Apple's New Location Privacy Feature Blocks Cellular Networks from Precise Location Tracking [2025]
Your cell carrier knows more about you than you probably realize. They know where you live, where you work, which coffee shops you visit, and which hospitals you frequent. They know this because your phone is constantly sharing its precise location with the network infrastructure that keeps it connected. But Apple just rolled out a feature that throws a wrench in that surveillance machine.
The feature, called "Limit Precise Location," launched on select iPhone and iPad models in early 2026. When you enable it, your device stops sharing exact location coordinates with your cellular carrier. Instead, it shares only approximate location data, like your general neighborhood rather than your exact street address. This simple change blocks a surveillance vector that's been wide open for years: the ability for law enforcement, foreign intelligence agencies, and malicious hackers to request your movement history directly from your carrier without a warrant.
It sounds technical, but the implications are massive. We're talking about a fundamental shift in how cellular networks can collect and share your location data. For the first time, a major device manufacturer is giving users the ability to defend themselves against network-level location tracking. No VPN required. No complicated settings to configure. Just flip a toggle.
Let's break down what's actually happening here, why it matters, and what it means for your privacy going forward.
Understanding How Cellular Location Data Collection Works
Before we can understand why Apple's new feature is significant, we need to look at how cellular networks collect location data in the first place. Most people assume their location privacy is entirely controlled by app permissions and GPS settings. They think as long as they don't give an app permission to access their location, they're safe. That's only half the story.
When your phone connects to a cellular network, it performs what's called "cell site selection" or "cell site registration." Your device communicates with nearby cell towers to determine which ones provide the strongest signal. This is a fundamental requirement of how mobile networks work. The phone doesn't just pick any tower; it goes through a process where it measures signal strength from multiple towers and registers with the strongest one.
Here's where location data enters the picture: the cell carrier knows exactly which tower your phone is connecting to. They also have detailed records of every tower your device has registered with over time. By combining this information with the known locations of cell towers, the carrier can triangulate your approximate location. With enough data points from multiple towers, they can determine your position with surprising precision.
But there's another layer to this. Modern cellular devices do something more revealing. They can share their GPS-derived location directly with the carrier. When your device sends this information, it's not just approximate. It's exact. It includes latitude and longitude coordinates accurate to a few meters.
This is the critical part that most people don't understand: your device itself is voluntarily sending this precise location information to your cell carrier. It's not the carrier extracting the information from cell tower triangulation. It's your phone, on behalf of the network infrastructure, actively transmitting its GPS coordinates. This happens in the background, independent of any app permissions you've granted.
Why does the carrier want this information? There are legitimate reasons. During emergency calls, carriers use precise location data to help first responders find you quickly. The Enhanced 911 system (E911) requires carriers to provide location accuracy within 50 meters for 67% of calls and within 150 meters for 90% of calls. For this to work, the phone needs to share its precise location with the network.
But precise location data serves another purpose for carriers: network optimization and billing. The carrier can use location information to understand network usage patterns, manage congestion, and optimize infrastructure. They can also use it for targeted services and analytics.
The problem is that this data, once collected and stored by the carrier, becomes vulnerable to abuse. Law enforcement can request it through legal processes (not always warrants). Foreign intelligence agencies can try to access it through hacking. Malicious actors inside the carrier can steal it. And the data itself can be breached, exposing millions of people's location histories.
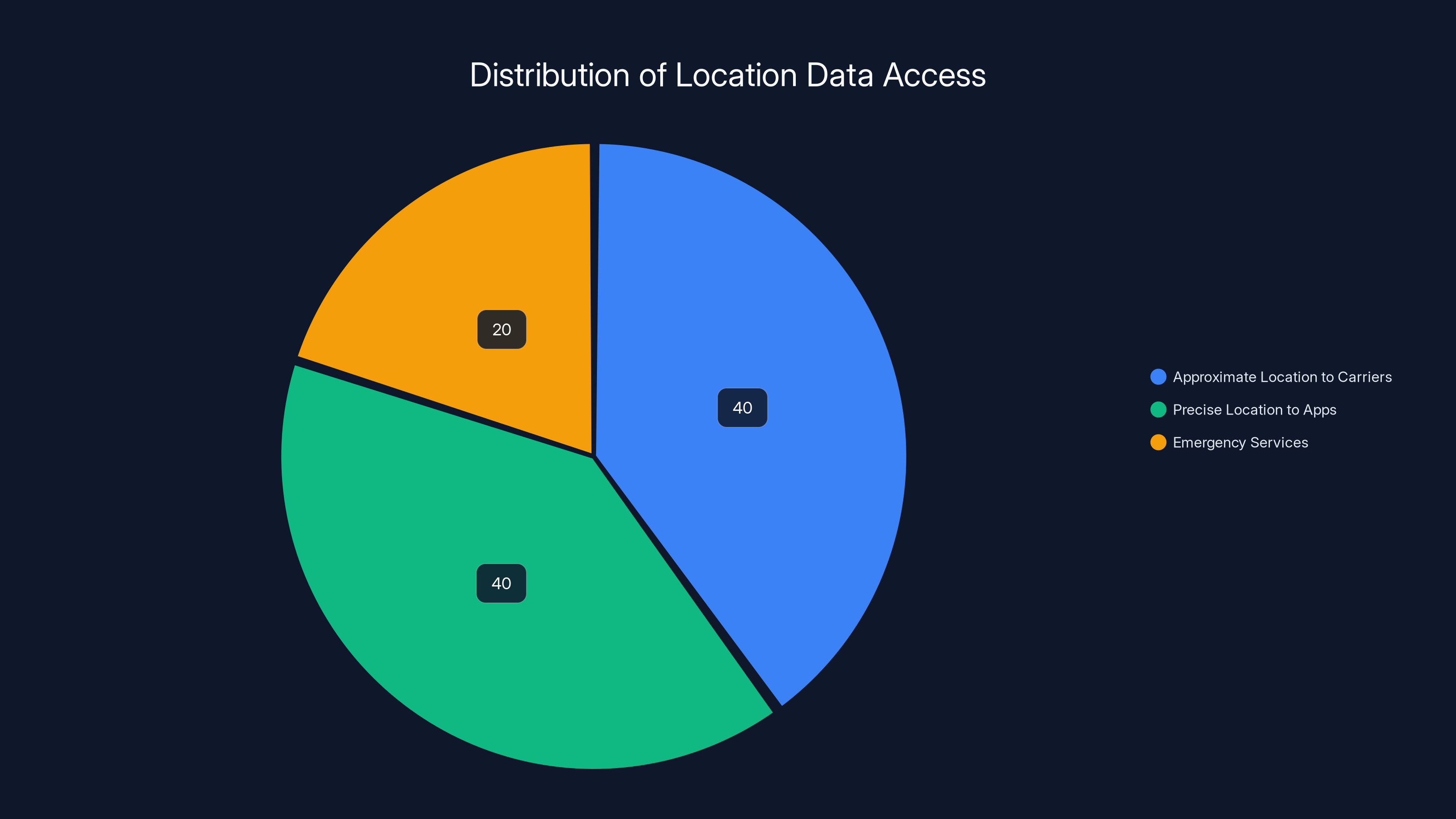
With Apple's Limit Precise Location, carriers receive only approximate location data, while apps and emergency services maintain access to precise data. Estimated data.
Why This Vulnerability Has Been Ignored for Decades
The ability for cell carriers to collect and share precise location data has been a privacy vulnerability since the early 2000s when GPS became standard on mobile phones. Yet remarkably few people have raised concerns about it, and even fewer have demanded solutions.
Part of the reason is technical complexity. Location data collection at the network level is invisible to users. Unlike app permissions, which pop up and ask for your consent, network-level location sharing happens silently. You don't see it happening. You don't get a notification about it. There's no "Allow or Deny" dialog. Most people have no idea their carrier is collecting this data at all.
Another reason is regulatory capture. The carriers themselves benefit from collecting this data. They argue it's necessary for network operations, emergency services, and customer service. Regulators, particularly the FCC, have been slow to mandate privacy protections at the network level. The carriers have successfully lobbied to keep things as they are.
There's also the trust factor. For decades, the assumption was that only "authorized" entities could access this data. Law enforcement needs a warrant. The carrier won't share it with random strangers. This assumed safety meant that many security researchers didn't prioritize this attack vector. They focused on more visible threats like malware and phishing.
But over the past five years, the vulnerabilities became impossible to ignore. Researchers demonstrated that hostile governments were accessing carrier location data. Hackers were breaching carriers and stealing years' worth of location histories on millions of people. The Salt Typhoon breaches at AT&T and Verizon exposed the reality that sophisticated attackers could access this data with relative ease.
These breaches made it clear that the security of carrier-held location data couldn't be trusted. If the carriers themselves couldn't protect it, then users needed the ability to prevent the data from being collected in the first place.
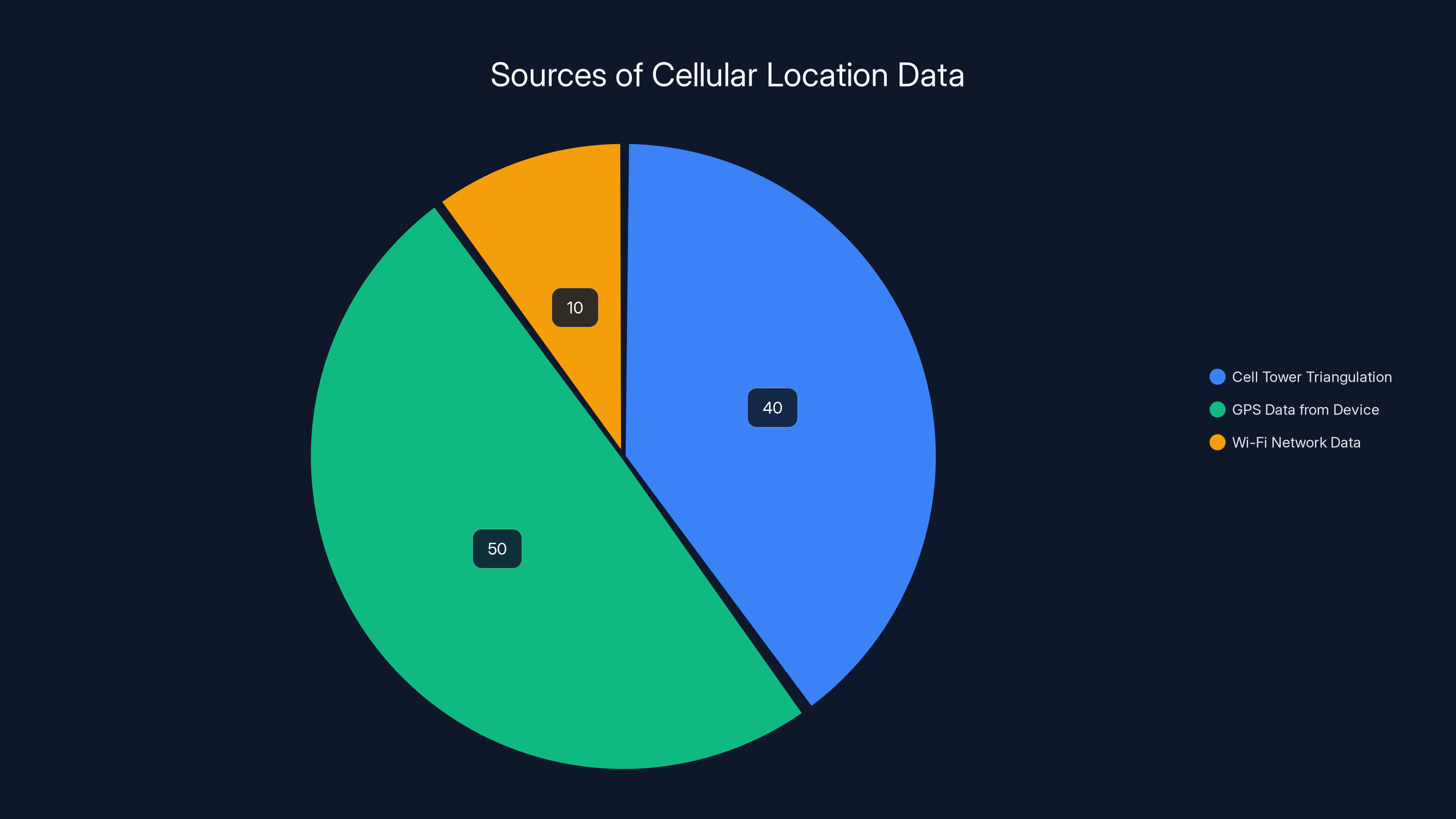
Cellular networks primarily use GPS data from devices (50%) and cell tower triangulation (40%) to determine location, with a smaller contribution from Wi-Fi network data (10%). Estimated data.
The Salt Typhoon Breaches and the Wake-Up Call
In late 2024 and early 2025, the security research community was rocked by revelations about a Chinese government-backed hacking group called Salt Typhoon. These hackers had penetrated major U.S. telecommunications companies, including AT&T, Verizon, and others. What made these breaches particularly alarming was their scale and sophistication.
Salt Typhoon wasn't after credit card numbers or passwords. They were targeting call records, text messages, and location data on high-value targets. The group was specifically interested in the communications and movement patterns of senior U.S. government officials, military personnel, and intelligence community members. They had access to these systems for months without detection.
What Salt Typhoon demonstrated was that network-level location data, once captured by carriers, is a prized target for hostile intelligence agencies. The data is so valuable because it provides a complete movement history without requiring access to the target device. A person might delete their browser history or wipe their phone, but their carrier still has months of location records that show everywhere they've been.
Further complicating the situation are vulnerabilities in the cellular network protocols themselves. Security researchers have long known that the core cellular network architecture has design flaws that make it vulnerable to location tracking, eavesdropping, and impersonation attacks. These vulnerabilities exist at the SS7 and Diameter protocol layers, which are the fundamental infrastructure that carriers use to communicate with each other.
These protocol vulnerabilities have been exploited by surveillance vendors for years. Companies like Cellebrite and Phantom, which sell surveillance technology to law enforcement and intelligence agencies, can take advantage of these weaknesses to access location data on targets. Hackers have also exploited these vulnerabilities to track individuals or intercept their communications.
The combination of known protocol vulnerabilities, demonstrated hacking by foreign governments, and the massive value of location data all pointed to the same conclusion: the current system where carriers collect and store precise location data is fundamentally broken. Users needed protection at the device level.
How Apple's Limit Precise Location Feature Works
Apple's solution is elegantly simple in concept but complex in execution. When you enable "Limit Precise Location," the device changes what it sends to the cellular network during the E911 position reporting process. Instead of sending GPS-derived precise coordinates, it sends a rounded or reduced-precision location.
The technical implementation involves modifying how the device responds to "Location Information Request" (LIR) messages from the carrier. When a carrier requests location information for E911 purposes, the device can choose to provide either precise location data (derived from GPS) or coarse location data (derived from cell tower information). By default, devices have been sending precise data.
With Limit Precise Location enabled, the device responds with coarse location data instead. This coarse data is still accurate enough for emergency services to find you (typically within a few hundred meters to a kilometer), but it's not precise enough for law enforcement or intelligence agencies to track your exact movements.
The feature requires cooperation from the carrier because the carrier needs to understand that the device is intentionally providing coarse data and not treat it as a network error or fallback. Apple has worked with a select group of carriers to implement this, which is why the feature is initially only available on a handful of networks globally.
Crucially, enabling Limit Precise Location does NOT affect the precision of location data you share with apps or with emergency responders. When you call 911, emergency dispatchers still receive precise location information. Apps that have location permission still receive precise location data. The feature only affects what gets sent to the carrier's network infrastructure.
This is a clever design choice. It maintains the functionality that legitimate users need (emergency response accuracy, app functionality) while blocking the channel through which carriers have been collecting location surveillance data. The carrier still knows approximately where you are (from cell tower registration), but they no longer have a record of your exact coordinates.

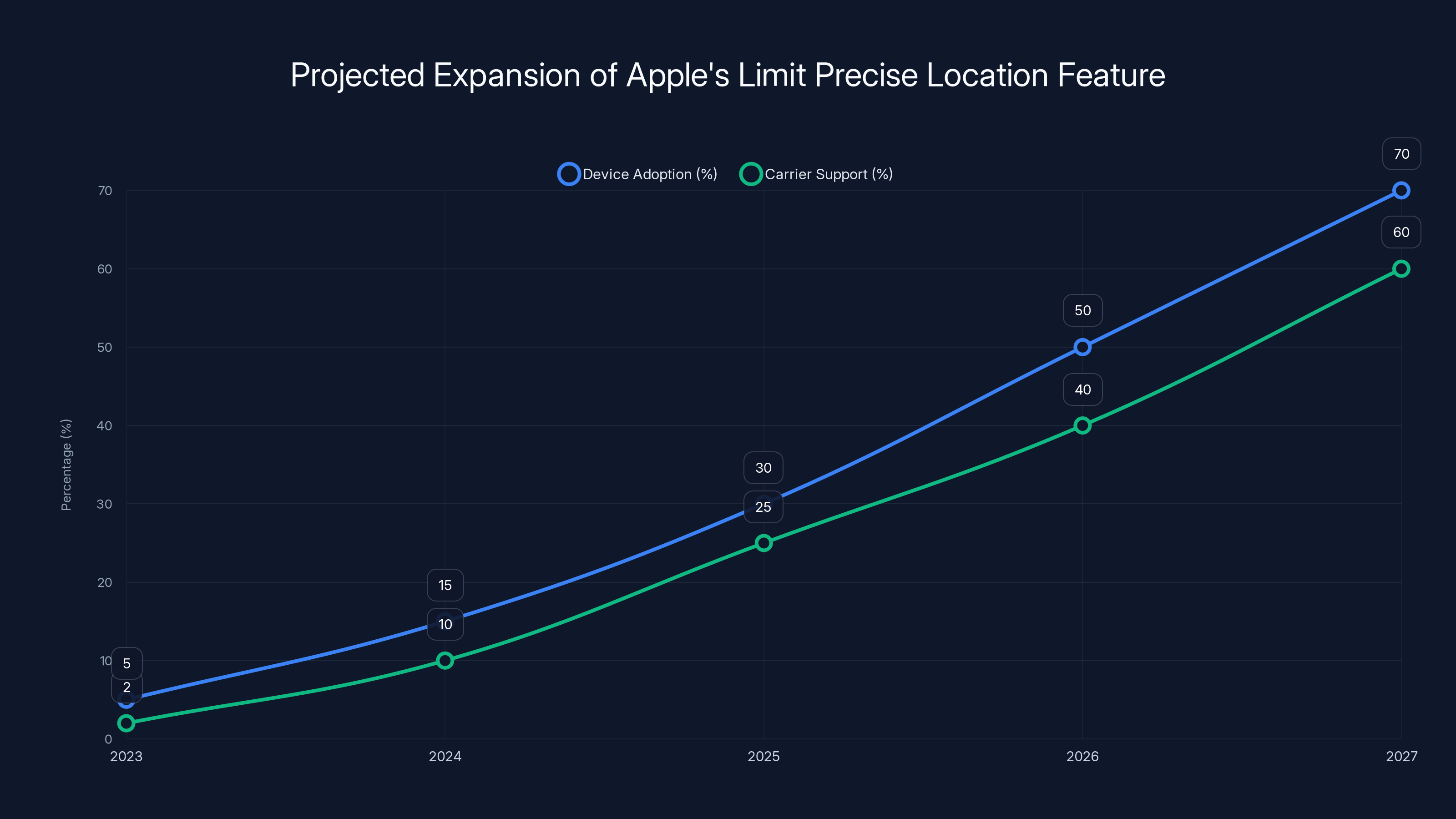
Estimated data suggests that by 2027, 70% of devices may adopt the feature, with 60% carrier support, significantly impacting privacy norms.
Which Devices and Carriers Support the Feature
Initially, Apple's Limit Precise Location feature is incredibly limited in availability. It's only supported on three device models: iPhone Air, iPhone 16e, and iPad Pro (M5) Wi-Fi + Cellular. These are among Apple's newest devices running iOS 26.3 or iPadOS 26.3 or later.
The carrier support is even more restricted. Only a handful of global carriers have implemented the necessary technical changes to support the feature. In the United States, it's available on Boost Mobile. In the United Kingdom, it works with EE and BT. In Europe, Deutsche Telekom in Germany has implemented it. In Southeast Asia, both AIS and True in Thailand support it.
This limited rollout reflects the complexity of implementing the feature at the carrier level. Each carrier needs to modify their network infrastructure to properly handle devices that send coarse location data instead of precise data. They need to update their E911 systems, their location request handlers, and their billing systems. For large carriers managing millions of devices, this is a significant undertaking.
Apple hasn't announced plans to expand the feature to older devices, but it's likely that future iPhone and iPad models will include support as more carriers implement their infrastructure changes. The company also hasn't publicly committed to pushing carriers to adopt the feature more widely, which suggests the expansion will depend on carriers' own initiative.
The limited availability is a frustration for privacy advocates. They argue that Apple should be more aggressive about requiring carriers to support the feature as a condition of selling iPhones on their network. Currently, the feature is optional, and carriers can choose not to implement it without any consequences.
However, the rollout approach does make sense from a business perspective. Apple wanted to demonstrate that the feature works and that emergency services can handle coarse location data. By limiting the initial release to a few carriers, Apple can gather real-world data about how the feature performs, whether emergency responders encounter any issues, and what technical challenges arise. This information will be valuable for broader rollout.
The Impact on Law Enforcement Location Tracking
From a law enforcement perspective, Limit Precise Location is a significant problem. Police agencies have become accustomed to requesting location data from carriers as part of criminal investigations. They use this data to establish timelines, place suspects at crime scenes, and track fugitives.
Traditionally, law enforcement obtains this data through several mechanisms. The most common is a "cell-site location information" (CSLI) request. This is a legal request for historical location records. In the United States, the legal standard for CSLI requests has been ambiguous. The Supreme Court clarified in the 2018 Carpenter v. United States decision that accessing historical CSLI requires a warrant, but law enforcement agencies have found various workarounds to this requirement.
One workaround is the "pen register" or "trap and trace" device, which law enforcement can obtain with a less stringent standard than a full warrant. Another is the "emergency disclosure" exception, which allows carriers to voluntarily disclose location data when law enforcement claims an emergency requires it. Police have been criticized for overusing this emergency exception to access location data in non-emergency situations.
With Apple's Limit Precise Location feature enabled, the location data that law enforcement receives in response to these requests becomes less useful. Instead of being able to pinpoint someone's exact location at a particular time, they get a general neighborhood. This doesn't destroy the investigative value of the data, but it significantly reduces it.
For active investigations, this is a manageable setback. Law enforcement can still corroborate location data with other evidence, surveillance footage, and witness statements. For trying to establish a timeline or rule out a suspect, coarse location data is often sufficient.
For the kind of dragnet location tracking that law enforcement has increasingly been practicing, however, the feature is much more problematic. Agencies like the DEA and FBI have been purchasing bulk location data from data brokers. This data, derived from cell carriers and other sources, is used to identify people at protests, religious gatherings, and other sensitive locations. With Limit Precise Location, the data available to these agencies becomes less granular.
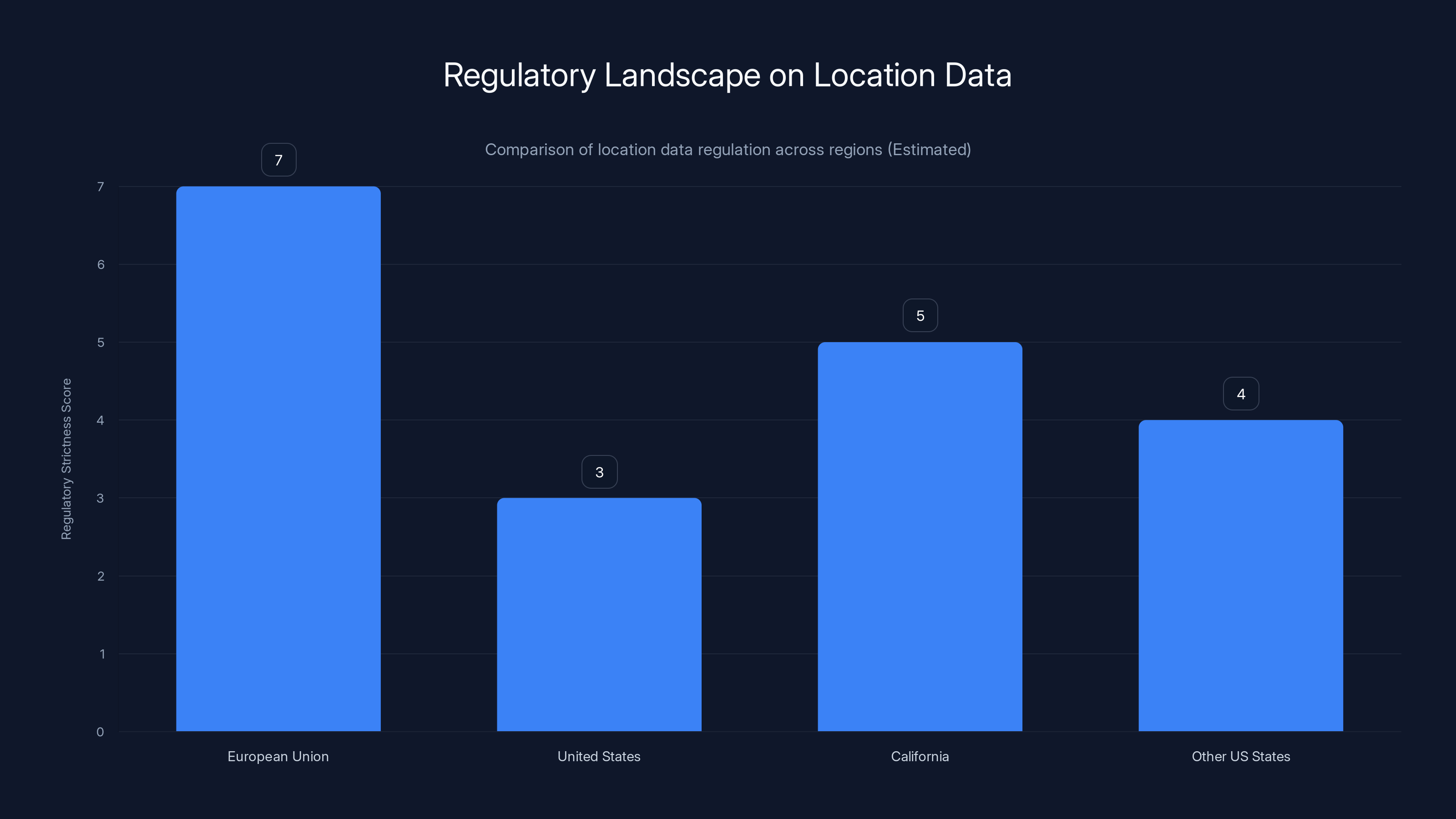
The European Union has the strictest regulations on location data due to GDPR, while the United States lacks a comprehensive federal law, resulting in varied state-level regulations. (Estimated data)
National Security Implications
From a national security perspective, Apple's feature has more significant implications than its impact on routine criminal investigations. Intelligence agencies have long relied on location data from carriers for surveillance of foreign agents, terrorists, and other national security targets. When targeting a known terrorist suspect, access to their precise location history is invaluable for understanding their network, identifying associates, and predicting their next movements.
Apple's feature doesn't block intelligence agencies' access to carrier location data entirely. It just makes the data less precise. For many intelligence purposes, this is acceptable. A coarse location is often sufficient to identify patterns and movements.
However, for the highly detailed surveillance that governments increasingly depend on, the feature is a setback. This is particularly true for five-eyes intelligence agencies (U.S., U.K., Canada, Australia, New Zealand), which have been among the most sophisticated consumers of carrier location data.
The U.S. National Security Agency (NSA) has historical relationships with major carriers that provide it access to location data streams. The details of these programs are classified, but reporting by the Wall Street Journal and others has revealed that the NSA has been using carrier location data for purposes well beyond counterterrorism. The agency has accessed location data to track Americans' movements within the United States, raising constitutional concerns.
Apple's feature doesn't break these intelligence programs, but it does degrade their effectiveness for targets using supported devices and carriers. Intelligence agencies can adapt by using other sources of location data, but the loss of carrier-derived precise location is still a meaningful degradation of their capabilities.
National security officials have reportedly expressed concern about the feature. They argue that it could hinder legitimate counterterrorism and counterintelligence operations. Privacy advocates counter that if intelligence agencies need access to location data, they should obtain warrants like any other entity, rather than relying on data collection pipelines that have historically been used without appropriate oversight.
How Malicious Hackers Abuse Carrier Location Data
Beyond law enforcement and national security agencies, carrier location data has long been a target for malicious actors. Hackers breach carriers to steal location data. They sell it. They use it to track targets. They use it for stalking, harassment, and worse.
The most prominent recent example is the Salt Typhoon breach, but there have been many others. In 2022, federal law enforcement investigated a major breach at a mobile carrier that exposed location data on millions of people. Cybercriminals have established a market for stolen carrier location data. In underground forums, you can purchase location histories on specific individuals for prices ranging from a few hundred to a few thousand dollars, depending on the time period and granularity of the data.
Stalkers and domestic abusers have been known to access their targets' location data through breaches or insider help at carriers. Criminals use location data to identify vulnerable robbery targets. Data brokers aggregate carrier-derived location data and sell it to insurance companies, employers, and other entities.
Apple's Limit Precise Location feature doesn't eliminate this threat entirely. Attackers can still infer general location information from coarse data. But it does reduce the value of the stolen data. A complete movement history with coarse resolution is less useful than one with precise resolution.
For someone trying to stalk or track another person, the difference between knowing someone was "in the downtown area" versus knowing they were "at 123 Main Street at 3:47 PM" is significant. The precise location is actionable. The coarse location requires additional information and surveillance to pin down the target.
This is particularly important for vulnerable populations. Stalking victims, abuse survivors, and activists are disproportionately harmed by precise location tracking. Making the data less precise provides them with an additional layer of protection.
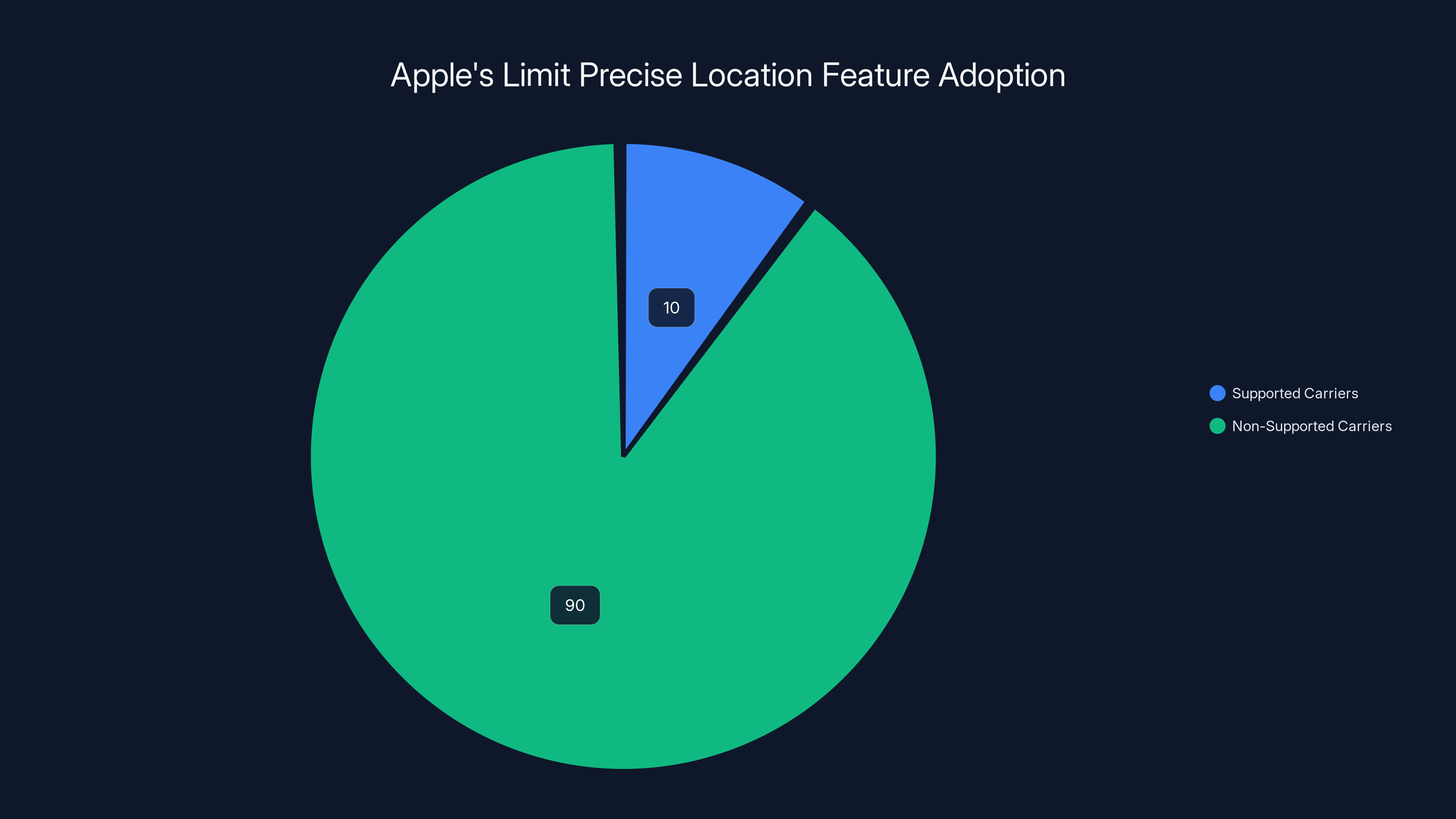
Estimated data shows that currently, only a small percentage of carriers globally support Apple's Limit Precise Location feature, highlighting its limited initial rollout.
The Technical Details and Limitations of the Feature
Understanding the limitations of Apple's feature is important for having realistic expectations about what it actually protects. The feature is not a complete defense against location tracking. It's a narrowly scoped solution to a specific problem: the collection of precise location data by cellular networks.
When Limit Precise Location is enabled, Apple's devices report coarse location information to the carrier, typically at the cell-tower level. Cell tower location granularity varies, but is typically accurate to within a few hundred meters to several kilometers, depending on network density. In rural areas, this could be several kilometers. In dense urban areas, it might be a few hundred meters.
This coarse location data still reveals meaningful information about a person's movements. If you're tracked at the neighborhood level over time, patterns emerge. Researchers have shown that it's often possible to identify someone's home and workplace using only neighborhood-level location data. Combining coarse location with other information (purchase records, web browsing history, social media posts) can narrow down a person's exact location.
The feature also doesn't prevent carriers from using other methods to determine location. Cell tower registration patterns, which occur independently of the Limit Precise Location feature, still reveal approximate location. Carriers can combine multiple data points to improve location accuracy even when precise data isn't available.
Another limitation is that the feature only affects data sent to the carrier for network purposes. It doesn't affect location data that apps send to their own servers. If you're using Google Maps, Apple Maps, or any other location-aware application, those apps still receive precise location data. The servers of those companies still know where you are.
The feature also requires active enablement. Most users won't enable it. Apple hasn't made it the default. This means that by default, the privacy problem persists for the vast majority of iPhone and iPad users.
Because carrier support is so limited, many users won't have the option to enable the feature at all. They'll use a carrier that hasn't implemented support. For these users, there's no immediate benefit.

Privacy Implications Beyond Carriers
While Apple's feature addresses a specific privacy vulnerability at the carrier level, the broader question remains: how much location data should companies collect and store about us? The feature provides a partial answer: when it comes to carriers, maybe less. But the feature also highlights how fragmented our approach to location privacy has become.
Consider the various entities that currently have access to your location data. Your carrier has it. Apps on your phone have it. Google has it (from Maps, Android location services, web browsing). Apple has it (from Siri, Maps, Health). Facebook, Instagram, TikTok, and Snapchat have it. Your credit card company knows your location through merchant data. Your banking app has it. Your car manufacturer might have it. Retailers you visit have location inferences from purchase patterns.
Each of these entities has requested data collection from you. Some have asked for explicit permission. Some have collected it in the background. The privacy landscape has become so fragmented that no single technical solution can address all the vulnerabilities.
Apple's feature is valuable because it addresses a vulnerability that users have minimal control over. You can choose not to use Google Maps. You can turn off location for apps. You can't, however, easily prevent your carrier from collecting location data without also preventing emergency services from working. That's what made this vulnerability particularly insidious.
But the feature also highlights the limitations of individual companies making privacy improvements. Apple can improve the privacy of location data sent to carriers, but it can't improve the privacy of location data that apps send to their own servers. It can't force other companies to stop collecting location data. It can't prevent governments from exploiting network protocol vulnerabilities.
A comprehensive approach to location privacy would require changes at multiple levels: device level, application level, network level, and regulatory level. Apple's feature addresses one small piece of this puzzle.
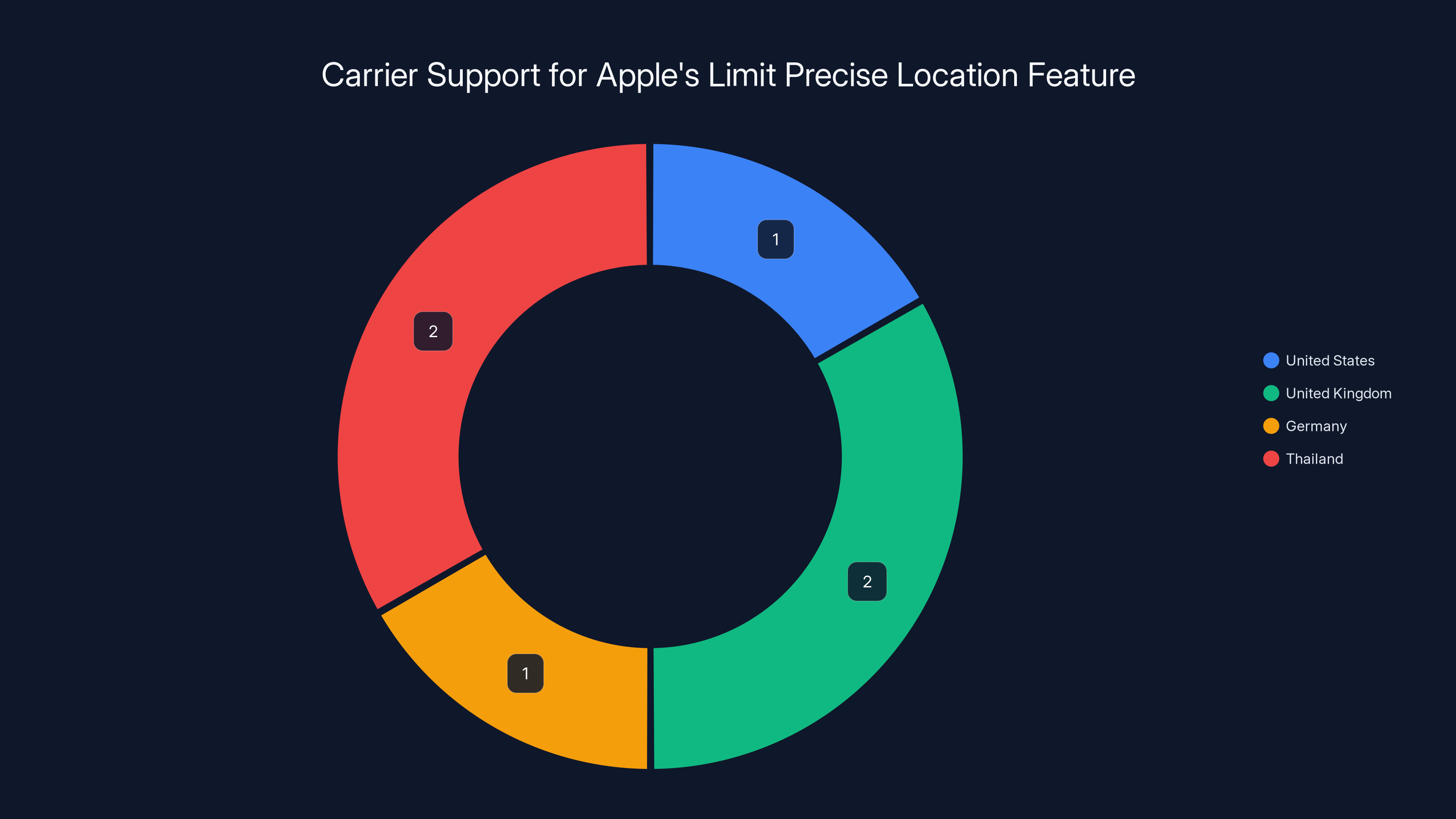
The feature is supported by a limited number of carriers globally, with only six carriers across four regions. This highlights the complexity of implementing the feature at the carrier level.
How to Enable and Use the Feature
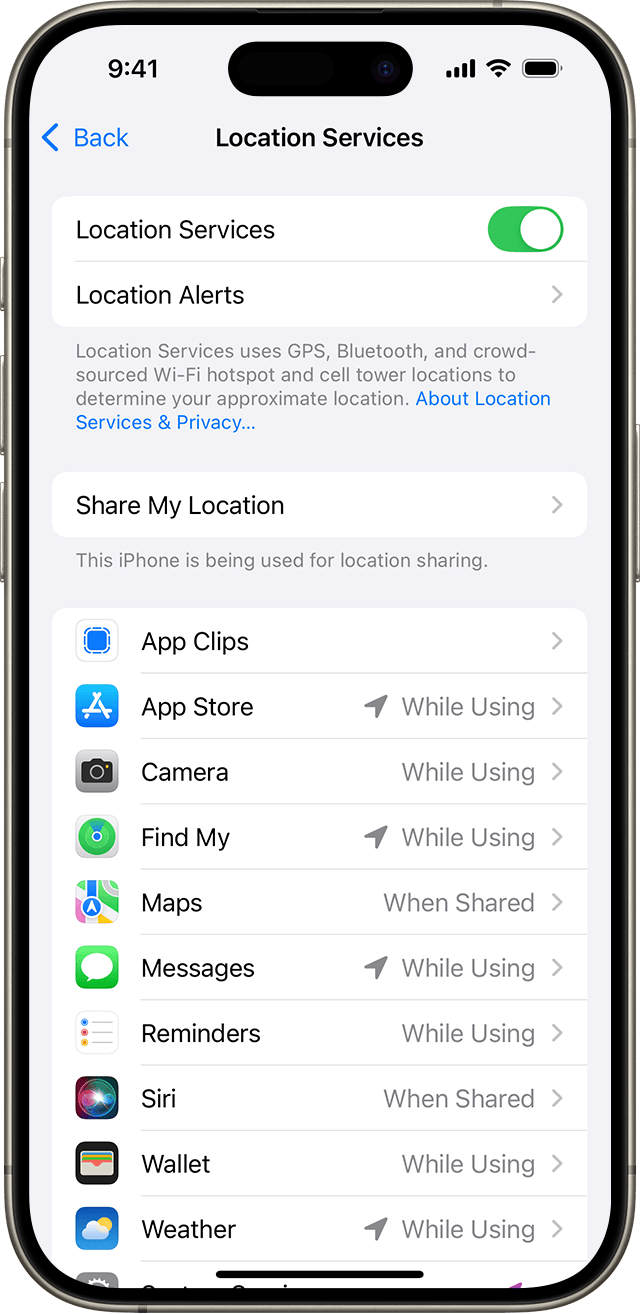
For users whose devices and carriers support Limit Precise Location, enabling the feature is straightforward. On iOS, you go to Settings > Privacy & Security > Location Services. At the bottom of the screen, under "Limit Precise Location," you toggle on the switch. That's it. The feature takes effect immediately.
On iPad, the process is identical. Settings > Privacy & Security > Location Services > toggle on Limit Precise Location.
Once enabled, the feature works invisibly in the background. You don't get notifications about it. You don't see any indication that it's active. The only way to know it's working is if you look at the setting again.
Some users might wonder if enabling the feature will break their 911 service or prevent emergency location reporting. It won't. The technical implementation preserves the ability for emergency services to receive location data. When you call 911, the dispatcher will still receive location information. It will be less precise than if the feature were disabled, but it will still be functional.
Apps that require location access will continue to work normally. Navigation apps, location-based social apps, and mapping apps all receive precise location data directly from the device, not from the carrier. The Limit Precise Location feature doesn't affect this.
Users might also wonder about battery life. Limiting the precision of location data sent to the network might theoretically improve battery life by reducing the frequency of GPS location requests. However, the actual impact on battery life is likely minimal. Modern iPhones are efficient about location collection, and the network-level location requests happen independent of app-level location collection.
Comparing Limit Precise Location to Other Privacy Features
Apple has a history of rolling out privacy features that frustrate other companies while claiming to protect users. App Tracking Transparency blocked third-party apps from accessing the advertising identifier. Mail Privacy Protection hides whether you've opened emails. Intelligent Tracking Prevention limits cross-site tracking in Safari. These features have been controversial because they do provide real privacy benefits, but they've also benefited Apple by disadvantaging competitors.
Limit Precise Location is different. It's not primarily about benefiting Apple relative to competitors. It doesn't give Apple a business advantage the way App Tracking Transparency did. The feature is genuinely about protecting users from a surveillance vulnerability that affects everyone equally.
Comparing it to other privacy features, Limit Precise Location is less noticeable to users than App Tracking Transparency, which apps complained about loudly. It's more useful than Mail Privacy Protection, which provides a privacy benefit that many users don't particularly care about. It's conceptually similar to Intelligent Tracking Prevention, in that it limits the ability of external entities (carriers instead of ad networks) to track a user's activities.
One important difference is that many of Apple's previous privacy features were controversial because they appeared to change the fundamental business model of the internet. Limiting tracking ads is seen by some as limiting the ad-supported web. Limit Precise Location, by contrast, doesn't challenge any fundamental business models. Carriers still make money without precise location data. Emergency services still function. It's a pure privacy win without obvious downside, which is why it hasn't generated the same level of backlash.
Other device manufacturers could theoretically implement similar features. Google, for example, could enable Limit Precise Location on Android devices. In fact, Android already has granular location permissions that allow users to grant apps only approximate location. Android also has privacy features like randomized MAC addresses and background location limits. However, Android hasn't implemented a feature specifically to limit location data sent to the carrier, probably because Google hasn't prioritized it.
What This Means for Privacy-Conscious Users
For users who care about privacy, Limit Precise Location is a meaningful but limited win. If your device and carrier support it, enabling the feature is a no-brainer. There's no downside and a clear privacy benefit. But it's important to have realistic expectations about what the feature does.
It doesn't make you anonymous. Carriers still know approximately where you are. Combined with other data, your location can still be inferred. If you're using apps that collect precise location, that data is still being collected. If you're using services like Google Maps or Apple Maps, your location is still being shared.
The feature specifically protects you against three threats: law enforcement location tracking, foreign intelligence agency location tracking, and hackers who breach carriers. For each of these threats, the feature degrades the quality of location data available, making it less useful for surveillance purposes.
For most users, the most relevant threat is law enforcement. If you're concerned about police accessing your location history, Limit Precise Location provides meaningful protection. Police will be able to establish that you were in a general area, but not your exact location at a specific time. This makes it harder for law enforcement to establish alibis or place you at crime scenes.
For users concerned about foreign governments tracking them, the protection is meaningful but not complete. Intelligence agencies can use other data sources. But the feature does eliminate one channel through which they can access location data.
For users concerned about criminal hackers, the feature provides some protection. A hacked location database containing coarse location data is less valuable than one containing precise data. But it's still privacy-sensitive information.
Beyond these specific threats, the feature also provides a philosophical benefit. It represents the idea that companies should collect the minimum amount of data necessary to provide services. Carriers don't need precise GPS coordinates to operate their networks or provide service. They need enough information to route calls and messages. Limiting the precision of data collected aligns with this principle.
The Regulatory Landscape and Future Developments
Apple's Limit Precise Location feature exists in a regulatory vacuum. The United States, European Union, and other jurisdictions have been slow to regulate location data collection at the carrier level. This has allowed carriers to continue collecting and storing precise location data without meaningful oversight.
The GDPR in Europe has created some constraints. Under GDPR, companies must have a lawful basis for processing personal data. Location data is considered personal data. Carriers must obtain consent for non-essential location processing. This has created some pressure on European carriers to limit collection, but they've largely responded by claiming that location collection is necessary for network operations and emergency services.
In the United States, there's no federal privacy law that specifically governs location data collection. The FCC has regulatory authority over telecommunications carriers, but it has been hesitant to impose strict privacy requirements. Some states have passed privacy laws (California, Colorado, Connecticut, Utah, Virginia), but these laws are inconsistent in how they treat location data.
The lack of regulation means that privacy-conscious users must rely on technical solutions like Apple's feature. This is suboptimal because it requires device manufacturers to anticipate privacy problems and implement solutions. It also limits protection to users of advanced devices from companies that prioritize privacy.
Looking forward, there are a few possible regulatory developments. The FCC could impose stricter requirements on carriers to limit location data collection. The Federal Trade Commission could target carriers for unfair privacy practices. Congress could pass a federal privacy law that explicitly restricts location data collection.
None of these seem imminent, but the conversation around location privacy is starting to change. Breaches like Salt Typhoon have raised awareness of the risks. Privacy advocates are pushing for stronger protections. Technology companies like Apple are demonstrating that technical solutions are possible.
The Carrier Perspective and Business Implications
Carriers have been quiet about Apple's Limit Precise Location feature. This silence likely reflects uncertainty about what to say. On one hand, they've benefited from being able to collect and share location data. On the other hand, they've also been victims of the breaches that have resulted from storing this data.
For carriers, location data has become a double-edged sword. They can monetize it, but they also assume significant liability for protecting it. Every breach results in regulatory scrutiny, lawsuits, and reputational damage. From a business perspective, some carriers might actually welcome a technical solution that reduces the amount of sensitive data they need to store.
Salt Typhoon breached several major carriers and stole location data on millions of people. The reputational and financial cost to those carriers has been significant. Enabling Limit Precise Location reduces the maximum exposure in future breaches. If there's no precise location data to steal, there's less liability.
However, carriers also worry about the competitive implications. If some carriers support Limit Precise Location and others don't, customers might switch to carriers that protect their privacy. Conversely, if Limit Precise Location becomes widespread and expected, carriers that don't support it might face regulatory pressure.
For now, most carriers are taking a wait-and-see approach. They're allowing Apple to demonstrate that the feature works without their enthusiastic support. As more carriers implement it, especially if regulatory pressure increases, more will likely adopt it.
The business model question is: how does the carrier ecosystem change if carriers can no longer collect and share precise location data? This is a smaller concern than it might initially appear. The vast majority of carrier revenue comes from service fees, not from location data monetization. The location data is useful for internal purposes (network optimization) and for law enforcement/intelligence relationships, but it's not a primary revenue driver.
Comparing to Alternative Privacy Solutions
Users who want to protect their location privacy have several options beyond Apple's Limit Precise Location. Each approach has different trade-offs in terms of effectiveness, usability, and impact on device functionality.
VPNs are a popular privacy solution, but they don't actually protect location data sent to carriers. A VPN encrypts internet traffic, but your phone still has to connect to a cell tower to get cellular service. The carrier still knows your approximate location from cell tower registration. VPNs don't help with this.
Faraday cages or signal-blocking pouches can prevent your phone from connecting to any cellular network. This protects you from carrier location tracking, but it also breaks all cellular functionality. You can't make calls, send texts, or use mobile data. This is impractical for most users.
Switching carriers might help if you switch to a carrier that doesn't collect location data. However, carriers don't advertise this distinction, and most collect location data for emergency services purposes. Practically speaking, there are no carrier options that completely avoid location collection.
Using WiFi-only devices avoids carrier location collection entirely, but breaks the functionality of cellular devices. This is only practical for specific use cases where WiFi is available.
Using a dumb phone without GPS avoids precise location collection but requires abandoning a smartphone. Most modern users aren't willing to do this.
Using burner phones can reduce location tracking exposure, but requires constantly switching devices and is impractical for most users.
Compared to these alternatives, Limit Precise Location is elegant because it solves a specific privacy problem without requiring users to sacrifice functionality. You keep your smartphone. You keep cellular service. Emergency services still work. But the carrier no longer has a detailed record of your exact coordinates.

Future Expansion and Long-Term Impact
Apple's Limit Precise Location feature is currently very limited in availability. It's only on a few device models and a handful of carriers. But if it's successful, we might expect to see significant expansion over time.
Apple will likely add support for the feature to older iPhone models in future iOS updates. This would require the older devices to have the right cellular hardware (which most do), but Apple has historically been conservative about backporting major features to older hardware.
Carrier support is likely to expand more slowly. Each carrier needs to make technical changes to their infrastructure. However, as more carriers implement support, the feature becomes more valuable to Apple as a marketing differentiator. Eventually, Apple might leverage its market power to require carriers to support the feature as a condition of being an authorized seller of iPhones.
Other device manufacturers might also implement similar features. Google could enable Limit Precise Location on Android devices. Samsung could do it on its phones. Once the feature becomes standard across device platforms, carriers would need to support it or risk losing customers.
From a user perspective, the long-term impact depends on adoption. If only a small percentage of users enable the feature, carriers continue collecting precise location data on the majority of devices. The feature becomes a privacy tool for privacy-conscious users, but doesn't fundamentally change the carrier location data ecosystem.
If adoption becomes widespread, the feature could shift the entire industry. Carriers would accumulate less precise location data. The maximum exposure in future breaches would be reduced. Law enforcement and intelligence agencies would have less precise location data available.
Regulators might also look at Apple's feature as a model. If users can opt out of precise location collection with a simple toggle, why can't regulators require that all carriers provide the same option? This could eventually become a legal requirement rather than a voluntary feature.
Conclusion: A Small Step Toward Location Privacy
Apple's Limit Precise Location feature represents a meaningful but limited step toward protecting location privacy. It addresses a specific vulnerability: the collection of precise location data by cellular carriers. For users whose devices and carriers support it, enabling the feature provides real privacy protection against law enforcement, intelligence agencies, and hackers.
The feature's limitations are important to acknowledge. It doesn't prevent location tracking entirely. It doesn't affect location data collected by apps or other services. It doesn't solve the broader problem of how companies collect and use location data. It only addresses one specific vector of location data collection.
However, this focused approach is exactly what makes the feature valuable. Rather than attempting to solve the entire location privacy problem, Apple focused on a specific vulnerability that users had no control over. Carriers were collecting precise location data, and users had no way to opt out without breaking critical functionality like emergency services.
Apple's solution elegantly addresses this specific problem while maintaining the functionality that legitimate uses of location data depend on. Emergency services still work. Apps still function. But the carrier no longer has a record of your exact location.
The feature also represents a shift in how device manufacturers think about privacy. Rather than leaving location privacy entirely to users to manage through app permissions and privacy settings, Apple recognized that some location data collection happens at the network level, and users need protection there too.
For the broader location privacy landscape, the feature is significant not because it solves the problem, but because it demonstrates that technical solutions are possible. Once users get a taste of being able to prevent location data collection without sacrificing functionality, they'll likely demand similar options for app-level location data, location data sent to servers, and location data collected through other means.
The feature also has implications for the regulatory landscape. If a simple technical toggle can protect users from location tracking, why shouldn't all carriers offer this option? Why shouldn't it be the default? These questions might eventually lead to regulatory action.
For now, Limit Precise Location is a tool for privacy-conscious users whose devices and carriers support it. Over time, as support expands, it could become a standard feature that everyone uses. And eventually, it might spark broader changes in how location data is collected and protected across the entire digital ecosystem.
The feature won't stop governments or sophisticated hackers who are determined to track you. It won't prevent the companies whose apps and services you use from collecting location data. But it does prevent your carrier from maintaining a detailed record of your movements. In a world where location data has become a currency of surveillance, that's a meaningful protection.
FAQ
What is Apple's Limit Precise Location feature?
Apple's Limit Precise Location is a privacy feature available on select iPhone and iPad models that prevents cellular carriers from collecting precise GPS coordinates. When enabled, devices share only approximate location data (such as neighborhood-level information) with carriers instead of exact coordinates. The feature maintains full functionality for emergency services and apps while reducing the precise location data available to carriers, law enforcement, and potential hackers who breach carrier systems.
How does Limit Precise Location differ from app-level location permissions?
App-level location permissions control what location data specific applications can access on your device. Limit Precise Location, by contrast, controls what location data your device sends to your cellular carrier at the network level. Apps can still receive precise location data from your device even if Limit Precise Location is enabled. The feature specifically addresses the separate vulnerability of carriers collecting GPS coordinates for network purposes, independent of what apps you've granted location permission.
Will Limit Precise Location affect my emergency 911 calls?
No. Apple's implementation preserves the ability to provide emergency services with location information. When you call 911, emergency dispatchers still receive location data that is accurate enough for first responders to find you. The technical implementation ensures that devices can respond to emergency location requests while still limiting non-emergency precise location data sent to carriers for normal network operations.
Why is this feature only available on certain carriers?
The feature requires technical changes at the carrier level to function properly. Carriers need to modify their network infrastructure to understand and correctly process devices that intentionally send coarse location data instead of precise data. This infrastructure change requires updates to E911 systems, location request handlers, and billing systems. Limited initial availability allows Apple to work with willing carriers to validate that the feature works correctly before broader rollout.
Can carriers still track my location if I enable Limit Precise Location?
Carriers can still determine approximate location through cell tower registration, which is independent of the Limit Precise Location feature. Devices must register with cell towers to maintain cellular service, and carriers know which towers devices connect to. This allows carriers to narrow down your location to a general area. However, without precise GPS coordinates, they cannot determine your exact location or build a detailed record of your precise movements.
What happens to my location data if it's already been collected by my carrier?
Limit Precise Location only affects new location data collected after you enable the feature. Historical location data that carriers have already collected remains in their systems and is subject to the same access controls and security (or lack thereof) as before. If you're concerned about historical data, you could contact your carrier to request information about what location data they have on you and ask them to delete it, though carriers aren't required to comply with such requests in most jurisdictions.
Can malicious hackers still steal location data from carriers even with Limit Precise Location enabled?
Hackers can still breach carriers and steal the location data that's available, including coarse location information. However, coarse location data is significantly less valuable for most malicious purposes than precise location data. It's sufficient to identify general movements but not specific locations. Hackers selling stolen location data on black markets will find coarse data less valuable and will demand lower prices for it, reducing the incentive to target location data in breaches.
Will Limit Precise Location come to older iPhones and iPads?
Apple hasn't officially announced plans to backport Limit Precise Location to older devices. The feature currently requires newer models with the latest cellular hardware. However, Apple might add support for older models in future iOS updates, particularly as carrier support becomes more widespread. The timeline for such expansion is unclear.
How does this compare to other privacy features like app privacy labels?
Limit Precise Location is a narrower feature that addresses a specific privacy vulnerability at the network level. App privacy labels, by contrast, provide transparency about what data individual apps request and use. The two features address different parts of the location privacy problem. You need both: app privacy labels to see what apps are requesting location data, and Limit Precise Location to prevent your carrier from collecting precise network-level location data. Neither feature eliminates all location tracking, but both provide meaningful protections for different vectors of location data collection.

The Bottom Line
Apple's Limit Precise Location feature won't make you completely anonymous or prevent all location tracking. But if you can access it, enabling the feature is a simple, effective way to prevent your carrier from maintaining a detailed record of your movements. In an era where location data has become a key tool for government surveillance and criminal tracking, that matters more than you might think.

Key Takeaways
- Apple's Limit Precise Location feature prevents carriers from accessing precise GPS coordinates by sharing only neighborhood-level location data
- The feature maintains full emergency service functionality while reducing data available to law enforcement, intelligence agencies, and hackers
- Currently available on only iPhone Air, iPhone 16e, and iPad Pro M5 on a handful of carriers including Boost Mobile (US), EE/BT (UK), Deutsche Telekom (Germany), and AIS/True (Thailand)
- Recent carrier breaches like Salt Typhoon demonstrated that precise location data is a high-value target for foreign governments and criminals
- The feature addresses a vulnerability that users previously couldn't control without breaking emergency services or cellular functionality
Related Articles
- Why Brits Fear Online Privacy But Trust the Wrong Apps [2025]
- Google Pixel Take a Message Audio Leak: What Happened [2025]
- License Plate Readers & Privacy: The Norfolk Flock Lawsuit Explained [2025]
- I Tested a VPN for 24 Hours. Here's What Actually Happened [2025]
- Samsung Galaxy S26 Ultra Privacy Display: How It Works [2025]
- Best VPN Under $3/Month: Advanced Features for Less [2025]
![Apple's Location Privacy Feature Blocks Cellular Networks [2025]](https://tryrunable.com/blog/apple-s-location-privacy-feature-blocks-cellular-networks-20/image-1-1769699400832.jpg)



