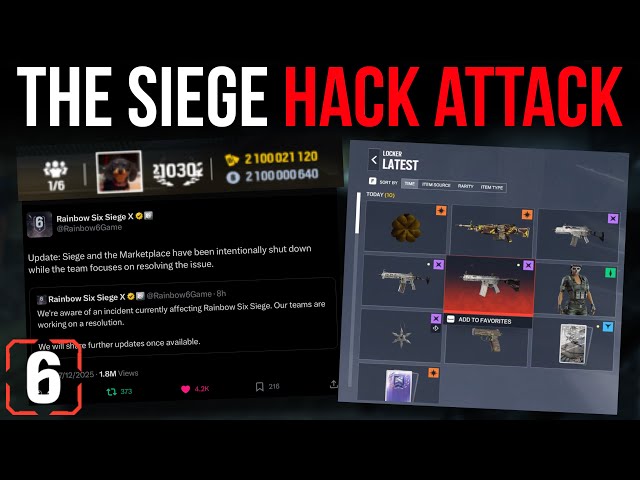
The Rainbow Six Siege Hack That Forced a Complete Shutdown
Last Saturday, one of gaming's most popular competitive shooters went dark. Not because of scheduled maintenance or a software update. Ubisoft took down every single Rainbow Six Siege server after hackers breached the game's core systems and handed out something unprecedented: 2 billion in-game credits to literally every player. This breach was reported by BleepingComputer as a massive security incident.
This wasn't some minor exploit or a cosmetic glitch. Hackers gained administrative control over significant portions of Rainbow Six's infrastructure. They banned players at will. They unbanned them just as easily. They sent custom messages through the ban ticker. They unlocked every in-game item for everyone. And they distributed enough virtual currency to make the in-game economy genuinely meaningless, as detailed by Times Now News.
To put numbers on it: Ubisoft prices R6 Credits in its store at 15,000 credits for
What happened next matters. Ubisoft made a public statement assuring players they wouldn't be punished for spending credits they'd received. The company rolled back transactions made after a specific timestamp to prevent economic abuse, but they accepted the fundamental reality: the damage was done, and the best path forward was transparency and restraint, as reported by Rolling Out.
This is one of the most significant security breaches in competitive gaming history. It exposed not just a vulnerability, but structural weaknesses in how live-service games protect player data and in-game economies. And it raises questions that every gaming company and cybersecurity professional is still wrestling with.
TL; DR
- The hack was catastrophic: Attackers gained control over banning systems, item unlocking, currency distribution, and player management tools, as noted by NotebookCheck.
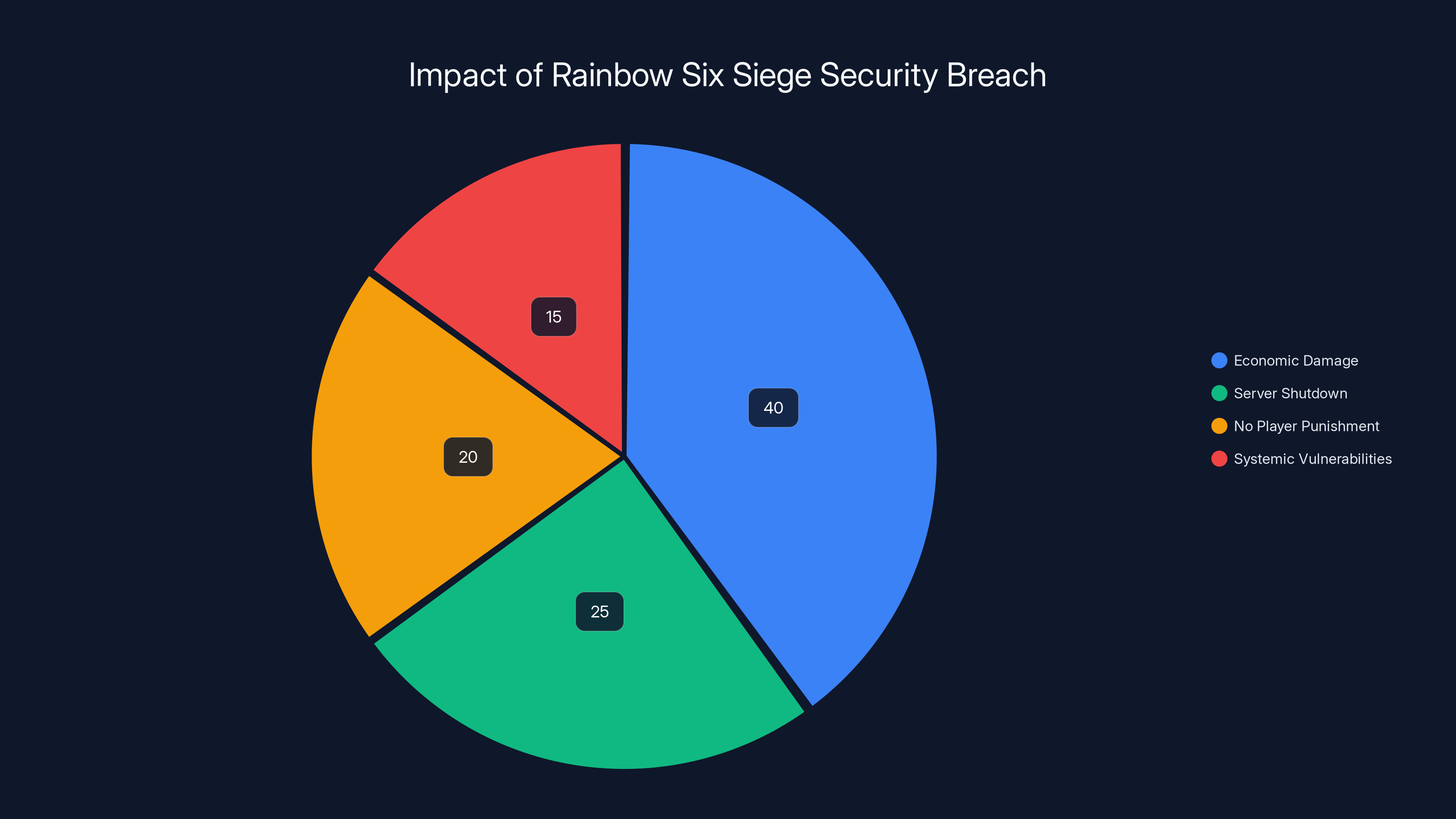
- The economic damage was massive: 2 billion R6 Credits worth approximately $13.33 million were distributed free to millions of players.
- Server response was immediate: Ubisoft shut down all Rainbow Six Siege servers and the marketplace within hours of discovering the breach, according to Tom's Hardware.
- No player punishment: Ubisoft pledged not to ban players for spending distributed credits, showing a player-first response to a corporate security failure.
- Systemic vulnerabilities exposed: The breach revealed that competitive multiplayer games may not have adequate security segregation between player-facing systems and administrative tools.

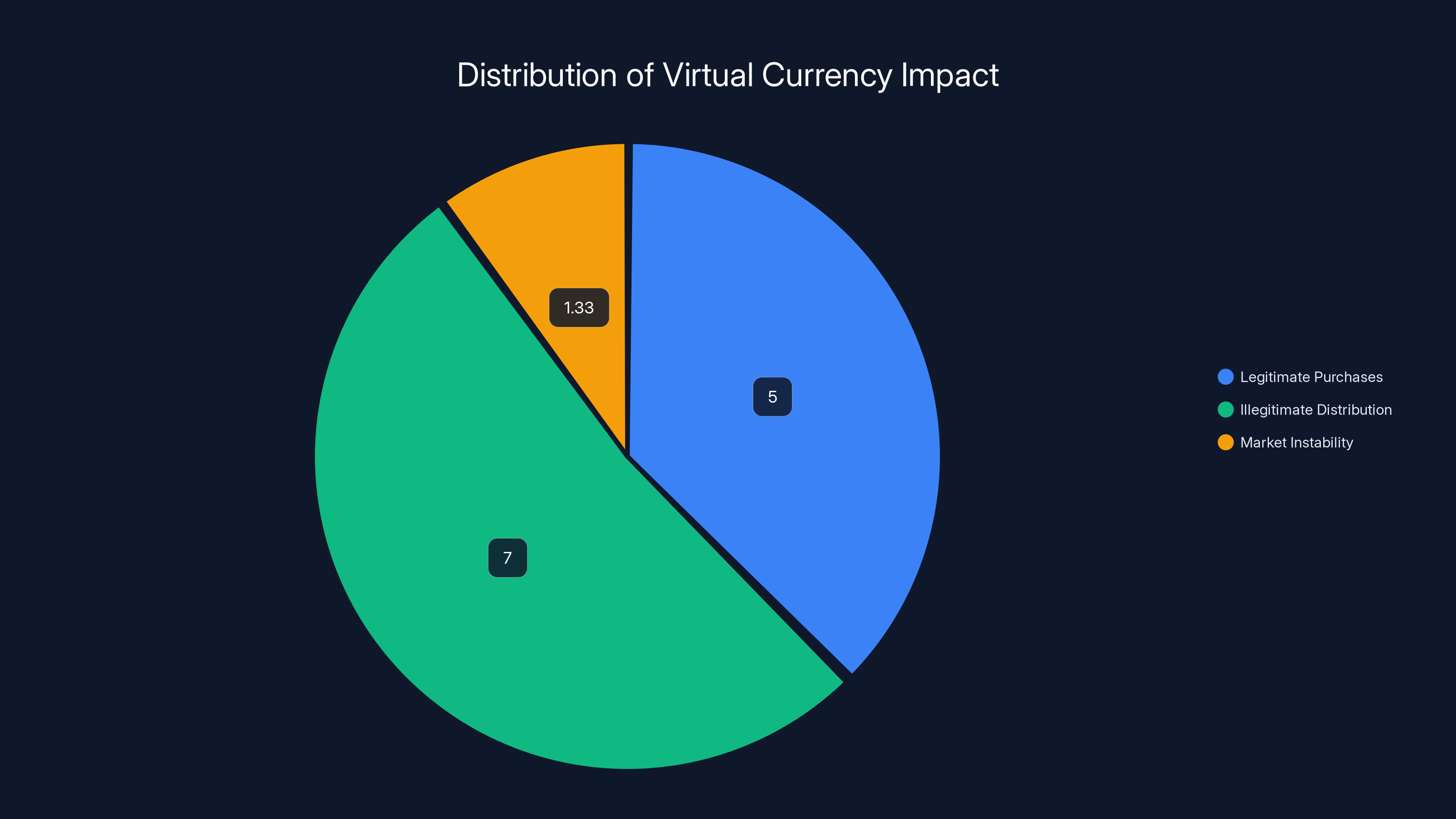
The $13.33 million impact of distributed virtual currency is divided into legitimate purchases, illegitimate distribution, and market instability, with the largest share being the illegitimate distribution.
How Hackers Gained Access to Rainbow Six's Administrative Systems
The exact entry point remains unclear in public statements, but the scope of access tells us something critical: whoever broke in didn't just find a single vulnerability. They had comprehensive, persistent access to systems that should never connect to the public internet, as discussed by Goosed.
Administrative accounts in any online service are typically isolated behind multiple layers of security. They live on separate networks. They require multi-factor authentication. They're monitored obsessively for unusual activity. Bypassing all of that suggests either an employee with legitimate credentials was compromised, a sophisticated supply chain attack occurred, or there's a fundamental architectural flaw in how Ubisoft segregated these systems.
Consider what the attackers could do: they modified banning lists directly. That's a function that touches the core player account database. They changed player items and credits. That touches both the inventory system and the currency ledger. They sent messages through the ban ticker, which is a communication channel typically reserved for administrative notifications. This level of access isn't typically available to a single system or account. It suggests either compromised admin credentials with excessive permissions, or a vulnerability that allowed privilege escalation from a lower-trust system.
The timing matters too. The breach was discovered and shut down within hours. That rapid response suggests either automated monitoring caught unusual patterns, or a player reported something suspicious and incident response kicked into gear. Either way, the attackers had access long enough to touch multiple critical systems, which means they had reconnaissance time. They found what to target. They mapped out the dependencies. And then they executed a coordinated, multi-system attack, as noted by TwistedVoxel.
This is the operational pattern of sophisticated attackers. Not random script kiddies. Not bored teenagers testing their skills. Organizations that understand the systems they're targeting and know exactly what they're going to do before they touch the keyboard.

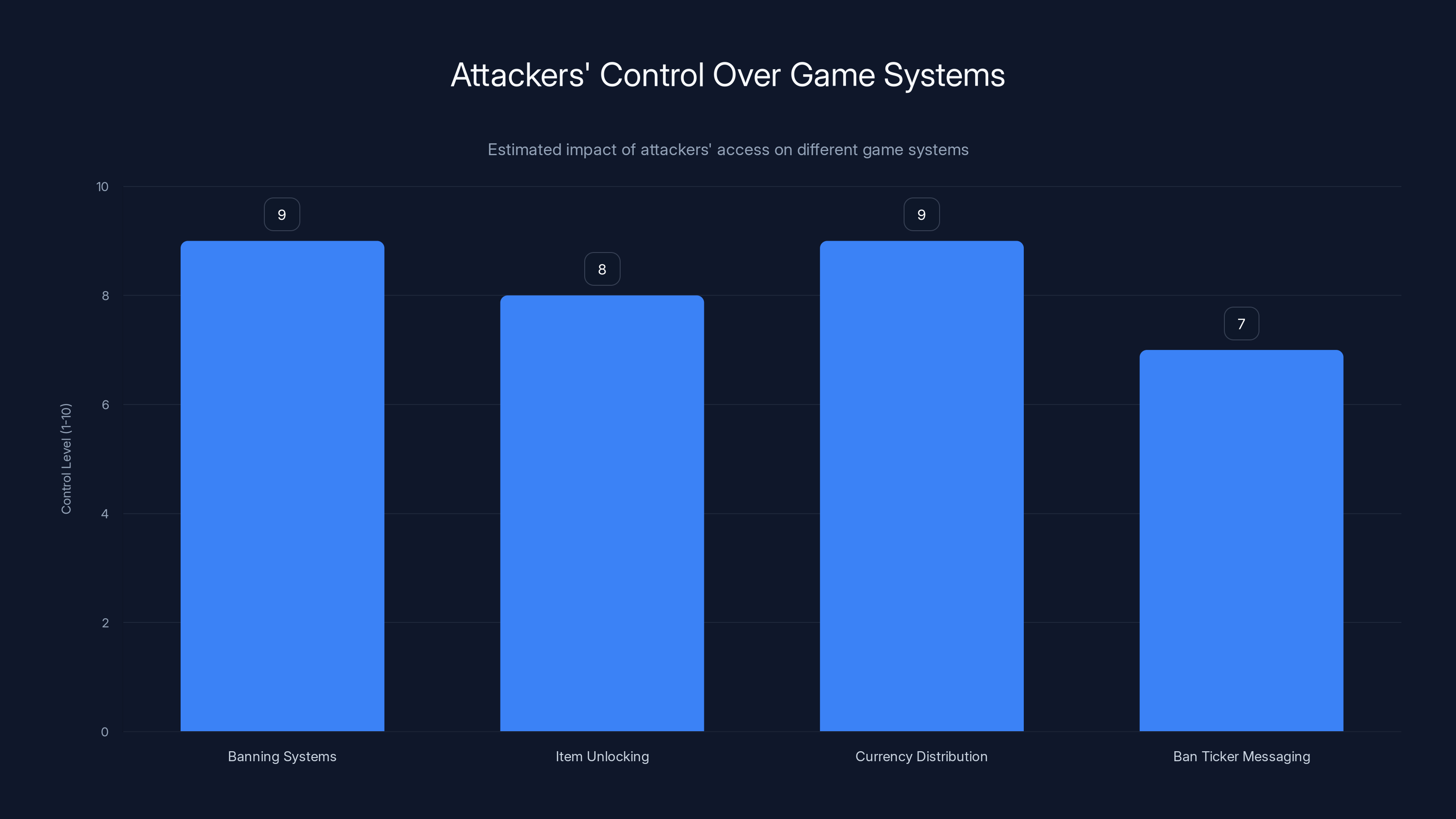
Attackers had significant control over various game systems, with the highest impact on banning systems and currency distribution. Estimated data.
The Scope of Compromise: What Attackers Actually Controlled
Let's break down what access looked like from the attacker's perspective. They weren't just reading data. They were writing it at scale.
Banning and Unbanning Systems: This is player account management at the highest level. Attackers demonstrated the ability to remove players from the game with full administrative access. Then they showed they could restore those players. This kind of access typically requires elevated privileges because it directly impacts player progression, playtime, rank, and match history. When someone gets banned, it's not just removing them from the matchmaking queue. It's flagging their account in every system that touches ranked play. Reversing that requires understanding the entire dependency graph of how bans propagate through the game's backend.
Item and Cosmetic Unlocking: Every player woke up to find all in-game items unlocked in their inventory. This is the monetization layer of the game. Players spend real money to unlock specific cosmetics, operators, weapon skins, and other visual customizations. Unlocking everything for everyone means the attackers had write access to the inventory database at a level where they could bypass normal unlock verification. They didn't have to unlock items one player at a time. They executed a bulk database operation that affected millions of accounts simultaneously.
Currency Distribution: The 2 billion R6 Credits weren't stolen from individual accounts. They were created and distributed through the currency system itself. This requires access to the transaction ledger and the ability to create legitimate-looking currency grants. The system probably has safeguards that prevent individual players from granting themselves unlimited currency—that's basic game design. But the attackers bypassed those safeguards entirely, operating at a level where they could modify the source of currency truth itself.
Ban Ticker Messaging: This is the notification system that appears when players are banned or experience account issues. Attackers sent custom messages through this channel. It's a relatively low-risk capability compared to the others, but it's significant because it demonstrates they could manipulate player-facing communications. They could have potentially impersonated official Ubisoft messages. They could have sent instructions or collected information by posing as staff.
The pattern here is clear: attackers had administrative credentials or found a way to escalate from compromised lower-privilege accounts to administrative access. They knew which systems to target. And they had enough time to execute coordinated operations across the banning system, the inventory system, the currency system, and the notification system.
The Economic Impact: $13.33 Million in Distributed Virtual Currency
Let's talk about what this means in real money terms. R6 Credits pricing in the Ubisoft store is tiered, but the baseline is clear: 15,000 credits cost $99.99. That's roughly 150 credits per dollar, or 0.0067 dollars per credit.
With 2 billion credits distributed:
That's not theoretical value. That's actual revenue that Ubisoft would have collected if those credits had been purchased legitimately. For context, that's equivalent to the entire annual spending of thousands of individual players.
But the economic damage extends beyond that single number. When you flood a game economy with unlimited currency, you break the fundamental mechanics that make progression meaningful. Players who spent hundreds of dollars grinding ranked matches to earn cosmetics now see those cosmetics worthless. The cosmetics themselves become meaningless as unlock status. Players who paid for operator packs find everyone has access to every operator. The entire monetization model collapses because the scarcity and exclusivity that justifies cosmetic prices no longer exists.
This creates a secondary economic problem: the in-game marketplace becomes unstable. Players with legitimate transactions made before the hack are now competing in a market where everyone has unlimited currency. Transaction prices spike. Market manipulation becomes trivial. And the game's economy enters a period of uncertainty where normal pricing mechanisms don't function, as highlighted by Red94.
Ubisoft's decision to roll back transactions made after a specific timestamp (11:00 AM UTC Saturday, 6 AM ET) was economically pragmatic but operationally complex. Identifying legitimate transactions, distinguishing them from exploitative ones, and rolling them back without corrupting valid player data requires meticulous database operations. One mistake and you've created a secondary corruption problem while trying to fix the first one.
The currency destruction has longer-term implications too. Every player who received 2 billion credits now has an effectively infinite resource for cosmetic purchases. Even if they spend aggressively, they'll likely never run out. This creates a permanent cohort of players who've completely opted out of the cosmetic monetization system through no choice of their own. For a free-to-play game where cosmetics are a primary revenue stream, that's a meaningful hit to lifetime player value calculations.

The hack resulted in 2 billion R6 Credits being distributed, valued at approximately $13.33 million, representing potential lost revenue from cosmetic purchases. Estimated data.
Why Server Shutdown Was the Right Call (But Also Reveals Architectural Problems)
Ubisoft's decision to shut down all Rainbow Six Siege servers and disable the marketplace simultaneously was the correct incident response. But it's also a damning indictment of the game's architecture.
When a system is compromised at the administrative level, you have limited options. You can attempt to identify the intrusion vector, patch it, and restore from backup. But if you're not certain you've fully removed the attacker's access, you risk them maintaining persistence. They could have created backdoor accounts. They could have installed rootkits or web shells. They could have exfiltrated player data. The safest approach is the nuclear option: take the entire service offline, conduct a comprehensive security audit, identify and patch all vulnerabilities, verify that administrative access is genuinely secure again, and then bring services back online in a controlled manner.
That's exactly what happened. Complete shutdown. No partial operations. No trying to keep casual play online while securing ranked. All services offline until the company could be reasonably certain the breach was contained and remediated, as reported by BleepingComputer.
But here's the architectural problem this reveals: if one security breach can take down an entire global multiplayer game instantaneously, that suggests the game doesn't have the kind of segmentation that mature online services require. Modern cloud architecture involves multiple isolated availability zones, database replicas that are read-only from a security perspective, and administrative functions that are completely divorced from player-facing systems.
Rainbow Six Siege clearly has some of that—it does run across multiple regions and presumably has database replicas. But the fact that discovering a breach meant immediately taking everything offline suggests that either the security response protocols lack the nuance needed to contain breaches to specific systems, or the architecture itself doesn't isolate systems enough to allow partial recovery.
A truly segmented architecture would have allowed Ubisoft to shut down administrative functions and currency systems while maintaining read-only access to matchmaking and basic gameplay. Players could have kept playing while the company worked on remediation. Instead, the entire playerbase was locked out.
This is the operational cost of an architectural vulnerability. It's not just about preventing the breach—it's about being able to respond to a breach without complete service disruption.
The Player Impact: How Millions Were Affected Simultaneously
For the average Rainbow Six Siege player, Saturday morning went from normal to chaotic in minutes. Players logged in expecting a regular gaming session and found everything unlocked. All cosmetics. All operators. All items. And suddenly their bank account had 2 billion R6 Credits.
That's not a feature. That's economic chaos. And the player psychology around it is complicated.
Initially, players celebrated. Free cosmetics. Free progression. Free currency. For a free-to-play game where cosmetics are gated behind paywalls, this looks like the game company just decided to be generous. Some players immediately started spending the currency on cosmetics they'd been saving up for across dozens of play sessions. Others tried to sell the currency somehow (which isn't possible, but that didn't stop some people from trying). Others just enjoyed having every cosmetic and operator available without grinding.
Then came the uncertainty. Ubisoft's statement was clear: you won't be punished for spending credits you received. But players read that statement through the lens of years of online gaming horror stories. They'd heard about mass bans after exploits. They'd seen account suspensions for unintended purchases. They weren't sure they trusted the company's promise.
Then came the actual impact. The servers shut down. Match services went offline. Ranked matches stopped. The marketplace disappeared. Suddenly the unlocked cosmetics and unlimited credits didn't matter because players couldn't actually use the game.
For competitive players especially, this was devastating. Tournament preparation halted. Rank decay started. Scrim partners couldn't organize practice. Professional teams couldn't practice for upcoming competitions. For a game that positions itself as a competitive esports title, taking servers offline affects both casual players and semi-professional players whose income depends on the game.
The downtime also exposed the infrastructure difference between regions. Some regions came back online before others. Some players couldn't access their accounts for extended periods. Account data had to be verified before being allowed back online, and Ubisoft prioritized careful verification over speed, which meant some players waited 24+ hours before they could play again, as noted by Duo.
For older accounts with extensive cosmetic collections, the psychological impact was different. These players had spent real money on cosmetics, grinding for operators, building a visual identity in the game. Suddenly everyone had their exact cosmetics and every operator. The scarcity that made their purchases feel special evaporated. That's not just an economic loss—it's a status loss for players who've invested heavily in cosmetic differentiation.

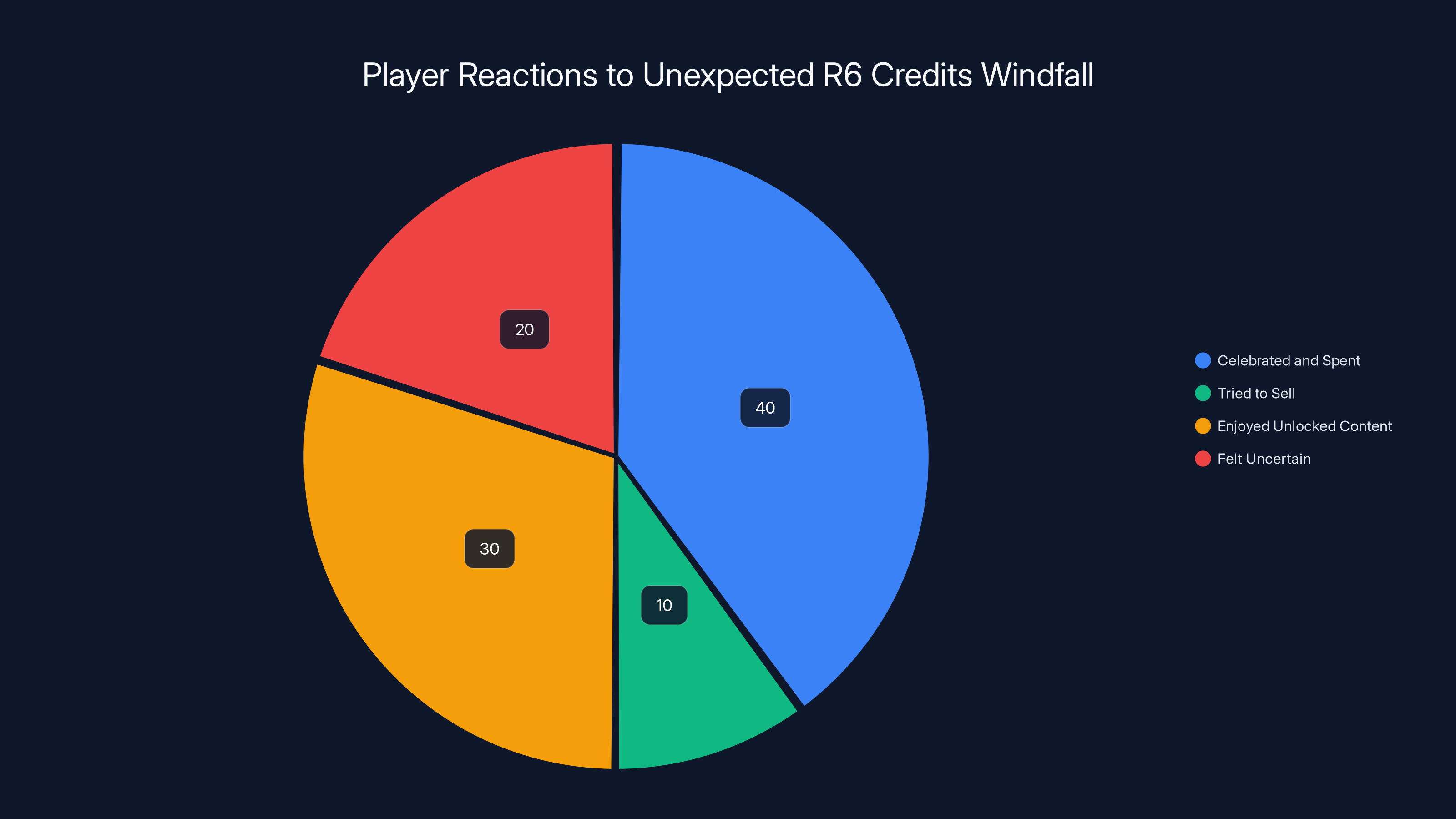
Estimated data shows that 40% of players celebrated and spent the unexpected credits, while 30% simply enjoyed the unlocked content. A notable 20% felt uncertain about the situation.
The Timeline: From Discovery to Complete Shutdown
Accurate incident response timelines are rarely public in the gaming industry, but piecing together the public statements and community reports gives us a reasonable picture of how fast this unfolded.
Saturday Morning (UTC): Players started reporting unusual activity. Some noticed everyone had unlocked cosmetics. Others saw the 2 billion credits in their account. Social media lit up immediately. The player community was generally amused at first, then concerned.
Early Saturday (UTC): Ubisoft's monitoring systems likely flagged the bulk currency distribution. Any mature online service has alerts for unusual transaction patterns. Distributing 2 billion credits across millions of accounts in a short time window would trigger every anomaly detection system. Incident response teams got paged.
Mid-Morning (UTC): Ubisoft made a public statement acknowledging the breach. This was crucial—transparency is the right approach. Players knew something serious had happened, and Ubisoft was taking it seriously enough to take action immediately.
By Noon (UTC): Servers were taken offline. The decision from detection to shutdown happened in hours, not days. This speaks to either exceptional incident response protocols, or the severity was obvious enough that there was no debate about the right action.
Next 24-48 Hours: Ubisoft conducted the security audit. Identified the breach vector. Patched vulnerabilities. Verified that administrative access was genuinely secure. This phase is where the real work happens.
Server Restoration: Services came back online gradually, with careful verification of account data. Some players regained access within 24 hours. Others waited longer depending on their region and account status.
The entire response—from discovery to shutdown to partial restoration—happened within 48 hours. That's actually not terrible for an incident of this scope. Many companies would have taken longer just to understand what happened.

Credential Compromise vs. Application Vulnerability: What Likely Happened
Without access to Ubisoft's internal incident report, we can't know exactly how the breach occurred. But the scope of access tells us it was likely one of two scenarios.
Scenario One: Compromised Administrative Credentials
An administrative account with legitimate access to the game's backend systems was compromised. This could happen through phishing, a malware infection on someone's personal device, credential stuffing from a leaked password database, or a sophisticated supply chain attack targeting Ubisoft specifically.
If an admin's credentials were stolen, the attacker would have legitimate, traceable access to the systems they compromised. They'd use real administrative interfaces. They'd execute commands that look normal in the logs (at least at first glance). The only unusual thing would be the timing and the commands executed.
This scenario is disturbingly common. Most data breaches involve compromised credentials rather than zero-day vulnerabilities. Attackers go after employees with access rather than hunting for application flaws. An employee's compromised laptop is easier to exploit than finding a vulnerability in a mature game engine.
Scenario Two: Critical Application Vulnerability
A vulnerability in the player-facing game client, the API layer, or a related service allowed unauthenticated access to administrative functions. This would be a critical privilege escalation bug or an authorization bypass that let attackers impersonate administrators without needing legitimate credentials.
This scenario is less likely but more worrying from a product security perspective. If a vulnerability exists that lets players escalate to administrative access, then the attack surface includes millions of players. Every one of them is a potential entry point.
Most Likely Synthesis
Given the sophistication of the attack—coordinated operations across multiple systems, knowledge of the database structure, ability to execute bulk operations—it's probably a combination. An employee's credentials were compromised, giving attackers a foothold in the network. Then they used that access to discover and exploit additional vulnerabilities in the game's backend, escalating their privileges further and establishing persistence.
This is the typical playbook for sophisticated attacks against large targets. You don't walk in expecting to immediately have full administrative access. You walk in with compromised employee credentials, use that to look around, find other vulnerabilities, and build up your access level over time. The fact that the breach was discovered and contained within hours means either automated systems caught them, or they were intentionally trying to cause maximum economic disruption rather than hide their activities.


Estimated data: Player trust recovery demands the most effort at 35%, highlighting its complexity and importance in post-breach scenarios.
Security Architecture Lessons: What This Reveals About Online Game Infrastructure
Rainbow Six Siege is one of the most popular competitive shooters globally. It's been running for nearly a decade. Ubisoft is a Fortune 500 gaming company with extensive infrastructure and security expertise. That this breach happened at all reveals systemic architectural problems that likely affect other games too.
Problem One: Insufficient Segmentation Between Administrative and Player Systems
Administrative functions should run on completely separate infrastructure from player-facing systems. Separate servers. Separate networks. Separate databases with one-way replication. This isolation means that compromising a player-facing API doesn't automatically compromise administrative functions. And compromising an admin's device doesn't immediately compromise every player's data.
The fact that a single breach let attackers modify banning lists, distribute currency, unlock items, and send administrative messages suggests these systems are on the same network, accessing the same databases, or connected through shared infrastructure that lacks proper segmentation.
Problem Two: Excessive Credential Permissions
Administrative accounts should have granular permissions. One account for modifying bans. Another for currency operations. Another for inventory management. If a single account has access to everything, then compromising one credential compromises everything.
The breadth of this attack—banning, currency, items, messages—suggests attackers either compromised a "super admin" account with permissions across all systems, or they compromised multiple accounts and chained them together to gain broader access.
Problem Three: Insufficient Logging and Alerting
Bulk currency distribution should trigger alerts. Modifying bans in unusual patterns should trigger alerts. Accessing player data in ways that differ from normal operations should trigger alerts. The fact that this breach happened for long enough for the attacker to distribute 2 billion credits to millions of players without immediate blocking suggests either:
- Logging exists but alerts didn't fire
- Alerts fired but weren't monitored in real-time
- The bulk operation was executed in a way that looked normal to the logging system
For a game company with Ubisoft's resources, this is surprising. Most mature platforms have sophisticated anomaly detection that catches unusual patterns in microseconds.
Problem Four: Insufficient Disaster Recovery Isolation
Backups of the database presumably exist. Replicas in other regions probably exist. But if those backups are accessible from the same administrative network that was compromised, then restoring from backup doesn't actually remove the attacker's access. You've just restored a clean copy while the attacker is still sitting on the admin network.
Proper disaster recovery requires that backup infrastructure is completely isolated from production systems. Restore operations should require explicit, monitored processes. And access to backup systems should require different credentials than access to production systems.
The fact that this breach didn't result in data exfiltration (as far as we know) suggests the attacker's focus was disruption rather than espionage. But compromised databases could have included player data, payment information, and account credentials—all high-value targets.
The Attacker Profile: Who Actually Does This?
Someone with skill, patience, and motivation executed this breach. It wasn't random. It wasn't careless. The coordination across multiple systems, the understanding of how to trigger bulk operations, and the timing all suggest this was either a professional attack group or an exceptionally skilled individual.
Motivations Could Include:
Financial disruption aimed at damaging Ubisoft's revenue or reputation. Damage to a company's operational capability and player trust is worth something to competitors or actors with financial motivations.
Proof-of-concept for selling vulnerabilities or access. Ransomware groups sometimes target gaming companies specifically because online games are highly profitable and vulnerable to downtime pressure. The attacker might have been building a negotiating position for future attacks.
Political or activist motivations. Demonstrating that a major corporation's security is inadequate could be the goal. No financial demand, just maximum disruption and publicity.
Game-specific motivation. A disgruntled employee, a banned player with a grudge, or someone with other personal motivation could also do this. The relatively targeted nature of the attack—going after the game's core systems rather than exfiltrating all player data—could suggest someone with specific knowledge of the game and anger toward the company or platform.
What's notable is what didn't happen: attackers didn't seem to exfiltrate player data in bulk. They didn't hold the game for ransom. They didn't install rootkits to maintain persistent access. They distributed currency and unlocked items, then apparently let the activity be discovered. This suggests the goal was primarily disruption and demonstrating capability, not long-term compromise or financial extortion.

The economic damage was the most significant impact of the breach, accounting for 40% of the total impact, followed by server shutdown and systemic vulnerabilities. Estimated data based on narrative.
Player Communication: How Ubisoft Handled the Transparency Challenge
Ubisoft's public response was notably direct. The company didn't bury the issue. Didn't claim it was a minor incident. Didn't try to obscure what happened. They said: breach confirmed, servers down, investigating, nobody will be punished for spending distributed credits.
This approach has tradeoffs. Transparency builds trust. Players appreciated knowing exactly what happened and seeing that Ubisoft was taking it seriously. But transparency also means public acknowledgment of a security failure. Competitors, investors, and regulators all see that acknowledgment.
The "no punishment" commitment was tactically smart. The last thing Ubisoft needed was players afraid to spend the currency, or worse, creating legal exposure by banning players who had done nothing wrong. By explicitly promising no consequences, the company removed uncertainty and kept the player community from turning hostile during an already tense incident.
The selective rollback—only transactions after a specific timestamp—was more complex. It preserved the ability to punish obvious abuse (someone who spent all 2 billion credits trying to trade or resell them), but didn't punish players for normal gameplay spending. This created a bright-line rule that players could understand and trust.
What's interesting is what Ubisoft didn't do: they didn't blame players, they didn't blame a third-party service provider, they didn't create scapegoats. They said "our systems were compromised" and moved on to fixing it. That kind of accountability is rare in incident response communications, and it probably contributed to the player community's relatively calm reaction given the severity of the breach.

The Competitive Gaming Impact: What This Means for Esports
Rainbow Six Siege has a professional esports circuit. Teams compete for money. Tournaments run on schedules. Players practice ranked matches to prepare. A global server shutdown doesn't just affect casual players—it disrupts the professional competitive ecosystem.
Tournaments scheduled during the downtime had to be postponed. Teams couldn't scrim (practice matches). Players couldn't practice on the live servers, which means their preparation was disrupted right before important competitions. For semi-professional players who depend on tournament winnings for income, this downtime translates directly to lost earnings and lost preparation time.
This creates interesting liability questions that are rarely discussed. If a server breach causes financial losses to professional players, who's responsible? Ubisoft's terms of service probably include language saying they're not liable for service interruptions. But that language was written assuming normal downtime, not security breaches caused by inadequate security architecture.
Some regions handled the restoration differently. The servers came back online in a staggered fashion rather than all at once, which meant some competitive teams could resume practice before others. This created asymmetric preparation time for tournaments happening during or shortly after the restoration window.
The incident also exposed the vulnerability of entire esports ecosystems that depend on a single game. If one security breach can take the entire game offline for 24+ hours, that's a systemic risk for anyone whose income depends on that game. Professional sports teams have venues owned by multiple entities and operate on schedules controlled by regulatory bodies. Esports teams depend entirely on a single corporation maintaining functional servers.
What Other Games Can Learn: Preventing Rainbow Six-Scale Breaches
Every live-service game with a substantial player economy should look at this breach and ask: could this happen to us? And if it did, how would we respond?
The answers might be uncomfortable.
Architectural Changes
Start with segmentation. Administrative functions should run on completely isolated infrastructure. Database replicas should be read-only from a player-facing perspective. Currency operations should require multiple approvals from different systems. Item unlocking should go through a verification system that checks if the unlock operation originated from an authorized source.
Implement zero-trust architecture for administrative access. Don't assume that being on the internal network is sufficient authentication. Require hardware-based keys for administrative access. Require multi-factor authentication. Require explicit, logged approval for any bulk operations. Make it harder for attackers to do anything interesting even if they compromise an admin account.
Detection and Response
Build monitoring systems that understand what normal looks like. Track the rate at which currency is distributed. Flag when unlocks happen in unusual patterns. Watch for administrative actions that deviate from normal operations. Anomaly detection systems should catch this breach within seconds, not minutes or hours.
Prepare incident response for compromised administrative access specifically. Have a runbook for "admin account compromised." It should include immediate password resets, review of actions taken with that account, revocation of API keys, and detailed logging of everything the account did. Don't assume you need to take the entire game offline immediately. Have a tiered response that starts by isolating the compromised account and escalates only if isolation doesn't work.
Regulatory and Legal Considerations
Document the security architecture. Document the incident response procedures. Test them regularly. When a breach does happen (and it probably will eventually), you'll want to demonstrate that you followed reasonable security practices and responded appropriately. This protects the company from negligence claims and helps with regulatory scrutiny.
Consider cyber insurance. It's expensive, but it covers breach response costs, forensic investigation, player notification, and legal liability. For large multiplayer games with millions of players, the downside risk of a breach is too large to self-insure.

The Precedent This Sets: Future Attacks on Games
When an attack succeeds at this scale, it becomes a proof-of-concept for other attackers. Now they know that at least one major game company's infrastructure is vulnerable enough to allow administrative access and bulk account modifications. If the attack vector becomes public, it becomes a blueprint.
This likely means we'll see copycat attacks. Attackers will target other games using similar techniques. Some attacks might be more sophisticated (focusing on exfiltration rather than disruption). Some might be targeted at smaller games with fewer resources for security. The overall effect is that the bar for what's acceptable security has been raised.
Ubisoft is incentivized to share lessons learned with the industry, both to improve overall security and to demonstrate that this was an aberration rather than the norm for their security practices. Expect industry conferences to feature sessions on this breach, how it happened, and what companies learned from it.
Playersbase expectations have also shifted. Before this, many players might have assumed "the big companies have security under control." This breach is a reminder that even Fortune 500 companies with substantial resources can have serious security architecture problems. Player communities are now more likely to question security practices at other games and expect more transparency when breaches occur.
The incident also raises questions about regulatory oversight. Gaming isn't currently regulated like banking or healthcare, where security standards are enforced by government agencies. As breaches get more public and more disruptive, that pressure might increase. Expect potential regulations around game security in the future, especially for games that involve financial transactions.
Recovery and Restoration: The Ongoing Work After Servers Came Back
Getting servers back online was only the beginning. Real recovery is much longer.
Technical Recovery: The company had to verify that all systems were genuinely clean. That meant forensic investigation of what the attacker did, exactly how they did it, and whether any persistence mechanisms remained. Only after that verification could the company be confident enough to bring systems back online and allow players to resume normal operations.
Economic Recovery: The in-game economy was disrupted. Cosmetics that were supposed to be rare were suddenly available to everyone. The relative value of different cosmetics changed. Player expectations about cosmetic pricing shifted. Ubisoft had to carefully manage the transition back to normal cosmetic sales without angering the player community or looking like they were trying to extract extra value after a security failure.
Player Trust Recovery: This is the longest and hardest part. Trust in security is built over time and destroyed instantly. Players who saw their accounts compromised will have reduced confidence in Ubisoft's security for years. The company has to demonstrate, through consistent action and transparent communication, that the breach prompted serious security improvements and that such a breach won't happen again.
This might involve periodic security audits from external firms (and publicly sharing the results), bug bounty programs that incentivize security researchers to find vulnerabilities before attackers do, and regular communication about security improvements. Some companies host transparency reports describing the security incidents they've experienced and how they've improved in response.
Competitive Ecosystem Recovery: Tournament schedules had to be adjusted. Teams needed time to practice. Rankings that were disrupted during downtime had to be addressed. Professional players and teams needed assurance that the game would be stable enough for future competition. This required both technical fixes and communication from Ubisoft to the competitive community.
The Broader Context: Why Gaming Security Matters More Than Ever
This breach didn't compromise classified military intelligence. It didn't expose critical healthcare data. But it affected millions of players and disrupted their ability to use a service they rely on. That matters.
Games are increasingly central to how people socialize, compete, and spend money. They're not niche hobbies anymore. They're mainstream entertainment. When a major game's security fails, the ripple effects touch professional players, esports organizations, content creators who earn income from the game, and casual players who just want to play with friends.
Security in gaming has historically been treated as a lower priority than it is in other industries. Banks invest heavily in security because customers assume their money is safe. Healthcare systems invest in security because patient data is sensitive. Games... games were sometimes treated as "not that important" from a security perspective.
This breach and others like it are changing that perception. Games handle real money. They store personal data. They're becoming targets for increasingly sophisticated attackers. The security architecture that worked for a game launched in 2015 doesn't necessarily work for the same game in 2025 with millions of players and hundreds of millions of dollars in annual revenue.
Ubisoft's breach is a signal to the entire industry: it's time to take security as seriously as you take performance optimization or player retention. Because the cost of not doing so is massive downtime, player trust erosion, and potentially significant financial losses.
FAQ
What happened during the Rainbow Six Siege hack?
Hackers gained administrative access to Rainbow Six Siege's servers and used that access to grant 2 billion R6 Credits to every player, unlock all in-game items for all players, and modify banning and messaging systems. Ubisoft discovered the breach and immediately shut down all game servers and the marketplace to contain the damage and conduct a security investigation.
How did hackers gain access to Rainbow Six's administrative systems?
The exact entry point hasn't been publicly disclosed, but based on the scope of access, attackers likely either compromised administrator credentials through phishing or malware, or exploited a critical vulnerability in the game's backend systems that allowed privilege escalation. The coordinated nature of the attack suggests sophisticated attackers with knowledge of the game's infrastructure.
How much money was the distributed currency worth?
R6 Credits are priced at
Did Ubisoft punish players for spending the distributed credits?
No. Ubisoft explicitly stated that players who spent the distributed credits would not be punished. The company only rolled back transactions made after 11:00 AM UTC on Saturday to prevent exploitation and abuse, but players who spent distributed credits on cosmetics during normal gameplay faced no consequences.
How long were Rainbow Six Siege servers offline?
Servers were shut down immediately upon discovery of the breach and were brought back online in a staggered fashion over the next 24-48 hours. Some regions were restored before others, with the company prioritizing careful security verification over rapid restoration to ensure no persistence mechanisms remained.
What does this breach reveal about game security architecture?
The breach exposed several architectural weaknesses: insufficient segmentation between administrative and player-facing systems, potentially excessive permissions on administrative accounts, possibly insufficient real-time anomaly detection, and likely inadequate isolation of backup and disaster recovery systems. These issues prevented the company from containing the breach to specific systems and forced a complete service shutdown.
Could this happen to other games?
Yes. This breach reveals vulnerabilities that likely exist at other games with similar architecture. Any game with inadequate segmentation between administrative systems and player-facing systems, insufficient credential management, or weak anomaly detection could be vulnerable to similar attacks. The gaming industry as a whole needs to improve its security architecture.
What are the long-term implications for competitive gaming?
Tournament schedules were disrupted and teams lost preparation time. Professional players questioned the stability of a game they depend on for income. The incident raised awareness that esports ecosystems are vulnerable to single points of failure (one game company's security). Expect future esports contracts to include provisions about minimum uptime guarantees and compensation for breaches that disrupt scheduled competitions.

Key Takeaways
The Rainbow Six Siege breach represents one of gaming's most significant security incidents, exposing architectural vulnerabilities that extend far beyond one game. The attack's speed and scope reveal a gaming industry that hasn't yet prioritized security architecture the way mature industries do. As games become more central to entertainment, esports, and player economies, security must become as important as performance and gameplay. For Ubisoft, the focus now is demonstrating that serious improvements are coming. For other game companies, this breach is a warning: it can happen to you, and when it does, the consequences are severe.

Related Articles
- OLED TVs 2025: Ultimate Guide to Next-Gen Brightness & Glare-Free Tech
- 33 Top Health & Wellness Startups from Disrupt Battlefield [2025]
- Google Pixel Watch 4 Review: The Smartwatch That Finally Gets It Right [2025]
- MayimFlow: Preventing Data Center Water Leaks Before They Happen [2025]
- 10 Best Air Fryer Recipes & Foods to Cook First [2025]
- NYT Strands Game #666 Hints & Solutions [December 29, 2024]
![Rainbow Six Siege Hack: 2 Billion Credits, Server Shutdown [2025]](https://tryrunable.com/blog/rainbow-six-siege-hack-2-billion-credits-server-shutdown-202/image-1-1766941560021.jpg)



