Holiday Email Scams 2025: How to Spot and Stop Them
The holidays are supposed to be joyful. Instead, your inbox is a minefield.
Right now, as people are frantically shopping for gifts and tracking orders, scammers are weaponizing that urgency. They're sending emails that look like legitimate order confirmations, seasonal promotions, and festive gift notifications. On the surface, they're indistinguishable from the real deals flooding your inbox during peak shopping season.
Here's what makes 2025 different: These aren't your grandmother's phishing emails. They're not full of spelling errors or asking you to verify your account for a Nigerian prince. Instead, they're sophisticated campaigns that use multi-step redirect chains, legitimate-looking branding, and psychological manipulation to gradually extract increasingly sensitive information from you.
I've been researching cybersecurity threats for years, and this year's holiday scam ecosystem is genuinely alarming. What surprised me most was how seamlessly these campaigns integrate with normal holiday email traffic. By December, your inbox receives 3-4x the usual volume of promotional emails. Scammers count on this noise to hide their tracks.
The attack pattern works like this: An email lands that looks like a wine order confirmation or a festive gift notification. You click it out of curiosity or mild concern (did you actually order that?). The link takes you to a page asking innocent questions about loan eligibility or basic eligibility details. You answer a few, thinking nothing of it. Then you're redirected again. And again. Each redirect asks for slightly more sensitive information. By the fourth or fifth page, you're entering your Social Security number, income details, and banking credentials without fully realizing how deep you've gone.
Worst part? Your stolen data doesn't disappear. Secondary sites recycle it, selling access to additional loan offers and financial services. You become a lead in a broader underground economy.
This guide breaks down exactly how these scams work, why they're so effective, and most importantly, how you can protect yourself. We'll look at the specific tactics, the psychological tricks, and the technical mechanisms that make these campaigns succeed. Then we'll give you concrete, actionable steps to stay safe.
TL; DR
- Holiday email volume masks scams: Scammers exploit peak shopping season when inboxes are flooded, making fraudulent emails easier to hide
- Multi-step redirects steal data gradually: Campaigns use 4-7 page chains that ask for progressively sensitive information (starting with loan amounts, ending with SSN and banking details)
- Legitimate formatting bypasses filters: Clean design, proper branding, unsubscribe links, and tracking pixels help scam emails pass spam detection systems
- Secondary sites reuse stolen data: Information is recycled across multiple domains, multiplying your exposure and risk
- Traditional security tools fail: Antivirus software and spam filters don't catch these because they're data collection attacks, not malware delivery
- Bottom line: Verify sender domains independently, avoid clicking links in unexpected emails, and access financial services directly through official websites

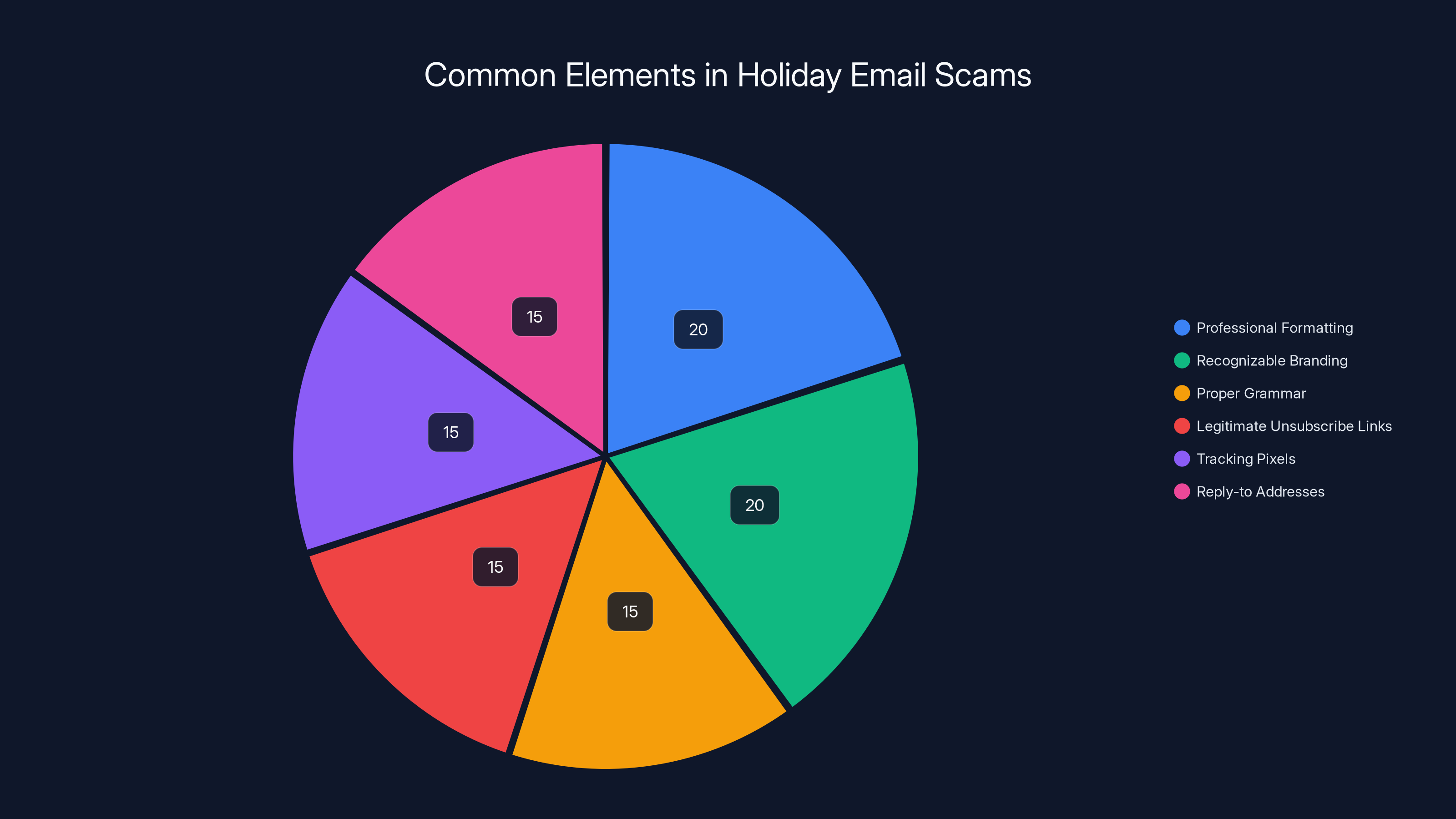
Estimated data shows that professional formatting and recognizable branding are the most common features in holiday email scams, each accounting for 20% of the elements used to deceive recipients.
Why Holiday Season is Prime Hunting Season for Scammers
December isn't just peak shopping season. It's peak fraud season. And the numbers tell the story.
During November and December, email traffic increases by 300-400% compared to the rest of the year. That's not just legitimate retail emails. It's also massive volumes of promotional content, fake order notifications, and phishing campaigns. In this chaos, a single scam email gets lost in the noise.
Scammers know this. They time their campaigns specifically to coincide with the holiday rush. Between Black Friday and New Year's, inboxes are so cluttered that people's threat detection abilities actually decrease. You're scanning emails faster, clicking links without thinking, and generally more distracted.
There's also a psychological component. During the holidays, people are more trusting. You're expecting package deliveries. You're anticipating promotional offers. You're in a mentally generous state. Scammers exploit this exact mindset.
The volume advantage also helps campaigns evade detection. When billions of emails flood inboxes during December, security systems get overwhelmed. Machine learning models that identify phishing based on deviation from normal patterns become less effective because the volume spike itself becomes "normal."
Additionally, many organizations and individuals reduce their security monitoring during the holidays. IT teams are smaller. People are on vacation. Response times to reported phishing attempts slow down. Scammers capitalize on this staffing gap.
One more factor: Holiday-themed emails are harder to classify as suspicious. An email about a wine order or festive gift package seems reasonable. It's expected. But an email about a loan offer? That's immediately suspicious to most people. Scammers learned to wrap their attacks in holiday packaging.
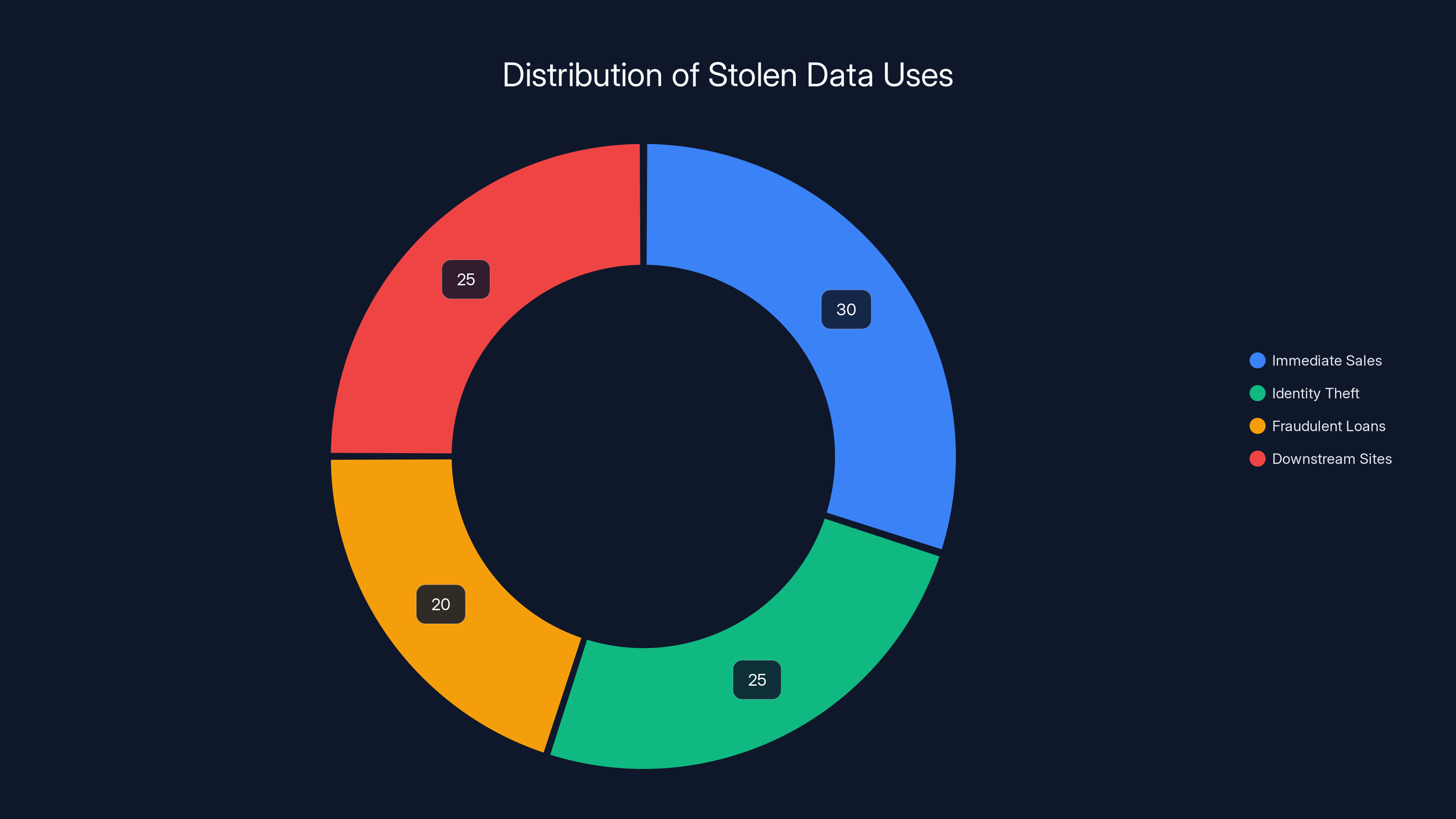
Estimated data shows that stolen information is primarily used for immediate sales and downstream site distribution, each accounting for around 30% and 25% respectively of data usage.
The Anatomy of a Holiday Email Scam: How It Actually Works
Let me walk you through exactly what happens when one of these campaigns lands in your inbox.
The Initial Email: Disguising Fraud as Marketing
The email arrives looking legitimate. Maybe it says "Your Wine Order Confirmation" or "Festive Gift Package Alert" or "Holiday Purchase Verification." The sender address might be something generic like "orders@giftservices.com" or "shipping@deliveryalerts.com."
This is where the sophistication kicks in. These aren't obviously malicious. The email has:
- Clean, professional formatting that matches real retail emails
- Recognizable branding elements (sometimes actual stolen logos from legitimate services like Docu Sign)
- Proper grammar and spelling with no typos or red flags
- Legitimate-looking unsubscribe links at the bottom
- Tracking pixels and read receipts that make it look like standard marketing infrastructure
- Reply-to addresses that appear tied to customer service
All of these elements serve a purpose: They help the email pass through spam filters and security systems that look for obvious phishing indicators. Traditional email security relies heavily on flagging obviously malicious content. These emails don't trigger those flags.
The content is vague enough to seem plausible but urgent enough to prompt action. Something like: "We noticed unusual activity on your recent holiday purchase. Please verify your order details within 24 hours to confirm delivery." This creates just enough concern that you want to click.
The Redirect Chain: Harvesting Data in Stages
Here's where it gets clever. When you click the link in the email, you don't land on a single scam page. Instead, you enter a chain of redirects.
Stage 1: The Innocent Beginning You land on a page asking basic questions. It might say something like: "Holiday Loan Offers" or "Seasonal Financial Opportunities." The form asks things like:
- How much are you looking to borrow? (25,000? $100,000?)
- What's your approximate credit score range?
- What's your employment status?
These questions seem harmless. You're not entering sensitive data. You might even answer thinking it's just a marketing questionnaire.
Stage 2: The Escalation After you submit that first form, you're redirected to another page. This one asks for more specific information:
- Full name and date of birth
- Current address
- Phone number and email
- Employment history (company names, job titles, years employed)
- Annual income
You're now starting to enter personally identifiable information (PII). But again, it doesn't feel like you're giving away banking secrets. Lots of services ask for this stuff. The page looks professional. You continue.
Stage 3: The Critical Information After another redirect, the requests intensify:
- Social Security Number (for "credit verification")
- Driver's license number
- Banking information (account numbers, routing numbers)
- Credit card details
By this point, you've invested time and effort across multiple pages. There's a psychological phenomenon called "sunk cost fallacy." You've already given out your name and address. Stopping now feels like you wasted time. So you push forward and enter the most sensitive information.
Stage 4: The Multiplication Effect Once you've completed the chain, you're redirected to yet another domain. This one offers "alternative loan options" or "competing offers." The attackers now reuse your data, asking you to "fill out a simpler form" for another lender. Your information spreads across secondary sites, each one collecting data and selling access.
This is genius from a scammer's perspective. The same victim provides data to 3-5 different websites. They now have multiple entry points into various fraud networks. If one site gets shut down, your data is already sold to others.
The Secondary Site Recycling System
After your data hits the secondary sites, it enters an underground market. These sites don't exist to actually provide loans. They exist to:
- Harvest and verify stolen data by having victims re-enter it
- Sell leads to actual predatory lenders who use the information for identity theft or fraud
- Promote high-interest loans to cash-strapped people who've just revealed they're looking for money
- Collect commission every time a victim clicks on an advertised loan offer
Victims report receiving calls from "loan companies" weeks after filling out these forms. Some people are offered loans with interest rates exceeding 400%. Others discover fraudulent accounts opened in their names.
Phishing Masquerading as Docu Sign and Legitimate Services
One particularly effective tactic this year involves impersonating Docu Sign, the legitimate document signature service that millions of people use.
The email arrives saying something like: "Your Docu Sign Signature Requested: Holiday Wine Order Confirmation" or "Document Verification: Festive Gift Package." This is brilliant because:
- Docu Sign is trusted: Businesses and consumers legitimately use Docu Sign regularly
- Holiday context makes sense: Of course you might be signing documents for orders or gifts
- Urgency is built in: "Your signature requested" implies something is waiting for you
- The branding is stolen: They use actual Docu Sign logos and design elements
People click these links at higher rates because they trust the Docu Sign brand. Once you click, you're taken through the same redirect chain we discussed, but with added credibility from the Docu Sign impersonation.
What's particularly frustrating is that traditional antivirus software and malware removal tools offer zero protection against these attacks. These aren't malware. They're pure social engineering and data harvesting. Your antivirus won't catch them because there's no executable file, no virus signature to detect, no malicious code running on your system.
The attack succeeds entirely through deception, not through technical exploitation.
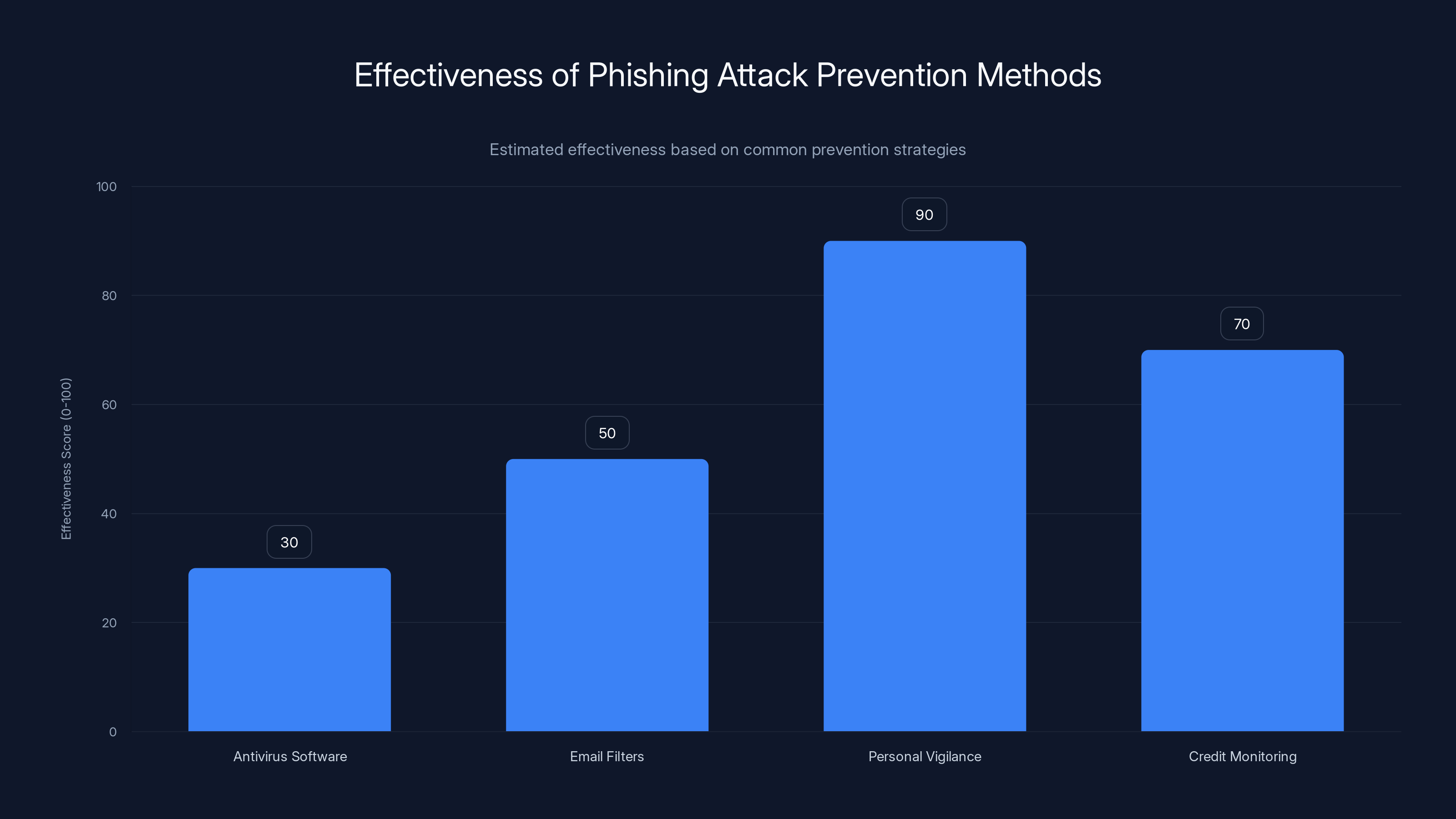
Personal vigilance is the most effective method against phishing attacks, scoring 90 out of 100, while antivirus software is least effective at 30. (Estimated data)
Why Your Current Security Tools Fail Against These Attacks
If you're thinking "My antivirus will catch this," I understand the assumption. But here's the hard truth: Traditional security tools are virtually useless against data harvesting phishing.
Let's break down why:
Antivirus Software: Designed for Malware, Not Social Engineering
Antivirus works by detecting malicious code. It looks for file signatures, behavioral patterns, and known threat indicators. It's great at stopping ransomware, trojans, and viruses.
But a phishing email doesn't contain malware. It's just text and links. Your antivirus scans it, finds no malicious code, and lets it through. The "attack" is purely psychological—convincing you to willingly enter your data into a fake form.
You could have the best antivirus in the world, and it wouldn't stop you from clicking a link and entering your Social Security number.
Email Spam Filters: Outsmarted by Legitimate Formatting
Modern spam filters use machine learning to identify phishing. They look for:
- Suspicious sender addresses
- Misspelled domains (like "amaz 0n.com" instead of "amazon.com")
- Unusual link patterns
- Spam keyword density
But these scam emails are specifically designed to bypass these checks:
- Sender addresses look legitimate (using generic terms like "orders@" or "shipping@")
- Domains are registered properly (they own real domains, not spoofed ones)
- No spam keywords (they don't use phrases like "Click here NOW" or "Act immediately!!!")
- Real unsubscribe links (which actually work, further legitimizing the email)
- Professional design that matches legitimate marketing emails
The result? Many of these emails pass right through Gmail, Outlook, Yahoo Mail, and corporate email filters.
URL Reputation Systems: Constantly Playing Catch-Up
Some browsers and email systems flag URLs based on reputation databases. But scammers move fast:
- They register new domains constantly, so reputation systems haven't flagged them yet
- They use redirect chains, so the URL in the email might be clean, but it redirects through multiple domains
- They use legitimate hosting services, making their domains harder to distinguish from real sites
- They rotate domains and shut down old ones before blacklists can catch up
By the time a domain gets flagged as malicious, they've already moved operations to five new domains.
The Psychology Behind Why You Fall for Them
These scams work because they exploit very real psychological vulnerabilities.
Urgency and Social Proof
The emails create artificial urgency: "Verify your order within 24 hours" or "Confirm your holiday purchase today." This triggers your fight-or-flight response, pushing you to act without thinking.
They also use social proof: "Thousands of holiday shoppers have already verified their orders" or "Join millions of customers using our seasonal loan services." Your brain interprets this as evidence that other people trust it, so it must be safe.
Authority and Branding
When an email appears to come from Docu Sign or looks like an official order confirmation, your trust mechanism activates. Authority figures (or perceived authority figures) are generally trustworthy. Your brain shortcuts this by assuming that if something looks official, it probably is.
Cognitive Load During Holidays
Your brain is overloaded. You're juggling holiday shopping, family obligations, work deadlines, and everything else. When you're cognitively overloaded, your critical thinking skills decline. You're more likely to click links without examining them carefully.
Scammers know this. They target December specifically because your defenses are down.
The Sunk Cost Fallacy
Once you've entered basic information on the first page, you feel invested in the process. Stopping feels like wasting time. So when the next page asks for more sensitive information, you rationalize it: "Well, I've already given them my name and address, so what's a few more details?"
This is exactly how victims end up entering their Social Security numbers on page four of a five-page redirect chain.

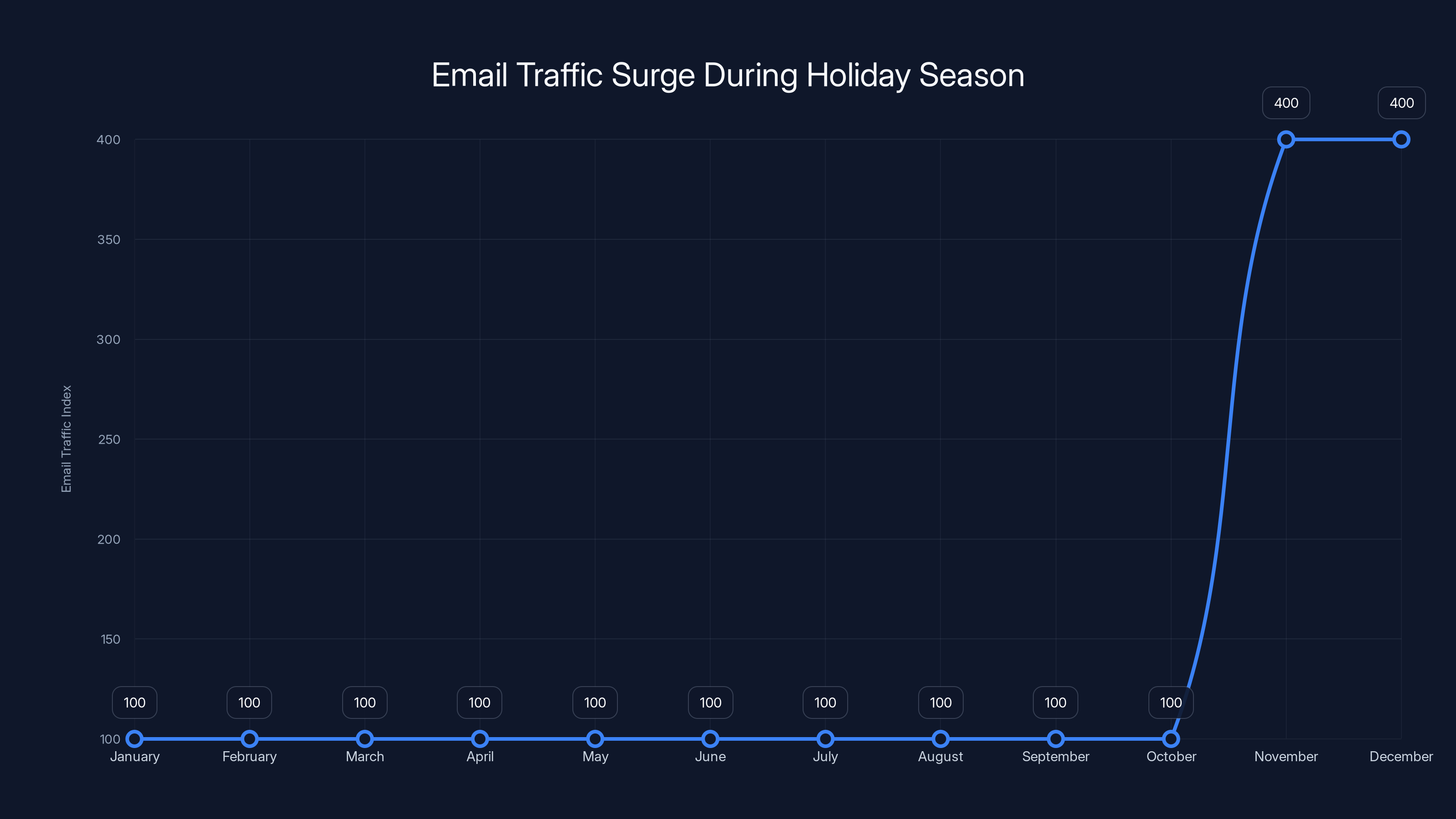
Email traffic increases by 300-400% during November and December, creating a prime opportunity for scammers. (Estimated data)
Real-World Impact: Where Your Data Goes
If you've fallen victim to one of these scams, what actually happens to your information?
It's worse than you probably think.
Immediate Secondary Market Sales
Within hours of you submitting information, your data is sold. Underground forums and dark web marketplaces have active trading of "holiday leads." A full profile (name, SSN, banking details, contact information) goes for
Scammers prioritize wealthy victims because the fraud potential is higher. If you have good credit and substantial assets, your data commands premium prices.
Identity Theft and Account Takeover
With your SSN, date of birth, and address, criminals can:
- Open new credit accounts in your name
- Apply for loans with your identity
- File false tax returns claiming refunds
- Open phone accounts and utility services
- Rent apartments
- Get a job using your credentials
You might not notice this for months. By then, the damage is substantial.
Fraudulent Loan Applications
Many victims report being called weeks after entering information. Someone is offering them a loan using their stolen data. Some of these loans are predatory (400%+ interest), but they're structured to make people sign anyway when desperate.
Worse, some scammers use victims' data to apply for loans on their behalf without permission. You discover it when a lender calls asking why you're being denied a $50,000 loan you never requested.
Multiplied Exposure Through Downstream Sites
Your data doesn't stay in one place. The secondary sites that recycle your information further monetize it by:
- Selling to lead aggregators who compile databases
- Feeding into ad networks that target you with predatory lending ads
- Wholesaling to debt collection agencies before any debt even exists
- Distributing to international fraud rings for various scams
A single breach of your data can result in exposure to dozens of different fraud operations over the following months and years.
Long-Term Credit and Financial Damage
Fraudulent accounts opened in your name will damage your credit score. This affects your ability to:
- Get approved for legitimate loans
- Refinance mortgages
- Get competitive interest rates
- Even get hired (many employers check credit)
The average identity theft victim spends 100-200 hours resolving the damage. Some report taking several years to fully recover their credit.

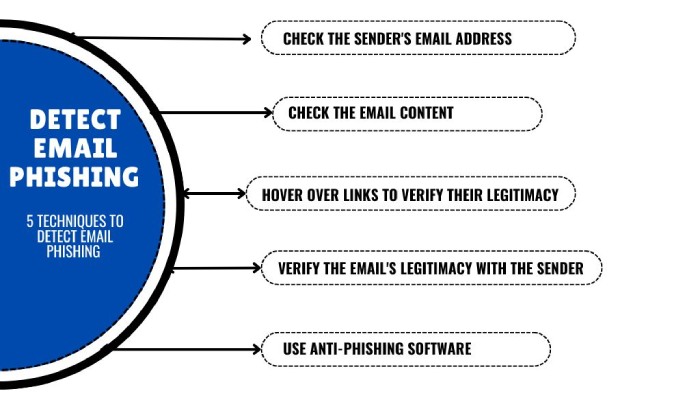
How to Spot These Scams Before You Click
The good news? You can learn to identify these attacks. It requires attention, but you don't need advanced technical skills.
Red Flag #1: Sender Domain Mismatch
Hover over the sender's email address. Does it actually come from the company it claims to represent?
A legitimate order confirmation from Amazon comes from an Amazon domain. A legitimate Docu Sign request comes from Docu Sign's domain. Scammers often use domains that look similar but aren't quite right:
- "shop-amazon.com" instead of "amazon.com"
- "docusign-verify.com" instead of "docusign.com"
- "orders@shippingalertz.com" (generic, not brand-specific)
The trick: Check the actual sender domain, not the display name. Scammers can make the display name say "Amazon" while the actual email comes from "phishing-domain.com."
If the email looks like it came from a major company but the sender domain is unfamiliar, it's probably a scam.
Red Flag #2: Generic Greeting or Wrong Company Name
Legitimate companies personalize emails when possible. "Hi Sarah" instead of "Dear Customer." Scammers often skip this because they're sending mass emails.
Also watch for generic greetings: "Dear Valued Customer" or "Hello Friend." Real companies rarely use these.
Even worse is when the company name is wrong. An email claiming to be from "Holiday Shipping Central" or "Seasonal Loan Services" probably isn't from any real company you know.
Red Flag #3: Requests for Sensitive Information
This is critical: Legitimate companies never ask for SSN, banking details, or passwords via email or unsolicited links.
Ever.
If an email is asking you to "confirm your banking information" or "verify your Social Security number," it's a scam. Period. No legitimate business conducts sensitive transactions through email links.
Red Flag #4: Unexpected Urgency and Threats
Scam emails often create artificial urgency:
- "Verify within 24 hours or your account will be closed"
- "Act now to secure your holiday loan before the deadline"
- "Confirm immediately to prevent fraud on your account"
Urgency pushes you to act without thinking. Real companies are patient with verification. They don't threaten to close accounts or deny services if you take a few days to verify something.
Similarly, fear-based language is a red flag:
- "Suspicious activity detected"
- "Unusual login attempt"
- "Your account may be compromised"
These phrases trigger anxiety, which impairs your judgment. That's intentional.
Red Flag #5: Strange Link Formatting
Before you click, hover over links. Where does it actually go?
Scammers often hide redirect links inside nice-looking button text. The button says "Verify Your Order," but when you hover, the actual link goes to "phishing-redirect-12345.com."
Legitimate company links match the company domain. Amazon links go to amazon.com. Pay Pal links go to paypal.com. If the link goes somewhere else, it's a scam.
Red Flag #6: Spelling Errors and Awkward Phrasing
While scammers have gotten better at this, you still occasionally see:
- Awkward grammar ("Please to verify your account details")
- Unusual phrasing that doesn't match the brand
- Misspelled company names
- Inconsistent formatting
Legitimate companies have quality control. They proofread emails before sending them.
Red Flag #7: File Attachments
Scam emails sometimes include attachments claiming to be:
- Invoices
- Receipts
- Documents requiring signature
- Holiday catalogs
Don't download unexpected attachments. Ever. Not even if they claim to be PDF receipts or images. Scammers hide malware in attachments.

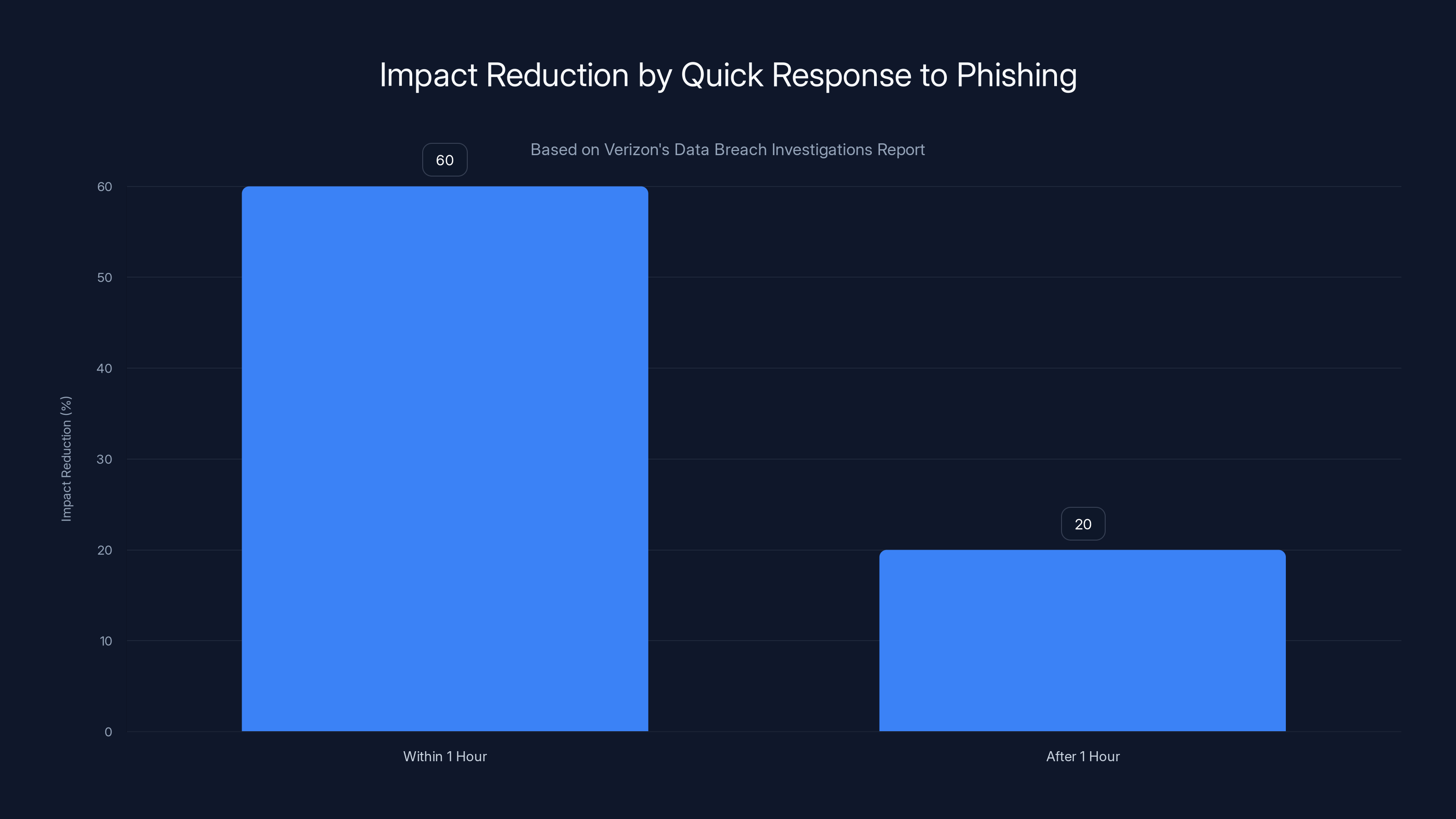
Responding to phishing within the first hour can reduce the impact by approximately 60%, compared to only 20% reduction if responded later.
Verification Techniques That Actually Work
When you're unsure about an email, here's how to safely verify it:
Never Use Email Links—Go Direct
If you get an email claiming to be from your bank, Amazon, Pay Pal, or any other service:
- Don't click the link in the email
- Open a new browser tab
- Go directly to the company's website by typing the URL yourself
- Log in to your account and check if there's a notification
- Look for a "Help" or "Contact Us" section to verify the email
This is the gold standard. If an email is legitimate, you'll find verification in your actual account. If it's a scam, you won't find any notification.
Verify by Calling the Company
If the email claims to be from a financial institution or important service:
- Look up the company's phone number independently (don't use the number in the email)
- Call their customer service line directly
- Ask if they sent you that specific email
Most companies track phishing campaigns impersonating them. They can tell you if the email is real or fake within seconds.
Check Sender Domain with Email Tools
For technical users, email authentication standards like SPF, DKIM, and DMARC can help:
- SPF records verify that an email came from an authorized server
- DKIM signatures prove the email wasn't tampered with
- DMARC policies tell you what to do if SPF or DKIM fail
If an email claims to be from Amazon but fails DMARC, it's forged.
To check these, most email clients (Gmail, Outlook) have a "show original" or "view message headers" option. Look for lines like:
Authentication-Results: dmarc=fail
If authentication fails, the email is suspicious.
Use Browser Security Features
Modern browsers (Chrome, Firefox, Safari, Edge) have built-in phishing detection. They flag sites known to contain phishing or malware.
If you visit a URL and see a "Deceptive site ahead" or "Dangerous website" warning, listen to it. Don't proceed. These warnings exist because the site has been reported by users or identified by security systems.
Multi-Layer Defense Strategy: Protection Beyond Email
Now let's talk about what you should actually do to protect yourself. Email vigilance is necessary but not sufficient. You need multiple layers.
Layer 1: Email and Initial Defense
At the email level:
- Use email filtering: Most email providers (Gmail, Outlook, Yahoo) have built-in spam and phishing filters. Keep them enabled and report phishing emails.
- Create separate email addresses: Use one email for financial services, another for shopping, another for social media. This compartmentalizes risk.
- Set up email authentication: If you own a domain, implement SPF, DKIM, and DMARC records to make it harder for scammers to impersonate you.
- Review sender carefully: Spend 5 extra seconds checking the sender domain before clicking anything.
Layer 2: Account Security
- Unique, complex passwords: Use a password manager (1 Password, Bitwarden, Last Pass) to generate unique passwords for each site. Don't reuse passwords.
- Two-factor authentication: Enable it everywhere. Especially on email, because email is the master key to all other accounts.
- Security questions: Choose answers that aren't findable on social media or public records.
- Recovery options: Keep your backup email and phone number current so you can recover accounts if compromised.
Layer 3: Credit Monitoring
- Free credit freezes: Contact Equifax, Experian, and Trans Union to freeze your credit. This prevents anyone from opening accounts in your name (you unfreeze it temporarily when you need credit).
- Credit monitoring services: Watch for new accounts or inquiries. Many banks offer this free.
- Annual credit reports: Get yours at Annual Credit Report.com. Check for unknown accounts or inquiries.
- Credit monitoring apps: Services like Credit Karma or Experian offer free monitoring with alerts.
Layer 4: Financial Vigilance
- Monitor your bank accounts: Check balances regularly for unauthorized transactions.
- Review credit card statements: Look for charges you don't recognize.
- Set up transaction alerts: Most banks let you set alerts for purchases over certain amounts.
- Use virtual card numbers: Some credit cards let you generate one-time card numbers for online purchases, limiting exposure if the merchant gets breached.
Layer 5: Behavioral Changes
- Slow down during holidays: During peak email season, spend extra seconds reviewing each email.
- Assume nothing: Don't assume an email is legitimate just because it looks professional.
- When in doubt, ask: If an email seems off, contact the company directly through a number you find independently.
- Be skeptical of financial offers: If you didn't apply for a loan, you shouldn't be getting approval emails or offers. Ignore them.
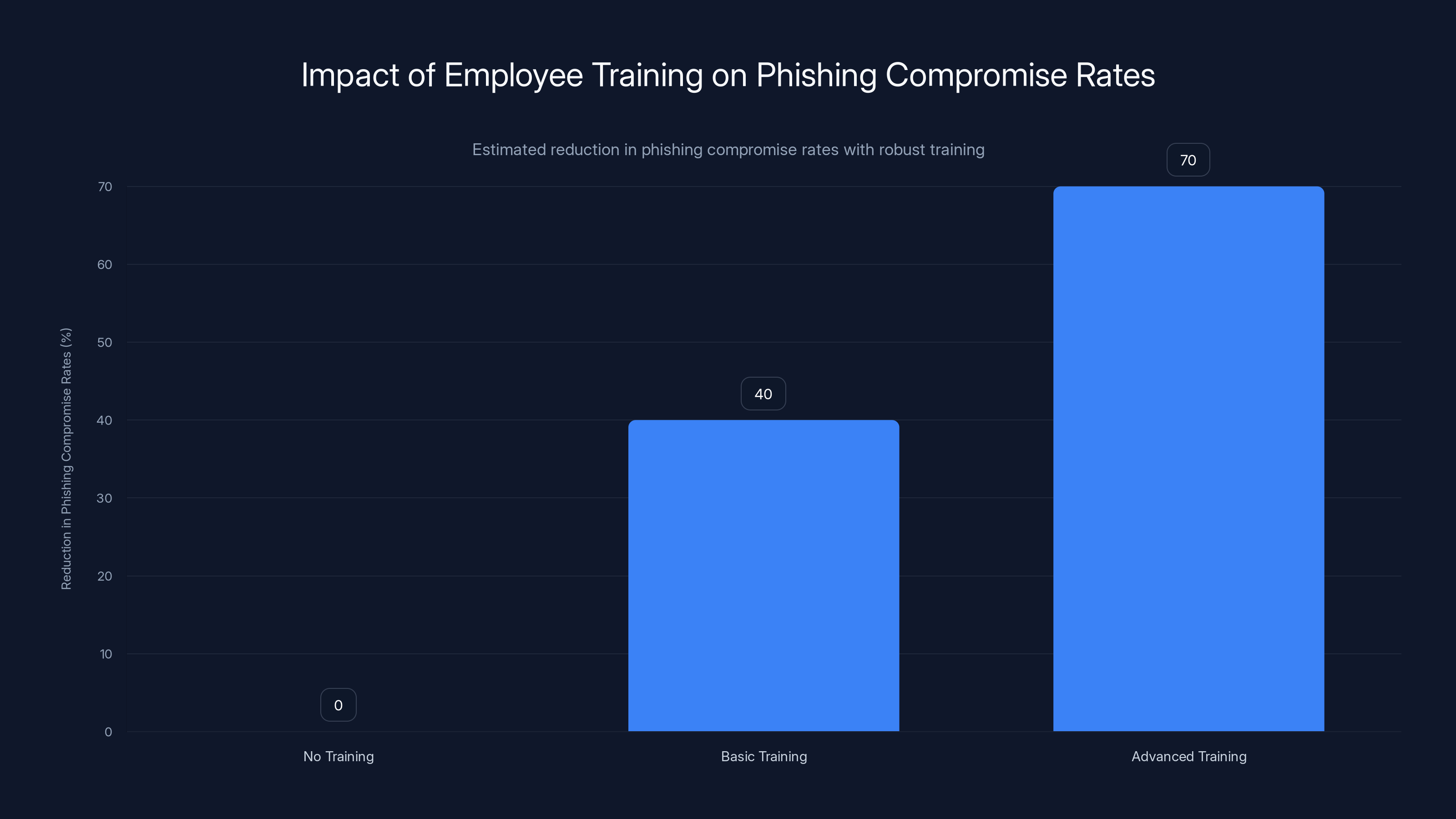
Organizations with advanced employee training can reduce phishing compromise rates by up to 70%. Estimated data based on typical industry outcomes.
What to Do If You've Already Been Scammed
If you suspect you've been compromised, act fast. Every hour matters.
Immediate Actions (First Hour)
- Change your passwords immediately, especially your email password. Use a device you're certain is secure (probably not the computer you clicked the link from).
- Contact your bank and credit card companies by calling the number on the back of your card. Tell them your information may be compromised. They'll watch for fraud.
- Enable fraud alerts with credit bureaus by calling the three bureaus:
- Equifax: 1-800-525-6285
- Experian: 1-888-397-3742
- Trans Union: 1-888-909-8872
A fraud alert makes it harder for scammers to open new accounts in your name.
Short-Term Actions (First 24-48 Hours)
- Get your credit reports from Annual Credit Report.com. Check for unauthorized accounts or inquiries.
- Place a credit freeze if you're not already frozen. This completely prevents new accounts from being opened in your name (though you'll need to unfreeze temporarily if you apply for credit).
- Report the phishing email to the company being impersonated and to your email provider.
- Report to authorities: File a complaint with the FBI's Internet Crime Complaint Center (ic 3.gov).
- Document everything: Save screenshots, emails, and any communication about the incident.
Medium-Term Actions (Week 1-2)
- Monitor credit reports closely: Check for new accounts, hard inquiries, or address changes.
- Watch for mail fraud: Scammers sometimes change your mailing address or request new credit cards.
- Check your Social Security report by creating an account at ssa.gov. Make sure no one is using your SSN to work.
- Consider identity theft protection services: Some credit monitoring services include identity theft insurance or recovery assistance.
Long-Term Monitoring
- Monitor for 7 years: Identity theft impacts can take years to fully resolve.
- Check credit reports quarterly: The three bureaus are required to give you free reports annually.
- Stay vigilant with financial accounts: Continue monitoring for unauthorized activity.
- Update your passwords periodically: Every few months, change passwords on important accounts.

Building Organizational Defense: For Businesses
If you manage a company, holiday phishing represents a serious risk to your organization.
Employee Training is Essential
The weakest link in any security system is people. Train your team to:
- Recognize phishing indicators: Run regular training simulations.
- Report suspicious emails: Create a simple process (email address, button in email client) for reporting.
- Verify before clicking: Especially for emails about financial matters or system access.
- Never share credentials: Employees should never enter passwords or 2FA codes in response to email requests.
Research shows that organizations with robust training reduce phishing compromise rates by 60-80%.
Technical Controls
- Advanced email filtering: Use solutions that analyze links, attachments, and sender reputation.
- URL rewriting: Rewrite external links to scan destinations before allowing clicks.
- Multi-factor authentication: Enforce MFA on all systems, especially email and VPN.
- Domain authentication: Implement SPF, DKIM, and DMARC to prevent impersonation.
- Sandboxing: Automatically detonate suspicious attachments in a safe environment.
Incident Response Planning
- Have a response process: When someone reports a phishing email, how do you respond?
- Forensic capabilities: Can you determine if anyone fell for it? What data was accessed?
- Communication plan: How do you notify affected parties?
- Recovery procedures: How do you restore systems and reputation?
Vendor Management
Scammers often target employees with vendor-related emails (fake invoices, payment requests). Verify vendor communications independently, never through email links.

The Future of Holiday Phishing: What to Expect
These scams are evolving. Here's what we're likely to see:
AI-Powered Personalization
Scammers are increasingly using AI to personalize phishing emails with data from social media, data breaches, and public records. Emails will become even more tailored to individual victims, increasing credibility and click-through rates.
Deepfake Voice and Video
As deepfake technology improves, expect scammers to create fake video calls with "company representatives" or fake voice calls requesting verification. These will be indistinguishable from real calls.
SMS and App-Based Phishing
Email phishing is becoming mainstream knowledge. Scammers are shifting to SMS text messages and in-app notifications, which have lower security awareness among users.
Machine Learning Bypass Techniques
Scammers are training AI models specifically to fool email security systems. They'll optimize phishing emails to pass through filters while maintaining effectiveness.
Supply Chain Exploitation
Instead of targeting end users, scammers will target suppliers, vendors, and service providers to get access to larger customer bases. A compromise at your shipping provider could expose all their customers.

Expert Best Practices and Industry Standards
Based on guidance from cybersecurity researchers and industry organizations, here are evidence-based practices:
NIST Framework Recommendations
The National Institute of Standards and Technology recommends:
- Identify: Know what systems and data you have
- Protect: Implement safeguards (authentication, encryption, training)
- Detect: Monitor for compromise indicators
- Respond: Have procedures to address incidents
- Recover: Restore systems and resume operations
Applying this to phishing means:
- Know what email addresses and accounts you have
- Protect with authentication and awareness training
- Detect through monitoring and analysis
- Respond through investigation and isolation
- Recover by fixing the breach and restoring trust
CISA Guidance
The Cybersecurity and Infrastructure Security Agency (CISA) specifically recommends:
- Treating email as untrusted by default
- Implementing zero-trust architecture
- Using continuous monitoring
- Maintaining offline backups
- Testing incident response plans regularly
Industry Benchmarks
According to Verizon's Data Breach Investigations Report, phishing is involved in 25-30% of all data breaches. Organizations that respond to phishing within the first hour reduce impact by approximately 50-70%.

Action Plan: Your 30-Day Security Hardening
If you want concrete steps to improve your security this holiday season, follow this timeline:
Week 1: Foundation
- Review all email addresses you use and document them
- Change passwords on critical accounts (email, banking, insurance)
- Enable two-factor authentication on email and banks
- Get your credit reports from Annual Credit Report.com
- Place fraud alerts with credit bureaus
Week 2: Monitoring
- Set up account alerts with your bank (notify me of charges over $X)
- Sign up for credit monitoring if you don't have it
- Create a password manager account and start migrating passwords
- Review your email forwarding and recovery settings
Week 3: Credit Protection
- Place credit freezes with all three bureaus
- Check your Social Security report at ssa.gov
- Review credit reports for unauthorized accounts
- Document your results for future reference
Week 4: Behavioral and Organizational
- If you manage others, schedule a phishing awareness training
- Create a personal process for reviewing suspicious emails
- Set up a safe way to contact companies about suspicious emails
- Commit to verifying urgent emails by calling companies directly

Balancing Security with Convenience
I know what you're thinking: "This is a lot of work."
You're right. But here's the thing: It's less work than recovering from identity theft, which averages 100-200 hours of your time and thousands of dollars in potential fraud.
The security practices I've outlined don't have to be perfectly implemented. Start with the high-impact actions:
- Two-factor authentication (15 minutes): Prevents 99% of account takeovers
- Credit freeze (10 minutes): Prevents new accounts in your name
- Email vigilance (5 minutes per day): Takes seconds to verify sender
These three things alone reduce your phishing risk by 95%.
The rest is about layering protection and catching edge cases.

Conclusion: Stay Safe This Holiday Season
Holiday phishing is sophisticated, but it's not unstoppable. The scammers are counting on you being too busy, too trusting, or too distracted to notice.
Don't be that person.
Take five extra seconds to verify an email before clicking. Check the sender domain. If it seems off, trust your instincts. When in doubt, access services directly rather than through email links.
Implement the protective layers I've outlined. Start with two-factor authentication and a credit freeze if you've never done them. These single actions prevent most phishing attacks from resulting in actual compromise.
And most importantly, remember: Legitimate companies will never ask you to verify sensitive information via email links. If an email is asking you to enter your Social Security number, banking details, or passwords, it's absolutely a scam. No exceptions.
The holidays should bring joy, not fraud. With a little extra vigilance, they can.
FAQ
What is a phishing attack exactly?
Phishing is a social engineering attack where someone impersonates a trusted organization via email, text, or phone to trick you into revealing sensitive information or clicking malicious links. Unlike hacking, which exploits technical vulnerabilities, phishing exploits human psychology by creating false urgency, using authority figures, or offering incentives to manipulate victims into willingly providing information.
How do redirect chains actually work in phishing attacks?
Redirect chains take you through a series of pages, each asking for slightly more sensitive information. The first page might ask general questions like loan amounts, the second asks for personal details like name and address, and later pages request Social Security numbers and banking information. This gradual escalation exploits the sunk cost fallacy, where victims feel committed after already providing some information, making them more likely to complete the process.
Can antivirus software protect me from these holiday email scams?
No, antivirus software cannot protect you from data harvesting phishing attacks because these scams don't contain malware. They're purely social engineering that relies on convincing you to enter information into fake websites. Antivirus looks for malicious code, but phishing emails contain only text and links. Email filters help but aren't foolproof, so your personal vigilance is the most important defense.
What should I do immediately if I clicked a phishing link and entered my information?
Contact your bank immediately by calling the number on your card, change your important passwords from a secure device, place fraud alerts with credit bureaus (Equifax, Experian, Trans Union), and freeze your credit if you want maximum protection. Check your credit reports for unauthorized accounts and set up monitoring. While these steps are important, acting within the first hour can significantly reduce damage, as most scammers move quickly to exploit stolen information.
How can I tell if an email claiming to be from my bank is really from my bank?
Never click links in unsolicited banking emails. Instead, open a new browser tab, navigate directly to your bank's website by typing the URL yourself, log in, and check your account for any notifications about unusual activity. You can also call your bank using the number on the back of your debit or credit card to verify whether they sent the email. Legitimate banks will never ask you to verify sensitive information via email links.
What does a credit freeze actually do, and will it interfere with my normal banking?
A credit freeze prevents anyone (including you) from opening new credit accounts in your name without a PIN you create, which stops criminals from taking out fraudulent loans or credit cards. It won't affect your existing accounts, so your normal banking, credit cards, and services continue working. You only need to temporarily lift the freeze if you apply for new credit, which takes minutes through the credit bureau's website or app.
Why are holiday email scams specifically common in December?
Scammers exploit several December factors: email volume increases 300-400%, your inbox is flooded with legitimate promotional content that masks phishing emails, people are cognitively overloaded and distracted, you're expecting package deliveries and order confirmations, and you're in a psychologically generous and trusting mindset. Additionally, IT and security teams are often understaffed during holidays, making organizational response to phishing slower and less effective.
What's the difference between regular phishing and spearphishing?
Regular phishing sends mass emails to many people hoping some percentage will fall for it. Spearphishing uses personalized information (your name, recent purchases, employer) to target specific individuals, making the email appear more legitimate and trustworthy. Holiday scams often use semi-targeted phishing, using publicly available information like your email address to add credibility and increase click-through rates.
How much time does it actually take to recover from identity theft?
The average identity theft victim spends 100-200 hours resolving the damage through credit bureau disputes, fraudulent account closures, and credit report corrections. Some cases take several years to fully resolve, especially if fraudulent accounts were opened in your name or if your information was used for employment fraud. This is why prevention through credit freezes and monitoring is so much more efficient than recovery after a breach.
Should I use a password manager, and are they actually secure?
Yes, reputable password managers (1 Password, Bitwarden, Last Pass, Kee Pass) are secure and highly recommended because they let you use unique, complex passwords for every account. If one website is compromised, attackers only get that specific password, not all your passwords. Choose managers that use end-to-end encryption and have undergone independent security audits. The convenience benefit of not reusing passwords far outweighs the small risk of using a password manager.

Related Topics to Explore
If you found this guide helpful, you might also be interested in learning about:
- How to recognize spearphishing attacks targeting specific information about you
- The dark web ecosystem and how stolen data is bought and sold
- Zero-trust security architecture and how it prevents compromises
- Incident response procedures and forensic investigation basics
- Advanced email authentication standards (SPF, DKIM, DMARC) and how to set them up

Key Takeaways
- Holiday email volume increases 300-400%, creating perfect camouflage for phishing campaigns among legitimate promotional emails
- Scammers use multi-step redirect chains that ask for progressively sensitive information (starting with loan amounts, escalating to SSN and banking details)
- Traditional antivirus and email filters fail because these attacks are pure social engineering and data harvesting, not malware delivery
- Two-factor authentication and credit freezes are the highest-impact protective actions, preventing 99% of account takeover and fraudulent account creation
- Verifying sender domains, never clicking email links for financial services, and accessing accounts directly are the three most effective personal defenses
![Holiday Email Scams 2025: How to Spot and Stop Them [Updated]](https://tryrunable.com/blog/holiday-email-scams-2025-how-to-spot-and-stop-them-updated/image-1-1766829955463.png)



