WordPress Plugin Security Flaw: Complete Guide to Staying Safe [2025]
Your WordPress website feels safe. You've got a password manager, you're running security plugins, and you update things regularly. Then you hear about a flaw in a plugin you installed three months ago, and suddenly your stomach drops.
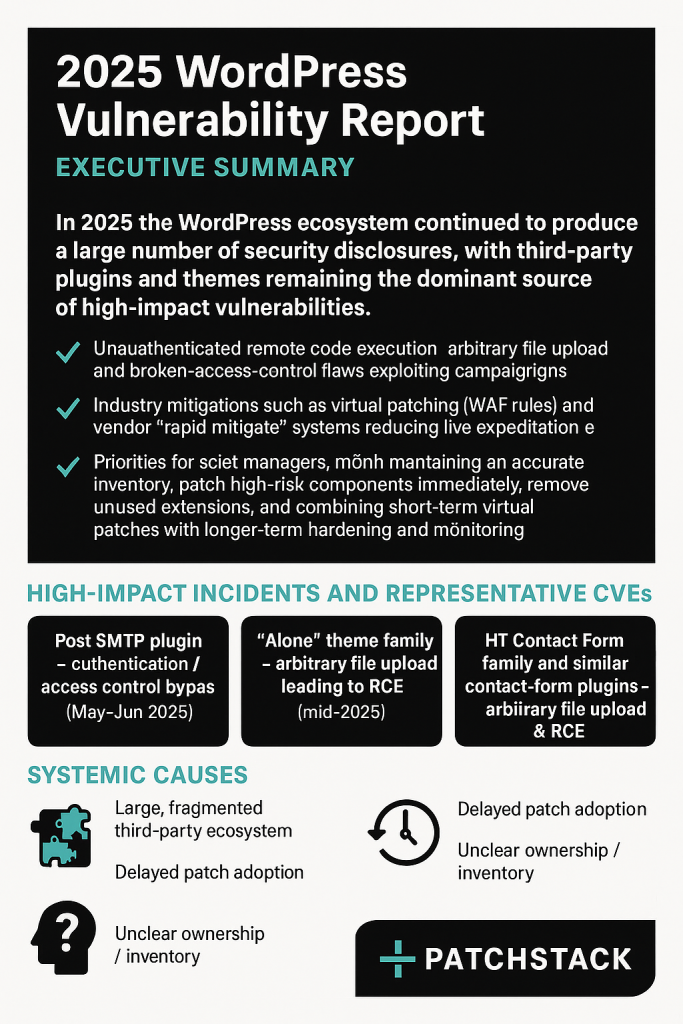
This isn't theoretical anymore. In January 2026, security researchers at Patchstack discovered a critical vulnerability in Modular DS, a popular WordPress plugin trusted by over 40,000 websites worldwide. The vulnerability scored a perfect 10/10 on the severity scale. And here's the part that keeps website owners awake at night: attackers were already exploiting it before the public even knew it existed, as detailed by The Hacker News.
The flaw is brutal in its simplicity. Once a site connects to Modular DS (which creates authentication tokens), attackers can bypass the authentication system entirely. There's no cryptographic connection between the incoming request and Modular itself, which means anyone—literally anyone—could potentially gain administrative access to your entire WordPress installation. We're talking about complete site takeover, data theft, malware injection, and ransomware deployment, as reported by TechRadar.
What makes this situation particularly scary is how quickly it spread. Security researchers confirmed the first active attacks on January 13, 2026. Within hours, the vulnerability was actively being weaponized against real websites. By the time most site owners heard about it, threat actors were already inside thousands of installations, according to BleepingComputer.
But here's the thing: understanding this vulnerability isn't just about Modular DS. It's about understanding how WordPress security works, why plugins create risk, and what you need to do right now to protect your website. This guide walks you through everything you need to know, from the technical details of the flaw to the specific steps you should take today.
Let's start with what happened, why it happened, and most importantly, what you need to do about it.
TL; DR
- The Vulnerability: Modular DS plugin versions before 2.5.2 contain a critical authentication bypass allowing attackers to gain admin access to 40,000+ WordPress sites
- The Risk Level: Scored 10/10 severity with active exploitation confirmed in the wild as of January 13, 2026
- The Technical Issue: No cryptographic link between authentication requests and the Modular service itself allows auth middleware bypass
- What You Must Do: Update immediately to version 2.5.2 or higher, regenerate all WordPress salts, reset OAuth credentials, and scan for malware
- Broader Lesson: Plugin vulnerabilities represent your biggest WordPress security risk—implement multi-factor authentication, use security scanning tools, and maintain a strict update schedule

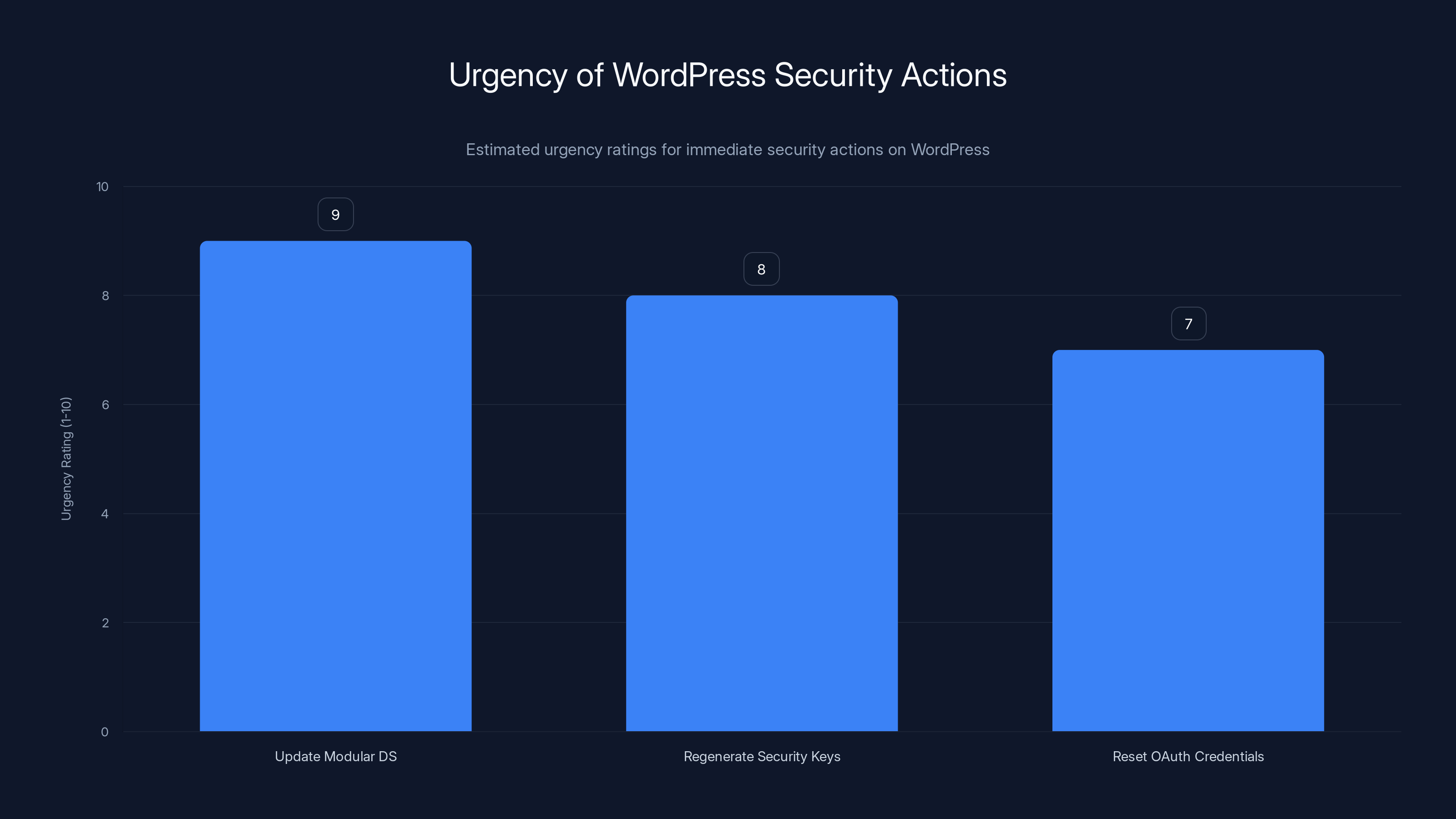
Estimated data: Updating Modular DS is the most urgent action with a rating of 9, followed by regenerating security keys and resetting OAuth credentials.
Understanding the Modular DS Vulnerability: What Exactly Went Wrong
Modular DS isn't some obscure plugin you've never heard of. It's a legitimate tool designed to solve a real problem: managing multiple WordPress sites from a single dashboard. If you run 5, 10, or 20 WordPress installations, the idea of controlling them all from one place sounds amazing. You don't need to log into each site individually. You don't need to manage separate credentials. Everything flows through one central hub.
That's exactly why 40,000+ websites installed it, as noted by InfoSecurity Magazine.
But convenience and security often move in opposite directions. When you centralize administration, you also centralize risk.
The vulnerability works like this: Modular DS uses authentication tokens to verify that requests coming to your website actually come from your authorized Modular dashboard. Makes sense, right? Your site needs to trust that the person making changes really is you.
The problem is in how those tokens are verified. According to Patchstack's technical analysis, once a site has been connected to Modular DS (which generates and stores those tokens), anyone can craft a request that passes the authentication middleware without actually being connected to your Modular account. There's no cryptographic validation tying the incoming request back to your specific Modular installation or account.
Think of it like a bouncer checking your ID. A secure system would verify that your ID is real, matches your face, and was issued by an official government. This vulnerability is like a bouncer who just checks "does this person have any ID?" without actually reading it. Anyone holding any ID gets in.
What makes this particularly insidious is the timeline. Patchstack disclosed that the first attacks were detected on January 13, 2026. The vendor (Modular) wasn't even notified until January 14—a full day after active exploitation began. This means threat actors had a window where they could compromise websites before vendors, security teams, or website owners even knew the vulnerability existed, as highlighted by The Hacker News.
The vendor did respond quickly, releasing version 2.5.2 with a patch just hours after being notified. That's actually commendable. But by then, thousands of sites had already been compromised or exposed.
The real lesson here isn't that Modular DS is a "bad" plugin. It's that any plugin that handles authentication, integrates with external services, or manages sensitive data requires extremely careful security implementation. One small oversight—like failing to cryptographically validate token ownership—can expose thousands of sites.
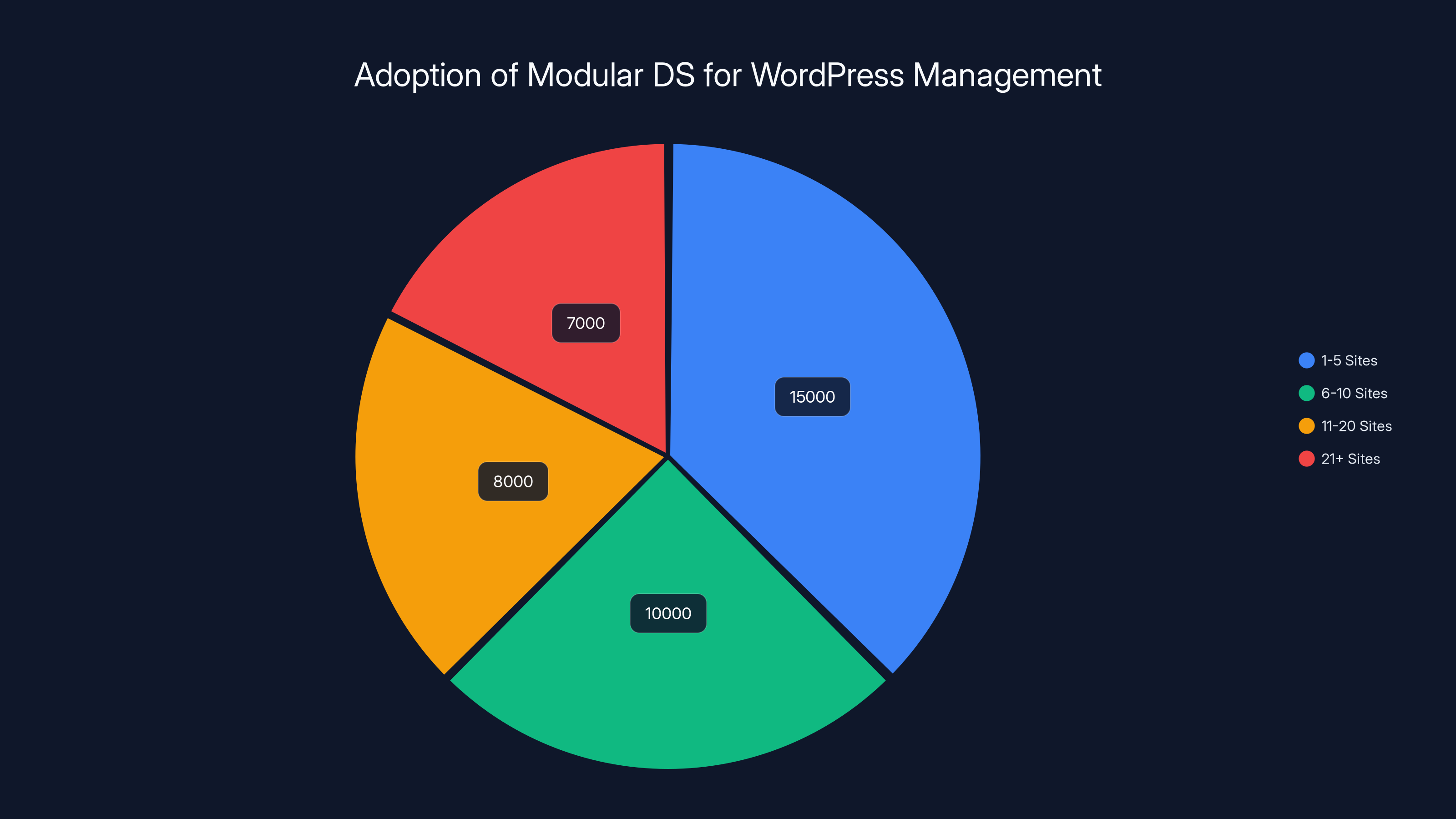
Estimated data shows that most Modular DS users manage between 1-5 WordPress sites, highlighting its popularity among smaller site operators. Estimated data.
Why Plugin Vulnerabilities Are WordPress's Biggest Security Problem
WordPress itself is reasonably secure. The core software is maintained by thousands of contributors, reviewed constantly, and updated regularly. Security researchers focus on it heavily, which means vulnerabilities get discovered and patched quickly.
But WordPress is also a platform. You install plugins to add functionality. And that's where security gets messy.
Here's the uncomfortable truth: WordPress security is only as strong as your weakest plugin.
You could have the most secure WordPress core installation possible, paired with the best security plugin available, updated religiously, with strong passwords and multi-factor authentication enabled. Then you install a popular plugin with 10,000+ active installations that nobody carefully audited, and suddenly you're exposed.
The numbers tell the story. Most major WordPress security incidents don't come from WordPress core vulnerabilities. They come from plugins. A large percentage of compromised WordPress sites have vulnerability traces pointing directly to a plugin that either wasn't updated or had a zero-day vulnerability that nobody knew about yet, as explained by All About Cookies.
Why are plugins such a problem?
Scale and Incentives: A popular WordPress plugin might be downloaded hundreds of thousands of times. Success in the WordPress ecosystem doesn't always correlate with security resources. A solo developer with a popular plugin has zero financial incentive to invest in security audits, penetration testing, or formal security processes. They're doing it on their own time, often for free.
Architectural Risks: Plugins have deep access to WordPress. They can manipulate the database, modify user permissions, change plugin settings, and inject code directly into pages. A plugin with poor security validation can become a complete site takeover tool in the hands of an attacker.
The Update Problem: WordPress itself pushes updates automatically. Plugin updates? Users have to manually enable them or manually apply them. A significant percentage of WordPress installations run outdated plugins because owners simply don't remember to update them. Or worse, they set plugins to auto-update and the plugin breaks, so they disable auto-updates and never re-enable them.
Discovery Lag: When a plugin vulnerability is discovered, there's often a lag between disclosure and patch availability. Some plugin developers fix issues quickly (like Modular did). Others take weeks or months. And some vulnerabilities get exploited in the wild before being officially disclosed, meaning users have zero warning.
Modular DS represents a perfect storm of these factors. It's popular (40,000+ installations), it handles authentication and site administration (high risk if compromised), and the vulnerability was exploited before disclosure (zero advance warning).
The broader implication is this: if you're running WordPress, plugin security should be one of your top priorities. This isn't paranoia. This is basic risk management.
The Technical Details: How the Authentication Bypass Actually Works
If you're not a developer, feel free to skip this section and jump to "What You Need To Do Right Now." But if you want to understand exactly why this vulnerability is so dangerous, the technical details matter.
Modular DS uses OAuth-style authentication to allow your WordPress site to communicate with the Modular dashboard. When you connect your site, Modular generates tokens that your WordPress site stores locally. These tokens prove to the Modular service that your site is legitimate and authorized.
The problem is in how the plugin validates those tokens on the receiving end. Here's the vulnerability:
- Token is generated: You connect your WordPress site to Modular, which generates an OAuth token and stores it on your site.
- Attacker makes request: An attacker crafts an HTTP request to your WordPress site claiming to come from Modular, and includes any random token.
- Plugin validates poorly: Instead of verifying that the token matches what's actually stored on your site, or that the request signature matches your specific Modular account, the plugin just checks: "Does a token exist?" If yes, the request is authorized.
- Attacker gets access: With the auth middleware bypassed, the attacker can perform administrative actions on your WordPress site.
The mathematical concept here is about cryptographic binding. A secure system would ensure that:
where the private key is unique to your Modular account, ensuring that only requests signed with your specific key are accepted. Modular DS's implementation appears to skip this step entirely.
Instead, it's more like:
This is catastrophically insufficient for an authentication system.
For attackers, this is remarkably easy to exploit. You don't need a stolen password. You don't need to crack any credentials. You don't need to social engineer anyone. You just need to make a request to any WordPress site running Modular DS (you can scan for this with basic tools), and if the plugin is installed and connected, you can bypass authentication and act as an administrator.
What's particularly troubling is the exploit timeline. Security researchers confirmed active attacks on January 13, 2026. This means threat actors discovered the vulnerability (or were tipped off about it), developed an exploit, and began compromising sites—all before the general public even knew the vulnerability existed.
By the time the vendor released a patch, potentially thousands of sites were already compromised.

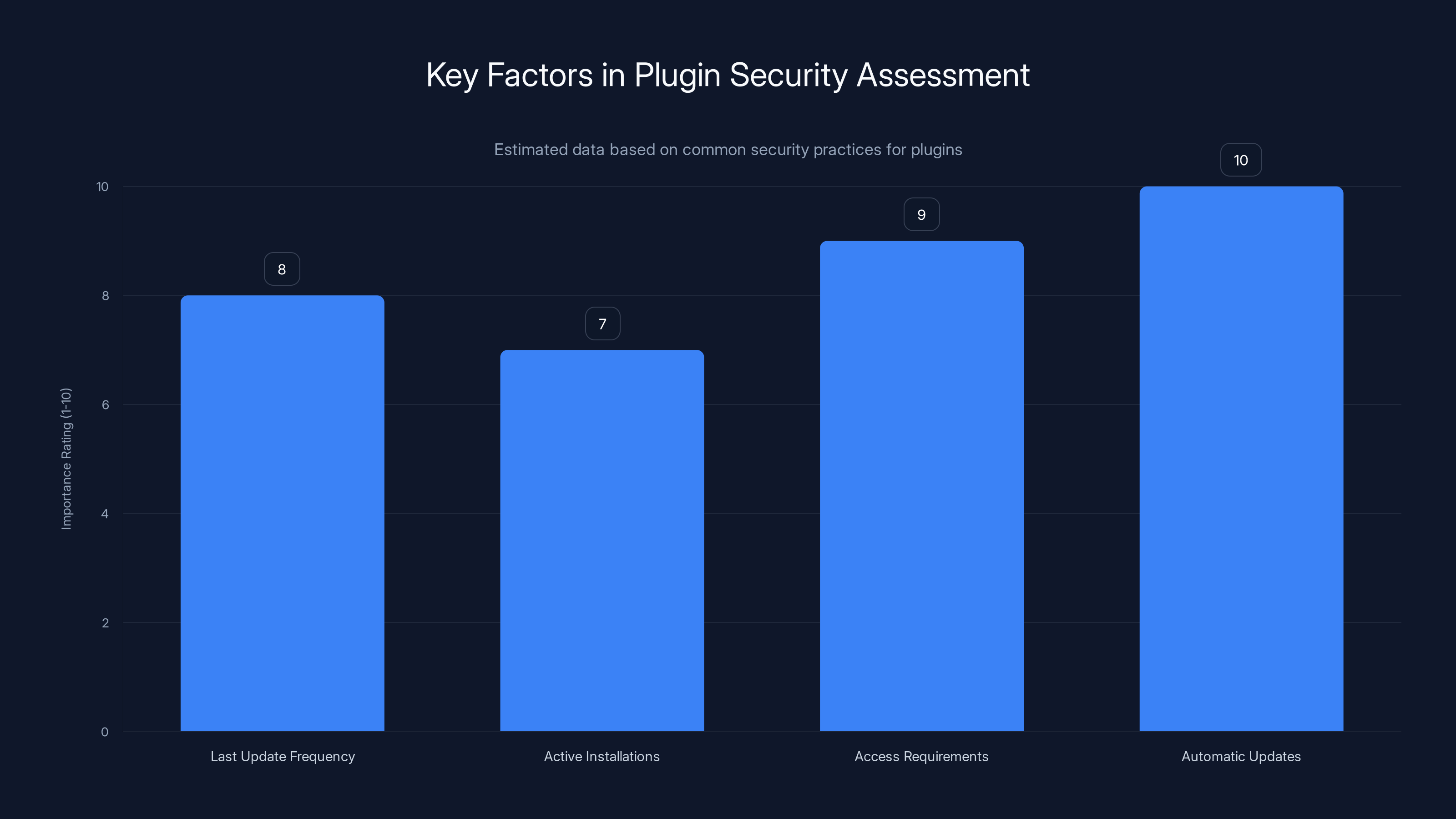
Regular updates, high active installations, minimal access requirements, and automatic updates are crucial for plugin security. (Estimated data)
The Attack Timeline: What Actually Happened
Understanding the timeline helps explain why this was such a serious incident and why the response needed to be immediate.
January 13, 2026: Security researchers at Patchstack detected the first active exploitations of the vulnerability in the wild. This suggests threat actors either had prior knowledge (possibly through underground security research sharing) or discovered it independently around the same time.
January 14, 2026: Patchstack notified the Modular DS vendor about the vulnerability, providing technical details and proof of exploitation.
January 14, 2026 (later that day): The vendor responded with a fix and released Modular DS version 2.5.2 containing the patch. This was remarkably fast—most vendors take days or weeks to respond to critical vulnerabilities. Modular handled this professionally.
January 15, 2026 and beyond: The vulnerability was publicly disclosed, and the race began. Users who quickly updated were safe. Users who didn't update within days were potentially compromised.
The critical window is that single day between January 13 and January 14. During that time, threat actors had knowledge of the vulnerability but the general public didn't. This is called a "zero-day" period because the vulnerability exists but is unknown to defenders.
For the 40,000+ websites running Modular DS, the implications were severe:
- Thousands were compromised during that zero-day window
- Administrators didn't know to check for intrusions
- Attackers had time to establish persistence (create backdoor accounts, plant malicious code)
- Data was potentially exfiltrated before anyone noticed
This is exactly how real-world breaches happen. Not with flashy hacker movies or dramatic discoveries. Just quietly, in the background, while people are working on other things.

Immediate Action Items: What You Must Do Right Now
If your WordPress site uses Modular DS, forget everything else you're doing and complete these steps today.
Step 1: Update Modular DS Immediately
Log into your WordPress admin dashboard. Navigate to Plugins. Find Modular DS. Update it to version 2.5.2 or higher immediately. If you have auto-updates disabled for plugins, this is exactly the exception where you override your normal process. Do it now.
If you can't update during business hours, schedule a maintenance window and do it as soon as possible. Yes, there's a small risk of downtime. There's a massive risk of site compromise if you don't.
Step 2: Regenerate Your WordPress Security Keys and Salts
Even after updating, attackers might have already compromised your site. To invalidate any existing sessions that might be used by attackers, you need to regenerate your WordPress security keys and salts.
These are random strings that WordPress uses to encrypt cookies and session data. If an attacker gained administrative access, they might have planted persistent backdoors. Regenerating salts forces everyone (including attackers) to re-authenticate.
You can generate new keys and salts from the WordPress.org salt generator website (search for "WordPress security keys generator"). Copy the generated code and paste it into your wp-config.php file, replacing the old values.
Be careful with this step if you're not comfortable with file editing. If you are, it takes two minutes. If you're not, consider asking a developer or your hosting provider to do it.
Step 3: Reset All OAuth Credentials
Since the vulnerability involves OAuth token handling, you need to reset all OAuth credentials connected to your Modular account.
Log into your Modular dashboard. Find the OAuth credentials or connected apps section. Revoke all current connections. This forces your WordPress site to re-authenticate and generates new tokens.
Yes, you'll need to reconnect your WordPress site to Modular if you want to use it going forward. Do it anyway. New tokens are infinitely better than tokens that might have been captured by attackers.
Step 4: Scan for Indicators of Compromise
Patchstack published a list of indicators of compromise (IoCs) that can help you determine if your site was actually compromised during the vulnerability window.
These include specific file paths, database changes, and suspicious admin account creations that are associated with exploitation attempts. Review the IoCs and check your site against them.
If you don't have technical expertise, your hosting provider likely has tools for this. Many hosting providers (especially WordPress-focused ones) offer automatic malware scanning and removal services.
Step 5: Scan for Malware and Backdoors
If your site was compromised, the attacker might have installed:
- Malicious plugins
- Backdoor themes
- Modified WordPress core files
- Hidden admin accounts
- Web shells
Use a security scanner to check your entire site. Wordfence, Sucuri, and similar tools can scan WordPress installations and flag suspicious files or plugins.
If you find anything suspicious, remove it immediately. Then change all passwords (admin accounts, database credentials, hosting control panel) to be absolutely sure.
Step 6: Check Your WordPress Users
Go to WordPress Dashboard > Users. Look for any admin accounts you don't recognize. Check the "Date Added" column if available. Any new admin accounts created around January 13-15, 2026 are highly suspect.
Delete any accounts that don't belong to you or your authorized team members.
Step 7: Review Your Site Activity Logs
If your site has logging enabled (from a security plugin or hosting provider), review the logs for the period January 13-15, 2026 and a few days after. Look for:
- Unusual file uploads
- Plugin installations
- User account creations
- Database modifications
- Theme changes
- Admin settings changes
Any of these might indicate that your site was compromised.

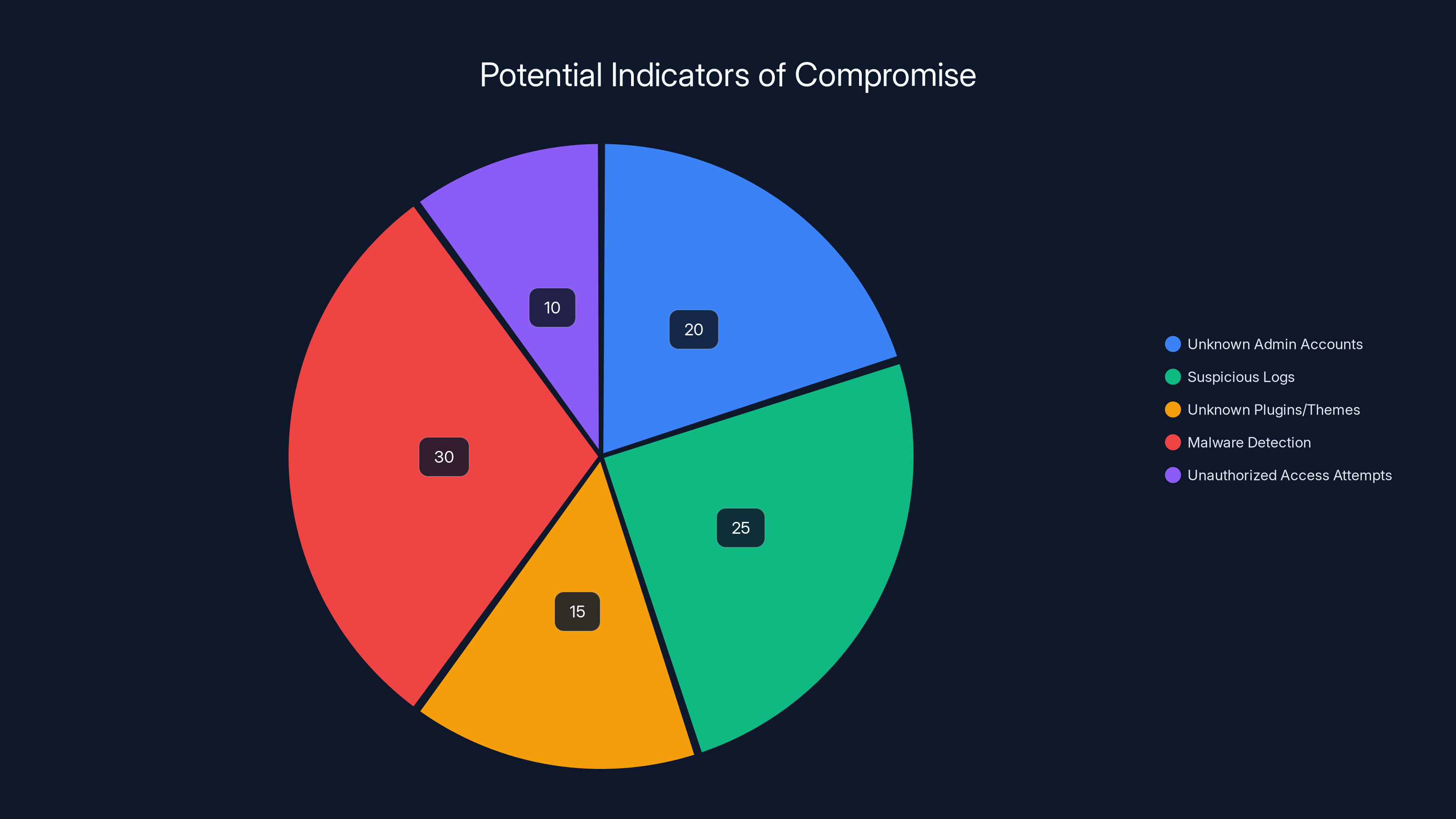
Estimated data suggests that malware detection and suspicious logs are the most common indicators of a WordPress site compromise. (Estimated data)
Preventing Plugin Vulnerabilities: Long-Term Security Strategy
Updating Modular DS and scanning for malware handles the immediate crisis. But there's a bigger question: how do you prevent this from happening again?
Here's the uncomfortable truth: you can't completely prevent plugin vulnerabilities. Vulnerabilities exist in software created by thousands of different developers with varying security expertise and resources. That's just reality.
But you can dramatically reduce your risk by implementing proper security practices.
Audit Your Installed Plugins
First, look at every plugin you have installed. Ask yourself: do I actually use this? Does it do something I need?
If the answer is no, delete it. Every installed plugin is potential attack surface. An old, unused plugin is often a security liability.
For plugins you do use, check:
- When was the last update? If it's been more than 6 months, the plugin might be abandoned. Consider replacing it with an actively maintained alternative.
- How many active installations? Plugins with more active installations usually get more security attention. (Though Modular DS had 40,000+ installations and still had a critical vulnerability.)
- What access does it require? Plugins that request full database access, file system access, or admin capabilities are higher risk if compromised.
Enable Automatic Plugin Updates
When a vulnerability like Modular DS is discovered, the window between disclosure and exploitation is extremely narrow. You need patches applied automatically.
Go to WordPress Dashboard > Settings > General > Automatic Updates. Enable automatic updates for plugins. Yes, there's a tiny risk that an auto-update breaks something. There's a massive risk that an unpatched plugin gets exploited.
The trade-off favors security.
Keep WordPress Core Updated Too
WordPress generally handles this automatically now, but confirm that your WordPress core installation is set to auto-update. Same reasoning: the vulnerability window is narrow, and you need patches applied immediately.
Use a Web Application Firewall (WAF)
A WAF sits between your site and the internet. It inspects traffic and blocks requests that look malicious.
For a vulnerability like the Modular DS auth bypass, a good WAF might detect and block the unusual authentication requests before they even reach your WordPress installation.
Services like Cloudflare, Wordfence, or Sucuri provide WAF functionality. They won't catch every attack, but they'll catch many.
Implement Multi-Factor Authentication (MFA)
This is possibly the single most effective security control you can implement. If your WordPress admin account requires MFA, then even if an attacker bypasses password authentication, they still need your phone or authenticator app.
The Modular DS vulnerability gave attackers a way to bypass the plugin's authentication. But if your WordPress admin accounts require MFA, they'd still be blocked.
Enable MFA on every admin account. Use an authenticator app (like Google Authenticator or Authy), not SMS if possible.
Regular Security Audits
Once every few months, spend 30 minutes reviewing:
- What plugins are installed?
- Are they all updated?
- Are there any new user accounts?
- Do your user roles make sense?
- Are there any suspicious file changes?
You don't need to be a security expert. Just paying attention is enough to catch most problems.
Use a WordPress Security Monitoring Service
Services like Wordfence, Sucuri, or iThemes Security provide real-time monitoring. They check your site for malware, notify you of vulnerability disclosures, scan for suspicious activity, and send alerts if something weird happens.
These aren't free, but the peace of mind and actual security improvements are worth the cost.

WordPress Security Best Practices Beyond Plugin Management
The Modular DS vulnerability is a plugin problem, but WordPress security is much broader. Here are additional practices that should be part of your standard security posture.
Principle of Least Privilege
Every WordPress user account should have the absolute minimum permissions required to do their job. If you have a content editor, they don't need admin access. If you have a designer, they don't need access to plugin settings.
WordPress's role system (Admin, Editor, Author, Contributor, Subscriber) is designed specifically to limit damage if an account is compromised. Use it.
Database Backups
If your site does get compromised despite all precautions, a clean backup lets you recover in hours instead of days or weeks.
Backup your WordPress installation and database regularly. Ideally, store backups off-site (not on the same server where your WordPress site lives). If an attacker compromises your server, local backups are useless.
Many hosting providers offer automatic backups. Enable them. Better yet, set up multiple backup systems. One backup is a single point of failure. Three backups means you're probably fine.
Restrict Admin Access by IP Address
If all your WordPress administrators work from known office locations or home offices, you can restrict WordPress admin access to specific IP addresses.
This doesn't stop all attacks, but it adds another layer. An attacker trying to access your WordPress admin panel from a random location on the internet would be blocked, even if they somehow had valid credentials.
Use HTTPS and Keep SSL Certificates Current
HTTPS encrypts traffic between your browser and your server. Without it, someone on your network could intercept your login credentials.
If you're still running WordPress over HTTP (not HTTPS), fix this immediately. Most hosting providers offer free SSL certificates through Let's Encrypt.
Change Default WordPress Database Prefix
By default, WordPress creates database tables with the wp_ prefix. Attackers know this. If you change the prefix to something random during WordPress installation, SQL injection attacks are slightly harder to execute.
This is a small hardening step that only matters if someone can inject SQL, but every small step helps.
Disable File Editing
WordPress has a built-in code editor. You can edit plugins and themes directly from the admin panel. This is convenient but dangerous. If an attacker gains admin access, they can directly modify your plugins and theme files.
Disable it by adding this line to your wp-config.php:
define('DISALLOW_FILE_EDIT', true);
Now, even if someone gains admin access, they can't edit theme or plugin files directly. They'd need file system access through FTP or SSH, which is a higher barrier to entry.
Monitor Login Attempts
When multiple failed login attempts happen, it usually means someone's trying to guess your password. Too many failed attempts should trigger a temporary lockout.
Security plugins like Wordfence implement this automatically. Enable it.
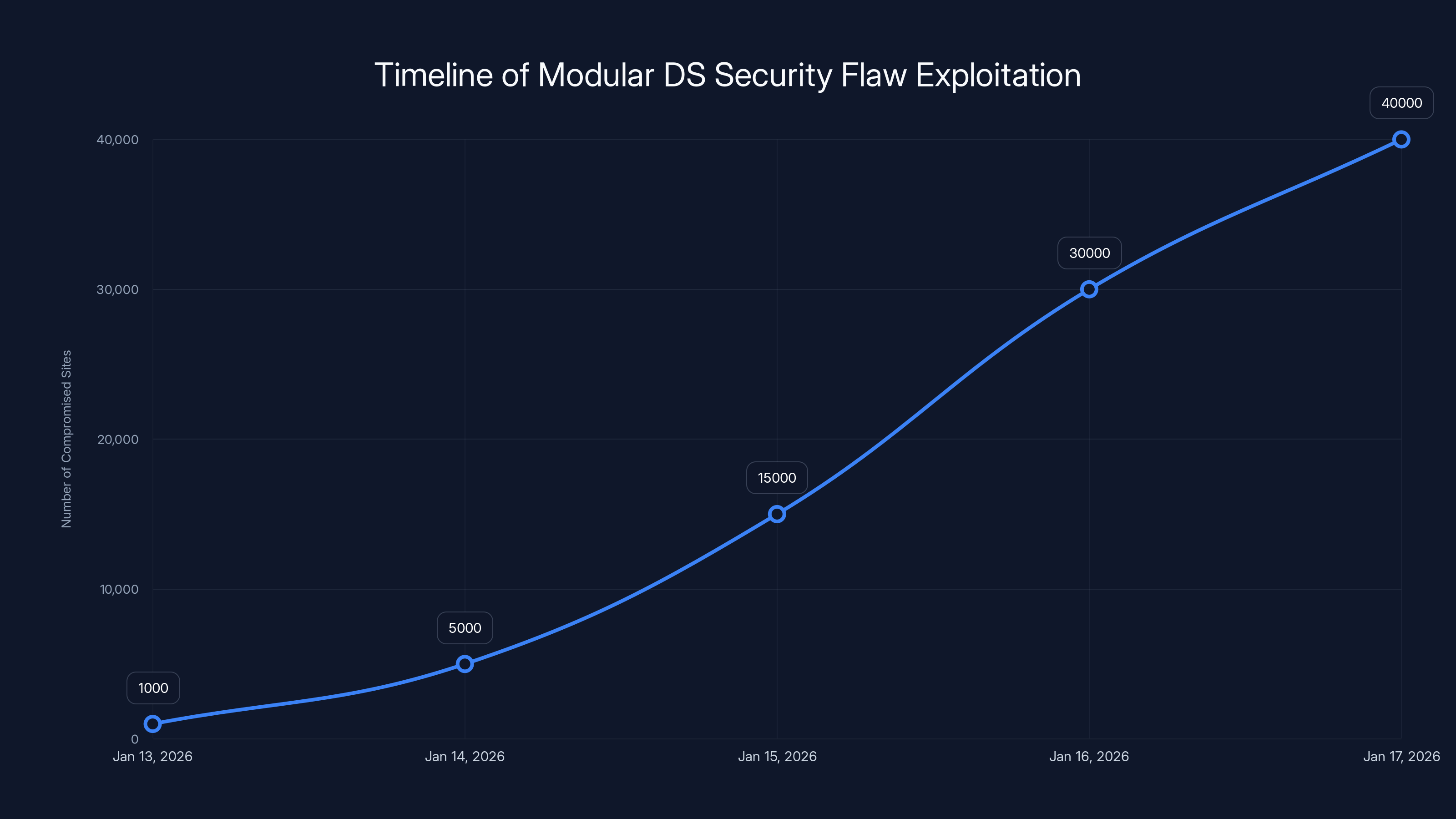
Estimated data shows rapid spread of attacks exploiting the Modular DS vulnerability, affecting up to 40,000 sites within five days.
The Bigger Picture: Why Vulnerabilities Like This Keep Happening
The Modular DS vulnerability highlights a systemic issue in open-source software: security takes resources, and resources are scarce.
Modular DS is a useful tool built by developers who probably care about security. But they're also humans with limited time and budget. They probably didn't conduct a professional security audit before releasing the plugin. They probably didn't have dedicated security staff reviewing code. They probably released it, got positive feedback, and moved on to adding features.
This is how most open-source WordPress plugins work. It's a sustainability problem, not a moral failing.
The WordPress ecosystem has improved significantly over the last few years. More developers take security seriously. Tools for identifying vulnerabilities are better. The community shares security knowledge more openly. But the fundamental dynamics remain: lots of code, lots of developers, limited resources dedicated to security.
The result is that vulnerabilities will keep happening. Some will be critical. Some will be exploited before patches are available. Some will affect tens of thousands of websites.
The Modular DS vulnerability isn't an anomaly. It's the baseline. Expect this to happen again with other plugins. The question isn't "will vulnerabilities happen?" It's "am I prepared when they do?"
That preparation comes down to:
- Staying informed about new vulnerabilities
- Updating quickly
- Monitoring your site for compromise
- Maintaining backups
- Using security tools and practices
None of these are glamorous. None are fun. All are absolutely necessary if you run WordPress.

Common Mistakes Site Owners Make When Vulnerabilities Are Disclosed
When a vulnerability like Modular DS is disclosed, site owners often make predictable mistakes:
Mistake 1: Assuming "It Won't Happen to My Site"
If 40,000 websites installed Modular DS, they're statistically diverse. Small blogs, medium businesses, large enterprises. They all thought they were unlikely targets.
Threat actors don't target specific sites. They automate attacks against known vulnerabilities. If your site is running vulnerable software, you're already targeted.
Mistake 2: Waiting to Update
"I'll update it during next week's maintenance window." Except next week, other priorities pop up. By week 3, the site's been compromised.
Critical vulnerabilities require immediate action. Schedule emergency maintenance if necessary.
Mistake 3: Not Scanning for Compromise
You update to the patched version and think you're done. But if attackers compromised your site during the zero-day window, just patching doesn't remove the backdoors they installed.
Scanning is tedious and might be scary (you might find something), but it's necessary.
Mistake 4: Not Changing Credentials
If an attacker gained admin access, they might have created backdoor accounts or installed persistent access methods. Updating the password for one admin account doesn't remove those backdoors.
After any significant security incident, treat it like you've been fully compromised: change all passwords, regenerate security keys, reset OAuth tokens, scan for malware.
Mistake 5: Not Learning Anything
After dealing with a vulnerability, many site owners move on and forget about it. Then the same thing happens with another plugin six months later.
Use vulnerabilities as a wake-up call to audit your security practices, enable auto-updates, and implement better monitoring.

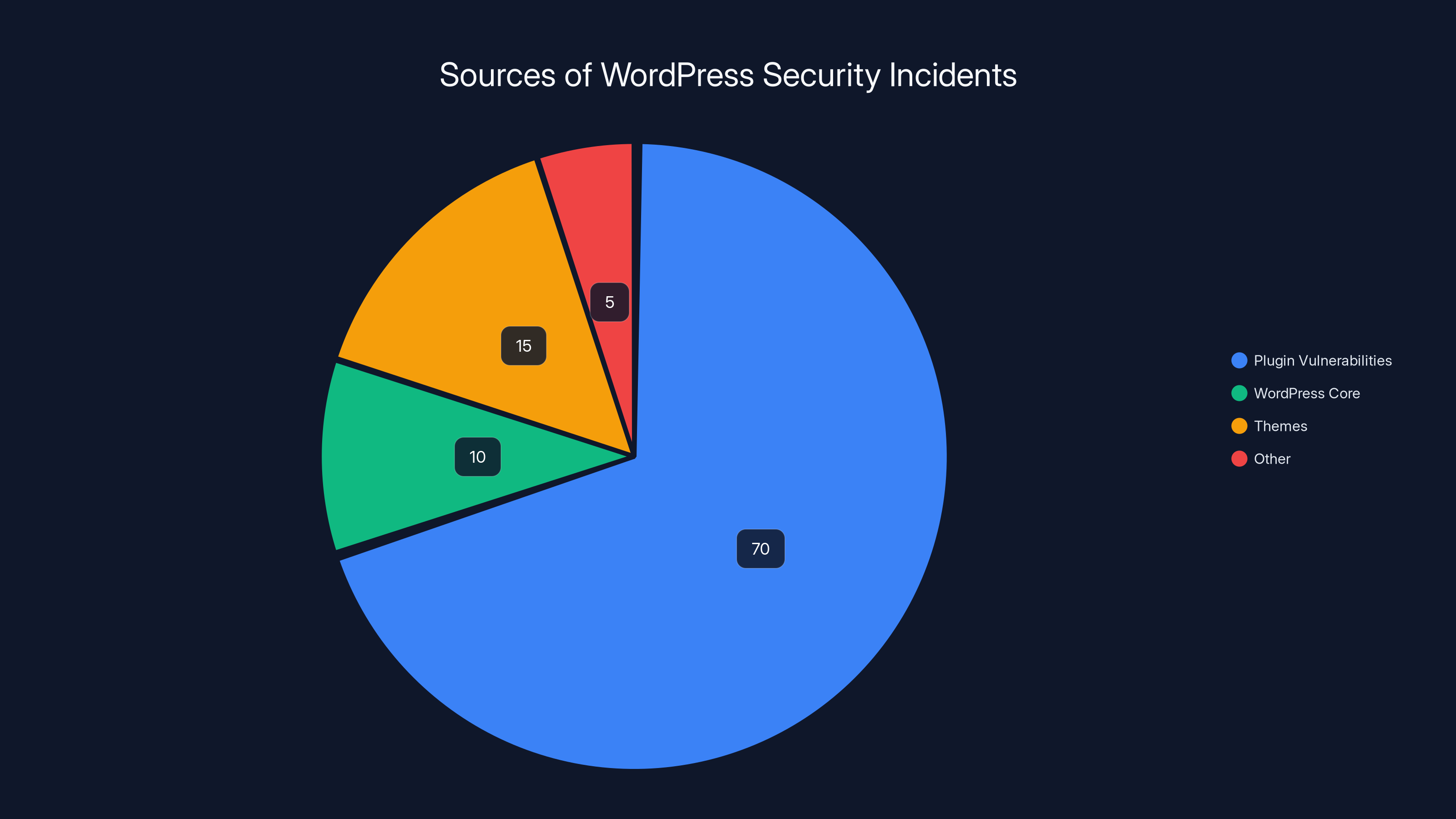
Estimated data shows that the majority of WordPress security incidents stem from plugin vulnerabilities, highlighting the critical need for plugin security audits.
Practical Security Checklist: Going Forward
Here's a checklist you can print out and actually use to improve your WordPress security:
Right Now (This Week):
- Check if you're running Modular DS, and if so, update to 2.5.2+
- Review all installed plugins and delete anything you don't actively use
- Check plugin update status and update anything that's outdated
- Enable automatic plugin and WordPress core updates
- Scan your site for malware and compromised files
- Review your WordPress user accounts and delete any you don't recognize
- Create a backup of your entire WordPress installation
This Month:
- Change all WordPress admin passwords to strong, unique passwords
- Enable multi-factor authentication on every admin account
- Review your WordPress plugin list and remove anything questionable
- Set up automatic daily backups (if not already enabled)
- Implement a WAF or WordPress security plugin with real-time monitoring
- Implement login attempt limiting and temporary lockouts
Ongoing (Monthly/Quarterly):
- Review your installed plugins for security updates
- Check your WordPress user list for unauthorized accounts
- Review activity logs for suspicious patterns
- Test your backup restoration process
- Update WordPress core, plugins, and themes
- Check your hosting provider's security updates
Annually:
- Conduct a full security audit of your WordPress installation
- Review your security strategy and tools
- Consider a professional security assessment
- Update your disaster recovery plan
- Document all your security practices
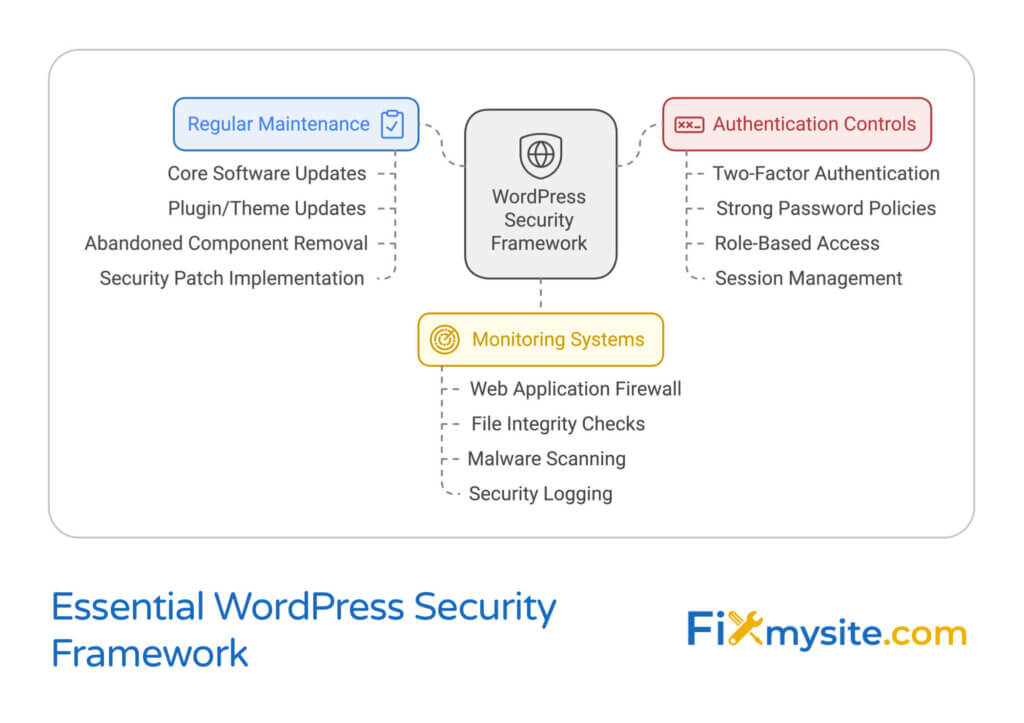
What Modular DS Should Have Done Differently
It's not productive to just blame Modular DS. But understanding what went wrong is educational.
Proper Cryptographic Validation: The core issue was failing to cryptographically validate that authentication requests actually came from an authorized Modular account. This is Security 101. Proper implementation would have tied each request to the specific Modular account cryptographically.
Security Audit Before Release: Any plugin that handles authentication should undergo a professional security audit before public release. A good security auditor would have caught this.
Threat Modeling: A simple threat model ("What if an attacker intercepts our OAuth tokens?" or "What if an attacker can craft forged requests?") would have identified the risk.
Rate Limiting and Monitoring: Even with a flawed auth system, proper rate limiting and intrusion detection might have prevented exploitation at scale.
Disclosure Coordination: Ideally, the vendor and security researchers coordinate on disclosure timing so there's no zero-day window. This appears to have happened here (pretty quickly), but it could have been handled even better.
The point isn't that Modular DS is uniquely bad. The point is that plugin authors need to treat security as a first-class concern, not an afterthought.

The Broader WordPress Plugin Ecosystem Challenge
Modular DS is one plugin. But there are tens of thousands of WordPress plugins. Some are maintained by large organizations with dedicated security teams. Some are maintained by solo developers maintaining them in their spare time.
This creates a two-tier security landscape:
Enterprise-Grade Plugins: Maintained by companies, security audited, quick to patch, well-documented. Examples: Yoast SEO, WooCommerce, Jetpack. These still have vulnerabilities, but less frequently and they're patched quickly.
Community Plugins: Maintained by volunteers, security practices vary wildly, update speed unpredictable, sometimes abandoned. These are where most vulnerabilities occur.
For site owners, this means:
- Prefer plugins from established organizations when possible
- Check how frequently a plugin is updated as a health indicator
- Assume any plugin could have vulnerabilities and plan accordingly
- Use defensive security practices (backups, monitoring, WAF) as a safety net
The security landscape is improving, but it's still fundamentally a resource problem.

FAQ
What is CVE-2026-23550?
CVE-2026-23550 is the official vulnerability identifier for the Modular DS authentication bypass flaw. CVE stands for Common Vulnerabilities and Exposures, which is the standard system for naming publicly disclosed vulnerabilities. This specific vulnerability affects Modular DS versions before 2.5.2 and was discovered by Patchstack security researchers. The CVE provides a standardized way to reference this vulnerability across different security tools and discussions.
How do I know if my WordPress site was actually compromised by this vulnerability?
You can check several indicators: review your WordPress user accounts for any admin accounts created around January 13-15, 2026 that you don't recognize; check your site's activity logs or security plugin logs for suspicious administrative actions during that period; look for unknown plugins or themes that might have been installed; scan your site with a security scanner like Wordfence that can detect malware and backdoors; and review your hosting provider's server logs for unauthorized access attempts. If you find any signs of compromise, clean your site thoroughly, reset all credentials, and consider professional security assistance.
Is Modular DS safe to use after updating to version 2.5.2?
Yes, once updated to version 2.5.2, the authentication bypass vulnerability is patched. However, the patch doesn't remove any backdoors or persistent access methods that attackers might have installed before the patch was applied. This is why scanning for compromise and resetting credentials is essential even after patching. If your site was compromised during the zero-day window, simply patching leaves backdoors in place.
Should I uninstall Modular DS entirely or is the patch sufficient?
The patch fixes the vulnerability, but whether you keep using Modular DS depends on your risk tolerance and how comfortable you are with the vendor's security practices. If you trust Modular and find it essential for your workflow, updating and maintaining careful monitoring is reasonable. If you want to eliminate the risk entirely, you could uninstall it and find alternative solutions for multi-site management. Either approach is defensible; it's a personal decision based on your needs and risk tolerance.
What should I do if I can't update Modular DS immediately due to compatibility issues?
Disable the plugin immediately while you work on fixing compatibility issues. The security risk of running a vulnerable plugin outweighs the risk of having that functionality temporarily unavailable. Once you've resolved compatibility issues, update the plugin. If you can't resolve compatibility, consider replacing Modular DS with an alternative solution that's actively maintained and compatible with your WordPress version.
How often should I scan my WordPress site for malware and vulnerabilities?
Ideally, you should have continuous monitoring through a security service like Wordfence or Sucuri that scans your site daily or in real-time. Additionally, perform manual or automated full-site scans at least monthly. After major events like this vulnerability disclosure, scan your site immediately. The more frequent your scanning, the faster you'll catch any compromise if it occurs.
What's the difference between patching a vulnerability and cleaning up a compromise?
Patching (updating the plugin) fixes the vulnerability that allowed exploitation. Cleaning up a compromise means removing the backdoors, malware, or persistent access that attackers installed while exploiting the vulnerability. Both are necessary: patching prevents future exploitation, while cleanup removes current threats. If your site was compromised, patching alone is insufficient—you must also scan, clean, and reset credentials.
Can my hosting provider protect me from plugin vulnerabilities?
Hosting providers can implement some protections like web application firewalls, intrusion detection systems, and automatic backups. However, they can't directly manage your WordPress plugins or prevent you from installing vulnerable plugins. Your responsibility includes choosing which plugins to install, keeping them updated, and monitoring your site for compromise. A good hosting provider helps, but it's not a substitute for personal security practices.
How long do I need to monitor my site after a vulnerability like this?
Monitoring should be permanent and ongoing, not just after specific vulnerabilities. However, after a major vulnerability disclosure like Modular DS, increase your monitoring intensity for at least 30 days while threat actors are most actively exploiting it. After that, maintain standard monthly or quarterly audits. The earlier you detect compromise, the more quickly you can respond.
What's the relationship between this vulnerability and WordPress security as a whole?
This vulnerability illustrates that WordPress core is not the main security weakness—plugins are. WordPress itself is maintained by thousands of professionals with strong security practices. Plugins, however, are created by thousands of different developers with varying expertise and resources. A single vulnerable plugin can expose an entire WordPress installation. Strong WordPress security requires not just updating WordPress core, but carefully managing plugins, implementing defensive tools like WAFs and security monitoring, and maintaining good security practices across the board.

Conclusion: Moving Beyond Crisis Mode
The Modular DS vulnerability is serious, but it's also a teaching moment. It demonstrates exactly why WordPress security can't be a set-it-and-forget-it proposition.
Your WordPress site is built on a foundation of free software created by thousands of developers. That software is under constant scrutiny from both security researchers and malicious actors. Vulnerabilities will be found. Some will be severe. Some will be exploited before patches are available.
You can't prevent vulnerabilities. But you can prepare for them.
Start today:
- Check if you use Modular DS. If so, update to 2.5.2 immediately.
- Audit your plugins. Delete anything you don't actively use.
- Enable automatic updates for both plugins and WordPress core.
- Set up monitoring with a security service or plugin.
- Enable multi-factor authentication on all admin accounts.
- Create backups. Multiple backups, stored off-site.
- Scan your site for any signs of compromise.
These steps take a few hours initially, then minimal ongoing maintenance. They're not exciting. They won't impress anyone. But they're the difference between running a secure WordPress site and running one waiting for disaster.
The vulnerability window has already passed for this particular flaw, but other vulnerabilities are coming. Your preparation today determines whether you can respond quickly or become a victim tomorrow.
The good news is that WordPress security is entirely within your control. You don't need special expertise or massive resources. You just need discipline, attention, and a willingness to prioritize security. Start now, before the next vulnerability is discovered.
Your WordPress site—and your reputation—depend on it.

Key Takeaways
- Modular DS plugin vulnerability (CVE-2026-23550) exposed 40,000+ WordPress sites with 10/10 critical severity score
- Attackers exploited the flaw on January 13, 2026 before vendor notification and public disclosure, creating a dangerous zero-day window
- The vulnerability is an authentication bypass: Modular DS lacks cryptographic validation of OAuth tokens, allowing unauthorized admin access
- Immediate actions required: update to version 2.5.2, regenerate WordPress salts, reset OAuth credentials, scan for malware, and review user accounts
- Plugin vulnerabilities are WordPress's biggest security weakness—implement auto-updates, enable MFA, use security monitoring, and maintain regular backups as long-term protection
![WordPress Plugin Security Flaw: Complete Guide to Staying Safe [2025]](https://tryrunable.com/blog/wordpress-plugin-security-flaw-complete-guide-to-staying-saf/image-1-1768563394522.jpg)



