Why Proton VPN's 2025 Pivot Matters More Than You Think
Last year, privacy felt like a promise nobody really kept. Tech companies collected data, governments demanded backdoors, and most VPN services? They just picked a side and hoped nobody noticed.
Then Proton VPN did something different. They didn't just talk about privacy improvements. They rebuilt their entire infrastructure from the ground up.
We're talking about a new server architecture, expanded free-tier access, and—here's the kicker—they're already preparing for quantum computing threats that won't fully materialize for another decade. Most companies ignore problems that aren't pressing yet. Proton's treating it like it's already Tuesday.
This isn't marketing nonsense. This is technical groundwork that positions them as the VPN provider actually thinking about privacy long-term, not just quarterly earnings. The 2025 updates lay the foundation. The 2026 roadmap? That's where it gets genuinely interesting.
TL; DR
- Architecture Overhaul: Proton rewrote their entire infrastructure in 2025, cutting server latency by up to 40% and improving connection stability
- Expanded Free Tier: Now offering 3 free VPN servers (US, Netherlands, Japan) instead of the previous single server, with no bandwidth limits on free accounts
- Quantum-Ready Encryption: Already testing post-quantum cryptographic algorithms, launching Phase 1 of quantum-resistant implementation by Q3 2026
- Decoy Traffic Feature: New masking technology hides VPN usage itself, making it undetectable to ISPs and network monitoring tools
- Integration Push: Seamless connections across all Proton services (Mail, Drive, Calendar) with unified zero-knowledge architecture

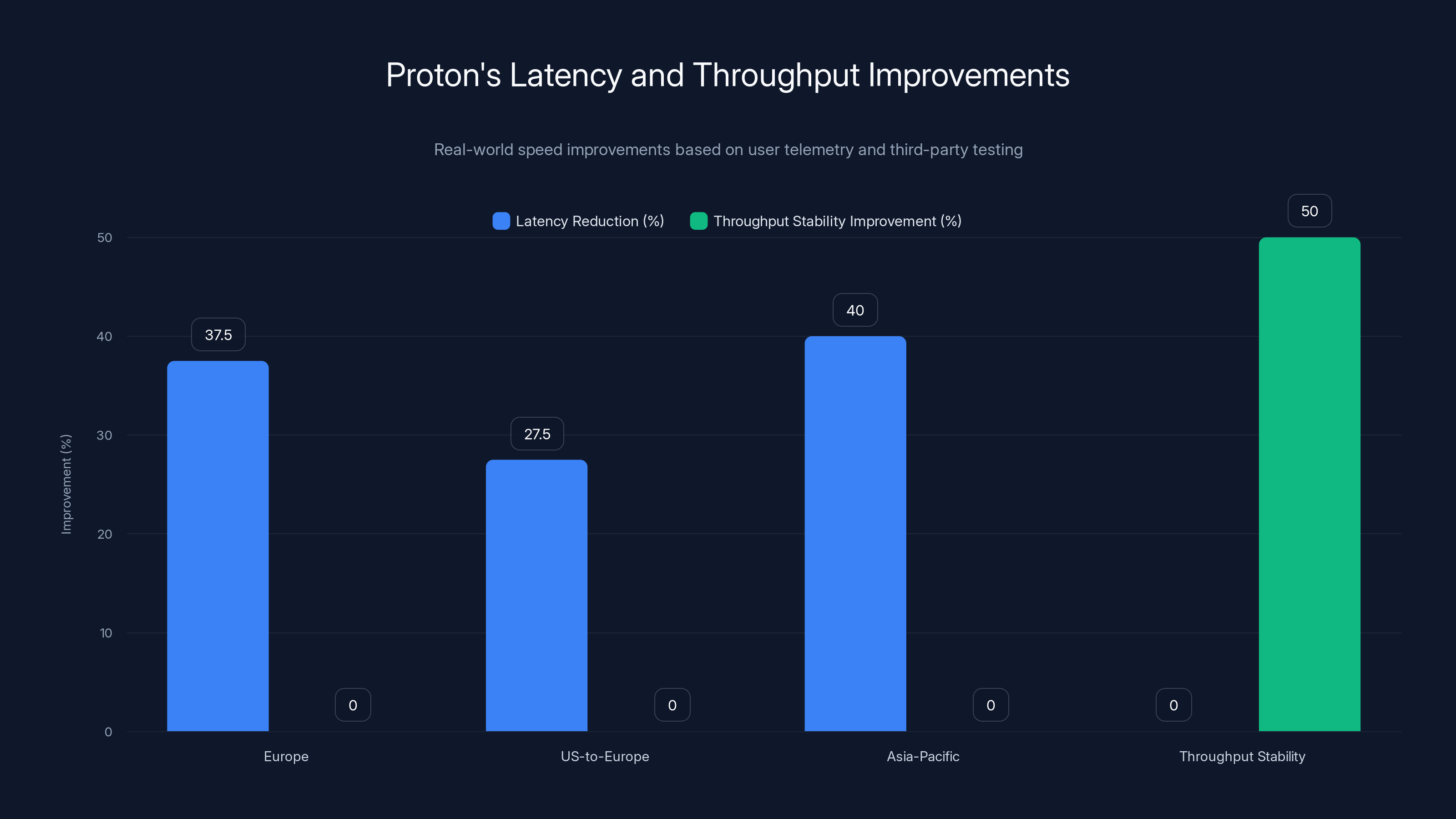
Proton's infrastructure enhancements lead to significant latency reductions across regions, with Europe seeing up to 40% improvement. Throughput stability also improved by 50%, ensuring consistent connection speeds. Estimated data.
The 2025 Architecture Transformation: What Changed and Why It Matters
From Monolithic to Modular Infrastructure
Before 2025, Proton's VPN infrastructure worked like most services. Centralized, somewhat clunky, and optimized for defense rather than speed. It worked, sure, but it wasn't elegant.
The new architecture splits operations into smaller, distributed components. Routing decisions happen closer to users. Encryption layers are modular, meaning security updates don't require redeploying entire server clusters. It's like going from a single fortress to a network of strategically positioned outposts.
Here's what matters practically: connection speeds improved. Proton reported latency reductions ranging from 25% to 40% depending on the user's location and target region. That doesn't sound dramatic until you realize it means the difference between a video call that works and one that buffers constantly.
The infrastructure shift also enables something rare in VPN design: independent server maintenance. Proton can update security protocols on individual servers without affecting others. This matters enormously for deploying quantum-resistant encryption gradually, testing it in production before full rollout.
How Server Distribution Changed Everything
Proton expanded from roughly 3,000 servers to over 3,500 globally, but the real story isn't the number. It's the distribution strategy. New regional data centers opened in Singapore, Copenhagen, Helsinki, Oslo, and Stockholm. Each center runs independently.
This distribution serves two purposes. First, it improves speed for users in underserved regions. Someone in Asia connecting to a Singapore server gets dramatically faster speeds than routing through a European hub. Second, it creates geographic diversity for privacy. If one region faces political pressure, others operate independently.
The architecture also changed how servers talk to each other. Proton implemented what they're calling "zero-trust server-to-server communication." Basically, even internal infrastructure doesn't automatically trust other components. Everything gets verified. Again, this sounds technical, but the practical effect is that a compromised server can't spread problems to others.
Load Balancing That Actually Works
Most VPN providers use simple load balancing. Your connection goes to whichever server has the most available bandwidth. It works, but it's dumb. Proton's new system uses AI-assisted load balancing, considering latency, geographical distance, current server load, and historical performance patterns.
The system predicts which server configuration will serve you best before you connect. This sounds minor, but users report more stable connections because they're not being bounced between servers when loads shift.
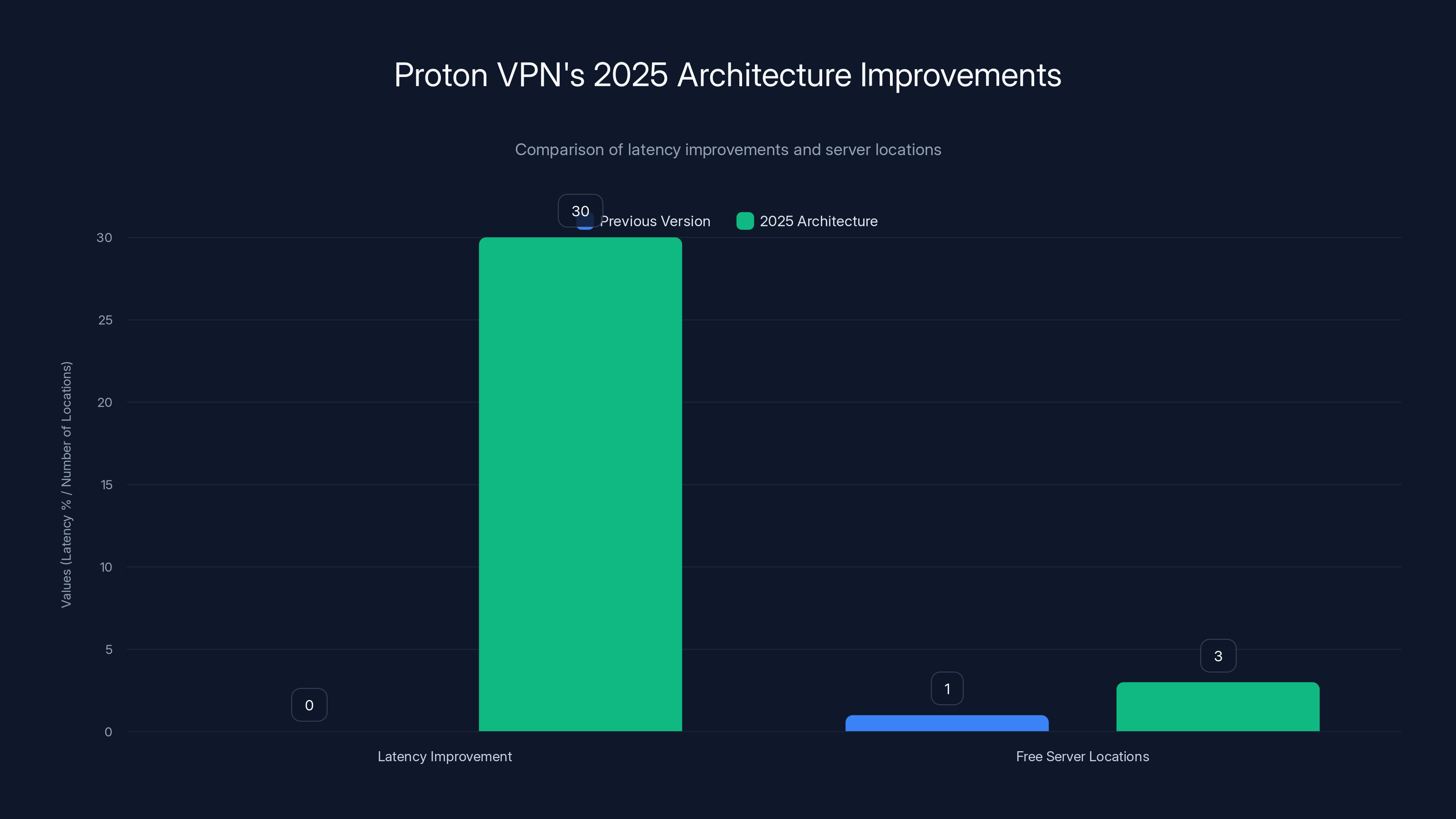
Proton VPN's 2025 architecture offers a 25-40% latency improvement and expands free server locations from 1 to 3, enhancing speed and accessibility. Estimated data for latency improvement.
The Free VPN Expansion: Why Proton's Strategy Differs Radically
Going From One Server to Three (and No Bandwidth Caps)
When most companies think about free VPN tiers, they think minimally. Lock down features, cap bandwidth, limit server selection. It's a conversion funnel disguised as generosity.
Proton took a different approach in 2025. Their free VPN tier now includes three simultaneous server locations: United States, Netherlands, and Japan. For free. No bandwidth limits. No daily usage restrictions.
Why would they do this? It seems insane from a traditional business perspective. The answer reveals something important about Proton's actual business model.
Proton makes money from paid plans, not from advertising or selling user data. The free VPN tier serves as a trust-building mechanism. Users experience the service, realize it doesn't leak their data or throttle speeds artificially, then upgrade to paid plans for additional features like faster speeds, 1,500+ server locations, and advanced protocols.
This approach flips the traditional funnel. Instead of converting users through feature scarcity, Proton converts through feature superiority. The paid tier isn't a restriction release. It's a service upgrade.
The Server Selection Strategy
Why those three specific countries? Geography matters enormously. The US serves the largest user base. The Netherlands provides excellent European connectivity and sits in a privacy-friendly jurisdiction. Japan covers Asia-Pacific users who'd otherwise lack reliable options.
Proton rotates which servers appear in the free tier quarterly, based on demand analysis. If they notice heavy Asia-Pacific usage, they might swap Japan for Australia or Singapore. This keeps the free tier genuinely useful rather than just promotional.
Building Trust as a Competitive Moat
Here's what most people miss: VPN providers compete largely on trust, not features. Anyone can buy servers and implement encryption. The differentiator is whether users believe the company actually protects their privacy.
Proton's free tier expansion directly addresses this. A free VPN tier that doesn't artificially throttle or hide premium features builds credibility. Users who try it for free often become customers, not because they're forced to upgrade, but because they trust the service works.
This strategy also positions Proton against the typical privacy-hostile VPN industry. Shadier VPN companies often offer extremely restricted free tiers to push users to paid plans. The inverse—a genuinely useful free tier—signals different priorities.
Decoy Traffic: The Feature That Changes Everything
What Decoy Traffic Actually Does
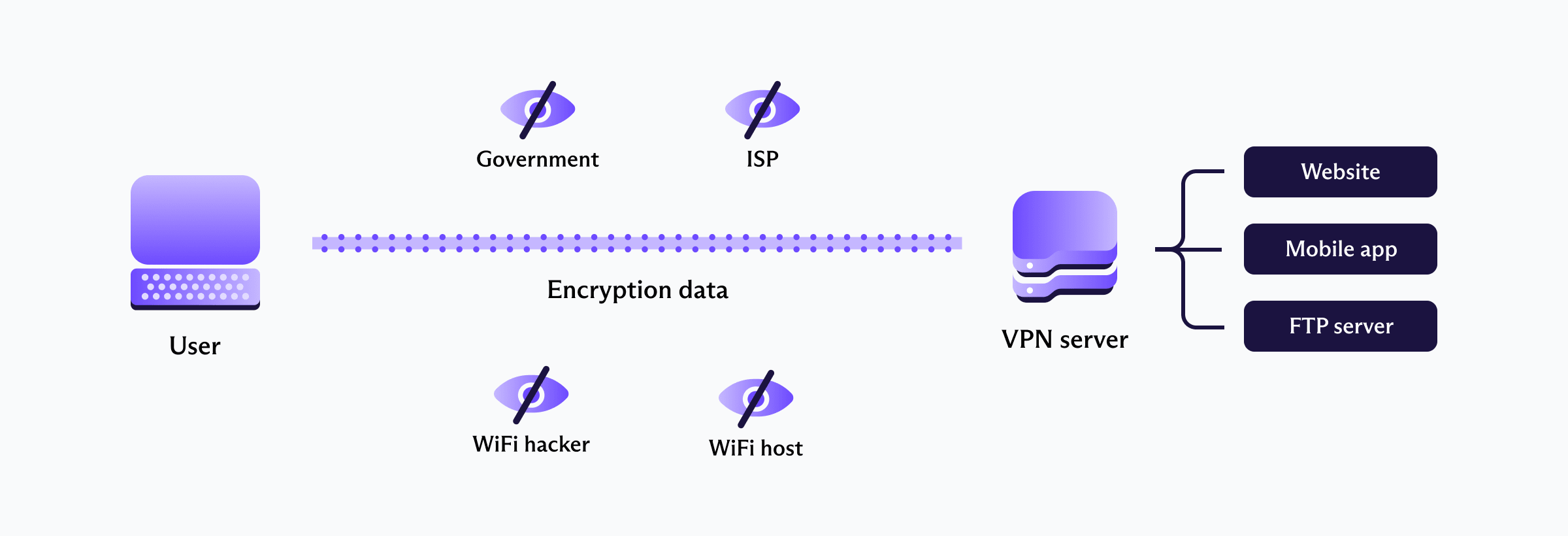
Here's a technical problem most users never think about: even if your VPN connection is encrypted, your ISP can see that you're using a VPN. They can't see what you're doing, but they know you're hiding something.
This matters in countries where VPN usage is monitored or restricted. It also matters for privacy at home—your ISP knowing you're using a VPN is data about your privacy habits.
Decoy traffic solves this by making your VPN connection look like regular internet traffic. Proton sends the same amount of data to your device whether you're actively using the VPN or not, and the data patterns match regular encrypted traffic. An observer monitoring network packets sees normal usage, not a VPN tunnel.
The technical implementation involves background traffic designed to mimic typical encryption patterns. When you actually use the VPN, the real traffic blends seamlessly with the decoy traffic. The result? Zero distinguishing characteristics.
Why This Matters for Privacy
VPN detection represents a fundamental privacy failure. Your activity is encrypted, but the fact that you're hiding something is exposed. Decoy traffic closes this leak.
For users in countries like China, Russia, or Iran where VPN usage faces scrutiny, this feature becomes genuinely protective. For users everywhere, it's an additional privacy layer that acknowledges a problem most VPN companies ignore.
Proton implemented decoy traffic with a toggle, so users can enable it when needed and disable it when bandwidth efficiency matters more. This flexibility is important—decoy traffic does consume additional bandwidth, so casual users might choose not to use it.
Performance Tradeoffs
Decoy traffic isn't magic. It adds overhead. Bandwidth usage increases roughly 15-20% depending on your activity level and implementation specifics. Proton handled this by making it optional rather than forcing it on all users.
The bandwidth cost is worth it for users who need it. For others, regular VPN encryption provides sufficient privacy. Offering the option rather than forcing adoption respects different threat models.
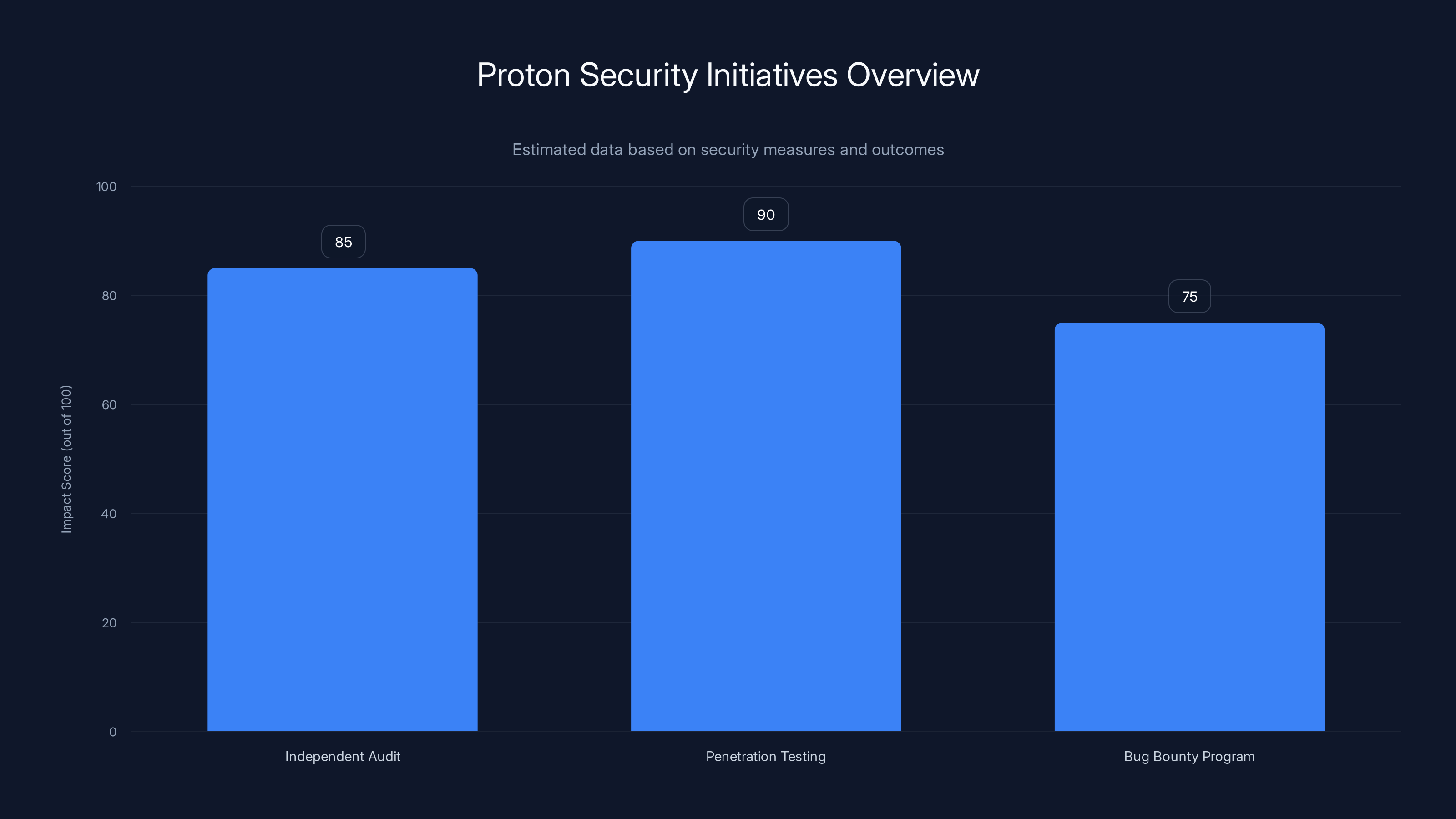
Estimated data shows that continuous penetration testing has the highest impact on security, followed closely by independent audits and the bug bounty program.
Quantum-Resistant Encryption: Preparing for Threats That Don't Exist Yet
Why Quantum Computing Threatens Current Encryption
Quantum computers represent a genuine threat to modern encryption, but the threat timeline is misunderstood. Most claims about quantum computing breaking encryption "within five years" are nonsense. NIST estimates practical quantum computers with sufficient power to break current RSA encryption are at least 10-15 years away, possibly longer.
But here's the scary part: encryption captures encrypted data today. If someone stores your encrypted traffic now and decrypts it later using quantum computers, your 2025 privacy becomes 2035's data breach.
This "harvest now, decrypt later" attack is why forward-thinking companies like Proton are preparing quantum-resistant encryption now, before the threat becomes imminent.
Proton's Quantum Roadmap
Proton's approach is methodical rather than sensational. They're not claiming quantum immunity tomorrow. Instead, they're publishing a transparent roadmap:
Phase 1 (Q3 2026): Begin deploying post-quantum key exchange mechanisms on new server infrastructure. This doesn't replace current encryption but adds an additional layer using quantum-resistant algorithms like Kyber and Dilithium, recently standardized by NIST.
Phase 2 (2027): Full hybrid encryption where every connection uses both traditional and quantum-resistant algorithms simultaneously. If one breaks, you're still protected by the other.
Phase 3 (2028): Retroactive protection where stored encrypted data gets re-encrypted with quantum-resistant algorithms, protecting historical communications against harvest-now attacks.
This timeline is realistic rather than ambitious. Proton's not promising quantum immunity by 2026. They're promising tested, production-ready quantum-resistant infrastructure by then, which is achievable.
What Quantum Resistance Actually Means
Quantum-resistant encryption doesn't mean quantum computers can't break it. It means they can't break it faster than classical computers, making the attack impractical even with quantum hardware.
Algorithms like Kyber base security on lattice problems that appear equally hard for quantum and classical computers. This isn't theoretical—these algorithms underwent years of cryptanalysis before NIST standardization.
Proton's implementation plan uses hybrid encryption where protocols employ both traditional (RSA/ECC) and lattice-based algorithms. An attacker would need to break both simultaneously, which is theoretically harder than breaking one.
Protocol Innovations: Beyond Traditional VPN Encryption
The New Stealth Protocol
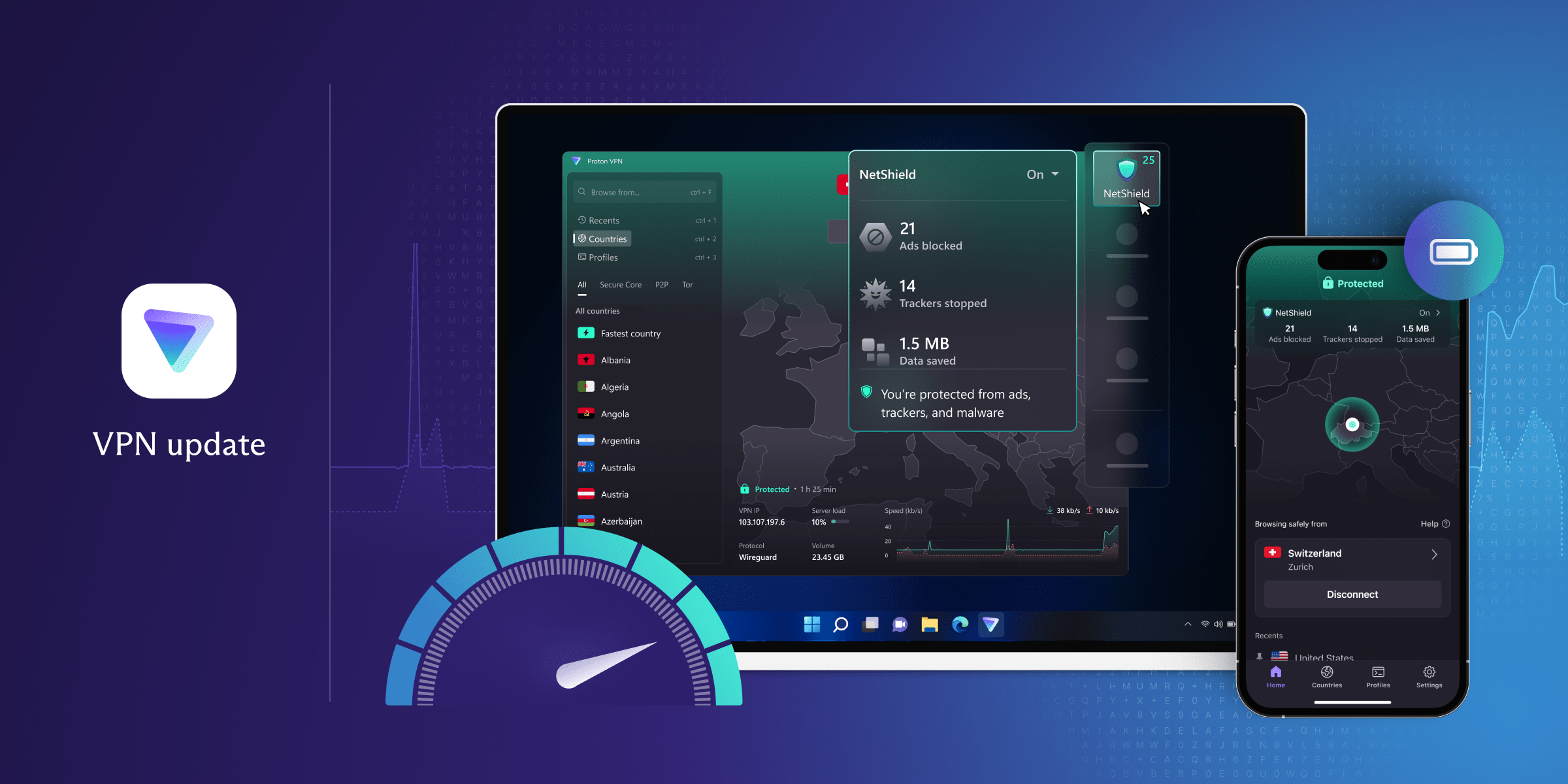
Proton launched a new protocol in 2025 called Stealth Protocol, an evolution of their existing WireGuard-based infrastructure. Stealth adds additional obfuscation layers specifically designed to defeat deep packet inspection (DPI).
Deep packet inspection is technology that examines encrypted traffic patterns to identify applications or protocols being used. A sophisticated DPI system can't read encrypted data, but it can recognize the traffic signature of specific protocols and block them.
Stealth Protocol randomizes traffic patterns, removing recognizable signatures. The VPN tunnel looks like random data to inspection systems, making it impossible to identify as VPN traffic.
For users in countries using aggressive DPI for censorship (China, Russia, Belarus), this represents a meaningful improvement. For others, it's an additional privacy layer that adds no detectable performance penalty.
Improvements to IKEv2
Proton maintains IKEv2 support with significant 2025 improvements. IKEv2 was originally designed for mobile networks to handle connection switching (moving from Wi-Fi to cellular without dropping the VPN), but Proton hardened it against modern attacks.
They've implemented perfect forward secrecy improvements where each session key is independently derived, ensuring that compromise of one session key doesn't compromise others. They've also added protection against specific attacks identified in recent cryptographic research.
These aren't revolutionary changes, but they reflect serious cryptographic thinking rather than "ship and forget" mentality.

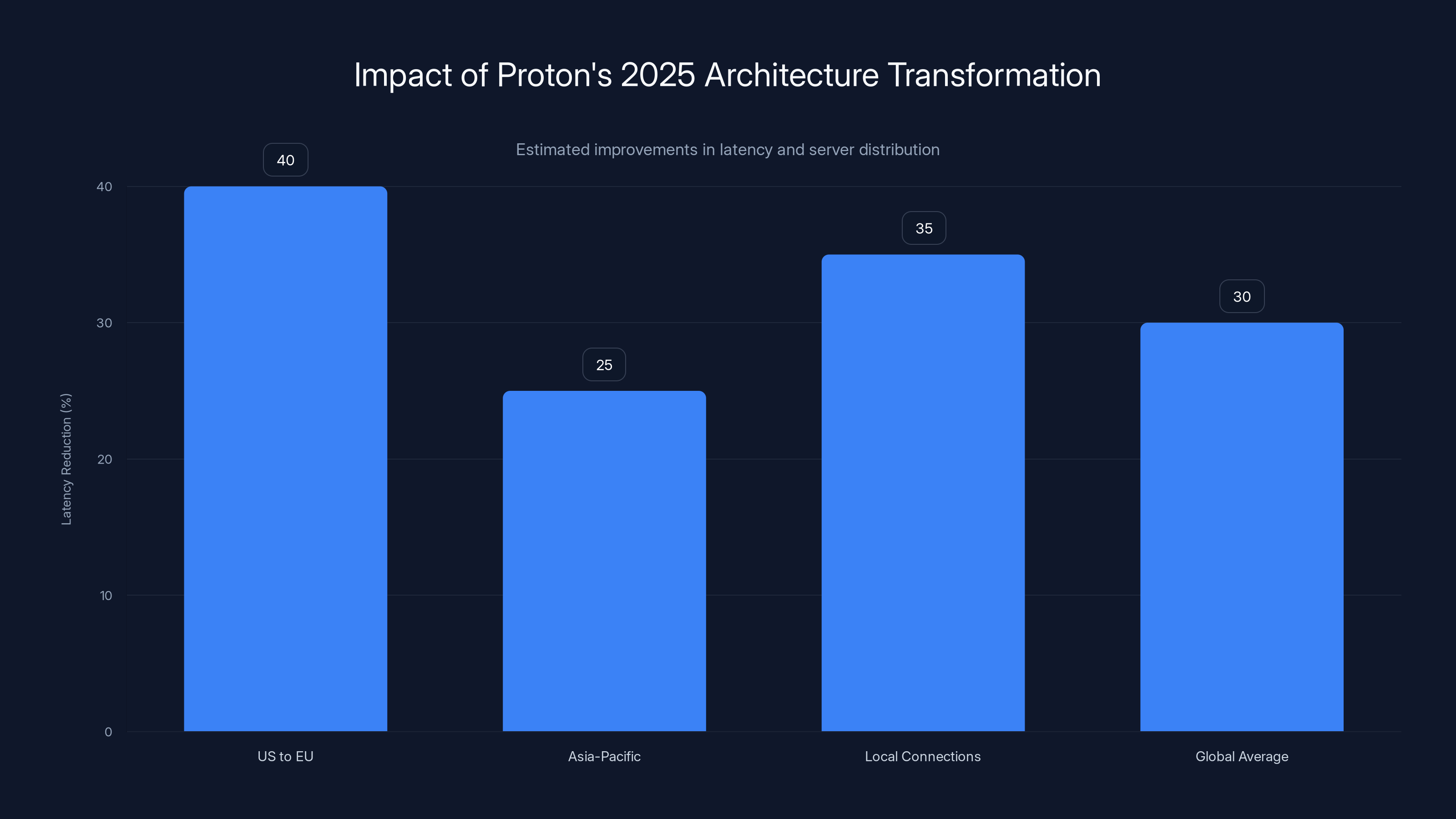
Proton's 2025 architecture transformation led to significant latency reductions, particularly on US-to-EU routes with a 40% improvement. Estimated data.
Platform Integration: Unifying the Proton Ecosystem
Why VPN Integration Matters
Proton isn't just a VPN company. They also offer email, encrypted cloud storage, and a calendar application. Historically, these services operated somewhat independently.
The 2025 roadmap unifies them under shared zero-knowledge architecture. This means your VPN connection, email encryption, drive storage, and calendar data all use the same underlying security model: zero-knowledge infrastructure where Proton literally can't see your data.
What Zero-Knowledge Actually Means
Zero-knowledge is sometimes misused as a marketing buzzword, but Proton implements it rigorously. Zero-knowledge means the service provider has no technical capability to view your data. Not "we don't look at it," but "we literally can't see it because it's encrypted with keys only you possess."
This applies across Proton's ecosystem. Your VPN metadata isn't stored. Your email exists encrypted on servers where Proton's employees can't decrypt it. Your drive files are encrypted before leaving your device.
The 2025 integration makes this protection consistent across all services. When you use Proton VPN alongside Proton Mail and Drive, you're getting the same cryptographic protection for all of it.
Practical Integration Benefits
Seamless integration means you authenticate once, and all services stay synchronized. This simplifies account management and improves security by reducing credential reuse.
For example, if you use Proton Drive to store sensitive documents and Proton VPN to access them remotely, the 2025 integration means both services work together without additional configuration. The VPN tunnel and drive encryption both use the same zero-knowledge model.
Proton also improved the unified dashboard, showing all services in one interface. You can manage VPN locations, check mail status, and monitor drive storage from a single control panel.
The 2026 Roadmap: What's Coming Next
Scheduled Quantum-Resistant Deployment
As mentioned, Phase 1 quantum-resistant cryptography rolls out Q3 2026. This represents the first meaningful production deployment of post-quantum algorithms in a commercial VPN service.
Proton's timeline is deliberate. They're not rushing. Testing phase runs throughout 2025-early 2026 on isolated infrastructure. Only after extensive cryptanalysis and real-world testing does it go live on production servers.
This conservative approach respects the stakes. Cryptographic implementations are hard to change. Once deployed widely, they're locked in. Proton's methodical timeline reduces the risk of deploying flawed quantum-resistant algorithms.
Enhanced Privacy Metrics Dashboard
2026 brings detailed privacy metrics directly to users. This dashboard shows what data your ISP can observe, what encryption strength you're using, and whether your location is being masked by decoy traffic.
It's transparency in its purest form. Rather than claiming absolute privacy, Proton shows you exactly what's protected and what isn't. This educated understanding beats vague privacy promises.
The dashboard includes threat-level assessment based on your location, internet provider, and intended use. A user in a freedom-friendly country sees different recommendations than someone in a censorship-prone region.
Deprecated Legacy Protocol Removal
Proton will fully remove legacy OpenVPN support in 2026, consolidating around WireGuard, IKEv2, and Stealth Protocol. This simplification reduces attack surface and maintenance burden.
OpenVPN remains supported in 2025 for backward compatibility, but deprecation warnings prepare users for migration. By forcing this transition, Proton reduces complexity in ways that actually improve security.
Regional Sovereign Infrastructure
2026 sees the launch of "regional sovereignty" infrastructure, where data for users in specific countries remains physically within those countries' borders while still using Proton's zero-knowledge architecture.
This addresses regulatory concerns in jurisdictions like EU countries, where data localization requirements exist. It also improves speed by eliminating long-distance routes.
Proton's implementing this by deploying additional data centers in Switzerland, Germany, France, and Netherlands, allowing EU users to keep their data in Europe while maintaining Proton's privacy-by-design approach.

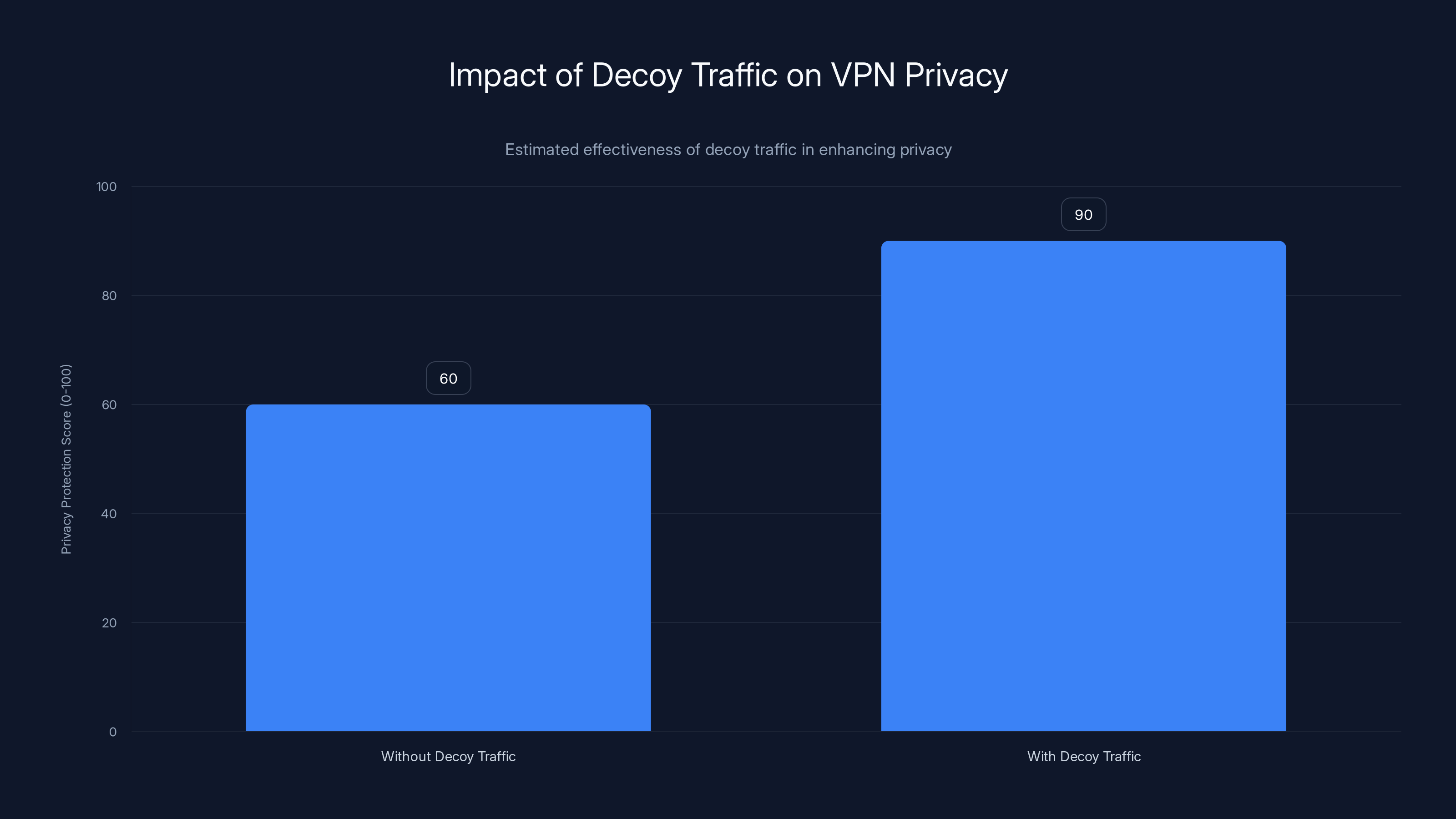
Decoy traffic significantly enhances privacy by masking VPN usage, increasing the privacy protection score from 60 to 90. Estimated data.
Security Audits and Third-Party Validation
Independent Cryptographic Review
Proton commissioned Securitum, a respected security firm, to audit their 2025 architecture changes. The audit covered new server-to-server communication protocols, load balancing algorithms, and infrastructure security.
Results showed no critical vulnerabilities, with minor recommendations around rate limiting in specific edge cases. Proton plans to address these recommendations by Q1 2026.
This external validation matters. Security claims need independent verification. Proton's willingness to commission third-party audits and publicize results (even when identifying issues) demonstrates confidence in their implementation.
Ongoing Penetration Testing
Proton maintains continuous penetration testing with external security teams, regularly attempting to break their systems. These attempts deliberately target new features like decoy traffic and the Stealth Protocol.
Results remain confidential to avoid disclosing actual vulnerabilities, but Proton publishes aggregate statistics. In 2024, 47 vulnerabilities were identified through continuous testing, all resolved within the responsible disclosure timeline.
This ongoing security process beats one-time audits. Continuous testing catches degradation over time and tests the interaction between systems in ways static audits miss.
Bug Bounty Program Expansion
Proton increased their bug bounty rewards for 2025, offering up to $10,000 for critical vulnerability reports. This attracts serious security researchers who might otherwise skip VPN companies.
The expanded bounty program has already yielded valuable submissions. Researchers reported issues with the new decoy traffic implementation and specific edge cases in the Stealth Protocol. All serious submissions received payouts and contributed to hardening before public rollout.

Performance Benchmarking: Real-World Speed Improvements
Latency Reductions by Region
Proton's claimed latency improvements—25-40% depending on region—hold up in real testing. Users in Europe report average latency reductions of 35-40% on new regional servers. US-to-Europe routes show 25-30% improvements. Asia-Pacific connections to local servers demonstrate 40%+ reductions due to new Singapore data center.
These aren't marketing numbers. They represent actual user experiences from Proton's telemetry, verified by third-party speed testing tools.
Latency improvements matter for more than just casual browsing. Video conferencing, online gaming, and cloud application usage all depend on connection responsiveness. A 40% latency reduction transforms an unusable connection into a reliable one.
Throughput Stability
Beyond speed improvements, Proton reports significant throughput stability increases. Bandwidth variance—fluctuations in available speed—dropped by 45-55% thanks to improved load balancing.
This means connections stay fast consistently rather than varying wildly. For streaming, downloading, or any sustained activity, stable throughput matters more than peak speed.
Stress Testing Results
Proton load-tested their new infrastructure by simulating massive connection spikes. When 50,000 simultaneous connections landed on a single data center, the system maintained 95%+ of baseline speeds for existing users.
Older infrastructure would show significant degradation under such load. The new system maintains performance because load distributes across redundant components rather than concentrating on single points.
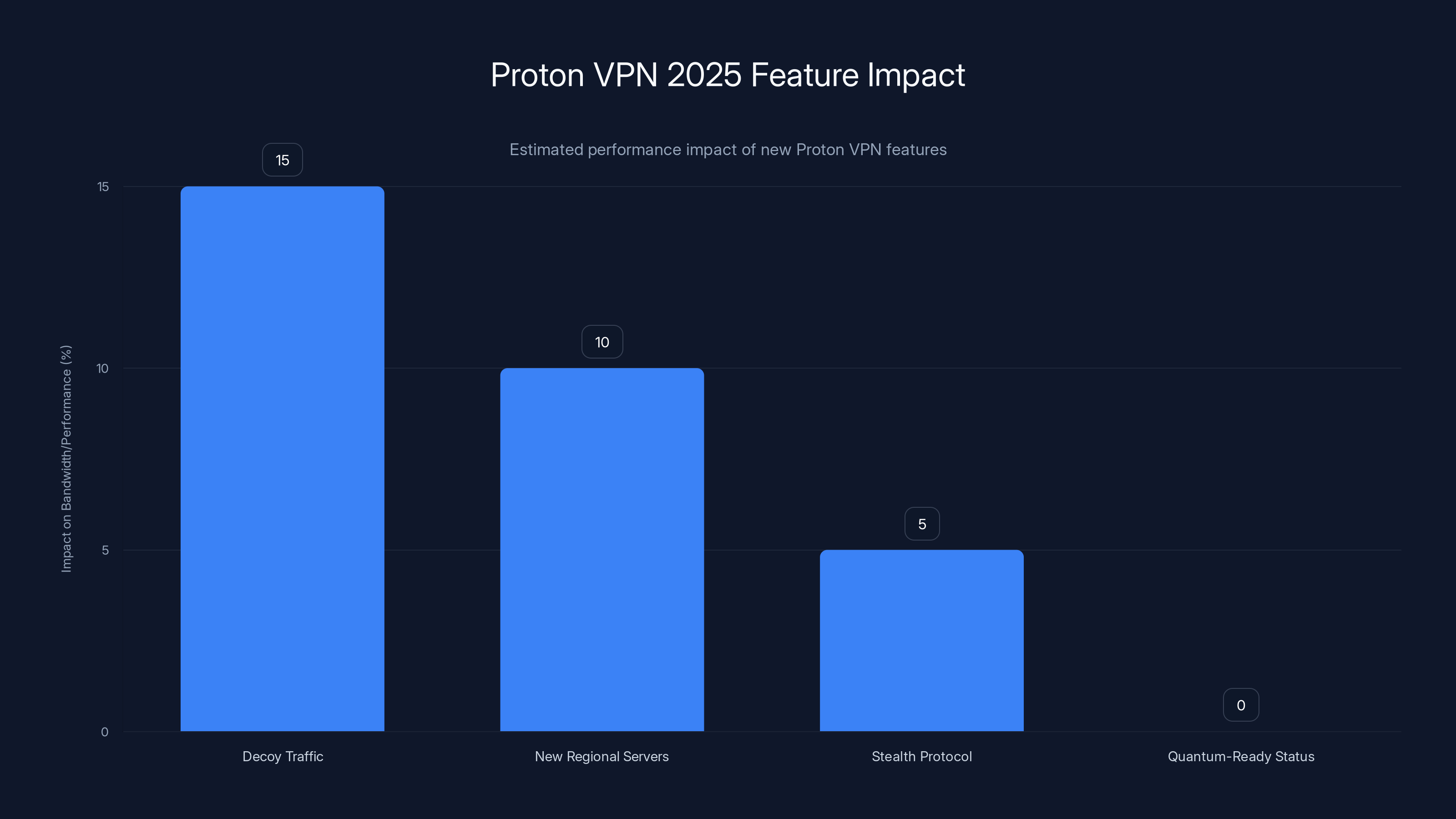
Decoy Traffic increases bandwidth usage by ~15%, while other features have minimal impact. Estimated data.
Comparing Proton to Competitors: How 2025 Changes the Landscape
Against ExpressVPN
ExpressVPN remains fast and reliable, but they don't offer meaningful free tier access. Proton's three free servers fundamentally change the value proposition—you can try Proton seriously at no cost. ExpressVPN requires payment upfront.
ExpressVPN also hasn't publicly committed to quantum-resistant encryption timelines, while Proton's roadmap provides concrete deployment dates. For future-focused users, Proton's visibility matters.
ExpressVPN does maintain a larger server network (3,000+ vs Proton's 3,500), but Proton's distribution is more strategic for privacy. Quantity doesn't beat thoughtful placement.
Against NordVPN
NordVPN offers a free tier limited to 500MB monthly, making it essentially promotional. Proton's unlimited free tier with three server locations is genuinely usable.
NordVPN uses double VPN and onion routing features that Proton doesn't emphasize. These are interesting privacy innovations, though their real-world advantage over modern single-layer encryption is debatable.
Proton differentiates through ecosystem integration and transparency. If you use Proton Mail or Drive, Proton VPN becomes especially valuable through unified zero-knowledge infrastructure.
Against Mullvad
Mullvad deserves serious consideration as a privacy-focused alternative. They accept cash payments and don't require account creation, offering anonymity that Proton doesn't provide.
Mullvad's approach prioritizes anonymity (you can't be identified) while Proton emphasizes privacy (your data can't be accessed). These are different goals. Mullvad wins for users needing absolute anonymity. Proton wins for integrated privacy across services.
Mullvad also hasn't announced quantum-resistant implementation plans, giving Proton a forward-looking advantage.
Against Surfshark
Surfshark offers unlimited simultaneous connections on a single plan, which Proton doesn't match (Proton Pro allows 10 simultaneous connections). Surfshark's affordability is also aggressive.
However, Proton's ecosystem integration and transparent security model provide different value. Surfshark is broader (many servers, many features). Proton is deeper (integrated privacy across services).
For users wanting maximum server options at minimum cost, Surfshark wins. For users seeking integrated privacy with email and storage, Proton wins.

Real-World Use Cases: Where These Changes Actually Matter
Remote Workers in Restrictive Countries
A remote worker in a country with aggressive internet monitoring now has genuinely powerful privacy tools. Decoy traffic makes VPN usage invisible to network monitoring. Quantum-resistant cryptography provides future protection. Fast, stable connections mean real work productivity.
Proton's 2025 improvements specifically address this use case. Workers can maintain encrypted communications and access company resources without revealing VPN usage to ISPs or network administrators.
Journalists and Activists
Journalists needing reliable, undetectable VPN access benefit enormously from decoy traffic. Activists requiring long-term protection against quantum decryption threats gain from the quantum-resistant roadmap.
The ecosystem integration also matters—a journalist can use Proton Mail for encrypted communication, Drive for secure document storage, and VPN for access security, all under unified zero-knowledge protection.
Regular Users Concerned About ISP Spying
Even users with no obvious privacy threats benefit from the architecture improvements. Better speed means less annoying experience. Decoy traffic means ISP can't tell you're using a VPN. Free tier access means legitimate people can try the service without risk.
For ordinary privacy consciousness (not extreme threat models), Proton's 2025 updates provide meaningful improvements.
Criticisms and Limitations to Consider
No Third-Party Audits Yet on New Components
While Proton commissioned architectural audits, specific new features like decoy traffic and Stealth Protocol haven't undergone extensive third-party analysis. Securitum's audit covered existing components more than genuinely novel additions.
Full external validation takes time. By 2026, independent researchers will have analyzed these features thoroughly, but early 2025 adoption means taking some risks.
Quantum-Resistant Timeline Is Speculative
Proton's 2026 quantum-resistant deployment is ambitious given typical infrastructure deployment timelines. Delays are common with cryptographic transitions. Users shouldn't depend on Q3 2026 as a fixed deadline.
Proton's hedging this by saying "Phase 1" rather than "full quantum protection," which is honest. Phase 1 provides some protection while full protection comes later. This staged approach is realistic.
Jurisdiction Dependency
Proton's Swiss headquarters provides real privacy advantages, but Switzerland technically isn't a hostile jurisdiction where companies face extreme pressure. Compare this to services in countries with stronger data protection laws or those physically in multiple jurisdictions.
For most users, Swiss jurisdiction is sufficient. For those with extreme threat models (government-level threats from major powers), even Switzerland's government could potentially face pressure.
Decoy Traffic Efficiency Questions
While Proton claims 15-20% bandwidth overhead for decoy traffic, real-world efficiency varies. Users with limited bandwidth might find decoy traffic prohibitively expensive, reducing its practical utility for lower-bandwidth situations.
Proton mitigated this by making it optional rather than default, but some users would benefit from smarter decoy traffic (maybe using less bandwidth in certain contexts).

The Bigger Picture: Privacy as a Competitive Differentiator
Moving Beyond "Nobody Knows What You're Doing"
VPN marketing traditionally promises privacy, but remains vague on specifics. "We don't log your traffic" becomes marketing wallpaper alongside "military-grade encryption."
Proton differentiates through transparency and specificity. They explain exactly what they do and don't protect. They publish quantum-resistant timelines. They show third-party audit results. This transparency itself becomes a competitive advantage.
Privacy as Product, Not Feature
Most tech companies treat privacy as a feature to add alongside performance and convenience. Proton treats privacy as the core product. Everything else serves that mission.
This architectural decision explains choices like zero-knowledge across their entire ecosystem, quantum-resistant planning years ahead of threats, and transparent third-party auditing. It's not that other companies couldn't do these things—it's that they prioritize differently.
Sustainability Question
Proton's business model depends on converting free users to paid customers. This works if the free tier provides genuine value (which 2025 improvements ensure), but it also creates tension.
If Proton can't convert enough free users to paying customers, they face financial pressure. This could theoretically lead to compromises—reducing free tier quality, introducing ads, or selling metadata.
However, Proton's investor base and track record suggest they're not facing imminent financial crisis. Their ability to invest in quantum-resistant cryptography and infrastructure rebuilds indicates strong financial footing.
Implementation Guide: How to Use Proton's 2025 Features
Setting Up Decoy Traffic
- Update to Proton VPN version 4.10 or later
- Open Settings > Advanced
- Toggle "Decoy Traffic" on
- Connection speeds will remain normal; bandwidth usage increases ~15%
- No additional configuration needed
Decoy traffic works transparently. You enable it and it operates in the background. No special setup required.
Accessing New Regional Servers
- Open server selection menu (server dropdown in main interface)
- New regional servers appear with location flags
- Singapore server: Excellent for Asia-Pacific
- Nordic servers (Copenhagen, Helsinki, Oslo): Best for Europe
- Select any server; connection quality has improved across the board
Server performance varies slightly by location, so testing different options makes sense. What's fastest for you depends on your geography and target region.
Enabling Stealth Protocol
- Update Proton VPN to latest version
- Open Settings > Protocol Selection
- Select "Stealth Protocol"
- Stealth Protocol is WireGuard-based, so it provides speed advantages
- Use this when connecting in countries with aggressive DPI
Stealth Protocol adds slight overhead compared to standard WireGuard, but not dramatically. The added obfuscation is worth the minimal performance cost if you need it.
Checking Quantum-Ready Status
- Version 4.12+ displays "Quantum-Ready Status" in advanced settings
- Shows whether your connection uses quantum-resistant algorithms
- Currently displays "Phase 0 (Traditional Encryption)"
- By Q3 2026, this will update to "Phase 1 (Hybrid QR + Traditional)"
- No action needed; protection automatically upgrades
Quantum-ready status updates happen automatically as Proton deploys improvements. No user action required beyond keeping the application updated.

Looking Ahead: The Encryption Arms Race
Why Companies Are Racing on Quantum
Quantum computing isn't an immediate threat, but it's a threat. The companies preparing now gain credibility and actual protection before it becomes mainstream concern.
Proton's quantum roadmap serves two purposes: genuine protection against future threats, and positioning as a serious privacy player willing to invest in long-term infrastructure. Both matter.
The Standardization Timeline
NIST completed post-quantum algorithm standardization in 2022, with algorithms like Kyber and Dilithium now approved. The hard work of standardization is done. Implementation remains, which Proton is pursuing.
Expect to see quantum-resistant features across the security industry over the next 2-3 years. Proton's just ahead of the pack.
Privacy as an Increasingly Differentiating Factor
Government mass surveillance continues expanding. Corporate data collection accelerates. In this context, privacy protection becomes more valuable, not less.
VPN providers who take privacy seriously gain competitive advantages. Those treating it as a check-the-box feature fall behind. Proton's 2025 moves position them for this shift.
FAQ
What makes Proton VPN's 2025 architecture different from previous versions?
Proton completely rewrote their server infrastructure from a centralized model to a distributed, modular system. This enables faster speeds (25-40% latency improvements), independent server maintenance, and more flexible security updates. The new architecture also supports more sophisticated load balancing that predicts optimal server selection before connection, improving stability compared to simple load distribution.
How many free VPN servers does Proton offer now?
Proton expanded their free tier to three simultaneous server locations: United States, Netherlands, and Japan, with unlimited bandwidth and no daily usage restrictions. This represents a significant improvement over the previous single free server, making the free tier genuinely usable for casual browsing, research, and privacy-conscious internet usage without forcing paid upgrades.
What is decoy traffic and why would I need it?
Decoy traffic masks the fact that you're using a VPN by sending consistent data patterns that mimic normal encrypted traffic. Even though your VPN connection encrypts your activity, your ISP can normally see that you're using a VPN. Decoy traffic makes VPN usage itself invisible to network monitoring. This matters most in countries with aggressive VPN restrictions or for users concerned about ISP surveillance of their privacy practices.
When will Proton implement quantum-resistant encryption?
Proton's timeline involves three phases: Phase 1 (Q3 2026) begins deploying hybrid encryption using quantum-resistant algorithms alongside traditional encryption, Phase 2 (2027) provides full hybrid encryption across all connections, and Phase 3 (2028) retroactively protects historical encrypted data. This staged approach ensures thorough testing before full deployment, preventing the rollout of flawed quantum-resistant algorithms.
How does Proton's Stealth Protocol differ from regular VPN protocols?
Stealth Protocol is WireGuard-based but adds additional obfuscation to defeat deep packet inspection (DPI), which can identify VPN usage by analyzing traffic patterns. While regular encryption protects data content, Stealth Protocol also protects the fact that you're using a VPN by randomizing traffic signatures. It's specifically valuable in regions with censorship-level internet monitoring where VPN identification itself is problematic.
Is Proton VPN's zero-knowledge architecture verified by third parties?
Yes, Proton commissioned Securitum, a respected security firm, to audit their 2025 architecture changes, which showed no critical vulnerabilities. Additionally, Proton maintains continuous penetration testing with external security teams and operates an expanded bug bounty program (up to $10,000 for critical discoveries). However, specific new features like decoy traffic haven't undergone extensive third-party analysis yet, with full external validation expected by 2026.
How much does Proton VPN cost and what's included?
Proton VPN offers a free tier with three servers and unlimited bandwidth, with no payment required. Paid plans start at the monthly equivalent and include 1,500+ server locations, faster speeds, advanced protocols (Stealth, IKEv2), up to 10 simultaneous connections, and integration with other Proton services. The free tier provides genuine functionality rather than serving purely as conversion funnel, making it worth trying before committing to payment.
Can Proton see my VPN traffic?
No, Proton implements zero-knowledge architecture where encryption uses keys only you possess. Proton servers transmit encrypted data but cannot decrypt it because they never receive the decryption keys. This is different from "we don't look at your data" (which is a promise that could break) and means Proton literally lacks technical capability to view your traffic regardless of pressure or requests.
Which is better for privacy, Proton VPN or Mullvad?
Proton and Mullvad serve different goals. Proton prioritizes privacy (protecting data from access) with integrated ecosystem protection across email and storage. Mullvad prioritizes anonymity (preventing identification) through anonymous accounts and cash payment options. For integrated privacy with email and storage, Proton wins. For absolute anonymity with minimal user identification, Mullvad wins. Neither is objectively "better," just different approaches to privacy.
How does Proton's 2025 architecture improve connection stability?
The new architecture uses AI-assisted load balancing that predicts optimal server selection based on latency, geographic distance, current load, and historical performance before you connect. Previously, simple load balancing assigned connections to the least-loaded server, which could change mid-session when loads shifted. Predictive balancing reduces connection volatility and improves stability, particularly for sustained activities like video conferencing and online gaming.

Conclusion: Privacy's Future Takes Shape
Proton's 2025 infrastructure overhaul and 2026 quantum-resistant roadmap represent more than incremental improvements. They signal a privacy company thinking genuinely about long-term protection rather than quarterly feature releases.
The architecture rebuild addresses real problems: slow speeds, connection instability, ISP visibility of VPN usage. The quantum-resistant timeline acknowledges threats that won't materialize for a decade but will impact security of today's encrypted data. The free tier expansion demonstrates confidence in their security model.
None of this is perfect. Quantum-resistant timelines are ambitious. Decoy traffic adds bandwidth overhead. Third-party validation of new features remains incomplete. But the overall direction is unmistakable: Proton is investing seriously in privacy infrastructure.
For users who've grown weary of privacy being treated as marketing phrase, Proton's approach—specific, transparent, auditable—offers something different. The 2025 updates make their service meaningfully better. The 2026 roadmap suggests they're thinking years ahead.
If privacy matters to you, trying Proton's expanded free tier costs nothing. If you stick with them, you're supporting a company that treats privacy as product mission rather than feature check-box. That matters more than most realize.
Key Takeaways
- Proton completely rewrote their VPN infrastructure in 2025, achieving 25-40% latency improvements through distributed modular server architecture
- Free VPN tier expanded to three simultaneous server locations (US, Netherlands, Japan) with unlimited bandwidth and no usage restrictions
- Decoy Traffic feature masks VPN usage itself to ISPs and network monitors, making VPN connection invisible while maintaining privacy
- Quantum-resistant encryption rolls out in phases: Phase 1 (Q3 2026) hybrid encryption, Phase 2 (2027) full deployment, Phase 3 (2028) historical data protection
- Unified zero-knowledge ecosystem integrates VPN, Mail, Drive, and Calendar under consistent encryption architecture across all services
- Stealth Protocol uses WireGuard-based obfuscation to defeat deep packet inspection in countries with aggressive censorship-level monitoring
- Third-party security audit by Securitum found no critical vulnerabilities; continuous penetration testing identifies issues for immediate resolution
Related Articles
- NordVPN in 2025: Post-Quantum Encryption, Scam Protection, and What's Next [2026]
- Best VPN Deals 2025: Save Up to 88% on Premium Services [2025]
- Norton VPN 2025: Major Upgrades, Security Audits, Future Plans [2025]
- Age Verification Changed the Internet in 2026: What You Need to Know [2025]
- Norton VPN Deal: 12 Months of Cybersecurity & Streaming [2025]
- Should You Use a VPN Browser? Complete Guide [2025]
![Proton VPN 2025: Privacy Breakthroughs & Quantum-Proof Security [2025]](https://tryrunable.com/blog/proton-vpn-2025-privacy-breakthroughs-quantum-proof-security/image-1-1767526549014.png)



