Critical Microsoft Zero-Days: What You Need to Know Right Now
Microsoft just disclosed something that should make every Windows and Office user sit up and pay attention. They patched a cluster of zero-day vulnerabilities that were already being actively exploited in the wild. These aren't theoretical bugs discovered in a lab somewhere. Real hackers, right now, are using these exploits to break into systems.
Here's what makes this different from typical security updates. These flaws require almost no user sophistication to exploit. Click a link. Open a file. That's it. Your system can be completely compromised.
The vulnerabilities span multiple components of the Windows ecosystem. The Windows shell itself. Microsoft's MSHTML browser engine. Office file handlers. Each one a potential entry point for attackers.
What's particularly concerning is that details about how to exploit these bugs have already been published. Microsoft acknowledged this in their security advisories. When exploit code becomes public, the attack window opens wide. Script kiddies with minimal technical skill can weaponize these flaws. The clock started ticking the moment those details hit the internet.
I've covered security incidents for years. The pattern is always the same. Microsoft patches something. Attackers immediately begin targeting those who haven't updated. The first 48 hours are critical. Organizations that move slowly during that window often wake up to ransomware, data exfiltration, or worse.
This article breaks down exactly what these vulnerabilities are, who's being targeted, why they're dangerous, and what you should do immediately to protect yourself. Because if there's one thing I've learned covering cybersecurity incidents, it's this: zero-days don't stay hidden for long.
Why Zero-Days Matter More Than Regular Bugs
Zero-day vulnerabilities exist in a special category of badness. By definition, they're bugs that vendors don't know about. Attackers found them first. They used them in the wild before Microsoft even had a chance to understand the problem, let alone fix it.
That means there's no preventative patch. No warning sign. No detection signature that security tools can use to block attacks. The attacker has asymmetric advantage. They know about the vulnerability. The defender doesn't.
In this case, that advantage lasted long enough for widespread exploitation to occur. Google's Threat Intelligence Group uncovered what was happening and reported it to Microsoft. But by then, attackers had already struck multiple times.
The fact that exploit details are now public amplifies the danger exponentially. When CVE information includes working proof-of-concept code, every attacker and script kiddie worldwide has the roadmap. Attackers don't need to reverse-engineer anything. They just need to copy and paste.
Understanding CVE-2026-21510: The Windows Shell Bug
Let me break down the first critical vulnerability in terms that actually make sense.
The Windows shell is the interface between you and your operating system. It's how you click icons, open programs, and interact with your files. Think of it as the command center for everything Windows.
CVE-2026-21510 is a flaw in how the Windows shell processes certain types of files and shortcuts. Specifically, it's a vulnerability in the way Windows validates links before executing them.
Microsoft built a safety feature called Smart Screen to protect users from malicious links and files. It's supposed to intercept dangerous content before it reaches your system. Smart Screen checks files and links against a database of known malware. If something looks suspicious, it blocks it.
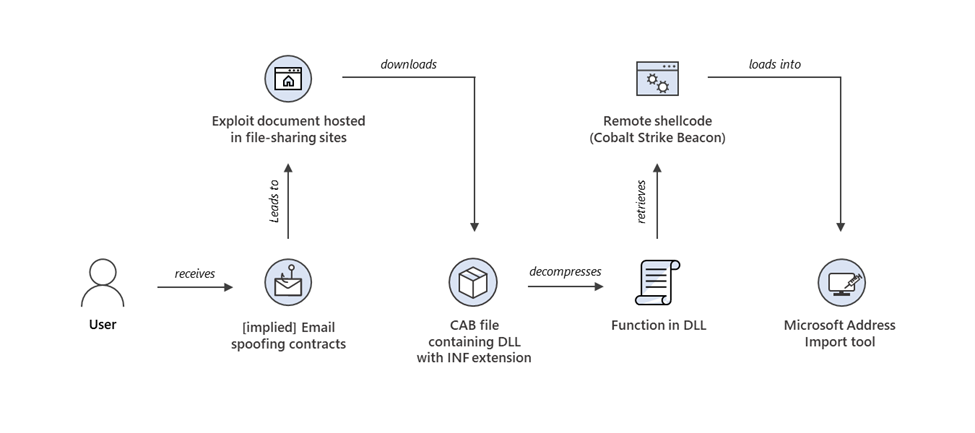
The vulnerability allows attackers to bypass Smart Screen entirely. They craft a malicious link or shortcut file that exploits the shell flaw. When you click it, Windows processes the malicious payload before Smart Screen gets a chance to intervene. By the time Smart Screen checks the file, it's too late. The malware is already running.
According to security expert analysis, this gives attackers the ability to execute code with high privileges. That means they're not running as a limited user account. They're running as system administrator. With that level of access, an attacker can install ransomware, steal data, modify files, create backdoors, or do virtually anything they want with your computer.
The scary part? This requires user interaction, yes, but just barely. You don't need to disable any security features. You don't need to modify system settings. You just click a link that looks legitimate, or open a file that an attacker tricked you into downloading.
Here's the thing: attackers are really good at social engineering. They'll craft emails that seem to come from your boss, your bank, a package delivery service, or someone else you might trust. They'll create links that look legitimate. They'll use compromised websites to serve the malicious files. By the time you realize something's wrong, the damage is done.
The vulnerability affects all supported versions of Windows. That's Windows 11, Windows 10, and Windows Server versions that Microsoft is still updating. No version is safe. No older Windows version is somehow immune. If you're running Windows, you're potentially affected.
CVE-2026-21513: The MSHTML Engine Exploit
Now here's where it gets weird. Microsoft hasn't used Internet Explorer as their default browser since 2015. They switched to Edge years ago. Internet Explorer is dead. Microsoft killed it. It's gone.
Except it's not.
The MSHTML engine that powers Internet Explorer still exists in Windows. It's embedded in newer versions of the operating system for backward compatibility. Old applications still use it. Legacy business software depends on it. Microsoft can't rip it out without breaking thousands of enterprise applications that major organizations depend on.
So MSHTML lives on as a ghost in the machine. A potential attack surface that many people don't even know exists on their systems.
CVE-2026-21513 is a vulnerability in this legacy browser engine. Like CVE-2026-21510, it allows attackers to bypass security features and execute malicious code.
The attack works slightly differently. Rather than exploiting the shell, this vulnerability targets how MSHTML processes certain types of web content. An attacker can craft a malicious webpage or document. When that content is processed by MSHTML, it triggers the vulnerability.
The attacker gains code execution with high privileges. Again, system-level access. Again, the ability to install malware, steal data, or compromise the entire system.
What makes this particularly dangerous is how many legitimate applications still use MSHTML behind the scenes. You might not realize it, but an application you use daily could be processing content through this engine. An attacker could compromise you through that application without you ever knowing the vulnerability even existed.
The Office File Vulnerability
According to reporting from independent security researchers, Microsoft also patched another zero-day affecting Office files.
Office documents are everywhere in the enterprise world. Microsoft Word, Excel, Power Point. Billions of people use these tools every day. Documents get shared constantly through email, cloud storage, messaging apps.
The Office vulnerability allows attackers to exploit the way these applications process certain file content. An attacker creates a malicious Word document, Excel spreadsheet, or Power Point presentation. They send it to you via email or trick you into downloading it.
You open the file. Nothing seems unusual. The document looks normal. But in the background, the Office application is processing embedded content that exploits the vulnerability. Malicious code executes. Your system is compromised.
Office macro attacks have been a vector for years. But this is different. This vulnerability doesn't require macros to be enabled. It doesn't require you to click a warning dialog. It doesn't require you to dismiss any security prompts. Just opening the file is enough.
The Threat Landscape: Who's Getting Targeted?
Zero-day exploits typically follow a pattern. First, they're used by sophisticated threat actors against high-value targets. Governments target governments. Criminal syndicates target enterprises with money. Competitors engage in espionage.
Then public disclosure happens. Either the vendor finds out through their own researchers or external researchers report it. Exploit code gets released. Suddenly these tools are available to everyone.
That's when the targeting broadens dramatically.
Initially, the organizations hit by these particular Microsoft vulnerabilities included government agencies and enterprises in critical sectors. The type of targets you'd expect zero-day developers to focus on: high-value, resource-rich organizations where the investment in developing exploits makes sense.
But once exploit details became public, the attack surface expanded massively. Now, every organization and individual becomes a potential target.
Small businesses don't think they're targets for sophisticated attacks. That's a mistake. Threat actors compromise small businesses to use them as stepping stones into larger enterprises. They steal credential data. They install backdoors for later use. They gather information for follow-up attacks.
Individuals think they're not targets either. Also a mistake. Your computer might be compromised and used to send spam, participate in botnets, or compromise other systems. Your data might be stolen for identity fraud. Your computing power might be rented out to cybercriminals.
Remote workers are particularly vulnerable. If you're working from home and using a personal computer or an unpatched corporate machine, your risk is elevated. Home networks often lack the security controls that corporate networks have. An infected home computer can compromise your employer's network.
Why Exploitation Was Widespread
The fact that these vulnerabilities reached active exploitation stage before Microsoft knew about them suggests sophisticated adversaries were hunting for them deliberately.
Zero-days don't come from nowhere. Attackers either discover them through fuzzing, code analysis, or other vulnerability research techniques. Or they purchase them from brokers who specialize in finding and selling exploits.
The exploit market is real. Vulnerability researchers sometimes sell zero-days to brokers rather than reporting them responsibly to vendors. These brokers then sell them to governments, criminal organizations, and other buyers. A critical Windows vulnerability might sell for anywhere from tens of thousands to millions of dollars, depending on the buyer and the specifics of the flaw.
In this case, by the time Microsoft became aware through Google's Threat Intelligence Group, attackers had already deployed these exploits in the wild. Google and Microsoft have a coordinated disclosure policy. When Google finds a critical zero-day in Microsoft software, they report it immediately.
But the damage was already done. Active exploitation had already occurred. That's why Microsoft classified these as actively exploited zero-days rather than theoretical vulnerabilities.

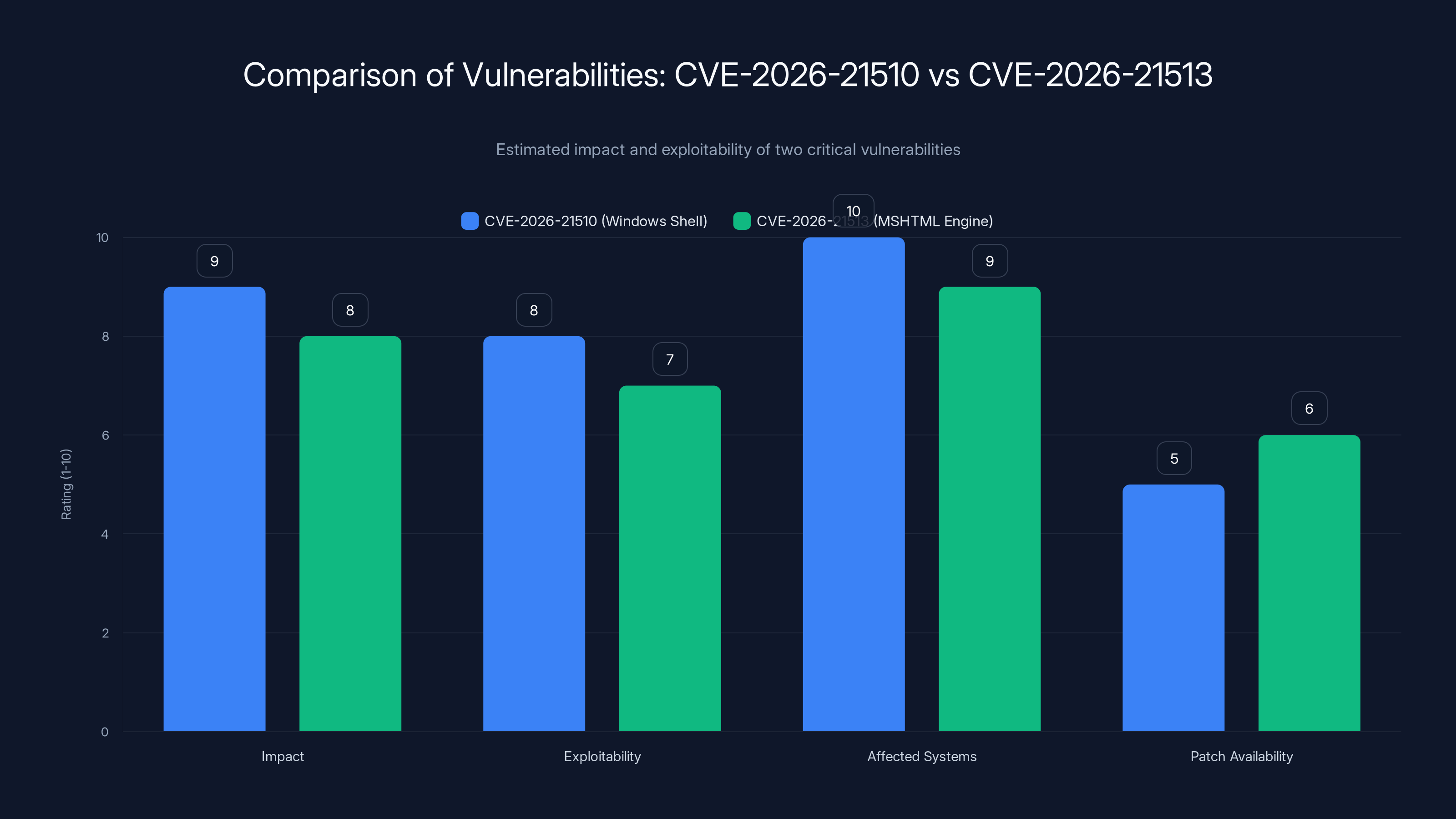
CVE-2026-21510 has a slightly higher impact and exploitability compared to CVE-2026-21513, affecting all Windows versions. Estimated data.
The Privilege Escalation Problem
One detail that security experts emphasized was the ability for attackers to gain high-privilege access immediately.
Typically, when an attacker exploits a vulnerability, they gain code execution in a limited context. They might run code as the currently logged-in user, which has certain restrictions. Operating systems limit what any single user account can do. You can't delete other users' files. You can't modify system settings. You can't install drivers.
But if an attacker escalates to administrator or system privileges, those restrictions vanish. They become all-powerful within the operating system.
These Microsoft vulnerabilities allowed exactly that. An attacker with user-level privileges could immediately escalate to system privileges. No additional steps needed. No second exploit required. One click, one vulnerability, system compromise.
That's the difference between an annoying intrusion and a catastrophic breach.
With system-level access, an attacker can do anything. Install rootkits that hide from antivirus software. Deploy ransomware that encrypts every file on your drives. Steal encryption keys and passwords stored on your system. Install keyloggers to capture everything you type. Modify Windows system files. Create persistent backdoors that survive reboots.
Security specialists call this the "game over" moment. Once an attacker has system-level access, detecting and removing them becomes extremely difficult. You're usually better off completely wiping the system and restoring from backups, assuming you have backups.
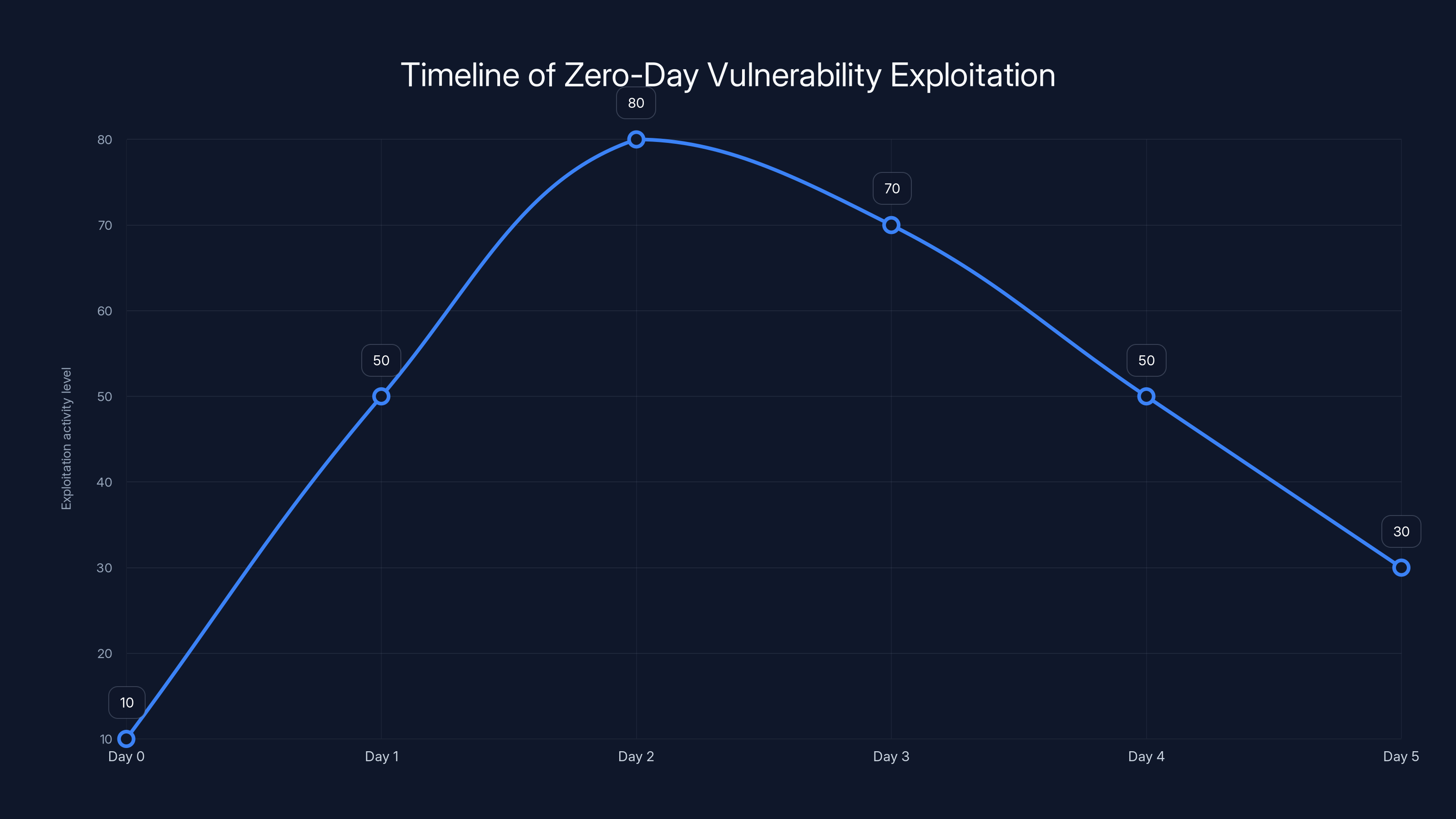
Exploitation activity typically spikes immediately after zero-day disclosure, peaking within the first 48 hours. Estimated data based on historical patterns.
Patch Management: The Critical Response
Microsoft released patches for these vulnerabilities as part of their regular monthly update cycle. But in security incidents like this, the regular update schedule is too slow.
They pushed out patches with high priority designations. Security advisories flagged them as critical. The messaging was clear: update immediately, don't wait.
This creates a real tension in enterprise environments. IT departments have to balance security with stability. Rapid patching can introduce unforeseen compatibility issues. Applications might break. Systems might become unstable. Organizations sometimes test patches thoroughly before deploying them widely.
With zero-days, there's no time for extensive testing. The vulnerability is actively being exploited. Every hour you don't patch is an hour an attacker could be compromising your systems. The risk of running unpatched systems exceeds the risk of potential compatibility issues from the patch.
For critical zero-days, security best practices recommend patching within 24-48 hours. Some organizations even establish emergency patching procedures for high-severity vulnerabilities, bypassing their normal testing phases.
Patching Windows Versus Office
Patching Windows itself requires a system restart in many cases. That's disruptive in enterprise environments. Servers might need scheduled downtime. User computers need coordination if you're managing multiple machines.
Patching Office is typically less disruptive. Office updates don't always require restarts. You can apply them while systems are in use in some cases.
But both need to happen. Both are critical. Ignoring either one leaves you vulnerable.
The challenge for security teams is communicating this to non-technical users. "You need to restart your computer for critical security updates" is a message people often ignore or delay. They're in the middle of work. Restarting is inconvenient. They'll do it later.
Later might be too late if they encounter an exploit in the meantime.
Broader Implications: The Vulnerability Ecosystem
These Microsoft zero-days are part of a larger pattern that's concerning security researchers.
Vulnerability discovery rates are increasing. The number of zero-days being found is growing faster than vendors can patch them. More sophisticated attackers mean more people hunting for flaws. Better tools for vulnerability research mean finding bugs is easier than ever.
At the same time, patch deployment is often slow. Organizations struggle with testing, compatibility verification, and deployment across their infrastructure. The gap between vulnerability discovery and patch deployment is widening.
That gap is where attackers operate. That's where the exploitation happens. That's where the damage occurs.
Microsoft is massive. Billions of systems run Windows. Billions run Office. Even if 90% of users patch immediately, that leaves millions of systems vulnerable. And many organizations patch much slower than 90% compliance.
The exploit economics work like this: if even a small percentage of targeted systems remain unpatched, attackers can compromise large numbers of machines. A 10% compromise rate across millions of systems means hundreds of thousands of compromised machines. Each one potentially used for follow-up attacks, data theft, or other malicious purposes.
Why Public Exploit Details Are Problematic
When Microsoft disclosed these vulnerabilities, they had to explain enough about the flaws for organizations to understand the severity and deploy patches correctly. But those same explanations served as blueprints for attackers.
In an ideal world, vulnerability details would remain secret until patches are widely deployed. But that's impossible at scale. Too many people need to know. Security researchers need to understand the problem. IT administrators need to know what they're patching. News organizations report on significant security issues.
Once information is public, determined attackers can use it to develop exploits if they don't already have them. Security researchers can create proof-of-concept code to demonstrate the vulnerability. That code sometimes gets published online intentionally or accidentally.
Public exploit code accelerates weaponization dramatically. Script kiddies and unsophisticated attackers who couldn't develop exploits themselves suddenly have fully functional tools they can deploy.
Security researchers debate whether publishing exploit code is ethical. Some argue it's necessary for raising awareness and encouraging patching. Others argue it just speeds up weaponization and increases harm.
In practice, exploit code almost always gets published eventually. The question is whether it happens at an academic conference, a security blog, a darknet forum, or somewhere else. Once it's anywhere on the internet, assume it will be found and used.
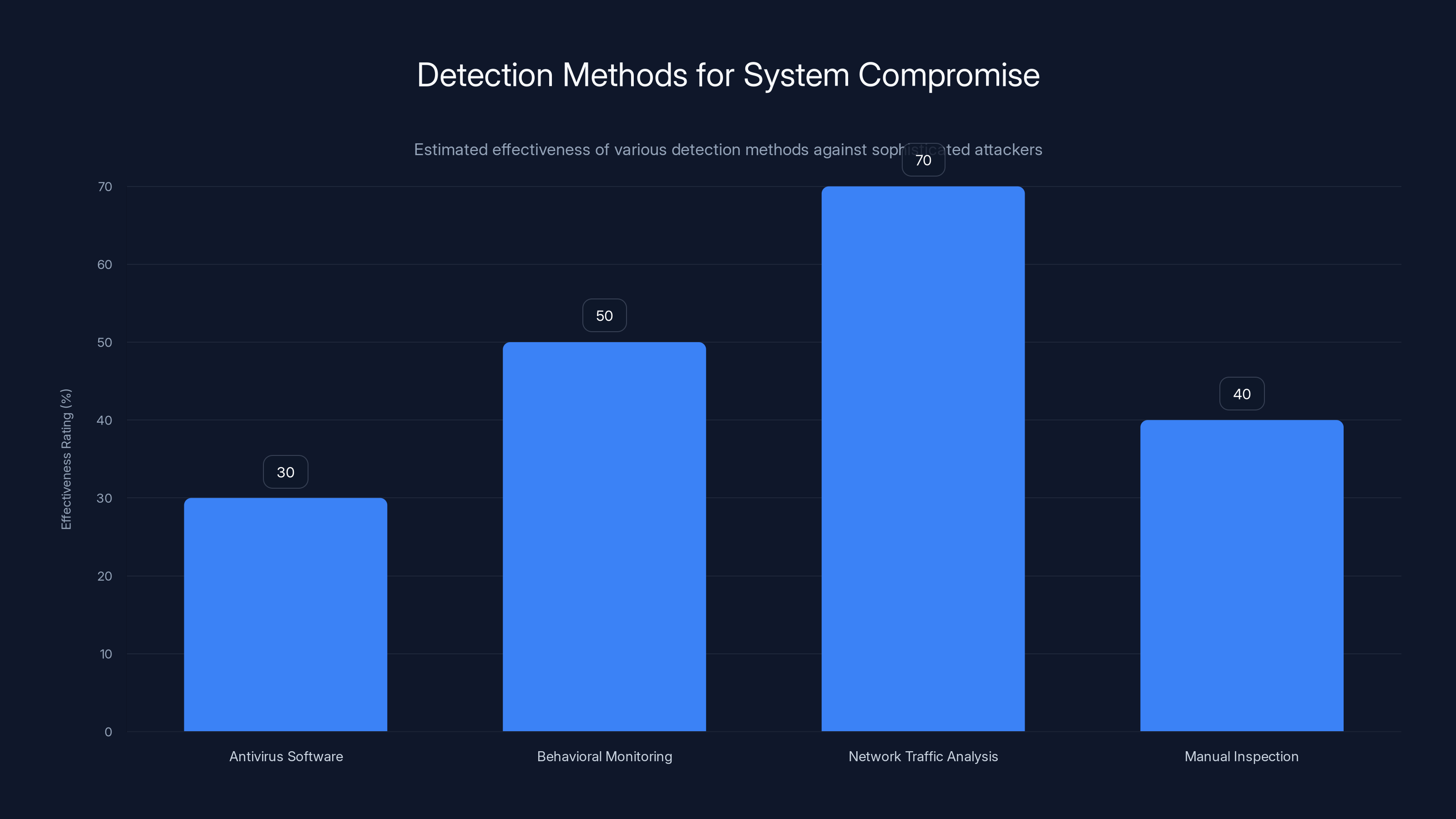
Estimated data shows that network traffic analysis is the most effective method for detecting sophisticated attackers, while antivirus software is the least effective.
Detection and Response: Can You Tell If You're Compromised?
This is where many organizations face a harsh reality. Detecting exploitation of these vulnerabilities is difficult.
If an exploit executes successfully, the attacker gains system-level access. At that point, they have the ability to hide their presence. They can disable security monitoring. They can modify log files. They can install rootkits that hide from detection.
A skilled attacker with system-level access can operate on a compromised system for months or years without being detected. They move slowly. They don't scan for valuable data aggressively. They hide their presence carefully.
Unsophisticated attackers, on the other hand, often leave obvious traces. They run malware that creates network traffic. They exfiltrate large amounts of data quickly. They encrypt files with ransomware that announces itself with ransom notes.
For the average user, detection is nearly impossible without external security tools. Antivirus software might catch some threats, but a sophisticated attacker can evade it. Behavioral monitoring tools might flag unusual activity, but false positives are common.
This is why prevention is so critical. It's much easier to prevent a compromise than to detect and remediate one after the fact.
Incident Response Considerations
If an organization suspects they've been compromised through one of these vulnerabilities, the response is complex.
First, isolate affected systems from the network. Disconnect them from the internet and from other computers. This prevents the attacker from accessing other systems through the compromised machine.
Next, preserve evidence. Security teams need to capture memory dumps, hard drive images, and log files for forensic analysis. You need to determine what the attacker accessed, what data they stole, and what persistence mechanisms they installed.
Then, remove the attacker. Delete malware. Close backdoors. Remove stolen credentials from systems where they might be used.
Finally, rebuild. Sometimes the safest option is to completely wipe affected systems and restore them from known-clean backups. If you don't have backups, you'll need to rebuild the system from scratch and restore data from an external source.
This process can take weeks or months for large breaches. It's expensive. It's disruptive. And it's why prevention through timely patching is so important.

Immediate Actions You Should Take Today
Let me give you the concrete steps you need to take right now. Not tomorrow. Not when you have time. Now.
1. Check Your Windows Version
First, verify what version of Windows you're running. Press Windows Key + Pause/Break or right-click This PC and select Properties.
You need to know if you're on Windows 11, Windows 10, or Windows Server. Both are affected by CVE-2026-21510. If you're running older versions of Windows, they're not getting security updates anymore, which means you're perpetually vulnerable to known exploits.
If you're on Windows 7 or older, you should be planning an upgrade urgently. Microsoft stopped supporting those versions years ago. They receive no security updates whatsoever.
2. Install Windows Updates Immediately
Go to Settings > Update & Security > Windows Update. Click "Check for updates."
If updates are available, install them immediately. If your system requires a restart, save your work and restart. Don't delay this. Don't postpone it until you "have time."
For those on Windows Pro or Enterprise, check your update status through your organization's IT department. Corporate systems might have centralized update management. Make sure your administrators know about the critical nature of these patches.
3. Update Office
Open any Office application. Go to File > Account > Update Options > Update Now.
Office should download and install the latest version automatically. Some Office versions allow you to install updates without restarting immediately, but you'll eventually need to restart to complete the installation.
If you're using Office 365 or Microsoft 365, updates should happen automatically in the background. Verify that you're on the latest version by checking the version number in File > Account.
4. Run Windows Defender or Your Security Software
Assuming you have antivirus software installed, run a full system scan. Windows Defender is built into Windows 11 and is actually quite good these days.
Go to Settings > Privacy & Security > Virus & threat protection > Scan options. Select Full scan and run it.
This will take time, possibly hours, depending on how much data is on your system. But if you've been compromised before now, this scan might catch the malware.
5. Change Your Passwords
If you've been compromised, an attacker might have stolen your passwords. Change the passwords for critical accounts: email, banking, cloud storage, social media.
Change them from a different, known-clean device if possible. Don't change them from the potentially compromised computer.
Enable multi-factor authentication (MFA) on all important accounts. This adds an extra layer of protection even if your passwords are compromised.
6. Monitor Your Accounts
For the next few months, watch your email, banking, and credit accounts carefully. Look for unusual activity, unauthorized charges, or suspicious logins.
Consider placing a fraud alert on your credit reports. Contact Equifax, Experian, and Trans Union. A fraud alert makes it harder for someone to open accounts in your name.
7. Backup Your Data
Once you've patched everything, make sure you have current backups. If you ever do get compromised in the future, you'll want to restore from a known-clean backup rather than trying to remove malware.
Use both local backups (external drive) and cloud backups (One Drive, Google Drive, etc.). Local backups are faster to restore from. Cloud backups protect against physical disasters like house fires or theft.

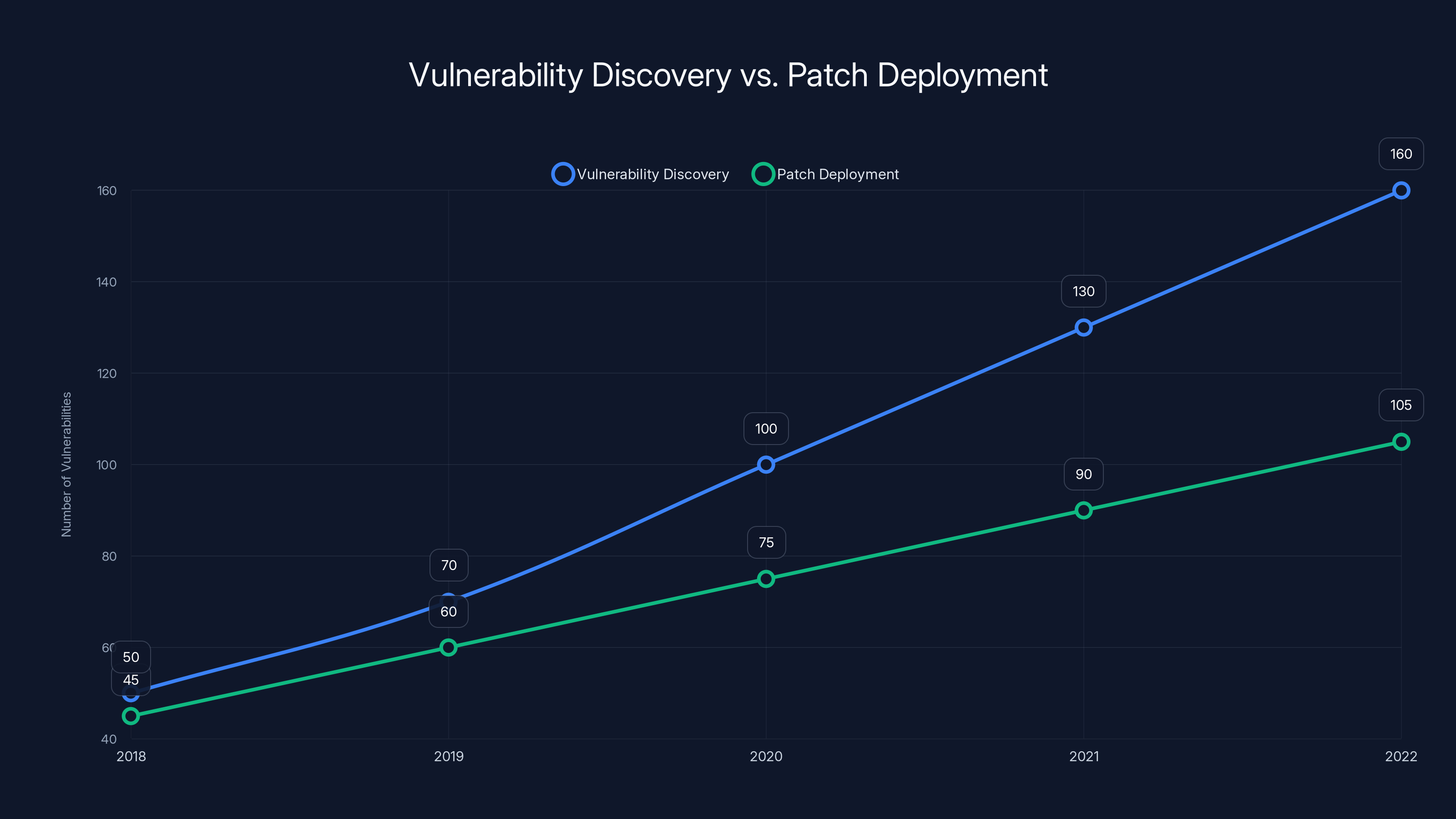
The gap between vulnerability discovery and patch deployment is widening, with discovery rates increasing faster than deployment. Estimated data.
For IT Professionals: Enterprise Deployment Strategies
If you're managing systems in an organization, this situation requires accelerated patching procedures.
Prioritization Framework
Start by prioritizing what to patch first. Internet-facing systems should be patched before internal-only systems. Critical systems that would cause business disruption if compromised should be patched before lower-risk systems.
Servers that face the internet directly are highest priority. Then servers that handle sensitive data. Then user workstations that access sensitive systems.
Testing and Validation
Normally, you might test patches in a staging environment for weeks. With critical zero-days, compressed timelines are necessary.
Test the patch on a small subset of systems first, if you can. Verify that critical applications still work. Confirm that no obvious compatibility issues exist. Then deploy more widely.
For truly mission-critical systems where testing is impossible, you might need to deploy the patch anyway and monitor closely for issues. The risk of exploitation outweighs the risk of compatibility issues in these cases.
Deployment Methods
Use whatever update mechanism you have available. Windows Update for Business. WSUS (Windows Server Update Services). MDM (Mobile Device Management) tools. Intune. Third-party patch management tools.
For remote workers, ensure your update mechanisms work over VPN connections. Some patch management systems struggle with distributed remote workforces.
Communicate with users about the importance of applying updates and restarting their systems. Make it easy for them by scheduling restarts for non-business hours if possible.
Monitoring and Verification
After patching, verify that the patch was actually applied. Don't assume it was. Check patch status across your systems. Some machines might have failed to patch due to connectivity issues, conflicts with other software, or other problems.
Monitor for exploit attempts even after patching. Update your intrusion detection and intrusion prevention systems with signatures for attempts to exploit CVE-2026-21510, CVE-2026-21513, and the Office vulnerability.
Watch for unusual process execution, unexpected network connections, or signs of privilege escalation.
Incident Response Preparation
Have an incident response plan ready. If you detect exploitation, your response team needs to know:
Who's involved in the response (security, IT, management, legal, PR)? What's the escalation procedure? Who communicates with leadership? Who contacts law enforcement if needed? What's your data breach notification procedure? Who contacts affected customers?
Run a tabletop exercise to practice your response procedure. Test your backups to make sure they actually work. You don't want to discover during an actual incident that your backups are corrupted or incomplete.

The Broader Security Posture: Beyond These Specific Vulnerabilities
These Microsoft zero-days highlight a reality that goes beyond these three specific vulnerabilities.
Your systems are always under attack. Attackers are always looking for flaws. New vulnerabilities are discovered constantly. The only question is whether you're ahead of the problem or behind it.
Security is a process, not a state. It's not something you achieve and then stop working on. It's ongoing.
The Principle of Defense in Depth
Don't rely on patching alone. Multiple layers of security make it harder for attackers to succeed.
Start with patching and keeping software current. That's the foundation.
Add antivirus and anti-malware tools. They won't catch everything, but they'll catch many obvious threats.
Implement firewalls. Network firewalls at the organization level. Personal firewalls on individual systems. Firewalls segment your network and reduce lateral movement by attackers.
Use intrusion detection and prevention systems that monitor for attacks. These systems look for suspicious network traffic and can block known attack patterns.
Implement email security tools that scan incoming emails for malware and phishing attempts. Most attacks start with email, so focusing security effort there pays dividends.
Use endpoint detection and response (EDR) tools that monitor system behavior and can alert on suspicious activity. These are more sophisticated than traditional antivirus and catch more sophisticated threats.
Enable multi-factor authentication everywhere it's available. Even if an attacker steals your passwords, they can't access your accounts without the second factor.
Maintain offline backups. If ransomware encrypts your systems, you can restore from backups that the attacker can't access.
Segregate your network. Keep sensitive systems on a separate network segment from general-purpose systems. If one segment is compromised, the other might still be safe.
Limit user permissions. Not every user needs administrative access. Run as a standard user by default. Use administrative access only when necessary.
The Human Element
Technology helps, but humans are often the weak link.
Security awareness training is essential. Employees need to understand phishing attacks, social engineering, and basic security practices. They need to know why they shouldn't click random links or open unexpected attachments.
But training alone isn't enough. You need to test it. Send fake phishing emails internally. See who clicks them. Provide additional training to those who fall for it.
Create a culture where security is valued. Make it easy to report suspicious activity. Don't penalize people for reporting a potential phishing email they're unsure about.
Make passwords a priority. Weak passwords are one of the biggest security vulnerabilities. Enforce strong password policies. Consider moving toward passkeys and other passwordless authentication methods.

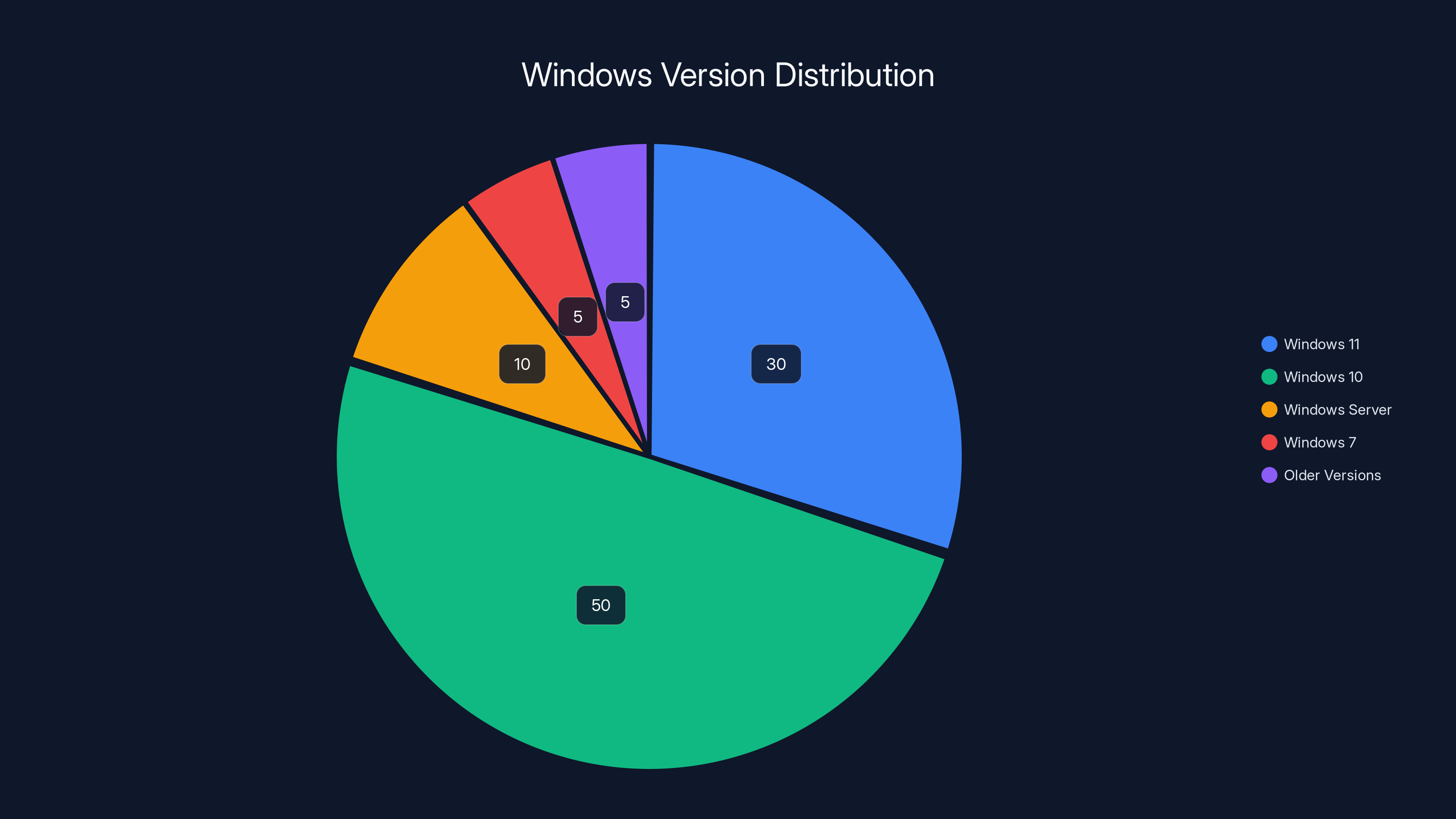
Estimated data shows that Windows 10 is the most widely used version, followed by Windows 11. Older versions like Windows 7 and earlier are less common but still present, highlighting the need for urgent upgrades.
The Patch Management Timeline: What Gets Patched When
Microsoft's patch cycle is interesting to understand because it affects when you get security fixes.
Microsoft releases major patches on the second Tuesday of each month, called "Patch Tuesday." That's the main cycle. You can expect critical updates to arrive on that day.
For emergency situations, Microsoft sometimes releases out-of-band patches outside the normal cycle. These are typically for exploited zero-days or critical vulnerabilities actively causing harm.
Security updates get installed differently depending on your Windows version and settings. Enterprise systems might have staged deployments, testing patches on some systems before deploying to all systems.
Home users with automatic updates enabled should get patches automatically, ideally within a few days of release.
But not everyone has automatic updates enabled. Some people disable them to avoid unexpected reboots disrupting their work. This leaves them vulnerable for extended periods.
The ideal scenario is: patch released, patch tested and validated, patch deployed organization-wide or installed on user systems within 48 hours. That timeline prevents most active exploitation.
In practice, timelines are often longer, which is why these zero-days cause damage even after patches are available.

Supply Chain Attacks: The Hidden Risk
These vulnerabilities exist in software that millions of organizations use. That makes them particularly valuable to attackers.
Imagine you're a nation-state or advanced cybercriminal. You want to compromise as many targets as possible. You could try to break into each one individually, which would take forever and require lots of resources.
Or you could exploit a vulnerability in software that everyone uses. Then you compromise the systems that matter to you.
These Microsoft vulnerabilities are exactly that kind of opportunity. They're in software used by governments, financial institutions, utilities, hospitals, schools, and private companies.
An attacker who successfully exploits these vulnerabilities on a government network might steal classified information. An attacker who exploits them on a financial institution might steal money or customer data. An attacker who exploits them on a utility might disrupt power or water supply.
This is why these vulnerabilities matter at a national security level. They're not just a nuisance for home users. They're a critical security risk for infrastructure and institutions.
Governments take these vulnerabilities seriously. The U. S. Cybersecurity and Infrastructure Security Agency (CISA) has likely published guidance on patching these vulnerabilities. They might recommend that critical infrastructure organizations patch within specific timeframes.
The Privilege of Early Patching
For organizations with IT security resources, being able to patch quickly is a major advantage.
Large enterprises have dedicated security teams, patch management infrastructure, and testing capabilities. They can deploy patches relatively quickly.
Small businesses often don't have these resources. They might have a single IT person managing everything. Patching becomes one of many tasks competing for attention.
Individuals often don't patch at all, or patch very slowly, unless they're reminded or unless their devices force updates.
This disparity means vulnerable systems exist on a spectrum. The most well-resourced organizations might be patched within hours. Mid-sized organizations within days. Small organizations and individuals within weeks or months.
For attackers, this is perfect. They can compromise the lower-risk, slower-patching targets first. Then they can use those compromised systems to target more important systems.

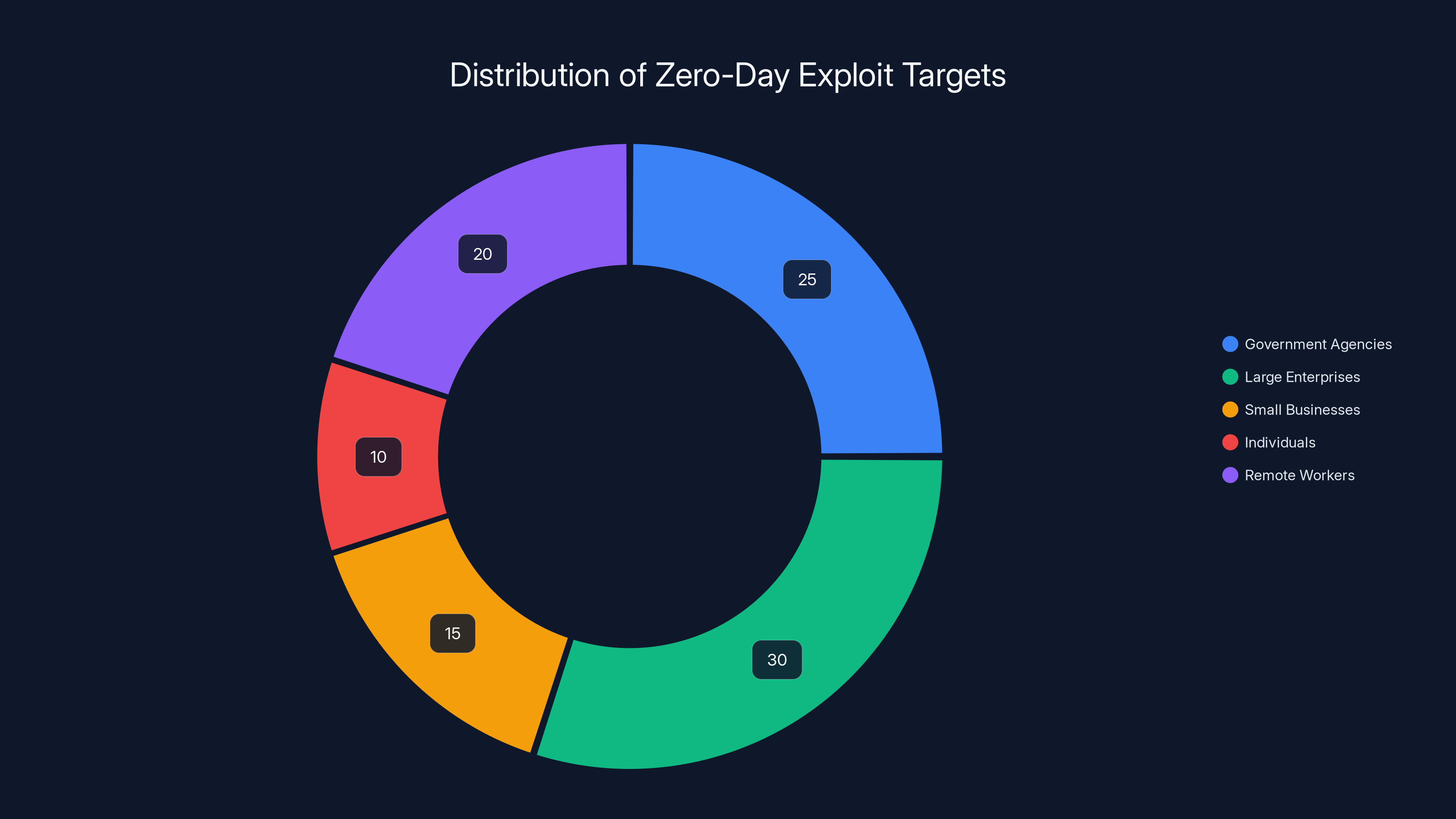
Initially, zero-day exploits target high-value entities like governments and large enterprises. Once public, the attack surface broadens to include small businesses, individuals, and remote workers. (Estimated data)
Future Outlook: Vulnerability Trends and What's Coming
These Microsoft zero-days are part of larger trends in cybersecurity.
Vulnerability discovery is accelerating. AI-powered vulnerability research tools are getting better at finding bugs automatically. More researchers are hunting for flaws. The annual number of CVEs (Common Vulnerabilities and Exposures) published has been increasing for years.
At the same time, the complexity of software is increasing. Modern software is huge. Windows is tens of millions of lines of code. Office is similarly enormous. More code means more opportunities for bugs.
The attack surface is expanding. Computers are more connected than ever. Cloud computing introduces new vulnerabilities. Io T devices have security nightmares. Mobile devices have their own vulnerabilities.
Threats are becoming more sophisticated. Ransomware as a service has industrialized attacks. Cryptominers are hijacking compute resources. Nation-states are conducting cyber warfare.
Meanwhile, patch deployment timelines aren't improving. Organizations still struggle to patch quickly. Users still ignore security warnings. The gap between vulnerability disclosure and patch deployment isn't shrinking.
This mismatch is the problem. Vulnerabilities are being discovered faster than they're being patched. Exploits are being developed faster than they're being detected and blocked. The pace of offensive security is outpacing the pace of defensive security.
AI and Vulnerability Research
Artificial intelligence is starting to play a role in vulnerability research. AI tools can analyze code, identify unusual patterns, and flag potential security issues.
This technology works both ways. Security researchers can use AI to find vulnerabilities so they can be patched. Attackers can use AI to find vulnerabilities so they can be exploited.
In the short term, this likely means more vulnerabilities will be discovered. Whether they're discovered by defenders or attackers remains to be seen.
Long term, this could fundamentally change the game. If AI can systematically find and classify vulnerabilities, it might finally shift the balance from attackers finding exploits to defenders finding and patching them first.
But we're not there yet. For now, we're in a world where vulnerabilities are abundant, patches take time, and attackers are winning.

Conclusion: Patches Save Lives (Digital Lives, Anyway)
Let me be direct. If you haven't patched your systems since reading this article, stop and go patch them now. I'll wait.
Seriously. This isn't alarmism. This isn't exaggeration. These are real vulnerabilities being actively exploited by real attackers. Patching is free. It takes minutes. The consequences of not patching can be catastrophic.
For organizations, make patching a priority. Yes, testing is important. Yes, compatibility issues are possible. But the risk of exploitation outweighs those concerns. Get these patches deployed. Get them deployed in the next few days. Make it non-negotiable.
For IT professionals, this is your moment. This is when security matters most. When vulnerabilities are actively being exploited and patches are available, your speed and execution determine whether your organization gets compromised or stays safe.
For everyone else, just patch. Enable automatic updates. Let your systems install security updates without waiting for your permission. Restart when your computer tells you to. This simple habit prevents most attacks.
The Microsoft zero-day situation is a reminder that security is never finished. There's no "set it and forget it" solution. Attackers are constantly looking for flaws. Vendors are constantly finding and fixing them. Your job is to stay ahead of the problem.
These particular vulnerabilities won't matter in a few months when most systems are patched. But other vulnerabilities will be discovered. Other exploits will be developed. The cycle continues.
But if you patch these, you'll be safe from this threat. That's worth a few minutes of your time. That's worth the system restart. That's worth prioritizing in your organization.
Security isn't complicated. It's unglamorous. It's boring. But it's essential. And right now, it means patching these Microsoft vulnerabilities.
Do it today. Not tomorrow. Today.
FAQ
What exactly is CVE-2026-21510?
CVE-2026-21510 is a critical vulnerability in the Windows shell component that allows attackers to bypass Microsoft's Smart Screen security feature and execute malicious code with high privilege levels. The flaw affects all supported versions of Windows and can be exploited through malicious links or shortcut files that users click on. When exploited, it gives attackers the ability to remotely execute code as a system administrator, potentially leading to complete system compromise, ransomware deployment, or data theft.
How does the MSHTML engine vulnerability (CVE-2026-21513) work differently from the Windows shell vulnerability?
While CVE-2026-21510 targets the Windows shell and exploits file handling, CVE-2026-21513 targets the legacy MSHTML browser engine that powers Internet Explorer and is still embedded in Windows for backward compatibility. This vulnerability allows attackers to craft malicious web content that, when processed by MSHTML, triggers code execution. The danger is that many applications still use MSHTML behind the scenes, meaning users could be compromised through applications they use daily without realizing the vulnerability exists.
What does "zero-day" actually mean, and why is it more dangerous than regular security vulnerabilities?
A zero-day vulnerability is a security flaw unknown to the software vendor that attackers are actively exploiting in the wild. It's called "zero-day" because the vendor has had zero days to develop and release a patch. These are more dangerous than regular vulnerabilities because there's no preventative patch available, no detection signatures in security tools, and attackers have a complete information advantage. Once patches are released and widely deployed, zero-day status is lost, but the exploitation window before that happens can cause significant damage.
Should I prioritize patching Windows or Office first if I can only do one?
Patch both immediately, but if you absolutely must prioritize, patch Windows first, specifically the Windows shell vulnerability (CVE-2026-21510), as it allows exploitation through simple link clicking with no additional user action beyond that. Office vulnerabilities still require opening a document, which adds a minor friction point. However, don't delay the Office patch—deploy both patches within 24-48 hours. In enterprise environments, try to deploy both simultaneously through your patch management systems.
How can I tell if my system has already been compromised by one of these exploits?
Detecting a successful compromise is difficult. If an attacker gained system-level access, they could disable security monitoring and hide their presence using rootkits. For average users, detection without external security tools is nearly impossible. Your best approach is prevention through immediate patching. After patching, run a full system scan with your antivirus software, change passwords on critical accounts, enable multi-factor authentication, and monitor your accounts for unusual activity over the following months. If you work in an organization with EDR (Endpoint Detection and Response) tools, your security team should be monitoring for exploit attempts.
Is Windows 11 safer than Windows 10 against these vulnerabilities?
Both Windows 11 and Windows 10 are affected by CVE-2026-21510 and CVE-2026-21513. Neither version is inherently safer against these specific exploits. Both require patches to protect against them. However, Windows 11 does have some architectural improvements and security enhancements compared to Windows 10, such as mandatory Secure Boot and stricter memory protections that make exploitation more difficult in some cases. But that doesn't protect against these specific zero-days—patching is equally critical for both versions.
Should I disable MSHTML if it's causing security problems?
Disabling MSHTML would break backward compatibility with legacy applications that depend on it, which would cause significant disruption in enterprise environments and for home users running older business software. The better approach is to keep MSHTML updated with security patches. If you have applications that absolutely require MSHTML, ensure they're always kept current. If possible, consider migrating away from applications that require legacy components, but do this strategically over time, not as an emergency response.
What should organizations do if they suspect they've already been compromised through one of these vulnerabilities?
Organizations should immediately isolate affected systems from the network to prevent the attacker from accessing other systems. Preserve evidence by capturing memory dumps, hard drive images, and log files for forensic analysis. Bring in incident response specialists or hire a third-party forensics firm to investigate. Determine what data was accessed, what persistence mechanisms were installed, and what damage occurred. Remove the attacker by deleting malware and closing backdoors. Finally, rebuild systems from scratch or restore from known-clean backups. Notify affected parties if data was compromised, comply with data breach notification laws, and file a report with law enforcement if appropriate.
How can small businesses without dedicated IT staff handle patching these critical vulnerabilities?
Small businesses should enable automatic updates on all Windows systems, Office installations, and other software. Set automatic restarts to occur during off-hours when they won't disrupt business. Consider using patch management tools designed for small organizations, such as Microsoft's Windows Update for Business or third-party solutions like N-able or Kaseya. If budget allows, hire a managed IT services provider (MSP) to handle patch management, monitoring, and security. At minimum, designate one person to check for updates weekly and ensure critical patches are deployed promptly. For Office 365 or Microsoft 365 subscriptions, most updates happen automatically in the background.
Will these specific vulnerabilities be exploited indefinitely, or will attackers move on to new exploits?
Once a significant percentage of systems are patched, exploitation of these specific vulnerabilities will decline sharply, because the remaining vulnerable systems become a smaller and smaller target pool. Attackers are economically rational—if 90% of potential targets are patched, it's not worth continuing to target these specific flaws. However, attackers will immediately shift their focus to other known vulnerabilities and will continue hunting for new zero-days. The vulnerability landscape is constantly changing. These specific flaws matter urgently right now, but in a few months, other vulnerabilities will take their place as the critical focus.
What's the long-term solution to the zero-day problem?
There's no perfect solution, but researchers and vendors are working on several approaches. Memory-safe programming languages reduce entire classes of vulnerabilities by eliminating buffer overflows and similar flaws. Formal verification mathematically proves code correctness in critical components. Fuzzing and automated testing find vulnerabilities before release. Increased investment in security research shifts the balance toward defenders. Bug bounty programs incentivize responsible disclosure. Ultimately, the long-term solution requires software vendors to prioritize security as heavily as features, organizations to invest in security infrastructure and expertise, and users to practice good security hygiene. All three components are necessary—focusing on just one isn't sufficient.

Key Takeaways
- CVE-2026-21510 and CVE-2026-21513 are critical zero-day vulnerabilities actively exploited in Windows and Office; patching is urgent and non-negotiable
- These exploits enable attackers to gain system-level privilege escalation from a single user click, allowing complete system compromise and ransomware deployment
- Public exploit details accelerate weaponization dramatically; unpatched systems face exponentially higher risk in the weeks following vulnerability disclosure
- Defense-in-depth strategy combining patching, antivirus, firewalls, EDR monitoring, MFA, and offline backups significantly reduces breach likelihood and impact
- Organizations that delay patching beyond 48 hours put themselves at severe risk; enterprise patch management procedures should prioritize zero-day response over normal testing timelines
Related Articles
- SmarterTools Ransomware Breach: How One Unpatched VM Compromised Everything [2025]
- Windows 11 26H1: The Exclusive Arm PC Release Changing Windows Updates [2025]
- Apple iOS 26.3 Update: Complete Guide to All Device Changes [2025]
- Trenchant Exploit Sale to Russian Broker: How a Defense Contractor Employee Sold Hacking Tools [2025]
- NordVPN Complete Plan 70% Off: Full Deal Breakdown [2025]
- Surfshark's Free VPN for Journalists: Protecting 100+ Media Outlets [2025]
![Microsoft Zero-Day Exploits: Critical Windows & Office Vulnerabilities [2025]](https://tryrunable.com/blog/microsoft-zero-day-exploits-critical-windows-office-vulnerab/image-1-1770844023588.jpg)



