Microsoft Cloud PC Access Failures: What's Breaking & How to Fix [2025]
It's mid-January, and your team's workday just hit a wall. Someone tries to log into their Cloud PC, and nothing happens. No error message. No clear reason. Just nothing. Then another person reports the same issue. Then another.
If this sounds familiar, you're not alone. Thousands of organizations discovered on January 13, 2025 that a recent Windows security update was quietly breaking their Cloud PC connections. Microsoft's latest patch, KB5074109 (OS Build 26100.7623), introduced a credential prompt failure that left users stuck outside their virtual desktops.
But here's what's frustrating: the issue didn't come with warning labels or clear communication. Users just started experiencing sign-in failures and intermittent access problems around 7 PM UTC, and it took a while for anyone to understand why. Some people didn't know if it was a network issue, a security problem, or something wrong with their device.
This article walks you through exactly what happened, who's impacted, why Microsoft's update caused this mess, and the practical workarounds you can use right now while waiting for the permanent fix. We'll also break down what this means for your organization's cloud infrastructure strategy moving forward.
TL; DR
- The Problem: Windows security update KB5074109 broke Cloud PC credential authentication, affecting Windows 11 and Windows 10 users
- The Scope: Impact includes Windows 11 (25H2, 24H2, 23H2), Windows 10 (22H2, 21H2), and Windows 10 Enterprise LTSC versions (2019, 2016)
- The Workaround: Use Windows App Web Client or traditional Remote Desktop client instead of the Windows App desktop application
- The Timeline: Microsoft promised an out-of-band update "in the coming days" but no exact date was provided
- The Lesson: Enterprise-grade updates need better testing and communication before widespread rollout
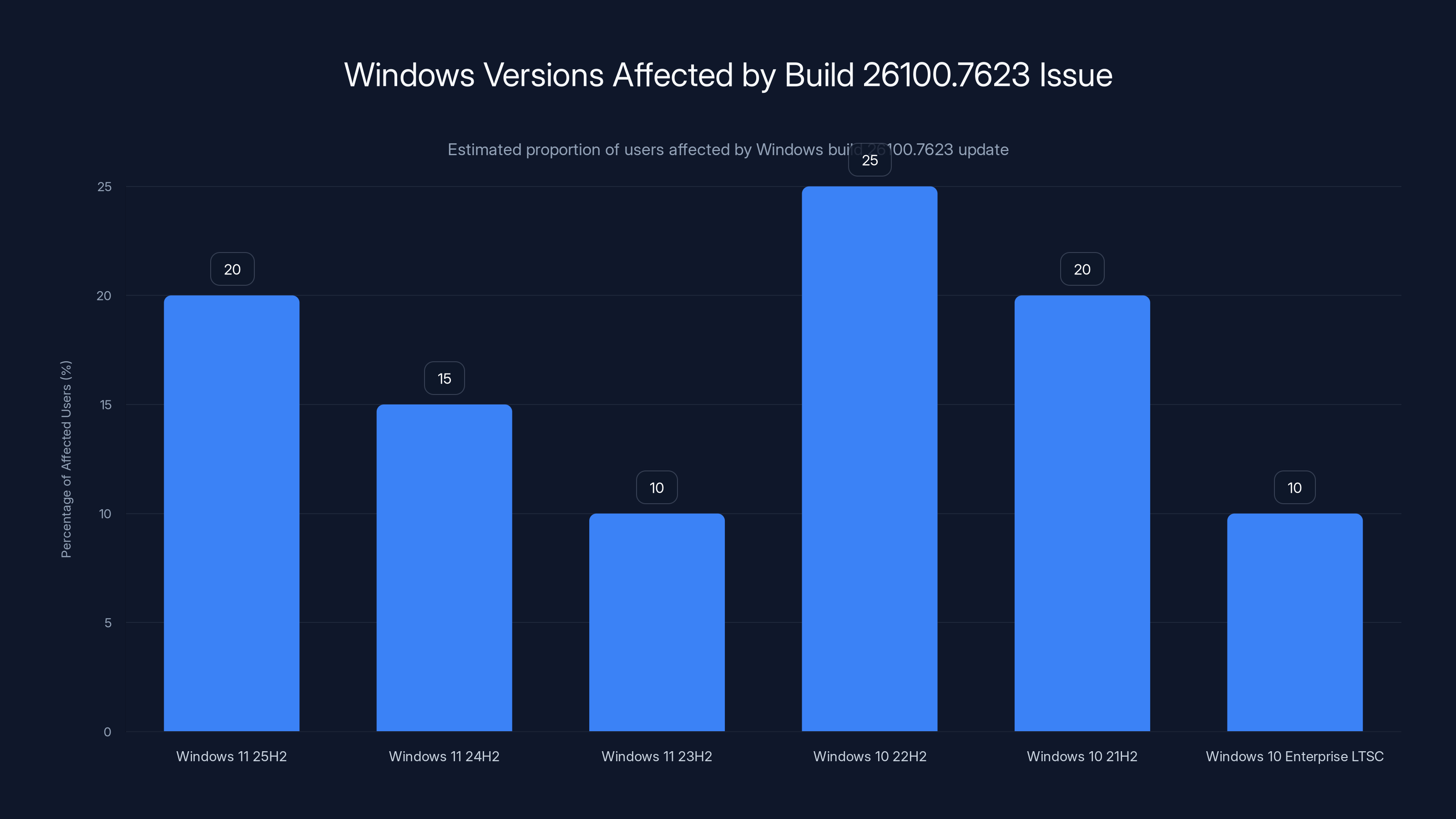
Estimated data shows that Windows 10 22H2 and Windows 11 25H2 are most affected by the credential prompt failure. Estimated data.
What Actually Happened on January 13
The timeline matters here because it shows you how fast this cascaded. At approximately 7 PM UTC on January 13, 2025, users across multiple continents reported that their Cloud PC connections were failing. The error wasn't a network timeout. It wasn't an authentication service down. It was something stranger: the credential prompt itself was malfunctioning.
When users tried to sign into their Cloud PC through the Windows App, the username and password prompt would appear, but submitting credentials went nowhere. Some users reported the dialog would freeze. Others said it would close without any response. A third group experienced intermittent access, where sometimes it would work and sometimes it wouldn't.
The weirdness accelerated during peak business hours in Asia, then Europe, then North America. By the time most organizations' IT teams arrived at work, their support queues were overflowing with people who couldn't access their virtual desktops. And nobody knew why.
Microsoft eventually traced the problem back to the January 2025 Windows security update (KB5074109). But initial communications were vague, and many organizations were left guessing whether this was a temporary glitch or a systemic problem that would persist.
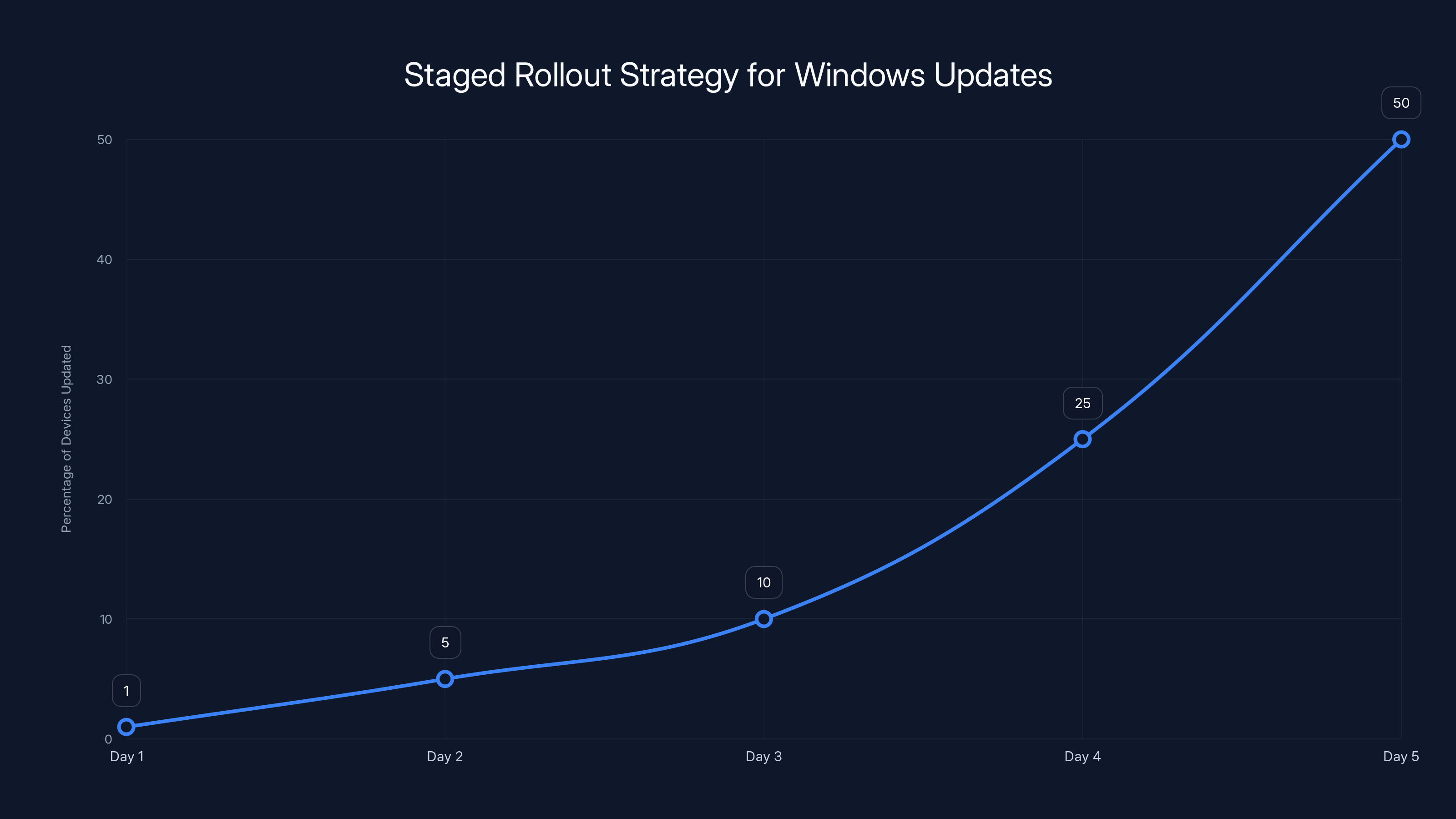
A staged rollout strategy helps mitigate risks by gradually increasing the percentage of devices updated, allowing for issue detection and resolution before full deployment. Estimated data.
Understanding OS Build 26100.7623 and Why It Broke Everything
Windows updates are supposed to make your system safer, not break critical functionality. So what went wrong with build 26100.7623?
The update was designed to patch several legitimate security vulnerabilities. Microsoft regularly rolls out security updates on the second Tuesday of every month, and this January release was no exception. The problem wasn't the intent. It was the execution.
Specifically, the credential prompt failure occurred because the update modified how the Windows App handles Remote Desktop authentication tokens. The Windows App (formerly known as Windows App or RDP client) is Microsoft's modern replacement for the older Remote Desktop Connection utility. It's the preferred tool for accessing Cloud PCs and Azure Virtual Desktop environments.
When the update deployed, it inadvertently changed a core authentication component that the Windows App depends on. The client would initiate the connection, the credential dialog would appear, but when you submitted your username and password, the authentication chain would break. The credentials weren't being passed correctly to the Cloud PC gateway servers.
What makes this particularly annoying is that Microsoft's testing labs apparently didn't catch this. The update passed through the Insider channel (where technically-inclined users test early builds) without triggering widespread complaints about Cloud PC access. This suggests the issue either affected a specific subset of configurations that aren't heavily represented in the Insider community, or the problem was masked by how testing is conducted.
The affected builds include Windows 11 versions 25H2, 24H2, and 23H2, as well as Windows 10 versions 22H2 and 21H2. Windows 10 Enterprise LTSC versions (2019 and 2016) are also impacted. That's a substantial portion of the Windows installed base, particularly in enterprise environments where companies often standardize on one or two versions.

Who's Actually Affected: The Real Scope
Not every Windows user experienced this issue. The impact was specifically limited to people using the Windows App to connect to Cloud PCs or Azure Virtual Desktop environments. If you use a physical computer at your desk with no Cloud PC setup, this update didn't hurt you.
But if you're part of the growing population of remote and hybrid workers relying on Cloud PCs as your primary computing environment, this broke your day.
The affected groups include:
Enterprise Knowledge Workers: Anyone whose organization deployed Cloud PC as their primary desktop offering. This includes finance teams, marketing departments, customer service centers, and any role where the actual computing work happens in a remote desktop rather than on a local machine.
Azure Virtual Desktop Users: Organizations using AVD (the older Azure-based version of virtual desktops) also experienced these failures. AVD is commonly used for VDI deployments where companies centralize desktop management.
Hybrid Workforce Teams: Companies with mixed on-site and remote workers often use Cloud PC for the remote crowd. When the update hit, remote workers suddenly couldn't connect while on-site workers with traditional desktops continued normally.
BYOD Environments: Organizations that let employees use personal Windows devices to access Cloud PC were particularly vulnerable since they can't control when the update deploys to each device.
The geographic distribution shows this wasn't a server-side outage. It was a client-side problem that hit simultaneously across regions. This means troubleshooting looked different than a traditional Azure service outage. IT teams couldn't disable a problematic Azure configuration or failover to a backup service. They had to work around the broken client application.
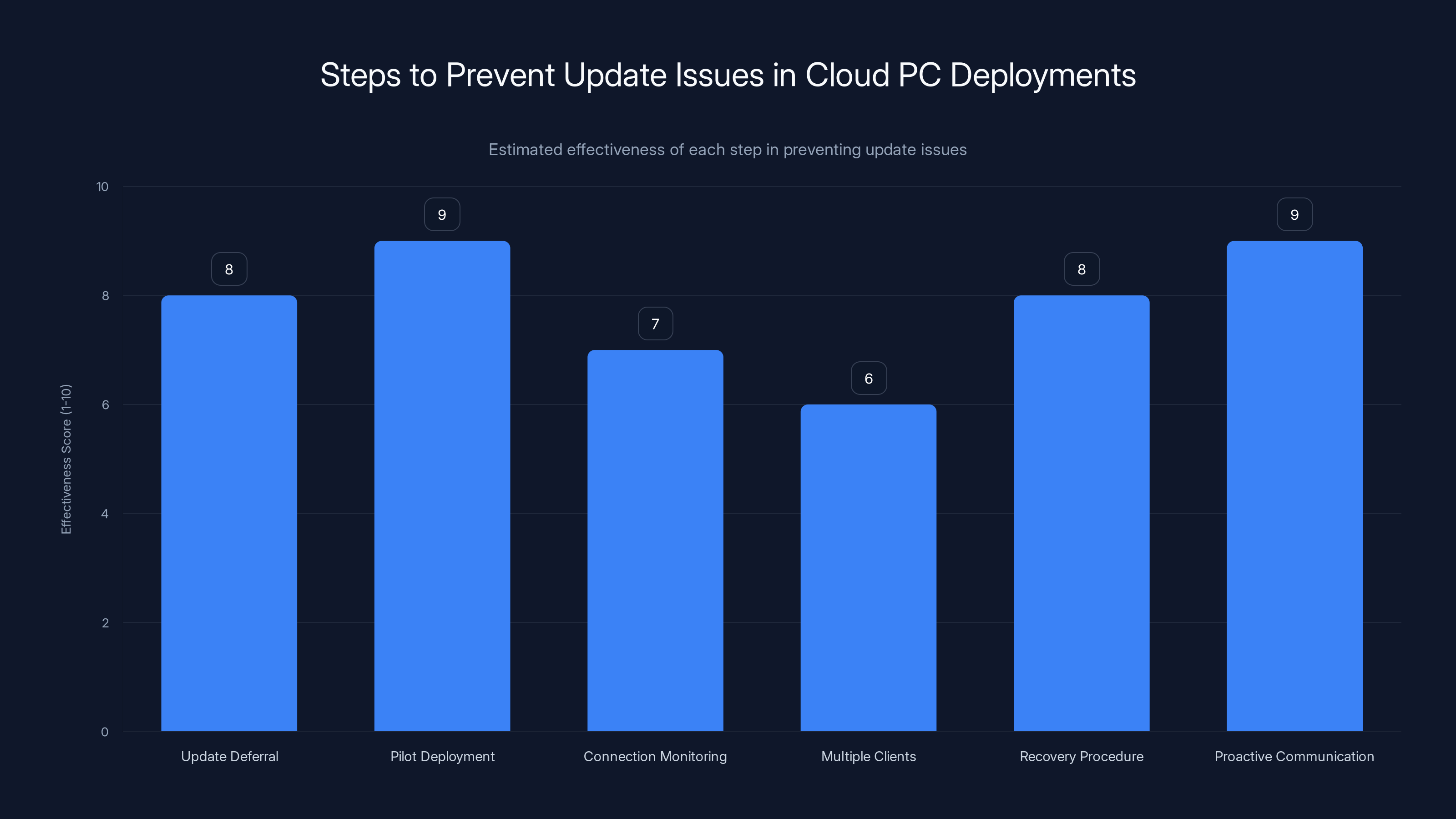
Proactive communication and pilot deployments are the most effective steps to prevent update issues, scoring 9 out of 10. Estimated data based on typical organizational practices.
Why the Windows App Failed Specifically
You might wonder why this update broke the Windows App but not the older Remote Desktop Connection client. The answer reveals something important about modern software architecture.
The Windows App is a Universal Windows Platform (UWP) application. It's built using modern Windows APIs and integrates with newer Windows components. The traditional Remote Desktop Connection (mstsc.exe) is a legacy Win 32 application that's been around for decades.
When Microsoft updated the Windows security components in KB5074109, they modified how authentication credentials flow through the system. The Windows App, being built on newer APIs, was affected by these changes. The traditional RDP client, relying on older APIs that weren't modified, continued working normally.
This is actually a known architectural challenge in software. New systems built on modern frameworks sometimes break when underlying system components change. The developers building the Windows App had to follow Microsoft's authentication APIs, but if those APIs change, the app breaks.
The irony is that Microsoft was trying to improve security by updating these components. But they didn't thoroughly test the impact on the Windows App before releasing the update. This is a failure in testing strategy, not the security update itself.
The Immediate Workarounds That Actually Work
Here's where it gets practical. Microsoft's official guidance recommended two immediate workarounds while they work on a real fix.
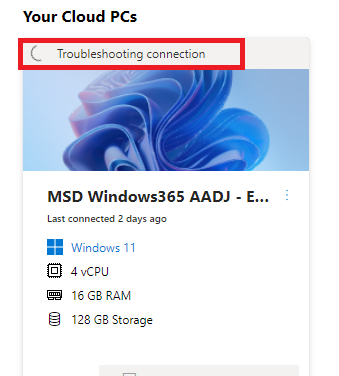
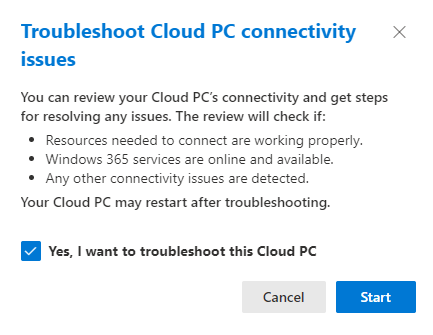
Workaround #1: Use the Windows App Web Client
Instead of the desktop Windows App, you can access Cloud PC through a web browser. Go to windows.cloud.microsoft.com and log in there. This web client doesn't rely on the updated authentication components because it communicates directly with Microsoft's cloud services rather than going through your local Windows system.
This works but has limitations. Web clients typically have slightly higher latency than desktop apps, and some advanced features (like clipboard redirection or local printer mapping) might not work as smoothly. But for basic access, it gets the job done.
Implementation is simple: bookmark windows.cloud.microsoft.com and distribute that link to your affected users. They can log in and access their Cloud PCs immediately. Most users won't notice performance issues for normal work like email, web browsing, or document editing.
Workaround #2: Use the Traditional Remote Desktop Client
The older Remote Desktop Connection application (mstsc.exe) continues to work normally. This is a Win 32 application that doesn't depend on the components modified by the security update.
To connect:
- Open Remote Desktop Connection (search for "mstsc" in Windows Start menu)
- Enter your Cloud PC hostname or IP address
- Enter your credentials
- Connect normally
This provides better performance than the web client because it's a native application. However, it requires more manual setup than the Windows App, particularly if you have multiple Cloud PCs.
For organizations with Azure Virtual Desktop, there's also the older RDP client available from the Microsoft Store. It's not as polished as the Windows App, but it functions normally with the updated Windows build.
Workaround #3: Defer the Update (Temporary, Not Recommended)
Some organizations tried blocking the update entirely or rolling it back. This isn't recommended because the update contains important security patches. But if your organization encountered this issue after the update deployed, you might have bought time by deferring it for a few days.
To defer updates on individual devices:
- Go to Settings > System > Windows Update
- Click "Pause updates for 7 days"
- Wait for Microsoft's out-of-band fix before allowing the update to resume
The maximum pause is 35 days (five 7-day intervals), but you shouldn't use the full duration. Microsoft said the fix would arrive in days, not weeks. Rolling back updates is also possible through Settings > System > Recovery, but this removes all security patches from the update.
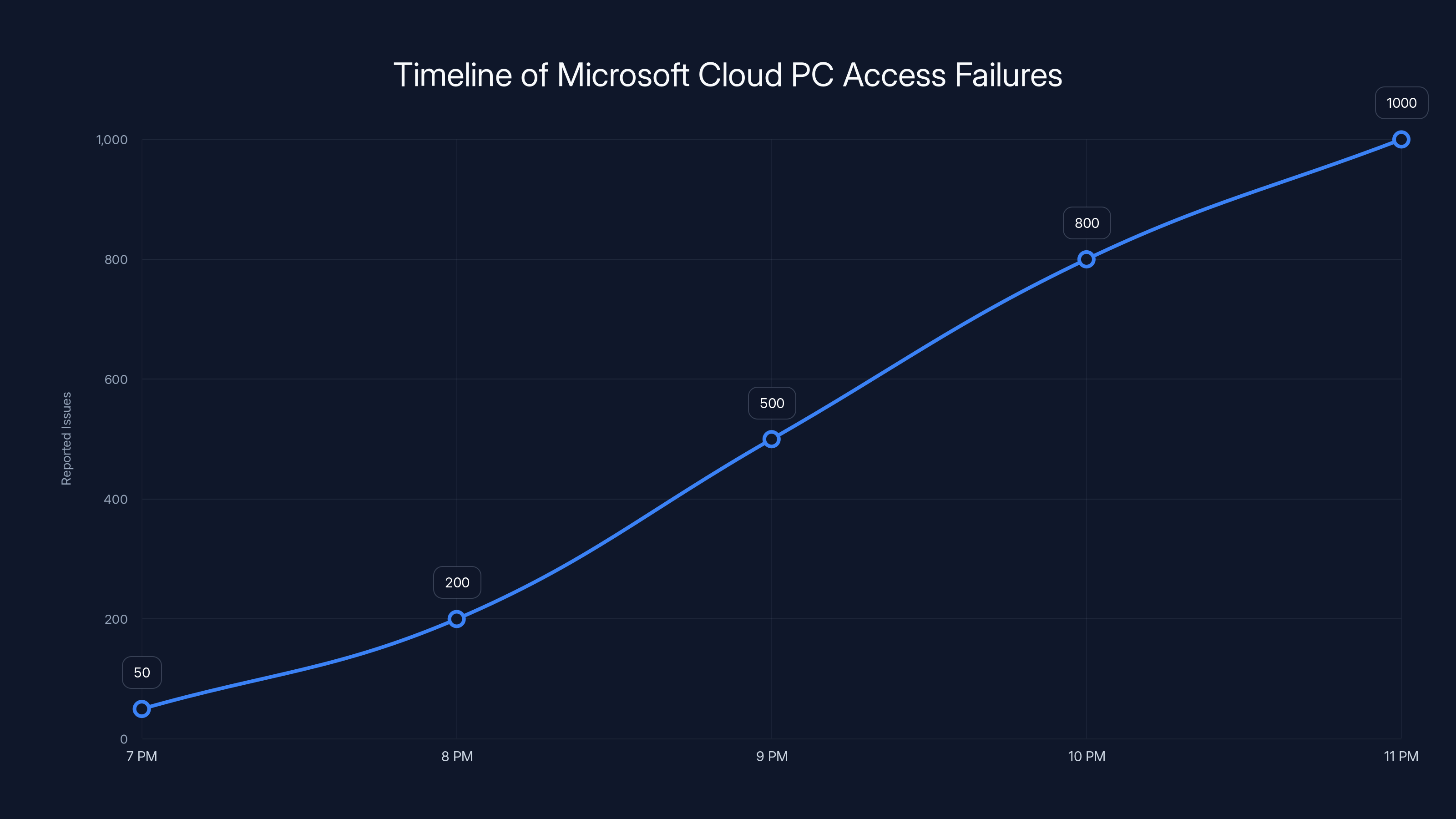
Estimated data shows a sharp increase in reported Cloud PC access failures starting at 7 PM UTC, peaking around 11 PM. Estimated data.
Microsoft's Response and the Out-of-Band Fix Timeline
Microsoft's handling of this issue provides lessons in how enterprise updates should (and shouldn't) be communicated.
The company acknowledged the issue publicly through its Azure status page and Azure Virtual Desktop announcements. They confirmed the credential prompt failures and identified KB5074109 as the culprit. Their status page read: "After installing the January 2026 Windows security update (KB5074109), credential prompt failures occurred during Remote Desktop connections using the Windows App on Windows client devices, impacting Azure Virtual Desktop and Windows 365."
Note the careful language. "Credential prompt failures" and "impacting Azure Virtual Desktop and Windows 365." They were precise about what broke and what was affected.
Microsoft committed to releasing an out-of-band (OOB) update "in the coming days." Out-of-band means they're not waiting for the regular monthly update cycle. They're pushing an emergency patch outside the normal schedule.
What we don't know: the exact timeline. "Coming days" is vague. It could mean 2 days or 10 days. For organizations with thousands of affected users, that vagueness creates uncertainty. Should they switch everyone to the web client? Should they hold off on deferring updates? The timeline ambiguity made planning difficult.
Some organizations criticized Microsoft for not providing more specific information about when the fix would arrive. The tech industry has experienced enough critical outages that users expect more detailed timelines for emergency patches. But Microsoft's cautious approach (not committing to a specific date they might miss) is also understandable from their perspective.
How This Connects to Broader Azure Virtual Desktop Issues
This incident highlights ongoing challenges with Azure Virtual Desktop that organizations should understand.
AVD is Microsoft's centralized remote desktop service. It powers Cloud PC, but it's also used as a standalone solution for organizations managing their own virtual desktop infrastructure. When client-side issues hit AVD, they affect enterprise deployments at scale.
Microsoft has been consolidating AVD and Cloud PC technologies. Cloud PC is essentially AVD with Microsoft handling all the infrastructure management. But both solutions depend on clients (the Windows App, Remote Desktop client, etc.) working correctly.
The underlying issue here is that client applications are often the weakest link in virtual desktop infrastructure. The servers can be perfectly stable, but if the client breaks, users can't connect. This is why many organizations maintain multiple client options. If one breaks, they have fallback alternatives.
Some organizations run both the Windows App and the traditional Remote Desktop client on user devices specifically to handle situations like this. It seems redundant until you encounter a situation where one breaks and the other becomes your lifeline.
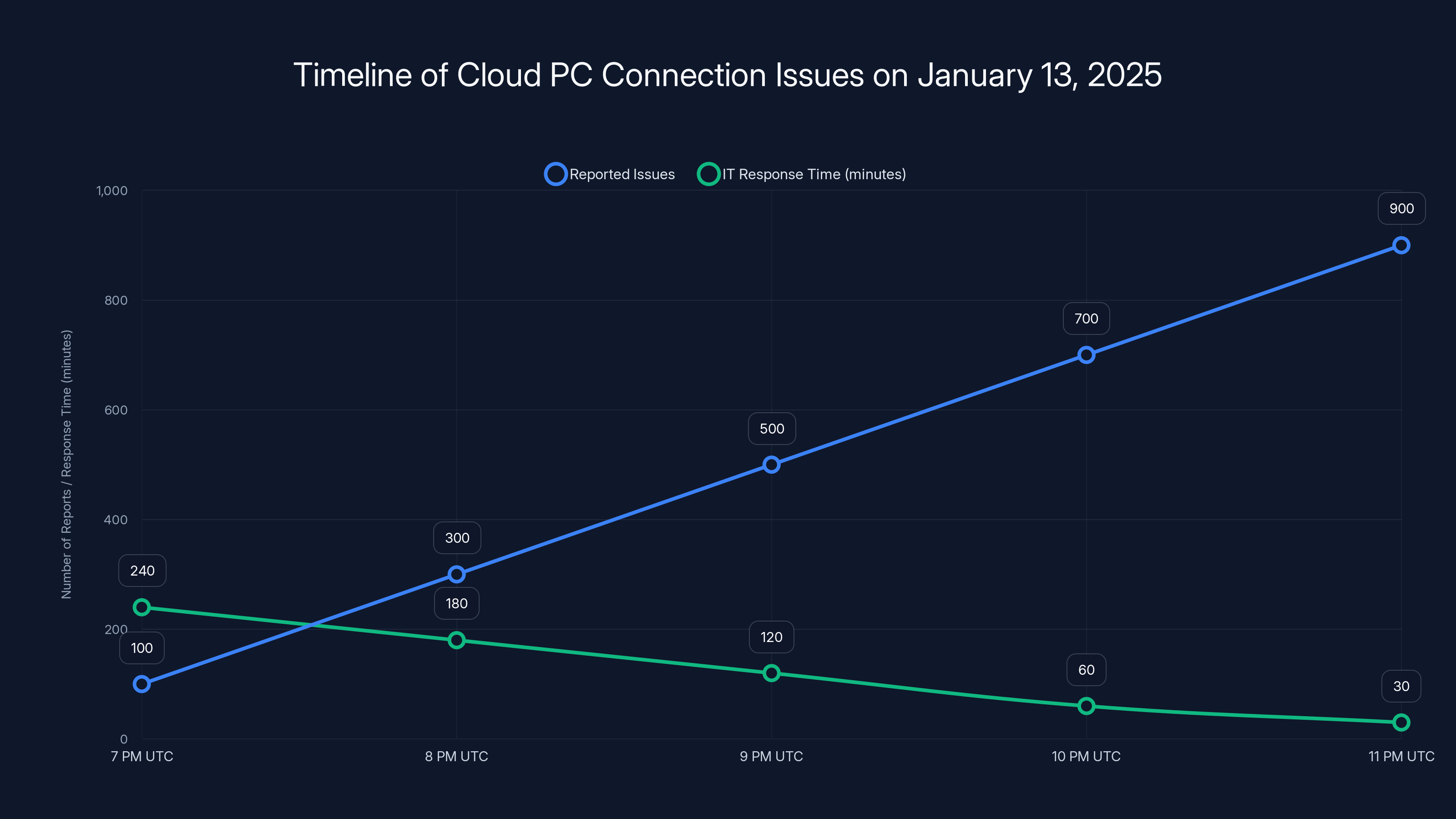
The number of reported issues increased rapidly, while IT response times decreased as teams became more aware of the problem. Estimated data.
What This Means for Update Strategy
The KB5074109 incident should prompt organizations to reconsider how they handle Windows updates, especially in environments where broken updates directly impact revenue-generating activities.
Consider a Staged Rollout Approach
Don't deploy updates to all 10,000 devices simultaneously. Instead, deploy to 1% of devices first. Monitor for issues for 24-48 hours. If nothing breaks, expand to 5%. Keep expanding gradually. This approach would have contained this issue to a small percentage of users rather than affecting everyone.
Implement Detailed Monitoring
After deploying updates, monitor your critical applications and services closely. Set up alerts for Cloud PC connection failures. Track how many users are experiencing authentication issues. Real-time visibility would have highlighted this problem within minutes rather than hours.
Test Updates in Your Environment
Microsoft tests updates, but they test in their lab environment, not yours. Your organization might have configurations or third-party software that Microsoft's labs don't replicate. Testing updates on a representative subset of your devices before broad rollout is essential.
Maintain Update Flexibility
For mission-critical services like Cloud PC, maintain the ability to defer, roll back, or selectively deploy updates. Use Windows Update for Business to control rollout timing. Don't let automatic updates dictate your deployment schedule.

Azure Virtual Desktop and Cloud PC Reliability
This incident reveals something uncomfortable: even enterprise-grade Microsoft services sometimes have reliability issues. This doesn't mean Cloud PC is unreliable overall. Cloud PC has good uptime records. But components fail, updates break things, and when they do, you need contingency plans.
Organizations relying on Cloud PC should approach it as part of their IT strategy, not as a replacement for all IT infrastructure. Have a plan for what happens if Cloud PC becomes unavailable. Where do users work from? How do they access their files? What's your recovery procedure?
Microsoft's service level agreement (SLA) for Cloud PC doesn't typically cover client-side issues like this. The SLA covers the cloud infrastructure. If your client can't connect, that's technically outside the SLA. This is why your own contingency planning matters.

Prevent This in Your Organization
If you manage Cloud PC or Azure Virtual Desktop deployments, here are concrete steps to prevent this issue from hitting you:
Step 1: Establish an Update Deferral Policy
Don't update immediately when Microsoft releases patches. Wait 3-7 days. Let Microsoft's users discover issues first. By day 3 of a problematic update, you'll typically see reports on Microsoft's forums or tech news sites.
Step 2: Deploy to Pilot Users First
Select a group of 20-50 power users across different departments. Deploy updates to them first. Monitor their Cloud PC connections for 48 hours. If they report no issues, proceed with broader rollout.
Step 3: Monitor Connection Health
Implement monitoring specifically for Cloud PC authentication failures. Set up alerts that trigger if your Cloud PC connection failure rate exceeds 1% of total attempts. When alerts fire, investigate immediately before deploying updates to more users.
Step 4: Maintain Multiple Client Options
Ensure users can access Cloud PC through multiple paths: the Windows App, the web client, and the traditional Remote Desktop client. If one breaks, users can switch to another.
Step 5: Document Your Recovery Procedure
Create and test a documented procedure for reverting a problematic update. Test it quarterly. When an incident hits, you don't want to be figuring out recovery steps for the first time in production.
Step 6: Communicate Proactively
When you discover an update issue, communicate with users immediately. Send an email explaining what's broken, what the workaround is, and when the fix will arrive. This prevents support tickets from overwhelming your team.

What We Learned From Similar Incidents
This isn't the first time a Windows update broke something critical. History shows patterns:
The Windows 10 October 2018 Update: This update inadvertently deleted user files from temporary directories. Microsoft had to pause distribution, investigate, and rebuild the update. The incident cost Microsoft credibility and made users skeptical of future updates.
The Windows 10 May 2019 Update: This update broke printer drivers for some users. Again, distribution was halted, investigation occurred, and rollback became an option.
The Windows 10 November 2021 Update: This update caused high CPU usage and battery drain. Users complained about performance degradation. Microsoft eventually released patches to address the issues.
These incidents follow a pattern: a problematic update releases, users discover issues, Microsoft investigates, fixes are released, but trust is damaged. Each incident teaches the industry something about why update testing needs improvement.
The KB5074109 incident follows the same pattern, but the scope is narrower (it specifically affected Cloud PC users) and Microsoft's response was faster (out-of-band fix within days). They're learning from history.
The Bigger Picture: Desktop Virtualization Trends
Cloud PC is part of a broader shift toward desktop virtualization. Rather than issuing each user a physical laptop, companies provision virtual desktops in the cloud. The advantages are significant: centralized management, easier security enforcement, simpler software deployment, and better data security (data stays in the cloud, not on user devices).
But issues like KB5074109 highlight the complexity. When everything works, cloud desktops are wonderful. When something breaks, users literally can't work. There's no fallback like "just use your laptop."
This is why incident response planning matters. This is why staged updates matter. This is why testing matters. Cloud desktops concentrate risk. If the service breaks, productivity stops.
Organizations moving to cloud desktops need to acknowledge this reality. You're trading some management overhead (physical devices are simpler to manage) for operational risk (cloud service disruption). That's a reasonable trade if you're prepared for it. It's a terrible trade if you're blindsided.
Looking Forward: What's Next
Microsoft promised an out-of-band fix "in the coming days." When that fix arrives, organizations should:
- Verify the fix in their test environment before broad deployment
- Document the incident in their change management system
- Update their update deployment procedures to be even more cautious
- Review their monitoring systems to ensure they caught this issue faster
- Test their rollback procedures to ensure they work
The incident isn't over when the fix arrives. The real lesson-learning happens in the days after when organizations analyze how they responded, what worked, and what they'll do differently next time.
FAQ
What exactly went wrong with Windows build 26100.7623?
Windows build 26100.7623 modified core authentication components in the Windows operating system as part of a security update. The Windows App relies on these components to pass credentials from the client to Cloud PC gateway servers. The update inadvertently broke this authentication flow, causing credential prompts to fail when users tried to log into Cloud PCs. The traditional Remote Desktop client continued working because it uses different, unmodified APIs.
Which Windows versions and devices are affected by this issue?
The credential prompt failure affects Windows 11 versions 25H2, 24H2, and 23H2, as well as Windows 10 versions 22H2 and 21H2. Windows 10 Enterprise LTSC 2019 and 2016 are also impacted. Essentially, any Windows device that received the January 2025 security update (KB5074109) and uses the Windows App to connect to Cloud PC or Azure Virtual Desktop is affected. However, not all Windows users are impacted, only those who rely on Cloud PC connections.
Can I use the workarounds permanently, or do I need to wait for the permanent fix?
You can use the workarounds (Windows App Web Client or traditional Remote Desktop client) for as long as needed, but they're temporary solutions. The web client works fine for most productivity tasks but may have slightly higher latency and reduced functionality for advanced features. The traditional Remote Desktop client is robust but requires manual setup for each connection. When Microsoft releases the out-of-band fix for KB5074109, you should deploy it because it resolves the underlying issue and restores full Windows App functionality.
How long will the out-of-band fix take to arrive?
Microsoft committed to releasing the fix "in the coming days" but didn't provide a specific date. Based on historical precedent with other critical updates, "coming days" typically means 3-10 days depending on the complexity of the fix and Microsoft's internal testing procedures. However, you shouldn't wait for the fix before implementing workarounds. Users should be able to access Cloud PC through alternative methods immediately.
Should I roll back the Windows update to fix the issue?
Rolling back the January 2025 security update is not recommended as a permanent solution. That update contains important security patches that protect your system from vulnerabilities. Staying unpatched exposes your organization to security risks. Instead, use the workarounds (web client or traditional RDP client) and implement a staged deployment process for future updates. Rolling back should only be considered if you absolutely cannot implement workarounds and you understand the security implications.
How can I prevent this kind of incident from hitting my organization in the future?
Implement a staged update rollout strategy where you deploy updates to small test groups first (5-10% of users) before broader rollout. Monitor Cloud PC connection metrics closely after each update. Maintain multiple client options so if one breaks, users can switch. Use Windows Update for Business to control update timing rather than relying on automatic updates. Create a documented recovery procedure and test it quarterly. Most importantly, don't deploy critical Windows updates to your entire population immediately upon release.
Is Cloud PC reliable enough for mission-critical work?
Cloud PC is generally reliable, but like any cloud service, it can experience issues. This incident was specifically a client-side problem, not a Cloud PC service outage, but the impact was the same: users couldn't work. Organizations using Cloud PC should treat it as a critical service with proper redundancy planning, backup access methods, and incident response procedures. The reliability depends on multiple factors including client software, network connectivity, and cloud infrastructure.
What's the difference between the Windows App and the traditional Remote Desktop client?
The Windows App is Microsoft's modern UWP (Universal Windows Platform) application designed as the primary client for Cloud PC and Azure Virtual Desktop. It offers a more polished interface and tighter integration with Windows 11. The traditional Remote Desktop Connection (mstsc.exe) is a legacy Win 32 application that's been part of Windows for decades. It's less feature-rich but generally more stable. Both connect to the same Cloud PC infrastructure; the difference is the client software used to establish the connection.
How does this incident affect Azure Virtual Desktop users separately from Cloud PC users?
Azure Virtual Desktop (AVD) is Microsoft's underlying remote desktop infrastructure. Cloud PC is a managed version of AVD where Microsoft handles infrastructure. Both use the same client applications (Windows App, Remote Desktop client). When the Windows App broke, both Cloud PC and AVD users experienced the same credential prompt failures. However, AVD users typically have more control over their infrastructure and might have deployed workarounds faster. Cloud PC users depend on Microsoft's support and fixes more directly.
Conclusion
The KB5074109 incident on January 13, 2025 exposed something uncomfortable about enterprise-grade software: even when built by the world's largest software company, updates can break critical functionality with minimal warning. But it also showed how effective workarounds can be when you have good alternatives available.
The real value of this incident isn't just the workarounds—it's the lesson for every organization using cloud services. Incidents happen. The question is whether you're ready for them.
If you manage Cloud PC or Azure Virtual Desktop, use this incident as a wake-up call. Implement staged update deployment. Monitor connection health. Maintain backup access methods. Test your recovery procedures. Create proactive communication plans.
When Microsoft releases the permanent fix, deploy it cautiously using the same staged approach. This incident is temporary. Your organization's update strategy is permanent. Make it robust.
The organizations that handled this incident best weren't the ones with faster fixes. They were the ones with better contingency planning. They had the web client bookmarked. They knew about the traditional Remote Desktop client. They had monitoring that caught the issue quickly. They had communication plans ready to deploy.
Build those capabilities now, before the next incident hits. Because there will be a next incident. It's not if—it's when. And the organizations that thrive are the ones prepared for it.

Key Takeaways
- Windows update KB5074109 broke Windows App authentication for Cloud PC connections, but the cloud service itself remained operational
- Three immediate workarounds exist: web client, traditional Remote Desktop client, or deferring the update temporarily
- The incident demonstrates why staged update rollouts and comprehensive monitoring are essential for mission-critical cloud services
- Organizations should maintain multiple client access methods and test recovery procedures quarterly to prevent user productivity losses
- Microsoft's response improved over previous incidents, but more specific timelines and proactive communication would have reduced support burden on IT teams
Related Articles
- ChatGPT Translate vs Google Translate: Complete Comparison Guide 2025
- Hannspree Lumo: The Dynamic Paper Tablet Redefining E-Readers [2025]
- Lizn Hearpieces Review: Affordable Hearing Aids with Major Comfort Trade-offs [2025]
- AI Accountability & Society: Who Bears Responsibility? [2025]
- Wikipedia's Existential Crisis: AI, Politics, and Dwindling Volunteers [2025]
- Norton VPN Exclusive Pricing 2025: Best Deals on Two-Year Plans [Guide]
![Microsoft Cloud PC Access Failures: What's Breaking & How to Fix [2025]](https://tryrunable.com/blog/microsoft-cloud-pc-access-failures-what-s-breaking-how-to-fi/image-1-1768478883886.png)



