Post-Quantum Cryptography: Securing TLS for the Quantum Era
Quantum computers aren't coming in a hundred years. They're coming much sooner than most people realize, and when they arrive, they'll shatter the encryption that currently protects nearly everything you do online. Your banking passwords, your sensitive emails, your API calls, your medical records, your financial transactions, even the firmware running on your infrastructure—all of it relies on cryptographic algorithms that quantum computers will crack in minutes.
Here's the unsettling part: attackers know this. Right now, sophisticated adversaries are harvesting encrypted data with the explicit intention of decrypting it later, once quantum capability becomes viable. It's called "Harvest Now, Decrypt Later," and it's already happening. The gap between theoretical quantum threat and actual quantum deployment is narrowing rapidly, and most organizations are still treating this like a distant problem.
They're wrong.
The quantum threat isn't hypothetical anymore. Major technology companies like IBM and Google have made tangible progress on error correction and quantum bit stability. Governments worldwide are pouring billions into quantum research. The White House has already issued post-quantum cryptography mandates for federal agencies. The EU is developing similar standards. And the cryptographic community has spent years identifying and standardizing quantum-resistant algorithms specifically designed to survive quantum attacks.
This article breaks down what post-quantum cryptography means for your security strategy, why TLS is the critical battleground, how hybrid approaches protect you today and tomorrow, and exactly what you need to do right now to prepare. Whether you're an enterprise security leader, a developer building APIs, or a compliance officer trying to stay ahead of regulations, the math is simple: you need to start this transition immediately.
Let's dig into why, and how.
TL; DR
- Quantum computers threaten RSA and ECC encryption: Shor's algorithm will crack 4096-bit RSA keys in minutes, making retroactive decryption of archived data feasible once quantum capability arrives.
- Harvest Now, Decrypt Later is already happening: Attackers are collecting encrypted data today, planning to decrypt it with future quantum computers.
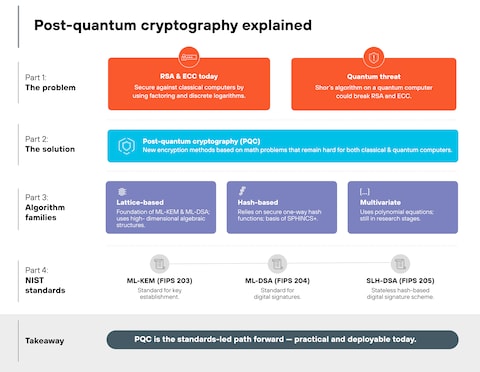
- ML-KEM is the cornerstone of post-quantum TLS: This lattice-based algorithm resists both classical and quantum attacks and is now NIST-standardized for hybrid TLS 1.3 deployments.
- Hybrid cryptography is the safest transition path: Combining classical algorithms (like X25519) with quantum-resistant ones (like ML-KEM) ensures backward compatibility while increasing security.
- Organizations must act now: Taking inventory, testing hybrid TLS configurations, assessing vendor readiness, and building a phased migration roadmap are critical first steps.
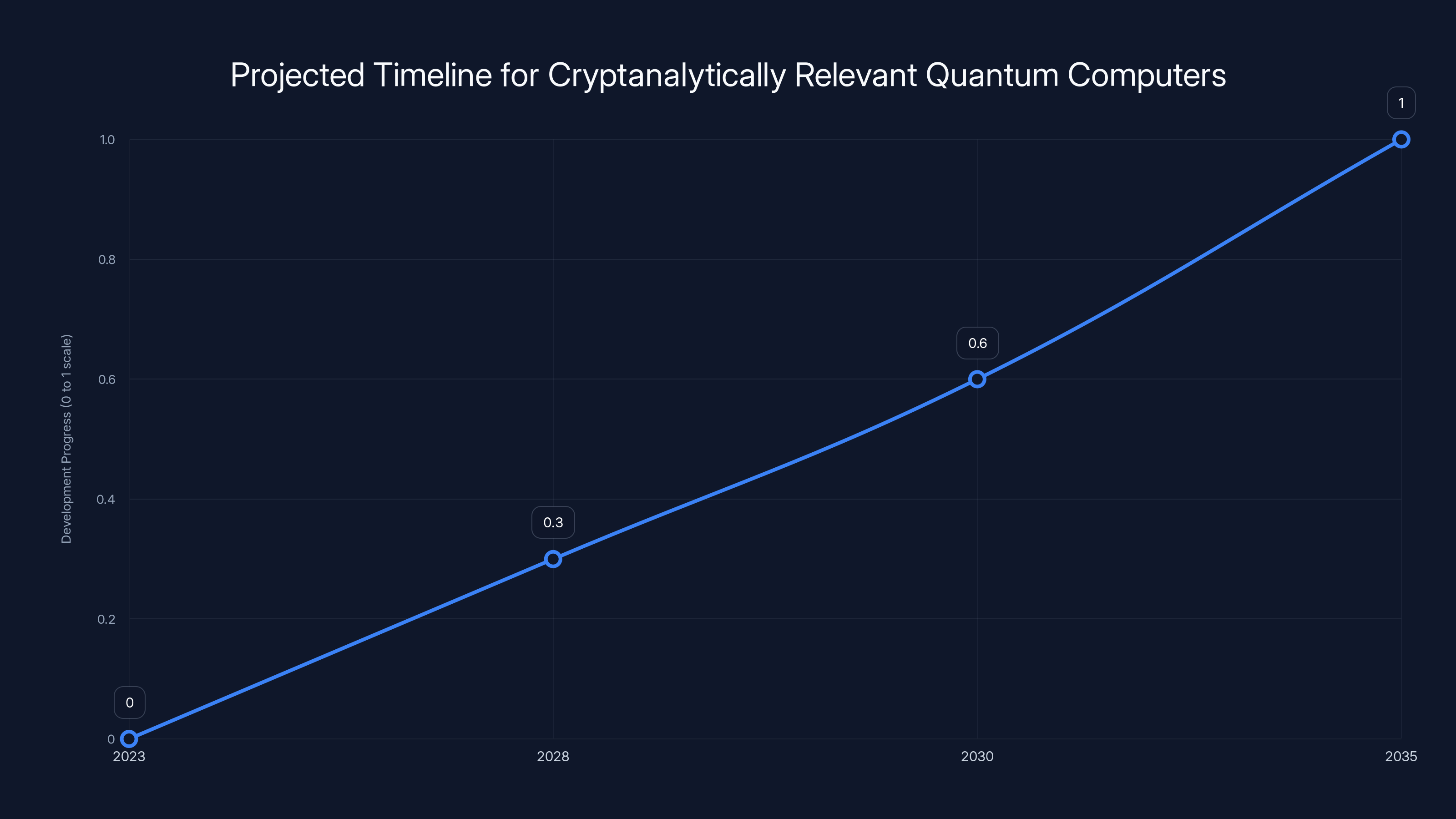
The development of cryptanalytically relevant quantum computers is projected to accelerate, potentially reaching significant milestones between 2028 and 2035. Estimated data based on current expert consensus.
The Quantum Computing Reality Check: What's Actually Happening
For decades, quantum computing was a theoretical curiosity. Scientists talked about it in labs, tech journalists wrote speculative pieces, and most organizations safely ignored it. That era is over.
Quantum research has entered what the industry calls the "NISQ era," short for Noisy Intermediate-Scale Quantum. This means we're past proof-of-concept. We're past "will this ever work?" We're now squarely in the "how fast can we scale this?" phase.
Google announced in 2019 that it had achieved quantum supremacy with a 53-qubit processor. Since then, the company has continued pushing error correction boundaries and qubit counts. IBM has rolled out increasingly powerful quantum systems, hitting 400+ qubits and announcing roadmaps for thousand-qubit systems within years. Multiple startups, including Ion Q and Rigetti, have demonstrated functional quantum computers accessible through cloud platforms. China, the EU, and other nations have launched massive quantum research initiatives.
The progress is real. It's measurable. It's accelerating.
But here's what really matters: even before fault-tolerant quantum computers arrive, the threat is active right now. A team of researchers from the Chinese Academy of Sciences published a paper suggesting they might be able to decrypt RSA-2048 encryption using a quantum computer with "only" 20 million qubits. That sounds impossibly large, but quantum research is doubling capacity regularly. Experts disagree on timelines, but the consensus is narrowing: nation-states could have cryptanalytically relevant quantum computers (CRQC) within 5 to 15 years.
Some security leaders think even that's optimistic. They point to undisclosed research happening in government and corporate labs that may be years ahead of public announcements. You never know what you don't know.
What matters isn't whether quantum computers arrive in 2028 or 2035. What matters is that the timeline has shifted from "theoretical threat" to "imminent probability." Organizations that wait until quantum computers are demonstrated to be practically useful will be far too late. By then, the damage to encrypted systems will already be catastrophic.
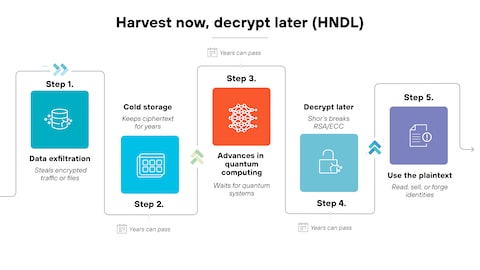
Why Harvest Now, Decrypt Later Is the Real Emergency
There's a fundamental asymmetry in cryptography that makes the post-quantum transition urgent even before quantum computers exist at scale: encryption is forward-looking, but harvesting is backward-looking.
Imagine an attacker collects TLS traffic from a major financial institution, healthcare provider, or tech company today. The traffic is encrypted with RSA-2048. Right now, with today's computers, there's no practical way to decrypt that harvest. So the attacker stores it. Terabytes of encrypted data, sitting in a server somewhere, waiting.
Fast forward 10 years. A functional quantum computer exists. The attacker runs Shor's algorithm on the archived TLS handshakes and decrypts every single session captured over the past decade. Instantly, they have access to:
- Trade secrets, R&D plans, and intellectual property
- Medical records, health diagnoses, and insurance claims
- Financial transactions, banking credentials, and account details
- Personal communications, private messages, and confidential documents
- Authentication keys that might still be in use
All of this is harvested in real-time today. The decryption happens later. And there's no way to know whether the traffic you're sending right now will be harvested and decrypted in a decade.
This is why the timeline matters so much. Data with long-term value is already at risk. Healthcare records, government documents, intellectual property, personal identities—these things have value today and will have value in 2035. If you're encrypting them with algorithms vulnerable to quantum attacks, you're betting that no quantum computer powerful enough to crack them will exist for at least the duration of the data's sensitivity.
Would you make that bet with your organization's most sensitive information?
Security agencies understand this. The US NSA has issued guidance recommending that organizations begin transitioning to post-quantum cryptography immediately. The UK, EU, Australia, and other nations have issued similar warnings. China is already standardizing quantum-resistant algorithms domestically. This isn't idle concern from paranoid security researchers. This is coordinated, high-level recognition that the threat window is closing.
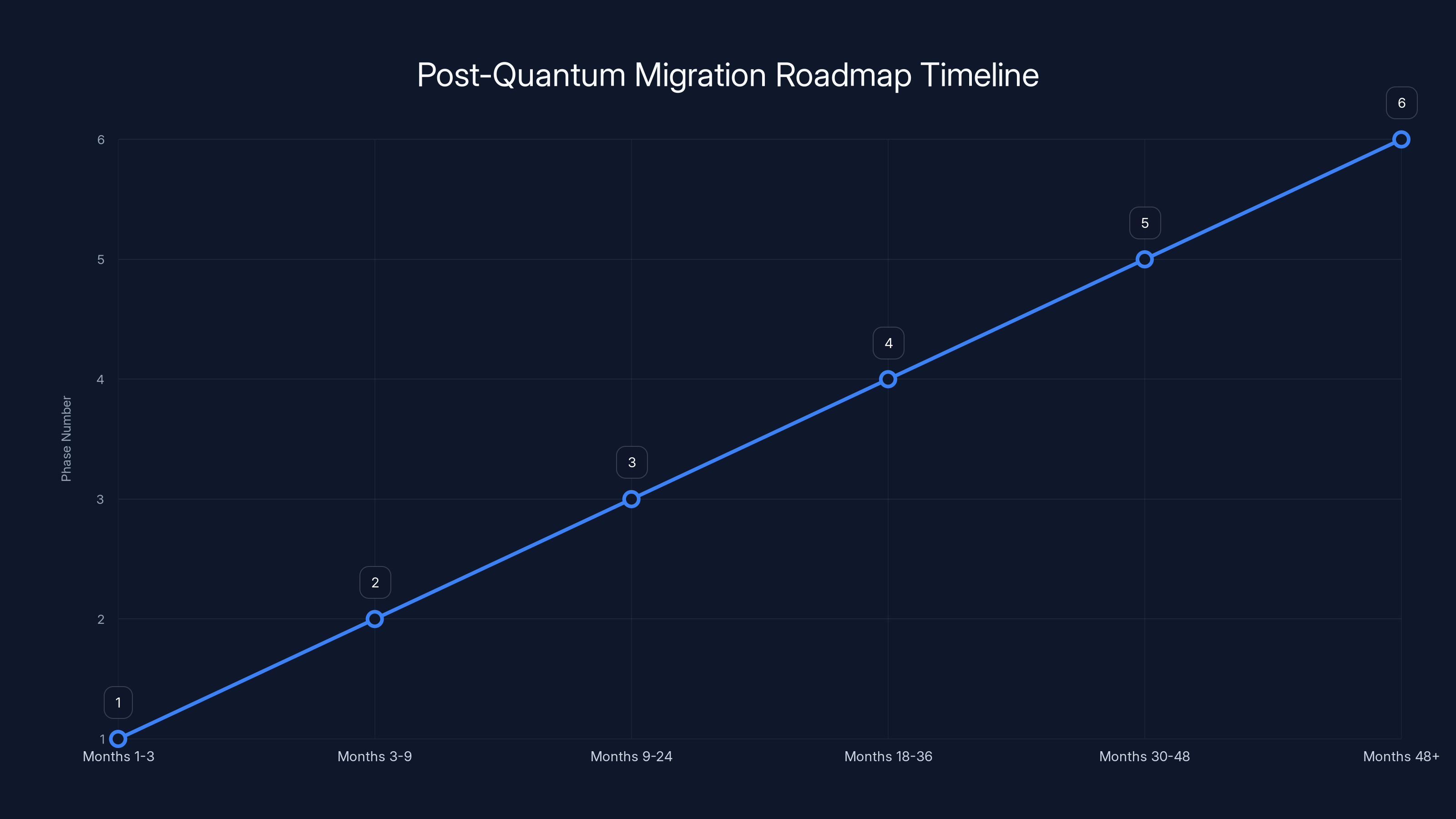
The roadmap outlines a structured multi-year transition to post-quantum cryptography, with each phase building upon the previous one. Estimated data.
How TLS Works Today and Why It's Vulnerable to Quantum Attacks
Transport Layer Security, or TLS, is the protocol that encrypts your web browsing, your emails, your API calls, and virtually every secure communication on the internet. When you visit a website with HTTPS, you're using TLS. When your application authenticates to a backend service, you're probably using TLS. It's foundational.
TLS works through a handshake process. Your client (browser, app, or service) contacts a server. The two sides agree on which encryption algorithms to use. They exchange cryptographic keys using public-key cryptography. Once the handshake completes, they have a shared secret that encrypts all subsequent traffic using symmetric encryption (much faster than public-key encryption, which is expensive computationally).
The critical moment is the key exchange. This is where public-key cryptography enters the picture.
For the past 20+ years, TLS has relied primarily on two public-key cryptosystems:
RSA (Rivest-Shamir-Adleman): Based on the difficulty of factoring large numbers into their prime components. A 2048-bit RSA key is considered secure today. Cracking it would require billions of years of classical computer time.
ECC (Elliptic Curve Cryptography): Based on the discrete logarithm problem on elliptic curves. It's more efficient than RSA and offers equivalent security with smaller key sizes. A 256-bit ECC key is roughly as secure as a 2048-bit RSA key.
Both of these algorithms are secure against classical computers. The math behind them is sound. The implementations are battle-tested. The problem is quantum computers.
In 1994, mathematician Peter Shor published a groundbreaking algorithm that solves both the integer factorization problem (breaking RSA) and the discrete logarithm problem (breaking ECC) in polynomial time on a quantum computer. Shor's algorithm is the reason that quantum computers are considered an existential threat to current encryption.
How severe is this threat? Let's put numbers on it.
A classical computer trying to break RSA-2048 through brute force would need approximately
But here's the thing that really matters: quantum computers don't just make encryption slower to crack. They make it crackable at all. The difference between "computationally infeasible" and "feasible" is the difference between security and catastrophic failure.
Increasing key sizes doesn't help. Making an RSA key twice as long doesn't make it twice as hard for a quantum computer to crack. Shor's algorithm is polynomial-time, meaning it scales gracefully even with larger key sizes. A 4096-bit RSA key, which takes classical computers millions of years to factor, would fall to a sufficiently powerful quantum computer in roughly the same timeframe as a 2048-bit key (just with more quantum gates required, but still polynomial).
This is the core of the quantum threat: not "slow," but "possible." Once quantum computers reach cryptanalytically relevant scale, classical public-key cryptography as we know it becomes obsolete overnight.
Shor's Algorithm: The Quantum Weapon That Changes Everything
Peter Shor's algorithm is deceptively elegant. It's not a brute-force attack that tries every possible key. Instead, it exploits the mathematical properties of factorization and discrete logarithms using quantum phenomena like superposition and entanglement.
Here's the intuitive version:
Classically, factoring a large number requires checking many possibilities. If you're trying to factor a number
Shor's algorithm uses quantum superposition to evaluate many possibilities simultaneously. It then uses a quantum Fourier transform to amplify the probability of the correct answer while canceling out wrong answers. When you measure the quantum state, you get the factors with high probability.
The math is intricate, but the practical implication is simple: Shor's algorithm reduces the time to break RSA-2048 from billions of years to hours or minutes, depending on quantum computer quality.
Someone building a quantum computer capable of running Shor's algorithm effectively would need:
-
Enough qubits: Estimates range from 2,000 to 20 million qubits depending on assumptions about error rates and implementation details. Current quantum computers have hundreds. Getting to thousands is hard but feasible within the next decade.
-
Low error rates: Quantum operations are fragile. Environmental noise, temperature fluctuations, and electromagnetic interference cause errors. Current quantum computers have high error rates (roughly 99% fidelity on single-qubit gates). They need to reach 99.99% or better for Shor's algorithm to work reliably.
-
Coherence time: Qubits need to stay in their quantum state long enough to complete the calculation. Current coherence times are measured in milliseconds. Longer calculations require longer coherence.
Each of these problems is solvable in principle. Companies and governments are actively solving them. The question isn't "if" but "when."
And that's why Shor's algorithm matters so much: it's not theoretical. It's not something that might work. Mathematicians have proven it works. The only questions remaining are engineering: how many qubits, how much coherence time, and how low do error rates need to be. Those are solvable problems on an engineering timeline, not a theoretical timeline.
The NIST Standardization Process: How Post-Quantum Algorithms Were Selected
The cryptographic community didn't wait for quantum computers to become real before identifying solutions. Starting in 2016, the US National Institute of Standards and Technology launched an open competition to find quantum-resistant cryptographic algorithms.
The competition was massive in scope. Researchers worldwide submitted candidates. The criteria were strict: the algorithms had to be secure against both classical and quantum attacks, efficient enough for real-world use, and implementable in existing systems with reasonable modifications.
For five years, NIST evaluated submissions. Cryptanalysts attacked them. Researchers looked for weaknesses. Some candidates fell. Others survived.
In 2022, NIST announced its first standardized post-quantum algorithms:
ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism), formerly known as Kyber, a key-establishment algorithm based on lattice cryptography.
ML-DSA (Module-Lattice-Based Digital Signature Algorithm), formerly known as Dilithium, for digital signatures.
SLH-DSA (Stateless Hash-Based Digital Signature Algorithm), formerly known as SPHINCS+, an alternative for digital signatures.
Multiple additional algorithms were standardized for specific use cases in subsequent announcements.
ML-KEM is the most relevant for TLS. It's a key-encapsulation mechanism, which means it's designed specifically for the kind of key exchange that TLS performs during its handshake.
ML-KEM is based on the Module Learning With Errors (M-LWE) problem, which is fundamentally different from the problems that RSA and ECC rely on. Instead of integer factorization or discrete logarithms, ML-KEM's security rests on the difficulty of solving linear algebra problems over lattices, even with quantum computers.
Why lattices? Because extensive research suggests that lattice problems don't have polynomial-time quantum solutions the way factorization and discrete logarithms do. The best quantum algorithms for lattice problems aren't significantly faster than the best classical algorithms. That makes lattice-based cryptography genuinely quantum-resistant.
The NIST selection process wasn't arbitrary. Each candidate underwent years of cryptanalysis. Researchers tried to break them. They looked for implementation vulnerabilities. They analyzed side-channel attacks. Thousands of hours of expert review went into confirming that these algorithms could resist quantum-scale attacks.
When NIST standardized ML-KEM, it wasn't saying "this might work." It was saying "we've analyzed this as thoroughly as possible and we believe it's your best option for quantum-resistant key exchange."
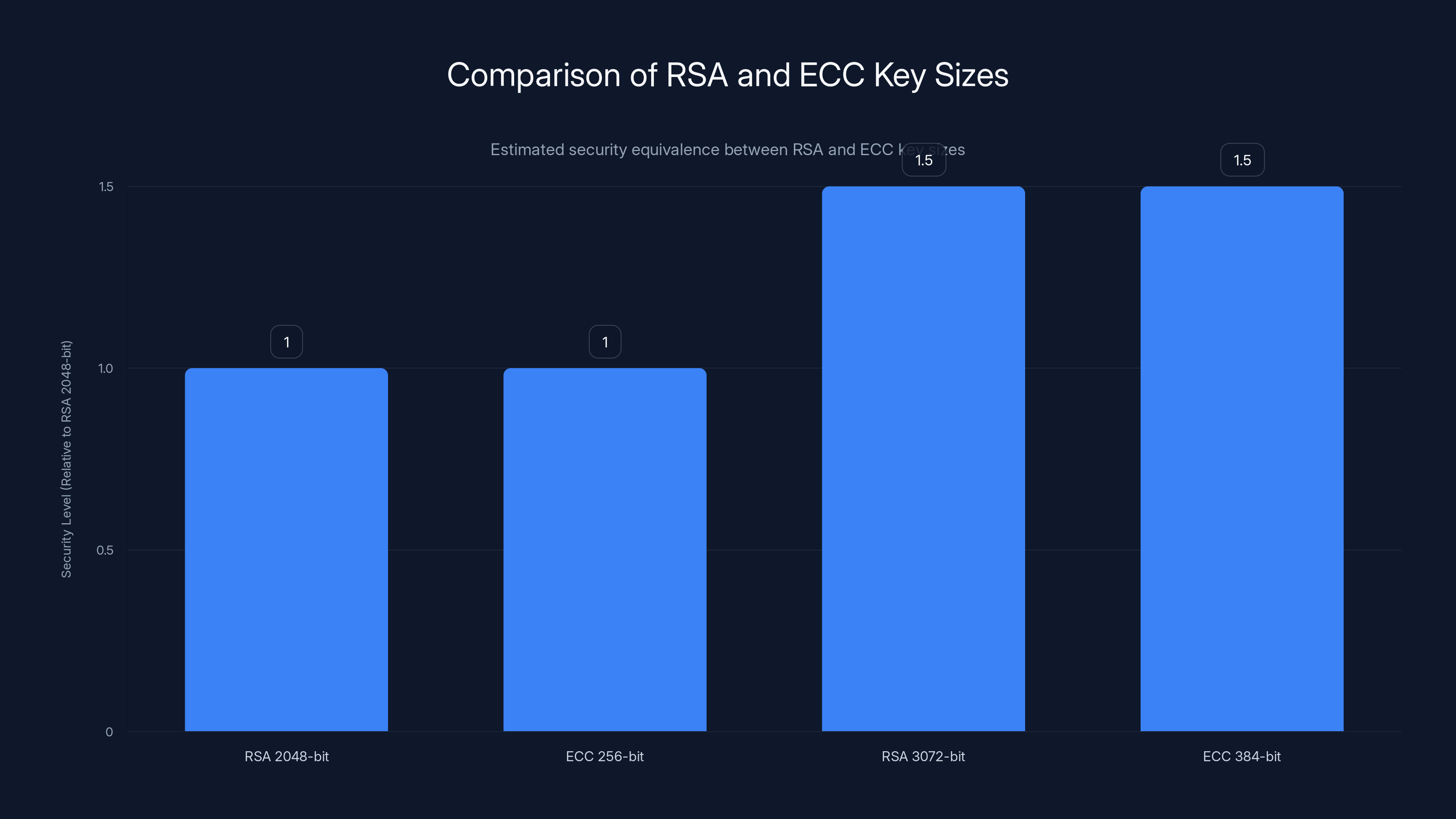
ECC provides equivalent security to RSA with smaller key sizes. A 256-bit ECC key offers similar security to a 2048-bit RSA key, demonstrating ECC's efficiency.
ML-KEM: The Foundation of Post-Quantum TLS
ML-KEM isn't just another encryption algorithm. It's specifically designed to be a drop-in replacement for the key exchange mechanisms used in TLS, while being secure against quantum attacks.
Here's what makes ML-KEM work:
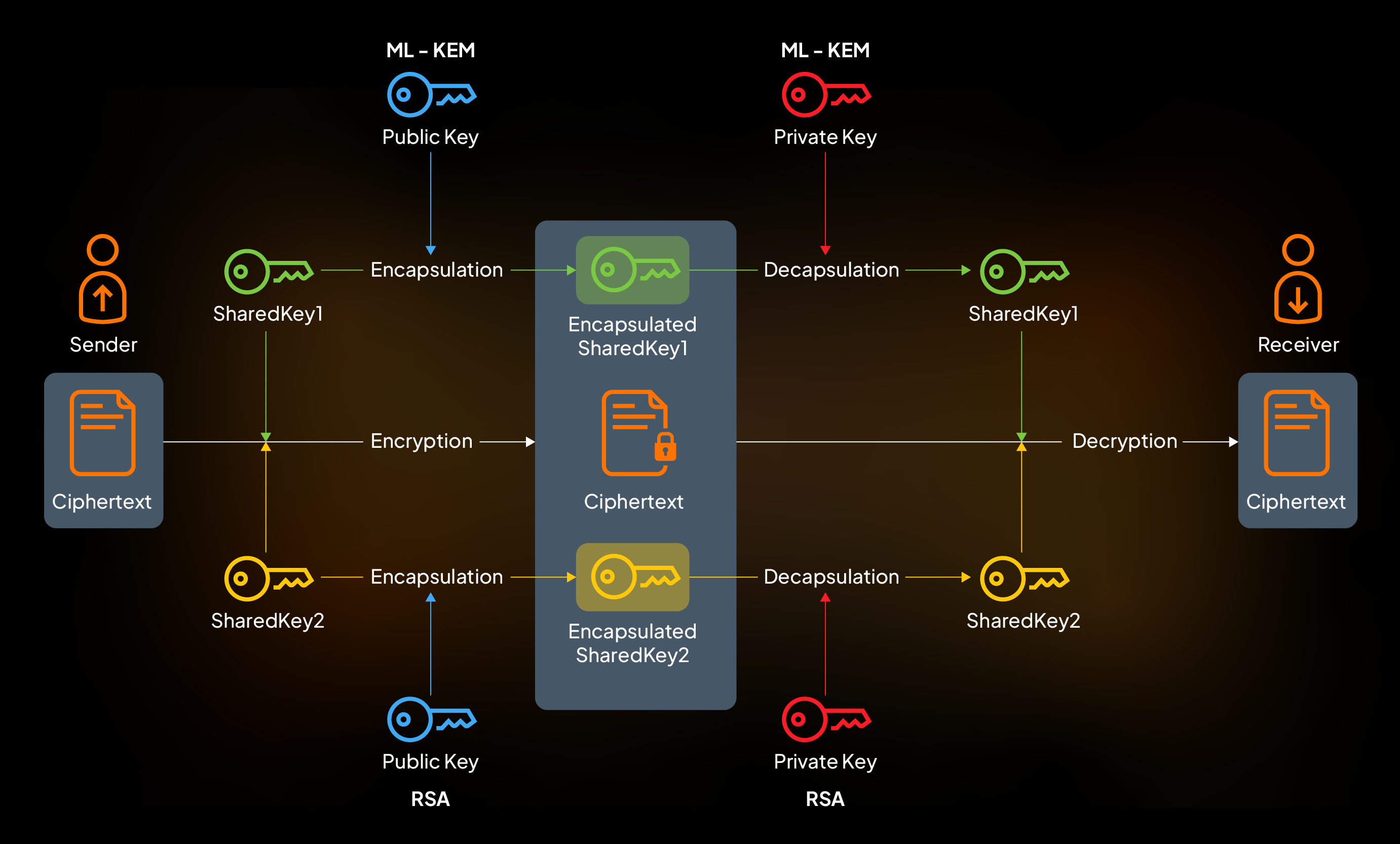
Traditionally, TLS uses elliptic curve algorithms like X25519 to perform key exchange. Two parties generate random values, exchange public information, and both independently compute a shared secret that an eavesdropper can't derive.
ML-KEM does the same thing, but using lattice mathematics. One party generates a public key based on a lattice problem. The other party uses that public key to encapsulate a secret, creating a ciphertext. The first party decapsulates the ciphertext using their private key and retrieves the same secret. Anyone eavesdropping on the public key and ciphertext can't recover the shared secret because solving the underlying lattice problem is hard.
The mathematical intuition is different from classical cryptography, but the functional result is identical: two parties derive a shared secret that's secure against eavesdropping.
ML-KEM offers multiple security levels: ML-KEM-512, ML-KEM-768, and ML-KEM-1024, offering security roughly equivalent to AES-128, AES-192, and AES-256 respectively. For most TLS deployments, ML-KEM-768 provides sufficient security.
But here's where it gets interesting for the transition: ML-KEM doesn't need to replace RSA or ECC entirely right away. Instead, TLS can use both simultaneously in a hybrid approach.

Hybrid Key Exchange: The Bridge Between Classical and Quantum-Resistant Cryptography
One of the smartest aspects of modern post-quantum transition strategies is the concept of hybrid key exchange. Instead of replacing classical algorithms immediately, organizations combine them with quantum-resistant ones.
A hybrid TLS 1.3 handshake works like this:
During the key exchange, both classical (e.g., X25519) and quantum-resistant (e.g., ML-KEM) algorithms are used simultaneously. The client generates key material using both methods. It sends public key data for both the classical and quantum-resistant components to the server. The server does the same.
Once both sides complete the exchange, they compute a shared secret that depends on both the classical and quantum-resistant key material. This combined secret is then used to derive the symmetric encryption keys for the TLS session.
The advantage is defensive depth. If either algorithm is broken tomorrow, the session is still protected because security depends on both algorithms. If the classical algorithm (X25519) is broken, quantum-resistant security remains. If somehow ML-KEM is broken, classical security remains.
This approach also ensures backward compatibility. Clients that don't support ML-KEM can still negotiate with servers that do (falling back to classical-only). Servers can support both hybrid and classical-only clients. The transition happens gradually without breaking communication.
The overhead is minimal. ML-KEM adds roughly 1 KB to the handshake size and a few milliseconds of computation. For modern networks and processors, this is negligible.
Hybrid key exchange is now the recommended approach for TLS transition. It avoids the "all or nothing" risk of replacing classical cryptography before you're sure quantum-resistant alternatives are bulletproof. It's cautious but not paralyzed.

The Industry's Post-Quantum Response: Who's Moving First
Major technology companies aren't waiting for mandates. Many are already experimenting with post-quantum TLS.
Cloudflare has been publishing detailed research on post-quantum cryptography for years and has been testing hybrid TLS with real traffic. In 2024, the company began supporting ML-KEM in experimental form for some of its services.
Google has been vocal about post-quantum transition priorities. The company announced plans to integrate post-quantum cryptography into Chrome and other products.
Amazon Web Services, Microsoft, and other cloud providers are working with customers on post-quantum readiness, offering consulting services and planning updates to their infrastructure.
Open-source projects are moving too. OpenSSL, the most widely used TLS implementation globally, has integrated support for ML-KEM. LibreSSL and other libraries are following.
But here's the problem: implementation is only half the battle. The other half is deployment.
Adding post-quantum support to a library doesn't automatically upgrade the billions of servers and applications using that library. Every organization, every application, every embedded system needs deliberate migration planning. And most organizations haven't even started.
A survey by security firm Anchore in 2024 found that over 60% of enterprise organizations hadn't begun post-quantum readiness assessments. Most don't even have visibility into which systems use public-key cryptography.
This is the crux of the urgency. The standards are done. The algorithms are vetted. The implementations are available. What's missing is organizational action.
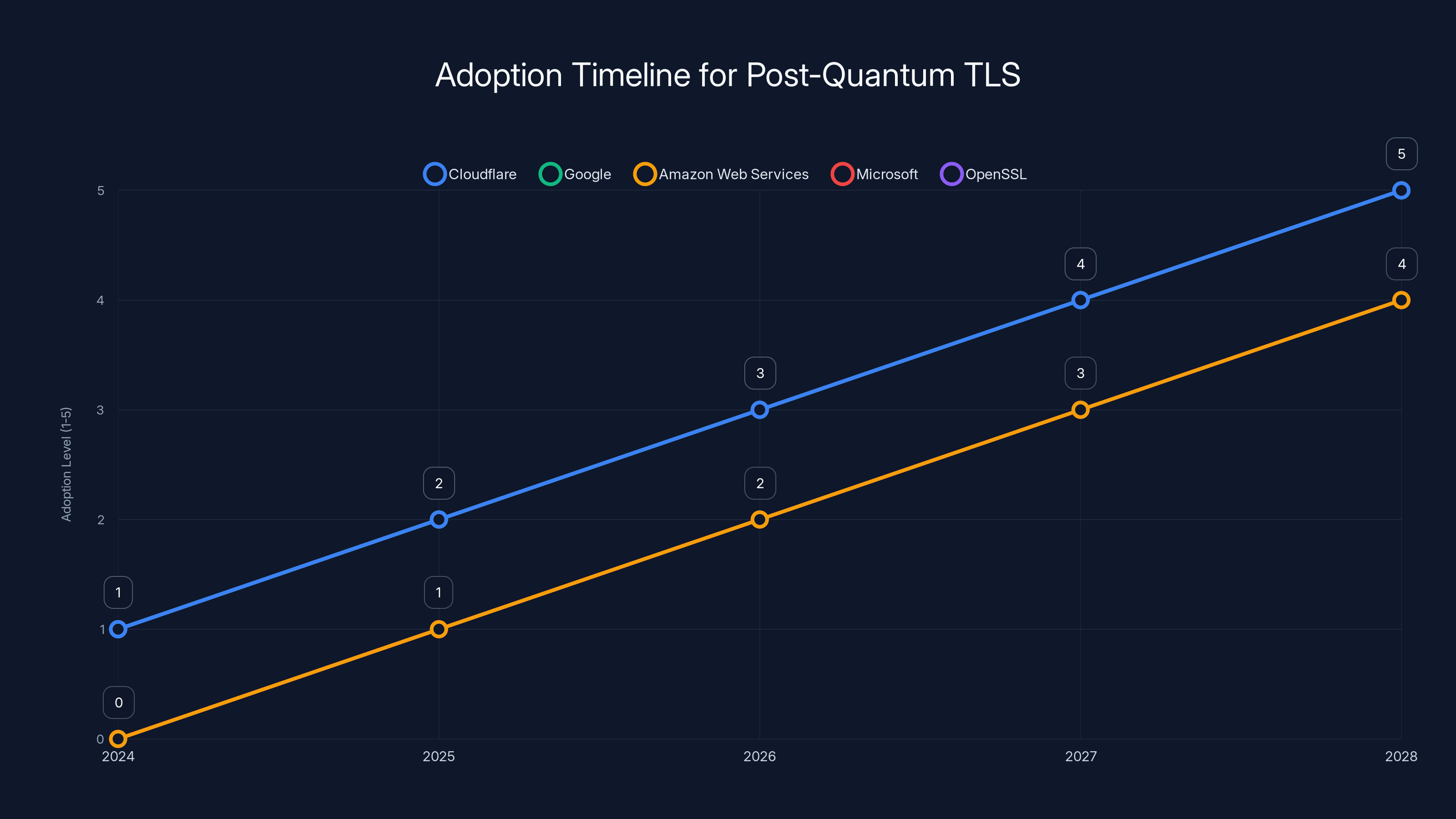
Estimated data shows that by 2028, major cloud providers and open-source projects are expected to fully support ML-KEM in production. Cloudflare and Google are leading the adoption curve.
Government Mandates and Regulatory Pressure
Governments globally are recognizing post-quantum cryptography as a strategic priority, and they're not being passive about it.
The White House released a National Security Memorandum in 2022 directing federal agencies to transition to post-quantum cryptography by 2025 for systems handling sensitive information. Subsequent guidance pushed this out to 2030 for most systems but maintained the 2025 deadline for the highest-risk categories.
The US National Institute of Standards and Technology followed up with specific implementation guidance on transitioning federal systems.
The European Union included post-quantum cryptography readiness in its proposed Cyber Resilience Act and is developing its own standardization efforts.
China has standardized the SM2PKE lattice-based algorithm for domestic use and is mandating its adoption in critical infrastructure.
The UK, Australia, Canada, and other nations have issued similar guidance and are updating their cryptographic standards.
What's driving this coordinated push? Recognition that the quantum threat is real, the transition will take years, and organizations that start early will avoid catastrophic failure when quantum computers arrive.
For US federal contractors and organizations handling government data, these mandates aren't optional. Compliance is becoming mandatory. And enforcement mechanisms are starting to emerge.
Beyond government, regulatory bodies like the SEC, HIPAA, PCI DSS, and others are beginning to include post-quantum readiness in their compliance frameworks. Some insurance companies are already asking about quantum readiness when evaluating cyber insurance coverage.
The message is clear: post-quantum cryptography isn't a future thing anymore. It's a present compliance requirement for many organizations.

Assessing Your Current Cryptographic Surface
Before you can transition to post-quantum cryptography, you need to know what you're transitioning. This sounds obvious, but many organizations lack comprehensive visibility into their cryptographic infrastructure.
Here's what a proper inventory looks like:
Network and Connectivity
- TLS certificates and which algorithms they use (RSA, ECC, or hybrid)
- VPN endpoints and their cryptographic configurations
- Load balancers and edge servers
- API gateways and how they handle encryption
- DNS security (DNSSEC) and its algorithms
Application and Data
- Internal APIs and their TLS configurations
- Messaging platforms (email, Slack, Teams, custom) and encryption
- Database connections and transport-layer encryption
- File transfer protocols (SFTP, HTTPS, custom) and key exchange methods
- Session management and how credentials are exchanged
Infrastructure and Operations
- Management interfaces (SSH, RDP, console access)
- Cluster communication (Kubernetes, Nomad, etc.) and mutual TLS
- Deployment pipelines and signing of code/artifacts
- Monitoring and observability infrastructure (security events, logs)
- Backup systems and how they authenticate to storage
Legacy and Specialized Systems
- Embedded systems and Io T devices using cryptography
- Industrial control systems and critical infrastructure
- Legacy applications that can't be easily updated
- Custom protocols using cryptography
Third-Party and External Dependencies
- Cloud provider services and their cryptographic standards
- Saa S applications and their TLS implementations
- API integrations and how they handle authentication
- CDN and DDo S protection services
- Hardware security modules and their algorithm support
Creating this inventory typically requires collaboration across teams: infrastructure, security, application development, compliance, and procurement. It's not a quick job, but it's essential.
During the inventory phase, also assess which systems have long-term data sensitivity. Not everything needs immediate post-quantum protection. A TLS session for a web page has minimal sensitivity—it's forgotten in seconds. A session containing trade secrets, medical records, or authentication tokens might be relevant for decades.
Prioritize accordingly.

Testing Hybrid TLS Configurations: How to Get Started
Once you've identified systems using TLS, the next step is testing hybrid configurations with quantum-resistant algorithms.
Here's a practical approach:
Step 1: Set Up a Test Environment
Create an isolated test network that mirrors your production TLS setup but doesn't carry production traffic. This might be a staging environment, a development cluster, or a lab setup. The goal is to test changes without risking availability.
Step 2: Deploy Updated TLS Libraries
Update OpenSSL, libssl, or whatever TLS library you use to a version supporting ML-KEM. Most major libraries have support in versions released in 2023-2024. Check your distribution's package repositories or build from source if necessary.
Step 3: Generate Hybrid Certificates
Your server certificates can contain both classical and post-quantum public key material. If using X.509 certificates (standard for TLS), you can either:
- Use composite certificates that include both algorithms
- Use classical certificates with PQ support negotiated during the handshake
Most implementations currently use the second approach because X.509 standards for composite certificates are still evolving.
Step 4: Configure TLS for Hybrid Key Exchange
In your TLS server configuration (nginx, Apache, HAProxy, etc.), enable hybrid key exchange. For OpenSSL-based servers, this might look like:
SSLECDHCurve X25519: kyber 768
Specific syntax varies by server, but the goal is the same: negotiate both classical and quantum-resistant key exchange.
Step 5: Test Client Compatibility
Connect various clients to your hybrid TLS endpoint:
- Modern browsers (Chrome, Firefox, Safari)
- curl and wget
- API clients in your applications
- Mobile clients
- Any older systems you support
Doc the results. Which clients support hybrid key exchange? Which fall back to classical? Which fail?
This testing phase reveals compatibility issues before production deployment.
Step 6: Monitor Performance and Side Effects
Run load tests on your hybrid TLS endpoint. Measure:
- Handshake latency (should be minimal, under 5ms additional)
- Throughput (should be identical to classical-only)
- CPU usage (should be negligible increase, unless hybrid key exchange is particularly expensive for your hardware)
- Memory usage
- Error rates
Also watch for unexpected behavior: certificate validation failures, protocol negotiation issues, timeouts, etc.
Step 7: Gradual Rollout
Once testing is successful, roll out hybrid TLS to production gradually:
- Internal APIs and non-customer-facing services first
- Customer-facing APIs and web services
- Load balancers and edge infrastructure
- Backward-compatibility endpoints (fallback to classical-only for older clients)
Monitor each phase for issues. Have a rollback plan.
The entire process typically takes weeks to months depending on the complexity of your infrastructure.
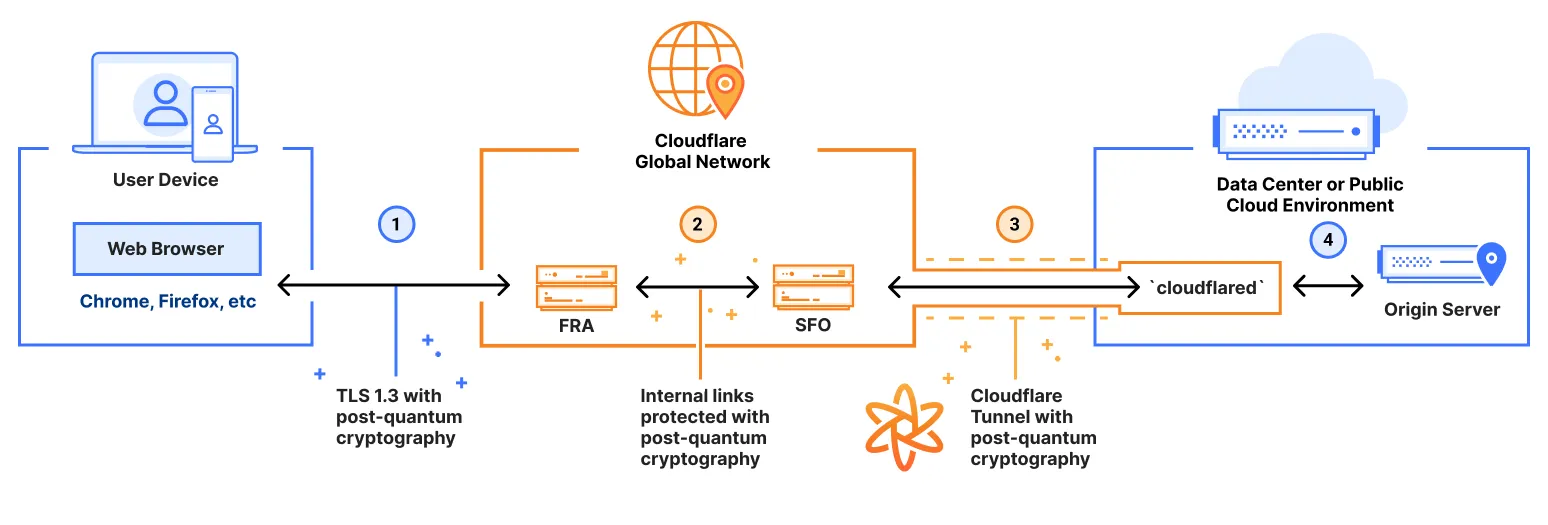
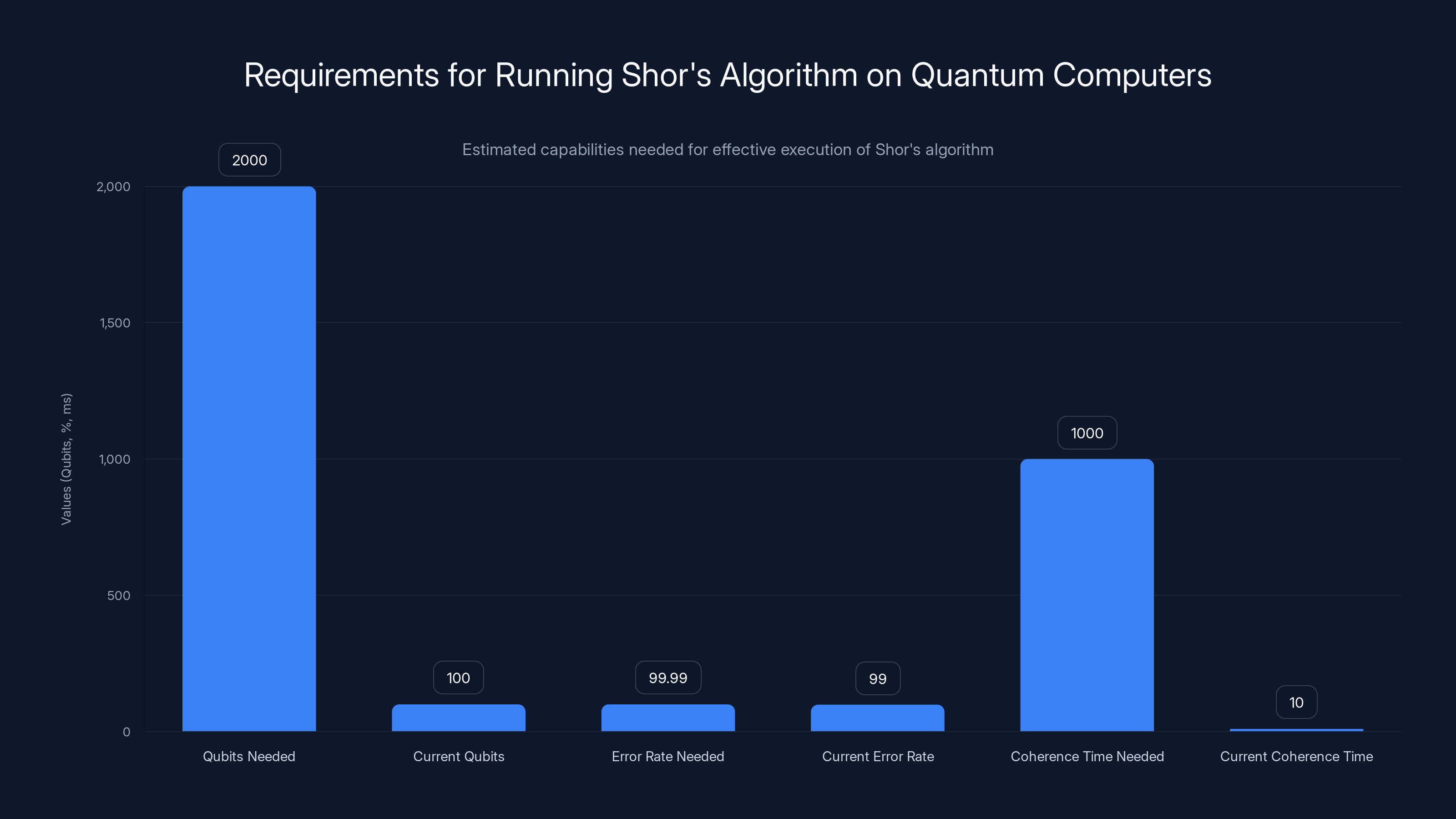
To effectively run Shor's algorithm, quantum computers need significant improvements in qubit count, error rates, and coherence time. Estimated data.
Vendor Assessment and Supply Chain Readiness
Your organization doesn't exist in isolation. You depend on vendors, cloud providers, SaaS platforms, and open-source components. All of them need to be post-quantum ready, or they become weak links in your security posture.
Start by assessing your critical vendors:
Cloud and Infrastructure Providers
- AWS, Azure, Google Cloud, and others should have post-quantum readiness roadmaps
- Ask about their TLS transition timelines
- Verify they'll support hybrid key exchange
- Understand their certificate replacement strategies
Software and SaaS Vendors
- Enterprise software often has long update cycles
- Ask vendors about post-quantum support timelines
- If a vendor can't commit to post-quantum cryptography, it's a risk factor
- For mission-critical systems, include post-quantum readiness in contract negotiations
Library and Framework Maintainers
- Your applications likely depend on third-party libraries
- Check whether those libraries support post-quantum cryptography
- For widely used libraries, support is usually available or in progress
- For niche libraries, you may need to contribute patches or maintain forks
Hardware Providers
- If you use hardware security modules (HSMs), verify they support ML-KEM
- Some HSMs are slow to add new algorithms; this might be a bottleneck
- Network appliances (load balancers, firewalls) should support post-quantum TLS
Certificate Authorities
- Your TLS certificates come from CAs
- Not all CAs support issuing composite certificates or hybrid certificates yet
- Verify your CA's roadmap for post-quantum support
- Some CAs are ahead of others; shop around
Document all of this. Create a matrix of vendors, their post-quantum support status, and their expected completion dates. Where there are gaps, create action items: reach out to vendors, request support, plan workarounds, or plan to switch vendors.
The supply chain is often where post-quantum transition stalls. A vendor using ancient, unsupported cryptographic libraries can block your entire organization's transition. Identifying these risks early gives you time to address them.

Building Your Post-Quantum Migration Roadmap
Post-quantum cryptography transition isn't a one-time event. It's a multi-year program with phases, dependencies, and risk management.
Here's a structured approach to building your roadmap:
Phase 1: Foundation and Awareness (Months 1-3)
- Complete cryptographic inventory
- Assess vendor readiness
- Educate internal teams on quantum threats and post-quantum solutions
- Secure executive sponsorship and budget
- Establish a post-quantum steering committee
Phase 2: Pilot and Testing (Months 3-9)
- Deploy hybrid TLS in development and staging environments
- Test with various clients and use cases
- Identify integration challenges
- Create internal guidance and best practices
- Train development and operations teams
Phase 3: Internal Transition (Months 9-24)
- Deploy hybrid TLS to internal APIs and non-public services
- Transition internal certificate generation to post-quantum capable CAs
- Update configuration management and deployment pipelines
- Monitor for performance and compatibility issues
- Gradual rollout to additional internal systems
Phase 4: Customer-Facing Transition (Months 18-36)
- Deploy hybrid TLS to public APIs and web services
- Communicate with customers about the change (non-breaking, backward compatible)
- Monitor for compatibility issues
- Create migration guides for customers using your APIs
- Maintain classical fallback for legacy clients
Phase 5: Full Quantum-Ready Infrastructure (Months 30-48)
- Complete transition from classical-only to hybrid infrastructure
- Update all TLS certificates to include post-quantum support (when composite certificates mature)
- Retire classical-only TLS endpoints (keep legacy fallback for extended period)
- Transition digital signatures to post-quantum algorithms
- Address any remaining cryptographic dependencies
Phase 6: Post-Quantum Only (Months 48+)
- After quantum computers are demonstrated at scale, transition from hybrid to post-quantum-only
- This phase only happens once hybrid is proven stable and universal support is achieved
- Full transition happens only when classical algorithms are definitively broken by quantum computers
Each phase includes specific milestones, success metrics, and risk mitigation strategies.
Success Metrics to Track:
- Percentage of TLS endpoints supporting hybrid key exchange
- Percentage of vendor partners supporting post-quantum cryptography
- Certificate inventory completely migrated to post-quantum capable CAs
- Zero compatibility issues reported from customers or internal systems
- Post-quantum cryptography support in 100% of critical applications
- Employee training completion rates
Risk Mitigation:
- Run pilot phases in non-critical systems first
- Maintain rollback plans and classical fallback indefinitely
- Test extensively before production deployment
- Monitor performance closely; scale back if issues arise
- Keep communication open with customers and vendors
- Plan for unexpected compatibility issues

Common Mistakes and How to Avoid Them
Organizations transitioning to post-quantum cryptography often make predictable mistakes. Learning from others' experience can save significant time and resources.
Mistake 1: Ignoring Legacy Systems
Many organizations focus on modern cloud infrastructure and forget about legacy systems. That 15-year-old embedded device running on classical cryptography? It's still a vulnerability. Legacy systems often can't be easily updated and become orphaned in the transition.
Avoid this by:
- Inventorying all systems comprehensively, including legacy
- Planning migration or retirement of unsupported systems early
- For systems that can't be updated, implement network segmentation to limit exposure
- Using intermediate proxies or gateways to upgrade cryptography for legacy systems
Mistake 2: Underestimating Vendor Timelines
Many organizations assume vendors will quickly support post-quantum cryptography. Some will. Others won't. Niche vendors especially might drag their feet or abandon products entirely.
Avoid this by:
- Assessing vendor readiness early, not late
- Building extra time into your roadmap for vendors that are slow
- Planning for vendor changes (switching to alternatives, in-house development)
- Including post-quantum support in vendor contracts and SLAs
Mistake 3: Rushing Full Replacement
Some security teams want to remove classical cryptography immediately. This is premature and risky. Hybrid key exchange for a transition period is the right approach.
Avoid this by:
- Maintaining classical algorithm support as fallback for multiple years
- Testing thoroughly with hybrid before considering full replacement
- Keeping hybrid even after quantum computers emerge (multiple algorithm support is good defense)
- Planning for full replacement only after classical algorithms are definitively broken
Mistake 4: Overlooking Certificate Management
Transitioning certificates to post-quantum capable CAs requires careful planning. Certificate renewals, intermediate CAs, and root CAs all need updates. Many organizations underestimate this complexity.
Avoid this by:
- Assessing your CA's post-quantum roadmap early
- Planning for certificate regeneration and renewal well in advance
- Automating certificate renewal and deployment
- Testing certificate rotation thoroughly
Mistake 5: Not Training Your Teams
Post-quantum cryptography is unfamiliar to most developers and operators. Without training, they'll struggle with implementation, testing, and troubleshooting.
Avoid this by:
- Providing education on quantum threats and post-quantum solutions
- Training on specific algorithms (ML-KEM, ML-DSA) and their properties
- Hands-on labs with hybrid TLS configurations
- Ongoing communication as implementations evolve
Mistake 6: Ignoring Performance Impact
While hybrid key exchange has minimal overhead, some organizations don't measure it properly and are surprised by impacts on latency or throughput.
Avoid this by:
- Testing performance early and thoroughly
- Measuring not just TLS handshake time but end-to-end performance
- Comparing against baseline classical-only performance
- Planning for hardware upgrades if needed
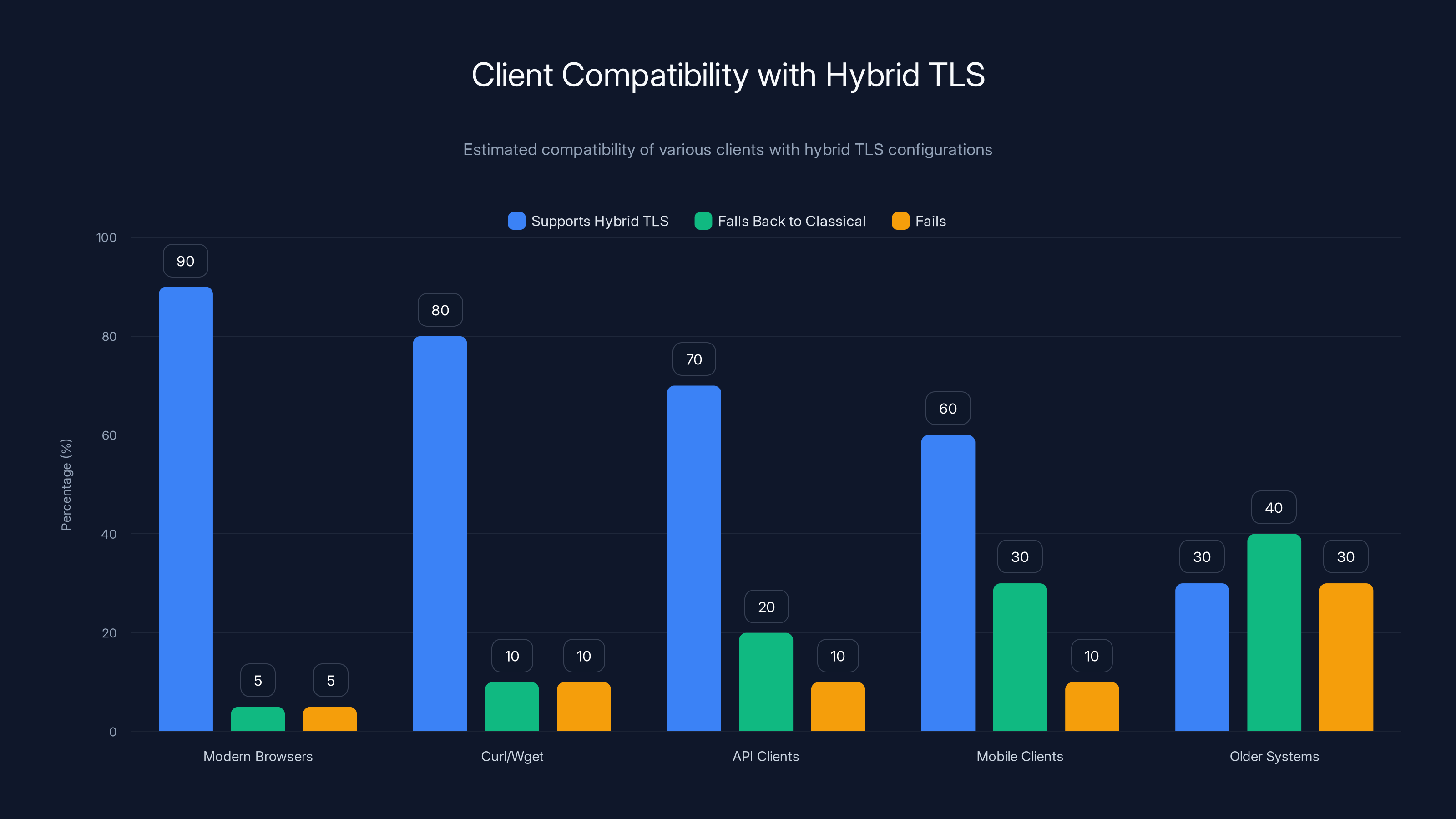
Estimated data shows modern browsers have the highest support for hybrid TLS, while older systems struggle, often failing to connect.
The Role of Digital Signatures and Authentication
While most attention on post-quantum cryptography focuses on TLS key exchange, digital signatures are equally important and similarly threatened by quantum computers.
Digital signatures are used for:
- Code signing (verifying software hasn't been tampered with)
- Document signatures (authenticating documents)
- Certificate signing (CAs signing TLS certificates)
- API authentication (signing API requests)
- Blockchain and cryptocurrency (signing transactions)
All of these rely on public-key algorithms like RSA or ECDSA, both vulnerable to Shor's algorithm.
Postquantum digital signature algorithms are part of the NIST standardization:
ML-DSA (formerly Dilithium) is the primary recommendation for general-purpose digital signatures. It's based on lattice cryptography like ML-KEM.
SLH-DSA (formerly SPHINCS+) is a hash-based alternative that's more conservative but less efficient.
Transitioning digital signatures is as important as transitioning TLS, but often overlooked. Code signing especially is critical: if an attacker can forge signatures on software updates, they can compromise infrastructure at scale.
Your post-quantum roadmap needs to address both key exchange (via TLS) and signatures (via certificates, code signing, document signing, etc.).

What About Quantum Key Distribution?
Some organizations think quantum key distribution (QKD) is the solution to quantum threats. It's not, and understanding why is important for your strategy.
Quantum key distribution uses quantum mechanics to distribute cryptographic keys with theoretical perfect security (assuming no hardware implementation flaws). It sounds like it should be the answer to quantum-resistant communication.
But QKD has severe limitations:
Cost: QKD systems are extremely expensive—tens of thousands to millions of dollars to deploy. Hybrid TLS with ML-KEM costs nearly nothing.
Distance: Most QKD systems work only over distances measured in tens of kilometers. Intercontinental communication requires intermediate repeaters, which introduce security complexities.
Maturity: QKD is less mature than post-quantum cryptography. Most implementations are experimental or limited to specialized use cases.
Integration: QKD requires specialized hardware and infrastructure. Integrating it with existing systems is complex.
Authentication: QKD solves key distribution but doesn't solve authentication. You still need digital signatures, which require post-quantum algorithms.
QKD might be valuable for specific high-security use cases (government agencies, critical infrastructure), but it's not a practical solution for general enterprise infrastructure. Post-quantum cryptography is the mainstream solution.
For most organizations: focus on post-quantum algorithms, not QKD.

Looking Forward: The Quantum-Ready Enterprise
Where does this all lead? What does post-quantum cryptography look like in practice for a modern organization?
By 2027-2030, a security-mature organization looks like this:
All TLS endpoints support hybrid key exchange combining classical and quantum-resistant algorithms. This provides immediate quantum resistance while maintaining backward compatibility and classical fallback.
All new TLS certificates include post-quantum public key material, either through composite certificates or negotiation during handshake. Legacy classical-only certificates are being phased out, but not eliminated until clients are fully upgraded.
Code signing and document signatures use post-quantum algorithms (ML-DSA or alternatives). Software distribution and critical documents are protected against both classical and quantum forgery.
Cryptographic libraries and infrastructure support multiple algorithms. Organizations aren't dependent on a single algorithm but have depth: if ML-KEM is compromised, alternatives exist. If a single vendor's implementation has a flaw, others provide options.
Vendor and partner ecosystems are post-quantum ready. The supply chain supports the transition. Organizations don't get stuck waiting for a critical vendor to update.
Legacy systems are either updated, retired, or network-segmented. Nothing is running unprotected public-key cryptography that can't be upgraded.
Teams are trained and capable. Developers, operators, and security staff understand post-quantum cryptography, implement it correctly, and troubleshoot issues.
Compliance requirements are met. Government mandates, regulatory frameworks, and industry standards are satisfied.
By the time quantum computers reach cryptanalytic relevance (possibly 2030-2035), the infrastructure is already quantum-resistant. The transition from hybrid to post-quantum-only happens smoothly as classical algorithms are definitively broken.
This is the achievable goal. It requires work, planning, and consistent execution. But it's eminently doable for organizations that start now.
The Quantum Threat Isn't Distant Anymore
Here's the reality: quantum computing's trajectory has accelerated dramatically. The gap between theory and practical capability is narrowing faster than most organizations expected. And by the time quantum computers are powerful enough to be weaponized, it will be too late to start transitioning cryptography.
You can't retroactively decrypt data that wasn't encrypted with post-quantum algorithms. You can't unsign software that was signed with classical algorithms. You can't roll back months of harvested encrypted communication.
Post-quantum cryptography transition isn't something to plan for 2030. It's something to start now, execute over the next 24-36 months, and mature progressively.
The good news: you're not starting from scratch. Standards are finalized. Implementations are available. Best practices exist. Guides and tools proliferate. The path forward is clear.
What's required is organizational commitment and consistent execution. Inventory your cryptographic surface. Test hybrid configurations. Assess vendors. Build your roadmap. Start small and scale. Learn from early deployments. Adjust as needed.
The quantum era is coming. Your infrastructure should be ready.

FAQ
What exactly is post-quantum cryptography?
Post-quantum cryptography refers to encryption and digital signature algorithms designed to resist attacks from both classical and quantum computers. These algorithms use mathematical problems (like lattice-based cryptography) that remain hard to solve even with quantum computers, unlike current algorithms such as RSA and ECC which are vulnerable to Shor's algorithm on quantum computers.
When will quantum computers be able to break current encryption?
Expert timelines vary, but most estimates suggest cryptanalytically relevant quantum computers could arrive within 5 to 15 years. However, the "Harvest Now, Decrypt Later" threat means attackers are already collecting encrypted data today to decrypt using future quantum computers, making the timeline for action urgent regardless of when quantum computers materialize.
Is hybrid key exchange mandatory or just recommended?
Hybrid key exchange is currently the recommended approach for TLS transition rather than mandatory. It provides immediate quantum resistance while maintaining classical security as a fallback. This allows organizations to test and gradually deploy post-quantum algorithms without breaking compatibility. However, government mandates and regulatory frameworks are making it increasingly necessary for organizations handling sensitive data.
How much does ML-KEM add to TLS handshake time?
ML-KEM adds minimal overhead to TLS handshakes, typically increasing latency by just a few milliseconds. The increase in data transmitted is roughly 1 KB for the key encapsulation material. For modern networks and processors, this overhead is negligible and rarely noticeable to end users.
Can I just increase my RSA key size to stay secure against quantum computers?
No. Increasing RSA key size provides no additional security against quantum computers. Shor's algorithm solves the factorization problem in polynomial time regardless of key size. A 4096-bit RSA key falls as easily to a quantum computer as a 2048-bit key. You need fundamentally different algorithms based on quantum-hard problems, like lattice-based cryptography.
What should I do first if I'm starting a post-quantum transition?
Start with a comprehensive cryptographic inventory of all systems using public-key cryptography, including TLS, VPNs, internal APIs, and digital signatures. Then assess your vendors' post-quantum readiness and create a phased migration roadmap prioritizing high-value assets. Finally, set up a test environment to validate hybrid TLS configurations before production deployment.
Is NIST's ML-KEM algorithm definitely secure, or could it be broken?
ML-KEM underwent five years of intense cryptanalysis from researchers worldwide as part of NIST's standardization process. While no algorithm can be guaranteed secure forever, ML-KEM represents the current best practice for quantum-resistant key establishment. The lattice problems it relies on have no known polynomial-time quantum solutions, making it credibly quantum-resistant based on current understanding.
Do I need to update my cloud provider to support post-quantum TLS?
Most major cloud providers (AWS, Azure, Google Cloud) are developing post-quantum capabilities and have publicly stated timelines for hybrid TLS support. However, you should verify your specific provider's roadmap and timeline. Some services may require migration to newer infrastructure or versions. Start conversations with your providers now rather than waiting for mandatory transitions.

Key Takeaways
- Quantum computers threaten to break RSA and ECC cryptography within 5-15 years, and attackers are harvesting encrypted data today to decrypt later.
- ML-KEM, standardized by NIST, provides quantum-resistant key exchange suitable for deployment in TLS today.
- Hybrid key exchange combining classical algorithms with ML-KEM provides immediate quantum protection while maintaining backward compatibility.
- Organizations must start post-quantum transition now through cryptographic inventory, hybrid testing, vendor assessment, and phased migration roadmaps.
- Government mandates, regulatory pressure, and the irreversible nature of encrypted data make post-quantum readiness a present priority, not a future luxury.

![Post-Quantum Cryptography: Securing TLS for the Quantum Era [2025]](https://tryrunable.com/blog/post-quantum-cryptography-securing-tls-for-the-quantum-era-2/image-1-1767604098181.jpg)



