Rainbow Six Siege Server Shutdown: The Marketplace Hack That Broke Everything
Last weekend, something genuinely unusual happened in the world of competitive gaming. Ubisoft, one of the biggest game publishers on the planet, had to completely shut down Rainbow Six Siege across all platforms. No warning. No maintenance window. Just a hard stop.
The reason? A sprawling, complicated security breach that somehow gave random players billions of in-game credits, weaponized skins worth real money, and fundamentally destabilized the game's entire economy in less than 24 hours.
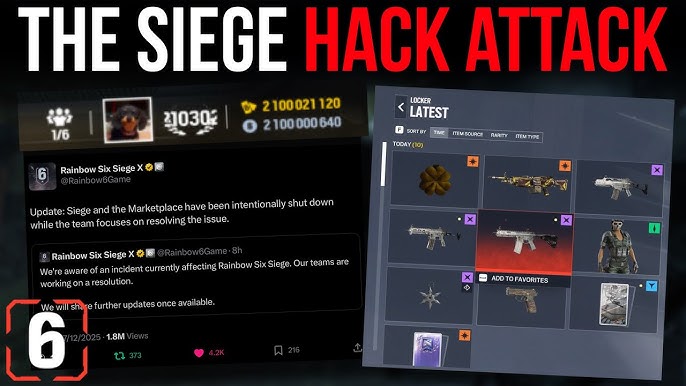
If you weren't paying attention, here's what went down: Players logged in Saturday morning expecting a normal day of tactical gameplay. Instead, some discovered they had accumulated billions of R6 credits in their accounts. Others found rare, exclusive skins sitting in their lockers that should have cost hundreds of dollars. Some accounts got mysteriously banned. Others got mysteriously unbanned. It was chaos.
Ubisoft had to make a hard choice: Either let the breach continue and completely destroy the game's economy and integrity, or hit the panic button and shut everything down. They chose the latter. By Saturday afternoon, the servers were offline across PC, PlayStation, and Xbox. By Sunday evening, after extensive rollbacks and quality control testing, they brought things back online.
But this wasn't just another gaming server outage. This was a wake-up call about how vulnerable even massive online gaming platforms can be, how quickly a security incident can spiral out of control, and what it actually takes to recover from something this severe.
Let's break down exactly what happened, why it matters, and what it tells us about online game security in 2025.
Understanding the Rainbow Six Siege Marketplace Breach
To understand how bad this breach was, you need to understand how Rainbow Six Siege's marketplace actually works. It's not some simple shop system. It's a complex ecosystem tied to real money transactions, battle pass progression, cosmetic unlocks, and seasonal content releases.
Players can earn in-game currency called R6 credits in limited quantities through gameplay. But most valuable cosmetics—particularly the rare, limited-edition weapon skins—require real money purchases. A single legendary skin can cost
That's where the vulnerability lived. Somewhere in the system that governs how these transactions work, how accounts are validated, and how the marketplace database communicates with player accounts, something broke catastrophically.
The breach didn't happen in a way that requires hardcore hacking expertise. It wasn't a zero-day exploit or some sophisticated social engineering attack. Instead, it appears to have been a relatively straightforward but devastating database or API vulnerability that allowed attackers to manipulate player accounts and inject credits directly.
Think of it like this: Imagine a bank where someone discovered that if you sent a certain request to their system, you could tell them you had a million dollars in your account. The bank's security didn't validate whether that was actually true. It just accepted the request and updated their records accordingly.
That's essentially what happened here. The marketplace system trusted account modification requests that it shouldn't have trusted, or it failed to properly validate the legitimacy of those requests before executing them.
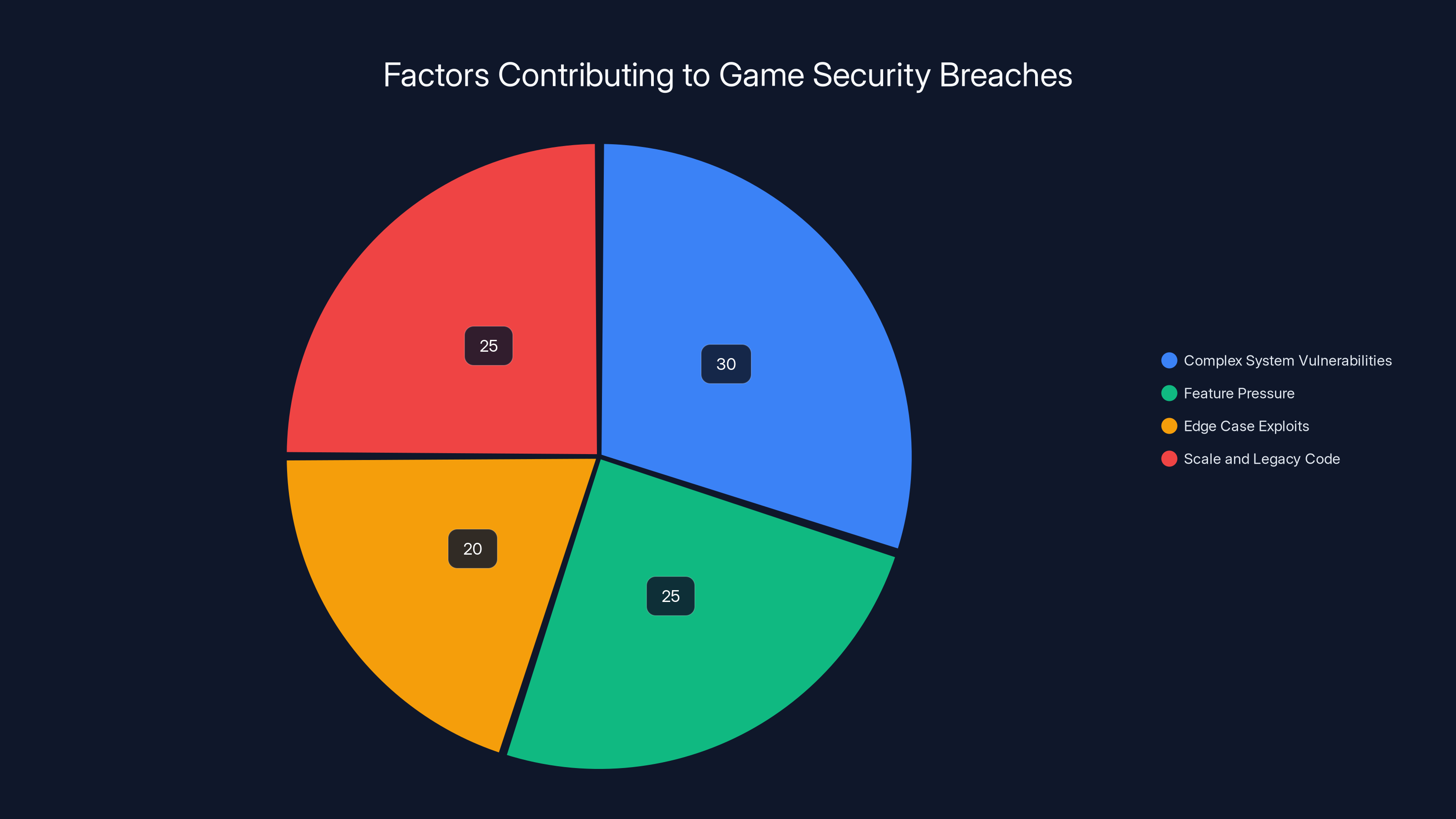
Complex system vulnerabilities and scale/legacy code are major contributors to security breaches in games, each accounting for about 30% and 25% respectively. Estimated data.
The Timeline: From Saturday Morning to Sunday Evening
Understanding exactly when this breach happened and how Ubisoft responded is crucial for understanding just how serious the situation was.
Saturday, 6:00 AM ET: The breach begins, though Ubisoft doesn't immediately know it's happening. Players start logging in and discovering billions of credits in their accounts. At this point, it's not clear to anyone—including Ubisoft—whether this is a display bug, a rollback gone wrong, or something worse.
Saturday, 9:00 AM ET: Reports flood Reddit, Twitter, and Ubisoft's support channels. Players are sharing screenshots of accounts with 50 billion credits. Others show screenshots of legendary skins they've never purchased. The company's social media team finally realizes something is genuinely wrong.
Saturday, 11:00 AM ET: Ubisoft posts on X (formerly Twitter) saying they're aware of "an incident currently affecting Rainbow Six Siege" and working on a resolution. This is the moment when players realize this isn't a simple bug. The company's use of the word "incident" signals something serious.
Saturday, 1:00 PM ET: Without warning, Ubisoft takes the servers offline. All regions go down simultaneously. PC, PlayStation, Xbox—everything goes dark. This is the nuclear option in game operations. Shutting down servers mid-day on a Saturday means acknowledging that the situation is so severe that keeping the game online poses a bigger risk than the downtime itself.
Saturday, 3:00 PM ET: Ubisoft clarifies on social media that players who spent their ill-gotten credits won't be permanently banned. This is a significant statement because it shows the company recognizes the breach was systematic and wide-reaching. Blaming individual players wouldn't be reasonable. They also announce that a complete rollback of all transactions starting from 6:00 AM ET will take place.
Sunday, 1:00 PM ET: Ubisoft provides an update saying they're performing extensive quality control tests to ensure the integrity of accounts and the effectiveness of the rollback. They explicitly state that "timing cannot be guaranteed" and don't provide an ETA for server restoration. This is significant because it tells the community that the company is prioritizing correctness over speed.
Sunday, 6:00 PM ET: After the testing window closes, Ubisoft confirms that servers are coming back online. The marketplace remains closed temporarily while they conduct additional validation.
The entire incident—from initial breach to full resolution—took approximately 36 hours. For an online game with millions of players, that's a long time. But it's also remarkable that they managed to identify the issue, shut down servers, perform a complete transaction rollback across millions of accounts, and bring everything back online that quickly.
What Actually Broke: The Technical Layer
While Ubisoft hasn't publicly released a detailed technical postmortem, we can make some educated assessments about what likely went wrong based on the nature of the breach and the specific symptoms players experienced.
The most telling symptom was that credits and items appeared in accounts instantly and across a wide range of users. This suggests the vulnerability wasn't in the account authentication system—if it were, we'd expect selective access for specific users. Instead, it appears to be in the transaction processing layer or the item distribution system.
One possibility is that the marketplace API had insufficient validation on requests. When a player buys an item, their client sends a request to Ubisoft's servers saying "Credit my account for this item." If the server-side validation of those requests was weak, attackers could craft requests that the server would accept as legitimate without actually charging the account or verifying the purchase was made.
Another possibility is that there was a race condition or concurrency issue in the database. Under heavy load—which Saturdays certainly experience in a game like Rainbow Six Siege—the system might fail to properly serialize transactions. This could allow multiple credits to be issued for a single purchase, or items to be distributed without the corresponding debit.
A third possibility, and perhaps the most likely given the indiscriminate nature of the breach, is that there was a direct database injection vulnerability. If the API wasn't properly sanitizing inputs, attackers could potentially execute arbitrary database commands to modify account balances directly.
The fact that Ubisoft rolled back transactions starting from 6:00 AM ET rather than attempting to selectively reverse only fraudulent transactions tells us something important: They couldn't reliably distinguish between legitimate and illegitimate transactions. The breach was so complete, the data so corrupted, that the only safe option was a full database rollback to a known-good state.

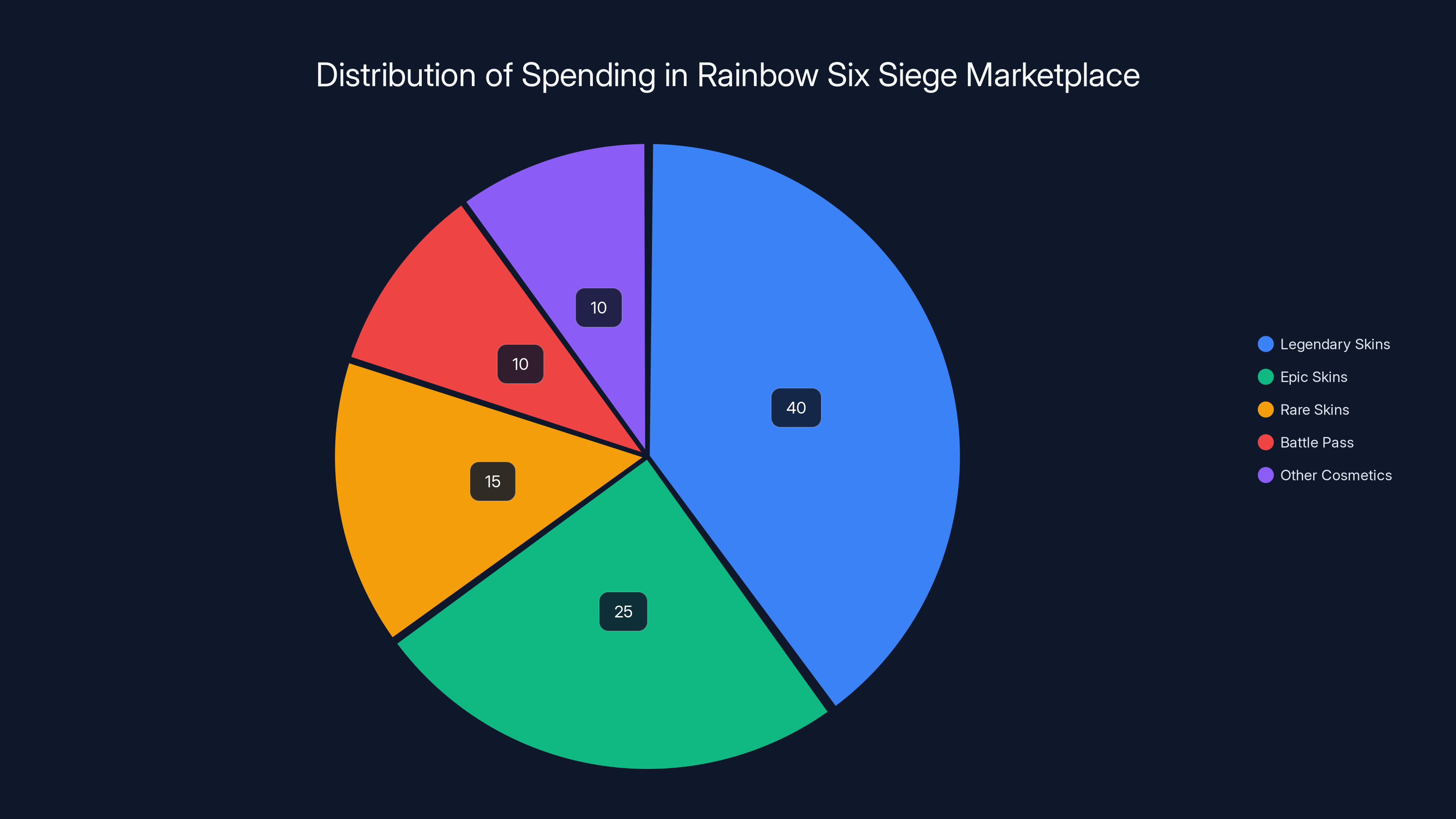
Estimated data shows that legendary skins account for the largest portion of spending in the Rainbow Six Siege marketplace, highlighting their high value and potential impact of the breach.
The Account Ban Confusion
One of the strangest aspects of the incident was the account ban situation. Some players found themselves suddenly banned. Others found themselves suddenly unbanned after previously being in violation of Ubisoft's terms of service.
This suggests that the breach didn't just affect the marketplace and account credit systems. It appears to have affected account status and enforcement records as well. Attackers may have directly modified the account database, not just to add credits, but to change account flags and restriction statuses.
This is actually more concerning than just credit inflation from a security perspective. If attackers could modify account status, they could potentially change player names, email addresses, recovery information, or other critical account data. Ubisoft's rollback addressed this, but it highlights how comprehensive the breach was.
Why a Complete Server Shutdown Was Necessary
Some players asked why Ubisoft didn't just lock the marketplace while investigating. Why take the entire game offline?
The answer is that a partial shutdown wouldn't actually solve the problem. As long as the servers were online, the vulnerability would remain exploitable. If attackers had access to the marketplace API once, they could continue exploiting it. As long as players could log in and see the corrupted account data, the evidence of the breach would remain in the system.
More importantly, from a database consistency perspective, if the vulnerability was in the transaction processing layer, having players continue to access their accounts could introduce additional corrupted transactions. Imagine if players, unaware of the breach, continued to make purchases or trades. Those transactions would layer additional complexity on top of the corrupted data, making the rollback process more complicated and riskier.
By taking the servers completely offline, Ubisoft was able to:
- Stop new exploitations from being executed
- Freeze the state of all databases at a known point in time
- Perform the rollback with confidence that no new transactions were being added during the process
- Run extensive validation and testing before bringing the game back online
It's the nuclear option, but sometimes the nuclear option is the right call.
The Economic Impact of the Breach
From a pure economic standpoint, this breach could have been catastrophic if not handled carefully. Rainbow Six Siege operates a marketplace where cosmetics are traded, bought, and sold. The game's economy depends on scarcity and trust.
If millions of rare skins had suddenly flooded the market, their value would have plummeted. Players who had legitimately purchased these items would have felt cheated. The trust in the marketplace would have eroded. Future cosmetic sales might have declined as players questioned whether their purchases would retain value.
Ubisoft's decision to perform a complete rollback rather than attempting to identify and remove only the duplicated items makes sense from this perspective. By rolling back to the pre-breach state, they preserved the integrity of the cosmetic economy. Players who had legitimately purchased items before the breach still owned them. The rare skins that flooded accounts were erased.
The trade-off is that players who spent the fraudulent credits on legitimate purchases during the window before the shutdown lost those purchases. This is why Ubisoft explicitly said players wouldn't be banned for spending the credits—the company recognized that expecting players to distinguish between legitimate and fraudulent currency was unreasonable.

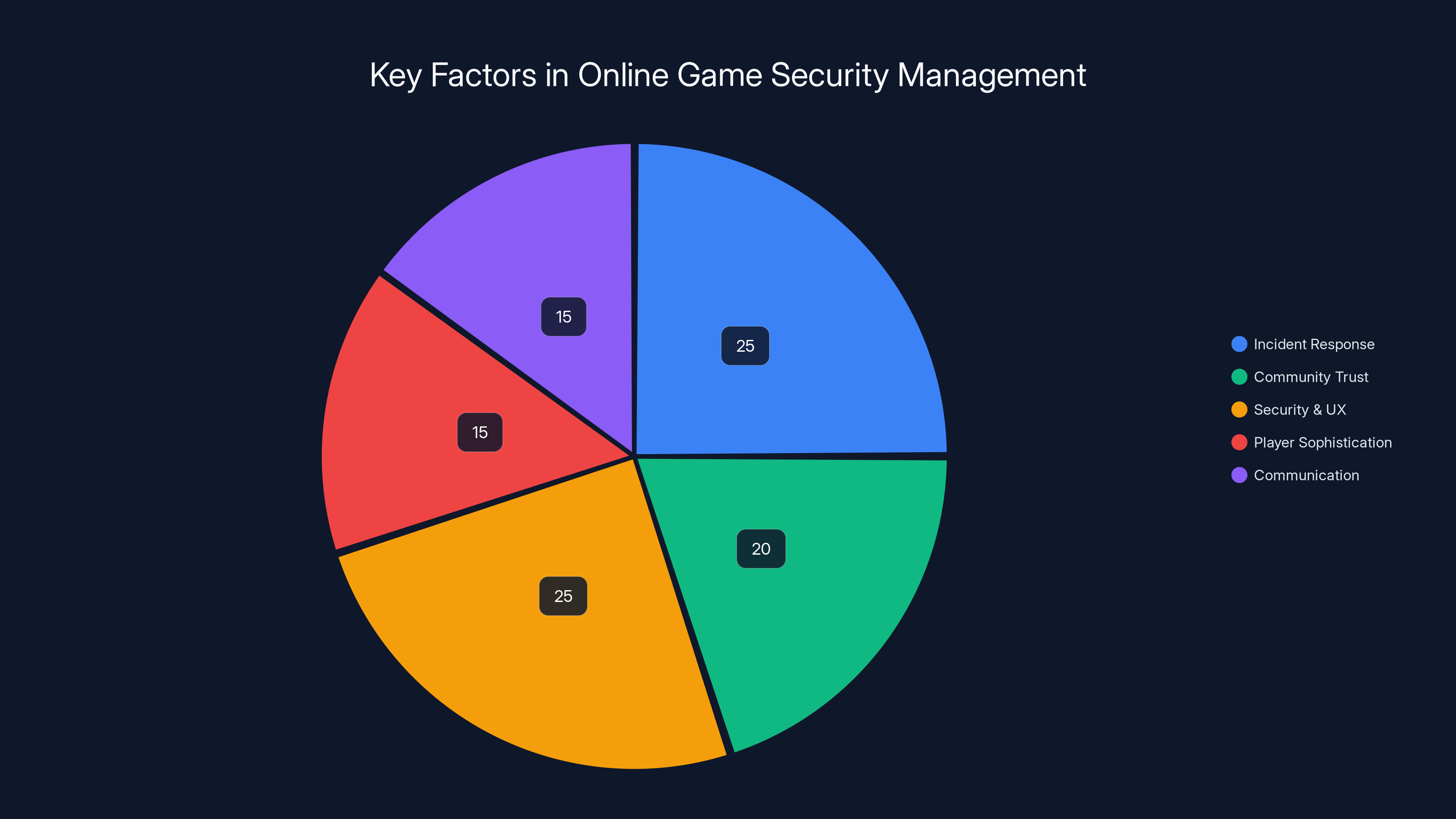
Estimated data: Incident response and security-UX balance are crucial in managing online game security, each accounting for 25% of the focus, highlighting their critical roles.
How This Compares to Other Gaming Security Incidents
Rainbow Six Siege isn't the first major online game to experience a significant security breach. But the scope and nature of this incident puts it in a particular category of gaming security failures.
World of Warcraft has experienced gold duplication exploits and item spawning bugs over the years, but these typically affected smaller player populations or were patched before widespread exploitation occurred.
Roblox has had security incidents involving account takeovers and virtual currency theft, but these usually target individual players rather than affecting the entire platform simultaneously.
CSGO and Dota 2, operated by Valve, have dealt with cosmetic marketplace issues, but Valve's distributed architecture and careful API design have generally prevented complete system compromises.
What made the Rainbow Six Siege incident unusual was that it affected such a large portion of the player base so quickly. Within hours, potentially tens of thousands of accounts had been affected. The breach achieved critical mass before Ubisoft even realized what was happening.
This suggests that the vulnerability wasn't something that required specific knowledge to exploit. It wasn't a zero-day that hackers had painstakingly discovered. It might have been something relatively simple that, once discovered, could be exploited by anyone with basic API knowledge.
The Response: Crisis Management in Real-Time
Ubisoft's actual response to the breach deserves analysis beyond just the technical fixes. The company had to manage several competing priorities:
- Stopping the bleeding (taking servers offline)
- Preserving data integrity (performing careful rollbacks)
- Maintaining player trust (clear communication about lack of bans)
- Understanding the scope (investigating how bad it actually was)
- Preventing recurrence (patching the vulnerability)
- Reopening safely (extensive testing before bringing servers back)
Ubisoft's public communication throughout the incident was notably measured. They didn't overpromise on timelines. They didn't blame players. They didn't minimize the severity. This is good crisis communication. When you're the source of the problem, managing expectations and being transparent about the recovery process is critical for maintaining player trust.
The decision to remain offline for 36 hours rather than rushing to reopen was particularly important. Getting the servers back online quickly would have been a PR win in the short term. But if the patch was incomplete or the validation inadequate, bringing servers back online prematurely could have led to a repeat of the original breach or the introduction of new issues.

What Changed About the System
While Ubisoft hasn't released specifics about the patch, based on the nature of the breach and standard security practices, we can infer what likely changed:
-
Strengthened API validation: The marketplace API now likely includes much stricter validation of all incoming requests, checking that they come from legitimate clients and match expected patterns.
-
Database transaction improvements: The system probably now uses more robust transaction handling to prevent race conditions or concurrent modification issues.
-
Input sanitization: All inputs to the marketplace system are likely now properly sanitized to prevent injection attacks.
-
Rate limiting: The patch probably includes rate limiting on marketplace API endpoints to prevent bulk exploitation.
-
Audit logging: The system likely now logs all marketplace transactions in a way that makes it easier to identify and investigate anomalies.
-
Staging environment testing: Ubisoft probably enhanced their staging and testing environments to catch similar issues before they reach production.
These are all fairly standard security improvements that should have been in place already. The fact that they apparently weren't is worth examining.

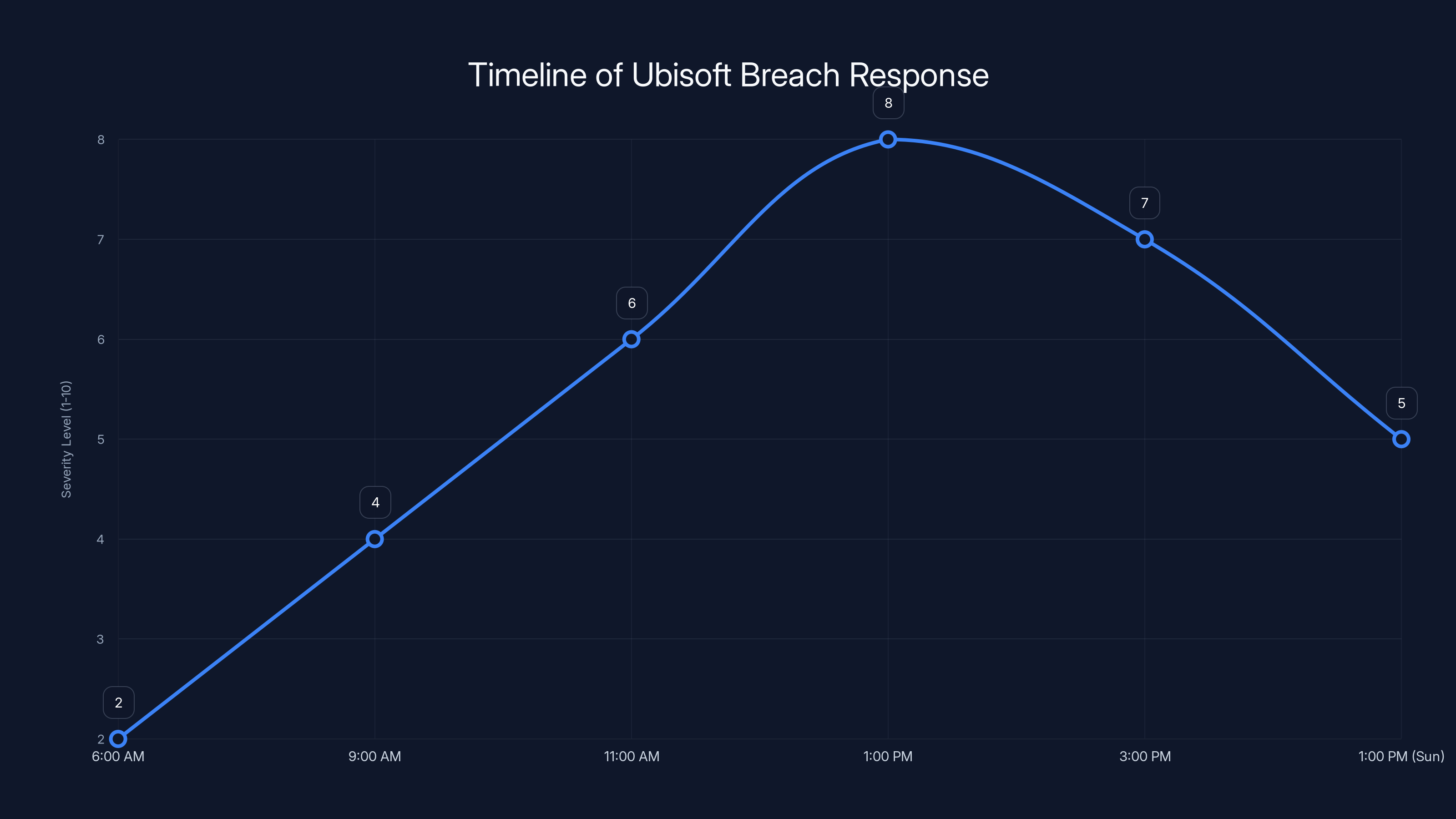
The timeline illustrates the escalation and response to the breach, peaking at 1:00 PM when servers were taken offline. Estimated data based on event descriptions.
Why Major Games Get Security Breaches
There's a temptation to treat security breaches as sudden, surprising events. But in most cases, they're the result of systemic issues that accumulated over time.
Large online games like Rainbow Six Siege are built incrementally. Features are added, systems are expanded, third-party libraries are integrated. Each addition is another potential surface area for security vulnerabilities. Over years of development, a complex system like a modern AAA game can accumulate hundreds or thousands of potential security issues.
Additionally, the pressure to ship features quickly sometimes conflicts with the pressure to make systems secure. Security often feels invisible to players. A marketplace that works and lets players buy cosmetics quickly is a good user experience. A marketplace with multiple layers of validation and security checks takes slightly longer to respond but prevents breaches. When you have deadlines and player expectations, the security often loses that trade-off.
Moreover, security vulnerabilities often hide in plain sight because they exploit edge cases or unexpected behaviors. A developer might test the happy path—the normal flow of how a feature is supposed to work—without exhaustively testing all the ways it could be attacked.
Ubisoft employs security experts and has robust security processes. But they're also operating at massive scale, with millions of concurrent players, decades of accumulated code, and constant pressure to ship new content. In that environment, security breaches become not a matter of if but when.
The Player Experience: A Saturday Ruined
For the millions of players affected, the practical impact was straightforward: They couldn't play on Saturday and Sunday. For a competitive esports title, that's significant. Saturday tournaments might have been affected. Seasonal progression ground to a halt. Playtime hours were lost.
But interestingly, the immediate community response wasn't entirely negative. Many players appreciated that Ubisoft took the situation seriously enough to shut everything down rather than letting the breach persist. Some of the players who benefited from the bug (receiving the fraudulent credits) were actually upset about the rollback but understood why it was necessary.
The question now is whether this incident has any lasting impact on the game. Will players trust the marketplace going forward? Will some stop spending real money on cosmetics? Will the community fracture over the loss of items purchased with fraudulent credits?
Historically, communities bounce back from these incidents. Players care more about the game itself than about specific cosmetics. Once the patch is confirmed to be working and confidence is restored, most players return to their normal habits.

Lessons for Online Game Security
The Rainbow Six Siege breach serves as a case study in how rapidly security issues can escalate in large online systems. Several lessons emerge:
First, security testing needs to be as thorough as gameplay testing. If Ubisoft had a security team attempting to break the marketplace API in the same way that QA testers attempt to break game mechanics, they might have caught this vulnerability before release.
Second, API validation is not optional. Every single input to every single API endpoint should be validated, sanitized, and checked for consistency. This should be automatic, not something developers have to remember to do.
Third, transaction processing systems need to handle concurrency correctly. Race conditions are subtle bugs that often escape testing because they occur under specific load patterns. But in a system with millions of concurrent users, those patterns occur all the time.
Fourth, breach response plans need to be practiced and rehearsed. Ubisoft's response, while generally good, took 36 hours. Part of that time was likely spent figuring out how to execute the rollback. Companies that regularly practice incident response can move faster.
Fifth, communication during a breach is critical. Ubisoft's decision to clearly state that players wouldn't be banned for spending fraudulent credits prevented panic and maintained trust.
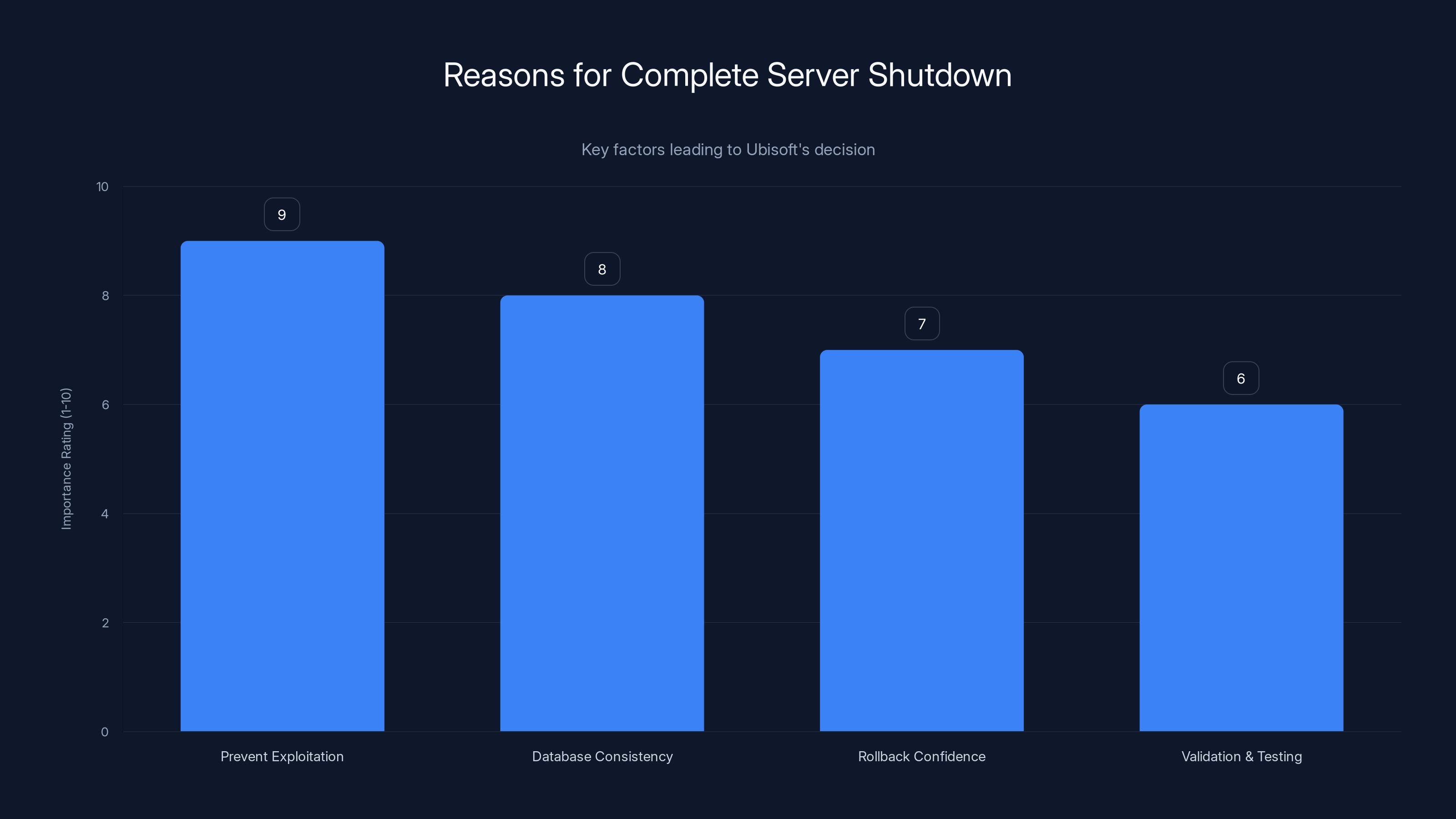
The complete server shutdown was crucial to prevent further exploitation, ensure database consistency, and allow a confident rollback and thorough validation. Estimated data based on narrative context.
The Broader Context: Server Security in 2025
It's worth considering why this breach happened now and what it tells us about online game security in 2025.
Game engines and frameworks have become more sophisticated, but they haven't necessarily become more secure. Backend systems have become more complex, but complexity is the enemy of security. API-driven architectures are standard now, but APIs are attack surfaces.
At the same time, the incentives for attacking game systems have increased. Online games manage billions of dollars worth of virtual goods. A marketplace with millions of transactions per day is a high-value target. Attackers have significant motivation to find vulnerabilities.
Ubisoft is certainly among the more well-resourced game publishers. If a company with their resources can have a breach of this magnitude, it raises questions about security across the entire industry. How many games are running systems with similar vulnerabilities but haven't been hit yet? How many are actively being exploited at smaller scales?
The honest answer is that online game security is probably worse than most players think. Developers and publishers invest in security because it's necessary, but they don't always invest as much as they should.
Technical Debt and Security
One way to understand the Rainbow Six Siege breach is through the lens of technical debt. Technical debt is the concept that shortcuts taken in software development have costs that accumulate over time.
When Rainbow Six Siege was initially developed, certain APIs and systems were probably built with less security validation than they should have had. Maybe the team was operating under tight deadlines. Maybe the vulnerability wasn't obvious until the game scaled to its current size. Maybe the system worked fine at launch but became vulnerable as features were added.
Over the years, patches and updates were applied, but the fundamental vulnerability might never have been addressed. Then, at some critical moment, someone found the vulnerability and exploited it.
The fix isn't just a simple patch. It's a repayment of the technical debt—rebuilding the system with proper validation and security controls.

What Happens to Compromised Accounts?
One question that remains somewhat unclear is what happens to accounts that were directly compromised during the breach window. If an attacker directly modified an account's data, changed its email address, or added recovery information, did the rollback restore the original account state?
Ubisoft would likely need to perform additional forensics on heavily affected accounts to understand what happened. Accounts with very unusual activity patterns might be flagged for manual review. In some cases, players might need to go through account recovery processes.
This is one of the hidden costs of a breach like this. The public story is the server shutdown and the rollback. But in the background, support teams are handling thousands of tickets from players whose accounts were compromised in more subtle ways.

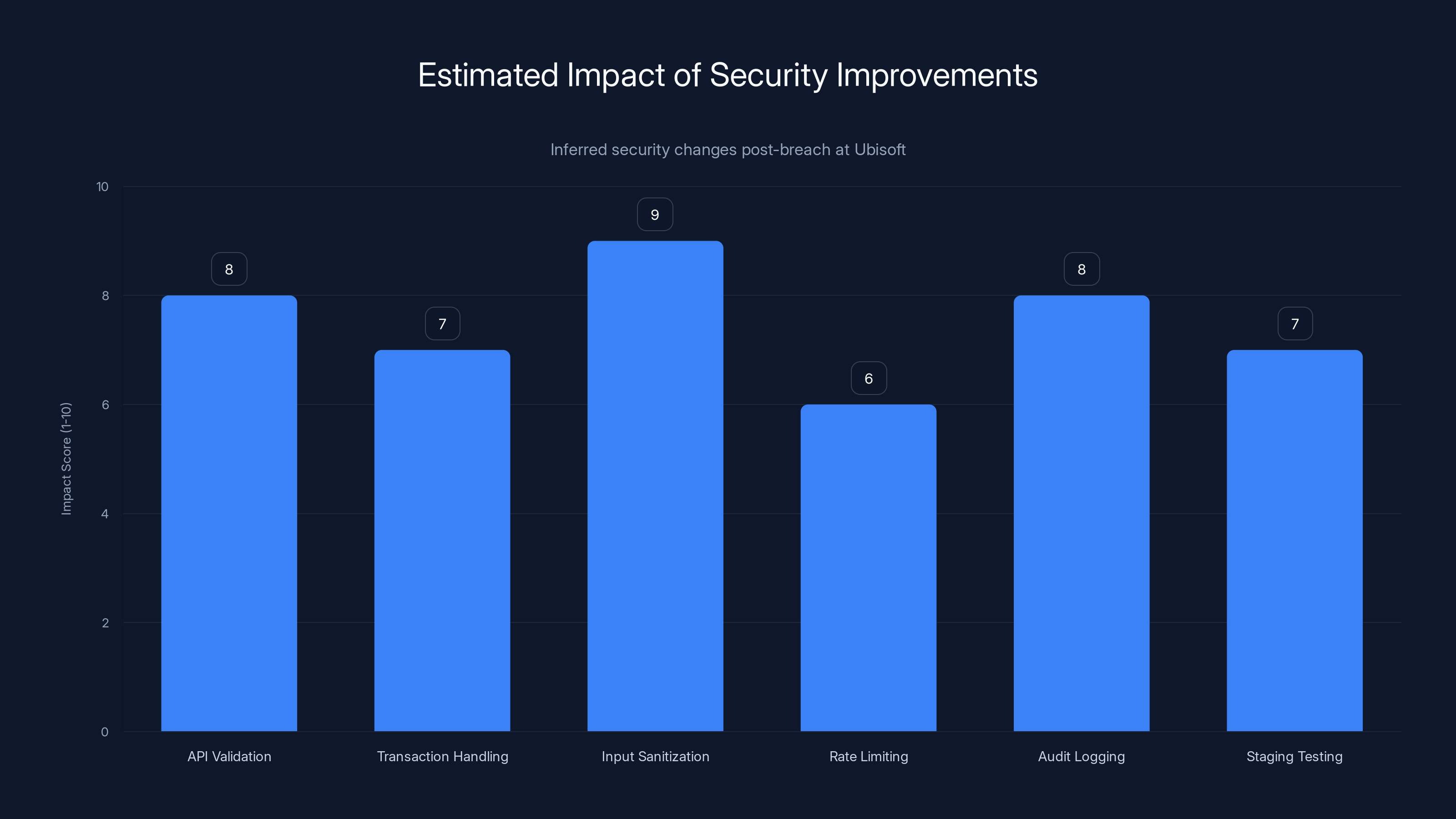
Estimated data suggests that input sanitization and API validation are likely the most impactful changes, improving security significantly.
The Marketplace Is Still Closed
One detail worth noting is that even after the servers came back online, the marketplace remained closed. This is a conservative approach that shows Ubisoft is still not fully confident in the fix.
Keeping the marketplace offline while running the rest of the game online is a good compromise position. It allows players to continue playing while the team does additional testing on the transaction system. It also prevents new marketplace-related exploits from being discovered immediately.
The question is how long Ubisoft will keep it closed. Even a week without the marketplace is significant for cosmetic sales. But reopening prematurely could be worse. The company is clearly prioritizing stability over revenue, which is probably the right call for long-term trust.

Learning From Incidents: The Postmortem Process
The best companies in the tech industry practice something called a blameless postmortem after incidents. The idea is to examine what happened, why it happened, and what can be changed to prevent similar incidents in the future, without assigning blame to individuals.
Ubisoft's internal postmortem on this incident is probably extensive. They're probably examining questions like:
- Why wasn't this vulnerability caught during code review?
- Why didn't security testing find it?
- What patterns of attack should have been expected and guarded against?
- How can the API validation framework be improved?
- What monitoring systems should have caught this faster?
- How can incident response be faster in the future?
- What changes to development practices can prevent similar issues?
If Ubisoft is mature about this process, they'll use these findings to improve not just Rainbow Six Siege but their entire development pipeline across all games.
The Community Response and Recovery
The gaming community's response to the breach has been mixed but generally accepting. Memes circulated about "the great credit shortage" and the community joked about the brief moment when everyone was rich. But seriously, most players recognized that Ubisoft made the right call and handled it reasonably well.
Recovery from an incident like this is as much about community perception as about technical fixes. If Ubisoft maintains transparent communication, follows through on promised improvements, and doesn't have another major breach in the near term, the community will likely move on.
But if there's another incident in the next few months, or if it emerges that Ubisoft knew about security issues and didn't address them, then this incident becomes part of a narrative about systemic problems.
Future Vulnerabilities: What's Next?
The patch that fixed this vulnerability addressed the immediate issue, but security is an ongoing process. There are probably hundreds of other potential vulnerabilities in the Rainbow Six Siege codebase right now. Most are likely minor. Some might be serious.
Future breaches are statistically likely. The next one might be in the marketplace again. It might be in the account system. It might be in voice chat or matchmaking. It might be completely unrelated to anything that would seem security-related to casual observation.
Ubisoft's goal now should be to:
- Build a security culture where every developer thinks about security as part of their job
- Implement automated security scanning into the development pipeline
- Regular penetration testing of critical systems by external security researchers
- Bug bounty programs that incentivize security researchers to report issues responsibly
- Security training for developers about common vulnerabilities and how to avoid them

Conclusion: The New Normal for Online Games
The Rainbow Six Siege breach and response demonstrate several important truths about online gaming in 2025.
First, security incidents are inevitable. They're not rare events caused by negligence. They're expected consequences of operating complex systems at massive scale. The only variable is whether companies handle them well.
Second, the ability to rapidly respond to incidents—to shut down systems, perform rollbacks, and bring systems back safely—is increasingly important. Speed matters, but correctness matters more.
Third, community trust is fragile and built slowly but broken quickly. How Ubisoft communicated during this incident probably matters more than the incident itself in determining long-term impact.
Fourth, the intersection of security and user experience is becoming increasingly critical. Players need to be able to trust that their accounts and purchases are safe while also having a smooth, responsive gameplay experience.
Final, players are increasingly sophisticated about understanding that online services will have problems. Most don't blame companies for breaches, but they do judge companies based on how they respond. Ubisoft's response, while not perfect, demonstrated competence and respect for the player base.
Rainbow Six Siege will recover from this incident. The servers are back up. The marketplace will reopen. Players will resume their normal activities. But the incident serves as a useful reminder that even massive, well-resourced game studios operate systems with significant security challenges, and that the next time you're benefiting from a bug or finding something unusual in your account, the best thing that could happen is that someone notices and takes it seriously enough to shut everything down and fix it properly.

FAQ
What caused the Rainbow Six Siege marketplace breach?
The breach stemmed from a vulnerability in the marketplace API or transaction processing system that failed to properly validate requests before executing them. This allowed attackers to inject credits, duplicate items, and modify account statuses without proper authorization. While exact technical details haven't been publicly released, the indiscriminate nature of the breach across thousands of accounts suggests it was a systemic validation or database injection vulnerability rather than a targeted exploit.
Why did Ubisoft shut down all servers instead of just closing the marketplace?
Ubisoft needed to completely shut down servers to stop the breach from continuing and to prevent new corrupted transactions from being added during the rollback process. Keeping servers online would have left the vulnerability exploitable and made the rollback process significantly more complicated. The full shutdown ensured data integrity and allowed the company to roll back to a known-good state without interference. A partial shutdown of just the marketplace wouldn't have addressed the underlying vulnerability or prevented additional exploits.
What happens to items purchased with the fraudulent credits?
Ubisoft explicitly stated that players wouldn't be banned for spending the fraudulent credits. However, the complete transaction rollback erased all purchases made with those credits during the breach window. Players lost items they acquired with the duplicate currency, but they weren't penalized for spending it. This was necessary to preserve the integrity of the cosmetic marketplace and prevent rare, valuable items from being permanently duplicated.
How long did the full recovery process take?
The entire incident, from initial breach to server restoration, took approximately 36 hours. Saturday morning saw the breach occur and discovery happen by mid-morning. Servers went offline by early afternoon. Sunday afternoon, after extensive testing and validation, servers came back online. The marketplace remained temporarily closed for additional testing. This timeline reflects both the severity of the breach and Ubisoft's commitment to careful recovery over rapid reopening.
Could this breach happen again?
The specific vulnerability that caused this breach has been patched. However, online systems as complex as Rainbow Six Siege's always have potential security issues, and breaches are statistically likely to occur again at some point. The key is whether future incidents are caught early and handled as well as this one was. Ubisoft's response, including the complete rollback and extensive testing before reopening, demonstrates a serious approach to security that should help prevent similar issues.
Why couldn't Ubisoft just selectively remove the fraudulent items instead of rolling back everything?
Ubisoft couldn't distinguish between legitimate and fraudulent transactions reliably. Some players made legitimate purchases, then spent the fraudulent credits on additional items. Some players had earned credits legitimately over time mixed with fraudulent credits. Untangling which specific items were legitimately purchased versus which were acquired with duplicate currency would have been enormously complex and risked penalizing innocent players. A complete rollback to a known-good state before the breach was the only way to ensure data integrity.
What security improvements likely resulted from this incident?
Based on the nature of the breach, improvements probably included stronger API validation on all marketplace endpoints, improved database transaction handling to prevent race conditions, enhanced input sanitization to prevent injection attacks, rate limiting on API calls, more comprehensive audit logging, and likely a complete security audit of related systems. Ubisoft probably also implemented automated security testing into their development pipeline and may have enhanced their incident response procedures.
How does this breach compare to other major gaming security incidents?
The Rainbow Six Siege breach is notable for its scope and speed. Unlike some gaming security incidents that affect individual players or specific regions, this breach affected a substantial portion of the global player base within hours. The fact that the vulnerability could be exploited by relatively straightforward means (not requiring sophisticated hacking) makes it particularly concerning and worth comparing to vulnerabilities in other major online games like World of Warcraft or Dota 2, though Rainbow Six Siege's incident recovery was remarkably fast.
Will players stop trusting the Rainbow Six Siege marketplace?
Short-term trust impacts are likely minimal. Ubisoft's clear communication and decisive action, combined with the company's decision not to ban players for spending fraudulent credits, probably maintained most players' trust. The real test will be if future breaches occur in the coming months. If the patched system remains secure and the marketplace continues functioning normally, player trust should normalize relatively quickly. Gaming communities are generally forgiving of security incidents if they're handled transparently and effectively.
What can other game developers learn from this incident?
Key lessons include the importance of thorough API security validation, robust transaction processing with proper concurrency handling, the value of taking security incidents seriously even when it means downtime, transparent communication with players during crises, and the need for comprehensive security testing as part of standard development processes. Additionally, developers should recognize that complex online systems will inevitably have vulnerabilities, and robust incident response capabilities are as important as trying to prevent every possible breach.

Key Takeaways
- Ubisoft shut down Rainbow Six Siege servers across all platforms after a widespread marketplace breach flooded accounts with billions in fraudulent credits and rare cosmetics within hours
- The vulnerability appears to have been in the marketplace API validation layer, allowing attackers to manipulate account balances without proper authorization checks
- The company performed a complete transaction rollback rather than attempting to selectively remove fraudulent items because data corruption was too extensive to distinguish legitimate from illegitimate purchases
- Ubisoft's 36-hour response time demonstrates the complexity of recovering from breaches affecting millions of concurrent users across multiple platforms and regions
- The incident highlights how even well-resourced publishers operate systems with serious security vulnerabilities and how rapid, decisive response matters more to player trust than avoiding breaches entirely
Related Articles
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- Rainbow Six Siege Server Crisis: What Happened & How It Impacts Gaming [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
- Stardew Valley Nintendo Switch 2 Free Upgrade [2025]
- Aflac Data Breach: 22.6 Million Exposed [2025]
![Rainbow Six Siege Server Shutdown: Marketplace Hack Explained [2025]](https://tryrunable.com/blog/rainbow-six-siege-server-shutdown-marketplace-hack-explained/image-1-1767022563816.png)




