Condé Nast Data Breach 2025: What Happened and Why It Matters
Introduction: Understanding the Breach
In December 2025, one of the media industry's largest security incidents unfolded when a hacker claiming the alias "Lovely" publicly disclosed a massive database breach affecting Condé Nast, one of the world's most recognizable media conglomerates. The incident exposed personal information from more than 2.3 million user accounts across WIRED, one of Condé Nast's flagship publications. What makes this breach particularly significant is not just its scale, but the circumstances surrounding it, the company's apparent response (or lack thereof), and what it reveals about security practices at major media organizations.
The breach came with a bold claim: the hacker stated they possessed access to 40 million additional user records spanning other Condé Nast properties, including Vogue, The New Yorker, Vanity Fair, and numerous other prestigious publications. This potential scope makes it one of the largest media industry breaches in recent history. Yet the incident also carried an unusual narrative. The hacker claimed they initially attempted to work with Condé Nast to patch security vulnerabilities, only to be rebuffed repeatedly over the course of a month. This narrative shifted the conversation from a typical extortion scenario to questions about corporate responsibility and security prioritization.
For Ars Technica readers specifically, there's important reassurance: Ars Technica operated independently of Condé Nast's vulnerable infrastructure. The publication runs on its own custom technology stack, meaning readers' data remained secure throughout the incident. This distinction became crucial in the aftermath, as it highlighted how even within the same corporate family, infrastructure decisions can dramatically affect security posture.
What unfolded over the following weeks was a masterclass in modern threat disclosure, ethical questions around security disclosure practices, and the tension between cybersecurity professionals who believe transparency helps companies improve versus those who see it as leverage for payment. The incident also exposed something darker: the possibility that the hacker's initial claims about wanting to help patch vulnerabilities were potentially misleading, raising questions about trustworthiness in the cybersecurity community itself.
This comprehensive guide breaks down what happened during the Condé Nast breach, examines the technical and organizational failures that made it possible, analyzes the security implications for users and the media industry, and explores what consumers should do to protect themselves going forward.

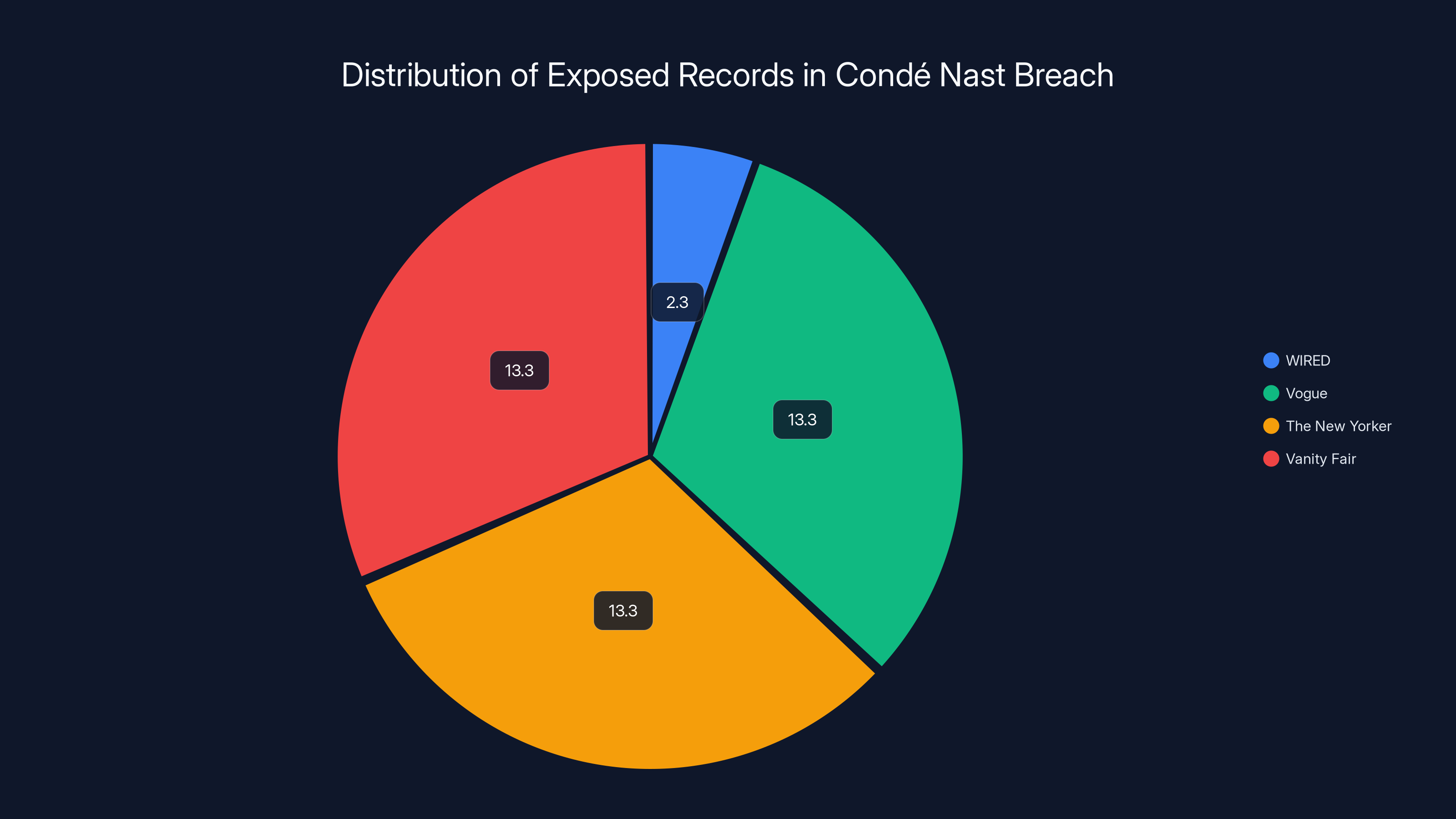
The breach initially exposed 2.3 million WIRED records. The hacker claimed an additional 40 million records from other Condé Nast properties, estimated equally among Vogue, The New Yorker, and Vanity Fair. Estimated data.
TL; DR
- The Breach Scale: A hacker exposed 2.3 million user records from WIRED, with claims of access to 40 million more from other Condé Nast properties
- Data Exposed: Demographic information including names, email addresses, physical addresses, and phone numbers, but notably NOT passwords
- Ars Technica Safe: Ars Technica readers' data was not compromised because the publication runs independent infrastructure
- The Unusual Circumstance: The hacker claimed they tried to get Condé Nast to patch vulnerabilities for a month before releasing data
- Credibility Questions: Cybersecurity researchers suggested the hacker may have been dishonest about their initial intentions, acting as a cybercriminal seeking payment rather than a security researcher seeking remediation
The Initial Disclosure: How the Breach Became Public
Breaches rarely announce themselves politely. This one came through the kind of channels that security researchers monitor constantly: underground forums, data marketplaces, and direct communications with established data breach tracking websites.
Early in December 2025, a hacker operating under the alias "Lovely" began circulating claims that they had successfully breached Condé Nast's user database infrastructure. Rather than sitting on the data or attempting a traditional extortion scheme, Lovely took the unusual step of reaching out to Data Breaches.net, a prominent independent security website that tracks and reports on data breaches worldwide. This direct approach initially gave Lovely a veneer of legitimacy. By going to recognized breach researchers first, rather than selling data on the dark web or contacting news outlets directly, Lovely appeared to be following responsible disclosure practices.
The initial leak included a substantial dataset: over 2.3 million user records from WIRED magazine specifically. The data came with detailed documentation showing exactly what information had been compromised. Names, email addresses, physical mailing addresses, and phone numbers were all included in the exposed records. The hacker provided samples of the data to verify authenticity, a standard practice in breach disclosures that demonstrates the attacker actually possesses what they claim to possess.
What the exposed data did NOT include was equally important as what it did. Passwords were notably absent from the breach. This distinction matters significantly because it means users' Condé Nast credentials couldn't be directly harvested for account takeovers. However, the demographic information exposed could still be valuable for various purposes: phishing campaigns could target WIRED readers by name, address data could feed into physical mail attacks or mailing list frauds, and phone numbers could be used for social engineering attacks.
Alongside the initial breach announcement came a dramatic claim: Lovely stated they possessed access to an additional 40 million user records spanning multiple other Condé Nast properties. The list included Vogue, The New Yorker, Vanity Fair, Allure, Architectural Digest, Bon Appétit, Condé Nast Traveler, Glamour, GQ, Wired.com, and numerous other publications under the Condé Nast umbrella. If true, this would represent one of the largest media industry breaches on record, affecting approximately 42 million people across multiple publications.
The timing of the disclosure mattered. Lovely began releasing data during the holiday season, when corporate security and incident response teams operate at reduced capacity. This timing often indicates an attacker with sophisticated knowledge of how corporate security operates, knowing that fewer personnel would be monitoring systems during late December.

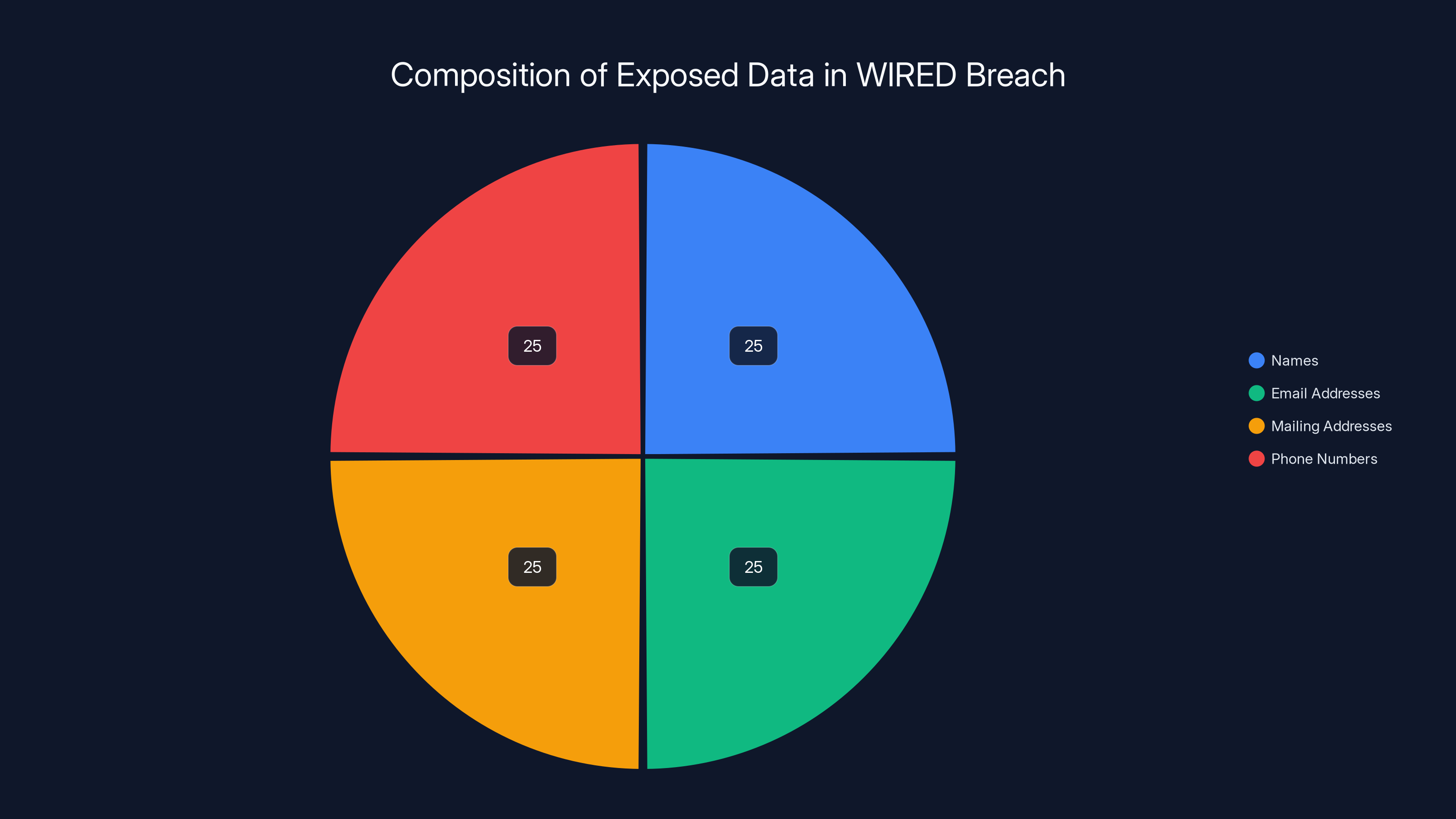
The breach exposed a balanced set of user information, each comprising 25% of the total data leaked. Notably, passwords were not included, reducing the risk of direct account takeovers.
The Hacker's Claims: The Vulnerability Disclosure Narrative
What made this breach distinctly unusual was the accompanying narrative. Lovely didn't just claim to have breached Condé Nast; they claimed to have attempted to help the company fix its security problems first.
According to Lovely's account, they had discovered serious security vulnerabilities in Condé Nast's infrastructure and proactively reached out to the company to report them. Rather than immediately exploiting these vulnerabilities, Lovely stated they spent an entire month trying to convince Condé Nast security teams to patch the flaws. The message conveyed frustration, claiming Condé Nast showed no concern for user data security and refused to take the vulnerability reports seriously.
In a public statement, Lovely wrote: "Condé Nast does not care about the security of their users data. It took us an entire month to convince them to fix the vulnerabilities on their websites. We will leak more of their users' data (40 + million) over the next few weeks. Enjoy!"
This framing was clever. By positioning themselves as a security researcher attempting responsible disclosure, Lovely could claim moral high ground. The narrative suggested this wasn't cybercriminal activity but rather a justified response to corporate negligence. From a social engineering perspective, it was effective: many in the security community sympathize with researchers who feel their vulnerability reports are ignored by large organizations.
The claims fit a pattern that security professionals see regularly. Major companies do sometimes ignore vulnerability reports. Security researchers do get frustrated when companies deprioritize fixes. Some researchers do ultimately leak data as a final resort to force attention and accountability. The Lovely narrative tapped into these real grievances.
However, there was a critical problem with this narrative: it may have been entirely fabricated.
The Credibility Question: When Hackers Play Researchers
As the breach story developed, researchers at established security tracking organizations began asking uncomfortable questions. Data Breaches.net, the very outlet that Lovely had contacted with the breach information, eventually published a critical analysis suggesting Lovely may have been dishonest from the start.
The assessment was damning. According to Data Breaches.net's investigation, Lovely appeared to have deliberately misled security researchers into believing they were dealing with a legitimate security professional attempting responsible disclosure. The actual behavior, when examined more carefully, looked more like conventional cybercriminal activity: someone who gained unauthorized access to systems, extracted valuable data, and was now using the threat of further releases as leverage.
"As for 'Lovely,' they played me," Data Breaches.net stated bluntly. "Condé Nast should never pay them a dime, and no one else should ever, as their word clearly cannot be trusted."
This assessment raised several critical points:
First, the timeline didn't fully add up. If Lovely had genuinely spent a month attempting to report vulnerabilities through proper channels, there would typically be documented communications: emails to security contacts, records of interactions with incident response teams, or at minimum evidence of good-faith attempts at coordination. No such documentation materialized.
Second, the behavior pattern resembled extortion rather than responsible disclosure. A security researcher genuinely concerned about user safety typically coordinates with authorities, works with regulatory bodies if necessary, and follows established disclosure frameworks like CVE (Common Vulnerabilities and Exposures) protocols. Lovely's approach of dumping data publicly and threatening to release more aligned more closely with ransom-based extortion tactics.
Third, the escalating threat pattern suggested cybercriminal motivation. Lovely's subsequent releases and communications, rather than becoming more cooperative or collaborative, became increasingly antagonistic. They were ramping up pressure, not attempting reconciliation.
This revelation highlighted a critical gap in cybersecurity: the inability of security researchers and the public to easily distinguish between legitimate security professionals and sophisticated attackers adopting the language and framing of security research to gain credibility and control the narrative.
Why Ars Technica Remained Unaffected
For readers of Ars Technica specifically, one piece of news provided genuine relief: the breach didn't affect them. Ars Technica's user data remained completely secure, despite being under the same corporate umbrella as the breached publications.
This wasn't luck. It was architecture. Ars Technica operates on what the publication describes as a "bespoke tech stack"—essentially a custom-built technology infrastructure developed specifically for its needs rather than relying on shared corporate systems.
This decision, made years before the breach, had significant implications. While WIRED and other Condé Nast publications shared common infrastructure, user databases, and services, Ars Technica maintained separation. This architectural decision meant that whatever vulnerabilities existed in Condé Nast's shared infrastructure didn't extend to Ars Technica's systems.
The distinction illustrates a critical security principle: infrastructure isolation. By maintaining independent systems rather than consolidating everything into a shared corporate platform, Ars Technica limited its vulnerability surface. When one part of an organization gets breached, any connected systems become vulnerable. By running independently, Ars Technica ensured its users remained protected even when sister publications experienced catastrophic security failures.
This also meant that Ars Technica readers received different communication from the breach than users of other Condé Nast properties. There were no notifications to send, no compromised accounts to monitor, no passwords to reset. For Ars readers, the breach was essentially a non-event from a personal security standpoint, though it carried important lessons about corporate security practices.
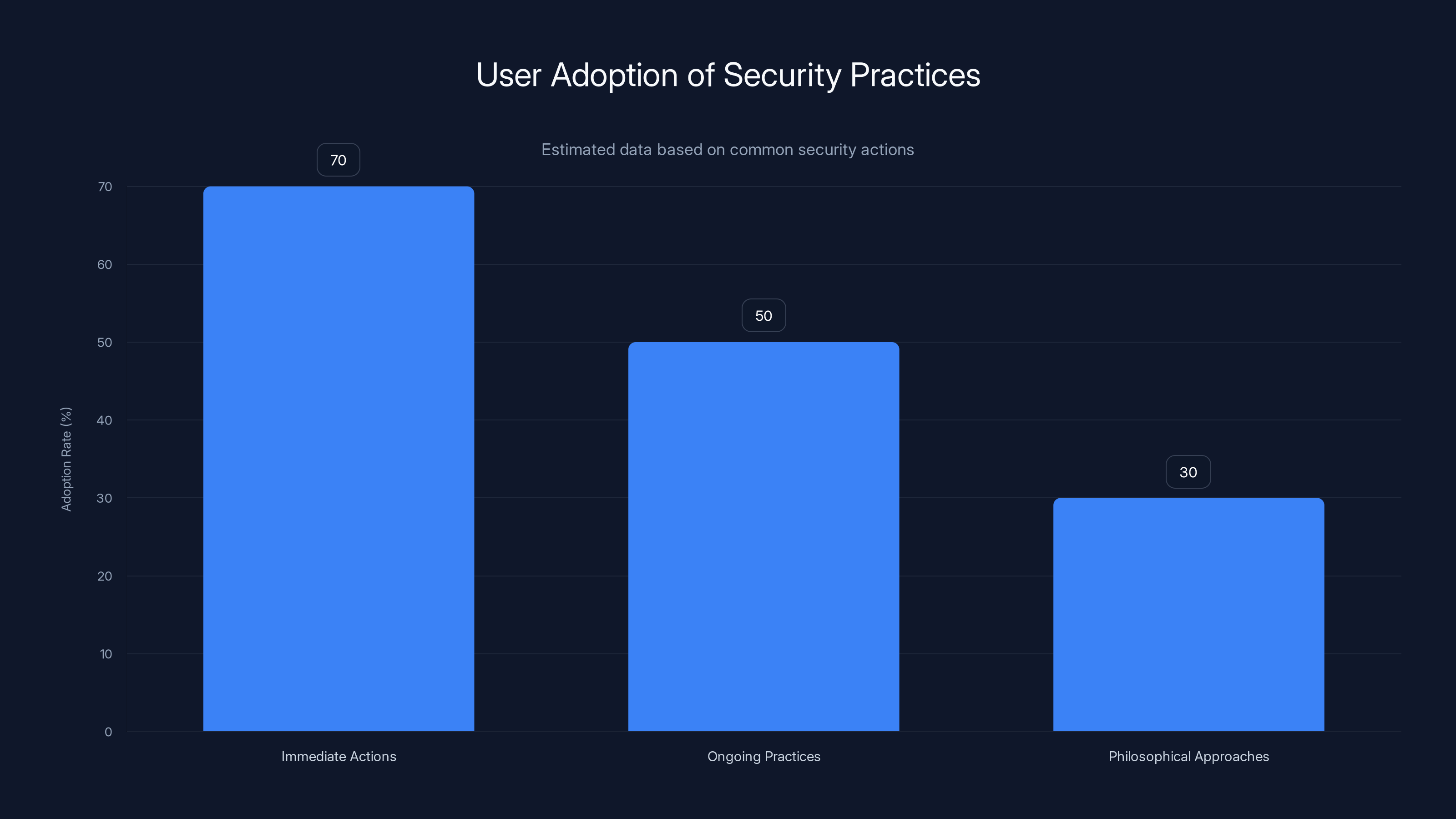
Estimated data suggests immediate actions have higher adoption rates among users compared to ongoing practices and philosophical approaches.
The Data Exposed: What Information Was Compromised
Understanding exactly what data was exposed matters significantly for affected users, because different types of data present different risks.
The 2.3 million records from WIRED that were publicly released included demographic information specifically: names, email addresses, physical mailing addresses, and phone numbers. This is the foundational personal information that identifies individuals and enables direct contact.
Critically, the exposed data did NOT include passwords. This distinction significantly reduces certain types of risk. Without passwords, attackers cannot directly access user accounts. They cannot log in to accounts to steal further data, change account settings, or impersonate users to fraudulent actors. This limitation means the attack vector remains more constrained than it could have been.
However, the absence of passwords doesn't mean the exposed data is harmless. Here's what attackers can do with names, email addresses, addresses, and phone numbers:
Phishing and Social Engineering: With names, emails, and phone numbers, sophisticated attackers can craft highly personalized phishing emails or phone calls that appear to come from legitimate sources. "Hello [Name], we need to verify your account with [Real Organization]..." These attacks have dramatically higher success rates than generic mass phishing.
Mailing List Compilation: Physical addresses in the dataset can be aggregated with other data sources to create targeted mailing lists for fraudulent promotions, scams, or even physical mail theft schemes.
Identity Theft Preparation: While complete identity theft requires Social Security numbers or financial information, the exposed data provides the foundational identity elements needed to launch social engineering attacks that might eventually yield more sensitive information.
Credential Stuffing: Attackers often assume people reuse passwords across sites. By trying the combination of WIRED email + common passwords at other services (banks, social media, etc.), attackers might gain access to accounts that share passwords.
Marketing and Targeting: The data can be sold to marketers or combined with other information to create highly detailed user profiles for targeted advertising or fraud.
The threat also depends on what else gets released. Lovely's claims suggested that 40 million additional records existed, potentially including data from multiple publications. If those releases contain more sensitive information, the risk profile increases substantially.
Understanding the Vulnerability: How the Breach Happened
While the full technical details of how Lovely exploited Condé Nast's systems remain somewhat opaque, security researchers and analysts have offered educated assessments based on the breach characteristics.
The fact that demographic data was stored in accessible databases suggests vulnerabilities in either database access controls, application security, or authentication systems. Possible attack vectors include:
SQL Injection: One of the oldest and most persistent web application vulnerabilities, SQL injection allows attackers to bypass normal database queries and directly access or extract data. A vulnerable login form or user profile page could potentially expose the entire database to an attacker with basic technical knowledge.
Insecure API Endpoints: Modern applications rely on APIs (Application Programming Interfaces) to transfer data between systems. If these APIs lack proper authentication, rate limiting, or validation, attackers can extract massive amounts of data through automated requests.
Credential Compromise: Sometimes the simplest explanation is accurate. If an employee account with database access was compromised through phishing, malware, or credential reuse, an attacker could potentially export entire databases directly.
Unpatched Vulnerabilities: Lovely's claim about vulnerabilities that weren't patched aligns with a common scenario where known security vulnerabilities exist in publicly available software, but organizations fail to update their systems promptly.
Misconfigured Cloud Storage: Increasingly, organizations store databases in cloud services like Amazon S3, Google Cloud Storage, or Azure. Misconfigured permissions on these services have led to massive breaches when data becomes accessible to unauthorized users or even the public internet.
Lovely's apparent claim about a one-month window to fix vulnerabilities, whether genuine or fabricated, suggests the vulnerabilities were either known to the organization or communicated to them. This pattern indicates either a patch that wasn't deployed or a vulnerability that was recognized but deprioritized.
The Incident Response: Condé Nast's Actions (and Inactions)
From a public perspective, Condé Nast's response to the breach was notably minimal. The company issued no public statement in the immediate aftermath of Lovely's disclosure. Ars Technica received no internal communication about the breach, though again, this made sense given that Ars wasn't affected.
For users of breached Condé Nast properties, the lack of immediate corporate communication created a vacuum. Typically, when breaches of this magnitude occur, organizations immediately notify affected users, provide guidance on protective steps, and detail what they're doing to investigate and remediate. The silence was conspicuous.
This response pattern raises important questions:
Why the Silence? Possible explanations range from genuine confusion about the situation's scope (were the breach claims legitimate or exaggerated?) to legal advice to stay quiet during investigation, to organizational dysfunction under crisis conditions. Large media companies often have complex legal and PR structures that can slow decision-making during emergencies.
Investigation Timeline: Determining the full scope of a breach and its root cause requires technical investigation time. Rushing to public statements before understanding what happened can backfire. However, delayed communication also erodes user trust.
Regulatory Requirements: Depending on jurisdiction and data type, organizations may be legally required to notify users within specific timeframes. If Condé Nast missed these windows, it could face additional regulatory action.
Damage Control: In some cases, organizations choose minimal public communication hoping a breach story will fade from media attention if not amplified by corporate statements.
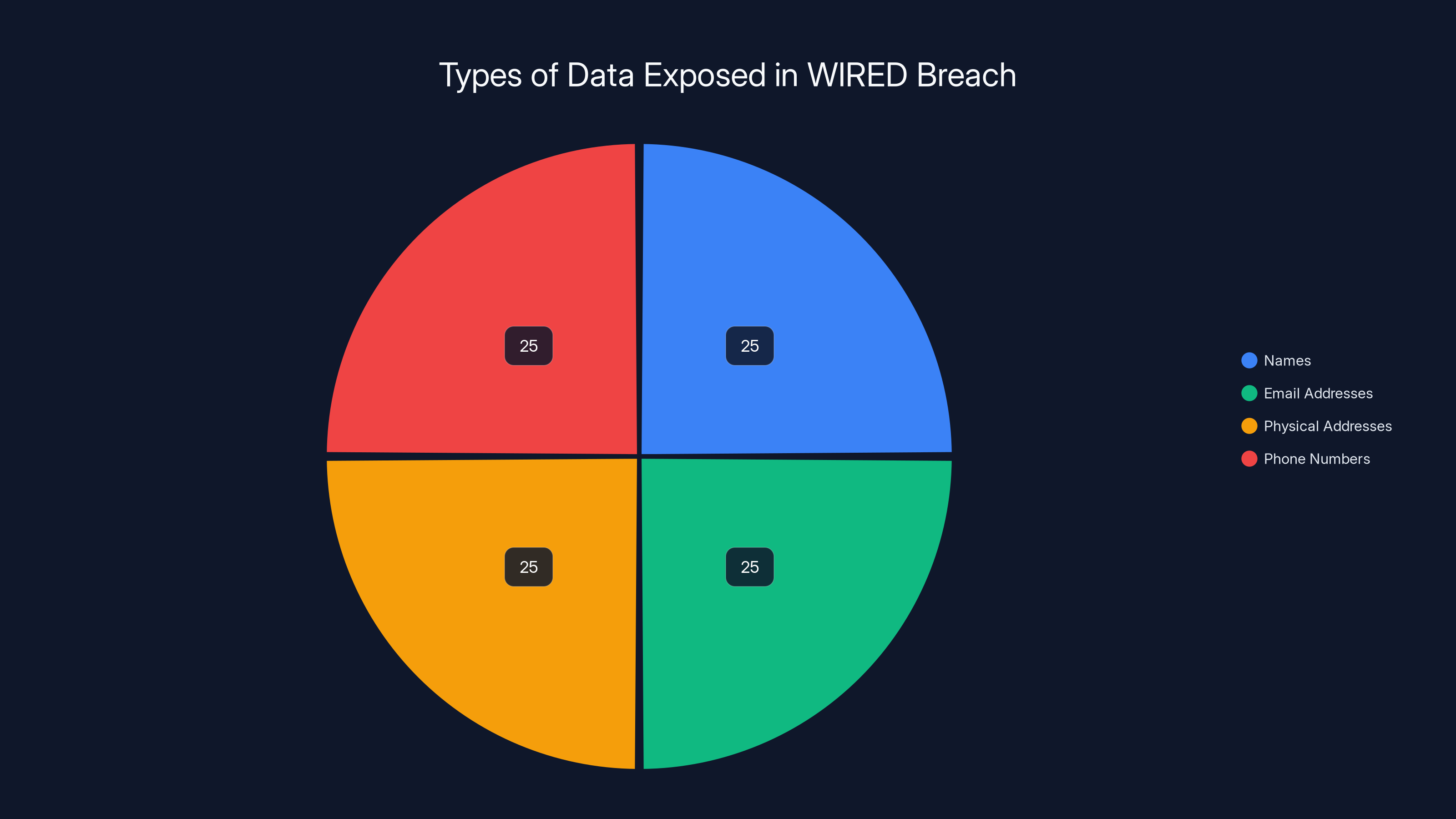
The breach exposed an equal distribution of names, email addresses, physical addresses, and phone numbers, each comprising 25% of the total data. Estimated data based on typical record structure.
The Media Industry's Security Problem: A Broader Pattern
The Condé Nast breach didn't occur in isolation. It reflects broader security challenges facing the media industry specifically.
Media companies operate in a unique position: they maintain large user databases to power subscription services, personalization, newsletters, and audience analytics. These databases are valuable both to the organization and to potential attackers. Yet media companies don't typically employ the massive security engineering teams that major technology companies maintain.
A typical media company's tech stack might include:
- Content management systems (sometimes decades old)
- User account and subscription systems
- Analytics platforms
- Email newsletter delivery systems
- Advertising technology integrations
- Third-party service integrations
Each integration point represents a potential vulnerability. Each system requires maintenance, updates, and security monitoring. As organizations add features, layers of technology accumulate without corresponding security investments.
Media companies also face pressure to ship features quickly and maintain reader engagement. Security can sometimes feel like a feature that doesn't directly drive revenue, leading to deprioritization when resources are limited. This creates exactly the scenario Lovely (claims to have) encountered: vulnerabilities identified but not patched because security takes a back seat to product releases.
The industry also struggles with talent. Security engineers command high salaries and have abundant job opportunities at major tech companies. A regional media outlet or even a national publication might struggle to compete for top security talent against Google, Meta, or Apple. This creates a gravitational pull where the most skilled security professionals migrate to large tech companies, leaving media companies with less experienced security teams.
Conversely, when a media organization does suffer a high-profile breach, the reputational damage can be significant. Readers don't want their personal information exposed. Advertisers become concerned about brand association. The breach becomes a story, reported by competing outlets, amplifying the damage.
User Risk Assessment: Who Was Actually Affected and How
For the 2.3 million WIRED readers whose information was exposed, the practical risk depends on individual circumstances and behavior.
High Risk Indicators:
- You received phishing emails claiming to be from WIRED or other "Condé Nast" entities
- You reuse the same password across multiple services
- You have significant assets or online accounts that could be targeted through social engineering
- You're a public figure or person with valuable identity information
- You live in a jurisdiction with active fraud operations
Medium Risk Indicators:
- You have an account with WIRED but maintain unique passwords
- You monitor credit reports and account activity regularly
- Your email address wasn't otherwise sensitive or widely circulated
- Your phone number was registered with the account
Lower Risk Indicators:
- Your account was inactive and contained minimal personal information
- You've already changed passwords since the breach
- You've enabled two-factor authentication on critical accounts
- You don't reuse passwords and monitor financial accounts regularly
The broader risk also extends beyond the 2.3 million initially compromised accounts. If Lovely's claims about 40 million additional records prove legitimate, the risk profile for other publications' readers scales dramatically. A 40-million-person exposure would rank among the largest media industry breaches.

Lessons in Information Security: What the Breach Reveals
The Condé Nast incident teaches multiple lessons for organizations, security professionals, and users.
For Organizations:
The most fundamental lesson is that security requires cultural commitment, not just technical solutions. Technical controls matter, but they only work if organizations consistently apply patches, update systems, and prioritize security alongside feature development.
Second, infrastructure decisions made years ago have consequences. Ars Technica's independent tech stack was likely a decision made for business reasons—independence, technical control, customization. Yet it provided security benefits as an unintended consequence. Organizations should recognize that architectural decisions have multi-dimensional impacts.
Third, incident response speed matters. Whether Condé Nast's silence reflected genuine confusion or deliberate strategy, the lack of immediate communication created space for speculation and potentially increased user anxiety.
For Security Professionals:
The breach highlights the importance of distinguishing between actual threat actors and those adopting the language of security research for leverage. Sophisticated attackers now routinely adopt responsible disclosure framing, making it harder for security researchers to identify genuine bad actors.
For Users:
The incident reinforces several critical practices:
-
Password Uniqueness: Use unique passwords for each significant service. Password reuse means a breach at one service compromises all related accounts.
-
Notification Vigilance: Monitor your email for breach notifications from organizations you've used. These notifications often contain important information about protecting your account.
-
Proactive Security: Rather than waiting for a breach notification, users should periodically review account activity, monitor credit reports, and enable additional security measures like two-factor authentication on critical accounts.
-
Trust but Verify: When you receive messages claiming to be from an organization, verify their legitimacy before clicking links or providing information.
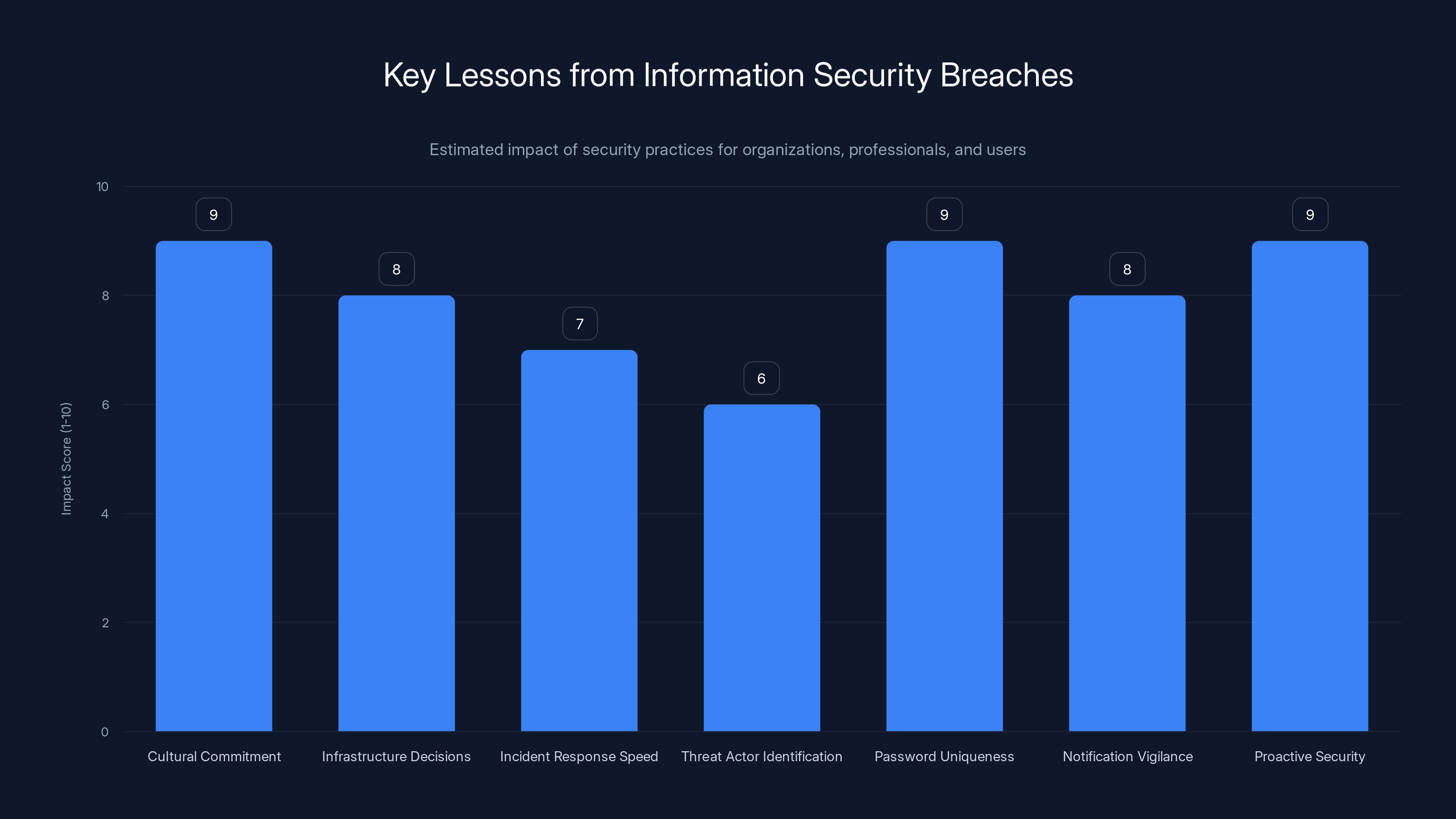
Cultural commitment and proactive security measures are rated highest in impact for preventing breaches. Estimated data based on typical security insights.
The Threat Landscape: Implications for Similar Organizations
The Condé Nast breach has implications extending far beyond one media conglomerate. Any organization with similar characteristics faces comparable risks.
Publications and media organizations specifically should recognize they're attractive targets. User databases connected to prestigious publications can command higher prices in criminal markets. Users of premium publications may have higher income levels, better credit, and more assets—making them more valuable fraud targets.
Software-as-a-Service (SaaS) providers that serve media organizations should review their security postures. If a platform serves multiple publications, a single compromise could affect all customers.
Advertising technology companies that integrate with media platforms should audit their access and authentication systems. These integrations are often the weakness exploited in larger breaches.
Organizations should also recognize that the threat isn't always external attackers. Insider threats—employees with system access—represent a significant risk vector. Controlling who has access to sensitive databases and auditing that access regularly matters as much as external security controls.

Regulatory and Legal Consequences: What Happens Next
While the immediate breach has occurred, significant regulatory and legal processes typically follow high-profile breaches.
Depending on jurisdiction, Condé Nast likely faces obligations including:
Notification Requirements: Most U.S. states and international jurisdictions require breach notifications within specific timeframes. If Condé Nast missed these windows, they could face regulatory fines.
Data Protection Compliance: Depending on where affected users are located, GDPR (European Union), CCPA (California), and similar regulations may impose specific requirements and potential fines for violations.
Class Action Lawsuits: With millions of users affected, law firms will inevitably file class action lawsuits on behalf of affected users. These lawsuits typically seek compensation for exposure time, credit monitoring costs, and damages from identity theft if it occurs.
Regulatory Investigations: State attorneys general, international data protection authorities, and industry-specific regulators may investigate the breach, particularly focusing on whether the company had adequate security controls and why vulnerabilities weren't patched.
Insurance Claims: Cyber liability insurance typically covers breach response costs, notification expenses, credit monitoring, and legal expenses. Condé Nast's insurance carriers will likely be heavily involved in incident response.
These processes can take years to resolve. During that time, the organization operates under regulatory scrutiny, faces ongoing legal costs, and experiences persistent reputational damage.
Prevention Strategies: What Organizations Should Do
For organizations genuinely concerned about avoiding similar breaches, several strategic approaches reduce risk.
Security Infrastructure Investment: Organizations need to invest in modern security infrastructure including vulnerability scanning, penetration testing, security incident response teams, and comprehensive logging and monitoring.
Patching Discipline: Establishing systematic processes for identifying, prioritizing, and deploying security patches is fundamental. Known vulnerabilities represent the easiest attack vectors and should be addressed with urgency.
Segmentation and Access Control: Rather than allowing broad database access, organizations should implement least-privilege access controls where systems and people only access data they specifically need. This limits damage if any individual access is compromised.
Monitoring and Detection: Organizations should deploy security monitoring that identifies unusual access patterns, bulk data extraction, or unexpected system behavior. Detection doesn't prevent breaches, but it dramatically reduces the volume of data an attacker can steal before being stopped.
Incident Response Planning: Organizations should develop and regularly test incident response plans before breaches occur. Knowing exactly who does what during a crisis reduces response time and minimizes errors.
Security Culture: Beyond technical controls, organizations benefit from building security-aware cultures where employees understand threats, report suspicious activities, and follow security practices as part of normal operations.
Third-Party Risk Management: With many breaches originating from compromised third-party vendors and integrations, organizations should regularly audit third-party security postures and maintain strict controls over what integrations access.
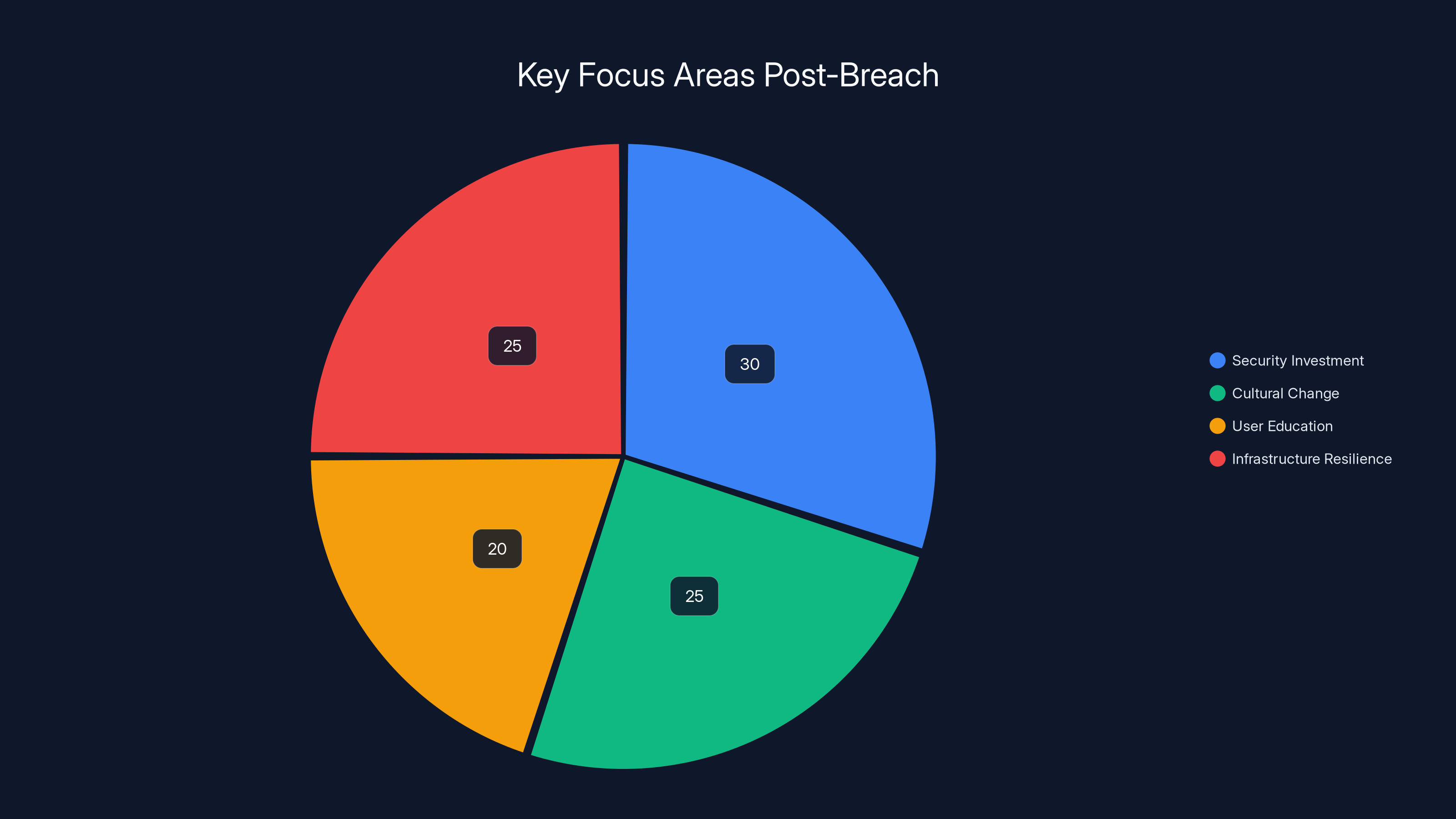
Estimated data distribution shows a balanced focus on security investment, cultural change, user education, and infrastructure resilience post-breach.
The Bigger Picture: Digital Trust and the Future of Media
This breach occurs against a backdrop of declining digital trust. Readers increasingly understand that their data is exposed, valuable, and potentially at risk. Each breach reinforces this understanding and makes building audience trust progressively harder.
For media organizations specifically, this matters profoundly. Media companies depend on reader trust. When readers lose confidence that their information is protected, they're more likely to view paywalls skeptically, resist newsletters, and abandon account creation. The breach creates friction in the reader relationship.
Long-term, this trend has implications for media business models. Subscription revenue depends on readers willing to create accounts and provide payment information. Personalization depends on readers willing to provide preferences and behavioral data. Analytics depend on readers accepting tracking and data collection. When breaches erode this trust, media companies lose valuable business capabilities.
The competitive implications are interesting too. In the Condé Nast case, Ars Technica's architectural independence provided competitive advantage—not from a revenue perspective, but from a security and trust perspective. Readers can be confident their Ars data wasn't compromised. This confidence has value.
Practical Security Actions for Users
For anyone concerned about the breach or their security generally, concrete actions reduce risk:
Immediate Actions:
- Change your Condé Nast property passwords to unique, strong passwords
- Check your email address on haveibeenpwned.com to identify other breaches you may not have known about
- Review account activity on compromised sites to identify any suspicious access
- Enable two-factor authentication on critical accounts if available
- Monitor credit reports through annualcreditreport.com for suspicious activity
Ongoing Practices:
- Use password managers to generate and maintain unique passwords for each service
- Review account settings regularly to identify unauthorized changes
- Monitor financial accounts for suspicious charges
- Be cautious with unsolicited emails, phone calls, or messages claiming to be from organizations you use
- Consider credit monitoring services if you're concerned about identity theft risk
- Review privacy settings on accounts to minimize data collection where possible
- Keep software and operating systems updated to minimize vulnerability exposure
Philosophical Approaches:
- Assume any service you use could be breached and operate accordingly
- Minimize the data you provide to services, sharing only what's necessary
- Recognize that free services often monetize user data and carefully consider whether that trade-off works for you
- Stay informed about major breaches that could affect you
- Understand that perfect security doesn't exist, but risk reduction is achievable
The Hacker's Perspective: Motivation and Morality
Understanding why attackers breach organizations matters for prevention.
In this case, Lovely's stated motivation was frustration with Condé Nast's security negligence. Whether or not this was genuine, it's a motivation that resonates in some segments of the security community. The narrative of "I tried to help, they ignored me, so I exposed them" creates a certain moral framework that some find compelling.
However, the suspected truth—that Lovely was a cybercriminal using social engineering on security researchers—reveals a more cynical reality. Attackers increasingly adopt the language and framing of security professionals because they understand it creates sympathy and complicates response efforts. It's a form of social engineering targeting the security community itself.
This dynamic matters because it shows how modern breaches aren't simply technical problems. They're also psychological, involving narrative construction, credibility management, and understanding how audiences react to different framings of the same events.
Cybercriminal motivation generally boils down to financial benefit: extracting value from breaches through extortion, selling data, or using compromised accounts for fraud. The "security researcher helping vulnerable users" framing is a cover story that makes the attacker appear sympathetic while negotiating for payment or establishing a relationship that could lead to payment later.
Industry Response and Standards
Following major breaches, the affected industry often reevaluates standards and practices.
For media organizations, this breach should prompt conversations about:
Security Budget Allocation: What percentage of technology budgets should go to security versus new features? Breaches tend to shift this allocation substantially, but often only temporarily.
Third-Party Vendor Audits: How rigorously do organizations evaluate the security practices of vendors and integrations? Weak vendor security is a common breach vector.
Disclosure Practices: How quickly and thoroughly should organizations communicate with affected users? This breach's minimal communication likely damaged Condé Nast's reputation beyond the breach itself.
Infrastructure Consolidation: Should media companies run shared infrastructure for cost efficiency or maintain separation for security resilience? The Ars Technica example shows real trade-offs exist.
Regulatory Relationship: How should organizations work with regulators during breach investigations? Proactive communication and cooperation can improve outcomes versus defensive, minimal engagement.

Conclusion: Lessons and Moving Forward
The Condé Nast breach of December 2025 represents a watershed moment for media industry security. While 2.3 million exposed records is significant, the implications extend far beyond the immediate users affected.
The breach exposes fundamental tensions in modern digital security. Organizations must balance innovation speed with security investment. They must balance infrastructure consolidation for efficiency with separation for resilience. They must balance transparency in communication with legal caution during crisis. None of these trade-offs have perfect answers, but the consequences of getting them wrong are substantial.
For users, the breach reinforces a critical reality: security is personal. Organizations will be breached. Data will be exposed. The question isn't whether it will happen but whether you're prepared when it does. That preparation means unique passwords, security awareness, credit monitoring, and acceptance that digital exposure is a feature of modern life, not a bug.
For the security community, the breach highlights how narratives matter as much as technical exploitation. The most sophisticated attackers understand they're not just hacking computers—they're hacking the social systems, trust networks, and communication patterns that surround organizations. As Lovely's alleged deception of security researchers demonstrates, defenders must be as skeptical of sympathetic-seeming disclosures as they are of obvious attacks.
For Condé Nast and similar organizations, the path forward requires sustained commitment to security as a business priority, not a cost center. It requires cultural change where security concerns slow down feature development rather than being overridden by schedule pressure. It requires investment in talent, tools, and processes. Most fundamentally, it requires recognizing that in an era of persistent breaches, security becomes competitive advantage. Organizations that protect user data better than competitors build greater trust and stronger customer relationships.
The Condé Nast breach is one incident among thousands that will occur in 2025 and beyond. Yet it offers useful lessons for anyone interested in how digital security actually works, why organizations often fail at it, and what it takes to build systems that better protect the users who depend on them.
FAQ
What exactly was exposed in the Condé Nast breach?
The Condé Nast breach exposed demographic information from approximately 2.3 million WIRED users, including names, email addresses, physical mailing addresses, and phone numbers. Importantly, passwords were NOT included in the exposed data, which limits the immediate risk of account takeovers. The hacker also claimed to possess 40 million additional records from other Condé Nast properties like Vogue, The New Yorker, and Vanity Fair, though these hadn't been publicly released at the time the initial breach was disclosed.
Was Ars Technica affected by the Condé Nast breach?
No, Ars Technica was completely unaffected by the breach. Despite being owned by Condé Nast, Ars Technica operates on its own independent technology infrastructure rather than using shared corporate systems. This architectural separation meant that when Condé Nast's shared databases were compromised, Ars Technica's user data remained secure. Ars readers received no breach notifications and don't need to take security action related to this incident.
How did the hacker claim to get access to Condé Nast's systems?
The hacker, operating under the alias "Lovely," claimed they discovered security vulnerabilities in Condé Nast's infrastructure and attempted to report them to the company for remediation. According to the story, Lovely spent a month trying to get Condé Nast to patch the vulnerabilities before ultimately deciding to leak the data publicly. However, cybersecurity researchers have questioned whether this narrative was truthful, suggesting Lovely may have been dishonest about their initial intentions and was actually operating as a cybercriminal rather than a security researcher attempting responsible disclosure.
What is the risk level for people whose data was exposed?
The risk level varies depending on individual circumstances. Since passwords weren't exposed, direct account takeovers are less likely. However, attackers can use the exposed information for phishing attacks, social engineering, and targeted fraud. Anyone concerned should monitor credit reports, watch for phishing emails, ensure they use unique passwords across services, and enable two-factor authentication on critical accounts. The risk increases if you reuse passwords across multiple sites or if you're a high-value fraud target.
Why did Condé Nast take so long to respond or communicate about the breach?
Condé Nast's response was notably silent, with no major public statements or immediate user notifications. This could reflect several factors: genuine confusion about the breach's scope and legitimacy, legal advice from attorneys to avoid statements during investigation, or organizational dysfunction during crisis situations. Large organizations often have complex decision-making structures that slow crisis response. However, the delayed communication likely damaged trust and reputation beyond the breach itself.
What should someone do if their information was exposed?
Immediate actions include: changing your password to a unique, strong one; checking haveibeenpwned.com to see if you're in other breaches; reviewing account activity for suspicious access; enabling two-factor authentication if available; and monitoring credit reports through annualcreditreport.com. Ongoing practices include using a password manager to maintain unique passwords, monitoring financial accounts regularly, being cautious with unsolicited messages, and staying informed about breaches that could affect you.
Could other media companies experience similar breaches?
Absolutely. The media industry faces specific security challenges: large user databases containing valuable personal information, technology teams that may be smaller than those at major tech companies, and pressure to ship features quickly rather than invest heavily in security infrastructure. Any media organization with shared infrastructure, unpatched vulnerabilities, or limited security resources faces similar risks. The Condé Nast breach serves as a cautionary example for the entire industry.
Is the hacker likely to release the other 40 million records they claim to have?
Lovely claimed to possess 40 million additional records and threatened to release them over the following weeks. Whether those records actually exist and whether they'll be released remains uncertain. Even if Lovely was dishonest about their initial motivation, the threat pattern suggests they're using the data as leverage. Whether that resolves through payment, law enforcement intervention, or eventual release is unpredictable, making it a source of ongoing concern for users of other Condé Nast properties.
How does infrastructure independence actually improve security?
Ars Technica's use of independent infrastructure exemplifies infrastructure independence. When all of an organization's properties share the same database, user system, and infrastructure, a single vulnerability or breach compromises everything simultaneously. By maintaining separate infrastructure, Ars Technica ensured that a compromise elsewhere in the organization couldn't cascade to their systems. This principle applies broadly: separation of systems limits damage scope, even if it costs more to maintain multiple systems.

Recommended Security Reading and Resources
For readers interested in deeper dives into data security, breach prevention, and personal security practices, several resources offer valuable perspectives. Industry publications regularly cover security incidents and analysis. The Electronic Frontier Foundation provides digital privacy guidance. Organizations like the SANS Institute offer security certifications and research. Personal security guides from established cybersecurity firms explain practical protection strategies.
Understanding your own security posture—what systems you use, what data they possess, and how well that data is protected—is the foundation for effective personal risk management in the modern digital landscape.
Key Takeaways
- Condé Nast suffered a major breach affecting 2.3 million WIRED users with demographic data exposed, plus claims of 40 million additional records from other properties
- The hacker's claims about attempting responsible disclosure were questioned by security researchers, suggesting cybercriminal motivation rather than security researcher ethics
- Ars Technica's independent technology infrastructure protected its readers, demonstrating the security value of infrastructure separation despite higher operational costs
- Organizations must balance security investment with feature development, a trade-off that Condé Nast apparently deprioritized to its detriment
- Users can reduce breach impact through unique passwords, two-factor authentication, credit monitoring, and heightened awareness of phishing and social engineering attempts
Related Articles
- Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data [2025]
- Condé Nast Data Breach: 40 Million Records Exposed [2025]
- 1Password Deal: Save 50% on Premium Password Manager [2025]
- 1Password 50% Off Holiday Deal: Complete Guide to Password Manager Savings [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
![Condé Nast Data Breach 2025: What Happened and Why It Matters [2025]](https://tryrunable.com/blog/cond-nast-data-breach-2025-what-happened-and-why-it-matters-/image-1-1767121666720.jpg)



