VPN Industry Standards: 3 Critical Changes Needed in 2026
Introduction: The VPN Industry at a Crossroads
Virtual Private Networks have become essential infrastructure for modern digital privacy. Yet here's the uncomfortable truth: the VPN industry is broken in ways most users never see.
I've spent years analyzing VPN services, testing protocols, reviewing privacy policies, and auditing the infrastructure behind these tools. What I've discovered is both troubling and fixable. The industry operates under outdated standards, murky transparency practices, and security assumptions that haven't been updated since the early 2010s.
The problem isn't that VPNs don't work. They do. The problem is that they work in an ecosystem held together by handshake agreements, regulatory workarounds, and practices that prioritize marketing over genuine security. When a VPN company claims "military-grade encryption" or promises "zero logs," there's often no independent verification, no standardized testing framework, and no accountability mechanism.
As we enter 2026, the industry faces unprecedented pressure. Governments are cracking down on VPN usage in restricted regions. Cybersecurity threats are evolving faster than defense mechanisms. Users are increasingly skeptical of privacy claims that seem too good to be true. And they should be.
I want to be clear about something upfront: I'm not anti-VPN. I use them daily. I trust VPNs with sensitive work, and I recommend them to people who genuinely need privacy protection. But I'm also tired of watching the industry ignore glaring issues that could be solved with commitment and standardization.
There are three specific changes the VPN industry needs to adopt before 2026 ends. These aren't hypothetical suggestions. They're practical improvements based on technical requirements, user needs, and lessons learned from security failures across the industry. Without these changes, VPN services will continue operating in a gray zone where user trust is earned through marketing claims rather than verifiable facts.
Let me break down each one, explain why it matters, and show you what meaningful change looks like.
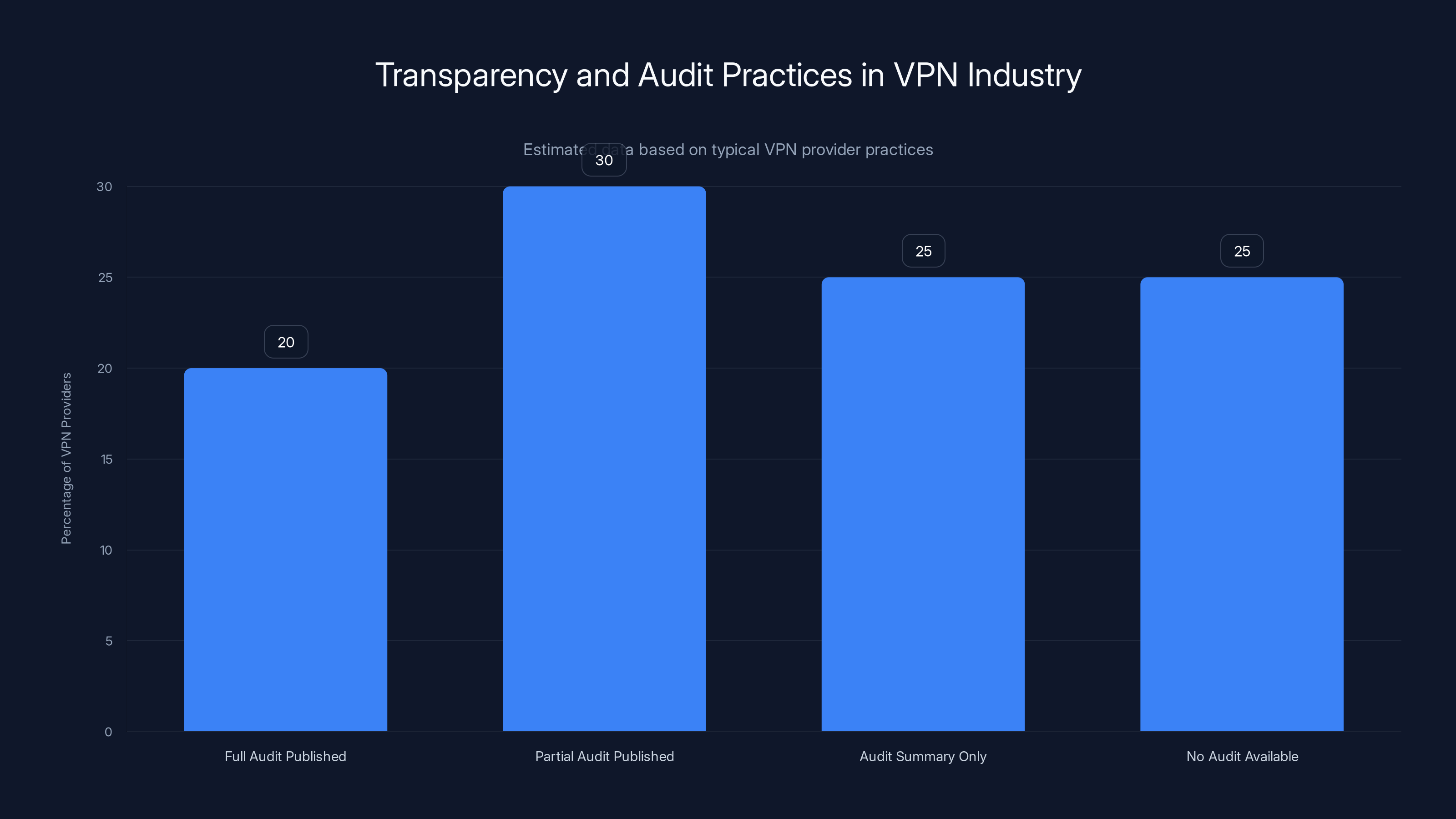
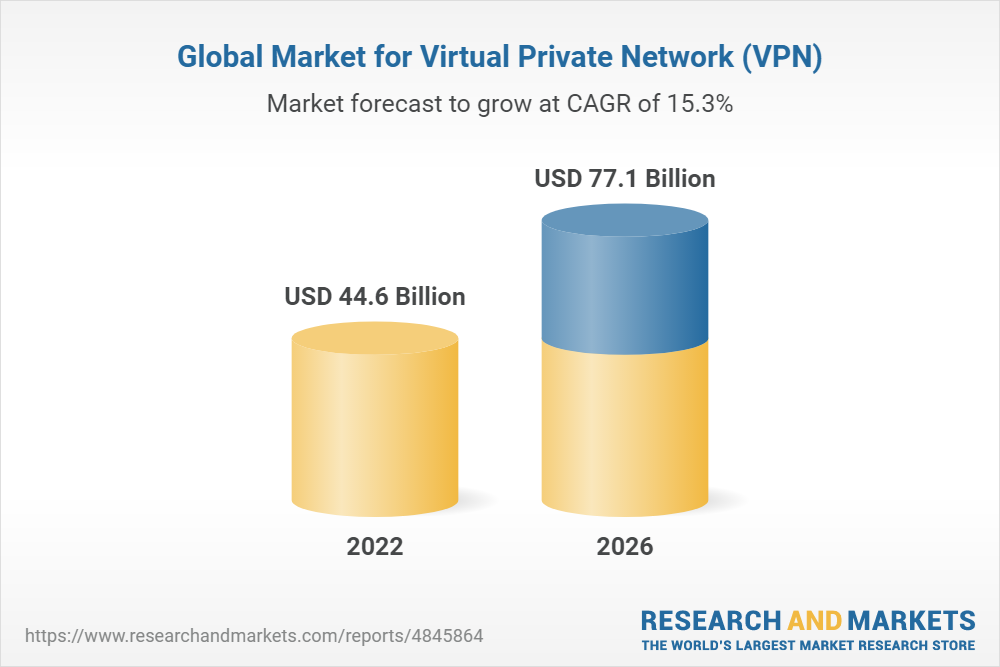
Estimated data shows that only 20% of VPN providers publish full audit reports, while 25% do not provide any audit information. This highlights the lack of standardized transparency in the industry.
TL; DR
- Independent audits must become mandatory, not optional marketing tactics. Every major VPN provider should commit to annual third-party security audits with published results.
- Protocol transparency standards are overdue: VPN companies need to publish detailed technical documentation, allow security researchers to review code, and commit to standardized encryption methodologies.
- Jurisdiction clarification is critical for user protection: The VPN industry must adopt clear, standardized definitions of data retention policies aligned with actual legal requirements in their operating jurisdictions.
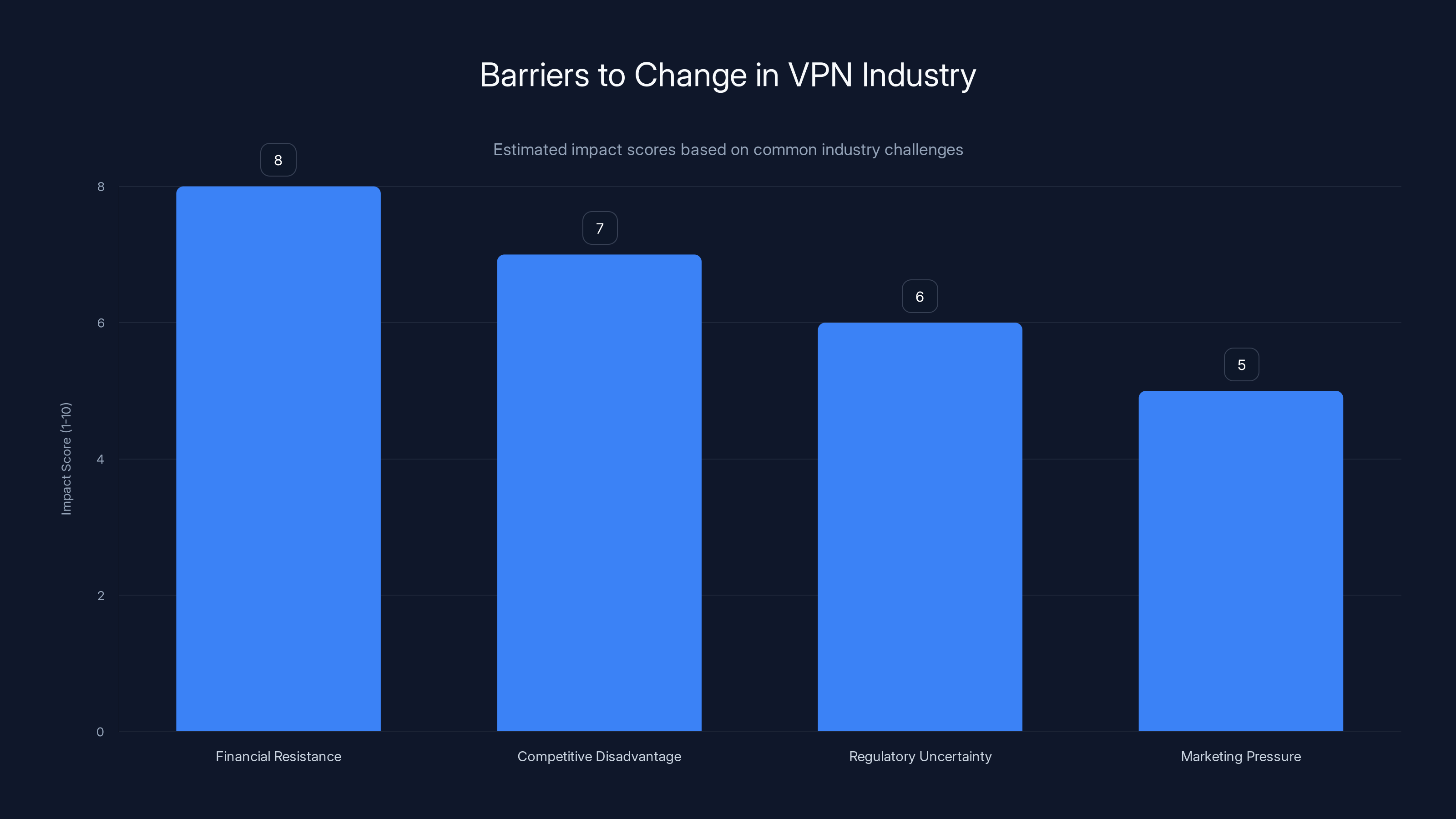
Financial resistance is the most significant barrier to change in the VPN industry, with an estimated impact score of 8 out of 10. Estimated data based on industry analysis.
The State of VPN Industry Standards Today
Why Current Standards Are Insufficient
The VPN industry operates without unified standards for security testing, privacy verification, or transparency reporting. This creates a situation where a company's claims about security are essentially self-reported.
Consider the marketing language used by VPN services: "AES-256 military-grade encryption," "100% zero-knowledge architecture," "unhackable connections." These sound reassuring. They're also often vague enough to be technically true while being functionally misleading. A VPN using AES-256 encryption might still have vulnerabilities in how that encryption is implemented, how keys are managed, or how data flows through their infrastructure.
The bigger issue is that there's no industry-wide standard for how these claims should be verified. A company can hire a security firm to audit their systems, but what gets audited? How deep does the review go? What gets published publicly versus what remains confidential? Different VPN providers answer these questions differently, making direct comparison impossible.
I've reviewed audit reports from major VPN companies. Some are thorough and transparent. Others are marketing documents with security language sprinkled in. Users have no reliable way to distinguish between them.
The Audit Problem: Verification Theater
Many VPN services have undergone security audits. But the audit landscape is messy. Different firms use different methodologies. Some audits examine the entire infrastructure, others focus narrowly on specific components. Some results are published in full, others are summarized by the company itself.
When a VPN company says "We've been audited," that statement conveys trust but provides almost no useful information. Audited by whom? For what? Using which standards? What was discovered? What was fixed? Without standardized audit frameworks, these statements are nearly meaningless.
The ideal scenario is simple: an industry-wide standard for annual security audits, conducted by pre-qualified third parties, with standardized reporting requirements and publicly available results. Every major VPN provider should publish audit findings annually, including vulnerabilities discovered and how they were addressed.
This isn't radical. It's how financial institutions, healthcare companies, and other privacy-sensitive industries operate. Yet the VPN industry has largely resisted this level of transparency.
The Transparency Gap: Marketing vs. Reality
VPN marketing departments excel at creating confidence. VPN security teams sometimes struggle with the actual technical implementation of that confidence.
A common issue: privacy policy transparency. A VPN company might claim "no logs" but the policy document reveals they collect certain metadata, behavioral data, or technical information necessary for service operation. The claim isn't technically false, but the policy reveals nuance that contradicts the marketing message.
Another gap: jurisdiction transparency. Many VPN companies operate from neutral countries, which sounds good for privacy. But "neutral" is vague. Does it mean they're legally exempt from government data requests? Actually, no. Most countries have extradition treaties and mutual legal assistance agreements. A company operating from a country with privacy protections can still be compelled to provide user data if facing extradition pressure.
Users need clearer information about what "no logs" means in the context of actual legal requirements. If a government serves a warrant on a VPN company in their jurisdiction, will they comply? Under what conditions? What can they actually provide if compelled?
Change #1: Mandatory Independent Security Audits with Standardized Reporting
Why Current Audits Fall Short
The security audit landscape for VPNs is fragmented. Some companies use large, well-respected cybersecurity firms. Others use smaller boutique auditors. Some publish comprehensive reports. Others release executive summaries that downplay or omit findings.
I've reviewed audit reports from major providers. The differences are striking. One audit examined the entire infrastructure, security practices, and encryption implementation. Another audit seemed to focus primarily on whether the company's claims about encryption methods were accurate. Both are labeled "third-party security audits," but they measure fundamentally different things.
This creates a false equivalence. A user can't determine whether an audit was thorough or cursory, comprehensive or limited in scope. The audit exists as a marketing asset rather than a transparency tool.
What Standardized Audits Should Cover
An industry standard for VPN audits should require examination of:
- Infrastructure security: How are servers secured? What physical access controls exist? How are credentials managed? What happens when someone gains unauthorized access?
- Encryption implementation: Is AES-256 actually implemented correctly? Are keys managed securely? Are random number generators properly seeded? What about forward secrecy and perfect forward secrecy?
- Data handling practices: What data is collected? Where is it stored? How long is it retained? What are the deletion procedures? Are backups handled securely?
- Privacy policy alignment: Do actual practices match published privacy policies? Are there discrepancies between claims and implementation?
- Jurisdictional compliance: Does the company comply with data retention laws in their jurisdiction? What happens when served with legal requests?
- Code review: Has any source code been reviewed by security researchers? What vulnerabilities were found historically? How quickly are patches deployed?
- Third-party dependencies: What external libraries and tools does the service use? Have those been audited? Are they vulnerable to supply chain attacks?
Currently, different audits examine different subsets of these areas. A standardized approach would require all major providers to submit to the same comprehensive evaluation framework.
How Standardization Would Work
The industry could establish a VPN audit standard similar to SOC 2 compliance for software companies or ISO 27001 certification for information security. Here's how it could operate:
- Establish audit criteria: A consortium of security experts, privacy advocates, and industry representatives defines what a comprehensive VPN audit should examine.
- Certify auditors: Pre-approved third-party firms conduct audits using the standardized framework, ensuring consistency and expertise.
- Require annual audits: Major VPN providers commit to annual audits. Results are published with standardized reporting formats.
- Public access to results: Audit findings are published in full or with only commercially sensitive information redacted. Users can review actual findings.
- Escalation procedures: If critical vulnerabilities are discovered, there's a standardized timeline for disclosure, remediation, and re-audit.
This approach works because it balances transparency with practical security. Companies can protect legitimate business secrets while revealing whether they actually implement claimed security measures.
The alternative is what we have now: audit theater where the existence of an audit matters more than its actual findings.
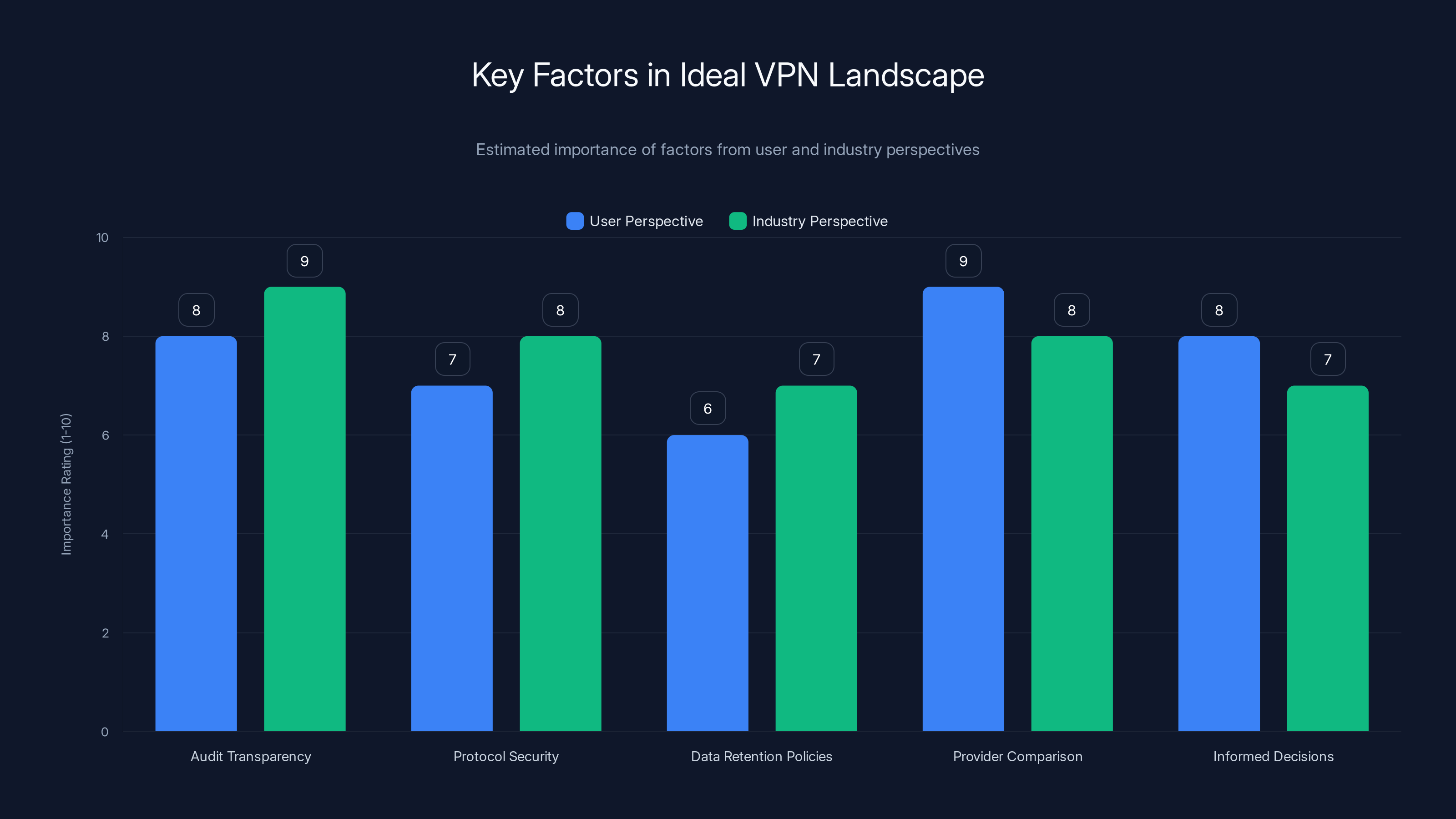
Audit transparency and provider comparison are highly valued by both users and industry, indicating key areas for VPN improvement. Estimated data.
Change #2: Protocol Transparency and Security Researcher Access
The Closed Protocol Problem
Cryptographic security depends on transparency. This isn't theoretical. It's a principle established over decades of security research. Strong encryption standards are strong precisely because thousands of experts have tried and failed to break them.
VPN protocols should follow the same principle. Yet many VPN companies maintain proprietary protocols or modifications to standard protocols without allowing independent review.
The argument companies make is reasonable on the surface: "Publishing our code reveals potential vulnerabilities." This is called "security through obscurity," and security experts universally reject it. A truly secure system is secure even when everyone knows how it works. An insecure system is vulnerable whether or not its details are public.
When a VPN company refuses to let security researchers review their code or protocols, it creates suspicion. Are they hiding inefficient encryption? Are there backdoors? Are there poor key management practices? Maybe not, but users can't know because they can't verify.
What Transparency Actually Means
Protocol transparency doesn't mean releasing everything. It means:
- Source code availability: Core encryption and key management code is available for review, either publicly or under controlled access for qualified security researchers.
- Protocol documentation: Technical documentation describes exactly how encryption is implemented, how keys are generated and managed, and what security assumptions the design makes.
- Responsible disclosure: When researchers discover vulnerabilities, there's a clear process for reporting, fixing, and disclosing the issue.
- Standards compliance: The VPN company commits to using established encryption standards rather than custom implementations that only they understand.
- Independent verification: Researchers can verify that the actual implementation matches the documentation and claims.
Consider the contrast between proprietary VPN protocols and established standards like Open VPN or Wire Guard. The open-source protocols have been reviewed extensively by the security community. Vulnerabilities are discovered, fixed, and hardened. The protocols are battle-tested by countless deployments.
A proprietary protocol might claim equal security, but that claim rests entirely on the company's assertion. There's no way to independently verify it.
The Researcher Access Model
Some VPN companies claim they "can't" publish their code for security reasons. But there's a middle ground: controlled researcher access.
A VPN company could establish a bug bounty program and responsible disclosure process. Qualified security researchers sign an NDA and receive access to review protocols and code. They conduct thorough security audits. They report vulnerabilities through a structured process. Critical issues get fixed before disclosure.
This approach is used by major tech companies, security software vendors, and other organizations handling sensitive security infrastructure. It protects legitimate business interests while enabling independent verification.
Without this transparency, VPN companies are essentially asking users to trust them based on marketing claims and optional third-party audits. With it, users can be confident that security researchers have reviewed the infrastructure and found it sound.
Real-World Impacts of Transparency
When VPN protocols lack transparency, several problems emerge:
Trust erosion: Users can't verify claims, so trust rests on brand reputation and marketing. A single breach or scandal shatters confidence completely.
Vulnerability discovery lag: Without external review, vulnerabilities stay hidden longer. When they're finally discovered, they may have affected users for years.
Standards divergence: Proprietary protocols prevent standardization. Each VPN company implements encryption differently, making the ecosystem harder to understand and audit.
Research stagnation: Security researchers focus on protocols they can review and understand. Proprietary protocols get less research attention, even if they're vulnerable.
Wire Guard, the modern VPN protocol, became popular partly because it's open and auditable. Researchers immediately recognized it as a significant security improvement over older protocols. That confidence was earned through transparency, not marketing.

Change #3: Jurisdiction Transparency and Standardized Data Retention Policies
The Jurisdiction Confusion Problem
VPN companies love to advertise their jurisdiction. "Incorporated in Panama!" "Registered in Singapore!" "Headquartered in Romania!" The implication is that these neutral countries provide privacy protection.
This is misleading. Jurisdiction matters, but not in the way marketing suggests.
A VPN company operating from a privacy-friendly country can still be compelled to provide user data through mutual legal assistance treaties, extradition requests, or even political pressure. The actual protection depends on complex legal arrangements between countries, the specific nature of the request, and the evidence presented.
I've reviewed privacy policies claiming "zero-logs" but allowing data retention for legitimate legal compliance. Legitimate is subjective. Does it include anti-money laundering regulations? Counter-terrorism laws? Copyright enforcement? The policies often don't specify.
What Transparency Should Include
VPN companies should publish clear, standardized documentation about:
- Actual legal jurisdiction: Not just where they claim to be incorporated, but where servers are physically located and where legal authority actually applies.
- Data retention requirements: What data must be retained due to legal requirements in their jurisdiction? For how long? Under what circumstances?
- Legal request procedures: What happens when a government serves a legal request? Is there a standardized process? Can the company notify users?
- Baseline data collection: Apart from legal requirements, what data does the service collect? User behavior data? Technical diagnostics? Connection logs? Payment information?
- Data deletion procedures: How is user data deleted? Are backups destroyed? What's the timeline? Are there any exceptions?
- Transparency reporting: Many companies publish transparency reports showing how many legal requests they receive. What categories of requests? How many do they comply with?
- Jurisdictional changes: If a VPN company's jurisdiction changes due to expansion or restructuring, how does that affect user privacy?
This information should be published in a standardized format, making it easy to compare different providers and understand the actual legal protections offered.
Standardized Policy Frameworks
The industry could adopt standardized privacy policy templates covering:
Data retention baseline: In the absence of legal requirements, the company retains no connection data, no traffic logs, and no behavioral data. This baseline applies in all jurisdictions.
Legal request compliance: When served with a legal request, the company follows a standardized process: internal review, user notification (where legally permitted), and compliance with valid court orders. Requests for data the company doesn't retain are declined.
Jurisdiction-specific disclosures: For each country where the company operates, disclosure of specific legal requirements that override the baseline policy.
Escalation procedures: If a jurisdiction demands data collection practices that violate the stated baseline, the company either complies (transparently disclosing the change) or ceases operations there.
Regular review: Annual review of jurisdiction-specific requirements. If legal demands change, privacy policies are updated accordingly.
This framework prevents the current situation where vague privacy policies create plausible deniability. A company couldn't claim "zero logs" while retaining behavioral data. They couldn't obscure which legal requirements actually apply in their jurisdiction.
Transparency Reporting as Standard
Many companies now publish transparency reports showing legal request volume. The VPN industry should standardize this reporting:
- Request volume: How many legal requests does the company receive monthly, quarterly, and annually?
- Request types: What categories? Data requests about specific accounts? Requests for user activity logs? Traffic data? Identifying information?
- Compliance rate: How many requests do they comply with? How many do they decline? Why?
- Jurisdictions: Which countries generate the most requests? How do different governments approach data requests?
- Disclosure notifications: When legally permitted, do they notify users of requests?
- Geopolitical trends: Are legal requests changing over time? Are certain countries becoming more aggressive?
Transparency reporting enables users to understand the actual privacy risks. A provider receiving minimal legal requests operates differently than one inundated with requests. A provider declining most requests offers more protection than one complying with everything.
Published data transforms privacy protection from a marketing claim to a verifiable fact.

Estimated data shows that infrastructure security and encryption implementation are likely to receive the most focus in standardized VPN security audits, followed by data handling practices and privacy policy alignment.
Implementation Roadmap: How the Industry Can Change
Phase 1: Industry Consensus (2026 Q1-Q2)
The VPN industry needs to establish working groups focused on each of the three core changes. These groups should include security experts, privacy advocates, industry representatives, and legal specialists.
Each group's mandate: define standards, establish implementation frameworks, and create transition timelines. The output should be published standards that any VPN company can adopt.
This isn't regulatory. It's the industry setting its own standards before regulation becomes necessary. Companies that embrace these standards early position themselves as genuine privacy advocates rather than marketing-driven services.
Phase 2: Early Adoption (2026 Q3-Q4)
The first wave of VPN companies commit to the new standards. They conduct comprehensive security audits using the standardized framework. They publish protocols for independent review or establish controlled researcher access programs. They update privacy policies with standardized jurisdiction and data retention disclosures.
Early adopters position themselves as privacy leaders. They differentiate themselves from competitors still using outdated approaches. They attract users who value verifiable privacy over marketing claims.
This phase creates competitive pressure. Companies that don't adopt standards become less trustworthy by comparison.
Phase 3: Widespread Adoption (2027+)
As more companies adopt standards, they become industry baseline expectations. Transparency becomes normal. Independent audits become standard. Jurisdiction disclosures become expected.
Companies that resist standardization become outliers. Users question why they won't undergo audits or disclose their practices. The marketing advantage flips from secrecy to transparency.
Within two years, standards-based practices could become the norm rather than the exception.
Barriers to Change: Why This Hasn't Happened Yet
Financial Resistance
Independent audits cost money. Meaningful security audits for a major VPN service can cost
But consider the alternative: a single major breach or privacy scandal could cost millions in lost users, lawsuits, and reputation damage. Audits are insurance. They're also table stakes for any service claiming to prioritize privacy.
Competitive Disadvantage Fears
Some VPN companies argue that transparency reveals competitive advantages or technical approaches that competitors could copy. This is real but manageable. Commercially sensitive information can be redacted from published audit reports. Protocols can be disclosed under controlled access agreements.
The real concern is that transparency might reveal vulnerabilities or suboptimal practices. That's exactly why audits matter. Better to discover problems internally through a rigorous audit than externally through a breach.
Regulatory Uncertainty
VPN companies operate in a complex regulatory landscape. Some jurisdictions are hostile to VPNs. Others are indifferent. Some demand data access. Standardized policies could lock companies into specific practices that later conflict with local regulations.
But regulatory uncertainty is exactly why transparency matters. Clear policies about what data can and can't be retained provide legal protection. They establish companies' practices as reasonable and foreseeable.
Marketing Pressure
VPN marketing thrives on bold claims. "100% encrypted," "Unhackable," "Zero logs." These statements drive customer acquisition. Standardized transparency might reveal nuance: "Encrypted except for metadata required for service operation," "Secure against common attacks, vulnerabilities possible," "No connection logs but technical diagnostics retained."
Nuance doesn't sell as well as absolutes. But transparency builds long-term trust better than marketing claims ever will.
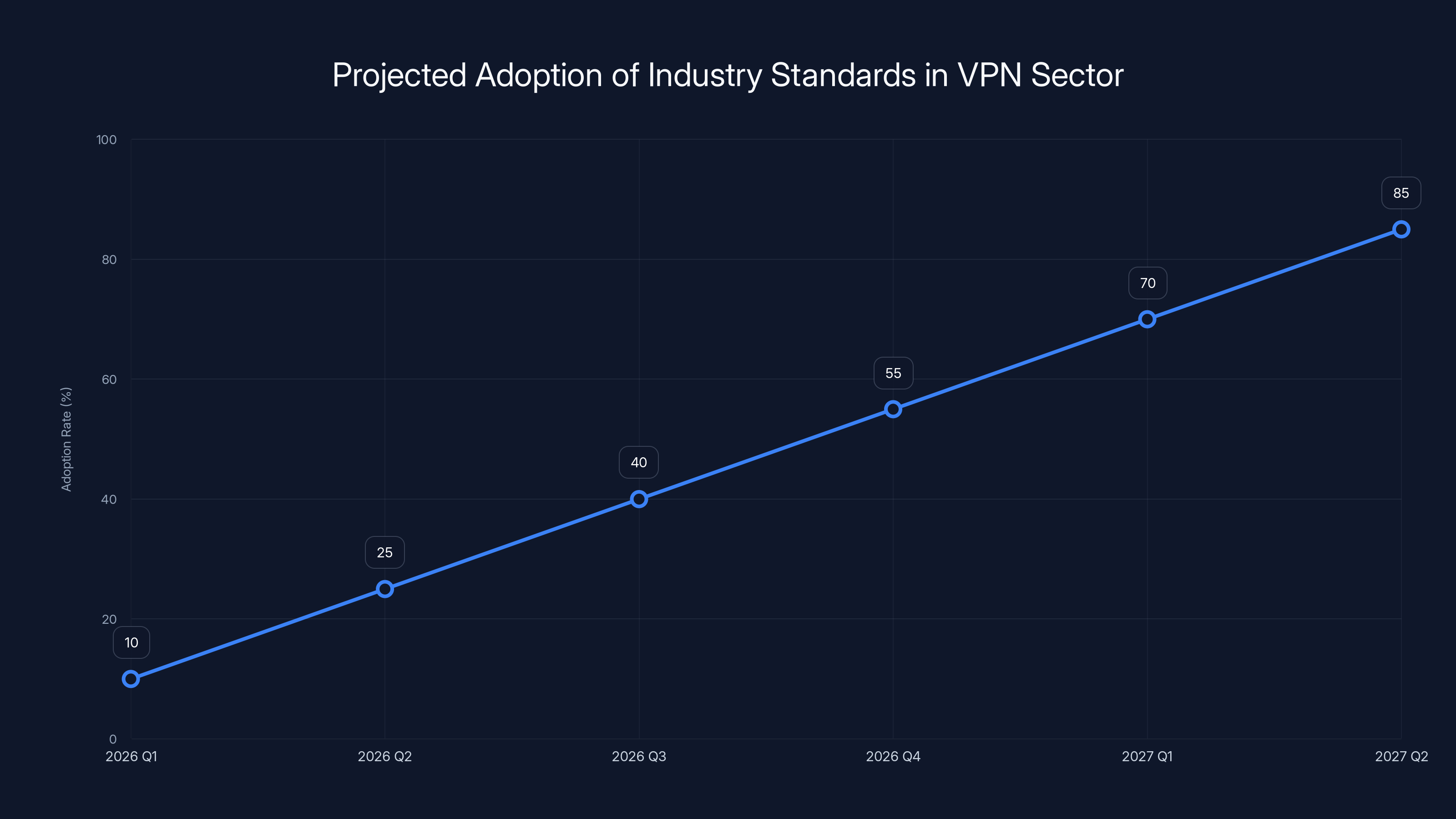
The projected adoption rate of new industry standards by VPN companies shows a significant increase from 10% in early 2026 to 85% by mid-2027. This trend highlights the industry's shift towards self-regulation and transparency. Estimated data.
What Success Looks Like: The Ideal VPN Landscape
User Perspective
In an industry that's adopted these standards, a user evaluating VPN services could:
- Review independent audit results: Access publicly available third-party audit reports showing exactly what security testing was conducted and what was found.
- Understand protocol security: Read transparent technical documentation or know that security researchers have independently reviewed the protocols and endorsed their security.
- Know data retention policies: Read clear, standardized disclosures about what data is collected, where, for how long, and under what circumstances.
- Compare providers directly: Use standardized metrics and reporting to compare different VPN services on security, transparency, and privacy protection.
- Make informed decisions: Base privacy decisions on verifiable facts rather than marketing claims.
This is possible. It requires industry commitment, but it's achievable.
Industry Perspective
For VPN providers, standards offer benefits:
- Differentiation: Companies exceeding standards become privacy leaders. This attracts privacy-conscious users willing to pay premium prices.
- Risk reduction: Audits identify vulnerabilities before breaches happen. Legal clarity prevents regulatory surprises.
- Trust building: Transparency builds genuine user confidence faster than any marketing campaign.
- Industry credibility: Standardized practices make the entire VPN industry more trustworthy, expanding the user base.
Companies that resist standards become increasingly isolated as competitors embrace transparency.
Market Dynamics
As standards become widespread, several market shifts occur:
Quality consolidation: Budget VPN services without resources for audits and transparency fall away. The market consolidates around providers who can meet standards.
Price alignment: As transparency becomes standard, companies can't hide mediocre security behind marketing. Pricing aligns with actual security and service quality.
Competitive focus shifts: Instead of competing on marketing claims, VPN companies compete on actual security, performance, and privacy protection.
User migration: Users realize their current provider doesn't meet standards and switch to ones that do. This creates pressure for rapid industry-wide adoption.

Timeline: Realistic Implementation
2026: The Year of Transition
Q1-Q2: Standards development (January-June) Industry working groups finalize audit standards, protocol transparency requirements, and jurisdiction disclosure frameworks. These are published as non-binding guidelines.
Q3-Q4: Early adoption (July-December) Major VPN providers commit to standards. First independent audits are conducted. Protocols are opened for review. Privacy policies are updated with standardized disclosures.
2027: Mainstream Adoption
Standards become industry baseline. Most major providers publish audit results, allow protocol review, and disclose jurisdiction practices clearly. Providers without standards lose competitive position.
2028+: New Baseline
Transparency becomes expected. The industry consolidates around providers meeting standards. Users evaluate VPN services based on verifiable facts rather than marketing claims.

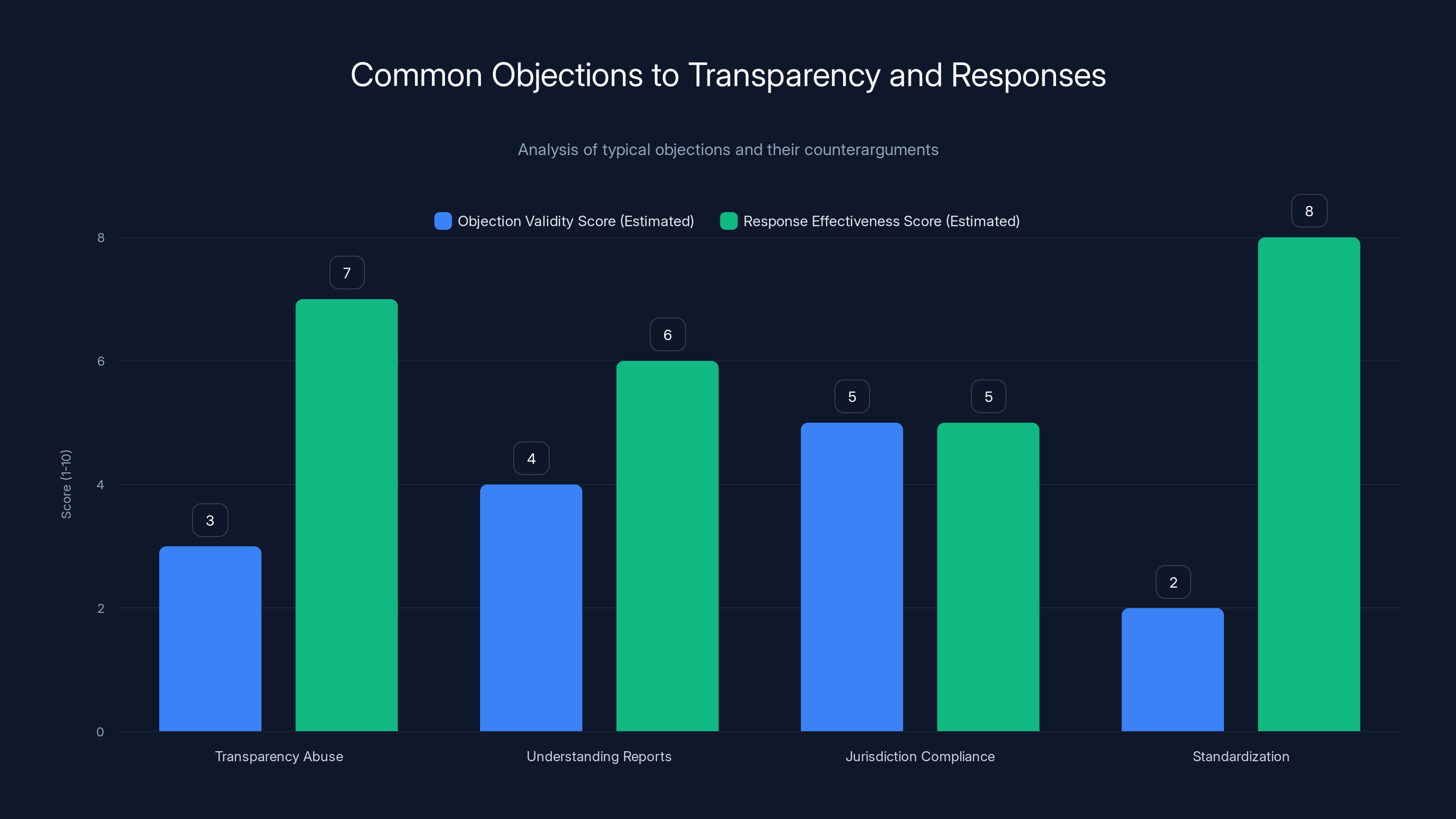
The chart compares the perceived validity of common objections to transparency with the effectiveness of responses. Responses generally score higher, indicating strong counterarguments. Estimated data.
Industry Players and Their Role
Large Providers
Major VPN companies have resources to lead. They should publish comprehensive audits, open protocols for review, and establish transparent policies. This positions them as industry leaders and makes standards adoption easier for smaller competitors to follow.
Security Firms
Cybersecurity companies providing audit services should standardize their VPN audit methodologies. This enables direct comparison across providers and builds industry credibility.
Privacy Advocates
Advocacy organizations focusing on privacy and digital rights should push for standardized transparency. Public pressure drives industry change when self-interest doesn't.
Regulatory Bodies
Governments should consider light-touch regulation requiring transparency rather than specific technical standards. This lets companies innovate while ensuring users have access to verifiable information.
Security Researchers
Independent security researchers should demand protocol transparency and establish bug bounty programs. Their work validates claims and drives improvements.
Common Objections and Responses
"Transparency will be abused by bad actors"
Possibly, but transparency is inherently more secure than secrecy. Open protocols enable the security community to identify problems. Closed protocols hide them. The security principle stands: a system is only truly secure if it remains secure even with full transparency about its design.
"Users won't understand audit reports"
True for complex technical findings. But audit reports can be summarized: "No critical vulnerabilities found," "Three minor issues discovered and fixed," "One significant vulnerability identified, remediation in progress." Users can understand these summaries and make informed decisions.
"Compliance with different jurisdictions is impossible"
Partially true, but manageable. A VPN company operating in multiple jurisdictions can disclose which legal requirements apply in each. If a jurisdiction demands practices violating their baseline policy, they can exit that market or transparently acknowledge the change.
"Standardization stifles innovation"
Conversely, standardization enables innovation. When security basics are standardized, companies innovate in performance, user experience, and advanced features. Innovation driven by race-to-the-bottom marketing decreases.

Building User Advocacy
Change requires user demand. Here's how users can push for industry standards:
Ask about audits: When evaluating VPN services, request recent third-party audit reports. If companies won't provide them, move to alternatives.
Demand transparency: Ask VPN providers about their data retention policies, protocol documentation, and jurisdiction details. Expect clear answers, not marketing language.
Support standard-compliant providers: Choose VPN services that publish audits, open protocols, and maintain transparent policies. Your subscription feeds the business model.
Report violations: If a VPN provider makes claims their practices don't support, report them to regulatory bodies or privacy advocates.
Participate in discussions: Engage with industry conversations about standards. User voices matter.

The Path Forward: What Each Stakeholder Should Do Now
VPN Companies
- Immediately: Review your current security, transparency, and audit practices against the standards outlined in this article.
- Q1 2026: Commit publicly to adopting industry standards, even if implementation takes longer.
- Q2-Q3 2026: Conduct or update independent security audits using the standardized framework.
- Q3-Q4 2026: Publish protocols for researcher review or establish controlled access bug bounty programs.
- Ongoing: Publish annual transparency reports showing legal requests received and compliance.
Users and Privacy Advocates
- Immediately: Evaluate your current VPN provider against the standards outlined here. Are they transparent? Do they publish audits? Can you verify their claims?
- This month: Ask your VPN provider directly about their audit practices, protocol transparency, and jurisdiction policies. Document their responses.
- This quarter: If current provider doesn't meet standards, research alternatives that do and switch.
- Ongoing: Share information about standards-compliant providers with your network.
Security Researchers
- Immediately: Develop standardized VPN audit methodologies and publish them as community resources.
- This year: Establish or strengthen bug bounty programs for VPN protocols.
- Ongoing: Review VPN implementations and publish findings. Help the industry improve through research.
Regulatory Bodies
- This year: Consider light-touch regulation requiring VPN transparency without mandating specific technical approaches.
- Going forward: Establish frameworks recognizing standards-compliant providers, reducing regulatory burden for transparency leaders.

Why This Matters Beyond VPN
The VPN industry's lack of standards reflects a broader problem in privacy-focused technology: the absence of clear, verifiable accountability mechanisms.
When users trust a service with sensitive information, they need to know that trust is earned through demonstrated security and transparency, not just marketing claims. The standards discussed here apply to VPNs, but the principles extend to password managers, encrypted messaging apps, and any service claiming privacy protection.
If the VPN industry can adopt meaningful standards in 2026, it sets a template for other privacy-focused services. It demonstrates that transparency and security can coexist. It shows that meaningful user protection requires more than marketing and more than optional audits.
The stakes are real. People rely on VPNs for genuine security: activists in oppressive regimes, journalists protecting sources, ordinary people protecting their privacy from governments and corporations. These users deserve more than a service that makes marketing claims they can't verify.
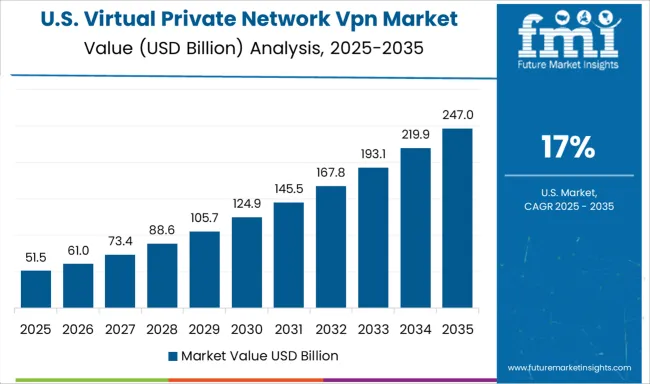
Conclusion: The Industry Can Change, But Choice Matters
I've spent this entire article arguing that the VPN industry needs to change. Now I need to be honest about something: change is optional. Nothing in this article is inevitable.
VPN companies can continue operating without independent audits, closed protocols, and vague jurisdiction policies. Users can continue trusting services based on marketing claims. The industry can keep operating in the gray zone that currently exists.
But the window for voluntary change is closing. As governments increase scrutiny of VPN services, as privacy becomes a more prominent issue, as users become more skeptical of unverified claims, pressure for change will increase. Companies that adopt standards now position themselves as leaders. Companies that resist will eventually face regulatory requirements that are far more onerous than voluntary standards would be.
The three changes outlined here are achievable. They're not technologically revolutionary. They're not impossibly expensive. They require commitment, transparency, and willingness to stand behind claims. That's actually the bare minimum for a service claiming to prioritize privacy.
Here's what I want to see in 2026: VPN companies publishing annual security audit reports. Protocols opened for researcher review. Privacy policies with clear, standardized disclosures about data retention and jurisdiction practices. These aren't radical asks. They're baseline expectations for a privacy-focused service.
If the industry adopts these standards, users get genuine protection instead of marketing theater. The industry gets credibility and legitimacy. The entire privacy technology space gets a template for meaningful transparency.
If the industry doesn't adopt them voluntarily, regulation will eventually impose something far stricter.
The choice is actually pretty simple.
FAQ
What exactly is a VPN and why do people use them?
A Virtual Private Network (VPN) encrypts your internet traffic and routes it through a secure server in another location, making your activity harder to track by your internet service provider, government agencies, or other observers. People use VPNs for privacy protection, accessing geo-restricted content, securing connections on public Wi-Fi, and protecting sensitive work communications.
What's the difference between a no-logs policy and actual data privacy?
A no-logs policy claims the VPN provider doesn't store connection records or traffic data. However, "logs" is ambiguous. Some providers collect technical diagnostics, user behavior data, or metadata while claiming no logs. Actual privacy requires clear disclosure of what data is collected, where it's stored, who can access it, and for how long. A standardized policy framework makes these distinctions explicit rather than allowing marketing wiggle room.
How can users verify that a VPN company actually does what it claims?
Users can request third-party audit reports and review the actual findings rather than just trusting that audits exist. They can research the VPN company's jurisdiction and legal obligations in that country. They can ask about bug bounty programs and researcher access, which indicate the company is confident enough to invite external security review. They can compare privacy policies directly and look for specific, verifiable claims rather than marketing language.
Why haven't VPN companies adopted these standards already?
Audits are expensive. Transparency requires disclosing practices that might seem less impressive than marketing claims suggest. Some companies fear revealing competitive approaches. And frankly, current opacity serves marketing interests. Bold claims like "unhackable" and "military-grade" are easier to make when users can't independently verify them. There's no financial pressure to change when the status quo drives customer acquisition.
Could standardized audits actually find problems with major VPN providers?
Absolutely. History shows that comprehensive security audits often identify vulnerabilities even in well-regarded services. This isn't a reason to avoid audits. It's a reason to conduct them. Better to discover problems through controlled testing than through breach reports. A provider that discovers and fixes issues through audits demonstrates commitment to security improvement.
What should someone do if their current VPN provider doesn't meet these standards?
First, research VPN providers that publish audit results, allow protocol review, and maintain transparent jurisdiction policies. Compare their practices against the standards outlined in this article. Evaluate whether they actually implement what they claim. Once you find a provider meeting standards, migrate your account. This creates market pressure for other providers to improve. Your subscription choices directly fund business models. Supporting transparent companies rewards their approach.
How would standardized jurisdiction disclosure help users?
Currently, users don't know what happens if their VPN provider receives a legal request for their data. Standardized disclosure would explain the company's jurisdiction, what legal requests they've received, how many they comply with, and what data they can actually provide. Users could understand actual privacy risks instead of relying on marketing claims. They could compare providers directly using standardized metrics.
Are there VPN providers already meeting these standards?
Some providers publish audit results and maintain transparent policies. However, the landscape is fragmented. Different providers meet different criteria but rarely all three (audits, protocol transparency, jurisdiction disclosure) simultaneously. That's precisely why industry-wide standardization matters. It would make compliance normal rather than exceptional.
Could regulation force these standards on the VPN industry?
Possibly, but regulatory approaches often create unintended consequences. Light-touch regulation requiring transparency while letting companies innovate on technical approaches would be healthier than heavy-handed mandates. The better scenario is that the industry adopts these standards voluntarily, making regulation unnecessary. That requires industry commitment happening in 2026.

Looking Ahead: The VPN Industry in 2027
I want to paint a picture of what's possible. Imagine a VPN landscape where:
- Users can read recent, comprehensive audit reports showing exactly what security testing was conducted and what vulnerabilities were found.
- Security researchers have reviewed VPN protocols and endorsed their security, or identified issues that companies are actively fixing.
- Privacy policies clearly state what data is collected, where, for how long, and under what circumstances.
- Transparency reports show legal request volume, request types, and compliance rates.
- Companies compete on actual security and performance rather than marketing claims.
This isn't fantasy. It's achievable with industry commitment in 2026.
The alternative is continued opacity, marketing theater, and user distrust. Users have legitimate privacy needs. They deserve services they can actually verify rather than trust blindly. The VPN industry can meet that need by embracing transparency and standardization.
The choice belongs to the industry. But the pressure belongs to users. Make it clear that you demand verifiable privacy protection, not marketing claims. Your choice of VPN provider is your vote for the kind of industry you want to exist.
Change starts now.
Key Takeaways
- VPN industry lacks standardized independent security audits, creating verification theater instead of genuine transparency
- Protocol transparency through researcher access is essential; security through obscurity is outdated cryptographic principle
- Standardized jurisdiction disclosure would clarify actual privacy protection levels vs. marketing claims about neutral locations
- Industry standards in 2026 can prevent stricter regulation while establishing baseline transparency expectations
- Users demanding audits, protocol transparency, and clear policies drive market pressure for industry-wide standardization