Instagram Password Reset Incident: What Really Happened [2025]
Last week, something odd started happening on Instagram. Users across the globe woke up to emails claiming their account had a password reset request—except they never asked for one. The incident triggered immediate concern: was Instagram hacked? Are millions of accounts exposed? Within hours, the narrative shifted. Instagram claimed it fixed a "technical issue" that allowed an "external party" to request password resets. But the company's vague response left everyone asking the real questions.
This is the kind of security event that defines how we think about platform safety for months. So let's dig into what actually happened, what it tells us about how social platforms handle security, and most importantly, what you should do to protect your account right now.
TL; DR
- What happened: An external party exploited a vulnerability in Instagram's password reset system to request resets for millions of accounts without authorization, as reported by Engadget.
- Scale of the issue: Approximately 17.5 million Instagram accounts were affected according to initial reports from Cyber Insider.
- Data exposed: Usernames, physical addresses, phone numbers, and email addresses were potentially compromised, as noted by Forbes.
- Instagram's response: The company fixed the vulnerability but provided minimal detail about the incident or the threat actor, according to Engadget.
- What you should do: Change your password immediately, enable two-factor authentication, and monitor your account for suspicious activity, as advised by PCMag.
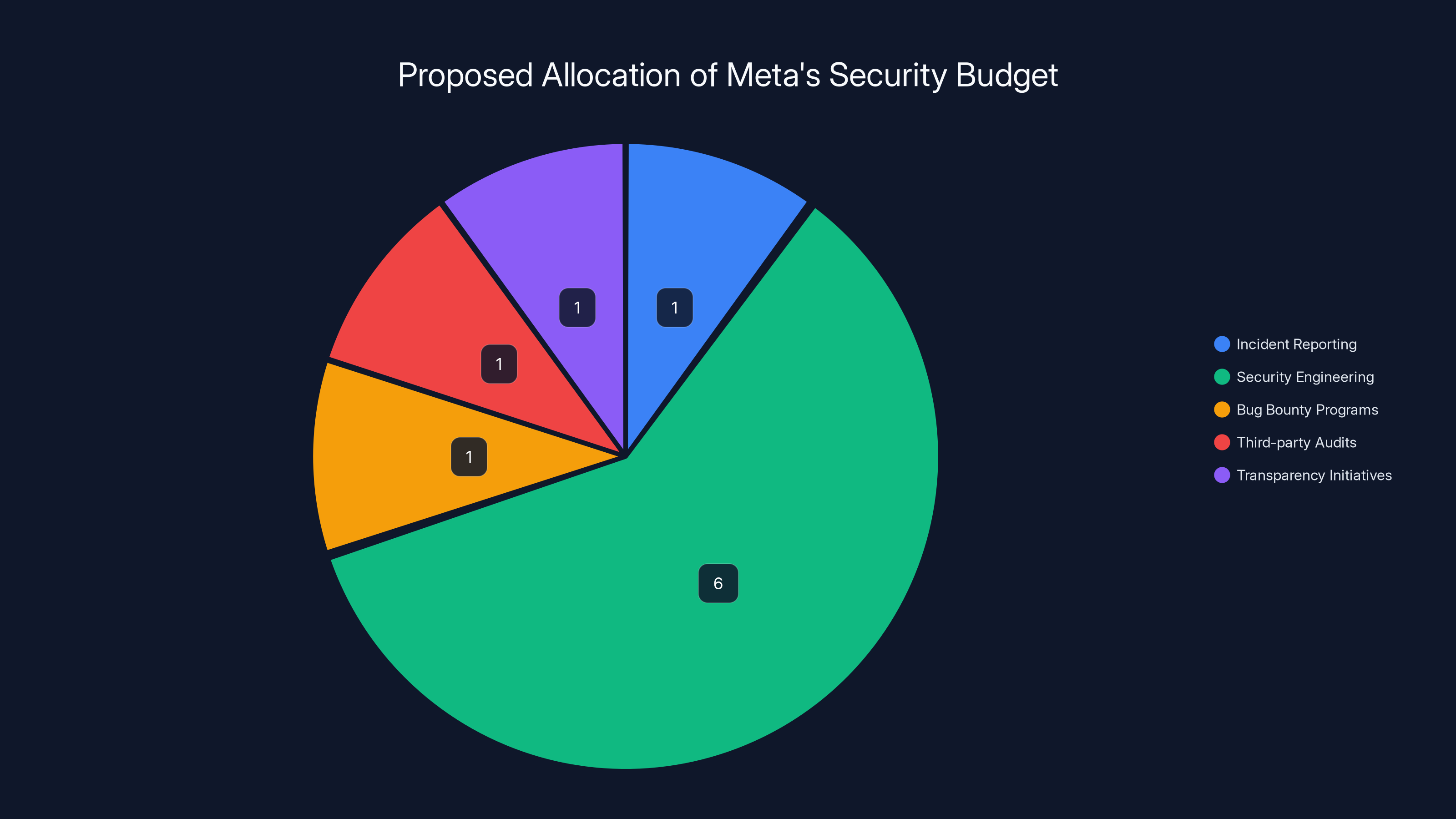
Estimated data shows a potential allocation of Meta's proposed $10 billion security budget, emphasizing security engineering and transparency. Estimated data.
The Timeline: How the Incident Unfolded
Understanding this incident requires looking at how it emerged in public, because the story got messier before it got clearer.
On Friday morning, Malwarebytes—a respected antivirus and cybersecurity company—posted on Bluesky about an alarming discovery. The post included a screenshot of an email from Instagram's official accounts, notifying a user of an unauthorized password reset request. Malwarebytes claimed that cybercriminals had stolen data from 17.5 million Instagram accounts, including usernames, physical addresses, phone numbers, and email addresses. The kicker? This data, they said, was being sold on the dark web.
This kind of post spreads fast. Within hours, Twitter, Reddit, and tech news sites were flooded with screenshots from users who'd received the same suspicious emails. The evidence seemed overwhelming: users were definitely receiving password reset requests they hadn't initiated. What wasn't clear was whether this was a mass breach, a targeted attack, or something else entirely.
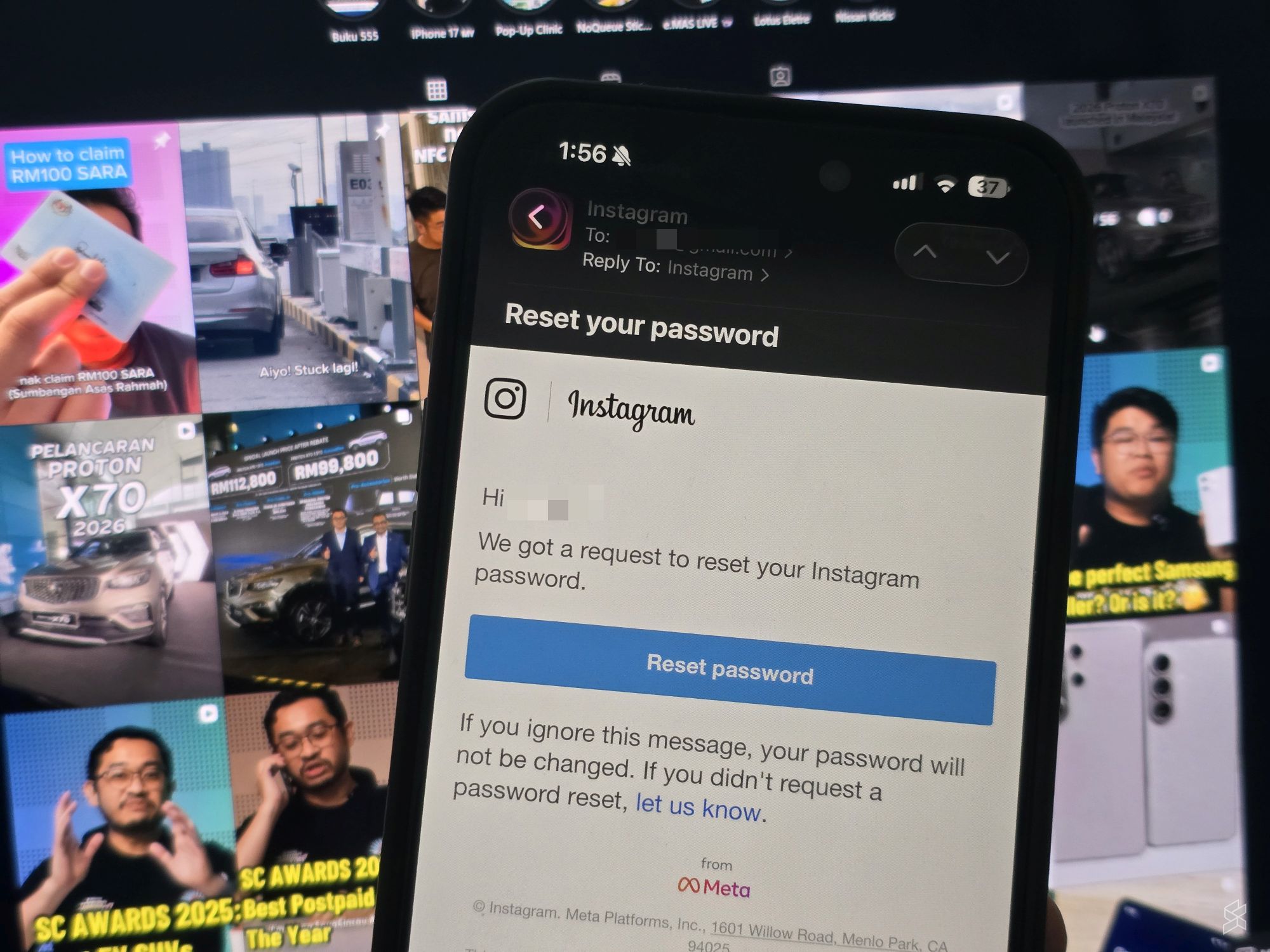
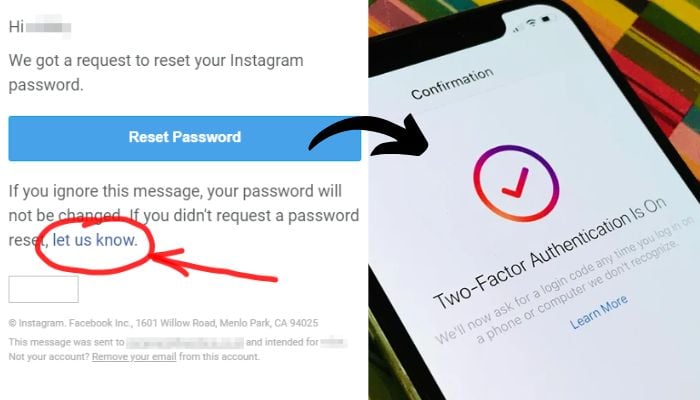
Then Instagram responded—not on Instagram or Threads, but on X (Twitter). The response was brief: "We fixed an issue that let an external party request password reset emails for some people. You can ignore those emails—sorry for any confusion," as noted by Forbes.
That's it. No explanation of how the vulnerability existed, who the external party was, how many accounts were actually affected, or whether any data was actually stolen.
The contrast between Malwarebytes' detailed claim and Instagram's dismissive response created a vacuum of information. That vacuum filled with speculation, fear, and legitimate security concerns.

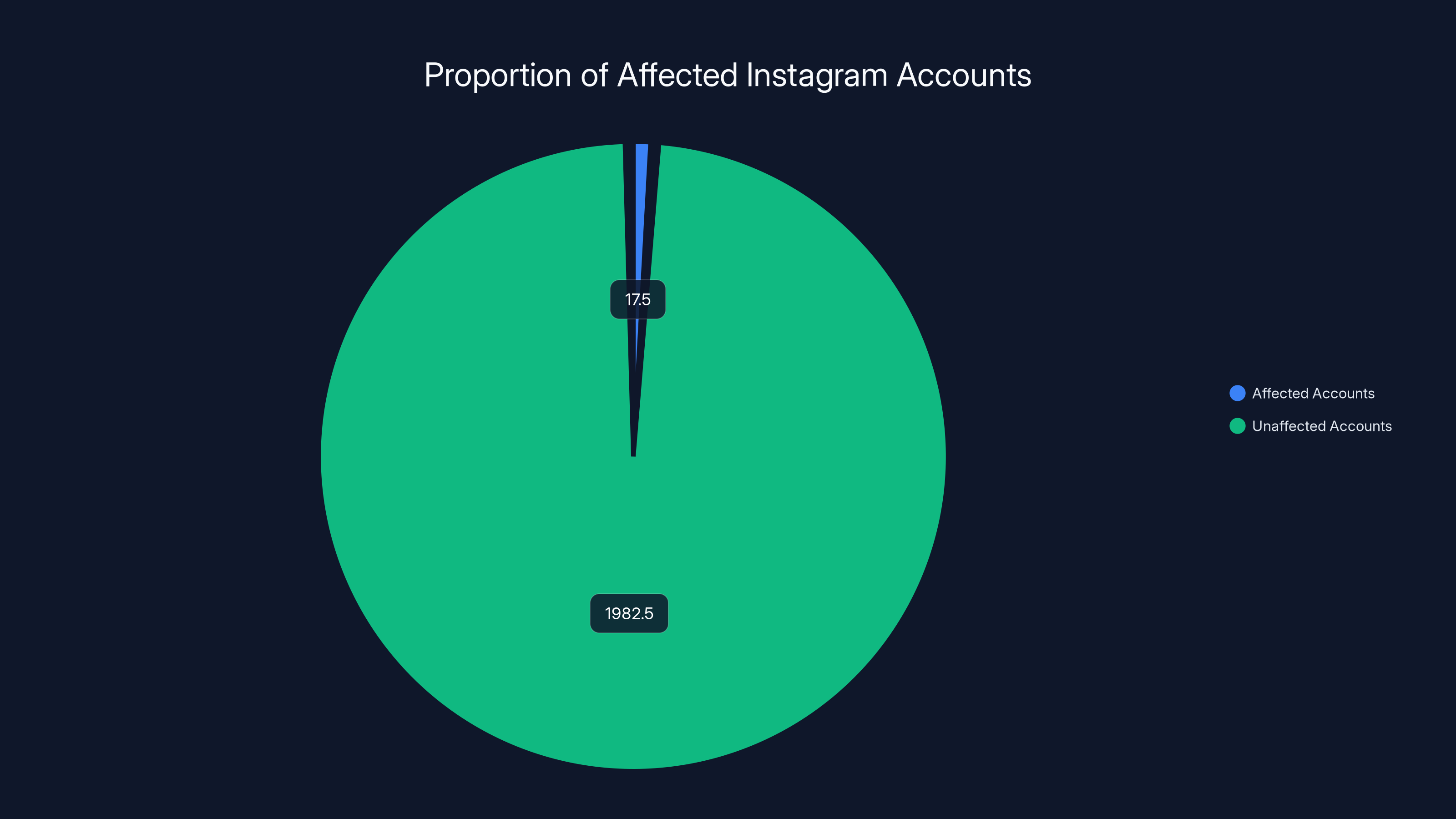
Estimated data shows that affected accounts represent less than 1% of Instagram's 2 billion active users, highlighting the scale of the issue in context.
What the Vulnerability Actually Was
Let's talk technical for a moment, because understanding how this happened matters more than Instagram's official statement.
Password reset mechanisms are typically considered low-risk because they're supposed to be gated. You request a reset, the service sends a link to your email, you click the link from your email inbox, and then you set a new password. The security model assumes that if someone requests a reset, it's either you or someone who has access to your email.
But something went wrong with this assumption on Instagram's side.
The vulnerability that was exploited allowed an external party to request password reset emails on behalf of other users without proper verification. This is a critical flaw in what's called "account takeover prevention." Essentially, Instagram's system accepted password reset requests without sufficiently validating whether the person making the request actually controlled the account, as detailed by WIBC.
Here's what that vulnerability likely enabled:
An attacker could have programmatically sent password reset requests for thousands or millions of accounts. Even if the attacker didn't immediately take over the accounts, they could achieve several objectives: they could monitor which emails the accounts were tied to, they could attempt to access those email accounts, or they could simply spam users with password reset emails to cause disruption.
The fact that this vulnerability existed at all is significant. Password reset functionality is fundamental to account security, and it's one of the first things security teams typically harden. That this slipped through suggests either inadequate testing, insufficient security review, or both.
What's unclear is whether the attacker actually weaponized this vulnerability to steal account data or simply to cause disruption. Malwarebytes claimed data was stolen and sold on the dark web, but Instagram's response suggests the main issue was the technical vulnerability itself, not necessarily that masses of data were exfiltrated, as noted by Forbes.

The Data Breach Debate: Breach vs. Vulnerability Exploitation
This is where things get semantically important and technically interesting.
Instagram's position is that there was no breach—just an exploited vulnerability. Malwarebytes' position is that there was a breach and data was stolen. Who's right?
Technically, both statements can be true simultaneously. A breach means unauthorized access to data. A vulnerability exploitation means taking advantage of a system flaw. You can exploit a vulnerability without accessing data. You can also exploit a vulnerability to access data, which would be a breach.
The critical question is whether the attacker who exploited this password reset vulnerability actually extracted the sensitive data (usernames, phone numbers, addresses, email addresses) or simply used the vulnerability to spam users with reset requests.
Instagram's silence on this point is telling. If the attacker had only spammed users with reset emails, Instagram could have easily said so. Instead, the company remained vague, which suggests uncertainty about the actual scope of the incident. Did they investigate fully? Did they find evidence of data exfiltration? Or did they simply plug the hole and hope the story would go away?
The presence of user data on dark web marketplaces is often cited as proof of a breach. But dark web data brokers regularly recycle old stolen data from previous breaches, repackage it, and resell it as "new." Without access to the actual dark web listing that Malwarebytes referenced, it's impossible to verify whether this data was freshly stolen or recycled from an older incident, as discussed by Corporate Compliance Insights.
What we can say with certainty: a vulnerability existed, it was exploited by an external party, password reset emails were sent without authorization, and Instagram fixed the issue. Everything beyond that is speculation.
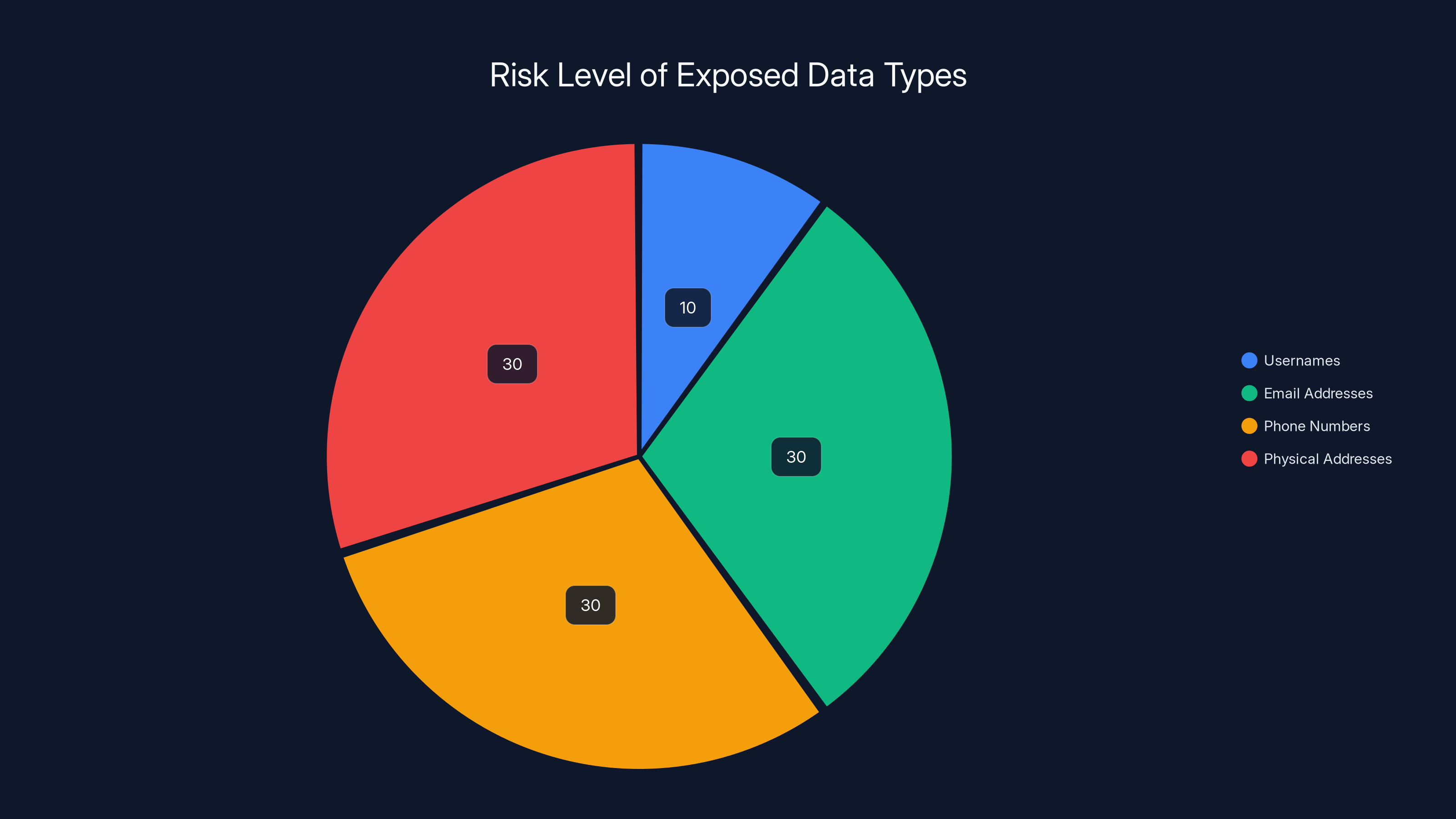
Physical addresses, email addresses, and phone numbers are estimated to carry higher risk levels compared to usernames due to their potential use in identity theft and phishing attacks. Estimated data.
Why Instagram's Response Was Inadequate
Let's be direct: Instagram's response to this incident was poor communication dressed up as transparency.
Here's what the company should have done:
First, they should have published a detailed security advisory explaining exactly what happened, when they discovered it, when they fixed it, and what they found during their investigation. Second, they should have disclosed concrete numbers: how many accounts were affected, over what time period, and whether any data was actually stolen. Third, they should have provided actionable guidance to users about what to do right now. Fourth, they should have explained how this slipped through their security processes and what changes they're making to prevent it from happening again.
Instead, Instagram posted a sentence on Twitter and went quiet, as highlighted by Gulf News.
This response reflects a broader problem in tech: companies treat security incidents as PR problems instead of actual problems. The goal becomes minimizing negative coverage rather than informing users and rebuilding trust.
When Instagram says "You can ignore those emails—sorry for any confusion," they're treating a potential account security threat as a minor glitch. But users received emails that looked exactly like legitimate password reset requests. Some probably panicked. Some might have clicked them. Some definitely tried to reset their passwords out of confusion or fear.
That's not confusion. That's a security incident.
The fact that we're piecing together what happened from Malwarebytes' post and Instagram's reluctant one-liner shows a failure of corporate responsibility. In the era of widespread data breaches, users deserve transparency. They deserve to know if their data might be at risk. They deserve to understand what they should do to protect themselves.
Instagram gave them none of that.
The Scale: How Many Accounts Were Actually Affected?
Malwarebytes claimed 17.5 million accounts were affected. That's a specific number, which is either based on actual data or an educated guess based on incomplete information.
Let's put that in context. Instagram has approximately 2 billion monthly active users. If 17.5 million accounts were affected, that's less than 1% of the user base. It's significant but not catastrophic. On the other hand, 17.5 million is massive in absolute terms—that's more people than live in many countries.
What we don't know:
Were all 17.5 million accounts actually targeted by the attacker, or is that the number of accounts that could have been affected by the vulnerability during the time it was active? There's a meaningful difference. A vulnerability might exist for days or weeks before anyone exploits it. Once an attacker discovers it, they might only target a subset of accounts. Or they might target millions within hours.
Did the attacker actually access and exfiltrate data from 17.5 million accounts, or did they simply request password resets for 17.5 million accounts? The latter is far less damaging than the former. A password reset request sitting in your email is a nuisance. Stolen personal data is a security and privacy violation.
Instagram's refusal to clarify these numbers is frustrating but not surprising. The company is likely still investigating, and publicly stating specific numbers before the investigation is complete could expose them to legal liability. But from a user perspective, this ambiguity is dangerous. It forces users to assume the worst and act accordingly, as discussed by MSN.
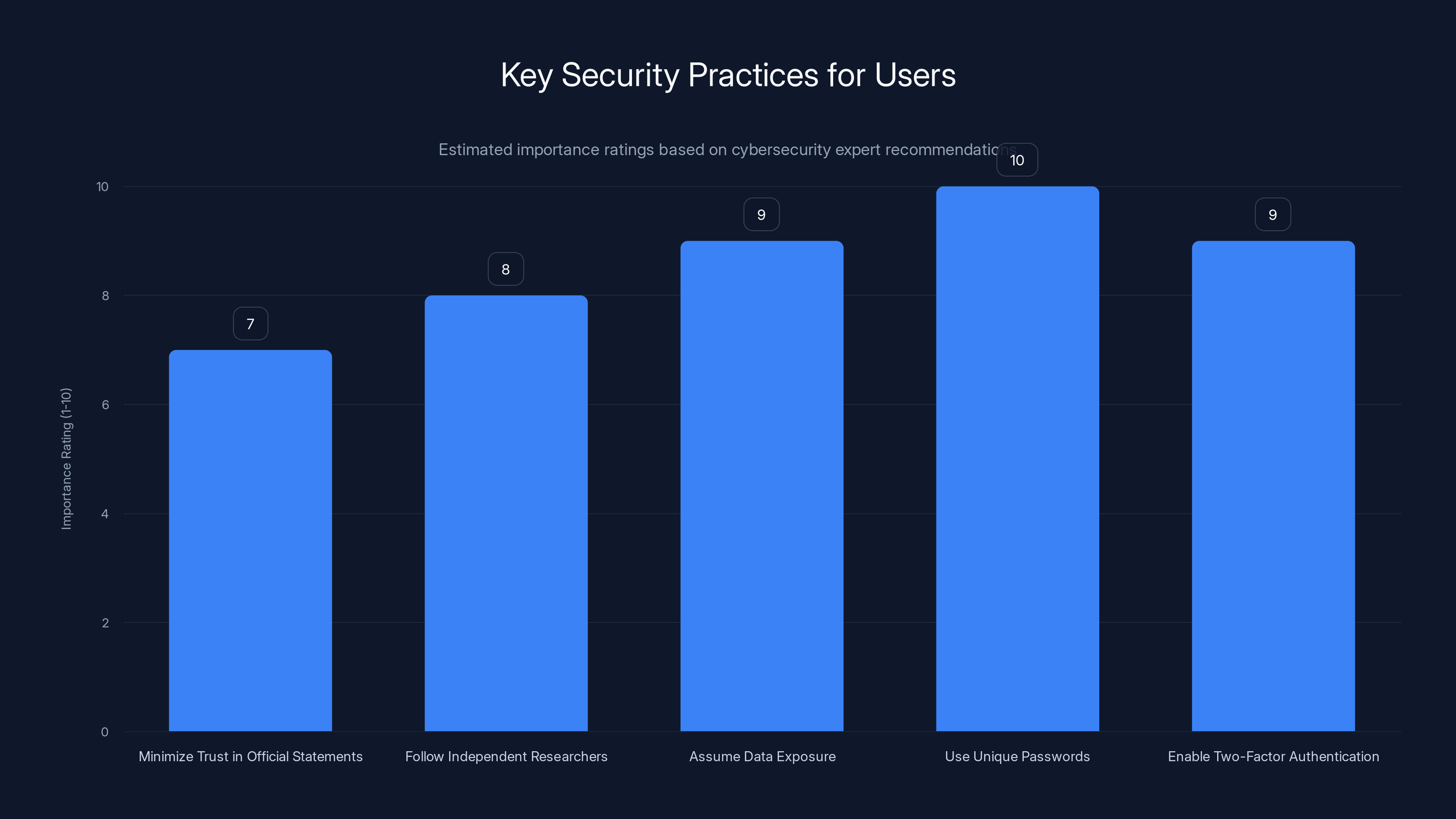
Using unique passwords and enabling two-factor authentication are rated as the most crucial practices for users to protect their data. Estimated data based on expert advice.
What Data Was Exposed (And What That Means)
According to Malwarebytes, the exposed data included:
- Usernames: Your public profile identifier
- Physical addresses: Your home location
- Phone numbers: Your contact number
- Email addresses: Your account email
Each of these has security and privacy implications, but they're not equally dangerous.
Usernames alone are low-risk. They're public by nature on social platforms. Knowing someone's Instagram username doesn't grant access to their account.
Email addresses and phone numbers are higher-risk. These are the recovery mechanisms for most accounts. If an attacker has both your email and phone number, they can attempt account takeover on other services. They can also use this data for targeted phishing attacks.
Physical addresses are the most invasive. Combined with your name (derived from your username and profile), an attacker has the information needed for identity theft, physical stalking, or targeted harassment.
The combination of all four data points creates a complete identity profile that can be weaponized in multiple ways. This is why the distinction between a mere vulnerability exploitation and an actual data breach matters.
If attackers do have this data, they'll likely use it for several purposes:
First, targeted phishing campaigns. Attackers can send emails or SMS messages that appear to come from Instagram, using your actual name and account details to add credibility. Second, account takeover attempts on other services. Many people reuse email addresses across multiple platforms. If your email is tied to other accounts—banking, email providers, social media—the attacker has more targets. Third, identity theft. With your full name, address, email, and phone number, attackers can attempt to take over or create fraudulent accounts in your name. Fourth, social engineering. This data can be used to impersonate you or conduct targeted social engineering attacks against your contacts or employers.
The severity of exposure depends entirely on whether the data was actually stolen or just the vulnerability was exploited. That's the answer Instagram won't clearly give, as noted by Forbes.
How Instagram's Security Processes Failed (And What That Reveals)
For a company as large as Meta, with billions in revenue and dedicated security teams, this vulnerability shouldn't have existed in the first place.
Password reset functionality is not cutting-edge infrastructure. It's well-understood, extensively documented, and there are established best practices for implementing it securely. The OWASP Top 10 (Open Web Application Security Project, the leading authority on web application security) explicitly covers account takeover and password reset mechanisms. Every security engineer knows how to implement password resets properly.
So how did this slip through?
There are several possibilities:
First, inadequate code review. The vulnerability might have been introduced in a recent code change and not caught during code review. This suggests either reviewers weren't looking for security issues or the code change wasn't flagged for security review.
Second, insufficient test coverage. If Instagram's automated and manual tests didn't include attempts to request password resets for unauthorized accounts, they wouldn't have caught this issue. This suggests either the test suite was incomplete or the testing process wasn't rigorous enough.
Third, security technical debt. Older code paths might have been refactored or updated without proper security auditing. The vulnerability could have been lurking in legacy code that was updated but not fully secured.
Fourth, insufficient threat modeling. During the design phase of new features, security teams conduct threat modeling to identify potential attack vectors. If this password reset vulnerability wasn't identified during threat modeling, it suggests the process wasn't thorough.
Fifth, misconfiguration or deployment issues. Sometimes vulnerabilities are introduced during deployment or configuration changes, not in the code itself. A wrong setting on an API rate limiter, an insufficient validation rule, or an improperly configured permission could all cause this kind of issue.
The real answer likely involves some combination of these factors. Large companies rarely suffer single points of failure in security—they fail due to multiple small failures that compound.
What this incident reveals about Instagram's security culture is concerning. For a company with billions of users and recurring privacy issues, you'd expect aggressive, paranoid security practices. The presence of this vulnerability suggests otherwise.
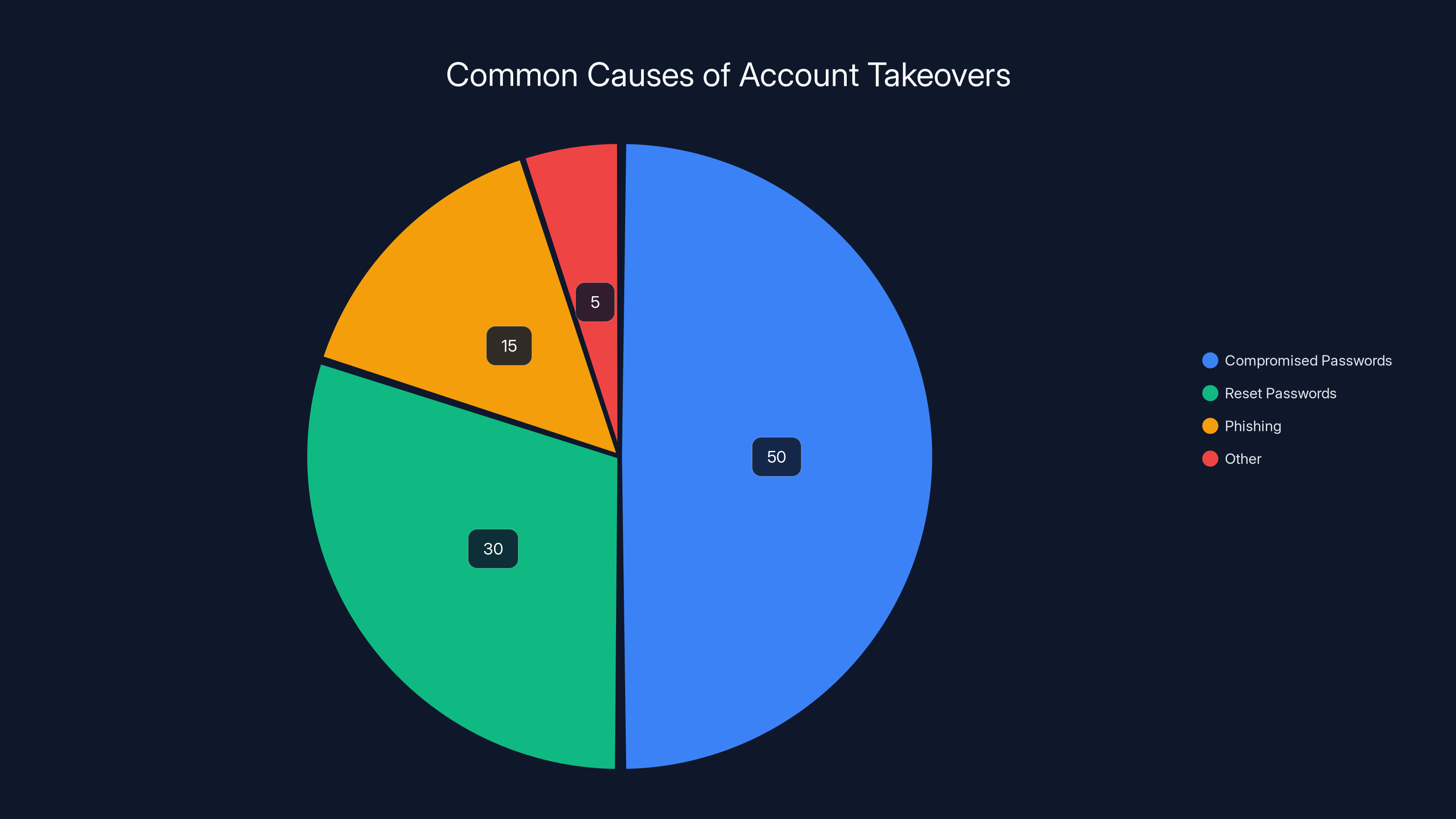
Estimated data suggests that compromised or reset passwords account for 80% of account takeovers, highlighting the critical need for robust password reset mechanisms.
The Bigger Picture: Why This Keeps Happening
This incident isn't an anomaly. It's part of a pattern.
Over the past five years, Instagram and its parent company Meta have experienced numerous security and privacy issues: the Cambridge Analytica data sharing scandal involving millions of user profiles, the leak of 533 million Facebook users' phone numbers, the Facebook Outages that exposed credentials, the Instagram API exposures that revealed millions of phone numbers and email addresses. The list goes on.
Each time, Meta publishes a statement expressing regret, assures users that security is a priority, and promises improvements. And then another incident happens.
This pattern suggests one of two things, or both:
First, Meta's security infrastructure is legitimately struggling under the scale of their operations. Managing security across billions of users, thousands of services, and millions of lines of code is incomprehensibly complex. Mistakes happen, and at that scale, even small percentages of failures affect millions of people.
Second, Meta deprioritizes security in favor of speed to market and feature development. Implementing rigorous security practices takes time and slows down feature releases. If the company's culture rewards rapid feature shipping over security, vulnerabilities will accumulate.
Both are likely true to some degree.
The problem is that users have no leverage to demand change. You can't switch to a different social platform because Meta owns the market. Instagram, WhatsApp, and Facebook collectively serve billions of people. There's no meaningful alternative. So Meta has little incentive to dramatically increase security spending or slow down feature development for security improvements.
This is a structural problem in how platform monopolies operate. When there's no competition, there's no pressure to improve security. Users get whatever security the company decides to provide.
What You Should Do Right Now (Actionable Steps)
Enough analysis. Here's what you need to actually do to protect your Instagram account.
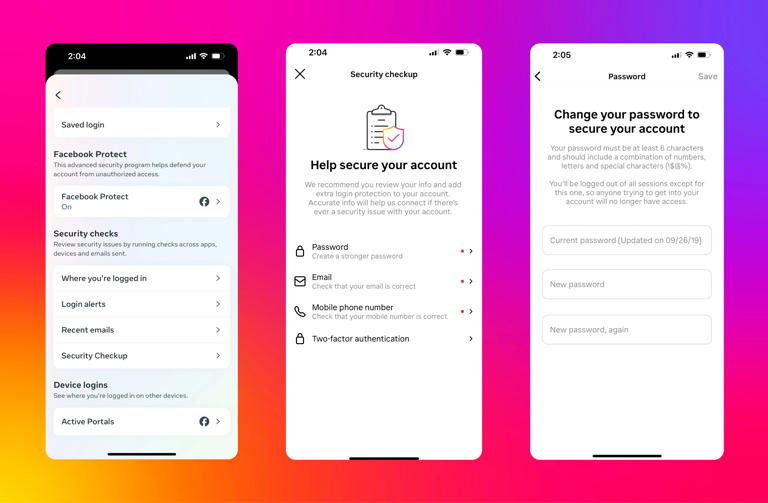
Step 1: Change Your Instagram Password Immediately
Don't wait. Even though Instagram says the vulnerability has been fixed, attackers might have already accessed your account or credentials. Use a strong, unique password that you don't use anywhere else. Your password should be at least 16 characters long and include uppercase letters, lowercase letters, numbers, and special characters.
Step 2: Enable Two-Factor Authentication
Log into Instagram, go to Settings > Security > Two-factor authentication, and enable it. Choose either an authentication app (Google Authenticator, Authy, or Microsoft Authenticator are all good options) or SMS-based 2FA. An authentication app is more secure than SMS, but SMS is better than nothing. Once enabled, anyone trying to log into your account will need both your password and a code from your phone.
Step 3: Review Your Account Activity
Go to Settings > Security > Login activity. Look at the list of devices and locations that have accessed your account. If you see any unfamiliar logins, click on them and select "Log out of that session." Then change your password again.
Step 4: Check Your Email and Phone Security
Since your email address and phone number might be exposed, secure those accounts too. Change the passwords for your email provider (Gmail, Outlook, Yahoo, etc.) and review the security settings. Enable 2FA if you haven't already. Add a recovery email or phone number to your email account in case someone tries to take it over.
Step 5: Monitor Your Accounts for Fraudulent Activity
For the next few months, watch your accounts carefully. Check your bank accounts, credit card statements, and email inboxes regularly. If you notice anything suspicious—unexpected charges, password reset emails from services you didn't sign up for, or emails to an account you don't recognize—report it immediately to the relevant service.
Step 6: Consider a Credit Freeze
If you're particularly concerned about identity theft, you can place a credit freeze with the major credit reporting agencies (Equifax, Experian, and Trans Union in the US). This prevents anyone from opening new credit accounts in your name without your permission. It's free and takes about 10 minutes per agency.
Step 7: Keep an Eye on the Dark Web
If you're technically inclined, you can check whether your email address or phone number appears in data breaches by using services like Have I Been Pwned. Just enter your email address and the service will tell you if it's appeared in any publicly documented breaches. This won't help with newly exposed data, but it gives you baseline information.
These steps might seem like overkill for a vulnerability that Instagram claims didn't result in a breach. But that's the point: Instagram won't clearly tell you what happened, so you should assume the worst and act accordingly. Taking these steps takes maybe 30 minutes and provides substantial protection against account takeover and identity theft.
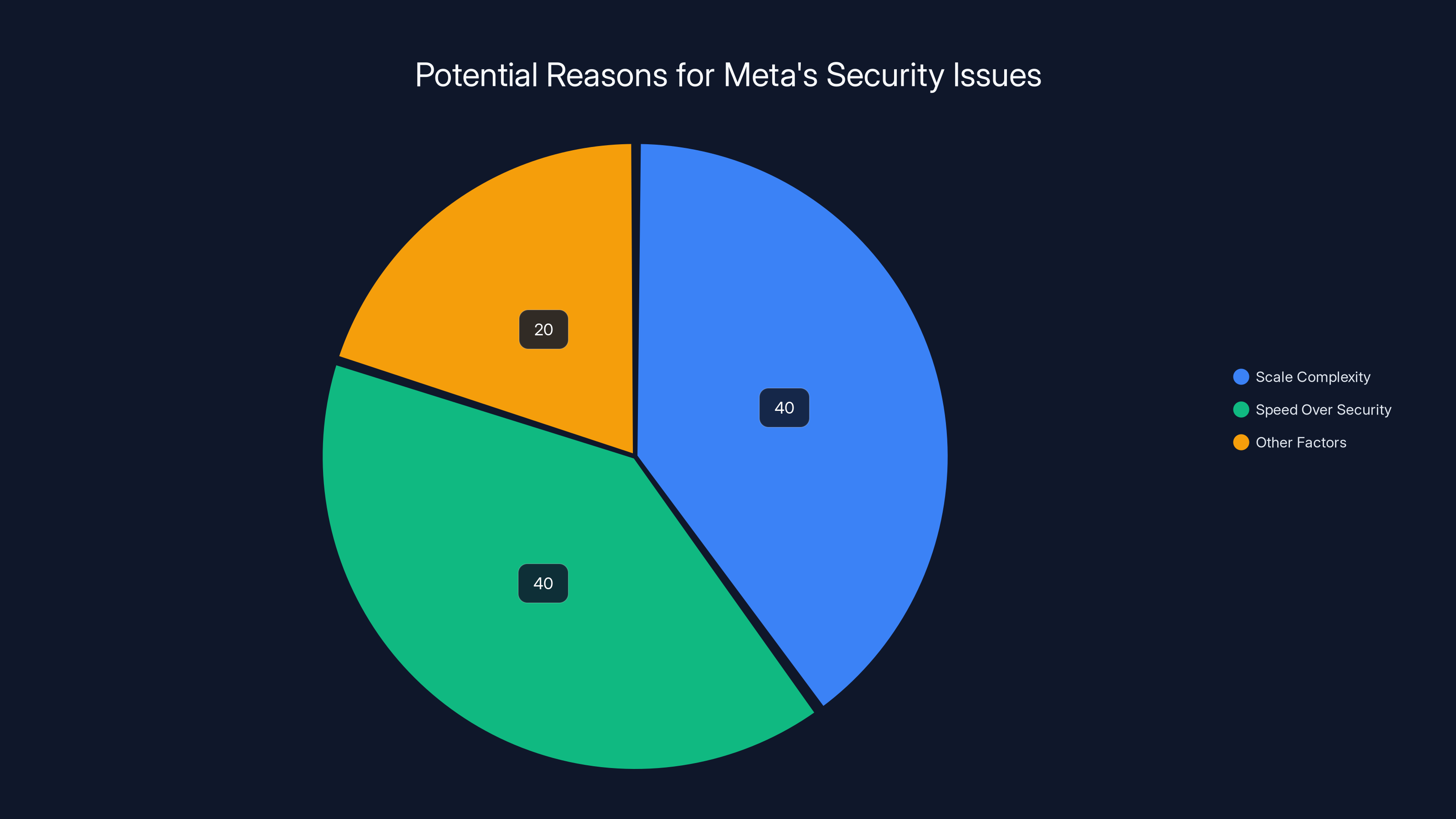
Estimated data suggests that both the complexity of scale and prioritizing speed over security equally contribute to Meta's security issues, with other factors playing a smaller role.
Instagram's Pattern of Vague Security Responses
One thing worth noting is that this response—"we fixed a thing, sorry, don't worry"—is exactly how Meta has responded to previous incidents.
When millions of Instagram phone numbers were exposed through the Instagram Friends app in 2019, Meta's response was brief and vague. When Facebook and Instagram suffered major outages in 2021 that exposed technical credentials, the company's response was minimal. When billions of user records were exposed across multiple breaches, Meta often claimed to have fixed the issue after the fact, without providing details.
This pattern suggests a deliberate strategy: acknowledge the problem minimally, fix the technical issue, and hope the news cycle moves on before detailed investigations reveal the full scope of what happened.
From a PR perspective, it's actually effective. Most people don't follow security incidents closely. They see a headline, maybe read one article, and move on. By the time security researchers publish detailed analyses, most of the public attention has already moved to the next story.
But this strategy is disrespectful to users. It treats security incidents as reputational problems to be managed rather than trust violations to be addressed. It prioritizes damage control over user protection.
If Instagram genuinely cared about user security, the company would publish a detailed incident report including:
- The exact vulnerability (technical description)
- When it was discovered and when it was fixed
- How long it was active
- How many accounts were affected
- What data was accessed
- What steps the company is taking to prevent similar issues
- What users should do
Instead, Instagram gave us a sentence. That tells you all you need to know about how much the company prioritizes your security.

The Regulatory Implications: What Happens Next?
This incident might have legal consequences beyond the immediate security issue.
In the European Union, Meta is subject to the General Data Protection Regulation (GDPR). Under GDPR, companies have a legal obligation to report data breaches to authorities and affected users within 72 hours. If data was actually stolen in this incident, Meta might face penalties for not reporting it quickly enough or thoroughly enough.
In the United States, there's no comprehensive federal privacy law covering social media, but various states have enacted their own privacy laws (California's Consumer Privacy Act, Colorado's Privacy Act, etc.). Meta must comply with these in addition to sector-specific regulations like HIPAA (healthcare) and FERPA (education).
Moreover, the Federal Trade Commission (FTC) has ongoing oversight of Meta following the Cambridge Analytica scandal. The FTC could use this incident as evidence of continued security negligence and pursue additional fines or restrictions.
The question is whether this incident qualifies as a data breach requiring regulatory reporting. If no data was actually exfiltrated—if the attacker only successfully requested password resets—then legally, this might be an exploited vulnerability rather than a breach. But if data was stolen, Meta has serious regulatory exposure.
The ambiguity in Meta's response might be deliberate. By not clearly stating whether a breach occurred, the company keeps wiggle room for regulatory purposes. If investigations later reveal no data theft, the company can say "we handled this correctly as a vulnerability fix." If data theft is confirmed, the company can say "we were working under incomplete information at the time."
This is cynical, but it's how large companies typically handle these situations.

The Role of Security Researchers: How We Know What Happened
The fact that we know anything about this incident is thanks to Malwarebytes and other security researchers who monitor the internet for evidence of breaches and exploits.
Malwarebytes posted on Bluesky because the company has a platform (it's a security software provider, so it has credibility and reach) and because Bluesky is more open to technical discussions than mainstream social media. The post got attention because it included a specific claim (17.5 million accounts) and named a specific data broker (dark web sales).
But here's the thing: we don't actually know if Malwarebytes' claim is accurate. The company didn't provide links to the dark web listing, didn't provide sample data, and didn't provide technical details about how they determined the scope of the breach. For all we know, Malwarebytes saw a rumor on a hacker forum and published it as fact.
That's not to say Malwarebytes is being dishonest. The company is reputable in the security community. But the nature of cybersecurity research means you often work with incomplete information. You see artifacts of breaches (like data on dark web markets) but struggle to determine their origin and scope.
This is why security professionals recommend treating all incident reports with some skepticism until official investigations are complete and verified. But it's also why we can't rely entirely on companies' official statements, because those are often intentionally vague.
The truth usually lies somewhere in between: Malwarebytes' claim is probably based on something real (either evidence of stolen data or an insider tip), and Instagram's response is probably both a genuine fix and a deliberate downplay of the severity.

Lessons for Users: How to Evaluate Security Claims
This incident teaches several lessons about how to think about cybersecurity in 2025.
First, assume companies will minimize security incidents. When a company experiences a breach or vulnerability, their first instinct is to minimize the damage and move on. This isn't because companies are evil; it's because security incidents are bad for business. Users lose trust, regulators investigate, and stock prices sometimes drop. So companies are incentivized to downplay incidents. This means you should never take a company's official security statement at face value.
Second, follow independent security researchers. Websites like Bleeping Computer, Brian Krebs' Krebs on Security, and the teams behind sites like Have I Been Pwned track breaches independently. These sources often have better information than official company statements because they're not trying to protect anyone's reputation.
Third, assume your data is already exposed. The average person's personal information has been involved in multiple breaches. Your email address, phone number, and home address are probably already circulating on dark web marketplaces. This might sound depressing, but it's liberating. You can't protect data that's already out there, so stop trying. Instead, focus on protecting the systems tied to that data (your email account, your bank accounts, your social media) using strong passwords and two-factor authentication.
Fourth, use unique passwords for everything. This is the single most important security practice. If one service gets breached (and statistically, services you use will get breached), attackers will try to use that password on other services. If your password is unique to that service, the breach is contained. If you reuse passwords, one breach compromises everything.
Fifth, enable two-factor authentication. Strong passwords can be cracked. Two-factor authentication can't be. If a service offers 2FA (and most major ones do), use it. Yes, it's slightly inconvenient. That inconvenience is worth the dramatic increase in security.
Looking Forward: What Changes Are Needed?
This incident suggests that Meta's approach to security needs fundamental change.
First, the company should publish detailed incident reports for all security issues, not minimal statements. Users deserve to know what happened, how it happened, and what the company is doing about it. Transparency builds trust. Vagueness destroys it.
Second, Meta should dramatically increase security spending. The company's revenue is over
Third, Meta should implement bug bounty programs more aggressively. Security researchers who find vulnerabilities like this one should be compensated well for reporting them. A $50,000 bounty is far cheaper than dealing with a large-scale incident.
Fourth, Meta should subject critical infrastructure (like password reset mechanisms) to third-party security audits regularly. External auditors can sometimes catch issues that internal teams miss because they approach the code with fresh eyes and no assumptions.
Fifth, Meta should be more transparent about its security practices generally. Publishing detailed information about how the company secures user accounts, what encryption standards it uses, and what security infrastructure it maintains would help users understand what protections they have and would build confidence.
Will any of this happen? Probably not, as long as Meta remains the dominant social media platform. Without competition or regulatory pressure to force change, the company will continue its current approach: minimal disclosure, reactive fixes, and hoping incidents fade from public memory.
But users should demand better. Your data security matters. It deserves more than a one-line Twitter response.

FAQ
What exactly was the Instagram vulnerability?
The vulnerability allowed external attackers to request password reset emails for Instagram accounts without authorization. Normally, only account owners should be able to initiate password resets. The flaw in Instagram's system meant that attackers could make these requests on behalf of other accounts, causing legitimate users to receive unsolicited password reset emails. This vulnerability suggests Instagram's authentication or authorization checks weren't properly validating whether the person requesting the reset actually owned the account.
How many accounts were actually affected by this vulnerability?
Instagram has not officially disclosed the exact number of affected accounts. Malwarebytes claimed approximately 17.5 million Instagram accounts were compromised, but this number has not been independently verified or confirmed by Meta. The actual number could be higher or lower, and it's unclear whether all affected accounts had data stolen or just received unwanted password reset requests. Without a detailed incident report from Instagram, the true scope remains unknown.
Should I change my Instagram password immediately?
Yes, absolutely. Even though Instagram says the vulnerability has been fixed, changing your password is a necessary precaution. Use a strong, unique password (at least 16 characters with mixed character types) that you don't use anywhere else. Additionally, enable two-factor authentication immediately. These two steps dramatically reduce the risk of account takeover, even if attackers have your email address and phone number.
What data was exposed in this Instagram incident?
According to Malwarebytes, potentially exposed data includes usernames, physical addresses, phone numbers, and email addresses associated with Instagram accounts. However, Instagram has not confirmed whether all this data was actually stolen or if only the password reset vulnerability was exploited. The distinction is important because having your username isn't dangerous, but having your address, phone, and email combined is quite serious for identity theft and phishing attacks.
Is Instagram a breach or a vulnerability?
This depends on whether data was actually stolen. If attackers only exploited the password reset vulnerability to send unwanted emails but didn't access actual account data, it's a vulnerability exploitation but not technically a breach. If attackers did extract personal data (addresses, phone numbers, emails), then it is a breach. Instagram won't clearly state which scenario occurred, so you should assume the worst (that it's a breach) and take appropriate protective measures.
How can I check if my account was affected?
Instagram has not published a tool to check if your specific account was targeted. You can use general breach-checking services like Have I Been Pwned by entering your email address to see if it appears in previously documented breaches, but this won't tell you about recently exposed data. Your best approach is to assume your account was potentially affected (given the large alleged scope) and take protective steps: change your password, enable 2FA, and monitor your accounts for suspicious activity.
Should I delete my Instagram account?
Deleting your Instagram account is an extreme measure that probably isn't necessary. The vulnerability has been fixed, and enabling strong security measures (unique password, 2FA, monitoring) significantly reduces your risk. However, if you're deeply concerned about your data privacy, or if you've had past experiences with Meta's privacy practices and want to limit your presence, deleting the account is a legitimate option. Just remember that Meta retains some data even after deletion for a period of time.
What should I do if I notice suspicious activity on my Instagram account?
If you see unfamiliar logins, changed profile information, or other suspicious activity, change your password immediately, enable two-factor authentication if you haven't already, and review your login history. Go to Settings > Security > Login activity to see all devices that have accessed your account. Click on unfamiliar sessions and select "Log out of that session." If you believe your account has been compromised, you can also report it to Instagram's support team through the app.

The Bottom Line
Instagram experienced a significant security incident that revealed both a technical vulnerability and an organizational culture that prioritizes minimal disclosure over user protection.
What we know: An external party exploited a vulnerability in Instagram's password reset mechanism to request password resets for millions of accounts without authorization. Instagram fixed the vulnerability but provided almost no details about the incident.
What we don't know: Whether data was actually stolen, how many accounts were truly affected, how long the vulnerability existed, or what Meta is doing to prevent similar issues.
What you should do: Change your Instagram password, enable two-factor authentication, monitor your account and email for suspicious activity, and assume your data might be exposed (because statistically, it probably is).
What this reveals: Meta's security practices may be inadequate for a company with billions of users. The company prioritizes speed and growth over security and privacy, and without competition or strong regulatory pressure, this is unlikely to change.
The broader lesson is that in 2025, you can't trust large technology platforms to voluntarily protect your data. You have to protect yourself. Use strong, unique passwords. Enable 2FA everywhere. Monitor your accounts. Assume your information is exposed. And demand that the platforms you use provide transparent security practices and detailed incident reports.
Your data security is ultimately your responsibility.
Key Takeaways
- Instagram's vague response to a password reset vulnerability suggests either incomplete investigation or deliberate minimization of the incident severity
- 17.5 million accounts allegedly affected—but unclear whether data was stolen or just password reset requests were made
- Exposed data (addresses, phone numbers, emails combined) creates significant identity theft and phishing risk
- Enabling two-factor authentication, changing passwords, and monitoring account activity are critical protective steps
- Meta's pattern of minimal disclosures on security incidents reveals a corporate culture prioritizing PR over user protection
Related Articles
- Instagram Password Reset Email Bug: What Happened and What You Need to Know [2025]
- Illinois Health Department Data Breach: 700K+ Exposed [2026]
- App Store Age Verification: The New Digital Battleground [2025]
- Porn Taxes & Age Verification Laws: The Constitutional Battle [2025]
- Kimsuky QR Code Phishing: How North Korean Hackers Bypass MFA [2025]
- Cyera's $9B Valuation: How Data Security Became Tech's Hottest Market [2025]
![Instagram Password Reset Incident: What Really Happened [2025]](https://tryrunable.com/blog/instagram-password-reset-incident-what-really-happened-2025/image-1-1768170953963.jpg)



