Windows 11's Critical Bug Crisis: What You Need to Know Right Now
Something went really wrong in January 2026. Microsoft's routine monthly security update did what nobody wants a security update to do: it broke things. And not in some obscure corner case. No. It made Outlook crash. It made One Drive files inaccessible. It made basic productivity grind to a halt for millions of Windows 11 users, as reported by Windows Central.
Then Microsoft did what they've done twice in recent weeks: released an emergency out-of-band patch. We're talking about unscheduled, "we need to fix this right now" updates. Not the normal Patch Tuesday rhythm. This is the second emergency fix in as many weeks, and honestly, it signals something deeper about how Windows 11 updates are being tested before they ship, according to Windows Central.
Let's unpack what actually happened, who got hit hardest, and what it means for your Windows 11 machine.
The Timeline of Chaos
Here's the sequence of events that led to this mess. Microsoft released its January 2026 security update—KB5078127 and related patches—as part of standard Patch Tuesday operations. These updates are supposed to patch vulnerabilities, tighten security, and improve stability. Most of the time, they do exactly that.
But this time, something in those updates introduced a critical bug. When apps tried to open or save files stored in cloud-backed locations, they'd become unresponsive. Think One Drive, Google Drive, or cloud-synced folders. The system would hang. Error messages would cascade. And users would stare at a frozen application wondering what went wrong, as detailed by Windows Latest.
Outlook users had it worst. If your PST files were stored anywhere on One Drive or similar cloud storage, Outlook wouldn't just get slow. It would crash entirely. Some users couldn't open the app at all. Others could launch it but any attempt to access emails would trigger an instant shutdown, as noted by XDA Developers.
Within days, Microsoft started investigating. Within a week, they issued the first emergency out-of-band patch. But that first patch? Incomplete. Didn't fully solve the problem for everyone. So here we are with the second emergency update, as reported by Gulf News.
This isn't normal. Microsoft typically releases updates on a predictable schedule. Emergency patches on this scale are rare. Two in succession? That's a sign the testing pipeline missed something significant, as highlighted by Engadget.
Why This Matters Beyond Just Annoyance
You might think, "Okay, update got broken. Microsoft fixed it. Story over." But the implications run deeper.
First, there's the productivity hit. Outlook isn't some niche app. It's the email and calendar tool for enterprise environments. Millions of people rely on it for their daily work. When it crashes, they can't send emails, they can't see meeting invitations, they can't coordinate with colleagues. For knowledge workers, that's essentially a system outage, as noted by TechBuzz.
Second, there's the trust factor. Windows 11 users already had concerns about forced updates and limited control over patch deployment. An emergency security update that breaks critical applications reinforces the worry that updates aren't being thoroughly tested before release. If a basic file access operation in Windows can trigger crashes in major applications, what else is potentially fragile? This concern was echoed by Reuters.
Third, there's the technical debt question. These kinds of widespread bugs suggest that either the test coverage for file system interactions is inadequate, or the code changes in these updates were insufficiently reviewed. Either way, it points to process issues that need addressing, as discussed by Forbes.
Who Got Affected and How
Not every Windows 11 user experienced the crashes. The bug had specific trigger conditions. You had to meet these criteria to hit the problem:
You were using cloud-backed file storage: Applications that accessed files on One Drive, Share Point Online, or other cloud-synced storage locations were vulnerable. If your files were entirely local, you weren't affected.
You had Outlook installed and configured: The Outlook crashes were specifically tied to PST files stored in cloud locations. Outlook Web Access users bypassed this entirely. Local PST files didn't trigger the crashes.
You applied the January 2026 updates: This seems obvious, but some enterprise environments delay updates for testing. If your organization held off on the January patches, you never experienced the problem.
You hadn't manually migrated your PST files: Some users quickly moved their Outlook data back to local storage as a workaround. Once files were off cloud storage, the crashes stopped.
So while this affected millions of users globally, it wasn't universal. Enterprise users with cloud-first strategies and One Drive integration got hit hardest. Small businesses relying on Microsoft 365 and cloud storage saw significant disruption. Home users who use One Drive for file backup but don't store their Outlook data there often weren't impacted, as reported by TechPowerUp.
The Technical Root Cause (What Actually Broke)
Microsoft's explanation indicates the problem existed in how Windows handled file access permissions and synchronization for cloud-backed locations. The January updates modified code related to how the operating system communicates with cloud storage services, how it manages file locks, and how it handles permission verification, as detailed by The Zero Day Initiative.
When an application tried to open a file stored in One Drive, Windows would initiate a specific sequence: authenticate with the cloud service, verify permissions, download the file (or access it through sync), and present it to the application. The buggy updates apparently broke something in this chain.
Specifically, the system would fail to properly release file locks or would get stuck waiting for cloud service responses. Applications would timeout. For something like Outlook, which needs to access PST files frequently and immediately, any delay causes the entire application to freeze. After enough timeouts, Outlook would crash entirely.
This also affected cloud storage tools themselves. One Drive sync would stall. Google Drive would become unresponsive. Any application relying on these services would experience performance degradation or crashes.
The fix involved reverting or modifying the specific code changes that touched cloud file handling. Microsoft had to identify which lines of code in which files were causing the hangs, patch them, and test the fix extensively before releasing it.
The Emergency Update Process Explained
Microsoft operates on a monthly "Patch Tuesday" schedule, typically the second Tuesday of each month. Updates are batched, tested, and released according to that schedule. It's predictable. Organizations can plan for it.
But when something breaks that affects critical functionality, Microsoft also has an emergency out-of-band (OOB) update process. OOB updates bypass the normal schedule. They're released as soon as they're ready, on any day of the week.
The process looks like this:
Discovery: Reports come in about widespread crashes or broken functionality. Microsoft's monitoring systems flag unusual error patterns.
Investigation: Engineers identify the problematic code change in the latest updates.
Triage: The team determines severity and scope. Is this affecting a small percentage or millions of users? Is it a workaround-able problem or a complete blocker?
Fix Development: Developers write and test the fix. This happens under pressure with multiple engineers involved.
Testing: The fix gets tested across multiple Windows 11 versions, configurations, and scenarios. This is accelerated but still rigorous.
Release: The update goes out globally as soon as testing clears it.
The problem is that with accelerated timelines, sometimes the fix itself has issues. That appears to be what happened here. The first emergency patch didn't fully address the problem, necessitating a second round, as noted by TechBuzz.
This kind of back-and-forth suggests that either the original fix was incomplete (it addressed some scenarios but not all), or testing during the accelerated timeline didn't catch all edge cases.
How to Tell If You're Affected
If you're wondering whether these bugs hit your system, here are the telltale signs:
Outlook crashes on startup or when accessing emails: If Outlook launches but immediately crashes, or crashes when you click on a folder or message, you're experiencing the file access bug.
Outlook works in Safe Mode but crashes normally: This is classic add-in interference or file access problem. Safe Mode disables some features, so if it works there, the bug is in the normal operation path.
Frozen applications when accessing One Drive files: If One Drive files take forever to open, or applications hang when touching cloud-stored documents, the bug is active on your system.
Error messages about file permissions or synchronization: Windows and apps may show specific errors about not being able to access cloud files or losing connection to cloud services.
System is sluggish when One Drive is syncing: General slowdown when cloud sync is active indicates file handling bottlenecks.
If you're seeing any of these, the emergency update should resolve them. If you've already installed the latest patches and still have issues, you might be hitting a different problem or need to try the manual workarounds.
Manual Workarounds Before Updating
If you need your system working immediately and can't wait for the update to deploy, there are temporary fixes:
Move Outlook data to local storage: Export your PST files and store them locally instead of One Drive. You lose cloud backup convenience, but Outlook will work. Once the update installs, you can move them back.
Use Outlook Web Access: Access your email through a browser instead of the Outlook desktop application. This completely bypasses the file access bug since it doesn't use local PST files.
Disable cloud sync for files temporarily: If you have One Drive Files On-Demand enabled, turn off cloud-only files. Make everything available offline. This forces local caching and avoids the cloud access code path.
Run Outlook in Safe Mode: Use "Outlook /safe" from the Run dialog. This disables add-ins and some features, which sometimes allows the application to work even with the bug present.
Delay updating until the fix is available: If you manage your own updates and haven't installed the January patches yet, you could hold off. Obviously, this has security implications, so it's a last resort.
None of these are permanent solutions. They're just ways to keep working while waiting for Microsoft's fix to deploy to your system.
Installation and Deployment Strategy
Here's how the emergency update reaches your computer. Windows 11 has multiple update channels:
Home and Pro editions: Automatic updates. The patch deploys automatically once it's released. You can check for updates manually via Settings, but you don't control the timing. Windows will install it and restart your computer.
Enterprise editions: More control through Windows Server Update Services (WSUS) or mobile device management. Organizations can deploy the update to test groups first, verify it works, then roll out broadly.
Organizations using Group Policy: Updates can be pushed and scheduled during maintenance windows.
For home users, the patch should arrive automatically within a few days of release. If you need it immediately, go to Settings > System > About and click "Check for updates now."
For business users, coordinate with your IT department. They likely have testing procedures for emergency patches. Don't apply it immediately to all machines if you can help it. Let a pilot group test it first.
The Broader Pattern of Recent Windows 11 Issues
This isn't an isolated incident. Windows 11 has been dogged by update-related problems since launch. Over the past year, we've seen:
Boot failures: Earlier emergency patches were needed because some users couldn't boot their computers after updates.
File explorer crashes: Updates that made File Explorer unstable, requiring users to restart Windows constantly.
Display and graphics issues: Updates that broke display drivers or caused screen flickering.
Networking problems: Updates that disconnected Wi-Fi or killed network connectivity.
Each time, Microsoft released emergency fixes. But the pattern is concerning. It suggests that Windows 11's update testing, code review, or CI/CD pipeline has gaps. Something fundamental in how updates are validated before release needs improvement, as discussed by The Zero Day Initiative.
Compare this to previous Windows versions. Yes, they had issues too. But the frequency and severity of emergency patches for Windows 11 is notable. It's raised questions in the industry about whether Microsoft's development practices have changed, whether testing infrastructure is adequate, or whether the complexity of Windows 11 simply outpaces the testing capability.
Why These Bugs Happen: The Complexity Problem
Windows is one of the most complex software projects ever created. Millions of lines of code. Support for thousands of hardware configurations. Tight integration with cloud services, device managers, security systems, and productivity applications.
When you make changes to core file handling code—which touches everything from local file access to cloud service integration—you're potentially affecting hundreds of applications and millions of users. The surface area for unintended consequences is enormous.
Modern development practices try to mitigate this through automated testing, unit tests, integration tests, and staged rollouts. But there are limits. You can't test every possible hardware configuration. You can't test every combination of installed software. You can't test every possible cloud service integration.
So bugs slip through. Not through carelessness, but through the sheer complexity of the problem.
The solution isn't to never update Windows. Security patches are essential. The solution is better testing infrastructure, more careful code review, and perhaps more conservative rollout strategies. Release to a small percentage first. Monitor for errors. Expand gradually.
Microsoft has improved in this area with their "Insider" testing programs and staged rollouts, but there's clearly more room for improvement given recent events.
Recovery and System Verification After Updating
Once you've installed the emergency patch, how do you verify everything's working correctly?
Check Windows Update history: Go to Settings > System > About, then "Update history." Verify that KB5078127 and any subsequent patches have installed successfully.
Restart Outlook and test basic functions: Open Outlook, check that emails load, try creating a new message, navigate through folders. Make sure the app is stable.
Test cloud file access: Open File Explorer, navigate to One Drive or your cloud storage. Try opening, editing, and saving files. Performance should be normal, not frozen.
Check One Drive sync status: Right-click the One Drive icon in the system tray. Sync status should show "Up to date" or show active syncing, not errors.
Review Event Viewer for errors: Open Event Viewer, check the Windows Logs section for any critical errors logged during startup or normal operation. Previous instability might have left error entries.
Run Windows Defender or third-party antivirus scan: Sometimes corruption from crashes or forced shutdowns can require a full system scan. Better to be thorough.
If you're still experiencing crashes after the update has fully installed, you may have a separate issue. Corrupted PST files, problematic Outlook add-ins, or hardware issues could still cause problems even after the Windows fix.
Impact on Enterprise and Business Users
For organizations relying on Microsoft 365 and cloud storage, these bugs have real costs. Downtime translates directly to lost productivity. If half your organization can't access email for a few hours, that's significant.
Enterprise IT departments face a difficult situation. They need security updates. But rushing to deploy updates that introduce new problems defeats the purpose. Many organizations will now adopt an even more cautious approach: wait longer before deploying updates, test more extensively, and only roll out to production when confident.
This can create a security gap. If everyone delays updates to avoid problems, then everyone's exposed to the vulnerabilities those updates were meant to patch. It's a tradeoff with no perfect solution.
Microsoft needs to respond by strengthening their testing and validation processes. If enterprises lose confidence in Windows updates, the security posture of the entire ecosystem suffers.
Forward Predictions: What Needs to Change
Based on the pattern of recent issues, here's what Microsoft needs to do differently:
Expand staged rollouts: Don't release updates to 100% of users simultaneously. Roll out to 10%, then 25%, then 50%, then 100%. Monitor each stage for errors before expanding.
Improve integration testing: Test not just Windows in isolation, but Windows running with common productivity applications like Office, One Drive, and third-party software.
Increase pre-release testing participation: The Windows Insider program helps, but it needs more users and more realistic workloads. Home users and small businesses aren't adequately represented.
Add continuous monitoring post-release: Track error telemetry in real-time. If crash rates spike after an update, trigger an immediate investigation rather than waiting for user reports to accumulate.
Establish clear rollback procedures: If an update causes widespread issues, Microsoft should be able to roll it back quickly rather than always pushing forward with patches.
Communicate proactively: When issues are known, get information out to users immediately with workarounds. Don't let confusion fester.
Some of these are already happening. Microsoft has improved significantly. But the recent emergency patches indicate there's still room for progress.
Outlook Specifically: Why It's Particularly Vulnerable
Outlook's crash issues during this incident reveal something about how the application architecture works. Outlook heavily relies on reading and writing PST files, which are essentially database files containing all your emails, calendars, and contacts.
When those files live on cloud storage, every operation involves a cloud communication. Open an email? Read from PST on One Drive. Create a new message? Write to PST on One Drive. The application's performance is directly tied to cloud service responsiveness.
If Windows hangs trying to access those cloud-stored files, Outlook has no choice but to hang as well. The application can't proceed until the file operation completes. Unlike a web app that can show a loading spinner and give the user feedback, Outlook's architecture means it freezes.
This highlights why Microsoft has been pushing the new Outlook for Windows, which doesn't rely on PST files in the same way. The new version stores data in Microsoft's cloud infrastructure directly, rather than syncing local files. It's more resilient to these kinds of file system issues.
But millions of users still run the classic Outlook, so this vulnerability will remain until everyone upgrades to the new version.
PST Files and Cloud Storage: An Inherent Tension
There's a fundamental architectural tension here worth understanding. PST files are optimized for local storage with synchronous file access. Cloud storage is optimized for distributed, asynchronous access with potential latency.
When you combine them, you get the worst of both worlds. Outlook expects file operations to be fast and predictable. Cloud storage sometimes has latency, occasional disconnections, or sync delays. Overlay a Windows bug that makes the situation worse, and everything breaks.
This is why cloud-native applications like the new Outlook, Gmail, or Microsoft Teams work better in modern environments. They're architected from the ground up to handle cloud latency and disconnections.
For users still using PST files on cloud storage, the safest long-term solution is migrating to cloud-native tools. But that's not something everyone can do immediately.
The Security Update Tradeoff
Here's the difficult reality: the January 2026 security updates were released because they patched actual security vulnerabilities. Those vulnerabilities are real threats. If Windows users don't get those patches, malicious actors can exploit the vulnerabilities.
So when one of those security patches introduces a stability bug, Microsoft faces a tough choice. Roll back the security patch and leave users vulnerable? Or push forward with a fix, accepting some transitional risk?
They chose the latter, and it was probably the right call. Security vulnerabilities are often worse than stability bugs. A stability bug prevents you from working. A security vulnerability can result in your computer being hacked.
But this highlights why testing is so critical. These kinds of tradeoffs should never need to exist. If updates were sufficiently tested, you wouldn't have to choose between security and stability.
What Users Should Do Right Now
If you haven't yet:
Install the latest updates: Go to Settings > System > About and check for updates. Install anything available. The emergency patches are cumulative, so the latest version includes all fixes.
Back up important data: If you're experiencing crashes, back up your email data, documents, and files before applying updates. A backup is always good practice anyway.
Update all your software: While you're at it, update Windows, Office, and other applications. Bug fixes often help with these kinds of issues.
If you have issues after updating:
Restart your computer: First troubleshooting step for everything. More often works than you'd think.
Check for incomplete installations: Windows Update sometimes needs to finish installing updates. Restart and check for updates again.
Repair Office: In Settings > Apps > Apps and Features, find Microsoft Office, click it, and select "Repair." This can fix corrupted installations.
Move PST files to local storage temporarily: If you're still having Outlook issues, move your data back to a local drive to eliminate the cloud variable.
Contact Microsoft Support: If nothing works, official support can help diagnose what's happening with your specific system.
Lessons for Other Software Companies
While this incident happened to Microsoft, it's instructive for any software company:
Test cloud integrations thoroughly: Cloud-backed features need special attention in testing. They introduce variables local testing can't always replicate.
Monitor early for issues: Use telemetry and crash reporting to detect problems immediately after rollout. Early detection allows faster fixes.
Have a kill switch: Consider ways to quickly disable problematic features or code paths without requiring a full update.
Communicate clearly: When something goes wrong, explain it clearly and provide workarounds. Users can handle technical issues better than uncertainty.
Build fault tolerance: Code should handle failures gracefully rather than crashing. Cloud operations should timeout rather than hang forever.
Microsoft has resources and expertise that most companies don't. If this can happen to them, it can happen to anyone. The lesson is that scale and complexity require extraordinary attention to testing and monitoring.
The Positive Side: Quick Response
To be fair to Microsoft, they did respond reasonably quickly. Within a week of the bug reports becoming widespread, they released an emergency patch. Within another week, they released a second one, as noted by TechPowerUp.
Compare that to how some software companies handle problems. Sometimes issues go unaddressed for months. Microsoft could have waited until the next Patch Tuesday to fix this. They didn't. They recognized the severity and acted.
The execution wasn't perfect (the first patch was incomplete), but the intent and speed were appropriate for the situation.
For users frustrated by these issues, it's worth noting that Microsoft is clearly investing in making Windows updates more reliable. The frequency of emergency patches is concerning, but it also shows that problems are being caught and fixed rather than left to fester.
Long-Term Implications for Windows 11
These incidents have longer-term implications for how users perceive and interact with Windows 11. If users lose trust in the update process, they might:
Disable automatic updates: This is dangerous from a security perspective, but users will do it if they feel updates are destabilizing their systems.
Delay adopting Windows 11: Some organizations considering Windows 11 upgrades might delay based on these stability concerns.
Switch to other platforms: For users with flexibility, reliability concerns might push them toward mac OS or Linux, where stability tracks like the Mac's approach to updates might seem more appealing.
Demand more update control: Users will increasingly want granular control over what updates do, when they install, and what gets changed.
Microsoft's ability to address these issues and rebuild confidence will shape Windows' competitive position. If they get it right, Windows 11 can remain the dominant PC operating system. If problems continue, the momentum could shift.
Looking Ahead: What Windows 11 Needs to Prove
As we move through 2025 and beyond, Windows 11 needs to prove that these emergency patches were anomalies, not the norm. That means:
Fewer emergency patches: Ideally, zero emergency patches required. All critical fixes should be caught during normal testing.
Faster resolution time: If emergency patches are needed, they should be deployed within days, not weeks.
Proactive communication: Users and IT departments should know about potential issues before they personally experience them.
Robust testing for cloud scenarios: With cloud integration becoming standard, Windows needs testing that thoroughly covers cloud-backed applications and storage.
Hardware compatibility focus: Windows needs to work reliably across the hundreds of millions of different hardware configurations in the wild.
Windows 11 has been out for several years now. The bugs encountered recently suggest that either the codebase is more fragile than it should be, or the testing pipeline needs improvement. Probably both.
But there's time to fix it. Microsoft has the resources and expertise. Whether they make the necessary changes depends on whether leadership prioritizes reliability as much as feature development and innovation.
FAQ
What is the Windows 11 Outlook crash issue?
The Windows 11 Outlook crash issue was caused by a bug introduced in Microsoft's January 2026 security updates. When applications tried to open or save files stored in cloud-backed locations like One Drive, they would become unresponsive or crash entirely. Outlook was particularly affected because users often store their PST files (email data) on One Drive, causing the application to crash or fail to open completely.
How does the emergency update fix the problem?
The emergency out-of-band update (KB5078127 and subsequent patches) contains code fixes that address the file access handling bug in Windows 11. The update modifies how the operating system communicates with cloud storage services, manages file locks, and handles permission verification. By correcting these underlying issues, the update restores normal functionality for cloud-based file operations, allowing Outlook and other applications to work properly again.
Who was affected by the Outlook crashes?
The crashes primarily affected Windows 11 users who met specific conditions: they were using cloud-backed file storage like One Drive or Share Point, they had Outlook installed with PST files stored in cloud locations, and they had installed the January 2026 Windows updates. Home users with entirely local files, Outlook Web Access users, and organizations that delayed updates were largely unaffected.
How can I tell if my system is affected?
You're affected if you experience Outlook crashes on startup or when accessing emails, frozen applications when opening One Drive files, error messages about file permissions or synchronization, or significant system slowdown when cloud syncing is active. If Outlook works in Safe Mode but crashes normally, that's also a sign of the file access bug. Check Windows Update history to see if you've installed the January 2026 patches.
What temporary workarounds exist for the Outlook crashes?
Several temporary solutions are available while waiting for the update to install: move your Outlook PST files from One Drive to local storage, use Outlook Web Access through a browser instead of the desktop application, disable One Drive Files On-Demand to force local caching, run Outlook in Safe Mode using "Outlook /safe", or delay updating if you haven't yet installed the January patches. These are temporary measures—the emergency update provides the permanent fix.
When will the emergency update be deployed to my computer?
For Windows 11 Home and Pro editions, the emergency update deploys automatically, though it may take several days to reach all users. You can manually check for updates by going to Settings > System > About and clicking "Check for updates now." Enterprise users should coordinate with their IT department, which typically stages updates through testing before broad deployment. The update will require a restart to complete installation.
Why does Microsoft release emergency patches instead of waiting for the next Patch Tuesday?
Emergency out-of-band updates are released when widespread critical bugs affect normal functionality or security. The January 2026 update bug was severe enough to warrant immediate action because millions of users couldn't access email or cloud files. Microsoft could have waited until the next scheduled Patch Tuesday, but doing so would have extended the disruption. Emergency patches balance the urgency of widespread problems against the need for proper testing.
Should I be concerned about update reliability going forward?
The recent emergency patches do suggest that Windows 11's update testing could be improved, as several updates in the past year have introduced stability issues. However, Microsoft has been responsive in deploying fixes. The broader lesson is that organizations should adopt cautious update strategies: implement staged rollouts, test updates in pilot groups before full deployment, and monitor systems for unexpected issues. For individual users, keeping current with updates remains essential for security despite these occasional stability issues.
Are there any risks to installing the emergency update?
The emergency update is designed to fix problems, not create new ones. Microsoft conducted accelerated testing before release, and the second emergency update was released specifically to address issues with the first one. The risks of not installing the update (continued crashes, inability to access cloud files) significantly outweigh the minimal risk of the update itself. Installation does require a system restart, so plan for minimal downtime.
What's the difference between this emergency patch and regular monthly updates?
Regular monthly "Patch Tuesday" updates are released on a predictable schedule (second Tuesday of each month), are batched with multiple fixes and patches, and undergo standard testing cycles. Emergency out-of-band updates bypass this schedule and are released whenever critical issues require immediate attention. They typically address specific problems rather than containing multiple unrelated patches. The emergency patches for the Outlook crashes were released outside the normal schedule because the problems affected too many users to wait for the next monthly cycle.

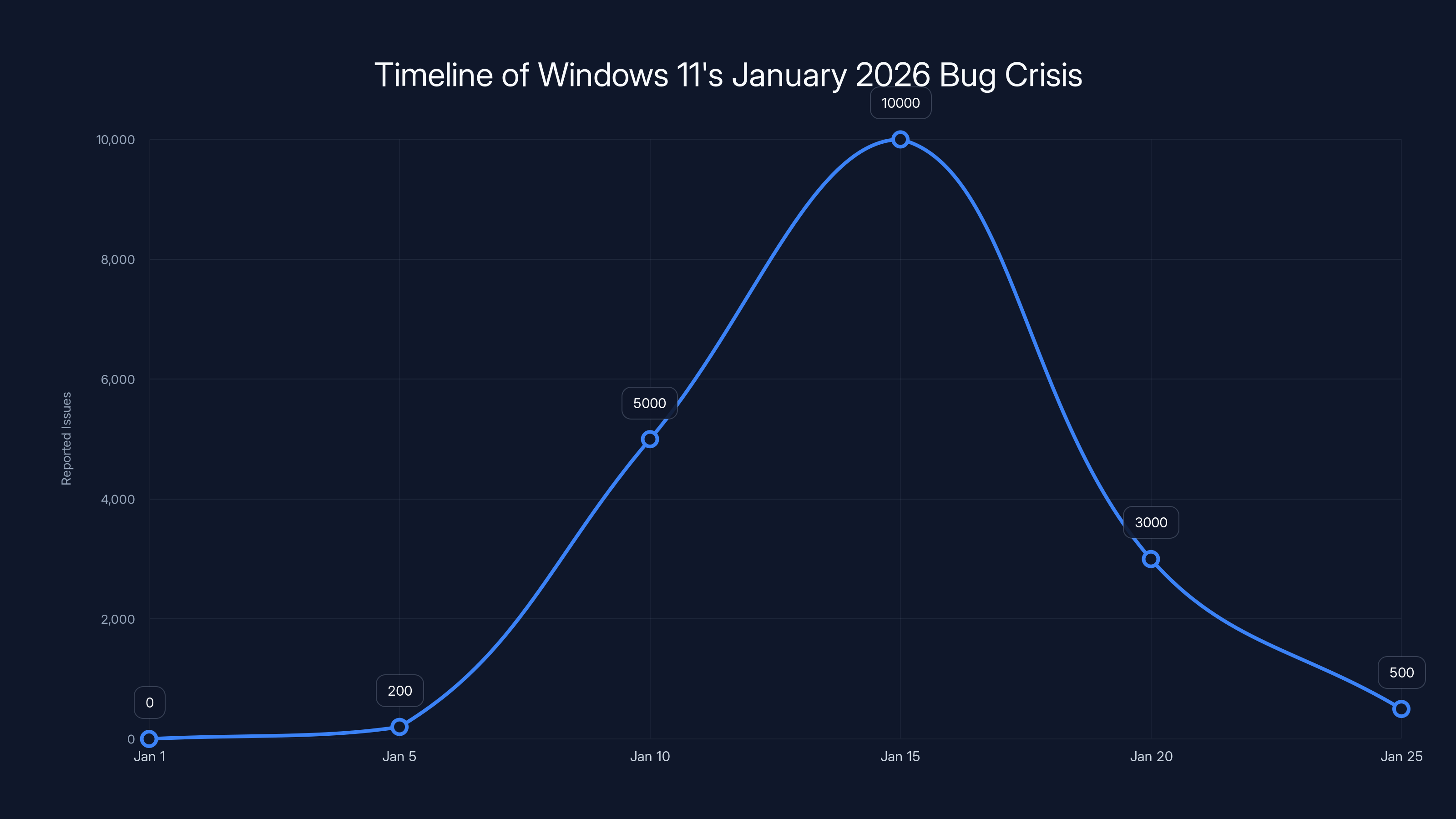
The number of reported issues peaked around January 15, 2026, following the release of the problematic update. Estimated data based on typical bug report escalation.
Key Takeaways
Microsoft's January 2026 security updates inadvertently introduced a critical bug affecting file access for cloud-backed storage, causing Outlook crashes and application freezes for millions of Windows 11 users. The company responded with two emergency out-of-band updates to address the issue, demonstrating both the severity of the problem and Microsoft's commitment to rapid response, though the need for a second emergency patch suggests testing gaps exist. Users affected by Outlook crashes can install the latest Windows updates, move PST files to local storage temporarily, or use Outlook Web Access as immediate workarounds while waiting for patches to deploy. The incident highlights the inherent complexity of modern operating systems and the challenge of testing updates across millions of hardware configurations and cloud service integrations. Going forward, Microsoft needs stronger integration testing with cloud services, more aggressive staged rollouts, and improved real-time error monitoring to prevent similar widespread issues. Organizations should adopt cautious update deployment strategies, including pilot testing and phased rollouts, rather than immediately installing updates across all systems. The episode underscores why security updates remain essential despite occasional stability risks, as the vulnerabilities they patch pose greater threats than temporary stability issues. Windows 11 users can maintain confidence in the platform while staying vigilant about monitoring system health and backing up data before major updates.
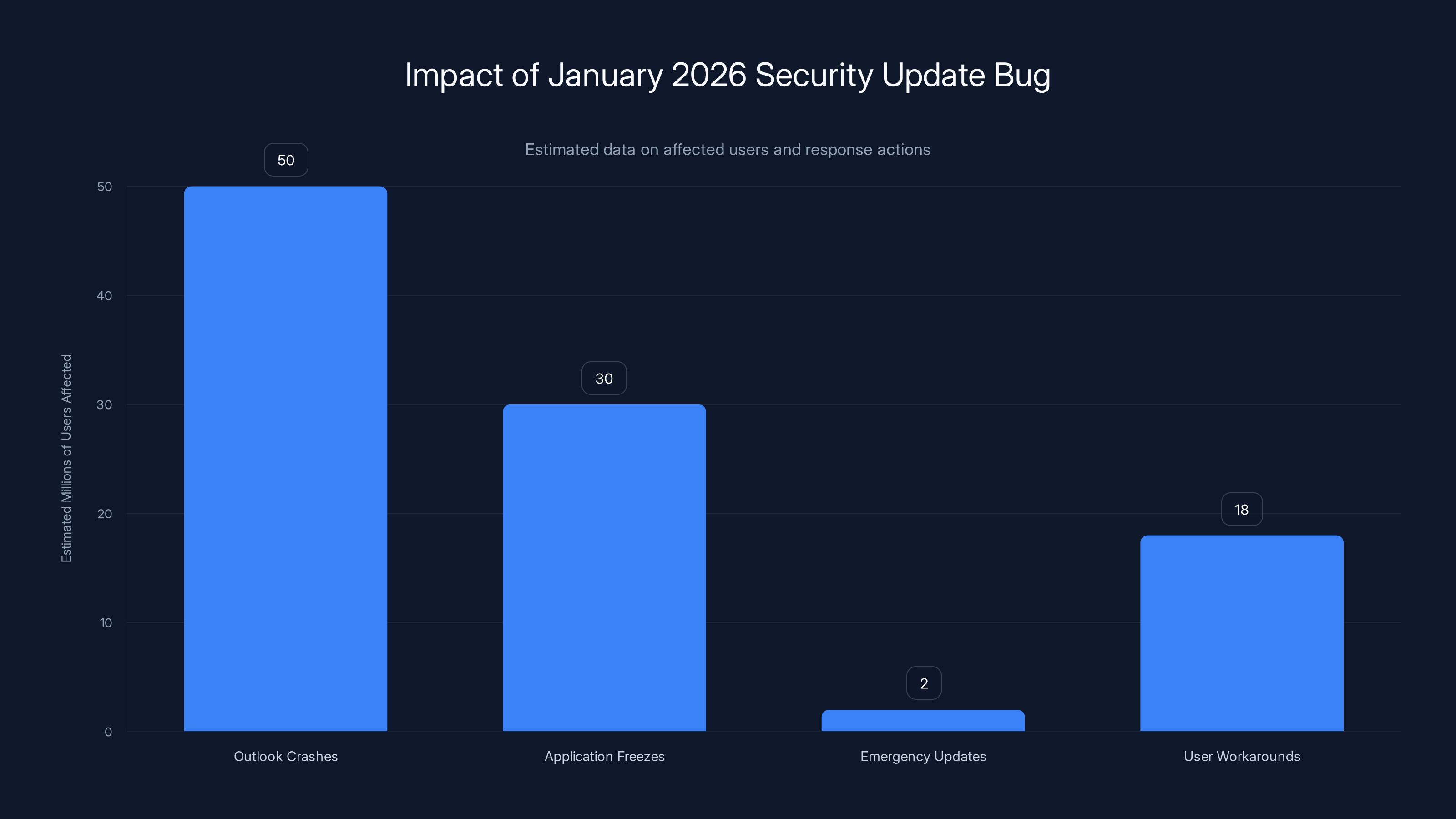
The January 2026 security update bug affected millions, with Outlook crashes impacting 50 million users and application freezes affecting 30 million. Microsoft's rapid response included two emergency updates, while 18 million users employed workarounds. (Estimated data)
Related Articles
- Windows 11 2026 Bugs Crashing Apps: Fixes & Workarounds [2025]
- Microsoft's Windows 11 Emergency Fix: Shutdown Crisis Explained [2025]
- Windows 11 Update Shutdown Bug: What Happened & How to Fix [2026]
- Windows 11 26H1 Update: Why Limited Snapdragon X2 Rollout Might Be Smart [2025]
- 5 Major Windows 11 Problems Microsoft Must Fix in 2026
- Windows 10's Legacy: What Microsoft Got Right (and How It Led to Windows 11 Problems) [2025]
![Microsoft's Emergency Windows 11 Update: Fixing Outlook Crashes [2025]](https://tryrunable.com/blog/microsoft-s-emergency-windows-11-update-fixing-outlook-crash/image-1-1769369750292.png)



