Are VPNs Really Safe? Security Factors to Consider [2025]
Introduction: Beyond the Hype
You've probably noticed VPN ads everywhere. They promise anonymity, security, and freedom from snooping. But there's an uncomfortable truth hiding beneath the marketing: not all VPNs are created equal, and some are actively dangerous.
I remember talking to a security researcher last year who told me something that stuck with me: "More people have been harmed by bad VPNs than helped by good ones." That's not because VPNs are fundamentally flawed. It's because the market is flooded with garbage.
The problem is threefold. First, most people don't understand what a VPN actually does and what it doesn't do. Second, app stores are packed with imposters masquerading as legitimate services. Third, even legitimate-looking VPNs sometimes cut corners in ways that completely undermine their security claims.
So when someone asks me "Are VPNs really safe?," I need to clarify what they're actually asking. Are the protocols safe? Yes, when implemented correctly. Is using a VPN enough to protect you? No. Is picking the wrong VPN dangerous? Absolutely.
This guide digs into the technical realities. You'll learn how VPNs work, what makes them safe or dangerous, how to test one before paying, and what VPNs actually do and don't protect you from. Most importantly, you'll understand how to separate the genuinely secure options from the ones that are using security theater to exploit your fears.
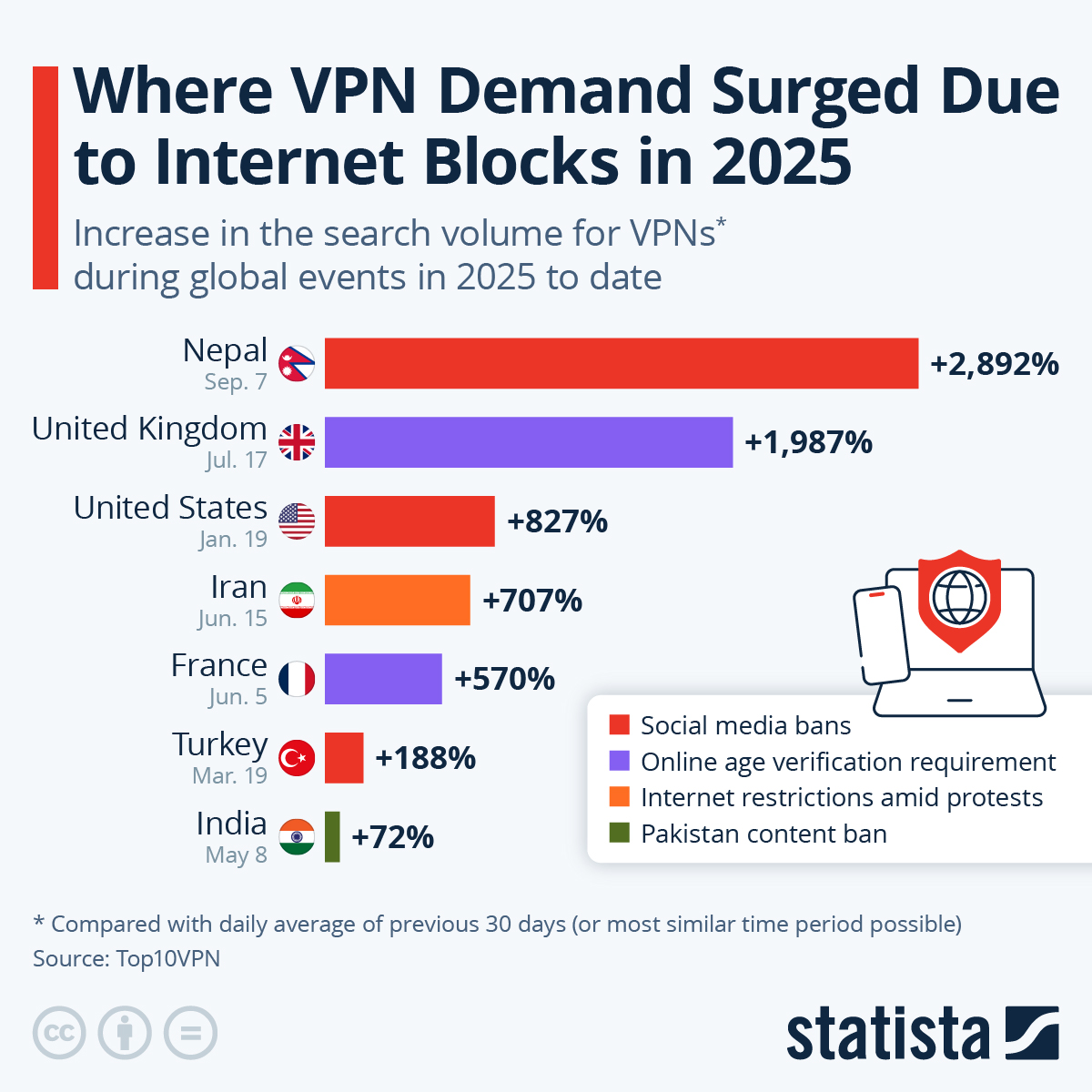
The chart highlights common red flags in VPN services, with 'Too Good to Be True Pricing' being the most prevalent at an estimated 70%. Estimated data based on industry insights.
TL; DR
- Not all VPNs are safe: Malicious VPNs harvest your IP address, track activity, inject malware, and sell data to advertisers. According to All About Cookies, these practices are prevalent in free VPN services.
- Negligent VPNs are equally dangerous: Outdated protocols, public DNS servers, IPv6 leaks, and missing kill switches expose you worse than not using a VPN. CyberGhost VPN highlights the importance of using updated protocols like OpenVPN, IKEv2, and WireGuard.
- Three protocols matter most: OpenVPN, IKEv2, and WireGuard are expert-verified; anything else needs AES-256 or ChaCha20 encryption.
- Test before you commit: Use leak testing sites, check kill switch functionality, verify no-logs policies during free trials. Engadget provides a guide on checking VPN functionality.
- VPNs aren't a complete solution: They hide your IP from websites, but don't protect against malware, phishing, weak passwords, or unencrypted services. PCMag suggests using additional malware protection tools.
What VPNs Actually Do (And What They Don't)
Let's start with the fundamental misunderstanding. Most people think a VPN is a magic shield that makes them invisible and unhackable. That's not what it does.
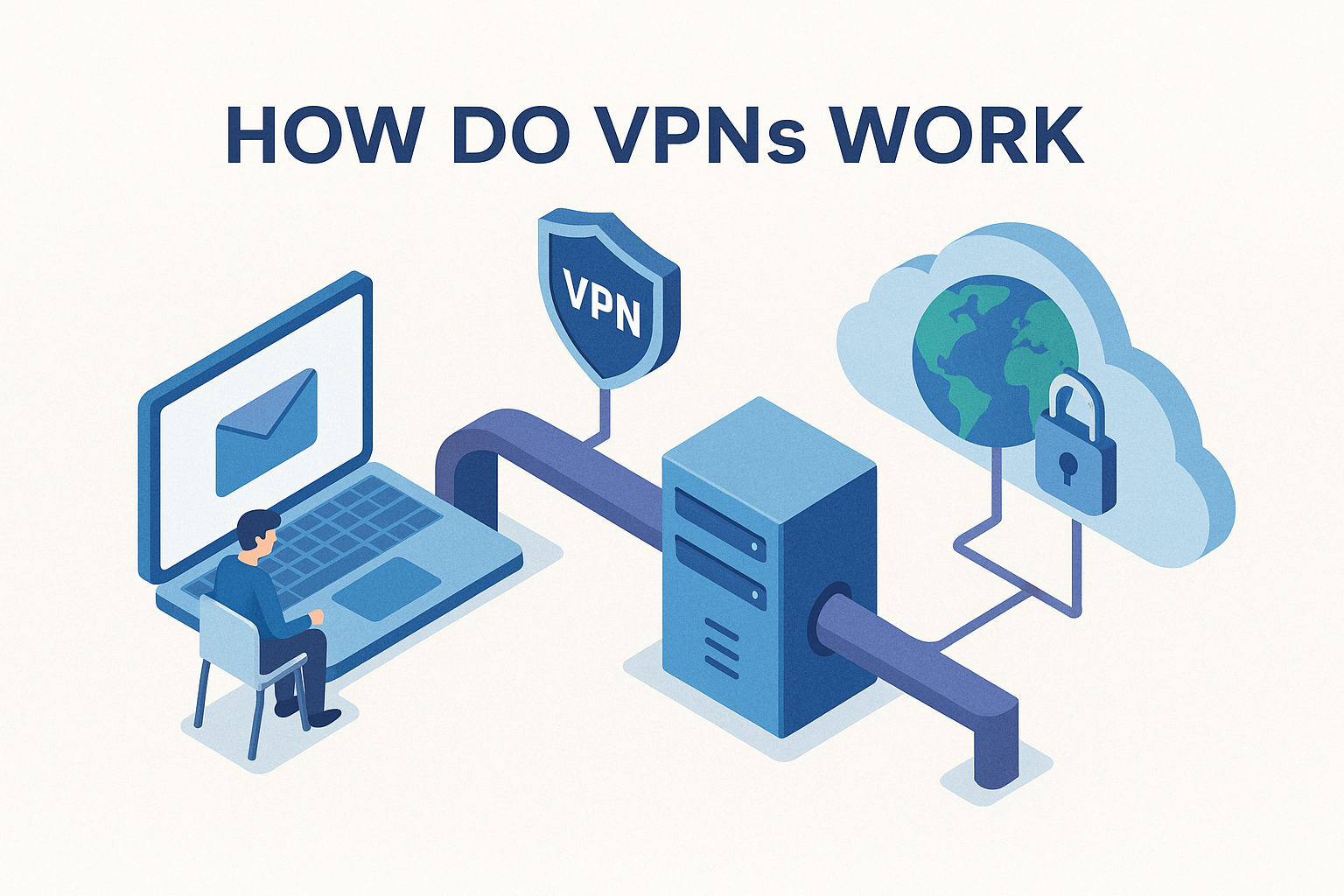
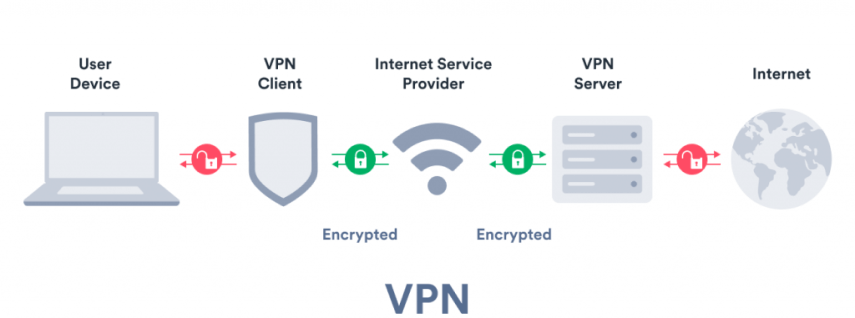
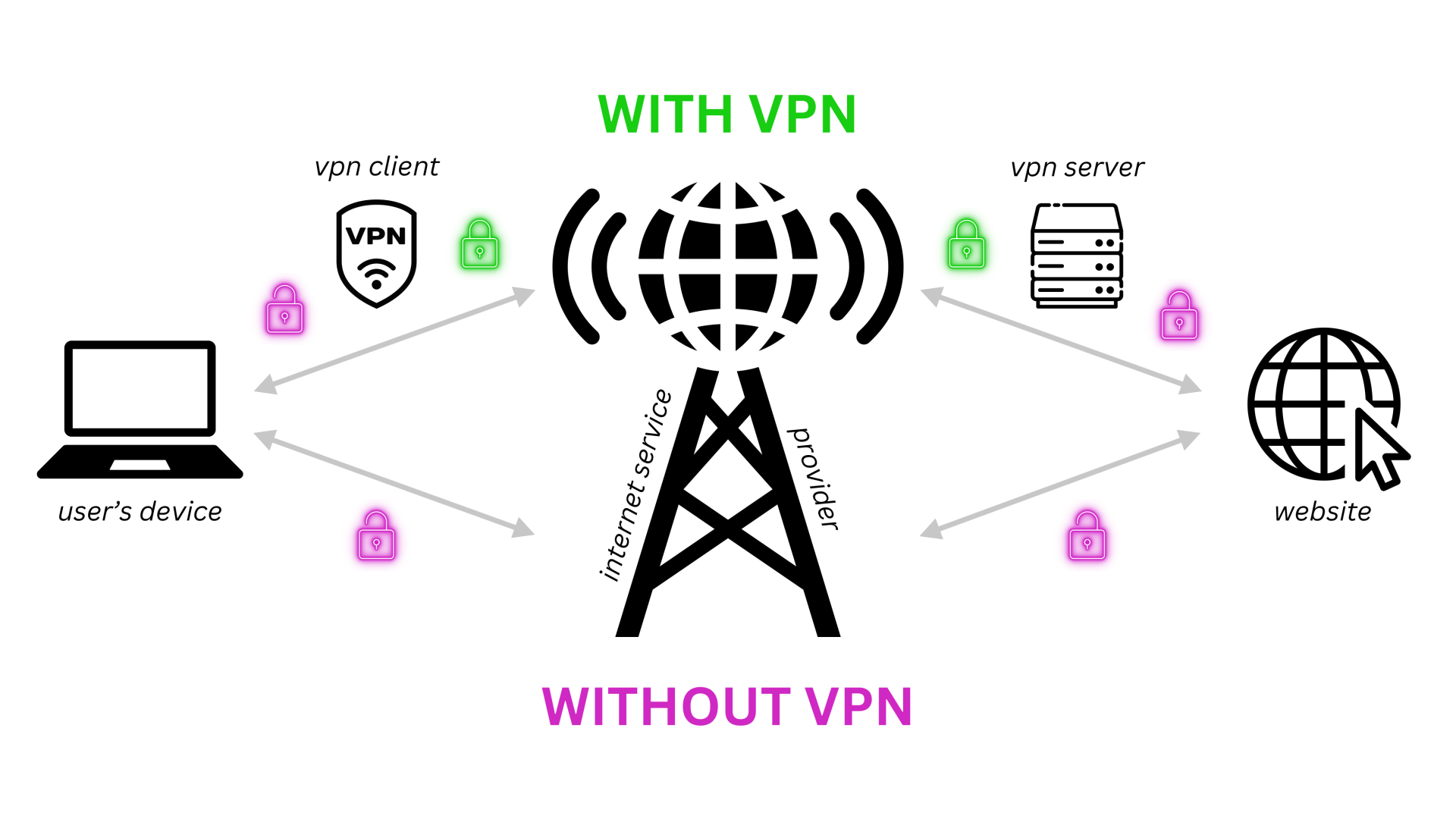
A VPN creates an encrypted tunnel between your device and a server operated by the VPN provider. All your internet traffic gets routed through this tunnel. To external websites and services, it looks like you're connecting from the VPN server's location, not your actual location. Your Internet Service Provider (ISP) can see that you're using a VPN, but they can't see what websites you're visiting or what data you're sending.
That's genuinely useful. Your ISP can't throttle your traffic based on what you're doing. Websites can't easily pinpoint your physical location. Local Wi-Fi networks can't snoop on your unencrypted data. These are real, valuable protections.
But here's where people get confused. A VPN does not:
- Make you anonymous if you log into your personal accounts. Once you log into Gmail with a VPN, Google knows exactly who you are.
- Protect you from malware, ransomware, or viruses. If you download an infected file, it's infected whether you're using a VPN or not.
- Protect you from phishing attacks. If you click a malicious link and enter your password, the VPN doesn't prevent that.
- Hide your activity from the VPN provider themselves. If the VPN company decides to log your traffic, they can see everything.
- Make weak passwords secure. If you're using "password123" as your password, a VPN doesn't change that.
- Encrypt traffic to unencrypted websites. If a site uses HTTP instead of HTTPS, a VPN doesn't add encryption for that connection.
Understanding these limits is crucial. Because if you're relying on a VPN to protect you from threats it can't address, you're actually less secure than if you understood your actual vulnerabilities.

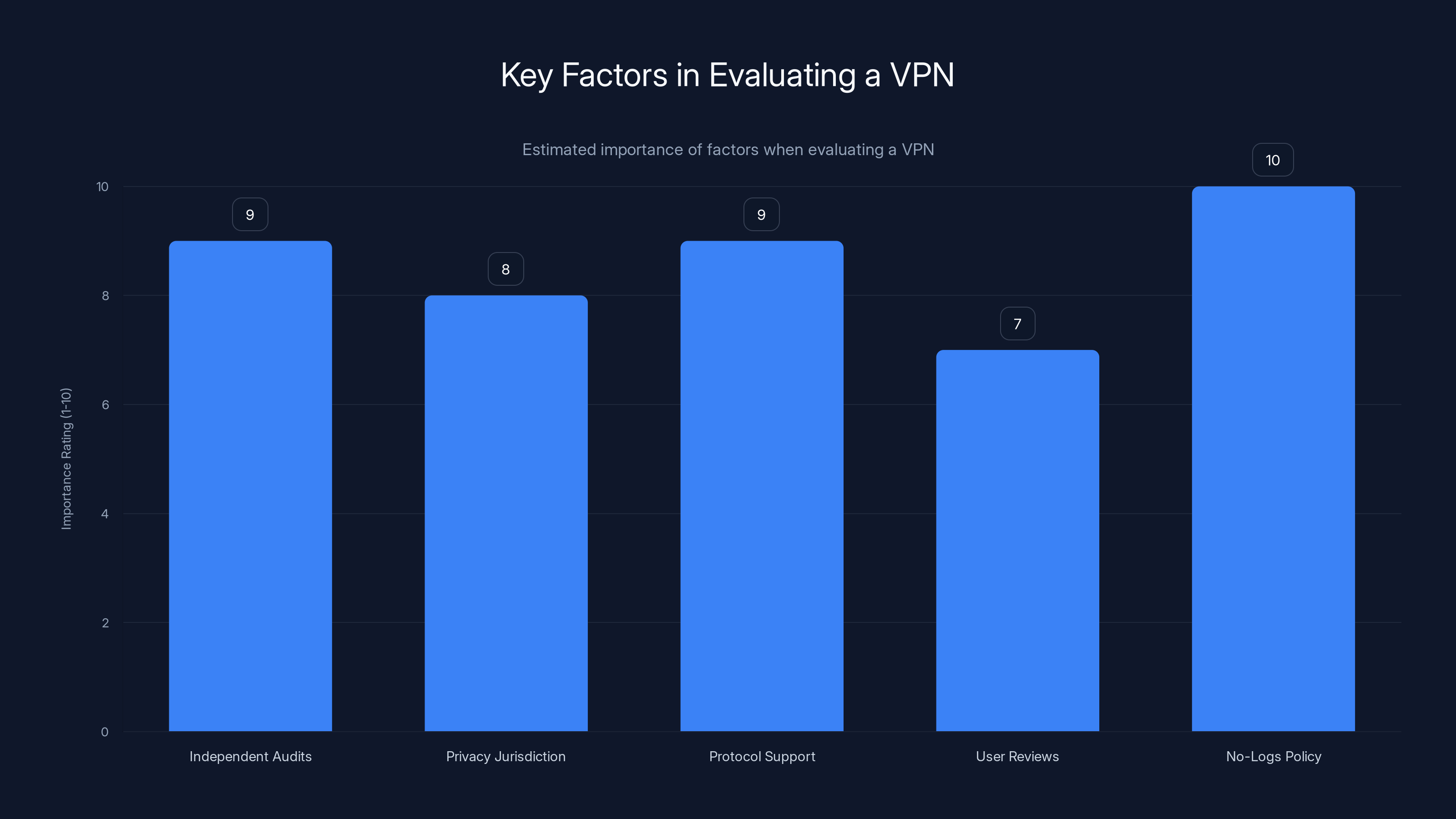
Independent audits and a strong no-logs policy are crucial when evaluating a VPN, with both scoring high on importance. Estimated data based on common evaluation criteria.
The Two Ways VPNs Become Dangerous
VPN danger comes in two forms: negligence and malice. Understanding the difference helps you spot red flags.
Negligence: When VPNs Fail at Their Basic Job
A negligent VPN is one that's poorly designed or poorly maintained. The people running it aren't trying to harm you, but they're cutting corners in ways that completely undermine the security they're supposed to provide.
The most common form is using outdated protocols. PPTP (Point-to-Point Tunneling Protocol) is a great example. It was released in 1995 and has been cryptographically broken since 2012. Yet some budget VPNs still use it because the code is old and available. If you connect through PPTP, you might as well not use a VPN at all. Someone with basic networking knowledge can intercept and read your traffic.
Some VPNs roll their own protocols. This seems like innovation until you realize that cryptography is hard. Really hard. Companies like OpenAI, Cloudflare, and major tech corporations have entire teams of cryptography experts. When a small VPN company decides to invent its own encryption protocol, the odds of it being more secure than established protocols are essentially zero. It's like a car manufacturer deciding to invent their own brakes because they think they can do better.
DNS leaks are another common negligence problem. Here's how it works: You're connected to a VPN, so your IP is hidden. But your device still needs to resolve website names into IP addresses. That's what DNS does. If a VPN sends these DNS requests to public servers (like Google's 8.8.8.8), those servers log that your device is looking up, say, pornsite.com. Your ISP and network administrator can see those DNS queries. The whole point of hiding your IP is defeated.
IPv6 leaks happen similarly. Most people think in terms of IPv4 addresses (four groups of numbers, like 192.168.1.1). But the internet is transitioning to IPv6, which uses a different format. If a VPN only tunnels IPv4 but not IPv6, your real IPv6 address leaks out. Someone checking your connection sees your actual location.
A kill switch is a feature that disconnects you from the internet if the VPN connection drops. Without it, you might suddenly be connected unencrypted while thinking you're still protected. A negligent VPN either doesn't include a kill switch or includes one that doesn't work reliably.
Server security matters too. Some VPNs use third-party data centers and don't properly secure them. When those servers get hacked, all the VPN traffic gets exposed. You're trusting your data with a company that didn't even invest in protecting their infrastructure.
Malice: When VPNs Are Designed to Exploit You
Malicious VPNs are worse because they actively work against your interests. The business model is "we'll use your data to make money."
The most common approach is in-app advertising with tracking. The VPN offers a free tier supported by ads. Except the ads contain tracking pixels that monitor your behavior. The VPN isn't just collecting data, it's instrumenting you for profiling. Then they sell that profile to advertisers.
Some VPNs have a more profitable scheme: harvesting your residential IP address. Here's why this matters. Your home IP address is valuable. Advertisers want it so they can track you across the web. Criminals want it so they can impersonate you. Spammers want it to send traffic from a "legitimate" residential network instead of obvious spam servers. A malicious VPN collects your real IP and sells it as a proxy to these parties. You paid them to hide your IP, and they're selling it to the highest bidder.
Activity tracking and selling is another revenue stream. The VPN logs everything you do and sells that data to advertisers, data brokers, or even governments. This completely defeats the purpose of using a VPN. You might as well use no VPN at all, because now you have a company specifically profiting from knowing your every move.
Some malicious VPNs install malware. They use the VPN installation as an entry point to add adware, spyware, or trojans. Your data is unencrypted to the VPN server, sure, but now your entire device is compromised.
The insidious part? These malicious VPNs often look legitimate. They have professional websites, thousands of reviews on app stores, and marketing that says all the right things. They're exploiting the fact that most people don't understand VPN security deeply enough to spot the difference.
VPN Protocols Explained: The Technical Foundation
VPN protocols are the underlying technology that does the actual encryption and tunneling. If you understand protocols, you understand what makes a VPN safe or dangerous.
OpenVPN: The Industry Standard
OpenVPN has been around since 2001 and remains one of the most trusted protocols in the world. It's open source, meaning security researchers worldwide can examine the code and find vulnerabilities. This transparency is a feature, not a bug.
The protocol uses OpenSSL for encryption, which means it benefits from decades of scrutiny and improvement. OpenVPN is used by corporate IT departments, security researchers, and privacy advocates. If a vulnerability were found, the open-source community would know immediately and push fixes.
OpenVPN is slower than some newer protocols because it's more conservative. It uses 2048-bit keys by default, though it supports up to 4096-bit for paranoid users. The protocol requires more computational overhead, which means a slightly bigger impact on your internet speed.
But here's the important part: OpenVPN with AES-256 encryption is considered cryptographically sound. There's no known way to break it. You could run OpenVPN today and know that in 20 years, the traffic would still be secure.
WireGuard: Speed and Simplicity
WireGuard is newer (released in 2015) but has gained massive adoption. It's designed with modern cryptography from the ground up. The entire codebase is only about 4,000 lines (compared to OpenVPN's hundreds of thousands), which makes it easier to audit for vulnerabilities.
WireGuard is significantly faster than OpenVPN. It uses Curve25519 for key exchange and ChaCha20 for encryption. These are modern cryptographic primitives that are considered extremely secure. The trade-off is that WireGuard has had less time in the wild, so statistically, there's a higher chance of discovering vulnerabilities in the future (though none have been found as of now).
WireGuard doesn't support all the configuration options that OpenVPN does. If you need to route specific traffic differently, or customize every aspect of the connection, OpenVPN is more flexible.
IKEv2: The Solid Middle Ground
IKEv2 (Internet Key Exchange version 2) is the protocol used by corporate VPNs and Windows servers. It's been thoroughly vetted by the cryptography community and is standardized by the IETF (Internet Engineering Task Force).
IKEv2 is fast, secure, and well-tested. It handles reconnection particularly well. If you drop your connection (switching from Wi-Fi to cellular, for example), IKEv2 re-establishes the tunnel seamlessly. OpenVPN and WireGuard require reconnecting, which might briefly expose unencrypted traffic.
The downside? IKEv2 is more complex to set up and audit. It's not open source in the way OpenVPN is, though the specification is publicly available and used in multiple implementations.
Protocols to Avoid
PPTP is ancient and broken. L2TP/IPsec works but has historically been suspected of having backdoors. SSTP is proprietary to Microsoft and not widely trusted in the privacy community. If a VPN uses anything other than OpenVPN, IKEv2, or WireGuard, check whether it's using military-grade AES-256 or ChaCha20 encryption. If it's using anything weaker, the protocol is insecure.
A good protocol with weak encryption is still weak. A strong protocol with poor implementation is still weak. All three factors matter.
How to Evaluate a VPN Before You Buy
The research phase is critical. This is where you avoid 90% of VPN disasters.
Phase 1: Background Research
Start by reading reviews from multiple sources. Engadget, TechCrunch, Wirecutter, and security-focused blogs all test VPNs regularly. But don't just read reviews. Read the methodology. Did they test for DNS leaks? Did they verify the no-logs policy? Did they contact the company for comment?
Check the reviews in app stores, but be skeptical. Look for patterns. Are most reviews five stars with no detail? That's a red flag. Companies sometimes buy fake reviews. Are critical reviews being deleted or hidden? That's also a red flag.
Research the company itself. Who founded it? Who owns it? Where is it based? A VPN based in a country with strong privacy laws (Switzerland, Panama, Romania) is inherently more trustworthy than one based in the US, UK, or China.
Look for any history of breaking no-logs promises. Turkish authorities once seized VPN servers and got user logs from companies claiming not to keep them. That happened. Know which companies were transparent about this failure and which ones still claim zero vulnerabilities.
Check whether the VPN has undergone independent audits. Companies like Cure53 and Deloitte regularly audit security companies. An audit doesn't guarantee safety, but lack of audits is suspicious.
Phase 2: Testing During Trial Period
Every respectable VPN offers a money-back guarantee. Use it. Most give you 30 days to test before requesting a refund.
Testing Protocol Support: Download the VPN app and check the settings. What protocols are available? You want to see OpenVPN, WireGuard, or IKEv2. If you see PPTP or custom protocols with weak names, uninstall and get your money back.
Testing for Leaks: Visit ipleak.net or whatismyipaddress.com. Note your real IP address. Connect to the VPN and check the IP address again. It should be completely different. Do this on multiple VPN servers, including servers in different countries.
Next, check for DNS leaks. Visit dnsleaktest.com. Your DNS servers should show as belonging to the VPN provider, not your ISP. If you see your ISP's DNS servers in the results, the VPN is leaking.
Check for IPv6 leaks using ip6leak.com. If the site shows any IPv6 address, you have an IPv6 leak.
Testing Kill Switch: Disconnect the VPN while browsing. You should immediately lose internet access. Reconnect the VPN. The kill switch should have prevented any unencrypted data from going out.
Testing Speed: Download a file through the VPN and through a regular connection. How much slower is the VPN? A 20-30% slowdown is normal. A 70% slowdown suggests poor infrastructure.
Checking the App: Does the app constantly try to show you ads? Does it ask for excessive permissions? Does it request access to your photos, contacts, or location? These are all red flags.
Phase 3: Verification of Claims
Before paying for a subscription, verify key claims:
No-Logs Policy: Read the actual policy, not just the marketing summary. Look for technical specifics. What exactly doesn't get logged? Connection logs? Traffic logs? DNS queries? Payment information? A vague policy isn't worth much.
Server Locations: Count them. Some VPNs claim presence in 94 countries but only have a dozen actual servers. More servers usually means more consistent speeds and better geographic coverage.
Jurisdictional Safety: Where is the company based? Are they subject to Five Eyes surveillance agreements? Are their servers in countries with strong data protection laws?
Payment Privacy: Can you pay with cryptocurrency without an account? Some VPNs require your real name and email. Others accept anonymous payment and let you use the service anonymously.
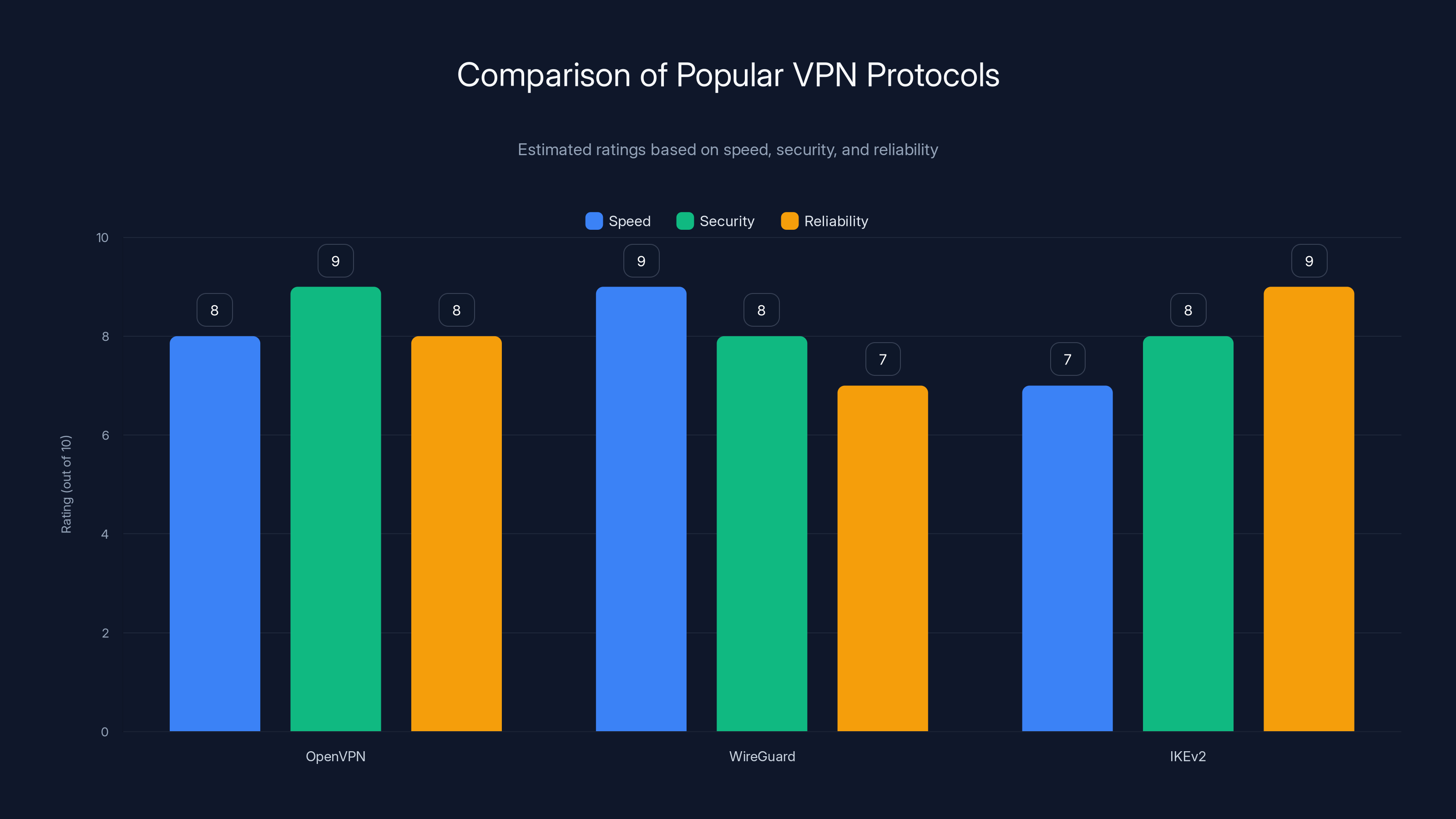
WireGuard scores highest in speed, while OpenVPN and IKEv2 excel in security and reliability respectively. Estimated data based on typical protocol characteristics.
DNS Leaks: A Specific Threat
DNS leaks deserve their own section because they're common, invisible, and completely undermine a VPN's core function.
Here's the scenario: You connect to a VPN. Everything routes through the encrypted tunnel. Great. But your device still needs to translate domain names into IP addresses. When you type www.example.com, your device asks a DNS server "What's the IP address for example.com?"
If that DNS query goes to your ISP's servers (or Google's public 8.8.8.8), they see that your device is looking up example.com. Your VPN provider doesn't see the query because it's not going through their tunnel. Your ISP can log it, and depending on your country, might be required to keep those logs.
A proper VPN uses its own DNS servers. The DNS query goes through the encrypted tunnel to the VPN's DNS resolver. The ISP can see you're using a VPN, but can't see which websites you're looking up.
So why do some VPNs still have DNS leaks? Sometimes it's negligence. The developer didn't configure DNS routing properly. Sometimes it's a bug in the OS. Windows, Mac, and Linux sometimes have quirks in how they handle DNS when multiple resolvers are available. A quality VPN prevents these edge cases. A cheap VPN doesn't bother.
How do you know if you have a DNS leak? Visit dnsleaktest.com while connected to the VPN. It will show you which DNS servers are being used. If you see your ISP's name, you have a leak.

IPv6 Leaks: The Invisible Threat
IPv6 is the next-generation internet protocol. It's been rolling out for over a decade, but adoption is still incomplete. This incompleteness creates a VPN vulnerability.
Most VPN providers focus on IPv4 protection because that's what most internet traffic currently uses. But if your device supports IPv6 (which most modern devices do), and the VPN doesn't tunnel IPv6 traffic, your real IPv6 address leaks.
To someone checking your connection, they'd see both your VPN IPv4 address (hiding your location) and your real IPv6 address (revealing your location). The VPN becomes useless.
Testing for IPv6 leaks is simple: Visit ip6leak.com while connected to the VPN. If you see an IPv6 address, you have a leak. Some VPNs handle this by disabling IPv6 entirely. Others properly tunnel IPv6 traffic. The best ones let you choose.
As IPv6 adoption accelerates, this becomes more important. In five years, ignoring IPv6 leaks will be as bad as ignoring IPv4 leaks today.
The Kill Switch: Your Safety Net
A kill switch is a feature that immediately stops all internet traffic if your VPN connection drops. It's not optional; it's essential.
Here's why: You're browsing with a VPN, thinking you're secure. The VPN connection drops for a split second due to a server hiccup. Your OS falls back to your regular internet connection. For a brief moment, data flows unencrypted. Your ISP sees it. Websites see your real IP.
Without a kill switch, this happens silently. You have no idea. With a kill switch, your connection cuts off immediately. When the VPN reconnects, you can resume browsing. You're never exposed.
But kill switches aren't all equal. Some are application-level, meaning they only stop a specific app from accessing the internet. Others are system-level, blocking all internet traffic. System-level is more effective but potentially more disruptive (you might need to manually reconnect the VPN if the connection drops).
When testing a VPN, actually test the kill switch. Disconnect the VPN by pulling the network cable or disabling Wi-Fi. Watch whether you maintain internet access or whether everything cuts off. A functioning kill switch will prevent you from browsing unencrypted.

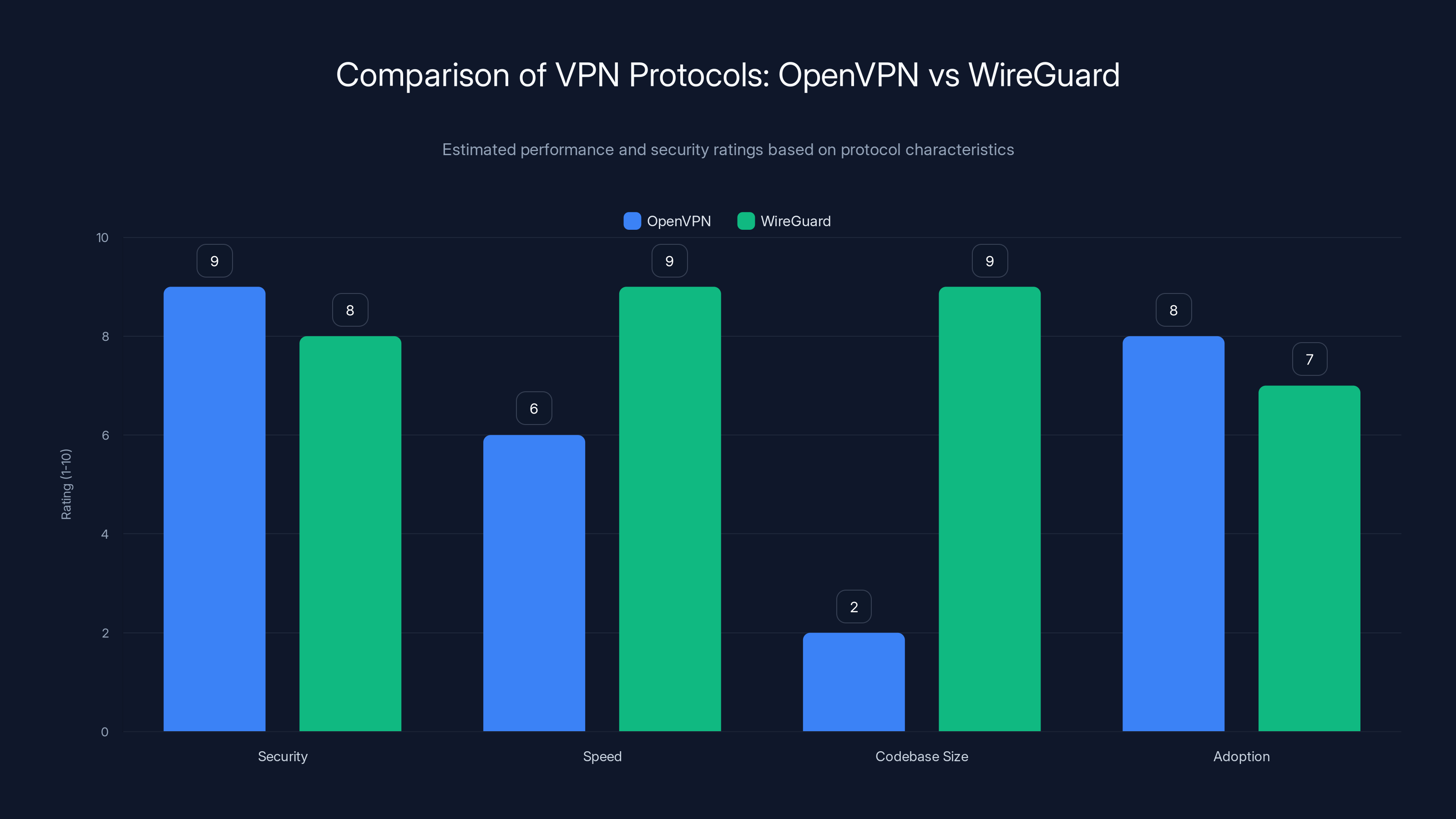
OpenVPN is highly secure but slower due to its larger codebase, while WireGuard offers faster speeds with a smaller codebase but slightly less adoption. (Estimated data)
Server Security and Third-Party Infrastructure
Your data is only as secure as the servers it passes through. This is where many VPNs cut corners.
Some VPNs rent servers from major cloud providers like AWS or Digital Ocean. That's not inherently bad, but it means the server infrastructure isn't fully controlled by the VPN company. If AWS has a security breach, the VPN company's servers might be affected. If Digital Ocean's security is compromised, the VPN's users are vulnerable.
The best approach? VPNs that own their infrastructure or rent from dedicated hosting providers with stronger security practices. These companies have higher overhead but lower risk.
You can't easily verify this as a consumer, but you can look for transparency. Does the company publish a transparency report about security incidents? Do they maintain a bug bounty program? Do they have a responsible disclosure policy? These suggest they're taking security seriously.

What's in Your VPN Traffic?
Understanding what a VPN encrypts helps you understand what it protects.
A VPN encrypts everything except the VPN protocol itself. The VPN provider can see that you're using a VPN and when, but not what you're sending through it. Your ISP can see you're using a VPN but not your traffic. Websites see a connection from the VPN server's IP, not your real IP.
But metadata matters. Your VPN provider can see:
- How much data you're using
- Rough usage patterns (you're online from 9 AM to 5 PM)
- Which VPN server you connected to
- How long your sessions last
Some VPNs claim "zero knowledge," meaning they can't see even metadata. In practice, this is difficult. Running a VPN service requires some visibility into what's happening. "Zero knowledge" really means "we don't keep logs of your activity," not "we have no technical ability to see anything."
Unencrypted metadata is still valuable. A surveillance agency could see that you connect to a VPN from 9 AM to 5 PM every weekday (implying work use), or that you use specific servers (a political journalist might always connect to servers in countries without extradition treaties). A VPN reduces visibility, but doesn't eliminate it.
The No-Logs Promise: What It Actually Means
Most quality VPNs claim they don't keep logs. But "no logs" is vague. What specifically isn't logged?
Traffic Logs: Records of what websites you visit, what data you send. A no-logs policy should cover this. Any VPN claiming not to keep these logs is making a strong statement.
Connection Logs: Records of when you connected, how long you were online, how much data you used. Some VPNs say they don't keep traffic logs but do keep basic connection logs for infrastructure purposes. This is a middle ground.
DNS Logs: Records of which domains you looked up. A proper no-logs policy covers this.
Payment Information: This is tricky. If you pay with your real name and credit card, the VPN must keep those records for tax and compliance reasons. Some VPNs solve this by accepting cryptocurrency, which enables truly anonymous usage.
Metadata: IP addresses used, server selection, session information. Some VPNs don't keep this, others do.
When evaluating a no-logs policy, read the fine print. A good policy specifies exactly what is and isn't logged. Vague promises are worth skepticism.
Also, realize that a no-logs policy doesn't mean the VPN can't comply with a government request. If law enforcement seizes the servers, they get whatever data exists, logged or not. What a no-logs policy means is that if a government asks for logs, there are none to provide (unless the government catches the VPN making false claims, in which case they have evidence of breaking the law).
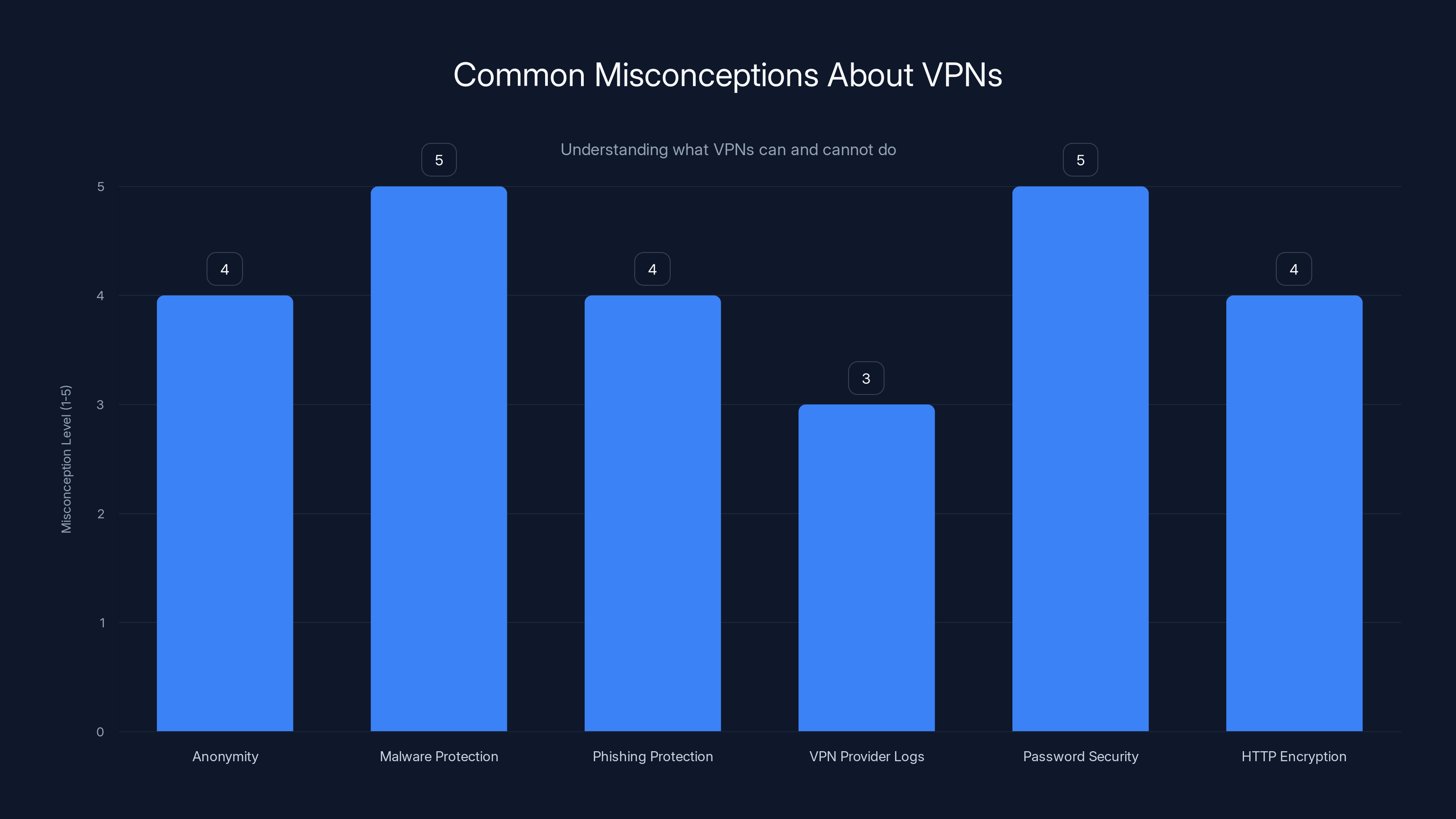
Many users mistakenly believe VPNs provide anonymity, malware protection, and more. Understanding these misconceptions can prevent over-reliance on VPNs for security.
Common VPN Vulnerabilities Beyond the Protocol
Even with solid encryption protocols, vulnerabilities can exist elsewhere.
Browser Fingerprinting
A VPN hides your IP, but it doesn't prevent websites from fingerprinting your browser. This involves collecting information about your device, OS, browser version, fonts, screen resolution, timezone, and other characteristics. Enough of these unique identifiers can pinpoint you despite the VPN.
A quality VPN provider suggests using a privacy-focused browser like Firefox or Tor. But the VPN provider themselves can't prevent fingerprinting. That's a broader privacy issue.
Timestamps and Behavioral Patterns
If you connect to a VPN every Monday at 9 AM and disconnect at 5 PM, you're establishing a recognizable pattern. Over time, if someone correlates your VPN usage with your physical location (detected by your phone, a security camera, or other means), they could link the VPN sessions to you.
A VPN provides reasonable protection against casual ISP tracking, but determined adversaries can still link sessions to individuals through behavioral analysis.
WebRTC Leaks
Some browsers support WebRTC, a technology for real-time communication. A poorly configured WebRTC implementation can leak your real IP address even while using a VPN. This is often a browser configuration issue, not a VPN flaw, but quality VPN providers document how to disable WebRTC in popular browsers.
Exit Node Vulnerabilities
The "exit node" is where your traffic leaves the VPN and goes to the public internet. A compromised exit node could potentially intercept traffic. However, as long as traffic is encrypted end-to-end (like HTTPS), the exit node can't read it. But unencrypted traffic (HTTP) could be exposed.
This is why HTTPS everywhere is so important. A VPN protects you from ISP snooping, but it doesn't add encryption on top of already-encrypted traffic.
Red Flags: What to Avoid
Certain characteristics almost always indicate a problematic VPN.
Price Too Good to Be True: If a VPN costs $2 per month with unlimited everything, where's the money coming from? Either the infrastructure is terrible (and speeds are unusable), or they're making money another way (selling your data, injecting ads, harvesting your IP).
Marketing That Emphasizes Anonymity Without Nuance: Legitimate VPN providers explain what they do and don't do. If all the marketing is "be completely anonymous" without mentioning limitations, they're exploiting misunderstandings.
App Store Reviews That Are All 5 Stars: Fake reviews are a common tactic. Look for a mix of ratings. Apps with only 5-star reviews from new accounts are probably fraudulent.
Aggressive Data Requests: A VPN doesn't need access to your camera, microphone, photo library, or location. If the app requests these permissions, it's harvesting data.
Constant Pop-ups for Upgrades: The free tier should be usable. If it's constantly interrupting you with upgrade offers, it's more scareware than legitimate service.
No Transparency Report: Quality VPNs publish annual reports showing government requests, how many they comply with, and why. If a VPN never mentions this, they're either hiding something or not professionally run.
Vague Technical Details: A legitimate VPN explains what protocols they use, which encryption ciphers, which features are included. If the website is all marketing and no technical substance, skip it.
Jurisdictional Considerations
Where a VPN is based matters because different jurisdictions have different laws and surveillance frameworks.
Five Eyes Countries (US, UK, Canada, Australia, New Zealand): These countries have developed intelligence-sharing agreements. A VPN based in these countries is technically subject to surveillance requests from any of these five governments.
Switzerland: Known for strong data protection laws and privacy-friendly regulations. Many legitimate VPNs are based here.
Panama: Has good privacy laws but is sometimes used as a jurisdiction-shopping destination by less reputable companies.
Romania: Strong data protection laws and not part of Five Eyes surveillance agreements.
China: Any VPN based in China is subject to Chinese government control. They can be forced to install backdoors or comply with censorship requests.
Ideally, choose a VPN based in a jurisdiction with strong privacy laws and not subject to Five Eyes agreements. But even a US-based VPN is better than no VPN if they're transparent and trustworthy.
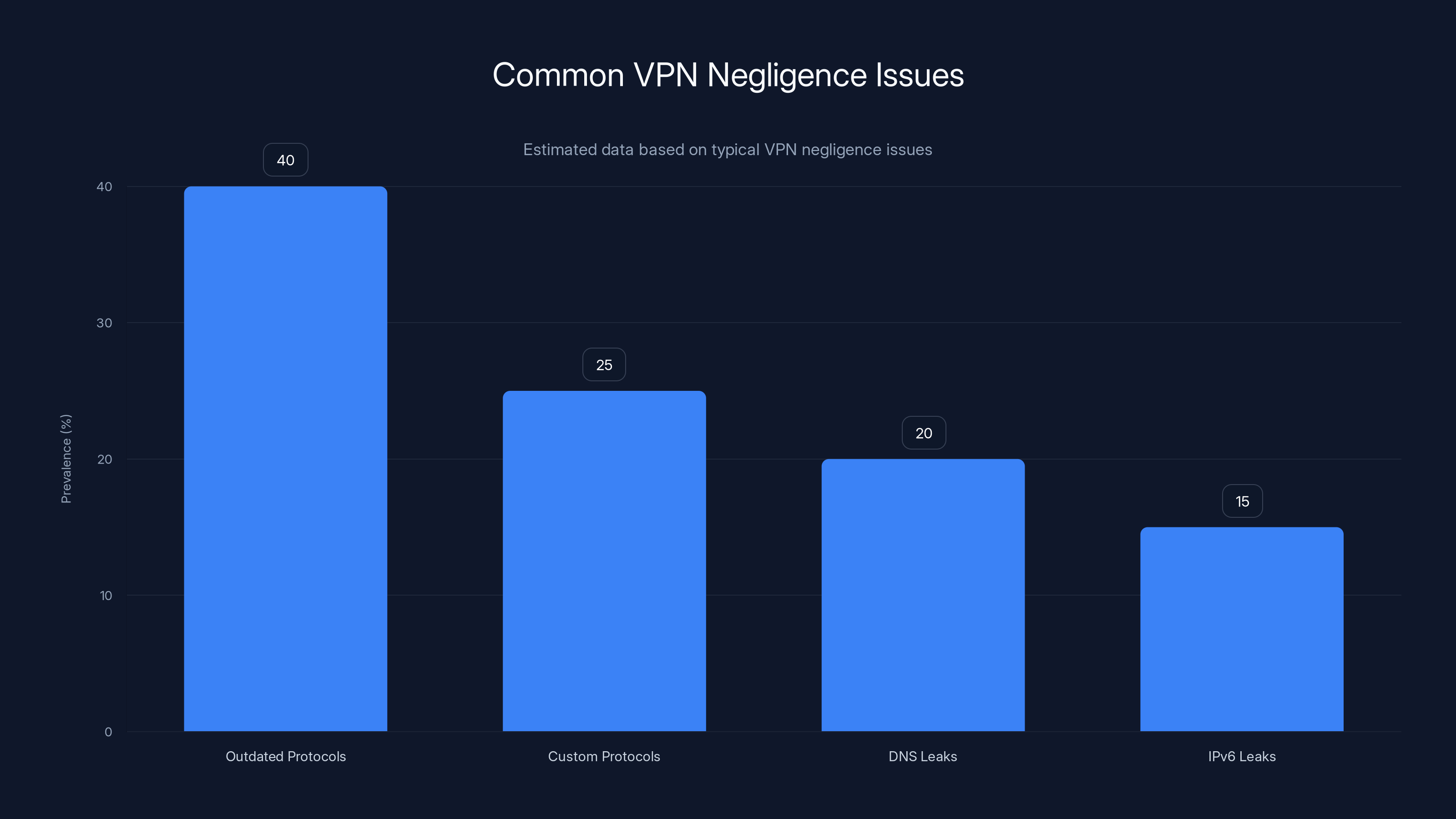
Outdated protocols are the most common negligence issue in VPNs, followed by custom protocols and DNS leaks. Estimated data based on typical issues.
VPN Usage Patterns That Stay Safe
Assuming you've chosen a legitimate, secure VPN, how do you use it safely?
Always Use HTTPS: A VPN doesn't encrypt data that's already encrypted. HTTPS protects the connection between you and a website. Together, HTTPS and a VPN provide robust protection against multiple threats.
Don't Trust Sites Just Because You're on a VPN: A VPN hides your IP, but it doesn't validate that a website is legitimate. Phishing attacks work just fine through a VPN.
Use Two-Factor Authentication: A VPN protects your IP, but if someone gets your password, they can access your accounts. 2FA prevents this even if your password is compromised.
Update Your OS and Apps: A VPN doesn't protect against malware that comes from unpatched vulnerabilities. Keep everything updated.
Use on Untrusted Networks: The real value of a VPN is on public Wi-Fi, in hostile countries, or on networks you don't trust. At home on your own Wi-Fi, the benefit is mainly ISP privacy.
Remember VPN Limitations: A VPN doesn't protect against you downloading malware, falling for phishing, or using weak passwords. It's one layer of security, not a complete solution.
The Difference: Commercial VPNs vs. Enterprise VPNs
This guide is about commercial VPNs like ProtonVPN and ExpressVPN. These are designed for personal privacy.
Enterprise VPNs like NordLayer and Cisco AnyConnect serve a different purpose. They're designed to securely connect remote workers to corporate networks. The trust model is completely different. You're trusting your employer, not a third party. The security model is tailored for corporate environments, not personal privacy.
They're both called "VPNs" but serve different purposes. Don't confuse them.

When a VPN Isn't Enough
A VPN is one security tool among many. It's not a complete solution.
For comprehensive security, also use:
- Password Manager: Generates strong, unique passwords for every site
- Two-Factor Authentication: Adds a second verification step
- HTTPS Everywhere: Encrypts traffic to websites automatically
- Antivirus/Antimalware: Detects and removes malicious software
- Firewall: Blocks unauthorized inbound connections
- Regular Updates: Patches vulnerabilities in your OS and apps
- Backups: Recovers data if ransomware strikes
- Privacy Browser: Blocks trackers and fingerprinting
- VPN Kill Switch: Ensures no leaks if the connection drops
A VPN handles one specific problem: ISP/network snooping. It's excellent at that job. But it's not a substitute for a comprehensive security approach.
Future of VPN Security
VPN technology is evolving. A few trends to watch:
Post-Quantum Cryptography: Current encryption will eventually be vulnerable to quantum computers. VPN providers are beginning to prepare for this by testing post-quantum resistant algorithms. In 5-10 years, this will become mandatory.
Decentralized VPNs: Some projects are building VPNs where users provide the exit nodes, rather than relying on a central company. This eliminates a single point of failure but introduces other complexities.
WireGuard Adoption: WireGuard is becoming the default for new VPN providers. As the protocol matures, it'll likely replace OpenVPN as the industry standard.
IPv6 Maturity: As more internet traffic switches to IPv6, properly handling IPv6 will become a minimum requirement instead of a nice-to-have.
Privacy by Law: Regulations like GDPR are forcing companies to be transparent about data collection. This is gradually raising baseline standards.

Conclusion: Making the Right Choice
VPNs are genuinely useful tools. They protect your traffic from your ISP, from local Wi-Fi snooping, and from ISP throttling. They provide plausible deniability that you visited certain websites.
But they're tools with limitations. They don't protect you from malware, phishing, weak passwords, or unencrypted services. They don't make you completely anonymous. They're only as good as the company running them.
The safety of a VPN depends entirely on your choice. A legitimate, well-implemented VPN from a trustworthy company is genuinely safe. A malicious or negligent VPN is worse than no VPN at all.
Before choosing a VPN, spend time researching. Read reviews from multiple sources. Understand what protocols the VPN uses. During the trial period, test for leaks, verify the kill switch works, and check the app for suspicious behavior. Only after being confident should you commit to a subscription.
The market is flooded with imposters. But legitimate VPNs exist, and they're worth using if you value your privacy. Just do the research first. Your security depends on it.
FAQ
What is a VPN and why would someone use one?
A VPN (Virtual Private Network) is a service that encrypts your internet traffic and routes it through a remote server. This hides your real IP address from websites and your ISP from seeing which sites you visit. People use VPNs for privacy on public Wi-Fi, to access geographically restricted content, to avoid ISP throttling, and to reduce tracking by websites and advertisers.
How does VPN encryption work?
VPNs use cryptographic protocols to create an encrypted tunnel between your device and the VPN server. Your traffic travels through this encrypted tunnel, making it impossible for eavesdroppers on your local network or your ISP to read the contents. The VPN provider can see you're using their service, but not your actual data. The encryption uses mathematical algorithms like AES-256 or ChaCha20 that are computationally impossible to break with current technology.
What are the best VPN protocols?
The three most trusted and expert-verified protocols are OpenVPN (open source, thoroughly audited, established since 2001), WireGuard (modern, fast, clean codebase, fewer lines of code to audit), and IKEv2 (standardized, reliable for mobile users, good reconnection handling). Any other protocol should use military-grade AES-256 or ChaCha20 encryption to be considered secure.
Can a VPN prevent malware infections?
No, a VPN cannot prevent malware infections. If you download an infected file or visit a malicious website through a VPN, the VPN doesn't add any protection. Malware comes from the files or code you execute, not from your network connection. A VPN only protects the data in transit between your device and the VPN server, not your device itself. You need antivirus software, regular updates, and careful browsing habits for malware protection.
What is a DNS leak and why does it matter?
A DNS leak occurs when your device sends domain name lookups to your ISP's DNS servers instead of through the VPN's encrypted tunnel. This means your ISP can still see which websites you're trying to visit, even though the actual traffic is hidden. A DNS leak completely defeats the purpose of a VPN regarding privacy from your ISP. Testing for DNS leaks at dnsleaktest.com takes 30 seconds and reveals whether your VPN properly handles DNS requests.
Can I be tracked while using a VPN?
Yes, you can still be tracked through other methods despite using a VPN. Websites can use browser fingerprinting to identify you based on device characteristics, cookies can track your behavior across sites, and logging into personal accounts (Gmail, Facebook, etc.) immediately identifies you to those services. A VPN hides your IP address but doesn't prevent websites from learning who you are if you provide that information. For comprehensive privacy, combine a VPN with a privacy-focused browser and cookie management.
What is a kill switch and why is it important?
A kill switch is a security feature that disconnects your internet access if your VPN connection unexpectedly drops. Without a kill switch, your device might automatically fall back to your regular ISP connection, exposing unencrypted traffic for a brief moment. You wouldn't even know this happened. A functioning kill switch prevents this by immediately cutting off internet access, ensuring you're never accidentally browsing unencrypted. Testing the kill switch involves disconnecting your VPN and verifying you lose internet access.
How do I know if a VPN is safe before paying for it?
Legitimate VPNs offer 30-day money-back guarantees specifically so users can test them. During the trial, verify the VPN protocols used (should be OpenVPN, WireGuard, or IKEv2), test for DNS and IPv6 leaks using free online tools, check that the kill switch prevents unencrypted browsing, measure speed impact, and review the app for excessive permissions or aggressive advertising. Also research the company's jurisdiction, check for security audit reports, and read detailed reviews from multiple sources. If anything seems suspicious during testing, request a refund.
Do free VPNs have different safety issues than paid VPNs?
Free VPNs almost always have significant safety issues. Since they don't charge for the service, they must make money another way, which typically means harvesting your data, selling your residential IP address to advertisers, injecting tracking ads, or selling your browsing activity to data brokers. Additionally, free VPNs often use outdated protocols, have poor infrastructure, and don't maintain security updates. The phrase "if you're not paying for the product, you are the product" applies perfectly to free VPNs. Even a cheap paid VPN at $3-5 per month is safer than free alternatives.
What's the relationship between VPNs and HTTPS encryption?
VPNs and HTTPS serve different purposes and work together. HTTPS encrypts the communication between you and a specific website, while a VPN encrypts all traffic from your device to the VPN server. A VPN protects you from your ISP and local network seeing that you visited a website. HTTPS protects the data you send to that website from being intercepted. For maximum security, you need both. A VPN alone doesn't add encryption on top of HTTPS, but it does hide the fact that you visited the HTTPS website from your ISP.
Is it legal to use a VPN?
VPN usage is legal in most countries, though a few authoritarian nations restrict or ban them. However, legality doesn't mean consequences-free. Using a VPN to access services you're legally restricted from (like streaming services in countries where you don't have rights to access them) is technically a violation of terms of service. Using a VPN to hide illegal activity is still illegal. A VPN is a tool that provides privacy, but it doesn't provide immunity from laws.

Key Takeaways
- VPN safety depends entirely on choosing the right provider. Legitimate VPNs with solid encryption are safe; malicious or negligent ones are dangerous.
- Three protocols matter: OpenVPN (proven), WireGuard (modern), IKEv2 (standardized). Anything else needs military-grade AES-256 or ChaCha20 encryption.
- DNS leaks, IPv6 leaks, and missing kill switches can completely undermine a VPN's security. Always test these during the free trial.
- Malicious VPNs harvest IP addresses, track activity, inject ads with trackers, and sell data to advertisers. Research company background before trusting.
- A VPN protects against ISP snooping and local network eavesdropping, but doesn't prevent malware, phishing, weak passwords, or unencrypted services.
Related Articles
- I Tested a VPN for 24 Hours. Here's What Actually Happened [2025]
- Why Brits Fear Online Privacy But Trust the Wrong Apps [2025]
- Best VPN Deals 2025: Save Up to 87% on Premium Services [2025]
- Iran's Digital Isolation: Why VPNs May Not Survive This Crackdown [2025]
- Best VPN Under $3/Month: Advanced Features for Less [2025]
- Best VPN Services 2025: Tested, Reviewed, and Ranked [2025]
![Are VPNs Really Safe? Security Factors to Consider [2025]](https://tryrunable.com/blog/are-vpns-really-safe-security-factors-to-consider-2025/image-1-1769694080127.png)



