The Worst Hacks of 2025: A Cybersecurity Wake-Up Call
2025 was the year cybercriminals stopped knocking politely and started kicking down doors. The breach headlines kept coming, each one bigger than the last. We're not talking about sketchy websites getting hacked by teenagers anymore. These were Fortune 500 companies, prestigious universities, and critical infrastructure getting compromised by sophisticated criminal networks and state-sponsored attackers.
Here's the uncomfortable truth: security became a luxury many organizations couldn't afford, even when they tried. The attack surface expanded. Third-party integrations became the weak link. Phishing emails got smarter. And the bad guys? They got bolder, more patient, and infinitely better at finding the cracks in our digital armor.
This wasn't just a bad year in cybersecurity. It was a turning point. The incidents of 2025 exposed a systemic problem that's been brewing for years: we're building interconnected systems without building interconnected security. We're trusting third parties without auditing third parties. We're assuming enterprise vendors are invulnerable when they're actually just big targets.
What makes 2025 different from previous years is the scale and sophistication combined with the targeting of essential infrastructure. It's not just about stealing credit card numbers anymore. Attackers went after health insurance records, university systems, financial institutions, and supply chain partners. They weaponized data through extortion campaigns. They shut down operations, cost companies millions in recovery, and exposed the personal information of tens of millions of people.
In this guide, we're breaking down the biggest breaches, hacking campaigns, and coordinated attacks from 2025. More importantly, we're explaining what actually happened, why it matters for your organization, and what you can do about it. Because here's the reality: the worst hack of 2025 might be the one that targets your company next year.
TL; DR
- Salesforce supply chain attacks: Criminals breached third-party integrators, exposing data from Google, Cloudflare, Cisco, LinkedIn, and 22.65 million Aflac customers. According to CPO Magazine, this breach affected over 200 organizations.
- Clop ransomware spree: A single vulnerability in Oracle E-Business exposed hospitals, universities, and media companies, including University of Pennsylvania, Harvard, and Princeton. As reported by CPO Magazine, this vulnerability was exploited extensively.
- University breach epidemic: At least 7 major universities hit in 2025, with some breaches exposing decades-old student and alumni data. SecurityWeek reported that the University of Phoenix breach alone affected 3.5 million people.
- Insurance industry targeted: Criminal networks systematically attacked insurance companies, stealing health records, SSNs, and financial information. Cybersecurity Ventures highlighted the financial impact of such breaches.
- Third-party integrations became the weak link: Attackers stopped targeting major vendors directly, instead hitting their contractors and partners. Shopify emphasized the vulnerabilities in retail cybersecurity.
- Bottom Line: 2025 proved that security is only as strong as your weakest integration, and criminals know exactly where to find it.
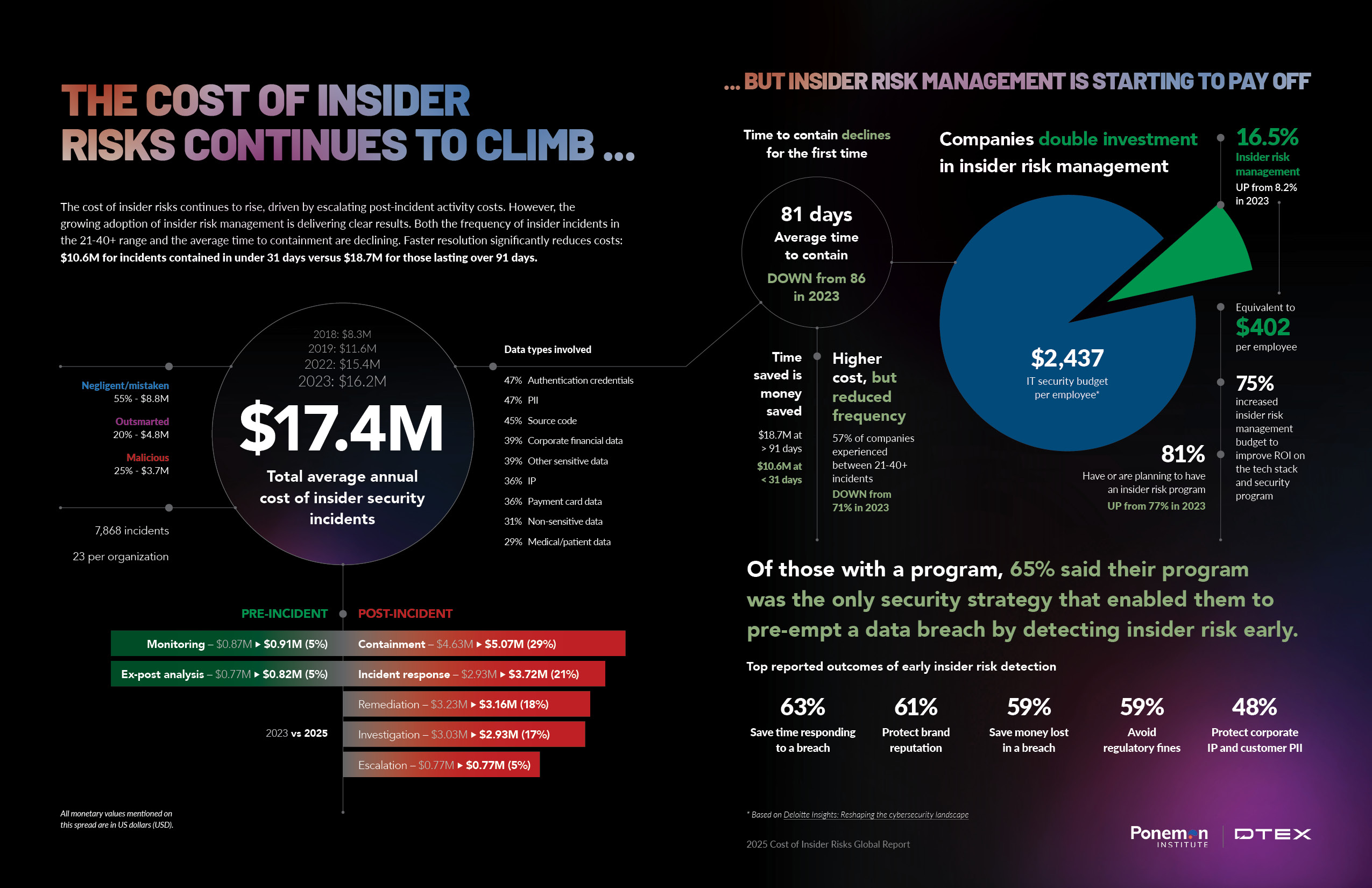
The Salesforce ecosystem breach affected multiple major corporations, Google Workspace, and TransUnion, highlighting the extensive reach of third-party vulnerabilities. Estimated data.
The Salesforce Ecosystem Collapse: When Third Parties Become Entry Points
Here's something that kept security teams awake at night in 2025: the bad guys figured out that hacking Salesforce directly was hard. So they didn't. Instead, they targeted Salesforce contractors and integrations, and it worked perfectly.
The campaign started with breaches of Gainsight and Salesloft, two companies that build on top of Salesforce's platform. Through these integrations, attackers gained access to customer data across an absolutely staggering number of major corporations. We're talking Cloudflare, Docusign, Verizon, Cisco, LinkedIn, Bugcrowd, Proofpoint, GitLab, SonicWall, Adidas, Louis Vuitton, and Chanel. This wasn't a breach of one company. It was a breach of an entire ecosystem.
The intelligence team at Google documented this spree in August, revealing that Google Workspace data had been compromised as part of the Salesloft Drift breach. For Google, that's significant. Alphabet's security reputation is spotless, but even their data wasn't immune to third-party compromise.
What made this campaign so devastating was the scale and the targeting. The attackers were clearly sophisticated enough to understand the Salesforce ecosystem and identify which integrations would give them access to the most valuable data. They weren't just stealing customer lists. They were stealing internal sales data, customer information, and strategic details that companies guard fiercely.
The Trans Union Connection and Mass Exposure
The Salesforce integration breach had a ripple effect that reached the credit reporting industry. Trans Union, one of the three major credit bureaus, suffered a breach apparently connected to the same campaign. This single incident exposed the information of 4.4 million people, including names and Social Security numbers.
Think about what that means. A breach in a third-party Salesforce contractor somehow cascaded to expose millions of people's credit information. It's a reminder that data flows through systems in ways we don't fully understand or control.
Meet Scattered Lapsus$ Hunters
The attackers behind this campaign operated under the name Scattered Lapsus
These attackers set up a data leak site where they previewed stolen troves of data and conducted digital extortion. This is the new playbook: steal data, announce the theft publicly to embarrass the victim, then demand millions in ransom to delete it instead of publishing it. Companies face an impossible choice: pay the extortionists or have their data exposed publicly.
The Real Problem: Third-Party Trust Without Third-Party Verification
What made this campaign possible was a fundamental security flaw in how companies approach integrations. When Salesforce customers plug in a third-party app like Salesloft or Gainsight, they're essentially giving that app access to sensitive business data. But most companies don't conduct rigorous security audits of third-party integrations. They assume if a tool is popular and reputable, it must be secure.
Not anymore. The 2025 Salesforce breaches proved that popular tools can be compromised, and when they are, every company using them becomes a victim.
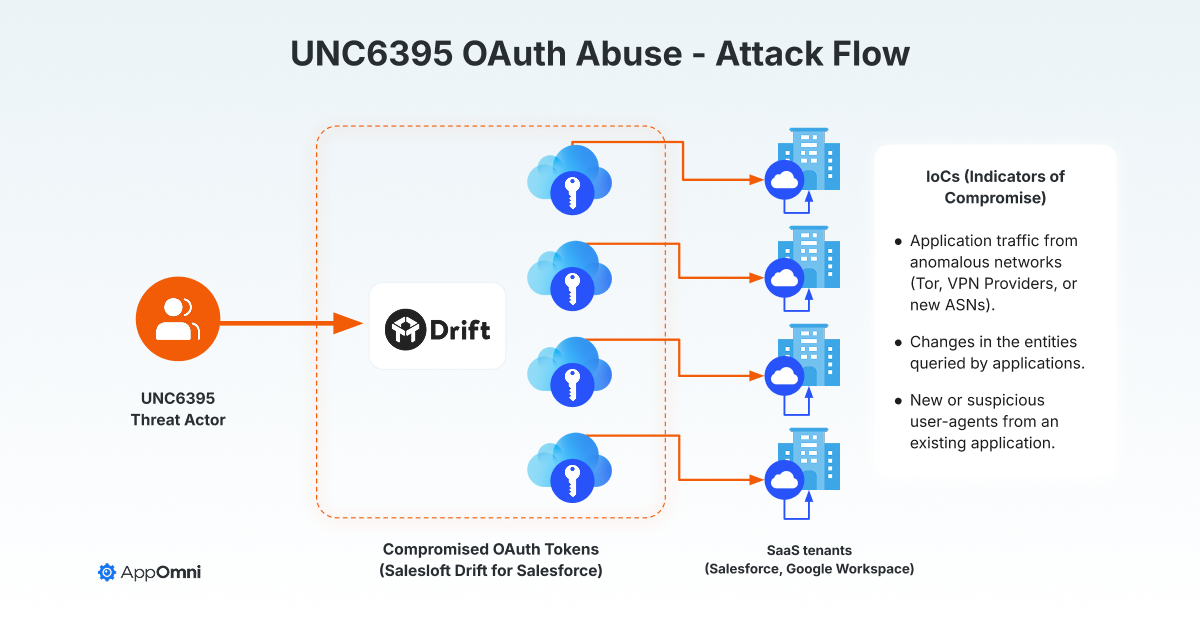
The most significant breaches of 2025 exposed millions of records, with Salesforce integration attacks affecting over 100 companies. Estimated data based on reported incidents.
The Oracle E-Business Vulnerability: A Ransomware Group's Gold Rush
Clop is a ransomware group that operates like a criminal enterprise with a business model. They find vulnerabilities, exploit them at massive scale, steal data, and then conduct extortion campaigns. In 2025, they did it again, and the impact was catastrophic.
The target was Oracle E-Business Suite, an internal management platform used by thousands of organizations worldwide. Oracle rushed to patch the vulnerability at the beginning of October, but Clop had been exploiting it for weeks before the patch was available. That window was enough.
What Clop Stole
During the exploitation spree, Clop gained access to employee data, including personal information of company executives. They didn't just steal the data and disappear. They weaponized it. The group sent threatening emails and communications to senior executives at victim companies, demanding millions of dollars in ransom to delete the stolen data instead of publishing it.
This is extortion in its modern form. The threat isn't physical violence. It's data exposure, public embarrassment, regulatory scrutiny, and damaged reputation.
Hospitals and Healthcare Organizations Hit Hard
One of the most concerning aspects of Clop's Oracle E-Business campaign was the targeting of healthcare organizations. Hospitals and health systems that were already stretched thin during the year faced operational disruptions from ransomware attacks. Patient data was compromised. Services were interrupted. In healthcare, that translates directly to real harm.
The Washington Post, Media, and Universities
Media companies were also on Clop's victim list. The Washington Post disclosed the breach. Universities across the country were hit, including some of the most prestigious institutions in the country. For universities, the breach was particularly significant because they house decades of historical data on students, alumni, and donors.
University Breaches: A Systemic Vulnerability in Higher Education
2025 was brutally bad for universities. At least seven major U.S. universities suffered significant breaches, and the targeting pattern reveals that attackers had systematic strategies for compromising academic institutions.
University of Pennsylvania: The Phishing Campaign That Started It All
The University of Pennsylvania disclosed a breach at the beginning of November that had occurred at the end of October. The breach was triggered by a phishing attack, not a sophisticated zero-day exploit. Someone sent emails to students and alumni, and those emails worked.
What's interesting about the Penn attack is the social engineering angle. The phishing emails described the university as "woke" and claimed that Penn prioritized "legacies, donors and unqualified affirmative action admits." The attackers used controversial cultural and political topics to create emails that would provoke a response and get clicked.
But here's the twist that security researchers found interesting: despite the cultural messaging, the attack appeared to be financially motivated. The hacker gained access to personal data spanning years or decades, internal university documents, and financial information. This was a data theft operation using social engineering as the delivery mechanism.
Harvard's Phone-Based Phishing Attack
Harvard's breach came in November and followed a different vector: phone-based phishing. An attacker conducted a "phone-based phishing attack" that compromised the Harvard Alumni Affairs and Development office systems.
Phone-based phishing is harder to defend against than email because it involves human voice, which creates social trust that email can't replicate. The breach exposed personal information of alumni, their partners, donors, parents of students, current students, faculty, and staff. The data included email addresses, phone numbers, physical addresses, event attendance records, donation information, and fundraising details.
For universities, donor information is as valuable as customer data is for retailers. When fundraising records are exposed, it creates a direct channel for future phishing and social engineering attacks.
Princeton, NYU, Columbia, and University of Phoenix: A Pattern Emerges
Princeton University suffered a similar breach in November with a more limited scope of affected data. But the pattern was clear: attackers had developed specialized techniques for compromising university systems, and they were deploying those techniques systematically.
New York University was hit in March. Columbia University faced a breach in June. The University of Phoenix had the worst outcome, with a breach in August that exposed data for close to 3.5 million people.
When you look at the timeline, it's not random. These are coordinated, strategic attacks against educational institutions. The attackers identified universities as targets, developed exploit chains that worked, and then deployed them across multiple institutions.
The Root Cause: Legacy Systems and Limited Security Budgets
Why are universities being targeted so heavily? Several factors converge:
- Legacy systems: Universities often run older technology stacks that haven't been updated in years. Security patches lag.
- Limited budgets: Higher education IT budgets are often stretched thin. Security is an afterthought.
- Open environments: Universities operate as open networks with significant guest access and student connectivity.
- Valuable data: Student records, alumni networks, and donor information are worth money.
- Limited security culture: Universities aren't necessarily built around security-first operations like banks or defense contractors.
Attackers recognized these vulnerabilities and built playbooks specifically for compromising academic institutions.
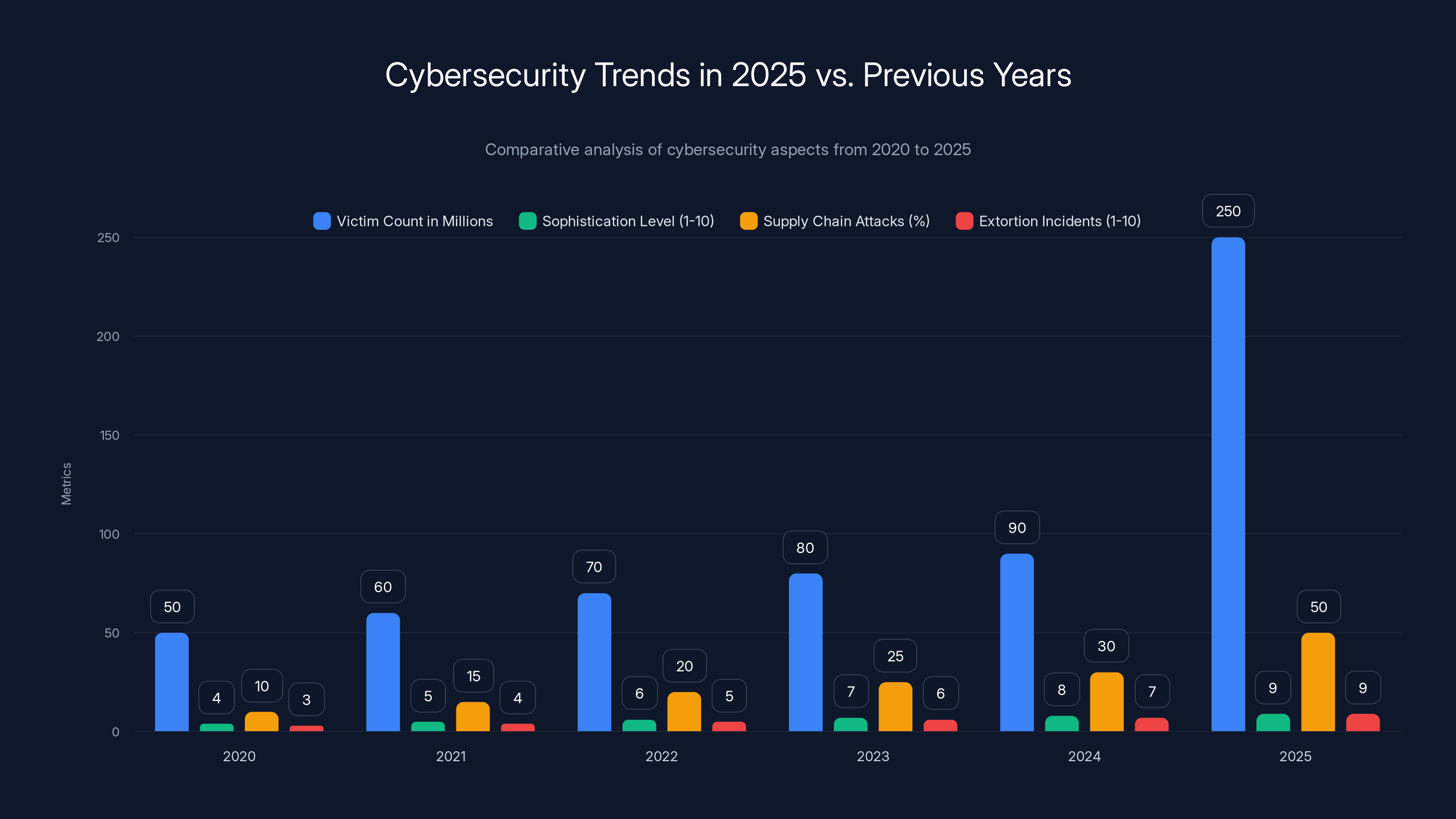
The year 2025 marked a significant increase in cybersecurity breaches, with a dramatic rise in victim count and sophistication of attacks. Estimated data based on trends.
The Aflac Insurance Breach: 22.65 Million People Exposed
Aflac disclosed a data breach in June and initially said it didn't know how many victims were affected. On December 19, 2025, the company dropped the real number: 22.65 million people. This was one of the largest breaches in U.S. history by victim count.
What Data Was Stolen
The stolen data included names, contact information, dates of birth, Social Security numbers, tax ID numbers, health information, medical record numbers, dates of service with medical providers, and health insurance ID numbers.
Let's be clear about what this means. For 22.65 million people, a sophisticated criminal now has the information needed to commit identity theft, file fraudulent tax returns, obtain medical services under false pretenses, or conduct social engineering attacks. This isn't just a privacy violation. It's a direct security threat to tens of millions of Americans.
The Insurance Industry Was Systematically Targeted
Legal notifications under state data breach laws in Texas, Iowa, and elsewhere revealed that the unauthorized actor may be affiliated with known cyber-criminal organizations. Federal law enforcement and third-party cybersecurity experts indicated that the group may have been targeting the insurance industry at large.
This aligns with a broader hacking spree carried out in spring 2025 by the Scattered Spider criminal hacking group. Insurance companies became high-priority targets because they hold extremely valuable data: health records, financial information, and identity details for millions of customers.
Why Insurance Companies Are Prime Targets
Insurance firms hold several elements that make them attractive to criminals:
- Health data: Stolen health records can be sold on the dark web for hundreds of dollars per record
- Financial data: Insurance companies track payments, claims, and customer financial profiles
- Identity information: SSNs, dates of birth, and addresses enable identity theft
- Legacy systems: Many insurance companies run older technology with historical security debt
- Regulatory liability: Insurance companies are liable for regulatory fines, making them more likely to pay ransom

Scattered Spider: The Criminal Group Behind the Chaos
Scattered Spider emerged as one of the most active and capable criminal hacking groups in 2025. They were behind the insurance industry spree that exposed millions of customers at companies like Aflac. But Scattered Spider was only one piece of a larger puzzle.
How Scattered Spider Operates
Unlike some hacking groups that focus on a single attack vector, Scattered Spider uses a diversified approach. They conduct phishing campaigns, exploit vulnerabilities, compromise third parties, and use social engineering to gain initial access. Once inside a network, they move laterally, escalate privileges, and steal whatever data is most valuable.
What makes them particularly dangerous is their patience and sophistication. They're not smash-and-grab operators. They establish persistent access, maintain it for extended periods, and exfiltrate data methodically.
The Connection to Lapsus$ and Shiny Hunters
Scattered Spider's tactics and tools show overlap with other known criminal groups. This suggests either shared training, shared tools, or actual collaboration between groups. The emergence of "Scattered Lapsus$ Hunters" as a moniker indicates that criminal networks are collaborating or at least sharing techniques.
This is a shift in the threat landscape. Historically, criminal hacking groups were competitive. In 2025, there's evidence they're becoming collaborative, sharing exploits, techniques, and infrastructure.

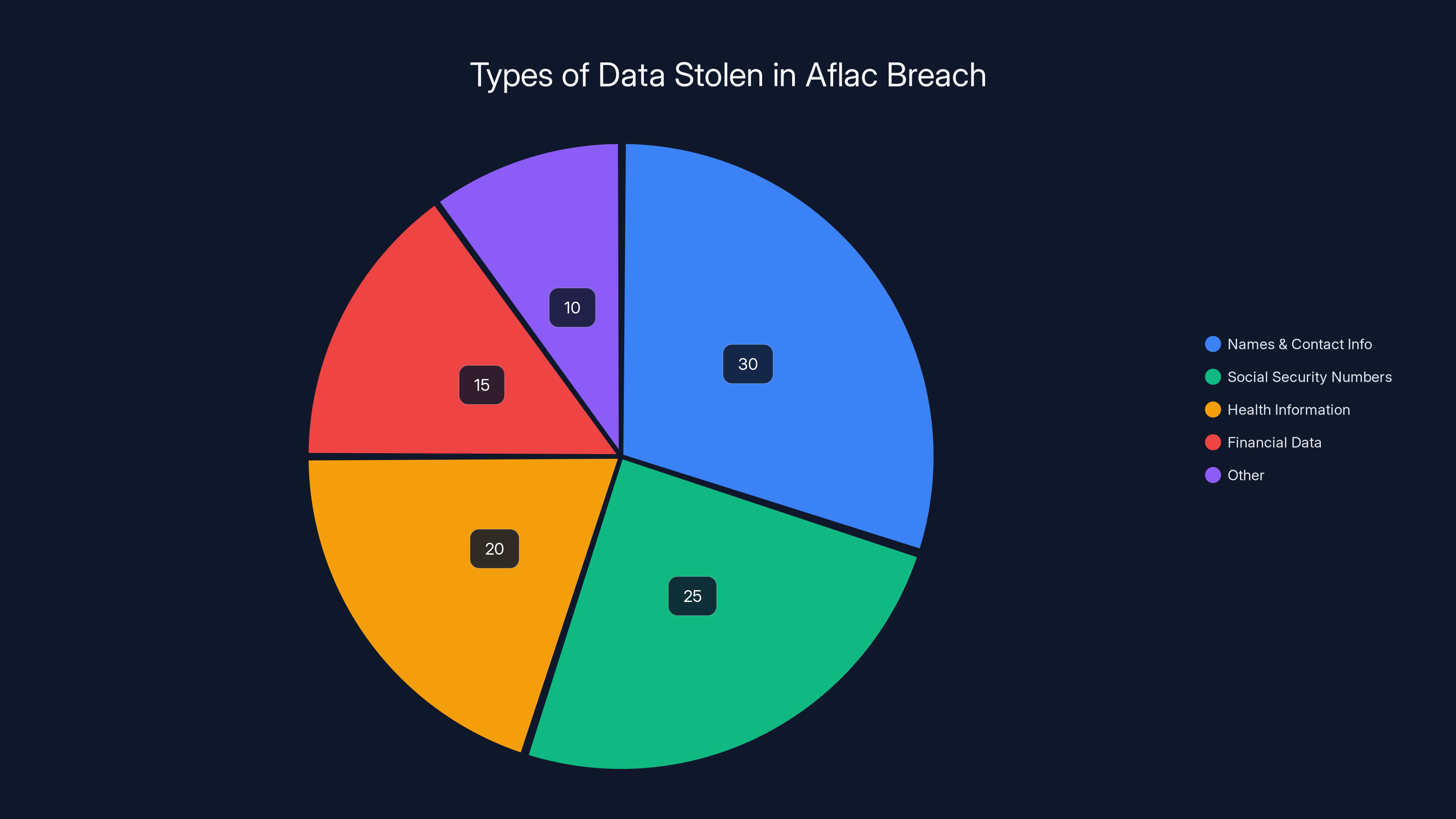
Estimated distribution of data types exposed in the Aflac breach, highlighting the variety of sensitive information at risk. Estimated data.
The Mixpanel Breach: SMS Phishing as an Attack Vector
Mixpanel, a web app analytics company, announced in late November that it had discovered a "security incident" on November 8. The breach resulted from a smishing campaign, which is SMS (text message) phishing.
Why SMS Phishing Works Better Than Email
Email has defenses. Spam filters, authentication protocols like SPF and DKIM, employee training on phishing emails. But SMS phishing bypasses many of these defenses because text messages feel more personal and urgent. A text from what appears to be your bank asking you to verify your credentials has a higher success rate than an email.
Mixpanel's breach demonstrates that criminals are diversifying their attack vectors. If email phishing gets blocked, they try SMS. If SMS fails, they try social engineering over the phone.
The Scale of the Incident
Mixpanel said it had notified all affected customers but didn't disclose the total number of victims. The company detected the smishing campaign, which suggests attackers sent fraudulent text messages to Mixpanel employees or customers, tricking them into visiting a fake login page or installing malware.
The incident highlighted a vulnerability in the analytics company's security posture and forced the company to conduct forensic investigations and breach notifications.

The Broader Pattern: Third Parties as Critical Infrastructure Vulnerabilities
When you zoom out from individual breaches and look at 2025 as a whole, a clear pattern emerges: attackers stopped trying to breach major vendors directly. Instead, they targeted third-party integrations, contractors, and supply chain partners.
Why This Strategy Works
Third parties are softer targets because:
- Smaller security budgets: A Salesforce contractor might have a fraction of Salesforce's security investment
- Fewer eyes: Smaller organizations have smaller security teams
- Trust advantage: When you're a trusted contractor, you get more access with fewer verification steps
- Leverage: Compromising a contractor gives attackers access to all the contractor's customers
The Supply Chain Attack Multiplier
A single breach of a popular SaaS integration reaches dozens or hundreds of downstream customers. The Salesforce integration breaches affected over 100 known victims. A single vulnerability in Oracle E-Business exposed hospitals, universities, and media companies.
This creates a mathematical advantage for attackers: compromise one contractor or platform, and you get access to dozens of downstream organizations.

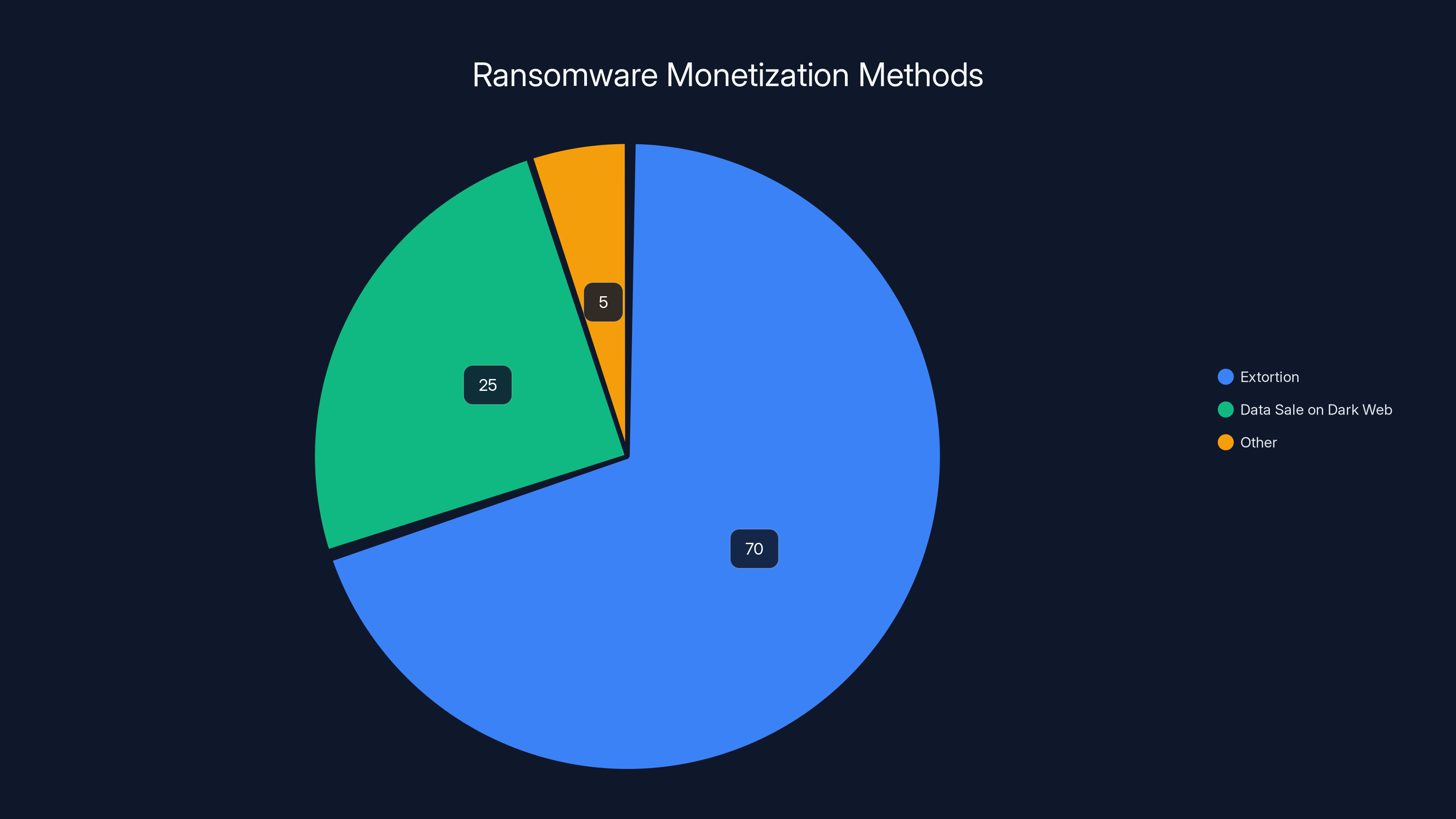
Extortion is the dominant monetization strategy in ransomware attacks, with an estimated 70% of attackers opting for this method due to its higher profitability. (Estimated data)
Ransomware as a Service: The Industrialization of Cybercrime
The 2025 breaches weren't all random attacks. Many were conducted by organized criminal networks operating ransomware-as-a-service (RaaS) platforms. This is cybercrime industrialization.
How RaaS Operates
Ransomware-as-a-service works like legitimate software-as-a-service (SaaS). A criminal group develops ransomware, sets up infrastructure, and then "sells" access to other criminals. The service provider takes a percentage of each ransom paid, incentivizing them to continually improve their tools and tactics.
Clop operates a RaaS model. So do several other major groups. This means attackers don't need to develop their own malware. They can rent access to proven, battle-tested ransomware and focus on the initial compromise.
The Economics of Extortion
When attackers steal data, they have two monetization options: sell it on the dark web or conduct extortion. Extortion is more profitable. Companies will often pay millions to prevent their sensitive data from being exposed publicly.
The extortion model creates a perverse incentive: attackers are incentivized to target the largest, most profitable organizations, not the most vulnerable ones. A hospital with critical patient data in a ransomware attack might pay $10 million to recover. A small business might pay nothing because they don't have the budget.

The Phishing Evolution: Social Engineering Meets Cultural Warfare
Phishing has been around for decades, but 2025 showed that attackers are getting better at crafting emails and messages that actually work.
Culturally Targeted Phishing
The University of Pennsylvania attack is a case study in sophisticated social engineering. Rather than generic phishing emails about password resets or account verification, the attackers crafted emails around controversial cultural and political topics. This increased the likelihood that recipients would open the email, click links, or respond with information.
It's a reminder that technical security tools don't defend against social engineering. The best defense is user awareness training and a culture of skepticism about unexpected emails and messages.
Multi-Channel Attack Strategies
In 2025, attackers didn't rely on a single vector. They combined email, SMS, phone calls, and social media. This multi-channel approach increases the likelihood of success because defenders can't protect every channel equally.

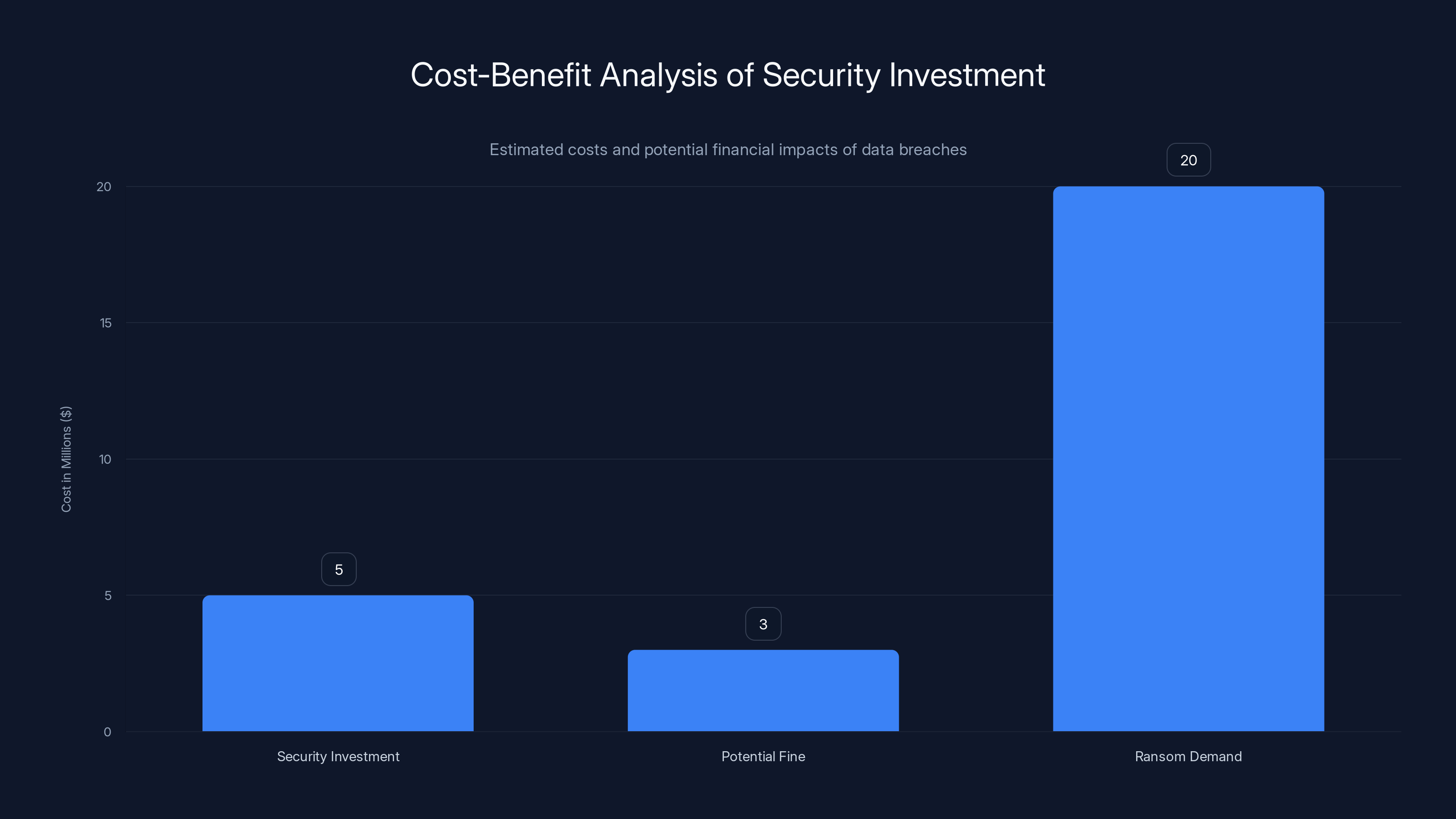
Estimated data shows that while security investment costs
The Human Element: Why Security Awareness Failed
Here's the uncomfortable truth about 2025's breaches: many of them succeeded because someone clicked a link, opened an attachment, or verified credentials on a fake website. Technology is part of the solution, but it's not the complete solution.
The Security Awareness Training Gap
Companies invest in security awareness training, but the effectiveness is limited. Attackers are constantly evolving their social engineering tactics. A training module from 2024 might not prepare employees for the attacks they'll face in 2026.
The Cost of Complacency
When employees see dozens of phishing emails daily and most of them are caught by filters, complacency sets in. The one phishing email that gets through, the one that uses current events or cultural moments, the one that appears to come from a trusted partner—that's the one that works.

The Regulatory Response: Not Fast Enough
As breaches escalated through 2025, regulators were playing catch-up. Data breach notification laws exist in most states, but they're reactive, not preventative. Companies notify people after the fact, but there's little incentive to prevent breaches in the first place.
The Cost-Benefit Analysis
For many companies, the math doesn't add up to invest heavily in security. A company might spend $5 million per year on comprehensive security infrastructure. If the probability of a breach is low, and the potential fine for a breach is a few million dollars, the expected cost of a breach might be less than the cost of prevention.
Ransom demands change this calculation. When attackers demand $20 million and the company has valuable data, the economics flip. Suddenly, security investment looks cheap compared to potential ransoms.

The Geopolitical Dimension: State-Sponsored Attacks
While 2025 saw plenty of financially motivated cybercrime, there's also evidence that state-sponsored attackers continued operations targeting U.S. organizations.
Why Nations Attack Corporations
Governments target corporations for intellectual property, competitive advantage, and strategic information. A foreign government might be interested in proprietary technology from defense contractors, financial institutions, or technology companies.
The Attribution Challenge
Attributing cyberattacks to state-sponsored actors is difficult and often uncertain. Intelligence agencies use techniques like malware signatures, infrastructure analysis, and timing patterns to attribute attacks, but the evidence is rarely public or conclusive.

2025 vs. Previous Years: What Changed
Cybersecurity incidents aren't new. Every year brings big breaches. But 2025 felt different in several ways:
Scale: Bigger Numbers
2025 saw some of the largest breaches by victim count in history. The Aflac breach alone affected 22.65 million people. When you add up all the breaches from 2025, the total number of exposed individuals is in the hundreds of millions.
Sophistication: Smarter Attacks
Attackers deployed more sophisticated social engineering tactics. They weaponized cultural moments and controversial topics to increase phishing success rates. They built collaborative networks sharing tools and techniques.
Strategy: Supply Chain Focus
The shift toward targeting third parties and integrations represents a strategic change. Attackers realized that major vendors were hardened targets, so they pivoted to the supply chain where security is often weaker.
Extortion: Business Model Maturation
Extortion became more systematic and professional in 2025. Criminal groups operate like legitimate businesses, with clear pricing, service level agreements, and even customer support.

What Companies Should Do Right Now
If you're responsible for security at an organization, 2025's breaches should serve as a wake-up call. Here's what to prioritize:
1. Inventory Third-Party Integrations
Create a complete inventory of every third-party app, tool, or integration connected to your systems. For each one, document what data the app can access and conduct a security assessment.
2. Implement Multi-Factor Authentication Everywhere
MFA is the single most effective defense against phishing and credential theft. If an employee's password is compromised, MFA prevents the attacker from using it to gain access. Implement MFA for email, VPN, and critical business systems.
3. Segment Your Network
Network segmentation means dividing your network into zones with restricted access between them. If an attacker compromises one segment, they can't easily move to others. This limits the damage from a breach.
4. Conduct Regular Security Audits
You can't defend what you don't know about. Conduct regular security assessments, vulnerability scans, and penetration tests. Find the weaknesses before attackers do.
5. Develop Incident Response Plans
When (not if) you're breached, having a plan matters. Develop incident response procedures, define roles and responsibilities, and practice the response regularly through tabletop exercises.
6. Invest in Security Awareness Training
Train employees to recognize phishing, social engineering, and suspicious activity. Make security part of your company culture, not an afterthought.
7. Monitor and Hunt for Threats
Don't just wait for alerts. Proactively hunt for signs of compromise in your logs and networks. Look for suspicious patterns, unusual file access, and lateral movement.

The Future of Cybersecurity: Trends From 2025
Based on the incidents of 2025, several trends are likely to continue and accelerate:
1. AI-Powered Attacks
Attackers are beginning to use AI to generate phishing emails, identify vulnerabilities, and automate attack workflows. As AI tools become more sophisticated and accessible, attackers will use them to scale their operations.
2. Ransomware as the Business Model
Ransom payments in 2025 exceeded billions of dollars. As long as ransom is profitable, attackers will continue deploying ransomware. The economics are simply too favorable for criminals.
3. Credential Stuffing and Account Takeover
With the number of breaches exposing credentials, attackers have vast databases of usernames and passwords. They use these to conduct credential stuffing attacks, attempting to access other services using stolen credentials.
4. Supply Chain Attacks Become Normalized
Attackers discovered that supply chain attacks are more effective than direct attacks. Expect more breaches of SaaS integrations, contractors, and third-party services in coming years.
5. Regulatory Pressure Increases
As breaches cost companies more money and individuals more harm, expect regulators to impose stricter requirements. Data protection laws will become more stringent, and breach fines will increase.

Learning From 2025: The Uncomfortable Truths
After reviewing the major breaches of 2025, several uncomfortable truths emerge:
Truth 1: Security Is a Low Priority Until It Isn't
Many companies don't invest adequately in security until after they've been breached. By then, it's too late. The cost of breach recovery far exceeds the cost of prevention.
Truth 2: Trust Is a Security Liability
We trust our vendors, our contractors, and our employees. That trust is exploited when attackers compromise trusted parties. Security requires constant verification and skepticism.
Truth 3: Humans Are the Weakest Link
Technology is important, but humans are where attacks succeed. Phishing works because people click. Social engineering works because people trust. The most sophisticated technical defenses can be bypassed by the right social engineering message.
Truth 4: Preparedness Isn't Optional
Companies that had incident response plans, regular security assessments, and strong detection capabilities recovered faster from 2025's breaches. Those that didn't faced months of remediation.
Truth 5: The Bad Guys Are Getting Better
Attackers in 2025 were more sophisticated, better resourced, and more professional than ever. They operate like legitimate businesses, collaborate across groups, and continuously improve their techniques. Defenders are falling behind.

The Bottom Line: 2025 Was Just the Beginning
2025's breaches set the stage for an even more challenging cybersecurity landscape in coming years. Attackers proved they could:
- Compromise third-party integrations and reach downstream customers
- Target essential services like healthcare and education
- Expose tens of millions of people's personal information
- Conduct sophisticated social engineering campaigns
- Operate industrial-scale criminal enterprises
- Demand and receive multi-million-dollar ransom payments
The response from organizations and regulators will determine whether 2026 brings improvement or escalation. If companies invest seriously in security, implement fundamental controls, and develop incident response capabilities, the breach rate could decline. If they continue treating security as an afterthought, expect the numbers to get worse.
The choice is yours, but 2025 made it abundantly clear: security isn't optional. It's foundational. And every organization, from universities to insurance companies to Fortune 500 enterprises, is a potential target.
FAQ
What were the most significant breaches of 2025?
The most significant breaches of 2025 were the Salesforce third-party integration attacks (affecting 100+ companies), the Oracle E-Business Suite vulnerability exploited by Clop ransomware (affecting hospitals and universities), the Aflac insurance breach (exposing 22.65 million people), and the series of university breaches affecting institutions like University of Pennsylvania, Harvard, Princeton, NYU, and Columbia. Each of these breaches exposed millions of records containing sensitive personal information, health data, and financial details.
Why were third-party integrations such a vulnerable target in 2025?
Third-party integrations became vulnerable because attackers recognized they were softer targets than major vendors. Contractors typically have smaller security budgets, fewer security staff, and often receive more lenient access permissions because of their trusted relationship with the primary vendor. A single compromise of a contractor like Salesloft or Gainsight reached dozens of downstream customers simultaneously. This supply chain attack strategy is highly efficient for attackers and difficult to defend against because organizations rarely audit the security of their third-party integrations thoroughly.
How did phishing attacks become more effective in 2025?
Phishing attacks became more effective through cultural and political targeting that created urgency and emotional responses. Rather than generic password reset requests, attackers crafted emails referencing controversial cultural topics (as seen in the University of Pennsylvania breach) that were more likely to be opened and clicked. Additionally, attackers diversified beyond email to SMS phishing (smishing), phone-based social engineering, and multi-channel campaigns that are harder to defend against with traditional email security tools.
What data did the major breaches expose, and what are the consequences?
The 2025 breaches exposed a comprehensive profile of personal information including names, addresses, dates of birth, Social Security numbers, health records, medical information, insurance details, financial information, and educational records spanning decades in some cases. The consequences include increased risk of identity theft, fraudulent tax filing, unauthorized medical services, targeted social engineering attacks, and regulatory fines for the breached companies. For individuals, the exposure of Social Security numbers combined with dates of birth and addresses creates immediate identity theft risk.
Why were hospitals and universities specifically targeted in 2025?
Hospitals and universities were specifically targeted because they operate with limited security budgets, run legacy systems, and hold extremely valuable data. For hospitals, patient records combined with health insurance information create high-value targets for criminals. For universities, decades-old records on students, alumni, and donors are valuable both for identity theft and for targeting sophisticated social engineering attacks. Additionally, these institutions often face pressure to pay ransom quickly because of operational disruption (hospitals can't provide patient care with systems down) and reputational damage (universities face alumni and donor backlash).
What is ransomware-as-a-service, and why is it dangerous?
Ransomware-as-a-service (RaaS) is a business model where criminal groups develop ransomware and infrastructure, then rent or sell access to other criminals. The RaaS provider takes a percentage of ransom payments, creating incentives to continuously improve tools and expand victim targeting. RaaS is dangerous because it lowers the technical barrier for criminals to conduct ransomware attacks. Instead of requiring sophisticated hacking skills, aspiring cybercriminals can rent proven, battle-tested ransomware and focus on the initial compromise. This has led to more frequent, more sophisticated ransomware attacks against larger targets.
How should organizations respond to the 2025 breach patterns?
Organizations should immediately prioritize: (1) auditing and securing third-party integrations, (2) implementing multi-factor authentication everywhere, (3) segmenting networks to limit breach damage, (4) conducting regular vulnerability assessments, (5) developing and testing incident response plans, (6) investing in security awareness training, and (7) establishing threat hunting capabilities to detect compromise early. The fundamental controls—MFA, network segmentation, and patch management—prevent the majority of breaches and should be the foundation of any security program.
What trends from 2025 are likely to continue in future years?
Trends likely to continue include: AI-powered attacks that automate and scale social engineering, ransomware remaining the primary attack model as ransom payments exceed billions annually, supply chain attacks becoming the preferred vector rather than direct attacks on major vendors, credential stuffing and account takeover leveraging breached databases, and increasing regulatory pressure resulting in stricter data protection laws and higher breach fines. Organizations should expect the threat landscape to become more sophisticated and professionalized with attackers operating like legitimate businesses.
The 2025 cybersecurity landscape showed us that breaches are no longer aberrations—they're part of the operational reality for most organizations. The question isn't whether you'll be targeted. It's whether you'll be prepared when you are.

Key Takeaways
- Salesforce third-party integrations were breached, exposing 100+ companies including Google, Cloudflare, and Cisco—the Aflac breach alone affected 22.65 million people
- Oracle E-Business vulnerability exploitation by Clop ransomware targeted hospitals, universities, and media companies systematically across multiple institutions
- Seven major universities (Penn, Harvard, Princeton, NYU, Columbia, University of Phoenix, and others) suffered phishing and credential-based attacks exposing decades of student, alumni, and donor data
- Attackers shifted strategy from direct vendor attacks to supply chain compromise, targeting third-party contractors and integrations as softer targets with downstream customer access
- Ransomware-as-a-service (RaaS) became industrialized, with criminal groups operating like legitimate businesses, collaborating across groups, and charging percentage-based fees for attack services
- Multi-factor authentication, network segmentation, and third-party security audits emerge as the three most critical defensive controls for 2026 and beyond
Related Articles
- Aflac Data Breach: 22.6 Million Exposed [2025]
- 9 Game-Changing Cybersecurity Startups to Watch in 2025
- France's La Poste DDoS Attack: What Happened & How to Protect Your Business [2025]
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
- Best Cybersecurity Journalism 2025: Stories That Defined the Year
- OpenAI's Head of Preparedness: Why AI Safety Matters Now [2025]
![The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]](https://tryrunable.com/blog/the-worst-hacks-of-2025-a-cybersecurity-wake-up-call-2025/image-1-1767011876453.jpg)



