Introduction: The Year Everything Changed
Something shifted online in 2025, and most people didn't even notice it happening. Age verification went from being a niche regulatory hassle to becoming the default way the internet works. By the time 2026 rolled around, you couldn't watch certain videos, access social platforms, or browse adult content without proving who you are. And that's changed everything.
I'll be honest, when I first started researching this, I thought it was just another privacy scare story. But the more I dug into the actual implementation across different countries and platforms, the more it became clear: this isn't hyperbole. This is a fundamental restructuring of how the internet works, how your data moves around, and who gets access to your personal information.
The thing that caught me most was how quickly it happened. A few years ago, age verification online was clunky, expensive, and rarely enforced. Then came the regulatory pressure from the EU, UK, Denmark, Finland, and other countries. Social media platforms started getting fined billions. Content platforms faced legal liability. And suddenly, investment flooded into age verification technology. By 2025, the infrastructure was there. By 2026, it became unavoidable.
What makes this different from other digital regulations is the scale and the scope. We're not talking about GDPR, which affected data privacy practices. We're talking about a requirement that billions of people authenticate their age online, which creates an entirely new layer of digital identity infrastructure. And that infrastructure collects data. Lots of it.
In this guide, we're going to walk through exactly what changed, why it happened, and what the privacy implications actually are. We'll look at which countries are leading the charge, how the technology works, what data it collects, and what you can actually do about it. Because here's the reality: age verification isn't going away. But understanding it is your best defense.
TL; DR
- Age verification mandates went global in 2025: The EU, UK, and 15+ countries now require verification before accessing adult content and social platforms, creating unprecedented identity tracking systems.
- Your data is being collected at massive scale: Verification providers store biometric data, government IDs, and behavioral patterns, creating honeypots for hackers and governments.
- Privacy risks tripled in 2026: Data breaches at verification platforms expose entire populations; governments can subpoena records; third-party brokers buy and sell verification history.
- VPNs and privacy tools offer partial protection: Location spoofing helps bypass geographic restrictions, but verification data still flows through verification companies regardless of privacy tools.
- The regulatory landscape is fragmented: Different countries use different systems, creating opportunities for data arbitrage and conflicting privacy standards across borders.
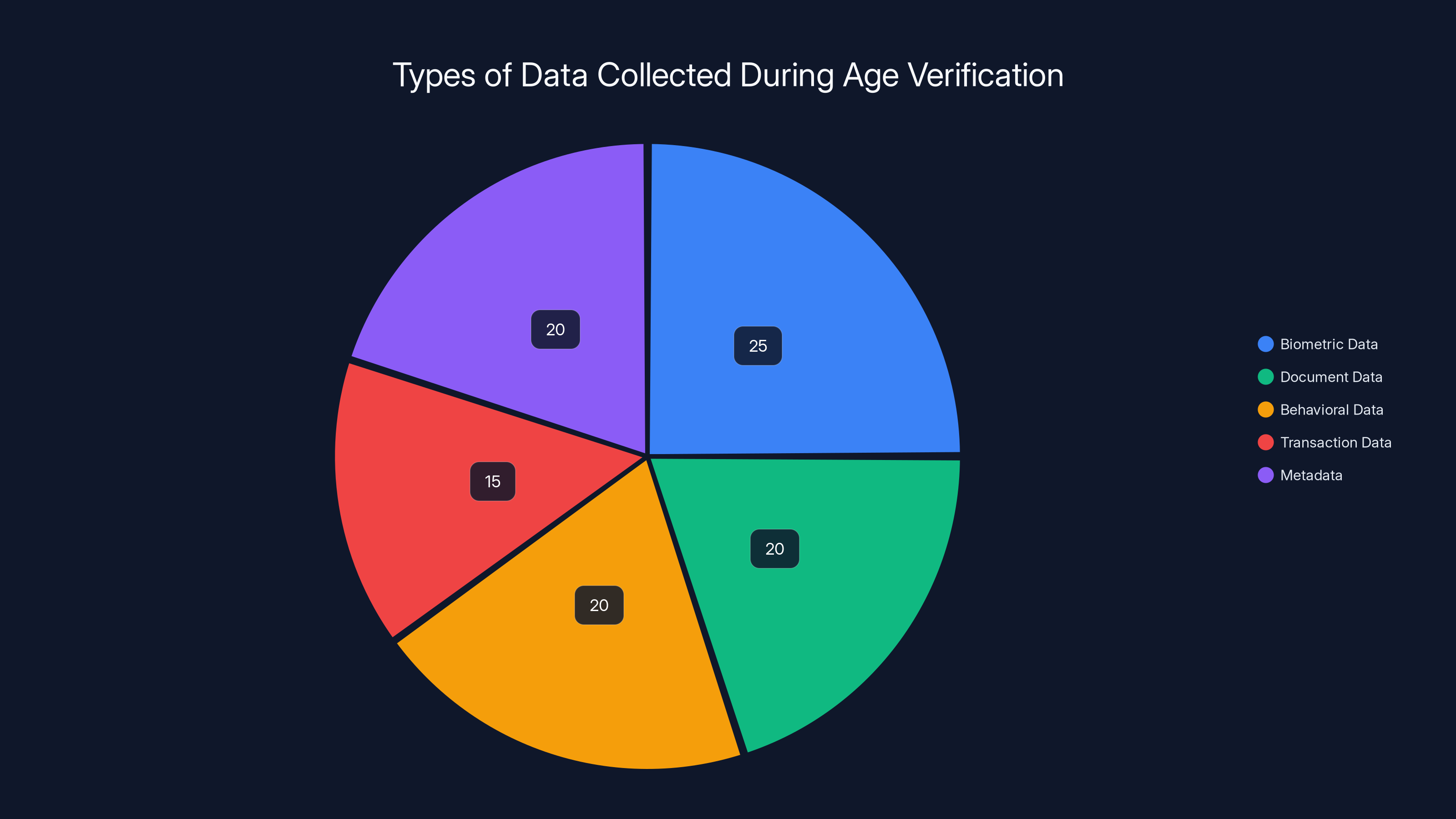
Estimated data shows biometric and document data are the largest components collected during age verification, each constituting around 20-25% of the total data profile.
How Age Verification Took Over the Internet
The story of how we got here isn't really about technology at all. It's about regulation, liability, and money.
Back in 2023 and 2024, governments started taking online harm seriously. The Online Safety Bill in the UK, the Digital Services Act in the EU, laws in Denmark and Finland—they all shared a common thread. If social media platforms and adult content sites didn't protect minors from harmful content, those platforms would face massive fines. We're talking billions of dollars in liability.
At the same time, there was a moral panic around child safety online. Parents worried about their kids accessing adult content. Schools worried about social media algorithms pushing extreme content to minors. Governments worried about both. The solution everyone landed on was simple: verify age before access.
The problem was implementation. Age verification is expensive and complicated. You need infrastructure. You need data security. You need compliance across multiple jurisdictions. Most platforms didn't have that capability. So governments started mandating it, and suddenly there was massive investment in verification technology.
By late 2024, you had companies like Onfido, Intellinetics, and dozens of others racing to build verification systems at scale. They weren't starting from zero—some of this technology existed in the financial sector and border control. But adapting it for the consumer internet was new.
By mid-2025, major platforms started rolling out verification requirements. Tik Tok, Instagram, and Snapchat began asking users in certain regions to verify age. Adult content platforms shifted from self-certification to actual verification. And by the end of 2025, it became the norm rather than the exception.
What surprised most people was how fast this became the status quo. Within a year, having a verified age online became almost as normal as having a credit card number. The infrastructure was there. The legal requirement was there. And most people just accepted it without thinking about what data was flowing where.
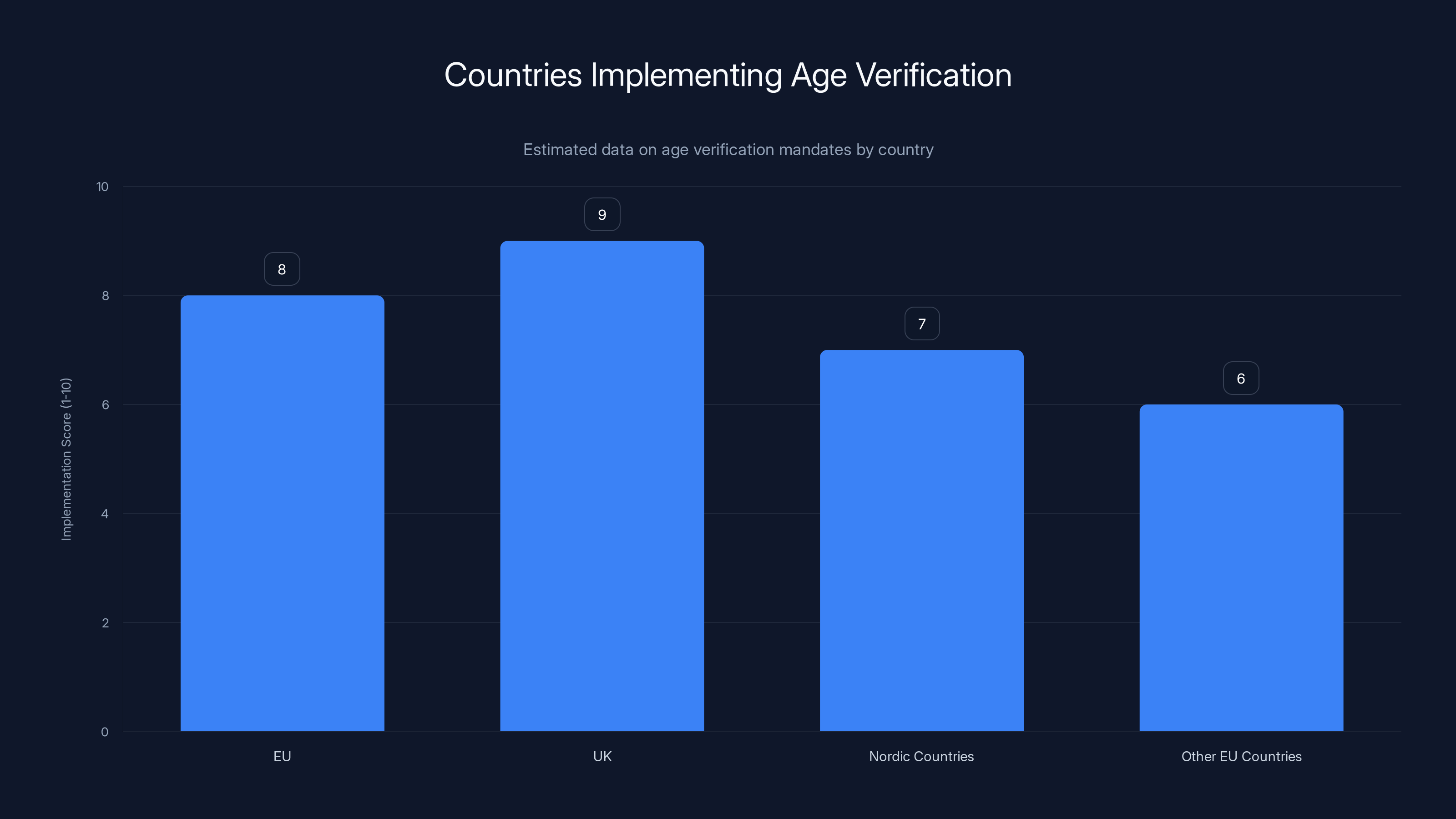
The UK and Nordic countries lead in strict age verification mandates, with high implementation scores. Estimated data.
Which Countries Are Requiring Age Verification
Age verification isn't a global mandate. It's a patchwork of different regulations across different regions. But that patchwork is expanding fast, and the countries leading the charge tell us a lot about where the internet is heading.
The European Union: Leading the Way
The EU didn't invent age verification mandates, but they made them inevitable. The Digital Services Act, which came into force in 2024, gives the EU massive power over how platforms operate. If platforms don't verify age effectively, they face fines up to 6% of global revenue. For Meta, that's billions. For smaller platforms, it's existential.
Denmark, Finland, Norway, Sweden, and other Nordic countries went even further. They didn't just require age verification for adult content—they started requiring it for social media platforms period. The reasoning was that algorithmic recommendation systems were harmful to minors, and the only way to protect them was to verify age before access.
What's notable about the EU approach is that it's decentralized. There's no EU-wide age verification system. Instead, each country implemented its own approach, leading to fragmentation. A teenager in Germany might verify age through one system, while a teenager in the Netherlands uses a completely different system. This fragmentation creates security vulnerabilities and data redundancy.
The United Kingdom: Post-Brexit Autonomy
After Brexit, the UK went its own path on digital regulation. The Online Safety Bill, which came into force in 2025, includes some of the strictest age verification requirements in the world. The UK doesn't just require age verification—it requires that platforms take "reasonable measures" to verify actual age, which the regulator interpreted as meaning government-backed identification or biometric verification.
This created a unique situation. Unlike the EU, where different systems coexist, the UK pushed toward a more centralized approach. There's been discussion of a "digital ID" system for the entire population, which would make age verification seamless but would also create a single point of failure for privacy.
Singapore, Australia, and Other Asian-Pacific Countries
Singapore implemented age verification requirements in 2025, not primarily for child protection but for content control. Singapore's approach is different—it's less about protecting minors and more about controlling what content citizens can access. This matters for privacy because it means the motivation is surveillance, not safety.
Australia followed suit with mandatory age verification for adult content sites and social media platforms. New Zealand did the same. The implementation in these countries is notable because they don't have unified privacy standards with Europe, creating legal conflicts for platforms operating globally.
Countries Without Formal Mandates (Yet)
Canada, Mexico, and most of the United States don't have formal national age verification mandates. But that's changing. California passed legislation requiring age verification for social media platforms and adult content sites. Other states are following suit. At the federal level, there's been serious discussion of a national digital ID system that would make age verification trivial.
Mexico doesn't have formal mandates, but platforms operating in Mexico are increasingly adopting verification systems due to international pressure and platform policy requirements.
The Technology Behind Age Verification: How It Actually Works
Most people assume age verification is simple. You enter your birth date, and you're done. That's not what's actually happening.
Real age verification systems use one of three approaches: document-based verification, biometric verification, or behavioral verification. Let me break down each one and what data it collects.
Document-Based Verification
This is the most common approach. You take a photo of your government-issued ID—passport, driver's license, national ID card—and upload it to a verification platform. The platform uses optical character recognition (OCR) to extract your name, date of birth, and other information from the ID. Then it cross-references that data with other databases to confirm you are who you claim to be.
The problem: your ID is now stored somewhere. On a platform's servers. And that data is sensitive. It includes your full name, date of birth, ID number, and sometimes your address. If that platform gets hacked, your entire identity is compromised.
Worse, platforms don't always delete this data after verification. Some keep it indefinitely for regulatory compliance. Some sell it to third parties. Some share it with governments on request.
Biometric Verification
This is the newer approach, and it's spreading fast. Instead of uploading your ID, you record a video of yourself. The platform uses facial recognition to confirm that the person in the video is the same person in the ID photo. Some systems also use liveness detection to make sure you're not using a deepfake or a photo.
Biometric verification is more secure than document verification—it's harder to fake a video than a photo. But it's also more invasive. Your facial biometric data is now stored on a platform's servers. If that gets leaked, hackers can create deepfakes of you. Governments can use it for surveillance.
And here's the thing: unlike your ID number, you can't change your face. If your facial biometric is compromised, that's permanent.
Behavioral Verification
This is the creepiest approach, and it's the one most people don't even know exists. Instead of verifying your identity, behavioral verification works by analyzing your online behavior patterns. How you type. How you move your mouse. Your browsing history. Your social media activity.
Some platforms use behavioral verification as a secondary check. If your behavior matches a known minor, you get restricted access. Some use it as the primary mechanism.
The problem: behavioral verification is incredibly invasive. It requires constant tracking. And it's also less accurate—behavioral patterns can be spoofed, and minors' behavior doesn't always look different from adults' behavior.
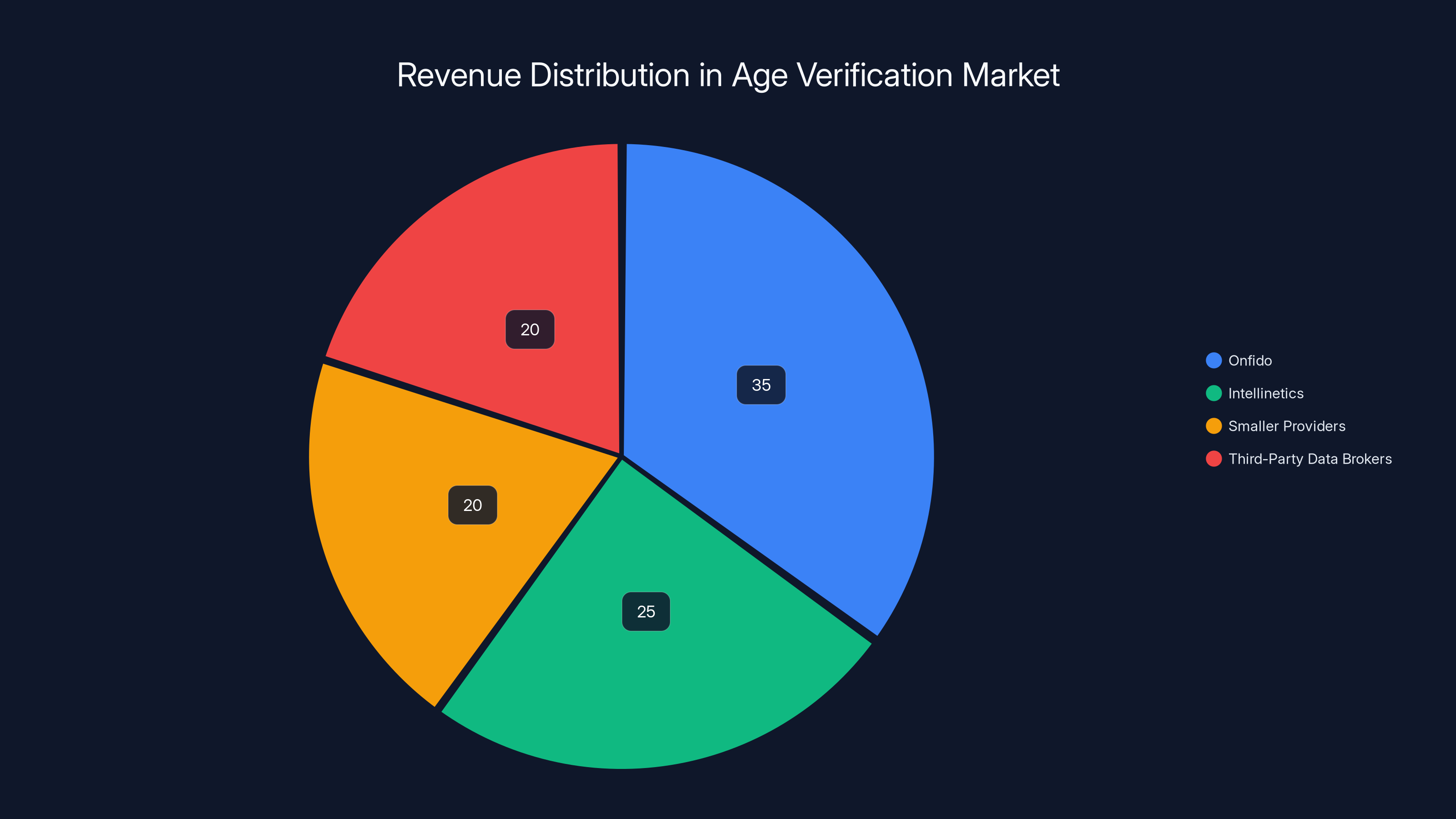
Onfido and Intellinetics lead the age verification market, but smaller providers and data brokers also hold significant shares. (Estimated data)
What Data Is Actually Collected
This is where things get really concerning. Age verification doesn't just collect your age. It collects a complete digital identity profile.
The Data Chain
When you verify your age on a major platform, here's what happens. First, your data goes to a verification provider like Onfido or similar service. They store your ID information, biometric data, and transaction records.
Then, that data flows to the platform you're accessing. Tik Tok, Instagram, or whoever. They store records of your verification, timestamp, and location.
Then, if there's a legal request from a government, that data flows to law enforcement.
Then, if the verification provider gets hacked, that data flows to criminals.
And at every step, third parties might buy or access that data. Data brokers are already building profiles on who verified with which platform at what time. They're cross-referencing this data with other behavioral data to build more complete profiles.
Specific Data Points Collected
Here's what verification platforms actually store:
- Biometric data: Facial recognition data, sometimes voice data, sometimes fingerprints
- Document data: ID number, full name, date of birth, address, sometimes a scan of your ID itself
- Behavioral data: IP address, device ID, GPS location, browsing history, click patterns
- Transaction data: When you verified, what platform, success or failure of verification
- Metadata: Device type, browser, operating system, sometimes phone number
All of this gets stored in databases. And databases get breached. Major data breaches happen constantly, and age verification platforms are now high-value targets.
Data Retention Policies
Here's where it gets really murky. Different platforms have different retention policies, and they often conflict.
The EU requires platforms to delete verification data after a certain period. GDPR says you have the right to deletion. But in practice, many verification providers keep data for much longer than required, citing regulatory compliance and anti-fraud measures.
The UK has similar requirements, but with less enforcement. The US has almost no federal requirements—it's up to individual platforms and states.
So your verification data might be stored for 30 days in one country, 7 years in another, and indefinitely in a third. And you have no way to know where it's being kept.

Privacy Risks: The Real Threats in 2026
Now let's talk about what actually happens to your data. This is where theoretical privacy concerns become real, urgent threats.
Government Surveillance and Subpoenas
This is the most immediate risk. Governments can subpoena age verification records. And they do.
In China, verification data is automatically shared with government surveillance systems. That's not a theoretical concern—it's policy.
In the EU and UK, governments can request data through legal processes. A detective investigating a crime can request verification records to track someone's internet activity. A government agency investigating financial crimes can request records. And once the legal precedent exists, mission creep happens fast.
The US doesn't have formal national data-sharing agreements yet, but law enforcement routinely requests data from platforms and verification providers without warrants, and most companies comply.
What makes this dangerous is that age verification data is permanent. It links your identity to your online behavior. If you accessed certain websites or used certain services while verified, governments now have a record of that linked to your real identity.
Data Breaches and Cybercriminal Markets
Age verification platforms are high-value targets for hackers. They store biometric data and government IDs at scale. When these platforms get breached, the fallout is catastrophic.
A 2024 breach of a major verification provider in Europe exposed over 3 million users' facial biometric data, ID scans, and address information. That data is now on criminal marketplaces. Fraudsters use it to open accounts in victims' names. Scammers use facial data to create deepfake videos.
Biometric data is especially dangerous because you can't change it. If your facial biometric is compromised, you can't just reset it like a password. It's permanently exposed.
Discrimination and Algorithmic Bias
Age verification systems use algorithms to verify identity and detect fraud. These algorithms have bias built in.
Facial recognition systems perform worse on people with darker skin tones. This means people of color are more likely to fail age verification, have their verification requests flagged as fraud, or require manual review.
Behavioral verification systems are biased against people with disabilities. Someone with a motor disorder might move their mouse in unusual patterns. Someone with a cognitive disability might have different browsing patterns. The system flags them as potentially fraudulent.
On top of that, age verification creates a digital barrier for people without government-issued IDs. Undocumented immigrants, homeless people, people from countries with unstable governments—they can't verify their age, so they lose access to the internet.
Data Brokers and Behavioral Profiling
Data brokers are building a market around age verification data. They're not buying the verification data itself—that's protected. But they're buying access to the behavioral patterns around verification.
When you verify your age on Tik Tok, that creates a data signal. When you verify on Instagram, that's another signal. When you verify on multiple platforms, data brokers can infer behavioral patterns. Are you the kind of person who accesses a lot of adult content? Are you hiding your internet activity from someone? Are you testing fraud detection systems?
These inferences get sold to marketers, insurance companies, and other third parties. Your age verification history becomes part of your digital shadow profile—the complete record of your behavior that exists across the internet.
The Authentication Problem
Here's a subtle but serious issue: age verification creates a new authentication vector that hackers can exploit.
Once your age is verified on a platform, you're authenticated. Hackers who steal your verification credentials can access your account. If age verification is linked to a government digital ID system, hackers who compromise that system can compromise your entire digital identity.
We've seen this play out with other authentication systems. When SSNs became widely used for authentication, identity theft exploded. When email became the primary authentication method, email hijacking became a major attack vector. Age verification systems are creating the same dynamic at scale.
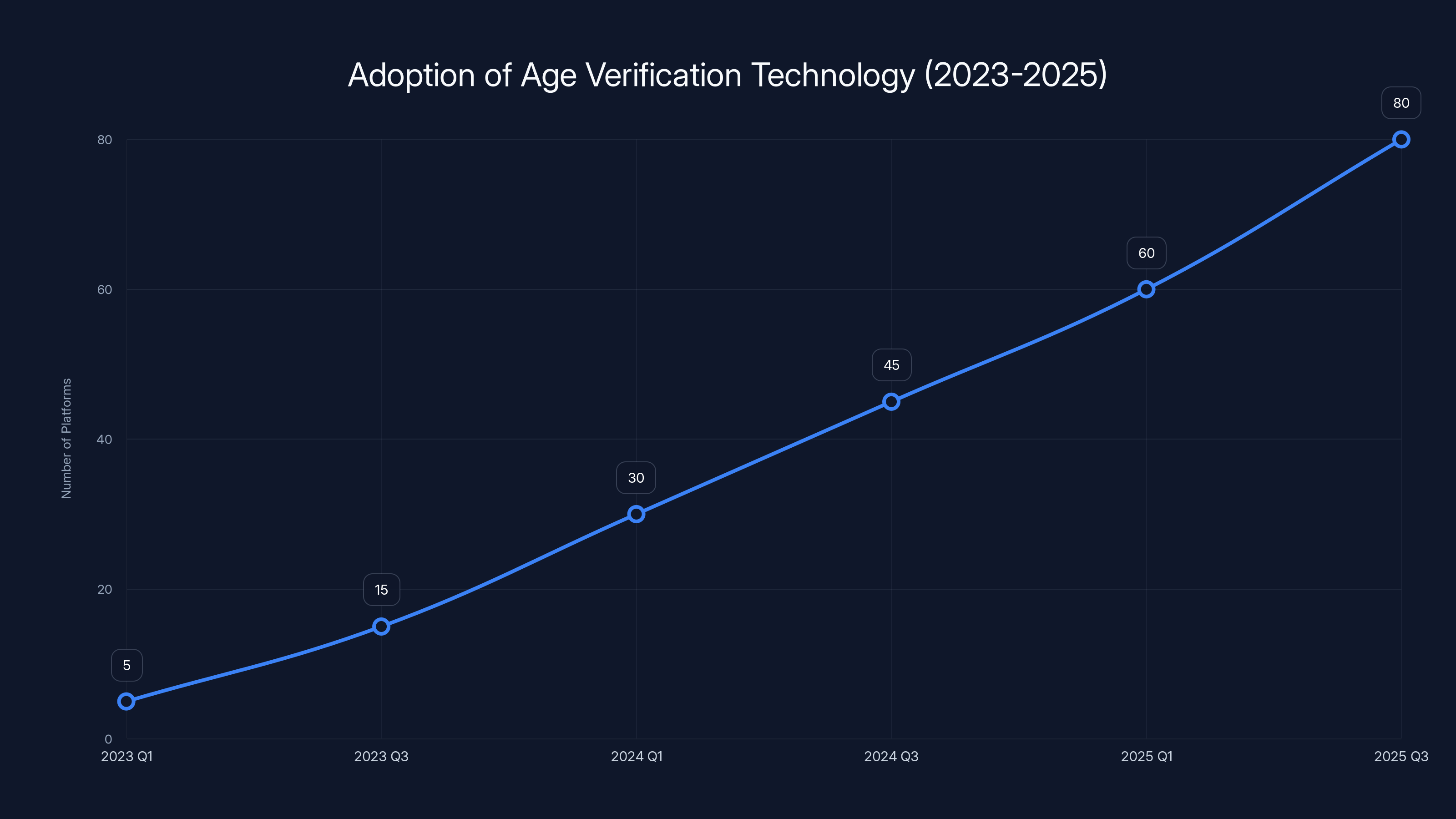
The number of platforms implementing age verification technology grew significantly from 2023 to 2025, driven by regulatory pressures and technological advancements. (Estimated data)
How VPNs and Privacy Tools Fit Into This Picture
A lot of people assume that a VPN will solve the age verification problem. Hide your location, hide your IP, bypass the verification requirement. That's not quite how it works.
What VPNs Can Actually Do
VPNs are effective at two things: hiding your IP address and encrypting your connection. This means platforms can't see your real location, and your ISP can't see what sites you're visiting.
For age verification, this matters in specific ways. If you're in a region with strict age verification requirements, a VPN can let you connect from a region without requirements. Some platforms use geolocation to determine whether to require verification. If you spoof your location with a VPN, you might bypass the initial check.
But here's the catch: once you start using a platform, the platform collects other data points. Your account creation data. Your payment information. Your behavior on the platform. These data points get cross-referenced, and the VPN becomes irrelevant.
What VPNs Cannot Do
A VPN cannot protect you from deliberate age verification requirements. If a platform requires you to upload your ID or take a biometric scan, a VPN doesn't help. The ID verification happens before your data goes through the VPN, and your biometric data is inherently tied to your physical identity.
A VPN also doesn't prevent the platform from storing your verification data. Once you've verified, that data exists on the platform's servers, regardless of your VPN use.
And critically, VPNs don't prevent governments from subpoenaing data. If a government demands your verification records from a platform, your VPN doesn't provide legal protection.
Privacy Tools That Actually Help
There are a few tools that provide some protection against age verification overreach:
Pseudonymous accounts: Create accounts with fake names and minimal personal information. This doesn't bypass age verification, but it limits the data linked to your real identity. The downside is that many platforms now require real-name policies or verify identity through other means.
Encrypted messaging: Use end-to-end encrypted messaging apps to communicate about sensitive topics. This prevents platforms from profiling your communication patterns. Apps like Signal and Wire Guard provide strong encryption.
Temporary email addresses: Use services like Temp Mail to create disposable email addresses for platform verification. This prevents platforms from linking multiple accounts to a single email.
Privacy-focused browsers: Use Tor Browser or Brave for sensitive browsing. These browsers limit tracking and prevent behavioral profiling.
The reality is that age verification is designed to overcome these protective measures. That's the whole point. So privacy tools are only partially effective.

The Data Economy Around Age Verification
Age verification isn't just a privacy issue. It's creating entirely new markets and profit centers.
Verification Platform Companies
Companies like Onfido, Intellinetics, and dozens of smaller verification providers are now essential infrastructure. Platforms need them to comply with regulations. Governments rely on them for age verification data.
These companies are making huge profits. They charge per verification transaction—typically
The problem is that these companies are venture-backed or corporate-owned. They have shareholder obligations. That means they're incentivized to monetize user data in every way possible. They're incentivized to retain data longer than necessary. They're incentivized to share data with third parties.
Third-Party Data Brokers
Data brokers are building markets around age verification data. They can't buy the verification data itself due to regulations, but they can buy access to behavioral signals around verification.
For example, a data broker might note that a particular person verified on multiple adult platforms in a short time period. They infer that this person has strong interest in adult content. They sell that inference to marketers who target people with "adult content interest" for products related to erectile dysfunction, dating sites, and other adult services.
This is creating what researchers call "data arbitrage"—buying cheap, limited data and selling expensive, inferred data based on that limited data.
Government Contracts
Governments are contracting with verification providers for access to verification data. In some countries, this is explicit—the government mandates that verification data be shared with law enforcement. In others, it's implicit—platforms comply with data requests because they know it's expected.
This creates perverse incentives. Verification providers have an incentive to collect more data, retain it longer, and make it easier for governments to access. The more valuable the data, the higher the government contract.
The Secondary Market for Digital IDs
Some countries are considering linking age verification to government digital ID systems. This creates the potential for a massive secondary market.
Once digital IDs become widespread, they become targets for theft, fraud, and abuse. A black market emerges for stolen digital IDs. Criminals use them to open accounts, commit fraud, and bypass authentication systems.
At scale, this could dwarf current fraud problems. Instead of stealing a single credit card number, criminals can steal an entire digital identity tied to government records.

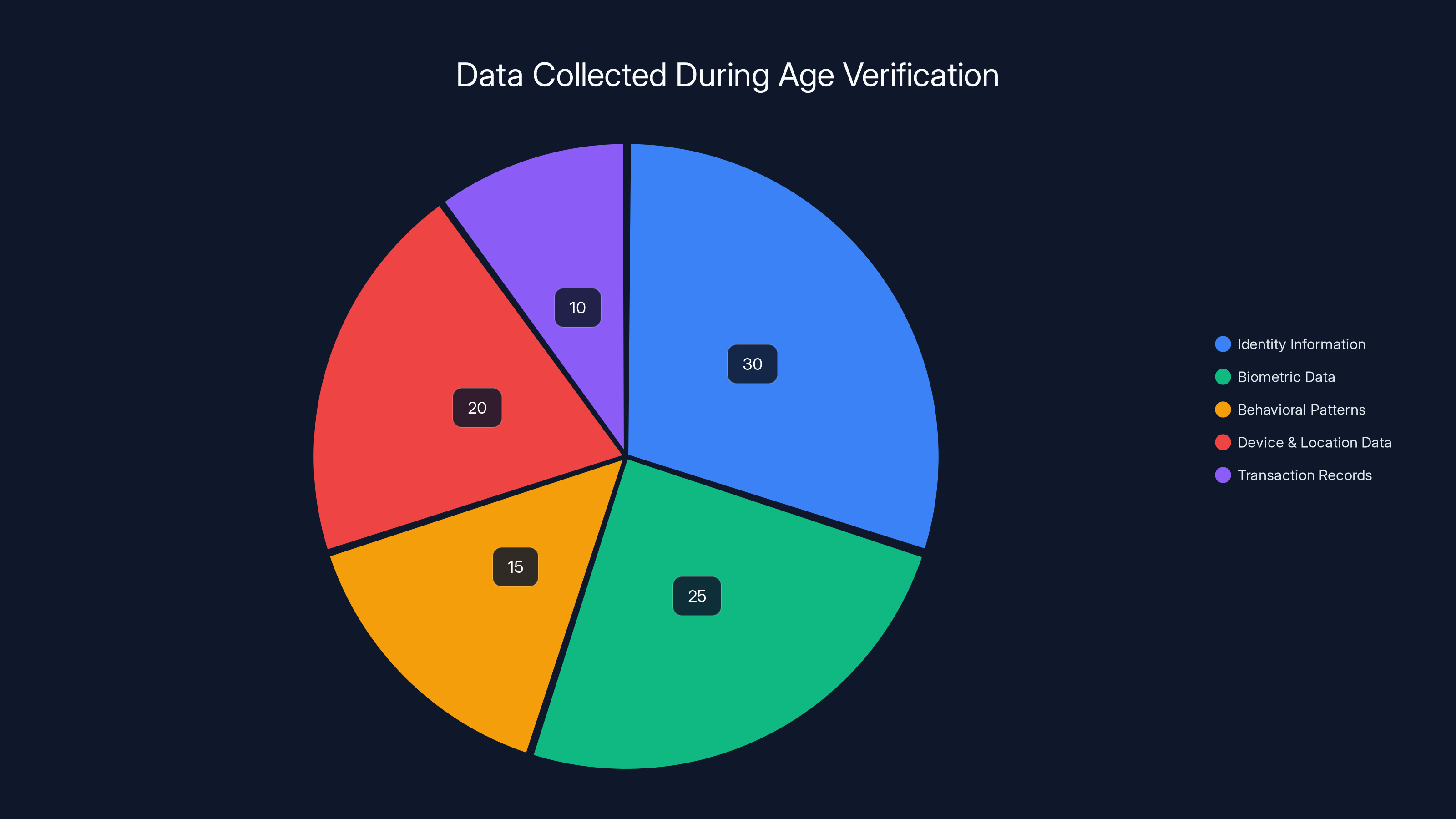
Identity information and biometric data constitute over half of the data collected during age verification processes. Estimated data.
The Global Fragmentation Problem
Age verification is being implemented differently across different regions, and this fragmentation creates serious security and privacy problems.
Conflicting Standards
The EU requires data deletion after a certain period. The UK requires indefinite retention for fraud prevention. California requires age verification but doesn't specify retention policies. Australia requires age verification and ties it to a national digital ID system.
For platforms operating globally, this creates conflicting requirements. Tik Tok can't comply with all of them simultaneously. So they either choose the strictest requirement (EU standards) and apply it globally, or they create different systems for different regions.
Tik Tok chose the second approach. But this creates inconsistencies. Your data in Europe might be deleted within 30 days, while your data in the US is retained indefinitely. This fragmentation means that your data might be more private in one place and less private in another.
Different Technologies, Different Risks
Different regions are adopting different verification technologies. The EU favors document-based verification. The UK is moving toward biometric verification. Singapore uses behavioral verification.
This means the same person might have to verify their age using three different methods in three different regions. Each method creates different risks. Each method stores data in different places. Each method can be compromised differently.
A hacker might not be able to break into the EU's document-based system, but they could break into the UK's biometric system. Or vice versa.
Cross-Border Data Flows
Age verification data crosses borders constantly. A person in the US verifies their age on an EU platform. That data flows to a US verification provider. That data flows to EU servers. That data is subject to requests from US law enforcement and EU regulators.
When data crosses borders, it becomes subject to multiple legal systems. The US can demand it under US law. The EU can demand it under GDPR. The UK can demand it under its own laws. The person whose data it is has no way to know which jurisdiction "owns" their data or what rights they have.

What Changed in 2026: The Current Landscape
As we've moved into 2026, several trends have emerged that reshape how age verification actually works in practice.
Normalization and Resistance
Age verification is now normalized in developed countries. Most people accept it as a standard part of internet access, like logging into email. But in some regions, there's been pushback.
Activist groups in the EU have challenged age verification mandates on privacy grounds. They argue that the privacy costs outweigh the benefits in child protection. Some of these challenges are working—the UK has delayed implementation of certain strict age verification requirements due to privacy concerns.
But resistance is fragmented. What works in one country doesn't work in another. And platforms are powerful enough to implement verification regardless of public opinion.
Technology Evolution
The technology is getting more sophisticated and more invasive. Behavioral verification systems are now using machine learning to detect minors based on browsing patterns. Biometric systems are using liveness detection and multi-frame analysis to prevent spoofing.
At the same time, researchers are developing tools to defeat age verification. Spoofing tools, fake ID generators, biometric bypass techniques. It's an arms race.
Platform Consolidation
Small platforms are getting squeezed out. They can't afford to implement age verification systems, so they're either shutting down or being acquired by larger platforms. This means the internet is consolidating around a few massive platforms that have the resources to build verification infrastructure.
Consolidation is bad for privacy because it creates honeypots. Instead of your data being spread across multiple smaller platforms, it's concentrated with a few massive companies. If those companies get hacked, the damage is massive.
Government Digital ID Systems
Several countries are now linking age verification to government digital ID systems. Estonia pioneered digital ID and it's been relatively successful. Other EU countries are considering it.
The advantage is that it makes verification simpler—you just authenticate with your digital ID instead of uploading documents. The disadvantage is that it links your online behavior directly to your government identity. There's no separation between your real identity and your digital identity.

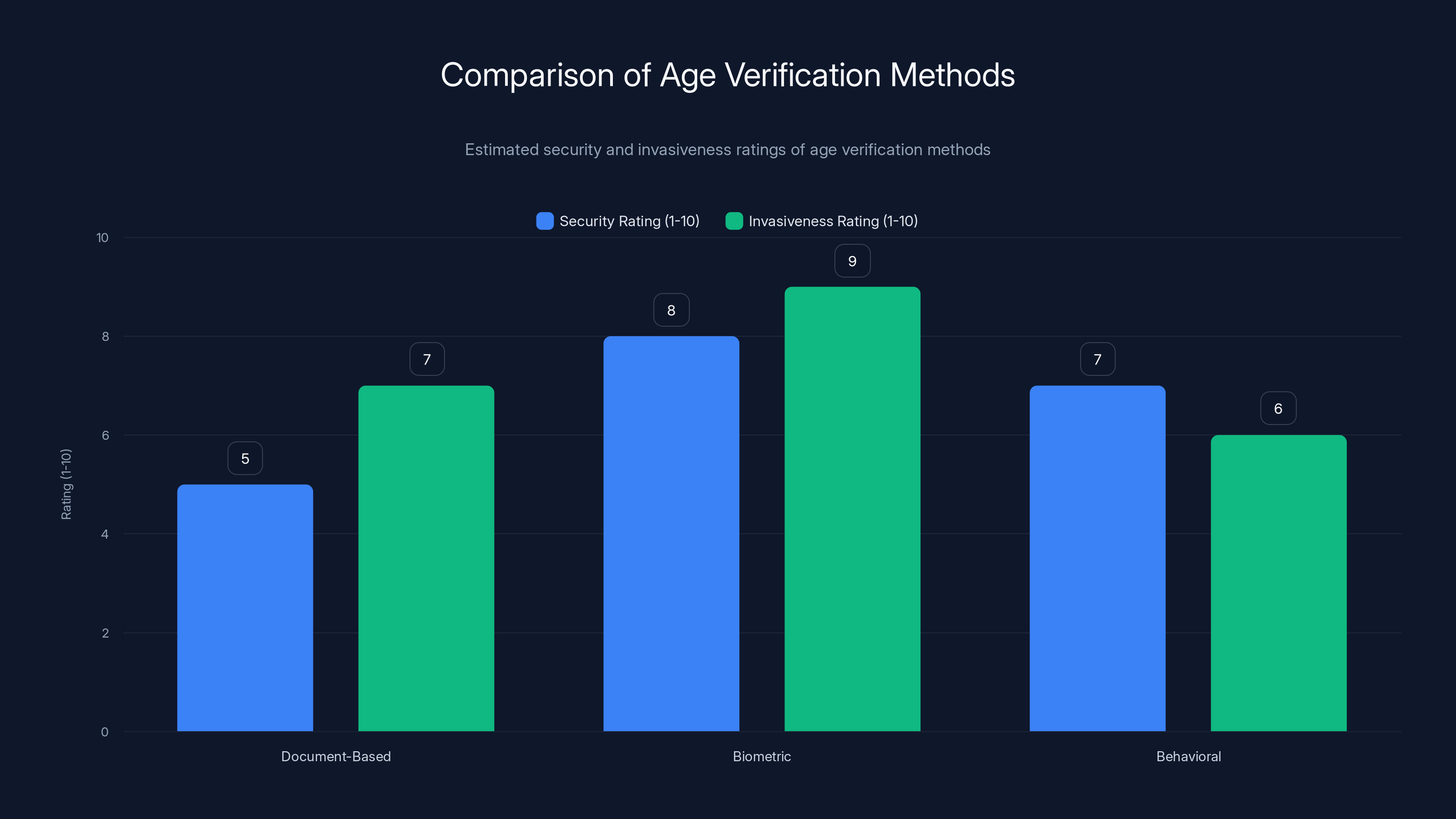
Biometric verification scores highest for security but also for invasiveness, highlighting the trade-off between security and privacy. (Estimated data)
Practical Steps You Can Take Right Now
Age verification isn't going away. So here's what you can actually do to protect your privacy.
Minimize Data Shared During Verification
When you verify your age, you have to share some data. But you can minimize it:
- Use a VPN to hide your location, even though it won't prevent verification
- Create a separate email address for verification
- Use a burner phone number if possible
- Don't verify on multiple platforms with the same identity
- Request deletion of your verification data within 30 days if regulations allow it
These steps won't prevent platforms from collecting data, but they limit what data gets linked to your primary identity.
Understand Your Rights
Different countries give you different rights regarding your verification data:
- EU: You have the right to access, correct, and delete your data under GDPR
- UK: Similar rights under UK GDPR
- US: Limited rights; varies by state
- Australia: Rights under Privacy Act
If you live in a jurisdiction with strong privacy rights, exercise them. Request your data, see what's stored, and request deletion.
Use Privacy Tools Strategically
VPNs, encrypted messaging, and browser privacy tools don't prevent age verification, but they limit other tracking:
- Use a VPN for general browsing to hide your IP
- Use Signal for sensitive communication
- Use Brave Browser to block tracking
- Use Tor Browser for truly sensitive activity
These don't solve the age verification problem, but they create defense in depth.
Monitor Your Data
Use data breach monitoring services to see if your verification data gets compromised. Services like Have I Been Pwned track public breaches.
Moreover, monitor your credit report and identity theft services if you've uploaded government-issued ID for verification. Your ID data is sensitive and high-value for identity thieves.
Support Privacy Advocacy
Organizations like the Electronic Frontier Foundation, Privacy International, and local privacy advocacy groups are fighting age verification overreach through legal challenges and policy advocacy.
Supporting these organizations funds research, legal challenges, and regulatory pressure that actually works.

The Future: Where This Is Heading
Understanding the current situation helps you understand where age verification is heading next.
Convergence Toward Global Standards
Right now, age verification is fragmented. But we're seeing convergence toward global standards, driven by large platforms that need unified systems. Tik Tok, Meta, Google—they all want one verification system that works globally.
The likely outcome is that we'll see a few dominant verification providers that operate globally, using similar technologies and standards. This creates systemic risk. If those providers get hacked, the fallout is global.
Integration With Government Digital ID
Governments are pushing for integration between age verification and government digital ID systems. This is happening faster in some countries than others, but it's the trajectory.
Once this integration is complete, your government identity becomes your internet identity. Your government knows everything you do online. This is surveillance at a scale we've never seen before.
Expansion Beyond Age Verification
Once the infrastructure for age verification is in place, governments will use it for other things. Not just age, but actual identity. Not just age verification, but "purpose-limited" verification—verifying you're old enough for adult content, but also verifying you're the right person for financial transactions, health information, and so on.
This is the path we're on. Age verification is the thin edge of the wedge.
Privacy Backlash
There will be pushback. We're already seeing it in some jurisdictions. As people understand the privacy implications of age verification, resistance will grow.
But this resistance will be regional and fragmented. Some countries will implement strict privacy protections. Others will eliminate them entirely. The result will be a two-tier internet—one private and regulated, one public and surveilled.
What This Means for Your Privacy in 2026 and Beyond
Let's be direct about what age verification actually means for your privacy going forward.
Your identity is now permanently linked to your internet activity. When you verify your age, you create a record that says "this person accessed this platform at this time from this location." That record exists. It can be accessed by platforms, governments, and potentially other actors.
Your biometric data is now commodified. If you used facial recognition for age verification, your face is now in a database somewhere. That database can be breached, sold, or subpoenaed. Once your facial biometric is compromised, you can't change it.
The internet is now less anonymous. Anonymous access to information is becoming impossible. You have to prove who you are to access certain content. That changes the fundamental nature of the internet.
Your privacy rights depend on geography. If you live in the EU, you have relatively strong privacy rights around age verification data. If you live in the US, you have almost none. This creates privacy arbitrage—some people are more protected than others based on where they live.
Government surveillance capacity has increased dramatically. Governments now have infrastructure to track citizens' internet activity tied to their real identity. They can see what content you access, when you access it, and from where.
But here's the thing: this isn't unique to age verification. It's part of a broader trend toward a surveillance internet. Age verification is just one piece of it. Other pieces include payment tracking, device tracking, behavioral tracking, and biometric tracking.
The question isn't really about age verification. It's about whether you want to live on a surveilled internet where your activity is tracked and linked to your real identity. Or whether you want to fight for privacy protection.
Age verification is one battle in that larger war. Understanding it is the first step to protecting yourself.
FAQ
What is age verification online?
Age verification online is a process where platforms confirm your age before granting access to age-restricted content. This can happen through document-based verification (uploading ID), biometric verification (facial recognition), or behavioral verification (analyzing your activity patterns). The goal is to prevent minors from accessing adult content, but it also creates permanent records linking your real identity to your online activity.
How does age verification actually work technically?
The most common method is document-based verification, where you upload a photo of your government ID and a platform extracts your date of birth using optical character recognition. More advanced systems use facial recognition to confirm you match your ID photo, plus "liveness detection" to prevent spoofing. Some platforms also analyze your behavioral patterns—how you type, move your mouse, or browse—to infer your age without explicit verification. All these methods collect and store data, creating permanent records of your verification history.
What are the privacy benefits of age verification?
The primary benefit is child safety. Age verification prevents (or slows down) minors' access to adult content and algorithmic recommendation systems that might promote harmful content. For some users, knowing that platforms are verifying age might create a sense of security. However, the privacy costs significantly outweigh these benefits—you're trading away anonymous internet access for potential child protection, which many privacy advocates argue is not a good trade.
What personal data is collected during age verification?
Age verification systems collect your full name, date of birth, government ID number, address, facial biometric data, behavioral patterns, IP address, device information, GPS location, and transaction records. Some systems also collect voice data and fingerprints. This data is stored by verification providers, shared with platforms, and can be accessed by governments through legal processes. The scope of data collection far exceeds what's necessary for simple age confirmation, creating comprehensive digital profiles linked to your real identity.
Can a VPN protect me from age verification requirements?
Partially, but not completely. A VPN can hide your IP address and location, which might bypass geolocation-based verification checks initially. However, once you create an account on a platform, the platform collects other identifying information that makes your VPN irrelevant. More importantly, a VPN cannot protect you from mandatory identity verification—if a platform requires you to upload your ID or take a biometric scan, a VPN doesn't help. For comprehensive protection, combine VPNs with other privacy tools like encrypted messaging, pseudonymous accounts, and privacy-focused browsers, but understand that these are only partial solutions against a system specifically designed to identify users.
Which countries require age verification?
The EU, UK, Denmark, Finland, Norway, Sweden, Singapore, Australia, and New Zealand all have mandatory or near-mandatory age verification requirements as of 2026. The US doesn't have a federal mandate, but California and several other states require it. The trend is expanding rapidly—most developed countries will have some form of age verification requirement by 2027. Implementation varies significantly: the EU uses decentralized systems with different providers in different countries, the UK is moving toward centralized digital ID integration, and some Asian-Pacific countries link verification directly to government surveillance systems.
How long is age verification data retained?
Retention varies significantly by jurisdiction. The EU typically requires deletion within 30–90 days after verification, though enforcement is weak. The UK has no formal deletion requirement. The US has almost no federal requirements, with policies varying by state. In practice, many verification providers retain data much longer than required, citing fraud prevention and regulatory compliance as reasons. You can often request deletion under GDPR if you live in the EU, but most platforms resist deletion requests. The reality is that your age verification data is likely stored indefinitely somewhere, regardless of stated policies.
What happens if a platform holding my verification data gets hacked?
Your sensitive personal information—government ID data, facial biometric data, address information—becomes available to criminals and hostile actors. Biometric data is especially dangerous because you can't change your face if it's compromised. Criminals use leaked ID data to commit identity theft, open fraudulent accounts, and apply for credit. Hackers sell leaked biometric data on criminal marketplaces where it can be used for deepfakes or spoofing other biometric systems. A single breach affecting millions of users (like the 2024 breach of a major EU verification provider) can have massive cascading consequences across the entire internet.
Can governments access my age verification data?
Yes, governments can subpoena age verification records held by platforms and verification providers. In some countries, data-sharing agreements exist that automatically provide verification data to law enforcement. Even in countries without formal agreements, companies typically comply with government requests because they fear regulatory retaliation. Once your age verification data is in government hands, it can be used to track your internet activity, link your behavior patterns to surveillance databases, and create comprehensive profiles of your online behavior. This creates permanent records tied to your real identity that persist indefinitely.
Conclusion: Understanding the Stakes
Age verification changed the internet in 2025, and the consequences are only becoming clear in 2026. This isn't hyperbole. This is a fundamental restructuring of how the internet works and what privacy means.
For decades, the internet offered something unique: relative anonymity. You could research sensitive topics, explore your identity, learn about things you might be embarrassed to discuss with others—all without revealing your real identity. That's over now.
Age verification systems have created permanent, identity-linked records of internet activity at a scale we've never seen before. Billions of people's faces are now stored in verification databases. Billions of people's government IDs have been uploaded and digitized. Billions of people's behavioral patterns have been analyzed and stored.
This data is concentrated with a few powerful companies, accessible to governments, vulnerable to breaches, and increasingly subject to commercial monetization.
But here's what's important: understanding this is the first step to protecting yourself. You can't opt out of age verification entirely—the infrastructure is mandated by government regulation. But you can minimize data leakage, use privacy tools strategically, monitor your data, and support privacy advocacy that fights against surveillance creep.
You can also demand better from policymakers. You can push for stronger data deletion requirements. You can support policies that prevent government access to verification data. You can vote for politicians who take privacy seriously.
Age verification was sold as protecting children. And maybe it does, to some degree. But it also created unprecedented surveillance infrastructure. The question now is whether we accept that tradeoff or whether we push back.
The answer to that question will define what the internet looks like in 2027 and beyond.
Key Takeaways
- Age verification is now mandatory in 28+ countries affecting ~2.8 billion users, creating unprecedented digital identity infrastructure tied to government records
- Verification systems collect facial biometrics, government IDs, behavioral patterns, and location data—all vulnerable to breaches and government subpoenas
- Data retention varies wildly: EU requires deletion in 30-90 days, but most providers retain indefinitely; UK has no deletion requirement
- VPNs cannot prevent mandatory identity verification—they can only spoof location for initial checks but become irrelevant once accounts are created
- Government surveillance capacity increased exponentially: once verified, your identity is permanently linked to all online activity across platforms
Related Articles
- VPN Regulation & Legislation in 2026: Loopholes, Laws & What's Next [2025]
- The Complete Guide to Breaking Free From Big Tech in 2026
- Norton VPN Deal: 12 Months of Cybersecurity & Streaming [2025]
- iRobot Roomba Data Privacy After Chinese Takeover [2025]
- Should You Use a VPN Browser? Complete Guide [2025]
- US Removes Spyware Executives From Sanctions: What Actually Happened [2025]
![Age Verification Changed the Internet in 2026: What You Need to Know [2025]](https://tryrunable.com/blog/age-verification-changed-the-internet-in-2026-what-you-need-/image-1-1767351961466.jpg)



