Introduction: When Your Smart Home Becomes Evidence
Last week, something happened that should make every smart home owner pause and think about what devices are actually recording in their homes. The FBI released footage from a Google Nest camera at Nancy Guthrie's front door, recovered from what they called "residual data located in backend systems." Not footage from the camera's local storage. Not from the homeowner's cloud account. From Google's backend servers, days after the device supposedly deleted the data.
This isn't a minor technical detail. It's a window into how smart home devices actually work, what data they retain, and who can access it.
When you buy a Nest camera or any connected smart home device, you're not just buying hardware. You're signing up for a complex ecosystem of cloud storage, data retention policies, law enforcement requests, and backup systems that most people don't understand. The devices record everything that happens in front of them. Some of that footage stays on your phone. Some goes to the cloud. And according to what the FBI just demonstrated, some stays in backend systems long after you think it's been deleted.
The Guthrie case is tragic, and the recovered footage could be crucial to finding her and prosecuting whoever took her. But it also raises uncomfortable questions that go far beyond this one incident. How long does your smart home data actually persist? Who can request it? What about cases that don't involve law enforcement? And most importantly, what should you do about it if you own these devices?
This article breaks down what happened, why it matters, and what you need to know about your smart home's privacy right now.
TL; DR
- FBI recovered Nest footage from Google backend systems, not from local storage or the user's cloud account, after the video was presumed deleted
- Smart home devices retain data far longer than users realize, often in residual or redundant backend systems for disaster recovery and compliance purposes
- Google confirmed law enforcement cooperation, raising questions about data access policies and user transparency
- Residual data recovery is common in digital forensics, but most consumers don't know their devices maintain backups
- Bottom line: Smart home privacy depends on understanding retention policies, deleting accounts properly, and knowing your legal rights when law enforcement requests device data
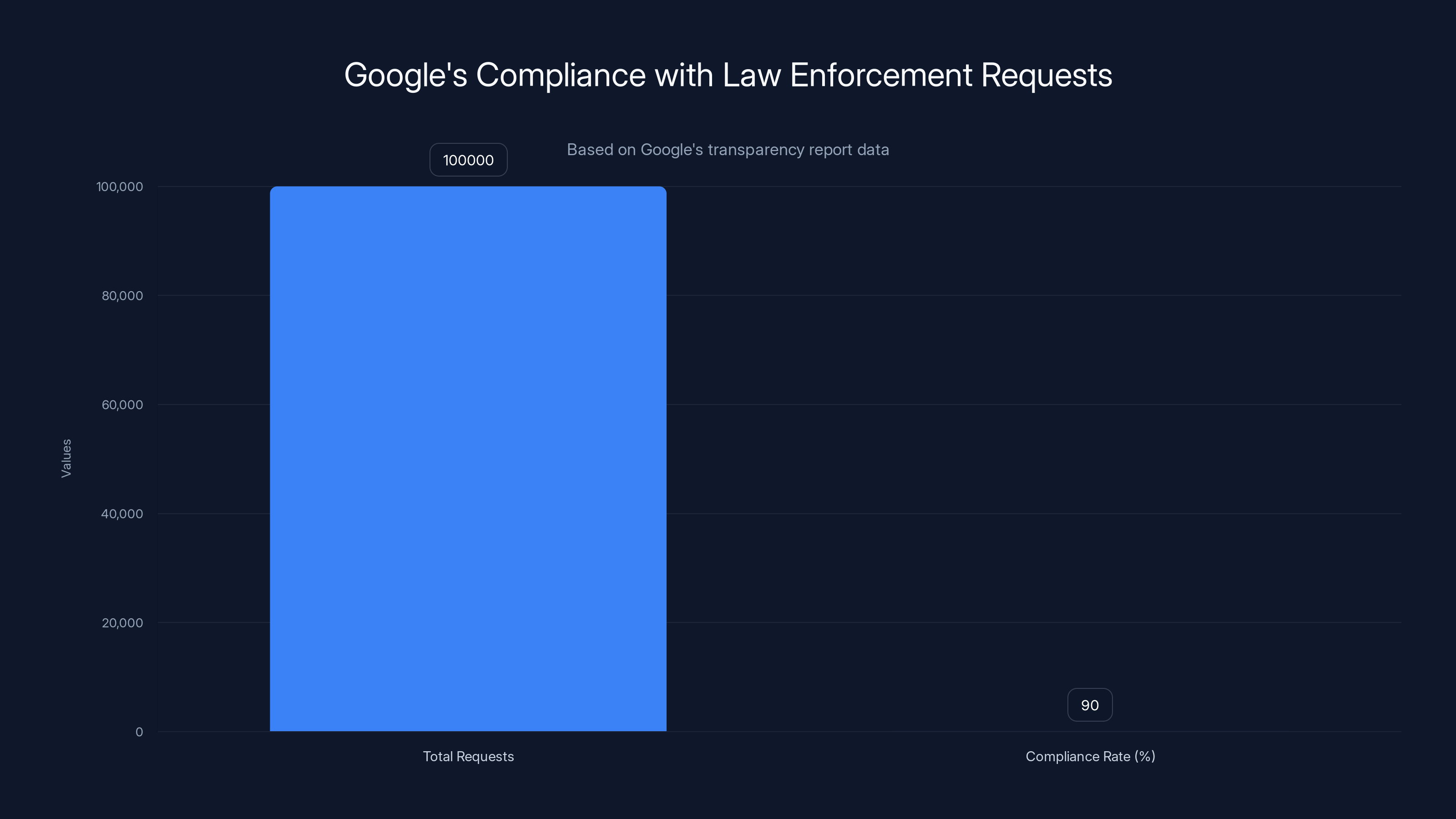
Google received over 100,000 requests from law enforcement and complied with over 90% of them, highlighting their cooperative stance.
What Actually Happened: The Nancy Guthrie Case
Nancy Guthrie disappeared from her Arizona home on the evening of January 31st. She's described as a vulnerable adult who has difficulty walking, has a pacemaker, and requires daily medication for a heart condition. Hours and days passed. Her family contacted authorities. Then, someone sent ransom letters to media outlets demanding millions of dollars in Bitcoin.
With no suspects identified and limited leads, law enforcement turned to digital forensics. The Nest camera at her front door had captured something. But here's where the story gets interesting: the footage wasn't readily available in Guthrie's account or on the device itself. The FBI had to recover it from Google's backend systems.
FBI Director Kash Patel announced the recovery on social media, explaining that law enforcement had been working with "private sector partners" and that the video was "recovered from residual data located in backend systems." Google's Patrick Seybold confirmed to media outlets that the company was "assisting law enforcement with their investigations."
The released footage shows a masked individual with a backpack approaching the camera, holding a glove in front of the lens while apparently touching something below it, then picking up something from the yard. A second video shows the individual trying to cover the lens with leaves. Still images were also released.
The case is now a federal investigation with a $50,000 reward for information leading to Guthrie's recovery or the arrest of those involved. But for anyone who owns a smart home camera, the technical details of how law enforcement recovered that footage are far more important than the ransom demand. They reveal how your devices actually work.

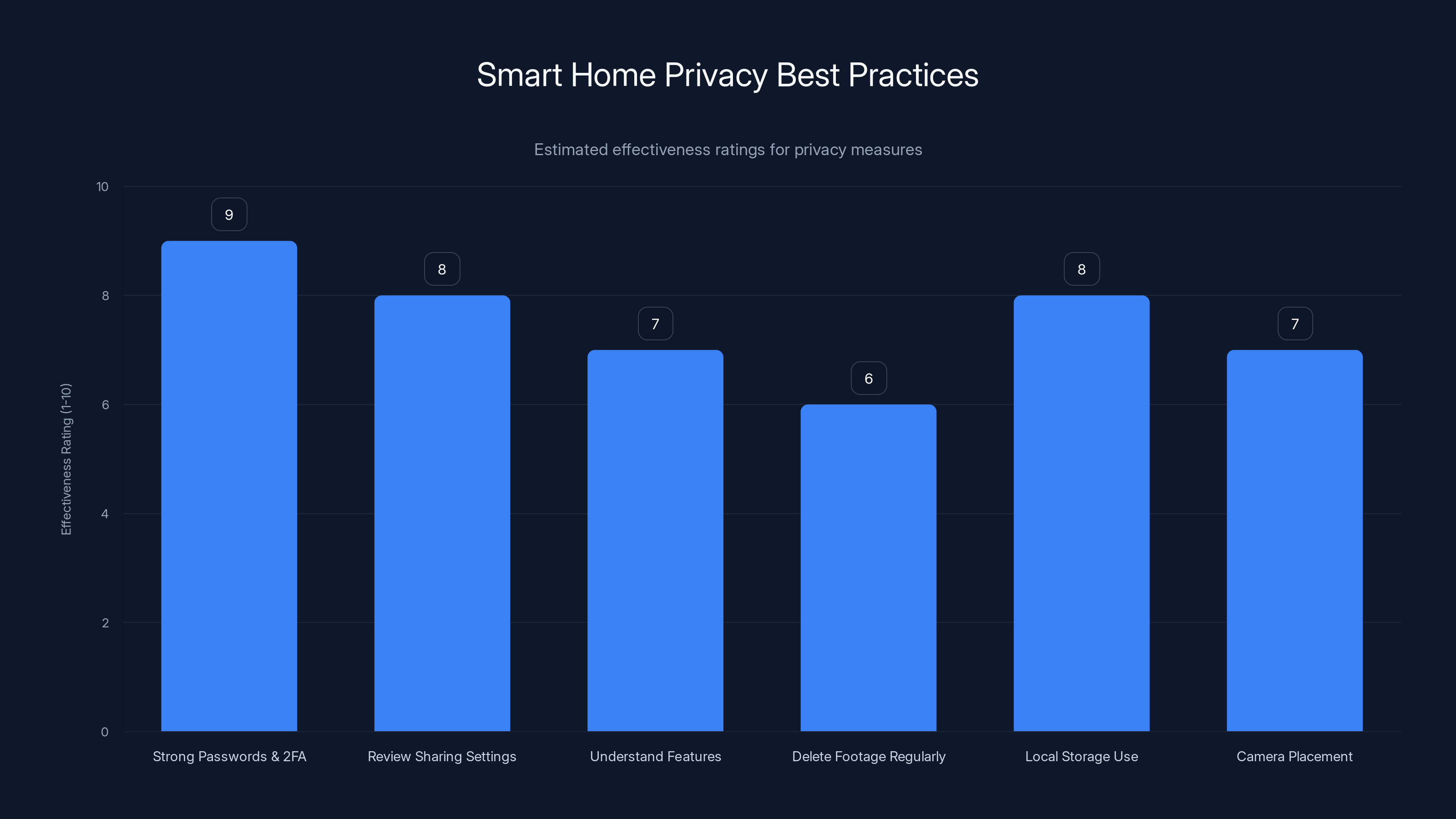
Using strong passwords and two-factor authentication is the most effective privacy measure, rated at 9 out of 10. Regularly reviewing sharing settings and using local storage are also highly effective, both rated at 8. (Estimated data)
Understanding Smart Home Data Architecture
Most people assume their Nest camera works like this: you press delete, the footage disappears. In reality, it's far more complicated.
When you record video on a smart home device, that data travels through multiple systems simultaneously. The live feed goes to your phone or computer. The recordings are stored locally on the device itself, usually on an encrypted SD card or internal flash memory. At the same time, the footage is being uploaded to Google's cloud servers. Some of it is being indexed for search functionality. Some is being backed up to redundant storage systems across multiple data centers for disaster recovery.
When you delete a recording from your account, what actually happens? The entry in the database is marked as deleted. Your access to it is revoked. But the underlying data often remains on the physical servers, just marked as "available for overwrite." Until that space is actually reused, the data can theoretically be recovered. This is true for any cloud service, not just Google. It's why hard drive recovery services exist. It's why your deleted emails can sometimes be retrieved.
Google maintains this redundant storage for legitimate reasons. If a data center fails, if there's a natural disaster, if there's a ransomware attack, the company needs to be able to restore your data. Customers expect 99.99% uptime. That requires backups. Multiple backups. Distributed across geographies. And those backups persist for a specific retention period, even after you think you've deleted something.
The FBI's recovery of the Guthrie footage suggests they had legal authority to request this data and that Google complied. Whether this happened through a standard subpoena, a warrant, or emergency provisions under law enforcement statutes, we don't know. But the process itself is likely routine. Law enforcement can request data from cloud providers. Providers often retain data longer than users realize, specifically because they know law enforcement might ask for it.

How Google's Data Retention Works
Google's privacy and retention policies are dense, technical documents that most users never read. But they matter. A lot.
When you set up a Nest camera on Google's infrastructure, you're agreeing to a specific terms of service. That service includes cloud storage, and the fine print explains what happens to your data. The company stores video footage in cloud servers. It creates backups. It maintains those backups for a specific period of time. The exact retention window varies depending on your subscription tier and the type of content.
For free-tier users, Google typically stores 3 hours of event footage that you can access through your account. But behind the scenes, more data exists. Google has historical data going back further. It has redundant backups. It has disaster recovery systems. Much of this exists outside the customer-facing interface.
When you delete a video from your Nest app, you're deleting it from your accessible library. You're not necessarily deleting it from every Google server. The data might persist in backup systems, in distributed databases, in archival storage. From Google's perspective, this makes sense. They need to be able to restore customer data if something goes wrong. They need to comply with legal holds when there's ongoing litigation or investigation. They need to keep data for compliance with regulations like GDPR, CCPA, and others that often require data retention for specific periods.
But from a user's perspective, this is opaque. You delete something, you expect it to be gone. The FBI's recovery of residual Nest footage shows that expectation is wrong.

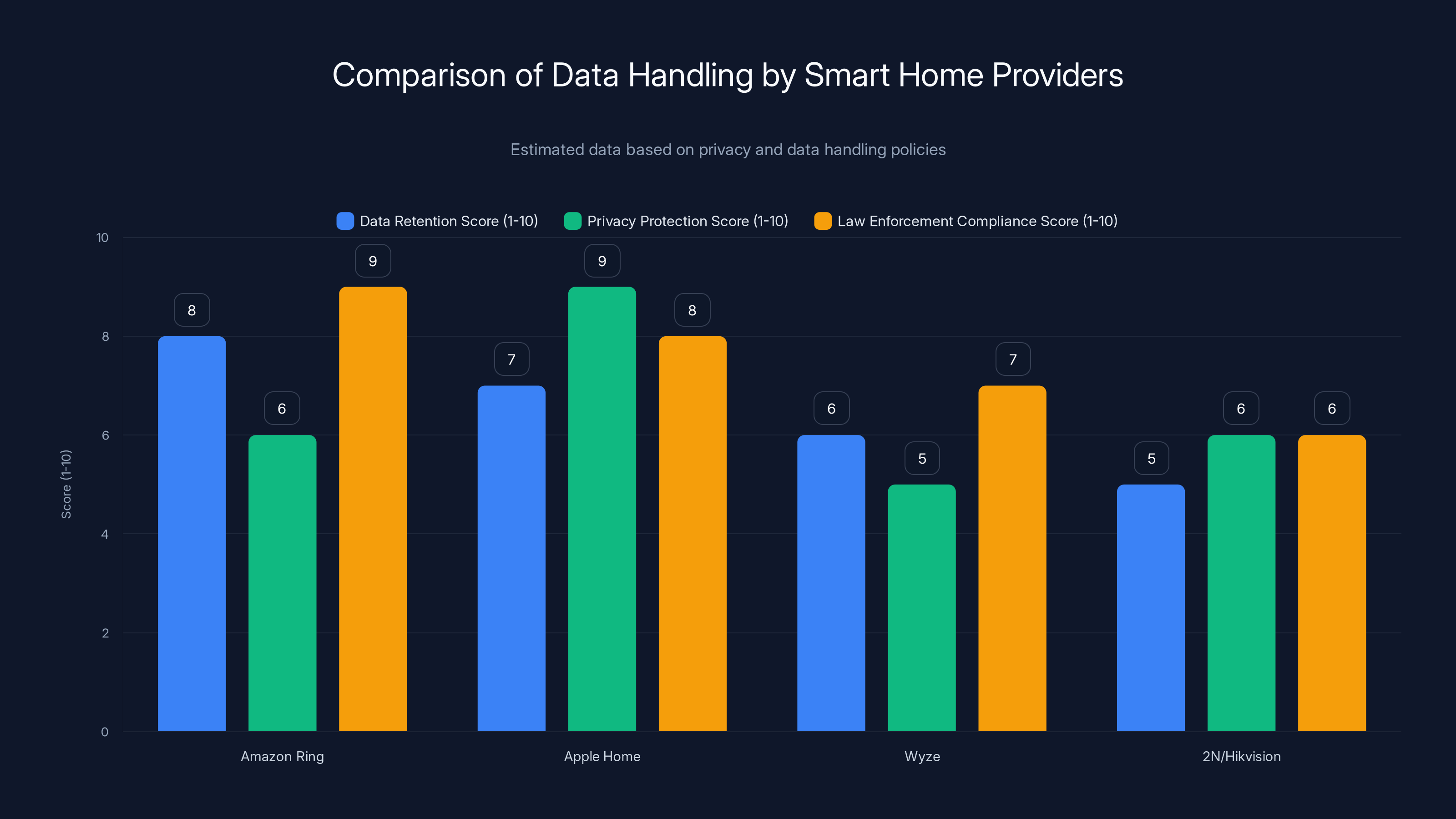
Estimated data shows Amazon Ring has high data retention and law enforcement compliance scores, while Apple Home leads in privacy protection. Estimated data.
The Law Enforcement Access Question
How did the FBI actually get this data? Google's statement that they're "assisting law enforcement with their investigations" is vague. It could mean several things.
First possibility: Warrant with immediate access. Law enforcement obtained a warrant, presented it to Google, and Google provided the data directly. This is the formal, legally required process. Google has protocols for handling warrants from federal agencies. A lawyer probably reviewed it. Google probably logged it. This is standard procedure.
Second possibility: Subpoena with compliance. Law enforcement issued a subpoena requesting the data, and Google complied without requiring a warrant. The rules around when companies can be subpoenaed without a warrant are complex and vary by jurisdiction. But many companies do honor subpoenas from federal agencies without additional legal process.
Third possibility: Emergency provisions. Under 18 U. S. C. Section 2702, companies can disclose customer data to law enforcement without legal process if they reasonably believe there's an emergency involving immediate danger. A missing person case with a potential abduction could qualify. Google might have provided the data under emergency protocols.
Fourth possibility: Assistance without legal process. Some companies voluntarily assist law enforcement with investigations by providing data beyond what's legally required. This happens more often than people realize. Some companies have dedicated law enforcement liaison teams.
We don't know which path Google took. The company didn't specify. But the key point is this: the legal threshold for law enforcement to access your smart home data might be lower than you think. If there's an emergency, if there's a warrant, if there's a subpoena, the company can probably give law enforcement your footage.

The Privacy Policy Fine Print
Google's privacy policies for Nest cameras are comprehensive, which is both good and bad. Good because the company is transparent about what data is collected. Bad because most people don't read them, and they're written in legal language that obscures what actually happens with your footage.
Here's what Google's privacy documentation actually says about Nest data:
Collection: Google collects video, audio (if the camera has a microphone), motion and sound detection data, device diagnostics, Wi-Fi information, and your account credentials. If you use any Nest features like person detection or activity zones, additional machine learning data is collected.
Storage: Video is stored on Google's servers. The company doesn't specify exactly how long, but indicates it depends on your subscription and account settings. The policy says Google retains data necessary for providing the service and to meet legal obligations.
Sharing: Google says it shares data with third parties in specific cases. These include: (1) when you share access with another person, (2) when law enforcement requests it, (3) when it's necessary to protect safety or security, (4) when required by law, and (5) when you consent.
Deletion: Google says you can delete videos from your account. The policy states that data deletion happens "in accordance with our data retention practices." This is vague. It doesn't say when data is truly erased from all systems.
Law Enforcement: Google's transparency report, published semi-annually, shows that law enforcement requests data from Google properties regularly. In the last published report, Google received tens of thousands of requests for data from law enforcement agencies worldwide. Google says it complies with legal requests. The company doesn't publicly detail which requests were granted, which were denied, and whether customers were notified.
The most important thing to understand: you don't own your Nest footage. Google does. You have a license to view it, to access it, and to manage it through your account. But Google controls the underlying data. Google decides how long it's kept. Google decides when to comply with law enforcement requests. Your privacy depends on Google's policies and Google's judgment about what constitutes a legitimate request.

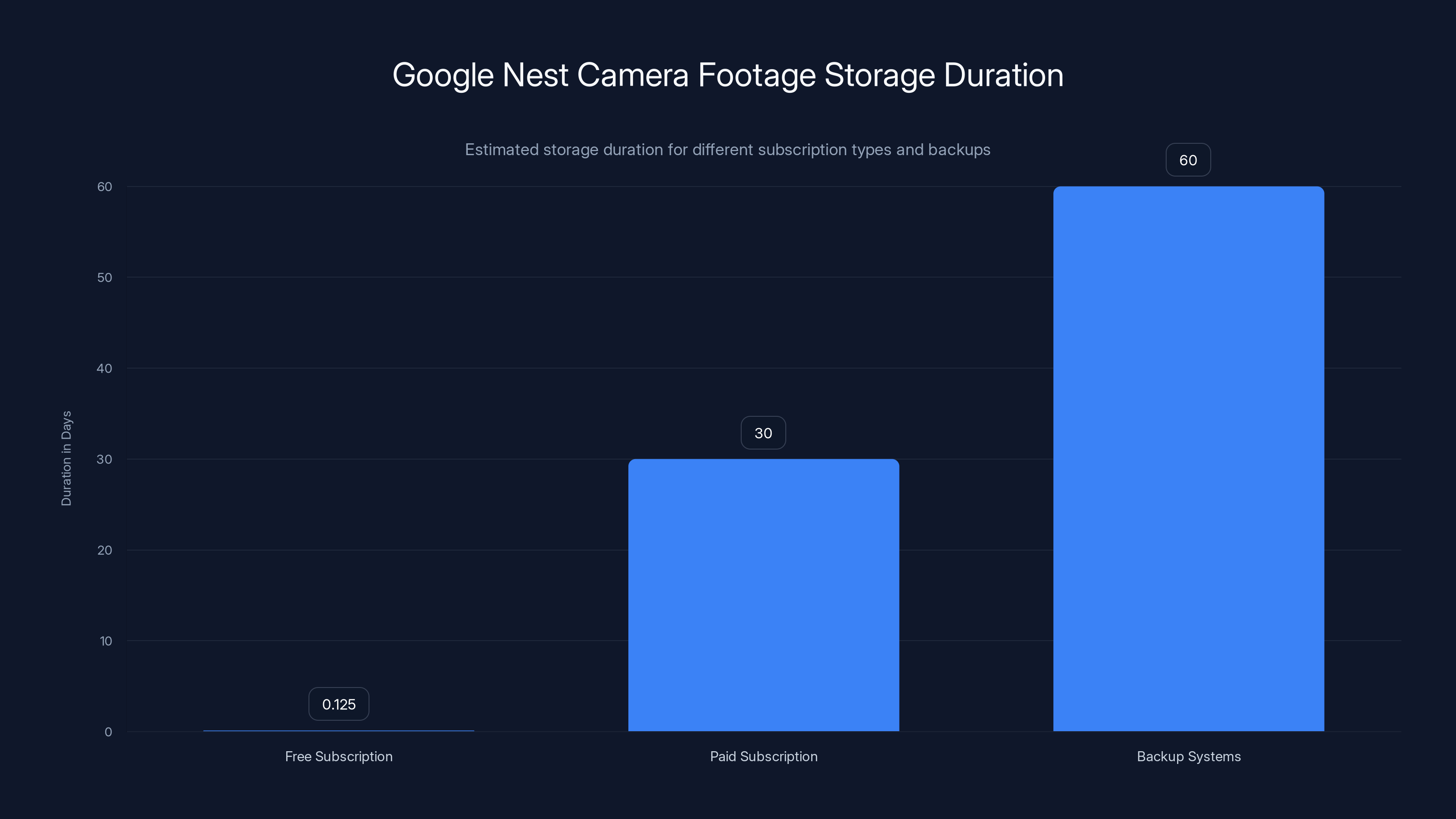
Google stores Nest camera footage for 3 hours with a free subscription and longer with paid plans. Backup systems may retain data for 30-90 days. Estimated data.
Residual Data and Digital Forensics
The term "residual data" is key here. When the FBI said they recovered footage from "residual data located in backend systems," they were using technical language that has specific meaning in digital forensics.
Residual data is data that remains on a storage system after deletion. When you delete a file, the operating system doesn't usually erase it completely. Instead, it marks the space as available for reuse. Until that space is actually overwritten with new data, the old data can be recovered using forensic tools. This is how forensic specialists recover deleted files from hard drives. This is how law enforcement recovers deleted text messages and emails.
In the context of cloud storage, residual data works similarly but at a larger scale. When Google's systems process a deletion request, the data might be marked as deleted in the user-facing database. But on the physical storage systems, the actual file might still exist. It might persist in backup systems. It might exist in redundant copies across multiple data centers. Until all those copies are overwritten, the data can theoretically be recovered.
Google's backend systems are sophisticated. The company uses something called "garbage collection" to identify and reclaim unused storage space. But garbage collection takes time. It's not instantaneous. There's a window, perhaps days or weeks, where deleted data technically still exists on physical drives, even if it's inaccessible to the customer.
This is true not just for Google, but for every major cloud provider. Amazon Web Services, Microsoft Azure, Dropbox, One Drive—all of them maintain residual data for periods of time after deletion. All of them can provide that data to law enforcement if legally required. This is a standard feature of cloud infrastructure, not a bug in Google's system.
The forensic recovery of data from backend systems is well-established in the industry. The FBI has forensic labs with specialists trained in cloud data recovery. When law enforcement suspects that deleted footage might be critical evidence, they request it from the provider. The provider, if legally obligated, retrieves it from backup systems or residual storage and provides it.

The Data Retention Timeline
Understanding how long your data actually persists is crucial to understanding the privacy implications.
Google doesn't publish a clear data retention schedule that customers can access. The company's privacy policies are intentionally vague about exact timelines. But based on industry standards and public information, here's what likely happens:
Immediate (0-24 hours): Your video is recorded and uploaded to Google's servers. Multiple copies exist simultaneously. Live streaming to your phone uses one set of systems. Cloud storage uses another. Backup systems create additional copies.
Short-term (1-30 days): Your accessible footage remains in your account. You can view it, delete it, or share it. Simultaneously, Google maintains redundant copies in backup systems. These exist for disaster recovery. If a data center has an outage, Google can restore from backups.
Medium-term (30-90 days): Even after you delete footage from your account, residual data exists on backend systems. It's not immediately overwritten. It persists in the same way deleted files persist on a hard drive before being overwritten.
Long-term (90+ days): Most of the accessible data should be truly gone. But Google might retain aggregate metadata, hashed versions, or machine learning models trained on the footage. The raw video data is probably overwritten by then.
But here's the complication: legal holds. If Google receives notice that data might be relevant to litigation or investigation, the company is legally required to preserve that data. Automatic deletion stops. The data is flagged and held until the legal matter is resolved. This can last months or years.
When the FBI requested the Guthrie footage, if the request came soon after deletion, Google could likely retrieve it from backup systems. If it came later, Google might have had to use forensic techniques to recover it from residual space. Either way, the technical capability exists.

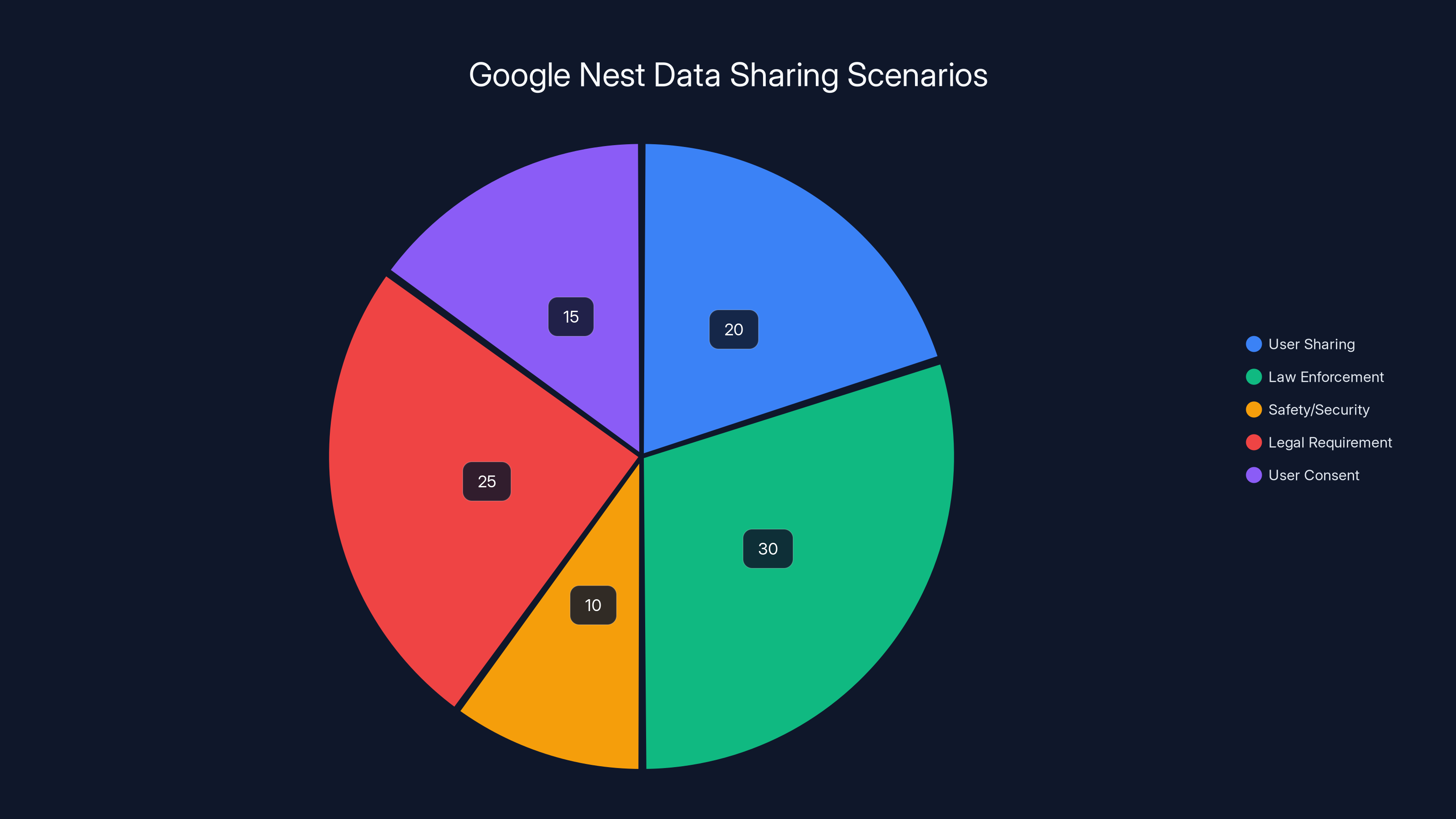
Estimated data shows that law enforcement requests account for a significant portion of data sharing scenarios, highlighting the importance of understanding privacy policies. Estimated data.
Comparison: How Other Smart Home Providers Handle Data
Nest is part of Google. But there are other smart home camera options. How do they compare?
Amazon Ring: Amazon's Ring cameras work similarly to Nest. Video is stored in the cloud. Amazon maintains backups. Ring's privacy policy says data is retained "as long as your Ring account is active." After account deletion, Amazon says data is "typically" deleted within 30 days. But similar to Google, the policy doesn't detail residual data or recovery capabilities. Amazon also complies with law enforcement requests and publishes a transparency report showing thousands of requests annually.
Apple Home: Apple positions itself as privacy-first. Home Kit Secure Video is designed to process video locally on an Apple TV or Home Pod, encrypting data so Apple can't see it. But video still goes to i Cloud for backup and accessibility features. Apple's privacy policies say Home Kit data is encrypted end-to-end. But end-to-end encryption doesn't prevent law enforcement access if Apple holds decryption keys or if law enforcement has proper legal authority.
Wyze: Wyze is a budget option. Their policies are simpler. Videos are stored in cloud storage. The company says they comply with legal requests from law enforcement. But Wyze is smaller than Google or Amazon, with fewer resources for sophisticated backup and recovery systems.
2N/Hikvision: These are enterprise security camera solutions. They allow more local storage options, which gives users more control. But many businesses still use cloud backup, which reintroduces the same residual data issues.
The pattern is consistent across the industry: all cloud-connected smart home cameras retain data longer than users realize, all are subject to law enforcement requests, and all maintain backup systems that preserve data even after deletion.
None of this is inherently wrong. Backup systems are necessary. Law enforcement access to evidence in criminal investigations serves a purpose. But users should understand what they're agreeing to.

Law Enforcement Requests: What's Legal?
The question of what law enforcement can legally request from tech companies is complex and varies by jurisdiction, but some principles are clear.
Warrants: If law enforcement obtains a warrant from a judge based on probable cause, they can request data from companies. The company is obligated to comply. The warrant must be specific about what data is requested and why. For the Guthrie case, law enforcement probably obtained a warrant to search for all data related to the front door camera.
Subpoenas: A subpoena is a court order requiring testimony or production of evidence. Prosecutors can often issue subpoenas with less legal justification than a warrant requires. Companies sometimes comply with subpoenas, sometimes challenge them. It depends on the jurisdiction and whether the subpoena is too broad.
Emergency Exceptions: Under federal law and most state laws, companies can disclose customer data to law enforcement without a warrant if there's an immediate risk of death or serious injury. A missing person case, especially one involving potential abduction, likely qualifies. Google might have provided data under emergency provisions.
Consent: If the person whose data is being requested consents, companies can provide it without legal process. In the Guthrie case, her family likely consented to law enforcement accessing her account data.
Stored Communications Act: Federal law (18 U. S. C. Section 2702) governs when companies can disclose electronic communications. The rules differ for contents of communications versus metadata. Law enforcement and companies interpret these provisions differently, which is why there's ongoing litigation about what constitutes proper legal process for data access.
What's important to understand: the law is not settled. Tech companies often comply with law enforcement requests that might not withstand legal challenge. Civil liberties organizations argue that some requests exceed what's legally permitted. But companies usually err on the side of compliance rather than risk facing obstruction charges.
If you're concerned about law enforcement access to your smart home data, know that you have limited legal recourse once law enforcement has requested it with proper legal process. You can't tell Google "don't give my data to the FBI" if the FBI has a valid warrant. Your legal protections come from the Fourth Amendment protection against unreasonable searches, which applies to the initial police action, not to subsequent requests to companies.

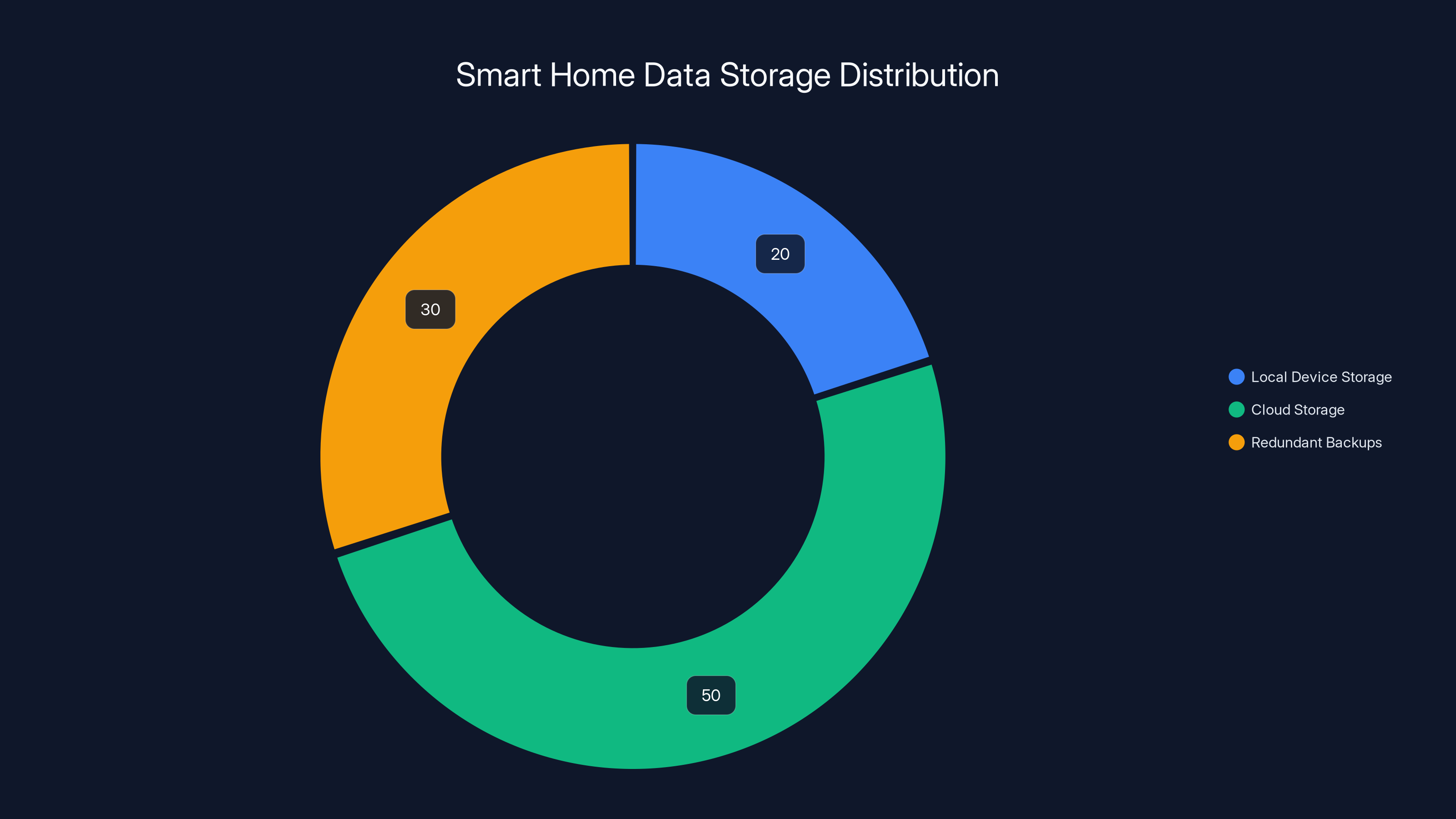
Smart home devices typically store 20% of data locally, 50% in the cloud, and 30% in redundant backups. Estimated data.
What Google's Response Reveals About Big Tech
Google's statement that it's "assisting law enforcement with their investigations" is revealing. The phrasing is important. Google didn't say "we were compelled to provide data." It said they're "assisting." This suggests voluntary cooperation beyond minimum legal requirements.
Big tech companies maintain relationships with law enforcement. Google has dedicated teams that handle requests from law enforcement. Amazon has Ring law enforcement portal where agencies can request footage. Meta allows police to request content from Facebook and Instagram.
These aren't adversarial relationships. Law enforcement and tech companies have mutual interests. Both want to solve crimes, catch criminals, and protect the public. For companies, responding helpfully to law enforcement requests builds goodwill and can reduce regulatory pressure. For law enforcement, having cooperative tech companies means faster access to crucial evidence.
But this cooperation happens largely out of public view. Users don't see it. They don't know how many times law enforcement has accessed their data. They don't know on what legal basis. They don't know if they were given notice (many jurisdictions allow "gag orders" that prevent companies from notifying users that their data was requested).
Google publishes a transparency report that provides some statistics. In the last published report, Google received over 100,000 requests from law enforcement agencies globally. For government requests overall, Google's compliance rate is extremely high, over 90% in most cases.
But the transparency report is aggregated. You can't see which specific requests were made about your account. You can't know if law enforcement accessed your Nest footage. Google could tell you, but in many cases, legal orders prevent the company from disclosing that information.

The Broader Implications for Smart Home Privacy
The Guthrie case is specific, but the implications are general. If you own a smart home camera, you should understand what you've actually agreed to.
Your smart home data is not private in the way you might assume. It's stored on company servers. It's backed up across multiple systems. It persists longer than you think. It can be accessed by law enforcement. It can be requested by courts. It can potentially be breached by hackers. It's used for product improvement, machine learning, and sometimes for ad targeting.
This doesn't mean you shouldn't own a smart home camera. The benefits are real. You can monitor your home when you're away. You can see who's at your door. You can check on family members. But you should do so with clear eyes about what you're trading off.
Consider what happens if your account is hacked. The hacker has access to your video footage. They can see when you're home, when you're away, what you're doing. They can use this information to plan a burglary or worse.
Consider what happens if there's a data breach at Google. Criminal hackers gain access to millions of people's smart home footage. This has happened with other tech companies. It could happen with Google.
Consider what happens in a legal dispute. If you're involved in a lawsuit, either as a defendant or plaintiff, the other side can subpoena your smart home footage. If you're going through a divorce, your smart home cameras become evidence. If you're suspected of a crime, your footage could be used against you.
Consider law enforcement overreach. Law enforcement can sometimes request data that exceeds their legal authority. Tech companies, not wanting legal trouble, often comply anyway. You might not find out until much later, if at all, that your data was accessed.
These aren't hypothetical concerns. They happen regularly. Privacy advocates have documented cases of improper law enforcement access to smart home data. They've found that companies sometimes don't require proper legal process for disclosures.
The question is what you want to do about it.

Best Practices for Smart Home Privacy
If you own smart home cameras, here are concrete steps to reduce privacy risks.
First: Use strong passwords and two-factor authentication. Most smart home account compromises happen because passwords are weak. Use a password manager. Create unique passwords for each account. Enable two-factor authentication on any device that supports it. This prevents someone from hacking your account and accessing your footage.
Second: Review sharing settings regularly. Check who has access to your smart home cameras. Remove people who no longer need access. Don't give access to people you don't fully trust. Each person with access is another security risk.
Third: Understand the features you're enabling. If your camera has cloud video recording, understand how it works and what data it's creating. If your camera has person detection or AI features, understand what data those features require. Sometimes privacy costs are worth specific benefits, but make that choice knowingly.
Fourth: Delete footage regularly. The longer footage persists in your account, the longer it's vulnerable to breaches or law enforcement requests. If you don't need old footage, delete it. This won't prevent law enforcement from recovering it from backup systems, but it reduces the attack surface.
Fifth: Separate concerns with local storage. If possible, use cameras that can record to local storage (SD card, hard drive, NAS) in addition to or instead of cloud storage. This gives you more control over the data. Local footage is harder for cloud providers to hand over to law enforcement and harder for remote hackers to access.
Sixth: Know your camera placement. Where you place your smart home camera matters. Cameras in private areas (bedrooms, bathrooms) are more legally protected than cameras in common areas. Avoid recording areas where people have a reasonable expectation of privacy. This protects you legally and ethically.
Seventh: Have a deletion plan if you move. When you stop using a smart home device, delete your account properly. This should delete all associated footage from your accessible account. But it won't delete residual data from backup systems. However, the company will stop actively maintaining that data if your account is gone.
Eighth: Read the privacy policy once. Pick a slow day and read through your camera manufacturer's privacy policy. Yes, it's boring. Yes, it's written in legal language. But understanding what you've agreed to is the first step to protecting yourself. You might decide the privacy tradeoffs aren't acceptable, and you should know that before you own the device.

The Technical Reality of Data Recovery
Understanding how forensic data recovery works helps explain why the FBI's recovery of the Guthrie footage wasn't surprising to anyone familiar with cloud infrastructure.
When a user deletes data from their Nest account, the deletion process updates the metadata in Google's database. The file is marked as deleted. The user's account no longer shows it. But the actual video file might still exist on the physical storage systems. Here's why:
Google's storage systems use a principle called "lazy deletion." Instead of immediately erasing data, the system marks it as deleted and removes it from the user-accessible database. The physical storage space is marked as available for reuse. But until that space is actually overwritten with new data, the old data remains intact and potentially recoverable.
This happens for performance reasons. Immediately erasing data would be slow and resource-intensive. Marking it for eventual overwrite is faster. From Google's perspective, this makes sense.
Forensic specialists recover data using this principle. They have tools that can read storage systems directly, bypassing the database layer. They can identify data marked for deletion and recover it. Law enforcement can request this recovery from Google. Google, with the proper legal process, can use forensic techniques to extract the data and provide it.
The technical capability has existed for years. The Guthrie case didn't reveal any new vulnerability. It just demonstrated that law enforcement knows how to use these capabilities and that companies will cooperate.
Is this a problem? That depends on your perspective. If you believe law enforcement should have broad access to evidence, then the data recovery capability is good. It helps solve crimes. If you believe privacy should be more absolute, then the capability is concerning. It means deletion isn't truly permanent.
The honest answer is that both perspectives have merit. Forensic data recovery helps law enforcement investigate crimes and protect public safety. But it also means that nothing is truly deleted from the cloud, and law enforcement can access it. Both things are true simultaneously.

Privacy Regulations and Smart Homes
There are laws that regulate how companies can handle personal data, but smart home camera footage occupies an interesting legal gray area.
GDPR (General Data Protection Regulation): In Europe, GDPR imposes strict requirements on data collection and retention. Companies must have a legitimate basis for processing data. They must retain data only as long as necessary. They must notify users of data breaches. They must honor user deletion requests. But GDPR also includes exemptions for law enforcement and public safety. So companies can retain data if law enforcement might need it.
CCPA (California Consumer Privacy Act): California's privacy law gives consumers rights to know what data is collected, to delete personal data, and to opt out of data sales. Smart home cameras fall under CCPA. But again, there are exemptions. If law enforcement requests data, companies can provide it despite user deletion requests.
State-specific laws: Various states are enacting smart home privacy laws. Some regulate video surveillance in specific contexts. Some require notice to people being recorded. But most don't address the cloud storage and law enforcement access issues at the heart of this case.
Federal law: The Stored Communications Act and similar federal laws govern when companies can disclose user data. But these laws provide significant exceptions for law enforcement, and they often allow companies to do more than users expect.
The pattern across all these regulations is similar: companies must protect data from general unauthorized access, but can provide data to law enforcement with proper legal process. The regulations don't create a strong right to delete data from backup systems. They don't prevent forensic recovery. They mostly ensure that law enforcement follows some legal process before accessing data, not that the data is truly inaccessible.
From a consumer perspective, these regulations provide some protections but fall short of addressing the core privacy concerns around smart home devices.

What This Means for Future Smart Home Development
The Guthrie case might influence how companies design smart home systems going forward.
One possibility: companies become more careful about retention policies. If the public backlash is strong enough, if there are legal challenges, if there are regulatory responses, companies might shorten how long they retain data. They might delete backups faster. They might design systems that are truly unrecoverable.
But there are countervailing pressures. Law enforcement and prosecutors will argue that long retention is necessary for investigations. Companies will argue that backup systems are necessary for reliability and disaster recovery. The two interests are in tension.
Another possibility: companies become more transparent about what they do. More detailed privacy policies. More information about law enforcement requests. Maybe notification to users when their data is accessed by law enforcement, except in cases where legal orders prohibit it.
A third possibility: companies offer encryption options that even they can't decrypt. End-to-end encryption for smart home footage is technically possible. Some companies, like Apple, are moving in this direction. But it comes with tradeoffs. Companies can't optimize video quality based on network conditions. They can't use machine learning to improve features like person detection. They can't provide law enforcement with unencrypted footage. End-to-end encryption is very private but less convenient.
A fourth possibility: regulation. If there's enough public concern about smart home privacy and law enforcement access, regulators might impose requirements. Maybe companies must delete data from all systems after a specific period. Maybe law enforcement must meet a higher standard to access data. Maybe users must be notified when their data is accessed.
It's too early to know which direction things will go. But the Guthrie case has put smart home privacy on the public agenda. That attention might lead to changes.
Practical Considerations for Different Use Cases
How much you should worry about smart home privacy depends on your specific situation.
If you live alone and have no visitors: Your smart home data is primarily about your own activities. The main risks are account hacking and law enforcement access. You're less at risk from roommates or family members seeing footage they shouldn't. Privacy is still important, but the acute risks are fewer.
If you have family members or roommates: The footage might capture them without their knowledge or consent. This has ethical and legal implications. In some jurisdictions, recording someone without their knowledge is illegal. You should tell anyone living in your home that you have cameras, what they record, and how the footage is stored.
If you have guests regularly: Same consideration applies. Guests should know they're being recorded. Some jurisdictions require notice. It's also a matter of respect.
If you're a landlord or property manager: Recording tenants' private areas without consent is illegal in most places. Recording common areas might be permitted but should be done with appropriate notice.
If you're a business using smart home cameras for security: You likely have different legal obligations than a home owner. Employee privacy laws might apply. Customer privacy might apply. Consult a lawyer.
If you're involved in litigation: Your smart home footage might become discoverable evidence. Opposing counsel could subpoena it. Expect that anything on your cameras might be seen by lawyers, judges, and juries.
If you're concerned about a stalker or abuser: Smart home data could be weaponized. An ex-partner might try to access it. Law enforcement might request it in a custody dispute. Consider what the worst case looks like and whether the security benefit outweighs those risks.
There's no one-size-fits-all answer to whether smart home cameras are right for you. But understanding the privacy implications helps you make that decision.

Looking Forward: Technology and Privacy Tradeoffs
Smart home devices will continue improving. Cameras will get better. AI will get smarter. Features will get more sophisticated. And with those improvements will come questions about privacy.
Here's the tension: the features people want most (person detection, package detection, identifying visitors by face) require machine learning. Machine learning requires data. Companies need to collect, process, and store massive amounts of video to train these models. That data is valuable. And valuable data is vulnerable to breaches and subject to law enforcement requests.
You can have absolute privacy or advanced features, but probably not both. You have to choose.
If you choose privacy, you get a basic camera that records video and stores it locally. You don't get AI features. You don't get cloud backup. You don't get the ability to access footage from anywhere in the world.
If you choose features, you get person detection, package detection, cloud backup, access from anywhere, integration with other smart home devices, and all the convenience that comes with it. But you trade privacy.
Some people will choose privacy. Some will choose features. Most will choose some middle ground: they'll use smart home cameras, they'll accept the privacy tradeoffs, and they'll hope law enforcement respects appropriate legal limits on data access.
The Guthrie case doesn't change this calculus. But it does make the tradeoff more visible. Before, smart home privacy was abstract. Now it's concrete: law enforcement can and will access your footage if they deem it necessary for an investigation.
That's not inherently wrong. But it's important to know.

FAQ
How long does Google store Nest camera footage?
Google typically stores 3 hours of event footage that you can access through your account with a free subscription. For paid subscriptions, storage is longer. But behind the scenes, Google maintains backup copies for disaster recovery purposes. These backups can persist for 30-90 days or longer, even after you delete footage from your account. The exact retention timeline for backup systems is not publicly specified by Google.
Can I permanently delete my Nest footage so law enforcement can't recover it?
You can delete footage from your account, which prevents casual access. But once data is stored in Google's cloud systems, truly permanent deletion is complicated. Residual data persists in backup systems and can potentially be recovered by forensic specialists. Deleting your entire Nest account might trigger more aggressive deletion, but even then, some data might remain in archival systems. For maximum privacy, use cameras with local-only storage that don't upload to the cloud, such as Wyze cameras configured for local storage or Ubiquiti Uni Fi equipment with local recording.
Does Google notify me if law enforcement requests my Nest footage?
Google publishes a transparency report showing aggregate numbers of law enforcement requests, but you won't know specifically if your account was targeted unless Google chooses to notify you. In many cases, legal orders (called gag orders) prevent companies from notifying users that their data was requested. If Google does notify you, it's usually after the investigation is complete. For real-time awareness, monitor your Google account security page regularly for unusual access patterns.
Is it legal for law enforcement to access my Nest footage without a warrant?
It depends on the circumstances. Law enforcement needs either a warrant, a subpoena, consent from the account holder, or an emergency exception to legally access your data. However, the definition of "emergency" is broad and includes situations like missing persons cases. Google has the legal right to provide data to law enforcement if proper legal process is followed. Challenging the legality of a data request requires hiring a lawyer and going to court, which is expensive and uncertain.
What smart home camera options offer the most privacy?
Privacy-first options include Apple Home Kit Secure Video, which processes video locally and encrypts data end-to-end. Ubiquiti Uni Fi devices allow local recording to a network drive. Wyze cameras can be configured for local SD card recording without cloud upload. Traditional security systems from companies like Honeywell and Vivint offer local storage options. The tradeoff is that you lose remote access and cloud-based features like AI detection.
Can I stop Google from backing up my Nest footage?
You can't disable backup systems at Google's end. Google maintains those systems for disaster recovery and to comply with law enforcement requests. You can manage your own backup: set footage to delete after a specific period, limit cloud storage to only active footage, and don't enable extended cloud storage if that option is available. Or choose a camera system that doesn't upload to the cloud. But if you want to use Google Nest with cloud storage, you can't prevent Google from maintaining backups.
What should I do if I suspect my Nest account has been hacked?
First, change your password immediately using a secure device. Second, enable two-factor authentication on your Google account if you haven't already. Third, review your connected devices and recent activity to see if anything looks suspicious. Fourth, check if anyone else has access to your Nest camera through account sharing settings and remove unauthorized access. Fifth, consider changing the Wi-Fi password for the camera if your home network might be compromised. If you believe data has been accessed maliciously, consider filing a report with the FBI's Internet Crime Complaint Center.

Conclusion: Making Informed Choices About Smart Home Privacy
Nancy Guthrie's case is a tragedy. If the recovered Nest footage helps find her and bring whoever took her to justice, that's a meaningful outcome. Law enforcement should have tools to investigate serious crimes. That's not in question.
But the recovery of that footage also reveals something important about how smart home devices actually work. They're not island devices sitting in your home, recording only what you decide. They're connected to vast cloud infrastructure. They're integrated with corporate systems. They persist longer than you think. And they're accessible to law enforcement.
This doesn't mean you shouldn't own a smart home camera. Millions of people own them and find them valuable for security and peace of mind. But you should own them with clear eyes about the privacy tradeoffs.
Your smart home data is powerful evidence. It shows who comes to your house, when you're home, what you're doing, who you're with. Law enforcement wants access to that evidence when investigating crimes. Companies want to maintain that data for backup and machine learning. And security researchers know that data can be stolen or misused.
You control some of these factors. You choose whether to own a smart home camera. You choose where to place it. You choose what features to enable. You choose how to manage access. You choose how often to delete footage. These choices matter.
But you don't control everything. You can't prevent law enforcement from requesting your data with a warrant. You can't prevent Google from maintaining backup systems. You can't prevent breaches of Google's systems. You can't prevent bad actors from hacking your account. You can only make informed choices within the constraints of the system.
Start by understanding what you're agreeing to. Read the privacy policy. Understand how long data is kept. Understand who can access it. Understand what happens if your account is hacked or if law enforcement requests it. Then decide if the benefits of having a smart home camera outweigh those risks for your specific situation.
For many people, the answer is yes. Smart home cameras are genuinely useful for security. The privacy risks are manageable with good security hygiene: strong passwords, two-factor authentication, regular review of access and settings. The chance that law enforcement will request your footage is low unless you're involved in a serious investigation.
For some people, the answer is no. They decide that the privacy risks are too great. They choose not to own smart home cameras, or they choose devices with local-only storage and no cloud backup. That's a legitimate choice too.
What's not acceptable is making the choice blindly, assuming that deletion means permanent erasure or that law enforcement can't access your data. Both assumptions are false, as the Guthrie case demonstrates.
The FBI's recovery of that Nest footage is a reminder that smart home devices have tradeoffs. The technology is useful. The privacy concerns are real. But neither fact should surprise you. Now you know how the system actually works. Now you can make an informed choice.
That's all you can really do.

Key Takeaways
- The FBI recovered Nest footage from Google's backend systems using forensic techniques on residual data that persists long after user deletion
- Smart home camera data is stored in multiple systems and backed up across data centers, making true permanent deletion impossible
- Law enforcement can access smart home footage through warrants, subpoenas, emergency exceptions, or voluntary company cooperation
- Residual data recovery is standard in cloud forensics, and all major cloud providers maintain backup systems that persist for 30-90 days minimum
- Understanding data retention policies and choosing appropriate devices with local storage options are key to managing smart home privacy risks
![FBI Recovers Nest Camera Footage: What This Means for Your Smart Home Privacy [2025]](https://tryrunable.com/blog/fbi-recovers-nest-camera-footage-what-this-means-for-your-sm/image-1-1770754062916.jpg)



