Introduction: The VPN Browser Question Nobody's Really Answered
You've probably seen the ads. Shiny browser extensions promising "military-grade encryption" while you scroll through social media. VPN browsers sound perfect—all the privacy protection without the speed hit or extra clicks. But here's the thing: they're more complicated than the marketing suggests.
I've been testing VPN browsers for years, and I keep running into the same contradiction. They're convenient. They're also... not always what they claim to be.
The average person now has legitimate reasons to care about online privacy. Your internet service provider can see every site you visit. Hackers on public Wi-Fi can intercept unencrypted traffic. Advertisers track your behavior across dozens of sites. Data breaches happen constantly—Statista reports that over 5,000 breaches occurred in the US alone in 2023.
So VPN browsers exist to solve a real problem. But do they actually solve it better than the alternatives? That's what we're diving into.
This guide breaks down exactly what VPN browsers do, how they compare to traditional VPNs, which ones are worth your time, and most importantly, whether you should actually use one. You'll learn the real security implications, the performance trade-offs, and the situations where a VPN browser genuinely makes sense.
TL; DR
- VPN browsers encrypt your traffic by routing it through encrypted servers, but they're limited to browser activity only
- Not a complete replacement for traditional VPNs, which protect your entire device and all applications
- Convenient for casual users who want basic privacy without installing additional software
- Speed penalty is real but varies by browser and server location, typically 15-35% slower than unencrypted
- Free options exist but have catches: limited data, slower speeds, or potential data collection practices
- Best for specific use cases like public Wi-Fi browsing or accessing geo-restricted content, not comprehensive privacy

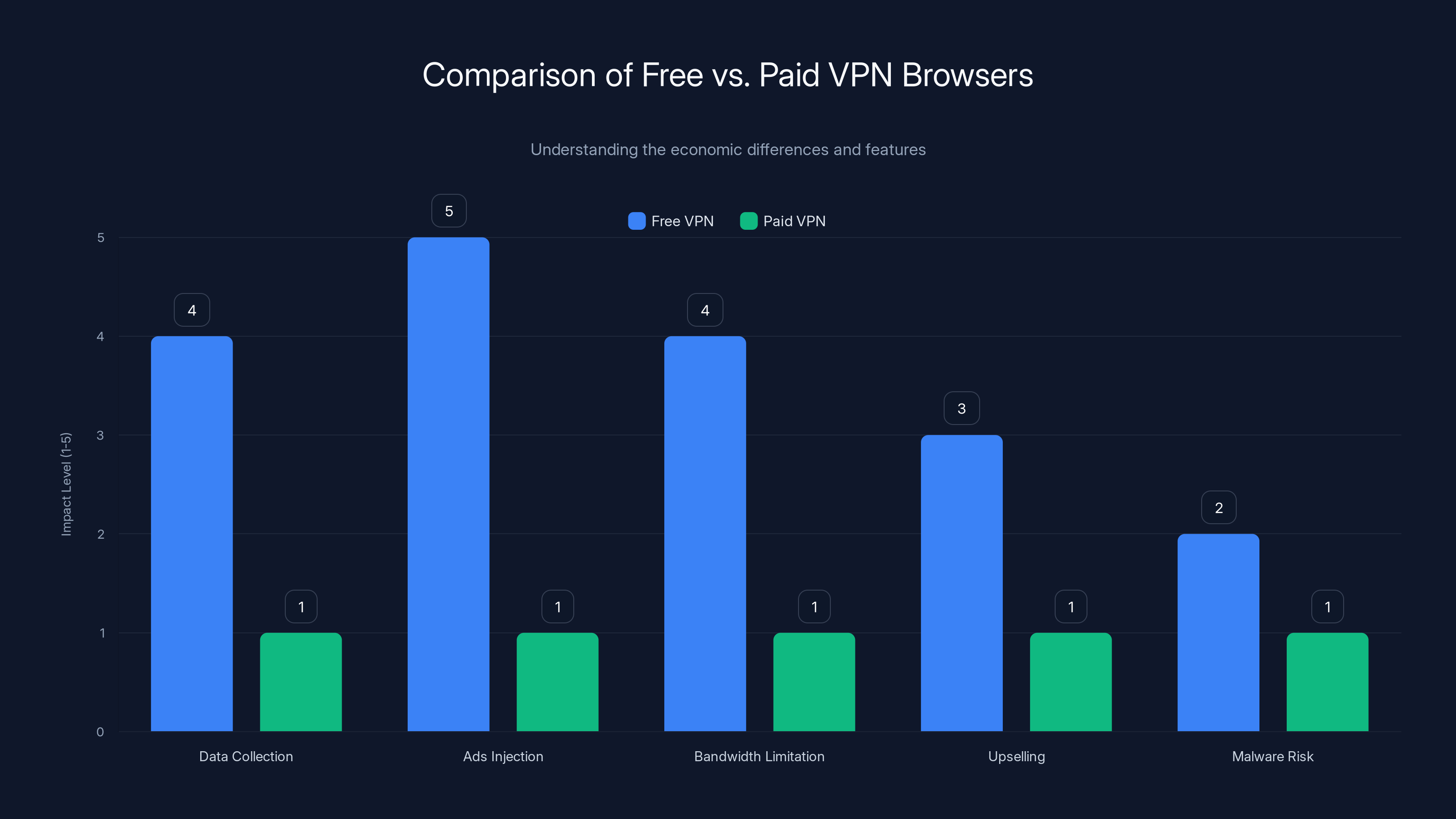
Free VPNs often involve higher risks and limitations, such as data collection and ads, compared to paid VPNs which offer better privacy and fewer restrictions. (Estimated data)
What Exactly Is a VPN Browser?
A VPN browser is either a dedicated web browser or a browser extension that encrypts your internet traffic and routes it through a remote server. The idea sounds straightforward: you get privacy without needing to install separate software.
The reality is more nuanced. When you use a VPN browser, everything you do inside that browser gets encrypted. Your ISP can't see which websites you're visiting. Someone on your public Wi-Fi network can't snoop on your login credentials. The websites you visit don't see your actual IP address.
But here's where it gets tricky. VPN browsers only protect browser traffic. If you're using an email client, messaging app, or any other application, those don't go through the VPN. That's a meaningful limitation most people don't fully understand until they're relying on it.
There are two main types. Some companies like Avast and AVG have created their own browsers built around VPN functionality. Others, like Proton VPN or Express VPN, offer browser extensions that turn your regular Chrome or Firefox into something with encryption built in.
The technology itself is sound. Your encrypted tunnel to the VPN server means traffic is unreadable to anyone monitoring your network. The server then makes requests on your behalf, so the destination website only sees the VPN server's IP, not yours.
What makes VPN browsers different from just installing a regular VPN app is convenience. You don't need to toggle it on and off. It doesn't slow down applications that don't need protection. Everything happens silently while you browse.
That convenience, though, comes with trade-offs. Some are technical. Others are practical. Understanding those trade-offs is exactly why this decision matters.
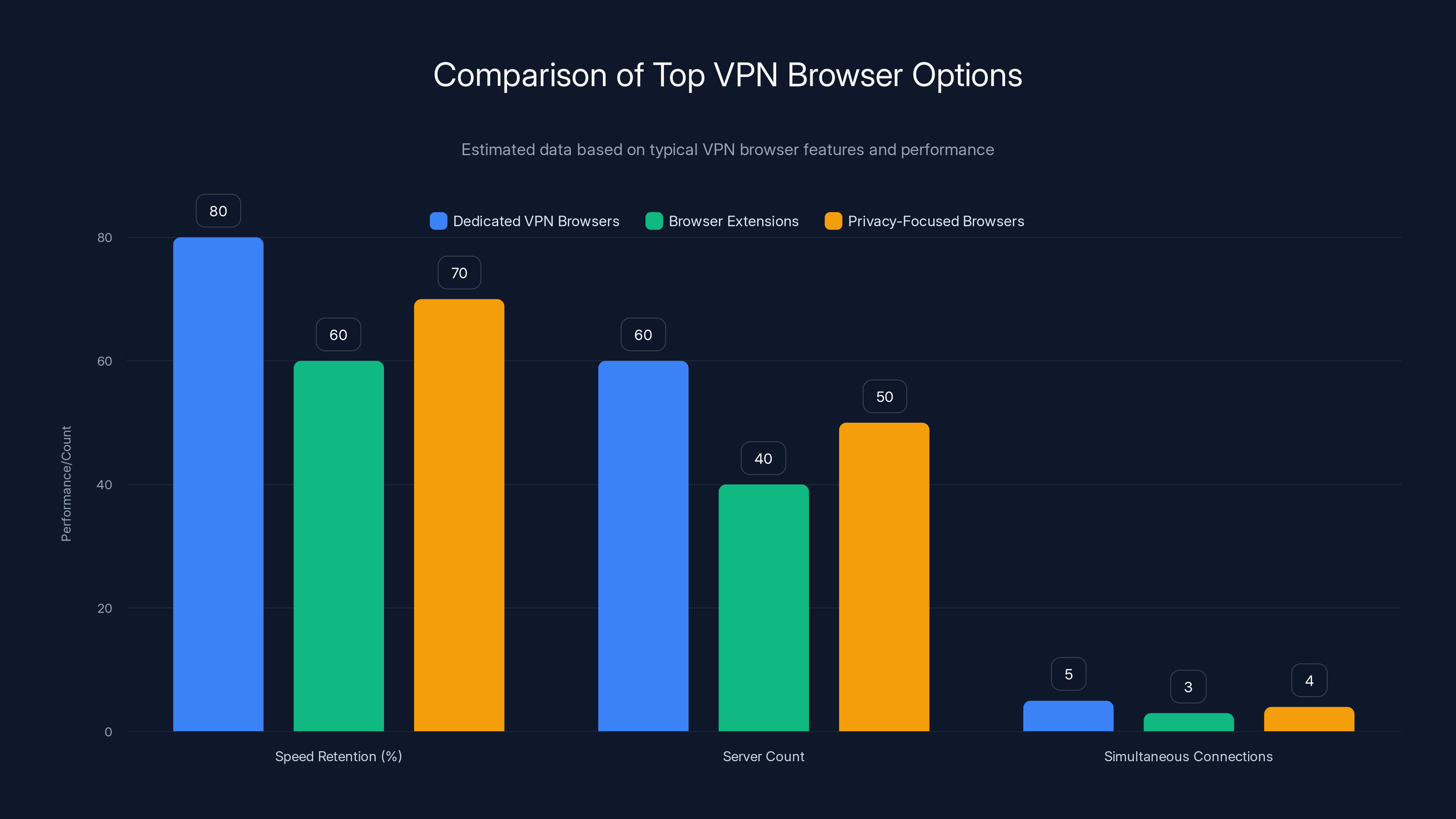
Dedicated VPN browsers generally offer the best speed retention and server count, while privacy-focused browsers provide a balanced approach. Estimated data based on typical features.
How VPN Browsers Actually Work Under the Hood
Understanding how VPN browsers function helps you evaluate their actual security. It's not magic. It's protocol-based encryption, and the details matter.
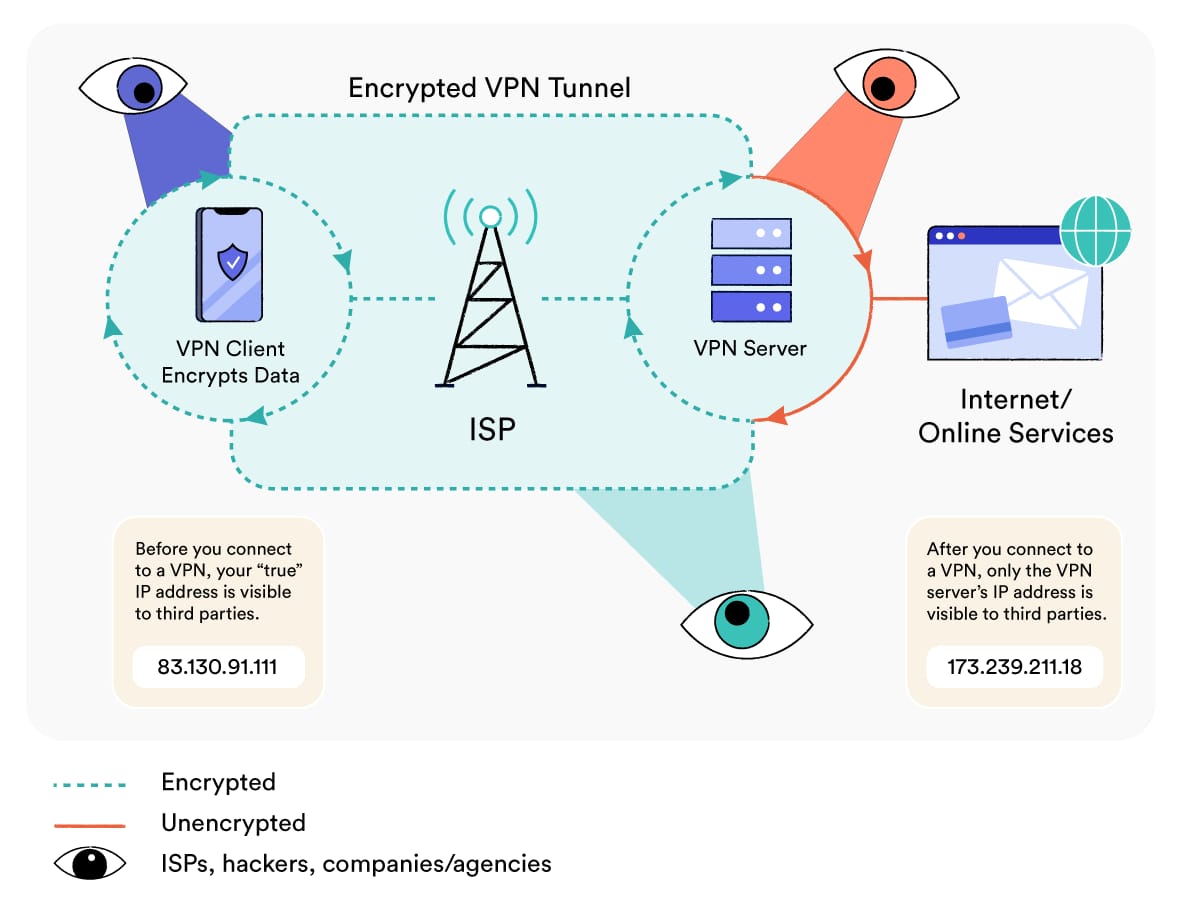
When you navigate to a website using a VPN browser, several things happen in sequence. First, your browser establishes an encrypted tunnel to the VPN provider's server using a security protocol, typically OpenVPN, WireGuard, or a proprietary variant. Your request to connect to your target website gets encrypted inside that tunnel.
The VPN server receives your encrypted request and decrypts it, then makes the actual connection to the website on your behalf. The website responds to the VPN server, not to you directly. The server then encrypts that response and sends it back through the tunnel to your browser.
This architecture creates what's called "split DNS." Your browser queries a DNS server controlled by the VPN provider instead of your ISP's DNS server. This prevents DNS leaks, where your ISP could still see which domains you're trying to access even with the VPN active.
The encryption layer is important. Modern VPN browsers use AES-256 encryption, which is mathematically robust enough that cracking it would require more computing power than exists on Earth. So from a cryptographic standpoint, the encryption itself isn't the weakness.
Where real-world problems emerge is at the endpoints. Your device needs to keep encryption keys in memory. The VPN server needs to log your activity to some degree to route traffic correctly. The browser itself might have security vulnerabilities unrelated to the VPN.
There's also the matter of protocol overhead. Encrypting and decrypting every packet takes processing power. Routing traffic through remote servers adds latency. Most VPN browsers will run your connection through multiple hops to increase privacy—each additional hop adds a small delay.
This is why performance matters practically. A 100ms latency increase might not sound significant. But when you're streaming video, that latency compounds. Video buffering gets worse. Page loads feel sluggish. At a certain point, the privacy benefit doesn't feel worth the frustration.
The other practical element is logging. Every legitimate VPN provider keeps some logs to maintain their service—connection timestamps, bandwidth usage, and so on. The privacy difference between providers comes down to which data they keep, how long they keep it, and whether they'd surrender it to authorities.
Some VPN browsers run under "no-log" policies. That means they claim not to keep records of your activity. This is harder to verify than you might think, but reputable providers do submit to independent audits to back up those claims.
VPN Browsers vs. Traditional VPN Applications: The Real Differences
This comparison matters because it determines whether a VPN browser can actually solve your privacy needs or whether you need something more comprehensive.
Traditional VPN applications protect your entire device. Every packet of data leaving your computer—whether from your browser, email client, video streaming service, or anything else—goes through the encrypted tunnel. A VPN browser only protects your web traffic.
This creates a significant practical difference. Imagine you're on public Wi-Fi at a coffee shop. You open a VPN browser and browse securely. But then you open Slack or your email client. That traffic isn't protected unless you also have a traditional VPN running.
Performance hits are also different. A traditional VPN slows down everything simultaneously, because everything uses the same encrypted connection. A VPN browser only affects browser traffic, leaving your other applications at full speed. For many people, this is actually a strong advantage.
Speed trade-offs are generally worse with traditional VPNs. A good quality VPN typically costs 15-35% in speed. Some cheap VPNs can be 50% slower or worse. VPN browsers often have similar speed penalties, but you only notice it when browsing. Everything else stays fast.
Installation and setup are completely different. Traditional VPNs require you to download software, configure it, and often restart your device. VPN browsers can be as simple as clicking a browser extension. This simplicity appeals to people who don't want to deal with configuration.
Server selection and customization also differ. Traditional VPN apps usually give you detailed server lists with options to choose specific countries or cities. Many VPN browsers simplify this—they might just offer an on/off switch. That makes them less flexible for specific use cases like accessing content that's geo-restricted to certain regions.
Data logging practices vary between the two. Traditional VPN providers have spent years building their reputation around privacy and frequently undergo independent audits. VPN browsers, especially those from larger software companies like Avast, have sometimes faced scrutiny over data collection practices. Not all, but it's worth checking.
Cost structure is different too. Many traditional VPNs cost $5-12 per month. Some VPN browsers are free or bundled with other software. This sounds better until you realize that free services make money somehow—usually through advertising or data collection.
One major advantage of traditional VPNs: they work everywhere. Gaming consoles, smart TVs, IoT devices, everything can route through the VPN if you set it up at your router level. VPN browsers only work in browsers, so they're inherently limited.
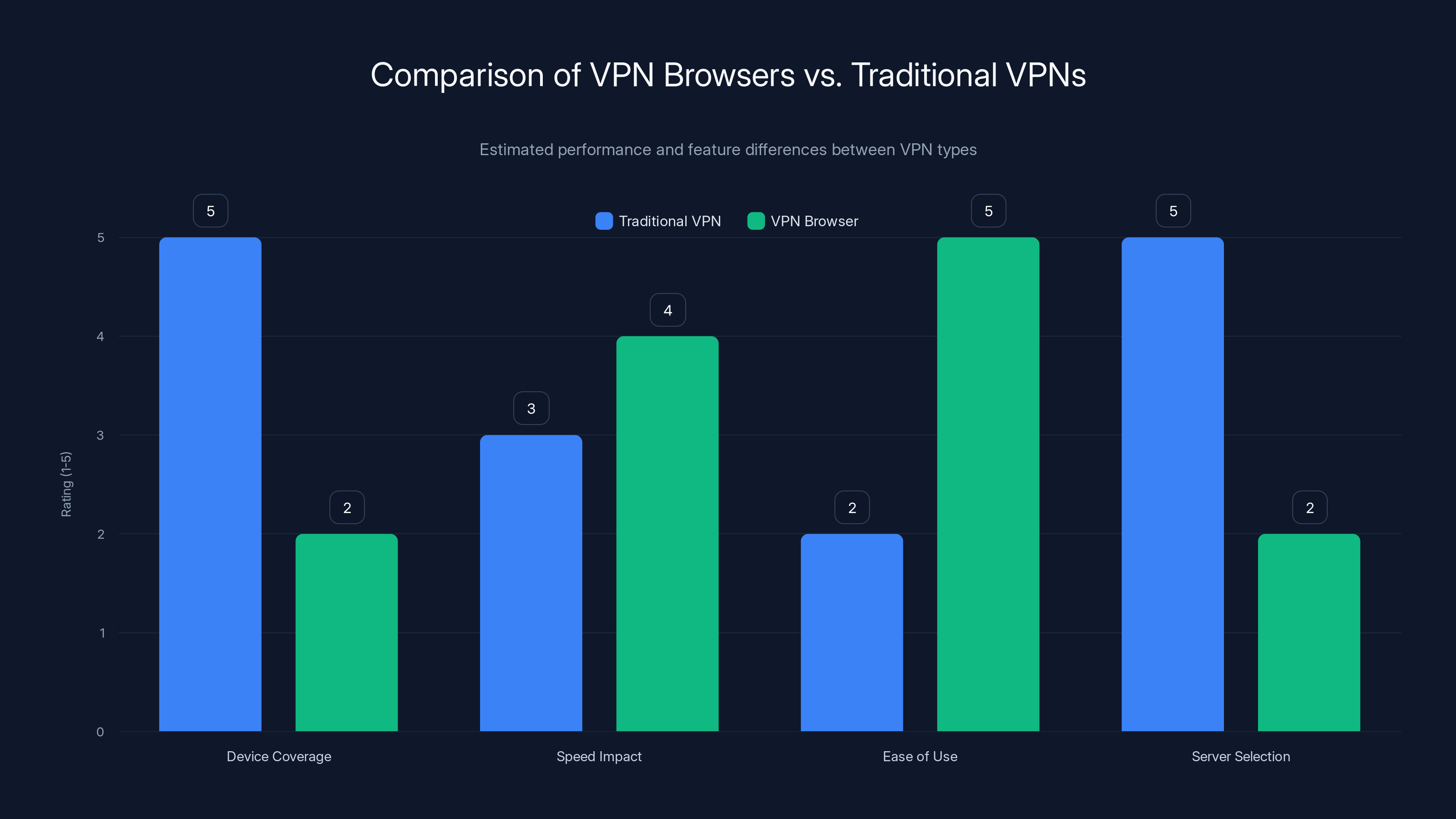
Traditional VPNs offer comprehensive device coverage and server selection but may impact speed more and are less user-friendly. VPN browsers excel in ease of use and minimal speed impact but offer limited coverage and server options. Estimated data.
Security Claims vs. Reality: What VPN Browsers Actually Protect
Marketing copy from VPN browser providers often implies complete protection. The reality is more bounded.
Here's what a VPN browser genuinely protects you against:
ISP snooping: Your internet service provider cannot see which websites you visit. They can see that encrypted traffic is flowing, but not its destination or content.
Network eavesdropping: Someone on the same public Wi-Fi network cannot intercept your credentials or data. The encryption prevents packet sniffing attacks.
Geographic IP blocking: Websites can't identify your location based on your IP address. You can access content intended for other regions if the VPN server is located there.
Basic tracking: Many trackers rely on IP addresses. With a VPN, you get a shared IP address with many other users, making individual tracking harder.
Here's what it doesn't protect you against:
Browser vulnerabilities: If your browser has a security flaw, an attacker can exploit it. The VPN doesn't fix browser bugs.
Malware: VPN browsers don't defend against malicious software. If something infects your device, the VPN is irrelevant.
Phishing attacks: A VPN won't stop you from entering credentials on a fake website. The encryption protects the data in transit, but doesn't verify the site is authentic.
Session hijacking through cookies: If a website's security is compromised, attackers might steal your authentication cookies. The VPN doesn't prevent this.
Non-browser applications: Email apps, instant messaging, game clients—these all run without VPN protection in a VPN browser setup.
This list matters because it shows VPN browsers solve specific problems, not all problems. If you're worried about your ISP knowing which websites you visit, a VPN browser helps. If you're worried about malware, it doesn't.
The technical distinction is important: VPN browsers encrypt traffic in transit. They don't validate website authenticity, patch software vulnerabilities, or clean infected systems.
One claim that deserves specific attention: "military-grade encryption." This phrase appears in nearly every VPN browser advertisement. The term is somewhat meaningless—it just means AES-256 encryption, which is standard across nearly all VPN services. Calling it "military-grade" doesn't make it stronger. It's effectively a marketing phrase that sounds impressive but doesn't differentiate between providers.
VPN Browser Performance Impact: Numbers and Real Experience
Speed matters. If a VPN browser makes browsing unbearably slow, the privacy benefit becomes theoretical rather than practical.
The performance impact of VPN browsers typically falls into three categories: latency increase, bandwidth reduction, and throughput impact.
Latency is how long it takes for data to travel from your device to the destination. Adding a VPN hop to the connection path adds latency, typically 20-80ms depending on server location and network congestion. This might sound small, but it compounds. Page loads feel slightly slower. Video streaming takes a second or two longer to buffer. In casual browsing, this is usually imperceptible. In competitive gaming or real-time trading, it matters significantly.
Bandwidth reduction refers to actual download speed. This varies wildly. A VPN browser using a server near you with good hardware might reduce speed by only 10%. Using a distant server or connecting to an overloaded VPN server might reduce speed by 50% or more.
Throughput is the total data amount your connection can handle. Premium VPN browsers usually don't limit throughput—you can download large files at whatever speed the encrypted connection allows. Free VPN browsers often impose bandwidth caps, sometimes as low as 500MB per month.
Real-world testing shows patterns. Video streaming at 1080p typically requires 3-4 Mbps. Most VPN browsers can handle this without noticeable buffering, assuming your underlying connection is 10+ Mbps. Streaming at 4K resolution (15+ Mbps requirement) becomes unreliable through many VPN browsers.
Web browsing for news, email, and social media is generally fine. These sites transfer small amounts of data with lots of waiting time. The added latency barely registers. The encryption overhead is negligible.
Large file downloads are where performance becomes noticeable. A 500MB file that normally takes 5 minutes might take 7 minutes through a VPN browser. Not catastrophic, but perceptible enough that some users notice and switch back.
One factor that affects performance: the VPN browser provider's infrastructure. A VPN service with many high-capacity servers in different regions can distribute load efficiently. A smaller provider with fewer servers might have significant congestion, especially during peak hours.
Server location matters too. If you're on the US East Coast and connect to a server in Singapore, you'll have high latency just from the geographic distance. Connecting to a nearby server reduces latency but might reduce geographic spoofing benefits.
Most quality VPN browsers report achieving 70-85% of your normal browsing speed. That means if your connection normally gets 100 Mbps, you'll see around 70-85 Mbps through the VPN. This is acceptable for most people. The noticeable slowdown kicks in below 70% or when your base connection is already slow.

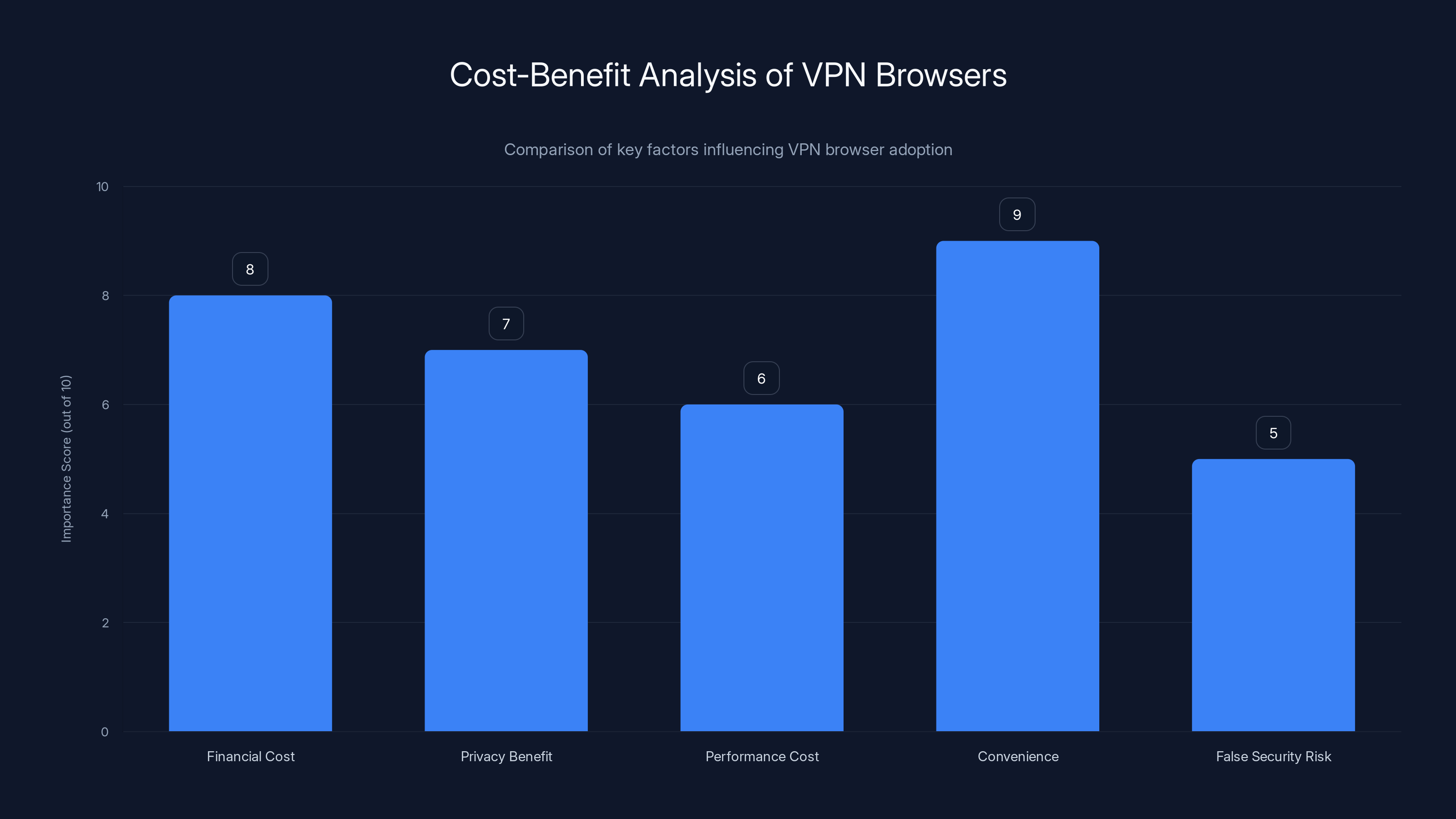
Convenience and financial cost are the most significant factors when considering a VPN browser, while false security risk is less emphasized. Estimated data based on typical user concerns.
Free vs. Paid VPN Browsers: Understanding the Economics
There's a saying in tech: if the product is free, you're the product. That doesn't mean all free VPN browsers are malicious, but it does mean you need to understand the business model.
Free VPN browsers generate revenue through several mechanisms:
Data collection and sale: Some free VPN services collect your browsing data and sell aggregated or anonymized information to advertisers or research companies. This directly undermines the privacy you're supposedly gaining.
Advertising injection: Free VPN browsers sometimes inject advertisements into websites you visit. This degrades user experience and potentially increases security risk if ads contain malicious content.
Bandwidth limitation: Free tiers typically cap monthly data usage, often at 500MB to 2GB per month. That's enough for casual browsing but not for streaming or large downloads.
Upselling: The free service is intentionally limited to push users toward premium paid tiers. This is legitimate business practice but means you're using a deliberately crippled version.
Malware bundling: In extreme cases, some free VPN providers have bundled malware with their software. This is less common now due to app store review processes, but it happened historically and occasionally resurfaces.
Paid VPN browsers address these issues by operating on a subscription model. Users pay monthly or annually, the VPN provider has direct revenue, and the incentive to monetize user data diminishes significantly.
Paid VPN browsers typically cost $5-15 per month depending on commitment length. Annual subscriptions are usually 40-50% cheaper per month than monthly subscriptions.
The price difference between cheap and premium paid VPN browsers often reflects infrastructure quality. A
Some paid VPN browsers include additional features beyond basic encryption. These might include:
- Malware blocking: Built-in detection of malicious websites
- Tracker blocking: Prevents advertisers from tracking you across sites
- Password management: Integrated password storage and auto-fill
- Identity theft protection: Monitoring of the dark web for leaked credentials
These additions justify higher pricing but aren't essential for basic privacy.
When evaluating free vs. paid, consider what you're trading. Free saves money but potentially trades privacy for convenience. Paid costs money but provides clearer privacy protection. The right choice depends on your threat model and budget.

When to Use a VPN Browser (And When Not To)
VPN browsers excel in specific scenarios and are inappropriate for others.
VPN browser is the right choice:
Public Wi-Fi browsing: You're working at a coffee shop and want to prevent anyone on the network from sniffing your passwords. A VPN browser solves this elegantly.
Light privacy preference: You want some privacy from your ISP and ad networks but don't need comprehensive device protection. A VPN browser is simpler than installing a full VPN application.
Accessing geo-restricted content: You want to watch a show that's only available in a specific country. Connecting through a VPN server in that country lets you access it.
Selective encryption: You want some traffic encrypted without affecting your entire device's performance. A VPN browser gives you granular control.
Multiple devices without installation: You need privacy on a device where you can't install applications, like a work computer or school laptop. A browser extension works around these restrictions.
VPN browser is NOT the right choice:
Complete device privacy: If you need to hide all your activity from your ISP or network administrator, you need a traditional VPN at the system level, not just a browser-level solution.
Privacy from workplace monitoring: Employers who monitor network traffic can detect VPN usage even if they can't see the contents. Many organizations actually block VPNs. A traditional VPN might work better, but your employer will still know you're using one.
Protecting non-browser applications: Email clients, messaging apps, and other software need protection too. A VPN browser doesn't help here.
Accessing applications that require ISP-level customization: Some services detect VPN usage and block it. A traditional VPN sometimes bypasses this better, and sometimes it doesn't help either.
Protecting IoT devices: Smart home devices, streaming boxes, and other connected devices can't use a VPN browser. You'd need a router-level VPN or a traditional VPN client.
The common theme: VPN browsers are great for browser-specific privacy. They're inadequate for comprehensive device security.
Most security professionals recommend using both, actually. A traditional VPN at the system level for comprehensive protection, combined with a VPN browser for additional browser-specific security and tracking prevention. This layered approach provides stronger protection than either alone, though the performance hit is more noticeable.
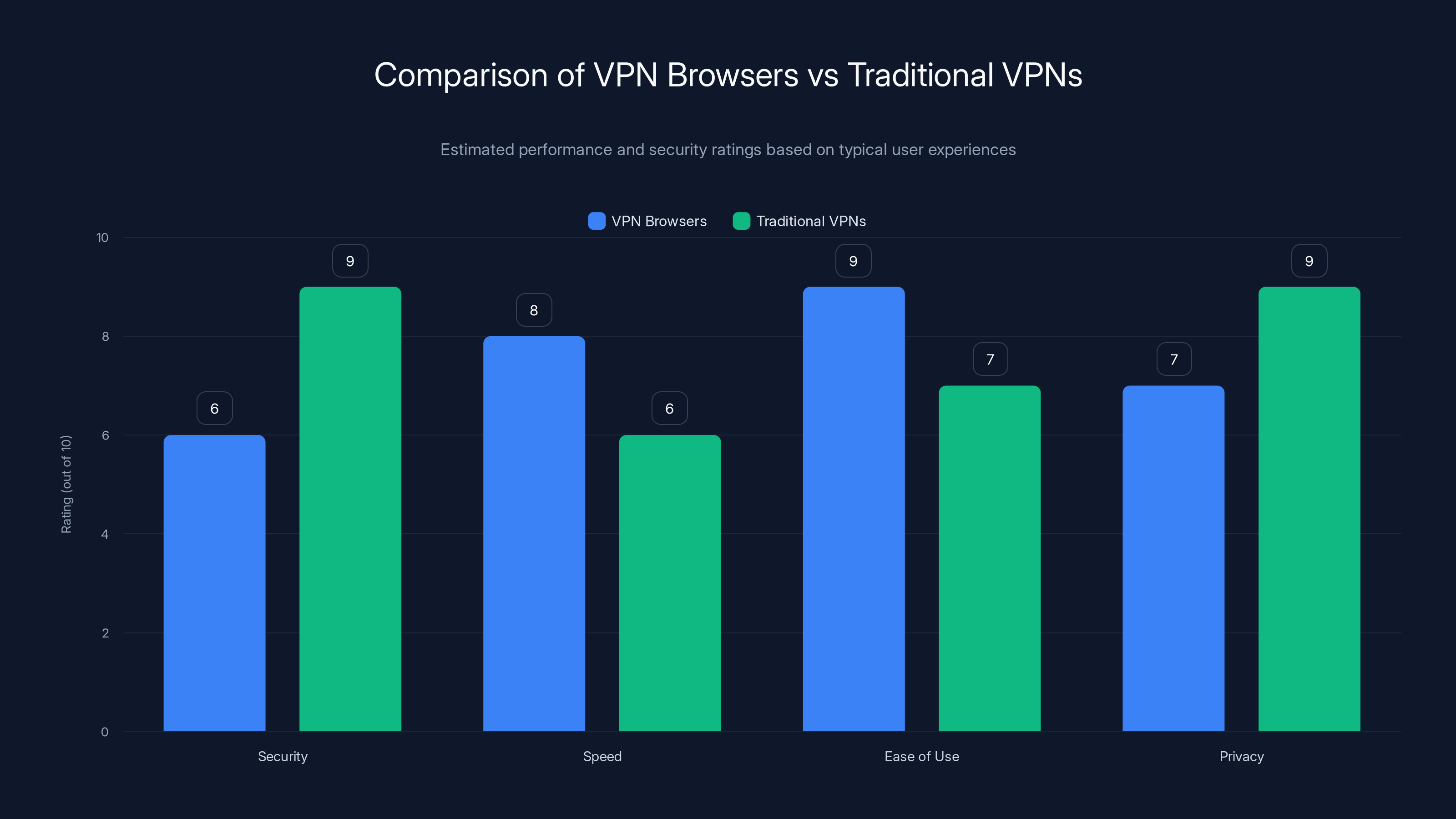
VPN browsers offer ease of use and speed but may compromise on security compared to traditional VPNs. Estimated data based on typical user feedback.
Privacy Policy Deep Dive: What to Actually Look For
Privacy policies are dense, often 50+ pages. But specific sections matter more than others when evaluating VPN browsers.
The most important section is logging policy. Specifically, which of these does the provider keep:
Connection logs: Records of when you connected, from which IP, and which VPN server you used. This alone doesn't reveal your browsing history but could connect you to activity.
Session logs: Records of your activity duration and data transferred. More revealing than connection logs.
Traffic logs: The actual websites you visited or data you transmitted. This is the real privacy violation.
Reputable VPN browsers state clearly that they keep connection metadata for technical purposes but do not keep traffic logs. Some claim a true "no-log" policy, keeping nothing. Be skeptical of true no-log claims—they're hard to verify and technically challenging to maintain.
The next critical section is data retention. Even if a VPN doesn't log traffic, how long do they keep connection metadata? 30 days? Forever? Most legitimate providers delete logs after a few weeks or months.
Third, look for the legal process section. Does the provider require government agencies to provide a warrant before surrendering user data? Or do they comply with any request? Does the company operate in a jurisdiction with strong privacy laws like Switzerland, or a jurisdiction with weak privacy protections?
Fourth, check for third-party audits. Has an independent security firm verified the no-log claims? Legitimate VPN providers often undergo annual audits published on their website. If no audit exists, that's a red flag.
Fifth, examine the threat model. What is the VPN designed to protect against? ISP snooping? Hackers on public networks? Advertisers? Different VPN browsers optimize for different threats.
Sixth, look for transparency reports. Does the company publish information about government requests received and how they responded? Transparency is a sign of confidence.
Finally, check the fine print about what happens if the company is purchased or goes out of business. Do they commit to deleting user data? Or could it be sold to a third party?
Reading privacy policies is tedious, but it directly determines what privacy you're actually getting. A VPN browser with good encryption but a bad privacy policy is worse than useless—it's a false sense of security.

Browser Fingerprinting and Advanced Tracking Methods
VPN browsers protect against traditional tracking methods. But tracking technology has evolved, and VPN browsers address only part of it.
Browser fingerprinting is the modern tracking technique that bypasses VPNs. Instead of using your IP address, trackers create a unique "fingerprint" based on your browser configuration. This includes:
- Screen resolution
- Browser type and version
- Installed fonts
- Operating system
- Hardware configuration
- Installed plugins
- JavaScript capabilities
With enough of these data points, trackers can identify you uniquely even if you change IP addresses through a VPN. Research from Princeton University showed that browser fingerprinting can accurately identify individuals with 94% accuracy when enough parameters are collected.
VPN browsers don't inherently solve this problem. A VPN alone doesn't change your browser fingerprint. You'd need to combine it with other privacy measures.
The solution involves multiple layers:
Browser privacy settings: Modern browsers like Firefox and Chrome offer privacy modes that reduce fingerprinting vectors.
Extensions that block trackers: Software like uBlock Origin or Privacy Badger blocks known tracking scripts.
Anti-fingerprinting extensions: Some extensions deliberately spoof fingerprinting data to prevent unique identification.
Using privacy-focused browsers: Browsers like Tor Browser or Brave are specifically designed to reduce fingerprinting opportunities.
The interaction between VPN browsers and fingerprinting is important. A VPN browser hides your IP (good for privacy), but if you're logged into Google, Facebook, or other services, those companies know exactly who you are regardless of VPN. The VPN only protects against ISP and network-level snooping, not service-level tracking from sites you've authenticated with.
This is why security experts emphasize that no single tool provides complete privacy. VPN browsers are one layer in a comprehensive privacy strategy, not a complete solution by themselves.
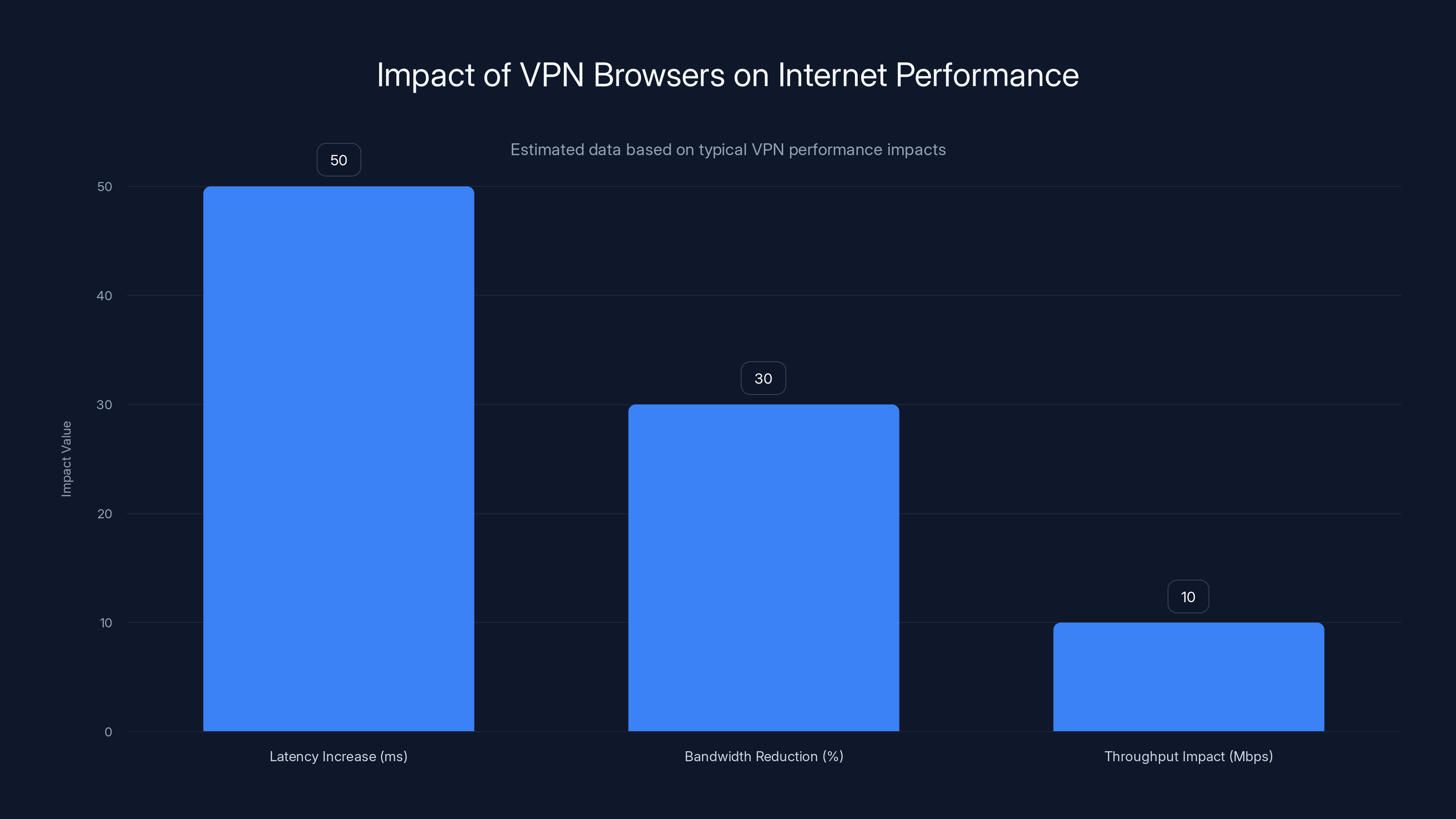
VPN browsers typically increase latency by 20-80ms, reduce bandwidth by 10-50%, and have minimal throughput impact. Estimated data based on typical VPN performance impacts.
Jurisdiction and Legal Considerations
Where a VPN browser company is incorporated matters tremendously for privacy protection.
Companies operating in certain jurisdictions are required by law to maintain certain data or surrender it on request. The most relevant legal framework is the Five Eyes Alliance—an intelligence sharing partnership between the US, UK, Canada, Australia, and New Zealand.
Countries within the Five Eyes have legal agreements to share surveillance data. A VPN company operating in the US, UK, or Australia might be required to hand over user data to these countries' governments even without warrant.
Other legal issues:
Mutual Legal Assistance Treaties (MLATs): Countries have agreements to cooperate on legal investigations. A VPN company operating in any MLAT signatory country could be legally required to comply with foreign government requests.
Data Localization Laws: Some countries require VPN providers to store user data locally. Russia, for example, requires VPN companies to store data on Russian servers subject to government access.
Copyright and patent laws: Some VPN browsers designed for accessing geo-restricted content might violate intellectual property laws in some jurisdictions.
The safest jurisdictions for VPN providers include Switzerland and Panama, which have strong privacy protections and favorable legal environments for VPN companies. Companies there have fewer legal obligations to surrender user data.
This matters because even a VPN browser with a strong no-log policy could be forced to log data if legal pressure is applied. A company in a strong privacy jurisdiction has more protection against this.
That said, all VPN companies operating globally must comply with laws in countries where they have significant user bases. Completely avoiding government legal action is impossible. The question is how much of a barrier a jurisdiction's laws present.

Common VPN Browser Mistakes and How to Avoid Them
People using VPN browsers often make mistakes that reduce or eliminate the privacy benefits.
Mistake 1: Thinking a VPN browser provides complete privacy.
This is the most common misunderstanding. A VPN browser protects your ISP and your network from seeing your activity. It doesn't prevent websites from tracking you (if you're logged in), doesn't protect non-browser applications, and doesn't prevent malware.
Avoid this by understanding what the VPN actually protects: transit-level privacy, not endpoint-level privacy.
Mistake 2: Not logging out of accounts while using a VPN.
When you're logged into your Google account, Gmail, or any authenticated service, that company knows exactly who you are. The VPN obscures your location to everyone except Google, Gmail, and the sites you're logged into. It's worse than useless in this case—it gives false confidence.
Avoid this by logging out of personal accounts when you want privacy, or use separate accounts for private and public browsing.
Mistake 3: Assuming VPN blocks ads and trackers.
A VPN blocks network-level snooping but doesn't block ads or trackers that are served through the same connection. Websites still load scripts that track you. YouTube still shows you personalized recommendations.
Avoid this by combining a VPN browser with tracker-blocking extensions.
Mistake 4: Using a VPN browser to access services that explicitly ban VPNs.
Many streaming services, banking sites, and betting sites block known VPN IP addresses. Using a VPN browser to access these services doesn't make them work—it just makes you look suspicious.
Avoid this by understanding which services block VPNs before trying to bypass restrictions.
Mistake 5: Choosing a VPN browser based solely on marketing promises.
"Military-grade encryption," "complete anonymity," "total privacy"—these are marketing phrases, not technical descriptions. A VPN browser that promises "total privacy" while operating in the US is misrepresenting what it can deliver.
Avoid this by reading privacy policies and checking for independent audits.
Mistake 6: Forgetting that public data is still public.
A VPN browser protects your connection but doesn't make your activities private from the services you use. If you post something on social media, it's public. A VPN doesn't change that.
Avoid this by remembering that VPN privacy is about connection security, not behavioral privacy.
Mistake 7: Using a free VPN without understanding the business model.
Free VPN browsers often make money through data collection. You're trading privacy to an advertiser for protection from ISP snooping. That's not a good deal.
Avoid this by checking privacy policies and understanding how free services monetize users.

Comparing Top VPN Browser Options
Various VPN browsers have different strengths and weaknesses. Here's a breakdown of categories worth evaluating.
Dedicated VPN Browsers: These are browsers built specifically around VPN functionality. They integrate the VPN directly rather than as an extension.
These typically offer better performance and tighter integration with the browser. The downside is they're not as customizable as your regular browser—you're limited to whatever features the VPN company includes.
Examples in this category offer strong encryption and reasonable speed. They typically cost $5-15 per month depending on commitment length and offer server selection in multiple countries.
Browser Extensions: These add VPN functionality to Chrome, Firefox, Edge, or other browsers you already use. They're more flexible—you get your favorite browser plus VPN protection.
The downside is performance. Browser extensions have more overhead than native browser implementations. They're also subject to browser security policies that might limit their effectiveness.
Most major VPN providers offer extension versions. Some like Opera have integrated VPNs directly into the browser.
Privacy-Focused Browsers: Browsers like Brave and Firefox include privacy features that reduce tracking alongside optional VPN functionality. They're designed to minimize fingerprinting and prevent data collection, which complements VPN protection.
These offer better integrated privacy but are specifically designed to replace your entire browser, not just add VPN functionality.
Comparison metrics:
Speed: Performance varies significantly. Good options maintain 70-85% of your normal speed. Cheap options might drop to 40-50%.
Server count: More servers generally mean better load distribution and faster speeds. Options with 50+ servers in diverse locations perform better.
Simultaneous connections: How many devices can you protect at once? This ranges from 1 device on cheap options to 6-10 devices on premium options.
Data limits: Free options cap at 500MB-2GB per month. Paid options offer unlimited data.
Jurisdiction: Check where the company operates. Swiss and Panamanian jurisdictions offer better privacy protection than US-based operators.
Audit status: Has an independent firm verified their claims? Published audits are a strong positive signal.
Kill switch: Does the service cut your internet if the VPN drops? This prevents accidental unencrypted connection.
Split tunneling: Can you choose which apps use the VPN and which connect normally?

Cost-Benefit Analysis: Is a VPN Browser Worth It?
Whether to use a VPN browser ultimately comes down to cost versus benefit.
Financial cost is straightforward. Premium VPN browsers cost
The privacy benefit depends on your threat model. If your concern is your ISP knowing which sites you visit, a VPN browser solves this well. If your concern is governments or sophisticated attackers, a VPN browser alone is insufficient.
The performance cost is real. You'll see 15-35% speed reduction. For streaming, that's mostly imperceptible. For large downloads, it's noticeable. For real-time applications, it's potentially problematic.
The convenience factor matters. A VPN browser is simpler than a traditional VPN. No software installation. No toggling on and off. It just works. For someone who values simplicity, this is worth something.
The false security risk is significant. If a VPN browser makes you think you have complete privacy when you don't, that's actively harmful. You might take risks (like using weak passwords) assuming the VPN protects you.
For a typical user:
Use a VPN browser if:
- You regularly use public Wi-Fi
- You want to prevent ISP tracking
- You don't need to protect non-browser applications
- You're comfortable with the speed reduction
- You understand it doesn't provide complete privacy
Skip a VPN browser if:
- You need complete device protection
- Speed is critical for your use case
- You can't afford the small monthly cost
- You're comfortable with ISP visibility
- You need to bypass VPN blocks (you'll need a robust VPN that doesn't fail)
Consider a VPN browser plus other measures if:
- You want comprehensive privacy (combine with privacy browser settings, tracker blocking, etc.)
- You want flexibility across multiple devices
- You need both browser privacy and some non-browser app privacy
The most rational choice for most people is probably to do nothing unless they have a specific privacy concern. The second most rational choice is to use a VPN browser for public Wi-Fi plus privacy browser settings. The third is a traditional VPN if you need more comprehensive protection.

The Future of VPN Browsers and Privacy Technology
VPN browser technology is evolving in interesting directions.
Decentralized VPNs are emerging as an alternative to centralized providers. Instead of routing through a single company's servers, traffic bounces through a network of distributed nodes. This makes it harder for any single entity to see user activity. Early implementations like Orchid are gaining traction, though performance is still not competitive with traditional VPNs.
Built-in browser privacy is improving. Modern browsers are implementing privacy features that reduce the need for separate VPN solutions. Firefox's Enhanced Tracking Protection, Safari's Intelligent Tracking Prevention, and Brave's native privacy features all chip away at the privacy gaps VPN browsers solve.
Zero-knowledge architecture is becoming standard. Instead of VPN providers seeing encrypted traffic, new designs use zero-knowledge proofs to verify transactions without revealing underlying data. This would provide privacy even if the VPN provider is compromised.
VPN-resistant authentication is becoming more sophisticated. As VPNs become common, services are developing better methods to detect and block VPN usage. This arms race means that bypassing restrictions with a VPN browser is becoming harder over time.
Integrated privacy ecosystems are replacing point solutions. Rather than a VPN browser plus a tracker blocker plus a password manager, we might see comprehensive privacy platforms that integrate all these functions.
Regulatory pressure is intensifying. The EU's Digital Services Act and similar regulations globally are pushing companies to change how they handle user data. This could make VPN browser privacy policies more stringent.
The trajectory suggests that VPN browsers will become more integrated into browsers themselves rather than remaining separate tools. We're already seeing this with Opera and Brave. Over the next 5 years, most mainstream browsers will likely include built-in VPN functionality.
This integration could improve performance and security. It could also reduce privacy if browsers make privacy tradeoffs to gain market share.

Key Takeaways Before You Decide
Let me distill this down to what actually matters for your decision.
VPN browsers encrypt your browser traffic and hide your IP address. This solves ISP snooping and prevents network-level eavesdropping. It's genuinely useful if public Wi-Fi is part of your routine.
VPN browsers don't provide complete privacy. They don't protect non-browser applications. They don't prevent websites from tracking you if you're logged in. They don't protect against malware or phishing. They don't make you anonymous.
The performance impact is real. Expect 15-35% slower browsing speeds depending on server distance and VPN provider quality. This is usually acceptable but occasionally noticeable.
Free VPN browsers are worth being skeptical about. If the service is free, the business model usually involves monetizing something. That something is often your data.
Jurisdiction matters for long-term privacy. A company incorporated in Switzerland provides better legal protection against surveillance than a US-based company. Check where your VPN browser provider is based.
Privacy policies matter more than marketing claims. Read the actual policy, not the sales page. Look for no-log claims backed by audits, clear data retention policies, and jurisdiction-based privacy protection.
VPN browsers are one tool in a privacy toolkit, not a complete solution. Combine with tracker blockers, privacy browser settings, and careful account management for actual privacy.
For most people, a VPN browser isn't essential. It becomes valuable when you use public Wi-Fi regularly or need to prevent ISP tracking. If you never use untrusted networks and trust your ISP, a VPN browser doesn't solve problems you actually have.
The right decision depends on your specific situation, comfort with minor slowdowns, and threat model. If this guide described concerns you actually have, a quality VPN browser solves real problems. If not, the time and money investment might be better spent elsewhere.
FAQ
What exactly is a VPN browser?
A VPN browser is either a dedicated web browser or a browser extension that encrypts your internet traffic and routes it through a remote server. This hides your IP address and prevents ISP snooping but only protects browser activity, not other applications on your device. The encryption makes your traffic unreadable to network eavesdroppers, though it can't protect against malware or phishing attacks.
How is a VPN browser different from a regular VPN app?
A regular VPN protects all traffic from your entire device through one encrypted tunnel. A VPN browser only protects browser traffic, leaving other applications like email clients and messaging apps unprotected. VPN browsers are simpler to use and faster for non-browser applications, but less comprehensive. A traditional VPN is better for complete device protection but causes more noticeable slowdown across everything.
Do VPN browsers actually keep you anonymous?
No. VPN browsers hide your IP address from websites and ISPs but don't make you anonymous. If you're logged into your Google account, Google knows who you are regardless of VPN. If you post your real name on social media, it's public. VPN browsers provide privacy from network-level snooping, not behavioral privacy or anonymity from services you use.
Can I get in legal trouble for using a VPN browser?
In most countries, using a VPN is completely legal. A few countries including China, Russia, and Iran restrict or block VPN usage, and some restrict certain VPN types. Using a VPN to commit crimes is illegal, but using one for privacy is legal in democratic countries. Check your local laws if you're in a restrictive region.
Are free VPN browsers safe?
Free VPN browsers have legitimate security risks. Some have been caught distributing malware, others collect user data to monetize, and others have poor security practices. The saying "if the product is free, you're the product" often applies. If you want a VPN browser, paid options from reputable providers are safer and more trustworthy than free options.
How much will a VPN browser slow down my internet?
Expect 15-35% speed reduction depending on server location and VPN provider quality. Local servers cause less slowdown than distant ones. Premium VPN providers with good infrastructure see less slowdown than cheap providers. Testing with a trial version will show you the actual impact on your specific connection.
Should I use a VPN browser on public Wi-Fi?
Yes. Public Wi-Fi is insecure, and a VPN browser effectively solves the main security risk: network-level packet sniffing. Using a VPN browser on public Wi-Fi prevents attackers on the same network from stealing your login credentials. Combined with HTTPS websites, it provides strong protection for the threats present on public networks.
Can websites detect that I'm using a VPN browser?
Yes. Websites can identify VPN IP addresses and see that traffic is coming from a VPN. Many streaming services and banks deliberately block VPN IP addresses. However, websites can't see your real IP or your actual location, which is the point of the VPN. Detection and blocking doesn't mean the VPN doesn't work—it just means some services restrict access from VPN addresses.
Is a VPN browser better than a VPN app?
Neither is universally better. VPN browsers are simpler, faster for non-browser traffic, and more convenient. VPN apps are more comprehensive, protecting your entire device. For most people, a VPN browser is sufficient for the privacy problem they're trying to solve. If you need complete device protection or plan to protect IoT devices, a VPN app is better.
What should I look for in a VPN browser provider?
Key factors include: jurisdiction (Switzerland and Panama are best for privacy), independent audits of privacy claims, clear data retention policies, performance in your geographic region, simultaneous device connections allowed, server count and diversity, and whether they offer a kill switch if the connection drops. Read privacy policies carefully—they reveal actual practices better than marketing claims.

Final Thoughts
VPN browsers exist in an interesting middle ground. They're not as comprehensive as traditional VPNs, but they're simpler and less intrusive. They provide real privacy benefits while being fundamentally limited in scope.
If you found yourself nodding along during the public Wi-Fi sections, a VPN browser makes sense for you. The protection is real, the convenience is genuine, and the slowdown is usually tolerable.
If you found yourself thinking "I don't really use untrusted networks," then a VPN browser is probably unnecessary. Most people's actual internet usage doesn't create the risks that VPN browsers solve.
The decision should flow from your actual behavior and concerns, not marketing anxiety. VPN browsers are a legitimate tool for legitimate privacy concerns. Using one for the wrong reasons creates false confidence rather than actual security.
Weigh the factors: your use of public Wi-Fi, your trust in your ISP, your performance tolerance, and your privacy concerns. That assessment will tell you whether a VPN browser belongs in your toolkit or whether your time and money is better spent elsewhere.
If you decide to use one, choose a reputable paid provider that undergoes independent audits. The monthly cost is small compared to the peace of mind of knowing your privacy is actually being protected by a company that has financial incentive to keep that promise.

Related Articles
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- Condé Nast Data Breach 2025: What Happened and Why It Matters [2025]
- Supply Chain, AI & Cloud Failures in 2025: Critical Lessons
- Cybersecurity Insiders Plead Guilty to ALPHV Ransomware Attacks [2025]
- Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data [2025]
- 1Password Deal: Save 50% on Premium Password Manager [2025]
![Should You Use a VPN Browser? Complete Guide [2025]](https://tryrunable.com/blog/should-you-use-a-vpn-browser-complete-guide-2025/image-1-1767274794111.jpg)



