Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
When a hacking collective brags about conquering a target, they're usually riding high on adrenaline and the thrill of getting away with something massive. But what happens when that target was designed specifically to catch them? That's the embarrassing reality facing Scattered Lapsus$ Hunters right now.
In late 2025, the infamous group announced they'd breached Resecurity, a respected cybersecurity firm. They claimed total system compromise, stolen employee data, client lists, internal communications—the whole catastrophic playbook. Except it was all a lie. Or rather, they were telling the truth about accessing something, just not what they thought.
Resecurity had built a perfect trap. A honeypot so convincing that one of the most dangerous hacking collectives on the planet fell straight into it, uploaded their fake "trophies" to the internet, and exposed their entire operational infrastructure in the process. What happened next—IP addresses, linked accounts, timestamps, law enforcement coordination—reads like a cybersecurity thriller, except it's real.
This story matters because it reveals something critical about modern hacking: even the biggest, baddest groups can be outmaneuvered by smart defense. It also shows that attribution and accountability might finally be catching up with attackers who've operated with near-total impunity for years.
Let's unpack how one honeypot changed everything.
TL; DR
- The Setup: Scattered Lapsus$ Hunters claimed to breach Resecurity and steal sensitive company data, employee information, and client records.
- The Catch: Resecurity revealed the breach target was a honeypot containing only fake accounts, fabricated data, and deceptive content designed to trap attackers.
- The Exposure: The group's attempt to prove the breach publicly exposed their IP addresses, linked personal accounts, device information, and operational timestamps.
- Law Enforcement: Complete forensic data, including network connections and exact activity logs, was shared with law enforcement agencies, raising arrest prospects.
- The Lesson: Even sophisticated threat actors can be caught by well-designed defensive infrastructure that mimics real attack surfaces.
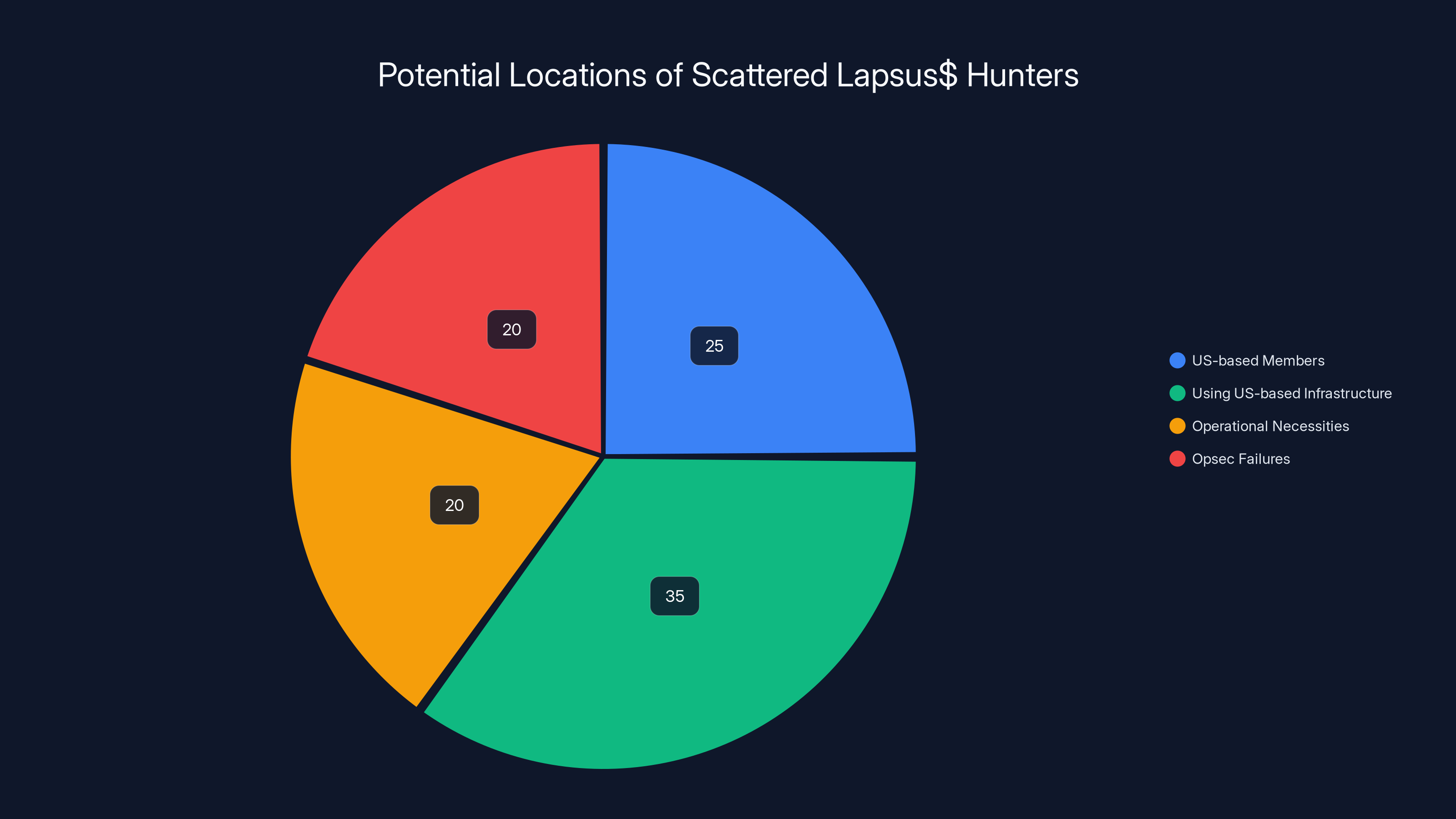
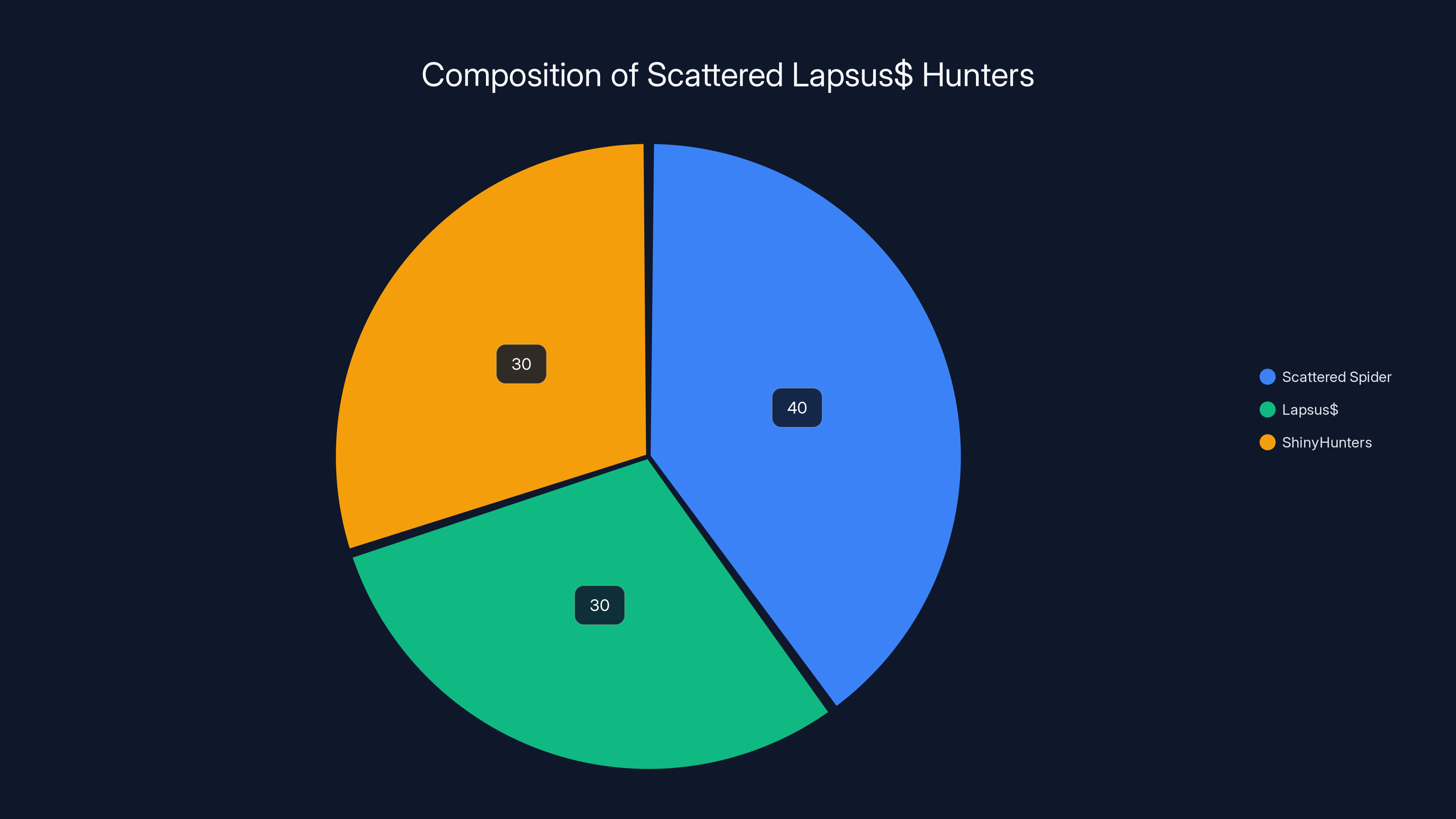
Estimated data suggests a diverse range of operational scenarios for Scattered Lapsus$ Hunters, with a significant portion potentially using US-based infrastructure.
Who Are Scattered Lapsus$ Hunters?
Scattered Lapsus
Scattered Spider is the oldest of the three constituent groups, operating since at least 2020 with a focus on social engineering and initial access broking. They're known for getting inside networks through charm, deception, and human manipulation rather than relying entirely on technical exploits. They've breached major tech companies and financial institutions by simply calling the right person and pretending to be the right person.
**Lapsus
Shiny Hunters operated in the shadows longer than the other two, specializing in stealing data from SaaS platforms, particularly Salesforce environments. They were methodical and quiet until they weren't. When they got caught, they pivoted, rebranded, and merged with others.
When these groups coalesced into Scattered Lapsus
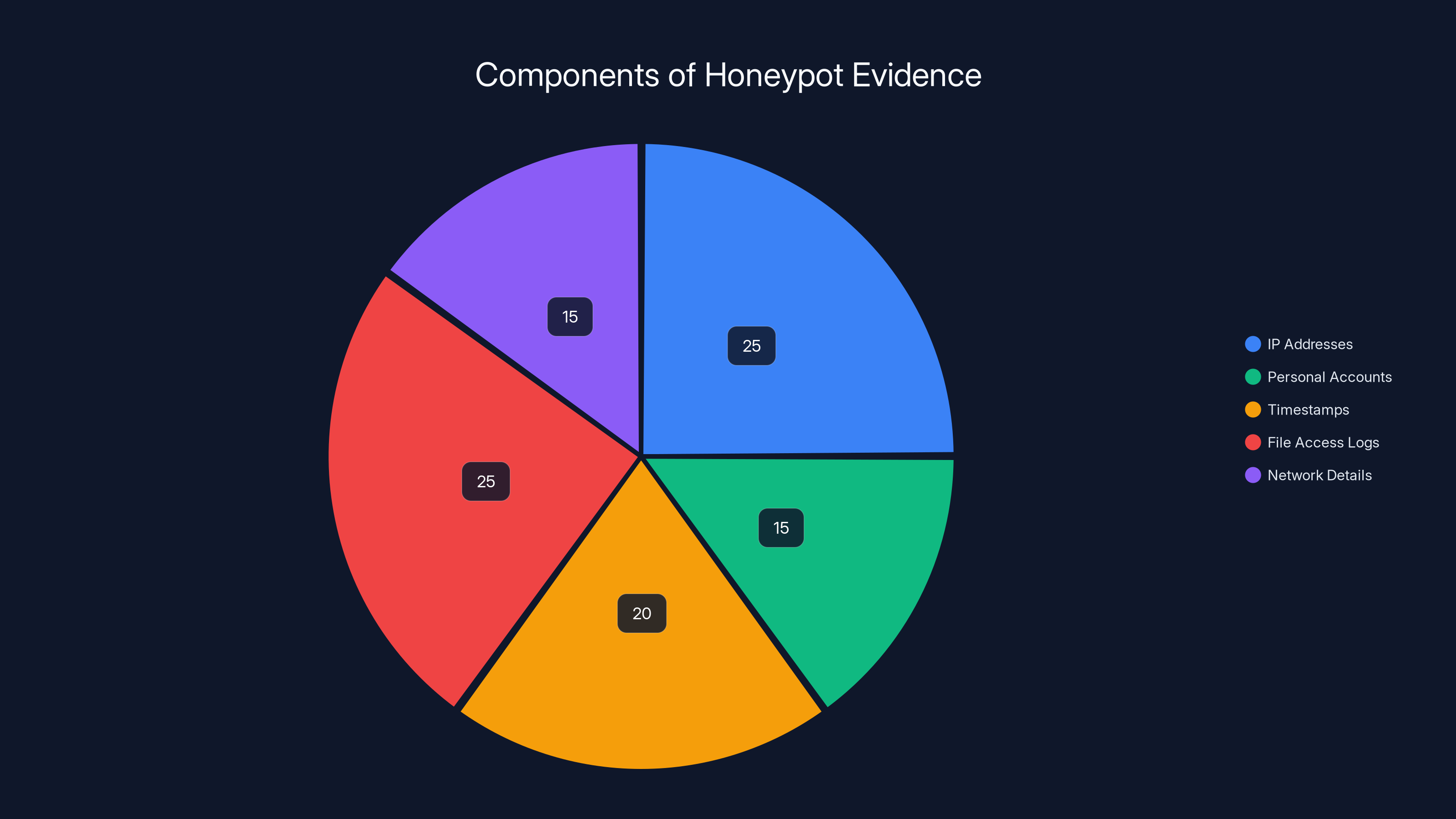
Honeypots capture a variety of forensic data, with IP addresses and file access logs being the most significant components. Estimated data.
The Jaguar Land Rover Incident: Why SLH Got Noticed
In September 2025, Scattered Lapsus$ Hunters claimed responsibility for a massive breach at Jaguar Land Rover. This wasn't just another hack. This was production-halting, supply-chain-disrupting, worldwide impact.
The attack forced JLR to halt vehicle manufacturing across multiple plants. Dealers couldn't access systems to configure cars or process orders. The operational impact rippled through the entire automotive supply chain. Customers waited weeks for deliveries that couldn't happen. The financial damage was staggering—one of the costliest cyber incidents in UK corporate history.
What made this attack so significant wasn't just the technical achievement. It was the geopolitical and economic fallout. Here was a group that could completely paralyze a Fortune 500 company's operations. They proved they could get past enterprise security, maintain persistence, and cause maximum disruption. And they did it with what seemed like almost casual confidence.
The JLR breach elevated Scattered Lapsus$ Hunters from being another criminal gang to being a genuine national security concern. Governments started paying attention. Security firms started profiling them obsessively. Law enforcement began coordinating across jurisdictions.
For a few weeks, they rode that wave of notoriety. But like most hacking groups that crave attention, they made the mistake of assuming their invincibility extended to their next target.
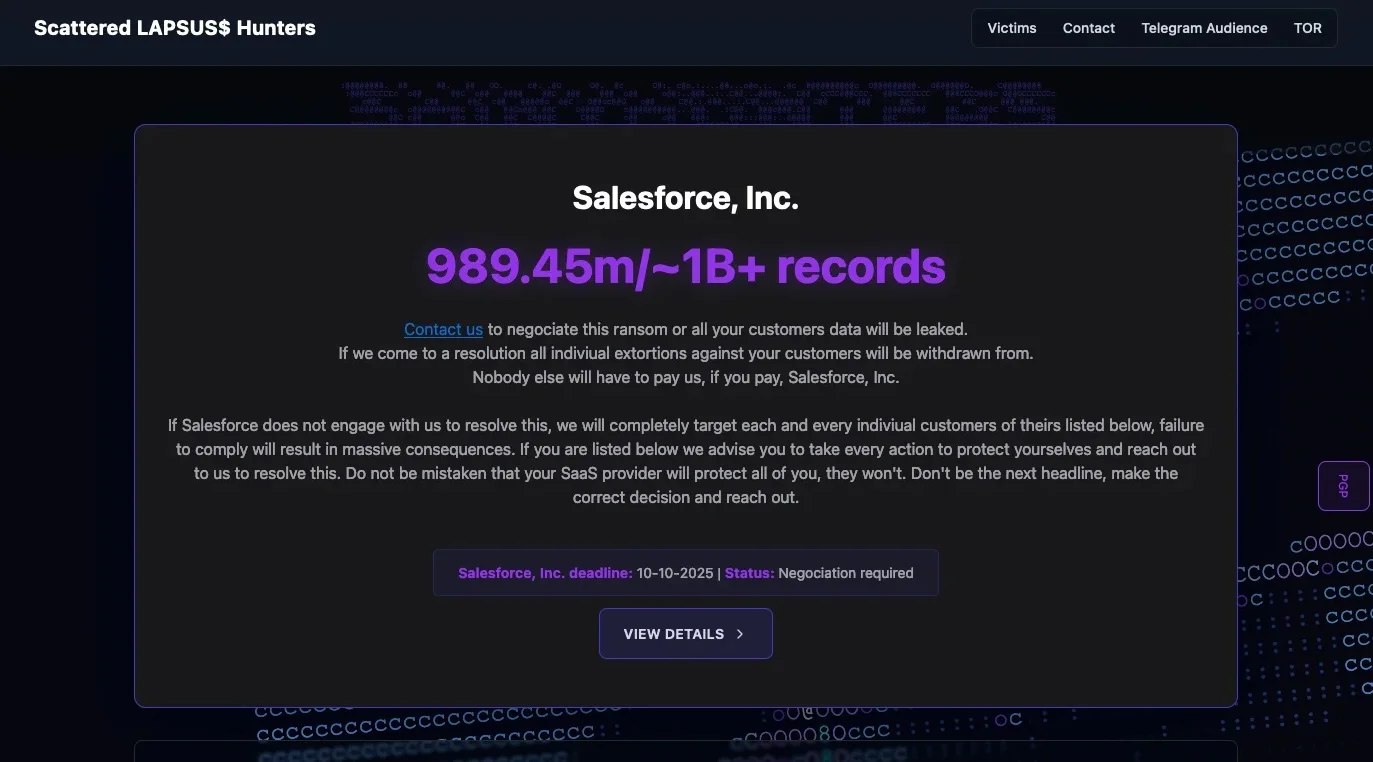
The Resecurity "Breach": What Actually Happened
On a Tuesday in late 2025, members of Scattered Lapsus$ Hunters logged into what they believed was Resecurity's internal network. The access came relatively easy—no zero-day exploits, no sophisticated persistence mechanism. Just old-fashioned compromise vectors that likely involved credential theft, social engineering, or exploiting an unpatched vulnerability.
What they found inside looked completely legitimate. Email systems. File repositories. Employee directories. Client information databases. Sensitive documents. Everything a data thief would want, all seemingly there for the taking.
They began extracting data. They took what appeared to be internal Slack communications, employee personal information (names, emails, phone numbers, sometimes addresses), client lists with contract details, and sensitive company information. They downloaded files, archived them, and prepared to publicize their success.
Then they made the announcement on Telegram, according to reports: "We would like to announce that we have gained full access to Resecurity systems. We took everything." The message was posted in channels where other threat actors, journalists, and security researchers monitor hacking news. It was designed to maximize reputation damage and establish SLH's credibility as a major threat actor.
Except everything they claimed to have stolen didn't actually exist in the real Resecurity network. It existed in a carefully constructed simulation designed specifically to trap them.
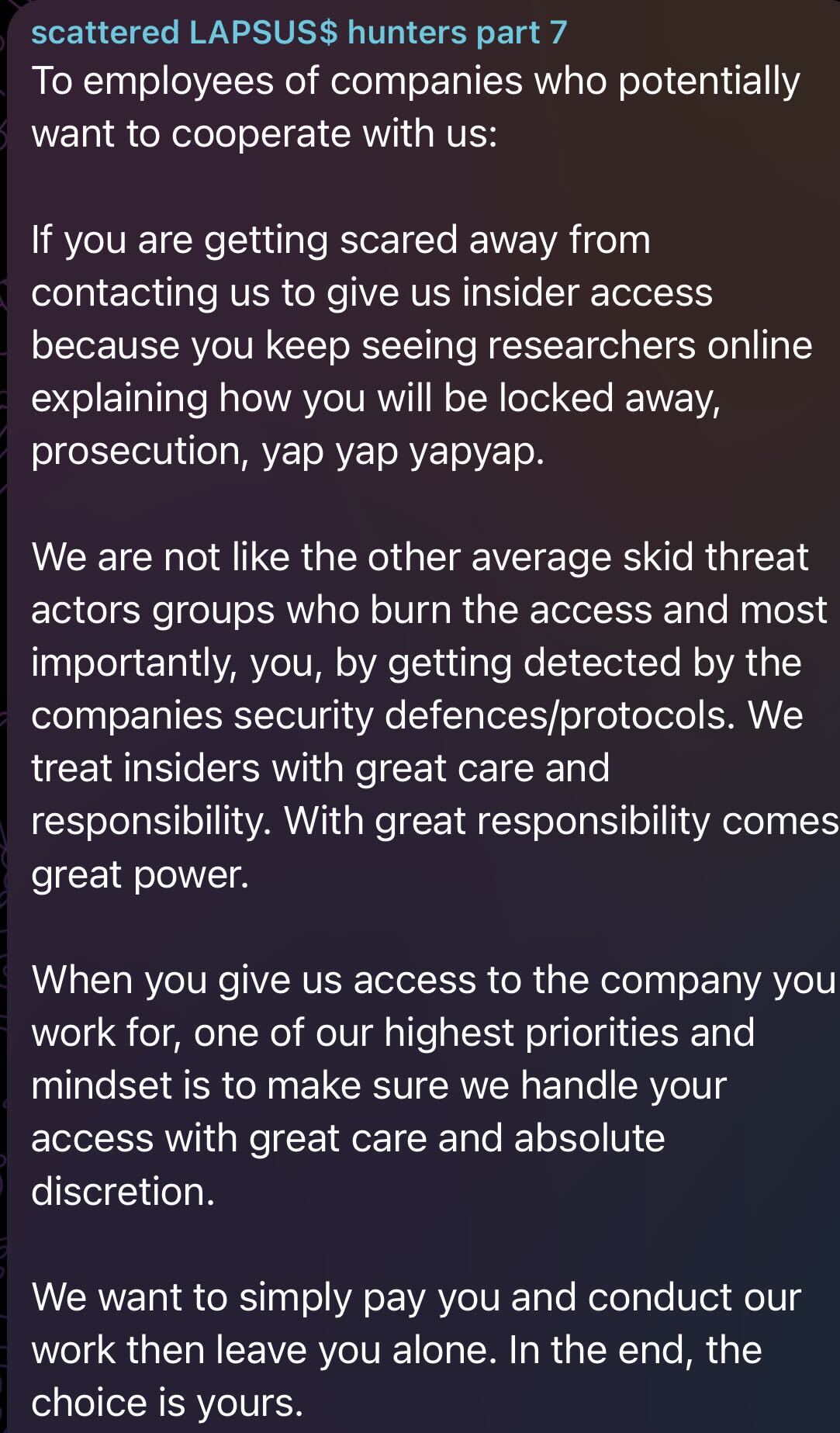
Scattered Lapsus
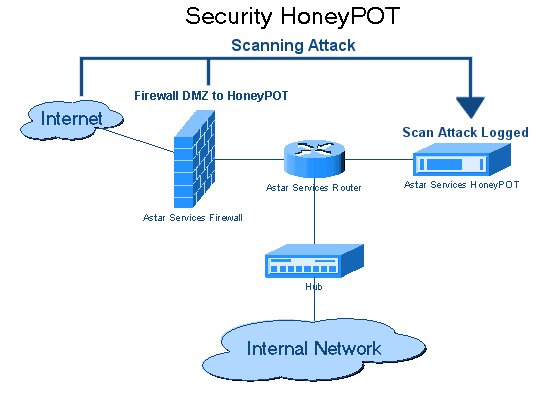
The Honeypot Explained: How the Trap Worked
A honeypot is a deliberately vulnerable or compromised system designed to look like a real corporate asset while actually being a controlled environment under the defender's complete control. Resecurity built one that was sophisticated enough to fool professional threat actors.
The honeypot environment contained several key deceptive elements:
Fake accounts that looked legitimate—complete with realistic email addresses, profile information, and communication histories. If an attacker checked whether someone worked at the company, the fake profile would confirm it.
Fabricated data that seemed sensitive and valuable. Not obviously fake, but designed to be traceable. If an attacker exported a file, Resecurity could track exactly what data they took and when.
Realistic folder structures organized the way a real company would organize files. Nothing felt out of place. The honeypot mimicked Resecurity's actual architecture closely enough to pass casual inspection.
Monitored access points meant that every file opened, every directory accessed, every system explored generated a log entry. Resecurity watched in real-time as the attackers navigated the fake network.
The trap was set with a specific vulnerability that Resecurity knew was attractive to attackers like Scattered Lapsus$ Hunters. The group had a known pattern of exploitation. Resecurity essentially left a door open they knew SLH would walk through.
What made this honeypot particularly clever was that it didn't just sit idle. It needed to be discoverable. Security researchers estimate that Resecurity may have seeded information about the vulnerability on forums or in intelligence channels where threat actors operate. They made the attack opportunity feel organic, inevitable, like something SLH would find through normal reconnaissance.
The Moment of Discovery: Resecurity's Public Reveal
Resecurity waited until Scattered Lapsus$ Hunters had made their public announcement and begun distributing samples of their "stolen" data. They let the group commit fully to the narrative of successful compromise. Then they published their response.
Resecurity's statement was comprehensive and devastating:
"Following our publication, the group called Shiny Hunters, previously profiled by Resecurity, fell into a honeypot. In fact, we are dealing with its rebranded version, which calls itself SLH due to the alleged overlap between the threat actors Shiny Hunters, Lapsus$, and Scattered Spider. The group claimed that it has gained full access to Resecurity systems, which is a clear overstatement, as the honeypot environment prepared by us did not contain any sensitive information."
This wasn't just a technical correction. It was a comprehensive dismantling of SLH's credibility. Every piece of data they claimed to have stolen turned out to be worthless. Every file they bragged about acquiring was either fake or honeypot bait. They had accessed and exfiltrated nothing of actual value.
But more importantly, by making that announcement, they had exposed themselves completely. The moment they publicized their supposed breach, they created a forensic record. They documented their own attack chain, inadvertently proving where they accessed the network from, what tools they used, how long they spent inside the honeypot, and exactly what they did.
It was like a bank robber getting caught because they mailed the bank a postcard from the location where they were hiding.
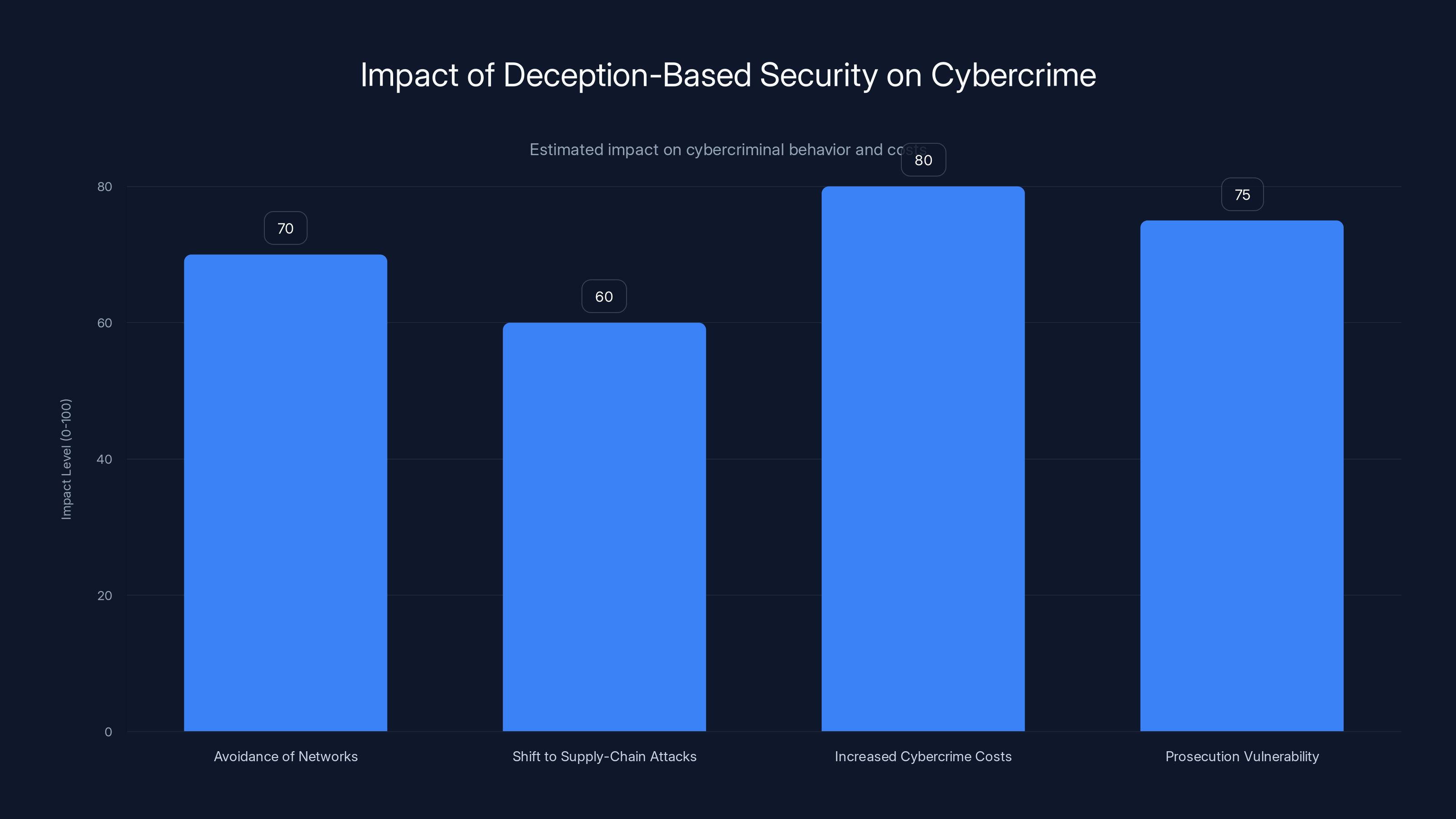
Estimated data suggests that deception-based security significantly increases cybercrime costs and prosecution vulnerability, while also prompting cybercriminals to avoid deceptive networks and shift towards supply-chain attacks.
The Infrastructure Exposure: IPs, Accounts, and Attribution
Here's where the trap transformed into active liability for Scattered Lapsus$ Hunters.
Resecurity had logged every connection to the honeypot. They had IP addresses. Not VPN exit nodes or proxy chains, but actual originating IPs that the attackers used. In some cases, attackers use residential proxies or VPNs, which makes attribution harder. But not always. And Scattered Lapsus$ Hunters made mistakes.
Resecurity stated they were able to "identify the actor and link one of his active Gmail accounts to a US-based phone number and a Yahoo account." That's extraordinarily specific. A Gmail account. A phone number. A secondary email account. These are the pieces of attribution that law enforcement uses to actually prosecute cases.
They had more than just network data. They had activity timestamps—exact records of when the attackers accessed which files, when they searched for data, when they began exfiltration. They could show a timeline of the entire attack from initial compromise through data extraction through public announcement.
They had network connection details—protocol information, transfer rates, data volumes, file types, software signatures. All of this is forensic gold. It can be used to link different attacks by the same group. It can show patterns and techniques. It can prove motive and capability.
But the exposure went deeper than just technical attribution. Scattered Lapsus$ Hunters claimed the breach, which means they created a public record linking themselves to this attack. They posted on Telegram. They contacted journalists. They announced on social media and in hacking forums. All of that communication created additional evidence.
Their announcement of the breach, combined with Resecurity's technical evidence of honeypot access, creates something law enforcement calls a "closed loop." It proves motive (they wanted to steal from Resecurity), capability (they could access the network), and knowledge (they knew they had accessed something they thought was valuable).
That's the foundation for prosecution in jurisdictions that have cybercrime statutes.
Law Enforcement Coordination and the Path to Prosecution
Resecurity stated clearly: "The activity has been imaged and retained, including exact timestamps and network connections, which have been shared with law enforcement."
This is significant because it indicates coordination with law enforcement agencies, likely including:
FBI Cyber Division (if the attack originated in the US or targeted US entities, which Resecurity may qualify as)
Europol or equivalent EU law enforcement (if any members are based in Europe)
Local law enforcement in jurisdictions where identified members are located
International cybercrime task forces that coordinate across borders
The sharing of evidence with law enforcement creates an official investigation record. It means law enforcement agencies now have:
- Complete forensic copies of the honeypot activity
- IP addresses and device information
- Linked personal accounts (Gmail, Yahoo, etc.)
- Phone numbers
- Payment information (if SLH used cryptocurrency or bank accounts to purchase infrastructure)
- Communication records from their announcement
- Timeline of their operational activity
From this point forward, any of these individuals can be located, surveilled, apprehended, and prosecuted. The honeypot didn't just embarrass them. It provided law enforcement with everything needed to build a criminal case.
Historically, prosecuting cybercriminals required cooperation from foreign governments, extradition agreements, and international coordination that often failed. But when the evidence is this clear, when the forensic record is this complete, and when the crime involves a US entity (Resecurity), the FBI has leverage.

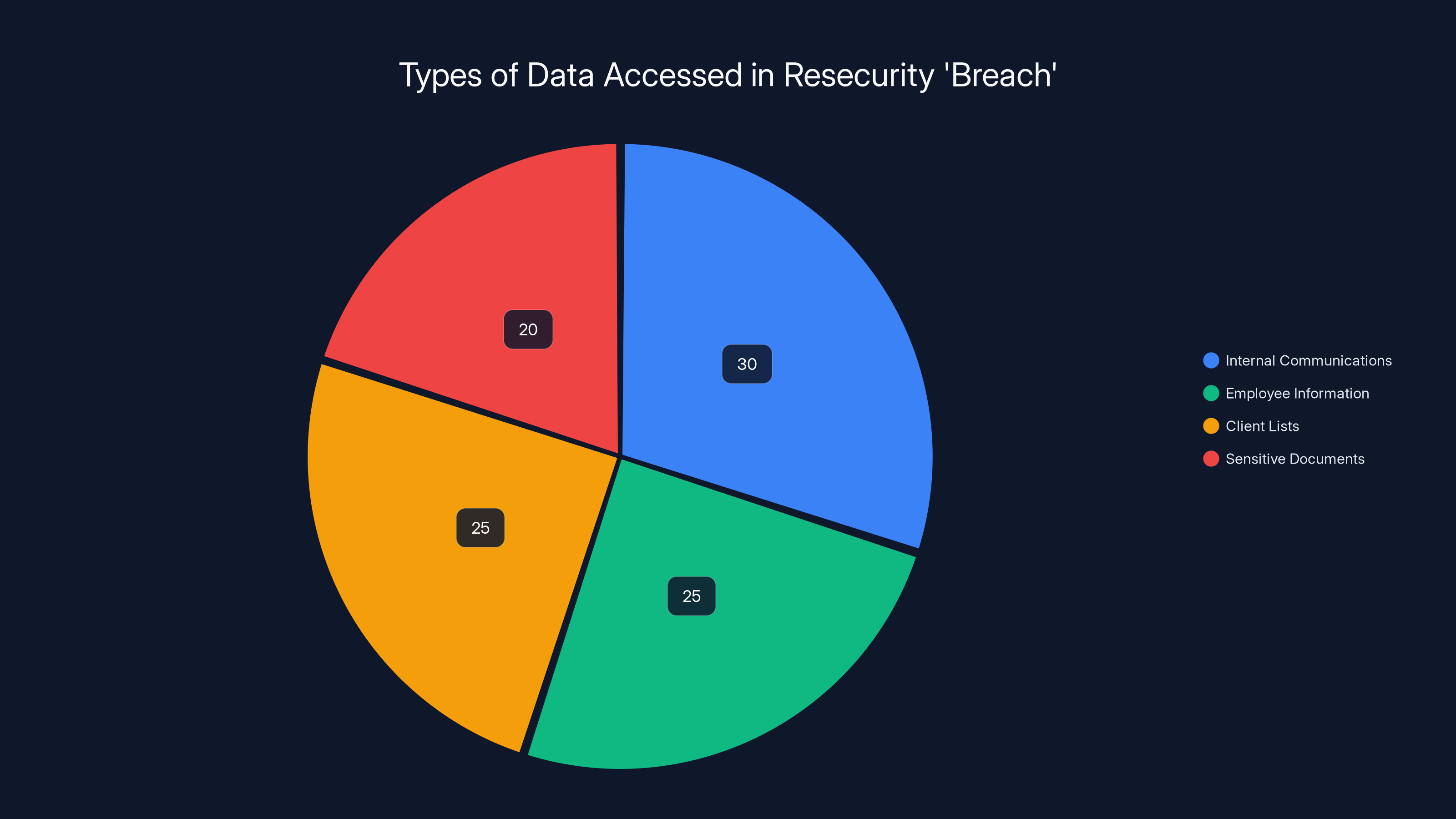
The attackers accessed a variety of data types, with internal communications and employee information being the most accessed. Estimated data.
Why SLH Fell for the Honeypot
It's worth asking: how did a group that successfully breached Jaguar Land Rover fall for an obvious trap?
The answer reveals something important about how threat actors think and operate.
Overconfidence after JLR success played a huge role. Scattered Lapsus$ Hunters had just pulled off what many considered impossible. They'd halted global manufacturing at a Fortune 500 company. That success created a sense of invincibility. When they looked at Resecurity, they assumed they would find what they wanted to find.
Resecurity's reputation as a cybersecurity company actually helped the honeypot work. Paradoxically, security companies often have interesting data that threat actors want: client lists showing who they protect, intelligence reports about vulnerabilities, threat analysis information. A security company's data has intrinsic value to hackers. So when SLH found what looked like Resecurity's internal systems, it made perfect sense that those systems would contain valuable data.
The vulnerability Resecurity exposed was attractive and legitimate. It wasn't obviously a trap. It was a real exploitable flaw that fit SLH's known attack patterns. They recognized the vulnerability, exploited it the way they had exploited other vulnerabilities, and expected to find the usual rewards.
Threat actors rarely second-guess their own success. When you access systems and find data, your instinct isn't to question whether it's real. Your instinct is to exfiltrate it, prove you got it, and move on to the next target. SLH followed this playbook exactly. They didn't do extensive due diligence to verify the data was real because they didn't think they needed to.
The honeypot was designed to withstand scrutiny. It wasn't obviously fake. Resecurity invested resources in making it look exactly like their real infrastructure would look. Fake accounts had realistic histories. Fake data was organized logically. File metadata looked legitimate. To an attacker spending hours or even days inside the network, everything checked out.
The combination of these factors—overconfidence, plausible target profile, legitimate vulnerability, real-looking infrastructure—created the perfect conditions for a sophisticated threat actor to make a critical error in judgment.
The Role of Deception in Modern Cybersecurity
What Resecurity did represents a broader shift in how organizations approach security. Instead of only defending against attackers (reactive security), they also deceive them (proactive deception).
Honeypots are one form of deception, but they're part of a larger landscape:
Decoy data that looks valuable but is actually tracked and fake. If an attacker steals employee lists, those lists can show fake employees at fake addresses. The moment those fake employees appear anywhere else, you know data was exfiltrated.
Canary tokens are invisible tracking mechanisms embedded in documents, spreadsheets, and files. When an attacker opens the document, the token alerts the organization to the breach. It's an early warning system.
Fake credentials scattered throughout systems. An attacker finding credentials in a config file or environment variable might assume they've discovered real access. If they use those credentials, they trigger alerts and navigate further into the honeypot.
Replica environments that mirror real infrastructure but are monitored completely. Everything that happens in the replica is logged and analyzed.
Fabricated communications that make the environment feel alive and authentic. Fake emails, fake Slack messages, fake Git commits, all of it designed to seem real.
When deployed together, these deception technologies create environments that are nearly impossible for attackers to distinguish from real networks. An attacker inside such a network might spend weeks or months before realizing they're trapped. By that time, they've already exposed themselves completely.
For organizations like Resecurity, deception isn't just a security tool. It's an intelligence tool. By observing what attackers do when they think they're in a real network, defenders can understand:
- What data attackers find most valuable
- What techniques they use to navigate unfamiliar systems
- What tools they deploy once inside
- How long they typically remain undetected
- What triggers them to move to the exfiltration phase
- How they verify that their breach was successful
Scattered Lapsus$ Hunters, by navigating Resecurity's honeypot, gave Resecurity a complete tour of their operational methodology. Resecurity now knows how SLH works. Other security firms can use that intelligence. Law enforcement can use it to identify similar attacks.
The attackers intended to humiliate Resecurity. Instead, they handed Resecurity the blueprints to their own organization.

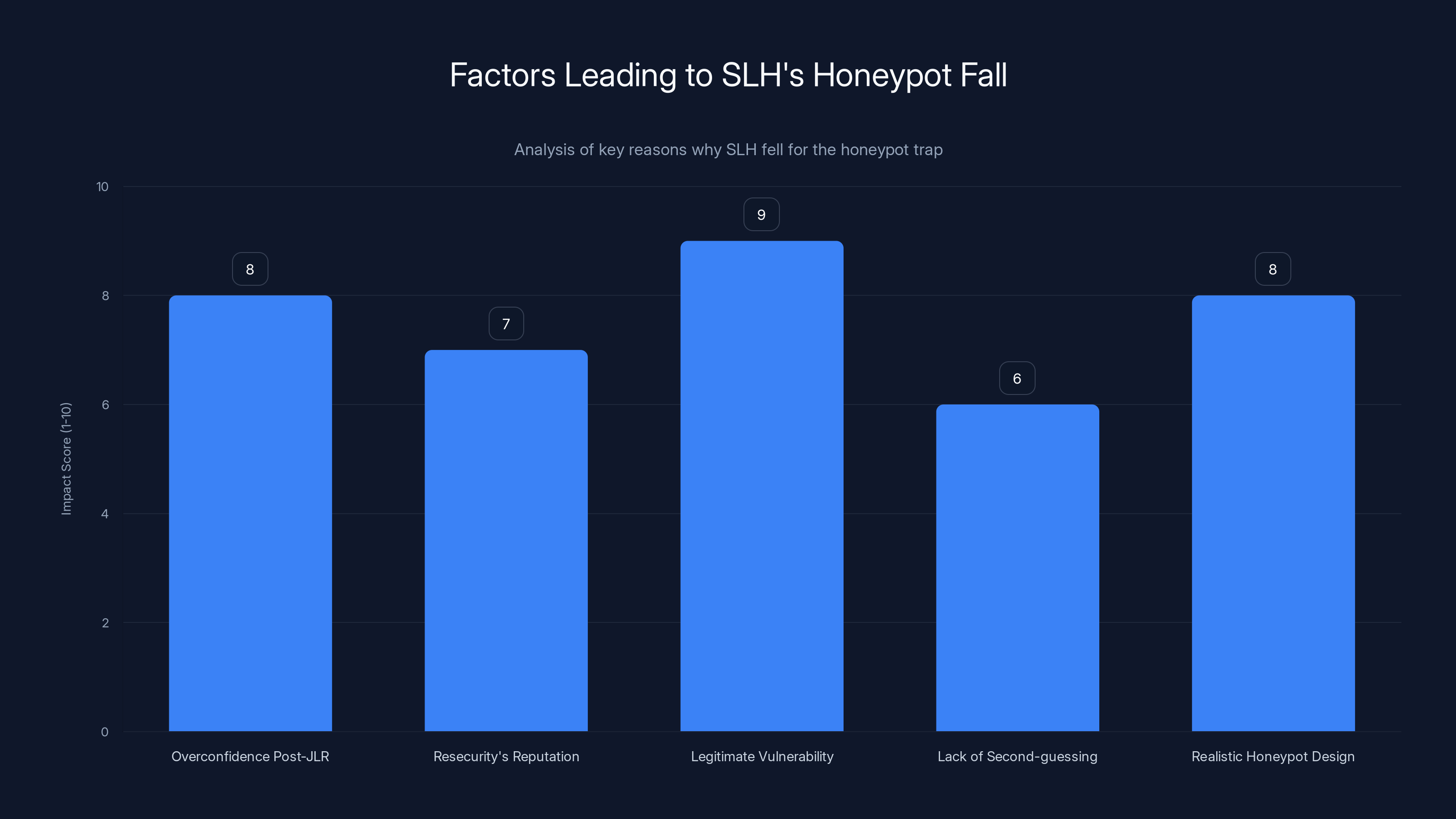
The chart illustrates the key factors that contributed to SLH falling for the honeypot, with the legitimate vulnerability and overconfidence post-JLR being the most impactful.
The Geographic and Identity Implications
Resecurity's revelation that they identified "one of his active Gmail accounts" linked to "a US-based phone number" opens significant questions about where Scattered Lapsus$ Hunters operate.
Historically, major hacking groups have been based in countries with weak cybercrime prosecution: Russia, China, North Korea, Iran. These countries either don't extradite cybercriminals or actively harbor them. A US-based phone number suggests something different.
SLH might have:
US-based members who are physically located in the United States, making them subject to US prosecution
Members using US-based infrastructure (compromised servers, stolen phones, purchased SIM cards) to hide their actual location, which law enforcement can often trace back through carrier records
Operational necessities that required someone physically in the US
Opsec failures where someone carelessly used real information while operating
Each scenario has different implications for prosecution. But all of them move SLH from being a distant foreign threat to being a domestic law enforcement matter. And domestic law enforcement has resources, jurisdiction, and ability to actually apprehend suspects.
The age question is also critical. Reports suggest Scattered Lapsus
Young attackers often lack the operational security discipline of older criminals. They make mistakes. They brag. They use real personal information. They forget that digital forensics is incredibly effective at tracking their activities. The US phone number might reflect exactly this kind of mistake.
What This Means for Enterprise Security
The Scattered Lapsus$ Hunters honeypot success has several implications for how enterprises should approach security:
Detection isn't enough. You need to deceive. Most security programs focus on detecting intrusions after they happen. The honeypot approach suggests that preventing attackers from succeeding might require making them think they've succeeded. This is a fundamentally different mindset.
Infrastructure visibility is critical. Resecurity could only trap SLH because they understood their own environment so completely that they could create a convincing replica. Organizations that don't have complete visibility into their own networks can't deploy honeypots effectively.
Forensic preservation matters legally. Resecurity's careful preservation of evidence in a format that law enforcement could use is part of what makes prosecution possible. Organizations need to think about forensics not just as an incident response tool, but as a potential component of a legal case against attackers.
Attribution is increasingly possible. The era of attackers hiding behind proxies and operating with complete anonymity may be ending. Careful forensic analysis, combined with traditional intelligence gathering, increasingly allows law enforcement to identify specific individuals behind attacks. That should change the risk calculus for potential threat actors.
Threat intelligence sharing accelerates justice. When organizations like Resecurity work with law enforcement and share evidence, the result is faster prosecution. But that only works if organizations commit to that cooperation rather than trying to handle breaches internally.
The Broader Implications for Cybercrime
This incident signals something potentially larger: a shifting balance in the eternal cat-and-mouse game between attackers and defenders.
For years, the assumption was that organized cybercriminals had structural advantages. They could operate from countries that don't cooperate with law enforcement. They worked in tight cells. They had no employees to blackmail or families to leverage. They could operate with near-total operational security.
But technology keeps changing. Forensic capabilities improve. Attribution becomes more reliable. Honeypots get more sophisticated. Law enforcement coordination accelerates. And perhaps most importantly, the scale of attacks keeps increasing, making it harder for threat actors to stay under the radar.
Jaguar Land Rover's breach was so massive that it drew government attention. Scattered Lapsus$ Hunters became a national security matter, not just a corporate cybersecurity incident. Once you reach that level, you have the full resources of intelligence agencies, law enforcement, and international task forces focused on finding you.
The honeypot was the specific trap that caught SLH. But the broader trap is the world they're operating in—a world where their scale of operations makes them too big to ignore, and their increasing sophistication is met by increasing sophistication on the defense side.
What Happens Next: Arrests and Prosecution
The forensic evidence Resecurity provided to law enforcement is comprehensive enough to support arrests. The question is: when?
Law enforcement investigations involving international cybercriminals typically take months or years. They need to:
Verify the evidence meets legal standards for admissibility in whatever jurisdiction will prosecute the case
Identify specific individuals from the IP addresses, linked accounts, and device information
Locate those individuals and determine jurisdiction
Coordinate with international partners if prosecution requires cooperation from foreign governments
Build additional evidence to corroborate the forensic findings and establish specific criminal charges
Prepare a case that can survive legal challenges and prove guilt beyond reasonable doubt
During this time, SLH members might try to:
Flee to countries with no extradition agreements with the United States
Destroy evidence of their activities (though much of what Resecurity collected would be safe)
Distance themselves from the group and claim they weren't involved
Cooperate with law enforcement in exchange for reduced sentences
History suggests some combination of these outcomes. Previous hacking cases have seen some members arrested, some members flee, and some members cooperate with authorities.
But the arc of the story is clear. Scattered Lapsus$ Hunters went from being an untouchable international cybercriminal organization to being a law enforcement target with identified members, documented locations, and concrete evidence linking them to major crimes.
The honeypot changed everything.

Lessons from Defense Victory
The Resecurity honeypot represents a rare moment where defenders decisively outmaneuvered attackers. Those lessons are worth drawing out:
Patience wins. Resecurity didn't immediately patch the vulnerability. They maintained it as bait, knowing eventually someone would take it. That required accepting risk for a longer period in exchange for a bigger payoff.
Understanding your enemy matters. Resecurity understood how Scattered Lapsus$ Hunters operated, what they looked for, and how they validated successful breaches. That knowledge informed the honeypot design.
Deception scales better than detection. Detecting intrusions requires monitoring constantly. Deception requires building a trap once and then waiting. It's a more efficient use of resources.
Public disclosure can be a weapon. By publicly revealing SLH's embarrassment and law enforcement involvement, Resecurity damaged the group's reputation in the underground economy. You can't recruit new members or attract legitimate criminal partners if you're known to have been caught by an obvious trap.
Law enforcement matters. Without coordinating with law enforcement and sharing evidence, Resecurity's honeypot is interesting but ultimately limited in impact. With law enforcement involved, it becomes a prosecution tool.
Documentation is critical. The fact that Resecurity preserved everything in admissible form, with timestamps and verified evidence chains, is what transforms technical achievement into legal accountability.

The Role of Organizational Security Culture
Resecurity's ability to deploy a successful honeypot reflects deeper organizational competencies:
They understood their own infrastructure deeply enough to replicate it convincingly. That requires detailed asset inventories, documented network architecture, and security architecture documentation.
They had incident response and forensic capabilities in-house. They could set up monitoring, preserve evidence, and analyze results without relying entirely on external parties.
They had security leadership willing to accept risk. Deploying a honeypot means accepting that attackers will have access to a portion of your infrastructure, even if it's deceptive. That requires courage and conviction that the long-term benefit (catching attackers) outweighs the short-term risk.
They had legal and compliance expertise to ensure the honeypot met legal requirements and didn't violate privacy laws in their jurisdiction.
They had strong relationships with law enforcement. Sharing evidence with authorities requires trust, clear communication protocols, and confidence that law enforcement will follow up.
Not every organization has these capabilities. But the organizations that do—large security firms, financial institutions, government agencies—have options that smaller organizations don't.
For most enterprises, the lesson isn't "deploy honeypots." It's "understand your environment so completely that you could deploy honeypots if you needed to." That kind of complete environmental knowledge is what defenders need to compete with sophisticated attackers.
Future of Deception-Based Security
What Resecurity did is becoming more common. Security vendors increasingly offer "deception-based security" platforms that automate honeypot deployment and management.
These platforms typically work by:
Creating fake infrastructure automatically—fake servers, databases, cloud instances
Seeding fake credentials throughout real systems in ways attackers will find them
Monitoring all access to fake resources with complete forensic logging
Alerting immediately when attackers interact with honeypots, providing early warning
Gathering intelligence about attacker tools, techniques, and processes
The impact is that defenders are gradually shifting from purely reactive (waiting to detect breaches) to proactive (setting traps and catching attackers).
This shift raises important questions about the future of cybercriminals:
If honeypots become ubiquitous, how do threat actors adapt? They might avoid networks they're not extremely confident about. They might move more toward supply-chain attacks where they compromise one vendor to reach many customers. They might shift to attacks that don't require long dwell times inside networks.
Does this increase the cost of cybercrime? If successful attacks become harder because networks are increasingly deceptive, the returns on attack investment decrease. That might push less-skilled or less-motivated criminals out of the game.
Does this change the nature of prosecution? As attribution becomes more reliable through forensic evidence, the legal consequences of cybercrime increase. Younger or less careful criminals become more vulnerable to prosecution.
The Scattered Lapsus$ Hunters honeypot might be a preview of a future where attacks that seem successful turn out to be disasters, where confidence leads to exposure, and where organizations have the means to not just defend but to actually trap and help prosecute attackers.

FAQ
What exactly is a honeypot in cybersecurity?
A honeypot is a deliberately vulnerable or attractive but fake system designed to appear as a legitimate part of your network infrastructure. It contains no real sensitive data, but is monitored to detect and analyze attacker behavior. When attackers access the honeypot thinking it's a real system, their activities are logged and analyzed, providing defenders with forensic evidence of the attack, including IP addresses, techniques used, and tools deployed. Honeypots are useful both for early detection of intrusions and for gathering intelligence about attacker methods.
How did Resecurity know Scattered Lapsus$ Hunters would target their company?
Resecurity likely didn't know for certain that SLH would target them specifically, but they understood the broader threat landscape and SLH's targeting patterns. They probably anticipated attacks from advanced threat actors given their profile as a security company with valuable data. They may also have deliberately seeded information about a vulnerability they knew fit SLH's exploitation patterns, creating an attractive target. This combination of understanding threat actor behavior and deliberately making their infrastructure appear vulnerable created the conditions for SLH to target them.
What is the legal significance of the honeypot evidence for prosecution?
The honeypot evidence is legally significant because it provides a complete forensic record of the attack from initial compromise through data exfiltration. It includes IP addresses, linked personal accounts, timestamps, file access logs, and network connection details. This evidence, carefully preserved and validated, is admissible in court and can establish that specific individuals attempted to gain unauthorized access to computer systems and exfiltrate data, which are the core elements of federal computer fraud statutes. The evidence trail is so complete that it's difficult for defendants to claim they weren't involved or didn't intend to commit crimes.
Could Scattered Lapsus$ Hunters have detected the honeypot?
Theoretically, extremely careful attackers with extensive time and resources might have detected the honeypot through careful analysis—comparing file metadata timestamps, looking for unrealistic patterns in data, or testing whether supposedly sensitive information actually matched public knowledge about the company. However, SLH didn't employ these detection techniques. They moved quickly to exploit the apparent vulnerability, accessed data that appeared valuable, and immediately publicized their breach. Their overconfidence and rush to claim credit prevented them from conducting the due diligence that might have revealed the deception.
What happens if SLH members are arrested?
If arrested, SLH members would face federal charges under the Computer Fraud and Abuse Act and potentially wire fraud statutes, which carry penalties including significant prison time and fines. The charges could be prosecuted in US federal court if the attacked entity or infrastructure is US-based (Resecurity may qualify), or through international cooperation if members are in other countries. Some members might face additional charges related to other breaches they've claimed, like the Jaguar Land Rover incident. Younger members might face juvenile proceedings depending on their age and where they're prosecuted.
Are honeypots legal to deploy?
Honeypots are generally legal to deploy within your own infrastructure. However, their legality depends on jurisdiction and implementation details. In the US, honeypots deployed internally are legal for defensive purposes and generating forensic evidence. However, deploying honeypots in other jurisdictions, particularly Europe where data protection regulations are stricter, requires careful compliance with privacy laws like GDPR. Honeypots that capture data from legitimate users (not just attackers) can create legal liability. Organizations deploying honeypots should consult with legal and compliance teams to ensure implementation meets regulatory requirements.
How common are honeypots in enterprise security?
Honeypots are increasingly common but still relatively uncommon in their sophisticated form. Organizations with mature security programs, significant cybersecurity budgets, and dedicated security operations teams are more likely to deploy them. Financial institutions, government agencies, and large technology companies frequently use honeypots. Smaller organizations often lack the resources and expertise to deploy them effectively. However, security vendors increasingly offer managed honeypot services and deception-based security platforms that make deployment more accessible to mid-market organizations.
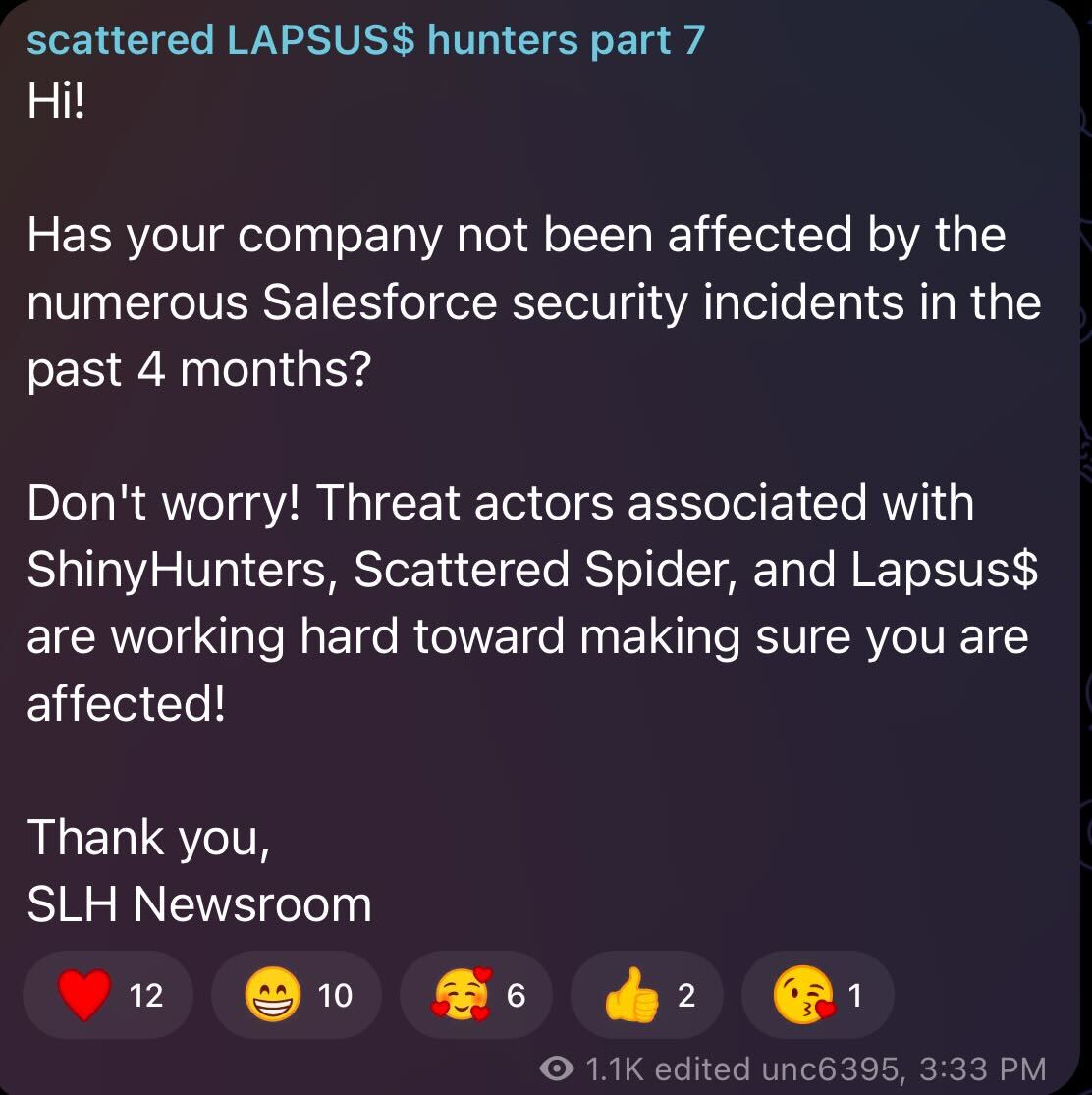
Could other threat actors learn from this incident?
Yes, absolutely. Sophisticated threat actors are likely analyzing what happened to Scattered Lapsus$ Hunters. They're learning that public announcements of breaches create forensic records that law enforcement can use against them. They're learning that defensive organizations might deploy sophisticated deception infrastructure. They're learning that attribution is becoming more reliable. Some groups might respond by becoming even more cautious, reducing their public profile, and avoiding unnecessary announcements. Others might double down on operational security or shift to attacks that leave fewer forensic traces. The incident raises the risk profile of cybercriminal activity globally.
Conclusion
The Scattered Lapsus$ Hunters honeypot story is a pivotal moment in the ongoing arms race between cybercriminals and defenders. For years, the narrative favored attackers. Sophisticated criminals operated with near-total impunity from jurisdictions that didn't cooperate with law enforcement. Even when breaches were detected, attribution was nearly impossible. Prosecution was rare.
Resecurity's honeypot success demonstrates that the calculus is shifting.
Attackers are becoming simultaneously more ambitious and more visible. The JLR breach was so massive that it drew government attention. Scattered Lapsus$ Hunters became a national security matter. Once you reach that profile, you have the full resources of intelligence agencies and coordinated law enforcement targeting you. A honeypot becomes the specific tool that transforms your operational security failures into prosecutable offenses.
But the broader implications are larger. They include:
Deception works. When defenders understand their environments completely and think creatively about defense, they can outmaneuver attackers who rely on conventional exploitation techniques.
Attribution is increasingly reliable. Forensic evidence, combined with traditional intelligence gathering, increasingly allows law enforcement to identify specific individuals behind major attacks. That should fundamentally change the risk-reward calculation for potential cybercriminals.
Organizational maturity matters. Resecurity could deploy a successful honeypot because they had the infrastructure knowledge, incident response capability, forensic expertise, and law enforcement relationships required. Organizations are being incentivized to develop complete visibility into their own environments, which has security benefits regardless of whether they ever deploy honeypots.
Scale creates exposure. Scattered Lapsus$ Hunters proved they could halt manufacturing at a Fortune 500 company. That massive success made them too big to ignore. Smaller, more careful criminals might evade law enforcement indefinitely. Large-scale operations by their nature become visible and attract attention.
For enterprises trying to build defensible security programs, the lesson is that defense doesn't mean only detecting intrusions. It means understanding your environment so completely that you can detect attacks early, respond decisively, preserve forensic evidence, and support law enforcement in prosecuting attackers.
For cybercriminals, the lesson is harsher. Operational security has become harder. Attribution has become easier. Prosecution has become more likely. The comfortable assumption of anonymity and impunity that allowed major hacking groups to operate openly is eroding.
Scattered Lapsus$ Hunters set out to embarrass Resecurity. Instead, they handed law enforcement the tools to embarrass and apprehend them. That represents a genuine shift in the balance of power in cybersecurity, and it signals a future where sophisticated defenders increasingly win against attackers, not through constant surveillance and reactive detection, but through patient deception and relentless attribution.

Key Takeaways
- Scattered Lapsus$ Hunters fell for a sophisticated honeypot trap containing only fake data and false infrastructure, exposing their entire operational infrastructure to law enforcement
- The honeypot incident reveals a fundamental shift in cybersecurity: defenders can now trap attackers through deception, rather than only detecting breaches reactively
- Complete forensic evidence including IP addresses, linked personal accounts, timestamps, and network connections was shared with law enforcement, creating a path to prosecution
- Honeypots and deception-based security platforms are becoming increasingly important defensive technologies that can both detect intrusions early and gather intelligence about attacker methods
- Attribution of cybercriminals is becoming more reliable through advanced forensic techniques, fundamentally changing the risk calculation for organized cybercriminal groups
Related Articles
- Blue Screen of Death Malware: How ClickFix Attacks Work [2025]
- Should You Use a VPN Browser? Complete Guide [2025]
- Jaguar Land Rover's 43% Sales Collapse After Cyberattack [2025]
- Deepfakes & Digital Trust: How Human Provenance Rebuilds Confidence [2025]
- NordVPN Salesforce Breach Claim: What Really Happened [2025]
- Covenant Health Breach Exposes 500K Patients: What Happened [2025]
![Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]](https://tryrunable.com/blog/scattered-lapsus-hunters-caught-in-honeypot-inside-the-bust-/image-1-1767717452879.jpg)



