From Bitcoin Heist to Cybersecurity: A Hacker's Path to Redemption
Introduction: The Second Act Nobody Saw Coming
Imagine stealing over 10 billion dollars worth of cryptocurrency. Now imagine walking out of prison and asking for a job in cybersecurity. That's not a movie plot. That's Ilya Lichtenstein's actual life story.
In early 2024, Lichtenstein posted on LinkedIn that he'd been released from prison and was looking to work in cybersecurity. The statement shocked many in the tech community. This wasn't just some wannabe hacker with grand ambitions. This was the guy who orchestrated one of the largest cryptocurrency thefts in history back in 2016, stealing 120,000 bitcoins from Bitfinex when the exchange was barely a household name. At today's prices, that haul is worth tens of billions of dollars, as noted by Statista.
But here's where it gets interesting. Rather than disappearing into the shadows like most criminals would, Lichtenstein did something unexpected. He cooperated with federal authorities. He helped recover the stolen assets. He assisted investigators on multiple high-profile crypto cases. And now, after serving nearly four years in federal prison, he's genuinely trying to turn his life around.
This isn't a simple redemption story where the bad guy becomes good and everything works out. It's far more complicated than that. It's about what redemption actually means in the tech industry. It's about whether technical skill matters more than past mistakes. It's about whether society should give second chances to intelligent people who made catastrophically bad decisions when they were younger.
The Lichtenstein case forces us to think about several uncomfortable questions: Can a hacker truly change? Should companies hire reformed criminals if they possess elite technical skills? What's the difference between punishment and rehabilitation? And perhaps most importantly, do we believe in genuine second chances or just performative forgiveness?
This article dives deep into Lichtenstein's story, examining not just what happened, but what it means for the broader security industry, for cryptocurrency regulation, and for how we think about redemption in tech.
What Makes This Story Different
There have been hackers before. There have been thieves. There have even been criminals who helped the government catch other criminals. But Lichtenstein's case sits at the intersection of so many interesting tensions that it demands deeper analysis.
First, there's the sheer scale. We're not talking about stealing a few thousand dollars from a small exchange. We're talking about compromising one of the largest cryptocurrency platforms in the world during a formative moment for digital currency. The ripple effects were massive.
Second, there's the cooperation angle. Unlike many criminals who serve their time silently, Lichtenstein actively helped authorities. He didn't just take a plea deal and disappear. He became part of the solution. That's unusual in cybercrime cases and raises questions about trust and genuine change.
Third, there's the professional ambition. Most reformed criminals try to fade into normal life. They don't announce their plans to work in the same industry where they committed their crimes. That takes either remarkable confidence, genuine conviction about reform, or a troubling lack of self-awareness. Figuring out which it is matters.

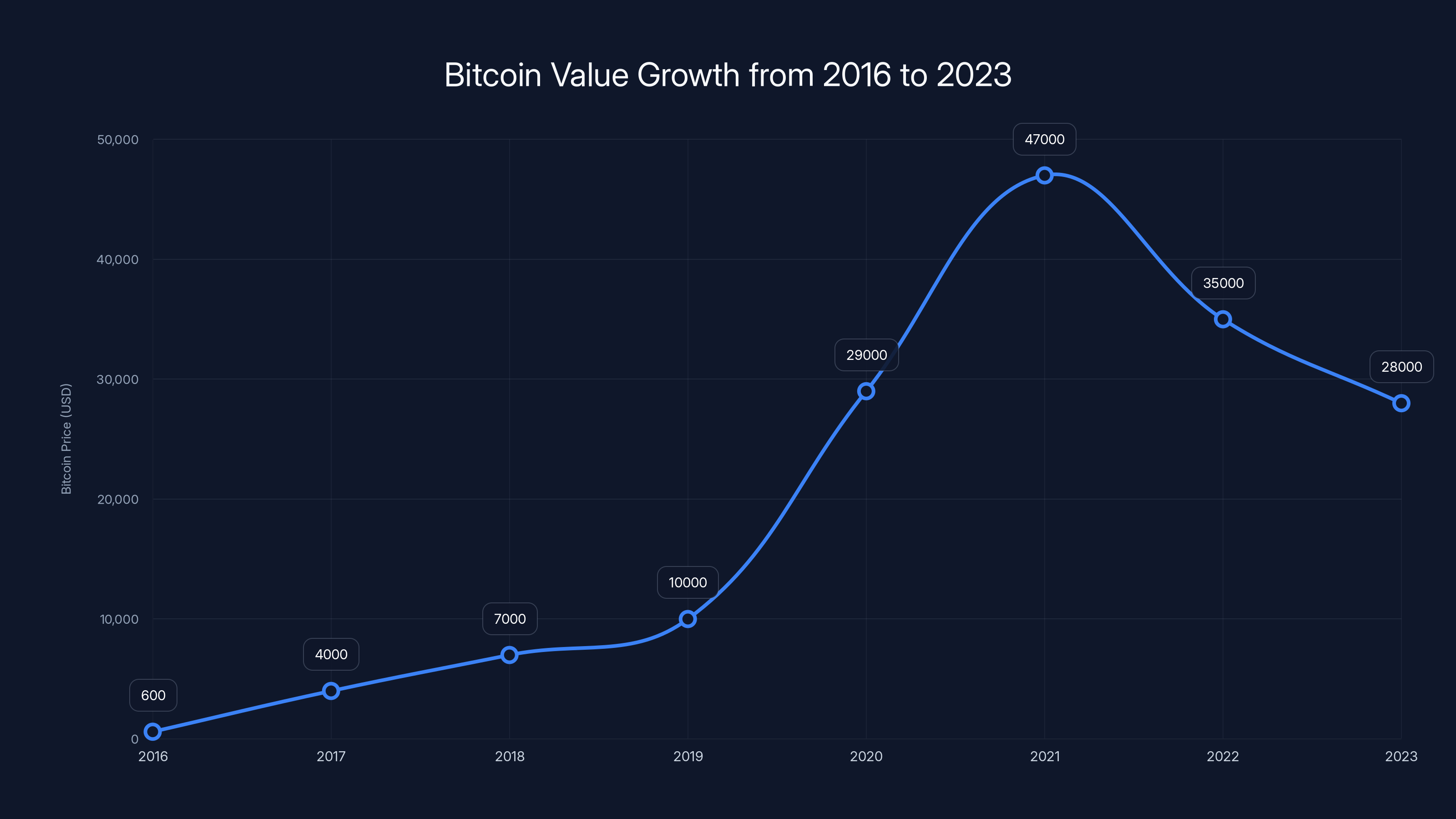
Bitcoin's value has seen significant growth since the 2016 Bitfinex heist, highlighting its transformation from a niche asset to a more mainstream investment. (Estimated data)
The 2016 Bitfinex Heist: When Cryptocurrency Met Organized Cybercrime
The Setup: A Perfect Storm of Opportunity
To understand why Lichtenstein chose to commit the heist, you need to understand the state of cryptocurrency in 2016. Bitcoin was valuable, but it wasn't the institutional asset it is today. Regulatory frameworks barely existed. Most exchanges were run by young entrepreneurs still learning how to secure massive amounts of digital currency. Security was an afterthought in many cases.
Lichtenstein's startup was struggling. Like many founders, he faced the pressure of building something meaningful while watching competitors raise funding and gain market share. He had technical skills. He had the knowledge to understand cryptocurrency systems. And he had access to Bitfinex.
The exchange wasn't some tiny operation. Bitfinex was one of the largest crypto trading platforms in the world at the time. It had thousands of users. It handled massive transaction volumes. But like many fast-growing tech companies, it was focused on velocity over security.
Here's where the criminal decision gets interesting. Rather than trying to improve his startup or seek legitimate funding, Lichtenstein decided to commit fraud. In an interview after his arrest, he admitted that desperation and poor decision-making drove him. His startup was failing. He needed capital. Instead of asking for help or taking a conventional loan, he decided to steal.
The decision was almost incomprehensibly shortsighted. He was bright enough to execute a sophisticated heist. Yet he wasn't wise enough to recognize that getting caught was inevitable. Digital currency leaves traces. Blockchain transactions are permanent. Law enforcement agencies improve their capabilities every year. Getting away with a 120,000 bitcoin theft wasn't a realistic goal. It was a fantasy masked as a plan.
The Execution: How the Hack Happened
The actual theft was sophisticated but not extraordinarily complex by modern standards. Lichtenstein and his wife, Heather Morgan, exploited vulnerabilities in Bitfinex's systems. They gained unauthorized access to customer accounts and exchange wallets. They siphoned off the bitcoins methodically.
What made the operation notable wasn't the technical wizardry. It was the audacity. They stole from one of the largest exchanges operating at the time. The theft triggered alerts across the cryptocurrency ecosystem. Major holders and exchanges became aware within hours that a serious breach had occurred.
Bitfinex responded publicly, confirming the theft and working with law enforcement. The exchange suspended operations temporarily while investigating. Users watched as billions of dollars in digital assets vanished. The incident shook confidence in cryptocurrency exchanges at a critical moment in the industry's development.
The aftermath was chaotic. Some users lost their holdings entirely. Others experienced delays accessing their accounts while the investigation unfolded. The incident became a cautionary tale about keeping large amounts of cryptocurrency on exchanges rather than in personal wallets.
What's particularly revealing is that despite stealing 120,000 bitcoins, Lichtenstein and Morgan didn't successfully disappear with the funds. They attempted to launder the money through various channels, but law enforcement tracked the movement of the stolen assets over years. Digital currency might provide some privacy advantages, but once you try to convert it to traditional currency or spend it, you create trackable transactions.
The Long Manhunt: When Technology Catches Up
The investigation took years. This wasn't a quick arrest. Law enforcement agencies had to trace cryptocurrency transactions, identify money laundering patterns, and build a case that would stand up in court. Blockchain analysis tools became increasingly sophisticated during this period, allowing investigators to follow the money even as criminals tried to obscure the trail.
Lichtenstein and Morgan lived relatively openly for years after the theft. They weren't hiding in foreign countries. They weren't living under assumed identities. They existed in New York City, occasionally traveling, attempting to use the stolen funds but not particularly carefully. This suggests either overconfidence or a naive belief that they could eventually integrate the stolen assets into their lives without detection.
When federal agents arrested them at their Manhattan home in 2022, it marked the end of years of investigation and the beginning of their legal reckoning. The charges included money laundering conspiracy and other related offenses. Both Lichtenstein and Morgan faced significant prison time, as reported by CNBC.
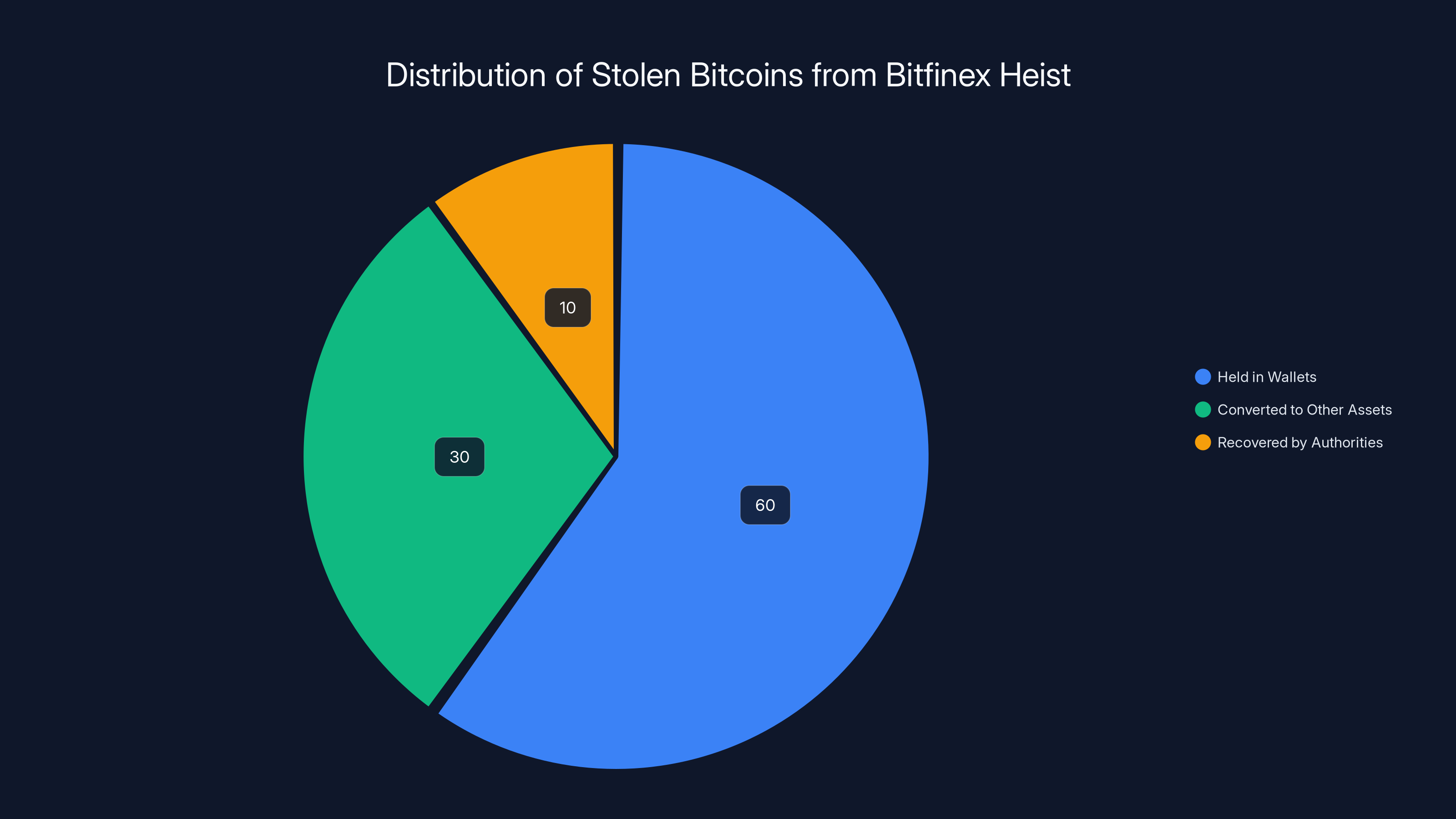
Estimated data showing that a significant portion of the stolen bitcoins remained in wallets, with a smaller amount converted to other assets and a portion recovered by authorities.
Prison, Redemption, and the Road to Reform
Five Years Behind Bars: The Transformation
Lichtenstein received a 60-month (five-year) prison sentence. He spent nearly four years in what he described as some of the harshest prisons in the country. Federal facilities range from minimum-security camp settings to maximum-security institutions. Lichtenstein's experience apparently included some of the tougher environments.
His account of life in prison provides insight into his mindset. Rather than wasting away or learning hardened criminal skills, he spent extensive time in the prison library studying mathematics. He engaged in intellectual pursuits. He reflected on his choices. This behavior is relatively uncommon in federal prisons, where many inmates focus on survival, forming connections, or just counting days until release.
The fact that Lichtenstein spent his time studying mathematics suggests several things. First, he was searching for intellectual stimulation. Second, he was using education as a form of mental survival, keeping his mind engaged to cope with the environment. Third, he was, perhaps, laying groundwork for eventual redemption by developing skills and maintaining intellectual rigor.
He describes his prison experience as isolating. Federal incarceration removes you from your entire support network. You lose your freedom, your career, your personal relationships. The psychological toll is significant, even for people adapting relatively well to the environment.
The Cooperation Angle: Working with Federal Authorities
One of the most interesting aspects of Lichtenstein's case is that he cooperated with federal authorities. After his arrest, he agreed to help investigators on various cryptocurrency cases. This wasn't a formal protective agreement where the government promised him a lighter sentence. He chose to cooperate.
According to Lichtenstein's own account, working with law enforcement was transformative. He describes the experience of "working with the good guys" as surprisingly fulfilling. When he was operating as a criminal, he was isolated and paranoid. Working as part of a team pursuing legitimate objectives felt different. He discovered that using his technical skills to solve problems and help others was more rewarding than using those same skills for criminal purposes.
This claim deserves scrutiny. It could be genuine. People do sometimes experience authentic transformations. They realize their skills were being used destructively and choose to redirect those skills toward constructive purposes. Or it could be partially performance, positioning himself as reformed to improve his reputation and prospects after release.
The truth is likely somewhere in between. Cooperation with federal authorities probably did provide Lichtenstein with a new perspective. Working on real security problems, helping catch other criminals, using his knowledge to strengthen systems rather than exploit them—those experiences probably did create genuine shifts in how he viewed his capabilities.
But framing this as some kind of spiritual awakening also serves Lichtenstein's interests. It makes him sympathetic. It suggests he's not just reformed out of legal obligation but out of genuine conviction. Whether that narrative is entirely accurate is impossible to determine from the outside.
Release to Home Confinement: The Next Phase
In early 2024, Lichtenstein was released to home confinement. This isn't full freedom. It means he can leave his residence but under supervision and with significant restrictions. He's been tagged with monitoring devices. His movements are tracked. He has regular check-ins with his supervising officer.
Home confinement is typically a step before full release. It allows formerly incarcerated individuals to reintegrate into society gradually while remaining under government oversight. It provides a testing ground for rehabilitation before complete freedom.
This is where Lichtenstein's LinkedIn post came into play. While on home confinement, with his future uncertain and his reputation in tatters, he publicly announced his desire to work in cybersecurity. He acknowledged the seriousness of his crime. He expressed genuine remorse. And he positioned his unique experience as an asset—someone who thinks like an adversary can be valuable in defensive security.
The Kevin Mitnick Precedent: When Hackers Go Legitimate
A Historical Parallel That Matters
Lichtenstein isn't the first hacker to serve time and then attempt legitimate redemption. The most notable precedent is Kevin Mitnick, one of the most famous hackers of the 1980s and 1990s.
Mitnick was convicted of multiple computer crime and phone fraud cases during an era when computer security was less sophisticated and law enforcement was still learning how to investigate cybercrime. He served time in federal prison. But unlike many criminals, he used his incarceration to reflect on his choices.
After release, Mitnick founded his own security consulting firm, Mitnick Security Consulting. He became a penetration tester, conducting authorized security testing for corporations and government agencies. He became a public speaker, sharing stories about his criminal past and lessons learned. He wrote books. He became a recognized expert in security.
Mitnick's transformation was remarkable. He took the skills he'd used to break into systems and redirected them toward helping organizations defend against the very attacks he'd once perpetrated. His criminal experience became an asset. Companies hired him specifically because he understood how attackers think.
Mitnick lived until 2023, building a legitimate career that spanned several decades. He demonstrated that genuine rehabilitation is possible. He proved that a hacker can transition from criminal to legitimate security professional.
Why the Mitnick Comparison Matters for Lichtenstein
Lichtenstein clearly understands the Mitnick precedent. His LinkedIn post basically references this exact parallel. He's positioning himself as another reformed hacker with valuable skills to offer. He's suggesting that his criminal background, combined with his technical knowledge and his apparent reform, makes him uniquely valuable as a security professional.
But there are important differences between Mitnick and Lichtenstein. Mitnick's crimes were against the digital infrastructure itself—hacking phone systems, accessing computer networks. His skills were in penetration and system exploitation. When he became a consultant, the value proposition was straightforward: hire the guy who used to break into systems to help you prevent break-ins.
Lichtenstein's crime was theft. Specifically, theft of digital assets. His skill was in identifying vulnerabilities in an exchange's security and exploiting them for financial gain. The value proposition is less clear. Yes, he understands how exchanges can be compromised. But that's somewhat different from being a general security consultant.
Additionally, Mitnick's path unfolded over time. He wasn't immediately hired by major corporations. He built his reputation gradually, demonstrating legitimate value over many years. Lichtenstein is arriving at this point already having served his sentence and already having assisted federal authorities. The timeline is different.
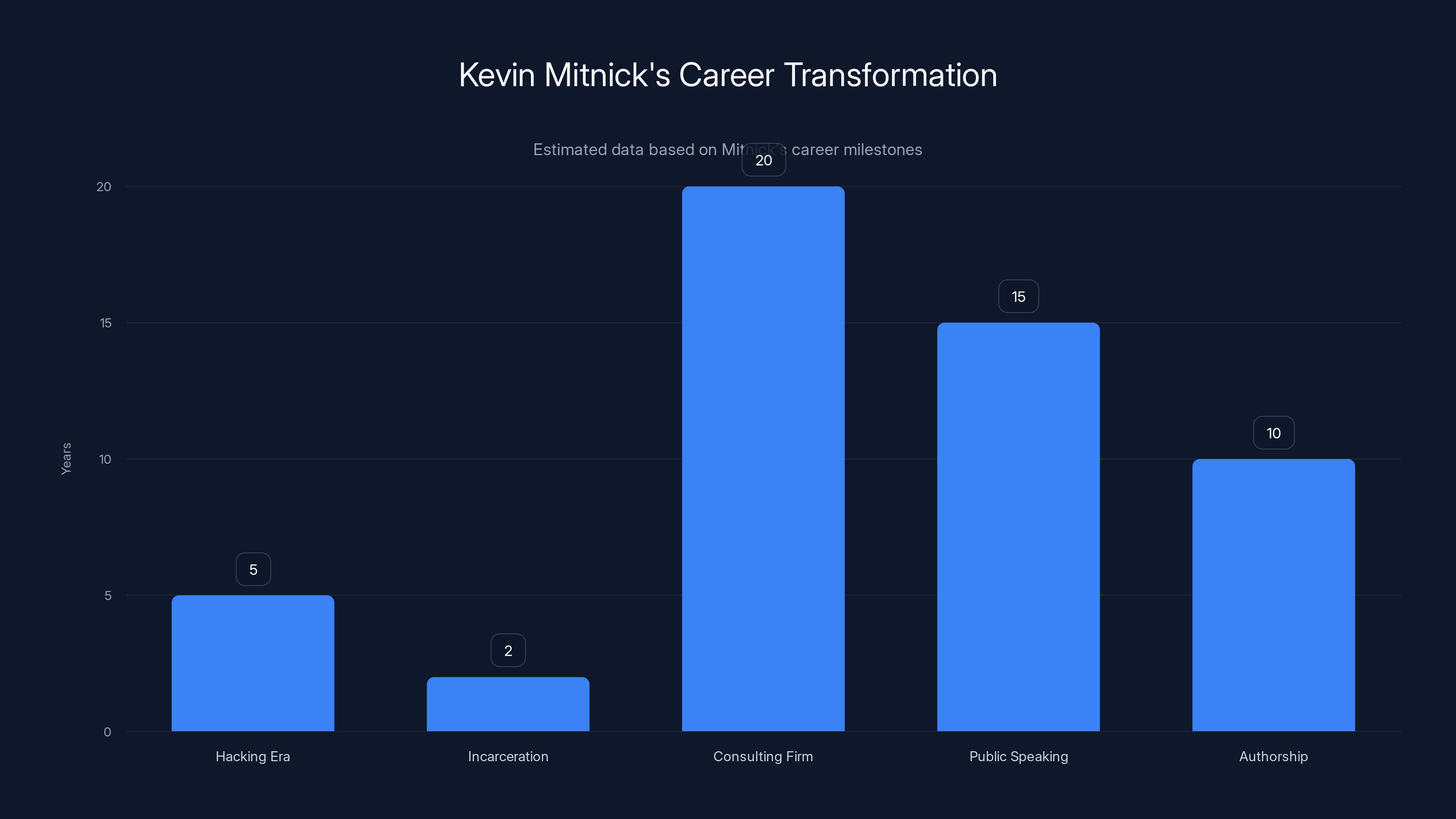
Estimated data shows Kevin Mitnick's career transformation from a hacker to a legitimate security expert over several decades.
The Cryptocurrency Theft Problem: Context for Understanding the Crime
Magnitude of the Problem Then vs. Now
When Lichtenstein stole 120,000 bitcoins in 2016, cryptocurrency theft was still relatively uncommon. Most of the crypto industry was small and emerging. Exchanges were learning security practices. Users were learning to protect private keys. Law enforcement had minimal experience investigating crypto crimes.
Today, cryptocurrency theft is a massive problem. In 2023 alone, losses from cryptocurrency fraud exceeded 14 billion dollars. Hacks, scams, and theft have become increasingly sophisticated. Criminal organizations have entire divisions dedicated to cryptocurrency crime.
The scale of the problem makes Lichtenstein's willingness to assist law enforcement more significant. He wasn't helping catch some trivial crime. He was helping law enforcement understand patterns and techniques that were becoming increasingly prevalent. His technical knowledge became more valuable as cryptocurrency crime became more sophisticated.
Evolution of Cryptocurrency Exchange Security
One major change since 2016 is how seriously exchanges now treat security. Bitfinex survived the theft and has spent millions improving its security posture. Other major exchanges have invested heavily in protection. Cold storage practices have become standard. Insurance products have emerged. Regulatory frameworks have developed.
The 2016 Bitfinex theft was a watershed moment for the industry. It demonstrated catastrophically what could happen if security wasn't treated as a primary concern. Every major exchange has since invested significantly in preventing similar incidents.
In that context, someone with actual knowledge of how these hacks happen could be genuinely valuable to exchanges seeking to harden their defenses. It's similar to how companies hire penetration testers—outside security experts who probe for vulnerabilities. The difference is that Lichtenstein wouldn't be authorized to test; he'd be advising on defense.
The Regulatory Response to Cryptocurrency Crime
Another context change is regulatory. In 2016, cryptocurrency existed in a regulatory grey zone. Nobody quite knew whether exchanges needed banking licenses, what compliance requirements applied, or how law enforcement should handle digital asset crimes.
Today, there's much more regulatory clarity. Exchanges are increasingly regulated. Know-Your-Customer (KYC) and Anti-Money-Laundering (AML) requirements apply to digital asset platforms. Law enforcement has dedicated cryptocurrency investigation units. Prosecutors have become much more sophisticated at handling digital asset crimes.
The Lichtenstein case itself benefited from this regulatory evolution. The fact that investigators could eventually track his stolen bitcoins and build a prosecutable case demonstrates how much law enforcement capabilities have improved, as noted by Coinfomania.
Redemption in Tech: Is Second Chances Really Possible?
The Philosophical Question
Lichtenstein's request for employment in cybersecurity raises a fundamental question: do we believe in second chances?
On one hand, there's an argument for redemption. Lichtenstein was young when he committed the crime. He made a catastrophic decision driven by desperation and poor judgment. He served his sentence. He cooperated with authorities. He spent his prison time studying and reflecting rather than hardening into criminal identity. He genuinely seems to have changed his perspective.
From a utilitarian perspective, it's wasteful not to employ a reformed criminal with elite technical skills if he's genuinely committed to contributing positively to society. Lichtenstein could be valuable in cybersecurity work. He understands how systems are exploited. He knows how criminal minds approach hacking. He could make real contributions.
On the other hand, there are legitimate concerns. Trust is fundamental in security work. How do you trust someone with system access when his criminal history involved betraying access in the most dramatic way possible? If a company hires Lichtenstein and then experiences a security incident, the optics are terrible. There's reputational risk.
Additionally, rewarding the successful criminal encourages crime. If Lichtenstein steals 10 billion dollars, serves a few years, and then lands a six-figure security job, what message does that send? It suggests that getting caught isn't catastrophically bad. Yes, you lose time. But you eventually rehabilitate and move forward.
Then there's the question of whether true reform is even possible or whether Lichtenstein is primarily concerned with escaping the consequences of his actions and reintegrating into the professional world.
Corporate Risk Considerations
From a corporate perspective, hiring Lichtenstein involves several layers of risk:
Reputational Risk: If the public learns that a company knowingly hired someone convicted of a 10-billion-dollar theft, there will be backlash. Customers might question whether the company's judgment is sound. Investors might worry about corporate governance.
Security Risk: Lichtenstein would need system access to be valuable in security work. Does the company have sufficient controls to prevent another major theft? Can they trust him implicitly? Or would they need to implement special monitoring that could be seen as insulting and would create a toxic work environment?
Legal Risk: If Lichtenstein is supposed to be monitoring things and something goes wrong, the company could face liability. There's also the question of disclosure—would the company need to tell its security team about his background? Would that create team dynamics issues?
Liability Risk: If Lichtenstein committed another crime while employed, what's the company's exposure? Could they be held liable for negligent hiring practices?
These aren't trivial concerns. They help explain why major companies might be hesitant to hire him despite his undeniable technical skills.
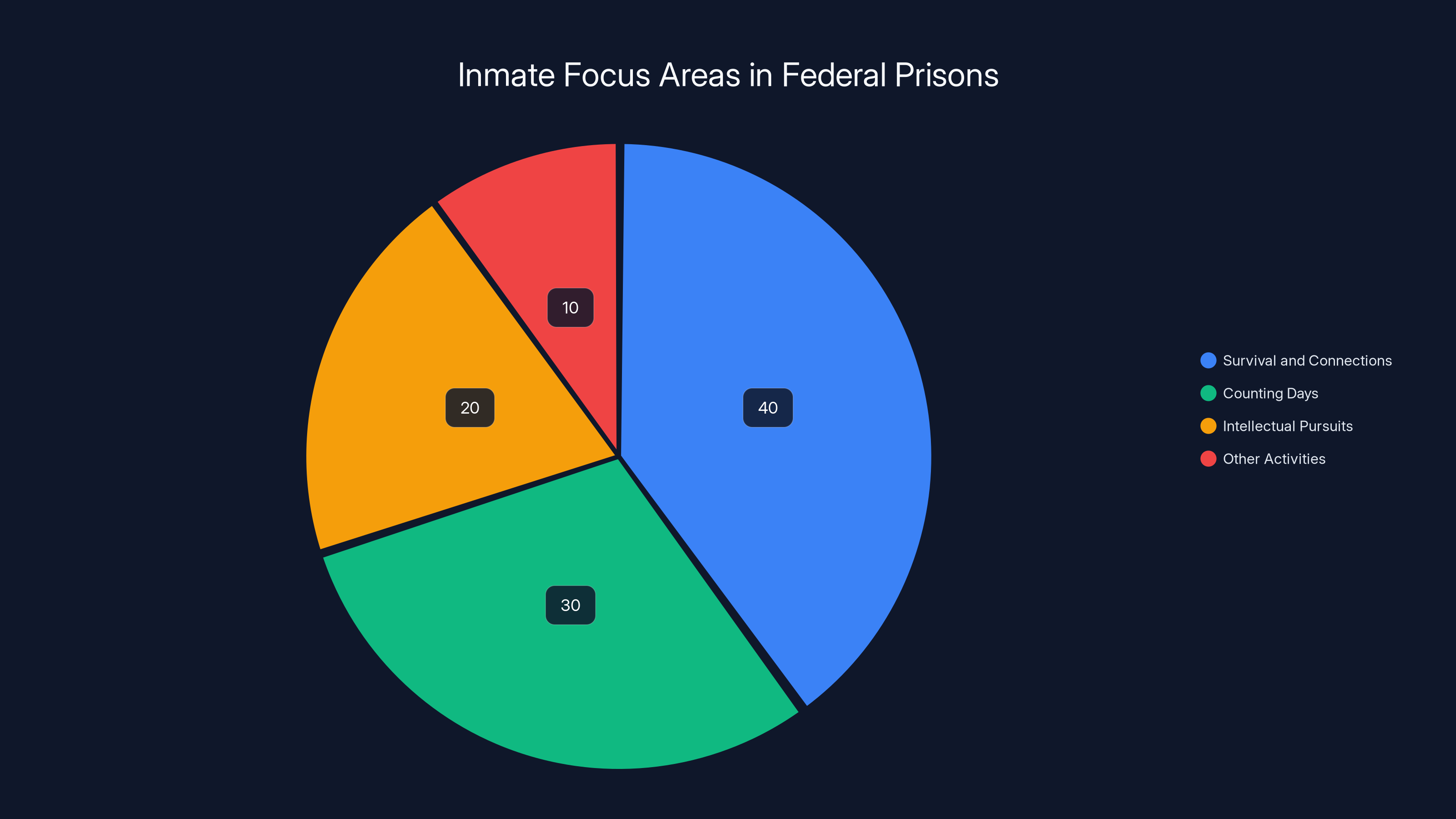
Estimated data suggests that while many inmates focus on survival and counting days, a minority, like Lichtenstein, engage in intellectual pursuits for rehabilitation.
The Nature of Cybersecurity Expertise: What Makes Someone Valuable
Technical Skills vs. Trust
In cybersecurity, technical skill is necessary but insufficient. You also need trust. Organizations have to trust that their security professionals aren't compromising systems for personal gain. They need to trust that access privileges are being used appropriately.
This is where Lichtenstein faces a structural challenge. He has the technical skills. He clearly understands how to compromise systems. But the trust component is harder to establish. Any security professional could theoretically commit fraud or theft. But Lichtenstein has actually done it. That history complicates everything.
Trusted security professionals typically develop their reputation over years of reliable work. They build credibility through demonstrated trustworthiness. For Lichtenstein, that credibility is starting from a deficit. He has to prove not just that he's competent, but that he's trustworthy in ways that ordinary security professionals don't have to prove.
The Value of Adversarial Thinking
There's something to be said for Lichtenstein's claim that thinking like an adversary is valuable in security work. It's true that penetration testers, red teamers, and security consultants benefit from understanding attacker perspectives. You're more effective at defending against attacks you understand deeply.
Lichtenstein has probably developed deep understanding of how exchanges are compromised, how digital assets are moved, how stolen funds are laundered. That knowledge is genuinely valuable from a defensive perspective.
But here's the nuance: that knowledge can be acquired in other ways. Security research, studying case studies of other breaches, working in forensic investigations, conducting authorized penetration tests—these all develop adversarial thinking without the baggage of actually having committed the crime.
Lichtenstein's advantage is that he has lived the crime. He understands not just the technical aspects but the psychological and operational aspects. He knows what investigators look for. He knows what mistakes criminals make. But again, that knowledge can be developed through law enforcement work, forensic analysis, or consulting with other reformed criminals.
It's not clear that Lichtenstein's personal criminal experience is actually necessary for him to be valuable in cybersecurity. It might be a differentiator. It might be why he believes he has something unique to offer. But it's not clear it's essential.
The Evolution of Security Careers
Cybersecurity as a profession has evolved significantly. It's now a mature field with structured career paths, certifications, established companies, and clear best practices. It's not like it was in the 1980s and 1990s when Kevin Mitnick was starting his career.
Today, someone can build a legitimate cybersecurity career by:
- Getting certified (CISSP, CEH, OSCP, etc.)
- Working in academia and research
- Starting at legitimate security companies
- Contributing to open-source security projects
- Publishing research
- Working in law enforcement or government agencies
- Building a track record through internships and junior roles
All of these paths are available to Lichtenstein if he's genuinely committed to legitimate work. The fact that he's promoting his criminal background as a credential suggests he might be trying to use that notoriety as a shortcut rather than building credibility through conventional means.

Cryptocurrency Law Enforcement: The Modern Battleground
How Blockchain Analysis Has Transformed Investigations
One of the most significant developments since the 2016 Bitfinex theft is the emergence of blockchain analysis as a investigative tool. Companies like Chainalysis, TRM Labs, and Elliptic now provide law enforcement with sophisticated tools for tracking cryptocurrency transactions.
These tools work by analyzing blockchain data, identifying patterns, and linking cryptocurrency addresses to real-world individuals and entities. They can track stolen funds as they move through mixing services and exchanges. They can identify connections between addresses that appear unrelated.
The Lichtenstein case demonstrates how effective these tools have become. Despite years of attempting to hide the stolen bitcoins, investigators eventually tracked them. The blockchain's permanent record of transactions meant there was nowhere for the stolen assets to truly hide.
This is relevant to Lichtenstein's case because it shows that law enforcement capacity has grown dramatically. The investigators who eventually caught Lichtenstein had capabilities that barely existed when he committed the crime. That growth in law enforcement sophistication means that future thieves face even steeper odds of evading capture.
International Cooperation in Crypto Crime
Another significant development is increased international cooperation on cryptocurrency crimes. Organized crime groups were exploiting differences in how different countries regulated and investigated cryptocurrency activities. As more nations have developed cryptocurrency law enforcement capabilities, coordination has improved.
The FBI, IRS Criminal Investigation, Secret Service, and other U.S. law enforcement agencies now coordinate closely on cryptocurrency crimes. International cooperation through organizations like Interpol and UNODC has also increased.
This matters because it means that fleeing the country is no longer a viable strategy for cryptocurrency criminals. Your assets might be hidden in another jurisdiction, but law enforcement can pursue them across borders through proper legal channels.
The Role of Cooperation in Modern Cryptocurrency Cases
Lichtenstein's cooperation with federal authorities is particularly significant in this context. As cryptocurrency crime has become more sophisticated, law enforcement has increasingly relied on cooperation from insiders and perpetrators who've been caught.
When someone like Lichtenstein helps authorities understand how particular attacks work, what vulnerabilities were exploited, and how the stolen funds were handled, that knowledge becomes invaluable for:
- Improving exchange security practices
- Developing better law enforcement investigative techniques
- Training prosecutors and agents on cryptocurrency crime patterns
- Helping other victims of similar attacks
- Building better blockchain analysis tools
Lichtenstein's cooperation likely resulted in concrete improvements to cryptocurrency security and law enforcement capabilities. That's a genuine contribution to public safety, even if it came as part of a guilty plea arrangement.
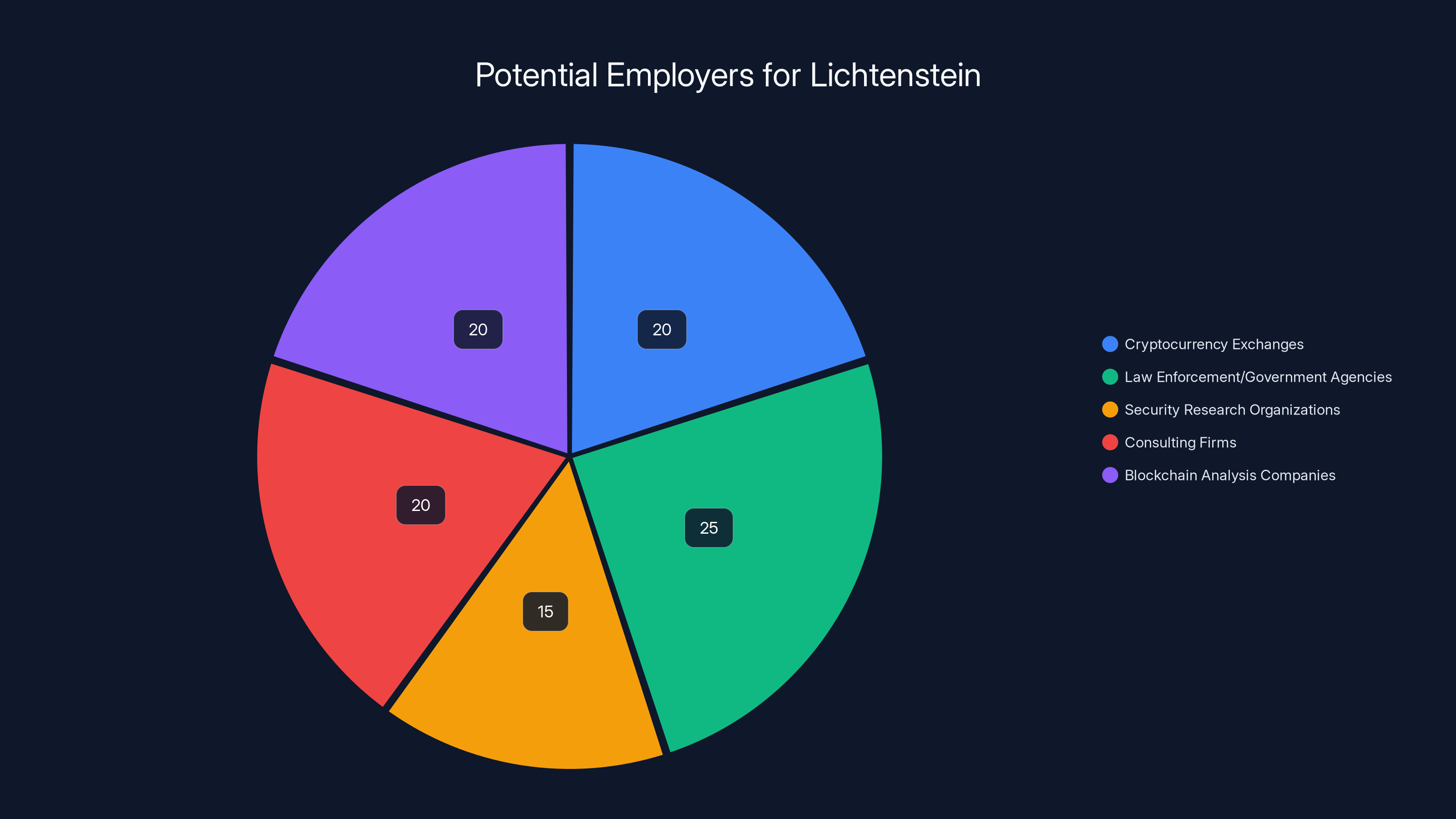
Estimated data suggests that law enforcement and government agencies might show the highest interest in hiring Lichtenstein, followed by consulting firms and cryptocurrency exchanges. Estimated data.
The Money Laundering Problem: How Stolen Cryptocurrency Gets Hidden
The Challenge of Converting Digital Assets
Once Lichtenstein and Morgan stole the bitcoins, they faced the fundamental problem of every digital asset thief: converting the stolen funds into something useful while not getting caught.
You can't simply spend bitcoins openly. Every major exchange requires identity verification before allowing withdrawals. You can't transfer stolen bitcoins into a bank account without the exchange knowing something is wrong. You can't just walk into a Bitcoin ATM and cash out 120,000 bitcoins without triggering massive alarms.
Money laundering—the process of hiding the origins of illegally obtained money—becomes the critical problem. Criminals need ways to convert stolen digital assets into cash or legitimate investments without creating a trail that leads back to the theft.
Traditional money laundering techniques involve moving money through multiple channels, mixing it with legitimate funds, and slowly integrating it into the financial system. Cash-based businesses like restaurants or casinos have historically been used because they naturally process large amounts of cash.
But digital asset laundering is different. The transactions are recorded on the blockchain forever. You can't physically hide bitcoins. You can move them between wallets, but the movement is visible to anyone analyzing the blockchain.
Mixing Services and Obfuscation Techniques
Criminals have developed several techniques for attempting to obscure the origins of stolen cryptocurrency:
Tumbling Services: These services take your cryptocurrency, mix it with other users' funds, and return different cryptocurrency to you, theoretically breaking the transaction chain. However, sophisticated blockchain analysis can sometimes identify patterns even through tumbling.
Privacy Coins: Monero and similar cryptocurrencies offer better privacy than Bitcoin. By converting stolen Bitcoin to Monero and then back, criminals attempt to break the trail. But this creates its own risks and hasn't proven as effective as many hoped.
Lightning Network and Sidechains: These payment layer solutions can move funds off the main blockchain. However, they eventually need to settle back to the main chain, and the settlement creates a transaction record.
Breaking It Into Smaller Chunks: Instead of moving large amounts that trigger alerts, criminals break stolen funds into smaller amounts moved through different channels at different times. This is slower but less obvious.
Trading for Other Assets: Converting to other cryptocurrencies, NFTs, or other digital assets that might be harder to trace. But this usually requires exchange interactions that create transaction records.
The fundamental problem remains: digital assets are traceable. Law enforcement and blockchain analysis companies have become better at following the money over time. The more moves a criminal makes to hide stolen assets, the more transaction records they create, and the more opportunities for investigators to find the trail.
Why Lichtenstein Got Caught
Despite attempting various money laundering techniques, Lichtenstein and Morgan were eventually caught. Investigators could follow the movement of the stolen bitcoins through their attempts to hide them. The combination of blockchain analysis and traditional financial investigation created a trail back to them.
Their arrest six years after the initial theft suggests that law enforcement was patient but thorough. They documented the full trail of the stolen assets. They identified the money laundering attempts. They built a prosecutable case, as detailed by CryptoRank.
The lesson for other potential crypto criminals is clear: getting away with digital asset theft is possible temporarily, but permanent escape is increasingly unlikely. Blockchain analysis tools have become too sophisticated. Law enforcement coordination has improved too much. The digital footprint is too permanent.

The Regulatory and Ethical Landscape: What's Changed Since 2016
From Wild West to Regulated Industry
In 2016, cryptocurrency existed in regulatory ambiguity. Nobody quite knew what the rules were. Exchanges operated with minimal oversight. Users had minimal consumer protection. Criminals exploited this uncertainty.
Today, the regulatory landscape has matured significantly. Major jurisdictions have established frameworks for digital asset exchanges. Know-Your-Customer (KYC) and Anti-Money-Laundering (AML) requirements apply to cryptocurrency platforms. Financial crimes investigation units exist in most developed countries.
Bitfinex itself was part of this regulatory evolution. The exchange faced regulatory scrutiny after the theft. It eventually settled with New York authorities for significant fines. It established more robust compliance programs. It improved security practices dramatically.
This regulatory maturation has made cryptocurrency exchanges safer for users and harder to exploit for criminals. It's also made the industry more legitimate and mainstream. What was once a frontier for technical enthusiasts and speculators is becoming a genuine financial infrastructure.
Ethical Responsibility in Exchange Operations
The Bitfinex theft also highlighted the ethical dimension of operating a cryptocurrency exchange. When your platform is hacked and users lose funds, you have responsibility to those users. You need to communicate transparently. You need to compensate victims if possible. You need to improve security.
Bitfinex's response to the theft, while not perfect, established some important precedents:
- Transparently communicating the breach to users
- Working with law enforcement
- Improving security infrastructure
- Eventually compensating most affected users through recovered assets
- Implementing regulatory compliance
These responses weren't guaranteed. Some companies in Bitfinex's position have simply shut down operations or disappeared entirely. Bitfinex chose to continue operating and to improve.
For Lichtenstein, understanding this ethical dimension matters. If he's going to work in cryptocurrency security, he needs to grasp not just the technical aspects but the ethical responsibility of protecting user assets. The fact that his actions harmed thousands of exchange users should inform his perspective on why security matters.
The Role of Standards and Best Practices
Since 2016, cryptocurrency exchanges have also adopted industry standards and best practices. The National Institute of Standards and Technology (NIST) provides cybersecurity frameworks that exchange operators can follow. Industry groups publish guidelines for secure operations.
Cold storage for cryptocurrency (keeping assets offline in secure vaults) has become standard practice. Multi-signature requirements (requiring multiple people to approve large transactions) are now common. Regular security audits by third parties are expected.
These improvements wouldn't exist without lessons like the Bitfinex theft. Each major hack has resulted in the industry adopting better practices. In that sense, even the damage from the theft contributed to improvements that protect future users.
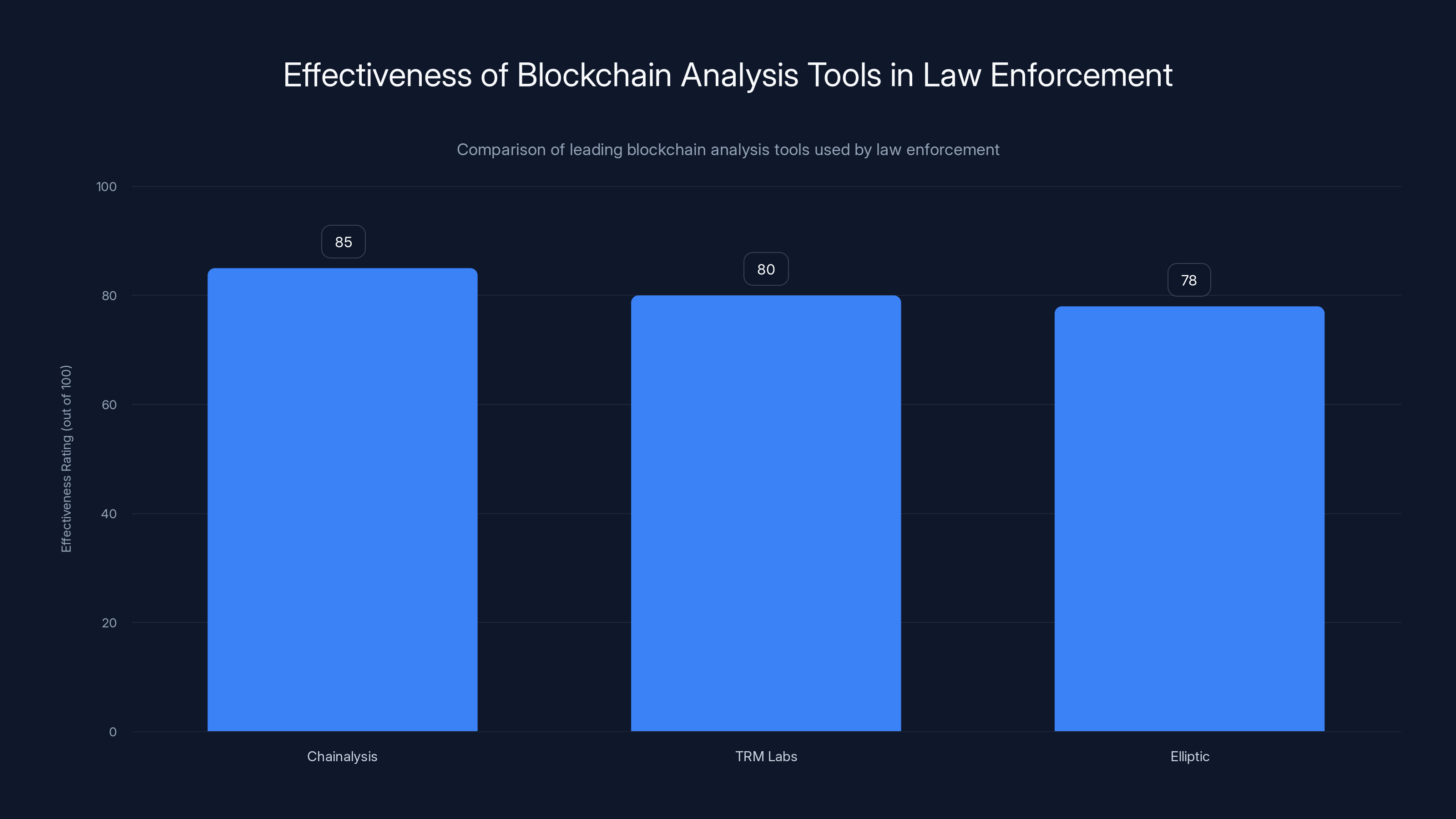
Blockchain analysis tools like Chainalysis, TRM Labs, and Elliptic have significantly enhanced law enforcement's ability to track and recover stolen cryptocurrency, with effectiveness ratings above 75%. Estimated data.
Practical Employment Prospects: Could a Major Company Actually Hire Lichtenstein?
Who Might Consider It
There are a few categories of employers who might realistically consider hiring Lichtenstein:
Cryptocurrency Exchanges: An exchange wanting to prove its security commitment might hire a reformed insider like Lichtenstein as a consultant or auditor. It's risky PR but also potentially impressive—showing such confidence in internal controls that you can hire a former criminal.
Law Enforcement or Government Agencies: Federal agencies often hire reformed criminals as advisors or investigators. Lichtenstein's experience could make him valuable to the Secret Service, FBI, or other agencies working on cryptocurrency crime.
Security Research Organizations: Academic or research-focused organizations studying cryptocurrency security might hire Lichtenstein for his expertise. This would focus on research rather than operational roles.
Consulting Firms: Security consulting firms working with government or large corporations might hire Lichtenstein. They could position him as an expert in digital asset security threats.
Blockchain Analysis Companies: Companies like Chainalysis might value his expertise in understanding how criminals move stolen assets.
Each of these carries reputational risk, but each also has potential benefits from hiring someone with genuine, deep expertise.
Barriers to Mainstream Corporate Employment
Large mainstream technology companies are unlikely to hire Lichtenstein, at least in the near term. The reputational risk is too high. If a Fortune 500 company hired someone convicted of a 10-billion-dollar theft and then experienced a security incident, the backlash would be severe.
Additionally, Lichtenstein would face employment verification challenges. Many corporate roles require security clearances or background checks that go beyond criminal records. They verify employment history, educational credentials, and references. After his crime, Lichtenstein's employment history is checkered. Building a conventional corporate career will be difficult.
Cybersecurity leadership roles in large corporations are particularly unlikely. Organizations want their security leaders to have unblemished reputations. Hiring someone with Lichtenstein's background would signal to the organization and to customers that the company's judgment is questionable.
Building Credibility Gradually
If Lichtenstein is genuinely serious about a legitimate career in cybersecurity, the realistic path would be:
- Start with government or law enforcement work where his background is less of a barrier
- Build a track record of legitimate contributions
- Publish research demonstrating expertise
- Work as a consultant or independent security researcher
- Gradually build reputation in the security community
- Possibly transition to mainstream corporate roles much later, if ever
This path requires patience. It requires building credibility through demonstrable work rather than relying on past notoriety. It means starting over from scratch professionally, despite being highly talented technically.
Lichtenstein's LinkedIn post suggesting he wants a security job might be premature. He's just released from prison. He doesn't have demonstrated track record in legitimate work yet. If he's serious about redemption, the focus should be on building that track record first.
The Broader Implications: What This Case Reveals About Tech Industry Values
Meritocracy vs. Moral Character
The Lichtenstein case forces the tech industry to confront fundamental tensions. The industry has historically valued meritocracy—the idea that technical skill and capability matter most. If someone can code well or secure systems effectively, they should be hired and advanced regardless of other factors.
But this meritocratic ideal has limits. Most companies recognize that other factors matter. Trust matters. Ethical standards matter. Moral character matters.
The question Lichtenstein's case raises is: where's the balance? How much does demonstrated technical skill matter compared to demonstrated moral lapses? Can someone genuinely change enough to overcome a massive crime?
Different people in the tech industry will answer these questions differently. Some will view Lichtenstein as having paid his debt and deserving a fresh start. Others will view his crime as disqualifying and believe he should be excluded from security-sensitive work permanently.
There's legitimate disagreement about the right answer. The tech industry needs to figure out where it stands on questions of redemption, second chances, and how past behavior should inform hiring decisions.
The Role of Narrative Control
Another thing Lichtenstein's LinkedIn post reveals is how narrative control matters in the modern era. By getting ahead of his own story, by publicly acknowledging his crime, expressing remorse, and positioning his experience as valuable expertise, Lichtenstein is attempting to shape how people perceive him.
This is a sophisticated PR strategy. It's not denying the crime. It's not hiding from accountability. Instead, it's framing the crime as a learning experience and positioning the criminal as reformed.
From a marketing perspective, it's actually quite clever. But it also raises questions about whether the narrative is honest. Is Lichtenstein genuinely reformed? Or is he demonstrating sophisticated understanding of how to rehabilitate a public image?
The difficulty in assessing genuine change is that truly reformed people and people skillfully performing reform can look identical from the outside. You can't tell the difference just from words. You have to observe behavior over time.
Creating Pathways for Genuine Reform
If the tech industry genuinely believes in redemption and second chances, it needs to create pathways for that. It needs ways for reformed criminals to contribute and rebuild their lives. Right now, those pathways are limited and informal.
Some industries have begun addressing this more systematically. Law enforcement agencies hire reformed criminals as advisors and investigators. Some government agencies have second-chance hiring initiatives. Some security research organizations specifically work with people who have backgrounds in cybercrime.
But mainstream tech companies haven't really figured out how to incorporate formerly incarcerated people, especially those with criminal histories related to security or finance. Creating those pathways would require developing trust mechanisms, designing roles with appropriate oversight, and accepting some risk.
It's not clear whether the industry should do this. There are legitimate concerns about liability, reputation, and security. But if companies believe in genuine redemption, they should be honest about the barriers and either commit to removing them or acknowledge that they don't actually believe in second chances.

Future Predictions: Where This Story Goes From Here
The Most Likely Scenario
Based on historical precedent and the current state of the security industry, the most probable outcome is that Lichtenstein eventually finds meaningful work in cybersecurity, but not in a mainstream corporate environment.
He'll likely work as:
- A government contractor or law enforcement advisor
- An independent security consultant
- A researcher for a specialized security firm
- An educator teaching others about digital asset security threats
He probably won't work for a major tech company or mainstream corporation anytime soon. The reputational risk is too high, and there aren't strong institutional drivers pushing for his employment.
He'll build credibility slowly through legitimate contributions. Over years, his reputation will shift from "famous crypto thief" to "reformed expert in digital asset security." That shift takes time and sustained positive work.
His criminal past will always be part of his identity professionally. It won't go away. But it can be contextualized as part of his journey toward expertise rather than his defining characteristic.
Alternative Scenarios
There are other possible outcomes:
The Failure to Reform: If Lichtenstein hasn't genuinely changed, he might eventually return to criminal activity. The pressures and temptations that led him to crime originally might resurface. This would be a tragic but not unprecedented outcome.
The Premature Celebration: The security industry might embrace Lichtenstein too quickly, hiring him for high-profile roles before he's demonstrated sufficient trustworthiness. This could backfire spectacularly if he commits another crime or if the public backlash becomes severe.
The Perpetual Outsider: Lichtenstein might spend years seeking legitimate employment in security but face consistent barriers. He might remain essentially unemployable in mainstream roles despite his technical capabilities, making him bitter and potentially driving return to criminal activity.
The Quiet Transition: Lichtenstein might successfully transition to legitimate work without much publicity. He might avoid the spotlight, build credibility in specialized areas, and eventually become just another security professional with an unusual background.
The outcome depends on many factors: whether his reform is genuine, how the industry responds, how he handles rejection, and whether law enforcement continues supporting him.
What This Tells Us About Redemption
The Lichtenstein case will likely become a reference point for how the tech industry thinks about redemption. Depending on how his story unfolds, it could either strengthen or weaken the case for hiring reformed criminals.
If Lichtenstein succeeds—if he builds a legitimate career, contributes meaningfully to cybersecurity, and doesn't reoffend—his story becomes a powerful narrative about second chances and genuine change. It suggests that redemption is possible and that technical talent shouldn't be wasted because of past mistakes.
If he fails—if he reoffends, if legitimate employment proves impossible despite cooperation, or if his reform turns out to be performative—his story becomes a cautionary tale. It suggests that some crimes are too serious to move past, that trust can't be rebuilt, and that genuine change is harder than we'd like to believe.
Most likely, his story will be somewhere in between. He'll have some successes and some disappointments. He'll find work, but not in his dream roles. He'll contribute meaningfully in some areas and face limitations in others. His path will illustrate both the possibility and the difficulty of genuine redemption.

FAQ
Who is Ilya Lichtenstein and what did he do?
Ilya Lichtenstein is a hacker who, along with his wife Heather Morgan, orchestrated the 2016 theft of 120,000 bitcoins from Bitfinex, a major cryptocurrency exchange. At the time worth approximately $10 billion today, this heist was one of the largest cryptocurrency thefts in history. Lichtenstein and Morgan used the stolen funds through various money laundering techniques until they were arrested in 2022. Both pleaded guilty to money laundering conspiracy.
How was Lichtenstein caught after so many years?
Lichtenstein was caught through a combination of blockchain analysis and traditional law enforcement investigation. Investigators used specialized blockchain analysis tools to trace the movement of the stolen bitcoins as they were moved through various wallets and attempted to be converted into other assets. The permanent and traceable nature of blockchain transactions meant that despite money laundering attempts through mixing services and other obfuscation techniques, law enforcement could eventually follow the money back to Lichtenstein and Morgan. The investigation took approximately six years from the initial theft to arrest.
Why did Lichtenstein cooperate with federal authorities?
According to Lichtenstein's own account, he chose to cooperate with federal authorities because the experience of working with law enforcement teams to solve security problems was more fulfilling than his previous life as an isolated criminal hacker. He described the collaboration with "the good guys" as surprisingly rewarding and stated that using his technical skills to help prevent crimes rather than commit them provided genuine purpose. Additionally, cooperation arrangements with federal authorities often result in more favorable sentencing, though Lichtenstein still received a 60-month prison sentence.
Is the Kevin Mitnick precedent applicable to Lichtenstein's case?
The Mitnick precedent is relevant but not directly applicable. Kevin Mitnick, a famous hacker from the 1980s-1990s, served prison time for computer crimes and subsequently built a legitimate career as a security consultant and penetration tester. While both are reformed hackers, their crimes differ: Mitnick's involved system exploitation while Lichtenstein's involved digital asset theft and money laundering. Additionally, the security industry has evolved significantly since Mitnick's era, becoming more professionalized and more cautious about hiring reformed criminals. However, Mitnick's successful career does demonstrate that genuine rehabilitation and legitimate employment in security are possible.
What are the realistic employment prospects for Lichtenstein in cybersecurity?
Realistic employment prospects for Lichtenstein include government and law enforcement advisory roles, independent security consulting, specialized research positions at academic or security research organizations, and possibly employment with blockchain analysis companies. Mainstream corporate technology companies are unlikely to hire him in the near term due to reputational risk. A realistic career path would involve starting with government-related work, building a track record of legitimate contributions, publishing research demonstrating expertise, and gradually building reputation over many years before potentially transitioning to mainstream corporate roles, if that becomes possible.
What does Lichtenstein's case reveal about cryptocurrency theft and money laundering?
The case demonstrates that while digital asset theft is technically possible, long-term concealment is extremely difficult. Blockchain transactions create permanent records that modern analysis tools can trace through mixing services and money laundering attempts. The evolution of blockchain analysis capabilities between 2016 (when the theft occurred) and 2022 (when arrests happened) shows how quickly law enforcement can adapt to new crime types. The case illustrates that digital assets cannot truly be "hidden" the way physical currency can be, making perpetual escape increasingly unlikely for cryptocurrency criminals.
How has the cryptocurrency industry changed since the 2016 Bitfinex theft?
The cryptocurrency industry has evolved significantly since 2016. Regulatory frameworks have matured substantially, with most jurisdictions establishing clearer rules for digital asset exchanges. Exchange security practices have improved dramatically, with cold storage, multi-signature requirements, and regular third-party audits now standard. Law enforcement agencies have developed specialized cryptocurrency investigation units. Blockchain analysis tools have become sophisticated enough to trace stolen assets effectively. International cooperation on cryptocurrency crime has increased. The Bitfinex theft itself drove many of these improvements as the industry learned from the incident.
Can someone genuinely change after committing a major crime?
Whether genuine change is possible is a fundamental philosophical question without a universal answer. From a utilitarian perspective, if someone demonstrates genuine reform over time through consistent behavior and positive contributions, society benefits from allowing reintegration. Psychologically, research suggests that people can change, especially when they experience consequence, reflection, and new perspectives. However, trust cannot be instantly granted based on words alone. Genuine redemption requires consistent demonstration of changed behavior over extended periods. In Lichtenstein's case, evaluating whether his reform is genuine would require observing his behavior over years of freedom, not just his LinkedIn post.
What prevents Lichtenstein from finding mainstream corporate employment?
Several barriers prevent Lichtenstein from mainstream corporate employment: reputational risk (companies fear backlash from hiring someone convicted of major theft), trust issues (security roles require high levels of trust, which Lichtenstein's crime history undermines), liability concerns (if a company hiring Lichtenstein experiences a security incident, they face potential negligent hiring liability), background verification barriers (his employment history is checkered, making conventional hiring processes difficult), and the fundamental challenge that large corporations want security leaders with unblemished reputations. These barriers aren't necessarily unjustified—they reflect real concerns about liability and organizational culture.
How does Lichtenstein's case reflect broader tech industry values regarding meritocracy and character?
The case forces the tech industry to confront tensions between meritocratic ideals (technical skill above all) and moral character considerations (trustworthiness and ethical standards). The industry has historically emphasized meritocracy but also maintains, practically speaking, that character and trustworthiness matter. There's no consensus on how to balance these values when considering someone like Lichtenstein. Different organizations and individuals will answer the question differently, reflecting broader disagreements about redemption, second chances, and how much past behavior should influence future employment decisions. The industry needs to develop clearer, more systematic approaches to this tension if it intends to genuinely offer pathways for reformed criminals.
What would need to happen for Lichtenstein to be hired by a major corporation?
For Lichtenstein to be hired by a major corporation would likely require: many years of demonstrated legitimate work in security, published research or recognized expertise in cryptocurrency security, strong references from credible sources, successful completion of his home confinement period and any supervised release terms, a significant shift in public perception of his character, a major change in corporate culture regarding hiring practices, and likely a role that doesn't involve direct access to critical systems. Even with all these factors, hiring would carry reputational risk that most corporations wouldn't accept. More realistically, he might transition to a major corporation only after building reputation in niche or government-related security work first.

Conclusion: The Uncertain Future of a Reformed Hacker
Ilya Lichtenstein's story sits at the intersection of several powerful forces: the possibility of genuine human change, the persistence of past mistakes, the evolution of the tech industry's values, and the question of what redemption actually means in practice.
He stole 10 billion dollars worth of cryptocurrency from a major exchange. That's not a minor transgression. That's not something that can be easily forgiven or forgotten. Thousands of users experienced losses. The entire cryptocurrency ecosystem suffered a loss of confidence. The crime had real consequences for real people.
But he also served his time. He spent years in federal prison, studying in the library, reflecting on his choices. He cooperated with law enforcement. He helped authorities understand cryptocurrency crime patterns. He apparently came to see the value in using his considerable skills for constructive rather than destructive purposes.
Whether his reform is genuine or performative, only time will tell. Words are easy. Sustained changed behavior is harder. The real test of Lichtenstein's redemption won't be whether he gets hired by a major security firm. It will be whether, years from now, he's still working legitimately, still contributing positively to the security community, still maintaining his commitment to having changed.
For the tech industry, his case forces important questions. Do we believe in genuine second chances? Are we willing to accept some risk to give people pathways to legitimate employment after they've served their time? Or do we believe some crimes are so serious that they permanently disqualify people from certain work?
These aren't easy questions, and reasonable people disagree about the answers. But they're questions the industry needs to grapple with intentionally, not just handle case-by-case based on the specifics and publicity of each situation.
What's certain is that Lichtenstein has already changed the trajectory of his life. He went from isolated criminal paranoia to a public figure attempting to rebuild his reputation. Whether that rebuilding succeeds will be a measure not just of his personal redemption, but of whether the security industry and tech companies genuinely believe that change is possible and that second chances have value.
His LinkedIn post suggested he wants to work in cybersecurity to prevent "the next billion-dollar hack." If he succeeds in that mission, even partially, his massive crime might eventually be understood as a learning experience that made him a better security expert. If he fails, his crime will remain primarily an example of what happens when technical brilliance meets poor judgment and moral failure.
The story isn't finished. The outcome remains uncertain. And that uncertainty is perhaps the most honest reflection of what redemption actually looks like in the real world.
Key Takeaways
- Ilya Lichtenstein stole 120,000 bitcoins from Bitfinex in 2016, worth over $10 billion at today's valuations, but was eventually caught through advanced blockchain analysis.
- After serving nearly four years in federal prison, Lichtenstein cooperated with law enforcement on cryptocurrency cases and now seeks legitimate work in cybersecurity.
- The Kevin Mitnick precedent shows reformed hackers can build legitimate careers in security, but Lichtenstein's digital asset theft crime differs substantively from Mitnick's system exploitation crimes.
- Mainstream corporate employment remains unlikely for Lichtenstein, but realistic paths exist through government work, research organizations, and specialized security consulting.
- The case reveals fundamental tensions in the tech industry between meritocracy (technical skill) and character considerations, forcing difficult questions about redemption and second chances.
![From Bitcoin Heist to Cybersecurity: A Hacker's Path to Redemption [2025]](https://tryrunable.com/blog/from-bitcoin-heist-to-cybersecurity-a-hacker-s-path-to-redem/image-1-1769121465228.jpg)



