The VPN Industry at a Crossroads: 2026 Will Define Everything
The VPN industry is about to get weird. And I don't mean the good kind of weird.
For years, Virtual Private Networks lived in this weird gray zone. Governments tolerated them. Tech companies used them. Privacy enthusiasts loved them. But nobody really knew what the legal status was supposed to be. That ambiguity? It's about to end.
2026 is shaping up to be the year when regulators around the world stop treating VPNs like a quirky tech footnote and start treating them like a genuine policy problem that needs solving. And depending on where you live, that could mean anything from stronger encryption standards to outright bans.
Here's what we're watching: The European Union is tightening its Digital Services Act requirements. The United States is pushing back against end-to-end encryption in some sectors. Russia and China are cracking down harder. India's already walking a dangerous line between allowing VPNs and restricting them. And smaller countries are following the big players' lead.
The reason? It's not really about you streaming Netflix from another country or securing your coffee shop browsing session. Those are convenient narratives, sure. But the real pressure comes from governments wanting to combat money laundering, terrorism financing, and illegal marketplaces. They want visibility. They want logs. They want to know who's doing what, when, and from where.
The problem is that real VPNs don't give them that. And that's where the conflict gets interesting.
I've spent the last two months digging through regulatory filings, talking to VPN company lawyers, interviewing privacy advocates, and reading between the lines of government statements. What I found is a landscape that's transforming faster than most people realize. The old assumptions about VPNs being "basically fine" are crumbling.
So here's what 2026 actually holds for the VPN industry: massive regulatory changes, new compliance requirements that some VPN providers can't meet, consolidation of the market around better-funded companies, and a fundamental shift in how VPNs operate. Some providers will adapt. Some will disappear. And some will find loopholes you haven't even thought of yet.
Let's break down what's actually happening.
TL; DR
- 2026 brings coordinated regulatory action from the EU, US, UK, and other nations targeting VPN providers and end-to-end encryption
- The core issue: Governments want surveillance capabilities; real VPNs prevent exactly that
- Key regulations: EU's Digital Services Act enforcement, US encryption restrictions, India's licensing requirements, Russia/China bans
- Industry impact: Consolidation toward compliant mega-providers, legal pressure on no-log policies, mandatory data retention for some jurisdictions
- The loopholes: Corporate VPNs, privacy-focused jurisdictions, decentralized tech, and encrypted tunnels marketed as "other tools"
- Bottom line: VPN providers must choose between privacy principles and regulatory compliance, and many will compromise
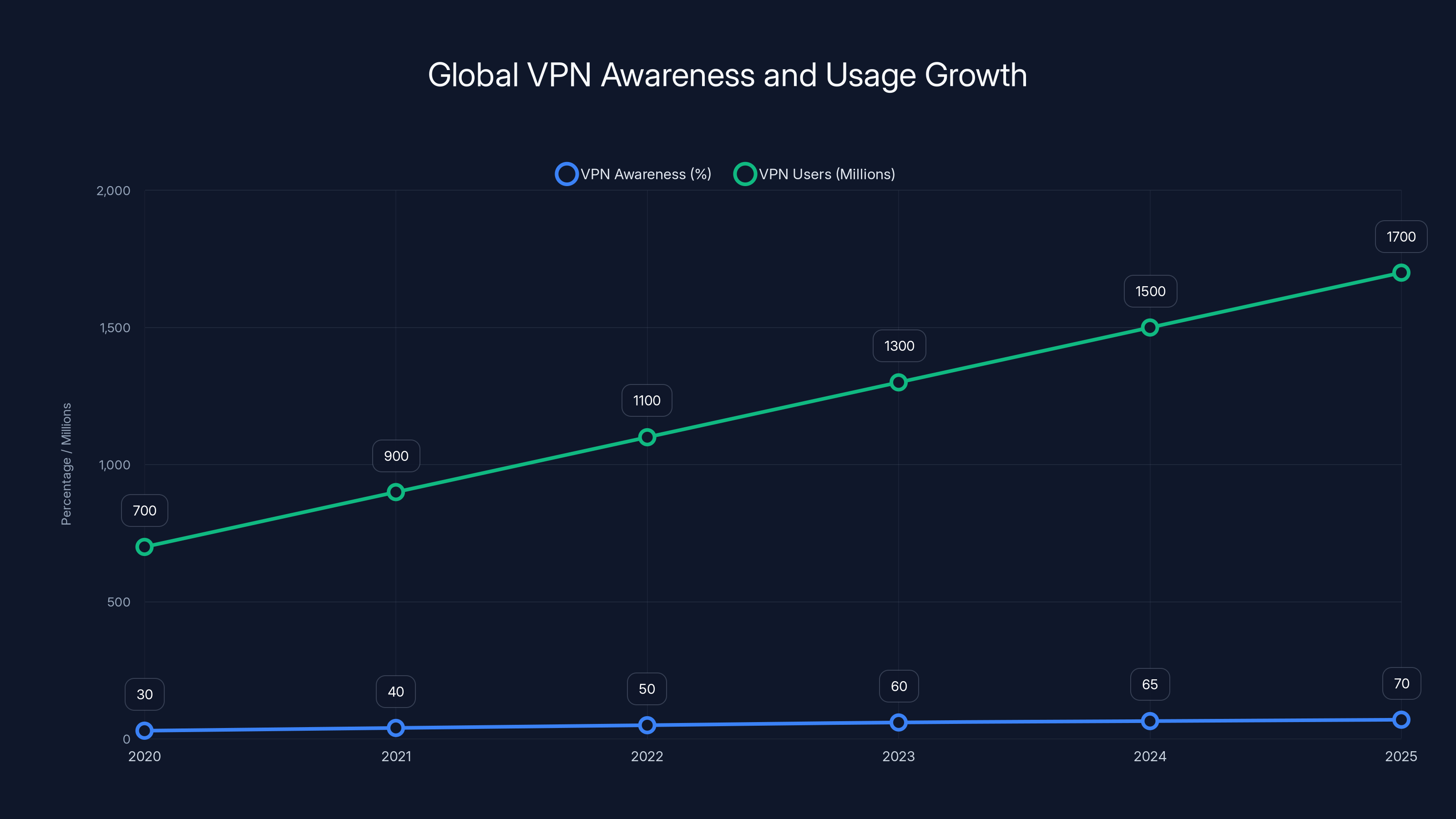
VPN awareness and usage have significantly increased from 2020 to 2025, with awareness rising from 30% to 70% and active users reaching 1.7 billion by 2025. Estimated data.
Why Governments Are Suddenly Obsessed With VPNs
Let's start with the obvious question: why now? VPNs have existed since the late 1990s. They weren't controversial for most of that time. So what changed?
Three things happened simultaneously.
First, VPN adoption exploded. In 2020, maybe 30% of internet users had heard of a VPN. By 2025, that number's closer to 70%. When adoption hits mainstream levels, governments start paying attention. It's not a niche anymore. It's infrastructure that could affect millions of people.
Second, VPNs became synonymous with accessing illegal content. Dark web marketplaces, streaming pirated movies, bypassing geolocation restrictions, avoiding corporate firewalls. The technology itself is neutral, but the public perception isn't. And when something becomes culturally associated with rule-breaking, regulators start treating it as a problem.
Third (and this is the real driver), governments lost something they had for decades: visibility into internet activity. Encryption, HTTPS, VPNs, and end-to-end messaging platforms stripped away the ability to passively monitor traffic. Governments don't like losing tools. So they're fighting back.
Intel agencies will tell you the issue is terrorism and organized crime. And sure, those are real concerns. But the underlying frustration is broader: they used to understand the internet. They could see what was happening. Now? Too much is hidden. The darkness is uncomfortable.
The EU framed it as a Digital Services Act compliance issue. The US talks about lawful access. Russia and China just banned things outright. But the core anxiety is the same everywhere: loss of control and visibility.
And 2026 is when that anxiety becomes policy.
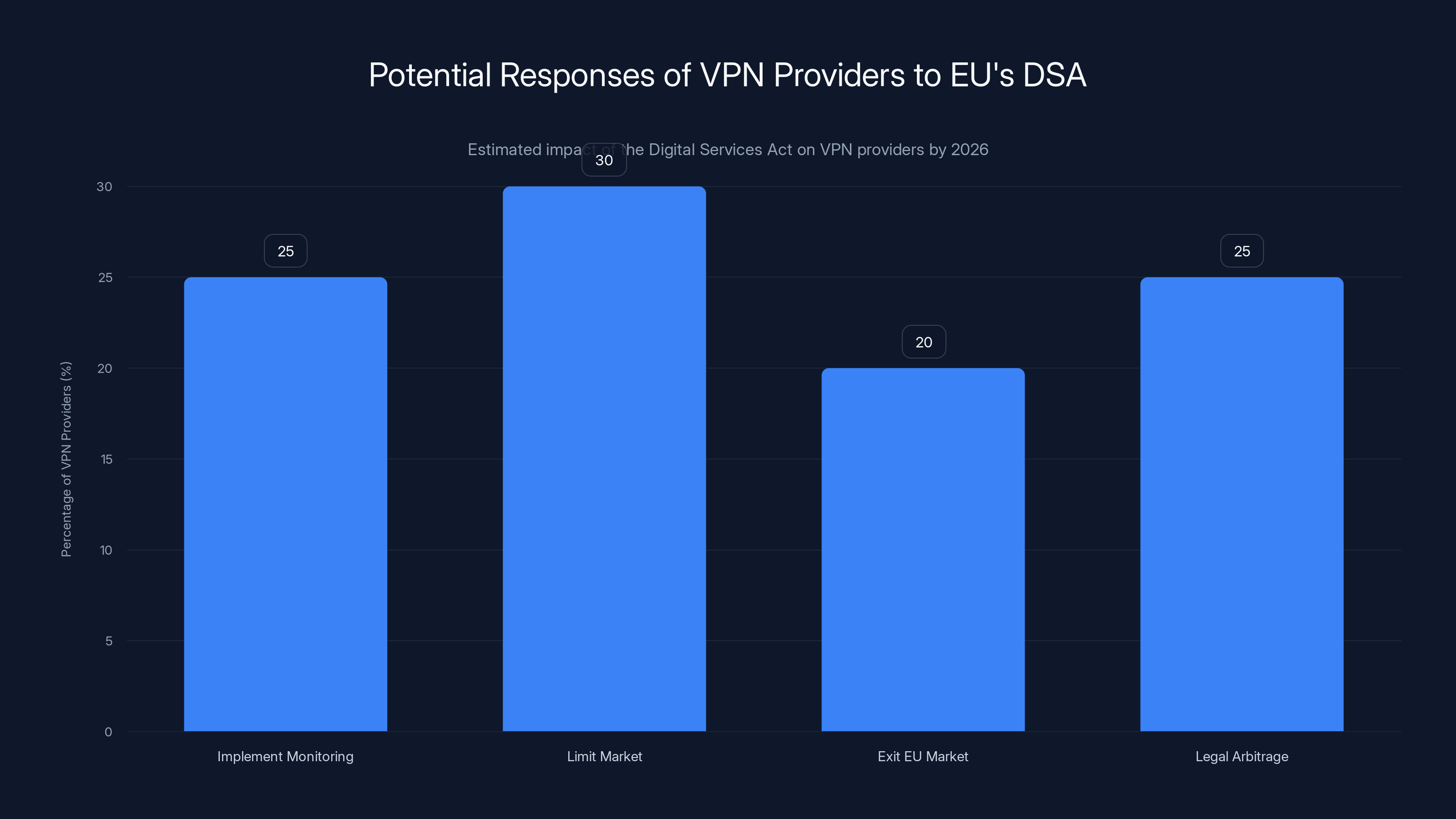
By 2026, VPN providers will likely adopt various strategies to comply with the EU's DSA, with some opting to limit their market or exit the EU entirely. (Estimated data)
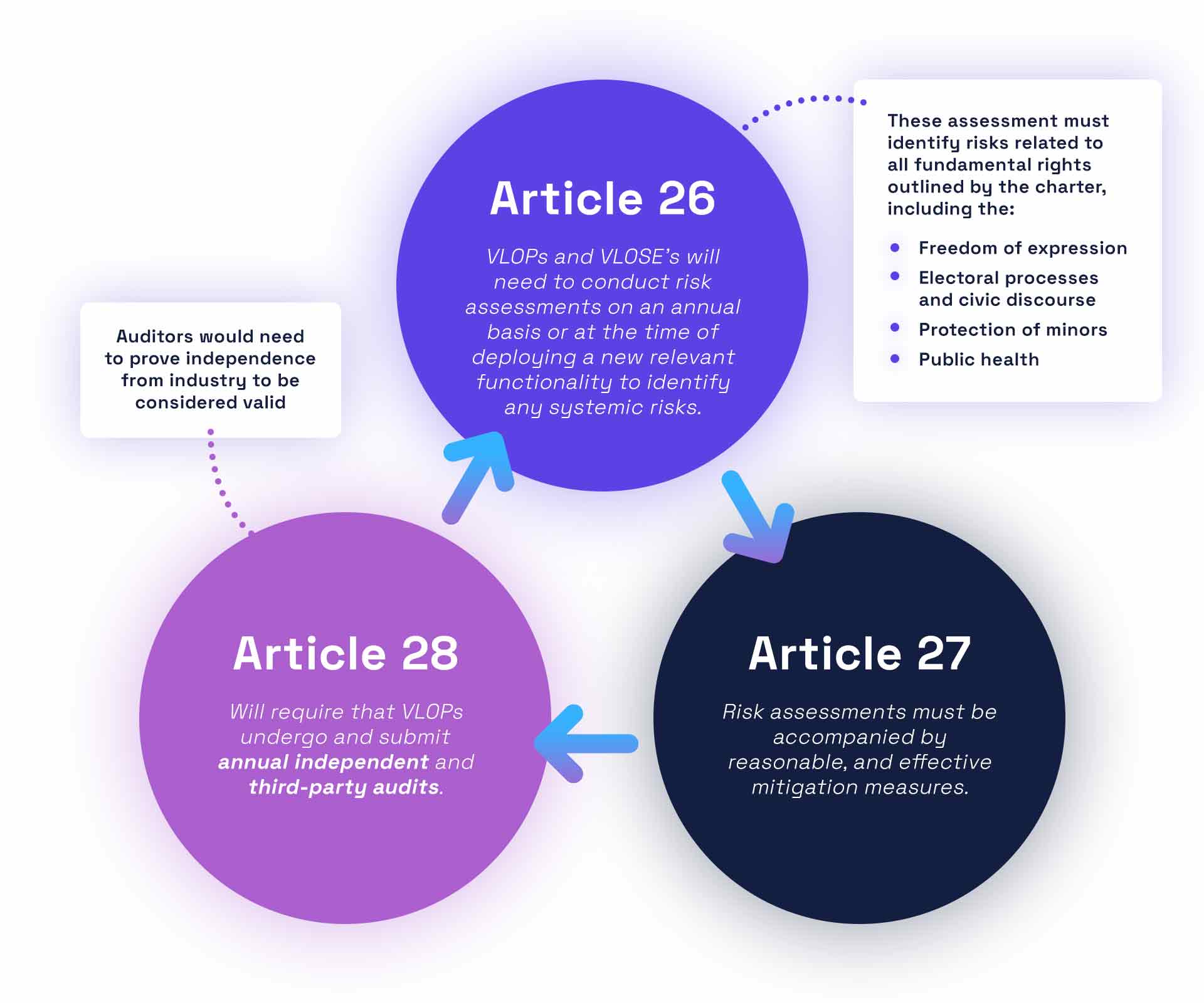
The EU's Digital Services Act: The Regulatory Bomb Everyone's Ignoring
The European Union's Digital Services Act (DSA) doesn't explicitly mention VPNs. That's the problem.
What it does mandate is that platform operators must prevent illegal content, halt financial flows to terrorist organizations, and cooperate with law enforcement investigations. Sounds reasonable in the abstract. But when you apply it to VPN providers, it becomes a regulatory minefield.
Here's the core tension: A VPN provider's entire value proposition is that they can't see what users are doing. That's literally the point. They don't store logs. They don't know which sites you're visiting. They claim they can't help law enforcement even if they wanted to.
But the DSA requires exactly that kind of cooperation. It requires knowing what's happening on your platform so you can prevent bad stuff.
The EU's starting to enforce this in 2025, and by 2026, it's going to create a hard constraint: VPN providers operating in or serving EU customers will either need to:
- Implement monitoring systems (which breaks the privacy promise)
- Operate only in jurisdictions with strong privacy laws (which limits their addressable market)
- Exit the EU market entirely (which some already are doing)
- Get creative with legal structures and jurisdictional arbitrage (more on this later)
Some VPN providers are already making moves. They're hiring compliance officers. They're establishing data centers in privacy-friendly jurisdictions like Iceland and Switzerland. They're trying to find that sweet spot between regulatory compliance and not destroying their brand promise.
The honest answer? They probably can't have both. And 2026 is when the compromises become unavoidable.
United States Encryption Policy: The Biggest Wildcard
The United States has been fighting encryption since the 1990s. The Crypto Wars of that era ended with a truce: encryption was legal for civilian use, but the government maintained backdoor access requirements for law enforcement.
That truce held for thirty years. Now it's breaking down.
The Biden administration's been quietly pushing for "lawful access" requirements in encryption. Basically: companies must build in backdoors that law enforcement can use with a warrant. The department of justice published a white paper on this in 2024, and it's become the de facto US policy position.
VPN providers are directly in the crosshairs of this initiative.
A true VPN uses military-grade encryption (AES-256) that even the VPN company can't decrypt. The data flows from your device through encrypted tunnels they can't see into. They literally cannot comply with law enforcement requests because the encryption prevents them from accessing the data.
This is either the whole point (if you're a privacy advocate) or a complete dealbreaker (if you're the FBI).
Where this gets messy: The US doesn't have explicit "VPN bans" yet. But they have enforcement mechanisms. In 2025, the FBI and DEA started sending cease-and-desist letters to VPN companies hosting services that facilitate illegal activity. By 2026, expect those letters to become standard operating procedure.
The real change will be more subtle: Payment processors will start refusing to work with VPN companies. App stores will delist VPN apps. Cloud providers will deny hosting to VPN infrastructure. The government doesn't need to explicitly ban VPNs. They just need to make them commercially unviable.
Some VPN companies are preparing for this by:
- Establishing payment infrastructure outside US jurisdiction
- Building their own hosting infrastructure instead of relying on cloud providers
- Creating subsidiary companies in different countries to insulate their main operations
- Starting to implement limited logging (which they claim is compliant with law enforcement requests)
The catch: Any of these moves undermine the privacy promise that makes VPNs valuable in the first place.
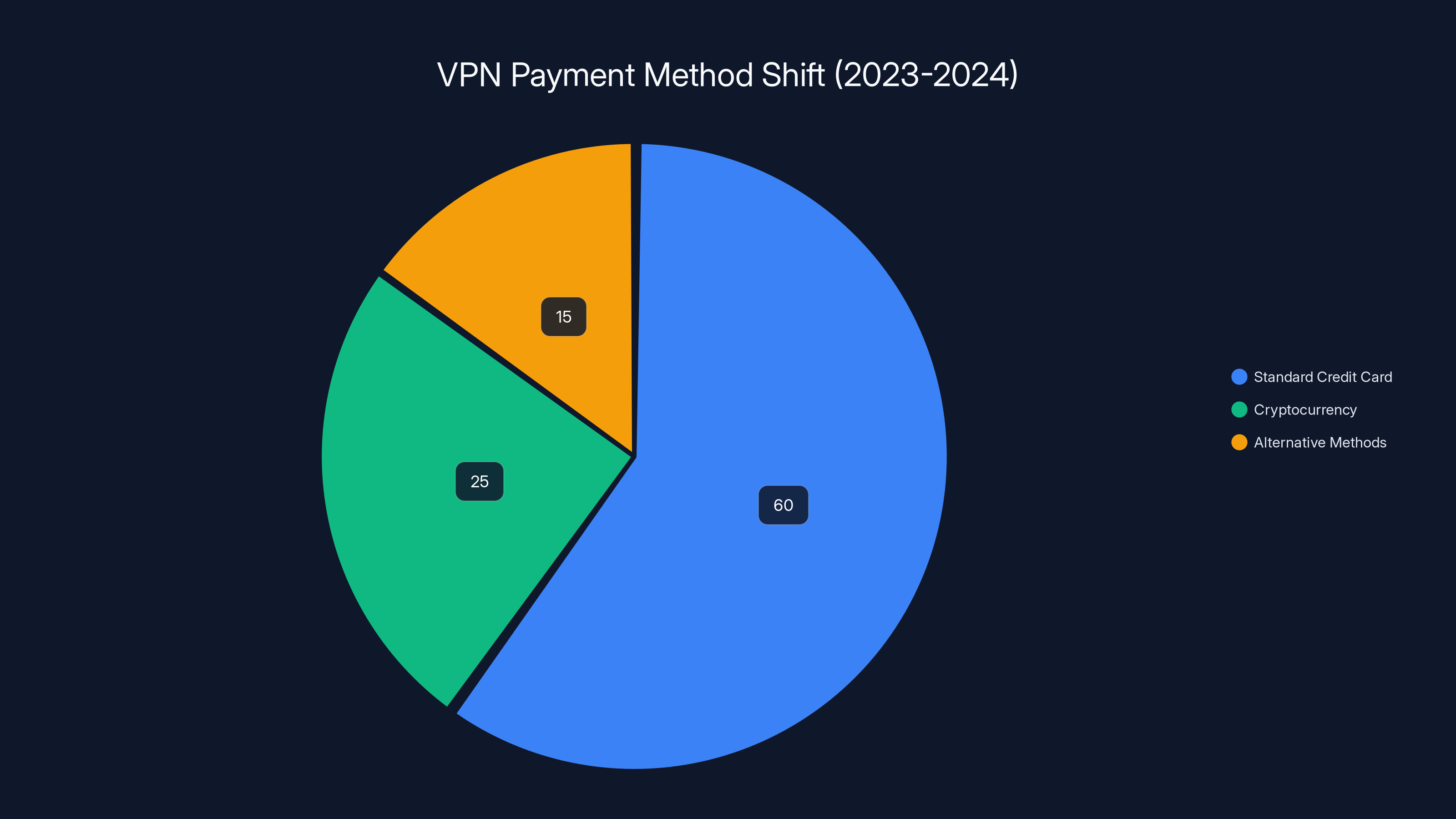
By late 2024, over 40% of VPN providers had shifted from standard credit card payments to cryptocurrency or alternative methods due to payment processor restrictions. (Estimated data)
India's Licensing Trap: The Blueprint for Authoritarian Tech Control
India's approach to VPNs is less of a ban and more of a slow regulatory squeeze.
India doesn't prohibit VPN use. But it requires VPN providers to register with the government, undergo security audits, and maintain user logs. In practice, this means:
- The government gets to approve which VPN companies operate in India
- Those companies have to maintain data that could be subpoenaed
- "No-log" policies become illegal because the law requires logs
- Dissidents, journalists, and minorities have to trust their own government with their browsing data
This framework is genius from an authoritarian perspective because it's not a ban. It looks reasonable on paper. It sounds like normal regulation. But the net effect is that real privacy-focused VPNs can't operate there. Only government-compliant versions can.
Other countries are watching. The India model is becoming the template for middle-income authoritarian and semi-authoritarian states:
- Pakistan introduced similar licensing requirements in 2024
- Vietnam is implementing a closely regulated VPN system
- Thailand's pushing through comparable mandates
- Indonesia's considering variants
By 2026, this framework will be standard in about a dozen significant markets. And it's spreading.
The US and EU are looking at India's approach and thinking: "Hey, that could work for us too." Not as a ban, which is unpopular. But as a licensing and compliance system. "VPNs are fine, but only if they're registered, audited, and compliant."
Russia and China: The Bans Everyone Expected
Russia and China went a different direction. They didn't create regulation. They created prohibition.
Russia banned most commercial VPN providers in 2017. They made exceptions for government-approved providers and corporate services. The intent was clear: suppress circumvention of censorship and maintain state control of information.
China has been more aggressive and less transparent. They don't officially ban VPNs, but they actively block them through the Great Firewall. They shut down VPN providers' payment infrastructure. They make it functionally impossible to use VPNs without getting arrested.
These weren't the first bans. But they're the most successful. By 2026, both countries have largely succeeded in eliminating consumer VPN use. Most remaining traffic is state-approved providers or corporate tools.
The EU and US will never explicitly copy this approach. It looks too authoritarian. But they'll achieve similar ends through other means: payment restrictions, app store removals, ISP-level blocking, and compliance mandates that are impossible to meet.
The goal is the same. The tactics are just more acceptable to Western audiences.

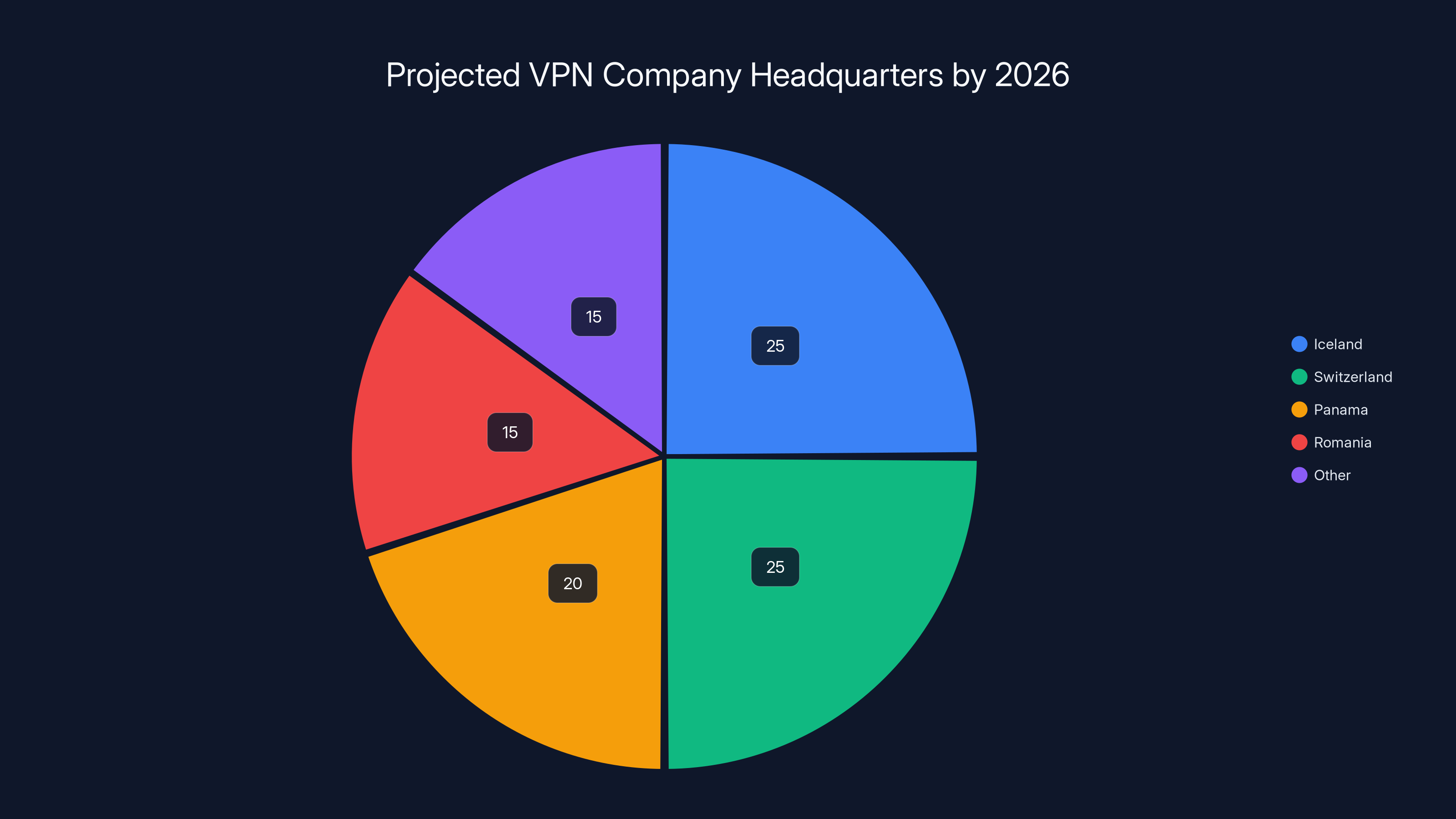
By 2026, it's projected that a significant portion of VPN companies will relocate to countries with strong privacy laws like Iceland and Switzerland. Estimated data based on current trends.
The Payment Problem Nobody's Talking About
Here's a quiet crisis nobody's discussing: VPN companies can't get paid.
Visa, Mastercard, and other payment processors are increasingly refusing to process transactions for VPN providers. They cite risk mitigation: VPNs are high-fraud categories, they're used for money laundering, they facilitate illegal activity. So the processors just don't want the risk.
For large, well-funded VPN companies, this is manageable. They can use payment processors in friendly jurisdictions, cryptocurrency, direct bank transfers, whatever. But for smaller providers, it's fatal.
This is the quiet consolidation mechanism. The big players (Express VPN, Nord VPN, Surfshark, Proton) can survive payment processor restrictions. The smaller, more privacy-focused, less-compliant alternatives can't.
By 2026, expect the VPN market to be dominated by companies that either:
- Have deep pockets and can afford legal battles
- Are willing to compromise on privacy to maintain compliance
- Operate payment infrastructure in unregulated jurisdictions
The scrappy startup that launches a privacy-first VPN from a basement in 2025? They won't be around in 2027.

The Loophole Economy: How Smart Companies Evade Regulation
Now here's where it gets interesting. Regulations create loopholes. And smart companies exploit them.
Corporate VPNs vs. Consumer VPNs
Regulations typically target consumer VPN providers. Corporate VPNs—the tools companies use to let employees access company networks remotely—exist in a different regulatory category.
A corporate VPN is basically the same technology. Same encryption. Same functionality. But it's sold under a different legal framework (B2B vs. B2C), and it's subject to different regulatory oversight.
Cynical prediction: By 2026, some consumer VPN companies will rebrand as "corporate VPN solutions" or "enterprise remote access platforms," even if they're primarily serving individuals. The regulatory pressure on "VPNs" won't apply to "encrypted enterprise networking tools."
It's not dishonest, technically. It's just smart regulatory arbitrage.
Privacy Havens and Jurisdictional Arbitrage
Some countries have legal systems that explicitly protect privacy. Iceland, Switzerland, Panama, and Romania have strong privacy laws, banking secrecy, and (in some cases) constitutional protections against surveillance.
VPN companies are moving their servers and legal entities to these jurisdictions. By 2026, expect the major privacy-focused VPN providers to be headquartered in countries with strong legal protections, even if their customers are in the EU or US.
The regulatory gamble: If a VPN company operates from a privacy-protected jurisdiction and doesn't process payments in regulated countries, how do governments enforce against them?
They can block them at the ISP level (as Russia and China do). They can prevent payment processing (as the US is doing). They can threaten users (which is unpopular). But they can't directly compel data if the company and their data are outside their jurisdiction.
This creates a stable equilibrium: VPN companies that operate from privacy havens can serve EU and US customers, but they'll face payment and access restrictions. Users can still use them, but it'll be more friction.
Decentralized Infrastructure
Some smart privacy advocates are building decentralized VPN alternatives: networks where thousands of individuals contribute bandwidth, and no central company controls the infrastructure.
These are harder to regulate because there's no company to sue, no central server to shut down, no payment processor to block. You're not subscribing to a service. You're participating in a peer-to-peer network.
By 2026, these alternatives won't have mainstream adoption. But they'll exist as a parallel ecosystem for people who need serious privacy and are willing to tolerate worse speed and reliability.
Governments will eventually figure out how to regulate these too (probably by going after individual node operators). But it'll be slower and messier.
The "Privacy Email + VPN" Bundle Loophole
Some companies are bundling VPNs with email, password managers, encrypted storage, and other privacy tools under one service.
From a regulatory perspective, this is genius. You're not a "VPN company." You're a "privacy and productivity suite." The VPN is just one feature.
This buys time and creates ambiguity. Which regulation applies? The digital services act? The encryption rules? Privacy law? When the regulatory framework is still uncertain, bundling creates enough complexity to avoid immediate enforcement.
Expect more of this in 2026. VPN features embedded in broader privacy suites. Plausible deniability for companies that mainly focus on privacy-preserving communication.

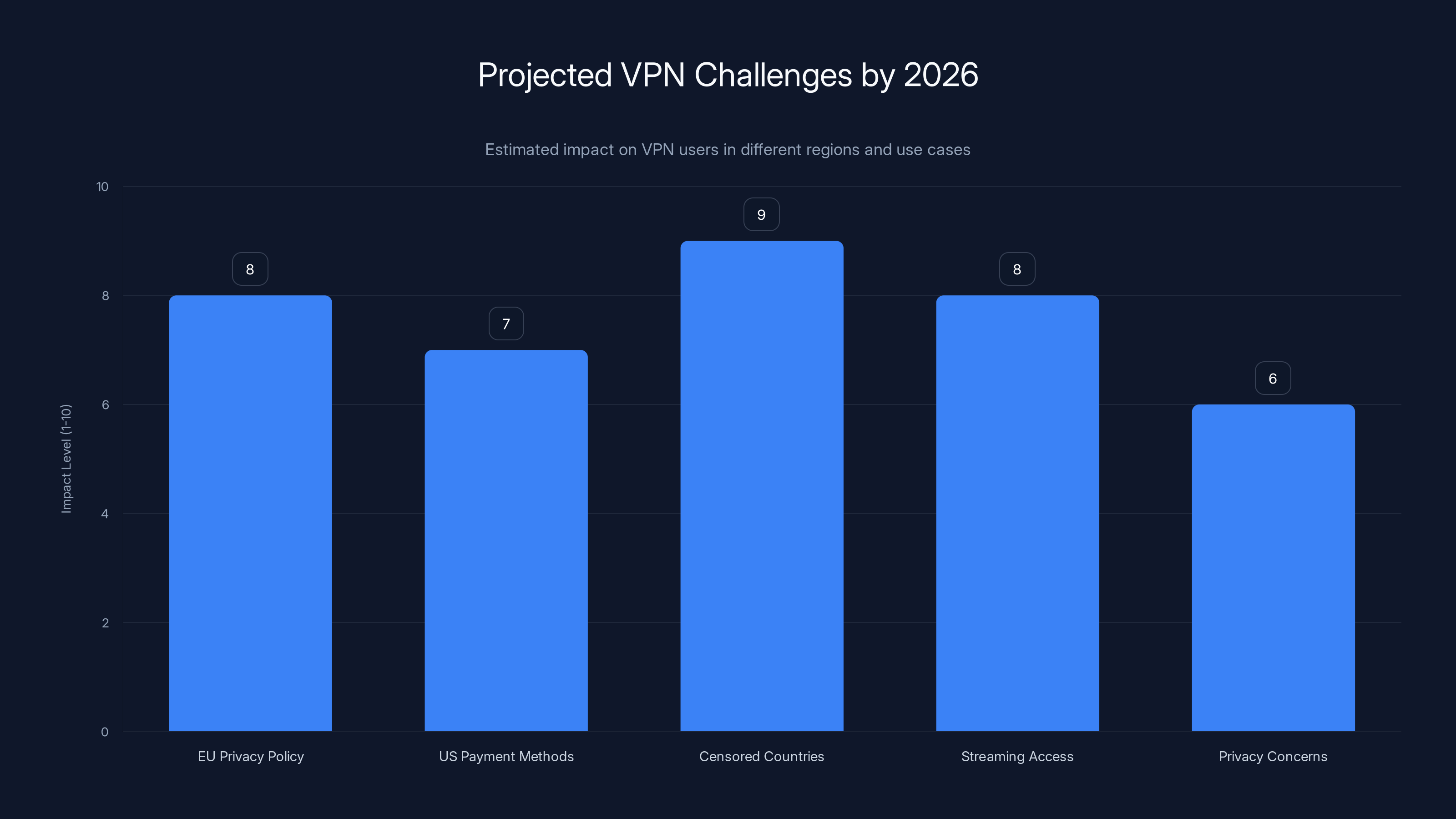
Estimated data suggests that VPN users in censored countries and those using VPNs for streaming will face the highest challenges by 2026, with increased detection risks and improved geofencing technology.
The European Data Retention Compromise
Here's the compromise that's probably coming in 2026: Limited log retention.
Privacy advocates hate this. Governments love it. The EU is likely to push through a framework that requires VPN providers to keep certain logs for limited periods.
Not browsing history. Not URLs you visit. But metadata: connection timestamps, duration, amount of data transferred, IP addresses (both your real one and the VPN exit IP).
This sounds like a reasonable middle ground. You get privacy on content. Governments get enough metadata to investigate serious crimes.
But metadata is more powerful than people think. With timestamps and volume data, law enforcement can infer behavior patterns. They can tell when you're online, which services you're using (based on traffic volume and patterns), and where your VPN exit points are.
VPN companies claiming "no logs" will have to choose: comply and keep logs (which makes them no longer true no-log VPNs), or refuse and get blocked in the EU.
Some will compromise. Others will exit the market. A few will keep their promises and operate only in privacy-friendly jurisdictions.

What Happens to "No-Log" Claims in 2026
One of the biggest marketing points for VPN companies is the "no-log" promise. We don't store your data. We can't see what you're doing. We can't comply with government requests because we literally don't have the information.
This claim is about to become legally uncertain.
Not because governments will ban no-log policies. But because regulatory compliance will make true no-log operations harder and harder.
Consider the technical reality: To truly operate with zero logs, a VPN company needs to:
- Never write user activity to disk
- Use RAM-only storage that clears on shutdown
- Not monitor connections for fraud detection
- Not record IP address assignments
- Not track user count or session information for billing
But regulators will require:
- Fraud monitoring (which requires logs)
- Ability to comply with law enforcement requests (which requires logs)
- Know Your Customer (KYC) verification (which requires identifying users)
- Financial audit trails (which requires payment logs)
These are incompatible. You can't be truly no-log and fully compliant. Companies will have to choose.
Some will choose privacy and accept reduced compliance (and potential legal consequences). Others will accept compliance and abandon no-log claims. Most will find a middle ground: minimal logs, encrypted logs, logs in privacy-friendly jurisdictions, logs that they claim they can't access. Some variation that technically complies while maintaining the PR benefit of sounding privacy-focused.
But the PR game is about to get a lot harder.

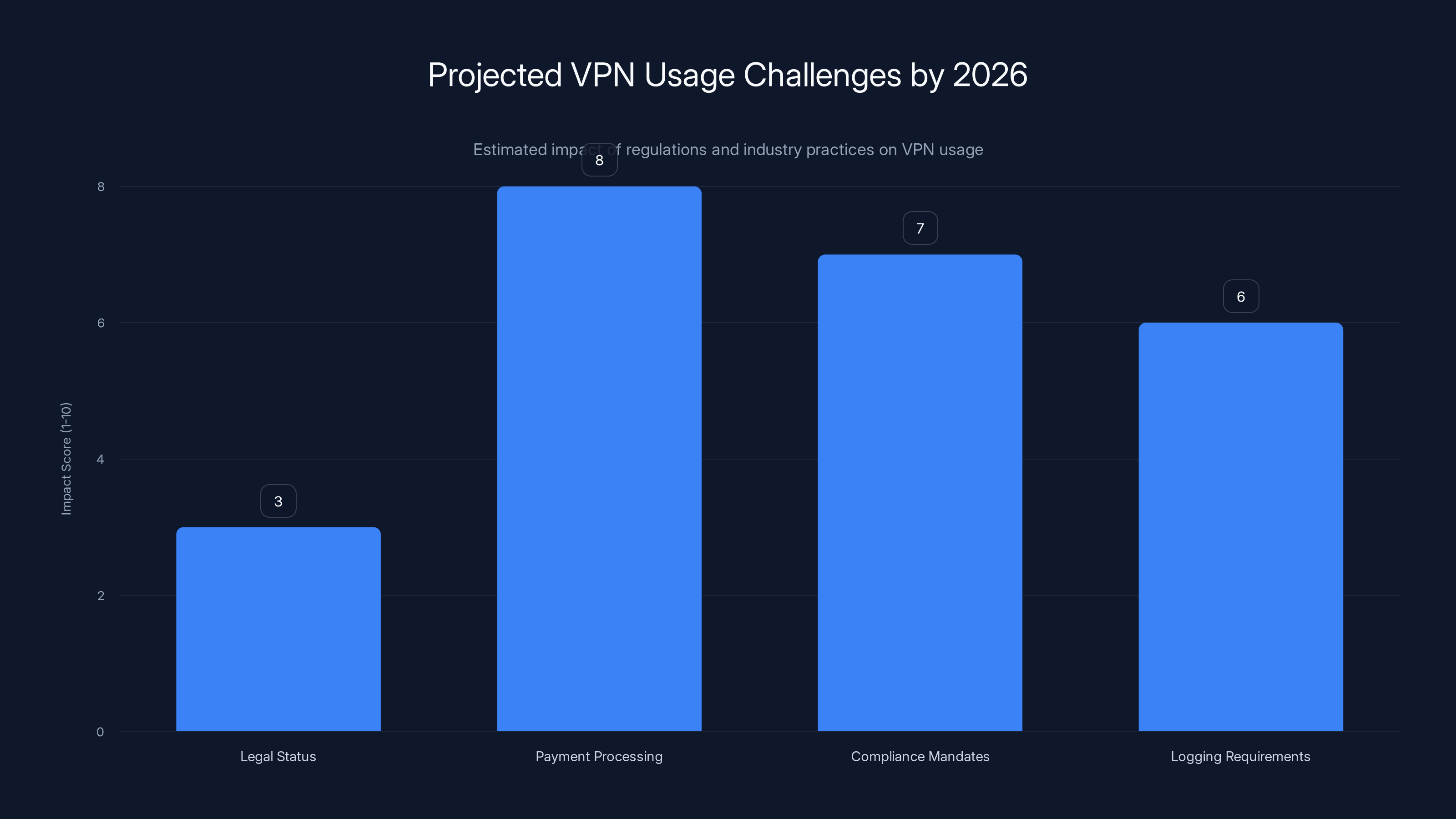
By 2026, while VPNs are unlikely to be illegal, payment processing restrictions and compliance mandates are expected to significantly impact their usage. (Estimated data)
The Impact on Different VPN Markets
Not all VPN use is equal in the eyes of regulators.
Business VPNs (Low Regulatory Pressure)
Companies using VPNs to protect corporate networks and facilitate remote work? Basically zero regulatory pressure. This is legitimate business infrastructure. Governments aren't threatening this.
Business VPN market continues growing. Maybe even accelerates as enterprise security budgets increase.
Geolocation Bypass VPNs (Medium Regulatory Pressure)
Using a VPN to watch Netflix from another country? This hits a different regulatory category. It's contract violation (you're breaking Netflix's ToS by accessing from a different region), but it's not illegal in most places.
The pressure here comes from content licensing companies, not governments. But by 2026, we'll see more geofencing technologies that break VPN bypass attempts. And content companies will be more aggressive about account suspension.
VPN adoption for streaming will decline, not because of government bans, but because it becomes less useful.
Censorship Circumvention VPNs (Highest Regulatory Pressure)
Using a VPN to bypass government censorship in authoritarian countries? This is existential threat territory for those governments.
Bans will become stricter. Detection and punishment will become harsher. But they also become harder to enforce perfectly, which is why VPN use in censored countries won't go to zero. It'll just become more dangerous and more limited.
Privacy advocates will continue funding alternatives. Users will continue finding workarounds. It becomes an arms race.
Privacy/Anonymity VPNs (Variable Pressure)
Using a VPN just because you want privacy? The regulatory pressure depends entirely on jurisdiction.
In the EU, expect increasing compliance requirements. In the US, expect payment processing friction. In authoritarian countries, expect bans. In other places, it'll remain legal and unregulated.

What the Consolidation Actually Means
By 2026, the VPN market will be consolidated. The survivors will be:
- Mega-companies with lobbying resources (Express VPN, Nord VPN, Surfshark) that can navigate regulatory complexity and afford compliance costs
- Privacy-haven companies that operate outside regulated jurisdictions
- Corporate VPN providers that serve business, not consumer markets
- Decentralized alternatives that don't have a central company to regulate
Everything else gets squeezed out. The smaller, scrappier, more innovative VPN startups? They probably won't make it to 2027 unless they can raise serious capital for compliance infrastructure.
This sucks for competition and innovation. But it's predictable. Regulation always favors incumbents.

Technology Workarounds: Encryption by a Different Name
Here's the thing about regulation: Smart people find loopholes.
If VPNs become heavily regulated, technologies that do the same thing by a different name will proliferate:
- Encrypted proxy services (not marketed as VPNs, but functionally identical)
- Encrypted tunnel applications (just a different marketing term)
- Privacy networking protocols (same technology, different legal category)
- Distributed relay networks (peer-to-peer version of VPN functionality)
The regulatory framework might say "VPNs must comply with X." But it doesn't say anything about "encrypted network routing services" or "privacy protocol software."
By 2026, you'll see migration toward these alternative names and structures. Not because they're different technologies, but because regulatory arbitrage.
The UK's Emerging Framework: A Possible Middle Path
While the EU is pushing aggressive compliance requirements and the US is favoring encryption backdoors, the UK is experimenting with a different approach.
The Online Safety Bill frames VPNs as a specific category that requires registration and compliance, but not necessarily bans or backdoor requirements. It's closer to India's licensing model: VPNs can exist, but they need to register, undergo audits, and comply with certain reporting requirements.
This might become the international template. It's less aggressive than China's approach, less libertarian than pre-2025 US policy, and more flexible than the EU's broad digital services requirements.
If the UK framework becomes the standard, VPN providers will need:
- Legal registration in each country they operate
- Annual security audits
- Incident reporting requirements
- Cooperation with law enforcement on serious crimes (with warrant requirements)
- Some form of usage data retention for compliance verification
Not terrible for consumers. Not great for privacy absolutists. Workable for major VPN companies.

Predictions for 2026 and Beyond
Based on everything I've seen, here's what I think actually happens:
Definite: VPN market consolidates. Regulatory pressure increases globally. Small providers exit markets or get acquired. Payment processing becomes harder for remaining providers.
Likely: The EU enforces DSA compliance starting late 2025, forcing some VPN providers to implement limited logging. India's licensing model spreads to 5-8 additional countries. US law enforcement increases pressure on VPN companies through indirect means (payment processors, ISPs, app stores).
Possible: The UK's licensing framework becomes the international standard. Some VPN companies rebrand as "privacy services" to avoid regulatory categorization. Decentralized alternatives gain small but meaningful adoption among serious privacy users.
Speculative: The US pushes through encryption backdoor requirements by 2027, forcing a major rift between US and non-US VPN providers. Major payment processors completely de-bank VPN companies, forcing cryptocurrency-only payment. China expands its ban to encrypted messaging apps more aggressively.
Unlikely (but possible): EU bans all consumer VPNs outright. US legislates mandatory VPN blocking at ISP level. Global agreement on VPN regulation (probably won't happen because countries have conflicting interests).

What This Means for You
If you use a VPN, here's what to watch in 2026:
If you're in the EU: Your VPN provider's privacy policy will probably change. They'll either add limited logging, exit EU markets, or rebrand as something other than a VPN. Don't assume "no logs" is still accurate by mid-2026.
If you're in the US: Payment methods might become limited or require cryptocurrency. VPN apps might disappear from major app stores. But VPN use probably remains legal. Just less convenient.
If you're in a censored country: Expect ongoing cat-and-mouse games with VPN blocking. VPNs will still work, but detection risks will increase. Authorities might start targeting users, not just providers. Be careful.
If you're using a VPN for streaming: Expect geofencing to become more robust. VPN blocking will improve. By 2027, VPN-based streaming access will be harder, not because of regulation, but because content companies will have better tech.
If you care about privacy: Consider which jurisdiction your VPN provider operates from. If they're in the EU or US, expect eventual compromise on privacy policies. If they're in a privacy haven, expect payment processing friction but better privacy. If they're decentralized, expect worse performance but true privacy. Choose accordingly.

The Uncomfortable Truth About Privacy and Regulation
Here's the thing that neither side of this debate wants to admit: Privacy and regulation are fundamentally in tension.
Governments need visibility to prevent crime and enforce law. VPNs explicitly prevent that visibility. These are directly opposed goals. You can't have both.
So 2026 isn't about finding some perfect balance. It's about choosing which value wins: privacy or governmental oversight.
Different countries will choose differently. That's fine. But let's be honest about what's happening. We're not having a technical debate about encryption. We're having a values debate about power.
VPN providers that claim they'll navigate this perfectly—that they'll keep privacy AND comply with all regulations—are probably lying. You can't have both. The best companies will be honest about the tradeoffs they're making.
The ones that scare me are the ones that pretend there's a middle ground. Because 2026 is when that illusion breaks down.

Looking Ahead: The VPN Industry in 2027 and Beyond
So what's the long-term future?
I don't think VPNs disappear. But I think the consumer VPN market as we know it—the "move to this country, unlimited data, no logs" commodity market—probably becomes less important.
What grows:
- Corporate/enterprise VPNs serving business networks
- Privacy-focused suites bundling VPN with email, storage, messaging
- Decentralized privacy networks for serious users
- Government-approved VPNs in countries with licensing requirements (sounds dystopian, but it's coming)
What shrinks:
- Commodity consumer VPN providers competing on price
- "No-log" marketing as a differentiation point
- Easy payment access through standard processors
- Straightforward geolocation bypass services
The industry doesn't end. It transforms. And 2026 is the inflection point where everyone finally realizes the comfortable ambiguity is over.

FAQ
What exactly is a VPN and why do governments care about them?
A Virtual Private Network is software that encrypts your internet traffic and routes it through servers in other locations, hiding your real IP address and making it appear you're browsing from a different country. Governments care because VPNs prevent them from seeing what users are doing online, which they view as critical for law enforcement, counterterrorism, and preventing illegal marketplaces like dark web drugs and weapons sales.
Will VPNs be illegal in the US or Europe by 2026?
Unlikely that VPNs become explicitly illegal in the US or EU by 2026. Instead, expect indirect pressure through payment processing restrictions, app store delistings, and compliance mandates. The effect is similar to a ban, but it's technically legal to use a VPN—just much harder to pay for one.
How does the EU's Digital Services Act actually affect VPN providers?
The DSA requires platforms to prevent illegal activity and cooperate with law enforcement. VPN providers struggle with this because their business model is explicitly preventing them from seeing (and thus preventing) illegal activity. By 2026, major VPN companies will face enforcement requiring either limited logging of user activity or exit from EU markets.
Why are payment processors de-banking VPN companies?
Visa, Mastercard, and other processors classify VPN services as high-risk for fraud and money laundering. They're increasingly refusing to process payments for VPN companies to reduce their own regulatory exposure. This isn't mandated by law yet, but it's becoming standard industry practice.
What's the difference between no-log VPNs and limited-log VPNs?
No-log VPNs claim they never record any user activity or connection data. Limited-log VPNs keep minimal metadata like connection timestamps and amounts of data transferred, but claim they don't log browsing history or user identity. In practice, metadata can reveal just as much about behavior as full logs. The regulatory trend is toward forcing all VPNs toward limited logging, making true no-log claims legally impossible to sustain in regulated jurisdictions.
Will using a VPN to watch Netflix from another country get me in legal trouble?
Unlikely for the user. Streaming services handle this through account suspension, not legal action. The real pressure in 2026 will come from better geofencing technology that blocks VPNs rather than regulatory bans. But it's not a legal issue for you, just a technical one that'll get harder.
What should I look for in a VPN provider if regulations are tightening?
Check where they're legally incorporated and where their servers are located. Privacy-friendly jurisdictions like Iceland, Switzerland, and Romania have better legal protections. Also verify their payment processing infrastructure—if they only accept cryptocurrency, it's a red flag for regulation avoidance but a good sign for privacy. Finally, watch their privacy policy changes in 2026; any move toward "limited retention" suggests they're compromising to stay compliant.
Is Tor better than VPNs for privacy in this regulatory climate?
Tor operates in a different regulatory category because it's not sold as a consumer product by a company; it's an open-source protocol. This gives it some insulation from the regulatory pressure hitting VPN companies. But Tor is slower and more complicated. For serious privacy users facing increasing VPN regulation, Tor or Tor bridges might become necessary, but they're not ideal for general use.
Will the VPN industry consolidate around a few major companies?
Yes. The compliance costs and regulatory friction make it harder for small providers to survive. By 2027, expect the market to be dominated by 5-10 major players that have the resources to navigate regulation, plus a parallel ecosystem of smaller privacy-focused operators in regulatory havens. The scrappy startup VPN space essentially dies in this scenario.
What does the India licensing model mean for VPN users?
India's requirement that VPN providers register with the government and maintain user logs is becoming the international template for how to regulate VPNs without explicit bans. By 2026, this framework will spread to Pakistan, Vietnam, Thailand, and other countries. It sounds reasonable but effectively makes true no-log VPNs illegal in those jurisdictions and gives governments surveillance capability.
Conclusion: 2026 Is When Everything Changes
The VPN industry's comfortable ambiguity is ending. For years, it operated in a gray zone where regulators didn't quite know how to treat it, users didn't worry about legality, and companies could market privacy without worrying too hard about compliance.
That era is over.
2026 brings coordinated action from the EU, US, UK, and other major jurisdictions. Some countries will ban VPNs outright. Others will regulate them into a different form. Payment processing will dry up. The marketing claims will become legally fraught. The gap between what companies claim and what they can actually deliver will become impossible to hide.
Some VPN companies will survive this transition. The well-funded ones, the adaptable ones, the ones willing to compromise on privacy to maintain compliance. They'll consolidate the market. They'll become profitable. And they'll offer a product that's less ambitious than the original vision: not anonymity, just some privacy.
Others will disappear. The small ones, the idealistic ones, the ones that prioritize privacy over compliance. They can't afford the legal battles or the compliance infrastructure. They'll shut down or get acquired by bigger players.
A few will find loopholes. They'll rebrand, relocate, or restructure to avoid regulatory categories. They'll operate from privacy havens and accept payment processing friction. They'll serve a smaller market but maintain their principles.
And a parallel ecosystem of decentralized, open-source, non-commercial privacy tools will continue existing in the margins, used by serious privacy advocates and people in censored countries who have no choice.
This isn't a prediction that VPNs go away. It's a prediction that the commercial VPN industry as we know it transforms. The product changes. The market structure changes. The regulatory environment stops being a background detail and becomes the central constraint on how companies operate.
2026 is when everyone has to pick a side: Privacy or compliance. Ideology or business viability. The original vision or a compromise product that keeps regulators happy.
Cynic prediction: Most pick compliance and business viability. The VPN industry becomes less interesting, less innovative, and less genuinely privacy-protective. But it survives, consolidated among a few major players that are compliant enough to operate but claim to be privacy-forward enough to maintain credibility.
Hopeful prediction: A bifurcated market emerges. Consumer VPN companies become boring infrastructure, regulated and compliant and fine but not radical. But decentralized privacy networks and privacy-forward projects funded by nonprofits and privacy advocates create genuine alternatives. You get choice: convenient VPN, true privacy alternative, or something in between.
Realistic prediction: Both. The market splits. Some people use mainstream regulated VPNs. Others use decentralized or jurisdiction-optimized alternatives. Privacy advocates accept worse user experience for better privacy. Regular people accept worse privacy for convenience. Governments get slightly more visibility but not as much as they want. Nobody gets what they fully want, which is the classic regulatory outcome.
Whatever happens, 2026 is the year the conversation changes. From "Should I use a VPN?" to "Which regulatory framework am I operating under, and which VPN can I actually use there?"
It's not as fun as the old conversation. But it's probably more honest.

Key Takeaways
- VPN regulatory frameworks are fragmenting globally in 2026, with some countries banning VPNs outright while others implement licensing requirements modeled on India's approach
- EU's Digital Services Act compliance requirements directly conflict with true no-log VPN operations, forcing providers to choose between privacy promises and regulatory compliance
- Payment processor de-banking of VPN companies creates indirect bans more effective than explicit legislation, consolidating the market around well-funded providers
- VPN companies are exploiting loopholes through corporate VPN rebrand, privacy-haven jurisdictions, and decentralized alternatives to avoid regulatory constraints
- By 2027, the consumer VPN market consolidates to 5-10 major players, with smaller providers disappearing and a parallel ecosystem of decentralized privacy tools emerging for serious users
Related Articles
- Norton VPN Deal: 12 Months of Cybersecurity & Streaming [2025]
- Should You Use a VPN Browser? Complete Guide [2025]
- US Removes Spyware Executives From Sanctions: What Actually Happened [2025]
- The Complete Guide to Breaking Free From Big Tech in 2026
- Best Cybersecurity Journalism 2025: Stories That Defined the Year
- How to Explain VPN Importance to Your Parents: 2025 Guide
![VPN Regulation & Legislation in 2026: Loopholes, Laws & What's Next [2025]](https://tryrunable.com/blog/vpn-regulation-legislation-in-2026-loopholes-laws-what-s-nex/image-1-1767335746468.jpg)



