DOGE's Social Security Data Scandal: What Happened and Why It Matters
When a federal judge blocked DOGE's access to the Social Security Administration's most sensitive databases, the Trump administration seemed to understand the stakes. The order was clear: no more unsupervised access to Social Security numbers, medical records, driver's license information, or tax data. The systems contained some of the most personal information millions of Americans possess.
Then came January 2025, and everything got worse.
Court documents filed by the Justice Department revealed what many security experts had feared: members of Elon Musk's Department of Government Efficiency may have deliberately circumvented that court order to hand over Americans' private data to a political advocacy group. The goal, according to the government's own admissions, was to "overturn election results in certain States" as reported by The New York Times. The methods they allegedly used violated the Hatch Act, federal data protection laws, and basic operational security principles that should never be negotiable in government.
This isn't a story about incompetence or bureaucratic overreach. It's a story about the erosion of data privacy protections, the politicization of federal agencies, and what happens when political goals override the constitutional rights of ordinary Americans. And it reveals something far more troubling: how little separates government agencies from being weaponized against citizens when proper oversight fails.
Let's break down what actually happened, why it matters, and what it means for everyone whose personal information sits in government databases.
The Timeline: How DOGE Gained and Abused SSA Access
Understanding this scandal requires knowing how we got here. When DOGE was created in late 2024 as part of the Trump administration's efficiency push, it wasn't just a consulting outfit. It had real authority. Members of the DOGE team were embedded directly within federal agencies, including the Social Security Administration. They had credentials. They had access. And according to SSA leadership at the time, they had minimal oversight.
The SSA oversees one of the most valuable databases in existence. Every American who's ever worked, collected benefits, or applied for a loan has a Social Security number in SSA systems. Alongside those numbers are medical records from disability applicants, tax information, address histories, and employment records spanning decades. The information is so sensitive that federal law treats unauthorized access as a serious crime.
In March 2025, a political advocacy group made contact with two DOGE members embedded at SSA. The request was straightforward: help us analyze voter rolls to find evidence of election fraud. The advocacy group wanted to cross-reference voter registration data with other information they'd "acquired." They wanted DOGE's help matching data, analyzing patterns, and identifying discrepancies that could prove fraud claims.
What happened next is where the scandal truly takes shape. Instead of refusing or escalating through proper channels, one DOGE member signed a "Voter Data Agreement" with the advocacy group. This wasn't a casual email. It was a formal contract. The member was acting as an SSA employee when they signed it, which means they were representing the U.S. government in a transaction involving voter data and election integrity claims.
According to Justice Department official Elizabeth Shapiro's testimony, the DOGE members then may have accessed information from SSA databases that a federal court had explicitly ruled off-limits. The accessed data didn't stay internal either. Instead, it was potentially shared with the advocacy group via unapproved third-party servers. Think about that for a moment: Americans' Social Security numbers, possibly traveling through cloud servers chosen by a political organization, potentially stored in facilities without any federal security oversight.
The full scope of what was accessed or shared remains unclear. The government's documents suggest emails indicate DOGE members "could have been asked to assist the advocacy group by accessing SSA data." The word "could" is doing a lot of work here. It means the government isn't entirely sure what happened. That uncertainty is itself terrifying.
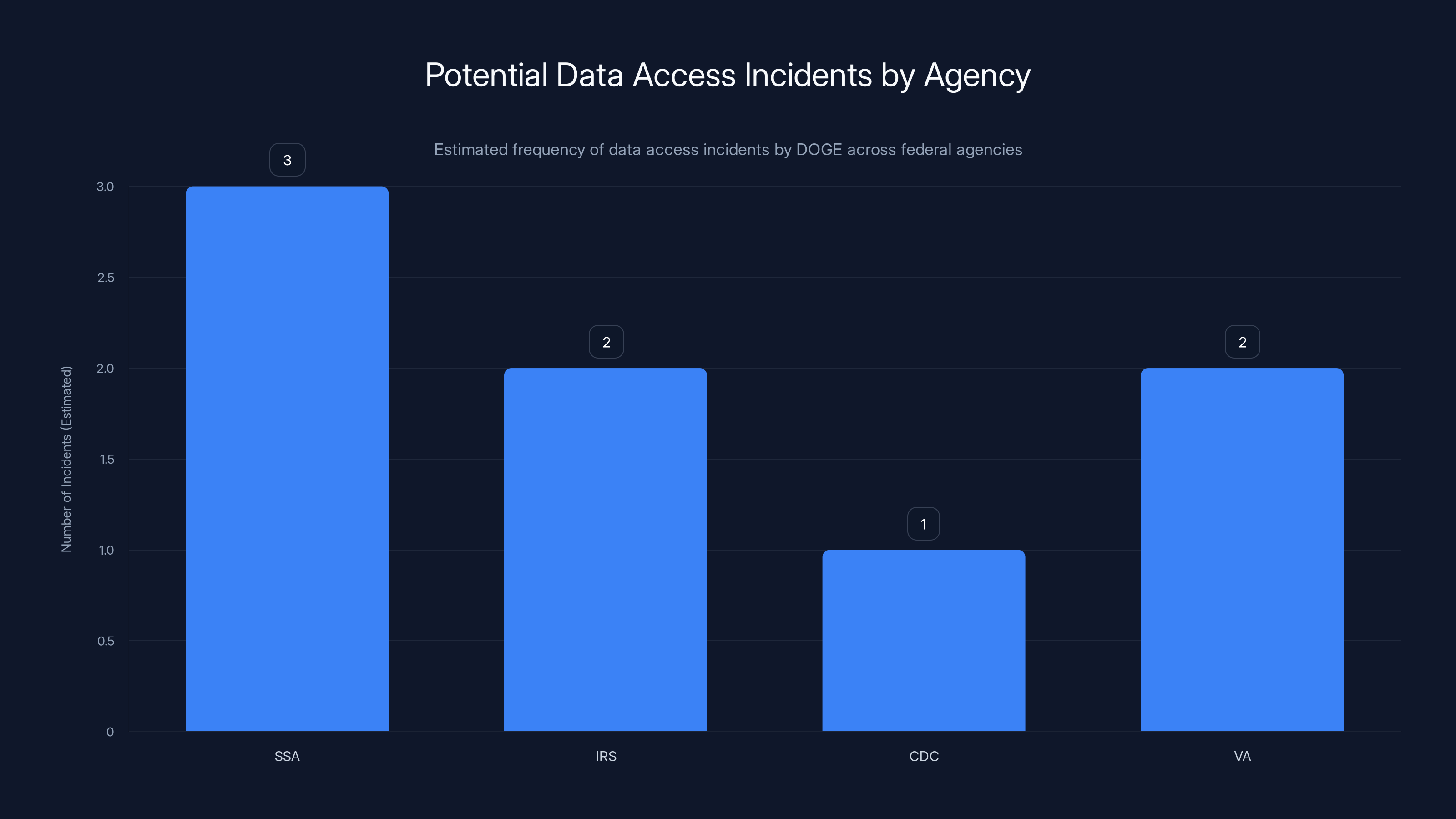
Estimated data suggests potential for multiple data access incidents across various federal agencies, with SSA being the most vulnerable due to its sensitive data.
Why the Court Order Mattered and Why It Was Violated
Before DOGE members showed up at SSA, there were already serious concerns about their access to sensitive data. Federal judges don't issue access restrictions casually. They issue them because they've reviewed evidence of potential misuse or security risks. In this case, a federal judge had determined that DOGE's unsupervised access to SSA systems posed enough of a risk to restrict it.
The judge's order was specific: DOGE members could no longer directly access databases containing Social Security numbers and related personal information. They could work at SSA. They could review efficiency improvements. But the most sensitive systems were off-limits. This wasn't bureaucratic obstruction. This was a constitutional check on government power.
Then DOGE members allegedly accessed those exact restricted systems anyway. The technical mechanism matters here. They didn't just read information and discuss it internally. They signed formal data-sharing agreements with external organizations. They moved data to third-party servers. They potentially enabled a political organization to match voter rolls against Social Security records.
This violated the court order in multiple ways. First, there was the direct violation: accessing restricted data. Second, there was the secondary violation: sharing that data beyond government systems. Third, there was the procedural violation: doing all of this through a formal agreement with an outside organization, which suggests this wasn't accidental but deliberate.
Why does the method matter? Because it shows intent. You don't accidentally sign formal data-sharing agreements. You don't accidentally upload millions of records to external cloud servers. These are deliberate, documented actions that require multiple decisions and approvals. The paper trail suggests this was planned.
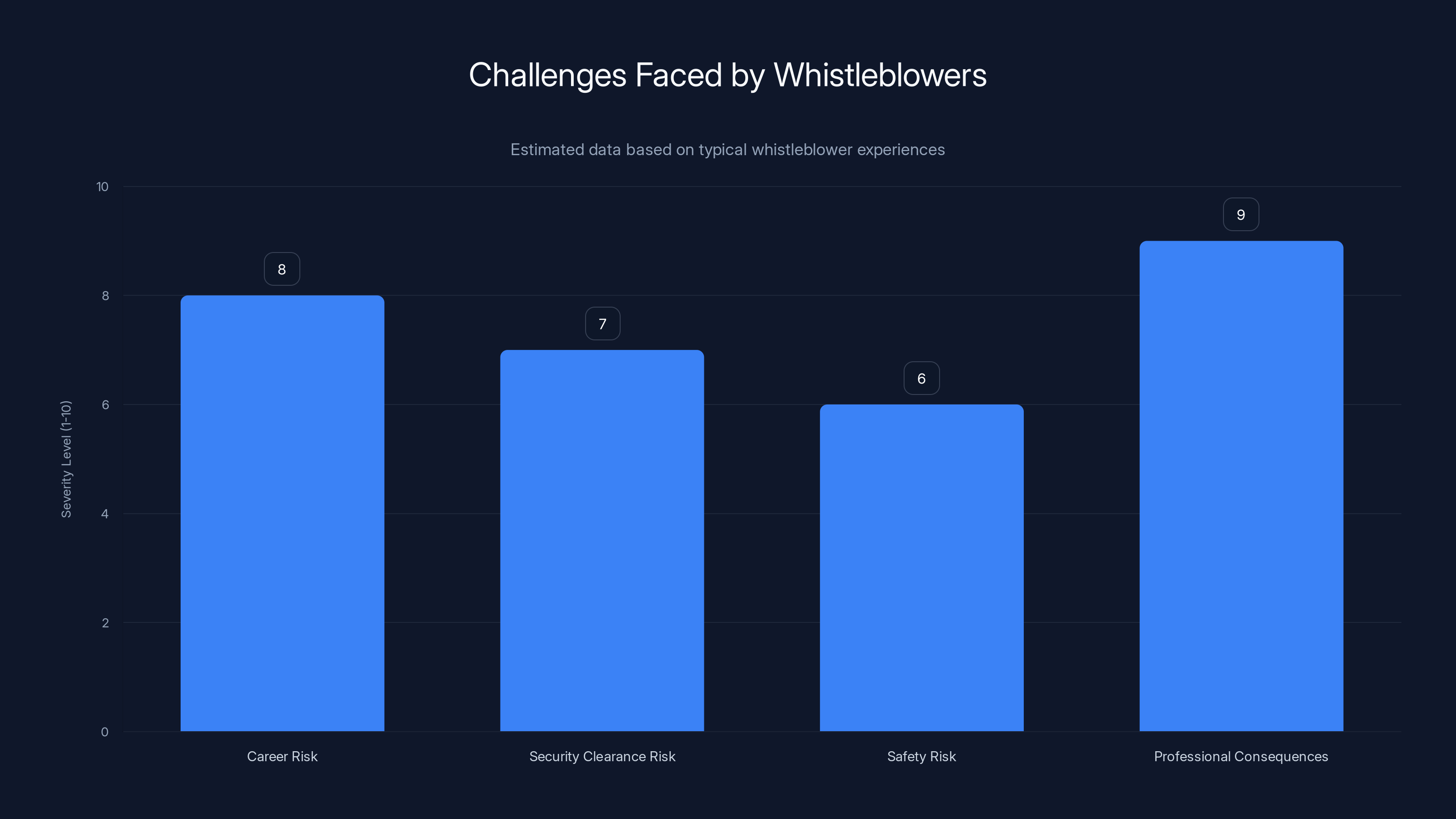
Whistleblowers often face high career and professional risks, with severe consequences for exposing wrongdoing. Estimated data.
The Hatch Act Violation and Political Weaponization of Federal Agencies
The Hatch Act is one of the oldest federal laws protecting government integrity. Passed in 1939, it's simple: federal employees can't leverage their official positions for political purposes. You can vote. You can donate to campaigns on your own time. But you can't use government resources, access, or authority to advance political causes.
What DOGE members allegedly did was textbook Hatch Act violation. They held government positions at SSA. They had access to government data as a result of those positions. They used that access to support a political goal: finding evidence of election fraud to overturn election results. They signed formal agreements with political advocacy organizations. They may have shared government data specifically to advance those political goals.
The SSA's response was to refer both DOGE members for potential Hatch Act violations. This is significant. Federal agencies rarely escalate these cases unless there's clear evidence of wrongdoing. The fact that SSA leadership made formal referrals suggests they believed the violations were serious enough to warrant investigation.
But here's where the political complexity deepens. DOGE was created by the Trump administration. Its members report to Elon Musk, who reports to President Trump. The Justice Department investigating DOGE for Hatch Act violations means the Trump administration is investigating its own team. Will that investigation be rigorous? That's uncertain. Will it result in accountability? That's even more uncertain.
This creates a perverse incentive structure. If you work for a DOGE-like initiative and you're told to find election fraud evidence but instructed not to violate laws, what do you do when your boss wants results and the law is in the way? The answer, apparently, is you violate the law. You trust that your political allies will protect you.
The Cloud Server Problem: How Millions of Records Got Compromised
The initial revelation about DOGE and SSA data involved the most alarming technical detail: hundreds of millions of Social Security records were allegedly uploaded to a vulnerable cloud server. This came from a whistleblower, and subsequent investigations confirmed the basic facts.
Think about the scale. Hundreds of millions of records. Each record containing at minimum a Social Security number, but potentially including medical information from disability claims, address histories, employment records, and tax data. All of it on a cloud server that wasn't maintained by the SSA, wasn't protected by SSA security protocols, and wasn't audited by federal oversight agencies.
How vulnerable was this server? According to security researchers who examined the incident, extremely. The server was configured with default or near-default security settings. Access controls were minimal. There's no indication the data was encrypted at rest. The basic security practices that federal agencies implement as standard procedure apparently weren't present.
Why does this matter beyond the obvious privacy violation? Because it creates multiple attack vectors. Foreign intelligence agencies. Criminal networks. Rogue individuals. Any of them could potentially access this data. They wouldn't even need sophisticated hacking. Some security researchers noted that the server was discoverable through basic internet scanning tools. You could potentially find it without special knowledge.
The political advocacy group's stated rationale was that they needed the data on an external server for analytical purposes. But federal law is clear: you don't move sensitive government data to external servers for convenience. You either do the analysis within secure government systems, or you don't do it at all. There are no exceptions for political purposes or efficiency gains.
Furthermore, if the advocacy group was conducting data analysis on voter rolls, why did they need actual Social Security numbers? Why couldn't the analysis work with anonymized data or aggregated statistics? The use of actual SSNs suggests the goal wasn't just analysis. It was matching individuals. It was identifying specific people. It was potential voter targeting.
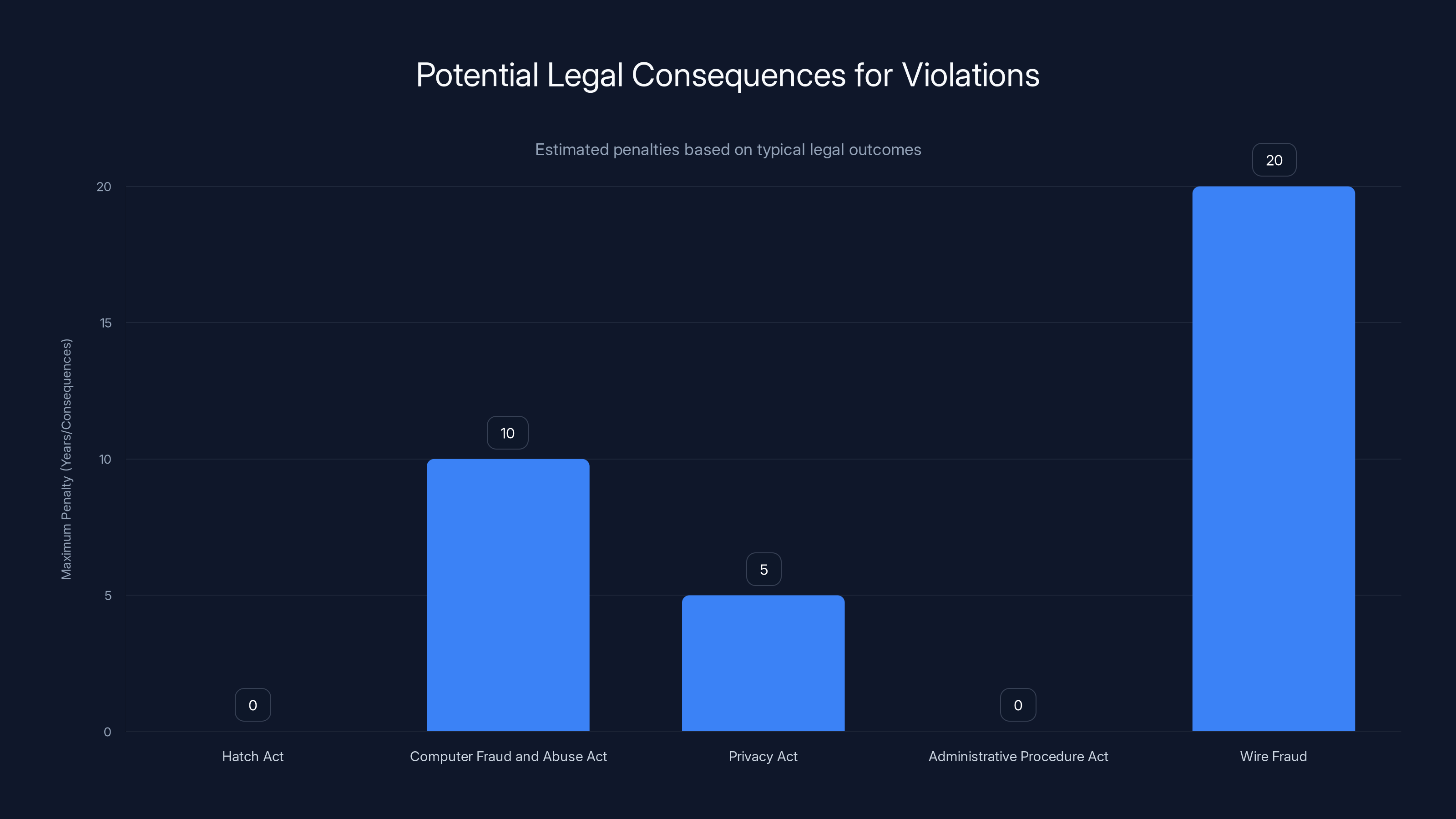
Estimated data: Hatch Act violations may lead to removal from office, while the Computer Fraud and Abuse Act can result in up to 10 years imprisonment. Privacy Act and Wire Fraud violations can lead to civil liability and significant penalties.
What About the Other SSA Employees? The Compartmentalization Question
One of the more disturbing details in the Justice Department's statement is what it says about what other SSA employees didn't know. Elizabeth Shapiro's testimony emphasized: "There is no evidence that SSA employees outside of the involved members of the DOGE Team were aware of the communications with the advocacy group. Nor were they aware of the 'Voter Data Agreement.'"
This statement is doing important work. It's suggesting that the two DOGE members operated independently, without broader SSA knowledge or approval. But does that make things better or worse?
On one level, it's better. It means this wasn't an agency-wide conspiracy. It means normal SSA employees weren't complicit. It means the institutional bias toward following rules remained, even if two specific individuals violated them.
On another level, it's worse. It means the security controls that should have prevented this didn't work. How did two people access restricted databases without triggering alerts? How did they sign formal agreements with external organizations without that appearing on any official record that colleagues would see? How did they operate for months without any oversight mechanism catching what they were doing?
This suggests fundamental problems with how federal agencies monitor employee activity. SSA likely has audit logs for database access. They should have showed which employees were accessing what data, when, and for what reason. If those logs revealed the DOGE members accessing restricted data but nobody noticed until a whistleblower came forward, that's a serious security failure.
The compartmentalization also suggests the DOGE members understood they were doing something wrong. If they thought their actions were appropriate, why keep them hidden from colleagues? Why not involve SSA leadership in the data-sharing agreement? Why sign the agreement as an SSA employee rather than a DOGE member? These are the actions of people who knew they were crossing lines.
The Election Fraud Investigation Angle: Why This Matters Beyond Privacy
The political context here is crucial. The advocacy group's stated goal was finding evidence of voter fraud and overturning election results. This wasn't vague. This wasn't exploratory. The documents explicitly state this.
Why is that significant? Because it means government access to citizen data was potentially weaponized for a specific political outcome. Federal law is designed around a principle: government power should serve all citizens equally, not partisan goals. When government employees use their access to advance particular political agendas, that's a fundamental violation of the social contract.
Furthermore, voter fraud claims were central to 2024 election disputes. Multiple courts had rejected fraud claims as unsupported by evidence. Federal and state election officials had certified results. The Department of Homeland Security called it "the most secure election in American history." So when a political advocacy group wanted to "find evidence" of fraud, they were looking for data they could use to contest an already-certified election.
And they allegedly asked government employees to help them do it using government systems and government data. That's not seeking truth. That's seeking ammunition.
The implications are profound. If DOGE members can access SSA data to support one political narrative, what prevents them from accessing it to support another? What prevents them from weaponizing data against political opponents? What prevents the normalization of using government databases as tools for partisan advantage?
This is why the Hatch Act exists. It's not bureaucratic red tape. It's constitutional protection against government tyranny. When government employees are allowed to use federal resources to advance partisan causes, democratic institutions erode.

Estimated data shows higher pressure on efficiency initiatives compared to legal compliance, highlighting potential risks of government overreach.
Security Implications: The Broader Pattern of DOGE and Data Access
This incident didn't happen in isolation. The broader pattern of DOGE's relationship with federal data is troubling. Before the SSA data access restrictions, DOGE had already been controversial for its approach to government efficiency.
The underlying philosophy seems to be: if it's inefficient, bypass it. If regulatory oversight slows things down, work around it. If security protocols prevent quick data access, find alternative routes. This approach works fine for optimizing paperwork processes. It's catastrophic for handling sensitive personal data.
Each government agency has different systems, different security requirements, different data types. The SSA handles some of the most sensitive personal information in government. The IRS handles tax data. The VA handles military medical records. The CDC handles health information. These agencies have different security profiles and different regulatory requirements for good reasons.
When DOGE members were embedded in these agencies with access to restricted systems, the assumption was that they would respect those boundaries. They would understand that some security restrictions aren't inefficiency, they're constitutional protection. They would accept that some data isn't theirs to move or share, regardless of political purpose.
But the SSA incident suggests that assumption was wrong. It suggests DOGE operates with a different framework: the restrictions are obstacles to overcome, not protections to respect.
Why does this matter beyond the SSA? Because DOGE has access to multiple federal agencies. If the pattern holds, we should expect similar incidents at other agencies with sensitive data. The IRS could face election-related data requests. The CDC could face requests for health data related to ongoing policy debates. The VA could face pressure to share military medical records.
The question becomes: how many times will this pattern repeat before Congress or courts intervene?

The Whistleblower's Role: How This Got Exposed
Without the SSA whistleblower, we might not know about any of this. The DOGE members weren't planning to announce they'd accessed restricted data or uploaded hundreds of millions of records to external servers. The advocacy group wasn't planning to reveal they'd requested government assistance with their data analysis. The Justice Department wouldn't have been forced to issue corrected testimony without pressure.
Whistleblowers are often the only check on government abuse. They risk their careers, their security clearances, potentially their safety to expose wrongdoing. In this case, the whistleblower flagged the cloud server incident, which triggered investigations, which revealed the broader pattern of data access and sharing.
But whistleblowing has become increasingly difficult in recent years. Federal protections for whistleblowers exist, but they're often inadequate. Agencies can make life miserable for anyone who reports problems. They can reassign you, deny promotions, create hostile work environments, or simply wait for your contract to expire.
What protections did this SSA whistleblower have? The documents don't say. But if the pattern holds at other agencies, they probably faced pressure and professional consequences. That's how the system discourages future whistleblowing.
This creates a vicious cycle. Wrongdoing occurs. Whistleblowers expose it, and suffer consequences. Future potential whistleblowers see those consequences and stay silent. The incentive structure systematically rewards silence and punishes accountability.

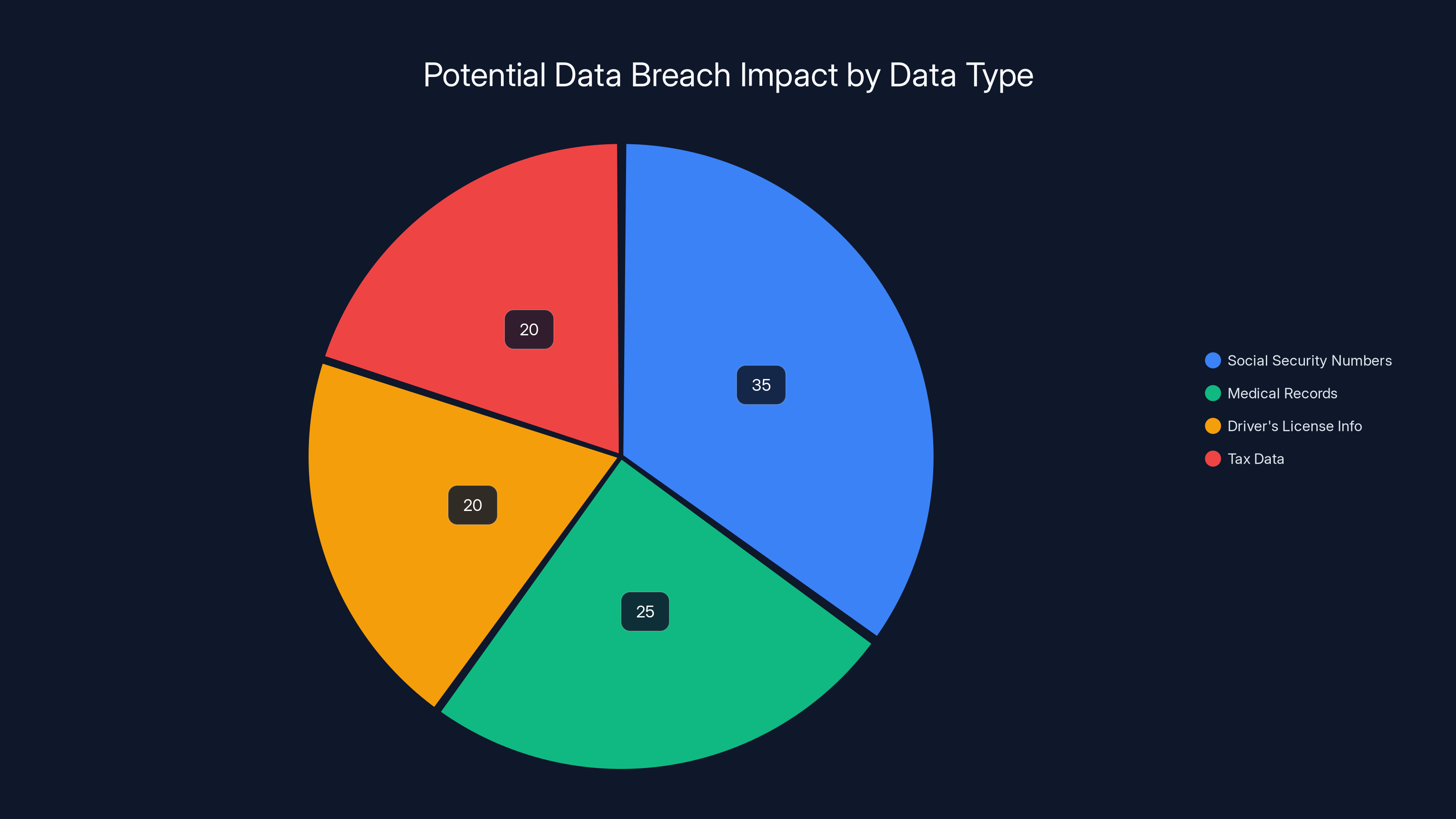
Estimated data shows that Social Security Numbers were most affected, comprising 35% of the breach impact, followed by medical records at 25%. Estimated data.
Legal Implications: What Laws Were Violated and What Happens Next
Let's catalog the specific federal laws that may have been violated:
Hatch Act violations: Using government position and resources to advance political goals. This is clear from the documents and the SSA's formal referral.
Computer Fraud and Abuse Act: Unauthorized access to government computer systems. The court order restricted access to certain databases. Accessing them anyway arguably violates this law.
Privacy Act violations: Unauthorized disclosure of personal information collected by federal agencies. Moving SSA records to external servers without proper authorization violates federal privacy protections.
Administrative Procedure Act violations: Acting without proper authorization or following established procedures. The data-sharing agreement wasn't signed through proper SSA channels.
Wire fraud: Using electronic communications to facilitate fraud. If the communications involved misrepresenting intent or authority, this could apply.
What are the potential consequences? Hatch Act violations typically result in removal from office. Computer Fraud and Abuse Act violations carry criminal penalties up to 10 years imprisonment for certain violations. Privacy Act violations can result in civil liability and criminal charges.
But the practical enforcement question is more complicated. Prosecuting government officials requires political will. It requires career prosecutors willing to take on politically sensitive cases. It requires not just investigation but indictment and conviction.
The Trump administration isn't likely to zealously prosecute members of its own efficiency initiative. So the question becomes: will Congress investigate? Will courts compel action? Will the Justice Department's official investigative processes produce accountability, or will they produce a findings that nothing really happened?
History suggests skepticism is warranted. Government employees involved in security breaches often face administrative discipline short of criminal prosecution. Some get fired. Some resign. Few face criminal charges unless their actions are egregiously obvious or politically convenient to prosecute.

The Court Order That Failed to Protect Anyone
Before diving into solutions, it's worth examining why the court order that was supposed to prevent this didn't work. A federal judge had issued a clear restriction: DOGE members couldn't access certain SSA databases. The order was specific. It was in writing. It had legal force.
And it was violated.
Why? Several possibilities:
First, there may have been inadequate technical controls. The court order may have been a policy decision, not a technical restriction. Meaning: SSA was supposed to block DOGE access through administrative procedure, not through systems-level controls. So DOGE members could still technically access the systems if they tried hard enough.
Second, there may have been inadequate monitoring. SSA may not have been checking database access logs to verify compliance with the court order. If nobody's actually monitoring who's accessing what, a policy restriction becomes essentially meaningless.
Third, there may have been insufficient consequences for violation. If the only consequence of violating a court order is that you get investigated eventually, the cost-benefit calculation changes. Especially if you believe your political allies will protect you from consequences.
This reveals a fundamental challenge in government oversight: you can issue orders and policies, but actually enforcing them requires vigilance, resources, and political support. When any of those are lacking, the restrictions become theater.

The timeline illustrates the progression of events from DOGE's creation to the scandal involving SSA data access. Estimated data based on narrative.
What Happens to the Advocacy Group? Accountability Questions
The court documents mention "the advocacy group" repeatedly but never name it. Why the anonymity? There are several possibilities:
The investigation may still be ongoing, and naming the group could compromise it. Federal prosecutors sometimes keep names confidential until they're ready to move forward with charges. Public identification could trigger destruction of evidence or allow the group to prepare legal defenses.
Alternatively, the Justice Department may be protecting the advocacy group. If they named it, it would become immediately apparent which organization had received government assistance. That organization would face public pressure and potentially legal consequences. By keeping it anonymous, the Department shields it from scrutiny.
But citizens have a right to know which political organizations are receiving government help. The public has a right to know if taxpayer resources are being used to support particular political narratives. Anonymity might be legally justified, but it's ethically problematic.
Assuming the advocacy group did receive SSA data or assistance, they presumably benefited significantly. They got government help analyzing voter rolls. They got access to data they might have been unable to obtain otherwise. They got credibility: DOGE, a government agency, was helping validate their claims.
What's their accountability? Will they face charges if the investigation proves they knowingly received stolen government data? Will they be required to delete all copies? Will there be sanctions?
The pattern in these cases is usually: the government employee faces discipline, while the private organization that benefited from the violation walks away free. That's not justice. That's misaligned incentives.

Administrative and Procedural Failures: How This Was Allowed to Happen
Beyond the individuals involved, this incident reveals systemic failures in how federal agencies manage data access and oversight.
Failure to implement technical controls: Access restrictions should be enforced at the system level, not the policy level. If a court order says someone can't access a database, the system shouldn't allow it, period. An audit log entry after the fact isn't a control. It's a detective measure. It catches violations after they've already happened.
Failure to monitor access: Even with policy-level restrictions, agencies should be reviewing access logs regularly to ensure compliance. Monthly or quarterly audits of database access by DOGE members would have caught this quickly. If SSA wasn't doing those audits, that's a failure.
Failure to require proper authorization: Data-sharing agreements involving government data should require approval from multiple levels of SSA leadership. A single embedded DOGE member shouldn't be able to unilaterally sign agreements committing government resources or data. The fact that this happened suggests authorization controls were inadequate.
Failure to separate duties: The people accessing the data shouldn't also be the people deciding who to share it with. There should be separation of duties built into the process. If DOGE members wanted to analyze data with external organizations, they should have had to go through SSA's official channels and involve career officials who have institutional incentives to follow rules.
Failure to establish clear policies: When DOGE members were embedded at SSA, was it clear what they could and couldn't do with data? Was it explicit that they couldn't sign agreements with external organizations? Was it clear that some databases were off-limits? If SSA didn't provide clear, written guidance, that's a failure of leadership.
Each of these failures, independently, would be concerning. Together, they suggest an agency that wasn't prepared for the challenge of embedding external officials with deep system access.

The Broader Context: Political Pressure and Government Data
This incident doesn't exist in a vacuum. It reflects broader tensions between efficiency initiatives and legal compliance, between political goals and institutional rules, between pressure from above and professional responsibility.
When a new administration comes in with an efficiency mandate, there's often pressure on agencies to produce results quickly. Prove you're more efficient. Reduce costs. Cut regulations. Speed up decision-making. These are reasonable efficiency goals in many contexts.
But not all inefficiencies are bad. Some are constitutional protections. Some are security measures. Some exist specifically to prevent the kind of abuse we're seeing here. When efficiency pressure overrides these protections, the result isn't a better government. It's a government that can more easily abuse citizen data.
DOGE members presumably believed they were advancing legitimate government goals. They were trying to find election fraud. They were responding to requests from what they may have perceived as legitimate oversight organizations. They may have believed the ends justified the means.
But that's precisely the reasoning that justifies every government overreach. Every authoritarian government has convinced itself that restricting rights, abusing power, and violating laws is justified by higher purposes. The constitutional protections that prevent this aren't inefficiency. They're democracy.
Solutions: How to Prevent This From Happening Again
Assuming Congress actually wants to prevent future incidents, what would that require?
Congressional oversight: Congress should investigate DOGE's data access across all federal agencies. Not just SSA. Where else has DOGE accessed restricted data? What other agreements have been signed? What other data has been moved to external systems? Congress has oversight authority and should exercise it.
Technical controls: Federal agencies should implement system-level access restrictions for anyone not employed by the agency. If a court orders that someone can't access certain databases, the system should enforce that restriction, not policy. This requires investment in security infrastructure, but it's essential.
Rotation policies: Embedded officials from external organizations should be rotated regularly. They shouldn't stay in positions of trust long enough to build relationships that override institutional rules. Longer tenure creates conflict of interest.
Separation of duties: Anyone with data access shouldn't also have authority to decide who that data is shared with. These decisions should require approval from multiple people, ideally career officials with institutional incentives to follow rules.
Regular audits: Agencies should conduct monthly audits of all database access by external officials, comparing access logs to official work purposes. Any unexplained access should trigger investigation.
Whistleblower protections: Federal employees who report violations should have meaningful protections against retaliation. Protections that exist only in theory while retaliation occurs in practice aren't actually protections.
Clear policies: When external officials are embedded in agencies, there should be written policies specifying exactly what they can and cannot do with government data. These policies should be more restrictive than normal employee policies, not less.

The Path Forward: Accountability and Restoration of Trust
For citizens, this incident is fundamentally about trust. Most people don't worry daily about their Social Security numbers. They assume the government is protecting that information. They assume federal employees are following rules. They assume courts' orders are enforced.
This incident undermines all three assumptions. If DOGE members can access Social Security data for political purposes, what stops them from doing it for other purposes? If courts' orders can be violated, are courts even functional? If institutional protections can be overridden, can we trust government with sensitive data?
Restoring trust requires accountability. It requires clear consequences for the DOGE members involved. It requires investigation of whether similar violations occurred elsewhere. It requires structural reforms that prevent future violations.
But it also requires honesty about what happened. No narratives about misunderstandings or technical errors. The documents are clear: DOGE members signed formal data-sharing agreements with political advocacy groups. They may have accessed restricted data to support those agreements. They may have uploaded hundreds of millions of Americans' records to vulnerable external servers. These weren't accidents.
Moving forward, federal agencies need to view data protection not as an efficiency obstacle but as a constitutional responsibility. Some slowness is worth the tradeoff for security and privacy. Some restrictions are worth the limitations for protection against abuse.
Democracy depends on government power being limited and checked. Data protection is one of those checks. When government officials violate those protections, democracy itself is undermined. That's not abstract principle. That's existential to American governance.
FAQ
What is the DOGE Social Security data scandal?
The scandal involves two members of the Trump administration's Department of Government Efficiency who allegedly violated a court order by accessing restricted Social Security Administration data and sharing it with a political advocacy group seeking to find evidence of election fraud. According to Justice Department documents, they signed a formal data-sharing agreement and potentially uploaded hundreds of millions of Americans' Social Security records to vulnerable external cloud servers without proper authorization.
How did DOGE members access Social Security data they weren't supposed to access?
While the exact technical method isn't fully detailed in court documents, DOGE members were embedded directly within the Social Security Administration as part of an efficiency initiative, which gave them system access. Despite a federal court order restricting their access to databases containing Social Security numbers and sensitive personal information, they apparently accessed those systems anyway and signed formal data-sharing agreements with external organizations, suggesting the restriction was violated deliberately rather than accidentally.
What laws were violated in this incident?
Multiple federal laws were potentially violated, including the Hatch Act (prohibiting federal employees from using their positions for political purposes), the Computer Fraud and Abuse Act (for unauthorized access to government systems), the Privacy Act (for unauthorized disclosure of personal information), and potentially wire fraud laws. The Social Security Administration formally referred the two DOGE members for investigation of Hatch Act violations, indicating these potential violations were serious enough to warrant official action.
Why does it matter that the data went to a political advocacy group?
It matters because it demonstrates potential weaponization of government data and systems for partisan purposes. Federal law is structured around the principle that government power should serve all citizens equally, not advance particular political agendas. When government employees use their access to federal data to support specific political narratives or organizations, that's a fundamental violation of the constitutional separation between government and partisan politics, which is precisely what the Hatch Act is designed to prevent.
What happened to the Americans whose data was potentially compromised?
Court documents don't detail specific notification or remediation efforts. Citizens whose Social Security numbers were potentially accessed or uploaded to external servers may not even know their data was compromised, depending on what official notifications were issued. The vulnerability of the external server suggests their information could have been accessed by malicious actors, though no evidence of further compromise has been publicly disclosed.
Will the DOGE members face criminal charges?
The documents show they were referred for Hatch Act investigation by the Social Security Administration, but whether they'll face criminal charges remains unclear. Hatch Act violations typically result in removal from office, but criminal prosecution depends on whether the Justice Department pursues charges. Given that these individuals worked for the Trump administration, which appointed the officials overseeing the investigation, there's uncertainty about whether enforcement will be rigorous or whether political considerations will influence the outcome.
What security protections failed to prevent this incident?
Multiple layers of protection failed. The federal court order restricting access wasn't enforced through technical controls, only policy. The Social Security Administration apparently wasn't monitoring database access logs to catch unauthorized access. Data-sharing agreements weren't required to go through official SSA authorization channels. There were no audit trails for who was accessing what data. When all of these safeguards fail simultaneously, it suggests the agency wasn't prepared for the challenge of embedding external officials with deep system access.
Could this happen at other federal agencies?
Yes, potentially. DOGE has embedded members across multiple federal agencies beyond the SSA, including agencies with other sensitive databases like the IRS (tax data), VA (military medical records), and others. The pattern suggests that if DOGE felt justified in violating court orders and federal law at SSA, similar incidents could occur elsewhere. Congressional oversight of DOGE's data access across all agencies would be necessary to determine if similar violations have already occurred.
What does this incident reveal about federal security practices?
It reveals significant gaps in how federal agencies handle sensitive data when external officials with deep system access are embedded within them. Agencies appear to rely heavily on policy-level controls rather than technical controls, trust institutional behavior rather than verify it through audit trails, and don't always maintain clear separation of duties between data access and data-sharing authorization. This suggests federal data security practices lag behind private sector standards and need substantial reform.
What changes would prevent this from happening again?
Effective prevention would require technical controls that enforce access restrictions at the system level rather than policy level, regular audits of all database access by external officials, meaningful separation of duties for data-sharing decisions, rotation of external officials to prevent relationship-based override of rules, clear written policies specifying what embedded officials can and cannot do with government data, congressional oversight of DOGE's data access across all agencies, and meaningful whistleblower protections for federal employees who report violations.

Key Takeaways
- DOGE members allegedly accessed restricted SSA databases containing Social Security numbers and other sensitive data, violating a federal court order
- The data was potentially shared with political advocacy groups seeking to find election fraud evidence, triggering Hatch Act investigations
- Hundreds of millions of Social Security records were uploaded to vulnerable external cloud servers without proper federal security controls
- Multiple federal laws were violated including Hatch Act, Computer Fraud and Abuse Act, and Privacy Act, with potential criminal penalties
- Systemic security failures including inadequate technical controls, insufficient monitoring, and poor authorization procedures enabled the violations
![DOGE's Social Security Data Scandal Explained [2025]](https://tryrunable.com/blog/doge-s-social-security-data-scandal-explained-2025/image-1-1768943298241.jpg)



