North Korean Hackers Target VS Code: Lazarus Group's Contagious Interview Attack Campaign [2025]
You're scrolling through job postings on a Tuesday afternoon. An email lands in your inbox from what looks like a legitimate tech company. They're impressed with your GitHub profile. They want to interview you for a senior developer role. The salary's incredible. The process moves fast. They send you a link to clone a repository. You open it in Visual Studio Code. Nothing seems unusual.
Then, quietly, your machine gets compromised.
This isn't hypothetical. It's happening right now to developers across the globe. The North Korean state-sponsored threat actor known as the Lazarus Group has evolved their infamous Contagious Interview campaign to weaponize one of the most popular developer tools on the planet: Microsoft Visual Studio Code. What makes this particularly insidious is how it leverages legitimate workflows. You're not visiting a malicious website. You're not opening a sketchy email attachment. You're doing your job. You're following normal development practices. And that's exactly why it works.
The Contagious Interview campaign has been around for years, but the tactics keep shifting. Security researchers at Jamf recently documented a troubling evolution. The attackers have refined their approach to create what amounts to a supply chain attack disguised as a job interview. They're targeting JavaScript developers, blockchain engineers, and security researchers in Western countries. They're after access to corporate networks, intellectual property, and crypto wallets. And they're using VS Code's trust system against developers who have every reason to believe they're authenticating a legitimate repository.
This is serious business. The Lazarus Group has been linked to some of the largest cryptocurrency heists in recent years. We're talking about tens of millions of dollars in stolen assets. The North Korean government allegedly uses these proceeds to fund weapons development and circumvent international sanctions. When you zoom out, a single developer accepting what seems like a legitimate job interview isn't just a personal security issue. It's a potential national security concern.
But here's what matters for you right now: understanding how the attack works, recognizing the red flags, and implementing the defensive measures that actually protect your systems.
TL; DR
- The Campaign: Lazarus Group's Contagious Interview uses fake job offers to trick developers into cloning malicious Git repositories and opening them in VS Code.
- The Attack Vector: Malicious Git repositories leverage VS Code's trust system to automatically execute arbitrary commands through the tasks.json configuration file.
- The Payload: On macOS systems, attackers retrieve JavaScript payloads that establish persistent backdoors for data harvesting and command-and-control communication.
- The Scale: The campaign has been linked to some of the largest cryptocurrency thefts in recent years, targeting developers across North America, Europe, and Asia.
- The Defense: Enable advanced threat detection, scrutinize untrusted repositories, and implement endpoint protection on developer machines before they become vectors for network compromise.

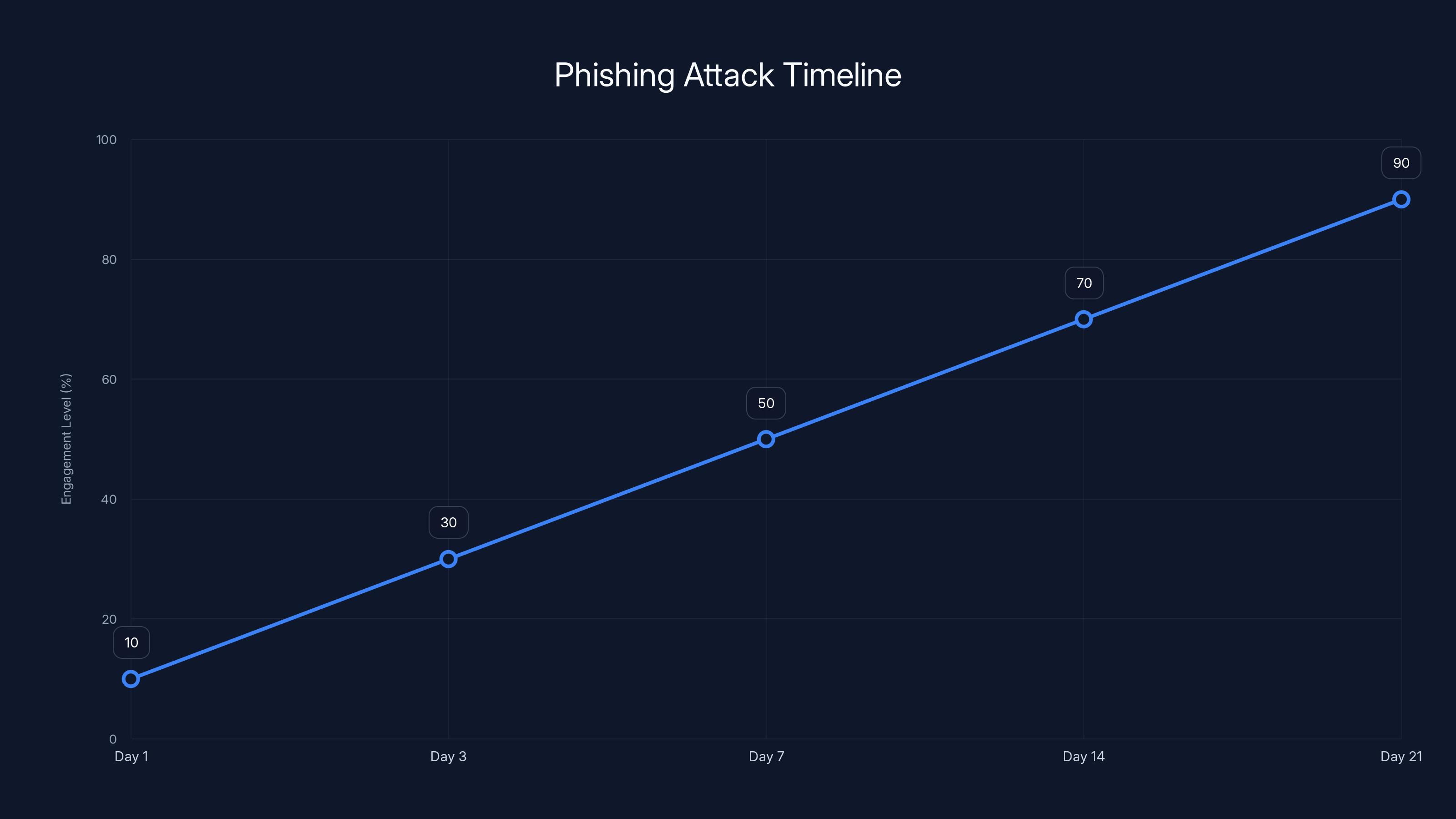
The engagement level in a phishing attack increases over time as the attacker builds trust and rapport with the target. Estimated data based on typical attack progression.
Understanding the Contagious Interview Campaign: Origins and Evolution
The Contagious Interview campaign didn't emerge overnight. It's the product of years of refinement by one of the world's most technically sophisticated state-sponsored threat actors. To understand what's happening now, you need to understand where it came from.
The Lazarus Group first gained international notoriety for the 2014 Sony Pictures hack, a devastating cyberattack that destroyed thousands of computers and exposed confidential data. Since then, they've been consistently linked to major incidents including the WannaCry ransomware outbreak in 2017, the ATM malware known as Fastcash, and most notably, the massive cryptocurrency exchange heists that have filled North Korean government coffers with hundreds of millions of dollars.
Contagious Interview represents a shift in their targeting strategy. Rather than broad-based malware campaigns, they've adopted a highly targeted social engineering approach. They're not trying to infect thousands of random users. They're trying to compromise specific individuals who have access to valuable resources: developers at cryptocurrency exchanges, blockchain firms, venture capital funds, and technology companies with deep-pocketed networks.
The campaign got its name from the interview-based recruitment process. The attackers create fake LinkedIn profiles associated with legitimate-sounding companies. They identify potential targets based on their skills, their work history, and their apparent access to valuable assets. Then they reach out with an opportunity that seems too good to be true because, well, it is.
What makes this approach so effective is its exploitation of normal human psychology. If you're a developer looking for a job, you want to believe good opportunities exist. You want to think that a company found you because of your talents. The attackers understand this. They flatter their targets. They move quickly. They create urgency. By the time the victim realizes something's wrong, the malware is already installed.
The evolution that researchers at Jamf documented in 2024 and early 2025 shows that the Lazarus Group is learning and adapting. They're incorporating newer attack methods. They're leveraging legitimate developer tools in ways that bypass traditional security controls. They're making their malware harder to detect and more persistent. This is what you get when you combine the resources of a nation-state with the creativity of advanced threat actors who have years of successful campaigns under their belt.
What's particularly concerning is the shift toward developer-centric attacks. Developers are the keys to the kingdom in modern organizations. They have access to source code repositories, production systems, cloud infrastructure, and sensitive data. Compromising a single developer can give attackers weeks or months of undetected access to a company's most critical systems.
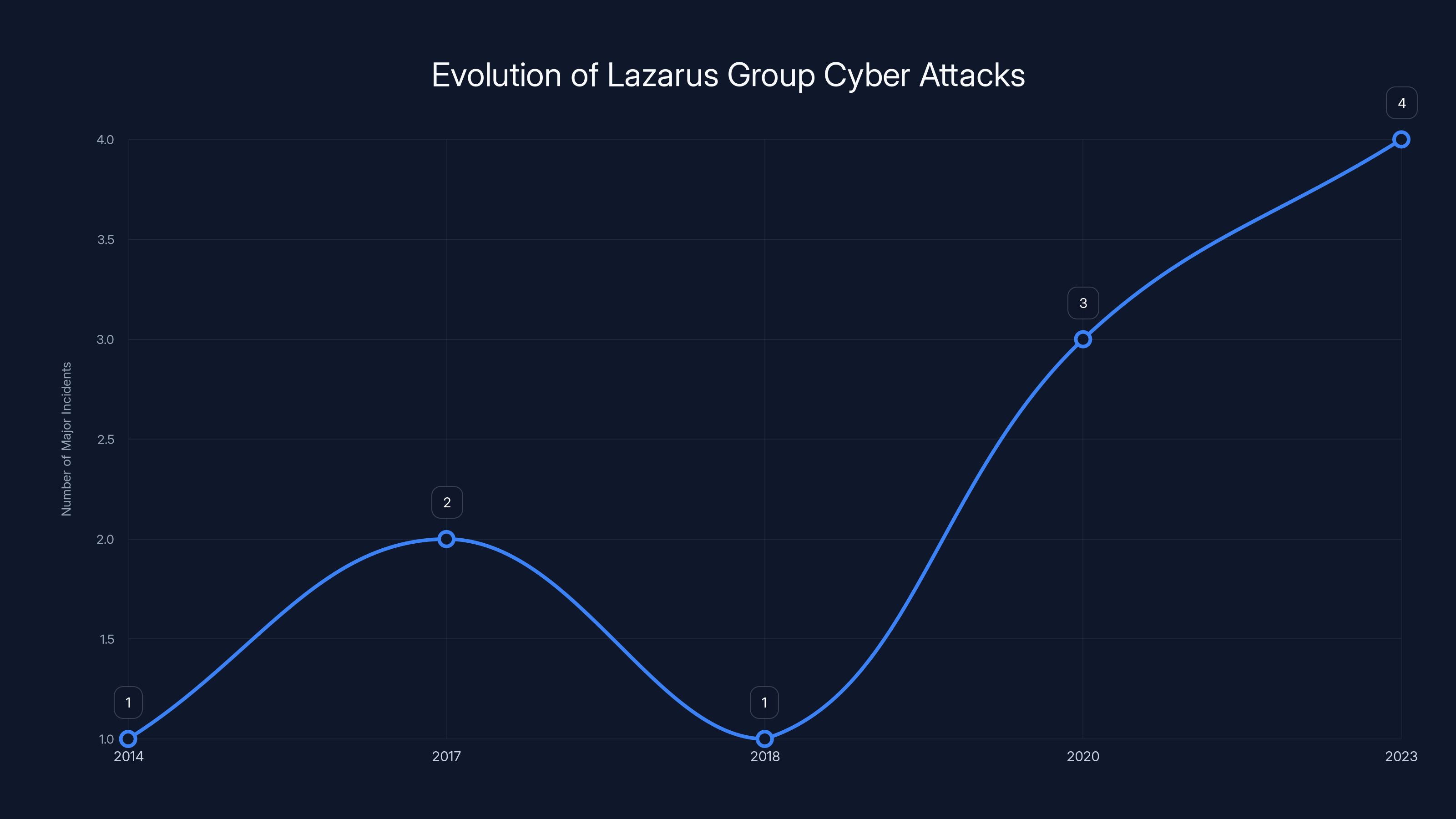
The Lazarus Group has evolved from broad cyberattacks like the Sony hack to targeted campaigns such as the Contagious Interview, increasing their major incidents over time. Estimated data.
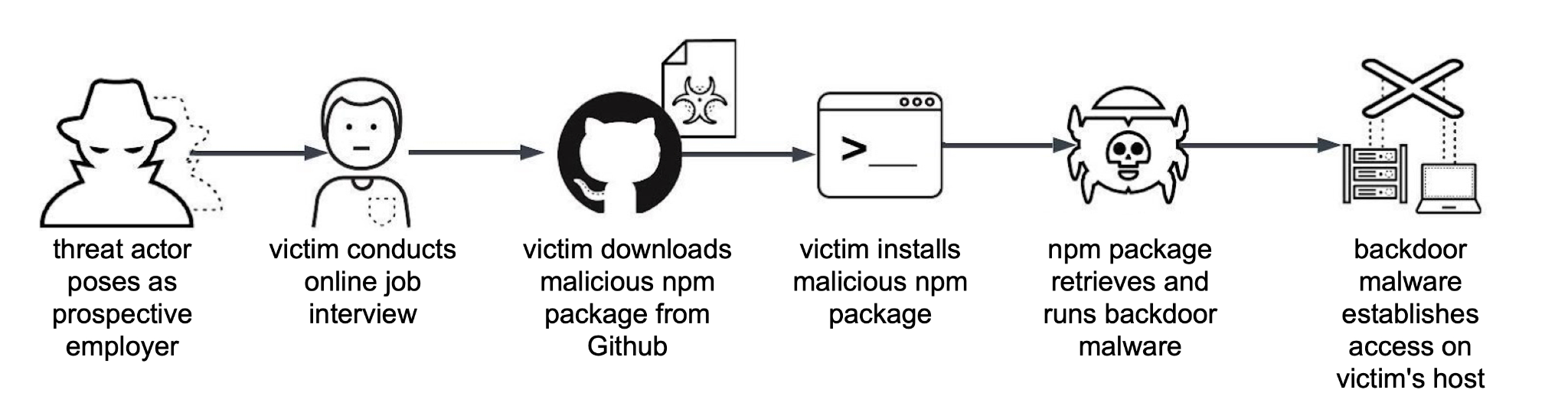
How the Attack Works: Step-by-Step Technical Breakdown
The technical execution of this attack is brilliant in its simplicity. It doesn't rely on zero-day vulnerabilities or complex code exploits. Instead, it weaponizes legitimate features of developer tools in ways that are technically sound but socially manipulative.
Here's how it unfolds:
Step 1: The Initial Contact and Fake Recruitment Process
It starts with a LinkedIn message. The attacker has done their homework. They know your technical skills. They understand your career trajectory. The message is personalized. It mentions specific projects you've worked on. It comes from someone at a company you've heard of, or a company that sounds credible in your industry.
The initial conversation is friendly and informal. There's no request for money. There's no urgency yet. The attacker is building rapport. They ask you questions about what you're looking for in your next role. They listen to your answers. They're learning about your motivations, your constraints, and what kind of opportunity would genuinely interest you.
This phase can last days or even weeks. The goal is to make the target comfortable. The attacker wants you to think of them as a real person, not a threat. They might share details about the company culture, the team you'd be joining, the technical challenges you'd be solving. Everything is designed to make the opportunity feel authentic.
Step 2: The Technical Assessment and Repository Handoff
Eventually, the attacker proposes moving to the "technical assessment" phase. This is where legitimate developers expect to prove their skills. Maybe they're asked to implement an algorithm. Maybe they're asked to review some code. Maybe they're asked to work with an existing codebase.
The attacker provides a Git repository link. It's hosted on GitHub or GitLab. It might look like this: a legitimate-sounding project name, proper documentation, a clean commit history. Everything that a real repository would have.
The attacker tells you to clone the repository and open it in Visual Studio Code. They explain that VS Code will auto-configure the environment with the tasks.json file, which contains the build instructions and test commands. This is actually how many legitimate projects work. VS Code can automatically set up your development environment based on configuration files. It's a productivity feature.
But in this case, the tasks.json file contains something much more sinister.
Step 3: The VS Code Trust Prompt and Automatic Execution
When you clone and open the malicious repository in VS Code, the editor detects that the workspace has configuration files. It prompts you with a question: "Do you trust the authors of this repository?"
This is a crucial moment. The prompt is designed to be non-alarming. It's a standard security measure. Thousands of repositories have this prompt. Your brain has been primed to expect it. The attacker's social engineering has also prepared you. They've told you the repository is legitimate. They've explained what you're about to do. So you click "Yes, I trust the authors."
Once you do, VS Code processes the workspace configuration files automatically. It's supposed to just set up your build environment. Instead, the malicious tasks.json file triggers embedded commands.
Step 4: The JavaScript Payload Execution Chain
On macOS systems, the attack uses a clever technique. The malicious commands in tasks.json invoke a background shell process. This shell script doesn't do anything obviously malicious on the target machine. Instead, it reaches out to an external server (often hosted on a legitimate content delivery network like Vercel) and downloads a JavaScript payload.
The shell script then pipes this JavaScript directly into the Node.js runtime on the victim's machine. Node.js executes the JavaScript, which is where the real damage begins.
The JavaScript payload is small, purposeful, and designed to be difficult to analyze. It immediately begins harvesting information about the compromised system:
- The hostname of the machine
- MAC addresses of network interfaces
- The operating system version and build number
- The username of the logged-in user
- Network configuration details
This reconnaissance data is critical. The attacker uses it to understand what they've compromised and whether it's worth maintaining access or if this is a honeypot or security researcher's machine.
Step 5: The Persistent Backdoor Installation
If the reconnaissance is successful, the JavaScript payload establishes a persistent communication loop. It connects to a remote command-and-control (C2) server. Every few seconds or minutes, the backdoor "pings" this server, sending the harvested system data and waiting for new instructions.
Because the payload is written in JavaScript and executed through Node.js, it can be updated without touching the file system. The C2 server can send new JavaScript code that executes in memory. This makes it extremely difficult for traditional antivirus tools to detect.
More importantly, the attacker can now issue commands to the compromised machine. They can download additional malware. They can create new user accounts. They can establish SSH access. They can begin lateral movement within the organization's network. They can exfiltrate data. They can install ransomware. The initial compromise, which seemed innocuous, becomes a beachhead for a full-scale intrusion.
Step 6: The C2 Communication and Data Exfiltration
Once the backdoor is established, the attacker has a quiet, persistent channel for communication. The C2 server can send JavaScript commands that the backdoor executes. These commands might:
- Enumerate the user's files and directories
- Copy sensitive documents and upload them to the attacker's server
- Check for cryptocurrency wallets or API keys stored on the system
- Monitor for sensitive information being used
- Wait for specific actions (like logging into a work VPN) before taking additional steps
The beauty of this approach from the attacker's perspective is that it doesn't require malicious processes to be running continuously. The backdoor can go dormant, waking up only periodically to check in with the C2 server. This makes it harder to spot through process monitoring.
The Technical Architecture of the Attack
Understanding the architecture helps explain why this attack is so effective against technical defenders.
The attack operates at multiple layers:
Layer 1: Social Engineering: The fake job interview is the vector. Trust is established before the technical compromise.
Layer 2: Legitimate Tool Abuse: VS Code is a trusted application. Developers use it daily. The trust relationship between the user and the tool is exploited.
Layer 3: Configuration-Based Execution: The tasks.json file is a legitimate configuration file. It's not an executable. It's not a script that looks obviously malicious. It's configuration data that developers expect to see.
Layer 4: Shell Command Execution: The actual commands executed are shell scripts. These can be written in ways that don't look obviously malicious to a human reviewer.
Layer 5: External Payload Loading: The actual malicious code is retrieved from an external server. This means the initial attack package contains no executable malware. It only contains configuration and shell commands.
Layer 6: JavaScript Execution in Memory: The final payload executes in memory through Node.js. There's no malware file written to disk. Antivirus tools that scan files on disk won't detect it.
Layer 7: Persistent C2 Communication: The backdoor maintains ongoing communication with a remote server. Even if the user closes VS Code, the processes might persist through other mechanisms.
Each layer has been deliberately designed to evade specific types of security controls. A security tool that looks for malicious executables won't find anything. A tool that monitors file system changes might miss the initial compromise because nothing is written to disk. A tool that monitors network traffic might see the C2 communication, but it could be encrypted or disguised as legitimate traffic.
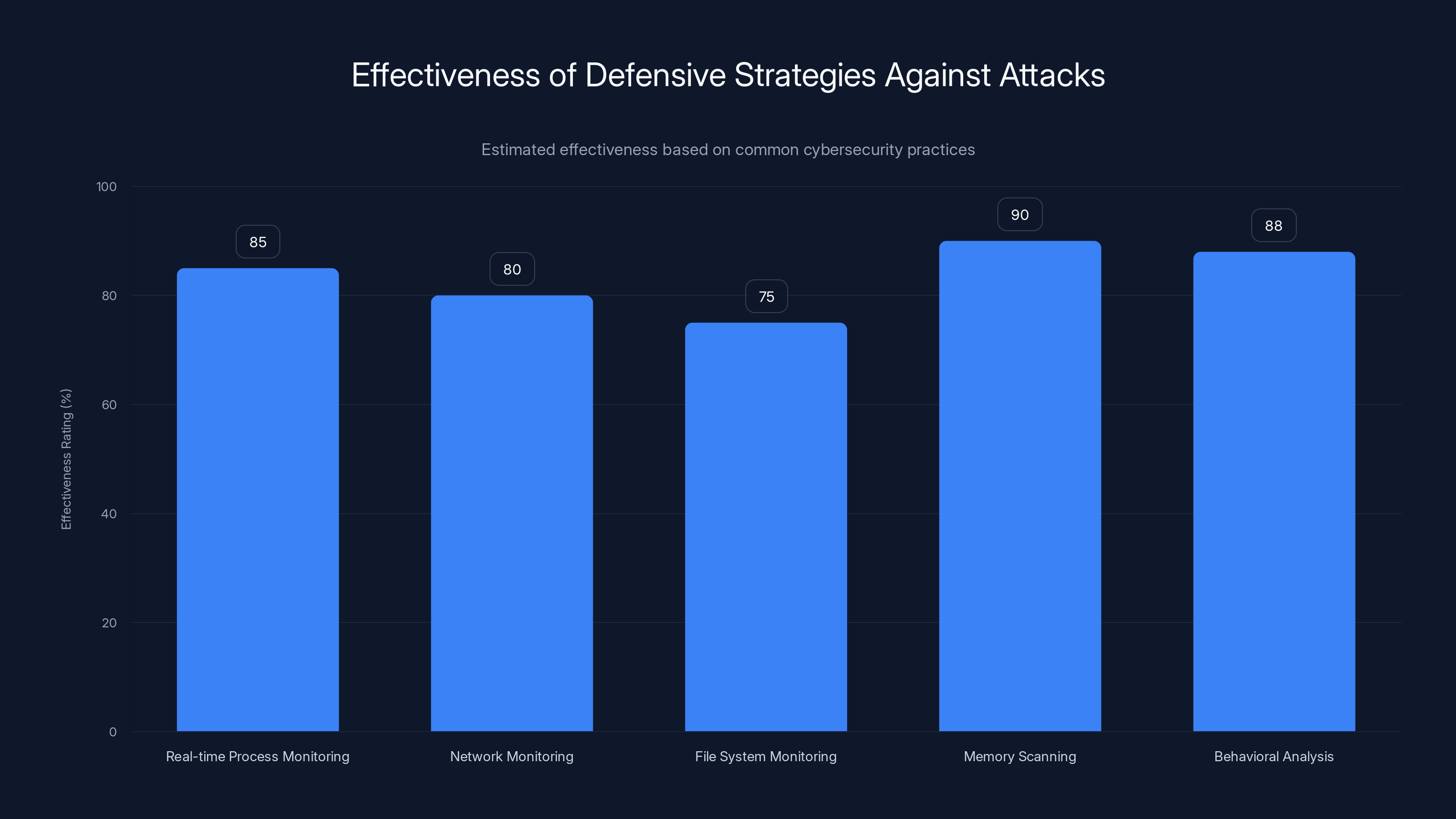
Estimated data shows that memory scanning and behavioral analysis are the most effective strategies, with ratings of 90% and 88% respectively. Combining multiple strategies enhances overall protection.
Why Developers Are Prime Targets
The targeting of developers isn't random. It's strategic. Developers occupy a unique position in modern organizations.
A developer has legitimate reasons to:
- Clone repositories from the internet
- Execute build scripts and automation
- Install packages and dependencies from public repositories
- Access multiple systems and networks as part of their job
- Have elevated privileges on their development machines
- Store sensitive credentials and API keys locally
- Connect to production databases and cloud infrastructure
All of these normal activities become vectors for attack if the developer's machine is compromised. A single compromised developer machine can provide attackers with:
- Source code for proprietary applications
- API keys and authentication tokens
- Access to cloud infrastructure
- SSH keys for production servers
- Cryptocurrency wallet information
- Customer data and databases
- Intellectual property and research
From the attacker's perspective, compromising one developer is more valuable than compromising 100 regular employees. The developer has keys to the kingdom.
Moreover, developers are often skilled enough to detect obvious security threats, which is why the attack uses sophisticated social engineering rather than crude malware. A developer might spot a suspicious executable. They might analyze a script before executing it. But a legitimate Git repository with legitimate VS Code configuration? That's much harder to question.
The macOS-Specific Attack Chain
The attack documented by Jamf researchers specifically targets macOS systems, though the core concept could be adapted to other platforms.
On macOS, the attack has several advantages:
First: macOS users often have strong beliefs about security. They think their systems are inherently safer than Windows. This psychological advantage makes them less likely to question what they're opening or installing.
Second: The JavaScript payload execution through Node.js is platform-independent. Node.js runs on macOS just like on Linux or Windows. But on macOS, there's an additional layer of sophistication. The attacker can leverage macOS-specific features for persistence.
Third: macOS development is common, but it's less saturated with security tooling than Windows environments. Enterprise macOS deployments often have weaker endpoint protection than comparable Windows deployments.
Fourth: The shell script execution can leverage macOS-specific tools and features that make persistence easier. For example, launchd daemons can be configured to start the backdoor automatically at boot time without the user's knowledge.
The Vercel connection is also strategic. Vercel is a legitimate content delivery network and serverless platform used by millions of developers. Network traffic to Vercel is expected. It won't raise red flags in firewall logs or DLP systems. The attacker is hiding malicious payload delivery inside legitimate traffic to a trusted third party.

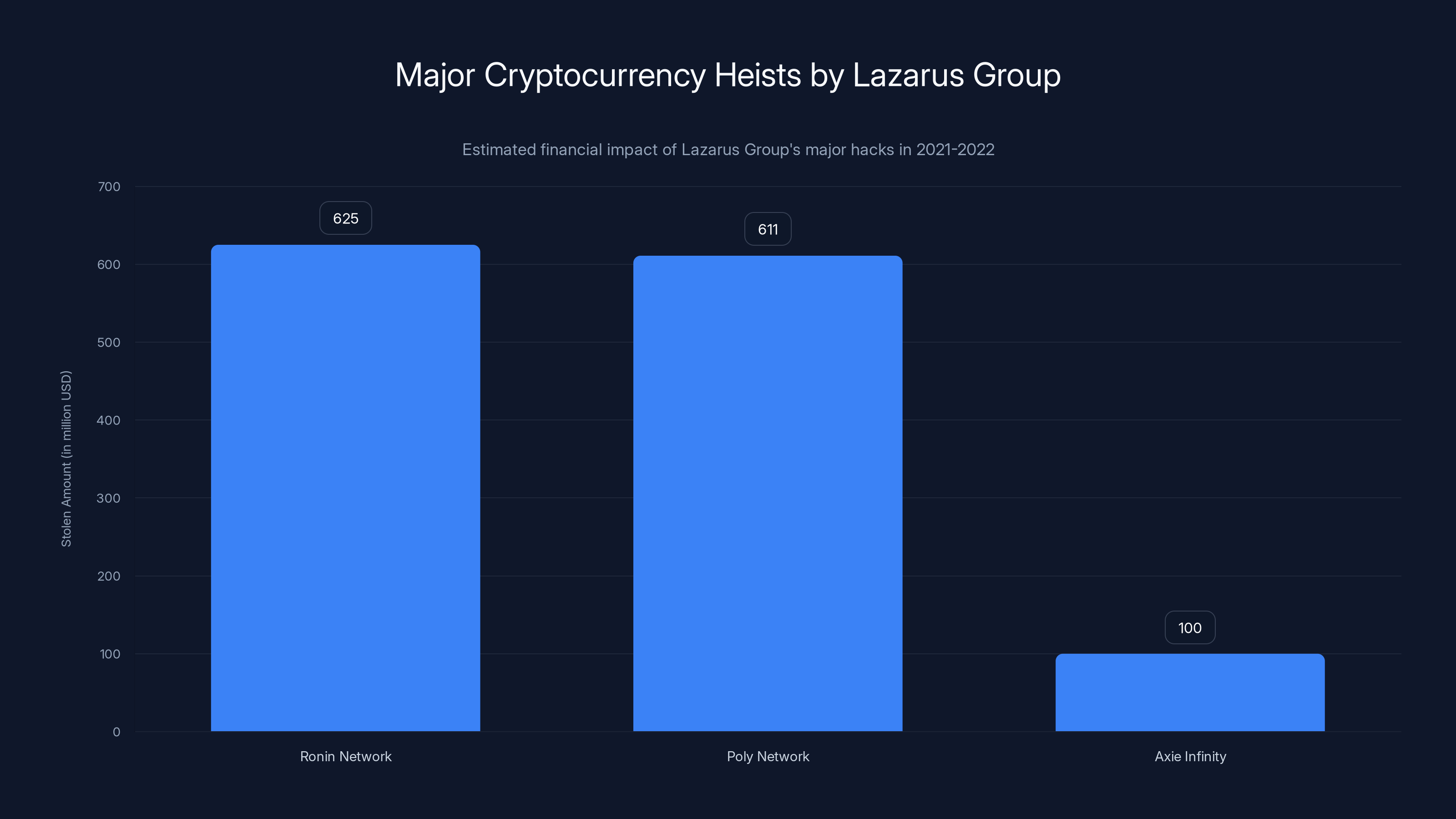
The Lazarus Group's major cryptocurrency heists in 2021-2022 resulted in over $1.3 billion in stolen funds, highlighting their significant financial impact.
Real-World Impact and Case Studies
The Lazarus Group's financial motivations are not hypothetical. The group has been linked to some of the largest cryptocurrency heists in history.
In 2021, the Lazarus Group was linked to the Ronin Network hack, which resulted in the theft of
In 2022, the Lazarus Group targeted Axie Infinity, stealing $100 million in cryptocurrency. They've also targeted traditional financial institutions, stealing hundreds of millions in various schemes over the years.
What's notable is that many of these attacks have some connection to developer compromise. The attackers gain access to systems by compromising developers or engineers at cryptocurrency companies. Once inside, they can move laterally to wallets and payment systems.
The financial incentives are enormous. The North Korean government, under international sanctions, desperately needs hard currency. Cryptocurrency theft provides untraced funds that can't be easily frozen or seized. A successful compromise of a major cryptocurrency exchange or blockchain company can fund the government's operations for months.
But cryptocurrency isn't the only target. The Contagious Interview campaign also targets:
Supply Chain Companies: Attackers compromise developers to gain access to software builds and deployments. This allows injection of malware into software that's distributed to thousands or millions of users.
Technology Companies: Access to development systems can provide source code, proprietary algorithms, and strategic plans.
Financial Institutions: Developers at banks and financial companies can provide access to payment systems and customer data.
Venture Capital Firms: Some of the fake companies used in Contagious Interview interviews appear to be targeting people who work at or are connected to venture capital firms. The goal might be intelligence gathering or access to limited partner funds.
Recognizing the Attack: Red Flags and Warning Signs
While the attack is sophisticated, there are warning signs that can help identify it.
Red Flags in the Recruitment Process:
- The company moves very quickly from initial contact to technical assessment. Real hiring processes usually take weeks. This one might happen in days.
- The job description is vague or doesn't quite match your experience. Legitimate hiring managers usually have specific requirements. Attackers might be less precise.
- The recruiter is eager to move communication off LinkedIn to email or messaging apps. Legitimate companies usually keep official channels official.
- The interview process focuses heavily on technical implementation with minimal discussion of company culture or team dynamics. Attackers want to get you cloning code, not learning about their culture.
- The compensation seems unusually high for the role. If it sounds too good to be true, it probably is.
- The company profile is relatively new or has minimal history. Real companies usually have established LinkedIn presence, news coverage, and online presence.
- The recruiter knows technical details about your background but seems unfamiliar with your industry. They've researched you personally but not your domain.
Red Flags in the Technical Assessment:
- You're asked to clone and open a repository in VS Code without explanation. Why that tool? Why not a standardized online coding challenge platform?
- The repository contains tasks.json or other configuration files that seem more complex than necessary for a simple technical assessment.
- You're asked to open a repository you've never heard of from a company you don't know well.
- There's pressure to do the assessment quickly or on a specific timeline.
- The repository contains minimal actual code or documentation. It seems like it might be a template or test setup.
Red Flags During Repository Execution:
- When you clone the repository, VS Code immediately prompts you about trusting the workspace. This prompt wouldn't appear if the repository was just random code.
- The tasks in tasks.json seem overly complex or unclear about what they're doing.
- Your machine suddenly becomes slow or uses unusual amounts of CPU or network bandwidth after opening the repository.
- You notice unfamiliar processes running in Activity Monitor (on macOS) or Task Manager (on Windows).
- Your network activity monitoring tools show unexpected outbound connections.
Post-Compromise Indicators:
- You notice new files or directories you didn't create.
- SSH keys or API credentials seem to be missing or were recently accessed.
- Your terminal history contains commands you don't remember executing.
- Your browser history contains sites you don't remember visiting.
- Antivirus or security tools alert about suspicious behavior (though the attack might evade these).
- Colleagues report unusual account activity or email forwarding rules they didn't set up.
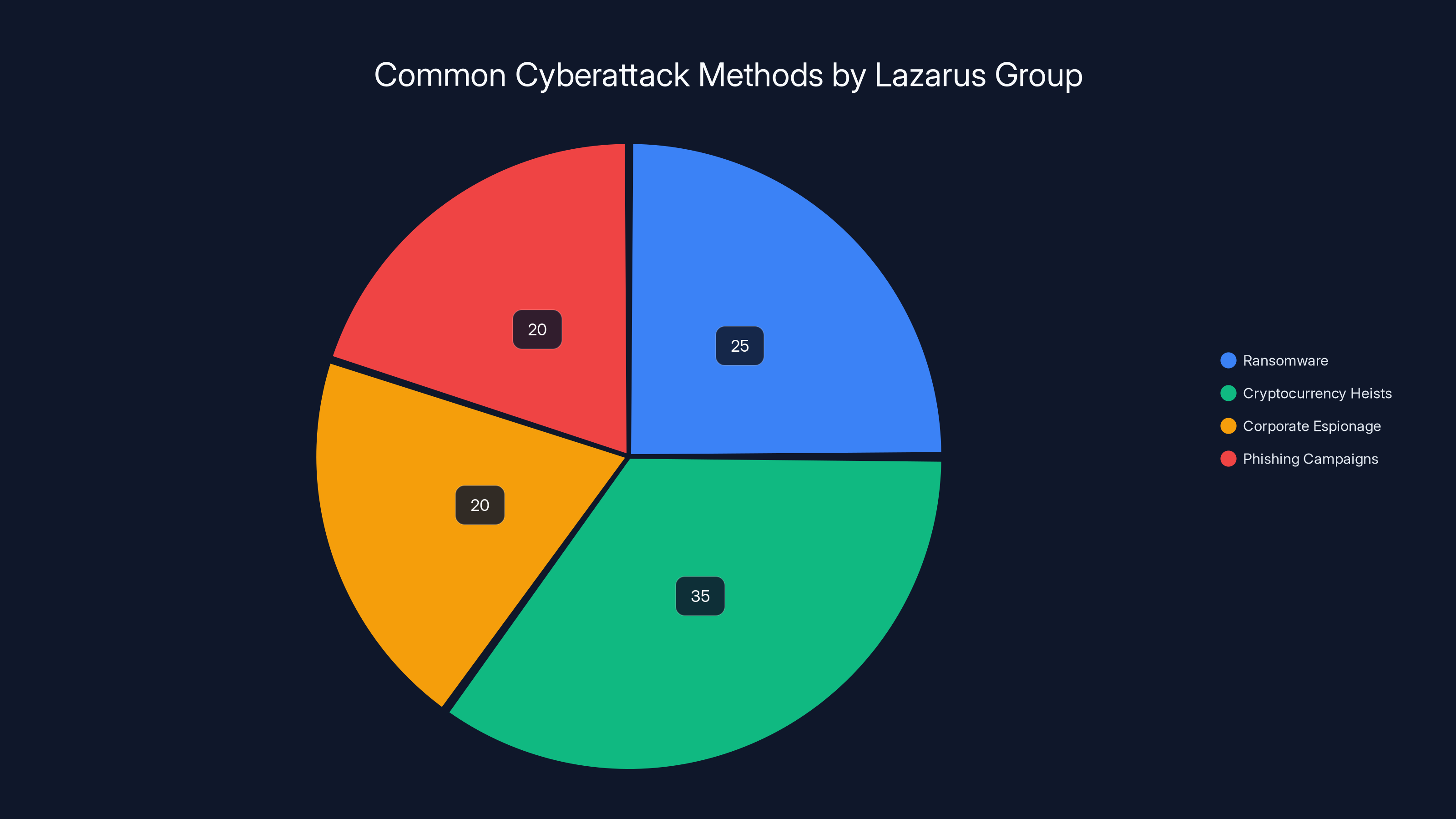
The Lazarus Group employs a variety of cyberattack methods, with cryptocurrency heists and ransomware being the most prevalent. Estimated data based on historical patterns.
Defensive Strategies: Protecting Against the Attack
Defense against this attack requires a multi-layered approach. No single tool or technique will completely prevent it, but combining several strategies significantly reduces risk.
Endpoint Protection and Threat Detection
Organizations should ensure that macOS endpoints have advanced threat detection enabled. Traditional signature-based antivirus might miss this attack because the actual malware is delivered as JavaScript in memory. Advanced threat detection looks for behavioral indicators.
Specific controls to enable:
- Real-time process monitoring that detects suspicious command execution
- Network monitoring that identifies unexpected outbound connections to unusual destinations
- File system monitoring that watches for suspicious modifications to system files or hidden directories
- Memory scanning that can detect malicious code executing in memory
- Behavioral analysis that looks for patterns consistent with command-and-control communication
Jamf specifically recommends enabling both Threat Prevention and Advanced Threat Controls in their management system, set to block mode. This means that suspicious behavior isn't just logged and alerted on; it's actually blocked and prevented.
Repository Verification and Code Review Processes
Developers should implement strict procedures before trusting new repositories:
Step 1: Verify the repository source. Does it come from a company you've directly engaged with, or through a mutual contact? Unknown repositories should be suspicious.
Step 2: Review the repository carefully before opening it in an IDE. Look at the commit history. Real projects usually have multiple commits from multiple contributors. A repository with only one or two commits from a newly created account is suspicious.
Step 3: Examine the configuration files. What's in tasks.json? What are the build scripts actually doing? If you don't understand what a script is doing, don't run it.
Step 4: Look for documentation. Real projects usually have comprehensive README files explaining what the project does, how to build it, and what the dependencies are. A repository without documentation is suspicious.
Step 5: Check the project on GitHub or GitLab directly. Does it have stars or followers? Does it have issue tracking? Does it seem like an active, legitimate project? New projects might have few stars, but they should still show signs of legitimacy.
Step 6: Communicate with the company through official channels. If a recruiter sends you a repository, contact the company's official website or LinkedIn and verify that the person recruiting you actually works there. Don't use contact information provided by the recruiter.
Step 7: Ask questions about the assessment. A legitimate technical interview should be able to explain clearly what the assessment is testing and why they want you to approach it this specific way.
Developer Machine Hardening
Organizations should implement hardening measures on developer machines:
User Account Control: Developers shouldn't run with administrative privileges for daily work. If their machine is compromised, the attacker shouldn't automatically have root access.
Application Whitelisting: Consider blocking Node.js execution from unexpected directories or with unusual parent processes. This can prevent the JavaScript payload execution chain.
Firewall Rules: Implement network-based controls that restrict outbound connections to known good destinations. The C2 communication in this attack requires outbound connectivity. Blocking unexpected outbound connections can prevent persistence.
Full Disk Encryption: Even if malware is installed, full disk encryption means the attacker can't read sensitive data from the hard drive if they obtain the machine.
System Integrity Protection: Enable all available system integrity protections. macOS has several built-in protections that can prevent privilege escalation and unauthorized modifications.
Secure Credential Management
Developers should never store sensitive credentials on their machines:
- Use a password manager that syncs credentials securely across devices
- For API keys and tokens, use temporary credentials or tokens with expiration dates
- Store sensitive credentials in hardware security keys when possible
- Implement SSH key management practices that prevent long-lived keys from sitting on disk
- Use certificate-based authentication instead of passwords when possible
- Regularly rotate credentials
If a developer's machine is compromised, these practices ensure that the attacker doesn't automatically gain access to all of the developer's credentials and API keys.
Monitoring and Incident Response
Organizations should assume compromise will happen and prepare for it:
Network Monitoring: Monitor for unexpected outbound connections from developer machines. If a developer's machine starts communicating with IP addresses in known threat actor infrastructure, that's a major red flag.
Endpoint Monitoring: Monitor for suspicious process execution, particularly Node.js spawning from unexpected parent processes, shell commands accessing sensitive files, or process execution from temporary directories.
Log Aggregation: Centralize logs from development machines. This makes it easier to detect patterns of suspicious activity across multiple machines.
Incident Response Plan: Have a clear process for what to do if a developer's machine is compromised. This includes:
- Immediate isolation of the machine from the network
- Preservation of evidence for investigation
- Rotation of all credentials the developer had access to
- Audit of all systems the developer accessed
- Notification to relevant teams
- Consideration of whether the developer should be granted access to sensitive systems pending investigation
Developer Education and Awareness
Technology can only do so much. Education is critical.
Developers should understand:
- Why they're targets. State-sponsored actors specifically target developers because of the access and privileges they have.
- How the attack works. Understanding the Contagious Interview campaign specifically helps developers recognize it.
- How to verify opportunities. Legitimate job opportunities can be verified through official company channels.
- The risks of opening untrusted repositories. Developers should understand that a repository can execute code just from opening it in an IDE.
- What to do if they suspect compromise. They should know how to report concerns and escalate security issues.
Regular security training that includes real examples from campaigns like Contagious Interview is more effective than generic security awareness.
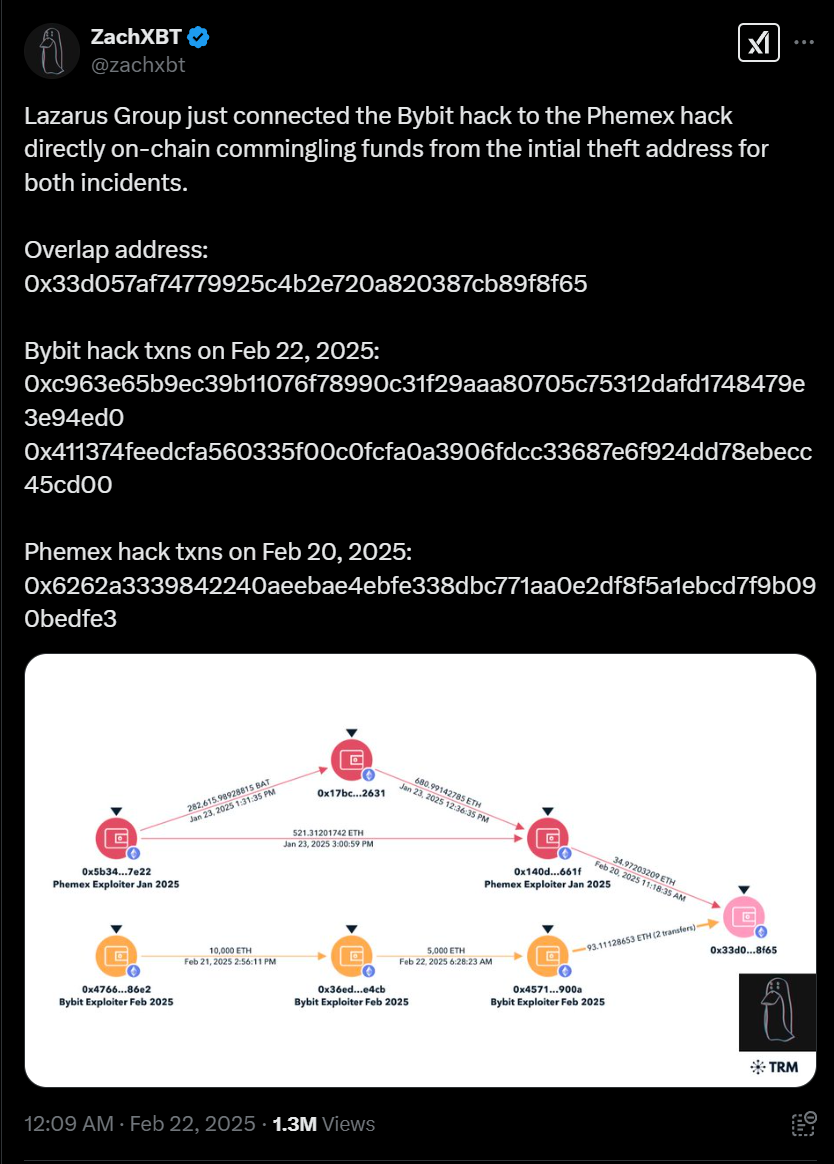
The Broader Context: Nation-State Cyber Operations and Developer Targeting
The Lazarus Group's targeting of developers is part of a broader trend in nation-state cyber operations.
Developer targeting is appealing to nation-states because:
Scale: Compromising a developer can provide access to systems serving millions of users. A single compromise can be leveraged into a massive supply chain attack.
Duration: Developers might maintain access to systems for years. Nation-states aren't always looking for quick wins. They're building long-term presence in critical infrastructure.
Impact: Developers often have access to the most sensitive systems in an organization. Compared to targeting a random employee, targeting a developer yields significantly more valuable access.
Attribution Difficulty: When attacks come through developer tools and legitimate workflows, they're harder to attribute to a specific attacker.
Other nation-states have noticed this opportunity. Russia's SVR has targeted software supply chains. China's APT groups have compromised developers to gain access to technology companies. Iran's hacking groups have targeted software developers. The United States and its allies have also been known to compromise developers in operations against foreign targets.
The targeting of developers is likely to increase. As security improves around traditional attack vectors, nation-states will focus more on the humans and tools that have legitimate access to critical systems.
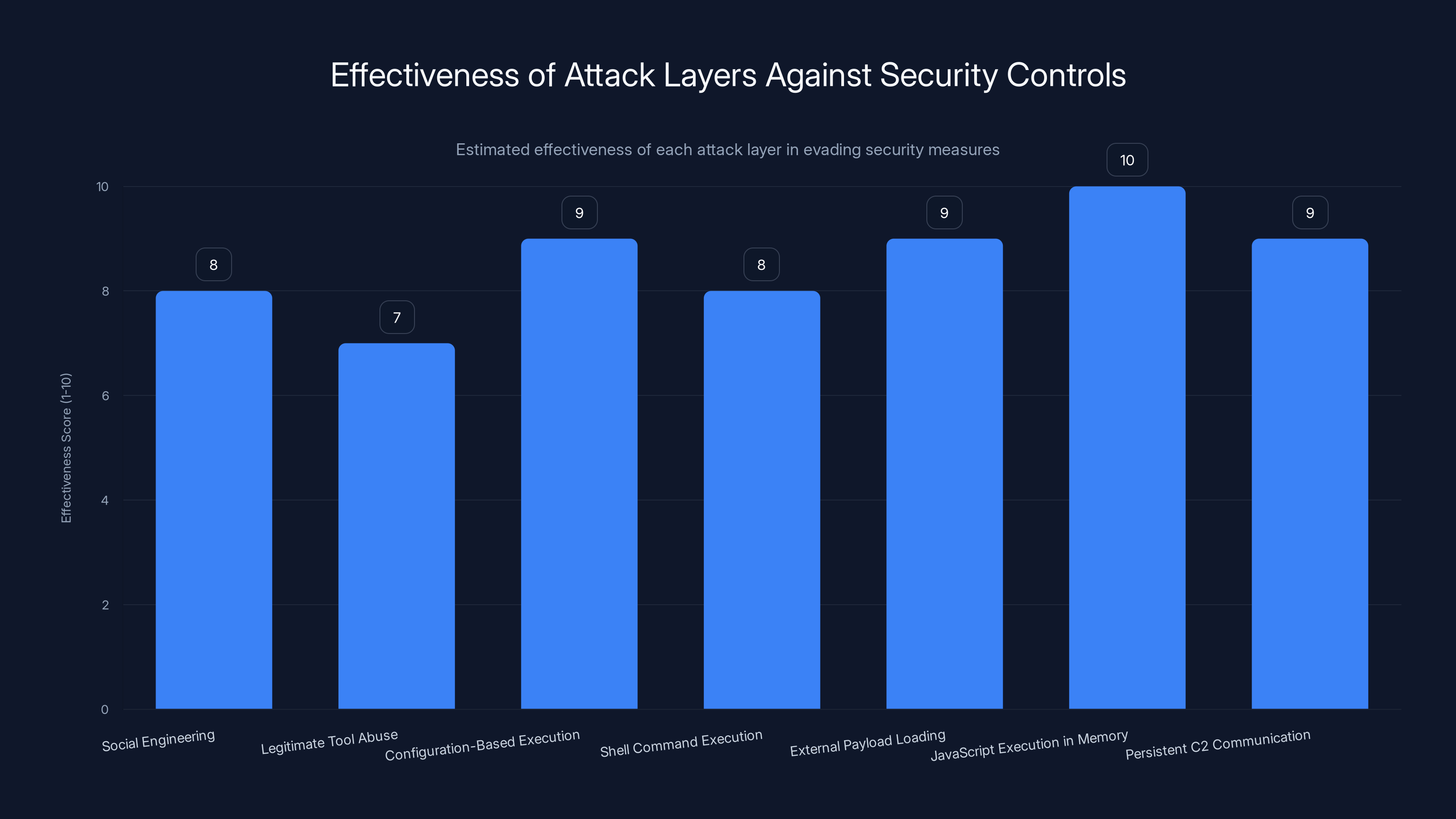
Estimated data shows that JavaScript Execution in Memory is the most effective layer in evading security controls, followed closely by External Payload Loading and Persistent C2 Communication.
Platform and Tool Specific Defenses
Visual Studio Code Specific Measures
Microsoft could implement several measures to reduce the attack surface:
Disable Automatic Execution: VS Code could require explicit approval before executing tasks. The current model automatically executes configuration files, which is convenient but dangerous.
Sandboxing: Code execution could be sandboxed so that even if malicious code is executed, it has limited access to the system.
Signing Requirements: VS Code could require that workspace configuration files be cryptographically signed by trusted parties.
Enhanced Warnings: The trust prompt could be more explicit about what trusting a workspace means. It could list the specific commands that will be executed.
Currently, VS Code's trust system is well-intentioned but insufficient for the threat landscape.
Git Repository Security
Git hosting platforms like GitHub and GitLab could implement:
Reputation Systems: New repositories could be flagged as untrusted until they demonstrate legitimate history.
Content Scanning: Repositories could be automatically scanned for known malicious patterns in configuration files.
Warnings for Unusual Configuration: When a repository contains configuration files that execute shell commands or external scripts, that could trigger warnings.
Verification Badges: Repository owners could verify their identity, and repositories could display verification badges.
These measures wouldn't eliminate the threat but could provide additional friction that helps defenders.
Node.js and JavaScript Runtime Security
The Node.js runtime could implement:
Restricted Module Loading: Restrict which modules can be loaded and from where. This could prevent certain techniques for establishing persistence.
Network Restrictions: Restrict which external hosts a Node.js process can communicate with without explicit permission.
File System Restrictions: Restrict which directories a Node.js process can access and modify.
These measures would represent significant changes to how Node.js operates but could improve security significantly.
Looking Forward: Future Evolution of the Attack
If the Lazarus Group's history is any guide, they'll continue evolving this attack.
Predictable evolution vectors:
Expanding to Other IDEs: The attack currently focuses on VS Code because of its market dominance among JavaScript developers. But the same techniques could be adapted to other IDEs like JetBrains products, Sublime Text, or even less obvious tools.
Targeting Other Languages: While the attack currently focuses on JavaScript and Node.js, the core concept could be adapted to target Python developers, Go developers, Rust developers, or any language ecosystem with configuration-based execution models.
Improving Persistence: The current attack relies on memory-based execution. The attackers might develop more sophisticated persistence mechanisms that can survive reboots and system updates.
Supply Chain Expansion: Rather than just targeting individual developers, the attack could be extended to target open source projects. Compromise a popular open source library, inject malicious code into a release, and the malware spreads to thousands of organizations automatically.
Social Engineering Sophistication: The fake job interview is effective, but it could be made more sophisticated. Attackers could create more elaborate backstories, fake employee directories, fake news articles about the company, and other social engineering elements.
Cross-Platform Attacks: While current attacks focus on macOS, they could be expanded to target Windows and Linux developers as well.
The fundamental advantage the attackers have is that they can experiment and iterate. They can try attacks and see what works. Defenders are always playing catch-up.
Organizational Response Frameworks
Organizations facing this threat should implement a structured response:
Assessment Phase
First, organizations should assess their risk:
- How many developers do they have? How many are active on job boards or open to recruiting?
- How attractive is the organization as a target? Are they in a high-value sector like crypto, finance, or defense?
- What are the consequences if a developer's machine is compromised? What systems and data would be at risk?
- How robust are current endpoint protections? Are they actually enabled and in blocking mode?
- How well trained are developers on security risks?
Mitigation Phase
Based on the assessment, organizations should implement mitigations:
- Ensure all developer machines have advanced endpoint protection enabled
- Implement code review processes for any new repositories
- Provide security training specific to Contagious Interview and supply chain attacks
- Harden developer machines and restrict their network access
- Implement monitoring to detect suspicious activity
- Prepare incident response procedures
Detection Phase
Organizations should implement detection mechanisms:
- Monitor for indicators of compromise
- Alert on suspicious process execution and network behavior
- Track access to sensitive systems and data
- Maintain detailed audit logs
Response Phase
If compromise is suspected:
- Isolate the affected machine immediately
- Preserve evidence for investigation
- Rotate all credentials the affected user had access to
- Audit all systems accessed by the affected user in recent weeks
- Investigate whether the compromise spread to other systems
- Implement additional monitoring to detect attacker activity

Industry Standards and Recommendations
Various organizations have released recommendations specific to this threat:
Jamf explicitly recommends:
- Enable Threat Prevention and Advanced Threat Controls
- Set these controls to block mode, not just alert mode
- Developers should be cautious with third-party repositories
- Review repository contents before trusting them in VS Code
CISA (Cybersecurity and Infrastructure Security Agency) has released advisories recommending:
- Implement robust endpoint detection and response (EDR)
- Monitor for indicators of compromise
- Maintain awareness of the Lazarus Group's tactics
- Report suspicious activity
SANS Institute recommends:
- Implement defense in depth for developer machines
- Assume that developer machines will eventually be compromised and prepare accordingly
- Focus on detection and response rather than only prevention
These recommendations reflect a realistic assessment: prevention is important, but it won't catch everything. Organizations need to be prepared to detect and respond to compromise.

Practical Implementation Checklist for Developers
If you're a developer, here's a practical checklist to reduce your risk:
Before Accepting a Job Interview Opportunity:
- Verify the company exists and is legitimate
- Contact the company through official channels to confirm the job opening and the recruiter
- Research the company online. Do news articles about them exist? Is there information about them beyond their website?
- Look up the recruiter on the company's employee directory or LinkedIn
- Be suspicious if communication happens primarily through unofficial channels
- Trust your instincts. If something feels off, it probably is
Before Opening a Repository in VS Code:
- Clone the repository without opening it in an IDE first
- Review the repository in a text editor or file browser
- Look at the tasks.json file specifically. What commands will be executed?
- Check the commit history. Does it look legitimate?
- Look for documentation and README files
- If you don't understand what's in the repository, ask the company to explain it
- Verify the company actually sent you this repository through official channels
During Repository Examination:
- When VS Code prompts you to trust the workspace, think carefully before accepting
- If you don't recognize the workspace author or understand why tasks.json exists, don't trust it
- Monitor your machine's activity while running any code from an untrusted source
- Have Activity Monitor open so you can see what processes are running
- Be aware of CPU and network usage spikes
After the Interview Process:
- If you don't get the job, that's suspicious. The "interview" was fake.
- Monitor your machine for any unusual activity
- Change your passwords, especially for sensitive accounts
- Rotate any API keys the machine had access to
- Consider factory resetting your machine if you're concerned about compromise
- Report the incident to your current employer and to security authorities

Conclusion: Understanding the Threat Landscape
The Lazarus Group's Contagious Interview campaign targeting Visual Studio Code represents an evolution in nation-state cyber operations. It's sophisticated, socially engineered, and technically sound. It exploits legitimate tools in ways that defenders struggle to detect.
But understanding the attack is the first step toward defending against it. The attack only works if developers don't recognize the red flags. It only succeeds if organizations don't implement proper defenses.
The good news is that this threat is defensible. Multi-layered defense, proper endpoint protection, code review processes, developer education, and incident response preparation can significantly reduce the risk.
The more important message: you are a target. If you're a developer with access to valuable systems, nation-states have an active interest in compromising you. This isn't paranoia. It's reality. The Lazarus Group is actively trying to compromise developers right now. They're sending fake job offers. They're setting up fake companies. They're creating malicious repositories.
Your defense starts with awareness. Know what attacks exist. Know how to spot them. Know how to verify opportunities before engaging with them. Know what to do if you suspect compromise.
Technology helps, but human judgment is the critical control layer. Trust your instincts. Verify everything. Assume every opportunity might be an attack. Do this, and you're already ahead of the attackers.
FAQ
What is the Lazarus Group?
The Lazarus Group is a state-sponsored threat actor believed to be part of North Korea's military intelligence apparatus. They're responsible for some of the most significant cyberattacks in history, including the Sony Pictures hack, the WannaCry ransomware outbreak, and numerous cryptocurrency heists totaling hundreds of millions of dollars.
How does the Contagious Interview campaign work?
The campaign uses fake job interviews to trick developers into cloning malicious Git repositories and opening them in Visual Studio Code. When the developer trusts the workspace in VS Code, malicious configuration files are automatically executed, leading to malware installation and system compromise.
Why are developers specifically targeted?
Developers are targeted because they have privileged access to critical systems, source code repositories, cloud infrastructure, and sensitive data. Compromising a developer provides attackers with far more valuable access than compromising a regular employee.
What happens after a developer's machine is compromised?
After compromise, attackers establish a persistent backdoor that communicates with a command-and-control server. The attacker can then harvest sensitive information, steal credentials, move laterally through the organization's network, or inject malware into software distributions.
How can I protect myself as a developer?
Verify job opportunities through official company channels, review repositories before trusting them in VS Code, maintain endpoint protection software, rotate credentials regularly, and report suspicious activity immediately to your security team.
What should I do if I think my machine is compromised?
Immediately isolate your machine from the network, disconnect from any VPNs, contact your organization's security team, and rotate all credentials your machine had access to. Avoid using the machine for any sensitive activities pending investigation.
Can this attack target other IDEs besides VS Code?
While the current campaign focuses on VS Code, the underlying concept could potentially be adapted to other integrated development environments that support workspace configuration files and automatic code execution.
How can organizations detect if this attack has occurred?
Organizations should monitor for suspicious process execution, unusual network connections from developer machines to unfamiliar external IP addresses, and behavioral indicators like unexpected command-and-control communication patterns from endpoint detection tools.
This article was developed based on security research from Jamf and industry analysis of the Lazarus Group's tactics. The information reflects the threat landscape as of early 2025. Threat actors continuously evolve their techniques, so security practices should be regularly updated based on the latest intelligence.
Key Takeaways
- The Lazarus Group's Contagious Interview campaign exploits VS Code's trust system to execute malicious code embedded in tasks.json configuration files during fake job interviews
- Attackers use JavaScript payloads delivered through legitimate CDNs like Vercel to establish persistent backdoors that harvest system data and communicate with command-and-control servers
- Developers are specifically targeted because their machines have privileged access to source code, production systems, cloud infrastructure, and sensitive credentials
- Multi-layered defense including advanced endpoint protection, code review processes, developer education, and incident response preparation significantly reduces compromise risk
- Red flags include rapid hiring processes, vague job descriptions, moving communication off official channels, and pressure to open unfamiliar repositories in VS Code
Related Articles
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
- Taiwan's 2.5M Daily Cyberattacks: China's Hybrid War Strategy [2025]
- Hyatt Ransomware Attack: NightSpire's 50GB Data Breach Explained [2025]
- HPE OneView CVE-2025-37164: Critical RCE Vulnerability & RondoDox Botnet [2025]
- Wi-Fi Security Flaws: How Hackers Crash Your Router [2025]
![North Korean Hackers Target VS Code: Lazarus Group's Contagious Interview [2025]](https://tryrunable.com/blog/north-korean-hackers-target-vs-code-lazarus-group-s-contagio/image-1-1769009931570.jpg)



