Illinois Data Breach Exposes 700,000: How Government Failed [2025]
Last September, something that should've been caught in the first week of deployment sat exposed on the public internet for months. The Illinois Department of Human Services accidentally left a database containing information about 700,000 people accessible to literally anyone with a web browser.
No malware. No sophisticated hackers. Just a folder that shouldn't have been public.
This isn't a ransomware attack or some nation-state espionage operation. It's something worse in some ways: a basic configuration mistake that exposed vulnerable people's most sensitive information for an unknown amount of time. The kind of thing that gets caught during a proper security review, or that never happens in the first place if you follow basic protocols.
Let's break down what actually happened, why it matters, and what this tells us about how government agencies handle data security.
TL; DR
- 700,000 people affected: Mix of Division of Rehabilitation Services customers and Medicaid recipients exposed through publicly accessible maps
- The mistake: IDHS posted resource allocation maps on the clearweb that contained sensitive personal data, thinking they were internal use only
- Data exposed: Addresses, case numbers, medical assistance plan information, demographic data, and case status details
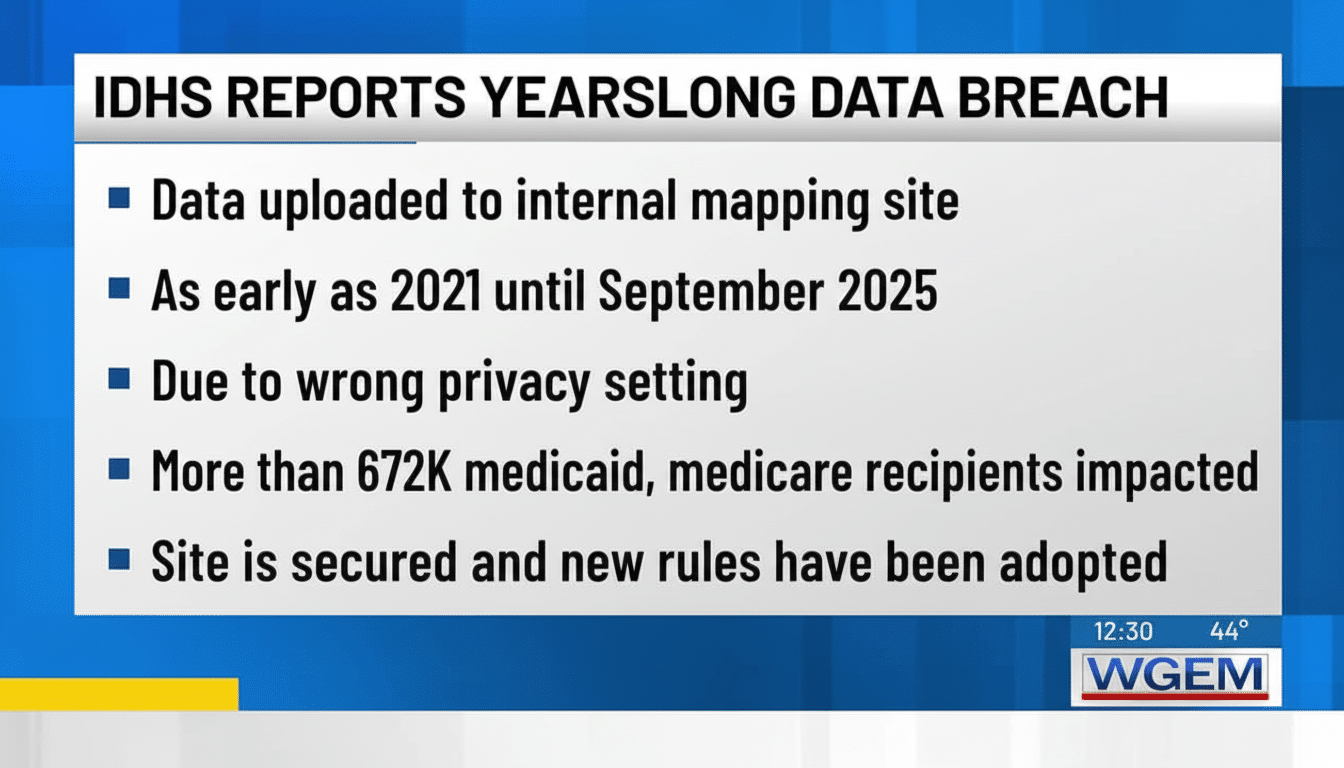
- Timeline: Maps were accessible for months; discovered and restricted in late September 2025
- Bottom line: A fundamental failure to secure data before publishing it, with vulnerable populations bearing the risk
On average, government data breaches take 287 days to discover. The IDHS breach followed this trend, taking months to identify the exposure. Estimated data for IDHS.
What Happened: The Breakdown
Here's the scenario that probably keeps data security directors up at night. The Illinois Department of Human Services created interactive maps to help plan resource allocation. These maps would show where low-income families were concentrated, where rehabilitation services were needed, which areas had the most Medicaid recipients. Useful stuff for internal planning.
Someone decided these maps would go on a public website. Maybe they thought it would help external stakeholders understand the distribution of need. Maybe they wanted to make the data accessible to regional offices. The exact reasoning doesn't really matter because what happened next was predictable: the maps went live without proper access controls.
Think about what's actually in resource allocation maps. You're not looking at aggregate statistics like "37% of county residents receive assistance." You're looking at specific locations, specific case numbers, specific individuals. When you overlay that with addresses and case details, you've essentially created a searchable directory of vulnerable people.
The mistake wasn't sophisticated. There was no zero-day exploit here. Someone just didn't lock down the directory properly, and the access was discoverable. Anyone running a basic web scraper could have harvested the entire dataset. Anyone curious enough to poke around public URLs could have stumbled on it.
What makes this worse is that it took months to catch. September 2025 is when IDHS restricted access. That means the data was potentially exposed since the maps were first published—nobody knows exactly when that was.
Who Was Actually Affected
This wasn't a random dataset breach. The 700,000 people affected were split into two groups, each with different information exposed.
The 32,000 Division of Rehabilitation Services Customers
These folks are people using state rehabilitation services, usually due to disability. IDHS exposed:
- Full names
- Home addresses
- Case numbers
- Case status information
- Referral source data
- Region and office location information
- DRS recipient status
For someone using rehabilitation services, this is deeply identifying information. You can map it. You can find where these people live. You can understand their relationship with the state. Someone with bad intentions could use this to target vulnerable individuals—whether for scams, financial exploitation, or worse.
The 670,000+ Medicaid and Medicare Savings Program Recipients
This is the larger group. Information exposed included:
- Addresses
- Case numbers
- Demographic information
- Names of medical assistance plans (Medicaid, Medicare, etc.)
Medicaid recipients tend to be lower-income individuals and families. Combine their address with the knowledge that they receive government medical assistance, and you've got data that's valuable to scammers, fraudsters, and identity thieves.
The difference between these two groups matters. The DRS group's exposure was more granular and personal. But the Medicaid group's scale makes it statistically more dangerous. In absolute numbers, there's a higher chance that at least some of those 670,000 people will experience fraud or identity theft as a result.
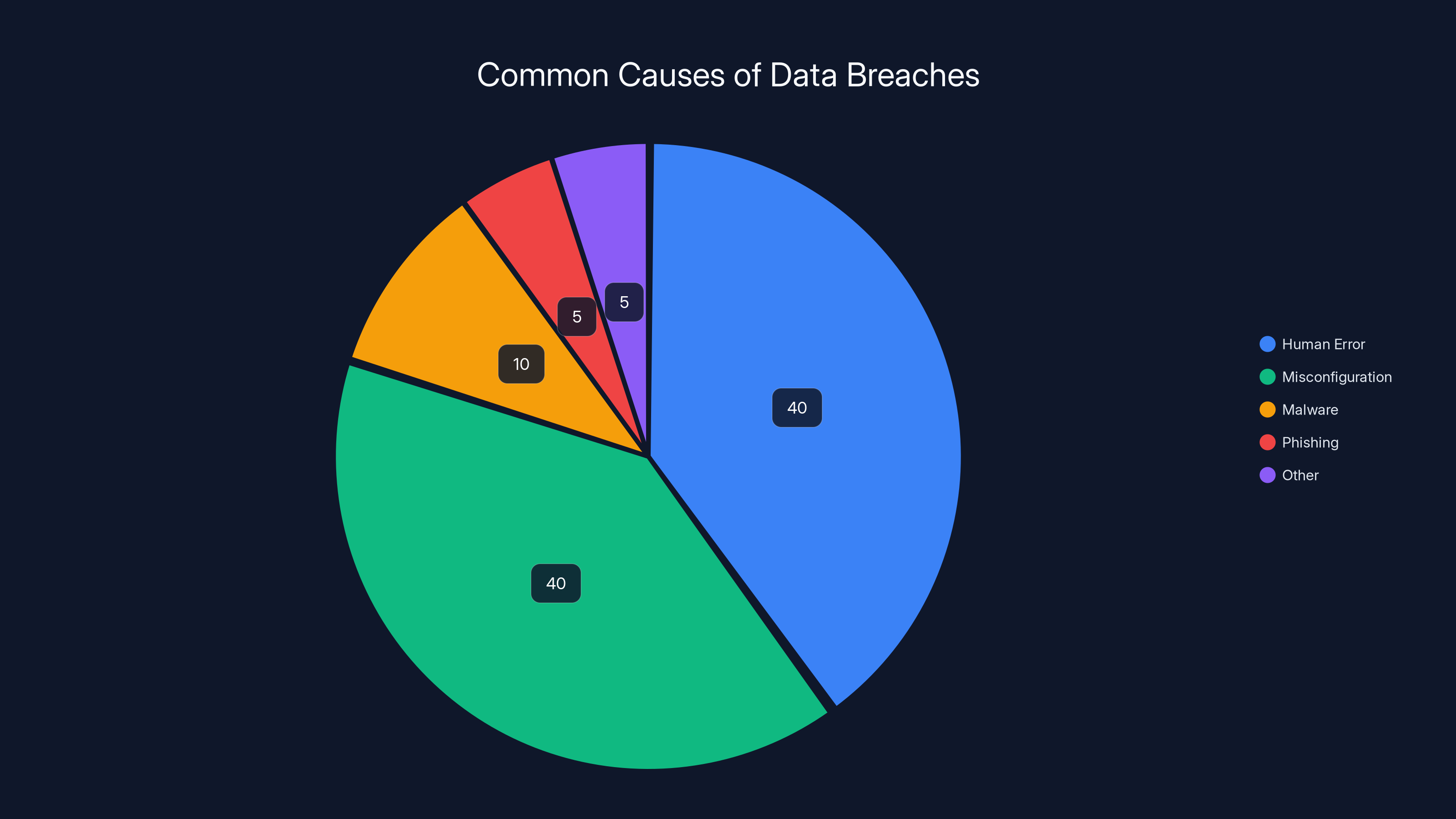
Estimated data shows that human error and misconfiguration account for 80% of data breaches, highlighting the importance of proper security protocols.
The Technical Failure
From a security perspective, this breach represents multiple layers of failure. Let's walk through them.
No Access Control Verification
When you're deploying a web application with sensitive data, the first question should be: "Who should be able to see this?" In this case, the answer was "internal IDHS employees only." But implementing that answer requires actual security controls.
Basic implementation would be:
- Authentication checks on every request
- Authorization logic that validates the user's role
- Testing from an unauthenticated perspective to confirm it doesn't work
- Using standard frameworks or services that enforce these controls by default
None of that happened. The maps just... sat there, openly accessible.
Pre-Deployment Security Review Failure
Before you push anything with personal data to the web, you need a security review. That review should catch this. Someone should have asked: "Can anyone on the internet access this without logging in?" And someone should have tested it.
No Data Classification Protocol
IDHS should have had policies defining what data requires what level of protection. Names and addresses of vulnerable populations clearly fall into "highly sensitive." You don't treat that data the same way you treat aggregate statistics.
Missing Monitoring
Once the maps went live, there should have been monitoring. What's accessing these maps? From where? How many requests are coming from internal IP ranges versus external sources? Unusual access patterns might have caught this weeks or months earlier.
Instead, the breach only got discovered through some other means—the details aren't clear, but it wasn't systematic monitoring.

Timeline: When Everything Went Wrong
Unfortunately, the full timeline isn't public. IDHS hasn't disclosed exactly when the maps were first deployed, which is a significant omission. But here's what we know:
Unknown Date (Early-to-Mid 2025): Maps deployed to the public web with sensitive data exposed
Late September 2025: IDHS discovered the exposure and immediately restricted access to authorized employees only
Early January 2026: IDHS published a press release acknowledging the incident
That gap between discovery and public disclosure is roughly three months. During that time, they notified affected individuals but haven't explained why it took that long to go public.
What Data Was Actually Vulnerable
Let's be specific about what an attacker could have done with this data.
Identity Theft Preparation
Names, addresses, and case numbers are the building blocks of identity theft. You've got the foundational information someone needs to:
- Apply for credit in someone's name
- Open utility accounts
- Create fraudulent government accounts
- Access other accounts if this person reused information elsewhere
Targeted Phishing and Social Engineering
Knowing someone's full name, address, and that they receive Medicaid is enough to craft convincing phishing emails or phone calls. "Hi, this is from your medical assistance program, we need to verify your account information..." Vulnerable populations are more likely to fall for these attacks, partly because they're more likely to be interacting with government agencies.
Insurance Fraud
Someone could have used this data to fraudulently claim benefits or set up false insurance claims. The intersection of addresses and medical plan information creates opportunities.
Discrimination and Targeting
This is the less quantifiable but arguably worse risk. Knowing where benefit recipients live could enable discrimination in housing, employment, or even physical targeting by bad actors.
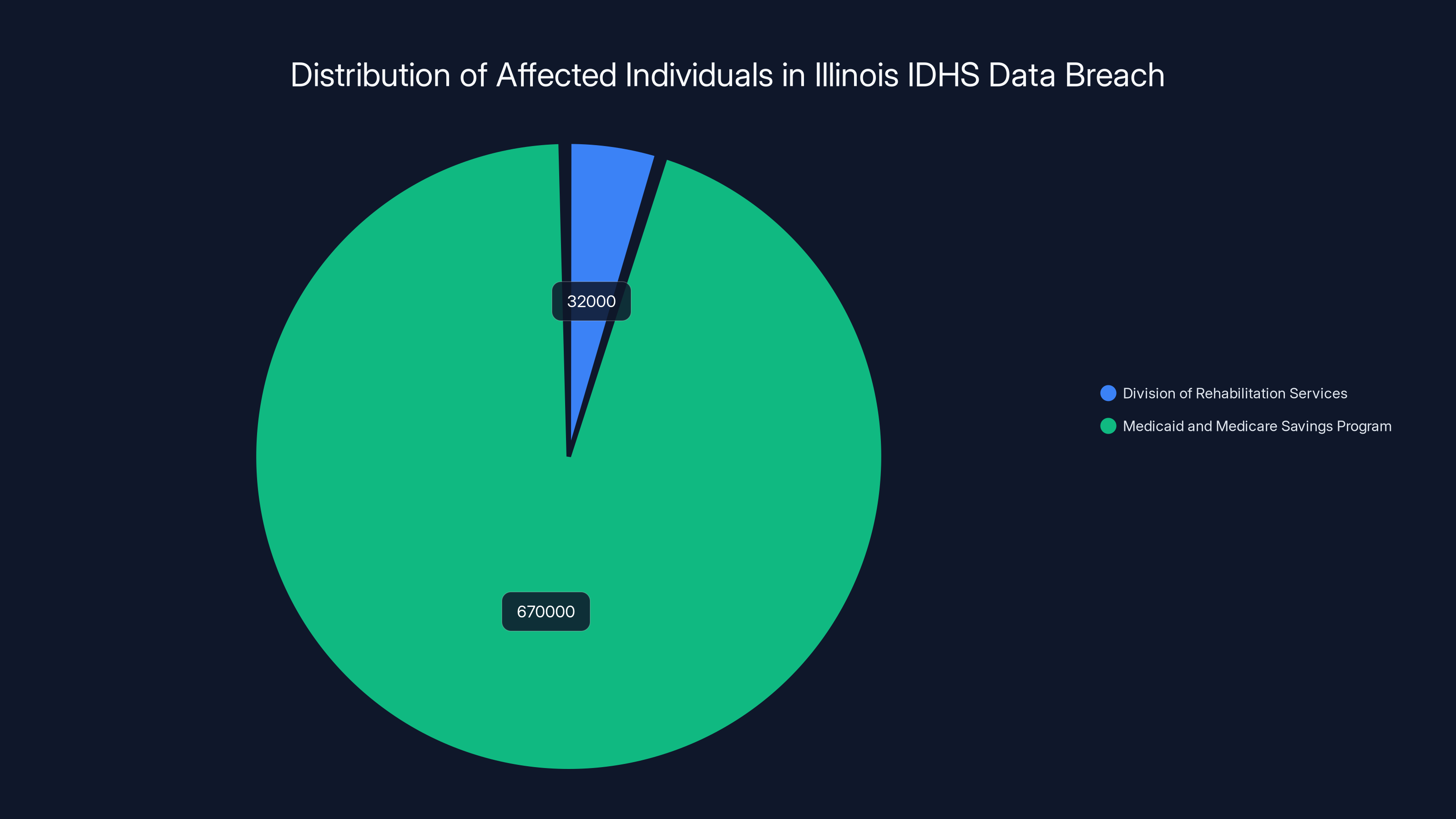
The data breach affected approximately 32,000 individuals from the Division of Rehabilitation Services and over 670,000 from the Medicaid and Medicare Savings Program, highlighting a significant exposure risk.
How It Should Have Been Handled
Let me walk through how a properly-run agency would have handled this situation.
Before Deployment
Step 1: Classify the data. Someone asks, "What's the sensitivity level?" The answer is obviously "high," because it includes personal information about vulnerable populations.
Step 2: Design security accordingly. High-sensitivity data means authentication requirements, encryption in transit, restricted access, and logging.
Step 3: Have a security review. A security person or team tests the application from an unauthenticated perspective. They verify that access controls actually work.
Step 4: Use secure-by-default frameworks. Modern web frameworks should require you to explicitly disable security features, not enable them.
Step 5: Run automated security checks. Pre-deployment scanning tools should flag configuration issues.
After Deployment
Step 1: Monitor access. Log who accesses what, from where, and when. Set alerts for unusual patterns.
Step 2: Perform periodic security audits. Test access controls regularly. Try accessing protected data without credentials.
Step 3: Have an incident response plan. If a breach is discovered, you know exactly what to do and who to notify.
IDHS did none of this. Or if they did, it wasn't enforced.
The Response and What's Missing
After the breach was discovered, IDHS took some steps. Access was immediately restricted. A free support line was set up for affected individuals. People are being notified.
But there's a glaring omission: no credit monitoring or identity theft protection services.
This is standard practice after data breaches involving sensitive information. Companies typically offer 1-3 years of credit monitoring through services like Equifax or Experian. It's not perfect protection, but it's something.
IDHS hasn't mentioned this. That's a problem.
What IDHS Did Offer
- Notification of affected individuals
- A support phone line
- Information about monitoring credit and bank accounts
- General fraud alerts
What They Didn't Offer
- Paid credit monitoring services
- Identity theft insurance
- Legal assistance if someone becomes a victim
- Any kind of financial compensation
They're essentially telling people, "Here's what happened, here's a phone number, now you handle the risk yourself."
The Impossible-to-Determine Damage
Here's what makes this particular breach so frustrating: we'll never know how much damage occurred.
Because IDHS couldn't determine who accessed the maps or when, there's no way to know if malicious actors found the data. It's possible nobody outside the organization ever accessed it. It's possible it was scraped entirely and is now circulating in the dark web.
From a risk management perspective, you have to assume the worst. If it was publicly accessible and contained valuable data, someone probably found it. Someone probably saved copies.
The uncertainty creates a different kind of problem. Those 700,000 people can't know if their data is safe or at serious risk. They're stuck in a waiting period that could last years, watching for signs of fraud that may or may not come.

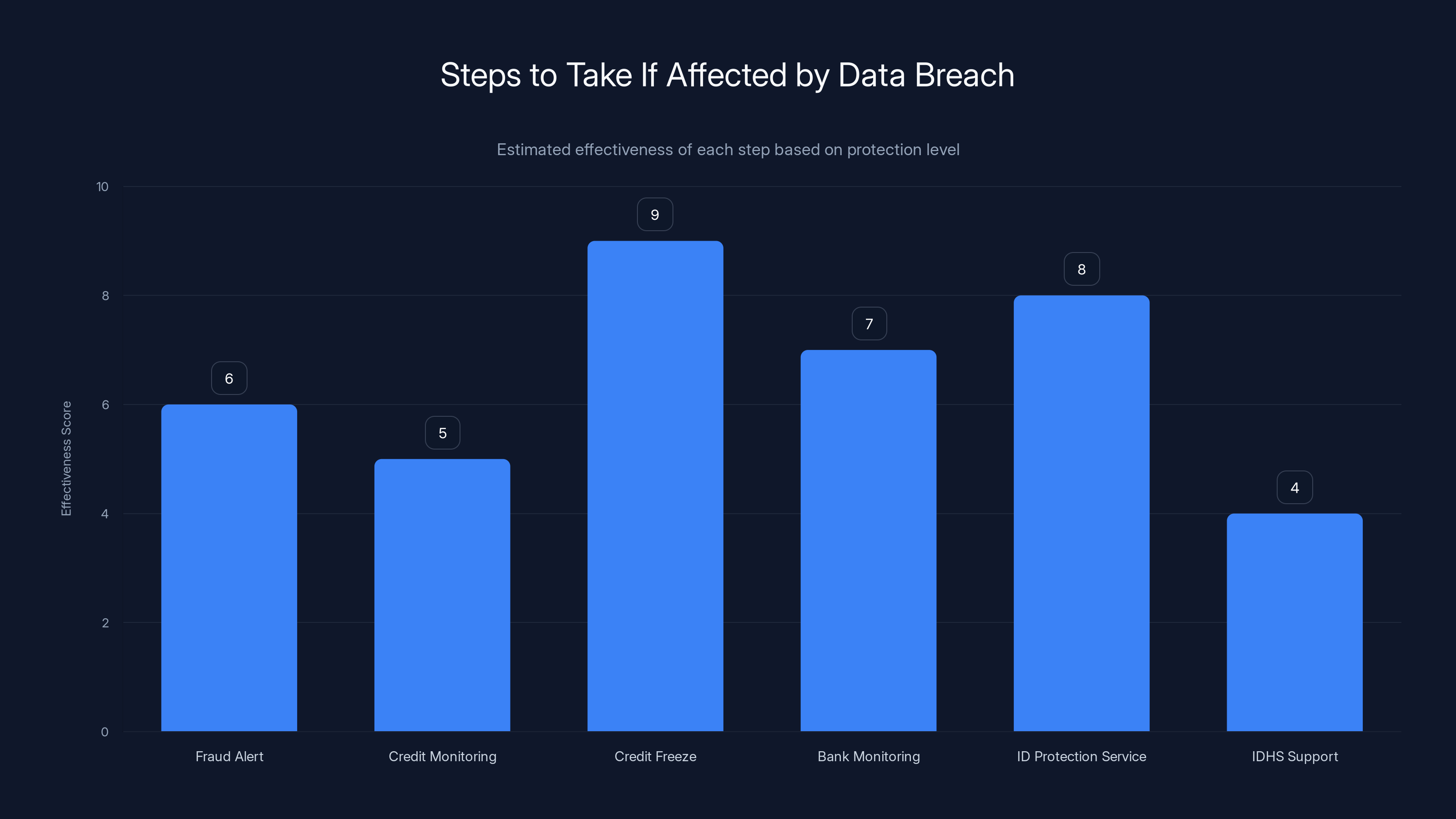
Credit freeze is estimated to be the most effective step in protecting against identity theft, scoring 9 out of 10. Estimated data based on typical protection levels.
Why Government Agencies Struggle With Security
This isn't the first time a government agency has had a major breach. It won't be the last. There are structural reasons why government lags behind private sector security practices.
Budget Constraints
Government IT budgets get cut constantly. Security investment is seen as a cost center, not a revenue driver. When budgets shrink, security spending gets cut first.
Legacy Systems
Most government agencies run on incredibly old infrastructure. These systems were never designed with modern security in mind. Bolting security onto legacy systems is complicated and expensive.
Hiring and Retention
Government salaries can't compete with private sector tech companies. A security engineer can make $150K+ in the private sector but significantly less in government. Agencies lose talent constantly.
Procurement and Red Tape
Buying new security tools in government requires going through procurement processes that take months. By the time you've approved the purchase, the tool is outdated. Private companies buy, deploy, and optimize in the time it takes government to write the RFP.
Lack of Accountability
When a private company has a major breach, there are consequences. Stock price drops, customers leave, executives face lawsuits. When a government agency has a breach, the responsible officials usually keep their jobs.

Broader Implications: This Happens More Than You Think
The IDHS breach is notable because it affected 700,000 people and involved government benefits data. But it's far from unique.
Public records show that government agencies face data breaches regularly. Healthcare systems, law enforcement databases, DMV records, tax information. The scale varies, but the pattern is consistent: inadequate security, discovered by accident, notified after long delays.
What's worse is that government agencies often hold data that's more sensitive than what private companies handle. Financial information, health records, personal identifiers. If your bank has a breach, you can freeze your account. If your Medicaid information is exposed, your options are more limited.

What You Should Do If You're Affected
If you think you might be one of the 700,000 people affected, here are concrete steps you should take immediately.
Step 1: Place a Fraud Alert
Call one of the three credit bureaus and request a fraud alert. You only need to call one, and they'll notify the others.
- Equifax: 1-800-525-6285
- Experian: 1-888-397-3742
- Trans Union: 1-800-680-7289
A fraud alert tells lenders to verify your identity before opening new accounts in your name. It's free and lasts one year.
Step 2: Monitor Your Credit Reports
Visit annualcreditreport.com and pull your credit reports from all three bureaus. Look for unfamiliar accounts or inquiries. You can do this for free once per year, but you might want to do it now and again in 3-6 months.
Step 3: Consider a Credit Freeze
If you want more protection, you can freeze your credit. This prevents anyone from opening new accounts in your name. It's free and more effective than a fraud alert, but it requires unfreezing to apply for credit yourself.
Step 4: Monitor Your Bank Accounts and Statements
Look for fraudulent charges or transfers. Check your mail for accounts you didn't open. Watch for unexpected bills from medical providers.
Step 5: Consider an Identity Theft Protection Service
Since IDHS isn't offering this, you might want to purchase it yourself. Services like Lifelock, Identity Guard, or IDWatchdog monitor dark web activity and alert you to threats. They run
Step 6: Call the IDHS Support Line
IDHS set up a line for affected individuals. Have your information ready and ask for specific guidance based on what data category you're in.

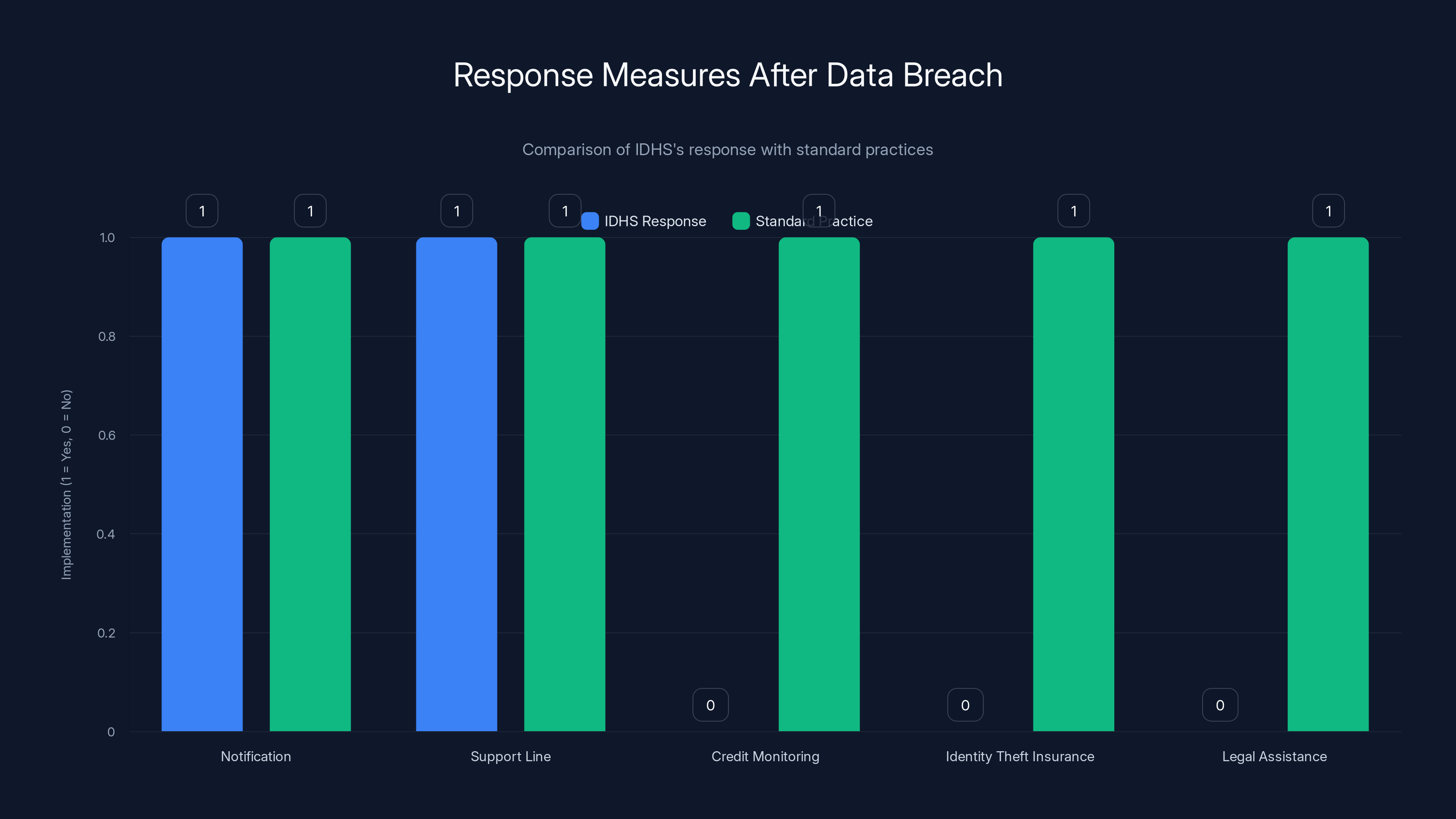
IDHS's response to the data breach lacks several standard measures such as credit monitoring and identity theft insurance, which are typically offered to mitigate risks.
The Bigger Picture: Why This Matters Beyond Illinois
The IDHS breach is a symptom of a larger problem. Government agencies everywhere are handling increasingly sensitive data with increasingly outdated security practices.
Medicaid data includes medical history, prescriptions, and health status. DMV records include biometric information. Tax records include financial details. Law enforcement databases include criminal history and personal information. When these get breached, the impact is enormous.
What's particularly troubling is that this data involves vulnerable populations who have fewer resources to protect themselves. A low-income person whose Medicaid information is exposed might not have the knowledge or resources to detect and resolve fraud as quickly as someone with more financial sophistication.
The asymmetry of vulnerability and power is worth noting. Those 700,000 people had no choice about whether their data would be collected. They were required to provide it to access essential services. And now they're expected to manage the risk when the government failed to protect it.

How Agencies Can Actually Fix This
If you're in government IT and reading this, here's what needs to happen.
Immediate Actions
Security training for all staff. Not just IT people. Developers, project managers, everyone needs to understand basic security principles. Make it mandatory.
Mandatory security review before deployment. No application with personal data goes live without documented security review and testing.
Implement logging and monitoring. You need to know what's being accessed, by whom, from where. This isn't optional.
Regular security audits. Hire an outside firm to test your security controls. Do this at least annually.
Medium-term Actions
Modernize legacy systems. This is expensive and takes years, but it's necessary. Old systems were never designed with security in mind.
Invest in security infrastructure. Web application firewalls, intrusion detection systems, encryption. These are expensive, but breaches are more expensive.
Hire security expertise. Dedicate budget to attracting and retaining security professionals. Use contractors if needed.
Implement identity and access management. Use multi-factor authentication. Implement role-based access controls. This is basic but surprisingly rare in government.
Long-term Actions
Shift security culture. Security needs to be everyone's responsibility, not just the IT security team's problem.
Invest in training and development. Developers need to learn secure coding practices. This isn't something you do once.
Establish incident response procedures. When breaches happen, you need to know who does what and when. Have this documented and practiced.
Implement data minimization. Only collect and store data you actually need. The less sensitive data you have, the less you can lose.

Lessons for Organizations of All Types
If you're in the private sector thinking this doesn't apply to you, think again. The IDHS breach teaches lessons that matter everywhere.
Security Is a Development Responsibility
You can't bolt security on at the end. It has to be part of the development process from day one. If your developers aren't trained in secure coding, you'll have breaches.
Access Control Matters More Than Encryption
IDHS encrypted the data in transit (probably) but failed at basic access control. Encryption doesn't help if unauthorized people can access the data anyway.
Testing Is Non-Negotiable
Before you deploy anything with sensitive data, test it from an unauthorized perspective. Try accessing protected resources without credentials. Try bypassing the authentication. If you can do it, so can attackers.
You Can't Assume Good Intentions
IDHS assumed that putting data on the internet with authentication was sufficient. That assumption was wrong. Never assume that attackers won't find your mistakes.
Transparency Matters
IDHS eventually disclosed this breach, which is good. But the long delay between discovery and disclosure damaged trust. When breaches happen, disclose them quickly and provide full details.

The Future: Will Anything Change?
Historically, government agencies are slow to implement lessons from breaches. There's no financial incentive like there is in the private sector. New administrations can change priorities. Budget cycles make long-term planning difficult.
That said, there are positive signs. Federal agencies are increasingly required to follow NIST cybersecurity frameworks. Some states have implemented breach notification laws with real teeth. Illinois itself has data protection laws.
The question is whether those laws and frameworks are actually enforced and whether funding follows. Based on this breach, the answer appears to be no.
IDHS clearly had some level of security governance. They must have had policies about data protection. Those policies just weren't followed or enforced.

Protecting Yourself in the Meantime
Until government agencies get security right, you need to protect yourself.
Limit Information Sharing
Only provide information to government agencies that's absolutely required. Don't volunteer extra information in applications or forms.
Use Strong, Unique Passwords
If you have an account with any government agency, use a password you don't use anywhere else. Use a password manager like Bitwarden or 1Password.
Monitor Financial Accounts Actively
Check your bank and credit card statements monthly. Unusual transactions can be caught and disputed quickly.
Review Your Credit Reports
Get your free annual credit reports from annualcreditreport.com. Look for accounts you don't recognize and inquiries you didn't authorize.
Consider a Credit Freeze
If you've been in a data breach, a credit freeze gives you the most protection. It prevents anyone from opening new accounts in your name without unfreezing first.
Use Credit Monitoring
Services like Experian Boost or Equifax Complete offer monitoring for a monthly fee. They alert you to suspicious activity.
Be Cautious About Unexpected Communications
Scammers use breached data to create convincing phishing emails and calls. Even if you receive an official-looking email from a government agency, don't click links or provide information. Call the agency directly using a number you look up yourself.

What Should Happen From Here
In an ideal world, this breach would trigger significant changes at IDHS and across Illinois government.
At minimum, there should be:
Accountability: Someone needs to be held responsible for this failure. Not necessarily fired, but definitely retrained and reassigned.
Comprehensive security review: A third-party firm should audit IDHS's entire technology infrastructure and security practices. The results should be public.
Resource allocation: IDHS should get the funding necessary to implement proper security controls across all systems.
Credit monitoring: The state should offer free credit monitoring to affected individuals. It's not about liability, it's about doing right by vulnerable populations.
Transparency: IDHS should publish a complete timeline of the breach, what they've learned, and how they're preventing future incidents.
Policy changes: Illinois should implement or strengthen data protection laws that apply to all state agencies.
Whether any of this happens remains to be seen. But for the 700,000 people affected, the time for action is now.

Conclusion: When Mistakes Cost Real People
Data breaches are abstract until they affect you personally. Then they become very real.
The IDHS breach wasn't sophisticated. It wasn't a complex zero-day exploit or a carefully planned nation-state operation. It was a basic failure to secure sensitive data before making it public. The kind of mistake that should be caught in routine security testing.
But it happened. 700,000 people's information was exposed. For months. And now they get to spend the next several years watching for signs of fraud, uncertainty about whether their data is being misused.
The broader lesson is that security is hard, especially at scale, especially in organizations with legacy systems and tight budgets. But hard doesn't mean impossible. It means investment, process, and accountability.
Until government agencies treat data security with the seriousness it deserves, breaches will continue. Until they allocate proper budgets and hire qualified staff, problems will go undetected. Until they face real consequences for failures, incentives won't change.
For now, if you're affected, take the steps we outlined. Protect yourself because the government clearly can't. And if you're in IT or security leadership anywhere, use this as a wake-up call.
Data breaches aren't someone else's problem. They're inevitable unless you treat security as non-negotiable. And when you fail, real people pay the price.
FAQ
What is the Illinois IDHS data breach?
The Illinois Department of Human Services accidentally exposed sensitive personal information about 700,000 individuals through publicly accessible interactive maps that were meant for internal use only. The maps contained names, addresses, case numbers, and details about Medicaid and rehabilitation services recipients. This represents a critical failure in basic security practices that allowed the data to remain exposed for months before being discovered in September 2025.
How did the Illinois data breach happen?
IDHS created resource allocation maps containing sensitive personal data and deployed them to the public internet without proper access controls or authentication requirements. The organization assumed the maps were restricted to internal use, but no technical controls were actually implemented to prevent public access. Anyone with a web browser could discover and access the maps, making it impossible to determine who viewed the data or whether malicious actors downloaded it.
Who was affected by the Illinois IDHS data breach?
Two groups were impacted: approximately 32,000 Division of Rehabilitation Services customers (people receiving disability assistance) and over 670,000 Medicaid and Medicare Savings Program recipients. The DRS group had more detailed personal information exposed including case status and referral details, while the Medicaid group's exposure included addresses combined with medical assistance plan information, making both groups vulnerable to identity theft and fraud.
What personal information was exposed in the IDHS breach?
The exposed data included full names, home addresses, case numbers, case status information, referral source data, demographic details, and the names of medical assistance plans (Medicaid, Medicare, etc.). For rehabilitation services customers specifically, IDHS also exposed region and office location information and their status as DRS recipients. This combination of information is sufficient for identity theft, phishing attacks, and fraudulent account creation.
How long was the IDHS data exposed to the public?
The exact timeframe is unknown because IDHS never disclosed when the maps were first deployed. The agency discovered the breach and restricted access in late September 2025, but the data could have been publicly accessible for weeks, months, or even longer. This uncertainty means affected individuals cannot know definitively whether their data was accessed by malicious actors.
What should you do if you were affected by the Illinois IDHS breach?
Begin by placing a fraud alert with one of the three credit bureaus, which will notify the others. Review your credit reports from annualcreditreport.com for unauthorized accounts or inquiries. Monitor your bank statements and mail for unexpected bills. Consider placing a credit freeze if you want maximum protection. You may also want to purchase identity theft protection services since IDHS is not offering free credit monitoring, and call the IDHS support line for additional guidance specific to your situation.
Why didn't the government offer credit monitoring after the breach?
IDHS has not offered free credit monitoring or identity theft protection services despite this being standard practice after data breaches involving sensitive personal information. Private companies typically offer 1-3 years of credit monitoring as part of their response, but government agencies face fewer financial and reputational pressures to do so. IDHS has instead asked affected individuals to protect themselves, creating a significant equity gap for vulnerable populations with fewer resources.
Could this data breach have been prevented?
Absolutely. Basic security practices would have prevented this entirely: implementing authentication and authorization controls before deployment, conducting security reviews to verify that unauthorized users cannot access sensitive data, using secure-by-default frameworks that require explicit disabling of security features, and performing regular security audits. The breach represents multiple layers of failure in fundamental security processes that are standard in organizations serious about protecting data.
What does this breach tell us about government security practices?
The IDHS breach demonstrates that many government agencies lack basic security practices, struggle with budget constraints that prevent proper security investment, have outdated legacy systems that were never designed for security, face hiring and retention challenges in security roles, and often lack accountability when breaches occur. These structural issues mean government agencies handling increasingly sensitive data are often less secure than private sector organizations, creating disproportionate risk for vulnerable populations dependent on government services.
How can government agencies prevent future data breaches?
Government agencies need mandatory security training for all staff, mandatory security reviews before deploying systems with personal data, implementation of logging and monitoring to detect suspicious access, regular third-party security audits, investment in hiring and retaining qualified security professionals, modernization of legacy systems, implementation of multi-factor authentication and role-based access controls, and a cultural shift where security is everyone's responsibility. This requires sustained funding and commitment, but breaches are far more expensive than proper prevention.
Can you get free credit monitoring for the IDHS breach?
Not from IDHS or the state of Illinois. IDHS has not offered free credit monitoring services as of January 2026. You must either purchase credit monitoring services yourself or monitor your accounts manually by regularly reviewing credit reports and bank statements. However, you can place a free fraud alert and review your credit reports for free once per year at annualcreditreport.com.

Key Takeaways
- 700,000 people's sensitive personal data was exposed by the Illinois IDHS through publicly accessible maps due to a basic access control failure
- The breach affected rehabilitation services customers and Medicaid recipients with information including names, addresses, case numbers, and medical details
- Data was exposed for months before discovery in September 2025, with exposure window remaining unknown, making damage assessment impossible
- IDHS has not offered credit monitoring or identity theft protection despite this being standard practice after comparable breaches
- Affected individuals should immediately place fraud alerts, review credit reports, consider credit freezes, and monitor financial accounts for fraudulent activity
- The breach represents a systemic failure in government security practices including lack of pre-deployment security review and absence of access monitoring
- Government agencies face unique challenges in cybersecurity including budget constraints, legacy systems, hiring difficulties, and limited accountability
- Basic security practices like authentication requirements, security testing, and access logging could have entirely prevented this breach
Related Articles
- Illinois Health Department Data Breach: 700K+ Exposed [2026]
- Covenant Health Breach Exposes 500K Patients: What Happened [2025]
- Iran's Internet Collapse: What Happened and Why It Matters [2025]
- US Withdraws From Internet Freedom Bodies: What It Means [2025]
- NSO's Transparency Claims Under Fire: Inside the Spyware Maker's US Market Push [2025]
- SwitchBot's AI Recording Device: Privacy, Ethics & What You Need to Know [2025]
![Illinois Data Breach Exposes 700,000: How Government Failed [2025]](https://tryrunable.com/blog/illinois-data-breach-exposes-700-000-how-government-failed-2/image-1-1767906388011.jpg)



