Illinois Health Department Data Breach: How 700,000+ Residents' Data Was Exposed for Years
Imagine your home address, demographic details, and government case information sitting on a website anyone could access. No password. No encryption. Just publicly visible for four and a half years.
That's what happened in Illinois.
On January 2, 2026, the Illinois Department of Human Services (IDHS) revealed a security failure that exposed personal information for over 700,000 state residents. The breach wasn't the result of sophisticated hacking. There was no ransomware. No criminal mastermind. Instead, an internal mapping website used for allocating state resources was accidentally left visible to the entire internet from April 2021 through September 2025.
This isn't just another data breach story. It's a case study in how organizations misunderstand the difference between "internal systems" and "internet-connected systems." It's about the gap between assuming something is secure and actually verifying it is. And it raises uncomfortable questions about how many other government agencies, hospitals, and companies are making the exact same mistake right now.
Let's dig into what happened, who was affected, why it matters, and what you need to know to protect yourself.
TL; DR
- Over 700,000 Illinois residents' data exposed from April 2021 to September 2025 through an unsecured internal mapping website
- Exposed data included addresses, case numbers, demographic information, and service status for Medicaid recipients and rehabilitation services recipients
- Four-year window with no evidence of unauthorized access found, though officials couldn't definitively rule it out
- Root cause was basic security misconfiguration: an internal tool accidentally made publicly viewable
- Ongoing response includes notification letters, credit monitoring, identity theft protection, and potential litigation
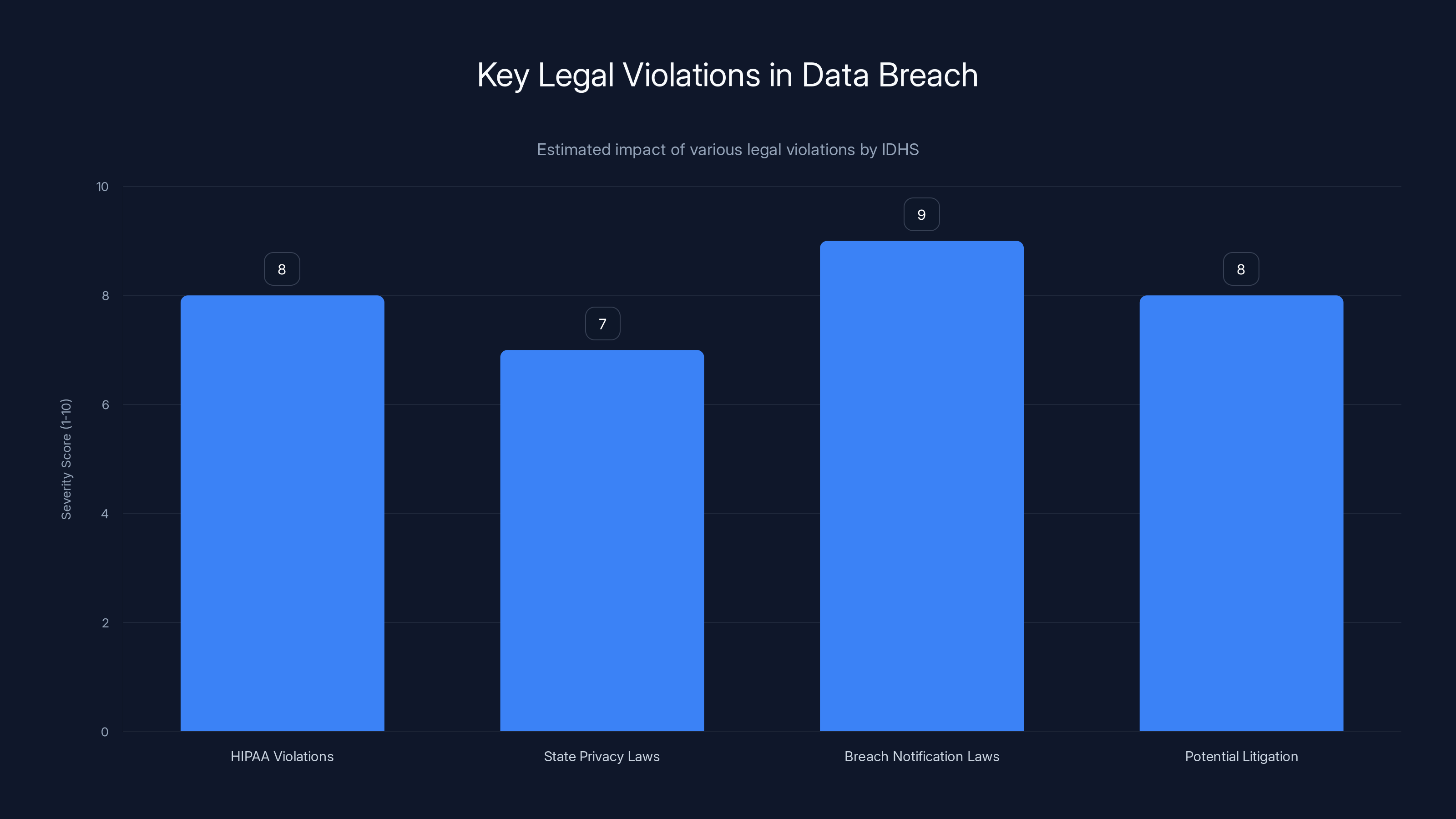
Estimated data shows breach notification laws as the most severely violated, followed closely by potential litigation risks and HIPAA violations.
What Exactly Happened: The Timeline of a Preventable Disaster
The story begins innocently enough. The Illinois Department of Human Services needed an internal tool to track where state resources were being allocated across the state. Someone built a mapping website. It showed locations, case information, recipient data, and demographic statistics. Useful for internal operations. Necessary for planning.
Then something went wrong.
Somewhere in the configuration process, whoever set up this website didn't properly restrict access. The website wasn't behind a firewall. It wasn't password-protected. It wasn't requiring authentication to view the data. It was simply sitting on the internet, visible to anyone who found the URL or discovered it through search engines.
And it stayed that way for 1,643 days.
From April 2021 through September 2025, anyone with an internet connection could have accessed this data. A journalist could have found it. A disgruntled employee could have scraped it. A criminal could have weaponized it. A malicious actor could have harvested the information for targeted scams.
The exposure wasn't discovered through an external security researcher. It wasn't flagged by a penetration testing firm. IDHS found it themselves during an internal security review in September 2025. Four years. Nine months. Gone before anyone even knew something was wrong.
When IDHS officials announced the breach, they made a critical statement: they were "unable to determine if anyone viewed the publicly exposed maps during the period they were accessible." Translation: they have no logs. No way to know if the data was accessed. No way to know if it was downloaded or sold. No way to know if anyone exploited it.
That uncertainty is almost worse than confirmed unauthorized access. It's the security equivalent of finding your front door open and wondering who walked through.
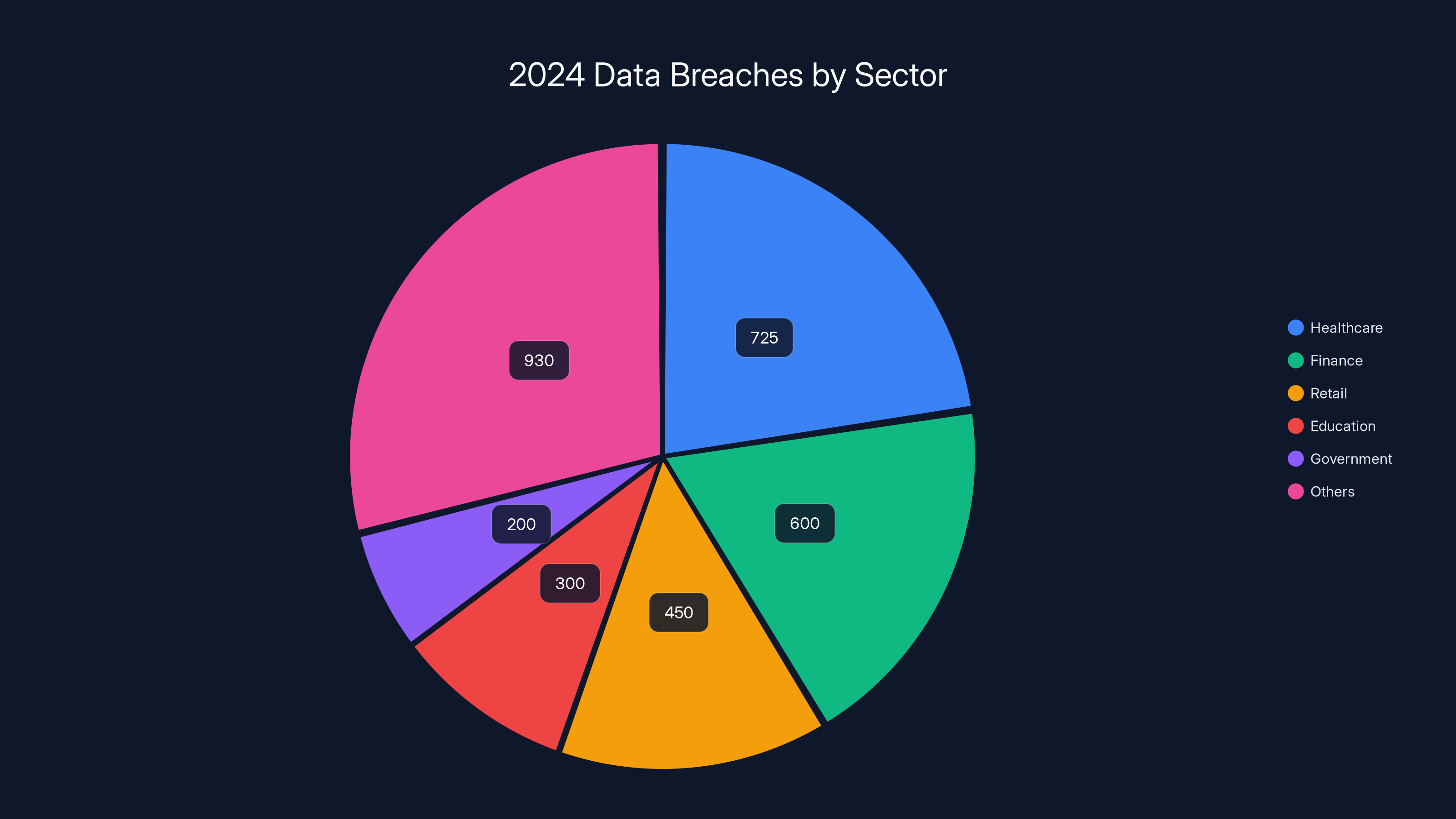
Healthcare led with 725 breaches in 2024, highlighting its vulnerability. Estimated data shows other sectors like finance and retail also faced significant breaches.
The Scope: Who Was Affected and What Data Exposed
The breach affected two distinct groups of Illinois residents, with different types of data exposed.
Medicaid and Medicare Savings Program Recipients: This group represented 672,616 individuals. The exposed information included their home addresses, case numbers, and demographic data. Notably, the data did not include Social Security numbers or full names, though officials confirmed that case numbers and addresses could potentially be linked to identify individuals.
The demographic data was particularly concerning because it could reveal sensitive information about recipients' circumstances: family composition, income ranges, employment status, and other factors that could be used for targeted scams or discrimination.
Division of Rehabilitation Services Recipients: An additional 32,401 individuals who receive services for disabilities or rehabilitation had their information exposed. This dataset included names, addresses, case statuses, and other service-related information. For this group, full identification was directly exposed.
In total, 705,017 individuals were affected, though some individuals may have appeared in both datasets, making the actual number of unique people somewhat lower.
What makes this breach particularly significant is the type of data exposed. This isn't a list of email addresses or usernames. This is government benefit information. Healthcare status. Addresses of vulnerable populations. The data is a roadmap for bad actors to identify and target people in specific circumstances.
Consider a scammer with this dataset. They can contact someone at their home address, reference specific government programs they're enrolled in, and craft a convincing social engineering attack. "Hi, this is from the Illinois Department of Human Services. We need to verify your Medicaid status. Can you confirm your case number?" Suddenly, the victim thinks they're talking to a legitimate government agency.
The Root Cause: A Failure of Basic Security Practices
This wasn't a sophisticated breach. No zero-day exploits. No advanced persistent threats. This was basic, fundamental security failure.
The root cause: an internal system that was accidentally exposed to the public internet without any access controls.
How does this happen? Usually in one of these ways:
Configuration Error: Someone set up a web server or cloud service and failed to configure access restrictions properly. They tested it locally, moved it to production, and assumed it was secure because "it's internal." The distinction between "internal" and "internet-facing" got lost in the shuffle.
Lack of Inventory: Many organizations don't maintain a complete list of all their web applications, databases, and services. If you don't know something exists, you can't monitor it or secure it.
Insufficient Testing: The system was probably never tested for external accessibility. If someone had simply tried accessing it from the public internet before it went live, this would have been caught immediately.
Missing Verification: There's often a gap between assuming something is secure and actually verifying it. Someone might have documented that the system requires authentication, but nobody actually tested whether that requirement was enforced.
Change Management Failure: Systems get moved, migrated, updated, and reconfigured constantly. If there's no process to verify that security settings survive these changes, something will slip through.
The IDHS incident checks multiple boxes on this list.
What's particularly striking is that this isn't a novel vulnerability or attack vector. Organizations have been making this mistake for decades. In 2019, researchers found an unsecured database containing millions of phone numbers. In 2021, a misconfigured AWS bucket exposed healthcare data. In 2023, an internal Slack workspace was exposed to the internet. The vulnerability type is ancient. The fix is straightforward. Yet it keeps happening.
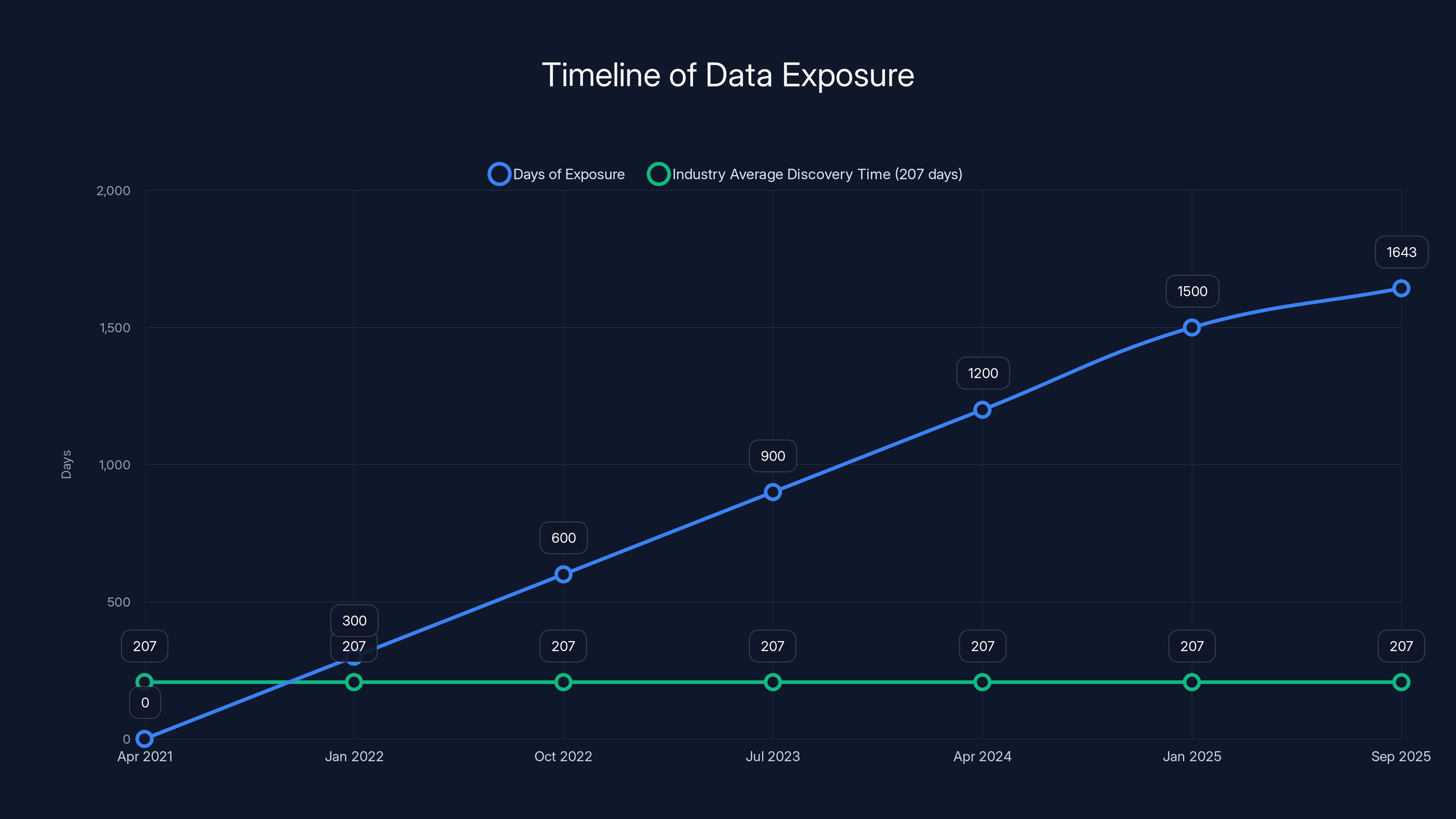
The data was exposed for 1,643 days, significantly longer than the 207-day industry average for discovering breaches. Estimated data for timeline visualization.
The Detection and Response: When and How IDHS Found Out
September 2025. Over four years into the breach.
Illinois IDHS was conducting an internal security review when they discovered the mapping website was accessible from the internet. Upon finding it, they immediately took the website offline and began investigating the scope of the exposure.
The immediate response was competent:
- Shutdown: The accessible website was removed from the internet.
- Investigation: IDHS reviewed logs to determine the exposure period and which data was visible.
- Notification: Letters were prepared and sent to all affected individuals.
- Support: IDHS is providing two years of credit monitoring and identity theft protection services to all affected residents at no cost.
- Documentation: Officials created incident reports and began the notification process.
However, the discovery process itself raises questions. Why was this discovered during an internal review and not through continuous security monitoring? Most organizations should have automated systems checking whether internal applications are accidentally exposed to the internet. This is not a complex or expensive tool to deploy. It's standard security hygiene.
The fact that it took an internal audit to find this vulnerability suggests IDHS was not running continuous security assessments.
Who's Actually at Risk: The Real-World Implications
Now here's where this gets serious. The data that was exposed isn't a random set of information. It's specifically the data of people who receive government benefits. That's a significant distinction.
Vulnerable Population Risk: People receiving Medicaid, Medicare Savings Programs, or rehabilitation services may be elderly, disabled, low-income, or facing health challenges. They're potentially less able to navigate identity theft recovery. They may have less financial cushion if fraudulent charges occur.
Targeted Scams: A scammer with this dataset can craft highly convincing social engineering attacks. They know the person's address. They know the programs they're enrolled in. They can call claiming to be from IDHS and ask for verification information. The victim has no reason to be suspicious because the caller knows legitimate details about their situation.
Medical Identity Theft: For people in the rehabilitation services dataset, their names and addresses were directly exposed. A bad actor could use this information to seek medical services in their name, creating fraudulent bills and records.
Discrimination: Employers, landlords, and others could use the data to discriminate against people based on government benefit status.
Persistent Risk: Even though the website is now offline, the data has been exposed for four years. If anyone downloaded the dataset during that period, the information is now in the wild. No amount of IDHS action can retrieve it. The risk persists indefinitely.
Illinois IDHS is offering affected residents credit monitoring and identity theft protection for two years. That's helpful but insufficient for a permanent breach. The data doesn't expire after two years. The risk doesn't end when the monitoring service stops.

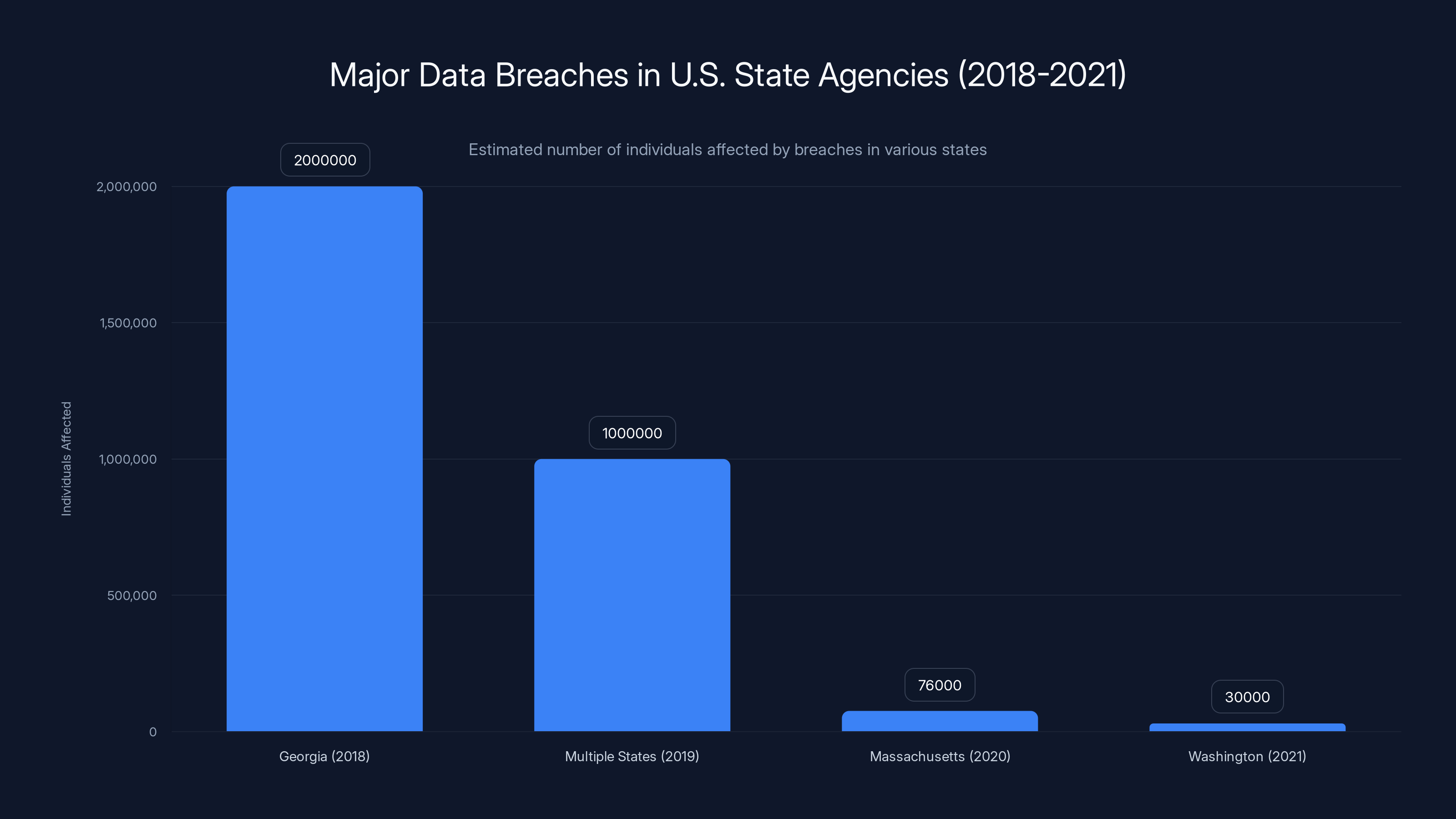
Significant breaches in state agencies highlight systemic security issues, with millions affected. Estimated data.
Legal and Regulatory Implications: What Happens Now
This breach almost certainly violates multiple regulations and laws.
HIPAA Considerations: While the Illinois Department of Human Services isn't strictly a HIPAA-covered entity for all its data, the Medicaid and Medicare Savings Program information likely falls under HIPAA requirements. The exposure of healthcare-related data to unauthorized parties is a HIPAA violation.
Under HIPAA rules, IDHS should have:
- Implemented access controls
- Used encryption for data in transit
- Conducted regular security audits
- Had a process for detecting and responding to unauthorized access
They appear to have done none of these things.
State Privacy Laws: Illinois has its own data privacy regulations. The state's personal information privacy law requires organizations to maintain reasonable security measures to protect personal information. An unsecured website visible to the internet doesn't meet that standard.
Breach Notification Laws: Illinois law requires that any breach of personal information be reported to affected individuals within a reasonable timeframe. IDHS's notification, coming in January 2026 for a breach discovered in September 2025 and occurring since April 2021, is dramatically late.
Potential Litigation: Class action lawsuits are nearly inevitable. Affected individuals will have grounds to sue for:
- Failure to protect their personal information
- Costs associated with identity theft protection and credit monitoring
- Emotional distress and loss of privacy
- Any actual damages from fraud or misuse of the data
- Punitive damages to deter future negligence
Under Illinois law, individuals can recover for violations of the Personal Information Protection Act. The case here is straightforward: personal information was exposed, IDHS failed to secure it, and affected residents are entitled to damages.
Federal Oversight: If HIPAA was violated, the U. S. Department of Health and Human Services Office for Civil Rights will likely conduct an investigation. Penalties for HIPAA violations can range from

The Broader Context: Why Governments Struggle with Security
This isn't unique to Illinois. Government agencies consistently rank among the most vulnerable to data breaches.
Why? Several factors:
Legacy Systems: Government IT infrastructure is often decades old, built before modern security practices were standard. Updating or replacing these systems requires legislative approval, budget appropriation, and lengthy procurement processes.
Budget Constraints: IT security spending is often treated as a cost center rather than a value creator. When budgets get tight, security projects get cut. Many government agencies operate with IT staff that's overworked and under-resourced.
Complexity: Government systems often need to integrate with dozens of other systems, multiple databases, and legacy applications. This complexity creates configuration errors.
Staffing: Government IT jobs pay less than private sector equivalents. This creates high turnover and difficulty attracting experienced security professionals. When experienced staff leave, documentation often leaves with them.
Bureaucracy: Security decisions often require approval from multiple committees and departments. By the time a security fix is approved, the vulnerability may have changed or evolved.
Privacy vs. Accessibility: Government agencies operate under public access requirements. There's tension between making services accessible to citizens and securing data. This tension often results in compromises on the security side.
None of this excuses the Illinois breach. It explains it, but doesn't excuse it.

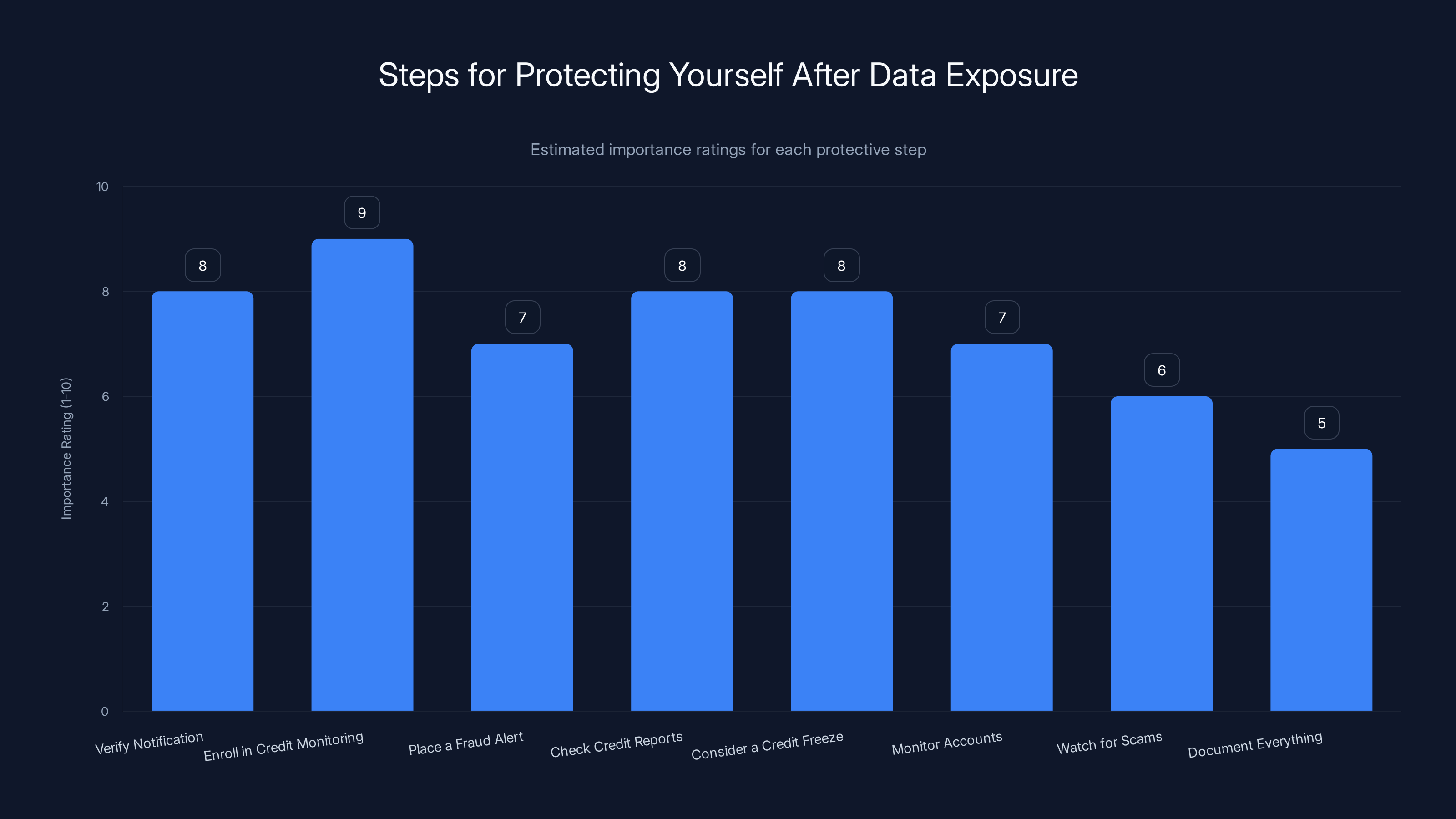
Estimated importance ratings suggest enrolling in credit monitoring and verifying notifications are the most critical steps for affected residents.
What Should Have Happened: Security Best Practices
A competent security program would have prevented this breach. Here's what should have been in place:
Asset Inventory: Every internet-connected system, application, and database should be cataloged. The organization should know exactly what systems are exposed to the internet.
Network Segmentation: Internal systems should be on internal networks, not accessible from the public internet. If the mapping website had been properly segmented, it would never have been exposed in the first place.
Access Controls: Every application should require authentication. The mapping website should have required IDHS staff to log in with credentials. This is not sophisticated security. It's baseline.
Encryption: Even if someone did access the system, data should be encrypted in transit and at rest. This adds a layer of protection if access controls fail.
Security Testing: Before deploying a system to production, it should be tested from outside the organization's network to verify it's not accidentally exposed. This should be automated and run regularly.
Monitoring and Logging: Access to sensitive data should be logged. The organization should have alerts if someone accesses the system from an unusual location or makes unusual queries. These logs would have shown if the data was accessed.
Regular Audits: Security audits should be conducted continuously, not as occasional events. Automated scanning should look for exposed systems and misconfigurations.
Incident Response Plan: When a breach is discovered, there should be a documented plan for response: who to notify, what steps to take, how to communicate with affected parties, and how to coordinate with law enforcement if necessary.
Illinois appears to have had none of these in place, or at least not effectively for this system.

Protecting Yourself: Steps for Affected Residents
If you live in Illinois and received a notification letter, or if you're unsure whether you were affected, here's what you should do:
1. Verify the Notification: Legitimate notification letters from IDHS will be official government documents. They'll have specific details about what data was exposed and contact information for enrollment in monitoring services. If you're unsure, contact IDHS directly using a phone number you find independently, not one provided in the letter.
2. Enroll in Credit Monitoring: IDHS is offering free credit monitoring and identity theft protection for two years. Sign up immediately. This service will alert you if someone tries to open new accounts in your name or makes fraudulent credit inquiries.
3. Place a Fraud Alert: Contact one of the three major credit bureaus (Equifax, Experian, Trans Union) and place a fraud alert on your credit. This tells lenders to verify your identity before extending new credit. It's free and lasts one year.
4. Check Your Credit Reports: Obtain free copies of your credit reports from each of the three bureaus at annualcreditreport.com. Review them carefully for suspicious accounts, inquiries, or accounts you don't recognize.
5. Consider a Credit Freeze: A credit freeze is more restrictive than a fraud alert. It prevents anyone, including you, from opening new accounts in your name without your explicit permission. It's free and lasts until you remove it.
6. Monitor Your Accounts: Review your bank, credit card, and other financial accounts regularly for suspicious activity. Many banks offer account alerts for unusual transactions.
7. Watch for Scams: Be aware that scammers may use the exposed data to craft social engineering attacks. Never provide personal information, case numbers, or other details in response to unsolicited calls or emails, even if the caller claims to be from IDHS.
8. Document Everything: Keep copies of notification letters, confirmation of enrollment in monitoring services, and any correspondence with credit bureaus. Save documentation of any fraud or identity theft attempts.
9. Report Fraud if It Occurs: If you discover fraudulent accounts or charges, report them immediately to the credit card company, bank, and the Federal Trade Commission at identitytheft.gov.
10. Consider Legal Action: You may have grounds to file a claim in a class action lawsuit against IDHS. Watch for notices of class action settlements or announcements. You might be entitled to compensation.

Similar Breaches: This Isn't the First Time
The Illinois IDHS breach isn't an outlier. It's part of a pattern.
2021 Washington State: The Washington Department of Social and Health Services exposed the personal information of over 30,000 residents through an improperly configured web server.
2020 Massachusetts: The Massachusetts Department of Unemployment Assistance experienced a breach exposing data for over 76,000 unemployment benefits claimants.
2019 Multiple States: The "Blue Leaks" incident exposed data from law enforcement agencies across multiple states through misconfigured cloud storage.
2018 Georgia: The Georgia Department of Revenue exposed millions of Social Security numbers and tax return information through a data visualization tool that was accessible without authentication.
These cases share common threads:
- Internal systems accidentally exposed to the internet
- Lack of access controls or authentication
- Extended periods before discovery (months to years)
- Vulnerable populations disproportionately affected
- Significant costs for remediation and litigation
The pattern suggests a systemic issue in how government agencies approach IT security. It's not isolated incompetence. It's endemic.

The Future: What Needs to Change
For this pattern to change, several things need to happen:
Mandatory Security Standards: Government agencies should be required to meet minimum security standards before deploying systems handling personal information. These standards should include access controls, encryption, and regular security audits.
Dedicated Security Budgets: Security should be its own budget line, not competing with other IT priorities. When budgets get cut, security should be protected, not slashed.
External Audits: Independent third parties should regularly audit government systems for security vulnerabilities. These audits should be transparent and public.
Accountability: Officials responsible for security failures should face consequences. If IT directors or CIOs repeatedly allow breaches to occur, they should be removed from their positions.
Modern Infrastructure: Legacy systems should be replaced with modern, cloud-based solutions that have security built in by default. This requires investment, but it's cheaper than continuing to patch ancient systems.
Staffing and Training: Government agencies need to invest in attracting and retaining talented security professionals. This means competitive salaries, training opportunities, and clear career paths.
Transparency: Breaches should be reported publicly quickly, not hidden until discovery. The public has a right to know when their data is exposed.
Faster Response: The time between breach discovery and notification should be measured in weeks, not months or years.
None of these changes are difficult or expensive relative to the cost of breaches. They're basic hygiene. The fact that they're not standard practice is the real issue.

The Broader Cybersecurity Landscape: Context and Trends
The Illinois breach happens against a backdrop of escalating data breaches across all sectors.
2024 Breach Statistics: There were 3,205 reported data breaches in the United States in 2024, affecting over 887 million individuals. That's an 8% increase from 2023.
Healthcare Particularly Vulnerable: The healthcare sector experienced 725 breaches in 2024, more than any other industry, affecting nearly 123 million individuals.
Ransomware Connection: Many data breaches are now connected to ransomware attacks, where attackers encrypt systems and demand payment. When organizations refuse to pay, attackers release the stolen data.
Compliance Failures: Many breaches occur because organizations fail to implement regulations like HIPAA, GDPR, or state privacy laws. The Illinois breach represents a failure to meet standards that have existed for decades.
Insider Threats: While the Illinois breach was external (public internet exposure), many breaches involve employees or contractors accessing data they shouldn't have access to.
Supply Chain Vulnerabilities: Increasingly, breaches occur through third-party vendors and service providers, not through direct attacks on organizations.
The broader context is that data security is now a critical infrastructure concern. Breaches affect not just individual privacy but critical services that depend on secure systems.

Expert Perspectives: What Security Professionals Say
Security professionals aren't surprised by this breach. They've seen it countless times.
The typical assessment:
"This is basic misconfiguration. It should never happen. But it does happen regularly because organizations don't treat security as a priority until after a breach." That sentiment is near-universal among security experts analyzing the Illinois case.
Another common observation: "The response is too little, too late. Two years of credit monitoring doesn't address the fact that data has been publicly available for four years. If someone has already exploited the data, the damage is done."
The overarching theme: This is preventable. Every single element of this breach could have been prevented with basic security practices that have been standard for decades.

Key Takeaways: What This Means for You
Here's what matters about the Illinois IDHS breach:
1. Your government data isn't as secure as you think: If you receive government benefits or services, your data may be at risk. This breach exposes a pattern where government agencies don't prioritize data security.
2. This will happen again: Unless agencies fundamentally change how they approach security, similar breaches are inevitable. The conditions that created this breach still exist at countless other government agencies.
3. You need to take personal protective measures: Waiting for organizations to secure your data is a losing strategy. You need to monitor your own credit, use fraud protection, and watch for identity theft.
4. Liability and cost are enormous: The Illinois breach will cost tens of millions in litigation, credit monitoring, notification, and remediation. That's money that could have been spent on actual services.
5. Regulation matters: Strong privacy laws with teeth (like GDPR in Europe) have forced better security practices. The U. S. needs similar comprehensive privacy regulation.
6. Security is a practice, not a product: You can't buy security and consider it done. Security requires continuous monitoring, testing, auditing, and improvement.

FAQ
What personal information was exposed in the Illinois IDHS breach?
The exposed data included home addresses, case numbers, and demographic information for 672,616 Medicaid and Medicare Savings Program recipients. For 32,401 individuals receiving Division of Rehabilitation Services, the data included names, addresses, case statuses, and service information. Social Security numbers were not directly exposed, but case numbers combined with addresses could be used to identify individuals.
How long was the data publicly accessible?
The mapping website was publicly accessible from April 2021 through September 2025, a period of approximately 4 years and 5 months. The vulnerability was discovered during an internal security review in September 2025, after being exposed for over 1,600 days.
Who was responsible for this breach?
The Illinois Department of Human Services is ultimately responsible for the breach. The specific fault lies with whoever configured the mapping website without access controls, those who failed to verify the system was secure before deploying it, and the organization's leadership for not implementing proper security practices and monitoring.
How can I check if I was affected by this breach?
If you received a notification letter from the Illinois Department of Human Services, you were affected. You can also contact IDHS directly at the number provided in the letter (verify the number independently) or check the Illinois government website for official breach announcement information.
What identity theft protection services are being offered?
Illinois IDHS is providing two years of complimentary credit monitoring and identity theft protection services to all affected residents. The notification letter should include enrollment instructions and contact information for the service provider.
What should I do if I discover fraudulent accounts in my name?
Immediately report fraudulent accounts to the relevant creditor or bank, place a fraud alert with the credit bureaus, and file a report with the Federal Trade Commission at identitytheft.gov. Document all communications and keep records of any fraudulent activity for potential legal claims.
Could this breach have been prevented?
Absolutely. Standard security practices would have prevented this breach entirely. Access controls, network segmentation, authentication requirements, security testing before deployment, and continuous monitoring would have caught this issue immediately or prevented it from occurring in the first place.
Will there be lawsuits against the state?
Yes, class action lawsuits are likely or already filed. Affected residents have grounds to sue for failure to protect personal information, costs of identity theft protection, emotional distress, and any actual damages from fraud. Check for notices of class action settlements or seek information from a lawyer specializing in data breach litigation.
How long should I monitor my credit after this breach?
You should monitor your credit indefinitely, not just for two years. The data was publicly exposed for four years, so if someone downloaded it, the risk persists beyond the credit monitoring period. Continue checking your credit reports and accounts regularly for the foreseeable future.
What regulations did Illinois IDHS violate?
The breach likely violates HIPAA (if healthcare data is covered), Illinois's Personal Information Protection Act, state privacy laws, and breach notification requirements. The U. S. Department of Health and Human Services Office for Civil Rights may investigate HIPAA violations and levy fines.

Related Articles
- Condé Nast Data Breach 2025: What Happened and Why It Matters [2025]
- SwitchBot's AI Recording Device: Privacy, Ethics & What You Need to Know [2025]
- US Withdraws From Internet Freedom Bodies: What It Means [2025]
- Brightspeed Data Breach Investigation: What Happened & What's Next [2025]
- Covenant Health Breach Exposes 500K Patients: What Happened [2025]
- WhatsApp Security Features: Complete Privacy Guide [2025]
![Illinois Health Department Data Breach: 700K+ Exposed [2026]](https://tryrunable.com/blog/illinois-health-department-data-breach-700k-exposed-2026/image-1-1767895812556.jpg)



