantum-resistant methods. The transition happens gradually, not as a hard cutoff.
Behind the scenes, Nord VPN's infrastructure had to be updated:
- VPN servers need to support ML-KEM key generation and decryption
- The protocol parsing layer needs to understand post-quantum handshakes
- The authentication system needs to work with quantum-resistant signatures
- Monitoring and logging systems need to track which algorithms are in use
- Testing frameworks need to validate that both classical and quantum-resistant paths work correctly
For a company operating hundreds of thousands of VPN endpoints globally, this is a massive engineering undertaking. But it's necessary.
Industry Adoption: Who's Moving to Quantum-Safe Encryption?
Post-quantum encryption isn't Nord VPN-specific. It's an industry-wide shift.
Microsoft has been deploying quantum-resistant algorithms in Azure and Active Directory. Google is implementing post-quantum cryptography in its infrastructure. IBM offers quantum-safe cryptography services.
Why the rush?
Regulatory pressure: Governments are mandating quantum-safe transitions. The U.S. government issued guidance in 2022 that federal agencies must transition to post-quantum cryptography by 2030. Other nations followed. When governments mandate something, enterprises listen.
Insurance and compliance: If a company gets breached and it's discovered they didn't implement available quantum-resistant measures, regulators and insurance companies won't be sympathetic. Compliance frameworks increasingly require it.
Talent and recruitment: Modern security engineers expect organizations to stay current with cryptographic standards. If your company is still using deprecated encryption, recruiting becomes harder.
Competitive advantage: Companies that can credibly claim quantum-safe infrastructure have a marketing advantage, especially in enterprise sales.
Adoption varies by industry:
Finance: Fastest to adopt. Banks handle data worth billions. Quantum threats are existential. Most major financial institutions have post-quantum pilots or deployments.
Healthcare: Also rapid. Healthcare data has decades-long value. Patient information from 2024 could be used for fraud or blackmail in 2044. Compliance standards like HIPAA increasingly reference quantum readiness.
Telecommunications: Telecom providers are implementing it because they're infrastructure, and infrastructure needs to last decades. A 5G network deployed today might operate for 20 years.
Government and defense: Universal adoption. Classified information needs to stay classified for decades or centuries. Quantum threats are treated as strategic risks.
Consumer tech: Slower adoption. Consumer apps have shorter lifespans. Users expect updates frequently. But forward-thinking companies like Nord VPN are deploying it anyway because it's the right long-term move.
Startups: Mixed. Some are crypto-focused and implement it day-one. Others think, "We'll deal with it when we're bigger." That's probably a mistake.
The adoption curve looks like other security transitions. Early adopters (banks, government) moved fast. The middle (enterprises, mid-size tech) are moving now. Late adopters (small businesses, legacy systems) will move only when forced.
But here's the interesting part: once adoption hits 50%, the pressure becomes irreversible. You can't use weak encryption if your competitors use strong encryption and customers notice.
The Challenges of Transitioning to Quantum-Safe Encryption
Sound simple? It's not. Transitioning cryptographic infrastructure is hard.
Consider the scale. There are billions of devices, servers, and systems using classical encryption. Every one needs to be updated or replaced. This isn't a software patch; it's an architectural change.
Legacy system compatibility: Your 10-year-old IoT device can't download new cryptographic libraries. Your embedded system is locked down. Your old payment terminals have RSA keys burned into firmware. These systems can't be easily updated, but they're still in use. Hybrid encryption helps—you support both old and new—but it adds complexity.
Certificate revocation: Today's public key infrastructure uses certificate authority hierarchies. Certificates are signed with RSA or ECDSA. To transition to quantum-safe, you need to re-sign everything with quantum-resistant digital signatures. That's millions of certificates globally.
Key storage and rotation: Classical encryption keys are well-understood and have mature storage solutions. Quantum-resistant keys are larger and have different performance characteristics. Your hardware security module might not be optimized for lattice-based keys.
Testing burden: Every application, system, and protocol needs testing to ensure post-quantum encryption works correctly. This requires setting up test environments, writing tests, and validating across multiple devices and OS versions. For a company like Nord VPN with millions of users, this is a monumental task.
Performance overhead during transition: Hybrid encryption (running both classical and quantum-resistant algorithms) has overhead. You're doing extra computation, using more bandwidth, and introducing latency. During the transition period, everyone pays this cost.
Ecosystem immaturity: Post-quantum cryptography is new. Tools, libraries, and best practices are still solidifying. You'll encounter bugs, incompatibilities, and edge cases that classical encryption solved years ago.
Algorithm selection uncertainty: NIST approved several algorithms, but different use cases might prefer different ones. You have to decide: are we an ML-KEM organization or an SLH-DSA organization? And what if NIST deprecates one later?
Cost: Implementing, testing, and deploying new cryptography across an infrastructure costs millions for large organizations. Smaller companies might struggle to afford it.
Staff expertise: Your team knows RSA and ECDSA. Most don't understand lattice-based cryptography. You need training, hiring, or consulting to close the gap.
Nord VPN's public commitments around cryptographic agility are their way of saying: we're acknowledging this is complex, and we're building systems that can adapt as we learn more.
This is the right approach. Perfect is the enemy of good. Rather than waiting for 100% standardization and certainty, organizations should be deploying quantum-resistant encryption now, with the understanding that they'll need to update and improve their approaches as the field matures.

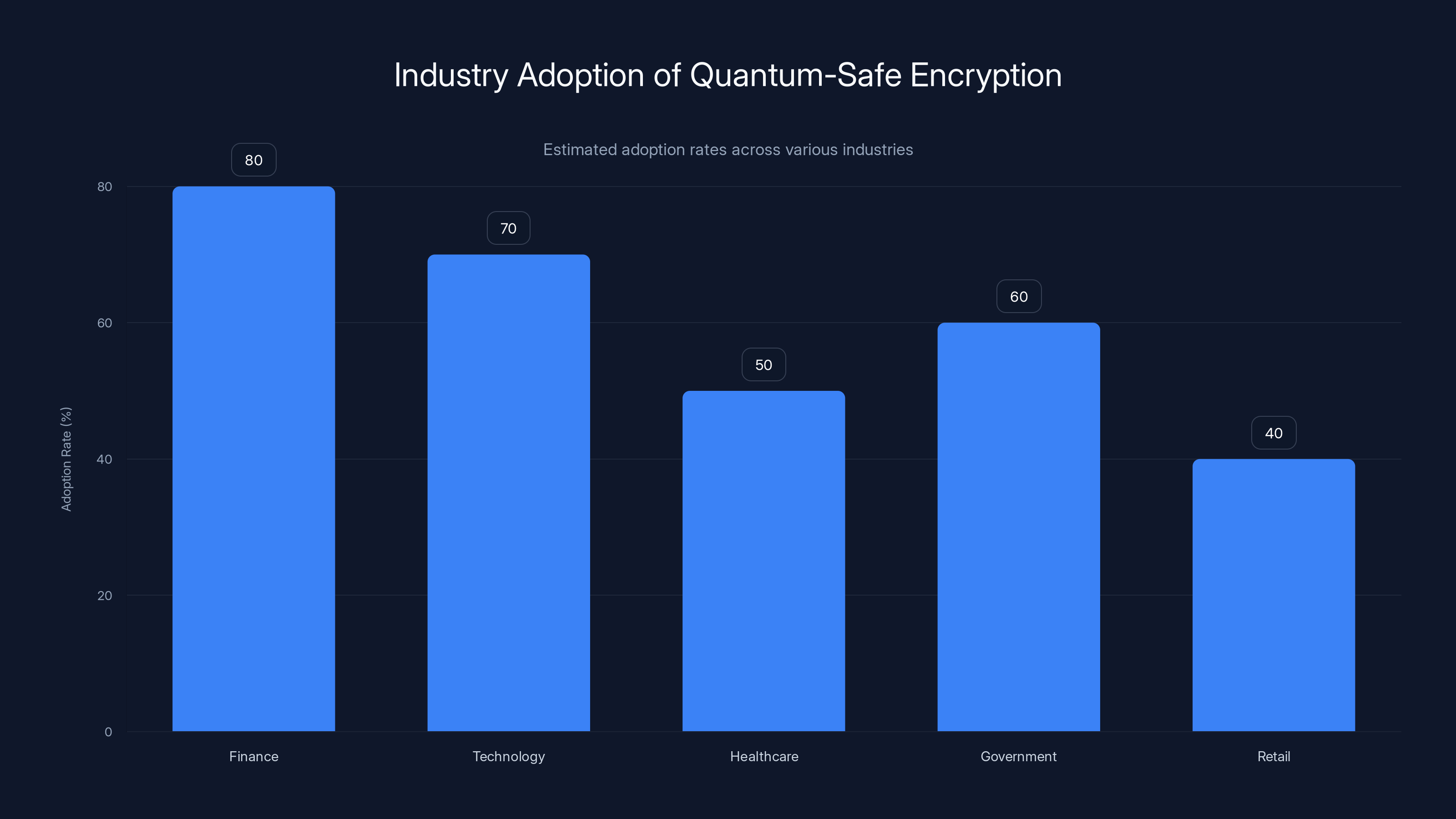
Finance leads in adopting quantum-safe encryption with an estimated 80% adoption rate, driven by the high value of data and regulatory pressure. Estimated data.
Nord VPN's 2026 Roadmap: What's Coming?
Nord VPN has been remarkably transparent about its future plans. The company isn't just implementing post-quantum encryption and moving on. It's working on larger structural improvements.
The 2026 roadmap includes several initiatives:
Certification frameworks for quantum-safe VPNs: Currently, there's no independent certification standard for "quantum-safe VPNs." Nord VPN is working with industry partners and standards bodies to create one. This would be similar to how you can certify a system as "FIPS 140-2 compliant" or "PCI DSS certified." Having a quantum-safety certification would let users and enterprises verify claims independently.
Open-source cryptographic libraries: Rather than building everything in-house, Nord VPN is contributing to and using open-source cryptographic implementations. This makes code auditable and lets the broader security community validate implementations. It's the right move—closed-source encryption is inherently suspicious.
Documentation and developer resources: Making it easy for other developers to implement quantum-safe encryption in their own applications. This speeds industry adoption and raises the overall security baseline.
Hybrid encryption by default: Moving to a model where all VPN connections use both classical and quantum-resistant encryption simultaneously. This provides defense-in-depth—an attacker would need to break both methods to compromise your traffic.
Regular algorithm evaluation: Periodically reviewing cryptographic choices and preparing to swap algorithms if new vulnerabilities emerge or standards shift. This is cryptographic agility in practice.
Quantum-safe DNS: Extending quantum-resistant encryption beyond VPN tunnels to DNS queries. Your DNS requests are currently vulnerable to interception. Quantum-safe DNS would protect those as well.
Transparent reporting: Publishing annual reports on their cryptographic implementations, including any issues discovered and how they were addressed. Transparency builds trust in a way marketing copy never can.
These aren't flashy features that users will see in the app. But they're foundational. They're the difference between deploying encryption and building a cryptographically secure system that can adapt over time.
Why is Nord VPN thinking this far ahead?
Partly, it's business strategy. A VPN company that's known for quantum-safe infrastructure has a competitive moat. It's hard to fake cryptographic security; enterprises verify with independent audits.
Partly, it's the right thing to do. People trust Nord VPN with their traffic. Honoring that trust means not just keeping current but staying ahead of threats.
Partly, it's forward-thinking leadership. The company's executives understand that security moves in cycles. RSA dominated for 30 years. Post-quantum algorithms will too, for a while. But eventually, something else will be necessary. Building systems that can adapt is smarter than betting on one cryptographic method.
Practical Implications: What This Means for Users
You don't need to understand lattice-based cryptography to benefit from post-quantum encryption. But it's useful to know what's actually happening.
For casual VPN users: Minimal change. You launch the app, connect, browse. The security behind the scenes is better, but the experience is the same. Eventually (in a few years), all apps will default to post-quantum encryption, and classical-only encryption will be phased out.
For enterprise security teams: Significant responsibility. Your organization needs to audit VPN vendors, understand their cryptographic choices, and plan transitions. If a vendor doesn't have a quantum-safe roadmap, that's a red flag. You should be asking, "What's your plan for post-quantum encryption?" when evaluating any security tool.
For researchers and cryptographers: This is exciting. New mathematical foundations, new optimization challenges, new attack vectors to explore. Post-quantum cryptography will keep security researchers employed for decades.
For IoT and embedded systems: Challenging. Quantum-safe algorithms have larger keys and different performance characteristics. Devices built for classical encryption might not have the storage or computational power for post-quantum equivalents. This is a real technical constraint, not a marketing excuse.
For data archivists and long-term storage: Critical. If you're storing data that needs to remain confidential for 20+ years, post-quantum encryption isn't optional. You can't encrypt sensitive documents with classical methods and expect them to remain secure in 2045.
From a user perspective, the key takeaway is: good VPN services are evolving. They're not resting on current security standards. They're preparing for an uncertain future. That's the kind of company you want handling your internet traffic.

The Broader Security Ecosystem: Where Post-Quantum Fits
Post-quantum encryption is one piece of a larger security puzzle.
Think about the attack surface for a VPN connection:
- Encryption in transit: Protected by post-quantum encryption (good)
- Encryption at rest: Your VPN provider's servers might store logs or metadata. Are those encrypted? With what algorithms? This is separate from VPN tunnel encryption.
- Authentication: How do you verify you're connecting to the real Nord VPN servers and not a man-in-the-middle? This typically uses certificate-based authentication, which also needs to be quantum-safe.
- DNS: Your DNS queries ("what's the IP for google.com?") are often unencrypted. Even with a VPN, your ISP or network provider can see what sites you're visiting. DNS over HTTPS or DNS over TLS helps, but those also need quantum-resistant encryption.
- Metadata: A VPN encrypts your traffic, but metadata (when you connect, how much data you transfer, which servers you use) can still leak information. A sophisticated adversary can infer activity patterns from metadata alone.
- Server security: If VPN servers are compromised, encryption doesn't matter. The stored encryption keys can be stolen. Server security is a separate concern from encryption algorithms.
- User device security: If your laptop is compromised with malware, no VPN will help. You're already exposed before encryption happens.
- Protocol vulnerabilities: Even with perfect encryption, weaknesses in the protocol (how encryption is used) can leak information. This is where cryptographic agility becomes important.
Post-quantum encryption addresses part of the problem—the mathematical strength of the encryption algorithm. But it doesn't solve everything.
This is why Nord VPN's roadmap includes more than just algorithm updates. It includes architectural improvements, transparency, and continuous validation. A holistic approach to security.
For organizations evaluating security tools, this is an important evaluation criterion. Is the vendor thinking about encryption algorithms in isolation, or are they thinking about cryptographic security holistically?
The vendors thinking holistically will be the ones that don't get breached because of a weak encryption variant in their DNS implementation.
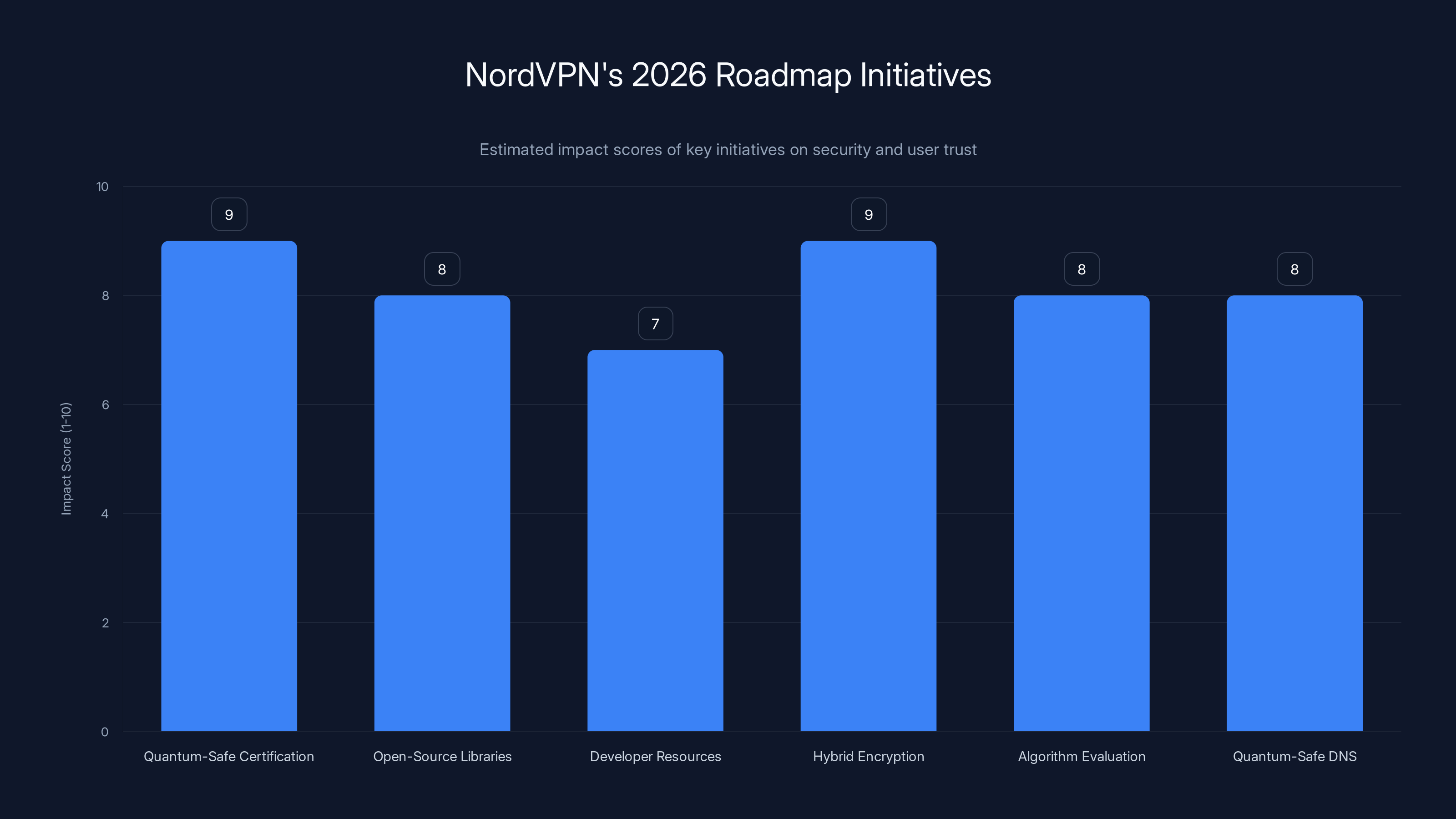
NordVPN's 2026 roadmap initiatives are projected to significantly enhance security and user trust, with quantum-safe certification and hybrid encryption scoring the highest. Estimated data.
Automating Cryptographic Compliance with Modern Tools
Managing cryptographic security across an organization is complex. Keys need to be generated, rotated, stored, and eventually retired. Configurations need to be validated. Compliance needs to be tracked and reported.
This is where automation becomes critical.
Platforms like Runable help security teams build automated workflows for cryptographic management. For example:
Automated key rotation: Instead of manually rotating encryption keys (which is error-prone and often delayed), Runable can orchestrate the process. New keys are generated, old keys are securely archived, systems are updated, and compliance is logged—all without human intervention.
Configuration auditing: Regularly scan systems to verify they're using approved cryptographic algorithms. If someone accidentally reverts to classical encryption or uses a deprecated algorithm, automated alerts notify the team.
Compliance reporting: Generate reports on cryptographic compliance for auditors and regulators. Instead of manually collecting data from dozens of systems, automation aggregates it and produces polished reports.
Protocol upgrades: When a new encryption standard is approved, automation helps roll it out across infrastructure. Test it in staging, deploy it to production, monitor for issues—coordinated across hundreds or thousands of servers.
Certificate management: Quantum-safe cryptography requires managing new certificate types and signatures. Automation handles the lifecycle.
Security teams using tools that enable cryptographic agility move faster. They can experiment with new algorithms in isolated environments, validate performance, and deploy with confidence.
For a company like Nord VPN managing millions of VPN endpoints, automation is essential. Manual processes would never scale.
Use Case: Automate your VPN's cryptographic algorithm rotation, from testing new post-quantum standards to deploying them across all servers without downtime.
Try Runable For FreeFor enterprises building quantum-safe security infrastructure, automation isn't a luxury—it's a necessity. The organizations that invest in automating their cryptographic workflows now will have a major advantage as standards evolve.

Common Misconceptions About Post-Quantum Encryption
Let's clear up some confusion.
Misconception 1: "Post-quantum encryption makes me unhackable."
No. Encryption is one layer of security. You can have perfect encryption and still get hacked because your password is weak, your device has malware, or your company gets socially engineered. Post-quantum encryption makes one specific attack (future quantum computers breaking your encryption) harder. It doesn't protect against every threat.
Misconception 2: "Quantum computers are coming next year, so I need post-quantum encryption immediately."
Unlikely. Credible estimates put cryptographically relevant quantum computers at 15-30 years away, possibly longer. That said, "harvest now, decrypt later" attacks are a real threat, so preparing now makes sense. But there's no need to panic.
Misconception 3: "Post-quantum encryption is slow and will ruin performance."
Modern post-quantum algorithms like ML-KEM are actually faster than RSA in many cases. They require more bandwidth for key exchange, but the computational overhead is minimal. Nord VPN's rollout had negligible performance impact.
Misconception 4: "All VPN services have post-quantum encryption by now."
No. Most don't. Nord VPN is ahead of the curve. Many VPN services still use classical encryption exclusively. This is an area where vendors differ significantly.
Misconception 5: "I don't need to worry about post-quantum encryption because quantum computers are government-level threats."
Partially true. But data breach and theft happen at all levels. If someone steals your encrypted data today and decrypts it with a future quantum computer, does it matter whether it was a government adversary or a private attacker? The data is still compromised.
Misconception 6: "Post-quantum encryption is standardized and mature."
Partially true. NIST approved algorithms in 2024, which is great. But implementations are still newer. Best practices are still evolving. In 10 years, post-quantum cryptography will be more mature than it is now.
Misconception 7: "One quantum-resistant algorithm is enough forever."
No. That's the whole point of cryptographic agility. Algorithms might be broken or deprecated. New standards might emerge. Systems need the flexibility to adopt new methods without massive disruption.
These misconceptions are understandable. Cryptography is technical and hard to explain. But they lead to poor security decisions. The reality is more nuanced.
The Future of Encryption: Beyond Post-Quantum
Post-quantum cryptography is a bridge to the future, not the final destination.
What comes after post-quantum encryption? Several possibilities:
Homomorphic encryption: The ability to compute on encrypted data without decrypting it. You could send encrypted data to the cloud, have it processed while encrypted, and get back encrypted results. Decryption happens on your device. Even cloud providers couldn't see your data.
This is still experimental and slow (can be 1000x slower than operating on plaintext), but it's advancing rapidly. In 20 years, it might be standard.
Multivariate polynomial cryptography: Another quantum-resistant approach based on the difficulty of solving systems of multivariate polynomial equations. Different mathematical foundation than lattices. Could be a backup if lattice-based methods have unexpected weaknesses.
Isogeny-based cryptography: Cryptography based on properties of elliptic curve isogenies. Also quantum-resistant. Smaller key sizes than lattice-based methods, but slower in some operations. Might be useful for specific applications.
Lattice-based variants: Even among lattice methods, there are different approaches. Module-lattice (what ML-KEM uses), polynomial-ring-based variants, and others. The field is still exploring which approaches are optimal for different use cases.
Continuous rekeying: Instead of periodic rekeying, encrypt continuously changing the keys. Makes it harder for an attacker to reuse a stolen key.
Quantum key distribution (QKD): Using quantum mechanics itself for key exchange. Exploits quantum properties to create key exchange that's provably secure. Currently expensive and requires specialized hardware, but it's being deployed in some high-security environments.
Where does cryptography go in 2035? 2050? We don't know for certain. That's precisely why cryptographic agility matters.
Systems built with the assumption that one encryption method will last forever will become obsolete. Systems designed to adapt as standards evolve will remain secure.
This is Nord VPN's insight: post-quantum encryption is important, but the ability to change encryption methods is even more important.
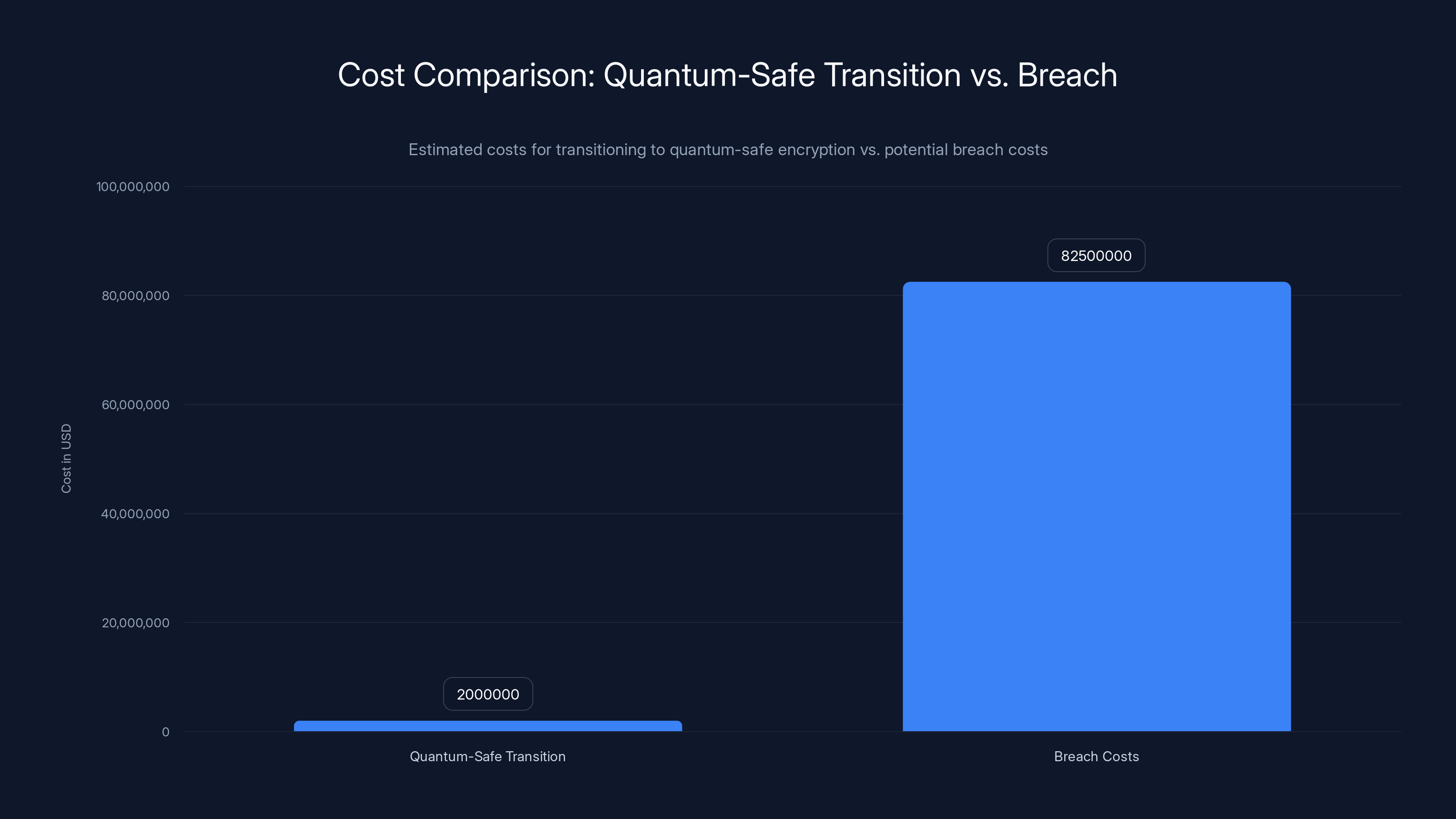
Implementing quantum-safe encryption is economically rational, with transition costs (
Regulatory and Compliance Perspectives
Security standards don't happen in a vacuum. Regulators mandate them.
NIST Guidance: NIST recommended all federal systems migrate to post-quantum cryptography by 2030. This is binding for government contractors and influences private sector practices.
EU Cyber Security Act: European regulations increasingly reference quantum-safe cryptography requirements. The NIS2 Directive requires critical infrastructure operators to consider post-quantum cryptography in their risk management frameworks.
UK National Cyber Security Centre: Published guidance recommending organizations begin quantum-safe transitions immediately.
Financial Industry: The banking sector is under pressure from regulators to implement quantum-safe encryption for protecting financial data.
Healthcare: HIPAA compliance increasingly requires consideration of long-term data confidentiality, which implies quantum-safe encryption for sensitive health information.
For enterprises, this means: quantum-safe cryptography will eventually be non-negotiable for compliance. Starting now gives you a 5-year head start before regulatory deadlines become hard requirements.
For VPN companies like Nord VPN, compliance readiness is a competitive advantage. An enterprise security team evaluating VPN providers will ask: "Are you quantum-safe? Do you have documentation for auditors? Can you prove compliance?" Nord VPN's public commitment and transparent roadmap answer these questions affirmatively.
Measuring Cryptographic Strength: What Makes Encryption "Good"?
How do you evaluate whether an encryption system is actually secure?
This is harder than it sounds. You can't just test encryption and see if it works—good encryption should work the same whether the underlying algorithm is secure or broken.
Cryptographers use several evaluation criteria:
Mathematical hardness: Is the problem that encryption relies on actually hard? For post-quantum algorithms, researchers use reductions: they prove that breaking the encryption is at least as hard as solving a known difficult mathematical problem.
Quantum resistance: Would a quantum computer with 1 million qubits break it? Estimates vary, but NIST's approved algorithms are believed to require quantum computers far larger than anything we'll see in the foreseeable future.
Real-world cryptanalysis: Researchers attempt actual attacks. Finding even a theoretical weakness (not a practical break, but evidence of weaknesses) is important.
Parameterization: Do the algorithm's key sizes, block sizes, and iteration counts make sense? ML-KEM was chosen partly because its parameter choices provide good security margins without being excessive.
Implementation resistance: Can the algorithm be implemented securely? Some mathematically strong algorithms are weak in implementation (timing attacks, side channels, etc.).
Performance: Is it practical? A theoretically perfect encryption that's 1000x slower than alternatives won't be adopted.
Standardization: Has it survived peer review and competitive evaluation? NIST-standardized algorithms have more credibility than proprietary methods.
For post-quantum encryption, the community has high confidence in algorithms like ML-KEM because they've survived years of public scrutiny, theoretical analysis, and practical attempts to break them.
But "high confidence" doesn't mean "absolutely certain." New attacks emerge. New insights appear. That's why cryptographic agility is important—if an algorithm is found to have weaknesses, you need to be able to switch to an alternative.

Cost-Benefit Analysis: Is Quantum-Safe Encryption Worth It?
Let's do some math.
Cost of implementing post-quantum encryption now:
- Development and testing: 2M (depending on organization size)
- Hardware updates (for some systems): 1M
- Staff training: 200K
- Ongoing maintenance and monitoring: $100K/year
- Total first-year cost: ~3M for an enterprise
Cost of not implementing quantum-safe encryption and being breached later:
- Regulatory fines: 100M+ (depending on jurisdiction and industry)
- Breach notification and remediation: 10M
- Reputation damage: Incalculable
- Litigation: 50M+
- Total potential cost: 160M+
Even with a 10% probability of a quantum-enabled breach, the expected value of preparing now is positive:
That's the expected economic value of security investment. For many enterprises, it's a no-brainer.
For consumers, the calculation is different. Individual breach costs are lower (identity theft, compromised passwords). But your data's value doesn't disappear in 10 years. Your health information, financial records, private communications—these retain value and sensitivity for decades.
Using a VPN service that's prepared for quantum threats is like having insurance. It's not thrilling, but when it matters, you're glad you have it.
Key Takeaways: What You Need to Remember
Post-quantum encryption is essential for long-term security, but it's not a silver bullet. The real innovation is cryptographic agility—the ability to adapt as threats and standards evolve. NIST-approved algorithms like ML-KEM provide a foundation, but implementation and ongoing updates matter equally. Organizations should start transitioning now because cryptographic migrations take years. VPN services like Nord VPN that have public, transparent quantum-safe roadmaps are setting industry standards. For enterprises, this is a compliance requirement that regulators are taking seriously. The cost of preparing now is far lower than the cost of breaches later. Automation tools will be essential for managing the complexity of cryptographic transitions.
Conclusion: The Evolution Continues
Post-quantum encryption isn't the end of the security story. It's a beginning.
What struck me most about Nord VPN's 2026 roadmap is that it doesn't present post-quantum encryption as a finish line. It's the company saying, "We deployed quantum-resistant encryption. Now we're thinking about how to build systems that can adapt as the field evolves."
That's mature thinking about security. Not, "We implemented the latest standard," but "How do we prepare for standards we don't know about yet?"
For organizations, the takeaway is clear: start your quantum-safe transition now. It's not an emergency (quantum computers that break encryption don't exist yet), but it's not something to procrastinate on either. Five-year plans for cryptographic migration are reasonable and increasingly expected by regulators.
For individuals choosing a VPN service, look for evidence that the provider is thinking long-term. Have they announced post-quantum support? Do they share a roadmap? Can they explain why their choices matter? These are signals of a company that takes security seriously, not just as a marketing feature but as a responsibility.
The quantum threat is real, but it's not imminent. We have time to prepare. The companies and organizations that use this time wisely—building flexible systems, understanding the technical landscape, and committing to ongoing improvement—will be the ones that remain secure in the post-quantum world.
The rest will scramble when quantum computers arrive, trying to retrofit cryptographic security into systems that were built for yesterday's threats.
Choose vendors and build systems with an eye toward the future. Post-quantum encryption is the foundation. Cryptographic agility is the architecture. Together, they'll keep your data secure for decades.
FAQ
What exactly is post-quantum encryption, and how is it different from current encryption?
Post-quantum encryption refers to cryptographic algorithms designed to resist attacks from both classical and quantum computers. Unlike current encryption methods (RSA, ECDSA) that rely on mathematical problems like factorization, post-quantum algorithms use different mathematical foundations—typically lattice problems—that remain difficult even for theoretical quantum computers. The key difference is the underlying math: classical encryption uses properties of prime numbers, while post-quantum encryption uses properties of high-dimensional lattices.
When will quantum computers actually threaten current encryption?
Cryptographically relevant quantum computers likely won't exist for 15-30 years, possibly longer. However, "harvest now, decrypt later" attacks are already a concern—adversaries intercept and store encrypted data today expecting to decrypt it with future quantum computers. This means organizations must implement post-quantum encryption now to protect data that needs to remain confidential for decades.
Does post-quantum encryption slow down my VPN connection?
No. Modern post-quantum algorithms like ML-KEM (which Nord VPN uses) are actually faster than RSA for key establishment. The computational overhead is minimal, and most users won't notice any performance difference. You might see a tiny increase in bandwidth for key exchange, but negligible in real-world use.
Why is cryptographic agility important if post-quantum encryption is secure?
Even secure encryption can have weaknesses discovered later, or new algorithms might become preferred as standards evolve. Cryptographic agility allows systems to swap encryption methods without service interruption. It's the difference between being locked into one algorithm and having flexibility to adapt. This forward-thinking approach protects organizations against unforeseen vulnerabilities or changing standards.
Are all VPN services implementing post-quantum encryption?
No. Most VPN services haven't deployed post-quantum encryption yet. Nord VPN is ahead of the curve, having rolled out post-quantum support across all apps. When evaluating a VPN service, ask directly whether they support post-quantum encryption and what their timeline is for full deployment.
Do I need to do anything to enable post-quantum encryption on my VPN?
No. If your VPN service has deployed post-quantum encryption (like Nord VPN), it happens automatically. Your device negotiates the strongest available encryption with the VPN server. Older app versions continue to work with classical encryption, while newer versions default to quantum-resistant methods. No user action required.
What's the cost of transitioning to post-quantum encryption for organizations?
For enterprises, implementation costs typically range from
What happens if my data is encrypted with classical encryption right now?
If your data needs to remain confidential for 20+ years, it's at risk from future quantum computers. This is why organizations with long-term data confidentiality requirements (governments, finance, healthcare) are prioritizing post-quantum encryption. Data encrypted today with RSA could theoretically be decrypted in 2045 if quantum computers arrive and the key is compromised.
How does Nord VPN's 2026 roadmap improve on current post-quantum deployment?
Nord VPN's 2026 roadmap focuses on cryptographic agility frameworks, certification standards for quantum-safe VPNs, hybrid encryption by default, and transparent reporting. Rather than just deploying one algorithm, the company is building systems that can adapt as standards evolve, and creating industry frameworks so other organizations can validate quantum-safety claims independently.
What should I look for when choosing a VPN service regarding cryptographic security?
Ask whether the service has deployed post-quantum encryption, request documentation of which algorithms they use, ask about their upgrade roadmap, verify they publish security audits, and check whether they discuss cryptographic agility. Services that are transparent about their cryptographic choices and have published timelines for improvements are more trustworthy than those using vague marketing language.
Is NIST's approval of post-quantum algorithms a guarantee they're secure forever?
No. NIST's approval means the algorithms have survived rigorous public evaluation and are believed secure based on current mathematical knowledge. However, cryptography is always subject to new discoveries. That's why cryptographic agility is important—no algorithm is guaranteed to remain secure indefinitely, so systems need flexibility to switch algorithms if necessary.
Key Takeaways Section
- Post-quantum encryption is essential for data with decade-long confidentiality needs, protecting against "harvest now, decrypt later" attacks by adversaries storing encrypted data today for decryption with future quantum computers
- Cryptographic agility is the real innovation, allowing systems to change encryption algorithms without service disruption, preparing for unforeseen vulnerabilities or evolving standards
- NIST finalized post-quantum standards in 2024, approving algorithms like ML-KEM that use lattice mathematics—a mathematical foundation resistant to quantum attack
- Implementation costs for quantum-safe transition (3M) are far lower than breach costs (160M+), making the security investment economically rational
- Nord VPN's 2026 roadmap focuses on certification frameworks and cryptographic agility, not just algorithm deployment, indicating forward-thinking approach to long-term security
- Regulatory pressure is accelerating adoption, with NIST recommending federal agencies transition by 2030 and other governments following suit
- Most VPN services haven't deployed post-quantum encryption yet, making Nord VPN an early adopter and highlighting the importance of vendor choice
- Automation tools will be essential for managing cryptographic transitions across organizations, from key rotation to compliance reporting
![Post-Quantum Encryption & Cryptographic Agility: The Future of VPN Security [2025]](https://tryrunable.com/blog/post-quantum-encryption-cryptographic-agility-the-future-of-/image-1-1766907498175.jpg)



