Government Spyware Targeted You? Complete Action Plan [2025]
Introduction: The Reality of Modern Surveillance
Jay Gibson's morning started like any other Tuesday until an ominous notification lit up his iPhone screen: "Apple detected a targeted mercenary spyware attack against your iPhone." The irony was brutal. Gibson had spent years working at companies developing exactly the kind of surveillance tools now targeting him. But reading those words on his own device triggered an immediate panic response.
He called his father. He powered down the phone. He went out and bought a new one. "I was panicking," he later admitted. "It was a mess. It was a huge mess."
Gibson isn't alone. And that's the uncomfortable truth about modern digital life: government-sponsored spyware isn't theoretical anymore. It's real. It's targeting people right now. And the notifications are getting more common.
Apple, Google, WhatsApp, and other major tech companies now regularly warn users when they detect government-sponsored hacking attempts. These aren't vague security alerts or generic phishing warnings. These are highly specific notifications indicating that nation-state actors or government-backed spyware companies have attempted to compromise your device.
The problem? These companies alert you, then they step back. They don't investigate further. They don't hold your hand. They point you toward help and disappear. That leaves millions of people standing in front of their phones thinking: "Now what the hell do I do?"
This guide answers that question. What actually happens after you get one of these notifications? What's the real risk? Who can actually help you? And what are your actual options, broken down into steps you can take today.
Here's the thing: these notifications are serious. But they're not a death sentence. There are concrete steps you can take, specific organizations ready to help, and technical measures that genuinely work. The key is knowing what those steps are and taking them in the right order.
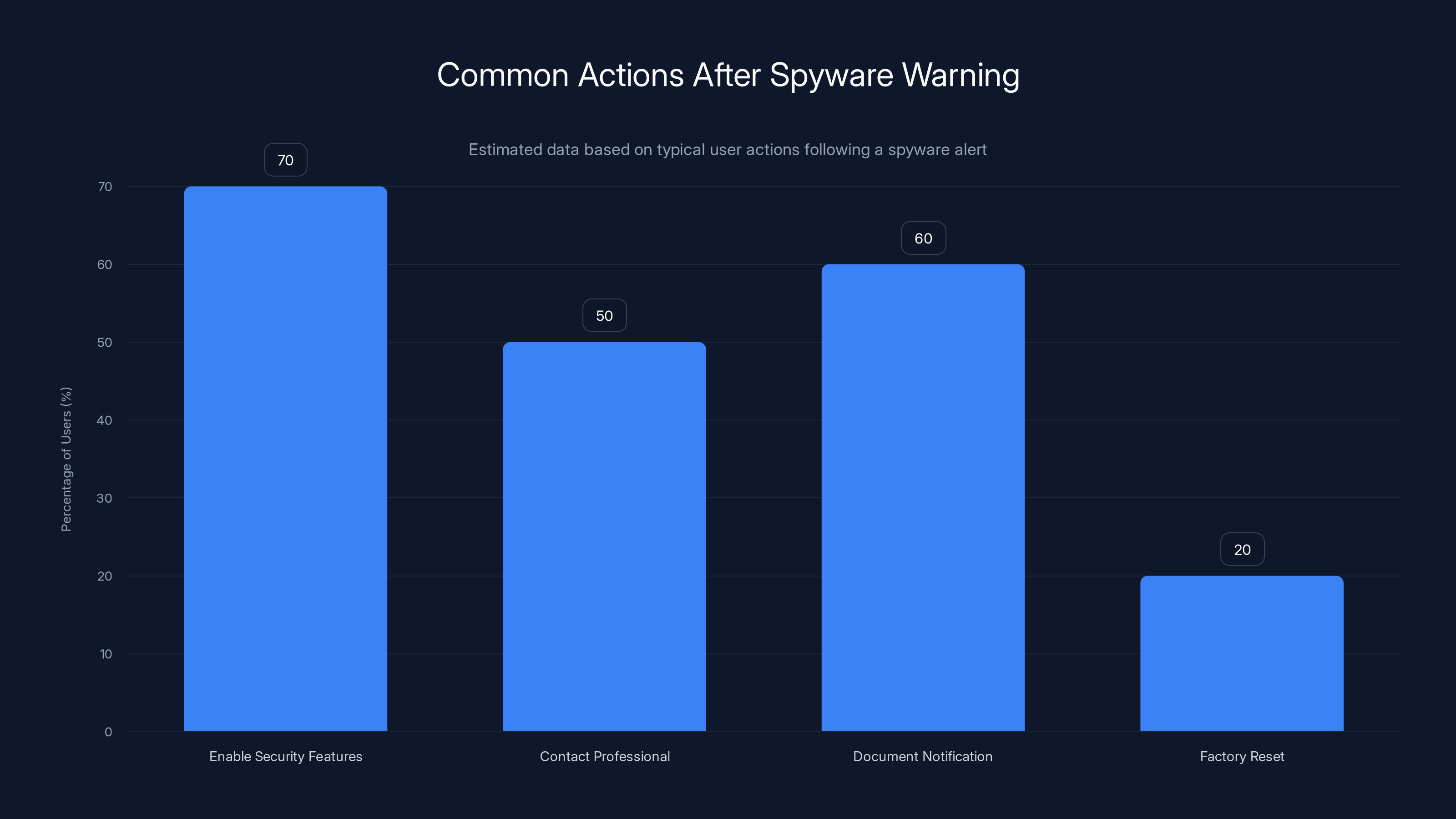
Most users enable security features and document notifications after a spyware warning, while fewer immediately contact professionals or perform a factory reset. (Estimated data)
TL; DR
- Take it seriously immediately: Tech companies only send these warnings when they have strong evidence. A notification means someone tried to hack you, though the attack may have failed.
- Activate security features now: Turn on Apple Lockdown Mode, Google Advanced Protection, or Android equivalents within hours of receiving the warning.
- Preserve your device: Don't wipe it yet. First, use forensic tools like Mobile Verification Toolkit (MVT) or contact experts who can extract evidence of the attack.
- Get professional help if targeted: Journalists, activists, and at-risk groups can contact Access Now, Amnesty International, or Citizen Lab at no cost.
- Understand the difference: Apple/WhatsApp warnings mean attempted attacks. Google warnings mean Google blocked the attack. Both require action.
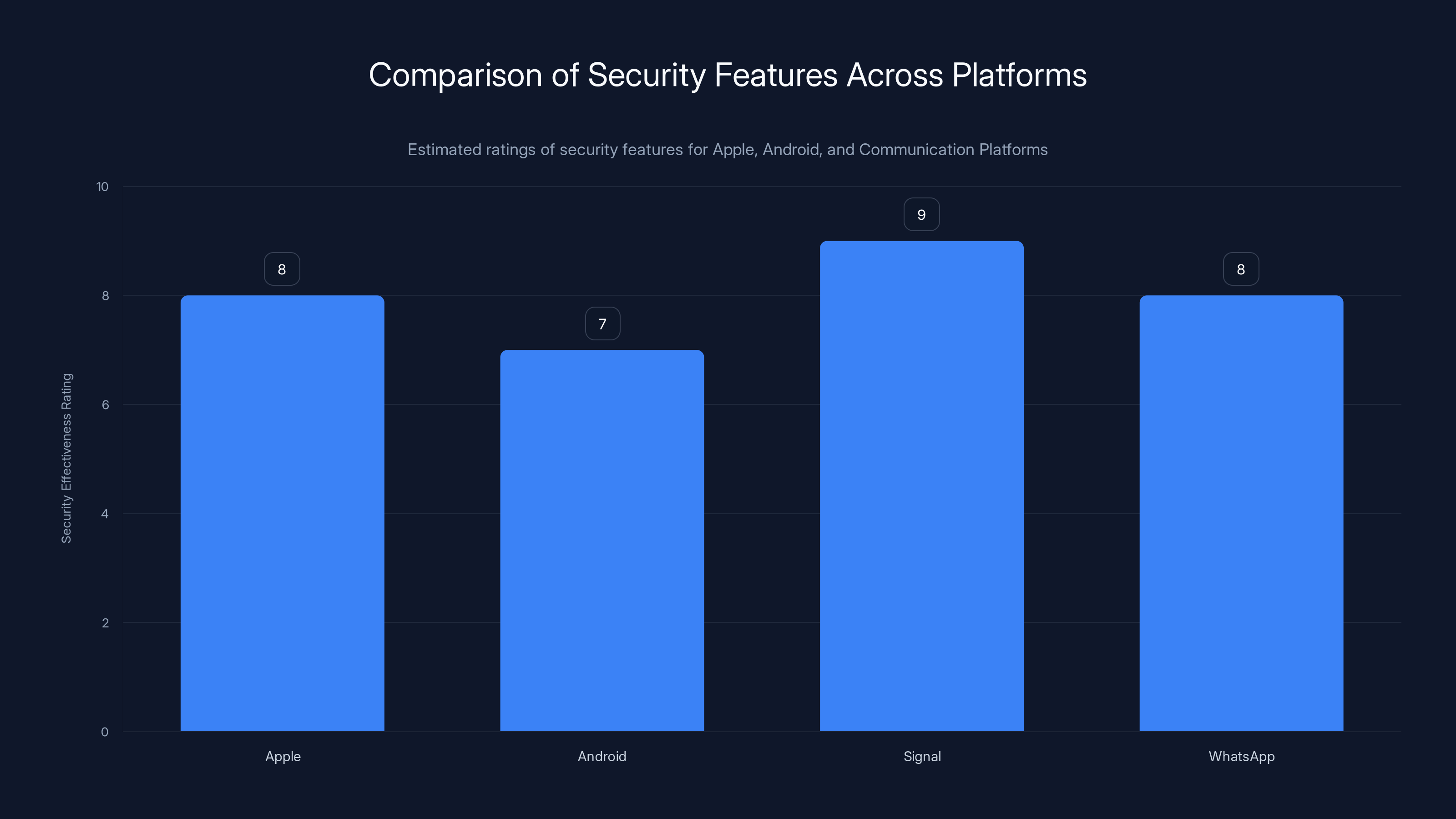
Apple's closed ecosystem provides strong security, but Android's openness presents challenges. Signal offers the highest security for communication. (Estimated data)
Understanding Spyware Threat Notifications: What Companies Actually Know
When your phone buzzes with a spyware warning from Apple or Google, that notification is backed by massive surveillance infrastructure. These companies aren't guessing. They're not being cautious. They're reporting findings based on telemetry data collected from millions of devices, security research teams that have been studying government spyware for years, and sophisticated detection systems that monitor for specific attack patterns.
Tech companies have firewall visibility across billions of connections. They can see when devices connect to known command-and-control servers used by spyware operators. They can spot network traffic patterns that match known government hacking tools. They can identify when someone attempts to install malicious code on your device during a security update.
When Apple sends you a threat notification, the company has detected network activity or attempted code execution that matches patterns from known government spyware. The company tracks these patterns against intelligence from its security team, collaboration with other tech companies, and forensic analysis of captured samples. The same applies to Google and WhatsApp.
Here's what matters: if you got the notification, someone tried to hack you. That's not paranoia. That's not a false positive. That's an actual attack attempt. The notification might mean the attack succeeded, it might mean it failed, but the attempt definitely happened.
This is fundamentally different from generic security warnings. You're not being warned because you might visit a phishing site. You're being warned because government-backed hackers specifically targeted your device. They used spyware software made by companies like NSO Group, Intellexa, Paragon Solutions, or other government surveillance contractors. They had your phone number or were physically near your device. They launched an active attack.
Why These Warnings Matter More Than You Think
The notifications matter because they represent a shift in how tech companies approach security. For years, tech companies quietly detected and blocked attacks without telling users. Apple in particular kept Lockdown Mode secret until certain journalists suddenly had their accounts breached by zero-day exploits.
Now companies realize silence doesn't work. Attackers will keep trying different methods. Users need to know they're under attack so they can change behavior, enable additional security features, and take precautions. A user who knows they're targeted will enable Lockdown Mode, use a security key instead of passwords, and be paranoid about suspicious links. A user who doesn't know will continue normal behavior and might accidentally give attackers a second chance.
Tech companies also know something else: people targeted by government spyware are usually people the government has a specific interest in. That means they're often journalists, activists, dissidents, human rights workers, or political opposition. These are people whose safety, not just privacy, depends on actual security.

Different Warnings, Different Meanings: Apple vs. Google vs. WhatsApp
Not all spyware warnings are identical. The notification you received matters because it indicates different levels of attack success and requires different responses.
Apple's Threat Notifications: Attempted Attacks
When Apple detects government spyware targeting your iPhone, the company sends a notification reading something like "Apple detected a targeted mercenary spyware attack against your iPhone." The exact wording matters because Apple uses the word "attempted." This means Apple detected someone trying to compromise your device, but it's not yet clear if the attack succeeded.
Apple's detection systems caught someone sending malicious payloads to your device, attempting to install government spyware, or exploiting known vulnerabilities. The company blocked what it could, but Apple can't be 100 percent certain the attack didn't partially succeed somewhere in the chain.
The Apple response should be immediate: turn on Lockdown Mode. This feature disables certain functionality that spyware commonly exploits. It restricts web browsing, limits JavaScript, disables certain attachment types, and reduces the attack surface significantly. Apple has emphasized repeatedly that Lockdown Mode makes you a much harder target.
Google's Threat Warnings: Attacks Google Stopped
Google's notifications come with a different implication. When Google sends you a government hacking warning, it means Google detected the attack and blocked it. Google's Safe Browsing systems prevented the link from working. Gmail's security detected and blocked the malicious attachment. Google Play Protect stopped the malicious app from installing.
Google's message means: the attack failed before reaching your device significantly. But Google wants you to know about it because the attacker will keep trying. And you should assume the attacker has your phone number, email address, or device identifier. They'll try different angles.
Google's recommended response includes turning on Advanced Protection Program, which requires security keys instead of passwords and adds additional security layers. Google also recommends ensuring two-factor authentication is enabled with the strongest possible secondary factor.
WhatsApp's Spyware Warnings: Exploit Attempts
WhatsApp notifications are more specific: they indicate WhatsApp's systems detected an attempt to install Pegasus spyware via WhatsApp's calling functionality. Pegasus uses zero-day exploits in WhatsApp's audio and video calling to deliver spyware payload. WhatsApp can detect when someone sends malicious calls to your number and tells you someone tried.
WhatsApp's detection works differently than Apple's or Google's. WhatsApp logs calls, analyzes them, and identifies malicious calls based on patterns and payload signatures. When WhatsApp detects this, the notification means someone specifically targeted you through the app.
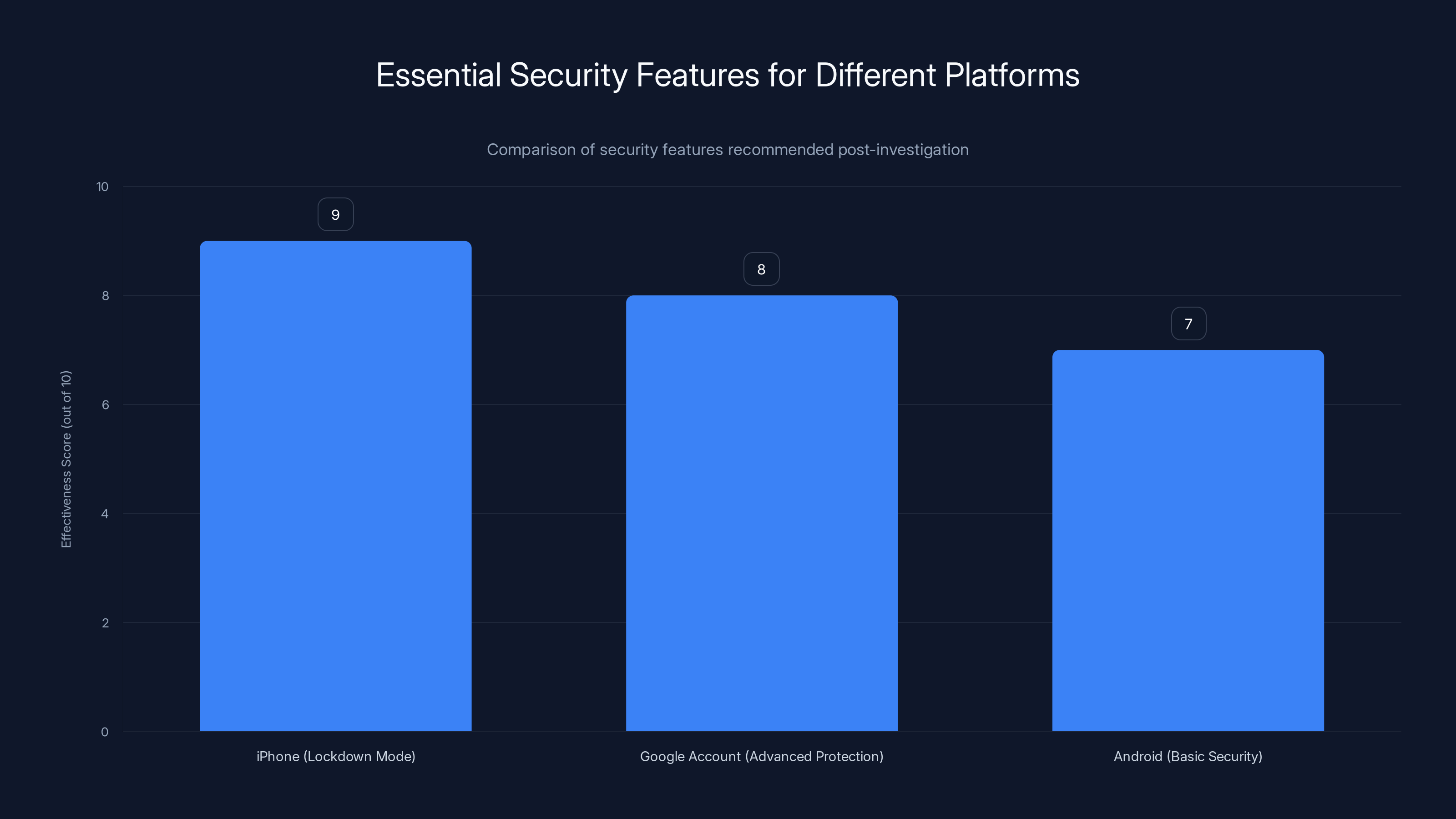
Lockdown Mode for iPhone users scores highest in effectiveness, followed by Google's Advanced Protection and basic Android security settings. Estimated data based on feature descriptions.
The Spyware Tools Targeting You: NSO Pegasus, Paragon Graphite, and Others
Understanding what's actually targeting you helps with defensive decisions. Government spyware isn't generic malware. These are sophisticated tools built by companies with deep technical expertise, unlimited budgets, and explicit support from governments.
NSO Group's Pegasus: The Industry Standard
Pegasus is probably the most famous government spyware, partly due to the Pegasus Project investigation that revealed extensive deployment against journalists, activists, and politicians worldwide. NSO Group sells Pegasus to governments for hundreds of thousands of dollars per installation.
Pegasus works by exploiting zero-day vulnerabilities in iOS and Android. NSO researchers find previously unknown security flaws, develop exploits, and incorporate them into Pegasus. The spyware then installs silently, giving attackers complete access to texts, calls, photos, location data, and everything else on the device.
Pegasus is particularly sophisticated because it can operate without the user noticing anything. The phone doesn't slow down noticeably. No suspicious apps appear in the app drawer. No weird notifications appear. The user has no indication their device is completely compromised.
The spyware can be deployed via text message links, WhatsApp video calls, iMessage attachments, or other vectors. Victims often have no idea when infection occurred.
Paragon Solutions' Graphite: The Newer Threat
Paragon Solutions is a newer player in the government spyware market, but Graphite is comparable to Pegasus in sophistication. Graphite targets both iOS and Android and uses similar zero-day exploits to gain complete device control.
What makes Graphite interesting is its origin and distribution. Paragon Solutions is a for-profit company but operates with closer ties to government agencies than NSO does. Some Graphite deployments are known to have been conducted by government agencies directly rather than purchased through commercial channels.
Graphite's capabilities are similar to Pegasus: complete device access, silent installation, remote command execution, and data exfiltration. The distinction is mainly in who's deploying it and how it's acquired.
Intellexa's Predator and Other Emerging Tools
Intellexa is a consortium of companies offering spyware products under brands like Predator and others. These tools operate similarly to Pegasus and Graphite but with some variations in deployment methods and capabilities.
The landscape of government spyware is constantly evolving. New companies emerge, new tools are developed, and new exploits are discovered. The common thread is that all these tools require significant technical sophistication and typically exploit previously unknown security flaws to work effectively.
What You Need to Know Right Now: Immediate Context
If you received a spyware notification in the last 48 hours, understand these facts clearly:
First, you were targeted. Someone at some government agency or government contractor decided your device was worth attempting to hack. That someone had resources, access to sophisticated tools, and motivation. This isn't random. This isn't a mass phishing campaign. You were individually selected.
Second, the attack may or may not have succeeded. The notification means an attempt occurred. It doesn't necessarily mean your device is currently compromised with Pegasus or similar spyware. Apple, Google, and WhatsApp have security measures that often block these attacks. But "often" isn't "always."
Third, you don't know for certain who targeted you or why. It could be your own government. It could be a government you've never interacted with. It could be because of your profession (journalist), activism, political beliefs, religious affiliation, or associations. Or it could be a case of mistaken identity or wrong phone number.
Fourth, panicking is normal but unhelpful. Jay Gibson panicked. Most people would. But panicking leads to bad decisions like immediately factory resetting your phone before forensic analysis, which destroys evidence of the attack and makes it impossible for experts to help you.

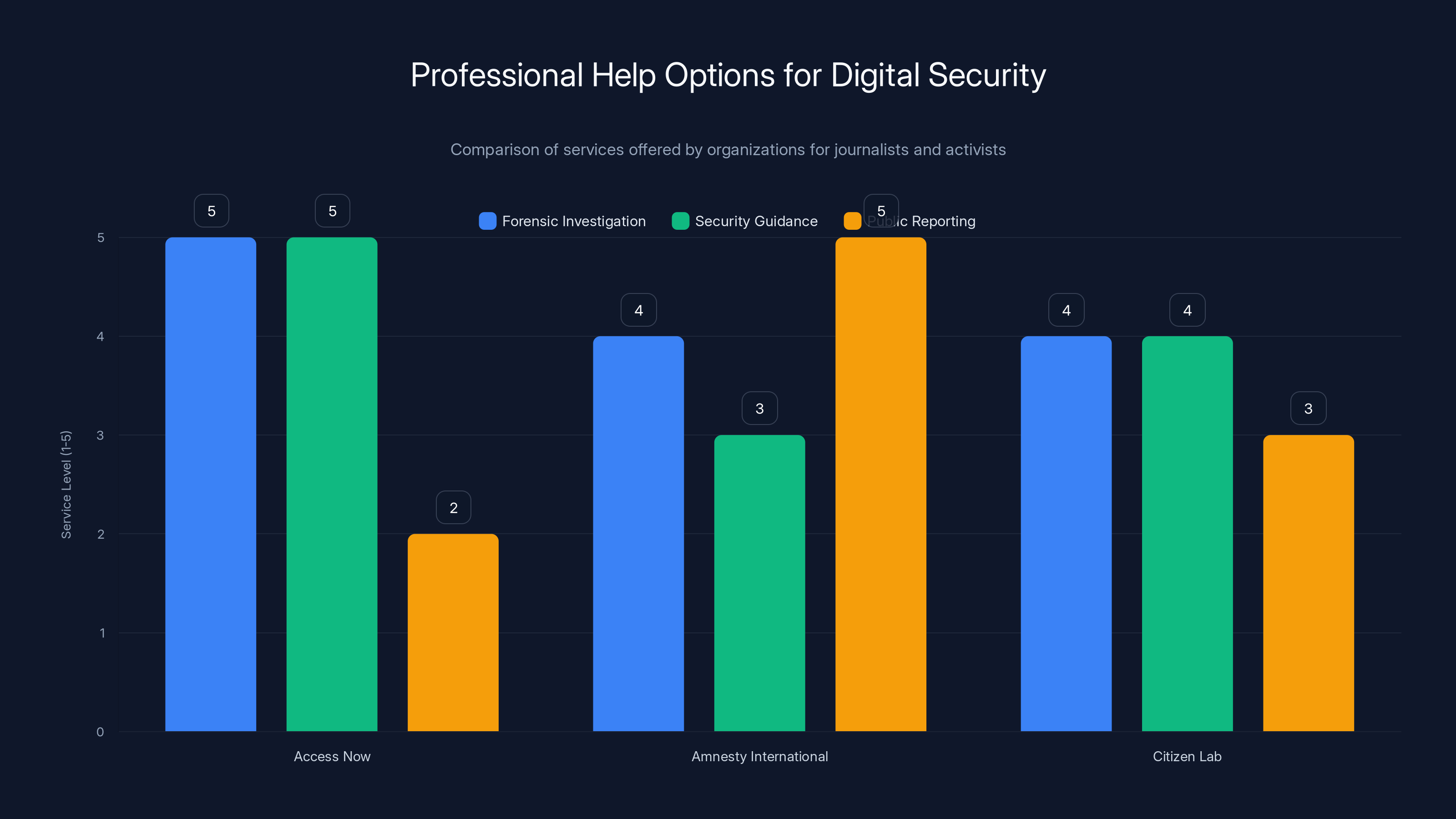
Access Now offers the most comprehensive forensic investigation and security guidance, while Amnesty International excels in public reporting. Estimated data based on service descriptions.
Step 1: Don't Panic, But Act Fast
The first hours after receiving a spyware warning are critical. Not because attackers are actively stealing data from your device in real time (though they might be), but because your immediate actions determine what help is available to you later.
Why the First 24 Hours Matter
If your device has been successfully compromised with Pegasus or similar spyware, that spyware is likely still installed and active. The spyware can be remotely uninstalled by the attackers if they realize you're seeking help or taking defensive action. This is actually good news in a way: it means the spyware is still detectable.
Forensic investigators need to examine your device while the spyware is still installed. They can extract the spyware, analyze it, identify which specific exploits were used, and sometimes even determine which government agency deployed it. But if you factory reset your device or power it off without proper forensic preparation, you destroy the evidence.
This is why experts' first advice is always: keep the device powered on, don't restart it unnecessarily, don't install new apps, don't change passwords, don't factory reset. Keep the device exactly as it is until forensic experts can examine it.
What To Do in the First Hour
-
Read the notification carefully. Write down exactly what it says. Screenshot it if possible. Different notifications mean different things, and you'll need to reference the exact wording when talking to security experts.
-
Don't immediately change your password or disable your account. I know this seems backward, but if your device is compromised, the attacker likely already has access to these credentials. Changing them might alert the attacker that you've been warned and cause them to remove the spyware before forensic examination.
-
Do enable security features. For Apple users, immediately turn on Lockdown Mode if you haven't already. For Google account users, enable Advanced Protection Program. For Android users, enable strict security settings. These steps won't help with already-installed spyware, but they prevent re-infection and additional attacks.
-
Do document your environment. Note what you were doing when you received the notification. Were you traveling? Were you near a particular physical location? Had you recently clicked a suspicious link? Had you been contacted by someone with unusual requests? This context helps investigators.
-
Don't tell everyone. If you publicly announce you received a spyware warning, attackers know you've been warned and will remove surveillance tools. If you suspect you're targeted for political reasons, alerting the targeting government defeats the purpose of investigation. Share the information only with people who absolutely need to know and who you trust completely.
Step 2: Assess Your Risk Level Honestly
Not everyone targeted by government spyware needs the same level of response. A businessman who might have been targeted due to corporate espionage needs different help than a journalist targeted by a repressive regime. Understanding your actual risk determines what actions to prioritize.
Who's Most Likely to Be Targeted
Governments and government contractors target specific categories of people because those targets have value to the government or are perceived as threats.
Journalists covering sensitive topics are frequently targeted. Investigative journalists especially, and those covering government corruption, military activities, or classified programs. Pegasus was notoriously used against journalists by multiple governments.
Human rights activists and defenders are common targets. Organizations like Amnesty International maintain teams specifically to investigate spyware attacks against human rights workers because these attacks are so common.
Political opposition figures in authoritarian countries are regularly targeted. Monitoring opposition figures and their communications is a standard tool of authoritarian governments.
Lawyers and legal professionals involved in sensitive cases sometimes become targets, particularly those defending dissidents or investigating government crimes.
Academics researching sensitive topics can be targeted, particularly those researching government surveillance, military technology, or sensitive geopolitical issues.
Minority group members and LGBTQ+ individuals in countries with oppressive policies may be targeted by governments seeking to identify and monitor vulnerable populations.
Business executives can be targeted for corporate espionage, intellectual property theft, or personal blackmail.
Anyone with critical information that governments want to access might be targeted if that government has resources and motivation.
Assessing Your Personal Risk
Ask yourself honestly: why might a government be interested in me? This isn't paranoia—it's realistic threat assessment. Do you work in journalism? Are you politically active? Are you in a minority or marginalized group? Do you work for a sensitive organization? Have you been contacted with unusual requests for information? Are you traveling in countries with poor human rights records? Do you know classified information?
If the answer to most of these is "no," your risk level is probably moderate. Someone attempted to target you, but it might be a case of mistaken identity, a test of new exploits, or targeting based on incomplete information.
If the answer to several of these is "yes," your risk level is higher. You've been specifically targeted by well-resourced attackers who likely have accurate information about you.
Your risk level determines whether you need forensic investigation, how carefully you need to operate going forward, and whether your situation warrants professional help from security organizations.

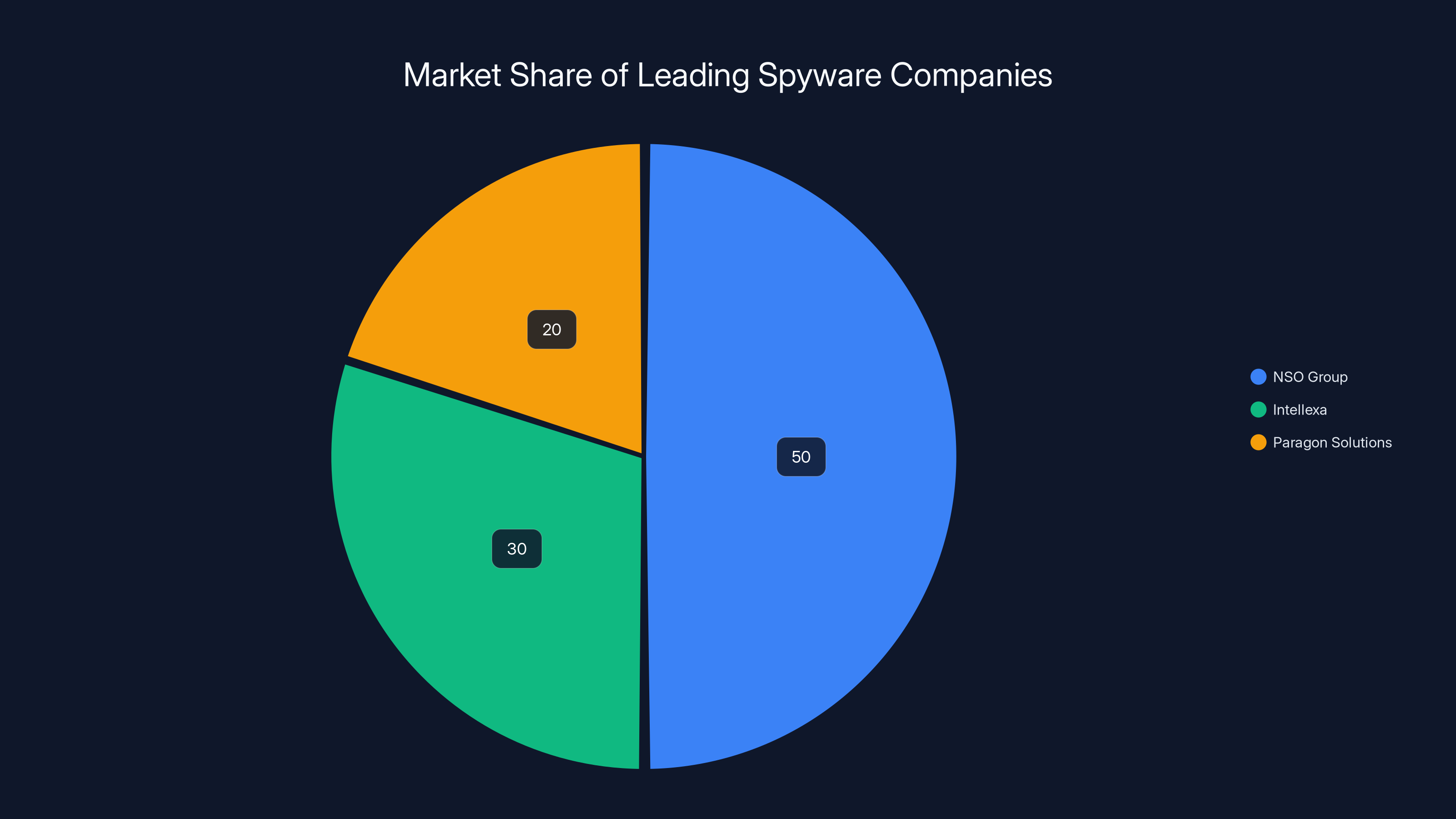
NSO Group holds the largest market share among major spyware companies, with Intellexa and Paragon Solutions also having significant influence. (Estimated data)
Step 3: Preserve Your Device for Forensic Analysis
If you think you might seek forensic investigation (and you probably should), you need to preserve your device in a condition that allows investigation. This means resisting the normal instinct to factory reset and start fresh.
Why Not to Factory Reset (Yet)
Factory resetting your device completely wipes it, including any traces of spyware installation. Forensic investigators need those traces. They need to examine the spyware, extract code samples, analyze how it was installed, and identify what exploits were used. Factory resetting destroys all of this.
A factory reset might make you feel safer because the spyware is definitely gone. But it also eliminates any evidence that could help investigators understand who targeted you and why. It eliminates any hope of formally documenting the attack for legal or journalistic purposes.
Instead of factory resetting, preserve the device as is. Keep it charged. Don't install new apps. Don't restart it unless necessary. Don't use it normally. Think of it as a crime scene that shouldn't be disturbed until experts examine it.
Device Preservation Best Practices
If you received a spyware warning and believe your device might be compromised:
-
Keep the device powered on. Leaving it on allows forensic tools to access the device's memory and file system.
-
Don't install new apps. New apps might interfere with forensic analysis or could themselves be compromised.
-
Don't update the operating system. Updates might overwrite or delete spyware traces.
-
Don't use cloud services actively. Don't sync new files to iCloud or Google Drive where they might be compromised or where you might overwrite evidence.
-
Minimize network activity. Don't install security software that might quarantine and remove spyware before forensic analysis.
-
Keep the device physically secure. If your device can be physically accessed, attackers might be able to remove spyware or install additional tools. Keep it with you or in a secure location.
-
Document the date and time of the notification. Write down exactly when you received the warning. This creates a timeline for investigators.
-
Isolate the device from sensitive information. If your device is compromised, assume any actions taken on it are visible to attackers. Don't access financial accounts, sensitive work information, or other critical systems from this device.

Step 4: Run Forensic Tools (If You're Technical)
If you have technical expertise and want to investigate your device yourself before contacting professionals, tools exist that can help identify spyware. The most commonly recommended tool is the Mobile Verification Toolkit (MVT).
Mobile Verification Toolkit (MVT): Self-Directed Investigation
MVT is an open-source forensic framework originally developed by Amnesty International to investigate spyware. MVT examines iOS and Android devices for traces of known spyware, analyzing system artifacts, network connections, and installed applications.
Using MVT requires technical knowledge. You need to extract forensic data from your device, run MVT against that data, and interpret the results. For iOS devices, you need to extract a full file system backup. For Android, you need to extract various system artifacts.
If MVT detects suspicious artifacts or known spyware indicators, that's significant information to bring to professional investigators. If MVT finds nothing, that doesn't definitively prove you're not compromised—advanced spyware can hide from standard detection tools—but it's useful data.
When MVT Is Useful and When It Isn't
MVT works best if the spyware infection occurred relatively recently and isn't actively hiding from detection. MVT can identify Pegasus in many cases because Pegasus leaves detectable artifacts. But sophisticated attackers can remove evidence before you run forensic tools, and new spyware might not have known signatures that MVT can identify.
Running MVT yourself is valuable if you're comfortable with technical tools and want baseline information before contacting professionals. But MVT isn't a replacement for professional forensic investigation. Professional investigators have access to more sophisticated tools, can interpret results with deeper expertise, and can provide legal documentation of findings.
If you run MVT and it shows nothing suspicious, you can feel somewhat reassured. If it shows suspicious artifacts, you should contact professional investigators immediately.
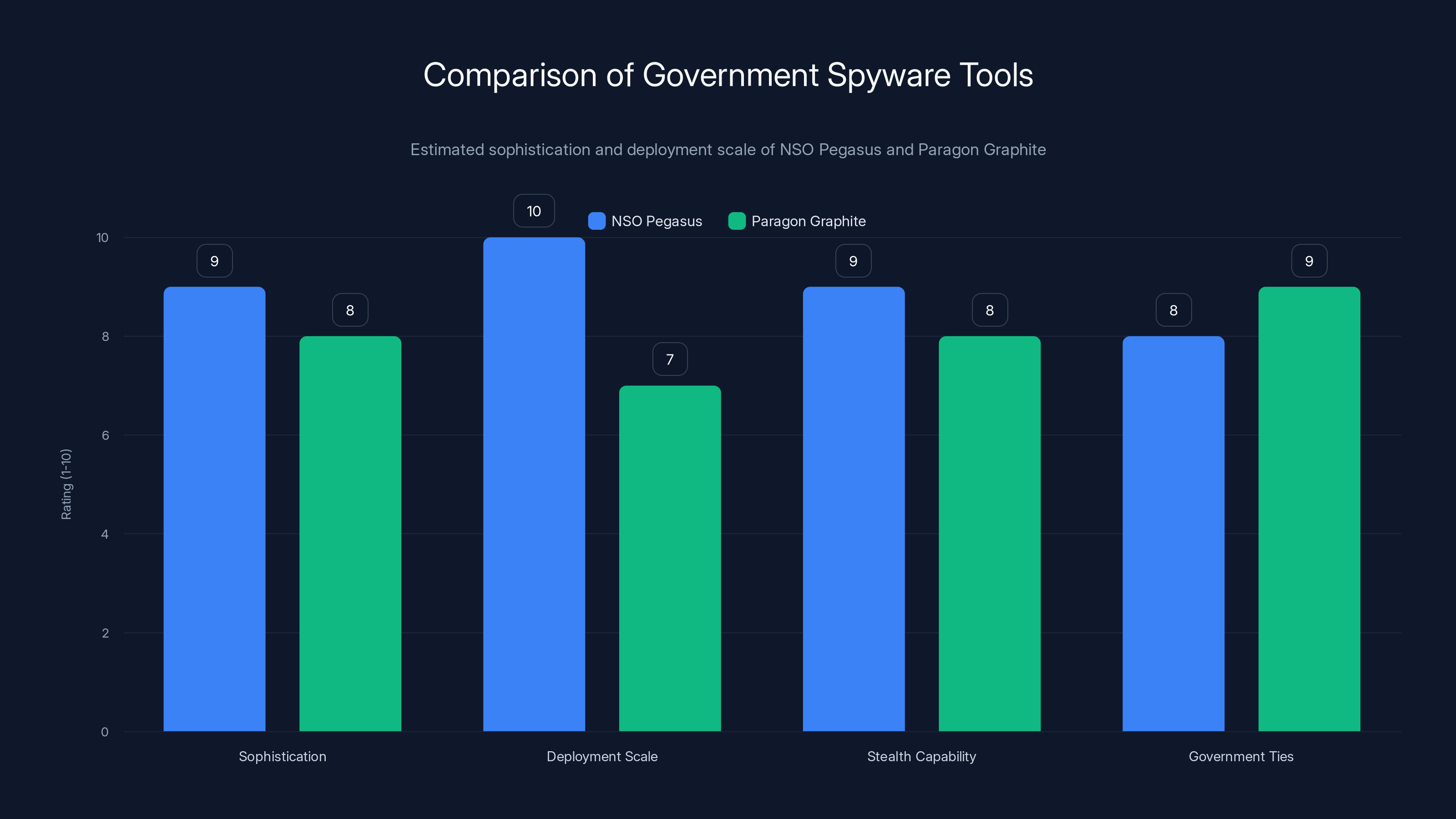
NSO Pegasus is slightly more deployed and sophisticated, while Paragon Graphite has stronger government ties. Estimated data based on available insights.
Step 5: Understand Your Options for Professional Help
After preserving your device and potentially running basic forensic tools, you have options for professional assistance. But those options vary dramatically depending on who you are.
For Journalists, Activists, and At-Risk Groups
If you're a journalist, human rights activist, dissident, or someone at risk of political persecution, multiple organizations offer free or low-cost forensic investigation and security help.
Access Now's Digital Security Helpline provides 24/7 global support for victims of digital attacks. Their team includes forensic investigators who specialize in spyware cases. Access Now focuses on civil society members, including journalists, activists, and human rights defenders. You can reach them through their website, and they'll help coordinate forensic investigation, provide security guidance, and connect you with other resources.
Access Now's approach is fundamentally pro-bono. They don't charge for investigation because they recognize that the people most vulnerable to spyware attacks often can't afford private security services.
Amnesty International's Security Lab investigates spyware abuses, particularly against human rights defenders. Amnesty has conducted forensic investigations that have exposed government spyware campaigns and documented abuses. If you're involved in human rights work, Amnesty's team can provide investigation and support.
Amnesty's investigations sometimes result in public reports documenting spyware campaigns. This means contacting Amnesty involves accepting some level of public exposure about your case (though Amnesty will protect your identity if requested). But it also means professional forensic investigation and potential public documentation of government abuses.
The Citizen Lab at the University of Toronto is a digital rights research group that investigates spyware and surveillance. Citizen Lab has extensively documented Pegasus and other spyware campaigns globally. If you're a journalist or researcher who's been targeted, Citizen Lab may investigate your case, particularly if your case reveals patterns about broader spyware campaigns.
Citizen Lab's investigations are academic and research-oriented. They won't provide the same type of immediate support as Access Now, but their research has exposed major government spyware campaigns and contributed to accountability efforts.
Reporters Without Borders Digital Security Lab specifically serves journalists and provides investigation of suspected hacking or surveillance. If you're a journalist who received a spyware warning, RWB can help coordinate investigation and provide security guidance.
For Business Executives and Politicians
If you're a business executive, politician, or someone outside the civil society sector, your options are more limited. You likely don't qualify for free services from organizations like Access Now because those organizations prioritize civil society members with fewer resources.
But professional help still exists, mostly through private security companies.
iVerify offers a smartphone security app that monitors for threats and provides rapid forensic investigation. iVerify offers a basic monitoring app available to anyone, plus an optional forensic investigation service. The app identifies suspicious device behavior, and if you request forensic investigation, iVerify's team can examine your device, extract spyware, and provide a detailed report.
iVerify's forensic investigation isn't free—it costs thousands of dollars—but it's substantially less expensive than traditional cybersecurity consultants and provides focused expertise on spyware.
Lookout Mobile Security analyzes government spyware and offers investigation services for organizations concerned about advanced threats. Lookout has analyzed Pegasus and other spyware extensively and can investigate suspected infections in your devices.
Safety Sync Group is a newer firm founded by Matt Mitchell, a well-regarded security expert who's spent years helping journalists and activists protect against surveillance. Safety Sync offers forensic investigation and security consulting focused specifically on government spyware threats.
Hexordia is founded by Jessica Hyde, a forensic investigator with extensive experience investigating government hacking. Hexordia offers forensic investigation and incident response for suspected spyware infections.
These private firms charge significantly more than free services, but they offer professional forensic investigation backed by expertise and legal documentation of findings.
For Everyone Else
If you're not a journalist, activist, executive, or politician, you might feel overlooked. Most specialized resources focus on these categories because they represent the most common targets.
But you still have options. Your company's security team (if you work for a large organization) can investigate your device or connect you with forensic experts. Your country's law enforcement, if it has cybercrime investigators, might investigate spyware targeting. Your telecommunications provider sometimes has security teams that can help.
You can also contact the organizations mentioned above and explain your situation. While they prioritize certain categories, they may still help, particularly if they have capacity.

The Complete Defense Stack: What to Do After Professional Investigation
Assume you've gone through forensic investigation and either confirmed or ruled out active spyware infection. The next step is preventing future attacks and making yourself a harder target going forward.
Activate Security Features: The Non-Negotiable Steps
After receiving a spyware warning, security experts unanimously recommend enabling specific features designed to prevent spyware attacks.
For iPhone users, Apple's Lockdown Mode is essential. Lockdown Mode restricts certain functionality that spyware commonly exploits. It limits JavaScript in web pages, disables certain attachment types, restricts font rendering, and reduces the attack surface. Apple claims it has never seen a successful Pegasus attack against a user with Lockdown Mode enabled.
Lockdown Mode does restrict functionality. Some websites display improperly. Some features don't work as expected. But for anyone targeted by government spyware, this trade-off is worthwhile.
For Google account users, Advanced Protection Program adds required security keys, restricts third-party app access, and enables additional verification. This prevents attackers from compromising your Google account even if they compromise your device, because they'd need physical possession of your security key to log in.
For Android users, security options are more fragmented because Android comes from many manufacturers. But basic principles apply: enable strict security settings, disable installation from unknown sources, enable Google Play Protect, use strong authentication, and keep the device updated.
Password and Account Security: Comprehensive Changes
Once you've confirmed your device status through forensic investigation, you can safely change passwords. Do this for all accounts, particularly email, financial accounts, and accounts with sensitive access.
Change passwords from a different device you're confident is secure. Don't change passwords from the device that received the spyware warning—if it's compromised, the attacker sees the new passwords.
For the most sensitive accounts, use unique, random passwords stored in a password manager. For email, use the strongest secondary authentication available, preferably a security key that requires physical possession.
Device Management: Ongoing Practices
After a spyware warning, maintain ongoing security practices:
Update everything religiously. Operating system updates, app updates, firmware updates—all of these patch security vulnerabilities that spyware exploits. Delaying updates leaves you vulnerable.
Be paranoid about links and attachments. Even a text from someone you trust might be compromised. Before clicking links, verify the sender through another communication channel. Before opening attachments, confirm the sender actually sent them.
Monitor for unusual device behavior. Excessive battery drain, unexplained data usage, unexpected restarts, or strange app behavior might indicate spyware. Document anything unusual and report it to security experts.
Use secondary devices for sensitive activities. If you're concerned about ongoing targeting, consider using a dedicated device for sensitive activities like accessing financial accounts or communicating with confidants. This limits exposure if one device is compromised.
Back up your data securely. If you need to eventually factory reset your device, you'll want a clean backup. Encrypted cloud backups from reputable providers (iCloud, Google Drive with encryption) are generally safe.

Understanding the Attacker Ecosystem: Who Built This?
Understanding who created the spyware targeting you provides context for understanding your risk and what to expect.
Commercial Spyware Companies: NSO Group, Intellexa, Paragon
NSO Group is the most well-known spyware company globally. Based in Israel, NSO develops Pegasus and sells it to governments for hundreds of thousands of dollars per installation. NSO's business model is straightforward: develop sophisticated spyware, obtain export licenses from government, sell to government customers.
NSO has faced international pressure and lawsuits over Pegasus deployments against journalists, activists, and political opposition. But as a private company, NSO doesn't face accountability mechanisms like governments do.
Intellexa is a European consortium offering government spyware under various brand names. Like NSO, Intellexa develops sophisticated tools and sells to governments. Intellexa faces similar international pressure and scrutiny.
Paragon Solutions sells Graphite and related tools, operating similarly to NSO and Intellexa. Paragon works more closely with some government agencies than typical commercial spyware companies.
These companies operate legally in their home countries (usually), obtaining export licenses and complying with government regulations. But internationally, they're controversial because their products enable governments to spy on citizens.
How Spyware Gets Deployed: The Technical Side
Understanding how spyware is deployed helps understand what attackers can and can't do.
Spyware deployment requires either a zero-day exploit (a previously unknown security vulnerability) or social engineering. Most sophisticated government spyware uses zero-day exploits because they bypass all security measures.
Once deployed, spyware establishes persistence on the device, meaning it survives device reboots and continues operating. The spyware then phones home to the attacker's command-and-control server, awaiting instructions for what data to steal.
The attacker can then extract text messages, calls, photos, location data, web browsing history, app activity, and anything else on the device. The attacker can also activate the microphone, camera, and other sensors for real-time surveillance.
How Attackers Get Targeted Devices
Governments targeting spyware have several ways to identify and compromise devices.
Telecom cooperation: Phone companies in many countries cooperate with governments, providing subscriber information and device identifiers. This allows governments to identify devices associated with specific phone numbers.
Telecommunications intercept: Governments with technical sophistication can intercept cellular network traffic, identifying devices based on their network behavior and associations.
Physical access: If governments have physical access to a device, deploying spyware is trivial. This is why people traveling to countries with repressive governments sometimes experience border searches of their phones.
Social engineering: Attackers sometimes use social engineering to compromise devices, sending malicious links or convincing targets to install malicious apps.
Most sophisticated government spyware uses zero-day exploits delivered through passive targeting—the government doesn't need to trick you, they just send a malicious message and the exploit works automatically.
Real-World Impacts: What Happens to People Targeted by Spyware
Understanding what actually happens to people targeted by government spyware illustrates why these warnings matter.
Journalists and Activists: Professional and Personal Consequences
Journalists targeted by spyware lose the ability to protect confidential sources. If a journalist's device is compromised, all communications with sources are exposed. This chills reporting and prevents future sources from coming forward.
Activists lose the ability to organize safely. If devices are compromised, protest coordination, organizing communications, and sensitive discussions are visible to governments. This enables governments to preempt activism, arrest organizers, or intimidate participants.
These impacts are concrete and measurable. Journalism suffers when journalists can't protect sources. Activism suffers when coordination is exposed. Dissent becomes more dangerous when governments can monitor all communications.
Business Impact: Intellectual Property and Competitive Intelligence
Business executives targeted by spyware lose competitive advantage. If device communications are compromised, negotiations, strategy discussions, and sensitive business information are visible to competitors or governments seeking intelligence.
Companies have lost competitive position after executives' devices were compromised, because competitors obtained advance knowledge of business strategy, negotiations, or product plans.
Personal Safety: Direct Physical Risk
For some people targeted by spyware, the risk is direct physical danger. Dissidents in authoritarian countries might be arrested based on communications obtained through spyware. Minority group members might face harassment based on communications revealed through spyware.
In some cases, governments have used spyware intelligence to target people for assassination or kidnapping. These are extreme cases, but they've occurred.

Living After Spyware Detection: Ongoing Considerations
If you've been targeted by government spyware, the targeting doesn't necessarily end. Once you're on a government's list, you're likely to remain interesting. This requires ongoing security consciousness.
Behavioral Changes That Reduce Risk
After being targeted, consider changing behaviors:
Reduce device connectivity when discussing sensitive topics. If you're having a conversation about something sensitive, consider doing it without devices nearby or in a Faraday bag that blocks signals.
Establish secure communication channels for sensitive discussion. For truly sensitive communications, consider in-person meetings or communication through trusted intermediaries.
Monitor your digital footprint. Know what information about you is publicly available online. Attackers use public information to socially engineer you or those close to you.
Consider leaving your phone at home for sensitive activities. If you're meeting someone sensitive or visiting a sensitive location, leaving your phone behind prevents location tracking and reduces device compromise risk.
Use operational security practices from high-risk groups. Journalists, activists, and security professionals use specific operational security practices. Study them and adopt relevant practices for your situation.
When to Consider a Fresh Start
In some cases, people targeted by spyware decide to factory reset their devices and start fresh. When might this make sense?
Factory resetting makes sense after you've completed forensic investigation and extracted evidence. Once investigators have analyzed the spyware and you've documented what happened, you can safely reset.
Factory resetting also makes sense if you've continued using a device for weeks or months after receiving a warning without professional investigation. In this case, if spyware was present, it's had substantial time to operate. A fresh start might be preferable to maintaining uncertainty.
Factory resetting does not make sense immediately after receiving a warning, before forensic investigation, or before understanding what's on your device.
Future Prevention: Staying Safer in an Era of State Spyware
Understanding how to prevent spyware helps prevent future targeting.
Device Ecosystem Choices
Apple and Google both receive spyware warnings sometimes, but the distributions differ. Apple's closed ecosystem makes some types of spyware harder. Android's openness enables some types of attacks. But both platforms remain vulnerable to zero-day exploits.
The most important factor isn't iOS vs. Android, it's keeping your device updated and enabling available security features.
Software Quality and Updates
Spyware exploits security vulnerabilities. Updates fix vulnerabilities. Delaying updates leaves you vulnerable. Making updates a non-negotiable practice provides substantial protection.
Apple and Google both release security updates regularly. Installing them immediately—sometimes within hours of release—provides protection before spyware developers have time to adapt.
Hardware Security Keys
Hardware security keys prevent account compromise even if your device is compromised. They require physical possession of the key to authenticate. Attackers with your passwords can't log into your accounts if they lack your security key.
For anyone at potential risk of targeting, a hardware security key is worthwhile. Options like YubiKey, Google Titan, and others cost under $100 and provide substantial protection.
Communication Choices
Some communication platforms provide stronger protections than others. End-to-end encrypted platforms like Signal and WhatsApp (for encrypted messages) prevent eavesdropping on communication content even if your device is compromised.
Important caveat: if your device is compromised with spyware, the attacker can still see messages because they're decrypted on your device before spyware intercepts them. But encrypted communication does prevent governments from intercepting communications at the network level.
Behavioral and Operational Security
Ultimately, the strongest protection against spyware is understanding your actual risk and adopting practices that reduce exposure.
If you're genuinely at risk of government targeting, consider security practices that minimize the value of compromised devices. These practices range from the practical (in-person meetings for sensitive discussions) to the extreme (dedicated devices, compartmentalized communications, limited device connectivity).

FAQ
What Should I Do Immediately After Receiving a Spyware Warning?
First, stay calm and don't panic. Immediately turn on available security features: Apple Lockdown Mode for iPhone users, Google Advanced Protection for Gmail accounts, and enhanced security settings for Android. Keep your device powered on and don't factory reset it. Document the exact notification text you received. Contact a security professional or appropriate organization within 24 hours if you believe you're at genuine risk. Don't publicize the warning, as this alerts attackers that you've been warned.
What's the Difference Between a Successful and Attempted Spyware Attack?
An attempted attack means someone tried to compromise your device but detection systems blocked it or it failed for technical reasons. Apple and WhatsApp notifications often indicate attempted attacks. A successful attack means spyware installed on your device and the attacker gained access to your data. Google notifications typically indicate Google blocked the attack at the network level. The distinction matters because successful infections require immediate forensic investigation, while attempted attacks require security hardening and monitoring.
Should I Factory Reset My Phone After a Spyware Warning?
Not immediately. Factory resetting destroys evidence that forensic investigators need to analyze. If you've received a spyware warning and suspect your device might be compromised, preserve it in current condition while you arrange forensic investigation. Only factory reset after investigators have completed their examination and extracted evidence. If you've waited weeks without investigation, factory resetting becomes more defensible, but immediate factory resetting eliminates crucial evidence.
How Can I Check If My Device Has Spyware?
You can run open-source tools like Mobile Verification Toolkit (MVT) if you have technical expertise, which can identify known spyware patterns. MVT works best with help from security experts who know how to extract device data and interpret results. Professional forensic investigators use more sophisticated tools and can detect more advanced spyware. Running MVT yourself provides baseline information, but professional investigation is more thorough and provides legal documentation of findings.
Is Lockdown Mode Enough Protection Against Spyware?
Lockdown Mode provides substantial protection by reducing the attack surface and disabling functionality that spyware commonly exploits. Apple claims it has never seen a successful hack against a user with Lockdown Mode enabled, though no security measure is absolute. Lockdown Mode works best combined with other protections: security keys for authentication, updated operating systems, avoiding suspicious links, and security awareness. It's a strong protection but not a guarantee against sophisticated attacks.
Who Should I Contact for Help If I Receive a Spyware Warning?
Options depend on who you are. If you're a journalist, activist, or human rights defender, contact Access Now's Digital Security Helpline, Amnesty International's Security Lab, or the Citizen Lab. If you're a business executive or politician, consider private firms like iVerify, Lookout, Safety Sync Group, or Hexordia. If you work for a large organization, contact your company's security team. Organizations like Reporters Without Borders help journalists specifically. Most specialized resources for civil society members offer free or low-cost investigation.
How Do I Know If I've Been Targeted Specifically or If This Is Random?
Government spyware targeting is not random. Receiving a warning means someone specifically targeted your device. They may have targeted you because of your profession, activism, political beliefs, associations, or other characteristics. Or they might have misidentified you or targeted the wrong phone number. The fact of targeting is real; the reason for targeting might not be what you initially assume. Professional investigators can sometimes determine targeting patterns and help explain why you were targeted based on the spyware used and deployment method.
What's the Cost of Professional Forensic Investigation?
Cost varies dramatically. Organizations like Access Now and Amnesty International offer free investigation for civil society members. Private firms charge thousands to tens of thousands of dollars for comprehensive forensic investigation, depending on complexity and scope. Basic forensic investigation might cost
Can Spyware Be Removed Without Detecting It?
Sophisticated spyware can be remotely uninstalled by attackers if they realize their compromise has been detected or is being investigated. This is actually useful because it means spyware is active and can be detected if investigation happens quickly. If you're investigating a potential spyware infection weeks after the initial warning, the spyware might have been uninstalled by attackers. This is why professional investigation should happen relatively soon after receiving a warning, while spyware is likely still active.
What Should I Tell People Close to Me About Being Targeted?
Use judgment about what to share. If you share publicly, attackers know you're aware and might remove spyware before investigation. If your close contacts are also at risk or need to take security precautions, they should know. But broadly publicizing the warning can interfere with investigation and understanding. Share information with family members who should know about potential security risks, with your organization's security team if relevant, and with professional investigators who can help. Otherwise, discretion serves your security.
How Long Should I Wait Before Considering My Device Safe?
If forensic investigation confirms no active spyware infection, your device is generally safe to use with hardened security practices. If investigation identifies spyware, then factory reset afterward makes the device safe. If you haven't pursued forensic investigation, waiting weeks or months doesn't make the device safer—it just means you're uncertain. The uncertainty itself is stressful. Most experts recommend either pursuing professional investigation relatively quickly (within days or weeks) or factory resetting to eliminate uncertainty.

Conclusion: Taking Control After a Spyware Warning
Jay Gibson's panic response when he received the spyware warning was entirely human and understandable. Someone had attempted to hack his iPhone. A government or government contractor was interested in what's on his device. That triggers primal fear responses.
But here's what Gibson and everyone else targeted by government spyware needs to know: the warning itself represents a shift in power. For years, spyware worked silently. People didn't know they were compromised. Governments could surveil without detection or accountability.
Now, tech companies detect and warn. That creates a brief window where you know you're targeted and can act. That window is valuable. It lets you preserve evidence, seek help, harden security, and understand your situation.
The steps outlined here are concrete. They're not theoretical. They work because they're based on how actual experts respond to actual spyware cases. Some steps are immediate and critical: don't panic, turn on security features, preserve your device. Other steps require resources or professional help: arrange forensic investigation, change passwords carefully, implement ongoing security practices.
Not everyone who receives a spyware warning will pursue all these steps. Some people will ignore the warning entirely. Others will panic and factory reset their devices. But if you want to take reasonable precautions without becoming paralyzed by fear, this guide provides the roadmap.
The hardest part isn't the technical steps. The hard part is accepting that you've been targeted and taking the whole situation seriously. Once you accept that reality, the actions follow naturally. Enable Lockdown Mode. Contact security professionals. Preserve your device. Let experts investigate. Implement stronger security practices going forward.
Being targeted by government spyware is serious. But it's not a situation where you're helpless. You have agency. You have options. You have organizations ready to help. The notification itself, while frightening, is actually good news compared to being compromised silently.
Take the warning seriously. Take action reasonably. Seek help if you need it. And don't let fear paralyze you into inaction.
Additional Resources and Organizations
For those seeking concrete next steps, these organizations provide genuine help:
Access Now (accessnow.org) provides 24/7 digital security support for at-risk groups. Their Digital Security Helpline can be reached through their website.
Amnesty International (amnesty.org) has a dedicated Security Lab investigating spyware campaigns against human rights defenders. Amnesty's team of forensic investigators can conduct comprehensive investigations.
Citizen Lab (citizenlab.ca) at the University of Toronto researches government spyware and surveillance. Citizen Lab investigates cases that reveal broader surveillance patterns.
iVerify offers both app-based monitoring and forensic investigation services for individuals concerned about advanced threats.
Reporters Without Borders (rsf.org) provides digital security support specifically for journalists and media workers.
These organizations exist because government spyware is real and increasingly common. They're staffed by experts who understand the threat and know how to help. Reaching out to them after a spyware warning is exactly what these organizations are designed to support.

Key Takeaways
- Tech company spyware warnings mean someone attempted to hack you. They're serious. They're not false alarms.
- Don't panic immediately. Don't factory reset. The first 24 hours are crucial for preserving evidence for forensic investigation.
- Enable Lockdown Mode (Apple), Advanced Protection (Google), and enhanced security features immediately after receiving warning.
- Journalists, activists, and at-risk groups can get free forensic investigation from Access Now, Amnesty International, and Citizen Lab.
- If spyware successfully infected your device, it can be forensically examined to identify which exploits were used and sometimes who deployed it.
- Business executives and politicians have fewer free resources but can contact private security firms like iVerify, Lookout, or Safety Sync Group.
- Document the warning immediately, preserve your device, and contact professional investigators within 24-72 hours for maximum effectiveness.
- Government spyware like Pegasus and Graphite requires zero-day exploits but provides attackers complete access to all device data.
Related Articles
- Rainbow Six Siege Server Crisis: What Happened & How It Impacts Gaming [2025]
- Juice Jacking: How to Protect Your Phone from Public Charging Threats [2025]
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
- WebRAT Malware on GitHub: The Hidden Threat in Fake PoC Exploits [2025]
- AI Agents Are Coming for Your Data: Privacy Risks Explained [2025]
- [2025] The Rise of Super Apps: Crypto Payments & Encrypted Chat
![Government Spyware Targeted You? Complete Action Plan [2025]](https://tryrunable.com/blog/government-spyware-targeted-you-complete-action-plan-2025/image-1-1767004938178.jpg)



