Network Modernization for AI & Quantum Success [2025]
Your company's AI strategy is doomed if your network infrastructure wasn't built for it.
I know that sounds dramatic, but the numbers back it up. Organizations are pouring billions into artificial intelligence systems, deploying models across data centers, clouds, and edge locations. Meanwhile, their networks? Still running on technology from the 2000s. Outdated architecture. Limited bandwidth. No visibility. It's like trying to run a Formula 1 engine through a garden hose.
Here's what happens in the real world: a financial services company implements an AI-powered fraud detection system. The model works beautifully in testing. But when they put it into production, latency skyrockets. The AI analysis that should take milliseconds now takes seconds. Decisions get delayed. Fraudulent transactions slip through. They've spent months and millions on AI without seeing the promised ROI. Why? The network couldn't handle the data flow the AI needed.
This isn't hypothetical. According to industry research, 53% of data center experts predict AI workloads will generate more network demand than cloud computing or big data analytics over the next two to three years. Think about that. AI is going to be the biggest driver of network traffic your company has ever seen. And most organizations' networks aren't ready.
The problem compounds when you factor in operational risk. Network fragmentation and outdated infrastructure contribute to outages averaging over 75 days per year of system downtime, costing enterprises roughly $400 billion annually in lost productivity and revenue. When you're running AI applications that support critical business decisions, downtime isn't just an inconvenience. It's a business crisis.
But there's a flip side: organizations that modernize their networks don't just fix the AI problem. They unlock something bigger. They build infrastructure that's secure, resilient, and future-proof. They prepare for quantum computing. They enable innovation they haven't even imagined yet.
This guide walks you through why network modernization matters for AI success, what actually needs to change, and how to think about quantum readiness. We're talking real infrastructure challenges, practical solutions, and a roadmap that works whether you're a mid-size company or an enterprise.
TL; DR
- Legacy networks bottleneck AI: Outdated architectures create latency, reduce visibility, and prevent AI from delivering ROI
- Modern networks accelerate AI: SD-WAN, SASE, and cloud-native architectures provide the speed, scale, and security AI demands
- 97% of IT leaders agree: Network modernization is critical to enterprise AI success
- Quantum threat is real: Encryption could be broken within 5 years; post-quantum cryptography migration must start now
- Modernization is incremental: Start with your highest-risk systems and build quantum-safe architecture as part of ongoing upgrades
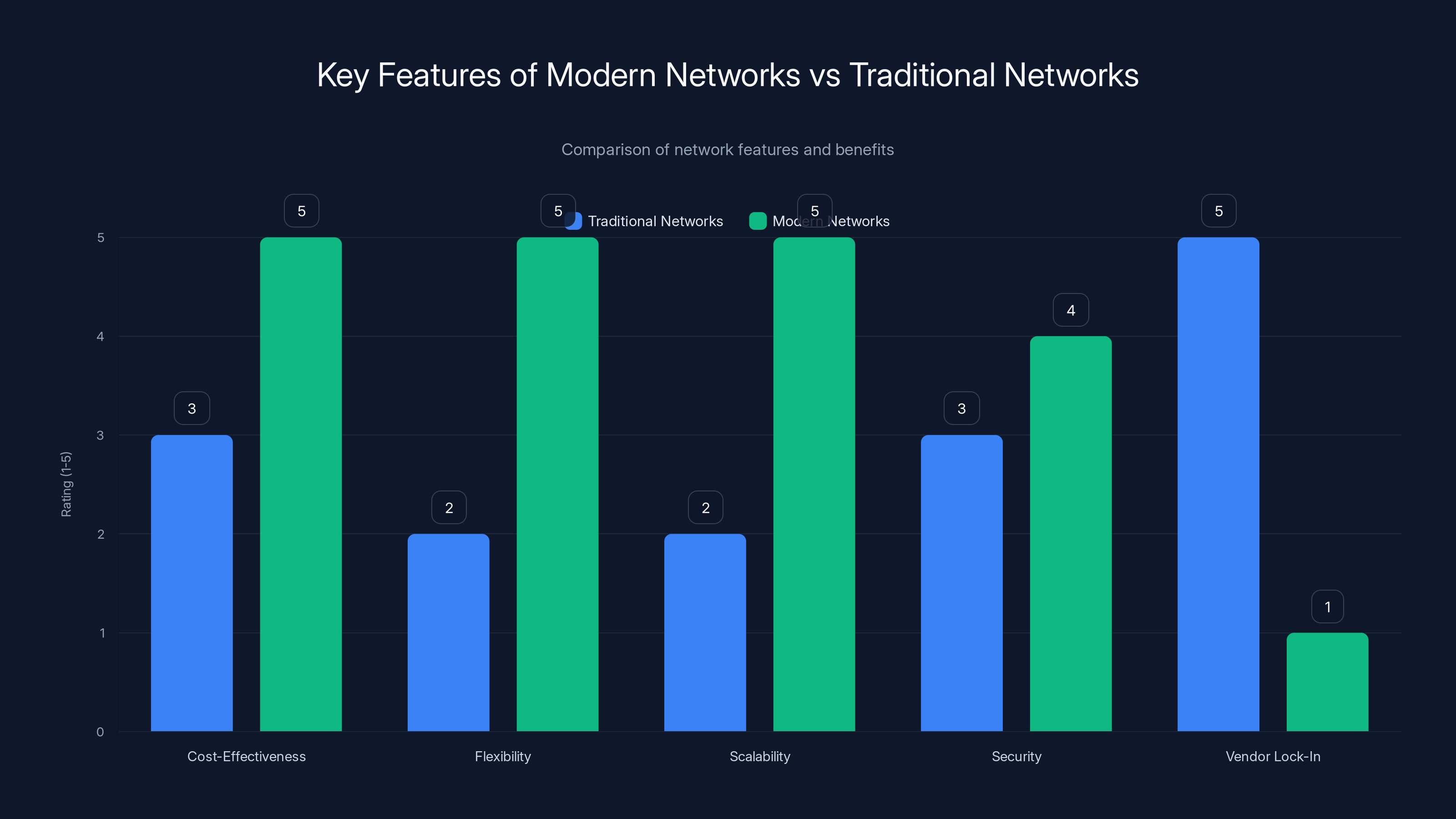
Modern networks excel in flexibility, scalability, and cost-effectiveness compared to traditional networks, which often suffer from vendor lock-in. (Estimated data)
How Legacy Networks Strangle AI Performance
AI applications are traffic machines. They move enormous amounts of data, constantly, in unpredictable patterns. An AI model training on terabytes of historical data. A real-time recommendation engine processing millions of user interactions per second. A predictive analytics system pulling from dozens of data sources simultaneously.
Legacy networks were built for different workloads. They were designed for steady, predictable flows of business data. Email traffic. File transfers. Occasional database queries. The architecture treats all traffic the same way. It pushes everything through the same pipes, using the same rules, at the same speeds.
When you force AI workloads through that infrastructure, several things go wrong.
Bandwidth Bottlenecks
First, you hit bandwidth limitations. A traditional enterprise network might have been sized for peak traffic of, say, 50 gigabits per second. An AI workload running model training, inference, and data movement can easily demand 100+ gigabits per second sustained, with spikes much higher.
When demand exceeds capacity, queuing happens. Data waits in buffers. That introduces latency. For an AI model doing inference, latency kills performance. If a customer-facing AI system takes 3 seconds instead of 300 milliseconds to respond, the application feels broken. Users abandon it. The whole AI investment yields nothing.
Data centers using older networking equipment face this constantly. They upgrade storage for AI workloads. They upgrade compute. But the network connecting it all? Still the same 10-gigabit connections from 2012.
Visibility Blind Spots
Second, you lose visibility. Legacy networks often lack real-time monitoring of traffic patterns. You can't see what's happening on your network at the speed it's happening.
Traditional network monitoring tools report statistics every few minutes. Fine for steady-state operations. Useless when you're trying to diagnose why an AI workload is performing poorly right now. By the time you see a report showing traffic bottlenecks, the problem has already caused business impact.
With AI, everything is too fast and too complex. The traffic patterns change minute by minute. Monitoring at minute-level granularity doesn't cut it anymore. You need real-time visibility, flow-level data, and intelligent analysis that can spot anomalies as they happen.
Security Fragmentation
Third, security becomes a nightmare. Most legacy networks grew organically over decades. A merger happened. New office opened. New application needed connectivity. A vendor was already entrenched. You add security controls here, adjust policies there, carve out exceptions for special projects.
Two decades later, you have a patchwork. Some traffic runs through a firewall. Some doesn't. Some applications are on an internal corporate network. Others are in public cloud. Some are at the edge. Network policies aren't consistent. You can't even say with certainty which devices connect to which systems.
This fragmentation is already a security problem in traditional environments. Add AI traffic, multiply it by orders of magnitude, and it becomes catastrophic. You can't enforce Zero Trust principles when your network is fragmented. You can't detect anomalies when you lack visibility. You can't respond to threats when systems aren't integrated.
The attack surface explodes. Attackers see AI traffic moving between systems and pounce. They recognize older network equipment that's reached end-of-life and has unpatched vulnerabilities. They find the gaps in your fragmented policies and slip through.
End-of-Life Equipment
Many enterprises are still running network equipment that's 10, 15, even 20 years old. Manufacturers stopped supporting these devices years ago. No security patches. No feature updates. No vendor support.
These devices often can't handle modern workloads. They can't do intelligent traffic prioritization. They can't integrate with cloud security services. They can't participate in modern security frameworks like Zero Trust.
Replacing ancient switches and routers isn't just about performance. It's about moving to platforms that understand modern threat models and can actually protect your infrastructure.
Slow Decision-Making
Finally, network limitations slow down decision-making. AI is valuable because it helps organizations make better decisions faster. A supply chain AI analyzes disruptions and recommends rerouting to avoid delays. A financial AI identifies market opportunities in real-time. A healthcare AI assists diagnosis with fresh clinical data.
But if your network can't move data fast enough, the AI can't see fresh information. The model trains on stale data. Insights arrive too late to act on them. The business advantage evaporates.
One enterprise deployed an AI system to predict equipment failures in manufacturing facilities. The model worked perfectly in testing. In production, the network couldn't deliver sensor data to the model fast enough. The model made predictions hours after problems had already occurred. Maintenance teams couldn't act on the advice. The company shut down the system and went back to manual processes.
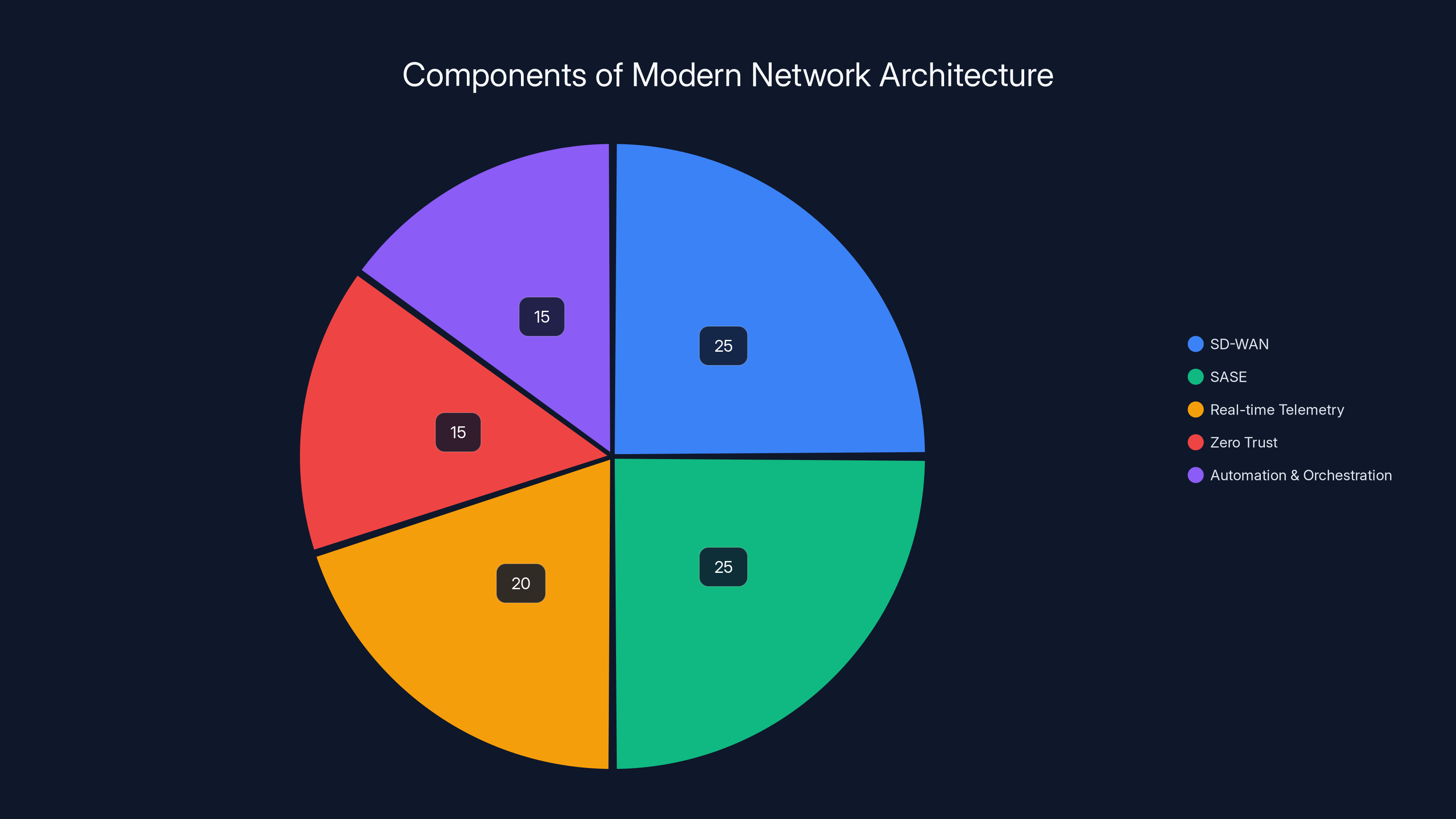
Modern network architectures are composed of multiple components, with SD-WAN and SASE each representing around 25% of the architecture, followed by real-time telemetry, Zero Trust, and automation. (Estimated data)
What Modern Networks Actually Do Differently
Modern network architecture solves these problems by rethinking how networks work from first principles.
Traditional networks were designed by vendors who wanted to lock you into their hardware. You bought expensive routers and switches, installed expensive management software, and paid them annually for support. The architecture was centralized: all traffic flows through data center equipment managed by the IT department.
This worked fine when applications ran only in the data center. Everyone connected through a corporate branch office. Traffic was predictable and manageable.
But that world is gone. Now applications run in multiple clouds, on edge devices, in customer locations, across hybrid environments. Employees work from anywhere. Traffic patterns are unpredictable. Security threats are constantly evolving.
Modern networks reject the old model. Instead of forcing everything through centralized hardware, they use software-defined networking. Instead of vendor lock-in, they use open standards. Instead of static policies, they use dynamic, intelligent controls.
Software-Defined WAN (SD-WAN)
SD-WAN (Software-Defined Wide Area Network) replaces expensive MPLS circuits with intelligent software that can use any connectivity available: broadband, LTE, dedicated circuits, cloud backbone services.
The key innovation: the software makes intelligent decisions about which traffic uses which path. A video conference that's tolerant of some latency might go over cheap broadband. A real-time AI inference that requires low latency goes over dedicated connections. A batch data transfer that's not time-sensitive might wait for off-peak hours.
This isn't just more flexible. It's far more cost-effective. You replace expensive MPLS circuits with cheaper, more abundant broadband. You add backup paths automatically. You can dynamically prioritize traffic based on business needs.
For AI workloads specifically, SD-WAN enables network paths optimized for data movement. Machine learning training often involves shuffling terabytes of data between compute nodes. SD-WAN can dedicate high-capacity paths to this traffic, separate from user traffic, keeping both performant.
SASE Architecture
SASE (Secure Access Service Edge) combines network services and security services into a cloud-delivered platform. Instead of separate firewalls, VPNs, and security tools, you get an integrated service that handles everything.
This matters enormously for AI security. With SASE, every connection is evaluated in real-time against security policies. Is this device authorized? Does it have current patches? Are the credentials legitimate? Is the traffic pattern normal? The system can block, log, or allow based on dozens of factors.
For AI specifically, SASE enables consistent security policy enforcement regardless of where the AI workload runs. An AI model processing data in the public cloud follows the same security rules as one running in your data center. An edge AI system processing sensor data follows the same rules. No exceptions, no gaps.
Real-Time Visibility and Telemetry
Modern networks provide real-time visibility into every flow. Not reports generated every few minutes. Live data, constantly updated, showing exactly what's happening.
You see which applications are consuming bandwidth. Which ones are experiencing latency. Which ones are generating unusual traffic patterns that might indicate compromise. All in real-time.
For AI operations, this is essential. When you deploy a new model, real-time visibility lets you immediately see how it's affecting network load. You can spot performance bottlenecks before they impact the business. You can detect if the model is generating unexpected traffic patterns that might indicate a misconfiguration or security issue.
Intelligent Traffic Management
Instead of treating all traffic equally, modern networks intelligently route traffic based on its characteristics. Real-time traffic needing low latency takes one path. Batch traffic that's latency-tolerant takes another. This creates better performance for everything.
For AI, this means different tiers of service for different use cases. High-priority inference gets premium service. Model training gets dedicated bandwidth. Non-time-sensitive data movement gets best-effort service when bandwidth is available.
Automation and Integration
Modern networks automate configuration and policy enforcement. When a new application needs to be deployed, network policies automatically adjust. When a new cloud environment is added, connectivity automatically adjusts. When threat patterns change, security policies automatically tighten.
This reduces manual configuration work (which is error-prone) and ensures consistency (which is better for security).
Why AI Success Depends on Network Modernization
The relationship between AI and network modernization isn't optional. It's fundamental.
AI applications fundamentally require things legacy networks can't provide. Let's look at each.
Low-Latency Communication
Many AI applications are time-sensitive. A recommendation engine that takes 5 seconds to respond feels broken. A fraud detection system that processes a transaction 10 seconds after it occurred can't prevent the fraud. An autonomous vehicle that processes sensor data with 100-millisecond latency can't safely react to obstacles.
Legacy networks introduce latency in every layer. Slow routing decisions. Oversubscribed links causing queuing. Inefficient traffic prioritization. For time-sensitive AI, this is crippling.
Modern networks eliminate these bottlenecks. SD-WAN routes traffic optimally, not through legacy paths. Real-time prioritization ensures critical traffic gets immediate attention. Direct cloud connectivity removes hops. Latency measured in milliseconds becomes achievable.
High-Bandwidth Movement
AI models and datasets are massive. Training a large language model might require moving petabytes of data through your network during preparation. Running inference at scale means constantly moving input data to models and predictions back to users.
This requires bandwidth that legacy networks simply don't have. A network designed for 100 gigabits per second can't handle 1 terabit per second of AI traffic. You need modern infrastructure with redundancy, load balancing, and proper capacity planning.
Multi-Environment Consistency
AI workloads run everywhere now: on-premises data centers, public clouds (AWS, Azure, Google Cloud), private clouds, edge devices. This creates a nightmare for legacy networks, which were designed for a single data center model.
How do you apply consistent security policies when AI runs in five different environments? How do you monitor and troubleshoot when data paths are completely different for each location? How do you maintain performance consistency?
Modern networks handle this through cloud-delivered services that follow the workload wherever it goes. SASE security policies apply everywhere. SD-WAN connectivity works across all environments. Management is unified and consistent.
Security at AI Scale
AI creates new security challenges. Models can be poisoned with bad data. Inference outputs can be manipulated. Models themselves can be stolen. Network traffic related to AI is particularly valuable to attackers: it reveals what your AI systems are doing, what data they're processing, who's using them.
Legacy network security (perimeter-based firewalls) offers little protection. Modern networks using Zero Trust principles work better: verify every connection, assume breach, monitor everything, respond automatically.
For AI specifically, modern networks can enforce policies like:
- Only authorized data can flow to model training pipelines
- Only approved applications can access trained models
- Unusual access patterns to AI systems are blocked automatically
- All model data movement is encrypted and logged
Cost Optimization
AI workloads are expensive to run. Storage, compute, data movement all add up. Network modernization reduces these costs.
SD-WAN reduces connectivity costs by eliminating expensive MPLS circuits. Intelligent traffic management reduces cloud egress costs (data movement out of cloud providers is expensive). Better visibility identifies wasteful workloads. Automation reduces operational overhead.
One enterprise moving to SD-WAN reduced network operating costs by 35% while simultaneously improving application performance by 28%. That's not a trade-off. That's what modern architecture delivers.
Future-Proofing
AI technology evolves constantly. New models, new frameworks, new deployment patterns. Your network infrastructure needs to be flexible enough to adapt.
Legacy networks are rigid. They're built for specific hardware, specific vendor software, specific deployment models. When technology changes, you often have to replace the entire network. Expensive, risky, time-consuming.
Modern networks are flexible. They run on standard servers instead of proprietary hardware. They use open standards instead of vendor-specific protocols. They're cloud-native, so they evolve alongside cloud technologies. When AI deployment models change, your network adapts without major disruption.
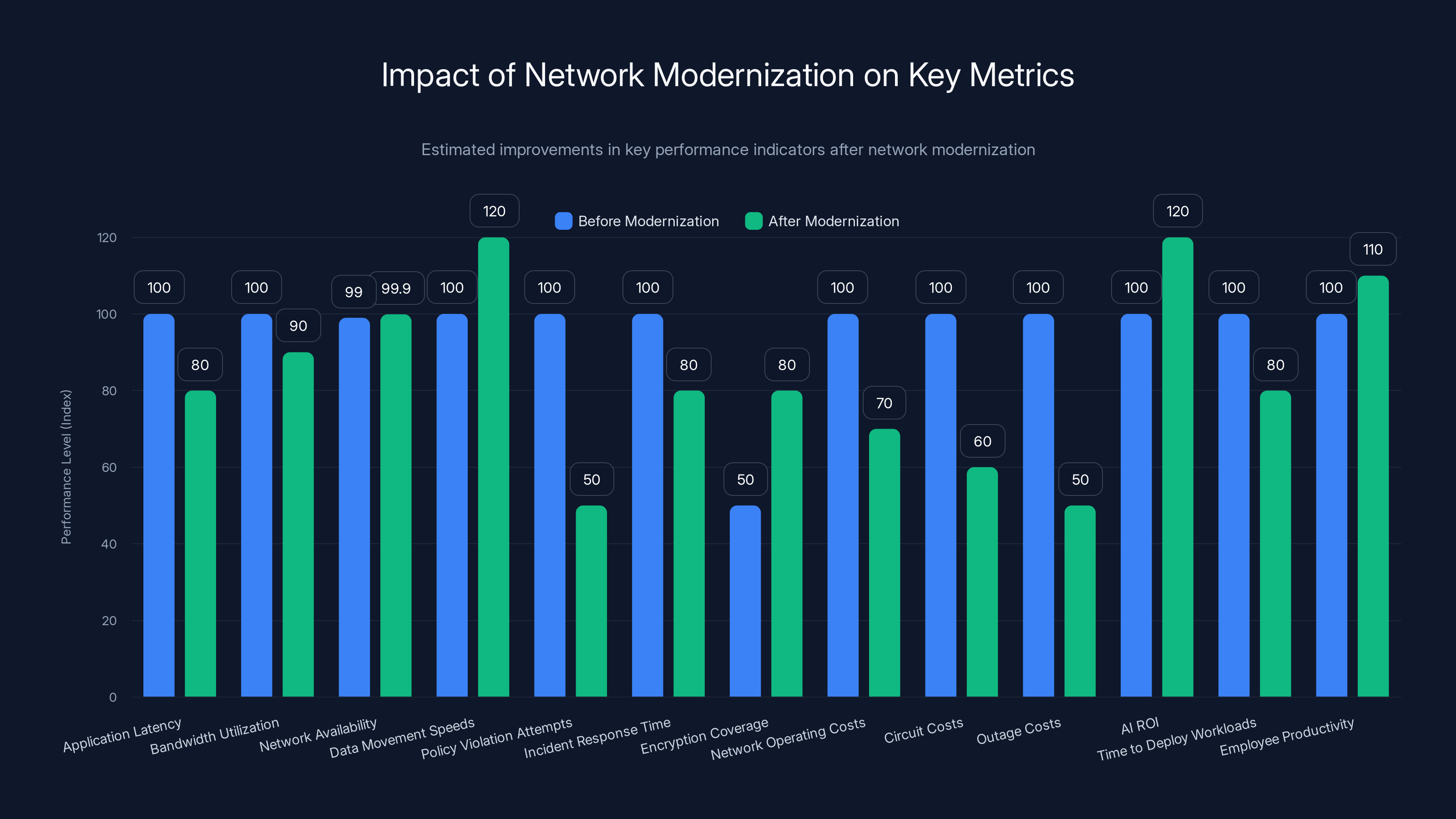
Network modernization is projected to improve application latency, bandwidth utilization, network availability, and other key metrics significantly, leading to better performance and cost efficiency. (Estimated data)
Specific Network Modernization Components for AI
Network modernization isn't a single product. It's a collection of components, each solving a specific problem, working together to create modern infrastructure.
SD-WAN Implementation
SD-WAN is often the first step because it delivers immediate ROI. You replace expensive MPLS circuits with cheaper connectivity and intelligent software. You can implement it without touching your other infrastructure.
For AI specifically, SD-WAN enables:
- Dynamic bandwidth allocation: as AI workloads demand more bandwidth, the system automatically uses available capacity
- Path optimization: AI traffic takes the fastest available path, not the default route
- Multi-path redundancy: if one connection fails, traffic automatically flows over another
- Cloud acceleration: direct paths to cloud providers reduce latency and improve performance
Implementation typically takes 3-6 months for a medium-sized organization. Start with a pilot location, measure results, expand from there.
Cloud-Delivered Security (SASE)
SASE provides firewalling, VPN, threat prevention, and encryption as cloud services instead of on-premises appliances. This is powerful for several reasons.
First, security policies are enforced in the cloud, not at the edge of your network. This means policies apply consistently to all users and devices, regardless of location. A policy that says "only authorized accounts can access AI systems" applies equally to office workers, remote workers, and field workers.
Second, cloud-delivered security scales automatically. You don't have to worry about adding more firewall capacity as traffic grows. The cloud service scales behind the scenes.
Third, threat intelligence is shared across millions of customers. When a new malware variant is detected targeting one customer, the security platform blocks it for all customers. You benefit from collective intelligence.
For AI, SASE enables security policy enforcement at the application level. You can say "only models trained in this data center can be accessed from external networks" or "inference access is restricted to authenticated applications." These policies are enforced in real-time without requiring network-level reconfiguration.
Network Segmentation and Zero Trust
Zero Trust means verify everything, assume breach, and apply least-privilege access. Instead of trusting everything inside your network perimeter, you verify every connection and grant only necessary permissions.
Modern networks implement this through segmentation. AI systems are in one segment. Data sources are in another. Production applications are in another. Each segment is isolated, and traffic between segments is controlled by policies.
For example, a data science team might have access to training data and development models, but not production models. An automated ML pipeline might have access to training infrastructure but not to human user systems. Production applications might have access to inference APIs but not to training data.
This prevents lateral movement if one system is compromised. If an attacker breaks into the data segment, they can't automatically access the model training segment.
Real-Time Monitoring and Observability
Modern networks provide continuous visibility into traffic, application performance, and security events. This is critical for AI operations.
You need to see:
- Which AI workloads are consuming most bandwidth
- What latency users experience when accessing AI applications
- Whether unusual data movement patterns are occurring
- If security policies are being violated
- Where bottlenecks exist in your infrastructure
Tools like network telemetry, flow analytics, and behavioral analytics provide this information in real-time. You can spot problems instantly instead of discovering them through complaints or incident reports.
Automation and Orchestration
Modern networks are automated. When you deploy a new AI workload, you provision the network connectivity through code, not through manual configuration. When you add a new cloud environment, connectivity is provisioned automatically.
This dramatically reduces the time to deploy AI systems. Instead of requesting network changes through tickets that take weeks to fulfill, provisioning happens in minutes. It also reduces errors: automated provisioning follows templates and best practices, unlike manual configuration which is often inconsistent.
The Business Impact: Real Outcomes from Network Modernization
Network modernization isn't just about technology. It's about business results.
Consider a financial services company that modernized its network to support AI fraud detection. Before modernization: the network couldn't move fraud detection data fast enough, causing delays in detection. False positive rates were high because the model wasn't processing fresh data. Manual review of suspicious transactions was a significant operational cost.
After modernization: fraud detection latency dropped from 8 hours to 2 minutes. The model processes fresh data continuously. False positive rates dropped by 34%. Manual review volume fell by 52%. The company prevented
Or consider a manufacturer deploying predictive maintenance AI. Legacy network meant connecting edge sensors directly to on-premises systems, which was inefficient. After SD-WAN deployment: the company created a hybrid edge-cloud architecture. Sensors send raw data to local edge processing (low latency, low bandwidth). The edge system performs local analysis and sends only high-value insights to the cloud for training the global model.
Result: equipment downtime decreased 34%, maintenance labor costs fell 28%, and the company identified failure patterns earlier, reducing catastrophic failures by 67%.
These aren't theoretical numbers. They're real outcomes that organizations achieve when they align infrastructure with their AI ambitions.
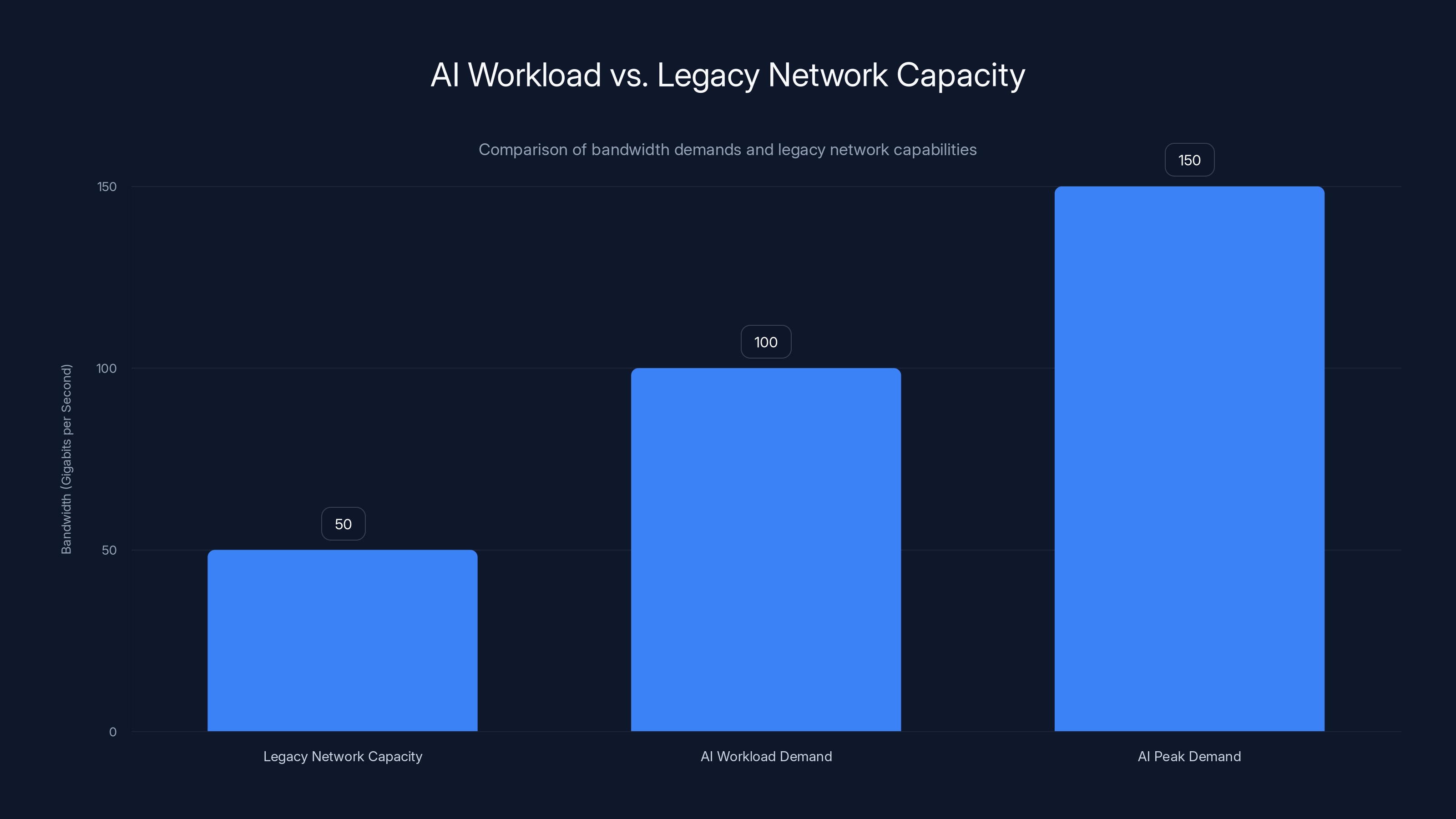
AI workloads demand significantly more bandwidth than legacy networks can provide, leading to bottlenecks and latency issues. Estimated data based on typical AI and legacy network capacities.
Quantum Computing: The Next Infrastructure Crisis
Just as enterprises are grappling with AI infrastructure demands, another transformation is looming: quantum computing.
Unless you've been living under a rock, you know quantum computers exist. Companies like IBM, Google, and others have developed quantum processors with dozens or hundreds of qubits. These machines are still relatively primitive. But they're advancing rapidly.
Here's what matters for your infrastructure: quantum computers can break current encryption.
Today, your organization protects sensitive data using encryption that relies on the mathematical difficulty of factoring large numbers. A classical computer trying to factor a 2048-bit number (which secures most internet traffic) would take millennia.
A sufficiently powerful quantum computer could do it in hours.
Experts estimate that quantum computers capable of breaking 2048-bit encryption could exist within 5-10 years. Some researchers think it could happen sooner. Others think it might take longer. The uncertainty is part of the problem: you don't know exactly when the threat arrives, but you know it's coming.
Which raises a terrifying question: what about data encrypted today that hackers steal and store?
The "Harvest Now, Decrypt Later" Problem
Attackers already operate on this timeline. They're stealing encrypted data right now, storing it in massive databases, planning to decrypt it when quantum computers become available.
This isn't paranoid speculation. Reports from major cybersecurity firms document sophisticated threat actors running sophisticated collection operations specifically targeting valuable encrypted data.
Consider the implications. Medical records encrypted today with current standards could be decrypted and exposed in 5 years. Financial data. Trade secrets. Personal information. Anything encrypted today that a sophisticated attacker valued enough to steal is potentially vulnerable.
For organizations in sensitive industries (healthcare, finance, government, defense), this is a critical concern. Data encrypted today might be valuable and sensitive for 10+ years. If an attacker can decrypt it in 5-10 years, the encryption was effectively useless.
Post-Quantum Cryptography
Cryptographers are developing new encryption algorithms designed to resist quantum computers. The National Institute of Standards and Technology (NIST) spent years evaluating candidates and has approved the first set of post-quantum cryptographic algorithms.
The challenge: migrating to post-quantum cryptography is complex. It's not just changing an encryption setting. It requires:
Replacing cryptographic libraries in applications and systems. Legacy applications often have encryption baked in. Updating them requires code changes, testing, and deployment. For organizations with thousands of applications, this is massive work.
Updating cryptographic infrastructure. Certificate authorities, key management systems, and other infrastructure needs to support new algorithms.
Phased rollout. You can't flip a switch and change everything at once. You have to migrate gradually, managing compatibility between old and new systems during the transition.
Key rotation. Even if you implement post-quantum encryption, you need to rotate old encryption keys and re-encrypt data encrypted with vulnerable algorithms.
Why This Relates to Network Modernization
Here's the connection: modern network infrastructure is foundation for post-quantum security migration.
First, modern networks provide the visibility and control needed to inventory cryptographic systems. You need to know everywhere in your organization where cryptography is used. Modern networks with real-time telemetry make this visible.
Second, modern networks support automated policy enforcement. When you implement post-quantum cryptography, policies automatically enforce use of approved algorithms. Legacy networks don't have this capability.
Third, modern networks support segmentation and Zero Trust, which reduces your attack surface against quantum-capable attackers. Even if someone eventually breaks your encryption, they won't be able to access everything because systems are segmented and policy-controlled.
Fourth, cloud-delivered security services (SASE) can be updated by vendors to enforce post-quantum cryptography without requiring changes to your on-premises systems. You get the benefit of new security without having to upgrade your hardware.

Quantum Readiness: What Organizations Need to Do
Quantum readiness doesn't mean implementing post-quantum cryptography today. It means preparing your organization to make that transition when the time comes.
Forming Leadership Task Forces
Quantum readiness requires coordination across teams: IT security, application development, network operations, compliance, business units. Creating a leadership task force ensures this work gets prioritized and funded.
The task force should include executives who can drive decision-making, technical leaders who understand the complexity, and compliance/risk leaders who understand regulatory implications.
Your task force's first job: develop a quantum readiness timeline. When will your organization start migrating? Which systems are highest priority? What resources are needed? What's the budget?
Most experts recommend starting the process within the next 2-3 years. Organizations that wait until quantum threats are imminent will be scrambling, making poor decisions, potentially exposing sensitive data.
Inventorying Cryptographic Systems
Before you can migrate, you need to know what you're migrating. Where in your organization is cryptography used?
Obviously, you have encryption for data in transit (HTTPS, VPNs, encrypted messaging). But you also have:
Data at rest encryption on storage systems. Digital signatures on documents and code. Certificate-based authentication. Cryptographic keys protecting other keys. Encryption in applications you've developed. Encryption in third-party software.
The inventory process is tedious but essential. You need to know:
What cryptographic algorithm is used (RSA, ECDSA, etc.). How critical is the system (does it protect sensitive data that needs to remain confidential long-term). How long before the system can be retired or updated. What dependencies exist (other systems relying on this cryptography).
For an enterprise with thousands of systems, this could take months. Plan accordingly.
Prioritizing High-Value Systems
You won't migrate everything at once. Prioritize based on:
Data sensitivity. Systems protecting data that needs to remain confidential for 10+ years are highest priority.
Cryptographic algorithm. Systems using RSA and ECDSA are highest priority (these are vulnerable to quantum computers). Symmetric encryption (like AES) is not vulnerable, so systems using only symmetric encryption can wait.
Update difficulty. Systems that are easy to update should be done first because you get quick wins and learn from the process.
Vendor support. Has the vendor of your software committed to post-quantum cryptography support? If not, you might need to replace the software.
Adopting Post-Quantum Cryptography Standards
NIST has approved initial post-quantum cryptographic algorithms. Organizations should plan to use NIST-approved algorithms, not experimental ones developed by researchers.
The approved algorithms are:
ML-KEM (formerly Kyber), for key encapsulation. This replaces RSA and ECDH for key exchange.
ML-DSA (formerly Dilithium), for digital signatures. This replaces RSA and ECDSA for signing.
SLH-DSA (formerly SPHINCS+), an alternative for digital signatures in cases where ML-DSA doesn't fit.
As an organization, you should:
Ensure your cryptographic libraries support these algorithms. Most major cryptography libraries (Open SSL, Java libraries, etc.) are adding support.
Require vendors to support these algorithms in their products. If a vendor can't commit to post-quantum cryptography support, consider replacing them.
Test migration paths. Before rolling out post-quantum cryptography to production, test the migration process. What breaks? What needs to be fixed?
Plan key rotation. When you migrate to post-quantum cryptography, old keys need to be rotated out of use. This can be complex if you have long-lived keys.
Hybrid Approaches and Transition Strategies
You don't have to go all-in on post-quantum cryptography immediately. Hybrid approaches let you gain security benefits while managing complexity.
Hybrid encryption uses both classical and post-quantum algorithms. You encrypt data with both RSA and post-quantum algorithms. To decrypt, an attacker would need to break both. This provides security against both classical and quantum computers.
Hybrid approaches are useful during transition periods. You can deploy hybrid encryption in new systems while keeping old systems unchanged. Over time, you migrate entirely to post-quantum cryptography.
For many organizations, a reasonable timeline looks like:
Years 1-2: Inventory systems, form task force, select NIST-approved algorithms, begin pilot migration on low-risk systems.
Years 2-4: Roll out hybrid encryption to systems protecting sensitive long-term data. Begin full migration of critical systems.
Years 4-6: Complete migration of most systems. Maintain legacy systems with classical encryption only if they don't process sensitive long-term data.
Years 6+: Decommission old cryptographic systems. Monitor for quantum computing breakthroughs.

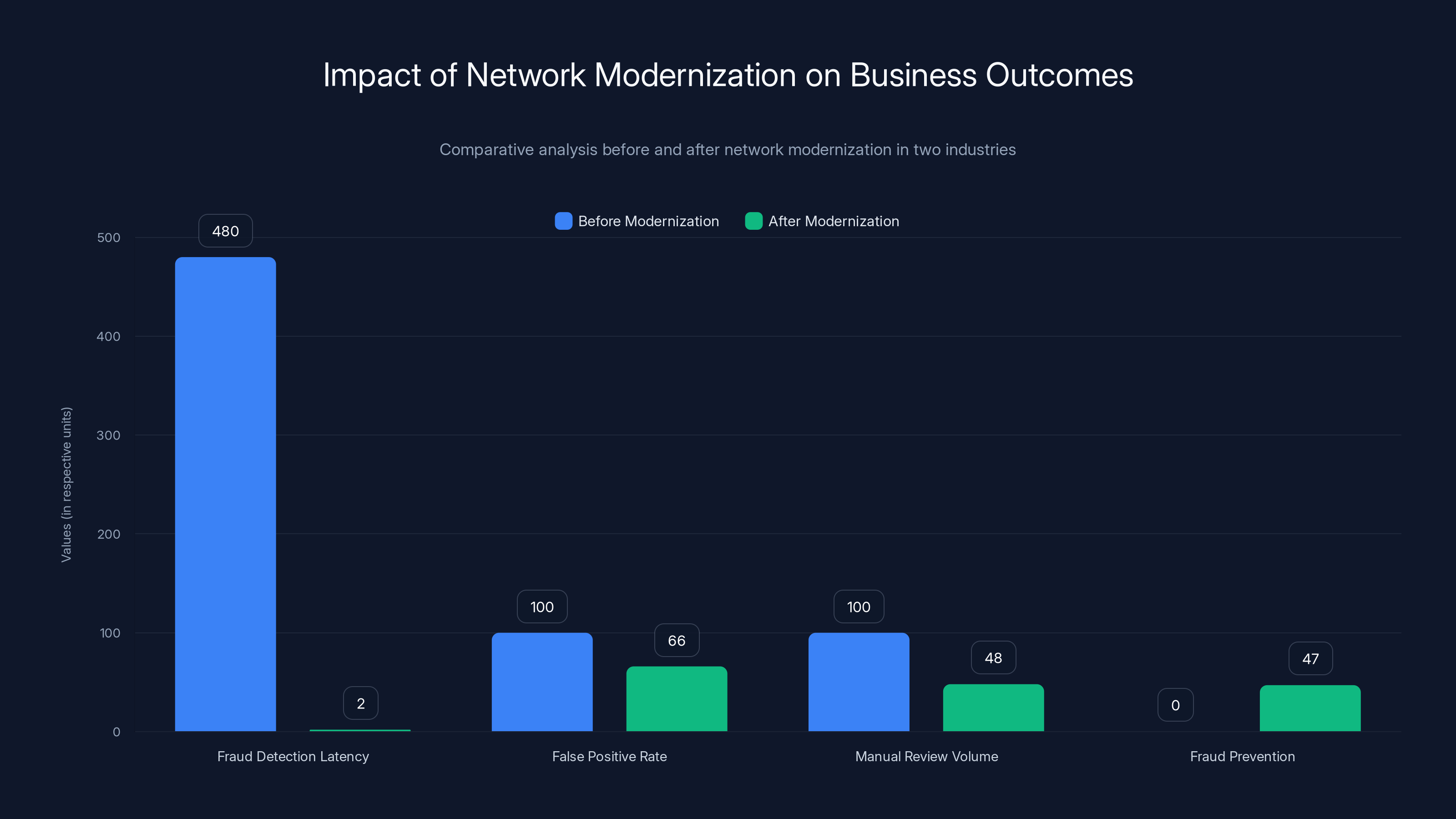
Network modernization significantly reduced fraud detection latency from 8 hours to 2 minutes, decreased false positive rates by 34%, and reduced manual review volume by 52%, resulting in $47 million fraud prevention. Estimated data.
Building a Modern Network Architecture: Step-by-Step
So how do you actually modernize your network? Here's a practical approach.
Phase 1: Assessment (Weeks 1-4)
Start by understanding your current state. What does your network look like today?
Map your current infrastructure: Where are your data centers? Which clouds do you use? Where are branch offices? What connectivity exists between these locations? What equipment is in use? When was it last updated?
Identify constraints and bottlenecks: Which links are oversubscribed? Where is latency highest? Where is reliability worst? Where do you lack visibility?
Document current security architecture: What firewalls do you have? How are policies enforced? Where are blind spots? How do you currently handle remote access?
Assess AI readiness: What AI workloads do you run today? What are you planning to deploy? What are the network requirements? Where will they run?
Inventory applications and dependencies: Which applications are critical? What are their network requirements? What dependencies exist?
This assessment should produce a clear picture of your current state and your target state.
Phase 2: Pilot Deployment (Months 2-5)
Don't try to transform your entire network at once. Start with a pilot program.
Select a pilot location with representative network needs. Maybe it's a branch office that uses multiple cloud providers. Or a data center running both traditional and AI workloads. The key: it should be representative but not your most critical infrastructure.
For the pilot, deploy:
SD-WAN at the location. Replace MPLS connectivity with SD-WAN, test the results.
Cloud-delivered security (SASE). Implement security through cloud services instead of on-premises appliances.
Real-time visibility. Deploy telemetry and monitoring tools.
Network segmentation. Implement Zero Trust principles at the location.
Run the pilot for 2-3 months, measuring results. How much did connectivity costs drop? How much did application performance improve? What issues came up? What needs to be fixed?
Use pilot results to refine your approach before rolling out to the broader organization.
Phase 3: Gradual Rollout (Months 5-18)
Once you've proven the approach with a pilot, gradually roll out to the broader organization.
Rollout is typically staged: maybe you move 20% of locations in month 6, another 30% in month 10, etc. Gradual rollout lets you:
Catch problems before they affect the entire organization. If something breaks, it affects a small population and you can fix it quickly.
Learn from each deployment. Each location teaches you something that informs the next location.
Manage change management. Gradual rollout gives teams time to adapt to new processes and tools.
During rollout, establish governance: how are changes made? Who approves them? How are incidents handled? What's the escalation path?
Phase 4: Optimization (Months 18-24+)
Once you've deployed modern infrastructure, optimize it. This is ongoing work.
Continuously monitor performance and security. Look for anomalies. Are there traffic patterns you don't understand? Are policies being violated?
Optimize policies. Are there policies that are too restrictive? Too permissive? Can you find a better balance?
Optimize costs. Are there expensive services you can eliminate? Traffic you can reduce? Negotiate better rates with vendors?
Plan for quantum readiness. Start implementing post-quantum cryptography in new deployments.
Stay current with technology. Network technology evolves. New capabilities emerge. Plan regular technology updates.

Measuring Success: KPIs for Network Modernization
How do you know if your network modernization is working? Track these key performance indicators.
Performance Metrics
Application latency: Measure latency for critical applications before and after modernization. Track percentiles (average, P50, P95, P99) because outliers matter for user experience.
Bandwidth utilization: Modern networks handle more efficiently. You should see the same or better performance with the same or less bandwidth.
Network availability: Track uptime and incident duration. Modern networks should reduce both.
Data movement speeds: For AI specifically, measure how fast data moves between systems. Model training should be faster. Inference latency should be lower.
Security Metrics
Policy violation attempts: Modern networks catch policy violations that legacy networks missed. Track the number of blocked attempts.
Incident response time: How fast can you detect and respond to security incidents? This should improve with real-time visibility.
Encryption coverage: What percentage of traffic is encrypted? This should increase with modern security infrastructure.
Cost Metrics
Network operating costs: Track total cost of ownership (hardware, software, support, labor). Modern networks should cost 25-40% less.
Circuit costs: If you're using SD-WAN, track cost per megabit of bandwidth. This should decrease significantly.
Outage costs: Track cost of network downtime and operational inefficiency caused by outages. Modern networks should reduce this substantially.
Business Metrics
AI ROI: Track the business impact of AI workloads. Modern networks enable better AI performance and lower costs, improving ROI.
Time to deploy new workloads: Modern networks with automation reduce deployment time. Track the time from request to live AI workload.
Employee productivity: Network improvements should enable faster work. Track productivity metrics relevant to your business.
AI-Specific Metrics
Model training time: Measure how long it takes to train models. Better network infrastructure should reduce training time.
Inference latency: Measure latency for model inference. Modern networks should reduce latency.
Model accuracy: Sometimes network latency or data movement issues affect model accuracy. Track whether modern infrastructure improves model quality.
Data pipeline reliability: Track the percentage of time data pipelines complete successfully. Modern infrastructure should improve reliability.
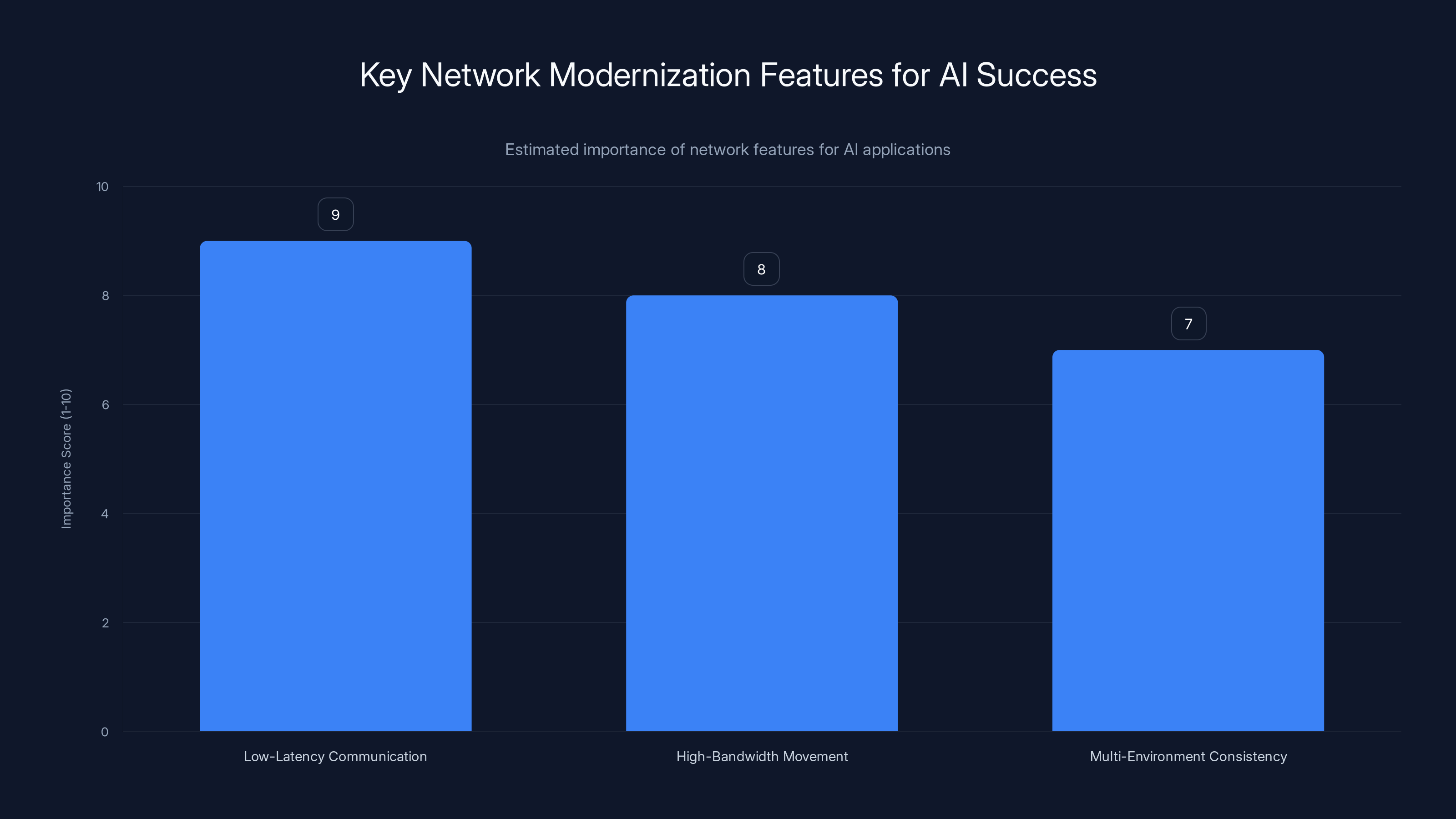
Low-latency communication is the most critical network feature for AI success, followed by high-bandwidth movement and multi-environment consistency. Estimated data.
Common Pitfalls and How to Avoid Them
Network modernization is complex. Here's what typically goes wrong and how to avoid it.
Pitfall 1: Underestimating Complexity
Many organizations think network modernization is straightforward. "We'll just install new equipment and everything will be faster."
Reality: Network modernization affects everything. Applications might need configuration changes. Security policies need to be rewritten. Operational processes need to change. Staff needs training.
Avoidance: Plan for comprehensive change, not just infrastructure replacement. Budget time for testing, training, and process improvement.
Pitfall 2: Not Starting with Assessment
Some organizations jump straight to purchasing new equipment without understanding what they need.
Reality: Different organizations have different needs. A financial services company has very different network requirements than a manufacturing company. Generic solutions often miss the mark.
Avoidance: Start with assessment. Understand your current state, your constraints, your requirements, your bottlenecks. Let assessment inform your decisions.
Pitfall 3: Insufficient Testing
Organizations sometimes test modernized networks in isolation from real workloads.
Reality: The network only works well if it works well with your actual applications and workloads. Testing in a lab environment might not catch problems that appear under real-world conditions.
Avoidance: Test with real workloads. Run your actual AI models through the network. Run your actual applications. See how they behave.
Pitfall 4: Ignoring Operational Readiness
Some organizations deploy new network infrastructure without training operations teams on how to use and manage it.
Reality: New infrastructure requires new skills. If your operations team doesn't understand SD-WAN or SASE or the new monitoring tools, they can't operate them effectively.
Avoidance: Plan training before deployment. Hire or develop expertise. Consider getting professional services help to bridge the skills gap.
Pitfall 5: Not Addressing Security Comprehensively
Some organizations focus on performance improvement and treat security as an afterthought.
Reality: Modern networks should improve security, not just performance. Security has to be built in from the start, not added on after.
Avoidance: Include security in every decision. Implement Zero Trust principles from the beginning. Plan security policies alongside infrastructure decisions.
Pitfall 6: Vendor Lock-in
Organizations sometimes choose proprietary solutions that make switching difficult or expensive.
Reality: Over time, your needs might change. You might want to switch vendors or integrate with tools from other vendors. Proprietary solutions make this difficult.
Avoidance: Prefer open standards. When evaluating vendors, ask about standards compliance and interoperability. Ensure you can export data and move to other platforms if needed.
The Future: Where Network Architecture Is Heading
Network modernization isn't a destination. It's a journey. Here's where the industry is heading.
AI-Optimized Networking
Networks are increasingly designed specifically for AI workloads. We'll see:
Networks that automatically detect AI traffic and prioritize it appropriately. Different AI workloads have different requirements (training, inference, batch processing). Intelligent networks will recognize these patterns and apply appropriate policies.
Direct connections between compute, storage, and AI infrastructure. Today, data often takes indirect paths. Future networks will have dedicated high-bandwidth paths for AI data movement, reducing latency and improving efficiency.
Predictive network management. AI models will predict network problems before they occur and automatically adjust to prevent them. Instead of reacting to network congestion, the network will predict it and adjust routing in advance.
Intent-Based Networking
Instead of configuring networks with low-level rules, you'll specify intent. You'll say "I want to ensure this AI training job completes in 4 hours" and the network will automatically configure itself to meet that requirement.
This requires networks that can understand business requirements and translate them to technical configuration. It's emerging now but will become standard over the next few years.
Quantum-Safe Networking
Post-quantum cryptography will become standard in network protocols. VPNs, HTTPS, authentication—all will use quantum-safe encryption. This won't happen overnight, but it's coming.
Organizations that invest in modern network architecture now will find the transition easier. Legacy networks will struggle to add quantum-safe encryption without major overhauls.
Edge Intelligence
More processing and decision-making will happen at the edge. Instead of sending all data to central data centers or cloud, processing happens locally. The network will support this edge-centric architecture.
This is particularly important for AI: edge AI systems (processing sensor data locally, making quick decisions) will reduce latency and bandwidth requirements.
Zero Trust Maturity
Zero Trust principles are still relatively new. Over the next few years, organizations will become more mature in implementation. This means:
Every device is verified before accessing any resource. Not just when connecting to the network, but continuously, for every action.
Encryption becomes default everywhere, not just for sensitive traffic.
Visibility and monitoring become ubiquitous, catching threats instantly rather than hours later.

Getting Started: Your Next Steps
If you've been thinking about network modernization, here's how to start.
For CIOs and Infrastructure Leaders
First, assess your current state. Work with your team to document existing infrastructure, identify bottlenecks, and understand your constraints. This assessment will inform every subsequent decision.
Second, align on AI strategy. What AI workloads is your organization deploying? What are the network requirements? What performance improvements would have meaningful business impact?
Third, develop a modernization roadmap. This should include phases, timelines, resource requirements, and expected ROI. Use your assessment and AI strategy to inform the roadmap.
Fourth, secure funding and executive sponsorship. Network modernization requires budget and organizational commitment. Get executive alignment before you start.
Fifth, form a team. This isn't a solo project. You'll need vendor management, technical architecture, operations, security, and application teams all involved.
For Practitioners (Network Engineers, Security Architects, etc.)
Start learning about modern network architectures. Read about SD-WAN, SASE, Zero Trust. Experiment with these technologies in a lab environment.
Explore how modern networks support AI. Run some AI workloads through the network. See what performance you can achieve.
Think about how quantum-safe cryptography will affect your networks. What do you need to do differently?
Start conversations with vendors. Understand what products and services are available. Evaluate which ones fit your organization's needs.
For Security Leaders
Evaluate your current security posture. How effective is your perimeter security? How visible is your network? How consistent are your policies?
Develop a Zero Trust strategy. What would it take to implement Zero Trust principles in your organization? What are the biggest challenges?
Start quantum readiness planning. Inventory your cryptographic systems. Identify high-risk systems that need post-quantum cryptography. Develop a migration timeline.
Evaluate SASE solutions. Understand how cloud-delivered security services could improve your security posture.

FAQ
What is network modernization?
Network modernization is the process of upgrading from legacy network architectures to modern, cloud-native architectures. This includes replacing proprietary equipment with software-defined solutions, implementing cloud-delivered security, adding real-time visibility and monitoring, and automating network operations. Modern networks provide better performance, stronger security, lower costs, and greater flexibility compared to legacy networks built 10-20 years ago.
How does network modernization enable AI success?
AI workloads require low-latency, high-bandwidth, consistent performance across multiple environments. Legacy networks were designed for steady, predictable traffic and can't meet these requirements. Modern networks provide the speed, scale, visibility, and security that AI applications need to deliver value. Additionally, modern architectures support consistent security policies regardless of where workloads run (on-premises, cloud, or edge), which is essential for secure AI deployment across hybrid environments.
What are the main components of a modern network architecture?
A modern network typically includes SD-WAN (Software-Defined WAN) for intelligent connectivity, SASE (Secure Access Service Edge) for cloud-delivered security, real-time network telemetry and monitoring for visibility, Zero Trust architecture for consistent security policies, and automation and orchestration for reducing manual configuration. These components work together to create networks that are faster, more secure, more flexible, and more cost-effective than legacy architectures.
How much does network modernization cost?
Costs vary based on organization size, current infrastructure, and scope of modernization. A medium-sized organization might spend $2-5 million on network modernization over 2-3 years. However, most organizations recover this investment within 1-2 years through reduced connectivity costs, reduced outages, improved productivity, and better support for AI workloads. Long-term, modern networks typically cost 25-40% less to operate annually compared to legacy networks.
How long does network modernization take?
A comprehensive network modernization program for a medium to large organization typically takes 18-36 months from planning to completion. This includes assessment (1-2 months), pilot deployment (3-4 months), gradual rollout to the organization (8-12 months), and optimization (ongoing). Smaller organizations might complete modernization in 12-18 months. The key is phasing implementation gradually rather than trying to transform everything at once.
What is quantum computing, and why does it matter for networks?
Quantum computers use quantum mechanics to perform calculations fundamentally different from classical computers. They could break encryption standards that protect most modern data. Experts estimate quantum computers capable of breaking current encryption could exist within 5-10 years. This matters for networks because encryption protects all sensitive data moving across networks. Organizations need to begin planning for post-quantum cryptography migration now, before quantum computers arrive, to protect data that needs to remain confidential for years.
What is post-quantum cryptography?
Post-quantum cryptography refers to encryption algorithms designed to resist attacks from quantum computers. The National Institute of Standards and Technology (NIST) has approved initial post-quantum algorithms including ML-KEM for key exchange and ML-DSA for digital signatures. Organizations will need to migrate to these algorithms to protect against future quantum computers. However, migration is a multi-year project requiring updates to applications, infrastructure, and processes.
How should an organization approach quantum readiness?
Start with awareness and planning. Form a leadership task force to coordinate quantum readiness efforts. Inventory systems using public-key cryptography. Prioritize systems protecting sensitive long-term data. Develop a timeline for migration to post-quantum cryptography (most organizations plan 4-7 year migration periods). Begin with pilot programs using NIST-approved algorithms. Use hybrid encryption approaches during the transition period to improve security against both classical and quantum threats.
What is Zero Trust?
Zero Trust is a security principle that means verifying every user, device, and connection regardless of whether they're inside or outside your network perimeter. Instead of trusting everything inside your network, Zero Trust assumes breach and verifies everything. This is implemented through network segmentation, real-time monitoring, and automated policy enforcement. Zero Trust significantly reduces the attack surface and improves ability to detect and respond to compromises.
How do modern networks reduce costs?
Modern networks reduce costs in several ways: SD-WAN replaces expensive MPLS circuits with cheaper broadband and intelligent software, reducing connectivity costs 30-50%. Intelligent traffic management reduces bandwidth consumption by 20-30% by prioritizing critical traffic. Cloud-delivered security eliminates the need for expensive on-premises security appliances. Automation reduces operational labor costs. Improved visibility and monitoring reduce the cost of outages and security incidents. In total, most organizations see 25-40% reduction in network operating costs.
Conclusion
Your organization is at an inflection point. AI technology is transforming how businesses operate, create value, and compete. But AI success depends on infrastructure that can support it.
Legacy networks built 10-20 years ago don't work for AI. They can't provide the latency, bandwidth, visibility, and security that AI demands. Trying to run AI on legacy infrastructure is like trying to run Formula 1 engines through garden hoses: technically possible but fundamentally limited.
Network modernization isn't optional for organizations serious about AI. It's foundational.
The good news: modernization is achievable. You don't have to transform everything overnight. You can phase it gradually, proving value with pilots before broader rollout. You can use phased modernization to manage costs and risk.
Organizations that modernize their networks now will outcompete those that wait. They'll deploy AI faster. They'll run it more efficiently. They'll secure it better. They'll achieve better ROI.
Beyond AI, there's quantum computing. In 5-10 years, quantum computers could break current encryption. Modern networks provide the flexibility and control to migrate to post-quantum cryptography. Legacy networks will struggle.
The path forward is clear: assess your current state, develop a modernization roadmap, secure commitment from leadership, form a team, and execute gradually. Start with a pilot, prove results, expand from there.
Don't wait for quantum computers to arrive to start thinking about security. Don't wait for AI ROI to disappoint before modernizing your network. Don't wait for competitors to move ahead.
The time to act is now. Your organization's future competitiveness depends on it.
Use Case: Automate network architecture documentation and compliance reports with AI-powered workflows.
Try Runable For Free
Key Takeaways
- Legacy networks designed for steady workloads can't handle AI's unpredictable, high-volume data flows, causing latency, bottlenecks, and limiting ROI
- Modern architectures like SD-WAN and SASE reduce costs by 25-40%, improve performance, and enable consistent security across hybrid environments
- 97% of IT leaders identify network modernization as critical to AI success, yet only 43% have actually modernized their infrastructure
- Quantum computers could break current encryption in 5-10 years; organizations must start post-quantum cryptography migration immediately
- Phased modernization starting with assessment and pilots allows organizations to manage costs and risk while proving ROI before full enterprise rollout
Related Articles
- CISA End-of-Life Edge Device Replacement Guide [2025]
- New York's Data Center Moratorium: What the 3-Year Pause Means [2025]
- New York Data Center Moratorium: What You Need to Know [2025]
- Benchmark's $225M Cerebras Bet: Inside the AI Chip Revolution [2025]
- Best VPNs for Super Bowl LIX: Complete Streaming Guide 2025
- AI Agent Social Networks: The Rise of Moltbook and OpenClaw [2025]
![Network Modernization for AI & Quantum Success [2025]](https://tryrunable.com/blog/network-modernization-for-ai-quantum-success-2025/image-1-1770546994632.jpg)



