Smarter Tools Ransomware Breach: How One Unpatched VM Compromised Everything [2025]
Introduction: The $47K Mistake Nobody Saw Coming
Last January, Derek Curtis, Chief Commercial Officer at Smarter Tools, had to make a phone call nobody wants to make. The company—a legitimate enterprise software provider trusted by businesses worldwide—had been hit with ransomware. But here's the thing that should keep security teams awake at night: this entire breach happened because of a single forgotten server.
Not a zero-day exploit. Not a sophisticated APT operation. Not even a particularly clever social engineering attack. One VM running outdated software. That's all it took.
When Curtis published the breach notification, he laid it all out with painful honesty. Out of approximately 30 Smarter Mail servers scattered across their network, one had been set up by an employee and simply... forgotten. It wasn't included in patch management systems. Nobody was updating it. It sat there like an open door while attackers walked right through.
The vulnerability they exploited was CVE-2026-23760, an authentication bypass flaw in Smarter Mail that lets attackers reset administrator passwords and grab full system privileges. The ransomware gang behind it? Warlock, a group known for targeting Windows infrastructure and aggressive encryption tactics.
But—and this matters—Smarter Tools' incident response actually worked. Because they'd invested in network segmentation and isolation, the breach affected their office network and some data center infrastructure, but not their customer-facing systems. No business applications got compromised. No customer account data went down. The attack was contained, painful but not catastrophic.
Yet the incident reveals something every security leader needs to understand: your most sophisticated defenses are worthless if you're not managing basic hygiene. You can have zero-trust architecture, EDR tools, and a SOC running 24/7, but one forgotten server will undo all of it. This is the story of how and why that happened, what you can learn from it, and exactly how to prevent it in your own environment.
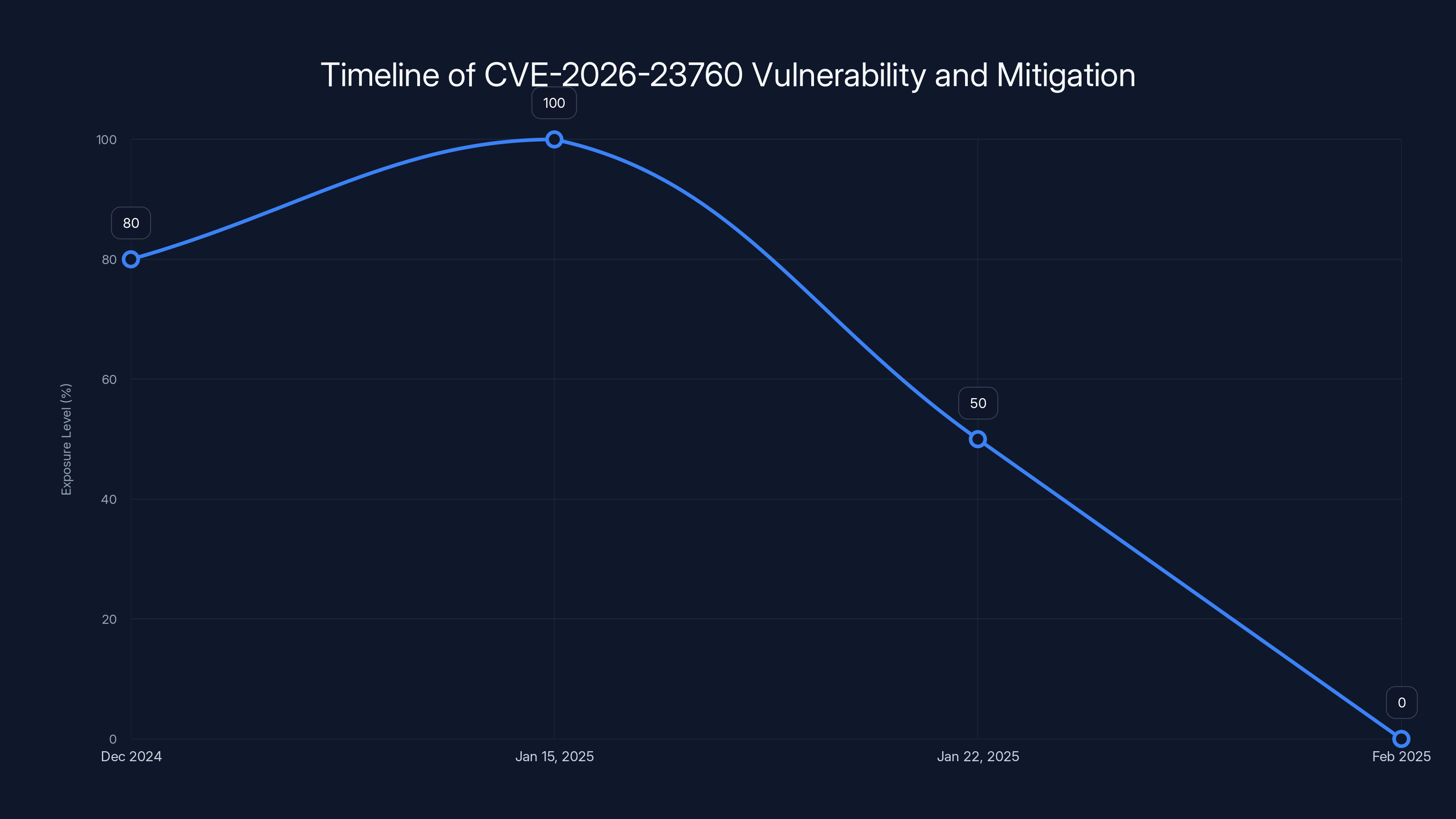
The vulnerability exposure peaked before the patch release on January 15, 2025, and significantly decreased after additional hardening on January 22, 2025. Estimated data based on typical exposure periods.
TL; DR
- One forgotten VM with unpatched Smarter Mail created an entry point for Warlock ransomware through CVE-2026-23760
- Authentication bypass vulnerability allowed attackers to reset admin passwords and escalate privileges without credentials
- Network segmentation worked, preventing customer-facing systems and account data from being compromised despite the breach
- Windows infrastructure was the target, but Linux-based systems remained unaffected because they represented 80% of their infrastructure
- Prevention requires four things: comprehensive asset inventory, automated patch management, network isolation, and active monitoring of all VMs
Understanding the Smarter Tools Breach: The Timeline
What Happened: The Sequence of Compromise
The breach didn't start with malware landing in an inbox or a compromised credential in a database dump. It started with a simple decision: someone created a VM for Smarter Mail and never told anybody about it.
This is more common than you'd think. Engineers spin up test environments. Contractors set up temporary infrastructure. Someone migrates a system and forgets to document it. The VM keeps running, maybe for months or years, completely invisible to your asset management team.
That's exactly what happened to Smarter Tools. Curtis was explicit about it: "Unfortunately, we were unaware of one VM, set up by an employee, that was not being updated."
Unaware. That word carries weight. They had 30 Smarter Mail servers running. They had processes. They had patch management. Except for this one system, which lived in a blind spot.
Warlock ransomware group identified that VM, likely through network scanning or initial access broker reconnaissance. They discovered it was running Smarter Mail with an unpatched vulnerability—CVE-2026-23760, which had been disclosed months earlier and patches were available.
Then they exploited it. The vulnerability allows attackers to reset administrator passwords without knowing the current password. It's an authentication bypass, meaning the normal security controls that verify who you are just... get skipped. Once they reset the admin password, they had full control of the mail server.
From there, they could access email systems, enumerate the network, and—critically—begin lateral movement to other systems.
Why This Happened: The Visibility Problem
There's a hard truth in cybersecurity: you can't protect what you can't see. This breach is Exhibit A.
Smarter Tools' security team wasn't negligent. They had patch management in place. They probably had reasonable update schedules. But their asset inventory was incomplete. Systems were created outside of formal documentation processes. One VM simply wasn't on anyone's radar.
This isn't unique to Smarter Tools. In fact, it's the norm. Research consistently shows that organizations can't even tell you how many devices are on their network. One study found that the average enterprise discovers new assets every single week that weren't previously in their inventory.
Why? Because modern infrastructure is dynamic. Teams are distributed. Cloud VMs spin up and down constantly. Employees build things for convenience. Documentation lags behind reality.
The Smarter Mail server that caused this breach was probably:
- Set up years ago by someone who no longer works there
- Not documented in the main asset management system
- Running a version of Smarter Mail from before the January 15 patch release
- Totally forgotten until ransomware operators found it
This visibility gap is why the breach happened. Not because Smarter Tools was careless, but because perfect visibility is genuinely hard to maintain at scale.
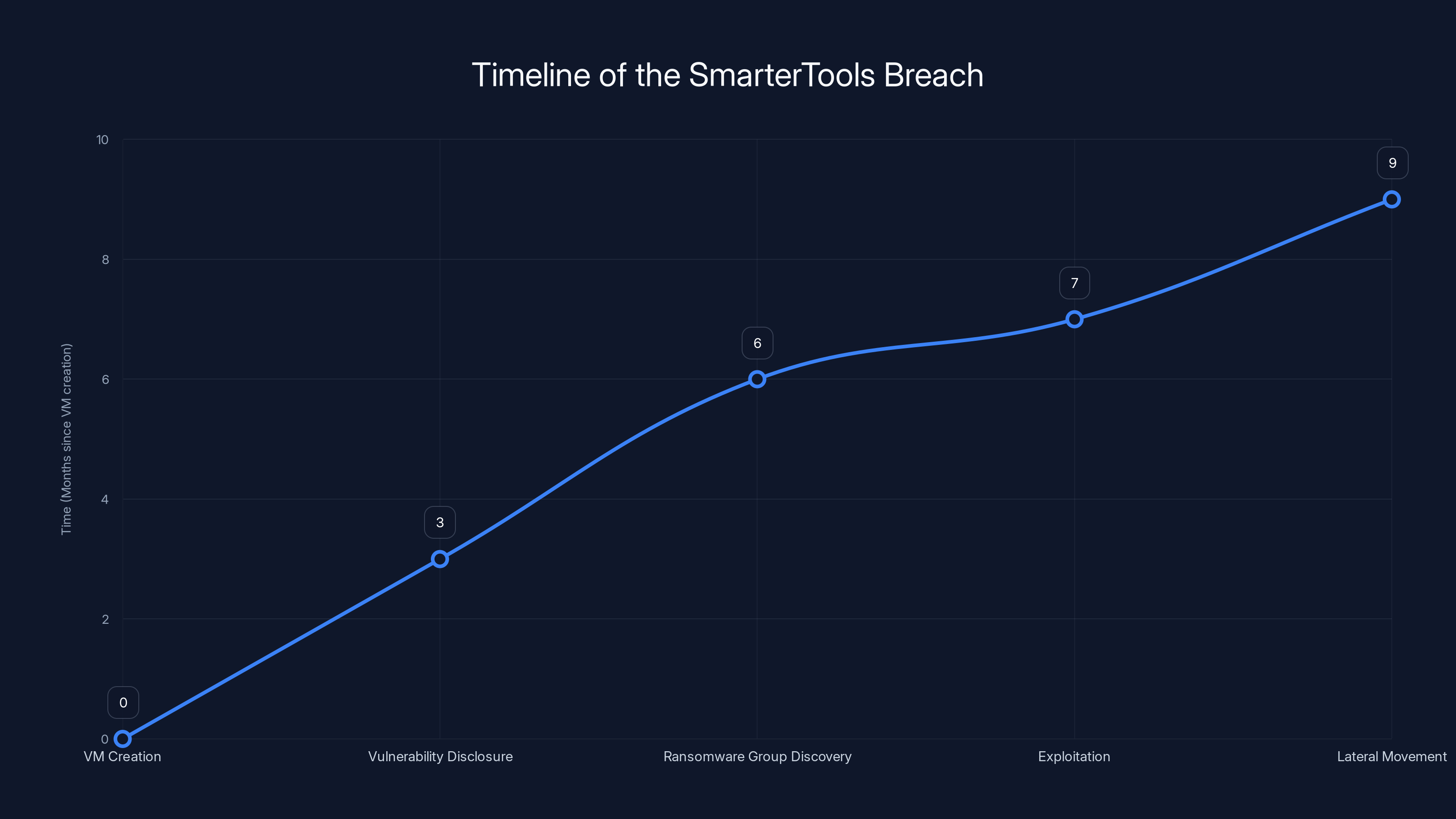
Estimated data shows the breach timeline, highlighting the critical delay between vulnerability disclosure and exploitation.
CVE-2026-23760: The Authentication Bypass That Did It
How the Vulnerability Works
Authentication bypass vulnerabilities are the ransomware attacker's dream. Instead of needing to guess or brute-force credentials, the flaw lets them just... skip the authentication process entirely.
CVE-2026-23760 affects Smarter Mail before Build 9518. It allows an attacker to reset administrator passwords remotely without providing the current password. That's extraordinary from a security perspective. Normal password reset flows require you to prove your identity somehow—with a recovery email, security questions, or your current password. This vulnerability sidesteps all of that.
Once an attacker resets the admin password, they have full administrative access to the mail server. That means:
- Reading all email on the system
- Creating new admin accounts
- Configuring email forwarding to external addresses
- Modifying server settings
- Installing additional malware or backdoors
- Using the compromised server as a pivot point to attack other systems
The vulnerability was known. Smarter Tools released Build 9518 on January 15 specifically to patch it. Build 9526, released January 22, included additional hardening measures.
But the forgotten VM never got updated.
Why Smarter Mail Was a Target
Smarter Mail is enterprise email software used by thousands of organizations worldwide. It's a legitimate product, not some obscure niche tool. That makes it valuable to attackers for several reasons:
Large attack surface: Thousands of potential targets. If you find a vulnerability affecting thousands of mail servers, that's a massive opportunity for ransomware operations.
Email access equals privilege: Control someone's mail server and you can read everything passing through it. For many organizations, that means accessing customer data, financial information, sensitive communications, and more.
Lateral movement potential: Mail servers typically sit in trusted zones of networks. Compromising one often gives you access to internal resources and other systems.
Predictable patching delays: Not every organization patches immediately. Some miss security updates entirely.
Smarter Tools' Smarter Mail was an attractive target precisely because it's widely deployed and email access is extremely valuable to attackers.
Warlock Ransomware: The Attackers Behind the Breach
Who Is Warlock?
Warlock is a ransomware-as-a-service (RaaS) operation, meaning they operate like a criminal business. They develop the ransomware, maintain infrastructure, negotiate with victims, and handle ransom collection. Affiliates rent access to their malware and tools, paying a percentage of successful ransom payments.
They've been active since at least 2023 and have a known preference for targeting Windows-based infrastructure. Their victims span multiple industries, from healthcare to manufacturing to software companies.
What makes Warlock notable is their focus on Windows environments specifically. They optimize their encryption malware for Windows systems and have detailed knowledge of Windows network architectures, which helps them move laterally and evade defenses.
Their Tactics: Persistence and Lateral Movement
Warlock operates using a fairly standard ransomware playbook:
- Initial access: They find an entry point (in this case, CVE-2026-23760)
- Establish foothold: They get interactive access or install a reverse shell for persistent connection
- Reconnaissance: They enumerate the network, identify valuable targets, and find weak points
- Lateral movement: They spread from the compromised system to other machines, escalating privileges as they go
- Data exfiltration: They steal sensitive data before encrypting anything (this gives them leverage for ransom negotiation)
- Encryption: They deploy ransomware across systems, rendering data unusable
- Extortion: They demand payment for decryption keys, threatening to sell stolen data if payment is refused
In the Smarter Tools case, they got through step 2 but were stopped before completing steps 3-7, thanks to network segmentation.
Why They Target the Windows Side
Curtis mentioned something important in his notification: "Because we are primarily a Linux company now, only about 12 Windows servers looked to be compromised."
This is strategic. Modern companies increasingly run on Linux for cloud-native infrastructure, containers, and backend services. But they often retain Windows systems for specific workloads, legacy applications, and administrative purposes.
Ransomware operators know that a single Windows compromise can sometimes give them access to the entire Windows domain through Active Directory. That's why Warlock focused on the Windows side—it was the path of least resistance to spreading throughout the network.
Smarter Tools' incident response team recognized this and immediately eliminated Windows from their infrastructure where possible, then disabled Active Directory entirely. That removes a major attack vector for this specific threat.

Why Network Segmentation Saved Smarter Tools
The Architecture That Worked
Here's what prevented this from being a complete disaster: Smarter Tools had network segmentation.
Network segmentation is the practice of dividing your network into isolated zones. Instead of a flat network where any compromised system can access any other system, you create boundaries. Traffic between zones is restricted and monitored.
Smarter Tools had segmented their customer-facing infrastructure (their website, shopping cart, My Account portal, and business applications) from their office and data center networks. When the mail server in the data center got compromised, that compromise didn't automatically spread to customer-facing systems.
This is exactly how segmentation is supposed to work. The ransomware operators couldn't move laterally from the compromised mail server to the production systems because network controls prevented it.
What Didn't Get Compromised
Curtis was explicit: "None of our business applications or account data were affected or compromised."
That's the key detail. The breach was painful, disruptive, and required investigation and remediation. But it wasn't catastrophic because the attackers couldn't reach:
- Customer account information
- Billing systems
- Business applications
- Core infrastructure
- Any system containing customer data
That's not luck. That's architecture. Specifically, architecture that recognized some systems are more critical than others and merit additional protection.
The Isolation Strategy That Works
Smarter Tools learned this lesson and implemented a change that's worth noting: "We isolate our networks in case of a breach," Curtis explained.
That's not a new concept, but it's often poorly implemented. Many organizations create network zones but don't enforce the boundaries. Traffic flows between zones when developers need quick access. Security groups get too permissive. Rules accumulate and become unmaintainable.
Effective segmentation requires:
- Clear zones: Identify which systems need to be protected and why
- Specific rules: Define exactly what traffic is allowed between zones
- Enforcement: Use firewalls, VLANs, security groups, or microsegmentation to prevent unauthorized traffic
- Monitoring: Log and alert on attempts to cross zone boundaries
- Testing: Verify that the boundaries actually work as designed
Smarter Tools had implemented this well enough that an attacker with administrative access to a mail server still couldn't reach customer systems.
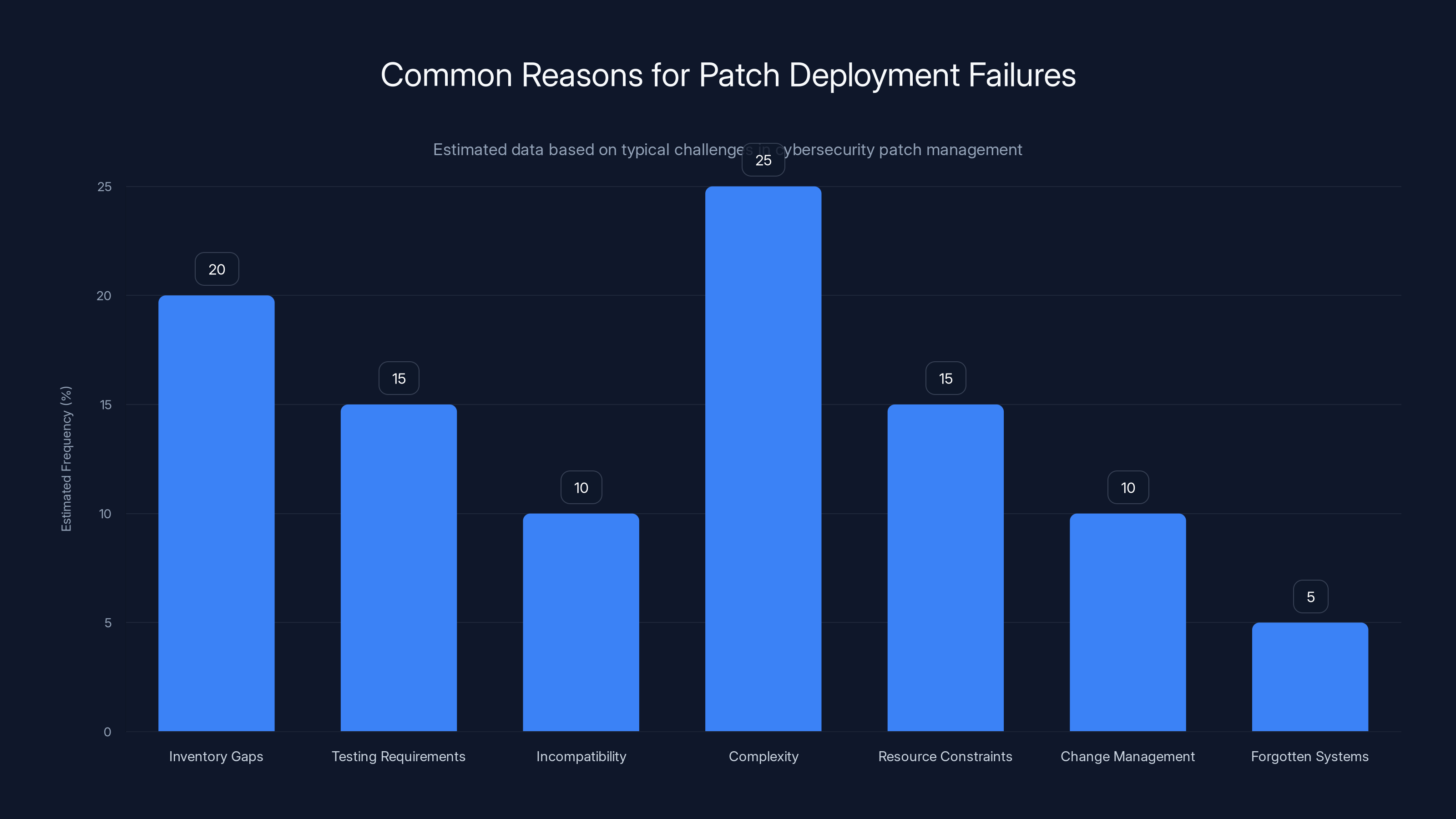
The chart highlights the estimated frequency of common reasons why patches fail to be deployed. Complexity and inventory gaps are leading causes, while forgotten systems, like in SmarterTools' case, occur less frequently. Estimated data.
The Failed Patch: Why Build 9518 Never Happened
The Vulnerability Was Disclosed
CVE-2026-23760 wasn't zero-day. Smarter Tools released a patch specifically to address it: Build 9518 on January 15.
That means the vulnerability was known. It was documented. A patch was available. But the forgotten VM never got updated.
This is one of the most frustrating aspects of cybersecurity: breaches often exploit vulnerabilities that have patches available. The Technical Advisory Board and security researchers identified the flaw, Smarter Tools developed a fix, and they released it to customers.
Somewhere in that process, communication failed. The patch didn't reach this one system. Maybe the update process was manual and someone forgot. Maybe the system wasn't included in automated patch management. Maybe nobody knew the server existed to tell them about the patch.
Why Patching Fails
The gap between vulnerability disclosure and patch deployment is where most breaches happen. Not because patches aren't available, but because organizations struggle to apply them.
Common reasons patches don't get deployed:
- Inventory gaps: You don't know all the systems you need to patch
- Testing requirements: Patches need testing before production deployment, which takes time
- Incompatibility: Patches might break applications or dependencies
- Complexity: Large organizations have hundreds or thousands of systems to patch
- Resource constraints: Not enough people to manage patching at scale
- Change management: Some organizations have complex approval processes for patches
- Forgotten systems: Like Smarter Tools, some systems just get lost
Smarter Tools' situation was specifically the last one: a forgotten system. But the underlying problem is universal. Most organizations can't patch everything immediately when vulnerabilities are disclosed.
The Math of Patch Delays
Let's think about the numbers. Assume an organization with 100 systems needs to apply a critical security patch.
- Manual process: 2 hours per system = 200 hours = 5 weeks with one person
- Semi-automated: 30 minutes per system with testing = 50 hours = 1-2 weeks
- Fully automated: All systems patched in hours with automatic rollback if issues occur
The difference between automated and manual patch management often determines whether you get compromised during the vulnerability window.
Smarter Tools' forgotten VM sat unpatched for weeks or months. During that entire time, Warlock or any other attacker could exploit it. The vulnerability window wasn't hours or days—it was potentially months.

The Lateral Movement That Was Prevented
How Active Directory Enabled Spread
Here's something that's rarely discussed in breach reports: Active Directory is a double-edged sword.
Active Directory is Microsoft's directory service that manages user identities, permissions, and credentials across Windows networks. For system administrators, it's incredibly useful. You can manage thousands of users and computers from a centralized system.
For attackers who compromise a system with domain privileges, it's a goldmine. Because Active Directory also means that compromising one system with the right privileges can give you paths to compromise many other systems.
When Warlock compromised the mail server through CVE-2026-23760 and reset the admin password, they didn't just get access to that server. If that server was part of an Active Directory domain, they potentially had paths to:
- Other servers in the domain
- Workstations
- Network services
- Domain controllers
- The entire directory structure
This is exactly why attackers love targeting systems that are domain-joined. One compromise becomes many compromises.
Smarter Tools recognized this post-breach and made a significant change: they eliminated Active Directory entirely for the infrastructure that matters.
The Nuclear Option: Removing Active Directory
Curtis explained: "We no longer use Active Directory services (which the crooks used to move laterally throughout the network.)"
That's a bold move. Active Directory is deeply integrated into Windows infrastructure at most enterprises. Removing it requires rearchitecting authentication and authorization.
But it's effective. If there's no Active Directory, there's no centralized directory service for attackers to abuse for lateral movement. Authentication has to happen differently—maybe through cloud-based services, or local authentication, or other methods.
This decision tells you something important: Smarter Tools was willing to make significant architectural changes to prevent recurrence. They didn't just patch the vulnerability. They changed their entire identity infrastructure.
Why This Matters for Your Network
Most organizations that get compromised through lateral movement are using Active Directory. It's not that Active Directory is inherently insecure—it's just that controlling it gives you control of the entire network.
If attackers compromise any system in an Active Directory domain, they have a clear path to escalate to domain admin and compromise everything else.
That's why modern security frameworks emphasize:
- Zero Trust: Don't assume internal systems are safe just because they're inside the network
- Microsegmentation: Even within Active Directory domains, restrict what each system can access
- MFA everywhere: Even internal systems should require multi-factor authentication
- Principle of least privilege: Give systems and users only the permissions they need
Smarter Tools went further—they eliminated the centralized directory service entirely for systems that don't need it, removing a whole attack vector.
Linux Infrastructure Remained Untouched: Why
The Strategic Advantage of Linux
Remember Curtis' statement: "Because we are primarily a Linux company now, only about 12 Windows servers looked to be compromised and, on those servers, our virus scanners blocked most efforts. None of the Linux servers were affected."
This is worth examining because it reveals something important: the attacker's toolkit was Windows-specific.
Warlock's ransomware and lateral movement tools are optimized for Windows environments. They exploit Windows vulnerabilities, use Windows-native tools, and navigate Windows-based infrastructure. That's not a limitation—it's a strategic choice. The vast majority of ransomware targets Windows because that's where the money is.
But if your infrastructure is primarily Linux, that doesn't help you. Ransomware designed for Windows won't run on Linux. Tools that abuse Active Directory don't work if there's no Active Directory.
Smarter Tools' infrastructure mix gave them protection through architectural diversity. Not perfectly (the Windows systems still got compromised), but significantly.
The Endpoint Detection That Worked
Curtis also mentioned: "on those servers, our virus scanners blocked most efforts."
Endpoint protection tools running on the Windows servers detected and blocked most ransomware activity. That's a second layer of defense working as intended.
But here's the important detail: the compromise still happened. Detection isn't prevention. The attackers still got in, still got administrative access, still potentially exfiltrated data.
What endpoint protection did was limit how much damage they could cause. They couldn't encrypt all the systems. They couldn't spread as far as they wanted. The tools provided visibility into what was happening and prevented the worst outcomes.

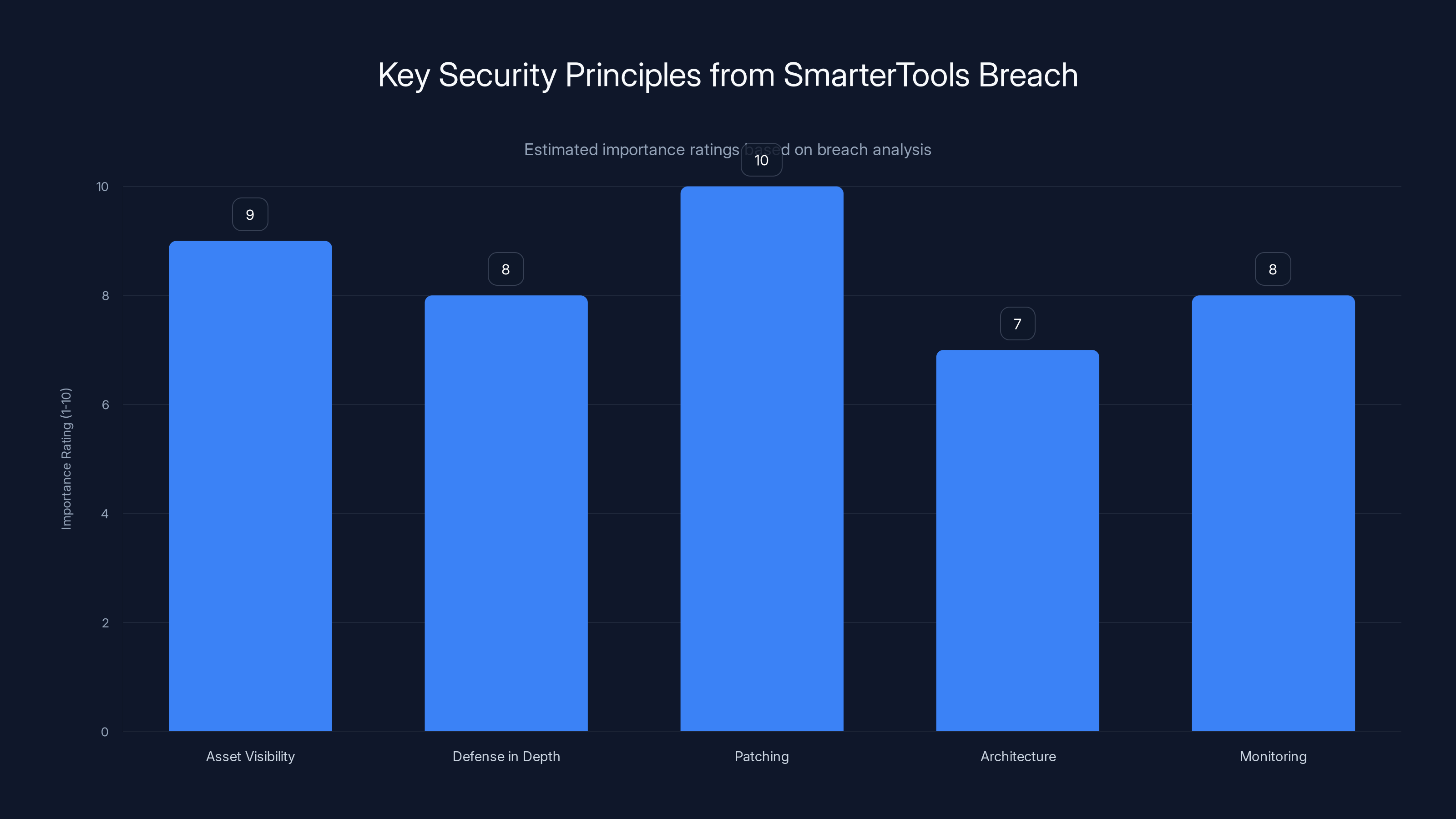
Estimated data shows 'Patching' as the most critical principle, followed by 'Asset Visibility' and 'Monitoring'.
The Patch Timeline: What Happened and When
January 15: Build 9518 Released
Smarter Tools released Build 9518 on January 15 as the patched version addressing CVE-2026-23760. Organizations that applied this patch immediately were protected against this specific vulnerability.
The forgotten VM didn't get this update.
January 22: Build 9526 Hardening Release
A week later, Smarter Tools released Build 9526 with additional improvements and hardening beyond the basic patch. This suggests they were actively monitoring for exploitation attempts and improved defenses based on what they saw.
Modern vulnerability response works like this: initial patch, then additional hardening, then continuous monitoring. Smarter Tools was responding appropriately to the threat.
The Recommendation for All Customers
Smarter Tools' guidance to customers was clear: upgrade to Build 9518 minimum (January 15 patch), with Build 9526 (January 22) recommended for additional improvements.
For organizations running Smarter Mail, this was time-critical. Any delay meant vulnerability to exploitation.
The Data Center Impact: What Was Affected
Office Network Compromise
The breach affected Smarter Tools' office network, which typically includes:
- Employee workstations
- Office productivity systems
- Internal services
- File servers
- Collaboration tools
This is disruptive for business operations but generally less critical than data center systems. Companies can usually recover from office network compromises more easily because critical business functions often run elsewhere.
Data Center Systems: Limited Impact
The data center was partially affected—specifically where quality control work is conducted. But the key infrastructure—customer-facing systems and business applications—remained protected through segmentation.
This partial compromise is actually instructive. It shows that even in a breach, you can limit damage through architectural design. The attackers had access to some systems but not others, not because of luck but because Smarter Tools had deliberately isolated critical infrastructure.
Why Quality Control Wasn't Critical
Curtis didn't elaborate on what the QC data center systems did, but the fact that they were compromised and the breach is now public suggests the information on those systems wasn't sensitive customer data.
Quality control typically involves test environments, testing scripts, and internal processes—valuable to the business but not customer-critical or legally sensitive in most cases.

Post-Incident Changes: How Smarter Tools Hardened
Eliminating Windows From Critical Infrastructure
Curtis explained that Smarter Tools made significant changes: "we ditched Windows entirely, wherever it could."
This is a major architectural shift. It means:
- Migrating or replacing Windows-based systems
- Converting workloads to Linux or other platforms
- Eliminating Windows dependencies in critical infrastructure
- Reducing the attack surface available to Windows-specific malware
For a company that was already "primarily Linux," this suggests they were running Windows for specific compatibility or legacy reasons and decided the security benefit of eliminating it outweighed the compatibility costs.
Removing Active Directory
"We no longer use Active Directory services" is the other major change. This requires:
- Redesigning authentication and authorization
- Implementing alternative identity management
- Migrating systems off Active Directory domain management
- Updating how permissions and access are controlled
Active Directory is deeply embedded in most Windows infrastructure. Removing it is non-trivial but eliminates a major lateral movement vector.
Monitoring for Similar Threats
While not explicitly stated, an incident like this typically triggers increased monitoring for:
- Unusual authentication attempts
- Credential reset activities
- Lateral movement patterns
- Data exfiltration indicators
- Anomalous network traffic
Smarter Tools likely implemented or expanded monitoring on:
- Mail server access patterns
- Authentication logs
- Network segmentation boundaries
- Admin account usage
- Suspicious process execution
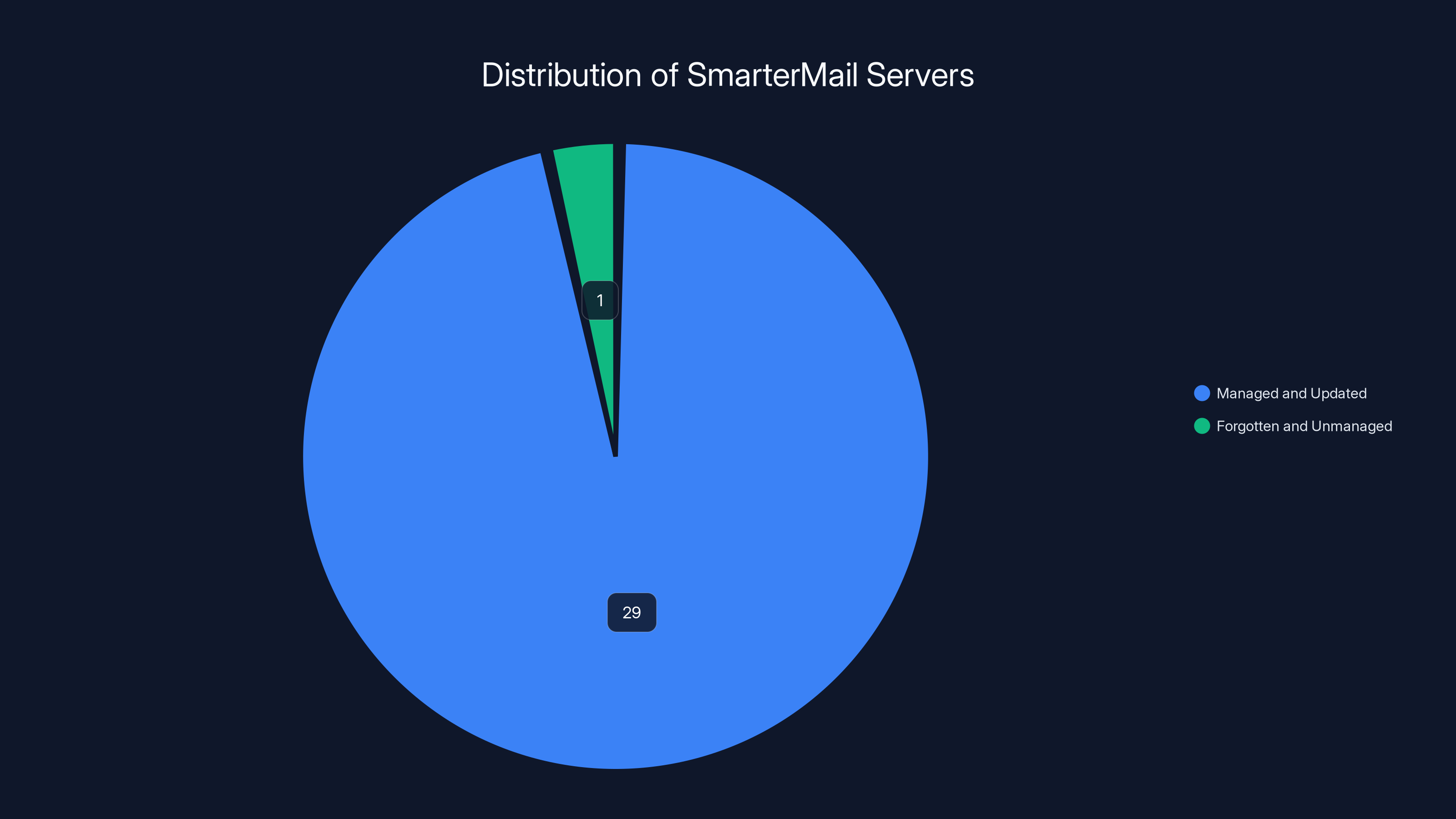
Estimated data shows that out of 30 SmarterMail servers, 1 was forgotten and unmanaged, leading to a costly security breach.
Critical Lessons: What This Breach Reveals
Lesson 1: You Can't Protect What You Can't See
The fundamental problem was visibility. The forgotten VM didn't appear in their asset inventory. You can have perfect patching processes, but if you don't know a system exists, the patches never reach it.
The first step in security is answering: What systems do I have? Where are they? What software runs on them? What data do they handle?
For most organizations, the answer is: "We're not entirely sure."
Lesson 2: Defense in Depth Actually Works
Smarter Tools didn't prevent the initial compromise. An attacker still got in through CVE-2026-23760. But they were stopped at the second, third, and fourth layers:
- Network segmentation prevented lateral movement to critical systems
- Endpoint protection blocked encryption attempts
- Architectural isolation protected customer data
None of these defenses alone would have been sufficient. Together, they contained the damage.
Lesson 3: Patching Is Still Your Foundation
Despite all the talk of advanced threats and zero-day exploits, this breach happened because a patch wasn't applied.
Patching remains the most cost-effective security control. It's not sexy. It's not flashy. But it prevents breaches like this one.
Lesson 4: Forgotten Systems Are Real Assets
Every organization has forgotten systems. Test environments that became production. Systems built by employees who left. Temporary infrastructure that became permanent.
These systems are time bombs because nobody's monitoring them, patching them, or securing them. They're not on anyone's radar until they're exploited.

Building a Resilient Infrastructure: Practical Steps
Step 1: Comprehensive Asset Inventory
Start with what you have. Use multiple discovery methods:
- Network scanning tools (active enumeration)
- CMDB and asset management tools
- Cloud provider APIs for cloud-hosted systems
- Endpoint detection tools on all systems
- Manual interviews with engineering teams
Combine these sources into a complete inventory. You should be able to answer:
- What is this system?
- What software runs on it?
- Who owns it?
- What data does it handle?
- When was it last patched?
Step 2: Automated Patch Management
Manual patching doesn't scale. Implement automated patch deployment:
- Scanning: Continuous vulnerability scanning identifies missing patches
- Testing: Automated testing environments validate patch compatibility
- Deployment: Automated tools push patches to systems according to schedules
- Verification: Automated verification confirms patches were applied
- Rollback: Automated rollback if patches cause issues
This should be fully automated for non-critical systems and semi-automated for critical systems (with staged rollout and monitoring).
Step 3: Network Segmentation
Design your network with zones:
- Public zone: Customer-facing systems accessible from the internet
- Application zone: Business applications and internal services
- Data zone: Databases and sensitive information
- Management zone: Administrative access and identity services
- Development zone: Non-production systems and testing
Control traffic between zones using firewalls, security groups, or microsegmentation. Test that the boundaries actually work.
Step 4: Identity and Access Control
Eliminate the single point of failure:
- Multi-factor authentication: On all administrative access
- Principle of least privilege: Services and users only get permissions they need
- Zero Trust: Verify every access attempt, even internal
- Conditional access: Restrict access based on location, device, time, and risk
Consider whether centralized directory services (like Active Directory) create unacceptable risk in your environment. They often do.
Step 5: Continuous Monitoring
You can't be blind to what's happening:
- Log aggregation: Collect logs from all systems
- SIEM or similar: Analyze logs for suspicious patterns
- Endpoint detection: Monitor all endpoints for anomalous behavior
- Network monitoring: Watch for unusual traffic patterns
- Alert tuning: Focus on signals that matter, not noise
The Role of Automation in Prevention
Why Manual Security Doesn't Scale
Here's the fundamental challenge: attackers work 24/7 and try thousands of approaches. Security teams work business hours and can't possibly respond to everything manually.
Automation bridges that gap. It lets you apply security at scale:
- Patches applied to thousands of systems in hours
- Threats detected instantly across your entire infrastructure
- Vulnerability scans running continuously
- Compliance checks performed automatically
Without automation, you're playing defense with limited resources against unlimited attackers.
Automation Examples
Patch automation: Tools like Rundeck, Ansible, or cloud provider services automatically deploy security patches according to schedules and business rules.
Vulnerability scanning: Tools run continuous scans, identify missing patches, and alert teams to new vulnerabilities.
Configuration management: Tools like Terraform ensure infrastructure is built according to security standards.
Compliance automation: Tools verify that security policies are enforced across all systems.
Incident response automation: SOAR (Security Orchestration, Automation, and Response) tools automatically handle repetitive incident response tasks.
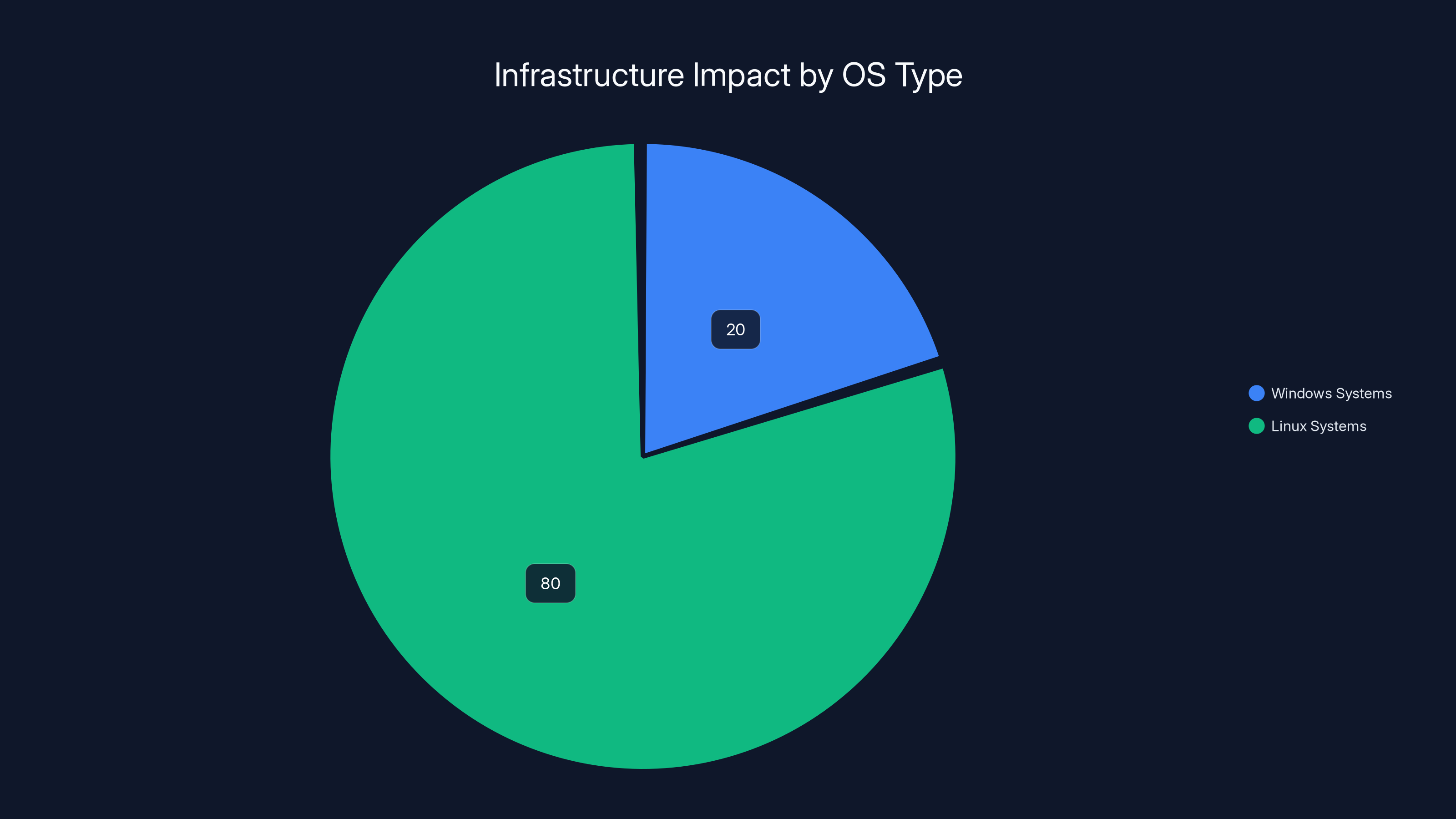
Despite the ransomware targeting Windows systems, the breach impact was limited as 80% of the infrastructure was Linux-based and remained unaffected. Estimated data based on context.
Industry Context: Similar Breaches and Patterns
The Forgotten Server Pattern
Smarter Tools isn't alone. This pattern appears regularly:
- An organization has multiple instances of a system
- Most are managed and patched
- One or more fall through the cracks
- Attackers find and exploit the unpatched ones
- The breach reveals inventory problems
This happens with web servers, databases, mail systems, development tools, and virtually every type of software.
Why Ransomware Groups Target SaaS and Managed Services
Warlock and similar groups target software companies specifically because compromising a software vendor can give them access to many customers. One breach becomes many breaches.
Smarter Tools is a software company with email infrastructure that's valuable to attackers. Other likely targets:
- Cloud hosting providers
- Backup services
- Monitoring and observability tools
- Identity and access management platforms
- Development platforms and tools
These are high-value targets because one compromise provides access to many downstream customers.
Prevention Framework: The Complete Picture
Technology Layer
Technology alone isn't sufficient, but it's necessary:
- Patching systems
- Firewalls and network segmentation
- Endpoint protection
- Authentication and access controls
- Monitoring and detection
Process Layer
Technology needs processes to be effective:
- Vulnerability management process (identifying, assessing, patching)
- Change management (controlling what changes in your environment)
- Incident response (responding when prevention fails)
- Security architecture review (designing for resilience)
- Compliance and audit (verifying controls are working)
People Layer
Processes need people to execute them:
- Security team with appropriate skills
- Developers and engineers who understand security
- System administrators who maintain infrastructure
- Management who allocates resources and prioritizes security
- Training for everyone about threats and their role in defense
Smarter Tools had technology and processes. What they lacked was visibility into all their assets, which is a people and process problem.

What Smarter Tools Did Right
Network Segmentation
This single decision prevented catastrophic damage. By isolating customer-facing infrastructure from office and data center networks, they contained the breach. This is the most important lesson.
Rapid Communication
Curtis' public statement was clear, honest, and specific. They explained what happened, what was affected, and what wasn't affected. This is how security incidents should be communicated.
Post-Incident Hardening
Instead of just patching the vulnerability, they made architectural changes:
- Eliminating Windows where possible
- Removing Active Directory
- Presumably increasing monitoring and detection
This suggests they learned from the incident and made systematic improvements.
Prioritizing Customer Safety
The most important detail: customer data and business applications weren't compromised. Despite being hit with ransomware, Smarter Tools prioritized keeping customer systems safe. This should be the priority for any company handling customer data.
Risk Assessment: Vulnerability Window Analysis
The Exploitation Timeline
Let's model when the compromise likely occurred:
- January 15: CVE-2026-23760 patch released (Build 9518)
- January 22: Additional hardening (Build 9526)
- Unknown date: Smarter Tools network was compromised
- Unknown date: Breach was discovered and contained
- Notification date: Smarter Tools published the breach notification
The forgotten VM wasn't patched on January 15. If attackers found and exploited it immediately after the patch release, the vulnerability window was very narrow.
But if the compromise happened weeks or months later, the window was much longer.
This uncertainty is exactly why rapid patching matters. Every day an unpatched vulnerability exists is a day attackers can exploit it.
The Cost of Delay
Let's calculate the cost of patch delays:
If vulnerability disclosed on January 15 and patch released immediately:
- 0-1 days to patch: Minimal risk window, most attacks prevented
- 1-7 days to patch: Small window, attacks possible but uncommon
- 7-30 days to patch: Significant window, high probability of compromise
- 30+ days to patch: Critical window, almost certain compromise from active threats
Smarter Tools' forgotten VM likely sat in the "30+ days to patch" category, or worse if it went weeks without patching.
Monitoring Strategies: Detection You Can Implement
Mail Server Monitoring
If you run Smarter Mail or similar mail servers, monitor for:
- Authentication anomalies: Failed login attempts, unusual patterns, password resets
- Admin account activity: Any administrative actions should be logged and reviewed
- Email forwarding rules: Attacker-created rules forwarding to external addresses
- Mobile device access: Unusual mobile access could indicate credential theft
- Outbound data: Large volumes of data leaving the system
- Process execution: Unusual processes running on the mail server
Mail servers are high-value targets and warrant detailed monitoring.
Network-Level Monitoring
Monitor network traffic for:
- Lateral movement: Unusual traffic patterns between network zones
- Data exfiltration: Large outbound data transfers
- C2 communication: Connections to known malicious IP addresses or domains
- Scanning activity: Systems scanning your network from inside
- Protocol anomalies: Unusual protocols or traffic patterns
Active Directory Monitoring (If You Use It)
If you still use Active Directory, monitor for:
- Privilege escalation: Users gaining unexpected elevated privileges
- Account lockouts: Brute-force attempts
- Password resets: Especially for service accounts
- Unusual authentication patterns: Time of day, location, method
- Group policy changes: Modifications to security policies
Compliance Implications: What Regulations Require
Data Protection Regulations
Depending on what data was exposed:
- GDPR (if European customers): Breach notification, data protection impact assessment, potential fines
- HIPAA (if health data): Specific breach notification and investigation requirements
- PCI-DSS (if payment card data): Forensic investigation and incident reporting
- SOC 2 Type II: Incidents like this require detailed documentation and remediation
Smarter Tools' notification carefully stated that customer account data wasn't compromised, which is critical for regulatory compliance.
Incident Investigation Requirements
Most regulations require:
- Forensic investigation: Understand how the breach occurred
- Root cause analysis: Identify the underlying cause
- Notification: Notify affected individuals and regulators
- Remediation: Fix the underlying issues
- Documentation: Document all of the above
Smarter Tools appears to have completed these steps based on their public statement.

Building a Sustainable Security Program
The Cycle: Prevent, Detect, Respond
Effective security has three components that work together:
Prevent: Stop attacks before they succeed
- Patching and hardening
- Network segmentation
- Access controls
- Secure development
Detect: Identify attacks that prevention misses
- Monitoring and alerting
- Threat hunting
- Vulnerability scanning
- Continuous assessment
Respond: Contain and remediate attacks that detection identifies
- Incident response plan
- Forensic investigation
- Communication and notification
- Root cause analysis
- Remediation
You need all three. Perfect prevention is impossible, so you need detection. Even perfect detection takes time to work, so you need response capabilities.
Smarter Tools' breach shows the prevent phase failed (unpatched VM), but the detect phase worked (they discovered the breach), and the respond phase was effective (they contained it and hardened).
Resource Allocation
Most organizations don't invest enough in any of these. Common allocation:
- 50%: Prevention (maybe)
- 30%: Detection (usually neglected)
- 20%: Response (usually understaffed)
A more realistic allocation for mature organizations:
- 40%: Prevention (foundational but not sufficient)
- 35%: Detection (the realistic center of gravity)
- 25%: Response (expensive but necessary)
Emerging Threats: What's Next
Ransomware Evolution
Ransomware tactics are evolving:
- Triple extortion: Encrypt data, steal it, and threaten to release it to competitors
- Subsidiary targeting: Attackers compromise subsidiaries of larger companies
- Supply chain attacks: Compromise suppliers to reach end customers
- Hybrid crypto-extortion: Mix of traditional ransomware and cryptocurrency theft
Smarter Tools' status as a software company made it a supply chain target. Compromising them potentially provides access to their customers.
Vulnerability Market
Vulnerabilities are commoditized:
- Vulnerability brokers: Buy undisclosed vulnerabilities and sell access
- Rapid exploitation: Days between disclosure and active exploitation
- Targeted attacks: Attackers focus on high-value vulnerabilities
- Supply chain focus: Vulnerabilities in widely-used software are prioritized
Smarter Mail's wide deployment made CVE-2026-23760 a valuable target.
Future-Proofing Your Organization
Architectural Resilience
Design systems that can survive compromise:
- Assume breach: Design as if attackers will get in
- Limit blast radius: Make breaches expensive and limiting
- Recovery capability: Ensure you can restore from backups
- Diversity: Different platforms and technologies reduce single-point failures
- Isolation: Critical systems separated from general infrastructure
Smarter Tools had most of these but missed the inventory aspect.
Technology Stack
Choose technologies wisely:
- Open source vs. proprietary: Open source allows security audit; proprietary provides support
- Managed vs. self-hosted: Managed services shift responsibility; self-hosted gives control
- Cloud-native: Modern architectures often have better isolation and recovery
- Active development: Maintained software gets security updates; abandoned software doesn't
Organizational Structure
Security requires organizational support:
- Executive sponsorship: Security needs to be a leadership priority
- Dedicated resources: Security can't be a side responsibility
- Clear accountability: Someone owns each security function
- Cross-functional collaboration: Security isn't just IT's job
Smarter Tools' incident response suggests they have organizational support for security.
Conclusion: Learning From Smarter Tools
The Smarter Tools breach is a valuable case study because it reveals fundamental security principles:
First principle: You can't protect what you can't see. The forgotten VM didn't appear in their asset inventory. No amount of sophisticated security tooling compensates for not knowing what systems you have.
Second principle: Defense in depth works. One forgotten VM didn't become a total disaster because Smarter Tools had network segmentation, endpoint protection, and isolation. None of these individually would have been sufficient, but together they contained the damage.
Third principle: Patching is still the foundation. This breach happened because a patch wasn't applied, not because of zero-day exploits or sophisticated APT tactics. Boring security hygiene prevents breaches.
Fourth principle: Architecture matters more than technology. Smarter Tools' decision to segment networks and eventually eliminate Windows and Active Directory prevented worse damage. These are architectural choices, not just technology selections.
For your organization, the lessons are clear:
- Know your assets: Comprehensive inventory is your starting point
- Patch ruthlessly: Automated patch management is non-negotiable
- Segment everything: Network isolation limits blast radius
- Monitor constantly: You'll miss the obvious without monitoring
- Respond quickly: When prevention fails, rapid response minimizes damage
No single security control prevents all breaches. Ransomware groups are professional, sophisticated, and well-resourced. But fundamental security hygiene, combined with defense in depth, dramatically reduces your risk.
Smarter Tools learned these lessons the hard way. You don't have to.
Use Case: Automate security documentation and incident reporting workflows to ensure your team consistently captures lessons learned like Smarter Tools did.
Try Runable For Free
FAQ
What is CVE-2026-23760 exactly?
CVE-2026-23760 is an authentication bypass vulnerability in Smarter Mail before Build 9518 that allows attackers to reset administrator passwords without knowing the current password. This gives attackers full administrative access to the mail server, including email access, user management, and server configuration capabilities.
How did the attackers get initial access to Smarter Tools' network?
The attackers exploited CVE-2026-23760 on the forgotten virtual machine running Smarter Mail. Because the system wasn't included in Smarter Tools' patch management process and was unknown to their security team, it remained vulnerable to this remotely exploitable flaw. Warlock ransomware group likely discovered it through network scanning or other reconnaissance techniques.
Why didn't the breach affect customer data?
Smarter Tools had implemented network segmentation, isolating their customer-facing infrastructure from their office and data center networks. When the mail server was compromised, the attackers couldn't cross the network boundaries to reach customer systems, account databases, or business applications. This architectural isolation prevented the breach from becoming a complete catastrophe.
What changes did Smarter Tools make after the breach?
Smarter Tools made three major changes: First, they eliminated Windows servers from their infrastructure wherever possible, removing the operating system that Warlock's tools were designed to attack. Second, they disabled Active Directory entirely, eliminating a central point that attackers could abuse for lateral movement. Third, they presumably improved monitoring and asset management to ensure no systems go undocumented in the future.
How long was the vulnerability window?
The patch was released on January 15, 2025 (Build 9518), with additional hardening on January 22 (Build 9526). The exact date of compromise isn't publicly known, but the forgotten VM likely remained vulnerable for weeks or months before discovery. Modern vulnerability windows are typically days to weeks, making rapid patching critical.
What should organizations do about systems like the forgotten VM?
Organizations need comprehensive asset discovery using network scanning, cloud provider APIs, endpoint detection software, and manual inventory processes. Any undocumented systems should be inventoried, risk-assessed, and either secured or decommissioned. Many organizations discover forgotten infrastructure this way, often revealing significant security issues.
Is Warlock still active?
Warlock ransomware group continues to operate as a ransomware-as-a-service platform, renting their tools and infrastructure to affiliate attackers. They continue targeting Windows-based infrastructure and have a particular focus on managed service providers and software companies. Organizations should assume Warlock remains an active threat and update their security posture accordingly.
Could this happen to my organization?
Most organizations have forgotten systems somewhere on their network. Unless you have comprehensive asset management and automated patch processes, you likely have undocumented infrastructure. The question isn't whether this could happen, but whether you've discovered your forgotten systems before attackers do. Regular network scanning and asset discovery exercises are essential.
How should we approach Active Directory security?
Active Directory is incredibly valuable for network administration but represents a single point of failure for security. Modern approaches include: implementing zero-trust architecture (don't assume internal systems are safe), using conditional access policies, requiring multi-factor authentication everywhere, applying the principle of least privilege strictly, and for some organizations, eliminating Active Directory entirely for sensitive infrastructure. The Smarter Tools approach is more radical than most organizations need, but it's worth considering for critical systems.
What's the relationship between patching speed and breach risk?
Research shows exploitation attempts begin within days of vulnerability disclosure for high-profile vulnerabilities. Every day a patch isn't applied increases breach probability. For critical vulnerabilities (especially those with public exploits), patching within 48-72 hours significantly reduces risk. For a vulnerability like CVE-2026-23760, weeks or months of delay substantially increases the probability of compromise.
Quick Navigation
- Understanding the Smarter Tools Breach for the incident timeline
- CVE-2026-23760 for technical vulnerability details
- Warlock Ransomware for threat actor analysis
- Network Segmentation for architectural defense strategies
- Building a Resilient Infrastructure for actionable implementation steps
- Critical Lessons for key takeaways
- Prevention Framework for comprehensive security strategy

Key Takeaways
- One forgotten VM with an unpatched vulnerability (CVE-2026-23760) enabled Warlock ransomware to compromise SmarterTools' network
- Network segmentation prevented lateral movement to customer-facing systems, containing the breach to office and data center infrastructure
- Authentication bypass vulnerabilities allow attackers to reset admin passwords without credentials, giving complete system control
- Asset visibility gaps are the root cause of most breaches involving forgotten systems—comprehensive discovery is critical
- Post-incident hardening through Windows elimination and Active Directory removal addresses the underlying architectural weaknesses
Related Articles
- Wikipedia vs Archive.today: The DDoS Controversy Explained [2025]
- Windows Secure Boot Certificate Renewal Explained [2025]
- Google's Enhanced Safety Tools Remove More Personal Data [2025]
- BeyondTrust RCE Vulnerability CVE-2026-1731: What You Need to Know [2025]
- Vega Security Raises $120M Series B: Rethinking Enterprise Threat Detection [2025]
- Proton VPN 70% Off Deal: Complete Breakdown [2025]
![SmarterTools Ransomware Breach: How One Unpatched VM Compromised Everything [2025]](https://tryrunable.com/blog/smartertools-ransomware-breach-how-one-unpatched-vm-compromi/image-1-1770756291888.jpg)



