Condé Nast Data Breach: What Happened, Why It Matters, and How to Protect Yourself
Something wild happened recently in the cybersecurity world, and if you're a reader of WIRED, Vogue, The New Yorker, GQ, or any of the other major publications owned by Condé Nast, you need to know about it.
A hacker going by the name "Lovely" broke into one of the world's largest media conglomerates and walked away with over 40 million records. But here's where the story gets interesting: this wasn't a typical ransomware attack or your standard cybercriminal move. The hacker claimed they had good intentions. They said they discovered serious security vulnerabilities and spent an entire month trying to get Condé Nast's attention. When the company ignored them, they reached out to security researchers and news outlets. Only after those efforts failed did they decide to leak the data publicly, as detailed in Cybersecurity News.
This breach is a wake-up call for everyone who uses digital services, reads news online, or has accounts with major publishers. It's also a masterclass in how modern data breaches work, why they happen, and what you should actually do about it.
Let's dig into what went down, why it matters to you, and most importantly, how to protect yourself right now.
TL; DR
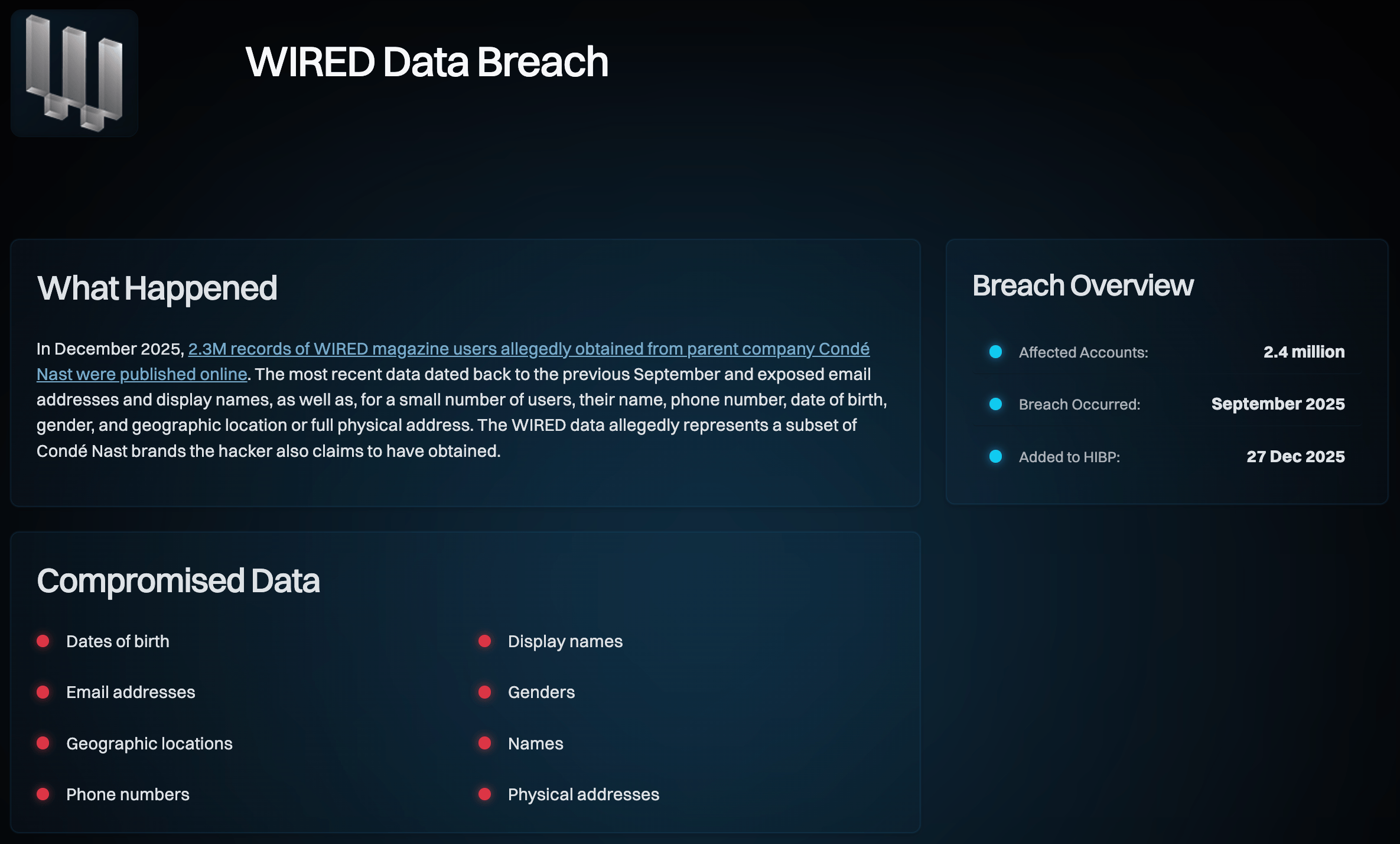
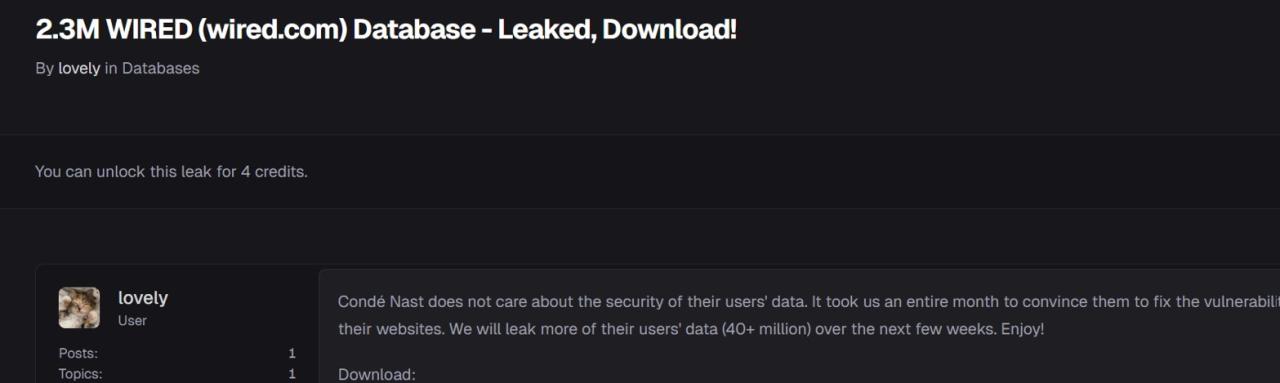
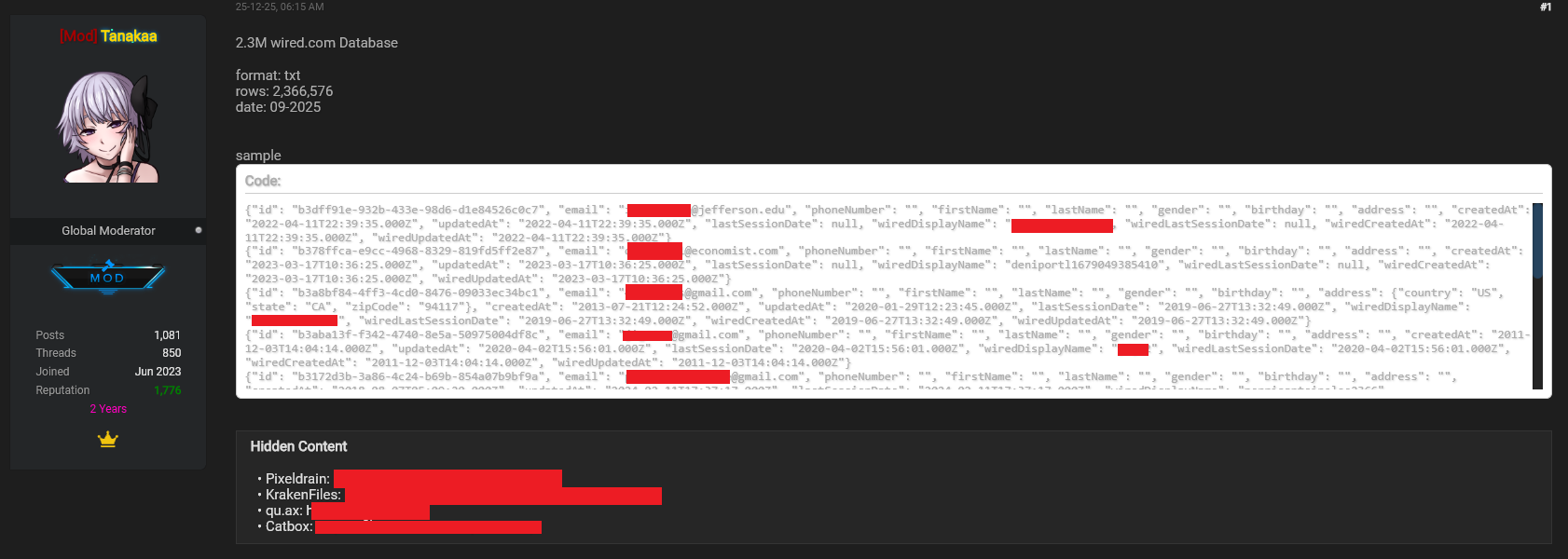
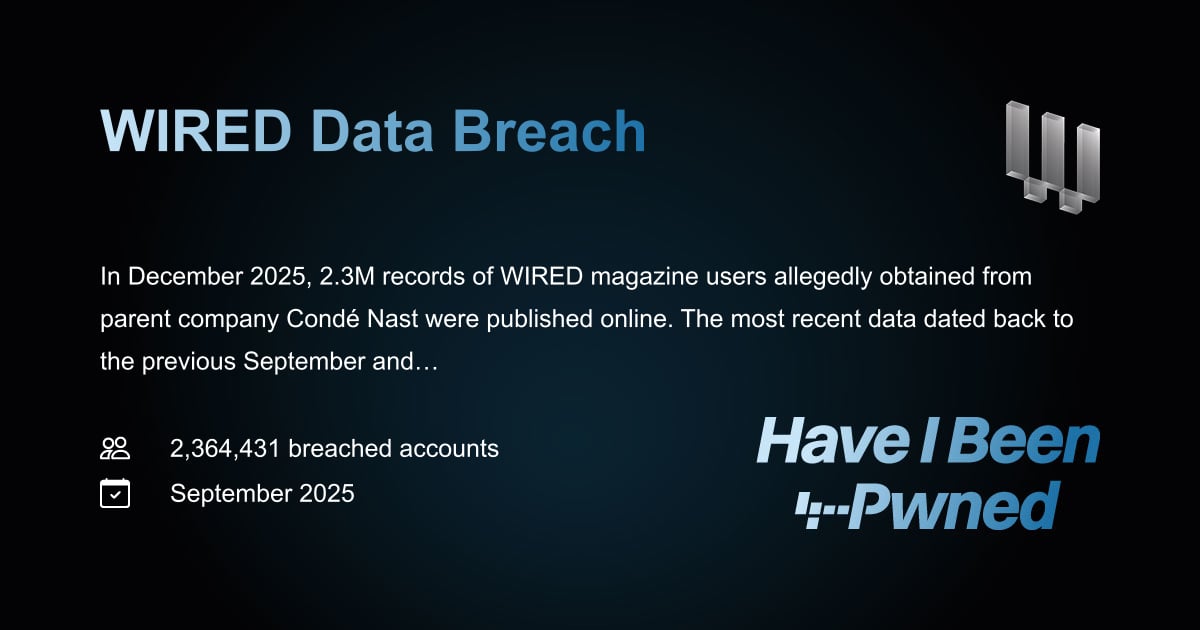
- The Breach: A hacker named "Lovely" accessed 40+ million records from Condé Nast, affecting 2.3 million WIRED readers and data from 13+ other publications including Vogue, The New Yorker, and GQ, as reported by SecurityWeek.
- What Was Stolen: Email addresses, full names, phone numbers, postal addresses, account IDs, genders, birthdates, account creation dates, and session information.
- The Hacker's Motivation: The attacker claimed to have discovered six critical vulnerabilities and tried to warn Condé Nast for a month before leaking data in frustration, according to Security Affairs.
- Immediate Risk: Phishing attacks, identity theft, and social engineering scams targeting affected users.
- What You Should Do: Change passwords immediately, enable two-factor authentication, monitor accounts for suspicious activity, and watch for phishing emails.

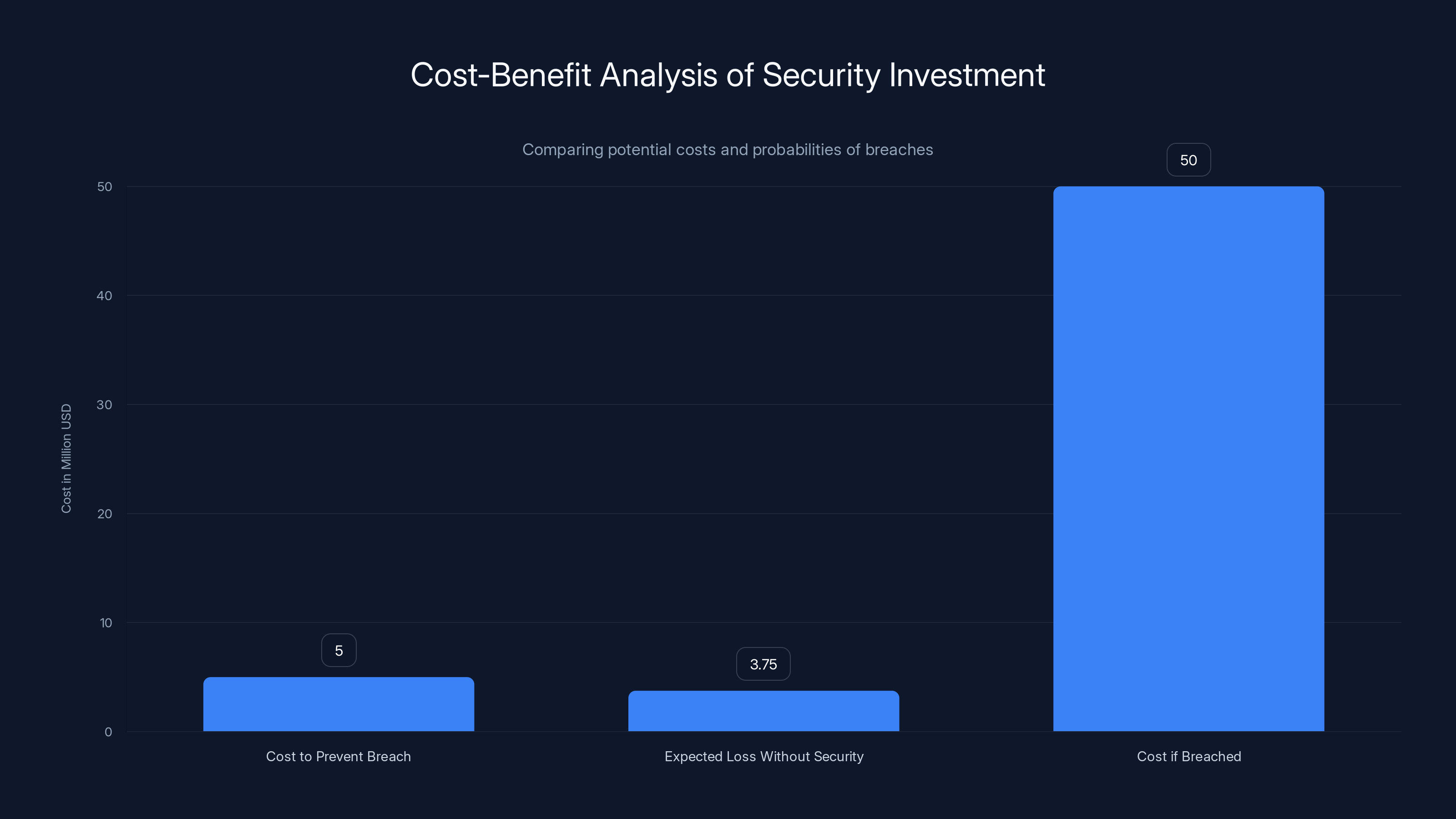
Estimated data shows that while the cost to prevent a breach is
The Condé Nast Breach: Timeline and Details
The Condé Nast data breach represents one of the largest media company compromises in recent years. Understanding the timeline helps you see how attackers operate and why quick response matters.
How the Breach Began
The hacker "Lovely" gained unauthorized access to Condé Nast's systems sometime before publicly announcing the breach. The exact entry point hasn't been fully disclosed, but security experts suspect it involved exploiting one or more of the vulnerabilities the hacker claimed to have discovered. These six vulnerabilities apparently gave the attacker access to sensitive customer data across multiple Condé Nast properties, as noted by Cybersecurity News.
The breach wasn't discovered by Condé Nast's security team. Instead, it was revealed when the hacker proactively tried to contact the company and warn them about the holes in their infrastructure. This is a critical detail because it shows Condé Nast's security monitoring systems failed to detect unauthorized access, even though an intruder had full run of their databases.
When initial attempts to reach Condé Nast failed, Lovely escalated. They contacted Data Breaches.net, a well-known security news site that covers major incidents. This move was designed to force Condé Nast's hand through public pressure and media attention. The strategy partially worked. WIRED was eventually notified about the vulnerabilities, and the company began patching, as detailed in Security Affairs.
The Turning Point
Here's where frustration set in. The hacker claims they gave Condé Nast a full month to address the vulnerabilities before leaking anything. During that time, the attacker grew impatient. They felt the company wasn't taking the threat seriously. No direct contact from executives. No emergency response team. No acknowledgment of the severity.
So Lovely made a decision. They uploaded the stolen data archive to multiple hacking forums and announced that more leaks would follow. The initial archive contained 2.3 million email addresses and associated personal information. But the threat was bigger: the hacker claimed they had 40+ million records total and would release them in phases over subsequent weeks, as reported by SecurityWeek.
The tone of the announcement was telling. In the forum post, the hacker wrote something like: "Condé Nast does not care about the security of their users' data. It took us an entire month to convince them to fix the vulnerabilities on their websites. We will leak more of their users' data (40+ million) over the next few weeks. Enjoy!"
This wasn't rage. It was disappointment masked as vindication.
What Data Was Exposed
Lovely had access to an extensive dataset. For WIRED readers specifically, the stolen information included:
- Email addresses (the most valuable piece for attackers)
- Full names
- Phone numbers
- Postal addresses
- Unique internal account IDs
- Gender information
- Birthday dates
- Account creation timestamps
- Last session timestamps
- Subscription and account-specific details
The combination of these data points creates a complete profile of each user. An attacker or criminal doesn't just get your email. They get your real name, where you live, when your birthday is, and when you last accessed your account. That's enough information to impersonate you, target you with social engineering scams, or sell your data to other criminals.
But Lovely's access went beyond WIRED. The hacker claimed to have stolen data from at least 13 other Condé Nast properties:
- The New Yorker
- Vogue
- GQ
- Vanity Fair
- Glamour
- Allure
- Architectural Digest
- Epicurious
- SELF
- Men's Journal
- Golf Digest
- Teen Vogue
- Style.com
- Condé Nast Traveler
Each publication has its own audience and database. When you combine all of them, you're looking at tens of millions of compromised records. That's why the hacker mentioned 40+ million total records, as highlighted by Security Affairs.
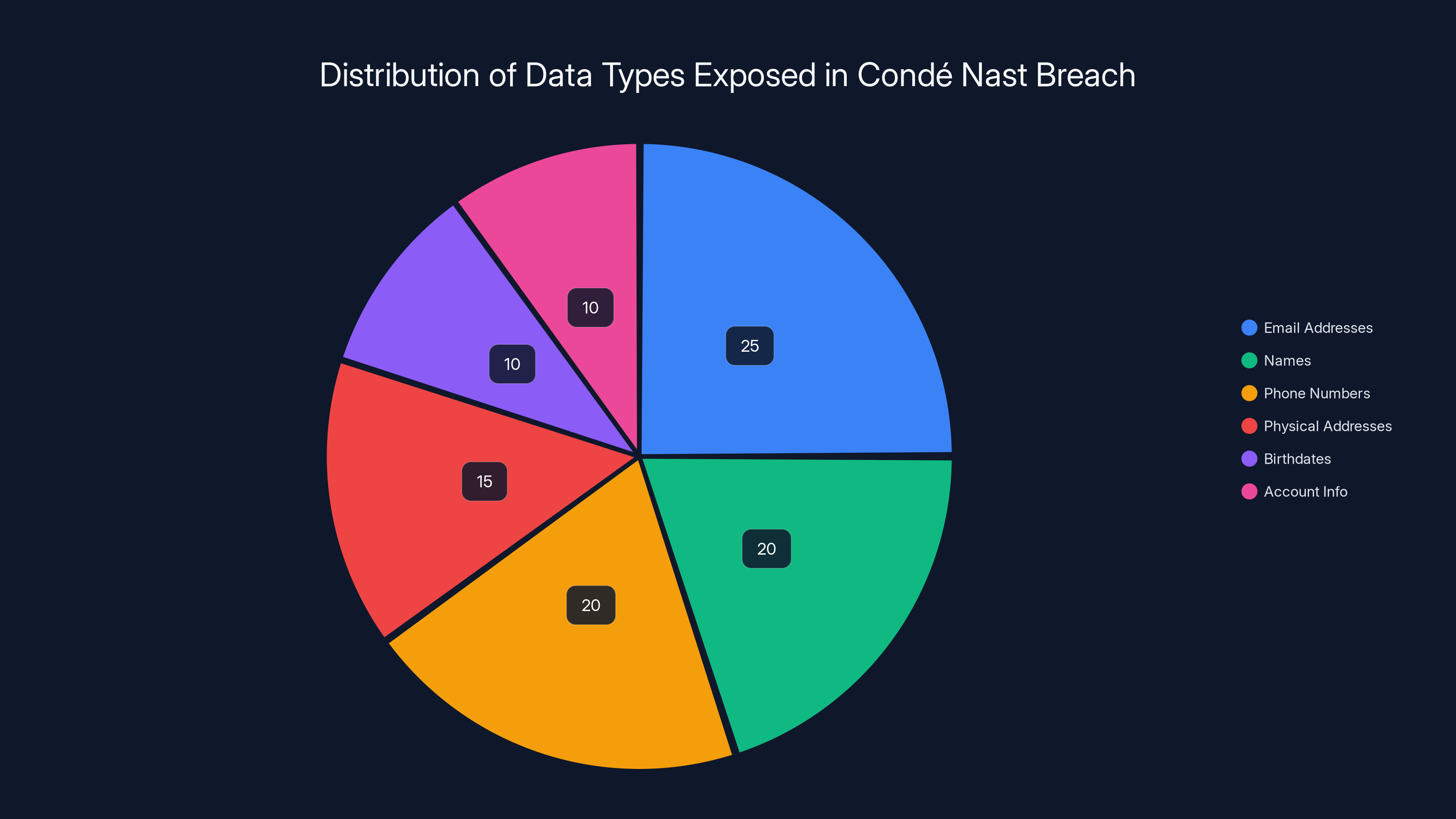
Email addresses and phone numbers constitute the largest share of exposed data, highlighting significant phishing and identity theft risks. (Estimated data)
Understanding the Attacker's Motivation
This is where the Condé Nast breach gets unusual. Most modern breaches fall into predictable categories: ransomware gangs holding data for money, state-sponsored actors gathering intelligence, script kiddies just trying to cause chaos, or opportunistic criminals looking for financial information.
Lovely presented a different narrative. According to their account, this was a responsible disclosure attempt gone wrong.
The Responsible Disclosure Attempt
Responsible disclosure is a term in cybersecurity that means: if you find a vulnerability, you tell the company about it privately, give them time to fix it, and only go public after they've patched. It's the ethical way security researchers operate.
Lovely claims they followed this playbook initially. They discovered six vulnerabilities in Condé Nast's infrastructure, reported them to the company, and waited for a response. For an entire month.
During those 30 days, according to Lovely, nothing happened. No acknowledgment from Condé Nast. No security team reaching out. No patch timeline. Radio silence.
So the attacker escalated to the next logical step: contact the media. Data Breaches.net is specifically designed to help security researchers get attention for serious issues that companies ignore. Lovely reached out with evidence of the vulnerabilities and mentioned they had data access.
That finally got someone's attention. Condé Nast was notified. The vulnerabilities started getting patched. Progress.
Frustration Turns into Leaks
But by that point, Lovely had already exfiltrated 40+ million records. Even with patches rolling out, the damage was done. The attacker had the data, and from their perspective, Condé Nast had shown they didn't take security seriously. Why sit on the data? Why let the company quietly fix things and move on without consequences?
The decision to leak wasn't random. The hacker put the data on multiple forums and made it available for a small fee in forum credits (approximately $2). This creates a few interesting dynamics:
- It's not financially motivated (few hackers would risk that kind of visibility for $2 per download)
- It's designed to cause maximum damage to Condé Nast's reputation
- It signals to other hackers that here's a tool they can use to target millions of people
Lovely's framing suggests this was about accountability. The hacker wanted to prove a point: major companies ignore security warnings, so they deserve to have their failures exposed. It's a form of digital vigilantism, as discussed in Security Boulevard.
Whether you believe Lovely's claims about good intentions or not, the outcome is the same: tens of millions of people's personal data is now in criminal hands.
The Scope and Scale of the Breach
Numbers matter when you're talking about data breaches. They help you understand whether this is a small incident or a catastrophic one. The Condé Nast breach is definitely in the catastrophic category.
40 Million Records: What That Really Means
When security experts say "40 million records," they don't just mean random data. They mean 40 million individual profiles with enough information to identify, contact, and potentially impersonate real people.
To put this in perspective, 40 million records is larger than the entire population of Canada. It's roughly equivalent to the population of California. If each of those 40 million records represents one person who read content from a Condé Nast publication, that's 40 million people whose lives are now affected.
But here's the thing that makes it worse: many of these records overlap. Someone might have accounts at both WIRED and Vogue. Another person might read The New Yorker and Golf Digest. When you buy a subscription or create an account, you're often not thinking about the central database behind the scenes.
Condé Nast runs a media empire, but from a data architecture perspective, they likely have consolidated customer information. One compromise of the right system gives attackers access to multiple publications at once, as noted by Security Affairs.
Which Publications Were Affected
We know for certain that these Condé Nast properties had exposed data:
Lifestyle and Fashion
- Vogue (print and digital)
- GQ (men's magazine)
- Glamour
- Allure (beauty and lifestyle)
- Style.com
Culture and Ideas
- The New Yorker
- Vanity Fair
- Teen Vogue
Design and Living
- Architectural Digest
- Home & Design
Food and Travel
- Epicurious
- Condé Nast Traveler
Sports and Wellness
- Golf Digest
- Men's Journal
- SELF (wellness and fitness)
News and Tech
- WIRED (2.3 million readers specifically mentioned)
If you've ever created an account with any of these publications, clicked through from a social media link, or subscribed to a newsletter, your information was likely in that database.
The Types of Data Exposed
The data Lovely extracted includes the most valuable pieces of information for attackers:
Personally Identifiable Information (PII)
- Full names
- Email addresses
- Phone numbers
- Physical addresses
- Birthdates
- Gender information
Account Information
- Account creation dates
- Last login timestamps
- Unique account IDs
- Subscription status
- Content preferences
- Reading history (potentially)
This combination is extremely valuable in the criminal marketplace. Here's why: with email, name, phone number, and address, you can execute sophisticated social engineering attacks. You can call someone impersonating their bank. You can send highly personalized phishing emails. You can run targeted scams.
The birthday and gender information adds another layer. These are commonly used as security questions. "What was your birth month?" "What is your gender?" If someone has this info, they can attempt account takeovers on other platforms.
The account creation date and last login timestamp tell attackers which accounts are active and which are dormant. They'll prioritize active accounts because they're more likely to have linked payment methods or other valuable data.
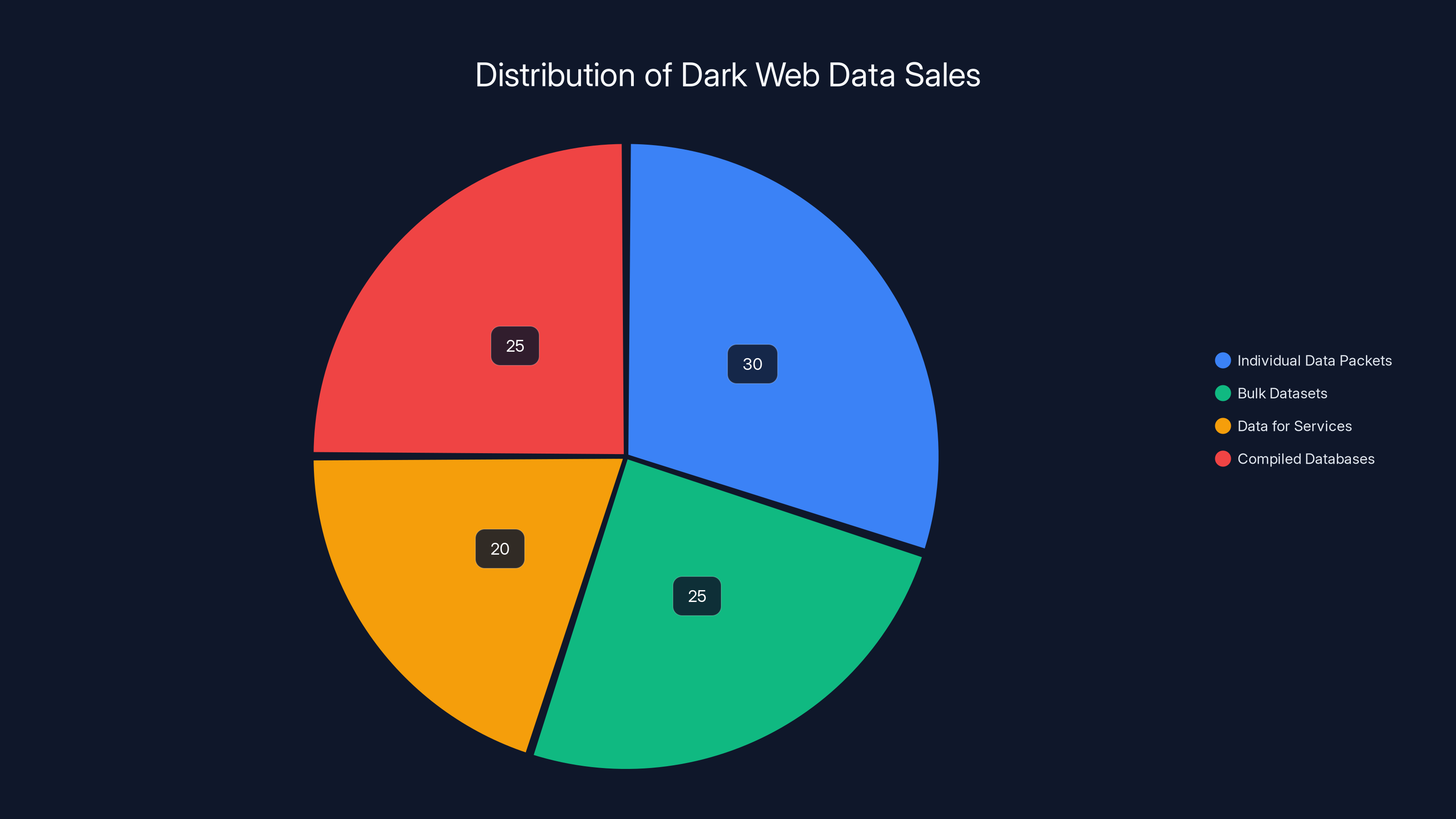
Estimated data shows that individual data packets and compiled databases each account for about 25-30% of dark web data sales, highlighting the varied methods of monetizing stolen data.
How This Type of Breach Happens: The Technical Side
Understanding how hackers get in is important because it shows you what companies should be doing to keep you safe. And it reveals why some organizations fail so badly at security.
The Six Vulnerabilities
Lovely claimed to have discovered six vulnerabilities in Condé Nast's infrastructure. We don't know the exact nature of all of them, but based on what typically gets exploited, we can make educated guesses:
SQL Injection This is a classic attack where an attacker inputs malicious code into a form field, and the application directly feeds it into a database query without proper validation. Suddenly, instead of searching for articles, the application is running the attacker's code directly in the database. From there, extracting entire customer databases is trivial.
API Authentication Bypass Many modern applications rely on APIs (application programming interfaces) for data. If the API doesn't properly validate who's making requests, an attacker can simply ask for everyone's data, and it returns everything. This is especially common when companies push updates quickly without security testing.
Unpatched Software Every software tool has bugs. When security researchers find bugs, they publish patches. Companies that don't apply those patches on time become easy targets. An attacker uses the same exploit on thousands of sites and compromises the ones that haven't patched yet.
Misconfigured Cloud Storage In 2025, most data lives in cloud services like AWS or Azure. When companies misconfigure these services, data becomes publicly accessible by accident. A researcher or attacker can simply enumerate the URLs and download everything.
Weak Authentication Default passwords. Passwords written on sticky notes. Admin accounts that nobody bothered to disable. A single compromised employee account can be the entry point for a massive breach.
Insufficient Access Controls Even if an attacker gets into the network, they should only be able to access specific data relevant to their role. If a junior developer account can access the entire customer database, that's a massive security failure.
Why It Took a Month to Fix
Here's a frustrating reality of enterprise security: even knowing there's a critical vulnerability doesn't mean it gets fixed immediately.
When a company discovers a vulnerability, they need to:
- Understand the scope - How many systems are affected? How many users? What's exposed?
- Determine the fix - Is it a simple patch? Does it require architectural changes?
- Test the fix - They can't just deploy a fix without testing, or they might break the entire service
- Coordinate the deployment - With 14 different publications running on potentially different systems, coordinating updates is complex
- Verify the fix works - After deployment, security teams need to confirm the vulnerability is actually closed
All of this takes time. A month is actually not that unusual for enterprise-level patching, especially if the fix is complex. But from an attacker's perspective—or from a concerned security researcher's perspective—a month feels like negligence.
Why Condé Nast Didn't Respond
Lovely claims they spent a month trying to get Condé Nast's attention. This raises a question: why didn't the company respond?
Possible explanations:
No Proper Security Contact Many companies don't have a clear, monitored channel for security researchers to report vulnerabilities. You might find a generic "contact us" form, but it goes to a customer service queue, not the security team.
Understaffed Security Team Condé Nast is a media company, not a cybersecurity company. They might not have the infrastructure to triage security reports quickly. A report might sit in a queue for weeks.
Internal Miscommunication Lovely contacted Data Breaches.net, which is a media site, not an official Condé Nast communication channel. It's possible the report never reached the right department.
Slow Enterprise Processes Large organizations move slowly. Even if a report reaches the right team, it might need to go through multiple approval processes before anyone can actually investigate.
The reality is likely a combination of these factors. Small companies can often respond to security reports in hours. Large enterprises can take weeks or months, especially if the report doesn't come through official channels.
The Dark Web Marketplace: Where Your Data Goes
Once Lovely leaked the data, it didn't just sit there. Hackers around the world are now using this information in various ways. Understanding the dark web marketplace helps you understand your actual risk.
How Breached Data Is Sold
The attacker posted the Condé Nast data archive on multiple hacking forums. According to reports, people could access the data by paying approximately $2 in forum credits. That's incredibly cheap, which suggests the primary goal wasn't profit.
But here's what happens next: once data is on hacking forums, it spreads. Other hackers download it, repackage it, and resell it on different platforms. What costs $2 initially might get redistributed for free or bundled with other datasets.
Within days or weeks of a major breach like this, the data enters a secondary market where:
- Individual data packets are sold: Your email and password for $0.50
- Bulk datasets are sold: "1 million emails from Condé Nast publications" for $500
- Data is traded for other hacker services: Someone might trade the Condé Nast data for access to a different company's systems
- Data is compiled into larger databases: Attackers combine this with other breaches to build more comprehensive targeting lists
The Buyer Profile
Who buys this stuff? Several types of criminals:
Phishing Specialists These attackers use your personal information to craft incredibly convincing phishing emails. Instead of generic spam, they can write: "Hi Sarah, we noticed unusual activity on your Vogue subscription from a new IP address in Russia. Click here to verify your account."
With real names and real email addresses, phishing success rates jump dramatically.
Identity Thieves With your email, name, address, phone number, and birthdate, they can apply for credit cards, loans, or open accounts in your name. Some criminals specialize in this and will focus on high-value targets.
Telemarketing Scammers Your phone number is valuable. Scammers can call pretending to be from your bank, credit card company, or favorite retailer. "We've detected fraud on your account. Please verify your information."
Data Brokers These companies buy and sell personal information legally (in most jurisdictions). They might purchase the Condé Nast data and resell it to marketers, employers, or other parties.
Ransomware Operators Even if attackers didn't originally intend to do ransomware, they can threaten to release sensitive data unless the victim pays. Email addresses and physical addresses make threatening emails more credible.
Spam and Marketing Lists Your email address is valuable for spammers and marketers. Breached email lists sell for cheap because there are millions of buyers.
How Criminals Organize
The hacking community is surprisingly organized. There are specific forums (both on the dark web and surface web) where criminals congregate. These forums have:
- Reputation systems: Users build credibility by making good trades
- Escrow services: Third parties hold money until both sides confirm the transaction
- Quality standards: Users rate datasets and report if they're outdated or invalid
- Specialization: Some forums focus on stolen credit cards, others on corporate data, others on personal information
When Lovely posted the Condé Nast data, they were essentially opening a marketplace. Now thousands of criminals have access to your information, and many of them are already devising schemes to exploit it.

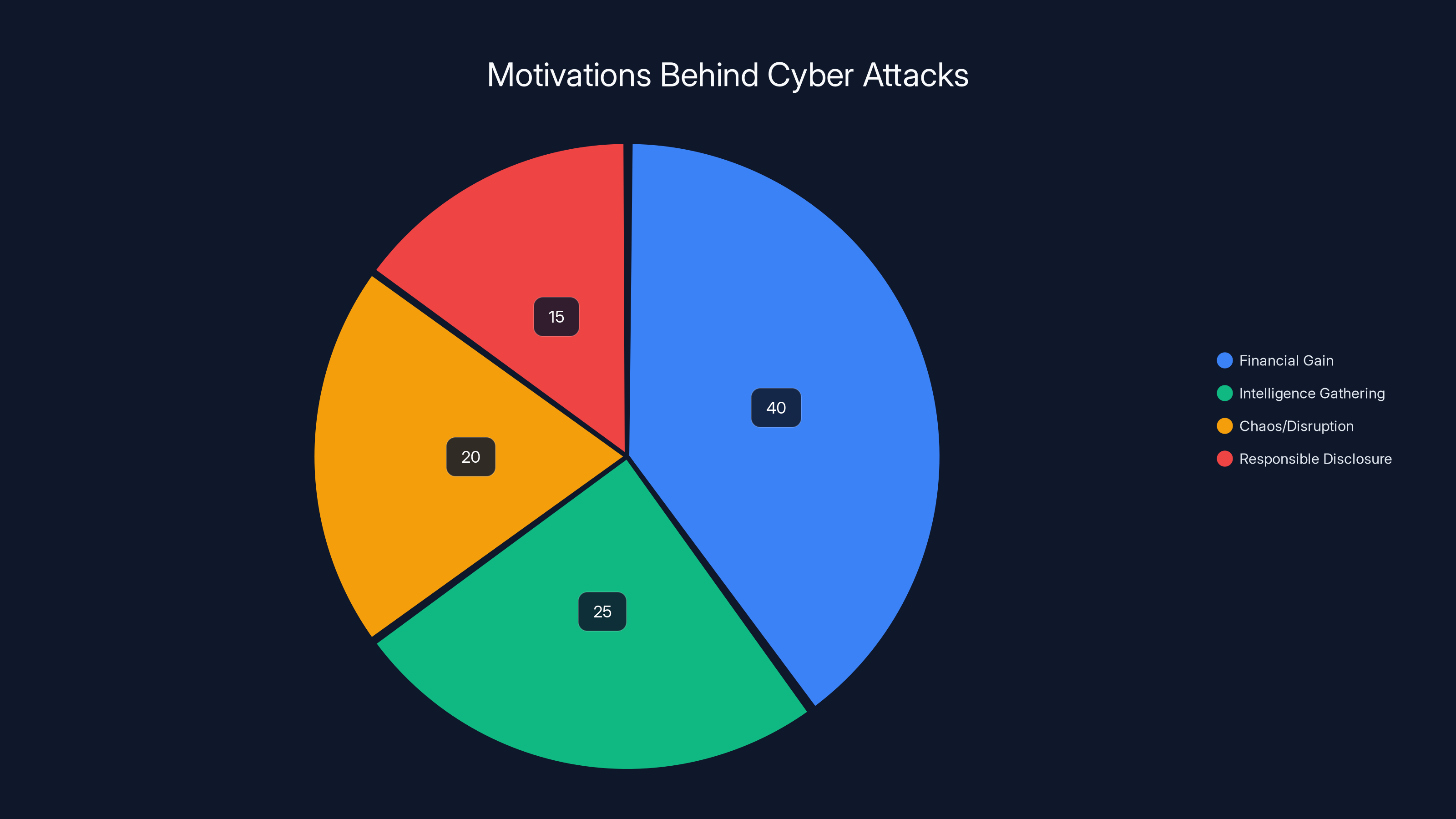
Estimated data shows financial gain as the most common motivation behind cyber attacks, followed by intelligence gathering. Responsible disclosure attempts, like the Condé Nast case, are less common.
Immediate Risks: What Attackers Can Do With Your Data
Now here's the part that matters most to you personally. If your data was part of this breach, what actually happens? What are the real, concrete risks?
Phishing Attacks (Most Common)
This is the most likely threat you'll face. Phishing attacks are emails designed to look like they're from a legitimate company but are actually trying to steal your password or information.
Before the Condé Nast breach, a phishing email might have said: "Dear valued customer, we've detected unusual activity on your account. Click here to verify."
You'd see that and think, "Which account? From which company? I have dozens of accounts." And you'd probably delete it.
Now, an attacker sends: "Hi Sarah, we've detected unusual activity on your WIRED subscription from a new IP address in Romania. Your account was accessed from a new location. Please verify your identity here: [malicious link]"
Now it's specific. Now it's credible. Now you're much more likely to click.
When you click, you land on a fake WIRED login page. You enter your email and password. The attacker captures both. Now they have:
- Your email
- Your password
- Confirmation that the email is active and monitored
From there, they can:
- Try that password on other accounts (many people reuse passwords)
- Attempt to reset your password on other services
- Check if that email is associated with payment methods or banking apps
Identity Theft
This is more complex and takes longer, but it's more damaging. An attacker uses your personal information to impersonate you and commit fraud.
With your name, address, birthdate, email, and phone number, they can:
Open Credit Accounts Call credit card companies impersonating you. "I'd like to apply for your premium card. My Social Security number is [yours]. You can reach me at [your phone number]."
If the company doesn't verify thoroughly, they approve the application. Suddenly there's a credit card in your name that you don't know about.
Get Loans Small personal loans, car loans, or even mortgage applications. Each hard inquiry damages your credit score.
Medical Identity Theft File for medical treatment using your insurance. They receive bills, you get confused. Your insurance records become contaminated.
Tax Fraud File a fake tax return and claim your refund. The IRS will eventually catch it, but sorting out the mess takes years.
Account Takeovers
If you reused your Condé Nast password across other sites, attackers can log into those accounts directly.
Your email is especially vulnerable because it's often the "master key" to your other accounts. If someone gets into your Gmail, Yahoo, or Outlook, they can:
- Reset passwords on any service tied to that email
- Access recovery emails for password resets
- View purchase histories and payment methods
- Interact with your contacts
- Restore backup codes or two-factor authentication methods
SIM Swapping
With your phone number and real name, attackers can call your mobile provider and convince them that they're you who just switched to a new phone. They request that the provider transfer your phone number to a new SIM card that the attacker controls.
Suddenly, all your two-factor authentication codes go to them, not you. They can reset any password. They can access any account protected by phone-based 2FA.
Social Engineering
Attackers use your information to build trust and manipulate you into disclosing more sensitive information.
They might call: "Hi, this is from your bank. We noticed unusual activity. Can you confirm the last four digits of your Social Security number so we can verify your identity?"
You provide them. They now have the last four digits, combined with your birthdate and address, which might be enough to attempt additional fraud.
Targeted Scams
Knowing you're a WIRED reader, they might:
- Impersonate a tech company offering free upgrades
- Pose as a cryptocurrency exchange (tech readers are seen as wealthy and tech-savvy)
- Create fake job postings or "consulting opportunities" targeting tech professionals
- Send targeted malware disguised as legitimate software updates
What Condé Nast Should Have Done (And What This Reveals)
The Condé Nast breach is a case study in what not to do. Let's break down the failures and what companies should actually do instead.
Security by Design, Not Afterthought
The fact that Lovely found six exploitable vulnerabilities suggests Condé Nast built their systems first and bolted security on later. Modern companies should build security into every layer from day one.
This means:
- Every code change gets security review
- Encryption is built in, not added later
- Access controls are strict by default
- Regular security audits (at least quarterly)
- Bug bounty programs (pay security researchers to find problems before criminals do)
Condé Nast has a global audience and handles millions of personal details. They should have treated security like core infrastructure, not a compliance checkbox.
Vulnerability Disclosure Programs
When Lovely tried to report the vulnerabilities, they had to jump through hoops. The company should have had a clear, public vulnerability disclosure program that says: "Found a security issue? Contact us here. We commit to responding within 24 hours and patching within 30 days."
Standards like Hacker One and Bugcrowd exist specifically for this. Condé Nast could have been running a bug bounty program, paying researchers to find issues, and patching them before attackers could.
Incident Response Plan
When the vulnerability was discovered, Condé Nast's response was slow. A company of that size should have an incident response plan that activates immediately.
That means:
- A dedicated security team (not shared with other departments)
- Clear escalation procedures
- Authority to implement emergency patches
- Communication templates for users
- Legal counsel ready to go
- A timeline for notification (most jurisdictions legally require notifying users within 30-60 days)
Database Isolation and Access Controls
If an attacker compromises one system, they shouldn't have automatic access to all 40 million user records. Better practices include:
- Segmenting data (customer data in one database, user preferences in another, billing in a third)
- Role-based access controls (junior employees can't access everything)
- Encryption at rest (data is scrambled when stored)
- Encryption in transit (data is scrambled when moving between systems)
- Data minimization (only collect and store data you actually need)
Monitoring and Detection
An attacker extracting 40+ million records should show up on monitoring systems. Data exfiltration creates patterns:
- Unusual database queries
- Large data transfers
- Access from unfamiliar IP addresses
- Activities outside normal business hours
Condé Nast apparently didn't have monitoring sophisticated enough to catch this, even though the breach happened before Lovely went public with it.
User Notification and Support
Once a breach is discovered, companies should:
- Notify users quickly (not weeks later)
- Be transparent about what was exposed
- Provide clear guidance on what users should do
- Offer free credit monitoring and identity theft protection
- Create a dedicated support line for affected users
Condé Nast's response has been relatively quiet, which leaves users uncertain about their own risk.
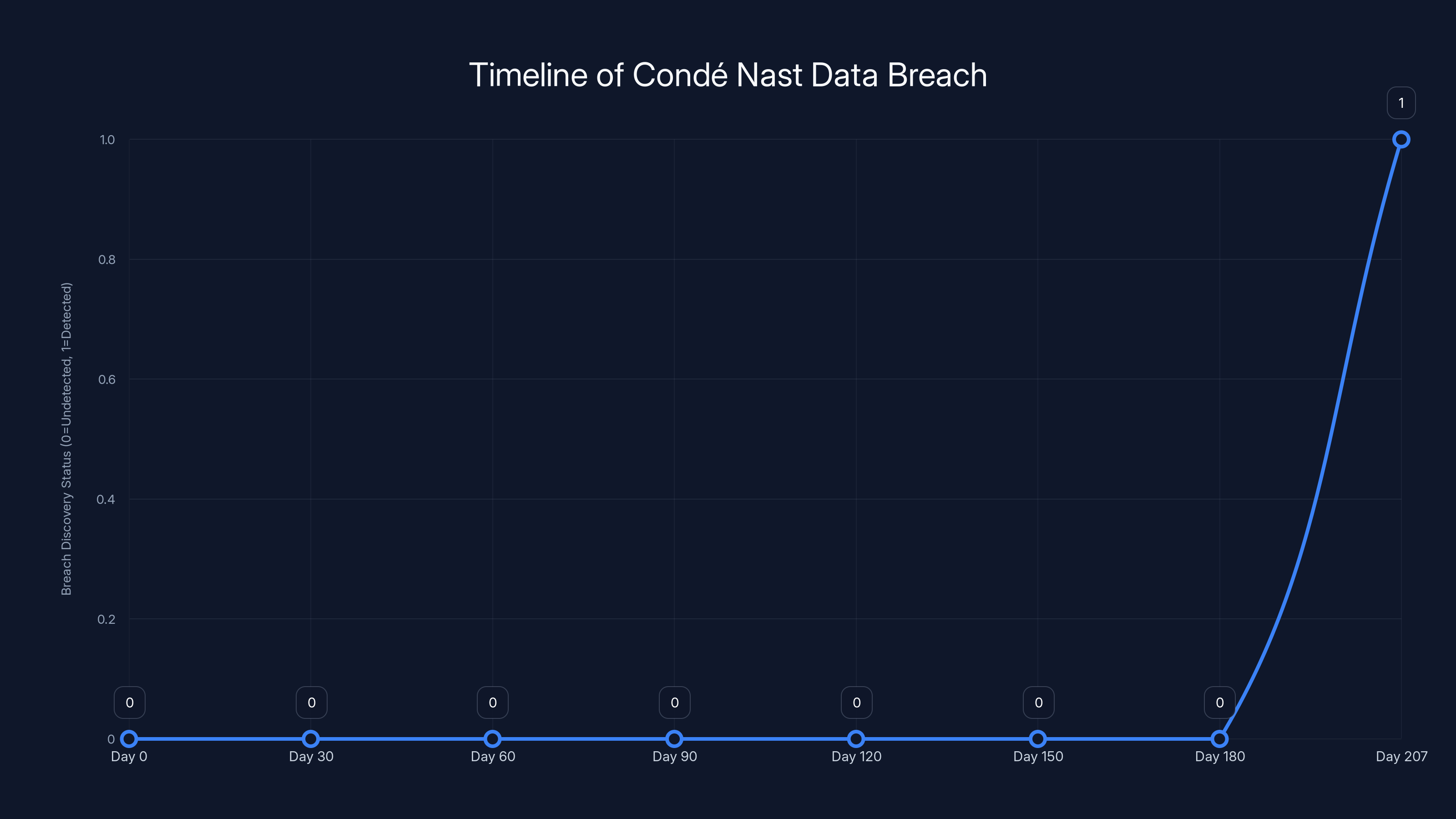
Estimated data shows that without the hacker's intervention, Condé Nast's breach might have gone undetected for the industry average of 207 days.
How to Protect Yourself Right Now
Let's move from theory to action. If you're affected by the Condé Nast breach (or any breach), here's exactly what you should do.
Step 1: Change Your Password Immediately
If you had an account with any Condé Nast publication, change your password today.
Make it:
- At least 16 characters (longer is better: 20+ is ideal)
- Random (use a password manager, not something you can remember)
- Unique (never reuse passwords across sites)
- Complex (mix of letters, numbers, and symbols)
Bad password: "Vogue 2024!" (Dictionary word + year + predictable)
Good password: "x$K9m P@2q L#v N8r T" (Completely random, generated by a manager)
Password managers like Bitwarden, 1 Password, or Last Pass generate strong passwords and remember them for you. You only have to remember one master password.
Step 2: Enable Two-Factor Authentication (2FA)
2FA means even if someone has your password, they can't access your account without a second form of verification.
Types of 2FA (in order of security):
- Authenticator Apps (Best): Use Google Authenticator, Microsoft Authenticator, or Authy. You get a code that changes every 30 seconds.
- Backup Codes: Print these and store them safely. Use if you lose access to your authenticator.
- SMS Text Messages: Less secure (susceptible to SIM swapping) but better than nothing.
- Email Codes: Better than SMS but slower.
- Security Keys: Physical USB devices that prove it's really you. Extremely secure but less convenient.
Combine methods. Use an authenticator app as your primary method, SMS as a backup.
Step 3: Check for Compromise
Use a service like Have IBeen Pwned.com (created by security researcher Troy Hunt) to check if your email appears in known breaches.
Don't trust email notifications claiming to check this for you—scammers use these to harvest credentials. Go directly to the site and enter your email.
You're not looking to "uncompromise" yourself. You're looking to know which companies have failed to protect your data so you can take appropriate precautions.
Step 4: Monitor Your Accounts for Activity
Set up monitoring for:
Credit Monitoring Check your credit reports at Annual Credit Report.com (legally free once per year in the US). Look for:
- Accounts you didn't open
- Inquiries you didn't authorize
- Address changes you didn't make
Consider using services like Credit Karma or Creditwise for continuous monitoring (often free).
Bank and Credit Card Accounts Review statements monthly. Set up alerts for:
- Large purchases
- Online purchases
- Purchases in different regions
- Account changes (address, phone number)
Email Account Check the "Security" section. Look at:
- Recent login activity
- Connected devices and apps
- Recovery email and phone number (make sure you recognize them)
Social Media Review login activity and connected apps. Remove access for apps you no longer use.
Step 5: Consider Freezing Your Credit
A credit freeze prevents anyone (even you) from opening new accounts in your name without unfreezing it first. It costs nothing and takes 10 minutes.
Request a freeze from all three bureaus:
- Equifax: equifax.com/personal/credit-report-services/credit-freeze/
- Experian: experian.com/freeze/center.html
- Trans Union: transunion.com/credit-freeze/place-credit-freeze
When you want to open a new account (mortgage, car loan, credit card), temporarily unfreeze, apply, then refreeze.
This is your best defense against identity theft.
Step 6: Be Vigilant About Phishing
With your personal information in criminals' hands, you'll likely receive phishing emails.
Red flags:
- Generic greetings ("Dear Customer" instead of your name—though better phishing uses your real name)
- Urgent language ("Act now," "Verify immediately")
- Unexpected login requests
- Typos or awkward phrasing
- Links that don't match the sender's domain
- Requests for sensitive information
- Offers that seem too good to be true
If you're unsure:
- Don't click any links in the email
- Don't call any numbers provided
- Go directly to the company's official website
- Contact them through the phone number on your account statement
Remember: legitimate companies will never ask you to verify your password via email.
Step 7: Strengthen Other Accounts
If you used the same password on your Condé Nast account and other sites, change those passwords too.
Start with high-value accounts:
- Email (the master key to everything)
- Banking and credit cards
- Crypto exchanges
- Cloud storage
- Social media
- Streaming services
- Work accounts
Then gradually work through lower-priority accounts.

What About Solutions Like Runable for Business Data Security?
If you work for a company handling sensitive data, this breach should be a wake-up call about automation and documentation.
Many breaches happen because security processes are manual and ad-hoc. Condé Nast likely doesn't have automated systems for:
- Detecting unusual data access patterns
- Enforcing consistent password requirements
- Automatically rotating credentials
- Documenting all system access
- Alerting security teams to anomalies
Businesses looking to strengthen their security posture can use automation platforms to create standardized, documented, auditable security workflows. This doesn't replace a dedicated security team, but it makes sure security processes are consistent, monitored, and transparent.
Automation helps with:
- Incident response workflows: When a breach is detected, automatically lock accounts, notify teams, and generate incident reports
- Security documentation: Maintain detailed records of who accessed what, when, and why
- Compliance reports: Generate SOC 2, HIPAA, or GDPR compliance documentation automatically
- Access reviews: Automate the process of reviewing user permissions and access rights
Companies that treat security as a continuous, automated process instead of a checkbox compliance task are much less likely to suffer breaches like this.

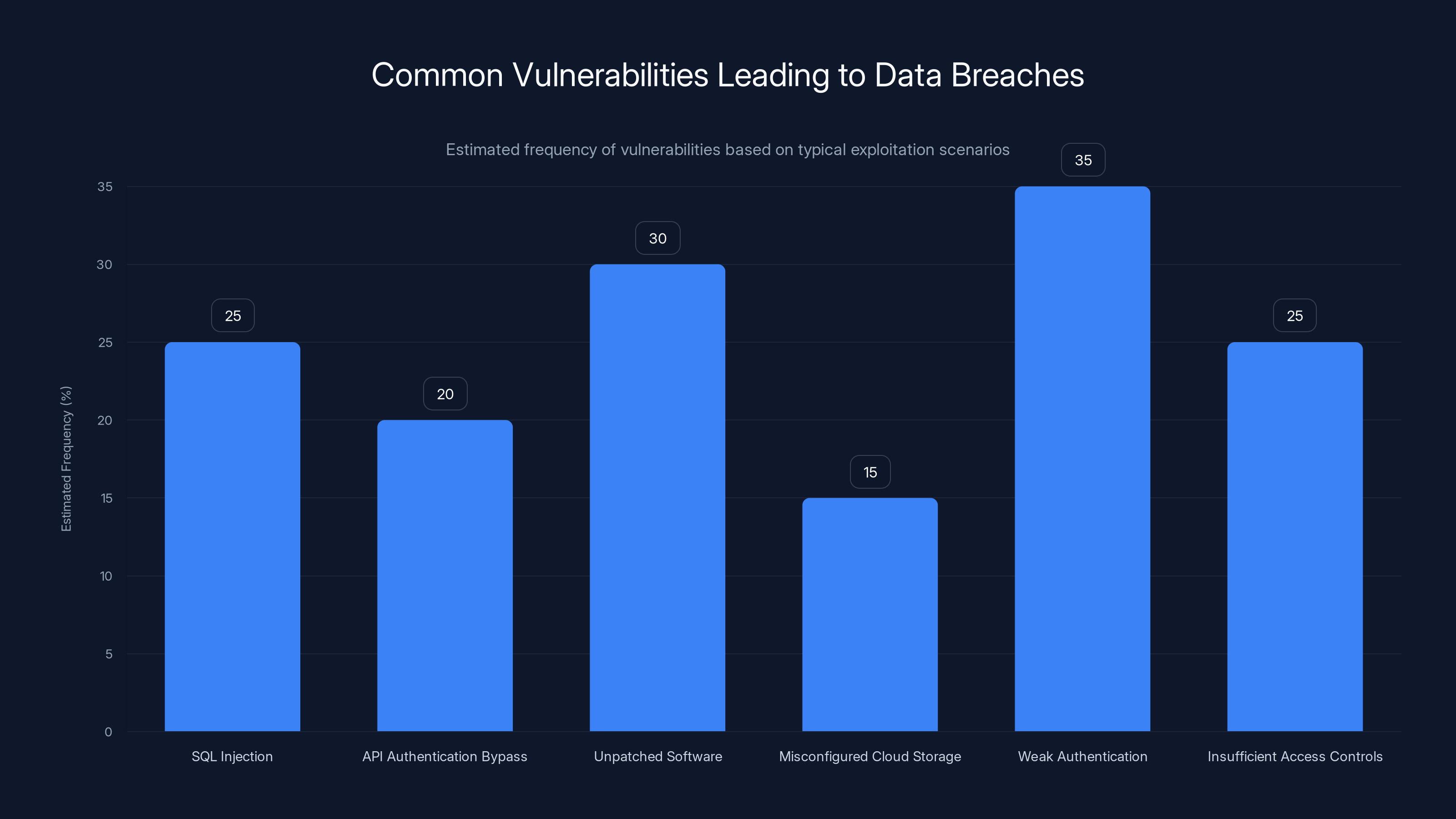
The chart estimates the frequency of different vulnerabilities exploited in data breaches. Weak authentication and unpatched software are common entry points. Estimated data.
The Bigger Picture: Why Companies Keep Getting Breached
The Condé Nast breach isn't an isolated incident. It's part of a pattern. Understanding that pattern helps you understand your actual risk in the modern world.
The Incentive Problem
Companies don't invest heavily in security until they're forced to. Why? Because security doesn't generate revenue. A million-dollar security investment doesn't translate to more sales or profit.
The math looks like this:
- Cost to prevent a breach: $5 million (better security team, tools, processes)
- Probability of being breached: 5-10%
- Cost if breached: $50 million (fines, lawsuits, credit monitoring, reputation damage)
- Expected loss without security: $2.5-5 million
Logically, you should spend
It's only when they get breached that they become serious about security. And then they move on to the next crisis.
The Speed vs. Security Trade-off
Big media companies are pushing new features constantly. They're competing with Netflix, Substack, and other platforms for attention. Speed wins attention. Security slows you down.
A feature that takes 2 weeks to develop might take 4 weeks if you do proper security review. From a business perspective, that's unacceptable. So companies skip the security review.
Some organizations deliberately choose to "ship fast and fix security issues later." This works until a Lovely decides to teach them a lesson.
The Talent Problem
Good security engineers are expensive and hard to find. A senior security engineer in a major city costs
Condé Nast likely doesn't have the security depth that Google, Microsoft, or Amazon have. With smaller teams, security becomes reactive instead of proactive.
The Complexity Problem
Condé Nast runs 14+ different publications. Each might have different websites, CMS platforms, databases, and infrastructure. Securing one system is hard. Securing 14 interconnected systems is exponentially harder.
This is why large-scale breaches are common for companies with legacy, fragmented IT infrastructure. They have gaps everywhere.
The Third-Party Problem
Condé Nast doesn't build all their own systems. They use Word Press, Drupal, various payment processors, analytics platforms, and cloud services.
If any of those third parties is compromised, Condé Nast is vulnerable. This is called "supply chain security" and it's incredibly difficult to manage.
Future Trends: More Breaches Like This Are Coming
Unfortunately, the Condé Nast breach is probably not an anomaly. Several trends suggest more major breaches are inevitable.
AI-Powered Vulnerability Discovery
Artificial intelligence is getting better at finding security vulnerabilities. Tools that automatically scan code for flaws are improving rapidly. This means attackers armed with AI will find vulnerabilities faster than companies can patch them.
Ransomware Evolution
Modern ransomware gangs aren't just encrypting data and demanding payment. They're exfiltrating data, threatening to release it publicly unless you pay, and sometimes leaking it anyway. The playbook is: demand ransom, leak anyway, repeat with another victim.
Insider Threats
Sometimes the attacker is an employee. Disgruntled developers with access to databases are less likely to be caught than external attackers. We'll likely see more breaches where the attacker is someone who worked for the company.
Supply Chain Attacks
Why hack a major company directly when you can hack their vendors? Attack a smaller vendor that manages data for dozens of companies, and suddenly you have massive leverage.
Nation-State Interest
Media companies like Condé Nast are interesting to governments. Journalists, political figures, and celebrities subscribe to these publications. Governments might breach them to gather intelligence on who reads what.
Blockchain and Decryption
As quantum computers improve, encryption standards that are secure today might become breakable. Companies that store encrypted data today could see that data decrypted in 10-20 years.

What Regulations Are Missing
Governments are starting to crack down on negligent data security. But the regulations are still lagging.
GDPR (Europe)
Under GDPR, companies must notify users of breaches within 30 days and face fines up to 4% of annual revenue if negligent. This is strong, but it's only in Europe.
State Laws (US)
Each US state has different data breach notification laws. California's newer regulations are stricter, but there's no federal standard. Condé Nast has to comply with 50 different state laws.
What's Missing
- Mandatory security standards: Companies should be required to meet specific benchmarks
- Security audits by regulators: Regular government inspections of security infrastructure
- Executive liability: CEOs and board members should face personal liability if their companies negligently expose data
- Mandatory breach insurance: Companies handling sensitive data should be required to carry cyber insurance
- Public breach registries: A centralized database of all breaches to make companies accountable
Without these, companies will keep taking risks and hoping they don't get breached.
Key Takeaways and Action Items
Here's what you need to do right now:
Immediate Actions (This Week)
- Change your Condé Nast password if you had an account
- Enable two-factor authentication on your email account
- Check your credit report at Annual Credit Report.com
- Set up one fraud alert or credit freeze
- Review recent account activity on your important accounts
Short-Term Actions (This Month)
- Create a password manager if you don't have one
- Update passwords on your top 10 most important accounts
- Enable 2FA on all accounts that offer it
- Document your security settings (backup codes, recovery emails)
- Set up account monitoring on your email and banking
Long-Term Changes (Ongoing)
- Use unique passwords everywhere (via a password manager)
- Keep software updated automatically
- Be skeptical of unexpected communications
- Monitor your credit regularly
- Review your digital footprint (what accounts do you actually need?)
FAQ
What exactly was exposed in the Condé Nast breach?
The hacker "Lovely" exposed over 40 million records including email addresses, names, phone numbers, physical addresses, birthdates, account creation dates, and last login information for users of WIRED, Vogue, The New Yorker, GQ, and 10+ other Condé Nast publications. The most valuable piece for attackers is the combination of email address and phone number, which enables phishing, SIM swapping, and identity theft attempts.
How did the hacker gain access to 40 million records?
According to the attacker, they discovered six vulnerabilities in Condé Nast's security infrastructure, likely including SQL injection, API authentication bypass, misconfigured cloud storage, or unpatched software. Rather than exploit the vulnerabilities immediately, the hacker initially tried to contact Condé Nast responsibly to report the issues. Only after a month of being ignored did they exfiltrate the data.
Should I be worried if my data was part of this breach?
Yes, but thoughtfully, not panic. With your personal information in criminal hands, you face elevated risk of phishing attacks, identity theft attempts, SIM swapping, and targeted scams. The risk is real but manageable with the protective steps outlined above. Start with changing passwords, enabling 2FA, and monitoring your accounts.
Can I sue Condé Nast for the breach?
Possibly, but it's complicated and expensive. You'd likely need to join a class action lawsuit. These typically result in settlements where affected users get small amounts (often less than $100) and lawyers get millions. Some users might have additional claims if they experienced identity theft or fraud as a direct result of the breach.
Will this happen to other companies?
Absolutely. Major breaches affecting tens of millions are becoming routine. In 2023-2024, we saw breaches at Snowflake, MOVEit, CDK Global, and countless others. The Condé Nast breach isn't unique—it's part of a pattern. Companies at scale are attractive targets, and many don't invest sufficiently in security until after they're breached.
How long will my data circulate on the dark web?
Permanently. Once data is leaked, it's out there forever. Your information might be sold and resold multiple times. However, the risk is highest in the weeks and months immediately after the breach, when criminals are most actively using it. The risk decreases over time as data becomes less fresh and criminals move on to newer breaches.
Is there a way to get my data removed from dark web forums?
Not really. You can't delete something once it's been copied and distributed across thousands of criminal forums. Your best approach is defense: monitoring, strong passwords, 2FA, and credit freezes. You're trying to make yourself a harder target than the next person.
What should I do if I receive a suspicious email claiming to be from Condé Nast or related companies?
Don't click any links or download any attachments. Don't call any phone numbers provided in the email. Instead, go directly to the company's official website or use the phone number from your account statement. Many criminals use breaches like this as a springboard for phishing—they know exactly which companies to impersonate and which users to target.
How can I check if my email was part of the Condé Nast breach specifically?
Use Have IBeen Pwned.com and search your email address. It will show all known breaches affecting that email. Go directly to the site—don't click links in emails claiming to check this for you, as those are often phishing attempts themselves. You can also enable notifications so you're alerted if your email appears in future breaches.
Should I get identity theft protection or credit monitoring service?
Credit monitoring is worth considering if you didn't freeze your credit, though many are available free from credit bureaus or your bank. Identity theft protection services vary widely in quality and cost. A credit freeze is your strongest defense and costs nothing. If you've experienced fraud, then paid services become more valuable since you'll need help recovering from it.
Conclusion
The Condé Nast breach involving 40+ million records is a watershed moment in data security. It's simultaneously a failure of corporate responsibility and a cautionary tale for anyone who has ever created an online account.
What makes this breach particularly instructive is the transparency around its cause. A security researcher discovered serious vulnerabilities, gave Condé Nast a month to patch them, escalated to the media when ignored, and only leaked data out of frustration. This isn't a sophisticated nation-state attack or random cybercriminal opportunism. It's a single person, armed with legitimate security knowledge, deciding to teach a lesson to a company that didn't take security seriously.
The reality is that Condé Nast is far from alone. Countless companies—maybe thousands—are running with similar vulnerabilities right now. Many haven't been found. Others have been found but not patched. Still others know about the issues but are too slow to fix them.
From Condé Nast's perspective, this is a catastrophic failure. It will cost hundreds of millions in lawsuits, settlement payments, credit monitoring, and reputation damage. It will force an organizational overhaul of their security practices. It will be studied in business schools as an example of how not to handle security.
From your perspective, the breach should prompt action, not panic. Your data is out there. You can't change that. But you can make yourself a much harder target through the protective steps outlined above. Strong, unique passwords. Two-factor authentication. Credit freezes. Monitoring. Skepticism about unexpected communications.
These aren't perfect defenses. They're practical, achievable steps that reduce your risk significantly. A criminal might still target you, but when they find you have 2FA enabled and a credit freeze in place, they'll likely move on to someone easier.
The broader lesson for companies is this: security isn't something you bolt on after the fact. It's something you build in from the beginning. It's not a cost center. It's a business necessity. And when researchers try to help you, respond. Fast.
For individuals: assume your data has been breached somewhere. It probably has. Act accordingly. The Condé Nast breach is just this month's headline. By next month, there'll be another one, and another after that. The question isn't whether your data will be compromised. It's whether you're prepared when it is.
Related Articles
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- 1Password 50% Off Holiday Deal: Complete Guide to Password Manager Savings [2025]
- The Complete Guide to Breaking Free From Big Tech in 2026
- GPS Jamming: The Vulnerability Threatening Modern Infrastructure [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- SMS Scams and How to Protect Yourself: Complete Defense Guide [2025]
![Condé Nast Data Breach: 40 Million Records Exposed [2025]](https://tryrunable.com/blog/cond-nast-data-breach-40-million-records-exposed-2025/image-1-1767037072840.jpg)



