Instagram Password Reset Emails: What You Need to Know [2025]
It happened without warning. Your phone buzzes. There's an email from Instagram saying someone requested a password reset for your account. You didn't request anything. Your heart skips a beat.
This scenario played out for millions of Instagram users recently, sparking panic across social media platforms and security forums. Meta was flooded with confusion, support tickets, and rightfully concerned users demanding answers. The company's response? It wasn't a breach. It was an error. But the situation reveals something more complicated and unsettling happening behind the scenes.
Here's what makes this particularly frustrating: Meta's official statement doesn't match what security researchers discovered. Malwarebytes reported that 17.5 million account details had been leaked, including user IDs, usernames, email addresses, phone numbers, names, and postal addresses. That's a massive dataset sitting on hacking forums. Yet Meta insists their systems weren't compromised.
So what's actually going on? Why are users getting password reset emails they didn't request? Is Meta downplaying a serious security incident, or is there genuinely a different explanation? And more importantly, what should you do right now to protect your account?
This article breaks down everything you need to understand about the Instagram password reset incident, separates fact from corporate spin, and gives you actionable steps to secure your account. We're going to examine Meta's claims, analyze what researchers found, explain the difference between a breach and other security failures, and show you exactly what you should do today.
TL; DR
- What Happened: Millions of Instagram users received unsolicited password reset emails in 2024-2025
- Meta's Claim: An external party triggered password resets using a system error, not a breach
- The Reality: Malwarebytes confirmed 17.5 million account details leaked on hacking forums
- The Confusion: Researchers disagree on whether data came from a 2022 or 2024 API incident
- What You Should Do: Change your password immediately, enable two-factor authentication, and ignore unsolicited emails

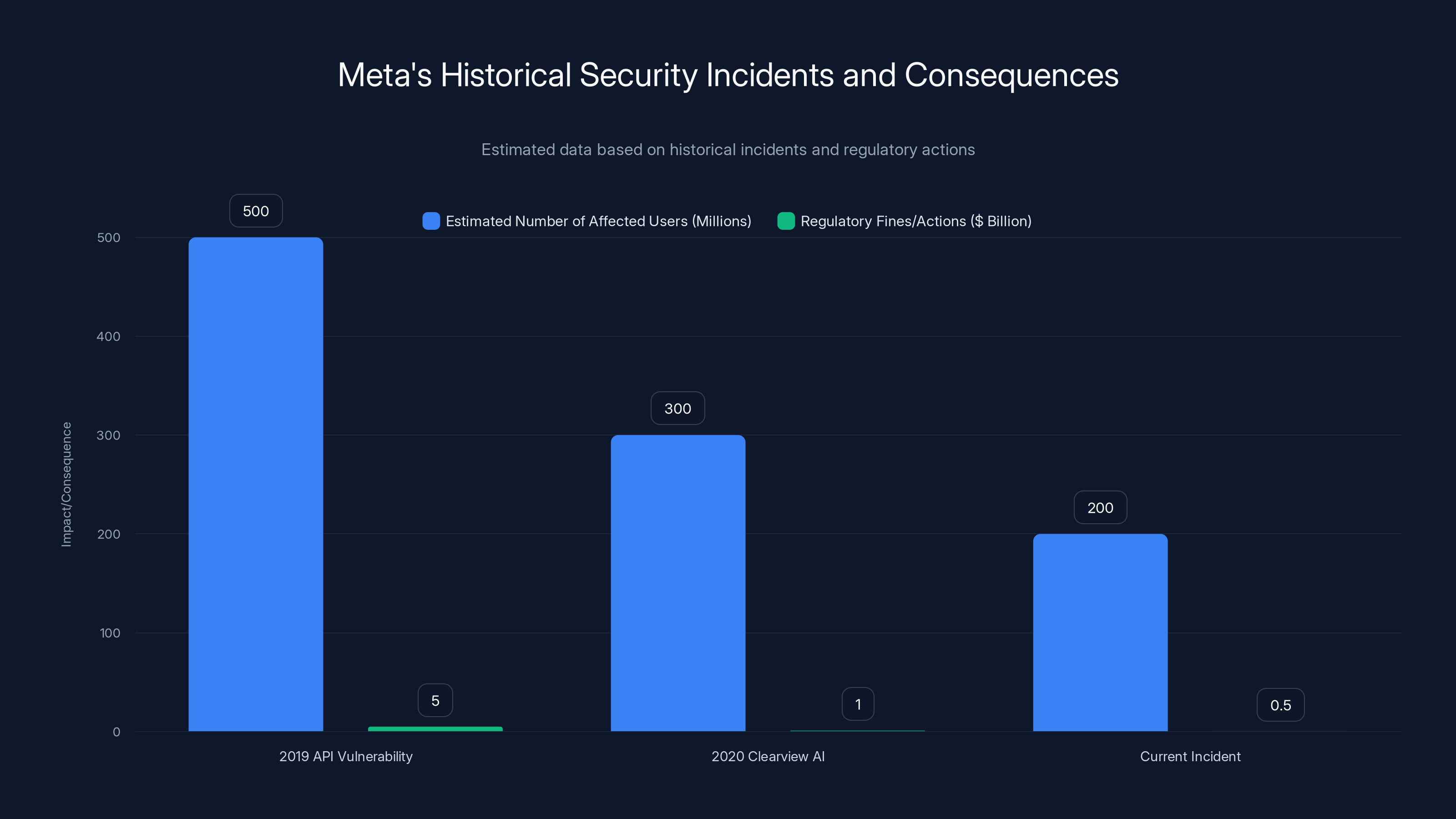
Meta's security incidents have historically affected millions of users and resulted in significant regulatory fines. Estimated data highlights the pattern of insufficient security measures.
Understanding What Actually Happened
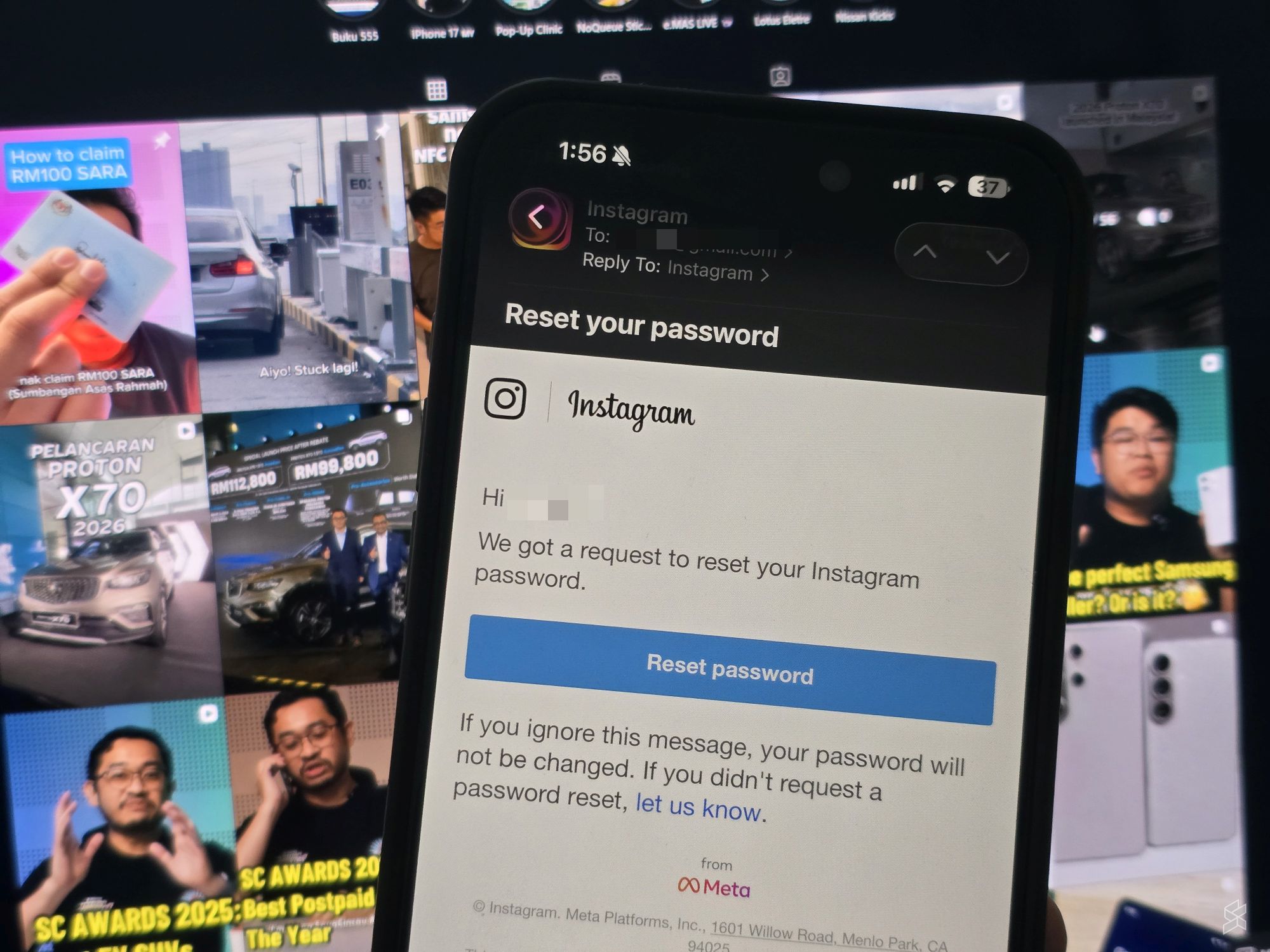
The timeline matters here. Starting in late 2024 and continuing into early 2025, Instagram users worldwide reported receiving password reset request emails they never initiated. At first, people thought their accounts were under active attack. Social media filled with screenshots of the emails, threads of confused users, and increasingly angry posts about Instagram's security.
Meta's official response came quickly but somewhat defensively. A spokesperson stated: "We fixed an issue that allowed an external party to request password reset emails for some Instagram users. We want to reassure everyone there was no breach of our systems and people's Instagram accounts remain secure. People can disregard these emails and we apologize for any confusion this may have caused."
This statement is carefully worded. Notice what it doesn't say: it doesn't specify how many users were affected, it doesn't explain how the external party gained the ability to trigger these emails, and it doesn't address the elephant in the room—the leaked data Malwarebytes discovered.
Malwarebytes' findings are concrete and alarming. Researchers discovered that 17.5 million account records had been stolen and were circulating on multiple hacking forums. This wasn't theoretical. Actual Instagram data, with real user information, was being bought and sold by threat actors. The dataset included sensitive information that could be used for identity theft, account takeovers, and targeted phishing attacks.
The critical disagreement centers on the source of this data. Malwarebytes initially reported the data came from a 2024 Instagram API leak. However, some independent researchers contested this, suggesting the data actually originated from a 2022 API scraping incident that Meta handled years ago. Meta itself claims they have no record of any significant API breaches in either 2022 or 2024.
This is where the story gets murky. If the data is old (from 2022), that explains why Meta isn't calling it a current breach. But if the data is fresh (from 2024), Meta's denial becomes questionable. Either way, the fact remains: 17.5 million people's personal information was stolen at some point and is now in criminal hands.

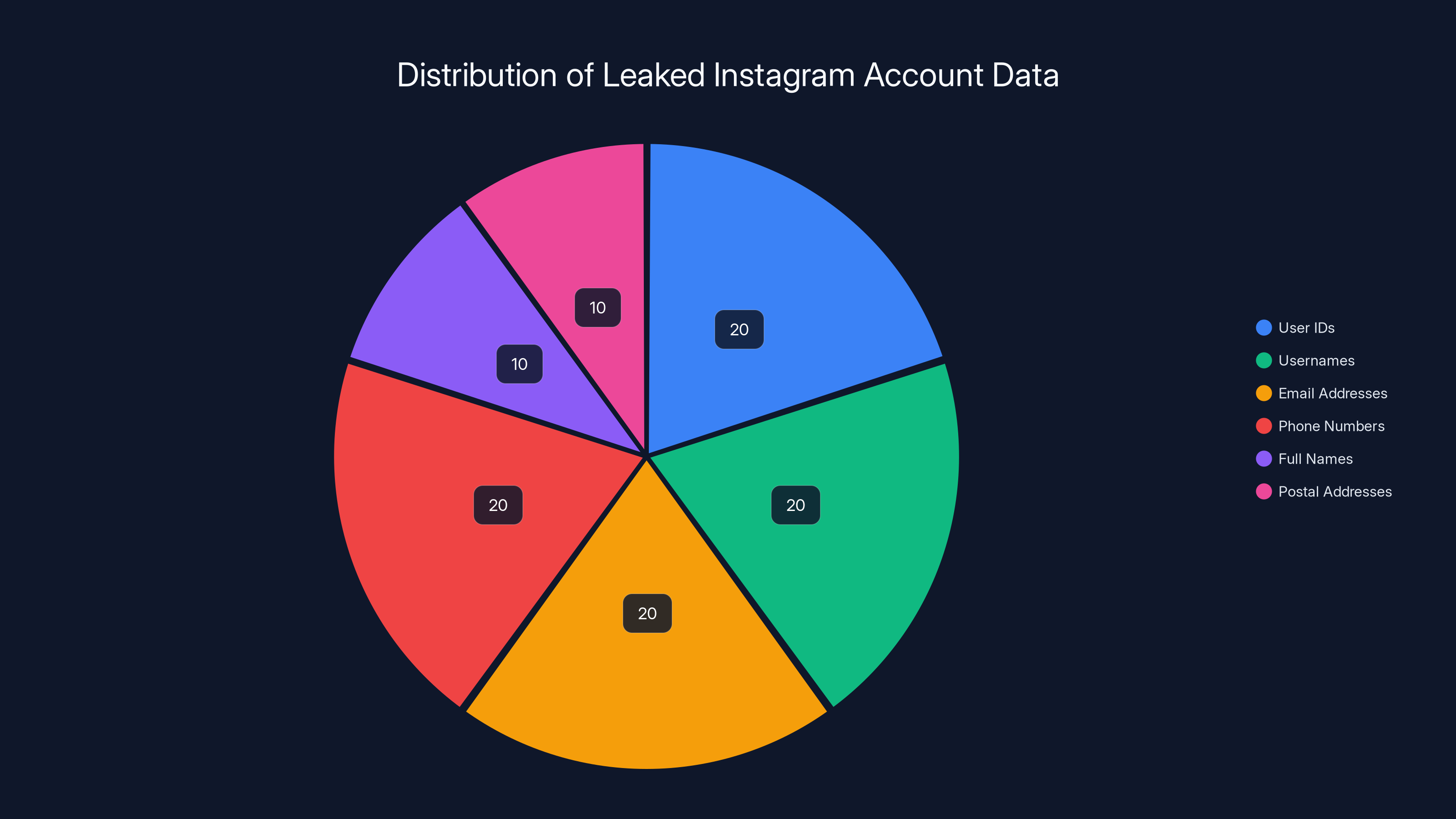
The leaked Instagram data includes various personal details, with user IDs, usernames, email addresses, and phone numbers each comprising 20% of the dataset. Postal addresses and full names make up the remaining 20%. Estimated data based on typical leak distributions.
The Difference Between a "Data Breach" and What Actually Happened
Meta is technically correct when they say there wasn't a "breach of their systems" in the traditional sense. A data breach typically means hackers penetrated security systems and extracted data directly. However, what happened here is arguably worse in some ways.
What Meta is describing sounds like an API abuse vulnerability. An external party—hackers, malicious actors, or unauthorized third parties—gained the ability to exploit an endpoint in Instagram's API that controls password reset requests. This endpoint apparently didn't have proper rate limiting, request validation, or authentication checks. So instead of breaking in, the attackers just... asked for password resets. Instagram's systems complied.
This is a critical distinction that changes how we should think about the risk. With a traditional breach, your data is compromised once. With an API abuse vulnerability, an attacker can continue exploiting the vulnerability until it's patched. Which means more password reset requests could potentially happen, affecting more users.
The real security failure here isn't necessarily that data was stolen. It's that Meta failed to properly secure an endpoint that handles password resets. Password reset functionality is one of the most sensitive operations a platform offers. If someone can trigger password resets on your account, they can potentially lock you out and take over your account entirely.
Think about it from a hacker's perspective. If you can trigger a password reset email to someone's account, and you also have their email address (which the leaked dataset includes), you can potentially intercept that reset link. Gmail, Outlook, and other email providers don't have perfect security either. The attack chain becomes: get email address from leaked dataset, trigger password reset, access email account or intercept the reset link, reset Instagram password, take over Instagram account.
Meta's defense—that "accounts remain secure"—is incomplete. Yes, an email asking you to reset your password doesn't automatically compromise your account. But it's a significant vector in a larger attack. And for users who reuse passwords across platforms (which most people do despite warnings), the risk escalates dramatically.
Here's another layer of concern: the fact that an external party had the ability to trigger these resets suggests they had some level of access to Instagram's infrastructure or API keys. How did they get it? Through a compromised employee account? A leaked API key? A vulnerability in a contractor's system? Meta hasn't explained.

The Malwarebytes Report: What the Data Shows
Malwarebytes isn't some random cybersecurity blog making wild accusations. They're an established, professional security research firm with a track record of investigating major incidents. When they report that 17.5 million Instagram account details were leaked, that's based on actual analysis of the datasets found on hacking forums.
The data allegedly includes:
- User IDs
- Usernames
- Email addresses
- Phone numbers
- Full names
- Postal addresses
Each of these data points has value to criminals. Phone numbers and email addresses are particularly valuable because they're used as recovery mechanisms on multiple accounts. If a hacker has your email address, they can attempt password resets on your email account. If they succeed, they can reset passwords on every service connected to that email—Instagram, Facebook, LinkedIn, banking apps, everything.
Postal addresses add another dimension of risk: they can be used for physical attacks, SIM swapping scams, or social engineering. Hackers can call your ISP or mobile provider, claim to be you, and request that phone numbers be transferred to a SIM card in their possession. With your postal address on file, they have the information needed to pass verification checks.
The fact that this data ended up on "numerous hacking forums" (Malwarebytes' phrasing) means it's not locked down in a single underground marketplace. It's distributed, shared, and being actively used by multiple threat actor groups. This dramatically increases the likelihood that you'll be targeted if your data was in that dataset.
Criminal marketplaces operate like underground eBay. Data is listed, sold, traded, and shared between groups. Once your information is out there, you lose control of it. That 17.5 million dataset will be exploited for years. Months from now, hackers will still be using it to target Instagram users, attempt account takeovers, and chain attacks into other accounts and services.
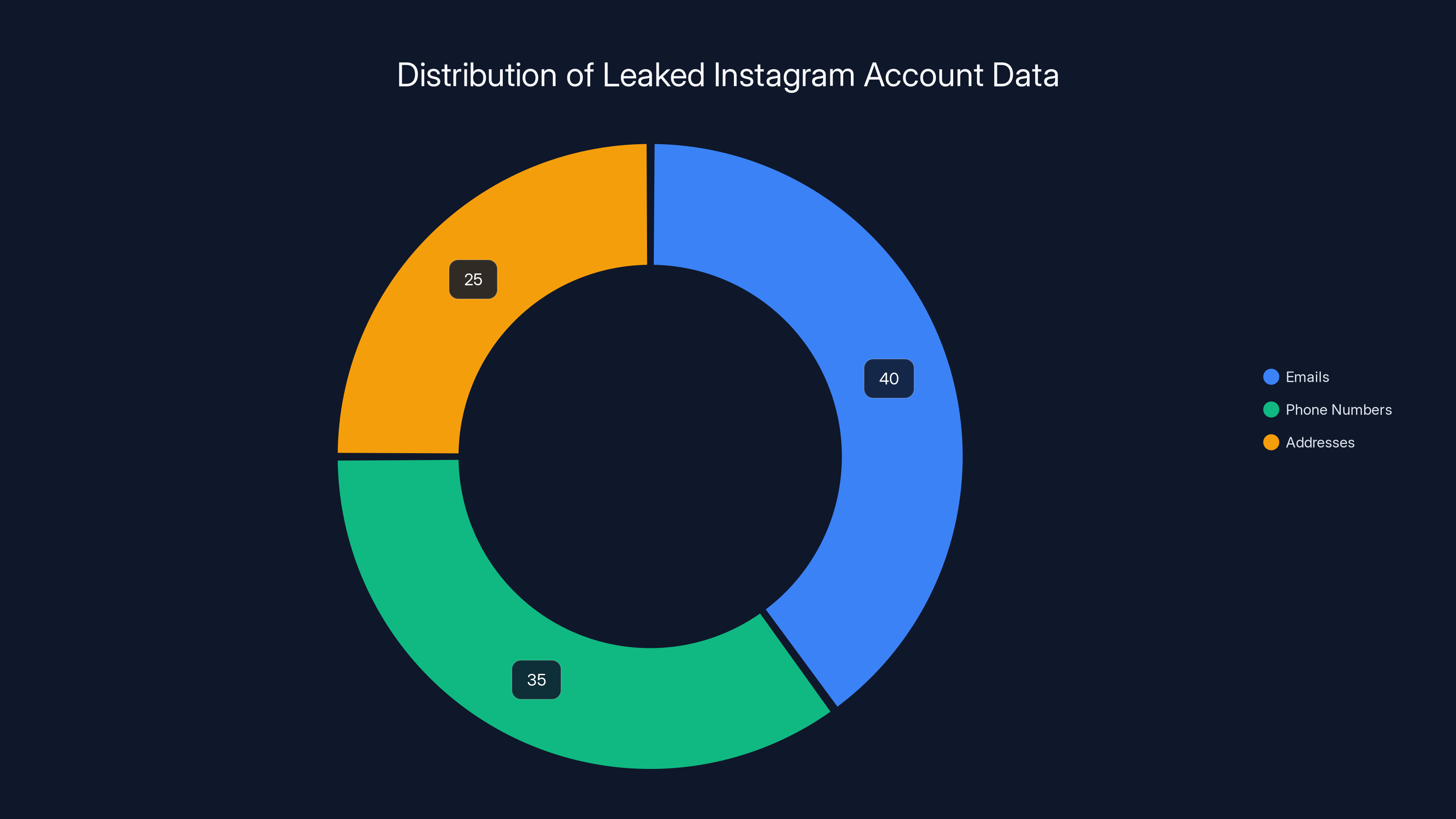
Estimated data shows that emails constitute the largest portion of leaked Instagram account information, followed by phone numbers and addresses.
Why Meta's Timeline Defense Doesn't Hold Up
Meta's primary defense is that even if data was leaked, it came from a 2022 API incident, not a current breach. The reasoning goes: "If the data is two years old, it's not our responsibility today, and it doesn't mean current systems are compromised."
There are several problems with this argument.
First, if the data is from 2022, why is it appearing on hacking forums now in 2025? Data doesn't typically sit dormant for two or three years and then suddenly emerge. Hackers use data quickly or distribute it immediately. If the dataset was sitting in criminal hands for years before appearing on forums, why the delay? One possibility: the data was repackaged and resold. Another possibility: this is new data from a recent incident, and Meta is mischaracterizing the timeline.
Second, the presence of fresh data doesn't erase the presence of older data. Even if some of the 17.5 million records are from 2022, the fact that Meta hasn't disclosed a 2022 API incident is a credibility issue. Users and the public deserved to know their data was compromised three years ago. Hiding past breaches to avoid liability is exactly the kind of thing that destroyed trust in major tech companies.
Third, Meta's denial of any API incidents in 2022 or 2024 strains credulity. Meta's APIs are used by hundreds of thousands of third-party apps and services. The Instagram platform has experienced known security issues and API problems in the past. The company's track record on transparency is poor. In 2019, Facebook disclosed that user data had been exposed through partner APIs. In 2020, another API vulnerability exposed user data. The pattern is consistent: vulnerabilities happen, Meta minimizes the incident, and the public learns about it months or years later.
The password reset incident itself is evidence that Meta's security practices have gaps. An external party had the ability to abuse an API endpoint. How long had they had this ability before Meta detected it? Were they using it to reset passwords on hundreds of accounts per day for weeks before the company noticed? We don't know because Meta hasn't provided those details.
What This Means for Your Account Security
Regardless of whether the leaked data is from 2022 or 2024, whether you want to call it a breach or an API abuse incident, or whether you believe Meta's explanations, one fact is certain: millions of Instagram users' personal information is now in criminal hands. Your email address, phone number, and postal address are being used right now in phishing campaigns, account takeover attempts, and social engineering schemes.
This isn't theoretical risk. This is active, ongoing danger. Threat actors have your data. They're using it. You should assume you're being targeted.
The password reset emails you received were a symptom of a larger security failure. Even though Meta patched the vulnerability that allowed external parties to trigger those resets, the underlying problem—that your data is compromised—remains. The attackers still have your information. They haven't lost interest in your account.
Your response needs to be comprehensive. Simply ignoring the password reset emails isn't enough. Simply changing your password isn't enough. You need a multi-layered defense that accounts for the fact that criminals have your contact information.
The first layer is account security. Change your Instagram password to something strong and unique. Don't reuse passwords across platforms. If you've used the same password on Instagram and other services, change those too. Use a password manager like Bitwarden or 1Password to generate and store complex passwords.
The second layer is two-factor authentication. Enable two-factor authentication on Instagram immediately. You can choose between authenticator apps (more secure) or SMS (less secure but better than nothing). With two-factor enabled, someone would need both your password and access to your authentication method to take over your account.
The third layer is email security. Your email account is the master key to everything else. If someone gains access to your email, they can reset passwords on hundreds of your other accounts. Enable two-factor authentication on your email account as well. Review connected apps and remove any you don't recognize or actively use.
The fourth layer is monitoring. Sign up for alerts that notify you when your email address is mentioned in new data breaches. Services like Have I Been Pwned and similar tools can send you notifications if your information appears in newly discovered breaches.
The fifth layer is skepticism. Be extremely cautious about emails, calls, or messages claiming to be from Meta, Instagram, Facebook, or any authority asking you to verify information, reset passwords, or confirm your identity. Assume any unsolicited communication is potentially a phishing attempt. Always navigate to the official website directly (don't click links in emails) if you need to verify something.
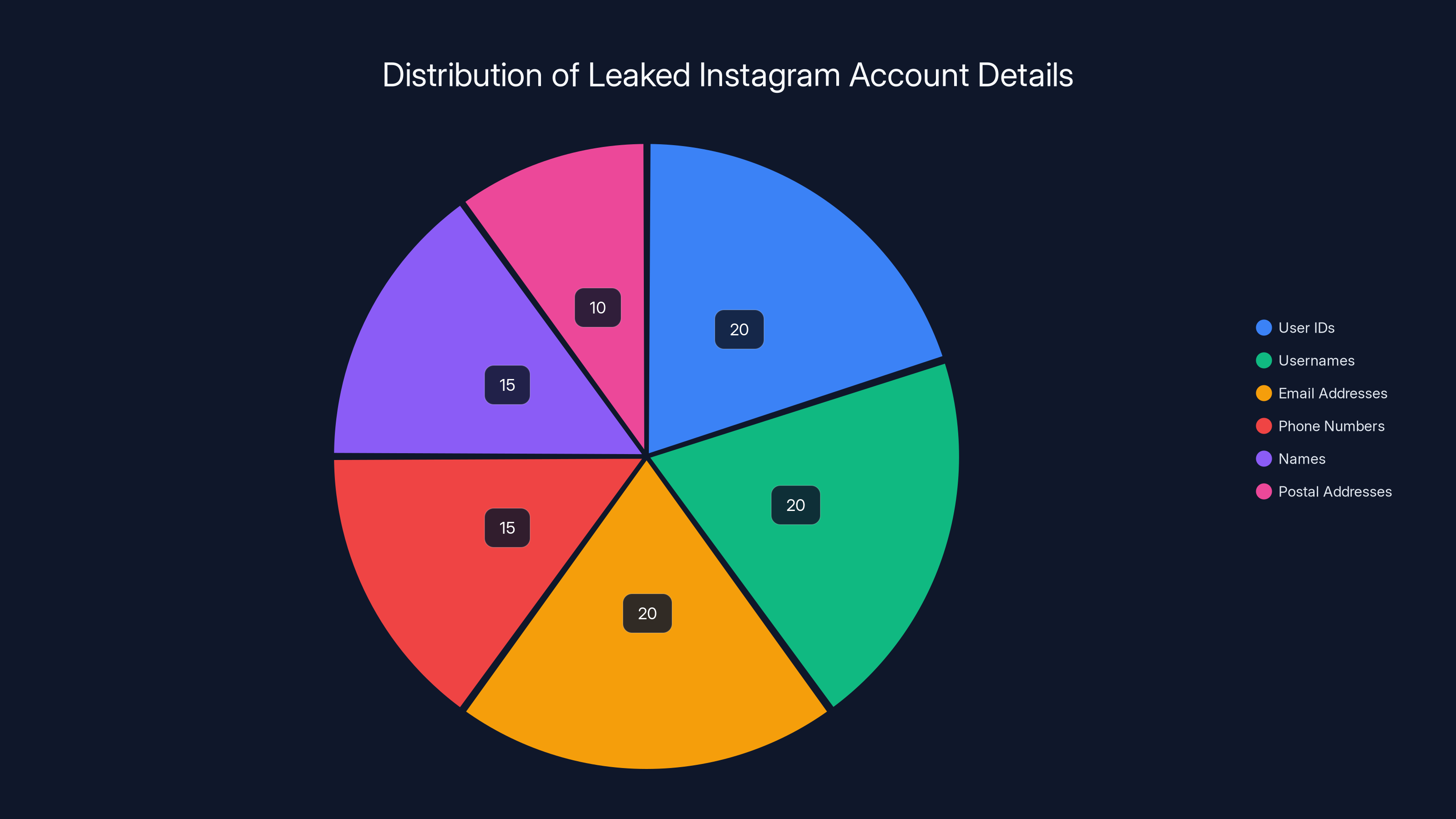
Estimated data distribution shows a balanced leak of user IDs, usernames, and email addresses, with slightly fewer phone numbers, names, and postal addresses.
How Hackers Will Use Your Stolen Data
Understanding the threat helps you take appropriate precautions. Criminals don't steal data to admire it. They steal data to exploit it for profit. Here are the most likely scenarios for how your stolen Instagram information will be used.
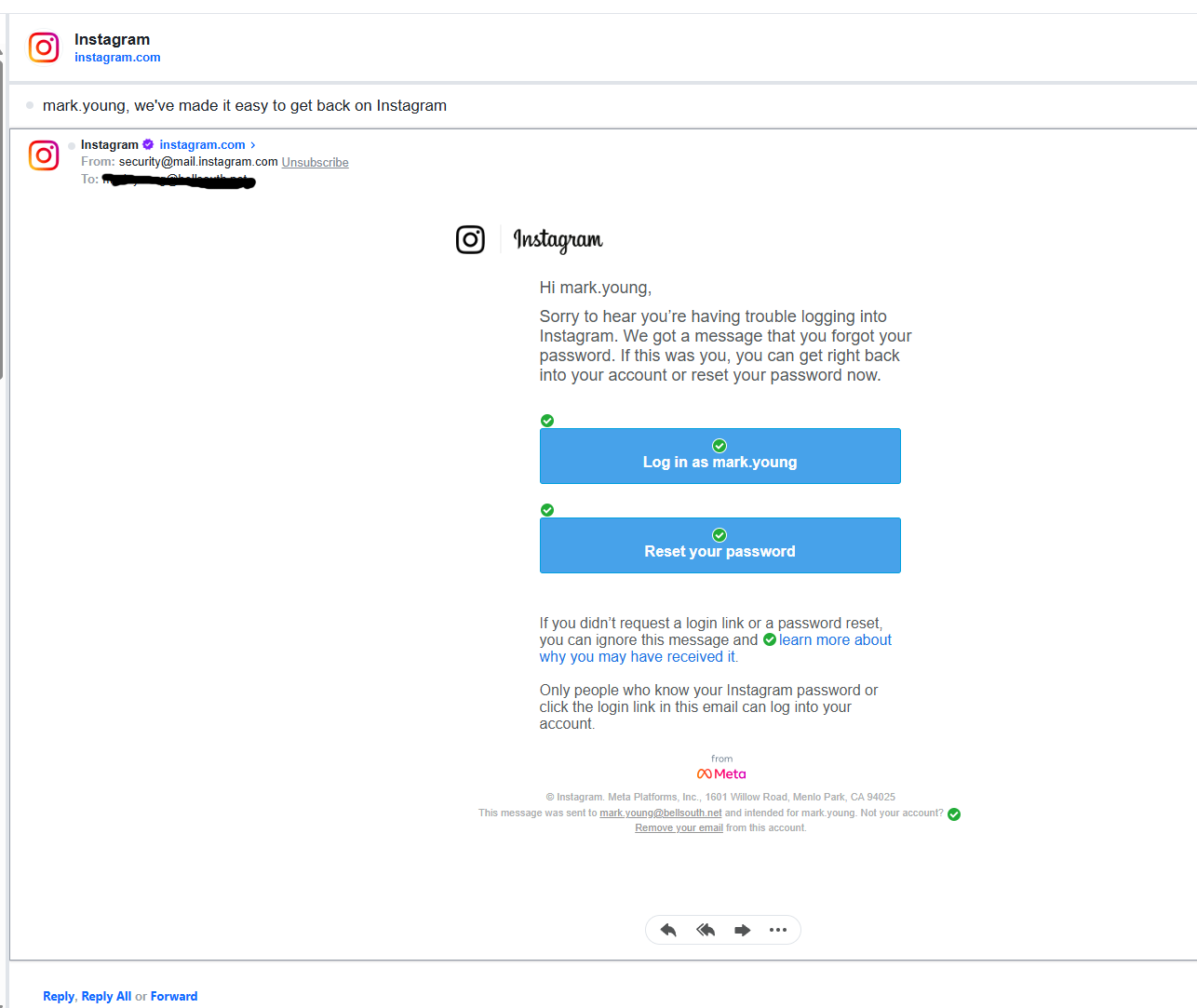
Phishing is the most common attack vector. You'll receive emails, text messages, or social media messages that appear to come from Instagram or Meta. The messages will create urgency: "Unusual activity detected," "Your account has been compromised," "Verify your identity," or similar language. The message will include a link directing you to a fake Instagram login page that looks identical to the real one. You enter your username and password. Boom. The attacker now has your real credentials.
Account takeover is the goal. Once they have your real password, they can log in, change the password to lock you out, and take control of your account. They'll change your email address and phone number so you can't recover it. Then they'll use your account to send phishing messages to your followers ("Click here to see a fun video") or simply use it to impersonate you.
Target-based attacks are more sophisticated. Since the leaked dataset includes your email, phone, full name, and postal address, attackers can craft highly personalized phishing messages that reference real details about you. They might send an email saying: "Hi [Your Name], we noticed unusual activity on your account from [City]. Click here to verify." The personalization makes it much more likely you'll fall for it.
SIM swapping is another threat. Using your phone number and sometimes your postal address, attackers can call your mobile carrier and claim they want to transfer your number to a new SIM card. They'll convince the customer service rep that they're you by using information from the leaked dataset. Once they control your phone number, they can use SMS-based recovery methods to reset passwords on email accounts and other services.
Data aggregation amplifies the danger. Attackers combine the Instagram data with other leaked datasets—credit reports from Equifax breaches, voter registration data, healthcare records—to build a complete profile of you. They know where you live, where you work, what you buy, who your family is, and what accounts you have. This information is sold to the highest bidder, enabling everything from identity theft to targeted scams.
The timeline of exploitation is important. Initial attacks happen within weeks. As the dataset circulates through criminal communities, secondary waves of attacks occur over months and years. Someone might use your data to create a fraudulent account somewhere else. Someone else might use it for identity theft. A third party might include it in a targeted ad campaign selling fake products to your friends using your name.
Meta's Responsibility and Accountability
Let's talk about corporate responsibility here, because Meta's response to this incident reveals a troubling pattern. The company is minimizing the incident, claiming there was no "breach" while simultaneously acknowledging that an external party had unauthorized access to their systems. That's contradictory.
Meta is also not being transparent about the scope of the incident. How many users were actually affected? How long did the vulnerability exist before it was discovered? What evidence does Meta have that no other data was accessed? These questions remain unanswered.
The company is also not taking responsibility for the larger security failures that allowed this incident to happen. An endpoint that controls password resets should be the most heavily protected part of Instagram's infrastructure. It should have rate limiting, request validation, geographic restriction, and multiple layers of authentication. The fact that an external party could abuse it suggests Meta's security practices fell short.
Historically, Meta has faced criticism for its handling of security incidents. After the 2019 API vulnerability exposed data on hundreds of millions of users, Meta paid a $5 billion FTC fine. After the 2020 Clearview AI controversy, Meta again faced regulatory scrutiny. These aren't isolated incidents. They're part of a pattern showing that Meta hasn't invested sufficiently in security.
For users, this has real consequences. You're expected to trust Meta with intimate information—photos, messages, friend lists, location data, activity history. If Meta can't secure that data against external parties triggering password resets, what else is vulnerable?
The company should be required to:
- Disclose the exact number of affected users
- Provide a timeline of when the vulnerability was discovered and fixed
- Explain how the external party gained access to the API endpoint
- Commit to independent security audits
- Offer affected users credit monitoring or identity theft protection services
- Implement stronger security controls
Instead, Meta issued a brief statement claiming everything is fine and asking people not to worry.
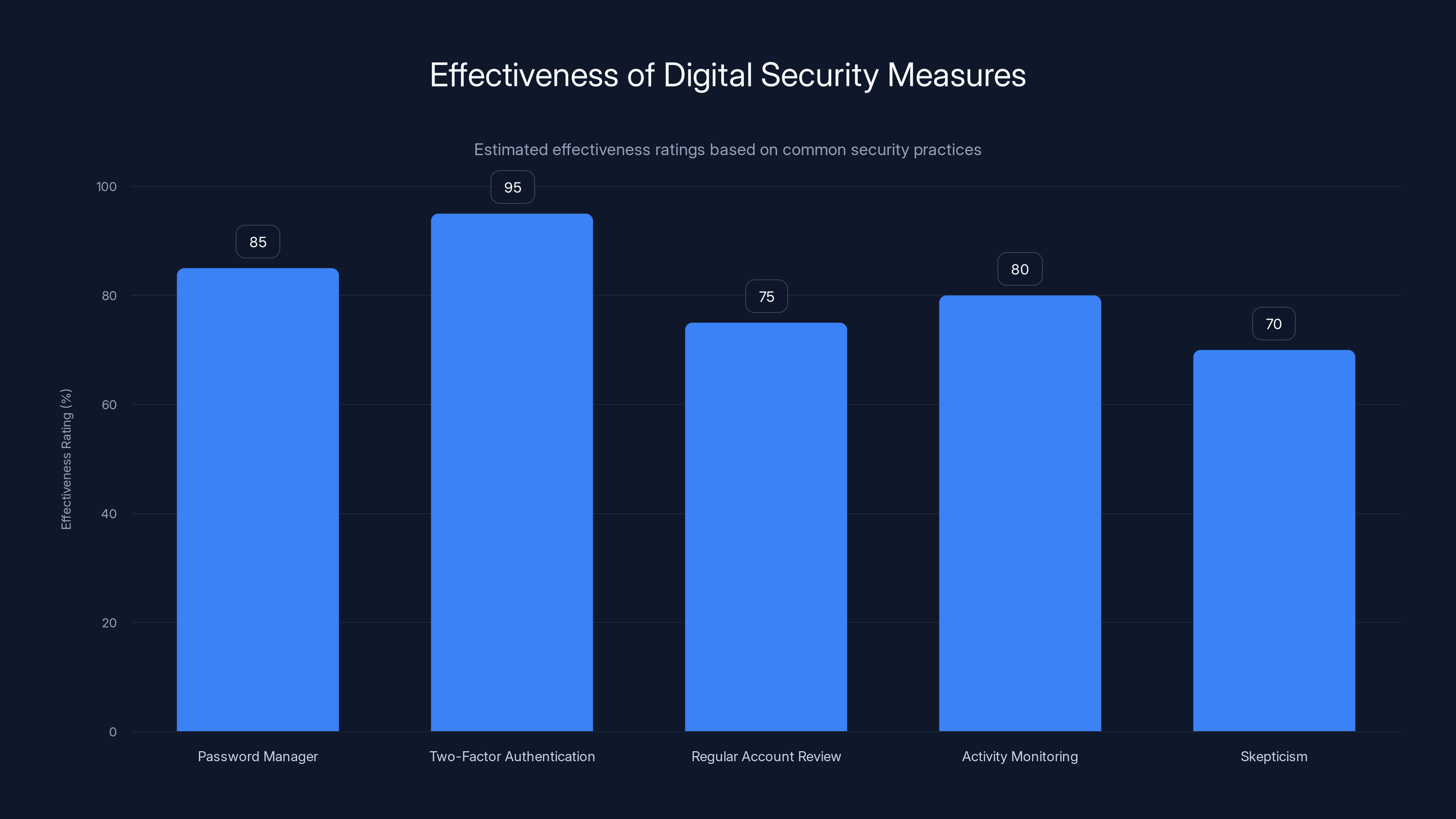
Two-factor authentication is estimated to be the most effective security measure, with a 95% effectiveness rating. Estimated data.
The Bigger Picture: Why This Keeps Happening
This incident isn't unique. It's part of a recurring pattern in the tech industry. Major platforms experience security failures, minimize the incidents, and avoid transparency while users bear the consequences.
Why does this pattern persist? Several factors:
Financial incentives: Transparency about security breaches is expensive. Companies must notify affected users, potentially offer credit monitoring, face regulatory fines, and manage PR damage. There's a financial incentive to minimize incidents and avoid disclosure.
Complexity: Modern tech infrastructure is incredibly complex. Platforms like Instagram have millions of lines of code, thousands of engineers, hundreds of third-party integrations, and distributed systems spanning continents. Security is genuinely difficult at this scale. But that complexity is partly a result of choices made by these companies to grow aggressively without investing proportionally in security.
Regulatory gaps: The regulatory environment is weak. The FTC can fine companies, but fines are often negotiated down and treated as a cost of doing business. There's no requirement for immediate disclosure, no requirement for independent audits, and no meaningful consequences for repeated incidents.
Market failure: Users can't easily switch away from Instagram because their friends, family, and professional networks are there. Network effects lock people in, regardless of security concerns. This removes the market pressure that normally incentivizes companies to invest in security.
Until these underlying factors change, expect more incidents. Expect more denials. Expect more minimization and deflection from major platforms.
Your responsibility in this environment is to assume the worst and protect yourself accordingly. Don't trust companies to keep your data safe. Use strong passwords, enable two-factor authentication, monitor your accounts, and assume that your data has probably been compromised at some point.
Immediate Action Steps You Should Take Today
Enough analysis. Here's what you need to do right now to protect your account.
Step 1: Change Your Instagram Password
Open Instagram or go to instagram.com. Navigate to Settings > Security > Password. Enter your current password and create a new one. Make it at least 16 characters, include uppercase and lowercase letters, numbers, and symbols. Use a password you've never used before and don't use anywhere else. If you don't have a strong password, use a password manager to generate one.
Step 2: Enable Two-Factor Authentication
Go to Settings > Security > Two-Factor Authentication. Instagram offers two options: authenticator apps or SMS. Choose the authenticator app option (Google Authenticator, Authy, Microsoft Authenticator, or similar). This is more secure than SMS. Download the authenticator app if you don't have one, scan the QR code Instagram provides, and save the backup codes in a secure location.
Step 3: Review Connected Apps and Services
Go to Settings > Apps and Websites. Check which third-party apps have access to your Instagram account. Remove any app you don't actively use or recognize. Hackers often gain access to accounts through connected applications with weak security.
Step 4: Enable Login Alerts
Go to Settings > Security > Logins. Toggle on "Get alerts about unrecognized logins." This will notify you if someone logs into your account from an unfamiliar device or location.
Step 5: Secure Your Email Account
Your email is the master key. Go to your email provider (Gmail, Outlook, Yahoo, etc.) and enable two-factor authentication there as well. Review connected apps and remove any you don't recognize. Enable recovery options (phone number, backup email) so you can regain access if your account is compromised.
Step 6: Check for Compromised Data
Go to haveibeenpwned.com and enter your email address. This will tell you if your email has appeared in any publicly disclosed breaches. If it shows up in the Instagram incident or others, take note and adjust your security posture accordingly.
Step 7: Monitor Your Accounts
Sign up for notifications from Have I Been Pwned or similar services. These will alert you if your email appears in any new breaches discovered. This gives you an early warning to take action.
Step 8: Be Skeptical of Communications
From now on, assume any email, text, or message asking you to verify information or reset passwords is potentially a phishing attempt. Never click links in unsolicited communications. Always navigate directly to official websites if you need to verify something.
Step 9: Change Passwords on Related Accounts
If you've used the same password on Instagram as you have on other accounts (email, Facebook, other social media), change those passwords too. Hackers will try credentials across multiple platforms.
Step 10: Consider Identity Monitoring
If you're concerned about identity theft (and you should be, given that your postal address and full name were leaked), consider enrolling in an identity monitoring service. Services like LifeLock, Experian, or similar platforms will alert you if your personal information is used fraudulently.
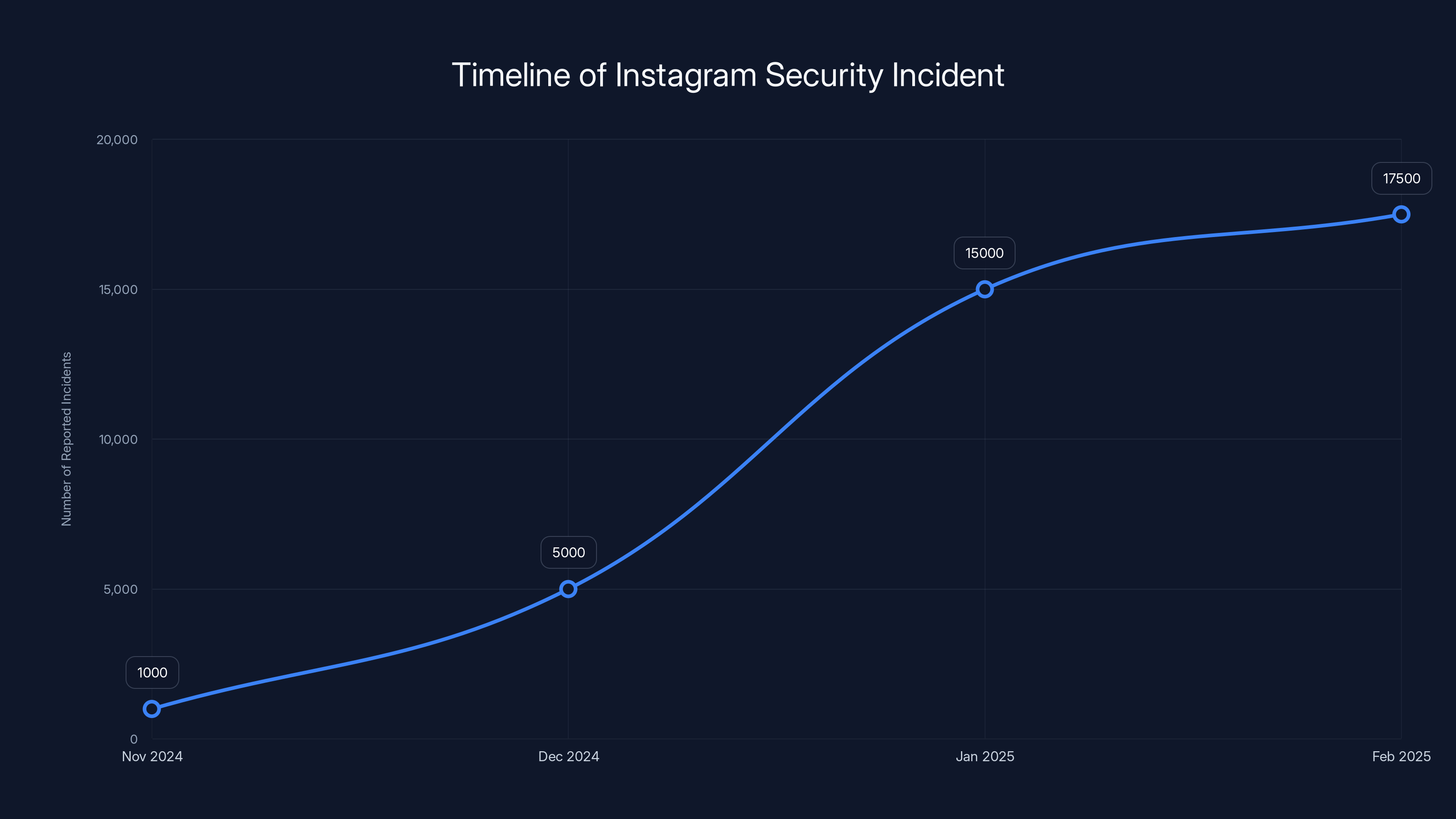
The number of reported incidents of unauthorized password reset requests increased significantly from November 2024 to February 2025. Estimated data based on narrative.
What to Expect Going Forward
The password reset emails you received may taper off, but your risk doesn't. Your data is still in circulation. Threat actors still have your information. The attacks won't stop overnight.
Expect to see phishing emails and messages increase over the coming weeks and months. Expect your Instagram account to remain a target. Expect that criminals will attempt to exploit every piece of information they have about you.
You'll likely receive emails claiming to be from Instagram asking you to verify your account. These will be phishing attempts. Ignore them. You'll probably get calls or texts about "unusual activity" on your account. Hang up. These are standard social engineering tactics that become much more effective when attackers have your real personal information.
The best you can do is stay vigilant. Monitor your accounts. Use strong, unique passwords. Enable two-factor authentication everywhere. Review your accounts regularly. Question unsolicited communications. Report phishing attempts to the appropriate platforms.
This is the reality of living in the digital age where major companies have been breached repeatedly. Your data is probably compromised in multiple ways you don't even know about. The best defense is to assume it's already out there and protect yourself accordingly.
Why This Matters Beyond Instagram
The Instagram password reset incident is concerning not just because it affects Instagram, but because it reveals weaknesses in the broader digital ecosystem.
When a platform as large and well-resourced as Instagram struggles to properly secure API endpoints, it suggests that many smaller platforms are likely struggling even more. If you use other social media platforms, messaging apps, photo services, or other digital tools, the same security weaknesses probably exist there too.
Your data is fragmented across dozens of services. A breach at one reveals information that hackers can use to attack you at others. A vulnerable API endpoint at one platform can be exploited to attack your accounts at another. Your email and phone number are the connective tissue linking all these accounts together. Once those are compromised, your entire digital identity is at risk.
The incident also matters because it illustrates the power imbalance between tech companies and users. Meta has billions of dollars, thousands of engineers, and massive resources dedicated to security. Yet they still fail to properly protect user data. Users, meanwhile, have no way to compel transparency, demand accountability, or take legal action when their data is mishandled.
Until regulations change significantly, expect this pattern to continue. Data breaches will happen. Companies will minimize them. Users will eventually learn about them through third-party security researchers. And by then, the data will already be in criminals' hands, being actively exploited.
Your best defense is to take responsibility for your own security. Don't rely on Meta or any major tech company to keep your data safe. Use the tools and practices available to you. Stay vigilant. Assume the worst. Protect accordingly.

Protecting Your Digital Identity Long-Term
The Instagram incident is one of many. If you want to maintain reasonably strong digital security over the long term, you need systems and habits that don't require constant vigilance.
Use a password manager as your foundation. Services like Bitwarden (free and open-source), 1Password, LastPass, or Dashlane store all your passwords securely. You only need to remember one master password. The password manager generates strong, unique passwords for every service and fills them in automatically. This solves the password reuse problem that makes data breaches so dangerous.
Enable two-factor authentication everywhere it's offered. This is the single most effective security measure you can implement. Even if your password is compromised, attackers can't access your account without your second factor (usually your phone or an authenticator app). It takes a bit longer to log in, but it's worth the inconvenience.
Review your accounts regularly. Every few months, check what apps have access to your accounts, what data you're sharing, and what settings might need updating. Platforms change permissions, add new features, and sometimes default to less secure settings. Regular review catches problems early.
Monitor your accounts for suspicious activity. Check your email's login history. Check your social media accounts for unfamiliar login locations. Enable alerts for anything unusual. The faster you catch a problem, the more damage you can prevent.
Be skeptical of everything. Assume emails are phishing attempts until proven otherwise. Assume that anyone contacting you unsolicited might be a scammer. Verify information independently rather than clicking links in communications. This skepticism is annoying, but it's increasingly necessary.
Stay informed about security issues. Follow security researchers and credible tech news sources. Know when major incidents happen. If a service you use experiences a breach, take action immediately rather than waiting and hoping.
Consider your digital footprint. The less personal information you publicly share, the less damage a breach can do. Consider making your social media profiles private. Use privacy-conscious email services. Think carefully about what information you provide to companies.
These practices create a security posture that's not perfect but is significantly better than most people have. Perfect security doesn't exist. But practical security—layered defense that makes you a harder target than the average person—is achievable.
The Role of Regulation and What Needs to Change
Individual security practices are necessary but insufficient. We also need systemic change. We need regulation that forces tech companies to prioritize security and transparency.
Here's what effective regulation should require:
Mandatory disclosure timelines: Companies should be required to disclose data breaches within 72 hours of discovery, not months later. This removes the incentive to hide incidents and gives users time to protect themselves.
Transparency about scope: Companies must disclose exactly how many users were affected, what data was compromised, and how the compromise happened. Vague statements should be prohibited.
Independent audits: Major platforms should be required to undergo regular independent security audits by third parties. Companies can't audit themselves.
Meaningful penalties: Fines should be large enough that they actually deter bad behavior. Currently, companies treat fines as a business expense. Penalties should exceed the savings companies made by under-investing in security.
Legal liability: Companies should be legally liable for harms caused by breaches. Users should be able to sue for damages. This aligns company incentives with user protection.
User consent for data collection: Platforms should only be allowed to collect data users have explicitly consented to. The current model of collecting everything and asking forgiveness later should be prohibited.
Right to deletion: Users should have an absolute right to delete their data from platforms. Companies shouldn't be able to maintain databases of deleted users.
Some of this is starting to happen. The EU's General Data Protection Regulation (GDPR) requires notification within 72 hours, independent audits in some cases, and hefty penalties. Other jurisdictions are moving in that direction. But there's a long way to go.
Until regulation catches up, tech companies have little incentive to change. They'll continue to under-invest in security, minimize incidents, hide breaches, and prioritize growth over protection. Users will continue to be at risk.
Advocating for stronger regulation, supporting privacy-conscious policies, and voting for leaders who prioritize digital rights are longer-term plays. But they're essential if we want the digital ecosystem to be genuinely secure and trustworthy.
FAQ
What exactly happened with Instagram's password reset issue?
An external party exploited a vulnerability in Instagram's API that allowed them to trigger password reset emails for millions of users. Meta claims this wasn't a data breach of their systems, but security researchers discovered that 17.5 million account details including emails, phone numbers, and addresses had been leaked and were circulating on hacking forums. The exact source of the leaked data is disputed—it may be from a 2022 or 2024 API incident.
Should I be worried if I received an unsolicited password reset email from Instagram?
Yes, you should take it seriously. While receiving a single password reset email isn't an immediate emergency, it indicates that someone had the ability to trigger requests on your account. More importantly, if you received this email, your account information is likely in the leaked dataset and is being used in phishing campaigns. The email itself isn't dangerous if you ignore it, but you should immediately change your password and enable two-factor authentication.
Is my account data still at risk even after Meta patched the vulnerability?
Yes. Meta patched the vulnerability that allowed external parties to trigger password resets, which is good. However, the underlying problem remains: your personal information (email, phone, name, address) is in criminals' hands and will likely be exploited for years. The patched vulnerability doesn't retrieve stolen data. It only prevents new attacks through that specific vector. Your risk profile depends more on your personal security practices than on whether this particular vulnerability exists.
What's the difference between what Meta calls a "system error" and what Malwarebytes calls a "data breach"?
Meta is technically correct that their systems weren't "breached" in the traditional sense—hackers didn't infiltrate secure systems to steal data. However, an external party did exploit a vulnerability in Meta's API, which is arguably worse in some ways because it suggests systematic security weaknesses. Malwarebytes' report that 17.5 million account details were leaked indicates that data was stolen at some point, whether from this incident or a previous one. The distinction is mostly semantic, and both paint a picture of inadequate security.
Can I do anything to protect myself from the phishing attacks that will likely target me?
Yes, several things. First, change your Instagram password to something strong and unique. Second, enable two-factor authentication on Instagram and your email account. Third, be extremely skeptical of any emails asking you to verify information or reset passwords—assume they're phishing attempts. Navigate directly to official websites rather than clicking links in emails. Use a password manager to avoid reusing passwords across platforms. Monitor your accounts for unfamiliar login activity. These practices make you a harder target and reduce the likelihood that you'll fall victim to attacks.
What should I do if my personal information was in the leaked data and I'm worried about identity theft?
Consider enrolling in an identity monitoring service that alerts you if your information is used fraudulently. Place a fraud alert with the credit bureaus (Equifax, Experian, TransUnion) to make it harder for fraudsters to open accounts in your name. You can also request a credit freeze, which prevents anyone from accessing your credit report without a PIN you control. These steps don't prevent identity theft but make it much harder for criminals to exploit your stolen information.
Why doesn't Meta just tell us exactly what happened and how many people were affected?
Transparency about breaches is expensive for companies. Disclosures trigger regulatory investigations, civil lawsuits, PR damage, and potential fines. There's a financial incentive to minimize incidents and avoid transparency. Additionally, providing exact numbers and timelines might reveal additional security failures or demonstrate how long vulnerabilities existed. From Meta's perspective, a vague statement is preferable to a detailed disclosure that could trigger greater liability.
Will Instagram's password reset functionality be less secure going forward to prevent this from happening again?
Meta will likely implement better rate limiting, validation, and authentication on the API endpoint that controls password resets. However, security improvements are usually invisible to users. You probably won't notice any changes because you won't be interacting directly with that API. The improvements will be on Instagram's backend. Whether these improvements are sufficient or just superficial is unclear since Meta hasn't been transparent about the technical details.
How do I know if my Instagram account was actually affected by this incident?
You can check if your email appears in the leaked dataset using Have I Been Pwned (haveibeenpwned.com). If your email is in the dataset, your account was likely affected. Meta hasn't provided an official list of affected accounts because it doesn't want to admit the scale of the incident. Security researchers and forensic investigators are slowly mapping the scope of the incident, but complete information isn't publicly available.
What are the signs that my Instagram account might have been compromised?
Signs include: inability to log in (password might have been changed), unfamiliar posts or stories on your profile, changes to your email address or phone number in account settings, friend requests you didn't send, messages sent from your account you didn't write, or notifications of login attempts from unfamiliar locations. If you notice any of these, try to regain access immediately. If you can't, use Instagram's recovery process or contact support.
Will regulatory action force Meta to improve security practices?
Possibly, but regulatory change is slow. The FTC has fined Meta multiple times for security failures, but the fines haven't been large enough to meaningfully change the company's behavior. Stronger regulation would require clearer security standards, mandatory disclosure rules, independent audits, and penalties that actually deter bad behavior. Some jurisdictions (particularly the EU with GDPR) are moving in this direction, but comprehensive global regulation is years away. In the meantime, users should assume personal responsibility for security.

Final Thoughts
The Instagram password reset incident is a reminder that no major tech platform has fully solved the problem of user data security. Even with enormous resources, sophisticated security teams, and regulatory pressure, Meta failed to properly secure a critical endpoint. Your data was stolen and is being actively exploited.
This isn't a reason to panic, but it is a reason to act. The steps outlined in this article aren't optional best practices. They're essential baseline security measures that everyone with an Instagram account should implement immediately.
Your data has probably been compromised multiple times in ways you don't even know about. That's the reality of the digital ecosystem we live in. But compromised data only becomes dangerous when combined with weak security practices on your part. Strong passwords, two-factor authentication, and healthy skepticism create a defense that makes you a much harder target.
The responsibility for your digital security lies partly with you and partly with the platforms you use. You can't control what Meta does or doesn't do. But you can control your passwords, your authentication methods, and your behavior online. Focus on what you can control and assume the worst about what you can't.
Stay vigilant. Take action today. Don't wait for another incident to force you to improve your security posture. The attacks are already happening. Your defenses should be in place now.

Key Takeaways
- Meta didn't experience a traditional breach, but an external party exploited an API vulnerability to trigger password resets on millions of accounts
- 17.5 million Instagram account records including emails, phone numbers, and postal addresses were leaked and are actively being used in phishing campaigns
- Change your Instagram password immediately to a strong unique password, enable two-factor authentication, and assume your data is already in criminals' hands
- The real security risks come through phishing attacks, SIM swapping, and data aggregation with other leaked datasets, not from the password reset emails themselves
- Long-term protection requires a multi-layered approach: password manager, two-factor authentication, account monitoring, skepticism of unsolicited communications, and regular security reviews
Related Articles
- Instagram Password Reset Incident: What Really Happened [2025]
- Instagram Password Reset Email Bug: What Happened and What You Need to Know [2025]
- WhatsApp Security Features: Complete Privacy Guide [2025]
- Rainbow Six Siege Server Shutdown: Marketplace Hack Explained [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- 1Password Coupons & Free Trial: Complete Savings Guide [2025]
![Instagram Password Reset Emails: What You Need to Know [2025]](https://tryrunable.com/blog/instagram-password-reset-emails-what-you-need-to-know-2025/image-1-1768217898236.jpg)



