ESA Cyberattack: What You Need to Know About the 200GB Breach [2025]
The European Space Agency just experienced one of its most serious cybersecurity incidents in recent memory. On December 18, external servers were breached, and a threat actor claiming the username '888' announced they'd stolen around 200 gigabytes of sensitive data. This wasn't some low-level misconfiguration either. We're talking source code, API tokens, infrastructure configurations, and documentation that could expose critical vulnerabilities across the entire ESA ecosystem.
What makes this particularly concerning is the ripple effect. The ESA doesn't work in isolation. It collaborates with space agencies across Europe, North America, and beyond. When one of the world's leading space research organizations gets hit, the implications stretch far beyond just one agency.
Let me break down exactly what happened, why it matters, and what this means for cybersecurity in critical infrastructure.
TL; DR
- The Breach: ESA confirmed cyberattack on external servers supporting collaborative engineering activities on December 18.
- Scale of Theft: Threat actor '888' claims to have stolen 200GB of data including source code, API tokens, and CI/CD configurations.
- What Was Stolen: Private Bitbucket repositories, infrastructure code, hardcoded credentials, internal documentation, and access tokens.
- Current Status: ESA initiated forensic analysis and implemented security measures; investigation ongoing.
- Historical Context: This follows ESA's 2024 web shop breach involving a credit card skimmer malware.
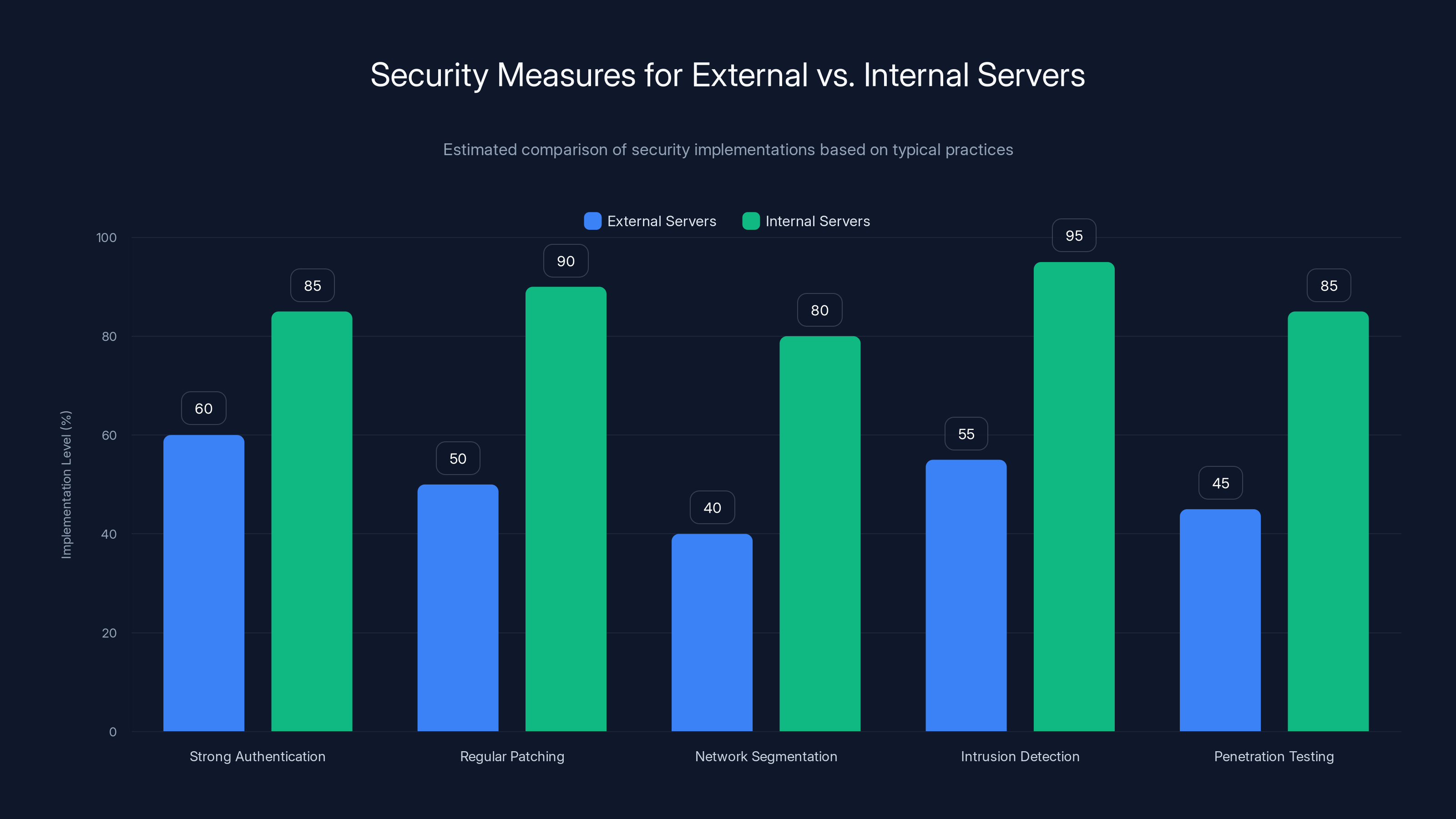
Estimated data shows that internal servers typically have higher implementation levels of security measures compared to external servers, highlighting a potential vulnerability in external systems.
The ESA Cyberattack: Timeline and Initial Details
Let's start with what we know for certain. The European Space Agency posted on X (formerly Twitter) acknowledging the incident, confirming that external servers had been compromised. The key phrase here is "external servers"—servers located outside ESA's corporate network perimeter.
On the surface, you might think "okay, external servers, they're probably not mission-critical." That's a dangerous assumption. External servers often support collaborative work between organizations. Scientists share data. Engineers exchange models. Researchers access computational resources. These aren't throwaway systems—they're essential infrastructure for modern space research.
The ESA statement read: "ESA is aware of a recent cybersecurity issue involving servers located outside the ESA corporate network. We have initiated a forensic security analysis—currently in progress—and implemented measures to secure any potentially affected devices."
Notice the careful language. They said "potentially affected devices." That's security-speak for "we don't yet know the full extent." They're still investigating, which is completely normal in the immediate aftermath of a breach, but it also means we're operating with incomplete information.
The agency emphasized that these servers support "unclassified collaborative engineering activities within the scientific community." Translation: the compromised systems handled non-classified work. That's important because it means actual classified space mission data likely wasn't touched. But unclassified doesn't mean unimportant.
What the Threat Actor Claims Was Stolen
A cybercriminal using the alias '888' posted on Breach Forums (a notorious hacker forum) taking credit for the breach. According to their announcement, they exfiltrated 200 gigabytes of data from ESA systems. That's roughly equivalent to:
- 1,000 feature-length movies in HD quality
- 40 million average documents
- Millions of lines of source code
Breakdown of what they claim to have stolen:
-
Source code from private Bitbucket repositories – This is enormous. Private repositories contain unfinished code, experimental features, and internal tools that might have vulnerabilities not yet patched.
-
CI/CD pipeline configurations – These are the automated systems that build, test, and deploy software. Knowing how these work gives attackers insight into security testing procedures and deployment processes.
-
API and access tokens – These are essentially digital keys that grant access to systems and services. Compromised tokens could allow unauthorized access to other ESA systems or partner organizations' infrastructure.
-
Internal documentation – Process documents, system architecture diagrams, and operational procedures that map out how systems work and where weaknesses might exist.
-
Terraform infrastructure code – Terraform files define how cloud infrastructure is configured. This tells attackers exactly what systems exist, how they're connected, and potentially where security gaps exist.
-
Hardcoded credentials and configuration files – Passwords, API keys, database credentials, and connection strings embedded directly in files. This is the kind of mistake that keeps security professionals up at night.
The threat actor posted screenshots as "proof" of the breach, but at the time of this investigation, no independent security researchers had verified whether those samples were legitimate. That's a critical distinction. Anyone can claim they hacked something. Proving it is harder.

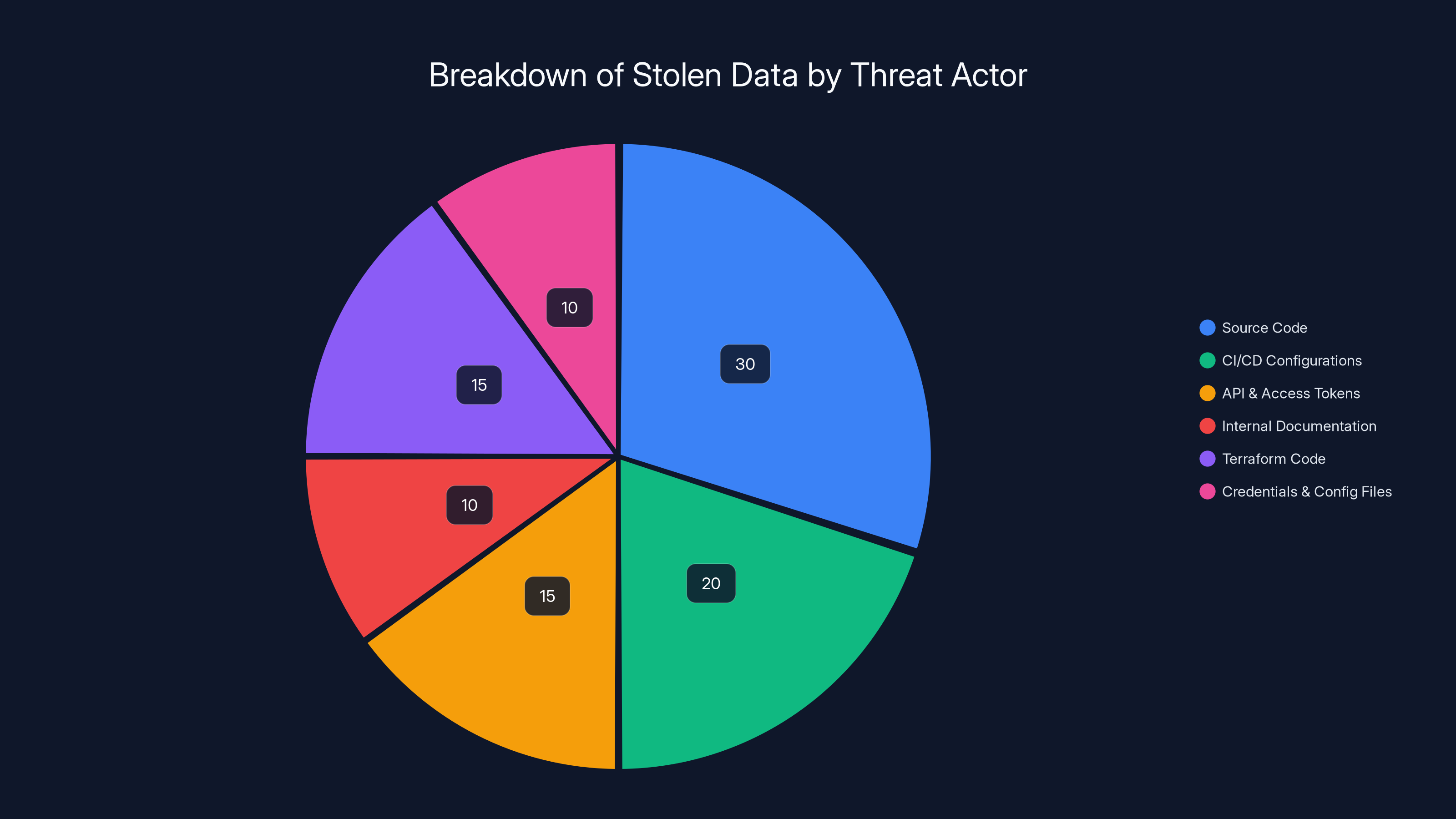
The pie chart illustrates the estimated distribution of stolen data types, with source code and CI/CD configurations comprising the largest portions. Estimated data.
Why External Servers Might Actually Be More Vulnerable
Here's something counterintuitive about cybersecurity: external systems are often less carefully guarded than internal ones. It sounds backward, but it makes sense operationally.
Internal corporate networks get the fancy firewall configurations, the zero-trust security models, the intrusion detection systems. They're locked down tight. External servers? They need to be accessible to external collaborators. That's their whole purpose.
When you need to enable access for scientists from 50 different institutions across 30 countries, you can't implement the same kind of restrictions you'd use internally. You need APIs that are broadly accessible. You can't require everyone to use your corporate VPN. Authentication gets more permissive by necessity.
This creates a classic security trade-off: usability versus security. ESA chose (like most organizations) to prioritize collaboration, which means accepting some additional security risk on external systems.
The question is: was that risk managed appropriately? Did they have:
- Strong authentication on those servers?
- Regular security patching and updates?
- Network segmentation isolating external systems from critical infrastructure?
- Intrusion detection systems monitoring for suspicious activity?
- Regular penetration testing and vulnerability assessments?
We don't have answers yet. The forensic investigation is ongoing. But the breach itself suggests that at minimum, something wasn't working as intended.
The Source Code Problem: Why This Matters
Let me explain why stolen source code is such a serious problem for a space agency.
Source code isn't just lines of text that make programs run. It's a blueprint of how systems work, where shortcuts were taken, where vulnerabilities might exist, and how security controls are implemented. When you have access to the actual code, finding vulnerabilities becomes dramatically easier.
Consider this scenario: An ESA system has a vulnerability in a particular function. The developers wrote a patch in version 5.2, but not everyone upgraded immediately. A normal attacker would need to reverse-engineer the binary to find that vulnerability. An attacker with the source code? They can just read it. They see exactly what was wrong in version 5.1 and how it was fixed in 5.2. They immediately know which systems running 5.1 are vulnerable.
This is especially problematic when source code includes hardcoded credentials or comments that reveal system architecture. I've seen source code dumps where developers left comments like: "TODO: fix this SQL injection vulnerability" or "HACK: temporary bypass for testing environment." Those comments become a roadmap for attackers.
For a space agency, additional concerns emerge:
- Competitor intelligence: Other space agencies (especially those in competitive relationships) could reverse-engineer ESA systems to identify vulnerabilities.
- Supply chain attacks: If ESA systems interact with contractors or partner organizations, attackers could use the code to identify attack vectors into those networks.
- Mission planning exposure: Even unclassified code might contain hints about future mission architecture or capabilities.
This is why ESA's statement that these were "unclassified" systems matters somewhat, but shouldn't be reassuring. Unclassified doesn't mean public. It just means not officially classified as top-secret.

API Tokens and Access Credentials: The Keys to the Kingdom
When attackers steal API tokens and access credentials, they're not just getting data—they're getting keys to systems they don't own. This is potentially more dangerous than stolen data itself.
An API token is like a digital key. It says: "This request is authorized." If ESA systems use weak token rotation practices (and many organizations do), those tokens might grant access for weeks, months, or even longer.
Consider the implications:
- Persistent access: Attackers can use stolen tokens to access systems long after the breach is detected.
- Lateral movement: A token that grants access to one system might allow hopping to connected systems.
- Resource abuse: Attackers could use credentials to spin up expensive cloud resources and rack up bills.
- Data exfiltration: Ongoing access means ongoing theft—attackers aren't limited to what they grabbed on day one.
- Persistence mechanisms: Attackers could create backdoor accounts or install persistent malware using the stolen credentials.
The standard incident response protocol for stolen credentials is:
- Immediate rotation of all potentially compromised credentials.
- Audit logs review to identify what systems were accessed with those credentials.
- System restoration from clean backups, because you can't trust anything that was accessible with those credentials.
- Network segmentation verification to prevent lateral movement.
- Extended monitoring because attackers might have created backup access mechanisms.
This isn't something that happens in a day. It's a multi-week project for a large organization.
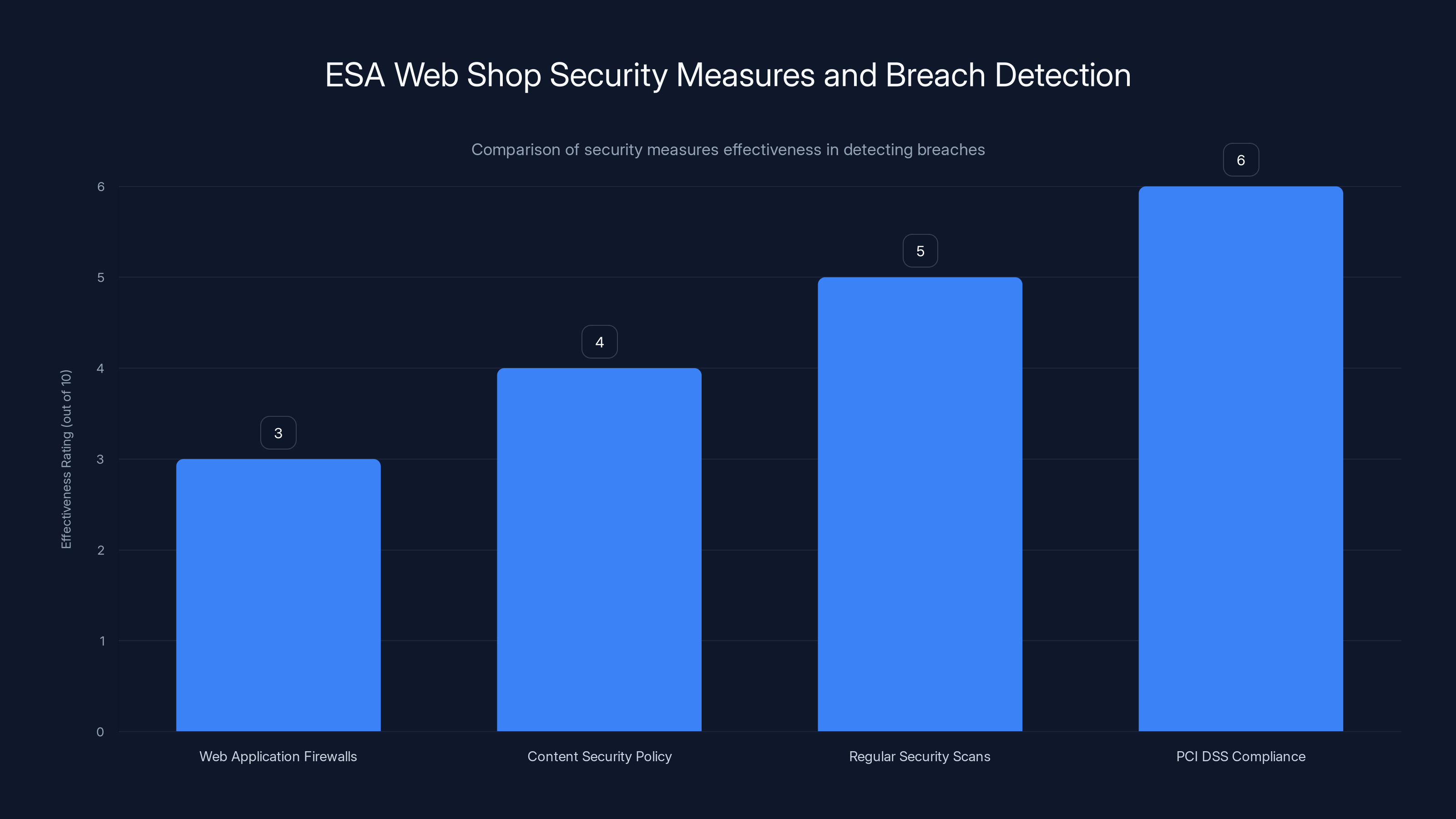
The effectiveness of ESA's security measures in detecting the 2024 breach was low, with regular security scans and PCI DSS compliance being slightly more effective. Estimated data.
CI/CD Pipeline Exposure: Where Attacks Get Sophisticated
CI/CD (Continuous Integration / Continuous Deployment) pipelines are the automated systems that build, test, and deploy software. They're incredibly powerful and incredibly dangerous if compromised.
Here's why: A CI/CD pipeline has credentials for deploying to production servers. If an attacker gains access to the pipeline, they can:
- Inject malware into software before it's deployed.
- Modify code without going through code review processes.
- Exfiltrate secrets that the pipeline uses to access other systems.
- Deploy backdoors that give them persistent access.
- Modify logs to cover their tracks.
This is what's called a "supply chain attack." Instead of breaking into the final system, attackers compromise the process that creates and deploys that system. It's like poisoning the source rather than the stream.
For ESA, this is especially concerning because:
- Scientific collaboration: ESA collaborates with universities, research institutions, and private contractors. If ESA's pipeline is compromised, those partners' systems could be at risk.
- Mission-critical updates: Software running on spacecraft, satellites, and ground control systems might be deployed through these pipelines.
- Multi-national coordination: Updates coordinated across multiple organizations and countries could be affected.
ESA would need to:
- Audit every deployment made since the compromise date.
- Review code changes in repositories accessed by the compromised pipeline.
- Potentially rebuild and redeploy all software deployed after the breach date.
- Verify that no malware or backdoors were introduced.
Infrastructure Code: The Map of Everything
Terraform is a popular tool for defining cloud infrastructure. When you write Terraform code, you're essentially creating a blueprint that says: "Here's how my infrastructure should look."
If attackers get your Terraform files, they see:
- All your cloud resources – Every server, database, storage bucket, and service.
- Network architecture – How systems are connected and communicate.
- Security configurations – Firewall rules, access controls, authentication mechanisms.
- System relationships – Which systems depend on which other systems.
- Resource sizing – How much computing power, storage, and bandwidth is allocated.
It's like giving attackers a map of your entire kingdom. They can identify the weakest points, the critical chokepoints, and the paths to valuable resources.
For a space agency, infrastructure code exposure reveals:
- Computational resources used for simulation and modeling.
- Data storage architecture and where sensitive datasets are kept.
- Backup and recovery systems that attackers could target.
- Development versus production environments and how they differ.
- Disaster recovery procedures that attackers could disrupt.
Recovery requires essentially rebuilding infrastructure from scratch, because you can't trust that existing infrastructure is configured securely. Attackers know exactly how it's set up, so they've had time to identify all the weaknesses.
Internal Documentation: The Owner's Manual for Exploitation
Internal documentation is sometimes overlooked by people outside cybersecurity. It sounds boring. But for attackers, it's gold.
Internal docs typically include:
- System architecture diagrams showing how systems connect.
- Operational procedures for deploying, updating, and troubleshooting systems.
- Incident response playbooks revealing how the organization responds to attacks (so attackers know what to avoid).
- User access procedures showing how people typically get authorized for systems.
- Security exception processes exposing workarounds that bypass security controls.
- Known issues and workarounds documenting vulnerabilities that haven't been fixed.
- Vendor contact information for supply chain attacks.
- Disaster recovery procedures that could be disrupted.
When you combine internal documentation with source code and infrastructure files, you have a complete operational picture. It's like having the employee handbook, the system administration guide, the incident response procedures, and the architectural blueprints all at once.
Attackers can use this information to:
- Impersonate employees by understanding their workflows.
- Identify the best time to attack (during maintenance windows documented in procedures).
- Craft social engineering attacks using information from documentation.
- Understand emergency procedures they can disrupt.
- Find old accounts or systems documented as deprecated but still running.
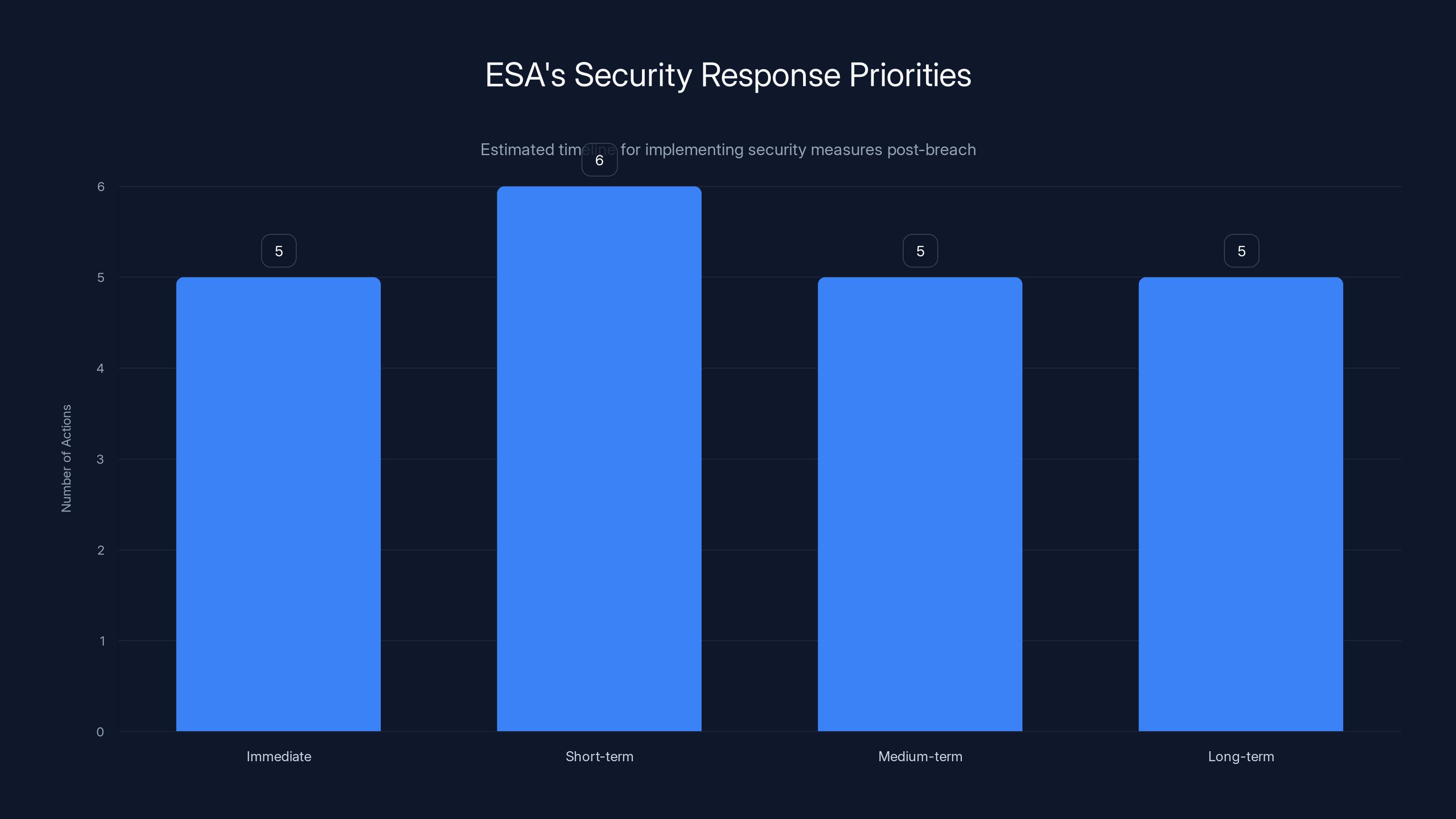
ESA's security response plan includes 21 key actions divided across four phases, with the most actions planned for the short-term phase. Estimated data based on typical breach response practices.
The 2024 ESA Web Shop Breach: History Repeating
This isn't ESA's first rodeo with cyberattacks. Just a year prior, in 2024, the ESA's web shop was compromised with a credit card skimmer.
Here's what happened: A malicious script was injected into ESA's e-commerce platform. This script did something insidious—it created a fake payment form that looked legitimate but actually captured customer information. When users thought they were entering payment data securely, they were actually sending it to attackers.
Security researchers from Sansec discovered the attack. The skimmer was stealing:
- Credit card numbers.
- Expiration dates.
- CVV codes.
- Cardholder names and addresses.
- Other personally identifiable information.
This wasn't a sophisticated zero-day attack. It was a relatively simple injection of Java Script into the payment processing workflow. It should have been caught by:
- Web application firewalls detecting unusual scripts.
- Content Security Policy headers preventing unauthorized script execution.
- Regular security scans identifying injected code.
- PCI DSS compliance checks (required for any organization handling payment cards).
The fact that it wasn't caught earlier suggests gaps in ESA's security monitoring and scanning procedures.
Now, a year later, ESA is dealing with an even more serious breach. This raises questions: Has ESA addressed the root causes of the 2024 breach? Have they implemented better security monitoring? Have they increased their security budget and staffing?
The quick timeline between breaches (roughly 12 months) suggests that either:
- The first breach created vulnerabilities that the second attacker exploited.
- The same attacker returned through a different vector.
- Multiple attackers are targeting ESA because they've demonstrated vulnerability.
- ESA's security improvements haven't been comprehensive enough.
Without complete information from the investigation, we can't know for certain. But back-to-back breaches are always a red flag.
Security Investigation and Response: What Happens Next
When an organization like ESA discovers a breach, the immediate response is crucial. Let's walk through what they've done and what needs to happen next.
Immediate actions (already announced):
- Forensic security analysis – Engaging forensic experts to understand how the breach occurred, what was accessed, and what systems were affected.
- Device hardening – Securing any potentially affected devices, which likely means:
- Taking systems offline if necessary.
- Resetting passwords and credentials.
- Patching known vulnerabilities.
- Installing updated security tools.
- Stakeholder notification – Informing relevant parties that their data might have been compromised.
- Preliminary assessment – Determining that "only a very small number of external servers may have been impacted."
Investigation phase (ongoing):
Forensic investigators will be:
- Analyzing system logs to understand the attack timeline.
- Identifying entry points and how attackers got in.
- Determining what systems were accessed and for how long.
- Identifying what data was copied or modified.
- Looking for persistence mechanisms (backdoors, hidden accounts, malware).
- Collecting evidence for potential law enforcement involvement.
Recovery phase (upcoming):
Once they understand the scope, recovery includes:
- Rotating all potentially compromised credentials.
- Patching vulnerabilities exploited in the attack.
- Rebuilding systems from clean backups.
- Implementing enhanced monitoring and detection capabilities.
- Conducting penetration tests to find other vulnerabilities.
- Improving security controls on external systems.
Investigation timeline estimate:
For an organization the size of ESA with the complexity of their systems, a thorough investigation typically takes:
- 2-4 weeks: Initial forensics and scope determination.
- 4-12 weeks: Complete investigation, root cause analysis.
- 12+ weeks: Full remediation and hardening.
So we're likely looking at mid-2025 before ESA publicly discloses the full findings.

Impact on International Space Collaboration
ESA doesn't operate in isolation. It's part of a global space exploration ecosystem that includes:
- National space agencies: NASA (USA), Roscosmos (Russia), CNSA (China), JAXA (Japan), ISRO (India).
- International partnerships: ISS program involving 15+ countries.
- Commercial partners: Space X, Blue Origin, Axiom Space, and hundreds of smaller contractors.
- Academic institutions: Universities across Europe and globally.
- Research networks: Computing centers, data repositories, simulation facilities.
When ESA's external servers are compromised, the ripple effects spread across this entire ecosystem.
Direct impacts:
- Partner organizations might be at risk if they share systems or credentials with ESA.
- Data shared through compromised servers could be exposed.
- Joint research projects might be affected.
- Collaborative missions could face delays if security reviews are required.
Indirect impacts:
- Trust in ESA's security practices is damaged, affecting future partnerships.
- Other space agencies might audit their own ESA interactions.
- Insurance costs for ESA and partners could increase.
- Regulatory scrutiny increases (especially regarding data protection in the EU).
- Competitive advantages gained by attackers might benefit rival space programs.
Operational impacts:
- Scientific collaboration might slow down during the investigation.
- Researchers might face access restrictions to systems being forensically examined.
- Data sharing procedures might become more cumbersome as security is tightened.
- Timelines for collaborative projects might slip.
For international space exploration, which increasingly depends on complex coordination and data sharing, security breaches create friction that's hard to undo.
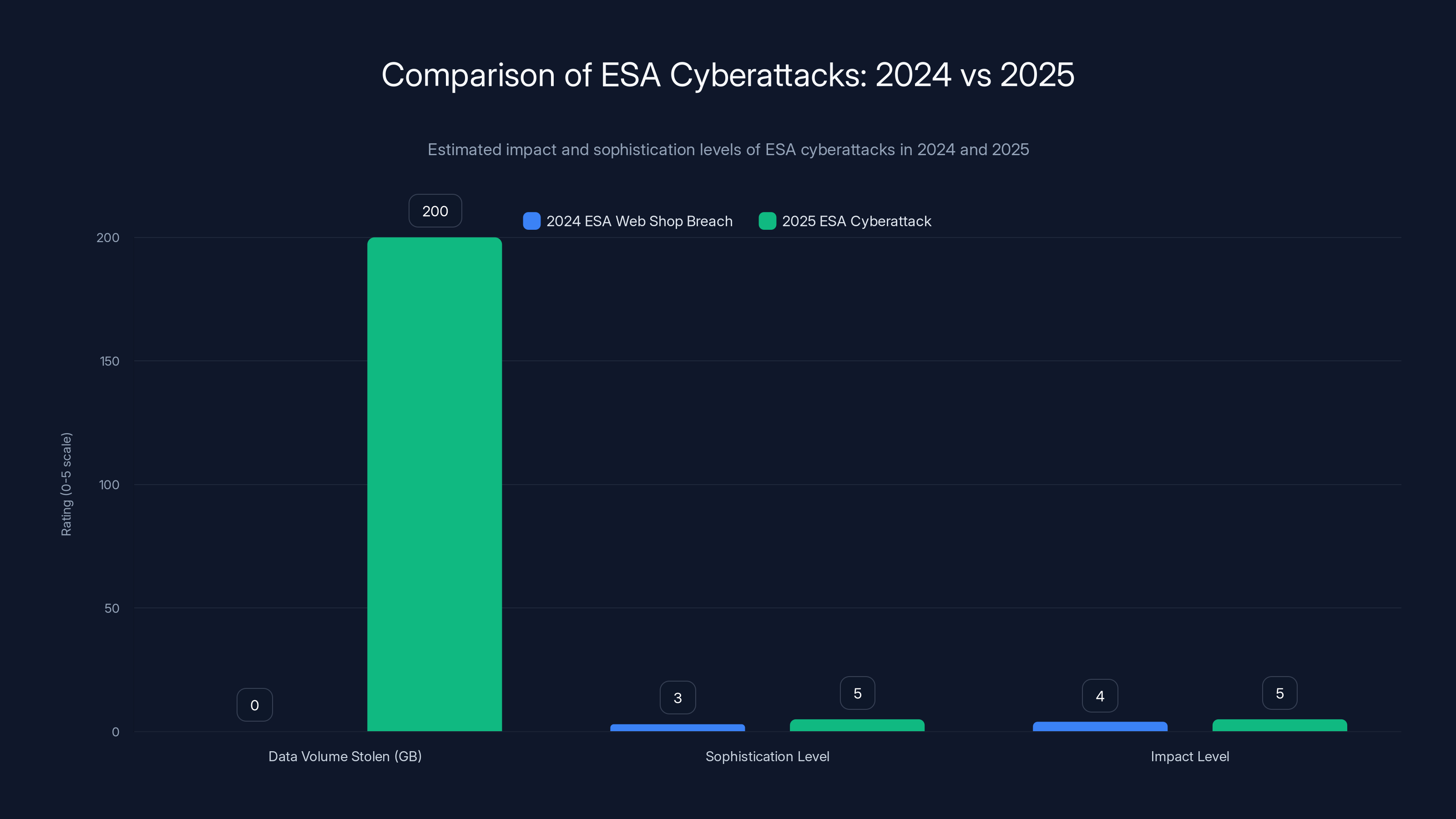
The 2025 ESA cyberattack involved a larger data theft (200GB) and was more sophisticated and impactful compared to the 2024 credit card skimming incident. Estimated data based on described events.
The Bigger Picture: Critical Infrastructure Vulnerability
The ESA breach isn't an isolated incident. It's a symptom of broader vulnerabilities in critical infrastructure security.
Space agencies, nuclear facilities, power grids, water systems, and healthcare networks all share common security challenges:
- Legacy systems: Much critical infrastructure runs on systems built decades ago, predating modern security practices.
- Resource constraints: Security budgets are often inadequate relative to the actual risks.
- Complexity: Modern systems are interconnected in ways that create unexpected vulnerabilities.
- Collaboration requirements: Critical infrastructure needs to work with external partners, creating security compromises.
- Vulnerability research lag: New vulnerabilities are discovered constantly, but patches are slow to deploy.
For space agencies specifically:
- Dual-use concerns: Civilian space research has implications for defense and national security.
- Long development cycles: Systems might take decades to develop, using technologies and practices that are outdated by deployment.
- Stringent requirements: Systems need to work perfectly in environments where you can't send a repair technician.
- Limited redundancy: Some systems can't be taken offline for updates without major mission impacts.
The ESA breach demonstrates that even well-resourced government organizations with sophisticated security teams are vulnerable to modern cyberattacks.

Hardened Response: What ESA Should Do Now
Based on breach response best practices and lessons from similar incidents, here's what ESA needs to prioritize:
Immediate (Days 1-7):
- Complete evidence preservation – Ensure forensic evidence isn't tampered with or degraded.
- Communication protocol establishment – Create clear messaging about the breach to stakeholders.
- Threat intelligence sharing – Work with law enforcement and government cybersecurity agencies.
- Access review – Disable any accounts that could have been compromised.
- Backup verification – Confirm that clean backups exist for recovery.
Short-term (Weeks 2-8):
- Complete forensic investigation – Understand exactly what happened.
- Vulnerability remediation – Patch all identified vulnerabilities.
- Credential rotation – Replace all potentially compromised credentials.
- System hardening – Implement additional security controls.
- Detection system deployment – Set up tools to identify similar attacks in the future.
- Partner notification – Clearly communicate risks to partner organizations.
Medium-term (Months 2-6):
- Architecture review – Evaluate whether external systems should exist at all.
- Network segmentation – Implement stronger isolation between external and internal systems.
- Security training – Increased awareness training for all staff (the 2024 breach suggests gaps).
- Third-party audits – Bring in independent security firms to verify everything.
- Incident response drills – Regular testing of breach response procedures.
Long-term (6+ months):
- Culture change – Make security a core organizational value, not an afterthought.
- Budget investment – Allocate appropriate resources to security (typically 5-8% of IT budget for critical infrastructure).
- Talent recruitment – Hire experienced security professionals.
- Continuous improvement – Regular vulnerability assessments and penetration testing.
- Industry leadership – Share lessons learned to help other organizations avoid similar breaches.
Geopolitical Implications and Nation-State Concerns
Here's something important that doesn't get discussed as much as it should: Space agencies are targets for nation-state actors, not just random cybercriminals.
When governments invest in hacking space agencies, they're trying to:
- Understand capabilities: What satellites can ESA launch? What can they observe?
- Identify weaknesses: Where are the technical or operational vulnerabilities?
- Steal intellectual property: What technologies has ESA developed?
- Establish persistence: Can we maintain long-term access to ESA systems?
- Create leverage: Can we use access to ESA to pressure Europe?
The threat actor '888' claiming responsibility on a public forum is interesting because it doesn't fit the typical nation-state playbook. Nation-state actors usually operate secretly. They don't announce their victories. They maintain access as long as possible.
So '888' could be:
- An independent cybercriminal looking to make a name for themselves and potentially sell the data.
- A criminal group that will auction the data to the highest bidder.
- A state-sponsored actor using an alias to obfuscate attribution.
- A disgruntled insider with criminal connections.
Without attribution analysis from intelligence agencies, we can't know for sure. But the public announcement suggests this is more about profit or notoriety than about state espionage.

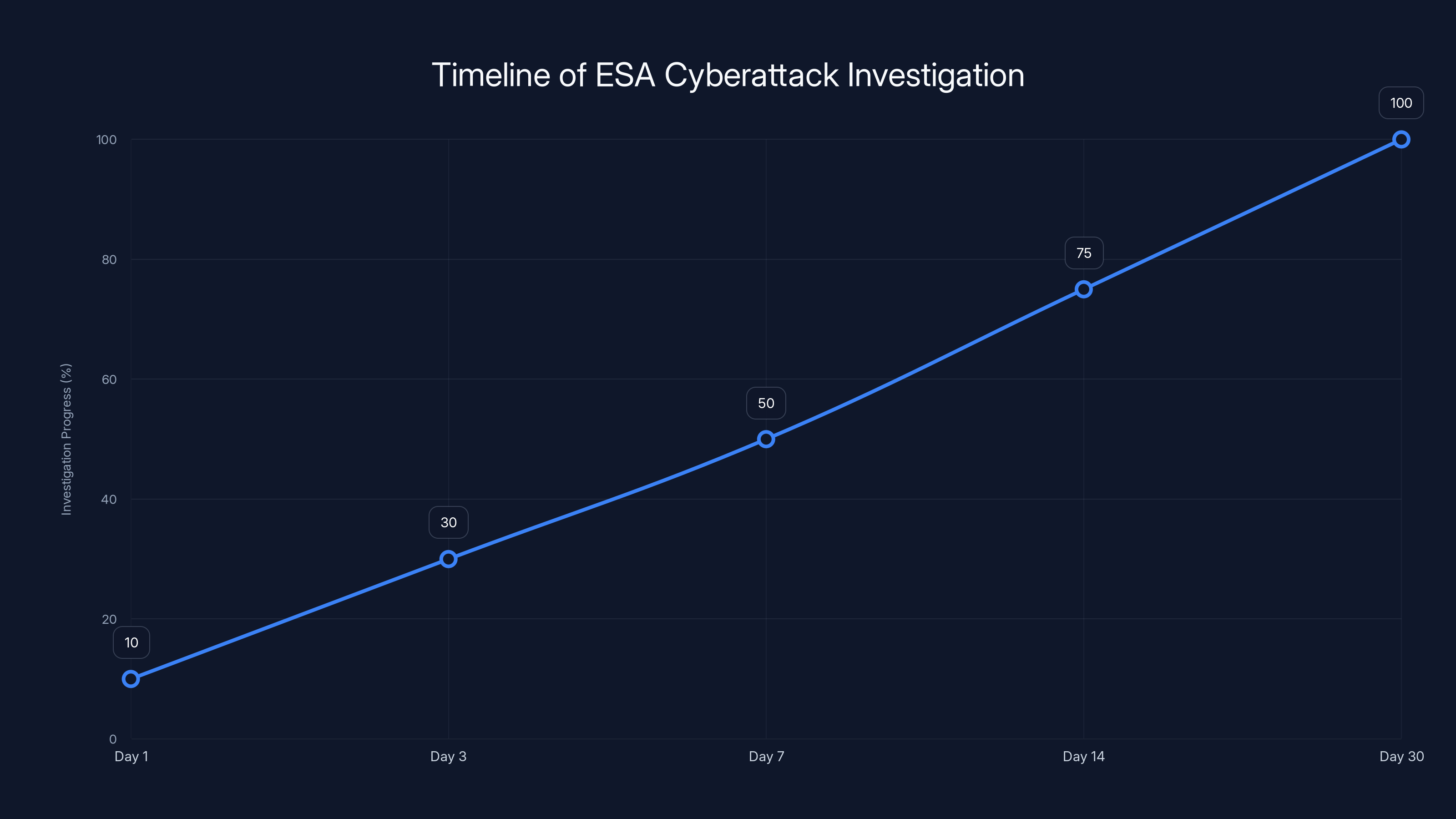
The estimated timeline shows typical progress in a cybersecurity investigation, reaching full understanding by day 30. Estimated data based on common investigation phases.
Data Classification Concerns: "Unclassified" Doesn't Mean Safe
ESA's repeated emphasis that these were "unclassified" systems is interesting because it reveals a potential gap in security thinking.
Information classification in government works like this:
- Classified/Top Secret: Information that could cause severe damage to national security if disclosed.
- Secret: Information that could cause serious damage if disclosed.
- Confidential: Information that could cause damage if disclosed.
- Restricted/Internal Use: Information that's not for public disclosure but doesn't fit above categories.
- Unclassified: Information that can be publicly released.
ESA systems handle "unclassified" information. That's perfectly fine for scientific work. But unclassified doesn't mean worthless. It doesn't mean not sensitive. It just means not officially classified as top-secret.
Unclassified information stolen in this breach includes:
- Research data that could give competitors insight into ESA capabilities.
- Technical designs that could reveal weaknesses.
- Organizational procedures that expose how decisions are made.
- Personnel information that could be used for social engineering.
- Vendor relationships that could be exploited for supply chain attacks.
Relying on classification levels as a security measure is outdated. Modern security should be based on:
- Data sensitivity: How would disclosure affect the organization and stakeholders?
- Business impact: What's the financial or operational damage from exposure?
- Regulatory compliance: What laws require protection of this data?
- Competitive advantage: Is this information proprietary or hard-won?
Data doesn't need to be classified as secret to be worth protecting.
Recovery and Resilience: Building Better Security
From a cybersecurity maturity perspective, organizations move through stages in their security evolution:
Stage 1: Reactive – No formal security program. Respond to incidents after they happen. (This is where ESA might have been for external systems)
Stage 2: Managed – Basic security controls in place. Some monitoring and detection. Incident response procedures exist.
Stage 3: Defined – Security practices are documented and standardized. Regular assessments and audits.
Stage 4: Measured – Continuous monitoring and metrics. Security KPIs drive decision-making.
Stage 5: Optimized – Continuous improvement. Threat intelligence drives prevention. Security is built into everything.
After a breach, organizations typically jump 1-2 maturity levels. ESA's response suggests they're moving from reactive toward managed security.
To truly recover and prevent future incidents, ESA needs to:
- Establish a Chief Information Security Officer (CISO) position with board-level authority and appropriate budget.
- Implement Zero Trust security – Verify every access request, don't assume anything is safe.
- Deploy EDR (Endpoint Detection and Response) – Tools that monitor for suspicious activity on every system.
- Conduct regular penetration testing – Have external experts continuously try to break in.
- Implement security awareness training – Make employees your first line of defense.
- Build threat intelligence partnerships – Work with government agencies and other organizations to share threat information.
- Establish incident response teams – Pre-planned teams with clear roles and procedures.
- Create security metrics and reporting – Measure security posture and communicate to leadership.
The goal isn't to prevent all breaches (that's impossible). The goal is to detect breaches faster, contain them better, and recover more quickly.

Lessons for Organizations Beyond Space Agencies
While ESA is a space agency, the breach offers lessons for any organization with critical infrastructure or sensitive data.
Key takeaways:
-
External systems are not less important – Just because something's outside your corporate network doesn't mean it's okay to secure it less carefully.
-
Credentials in code is a nightmare – Treat credentials like passwords. Never put them in source code repositories, configuration files, or documentation.
-
Infrastructure as code is powerful but dangerous – Document configuration in code, but protect those files with the same rigor as source code.
-
One breach can enable the next – The 2024 web shop breach might have provided attackers with initial reconnaissance that led to the 2025 external server compromise.
-
Incident response takes time – Don't expect complete answers within days. Real investigations take weeks and months.
-
Classification systems are outdated – Security decisions shouldn't be based on whether something's "unclassified." Base them on actual risk and sensitivity.
-
Continuous monitoring is non-negotiable – Organizations without 24/7 security monitoring won't detect sophisticated breaches for months.
-
Partners are extensions of your security – If you integrate with external systems, those integrations need the same security rigor as internal systems.
The Investigation Continues
As of now, the ESA is still investigating. They've implemented initial security measures, notified stakeholders, and begun forensic analysis. But the full scope of the breach won't be known for weeks or months.
Key questions still pending answers:
- Which specific systems were compromised?
- How long did attackers have access before being detected?
- What systems did they access after the initial compromise?
- Were any systems modified or compromised beyond just data theft?
- Can the stolen data be verified as authentic?
- How did attackers initially gain access?
- Are there ongoing persistent access mechanisms?
- What's the estimated financial impact?
The investigation will reveal these answers, but transparency will likely be limited by:
- Law enforcement requests for confidentiality.
- Privacy regulations limiting what can be disclosed about affected individuals.
- National security concerns.
- Partner organization privacy.
- Ongoing legal proceedings.

Looking Forward: Space Security in a Threat-Rich World
The space industry is increasingly digital, increasingly interconnected, and increasingly targeted by sophisticated adversaries. ESA's breach is significant but not unique. It's part of a broader trend.
Future considerations for space agencies and their partners:
- Zero-trust architecture – Every access request is verified, regardless of whether it's internal or external.
- Quantum-resistant cryptography – Preparing for potential future quantum computing threats.
- AI-powered security – Using machine learning to detect anomalous behavior faster than humans.
- International security standards – Developing shared security practices across national boundaries.
- Supply chain security – Verifying that contractors and vendors meet security standards.
- Space debris monitoring – Just as we track physical debris in orbit, we need to track digital threats in cyberspace.
The security of space infrastructure matters because it's increasingly critical to:
- Global communications.
- Weather forecasting and climate monitoring.
- GPS and navigation.
- Scientific research.
- National security.
- Economic activity.
When space agencies are breached, the ripple effects extend far beyond the agencies themselves.
FAQ
What is the ESA cyberattack and when did it happen?
The European Space Agency (ESA) suffered a cyberattack on external servers on December 18, confirmed publicly shortly after. A threat actor using the alias '888' claimed responsibility and announced the theft of approximately 200 gigabytes of sensitive data, including source code, API tokens, CI/CD configurations, and internal documentation from the compromised external systems.
How did the attackers access ESA systems?
ESA's forensic investigation is still ongoing, so the specific initial access method hasn't been publicly disclosed. However, given the scope of data stolen and the types of systems compromised, likely entry vectors include unpatched vulnerabilities in publicly facing systems, compromised credentials obtained from the previous year's breach or from credential trading platforms, or weak authentication on external collaboration servers. Once inside, attackers appear to have moved laterally to access the sensitive repositories and configuration files.
What data was stolen in the breach?
The threat actor claims to have stolen 200GB of data including source code from private Bitbucket repositories, CI/CD pipeline configurations that reveal how software is built and deployed, API tokens and access credentials, internal documentation describing system architecture and procedures, Terraform infrastructure code defining cloud resources, and hardcoded credentials and configuration files that could provide direct access to systems. Independent verification of these claims is still pending from security researchers.
How does this compare to the 2024 ESA web shop breach?
The 2024 incident was a credit card skimming attack on ESA's e-commerce platform, where malicious Java Script was injected to capture payment card data from customers. The 2025 breach is more serious in scope and sophistication, targeting critical infrastructure systems rather than e-commerce. The proximity of these incidents within a year suggests either persistent vulnerabilities from the first breach, recurring attacker behavior, or opportunistic exploitation by multiple threat actors targeting a known-vulnerable organization.
What is the risk to organizations that partner with ESA?
Partner organizations face several risks: if their systems share authentication credentials with ESA systems, those credentials are potentially compromised and need immediate rotation; data shared through compromised external servers could be exposed; if partners integrate with ESA systems, attackers with access to ESA infrastructure could potentially pivot to those systems; and supply chain attacks are possible if the compromised code or infrastructure was used in systems provided to partners. Organizations should conduct security audits of their ESA interactions and tighten access controls accordingly.
Why is stolen source code such a serious problem?
Source code reveals exactly how systems work, where vulnerabilities exist, which systems use deprecated technologies, and how security controls are implemented. With access to source code, attackers can identify vulnerabilities in unpatched systems in minutes rather than spending weeks reverse-engineering binaries. They can understand the exact workflow and find workarounds or exploits. For ESA, this means attackers have a complete roadmap of system functionality and security mechanisms, enabling much more sophisticated and targeted attacks going forward.
What does ESA need to do to recover from this breach?
Recovery involves a multi-phased approach: immediate containment including forensic preservation and credential rotation within days; investigation determining the full scope and impact across weeks; remediation including system patching and rebuilding from clean backups across weeks to months; hardening implementing improved security controls and monitoring; and long-term improvement establishing a mature security program with adequate budget, staffing, and continuous testing. A thorough recovery typically takes 3-6 months or longer for an organization the size and complexity of ESA.
Should organizations worry about this breach affecting them?
Organizations should be concerned if they directly partner with ESA, integrate with ESA systems, or rely on ESA services. General organizations should be concerned from a broader security perspective, as the breach demonstrates vulnerabilities in critical infrastructure. All organizations should use the ESA incident as a reminder to audit their own external systems, rotate credentials, implement continuous monitoring, and ensure adequate security resources. It's a good catalyst for security hygiene improvement.
What is Breach Forums and why did the attacker post there?
Breach Forums is an online marketplace and forum where cybercriminals buy, sell, and trade stolen data and hacking services. Threat actors post there to establish credibility, advertise stolen data, negotiate with potential buyers, and build reputation within criminal communities. The threat actor posting the ESA breach on Breach Forums suggests they intend to profit from the data, either through direct sale or through auctioning it to the highest bidder, rather than using it for espionage or other non-financial purposes.
How can organizations protect against similar breaches?
Key protective measures include: treating external systems with the same security rigor as internal systems; never storing credentials in code or configuration files, using secrets management systems instead; implementing zero-trust architecture where every access request is verified; deploying continuous monitoring and intrusion detection systems; conducting regular vulnerability assessments and penetration testing; providing ongoing security awareness training; establishing incident response plans and running regular drills; rotating credentials regularly; and maintaining clean backups that can be used for recovery. Additionally, establish a mature security program with appropriate budget, staffing, and C-level support.

Conclusion
The European Space Agency's confirmation of the cyberattack represents a critical inflection point for how we think about security in critical infrastructure. This wasn't a minor incident affecting a backup system. This was a major breach of external systems supporting collaborative space research across the continent, resulting in the theft of 200 gigabytes of sensitive data including source code, credentials, and infrastructure documentation.
What makes this particularly significant is the context. ESA experienced a serious breach less than a year prior involving payment card data theft. The back-to-back incidents suggest systemic security challenges that haven't been adequately addressed. When organizations suffer multiple breaches within 12 months, it typically indicates either:
- Fundamental architectural vulnerabilities.
- Inadequate security staffing and resources.
- Lack of executive commitment to security improvements.
- Or some combination of all three.
The stolen data is extraordinarily valuable to potential adversaries. Source code provides a complete roadmap for exploitation. API tokens grant direct access to systems. Infrastructure documentation reveals network architecture and resource allocation. Credentials and configuration files could provide persistent access long after the breach is discovered.
The immediate priorities are clear: ESA needs to rotate all potentially compromised credentials immediately, begin forensic analysis to understand the full scope, patch all identified vulnerabilities, and implement comprehensive monitoring to detect any ongoing unauthorized access. Their forensic investigation will take weeks or months to complete, and recovery will extend further.
For the broader space community, this incident should trigger a reevaluation of security practices. Space agencies collaborate across borders, with universities, with private contractors, and through complex networks of external systems. When one major player is breached, the security of the entire ecosystem is potentially compromised.
The investigation continues, and we'll learn more as ESA completes their forensic analysis and shares findings with partners and the public. But one lesson is already clear: external systems are not secondary systems. They're not less important or less worthy of security investment. They're critical infrastructure that requires the same level of security rigor, monitoring, and incident response as any internal system.
Other organizations should view this incident as a wake-up call. If ESA, a well-resourced government space agency with sophisticated capabilities, can suffer a breach of this magnitude, no organization is immune. The question isn't whether you'll be targeted. The question is whether you're prepared when it happens.
Key Takeaways
- ESA confirmed external server breach on December 18 with threat actor claiming 200GB data theft.
- Stolen data includes source code, API tokens, CI/CD configurations, and infrastructure code enabling sophisticated future attacks.
- Back-to-back breaches within 12 months (2024 web shop, 2025 external servers) suggest systemic security vulnerabilities.
- External systems require same security rigor as internal infrastructure—ESA's emphasis on 'unclassified' systems is insufficient justification for weaker protection.
- Credentials and API tokens represent ongoing persistent access risk, requiring immediate rotation and audit of historical access logs.
- International space collaboration ecosystem faces ripple effects, requiring partner organizations to audit ESA system interactions.
![ESA Cyberattack: What You Need to Know About the 200GB Breach [2025]](https://tryrunable.com/blog/esa-cyberattack-what-you-need-to-know-about-the-200gb-breach/image-1-1767191893204.jpg)



