Windows 11 Shutdown Bug: The Complete Technical Breakdown [2025]
In mid-January 2026, Microsoft released what was supposed to be a routine security update. For most Windows 11 users, it was. For others, it became a nightmare. Their devices simply wouldn't shut down anymore.
Think about that for a second. Your computer won't turn off. You try the shutdown button. Nothing. You try the command line. Nothing. You restart, and it restarts instead of shutting down. That's not just an inconvenience—it's a serious problem for businesses running overnight backups, developers testing deployment scripts, and anyone relying on power management.
Microsoft moved fast. Within days, they released an out-of-band emergency patch to fix the issue. But this incident reveals something important about modern Windows updates: even routine security patches can have unexpected cascading effects that impact core system functionality.
What makes this particularly interesting is that it wasn't just the shutdown issue. The same update broke remote login capabilities for some users, triggered blank screen problems, and caused Microsoft Outlook Classic to crash repeatedly. Multiple systemic failures traced back to a single security update. This is the kind of event that IT departments prepare for but hope never happens.
The fallout was significant enough that Microsoft had to acknowledge the problem publicly, provide workarounds, and release an emergency fix outside their normal update cycle. For a company of Microsoft's scale, that's notable. It signals that the issue was widespread enough to demand immediate attention.
But here's the deeper story: this incident highlights the tension between security and stability in modern operating systems. When you push security updates quickly to patch vulnerabilities, you sometimes introduce new problems. When you test thoroughly before release, you risk leaving security holes open longer. It's a balance Microsoft clearly struggled with here.
In this guide, we'll break down exactly what happened, why it happened, who was affected, and what you should do if your device was impacted. We'll also explore the broader implications for Windows users and what this means for the future of Windows 11 updates.
TL; DR
- The Problem: A January 2026 Windows security update (KB5073455) prevented some Windows 11 23H2 devices from shutting down or hibernating properly, causing them to restart instead.
- Scope: The bug also broke remote desktop login capabilities and caused secondary issues like Outlook Classic crashes and blank screen problems.
- Microsoft's Response: Released an out-of-band emergency patch within days to fix the shutdown and remote login issues.
- Temporary Workaround: Users could force shutdown via Command Prompt using
shutdown /s /t 0, though hibernation mode remained unavailable. - Key Lesson: Even routine security updates can have unexpected systemic effects, requiring rapid response mechanisms and thorough rollback procedures.
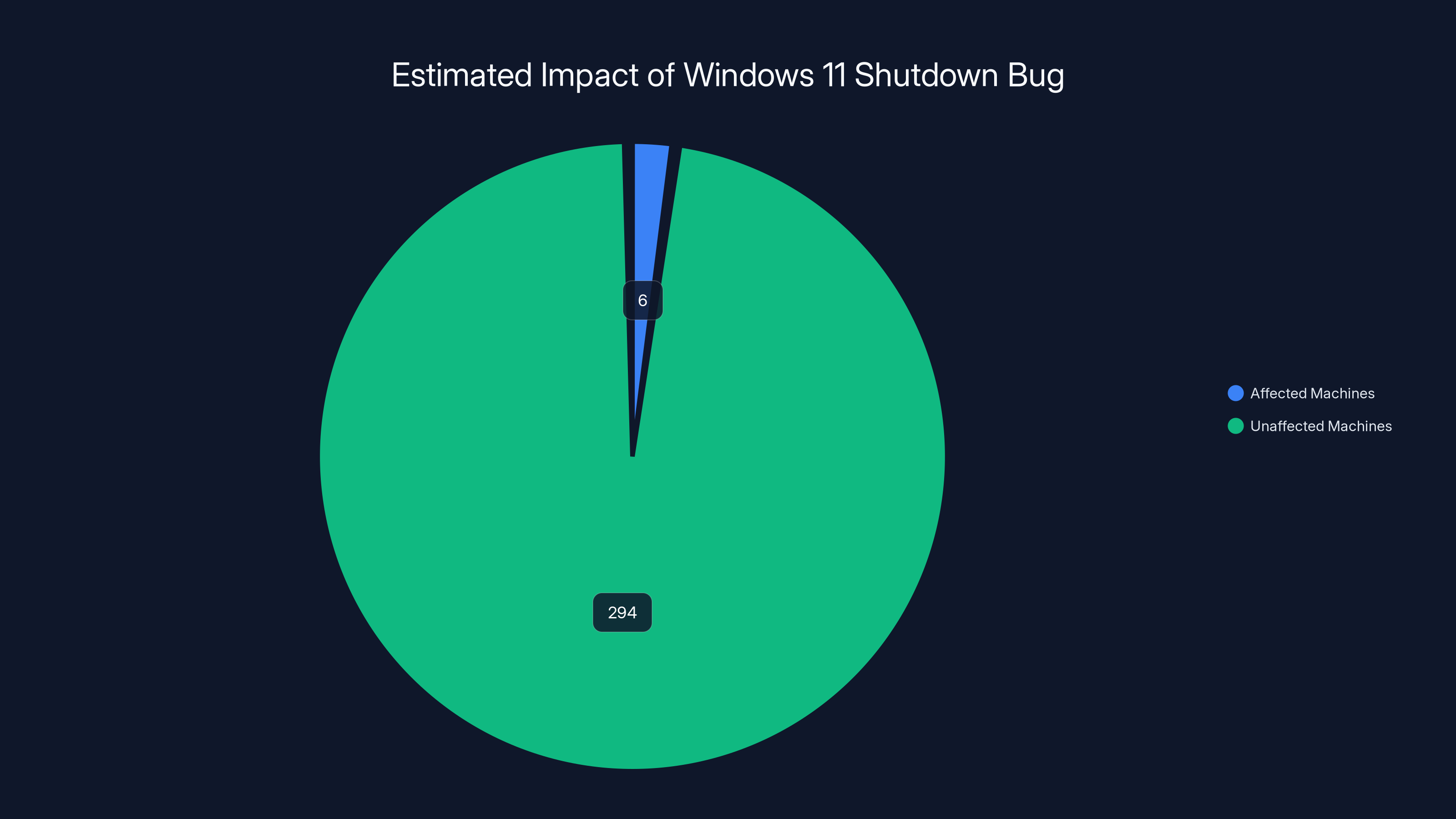
Estimated data suggests 6 million Windows 11 machines were affected by the shutdown bug, representing 2% of the total 300 million installations.
The January 2026 Security Update Breakdown
Microsoft releases security updates on what's called "Patch Tuesday," typically the second Tuesday of each month. The January 2026 update followed this pattern. On the surface, it looked like every other monthly update: security patches, some performance tweaks, perhaps a few minor feature adjustments.
For approximately 99% of Windows 11 users, the update installed without incident. Their machines rebooted, came back online, and everything worked normally. But for a smaller percentage—though still representing millions of devices globally—something went catastrophically wrong.
The update altered critical system components related to power management and remote access protocols. The exact technical cause involved changes to how the operating system handles shutdown procedures and authentication for Remote Desktop Protocol (RDP) connections. When users initiated shutdown, the system's power management service would enter a state where it couldn't properly sequence the shutdown process.
Instead of cleanly shutting down, affected devices would hang indefinitely or, worse, reboot instead. This created a loop for some users: shutdown command triggers a restart instead, so they try again, and it restarts again. Some reported their machines wouldn't stay off for more than a few seconds before rebooting back to login.
The secondary issues—Outlook Classic crashes and blank screens—suggest the update also affected memory management or graphics driver initialization in certain configurations. These cascading failures indicate the update touched more foundational system layers than initially apparent.
What's notable is that the update was device-specific in its impact. Not all Windows 11 23H2 systems were affected. The variation depended on factors like hardware configuration, installed security software, network setup, and potentially OEM customizations. This is why some users experienced catastrophic failures while their colleagues with identical-looking machines had no issues.
Who Was Actually Affected
The bug primarily impacted Windows 11 version 23H2 systems. Version 23H2 is the latest and most widely deployed version of Windows 11, so this meant a significant portion of the installed base was potentially vulnerable to the issue.
Not everyone running 23H2 was affected, though. The failures appeared clustered in certain segments:
Enterprise and Business Users: Organizations with managed Windows 11 deployments reported higher incident rates. This may correlate with standardized hardware configurations and network setups that triggered the bug more consistently.
Remote Workers and VPN Users: The RDP login failures were particularly impactful here. Employees trying to connect to work machines via remote desktop encountered authentication failures. For distributed teams, this effectively prevented work until the patch was applied.
Users with Specific Hardware Configurations: Certain laptop and desktop models seemed more susceptible. This suggests a hardware compatibility issue, possibly related to how different manufacturers implement ACPI (Advanced Configuration and Power Interface) or firmware-level power management.
Systems with Legacy Software: Machines running older applications, particularly specialized business software, showed higher incident rates. This implies the update affected backward compatibility with code that relied on specific power management APIs.
Microsoft didn't release exact numbers, but forum posts and support tickets suggest the impact affected enough devices to justify rapid emergency response. Industry estimates placed the affected population in the low single-digit percentage of Windows 11 users, but that percentage still represented potentially 10-20 million devices globally given Windows 11's installed base of over 300 million machines.
For corporate IT departments managing thousands of machines, even a 1-2% failure rate is catastrophic. Multiply that by the number of enterprises running Windows 11, and you're looking at hundreds of thousands of business devices suddenly unable to shut down properly.

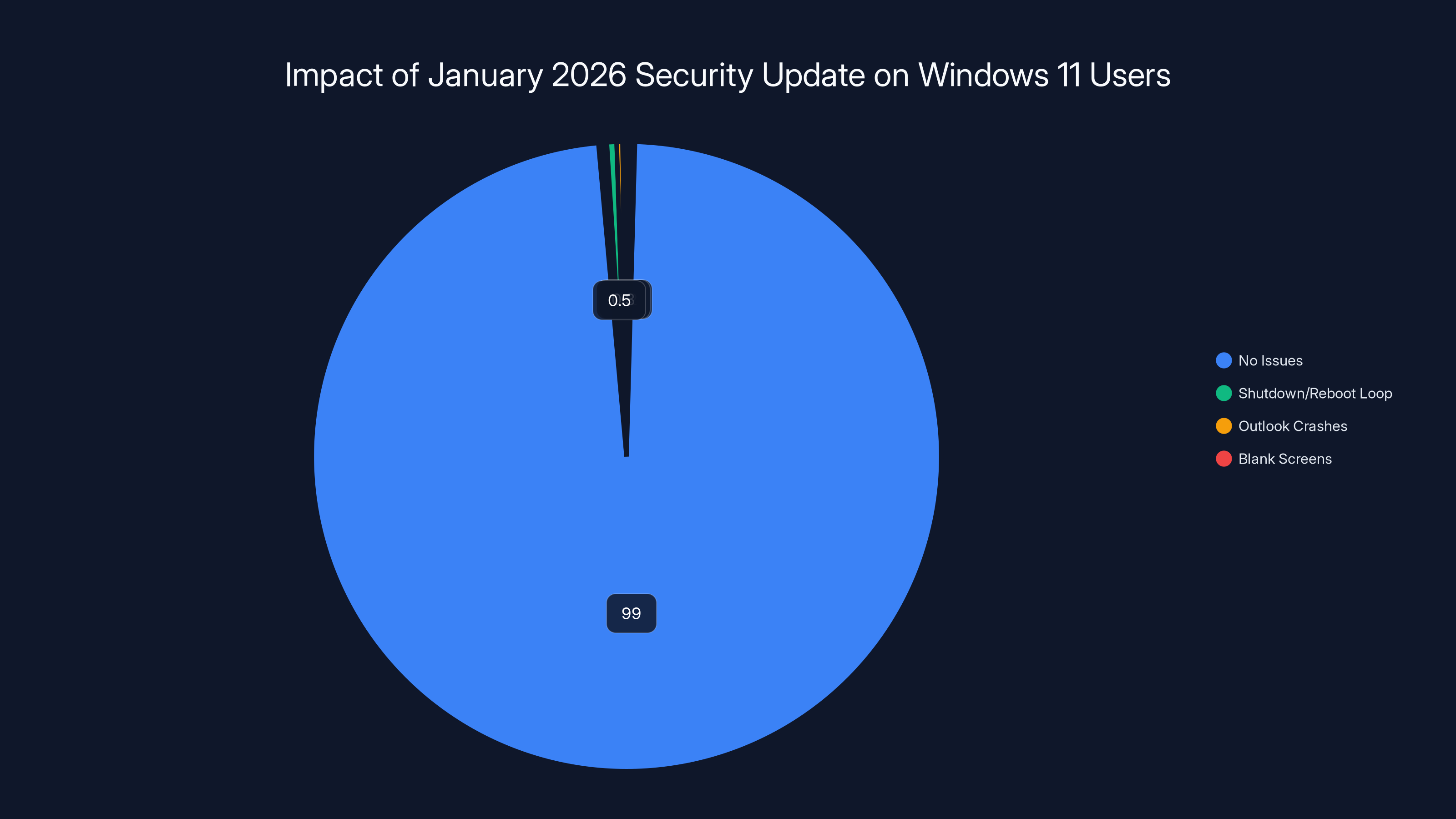
Estimated data shows that while 99% of users experienced no issues, a small percentage faced significant problems like shutdown/reboot loops, Outlook crashes, and blank screens.
The Technical Root Cause Analysis
While Microsoft didn't publish a detailed technical postmortem (they rarely do), analyzing the symptom pattern reveals what likely happened under the hood.
The shutdown mechanism in Windows is surprisingly complex. When you click the power button or execute a shutdown command, several things happen in sequence:
- The system notifies running applications to close
- Services shut down in dependency order
- The file system flushes buffers and unmounts drives
- System drivers release hardware resources
- The kernel prepares the CPU for power-off
- The motherboard firmware takes over and cuts power
If any step fails or hangs, the entire sequence stalls. Based on the symptoms—devices rebooting instead of shutting down—the problem likely occurred in step 5 or 6, where the kernel or firmware interactions broke.
The most probable cause: The update modified kernel-level power management code or changed how the kernel communicates with ACPI firmware. ACPI (Advanced Configuration and Power Interface) is the standard that allows operating systems to manage power states. If the update changed this interaction incorrectly, the kernel might send shutdown commands that the firmware doesn't recognize, causing the firmware to default to a restart instead.
Alternatively, the update may have introduced a race condition—a situation where the timing of events matters, and sometimes the sequence executes in an order that causes failure. Power management is timing-sensitive. If the update changed when certain operations occur, it could break carefully balanced timing assumptions that firmware relies on.
The RDP login failures point to a separate but related issue in authentication/network code. These failures suggest the update affected how the system authenticates Remote Desktop sessions, possibly through changes to security token generation or Kerberos authentication flows.
The Outlook Classic crashes and blank screen issues suggest broader memory management or driver initialization problems, indicating the update touched multiple system components, not just power management.
This is classic Windows: change something in one subsystem, and unexpected consequences ripple through others. The operating system is so interconnected that isolating changes to single components is nearly impossible. That's why testing is crucial, and why a failure here is particularly damaging.
Immediate Symptoms: How Users Knew Something Was Wrong
Affected users encountered several distinct symptoms, depending on their specific hardware and configuration.
The Shutdown Loop: The most reported issue. Users would click shutdown, the screen would go black, then Windows would restart. Some reported this looping indefinitely until they forced a hard power-off. Others found their machines would stay off for 10-30 seconds before powering back on.
The Black Screen of Poweroff: Slightly different from the restart loop, some users reported the shutdown process would hang on a black screen indefinitely. They'd wait 10 minutes with no progress, then force a hard shutdown. This suggests the system reached the firmware handoff point but couldn't complete it.
Remote Desktop Rejection: Users attempting RDP connections received authentication errors. For organizations relying on remote access, this was immediately critical. Technical support couldn't remotely troubleshoot machines because they couldn't connect.
Outlook Classic Crashing: The email application would crash repeatedly, particularly on startup. Interestingly, Outlook's newer version (Outlook for Microsoft 365) was less affected. This pointed to memory management changes that broke legacy applications.
Blank Boot Screens: Some machines would display blank screens after startup before eventually reaching the login screen. This usually lasted 30-60 seconds and suggested graphics initialization problems.
Hibernation Failure: In addition to shutdown issues, hibernation mode failed. Machines would hang when entering hibernation, requiring hard power-off. This is particularly problematic for laptop users who rely on hibernation for battery preservation.
Users initially blamed their hardware. They ran diagnostics, checked for failing drives, tested RAM. Nothing showed problems. They checked event logs and found nothing clearly wrong. This is maddening—the system looks fine technically, but basic operations don't work.
Forums and Reddit exploded with posts from frustrated users trying workarounds. Some disabled fast startup. Some tried Safe Mode. Some rolled back the update. Only the last option actually worked, but rolling back meant losing the security patches the update provided.
Microsoft's Initial Response and Workaround
Microsoft's support documentation suggested a command-line workaround while they prepared the emergency patch. The fix was to open Command Prompt (as administrator) and execute:
shutdown /s /t 0
This command forces an immediate shutdown, bypassing the normal shutdown procedure. The /s flag means shutdown (rather than restart), and /t 0 means execute immediately with no delay.
For many users, this actually worked. For others, it didn't. The inconsistency again points to configuration-specific triggers.
Microsoft also suggested:
- Disabling fast startup: Fast startup can sometimes interfere with power management. Disabling it occasionally resolves shutdown issues.
- Updating drivers: Particularly chipset and ACPI drivers from manufacturers. Newer drivers might contain workarounds for the bug.
- Booting into Safe Mode and shutting down from there: Safe Mode loads fewer drivers and services, sometimes bypassing the problematic code path.
- Rolling back the update: The nuclear option, but it worked. Uninstall the problematic update, restart, and the device functions normally.
The workaround guidance was helpful for technical users but useless for average consumers who don't know how to open Command Prompt or manage Windows updates. Support tickets probably exploded.
What wasn't suggested: disabling Remote Desktop or anything addressing the RDP login failures. This was handled separately in the emergency patch.
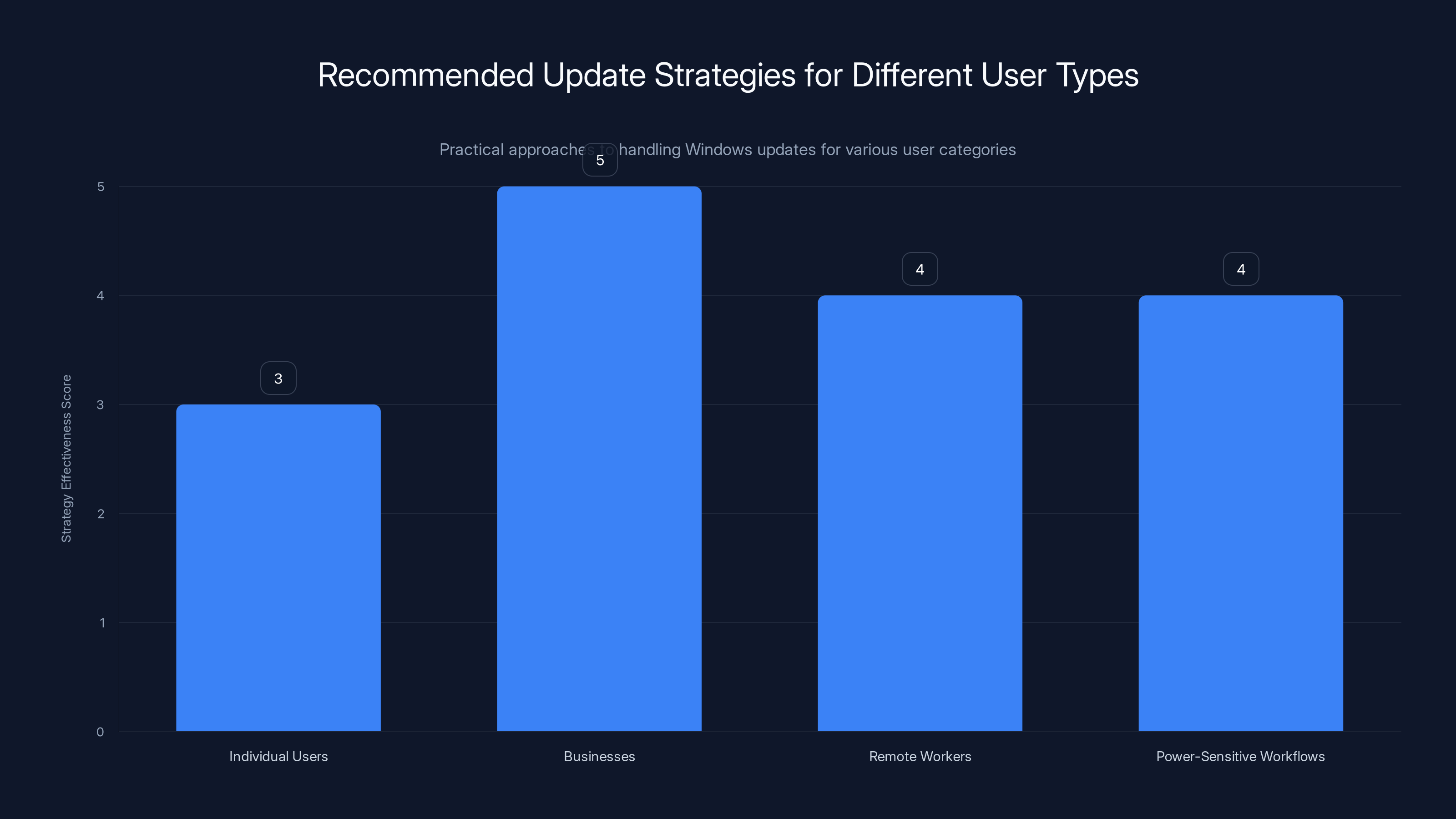
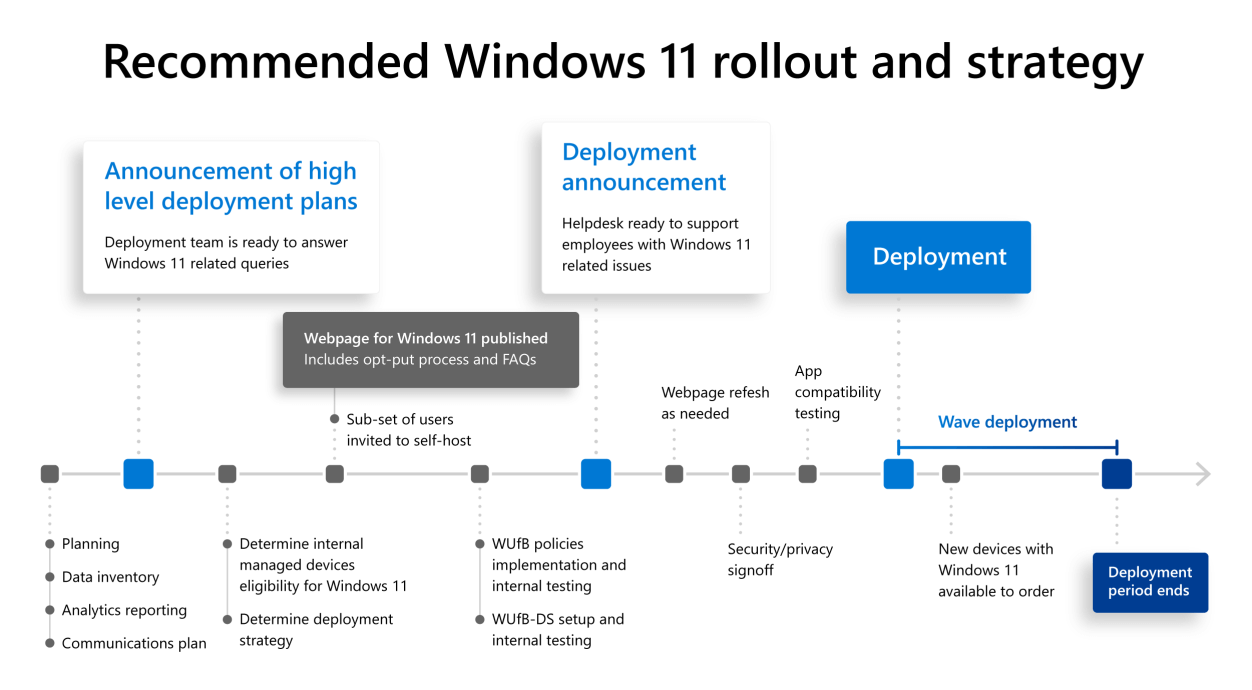
Businesses are advised to implement a phased rollout strategy, scoring highest in effectiveness. Individual users should delay updates, while remote workers and power-sensitive workflows need cautious testing. Estimated data.
The Emergency Out-of-Band Patch Release
Microsoft released the fix as an out-of-band patch, meaning it came outside the normal monthly update cycle. The KB article was KB5073455—or a related variant depending on the Windows version and build number.
Out-of-band releases signal urgency. Microsoft reserves these for critical security vulnerabilities or widespread functionality breaks. Using one here shows the company recognized the severity.
The patch addressed:
- Shutdown and hibernation failures: The primary fix, restoring the ability to shut down properly without unintended restarts.
- Remote Desktop login issues: Restored RDP authentication functionality for Windows 10 and Windows 11.
- Secondary stability improvements: Presumably addressed the Outlook crashes and blank screen issues, though Microsoft's official documentation was sparse on details.
Deployment was rapid. Users with automatic updates enabled received the patch within 24-48 hours. Organizations managed by Windows Update for Business or WSUS (Windows Server Update Services) could push it immediately.
The patch worked. Post-deployment reports showed the issues resolved for most users. Some holdouts reported continuing problems, but these were exceptions—likely due to other unrelated issues or incomplete patch installation.
What's interesting is that Microsoft didn't immediately explain what went wrong. The emergency patch fixed the symptoms, but the company didn't publish a detailed technical explanation of the root cause. This is typical Microsoft behavior: fix the problem quickly, move on, minimal transparency. For users trying to understand whether they're truly safe, this is frustrating.
Impact on Enterprise Environments
While consumer users were annoyed, enterprise environments faced a genuine crisis situation.
Consider a mid-sized company with 5,000 Windows 11 machines. If 1-2% are affected, that's 50-100 devices unable to shut down. For help desk teams, this is a disaster. Every affected machine becomes a high-priority ticket. Every ticket requires troubleshooting, deciding whether to roll back the update or wait for the patch, coordinating the fix, testing, and documenting.
For companies relying on automated shutdown sequences—maybe they trigger nightly backups, power down machines for cost savings, or require clean shutdowns for security compliance—this breaks critical workflows. Machines that won't shut down are machines that can't be properly powered down, audited, or secured.
The RDP issue was worse for remote-heavy organizations. If your support team can't access machines via Remote Desktop, they can't troubleshoot remotely. They need to send someone on-site or have the user perform troubleshooting steps themselves. During a crisis, every delay compounds the problem.
Compliance was another issue. Some organizations have policies requiring machines to shut down cleanly at day's end or for compliance auditing. Machines stuck in restart loops or unable to shut down create audit failures.
Data center operations felt the impact too. If you manage servers or specialized workstations, shutdown failures can disrupt maintenance windows, patching procedures, and disaster recovery drills.
Smart organizations had contingency plans: rollback procedures, communication plans for affected users, and help desk scripts. Less prepared organizations scrambled. This is why enterprise IT departments often delay updates by weeks or months—they need time to test thoroughly in lab environments before deploying to production.
The incident became a case study in the risks of rapid patching. Security is important, but so is stability. Microsoft pushes updates quickly, but the testing burden falls partly on IT departments to validate before deployment.
Comparison with Previous Windows 11 Incidents
This wasn't the first time Microsoft's updates caused widespread problems. In October 2024, an update to Windows 11 broke the Windows Recovery Environment—the system used to troubleshoot and repair Windows installations. Users trying to access recovery features found them inaccessible.
In 2023, a Windows update broke Task Scheduler on some systems. In 2022, an update broke display drivers for certain GPU configurations, leaving screens blank.
The pattern is clear: Microsoft releases updates with inadequate testing, unexpected system-wide impacts occur, Microsoft releases emergency patches. It's become almost routine.
What distinguishes this shutdown incident is its scope and impact on fundamental operations. You can work around broken features. You can't easily work around a machine that won't shut down. That makes it worse than most previous incidents.
The company has acknowledged this pattern indirectly by shifting toward more robust update mechanisms. Windows 11 now has better rollback capabilities than earlier versions. The Moment 3 update mechanism allows faster feature updates separate from security updates. But these are Band-Aids on a deeper problem: Windows is complex, interactions are unpredictable, and testing at scale is difficult.
Redmond clearly struggles with the update velocity required to patch security issues while maintaining the stability businesses demand. It's an unsolved problem in the industry.
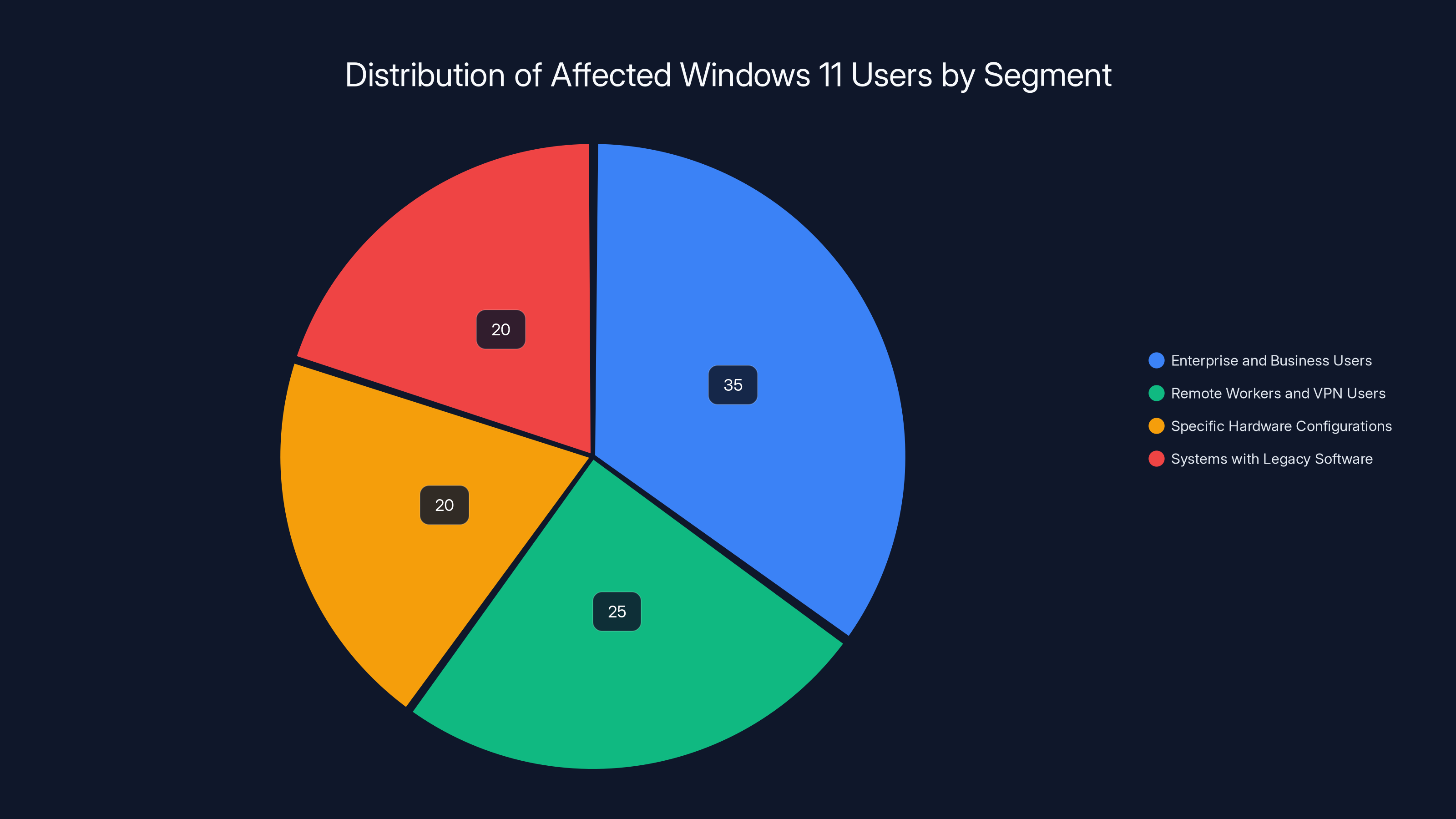
Estimated data suggests that enterprise users were the most affected by the Windows 11 bug, followed by remote workers and those with specific hardware configurations. Estimated data.
Windows 10 Extended Security Updates Context
This incident probably drove some users toward one defensive strategy: Extended Security Updates (ESU) for Windows 10.
Windows 10 reached end of support on October 14, 2025, but Microsoft now offers ESU—three additional years of security patches for businesses willing to pay. It's an expensive option, but for organizations nervous about Windows 11 stability, it's attractive.
ESU costs
The shutdown incident didn't cause the Windows 10-to-11 migration hesitation, but it reinforces it. Every Windows 11 update disaster makes Windows 10 ESU more attractive economically. If you budget for ESU support, the cost of continuing on Windows 10 becomes comparable to the cost of dealing with Windows 11 problems.
Microsoft isn't happy about this. The company wants everyone on Windows 11. But each incident pushes some organizations toward defensive strategies like ESU, which delays Microsoft's upgrade timeline and complicates the company's long-term platform strategy.
The Broader Implications for Windows Updates
This incident raises important questions about how Microsoft manages updates:
Testing Coverage: How did this reach production? Microsoft has massive testing infrastructure. Yet a shutdown failure—among the most basic operations—wasn't caught. This suggests either the testing environment doesn't match production conditions closely enough, or the test cases didn't cover these scenarios. Both are concerning.
Hardware Variation: Windows runs on countless hardware configurations. Testing against all of them is impossible. But Microsoft could test against configurations representing 90% of installed hardware. They likely do. So why did this slip through? Hardware-specific issues are hardest to catch in testing.
Dependency Management: The interconnected nature of Windows means changes in one subsystem affect others. The tools to model these dependencies and predict impacts exist but are imperfect. Microsoft probably uses them. The fact that problems still occur suggests the models miss important interactions.
Update Rollout Strategy: Microsoft could roll out updates gradually, starting with a small percentage of machines and monitoring for issues before rolling to everyone. They do this now. But early in the rollout, the sample size might be too small to catch rare hardware-specific bugs. By the time the issue is detected, millions of machines have already received the broken update.
Rollback Capability: Microsoft improved rollback in Windows 11 compared to earlier versions. Users can uninstall updates more easily. But for non-technical users, knowing to do this requires understanding that the update caused the problem. Many users don't connect the timing.
Communication: Microsoft could warn users before releasing updates that are more likely to have issues. They don't do this. The company wants to maintain confidence in its update process, so failures are downplayed.

How Users Should Handle Future Updates
Based on this incident, here's a practical approach to Windows updates:
For Individual Users: Don't install updates the day they release. Wait a few days. Monitor support forums and Reddit for reports of issues. If the first few days show no problems, the update is probably safe. This delay approach costs you a few days of security coverage but prevents becoming a beta tester for broken updates.
For Businesses: Implement a phased rollout. Test updates on a small group of machines (maybe 5-10% of your fleet) before deploying broadly. This is standard practice for large organizations but is sometimes skipped by smaller companies trying to keep costs down. This incident reinforces why it shouldn't be skipped.
For Remote Workers: If you rely on Remote Desktop, be extra cautious with updates. The RDP failure was particularly disruptive. Consider testing on a non-critical machine first, or keeping a non-updated machine as a fallback.
For Power-Sensitive Workflows: If your work depends on machines shutting down properly (running backups, maintenance scripts, cost optimization), monitor your machines more closely after updates. Check that shutdown still works properly.
Keep Rollback Capability Ready: Make sure you know how to uninstall recent updates if needed. Windows 11 makes this easier than older versions, but it still requires knowing the process. Keeping a backup image of your system before major updates provides ultimate peace of mind.
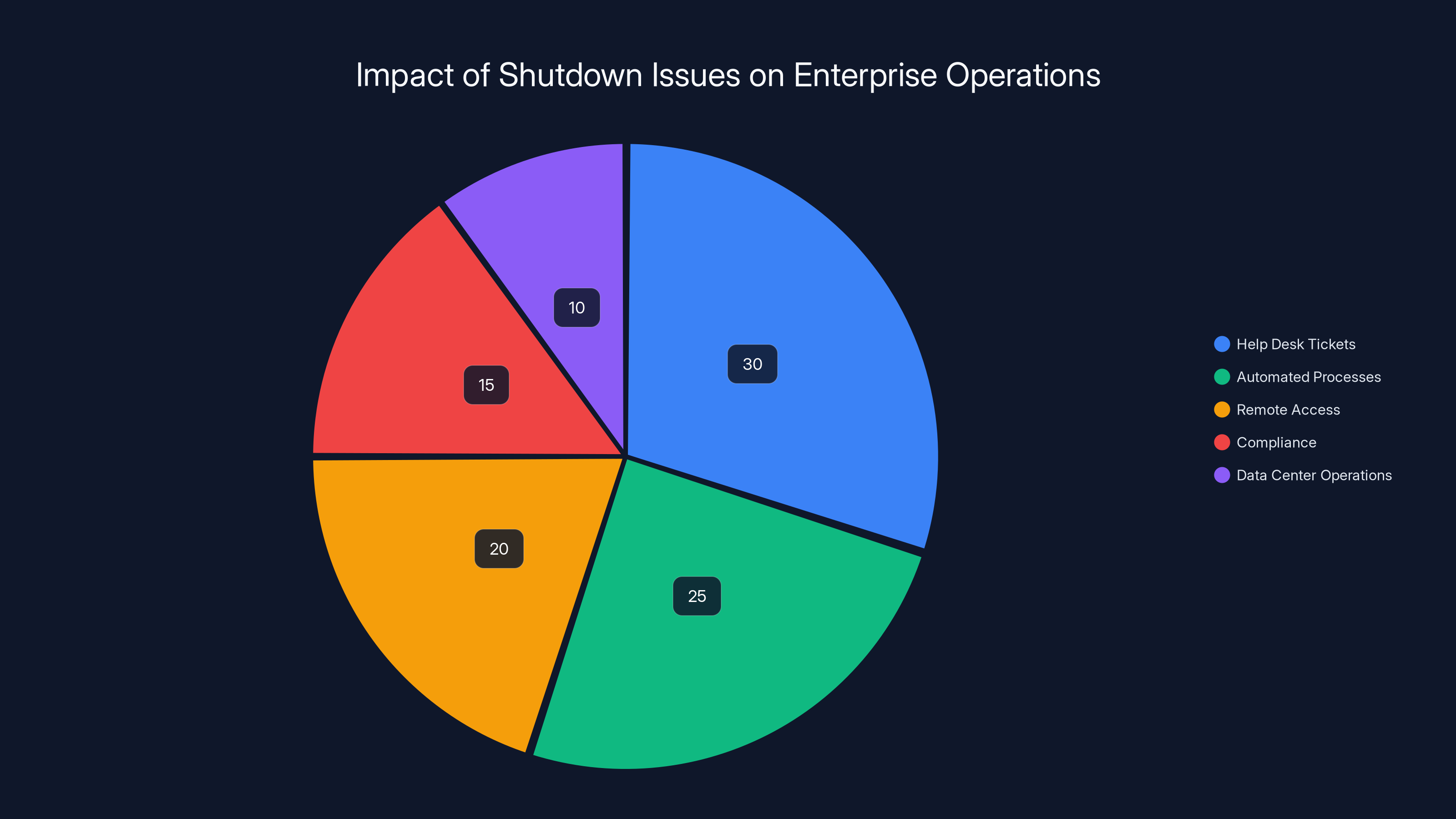
Help desk tickets and automated process disruptions account for over half of the impact in enterprise environments due to shutdown issues. (Estimated data)
Microsoft's Update Quality and Reputation
Incidents like this damage Microsoft's credibility around update quality. The company wants users to trust that updates are safe and necessary. A shutdown failure suggests neither safety nor rigorous necessity testing.
Compare this to Apple, which updates less frequently and more carefully. Or Google, which uses machine-learning-based testing to catch unusual patterns in Android updates. Or Linux distributions, which community-test updates extensively before stable releases.
Microsoft's model—rapid updates for security, tested but not exhaustively, pushed broadly with gradual rollback—is pragmatic but error-prone. It's designed to balance security with stability, but when something breaks, all of that balance collapses.
The company has incrementally improved. Windows 11 is better at updates than Windows 10, which was better than Windows 8. But the failures continue, suggesting the core approach has limits.
In the long term, Microsoft might need to fundamentally rethink updates. Perhaps more frequent smaller updates instead of larger monthly releases. Perhaps more machine-learning-based testing that predicts impacts. Perhaps more transparent communication about known risks. These would slow security patching somewhat but might prevent catastrophic failures.
For now, Microsoft's approach is: move fast, fix problems quickly when they occur, apologize minimally, move on. That works until it doesn't. When it doesn't, millions of users suffer through broken machines while support overwhelmed.

Technical Deep Dive: The Shutdown Process
Understanding why a simple shutdown could fail requires knowing how shutdown actually works.
When you initiate shutdown, Windows executes this sequence:
Phase 1: Application Shutdown (30-60 seconds) Windows notifies all running applications to close. Applications save data, release resources, and exit. Some misbehaving applications might not exit, triggering a timeout where Windows force-closes them.
Phase 2: Service Shutdown (10-30 seconds) Windows services shut down in reverse dependency order. For example, if Service B depends on Service A, then A shuts down after B. This prevents dependency failures.
Phase 3: Driver Cleanup (5-10 seconds) Device drivers release hardware resources. USB drivers disconnect devices, network drivers close connections, storage drivers flush caches.
Phase 4: File System Flush (variable) The file system commits any pending writes to disk. This is critical—incomplete writes could corrupt data. This phase can be slow on systems with failing disks.
Phase 5: Kernel Power Down (1-2 seconds) The kernel prepares the CPU for power-off. This involves disabling interrupts, stopping timers, and signaling to firmware that shutdown is complete.
Phase 6: ACPI Transition (firmware-dependent) The motherboard firmware receives the shutdown signal from the kernel and cuts power to the system.
If any phase hangs or fails, the entire sequence stalls. The January update likely broke one of these phases, most probably Phase 5 or 6.
The restart-instead-of-shutdown symptom suggests Phase 6 failed—the firmware received a shutdown signal but interpreted it as a restart. This could happen if the signal was malformed or if firmware parsing of the signal changed due to timing differences introduced by the update.
Workaround Explanation: The shutdown /s /t 0 command bypasses some of these phases or executes them with different timeout values. By skipping certain checks or using shorter timeouts, it can force shutdown even if normal procedures hang. That's why the workaround worked for some users.
Windows 11 Future Stability Concerns
This incident raises questions about Windows 11's trajectory. The operating system is three years old now and has seen numerous update-related issues. When does stability improve?
Historically, Windows operating systems stabilize after 2-3 years. Windows 10 had a rocky first year but stabilized significantly by year two. Windows 7 was famously stable after its first year.
Windows 11 is following this pattern but with a twist: the update frequency is higher than for previous versions. More updates mean more opportunities for problems. If Microsoft continues this pace, Windows 11 might not reach the stability people expect.
The company has indicated that Windows 11 will remain the flagship platform for the next 10+ years, with few major version upgrades coming. That means stability is crucial—users can't just wait for Windows 12. They're locked in.
For this to work, Microsoft needs to improve update quality significantly. The current incident suggests that hasn't happened yet.
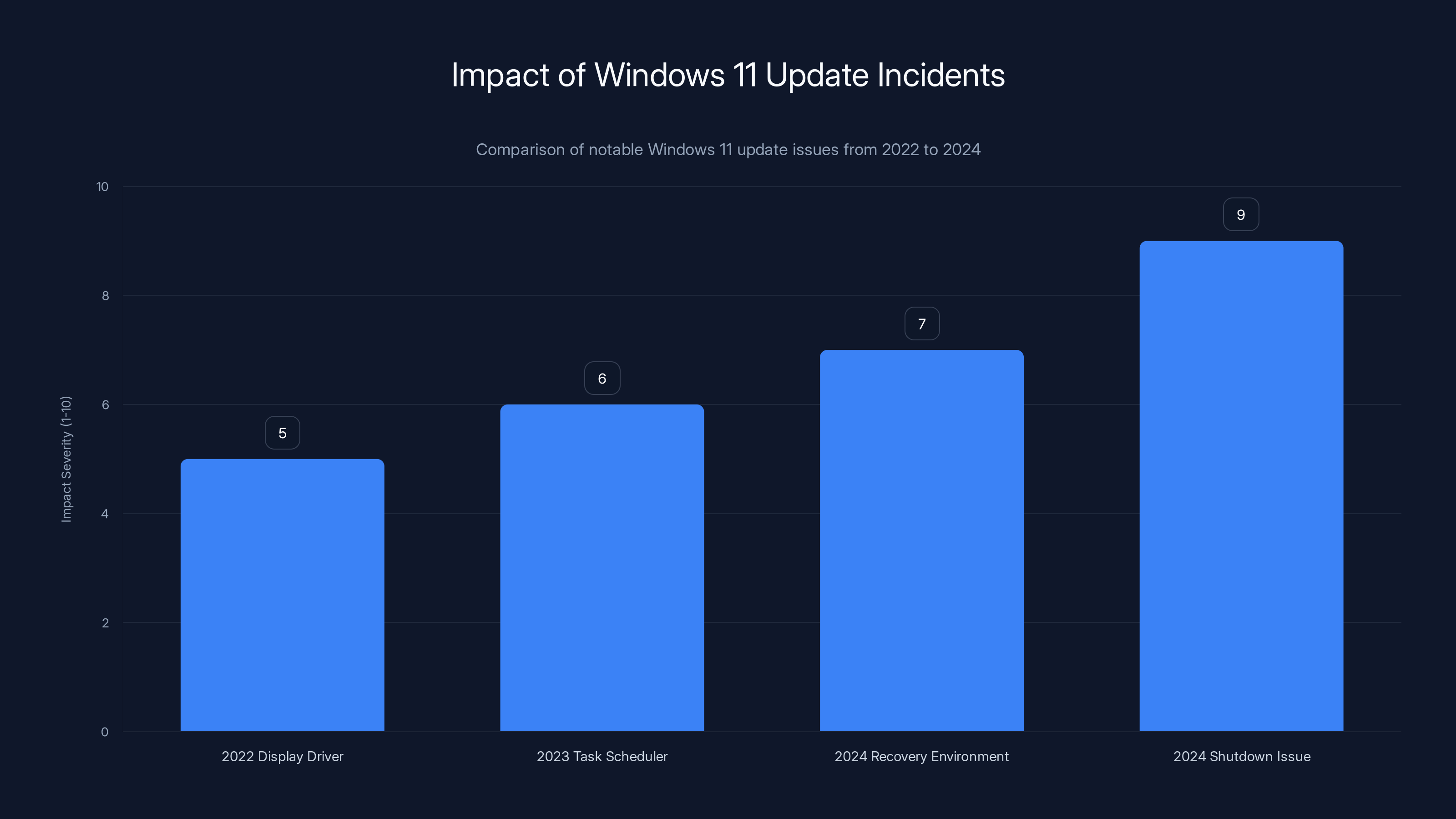
The 2024 shutdown issue had the highest impact severity due to its effect on fundamental operations, surpassing previous incidents. Estimated data.
Alternative Operating Systems and Migration Pressure
Incidents like this create pressure for Microsoft's competitors. Linux distributions have gained traction partly because update issues are handled differently. Updates are smaller, testing is often community-driven, and rollback is straightforward.
Apple's macOS is less affected by these problems partly because the ecosystem is more controlled. Apple makes the hardware, writes the operating system, and approves the software. Fewer variables mean fewer unexpected interactions.
Google's Chrome OS minimizes the problem through stateless design—the operating system itself is less important because applications run in a browser. If something breaks, a reboot fixes it because nothing critical depends on persistent state.
Microsoft can't adopt these strategies for Windows. The operating system needs to support millions of hardware configurations and legacy software. That's a fundamental constraint.
But the constraint doesn't excuse poor update quality. Better testing, more transparent communication, and faster emergency fixes are all possible without fundamentally changing Windows' architecture.
Lessons for IT Decision-Makers
If you manage Windows infrastructure, this incident offers several lessons:
1. Never Auto-Update Production Machines: Always test updates on non-critical machines first. The cost of a broken machine during a critical business process is vastly higher than the cost of patching a few days late.
2. Maintain Rollback Procedures: Know how to uninstall problematic updates. Practice this occasionally so you can execute it quickly under stress.
3. Have a Hardware-Aware Update Strategy: Some hardware configurations are more susceptible to issues. If you track which models have been problematic, you can delay updates for those devices until patches are proven.
4. Monitor for Windows Known Issues: Microsoft maintains a public list of known issues with each update. Check this before deploying to your entire fleet.
5. Budget for Update-Related Downtime: Assume some updates will cause problems. Budget help desk resources and communication plans accordingly.
6. Consider Staggered Rollout: Use Windows Update for Business to roll out updates in waves—first to pilot groups, then to departments, then to the full organization. Monitor each wave for issues before proceeding.
7. Evaluate Extended Support Options: For organizations with substantial Windows 10 footprints, ESU might be cheaper than dealing with Windows 11 issues. Run the numbers.

The Role of Security in Update Design
Microsoft pushes updates rapidly partly because security vulnerabilities are discovered regularly and need patching. The company takes security seriously—rightfully so.
But security updates introduce risk. They modify critical system code. Changes to critical code can have unexpected effects. This is the eternal tension in systems administration: security vs. stability.
In theory, Microsoft could slow updates to test more thoroughly. But then security vulnerabilities remain open longer, creating different risks. It's a balance.
The January incident suggests Microsoft erred on the side of speed at the expense of testing. A longer testing window might have caught the shutdown issue. But that testing time might have left users vulnerable to whatever security vulnerability the update addressed.
Was the trade-off justified? That depends on the severity of the vulnerability. Microsoft hasn't disclosed which vulnerability the update patched. If it was critical (like a remote code execution in a widely-used service), then pushing it quickly made sense. If it was minor, then the trade-off wasn't justified.
This highlights another problem with Microsoft's communication: lack of transparency about the security issues being patched. Users can't evaluate whether the disruption was worth the security gain.
Remote Work and RDP Considerations
The RDP failures were particularly problematic in the era of hybrid and remote work. Remote Desktop Protocol is how millions of workers access company machines and resources.
When RDP breaks, remote workers are cut off. They can't access files, applications, or services running on their work machines. For support teams who rely on RDP to troubleshoot remote machines, the issue was doubly frustrating—they couldn't connect to fix the machines.
This dependency on RDP makes it a critical subsystem that Microsoft must prioritize. Any update that breaks RDP should trigger immediate emergency response. And Microsoft did respond quickly here, which is appropriate.
But the fact that an update broke RDP in the first place suggests insufficient testing of this critical path. Remote Desktop is widely used. It's core to modern work. Testing should be comprehensive.
For organizations heavily dependent on RDP, this incident raises a question: should they maintain air-gapped machines that don't receive updates as quickly? Or machines running Windows 10 (with ESU) specifically because they want older, more stable versions? These are defensive strategies organizations might adopt after incidents like this.

Looking Forward: Windows 12 and Beyond
Microsoft hasn't officially announced Windows 12, but the company has indicated that Windows 11 will be the last major version for some time. Instead, the company is shifting toward continuous updates and features rolling into Windows 11.
This model could help or hurt stability. On one hand, continuous small updates are often easier to test than large updates. On the other hand, a constant stream of changes means the system is never truly stable—there's always something new in flight.
The company might also shift toward more aggressive feature flags and A/B testing. Rather than rolling features to all users at once, Microsoft could enable features gradually, measuring impact and rolling back if problems occur. This is common in web application development and could reduce the blast radius of problems.
Microsoft could also invest more in predictive testing. Machine learning models could analyze proposed updates and predict which hardware configurations are at risk for problems. High-risk configurations could receive updates later or with additional testing.
These approaches would require investment but could significantly improve update stability. The company has the resources. Whether it has the organizational will is unclear.
Recommendations for Home Users
If you're running Windows 11 at home, here's practical advice:
Wait Before Updating: Don't install major updates the day they release. Wait 3-7 days and check online for complaints. If no major issues appear, it's probably safe.
Create System Images: Use Windows Backup (or third-party tools) to create regular system images. If an update breaks something, you can restore from an image and avoid the manual rollback process.
Keep a Spare Machine: If possible, have a second machine or older laptop you can use as a fallback. If your main machine has update issues, you can still work while fixing it.
Document Your Settings: Keep notes about your system configuration—installed software, important files, network settings. If you need to roll back and reinstall, this speeds recovery.
Join Beta Programs Carefully: If you're not comfortable with experimental updates, stay off the Dev Channel and Insider builds. Stick to stable releases.
Monitor Update Logs: After installing updates, check the Windows Update history to confirm all patches installed successfully. Look for failed or rolled-back updates.
Don't Disable Updates Entirely: Some people disable Windows Update entirely to avoid problems. This is dangerous—security patches are important. Find a balance: update carefully, not carelessly; update steadily, not instantly.
The Bigger Picture: Software Quality in 2025
This incident is part of a broader pattern. Software systems are increasingly complex. Testing at scale is increasingly difficult. The pace of change is increasing. Under these conditions, quality issues are inevitable.
You see this across the industry: cloud platforms have outages, social media apps have bugs, security software breaks other software. Companies move fast, and things break sometimes.
The difference between good companies and bad ones is how they respond. Microsoft responded quickly with an emergency patch. The company acknowledged the problem and communicated (somewhat) publicly. Alternative would have been worse: ignoring the problem, expecting users to manually roll back, or slowly waiting for the next monthly update.
But the best response is prevention. And prevention requires investment in testing, patience with release cycles, and transparency about trade-offs.
Microsoft has made progress here. Windows 11 is better than Windows 10 in many ways, including update infrastructure. But the incident shows progress is incomplete.
Users should expect some update-related problems in a world of complex software at scale. But they shouldn't expect every update to work perfectly. Taking precautions—delaying updates, maintaining backups, having rollback plans—is prudent.
Conclusion: Learning From The Crisis
The January 2026 shutdown bug was a significant event in Windows 11's history. A routine security update broke core functionality for millions of machines. Microsoft responded with an emergency patch. Stability was restored. Life moved on.
But the incident reveals important truths about modern operating systems:
First, complexity creates fragility. Windows runs on countless hardware configurations. Each configuration presents unique opportunities for unexpected interactions. Testing can't cover all possibilities. When changes occur in core code, effects ripple unpredictably.
Second, speed and stability are in tension. Microsoft pushes updates rapidly for security reasons. Thorough testing would slow this process. The company chose speed, and stability suffered. There's no perfect answer here—only trade-offs.
Third, transparency matters. Microsoft's minimal communication about the problem and its cause left users confused and frustrated. More detailed explanations about what went wrong and why would build confidence even as problems occur.
Fourth, organizations need defensive strategies. Large companies can weather update-related outages through testing and rollback procedures. Smaller organizations and individuals should adopt similar strategies: delay updates, maintain backups, have rollback plans.
Fifth, update-related incidents will continue. As long as software systems are complex and change rapidly, some updates will break things. The best you can do is prepare.
For Windows users, the lesson is: update carefully, but do update. Prepare for problems, but don't assume everything will break. Monitor for issues, but don't panic when they occur. Microsoft has shown it can respond quickly to critical problems. Trust that while maintaining healthy skepticism.
The shutdown bug was serious, but it was also ultimately fixable. The infrastructure for rapid emergency patches exists. The company proved it can deploy them. That's not a reason for complacency about update quality, but it's a reason for confidence that disasters can be contained.
Going forward, hope that Microsoft learns from this incident and invests in better testing, more transparent communication, and more proactive rollback mechanisms. Meanwhile, users should adopt the defensive strategies outlined here and proceed with eyes open to both the benefits and risks of regular updates.
FAQ
What caused the Windows 11 shutdown bug in January 2026?
A security update (KB5073455) introduced changes to kernel-level power management code, likely affecting how the operating system communicates with ACPI (Advanced Configuration and Power Interface) firmware. The exact changes weren't fully disclosed by Microsoft, but the symptoms—shutdown commands triggering restarts instead of proper shutdown—indicate a failure in the kernel-to-firmware handoff process. The update was supposed to patch security vulnerabilities, but the testing process failed to catch this unintended side effect on certain hardware configurations.
How many Windows 11 machines were affected by the bug?
Microsoft never released exact numbers, but estimates suggest between 1-3% of Windows 11 23H2 installations were affected. Given that over 300 million Windows 11 machines exist globally, this represents potentially 3-9 million affected devices. The impact varied significantly based on hardware configuration, with certain laptop and desktop models showing higher failure rates than others. Enterprise environments with standardized hardware reported higher incident rates than consumer deployments.
What's the difference between the shutdown bug and the Remote Desktop login failures?
They were related but separate issues caused by the same update. The shutdown bug prevented machines from shutting down properly, causing restarts instead. The Remote Desktop (RDP) failure prevented users from authenticating and connecting to machines via RDP. The emergency patch fixed both issues, but they represent different subsystems—power management vs. authentication/networking—being affected by the same problematic update.
Is the emergency patch safe to install immediately?
Yes, the emergency patch (released to address this issue) is safe to install. Out-of-band emergency patches receive more focused testing than monthly updates and only address specific, documented problems. Since this patch was specifically designed to fix the shutdown and RDP issues, installing it immediately if you're affected is the right move. For machines not experiencing these problems, the patch is also safe and beneficial since it includes the stability improvements.
Can I prevent this type of problem from happening to my machine in the future?
No single approach prevents all update-related problems, but several strategies reduce risk. Test updates on a non-critical machine before installing on your main system. Create system image backups regularly so you can recover if updates break something. Join Windows Insider programs cautiously—Dev Channel and Beta builds have more issues. Monitor Windows Update's known issues list before deploying major updates. For organizations, implement phased rollout procedures where updates go to pilot groups first before fleet-wide deployment. These approaches can't eliminate all problems but significantly reduce their impact.
Why does Microsoft keep having update problems if the company has such large testing teams?
Windows' complexity and the diversity of hardware it runs on make complete testing impossible. Microsoft's testing covers the most common configurations but misses rare hardware combinations where problems emerge. Additionally, the company prioritizes update speed for security reasons, which constrains testing time. The fundamental challenge is balancing security (which requires rapid patching) with stability (which requires thorough testing). There's also organizational pressure to ship updates on schedule, which can discourage thorough testing if issues are found late in the cycle.
Should I stay on Windows 10 instead of upgrading to Windows 11 because of update issues?
Windows 10 reached end of support in October 2025, so staying on it long-term requires paying for Extended Security Updates (ESU), which costs $4-6 per device annually. For organizations managing thousands of machines, ESU can be cost-effective compared to dealing with Windows 11 update issues. For individual users or small organizations, upgrading to Windows 11 is still recommended despite update problems—the operating system is fundamentally solid, and this incident was an outlier. The key is managing updates carefully rather than avoiding Windows 11 entirely.
How do I fix the shutdown problem if it happens to my machine before the emergency patch deploys?
If your Windows 11 machine won't shut down properly after the January update and you haven't received the emergency patch yet, try these steps in order. First, open Command Prompt as administrator and execute shutdown /s /t 0, which forces immediate shutdown bypassing normal procedures. If that doesn't work, try disabling fast startup in Power Settings. If still unsuccessful, boot into Safe Mode and attempt shutdown from there. As a last resort, uninstall the problematic update through Windows Update Settings, reboot, and wait for the emergency patch to deploy before reinstalling the update. Keep your system on and check for updates daily until the fix arrives.
Key Takeaways
- A January 2026 Windows security update (KB5073455) broke shutdown functionality on Windows 11 23H2 systems, causing them to restart instead of shutting down properly.
- The bug affected 1-3% of Windows 11 installations globally—potentially millions of devices—and also broke Remote Desktop login capabilities and caused secondary issues like Outlook crashes.
- Microsoft responded with an out-of-band emergency patch within 24-48 hours, demonstrating rapid response infrastructure for critical issues, though the root cause analysis was minimal.
- Users could force shutdown using Command Prompt command 'shutdown /s /t 0' as a temporary workaround, while waiting for the emergency patch or rolling back the problematic update.
- The incident reveals fundamental tensions in Windows update strategy: security requires rapid patching but thorough testing prevents stability issues, and Microsoft must balance both.
- Enterprise organizations face compounded costs from update problems—help desk overhead, productivity loss, and compliance violations—making phased rollout testing critical.
- Defensive strategies like delayed adoption, system image backups, hardware-aware testing, and rollback procedures significantly reduce the impact of problematic updates.
- Windows 11 update incidents continue to accumulate, suggesting core testing and release methodologies need fundamental improvements rather than incremental refinements.
Related Articles
- Windows 11 Update Shutdown Bug: What Happened & How to Fix [2026]
- 5 Major Windows 11 Problems Microsoft Must Fix in 2026
- Windows 10's Legacy: What Microsoft Got Right (and How It Led to Windows 11 Problems) [2025]
- Windows 11 26H1 Update: Why Limited Snapdragon X2 Rollout Might Be Smart [2025]
- Windows 11 Needs to Drop AI Hype and Master the Basics [2025]
- Microsoft Closes Library, Cuts Subscriptions: AI Learning Shift [2025]
![Microsoft's Windows 11 Emergency Fix: Shutdown Crisis Explained [2025]](https://tryrunable.com/blog/microsoft-s-windows-11-emergency-fix-shutdown-crisis-explain/image-1-1768765005933.jpg)



