AMD's Stack Warp Vulnerability: A Deep Dive Into the Zen CPU Security Flaw
It's January 2025, and security researchers just dropped something genuinely alarming. The CISPA Helmholtz Center for Information Security in Germany unveiled a hardware-level vulnerability in AMD's Zen processors that fundamentally breaks the security model millions of people rely on. They called it Stack Warp, and it's the kind of flaw that keeps cloud infrastructure teams up at night.
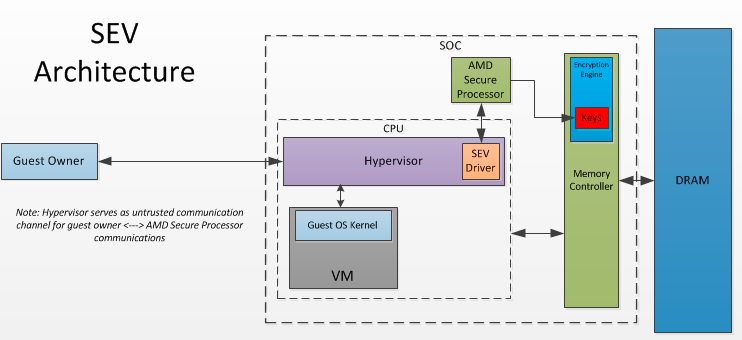
Here's the core problem: AMD's SEV-SNP (Secure Encrypted Virtualization with Secure Nested Paging) technology was supposed to create an impenetrable fortress around virtual machines. The entire premise is that even if someone has complete control over the host system, they still can't peek inside an encrypted VM. But Stack Warp breaks that premise by manipulating how the CPU tracks the call stack, essentially tricking the processor into revealing secrets that should stay hidden.
What makes this particularly concerning is the scope. The vulnerability affects AMD Zen processors from the first generation all the way through Zen 5, meaning potentially millions of devices worldwide are vulnerable. And the attack surface includes not just data theft, but also remote code execution and privilege escalation within supposedly isolated environments.
The good news? You can't just stumble into exploiting this accidentally. AMD's own assessment gave it a CVSS score of 3.2 out of 10, rated as low severity, primarily because the attacker needs privileged access to the host system first. But that's also the bad news: inside cloud providers, data centers, and corporate virtualization environments, there's no shortage of insiders, administrators, or sophisticated threat actors who might already have that access.
Let's break down what Stack Warp actually is, how it works, who it affects, and what you should do about it right now.
TL; DR
- Stack Warp is a hardware vulnerability in AMD Zen 1-5 CPUs that breaks SEV-SNP protections by manipulating the stack pointer
- Attacks require host-level access, meaning insider threats or compromised cloud providers pose the primary risk
- CVE-2025-29943 was assigned a CVSS score of 3.2/10 (low severity) but enables RCE, privilege escalation, and private key theft
- AMD has released patches, but deployment depends on cloud providers and data center operators applying them quickly
- Cloud VM users should verify patches immediately, while enterprise users running confidential VMs should audit access controls and monitor for suspicious activity
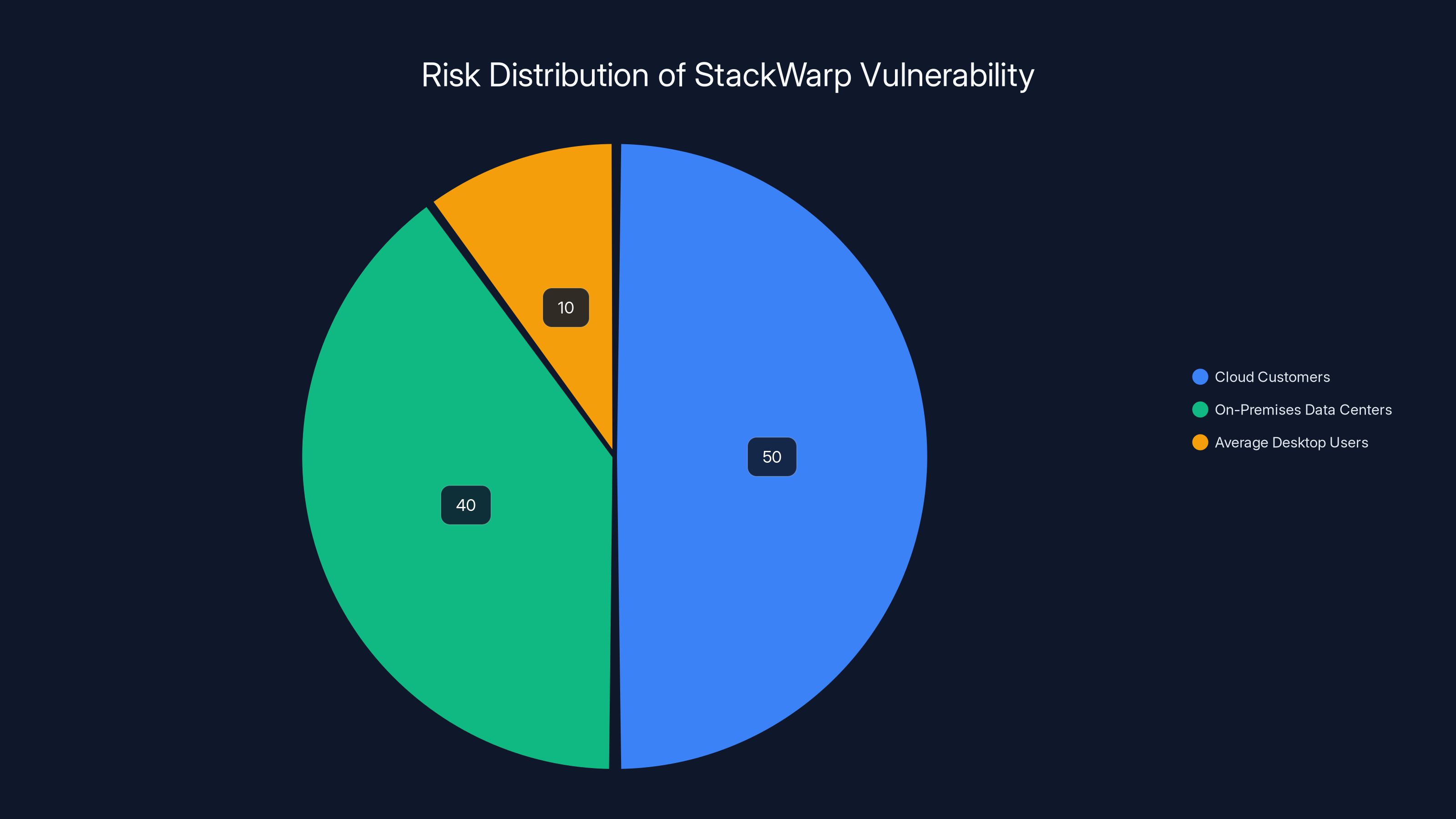
Cloud customers and on-premises data centers are most at risk from StackWarp, with cloud customers facing the highest exposure. Estimated data.
Understanding the Technical Foundation: What SEV-SNP Actually Protects
Before we can understand what Stack Warp breaks, you need to know what SEV-SNP is supposed to do. It's one of the most important security innovations in cloud infrastructure over the past decade.
Traditional virtualization creates an isolation layer between VMs and the host system, but it's fundamentally a software boundary. The hypervisor (the software that manages multiple VMs on one physical machine) still has complete memory access. If you're running a confidential database, a machine learning model with proprietary weights, or cryptocurrency private keys in a VM, the hypervisor could theoretically read all of it.
AMD's answer was to move encryption down to the hardware level. With SEV-SNP enabled, the CPU itself encrypts VM memory using keys that never leave the processor. Even the hypervisor can't decrypt the contents. It's a clever bit of hardware engineering: the CPU maintains a separate key for each VM, encrypts all memory writes transparently, and decrypts on reads. The hypervisor can manage VMs, allocate resources, and shuffle memory around, but it physically cannot read the actual data inside.
This technology became critical infrastructure. Microsoft Azure, Google Cloud, and AWS all offer confidential computing services built on top of AMD's technology. Financial institutions use it to run sensitive calculations without trusting the cloud provider. Healthcare organizations use it to process patient data. Cryptocurrency firms use it to protect private keys.
The architecture seems sound: encryption at rest, encryption in transit, encryption at the CPU level. But Stack Warp reveals a gap that nobody really focused on until now.
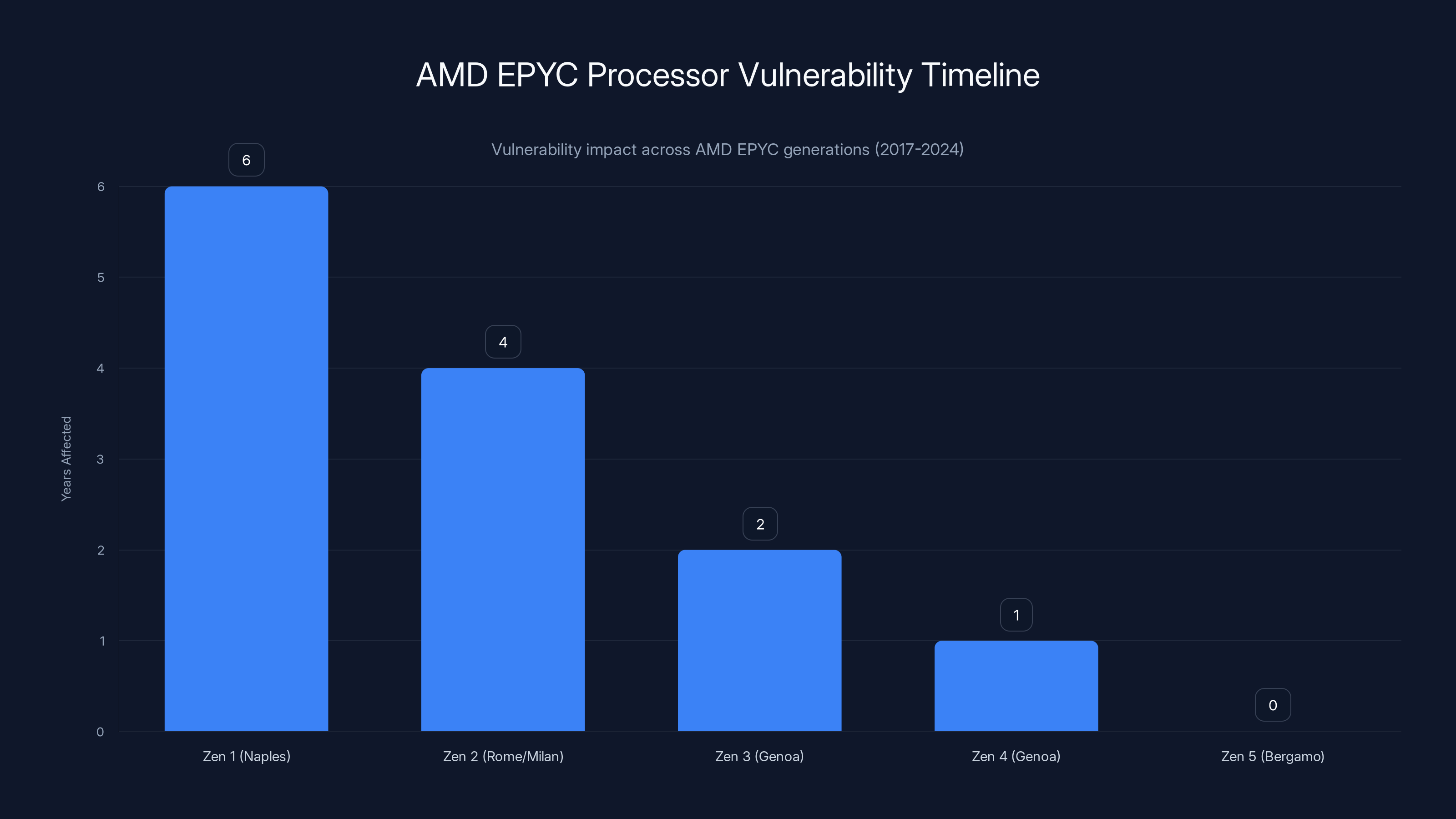
Virtually every AMD EPYC processor built in the last six years is affected by the StackWarp vulnerability, impacting multiple generations of server processors.
What Is Stack Warp and How Does It Work?
Stack Warp isn't a buffer overflow. It's not a memory corruption vulnerability in the traditional sense. It's something more subtle and more dangerous: a logical flaw in how the CPU manages the stack pointer and validates memory access.
Every program uses a stack. It's a region of memory where function calls store local variables, return addresses, and other temporary data. The CPU maintains a stack pointer (SP) register that points to the current top of the stack. When you call a function, the CPU pushes the return address onto the stack and increments the pointer. When the function returns, it pops that address and jumps back.
Now here's the vulnerability: Stack Warp allows a privileged attacker (someone with access to the hypervisor) to manipulate how the guest VM's stack pointer is validated inside the CPU's security context. By carefully crafting page table entries and memory access patterns, an attacker can trick the CPU into performing memory operations outside the intended boundaries of the guest VM's encrypted memory region.
The researchers demonstrated this by constructing specific memory layouts within the hypervisor and then executing instructions within the guest VM that would normally be blocked. The CPU's SEV-SNP security logic didn't catch the boundary violation because the exploit carefully walked through edge cases in how the CPU checks whether a memory address is actually within the encrypted region.
The attack is complex. It requires:
- Hypervisor-level access to set up malicious page tables and memory regions
- Knowledge of the guest VM's memory layout (which a hypervisor would have)
- Precise timing and instruction sequencing to exploit the race condition in the CPU's security logic
- A vulnerable AMD Zen processor running with SEV-SNP enabled
Once these conditions are met, the attacker can read arbitrary memory from within the guest VM, write to guest memory without authorization, or redirect execution flow.
The researchers proved this works by successfully recovering an RSA-2048 private key from a guest VM. In another test, they bypassed Open SSH password authentication by manipulating the authentication logic running inside the protected VM. These aren't theoretical attacks. They're reproducible, and they work on real hardware.

Which AMD Processors Are Vulnerable?
This is where the scope becomes clear: virtually every AMD EPYC processor built in the last six years is affected.
Stack Warp impacts:
- Zen 1 (EPYC Naples): Released in 2017
- Zen 2 (EPYC Rome/Milan): Released in 2019-2021
- Zen 3 (EPYC Genoa): Released in 2022
- Zen 4 (EPYC Genoa): Released in 2023
- Zen 5 (EPYC Bergamo): Released in 2024
That's roughly six years of server processors across multiple generations. In terms of installed base, this is massive. Every hyperscale cloud provider has AMD Zen processors in their data centers. Every financial institution running on-premises servers with AMD EPYC chips is vulnerable. Every hosting provider offering confidential VM services is vulnerable.
The vulnerability doesn't affect consumer-grade AMD Ryzen processors (at least not publicly disclosed yet), but the enterprise and cloud infrastructure impact is enormous.
AMD has assigned CVE-2025-29943 to track this vulnerability. The CVSS score is 3.2/10, which officially puts it in the "low severity" category according to industry standards. This rating is somewhat misleading because it heavily weights the "requires privileged access" factor. In reality, the impact is severe if you're running confidential workloads in a cloud environment where the attacker has insider access.

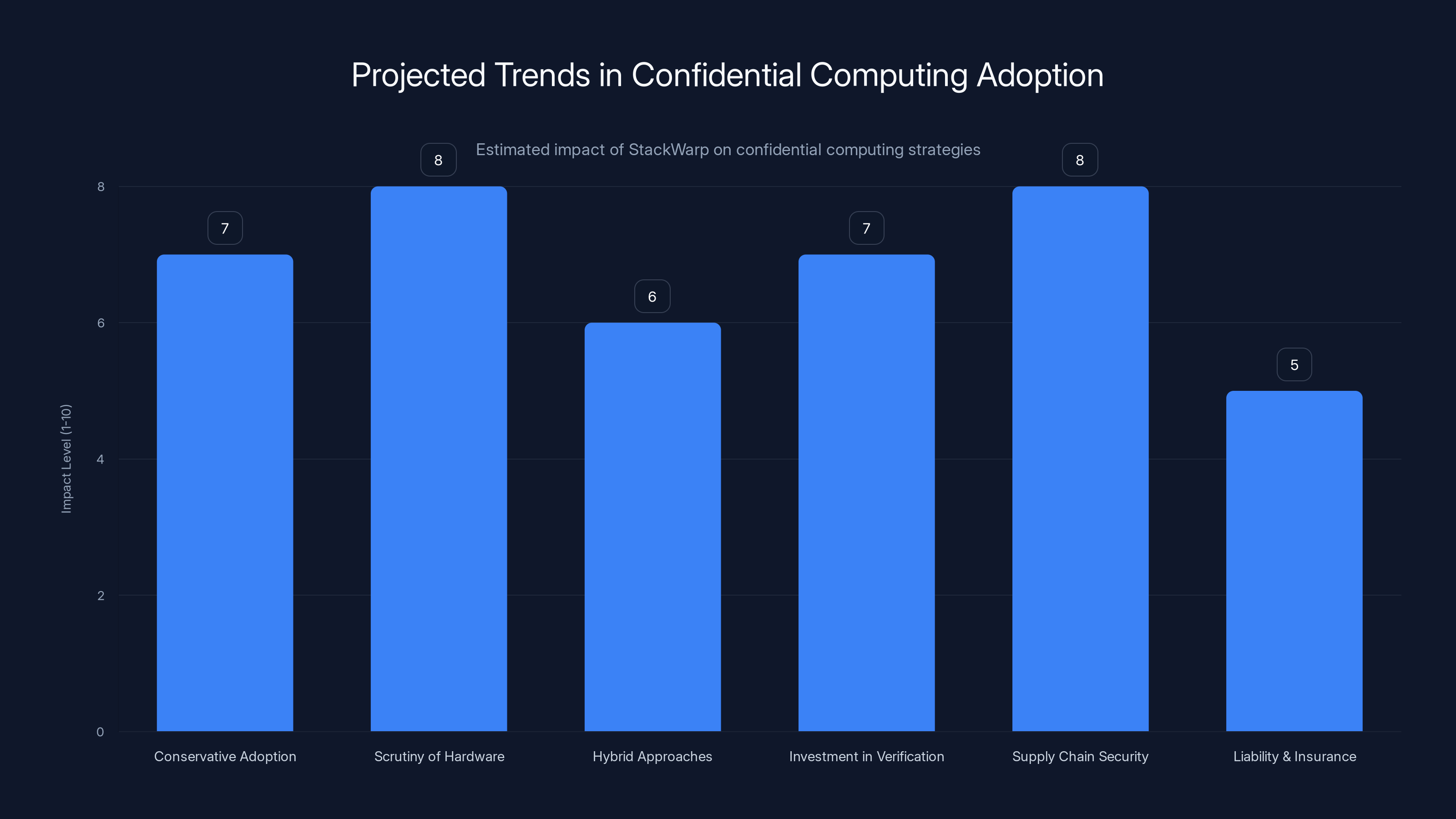
Estimated data suggests that scrutiny of hardware claims and supply chain security will see the highest impact due to StackWarp, with organizations adopting more conservative and hybrid approaches.
The Real-World Threat Model: Who's Actually at Risk?
Understanding whether you're at risk requires understanding the attack requirements clearly.
You're vulnerable if all of these are true:
- You're running workloads in a confidential VM or confidential container service powered by AMD Zen processors
- An attacker has hypervisor-level access (either as a malicious insider, via a compromised admin account, or through a separate hypervisor vulnerability)
- The VM is still running an unpatched kernel that hasn't applied mitigations
- You haven't verified your cloud provider has applied firmware patches
Let's walk through the actual risk tiers:
Tier 1: Cloud Users (High Risk Until Patched)
If you're using confidential VM services from Azure Confidential Computing, Google Confidential Computing, or AWS's confidential instance types, you're the primary target. These services specifically advertise protection against malicious cloud providers or insider threats. Stack Warp directly undermines that promise.
However, the risk depends on your threat model. If you trust your cloud provider completely and only worry about external attackers, your risk is lower. If you're using these services specifically to protect against insider threats (which is their main value proposition), you're at higher risk until patches are deployed.
Tier 2: Financial and Cryptographic Workloads (Critical Risk)
Organizations running cryptographic operations, private key management, or financial calculations in confidential VMs face the highest risk. Stack Warp specifically enables the recovery of private keys, which is devastating for cryptocurrency exchanges, certificate authorities, and payment processors.
The researchers' successful recovery of an RSA-2048 private key proves this isn't theoretical. A sophisticated attacker with insider access could potentially compromise the entire security infrastructure of a financial institution or crypto firm.
Tier 3: On-Premises and Private Cloud (Medium-High Risk)
Organizations running their own data centers with AMD EPYC processors and SEV-SNP enabled face risk from malicious system administrators or attackers who've compromised administrative access. The risk is somewhat lower than public cloud (fewer potential insider threats), but the impact is still severe if exploitation occurs.
Tier 4: Development and Test Environments (Lower Risk)
If you're running non-production workloads in confidential VMs, the risk is lower simply because there's less valuable data to steal. But this should still be patched because test environments sometimes contain production-like data or secrets.

How Researchers Discovered Stack Warp
Understanding how this vulnerability was found gives you insight into how many more might exist in similar systems.
The researchers at CISPA approached the problem from first principles. They knew SEV-SNP was supposed to be the state-of-the-art in hardware-based memory encryption. So they asked themselves: what are the fundamental assumptions in the design, and which ones might be wrong?
They focused on the boundary checking logic. SEV-SNP works by validating that every memory operation initiated from inside a guest VM actually targets that VM's encrypted memory region. But CPU designs are complex, with multiple execution paths, edge cases, and optimizations. The researchers hypothesized that there might be cases where the validation gets bypassed.
Specifically, they looked at how the CPU handles the stack pointer. The stack is special in CPU design because it's accessed extremely frequently and performance is critical. Optimizations here could create security gaps.
They discovered that by constructing specific patterns of memory access and leveraging the way the CPU's security logic handles stack operations, they could create scenarios where the boundary check didn't trigger. The attack required precise knowledge of CPU microarchitecture and millions of iterations of fuzzing and testing, but eventually they found reproducible cases.
The research demonstrates a critical lesson: even heavily scrutinized, formally verified security mechanisms can have subtle logical flaws that only appear under very specific conditions. This is why ongoing security research is essential.
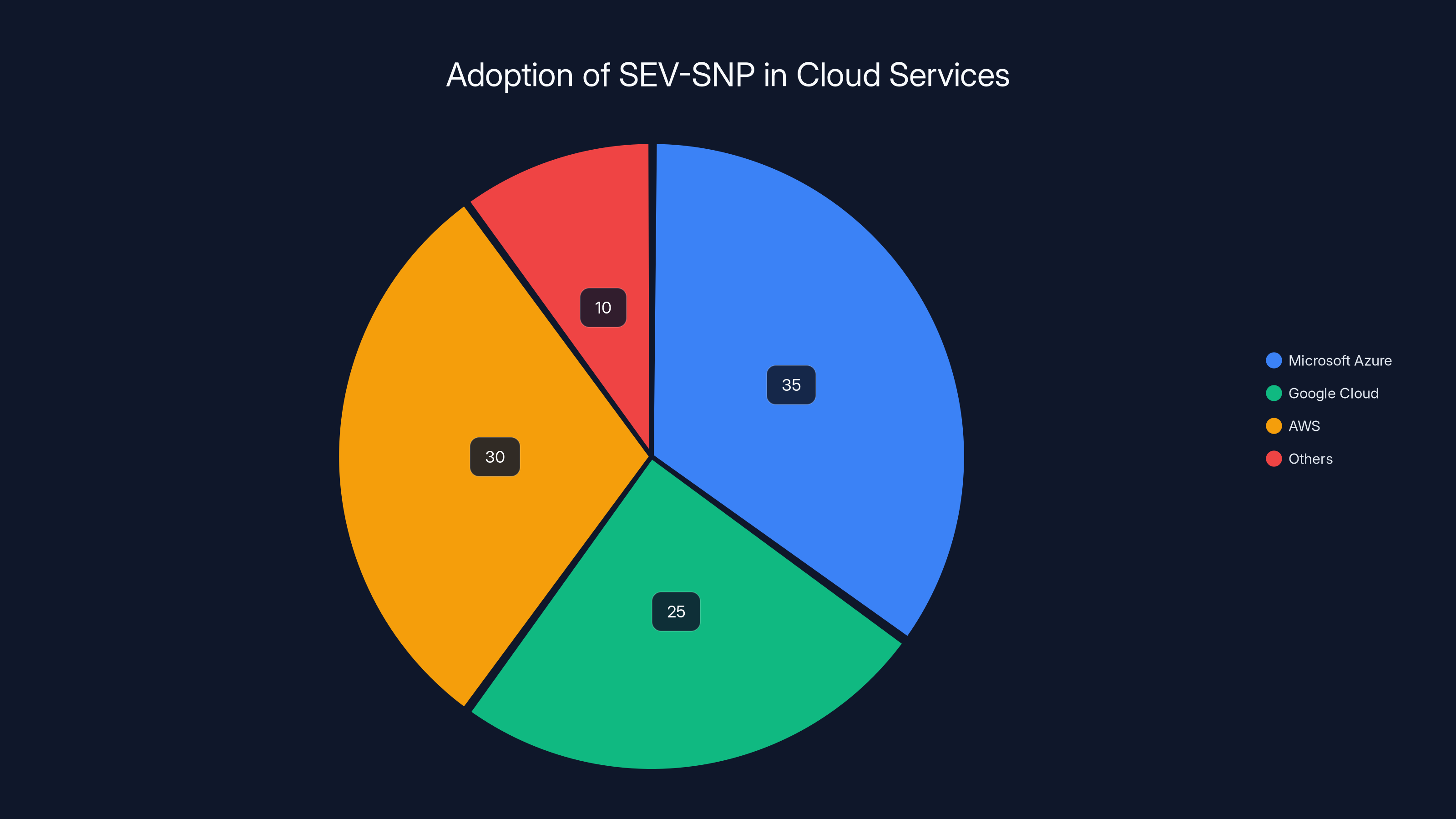
Estimated data shows Microsoft Azure, Google Cloud, and AWS as leading adopters of SEV-SNP technology, with Azure slightly ahead.
The CVSS Score Debate: Why 3.2 Feels Low
AMD assigned CVE-2025-29943 a CVSS score of 3.2/10, which officially classifies it as "low severity." This has sparked debate in the security community, and it's worth understanding why.
CVSS scoring weighs multiple factors:
- Attack Vector: Network vs. Adjacent vs. Local vs. Physical. Stack Warp is "Local" (requires code execution on the affected system), which lowers the score.
- Attack Complexity: How difficult is the attack to execute? Stack Warp is "High" (requires specific conditions, deep technical knowledge), which lowers the score further.
- Privileges Required: The attacker needs "High" privileges (hypervisor access), which significantly lowers the score.
- Impact on Confidentiality/Integrity: Both are "High" (secrets can be stolen, memory can be modified), which raises the score.
The formula mathematically produces 3.2 when you weight these factors according to CVSS methodology. And technically, the scoring is correct given the privilege requirements.
But here's the nuance: CVSS scores are designed for a general audience. For confidential computing specifically, the "requires privileged access" factor is less important. The entire reason you'd use confidential computing is to protect against threat models that include privileged attackers. So in context, Stack Warp is far more serious than 3.2 suggests.
Think of it like rating the security of a building's vault. If you give a score that says "low risk because you need a lockpick set and a month of training," that's technically accurate but ignores that the vault's entire purpose is to protect against skilled attackers.
For users relying on confidential computing specifically to guard against insider threats, the real severity is much higher. For general users, 3.2 is accurate.

Patch Status: What Has AMD Released?
AMD has published patches, but the story is complicated because the fix spans multiple components.
The microcode (CPU firmware) needs an update. AMD has released updated microcode for affected processors, but deployment depends on system manufacturers and cloud providers. AMD's security bulletin includes the specific microcode versions that address the vulnerability.
But here's the practical problem: microcode updates usually require:
- BIOS/UEFI firmware updates from the motherboard or server manufacturer (ASUS, MSI, Gigabyte, Supermicro, etc.)
- Cloud provider deployment (for cloud customers, your cloud provider must apply the firmware update to their servers)
- System downtime (in many cases, the firmware update requires a reboot)
- Operating system patches for mitigation in case firmware updates are delayed
The timeline looks like this:
- January 2025: Vulnerability disclosed, patches released
- January-March 2025: Cloud providers begin deploying patches (usually in rolling waves to avoid widespread downtime)
- March-June 2025: Motherboard manufacturers release BIOS updates for on-premises systems
- Late 2025: Full deployment expected across most infrastructure
Cloud providers like Microsoft Azure and Google Cloud have published their own timelines. AWS typically doesn't disclose patch schedules publicly but usually deploys patches within weeks. However, customers must also apply OS-level mitigations for older instances.
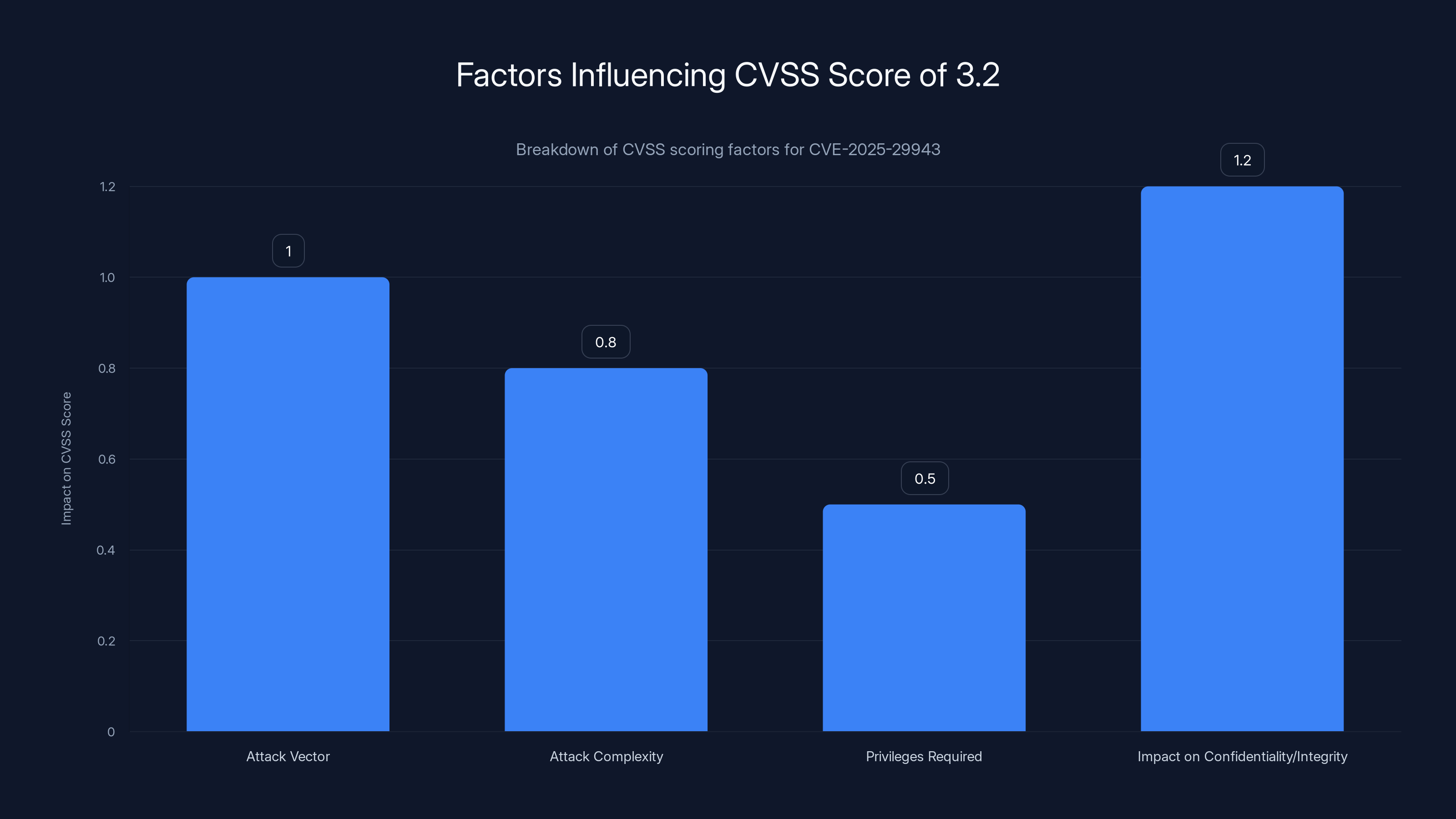
The CVSS score of 3.2 is influenced by factors like local attack vector and high attack complexity, which lower the score, despite high impact on confidentiality and integrity.
Operating System and Kernel Mitigations
While waiting for firmware patches, operating system vendors have released kernel-level mitigations.
The Linux kernel maintainers merged mitigations into recent versions. Ubuntu, Red Hat, and other distributions have released security updates.
What do these mitigations do? They can't prevent the exploit entirely without firmware fixes, but they can:
- Disable SEV-SNP as a fallback (which removes the security protection but also removes the attack surface)
- Implement additional validation on memory operations initiated from user space
- Add runtime monitoring to detect suspicious stack pointer patterns
- Restrict guest VM capabilities to reduce the information an attacker can extract
The trade-off is clear: you get security back, but you lose the performance and isolation benefits of confidential computing. For many workloads, this trade-off isn't acceptable.
For Windows environments, Microsoft Security Response Center (MSRC) has published updates for Hyper-V and Windows guests. The situation is slightly different on Windows because the hypervisor and guest isolation work differently, but the fundamental issue still applies.
What About Consumer AMD Ryzen Processors?
This is an important question for desktop and laptop users. The vulnerability has been disclosed only for server-grade EPYC processors so far.
Consumer Ryzen chips do support a similar feature called SEV (Secure Encrypted Virtualization) in some models, but with different implementation details. AMD hasn't confirmed whether Stack Warp affects consumer processors. The official security bulletin only mentions EPYC.
However, the security research community generally assumes that if a vulnerability exists in EPYC's implementation, similar issues likely exist in Ryzen's implementation too. AMD typically shares CPU architecture across consumer and server lines.
For desktop users running virtual machines with encrypted memory, it's worth monitoring AMD's security announcements for updates on consumer processors. If you're in this category, apply BIOS updates as soon as they're available from your motherboard manufacturer.

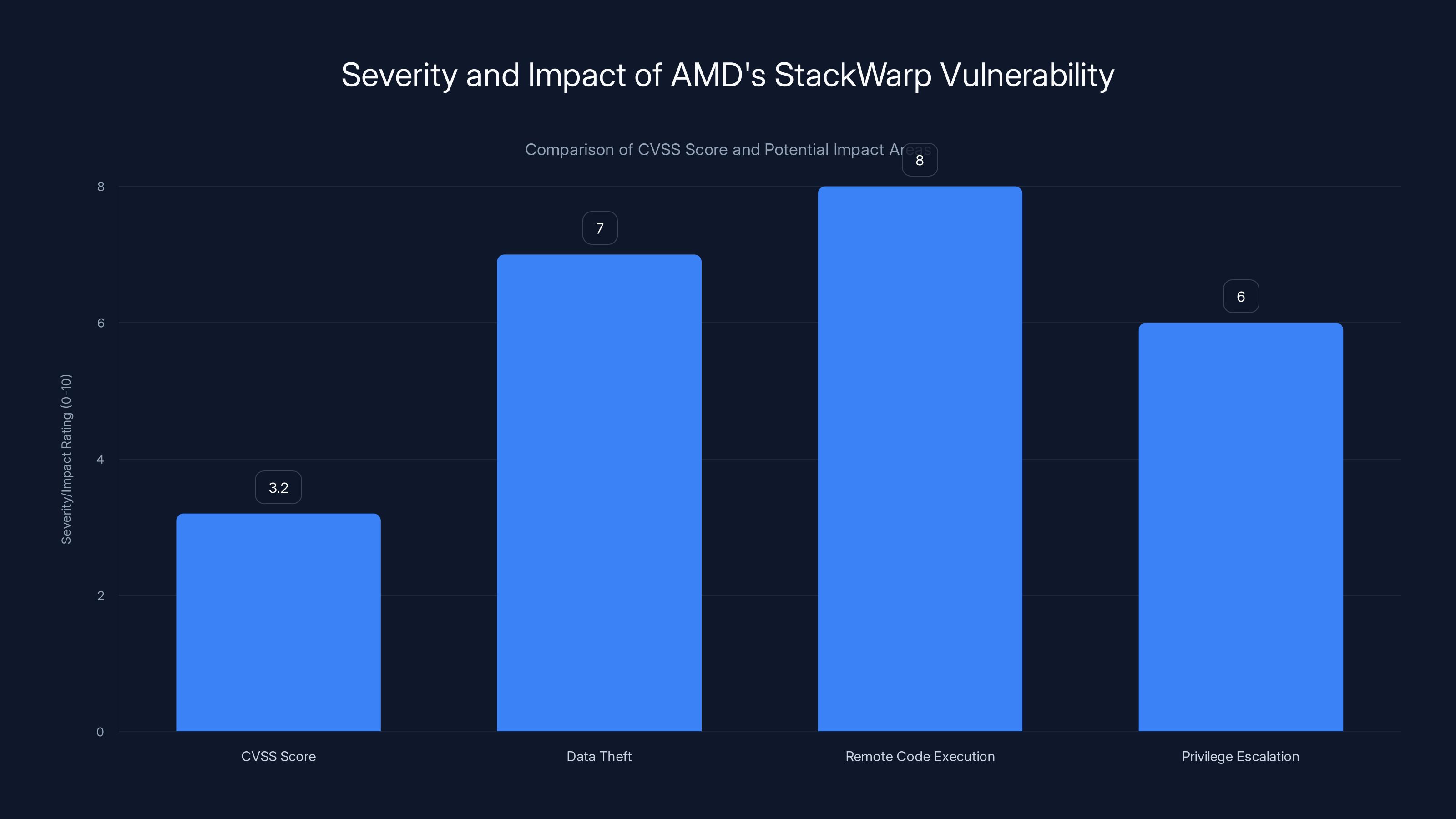
While the CVSS score for StackWarp is low at 3.2, its potential impact on data theft, remote code execution, and privilege escalation is significant, highlighting the need for vigilance in secure environments. Estimated data for impact ratings.
Detailed Exploitation Scenario: How an Attack Actually Works
Let's walk through a realistic exploitation scenario to understand the real-world mechanics.
Imagine a cloud provider using AMD EPYC processors running customer VMs. Customer A has deployed a confidential VM that runs a cryptocurrency wallet's private key signing service. Customer A trusted the cloud provider would never access their keys because of SEV-SNP encryption.
Now imagine a malicious employee at the cloud provider with hypervisor access. They know Stack Warp exists. Here's what they'd do:
Phase 1: Reconnaissance (Hours 1-4)
The attacker uses hypervisor access to map the guest VM's memory layout. They learn where the stack is located, where the key material is stored, and the general flow of the signing function. They don't need to decrypt anything yet; they just need the layout.
Phase 2: Exploit Construction (Hours 4-24)
The attacker creates a specially crafted set of instructions that would trigger the stack pointer validation bug. This is the hard part, requiring deep knowledge of AMD microarchitecture. They test it in a lab environment on identical hardware.
Phase 3: Trigger Condition (Hours 24-48)
The attacker injects a modified version of the guest OS kernel (via a hypervisor privilege) or triggers the guest to load the exploit through a side-channel communication method. Alternatively, they might wait for the guest to naturally execute a sequence of instructions that creates the vulnerability condition.
Phase 4: Data Exfiltration (Minutes 1-30)
Once the exploit executes, it can read arbitrary memory from the guest VM, including the private keys. The attacker copies the data out and exfiltrates it.
Phase 5: Cover-up (Hours 48-72)
The attacker removes evidence of the attack from logs and resets the hypervisor state.
The entire process requires significant technical skill and deep knowledge of the target architecture. But for a skilled insider at a cloud provider, it's feasible. And that's exactly the threat model that confidential computing is supposed to protect against.

Industry Response and Cloud Provider Actions
Major cloud providers have responded quickly, though with slightly different timelines.
Microsoft Azure has committed to patching all confidential computing instances by mid-2025. They've published a detailed timeline and mitigation strategy. In the interim, they're offering customers the option to disable SEV-SNP (which removes the vulnerability but also removes the protection).
Google Cloud has published detailed security advisories and is pushing microcode updates to all AMD-based instances. They've created a public tracking system for patch deployment status.
AWS typically doesn't disclose patch schedules publicly, but they've confirmed they're working with AMD and processor manufacturers on deployment. Customers can check their instance metadata to see patch status.
Beyond cloud providers, this has implications for:
- Cryptocurrency exchanges: May need to migrate private key storage to patched hardware or implement additional cryptographic safeguards
- Financial institutions: Must audit their use of confidential computing and assess risk from insider threats
- Healthcare providers: Processing sensitive patient data in confidential VMs should verify patch status
- Data centers: On-premises deployments need to coordinate with motherboard manufacturers on BIOS update availability

Should You Disable Confidential Computing While Waiting for Patches?
This is a practical decision many organizations are facing right now.
The answer depends on your threat model:
Disable SEV-SNP if:
- Your primary security concern is external network attacks (not insider threats)
- You're willing to sacrifice the isolation that confidential computing provides
- Your workload's performance benefit from SEV-SNP is negligible
- You can't wait for patches and need immediate remediation
Keep SEV-SNP enabled if:
- You're specifically using confidential computing to protect against insider threats
- The risk of inside attack is higher than the risk of Stack Warp exploitation (because Stack Warp requires hypervisor access)
- You can deploy patches within the cloud provider's timeline
- You can implement additional monitoring to detect suspicious activity
For most organizations, the recommendation is: patch as quickly as possible, but don't disable confidential computing entirely. The threat of Stack Warp exploitation is real but requires specific conditions (hypervisor access + deep technical knowledge + detection avoidance). For general threats, confidential computing is still valuable.
Monitoring and Detection Strategies
While patches are being deployed, you should implement detection strategies.
Stack Warp exploitation leaves traces, though they're subtle:
- Unexpected memory access patterns: The exploit requires accessing memory outside normal program flow. Kernel-level monitoring can detect this.
- Stack pointer anomalies: If you log CPU register state, unusual stack pointer values during function calls can indicate an attack.
- Process behavior deviations: If a cryptographic process suddenly starts executing code outside its normal code section, that's suspicious.
- Hypervisor audit logs: Examine hypervisor logs for unusual memory mapping changes, privilege escalation attempts, or unexpected hardware configuration modifications.
For cloud customers, this is limited because you don't have direct access to hypervisor logs. But you can:
- Monitor your own guest OS logs for suspicious kernel-level activity
- Implement cryptographic key versioning so you can detect if a key has been compromised and used
- Use cloud provider security services that log and alert on suspicious instance behavior
- Run integrity checks on running processes to detect code injection
For on-premises environments, you have more visibility:
- Implement comprehensive hypervisor auditing
- Monitor for unusual memory mapping patterns
- Restrict hypervisor access to minimal staff
- Implement multi-factor authentication for hypervisor access
- Log and monitor all firmware updates
The Broader Context: Are Hardware Vulnerabilities Becoming More Common?
Stack Warp is just the latest in a series of hardware-level security vulnerabilities that have emerged over the past five years.
We've seen:
- Spectre and Meltdown (2017-2018): Fundamental flaws in CPU speculative execution
- L1TF / Foreshadow (2018): Layer 1 cache timing attacks
- Micro Architectural Data Sampling (2018-2019): Information leakage through CPU buffers
- Inception (2023): Stack manipulation in AMD EPYC processors
- Stack Warp (2025): Another stack-based attack on AMD
The pattern is clear: as CPU designs get more complex and optimizations get more aggressive, new attack surfaces emerge. Confidential computing was supposed to be a solution to some of these problems, but it introduced its own surface area.
The security research community is now asking fundamental questions:
- Is hardware-level encryption sufficient? If the CPU logic itself has flaws, encryption doesn't help.
- Can we formally verify CPU security properties? It's theoretically possible but computationally intensive.
- Should we accept that hardware vulnerabilities are inevitable? Maybe. This would shift focus to detection and containment.
For organizations investing in hardware-based security, the lesson is: don't assume it's the complete solution. Layer it with other defenses.
Long-Term Implications for Confidential Computing
Stack Warp doesn't kill confidential computing, but it does change the conversation.
Confidential computing was supposed to be the answer to "how do you run sensitive workloads in the cloud while protecting against the cloud provider?" Stack Warp shows the answer is more nuanced.
Going forward, we can expect:
-
More conservative adoption: Organizations will be cautious about moving highly sensitive workloads to confidential VMs until multiple generations of patches have stabilized.
-
Deeper scrutiny of hardware claims: Marketing claims about "unbreakable" security will be viewed more skeptically. The benchmarks for security hardware will be much stricter.
-
Hybrid approaches: Rather than relying entirely on confidential computing, organizations will layer it with cryptographic protocols, key splitting, and detection mechanisms.
-
Increased investment in formal verification: Chip designers may invest more heavily in formally verifying security-critical logic, even though it slows down development.
-
Supply chain security focus: If a vulnerability can be exploited by insiders, then who has access to your infrastructure becomes even more critical. We'll see more stringent supply chain security audits.
-
Liability and insurance implications: Confidential computing providers may face liability claims if Stack Warp exploitation occurs. This could change insurance requirements and service-level agreements.
The security industry is learning that hardware security isn't a silver bullet. It's a component of a comprehensive security strategy, not a replacement for other controls.
Vendor-Specific Recommendations
Let's address what each major platform should do right now.
For Azure Customers:
Check your instance type to confirm if it supports confidential computing. If it does, request patch status from Microsoft Support. Set calendar reminders for the published patch date. In the interim, consider running non-critical workloads on non-confidential instances and re-enable when patches are confirmed deployed.
For Google Cloud Customers:
Google has published detailed patch timelines. Access your instance metadata to check firmware versions against the patched versions listed in Google Cloud's security bulletins. If you need immediate mitigation, you can request instance termination and recreate on patched hardware, though this may impact your workload.
For AWS Customers:
AWS typically patches underlying infrastructure without customer action required. However, for dedicated hosts or instances where you manage firmware, request patch information from AWS Support. Verify your instance type actually uses AMD processors (AWS uses a mix of AMD and Intel).
For On-Premises Deployments:
Contact your motherboard manufacturer (Super Micro, ASUS, etc.) for BIOS update availability. Test updates in a lab environment before deploying to production. Coordinate with your system administrators on a maintenance window for the BIOS update, as this typically requires reboots. Verify microcode versions post-update match AMD's published patched versions.
For Hypervisor Administrators (KVM, Hyper-V, ESXi):
Ensure your hypervisor software is updated to the latest version, as some patches are released at the hypervisor level. Review security advisories specific to your hypervisor platform. If you're running older hypervisor versions, prioritize updates.

FAQ
What exactly is Stack Warp and why is it dangerous?
Stack Warp is a hardware-level vulnerability in AMD Zen processors that allows an attacker with hypervisor-level access to break the memory encryption provided by SEV-SNP (Secure Encrypted Virtualization with Secure Nested Paging). It works by manipulating how the CPU tracks the call stack, tricking the processor into revealing data that should remain encrypted. The danger is that it enables attackers to steal private keys, execute code within supposedly isolated VMs, and compromise cryptographic operations, all while the memory is supposedly encrypted.
Who is most at risk from Stack Warp?
Cloud customers running confidential VMs on AMD EPYC processors with SEV-SNP enabled are at highest risk, particularly those running cryptographic operations, financial calculations, or sensitive data processing. Organizations within your cloud provider (insider threats) and highly sophisticated external attackers who've compromised hypervisor access are the threat actors. On-premises data centers running AMD EPYC with virtualization are also at risk if they trust system administrators implicitly. Average desktop users running consumer Ryzen processors are likely not at risk based on current disclosures, though this could change.
Does Stack Warp affect all AMD CPUs?
No. Stack Warp specifically affects AMD Zen 1 through Zen 5 processors, which are primarily server-grade EPYC chips used in data centers and cloud providers. Consumer Ryzen processors haven't been officially confirmed as vulnerable, though security researchers suspect they may be. AMD's security bulletin (CVE-2025-29943) explicitly lists affected processor families. You can verify your processor generation through your motherboard documentation or system information.
What has AMD done to fix Stack Warp?
AMD has released microcode patches that address the vulnerability. These patches need to be deployed through BIOS/UEFI firmware updates, which are the responsibility of motherboard manufacturers for on-premises systems and cloud providers for cloud infrastructure. Additionally, operating system vendors like Linux kernel maintainers and Microsoft have released kernel-level mitigations. However, the complete fix requires both firmware updates (which address the root cause) and OS updates (which provide defense-in-depth). Full deployment across all infrastructure is expected to take several months.
What's the difference between a CVSS score of 3.2 and what the real severity is?
CVSS scoring heavily weights the "requires privileged access" factor, which mathematically produces a 3.2/10 low-severity rating. However, for confidential computing specifically, the entire purpose is to protect against privileged attackers and insider threats, so the severity in context is much higher. It's like rating a bank vault's security as "low risk" because you need a lockpick set and technical knowledge. Technically correct by the formula, but misses the real intent. For confidential computing users, treat Stack Warp as a high-severity vulnerability despite the CVSS score.
Should I disable SEV-SNP while waiting for patches?
For most organizations, no. Disabling SEV-SNP removes both the vulnerability and the protection, leaving you with standard VM isolation. The risk calculation depends on your threat model: if your primary concern is insider threats or you're specifically using confidential computing for that purpose, keeping it enabled while monitoring for the vulnerability is usually better than disabling it. However, if you need immediate remediation and patches won't arrive for months, disabling it may be necessary. Contact your cloud provider or security team for guidance specific to your situation.
How do I know if my cloud provider has patched against Stack Warp?
Ask your cloud provider directly. Most major providers (Azure, Google Cloud, AWS) have published patch timelines and tracking information. Azure publishes estimated patch dates; Google Cloud shows patch status per region; AWS typically patches transparently without requiring customer action. Request a formal confirmation of patch status in writing and set calendar reminders to verify compliance. For on-premises systems, contact your motherboard manufacturer or check their support portal for BIOS update availability.
Can I detect if someone has exploited Stack Warp?
Partially. Detection requires kernel-level monitoring of memory access patterns and CPU register states, which is easier in on-premises environments than cloud environments. You can monitor for unusual code execution outside normal program flow, unexpected stack pointer values, and suspicious hypervisor-level activity. However, a sophisticated attacker could cover their tracks. The best defense is layered: prevent the vulnerability through patching, monitor for suspicious behavior, implement cryptographic key rotation so you can detect compromise, and restrict hypervisor access to minimal staff with strong authentication.
What's the timeline for full Stack Warp patch deployment?
Expect patches to roll out in waves through mid-to-late 2025. Major cloud providers began patches in January-February 2025. On-premises BIOS updates should be available by Q2 2025 as motherboard manufacturers release updates. Complete deployment across all affected infrastructure could take 6-12 months, with early adopters patched by Q2 2025 and laggards still deploying through Q4 2025. Legacy systems that don't receive BIOS updates will remain vulnerable indefinitely, making a strategic decision about hardware refresh cycles important for organizations running sensitive workloads.
Are there cryptographic countermeasures if I can't patch quickly?
Yes, but they're computationally expensive. Key splitting (storing cryptographic keys in multiple encrypted pieces across different systems), frequent key rotation (making stolen keys time-limited), and multi-party computation (spreading computation across multiple isolated systems) can reduce the impact of private key theft. However, these are complex to implement and don't eliminate the vulnerability. They're interim measures while waiting for patches. Additionally, organizations can implement zero-trust hypervisor access controls, multi-factor authentication for administrative access, and comprehensive logging of all administrative actions.
Key Takeaways and What You Should Do Now
Stack Warp is a significant vulnerability, but it's not an instant apocalypse. It requires specific conditions: the attacker needs hypervisor or administrative access, deep technical knowledge, and the patience to work through complex exploitation steps. For most users, the risk is lower than the headlines suggest.
But here's what you should do immediately:
For Cloud Customers:
- Identify which of your workloads are running in confidential VMs
- Contact your cloud provider and request their Stack Warp patch timeline
- Assess your threat model: does it include insider threats from cloud providers?
- Set up monitoring for unusual instance behavior
- Plan a timeline for verifying patches have been applied
For On-Premises Administrators:
- Audit which servers are running AMD Zen processors with virtualization
- Contact your motherboard manufacturer for BIOS update availability
- Test updates in a non-production environment first
- Plan a maintenance window for BIOS updates
- Implement kernel-level monitoring if you have sensitive VMs
For Everyone:
- Don't assume "low severity" means "not important" for your specific situation
- Understand that confidential computing is one layer of security, not a complete solution
- Use this as motivation to review your overall security posture
- Stay informed as patches roll out throughout 2025
Stack Warp is a reminder that security is continuously evolving. Hardware vulnerabilities happen. The key is responding quickly, understanding your actual risk, and implementing layered defenses rather than betting everything on a single technology.
Keep monitoring CISA's vulnerability database and your cloud provider's security bulletins for updates. And if you're running sensitive workloads that absolutely cannot be compromised, now is the time to audit your infrastructure and patch timeline.
The good news is that organizations are responding quickly. Patches are being deployed. The security community is engaged. By mid-2025, the vast majority of affected infrastructure should be patched. Until then, stay vigilant.
Use Case: Document and automate your security patch tracking across all infrastructure with AI-powered compliance reports.
Try Runable For Free
Related Articles
- Netflix's 45-Day Theatrical Window: What It Means for Cinema [2025]
- OpenAI ChatGPT Go: Everything About the $8 Subscription [2025]
- ChatGPT Ads Are Coming: Everything You Need to Know [2025]
- ChatGPT Memory Upgrade: Year-Long Conversation History [2025]
- LEGO Zelda Ocarina of Time Final Battle Set Guide [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
![AMD CPU StackWarp Vulnerability: What You Need to Know [2025]](https://tryrunable.com/blog/amd-cpu-stackwarp-vulnerability-what-you-need-to-know-2025/image-1-1768590496624.jpg)



