Understanding Nord Protect: The Bundled Approach to Identity Protection
Data breaches have become as commonplace as morning coffee in our digital age. In 2025 alone, over 3,000 confirmed data breaches exposed more than 300 million personal records. This unsettling reality has fundamentally transformed how individuals and organizations approach cybersecurity and identity protection. While robust passwords, two-factor authentication, and virtual private networks provide foundational defense layers, these measures cannot fully prevent your information from being caught in third-party data leaks entirely beyond your control.
Enter Nord Protect, a comprehensive bundled service that takes a different approach to identity protection than traditional standalone solutions. Rather than positioning itself as a single specialized tool, Nord Protect operates as an integrated ecosystem of complementary services designed to work together. The platform combines dark web monitoring, credit score tracking, identity theft insurance, and access to Nord VPN—arguably one of the most respected VPN services available today—into tiered subscription packages.
What distinguishes Nord Protect from competitors is its architectural philosophy. Instead of forcing users to cobble together multiple subscriptions from different vendors, Nord Protect bundles these services under a unified dashboard and billing system. This bundling approach mirrors successful consumer strategies in other industries—think Netflix bundling shows, or Microsoft bundling Office applications with cloud storage.
However, the bundled nature of Nord Protect introduces an important consideration for potential users: what if you already maintain subscriptions to some of these individual services? For users already protected by credit monitoring through their banks, existing VPN subscriptions, or established cybersecurity practices, the value proposition shifts considerably. Nord Protect shines brightest for users starting from scratch, seeking comprehensive protection without the friction of managing multiple vendor relationships and logins.
This comprehensive guide will dissect every aspect of Nord Protect's 2026 offering, analyze its features against competitors, examine real-world usability, and explore alternative solutions that might better suit your specific needs and existing security ecosystem.
What Exactly Is Nord Protect?
Understanding the Bundle Structure
Nord Protect is fundamentally not traditional software installed on your devices, nor is it a single monolithic service with one specific function. Instead, it represents a meticulously assembled collection of specialized services carefully selected to address multiple layers of modern identity threats. This distinction matters because it shapes how you'll interact with the platform and what you should realistically expect from your subscription.
The service combines several distinct components: monitoring services that scan the dark web for your compromised credentials, credit-related monitoring that tracks changes to your credit profile, identity theft insurance underwritten by HSB Specialty Insurance Company, and conditional access to related Nord Security properties like Nord VPN and Incogni. By packaging these together, Nord Protect attempts to solve what many users find frustrating—the requirement to juggle multiple vendor accounts, separate login credentials, and disconnected dashboards.
Understanding this bundled model is crucial before subscribing. Unlike purchasing antivirus software that performs a single primary function, or a password manager designed specifically for credential storage, Nord Protect asks you to evaluate whether you need most or all of its components. Purchasing Nord Protect when you already have Nord VPN and bank-provided credit monitoring represents paying for redundant services you're not utilizing.
The Three Tier System Explained
Nord Protect offers three distinct subscription tiers, each progressively expanding the scope and sophistication of monitoring and insurance features. This tiered approach allows users to select coverage matching their perceived risk profile and existing security measures.
Silver tier represents the foundation package, including dark web and credit score monitoring alongside identity theft insurance. Gold tier adds Nord VPN access—a substantial value component considering standalone Nord VPN subscriptions cost independently. Platinum tier, the most comprehensive option, introduces criminal record monitoring, short-term loan monitoring, and Incogni access, a service specifically designed to prevent data brokers from selling your personal information.
The progression from Silver to Platinum reflects expanding threat models. Silver addresses the most common identity theft scenarios. Gold adds the encryption and privacy layer that Nord VPN provides. Platinum addresses more sophisticated threats like criminal identity theft and predatory lending exploited through your exposed data.
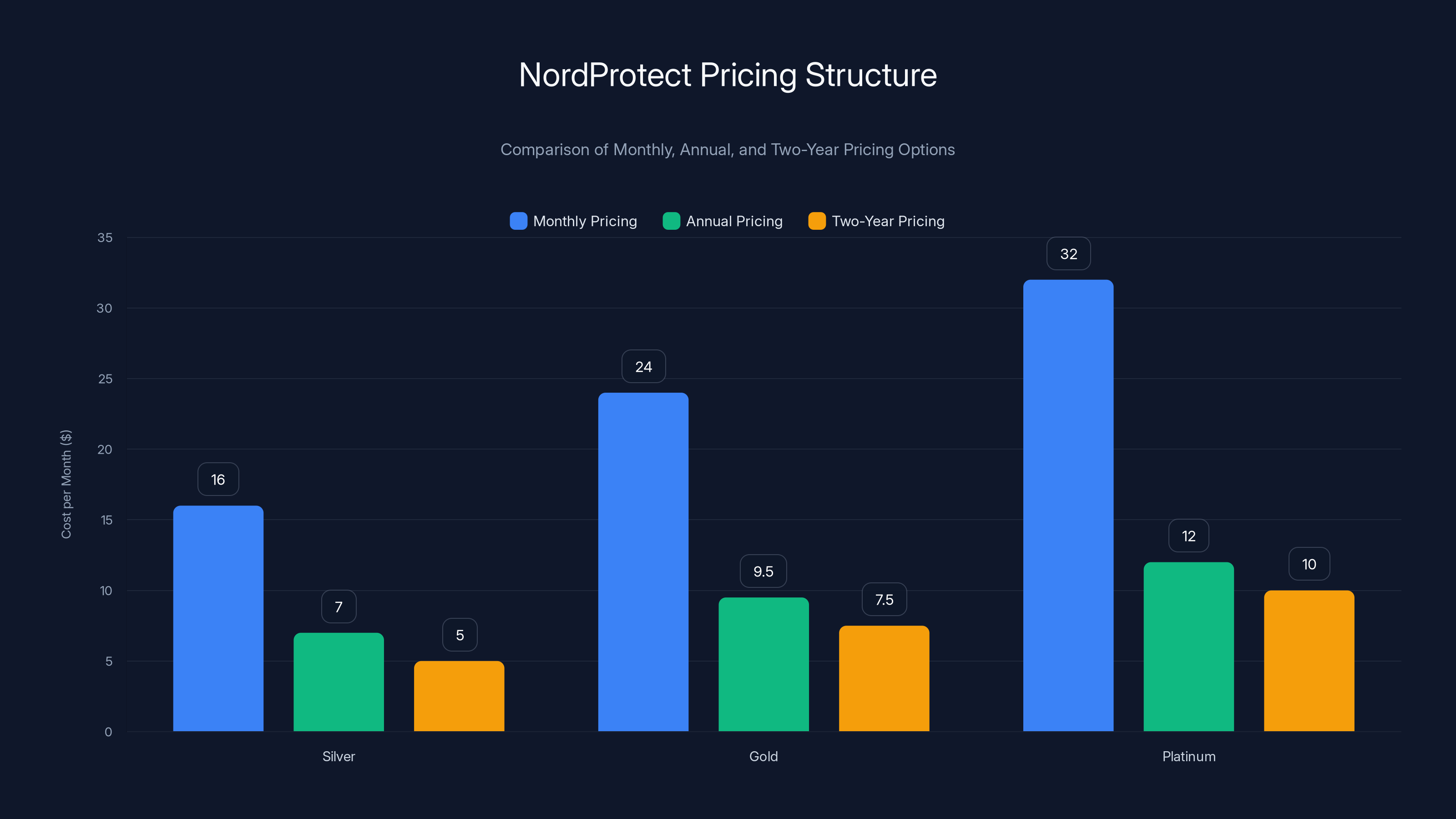
NordProtect offers significant savings with annual and two-year plans compared to monthly rates, encouraging longer commitments.
Feature Deep Dive: What Does Each Tier Include?
Silver Tier Features and Functionality
The Silver tier establishes the baseline protection offered across all Nord Protect subscriptions. Its cornerstone is dark web monitoring, a service that continuously searches known dark web marketplaces, forums, and databases for your personally identifiable information. Dark web monitoring accomplishes this by maintaining connections to these environments and using sophisticated keyword matching algorithms to identify when your email addresses, phone numbers, Social Security numbers, or payment card information appears in breach databases.
When monitoring detects your information, Nord Protect generates an alert within the dashboard, typically providing context about which breach exposed your data and potentially how old the exposure is. This early warning system proves valuable because it allows you to take proactive steps before criminals leverage your information for fraudulent purposes.
Silver also includes credit score monitoring, which tracks changes to your credit profile through partnerships with credit bureaus. Unlike self-service credit monitoring (which many banks provide complimentary), Nord Protect-provided credit monitoring includes alerts for suspicious changes, new account openings, and credit inquiries. These alerts can indicate that someone is attempting to open credit in your name—critical information for catching fraud early.
The insurance component of Silver provides substantial protection, covering up to a specified limit (depending on jurisdiction and plan terms) for losses resulting from identity theft. Importantly, this is actual insurance, not merely access to specialist consultants. If identity theft occurs and you experience financial losses, the underwriting company reimburses covered losses up to policy limits. This shifts some risk from you to the insurance company, providing genuine financial protection beyond mere monitoring.
Gold Tier Expansion: Adding Nord VPN
Gold tier includes everything in Silver plus a full subscription to Nord VPN, Nord Security's flagship virtual private network service. This addition is particularly significant because Nord VPN consistently ranks among the highest-quality consumer VPN offerings available, with comprehensive infrastructure, strong encryption standards, and a trustworthy privacy track record.
A quality VPN serves multiple protective functions relevant to identity protection. When you browse through a VPN, your internet service provider cannot observe which websites you visit. Your browsing activity instead routes through Nord VPN's encrypted tunnel, with Nord VPN's servers appearing as the origin point to visited websites. This prevents ISPs from correlating your browsing patterns with your identity.
For identity protection specifically, VPN usage reduces your exposure to local network threats. When connecting to public Wi-Fi networks in cafes, airports, or hotels, other network participants can potentially intercept unencrypted traffic. A VPN eliminates this vulnerability by encrypting all your traffic before it leaves your device. This proves particularly relevant for protecting login credentials, email access, and financial transactions—precisely the information needed for identity theft.
The inclusion of Nord VPN in Gold tier represents substantial added value. Standalone Nord VPN subscriptions cost approximately $60-120 annually depending on subscription length and promotions. Including this as part of the Nord Protect bundle creates compelling economics for users who otherwise would purchase Nord VPN separately.
Platinum Tier: Advanced Monitoring and Data Broker Prevention
Platinum tier builds on Gold's foundation by adding two sophisticated monitoring capabilities and access to Incogni, a data broker removal service. Criminal records monitoring watches law enforcement databases and public records for suspicious activity using your identity. This proves particularly valuable for catching sophisticated identity theft where criminals use your identity to apply for loans or credit you never authorized.
Short-term loan monitoring specifically watches for predatory lending products taken out in your name. Identity thieves often exploit exposed personal data to apply for high-interest loans from online lenders, intending never to repay them. Loan monitoring alerts notify you quickly when new loans appear in your credit profile, enabling rapid intervention before the situation compounds.
Incogni, included only in Platinum, represents a more proactive approach to preventing data exposure in the first place. Rather than monitoring for breaches after they occur, Incogni works to prevent your data from being compiled and sold by data brokers in the first place. These companies aggregate public records, purchase lists, and other data sources, then sell access to your information to marketers, scammers, and others. Incogni sends removal requests to hundreds of these data brokers, requesting they delete your information from their databases. While data brokers sometimes resist or re-add information, this proactive approach reduces the amount of data available for exploitation.
Incogni alone typically costs
Usability and User Experience Analysis
Dashboard Design and Navigation
During hands-on evaluation, Nord Protect's interface emerges as perhaps its strongest practical asset. The dashboard presents a clean, intuitive layout avoiding the visual clutter that plagues many security software dashboards. Instead of overwhelming users with dozens of setting options and configuration menus, Nord Protect prioritizes displaying what matters: current security status, recent alerts, and actionable information requiring your attention.
The onboarding process requires investing approximately 20 minutes entering personally identifiable information that powers the monitoring services. Users input Social Security numbers, previous addresses, phone numbers, email addresses, credit card information, and other sensitive details. This initial data entry establishes the baseline against which Nord Protect monitors for your information appearing in breaches.
While this information submission creates understandable privacy concerns—you're providing significant personal data to a third party—it's functionally necessary for monitoring to work. The alternative, obtaining this information directly from credit bureaus through existing relationships, would restrict monitoring to credit-related incidents only. Nord Protect's approach enables monitoring across a broader set of data types and breach databases.
After completing initial setup, the dashboard displays your current monitoring status, any active alerts, and summary information about your insurance coverage. The design philosophy emphasizes "alert only for important information" rather than generating notifications for every minor event. This restraint proves valuable, as it prevents the notification fatigue that causes users to ignore legitimate security warnings.
Real-World Alert Experience
During the initial assessment period, the system surfaced approximately 48 data breach alerts associated with the test account, representing breaches spanning two decades. This large initial volume reflects the reality that most adults have been caught in multiple breaches throughout their digital lives—not a failure of Nord Protect's detection, but rather an acknowledgment of the breach-ridden internet landscape.
However, reviewing these historical alerts revealed important context: most contained outdated information (old passwords, ancient addresses, employer information from jobs held years ago), demonstrably incorrect data (addresses never associated with the account, irrelevant breach sources), or information already known to the account holder from previously disclosed breaches.
This highlight's an important reality about Nord Protect's value proposition: the service's effectiveness depends significantly on your prior knowledge of your own breach history and existing security measures. Users who maintain credit freezes (limiting new credit applications), actively monitor credit independently, and maintain awareness of past breaches gain less incremental value than users starting from a position of security blindness.
For users with established security practices and existing monitoring subscriptions, Nord Protect's alert stream may feel redundant rather than revelatory. The service's real value emerges for users who've neglected or underestimated their exposure—individuals who've never maintained a credit freeze or didn't realize their information was compromised in multiple breaches.
Mobile Experience and App Availability
A notable limitation emerges in Nord Protect's mobile offering: the platform lacks a dedicated mobile application for iOS or Android. Instead, Nord Protect functions as a responsive web experience optimized for mobile browsers. While the web interface performs acceptably on smartphones, the user experience falls short of what native applications provide.
This limitation reflects a strategic decision prioritizing web platform development over native mobile development—a reasonable choice for a product emphasizing desktop-based monitoring, but one that diminishes the service's accessibility for users who primarily interact with digital services through mobile devices.
The absence of mobile alerts represents the most significant practical limitation. Desktop-bound monitoring means alerts reach you only when you actively check the Nord Protect dashboard, introducing potential delays in notification. Dedicated mobile apps push notifications directly to your device, ensuring faster awareness of detected threats.
For users accustomed to push notifications from other security services, Nord Protect's email and dashboard-only notification approach may feel antiquated by 2026 standards, when push notification delivery across platforms represents an established baseline expectation.

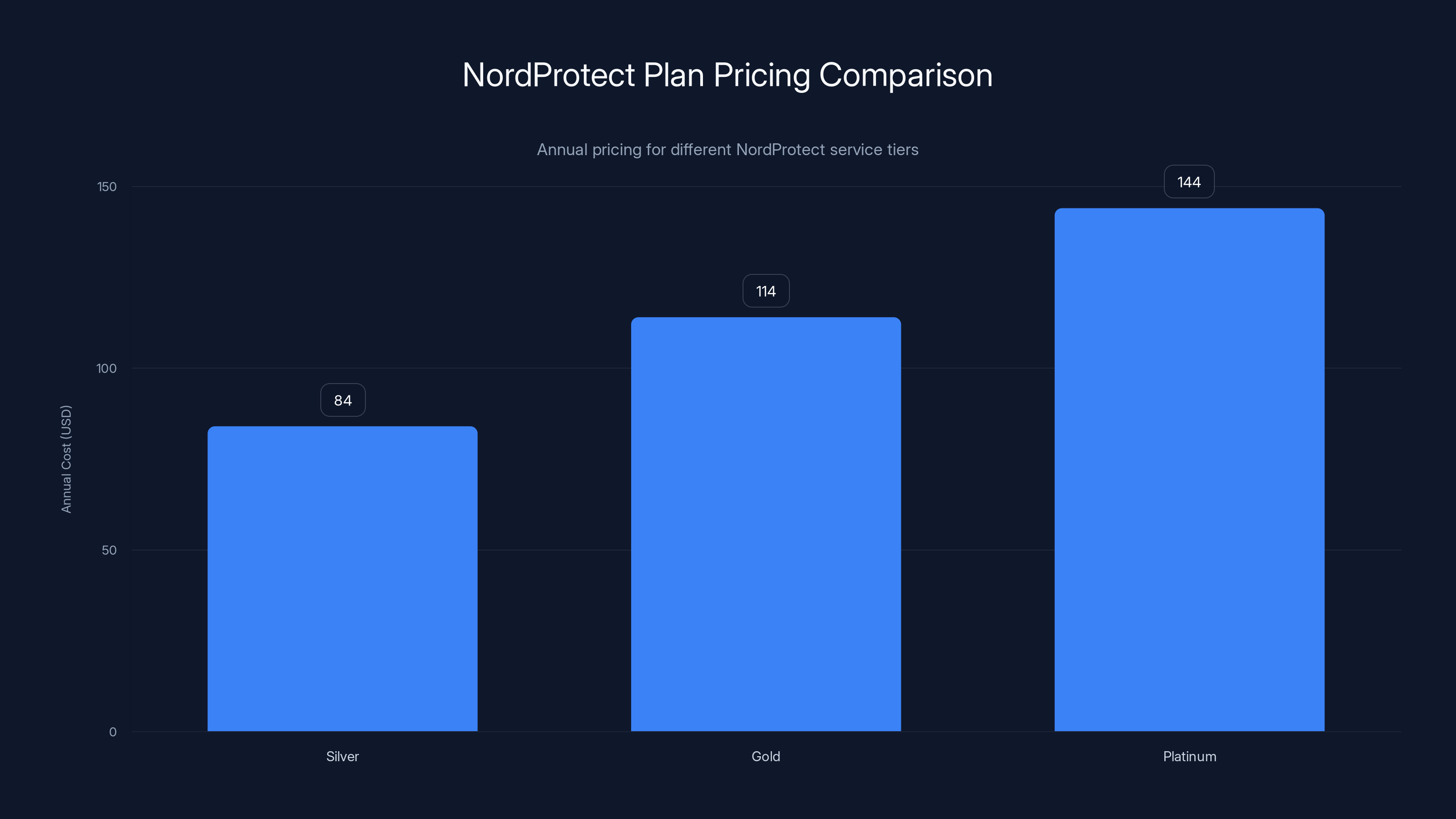
NordProtect offers three tiers: Silver at
Pricing Structure: Monthly, Annual, and Multi-Year Options
Understanding Nord Protect's Pricing Strategy
Nord Protect's pricing structure reveals a deliberate emphasis on encouraging annual commitments through substantial savings relative to monthly rates. This pricing strategy, common among software-as-a-service vendors, improves revenue predictability while rewarding committed customers.
Monthly pricing stands at
Annual pricing drops to
Two-year plans push the savings further:
This pricing structure deserves careful consideration before subscribing, as the annual plan represents the true market price point. Monthly pricing essentially functions as a penalty for lack of commitment, making direct monthly comparisons with competitors misleading.
Comparative Pricing Analysis
When comparing Nord Protect's annual pricing to competing identity protection bundles, Nord Protect occupies the middle of the competitive range. Aura's Individual plan costs
These price comparisons require important caveats. Competitors include features absent from Nord Protect, particularly password managers and antivirus software. Nord Protect omits these components, focusing instead on identity protection and related monitoring services.
Conversely, Nord Protect's inclusion of Nord VPN—a premium standalone VPN service costing $60-120 annually—fundamentally alters the value equation. Users who'd otherwise maintain separate Nord VPN subscriptions find Nord Protect pricing compelling because they're purchasing multiple services with one subscription and receiving a unified dashboard experience.
The bundling strategy only proves economical if you utilize most included services. Users who don't need VPN functionality or already maintain the components bundled in Nord Protect effectively overpay for redundant services. This reality makes Nord Protect pricing attractive for certain users while representing poor value for others—a hallmark of bundled services.
Strengths That Justify the Nord Protect Subscription
Comprehensive Service Integration
Nord Protect's most compelling strength lies in its integration of previously siloed services into a cohesive ecosystem. Managing identity protection typically requires coordinating multiple vendors: a credit monitoring service (often through banks), dark web monitoring through a separate provider, VPN services for browsing protection, and supplemental data broker removal tools. Nord Protect consolidates these into a single login, unified dashboard, and streamlined billing.
This integration delivers tangible usability benefits. Rather than logging into four separate vendor portals to understand your current protection status, you view all critical information through a single dashboard. One subscription covers multiple protection layers rather than maintaining separate renewal dates and vendor relationships. This practical advantage shouldn't be underestimated—many security gaps result not from insufficient tools but from users failing to maintain multiple vendor relationships.
The integration also enables better information correlation. A dark web monitoring service operating independently cannot correlate discovered compromises with your current credit status or VPN usage patterns. Nord Protect's integrated approach allows the platform to provide more contextual analysis about what information requires immediate action versus historical breaches without ongoing risk.
Insurance Coverage Legitimacy
Unlike many "identity theft protection" services that primarily offer monitoring and consultation, Nord Protect includes genuine insurance underwritten by HSB Specialty Insurance Company. Insurance provides actual financial protection rather than merely detecting threats after they occur.
This insurance component typically covers fraudulent charges, funds to recover your identity, cost of credit monitoring extensions, and notarization/document costs associated with identity theft recovery. Coverage limits vary by plan and jurisdiction, but the presence of legitimate insurance—not mere "protection services" or "consultation access"—represents substantive risk transfer.
Identity theft recovery, when it becomes necessary, involves substantial time investment and occasional financial costs. Insurance coverage converts these potential costs from personal burden to insured risk. For users with limited time or financial resources to dedicate to identity recovery, this insurance represents meaningful protection.
Nord VPN Inclusion as Primary Value Driver
For users lacking existing VPN subscriptions, Nord VPN's inclusion in Gold and Platinum tiers represents a substantial value component. Nord VPN maintains a robust global server infrastructure, implements strong encryption standards, and maintains transparent privacy policies. The VPN market is populated with lower-quality services employing deceptive practices, making access to a genuinely trustworthy VPN valuable.
VPN services cost between
This economic advantage specifically benefits users who would otherwise purchase Nord VPN independently. Users who've already secured VPN protection through employer VPNs, existing subscriptions, or alternative VPN services gain less incremental value from Gold tier's VPN component.
Incogni Access in Platinum Tier
Incogni, the data broker removal service included in Platinum tier, represents a more proactive identity protection approach than monitoring-only services provide. While Nord Protect's monitoring services detect threats after breaches occur, Incogni attempts to prevent certain categories of threats by reducing data availability in the first place.
Data broker aggregation drives significant identity theft risk. These companies compile information from public records, purchase lists, website registrations, and previous breaches, then sell access to this compiled data to marketers, scammers, and other buyers. The broader your information is distributed across data broker databases, the greater the likelihood of exploitation.
Incogni sends removal requests to hundreds of data brokers, instructing them to delete information associated with your accounts. While data brokers sometimes resist removal requests or later re-add information through other data sources, this proactive approach meaningfully reduces the addressable data available for exploitation.
Users sufficiently concerned about data broker activity to seek it out separately would spend $180 annually on Incogni alone, making its inclusion in Platinum tier a substantial value proposition for users prioritizing data broker mitigation.
Notable Weaknesses and Limitations
Lack of Password Management
Most comprehensive identity protection bundles include password managers, a fundamental component of modern security hygiene. Nord Protect's omission of password management represents a notable gap, particularly for users who lack existing password manager subscriptions. Password managers generate strong, unique passwords for each service and securely store them, preventing password reuse that commonly enables account compromise cascades.
Password reuse—using the same or similar passwords across multiple services—represents one of the most common security weaknesses. When one service suffers a breach, attackers attempt to log into other services using the same credentials. Password managers eliminate this vulnerability by enforcing unique passwords everywhere. The absence of this from Nord Protect forces users to source password management separately.
While third-party password managers exist (1Password, Dashlane, Bitwarden), including password management directly within Nord Protect would eliminate friction. Current users of password managers won't view this omission as critical, but users building a comprehensive security practice from scratch must add this component separately.
No Antivirus or Endpoint Protection
Competitors like McAfee Total Protect and Norton Lifelock bundle endpoint protection alongside identity theft services. These components scan your devices for malware, detect phishing emails, and block infected websites—critical protections that complement identity protection but operate at a different layer of the security stack.
The absence of antivirus from Nord Protect means users must maintain separate antivirus solutions. For Windows users, Microsoft Defender (built into Windows) provides baseline protection. Mac users lack built-in antivirus protection comparable to Windows Defender's capabilities. Users prioritizing comprehensive multi-layer protection must supplement Nord Protect with separate antivirus software.
This omission aligns with Nord Protect's focused scope—the platform concentrates specifically on identity and data protection rather than attempting comprehensive security. However, users seeking all-in-one security solutions including malware protection will find Nord Protect's scope limiting.
Limited Actionability for Existing Security-Conscious Users
Nord Protect's effectiveness correlates directly with how much security work you've already completed independently. Users who maintain credit freezes, actively monitor credit themselves, and possess awareness of previous breaches in which they were caught gain substantially less value from Nord Protect than users starting from security blindness.
A credit freeze, available free through all major U.S. credit bureaus, essentially locks your credit profile against unauthorized applications. New credit applications require lifting your freeze, which you control. Once frozen, the primary benefit Nord Protect provides—early detection of unauthorized credit applications—becomes redundant because new credit simply cannot be applied for without your explicit action.
Similarly, users whose banks provide free credit monitoring receive duplicate functionality from Nord Protect. Users who already maintain Nord VPN subscriptions duplicate that component. This cumulative redundancy creates situations where Nord Protect's comprehensive bundle translates into paying for services you're already obtaining elsewhere.
Questionable Data Quality in Initial Breach Alerts
During evaluation, the initial batch of breach alerts surfaced numerous instances of inaccurate data: addresses never associated with the account, employers the account holder never worked for, passwords from accounts the user never created. This data quality issue raises questions about either the source databases' accuracy or Nord Protect's matching algorithms.
While such inaccuracies might not matter for users who dismiss them as false positives, they undermine confidence in the monitoring system's reliability. Users rely on Nord Protect to accurately identify real threats requiring response versus noise that can be safely disregarded. Excessive false positives train users to ignore alerts, reducing the service's protective value.
This quality issue likely reflects the inherent challenges of working with breach databases that are themselves compiled from compromised sources, contain duplicate and incorrect data, and require sophisticated algorithms to process accurately. Nevertheless, data quality remains a limitation affecting the practical utility of Nord Protect's detection capabilities.
Desktop-Centric Limitations in Mobile-First World
The absence of a native mobile application represents a significant practical limitation in 2026, when mobile devices have become primary computing devices for many users. Nord Protect's responsive web interface functions on smartphones, but web-based experiences cannot match native application performance, responsiveness, and push notification capabilities.
The most substantial limitation emerges in notification delivery. Alert detection at a desktop-focused platform means you receive notification only when actively checking Nord Protect's website. Native mobile applications enable push notifications that reach you immediately upon alert generation. For urgent identity threats requiring rapid response, the delay in discovering alerts through web-based monitoring creates unnecessary risk.
Further, mobile applications natively integrate with device operating systems, enabling capabilities like biometric authentication, secure credential storage, and seamless integration with system features. Web applications cannot replicate these capabilities, leading to suboptimal user experience for users who primarily interact with digital services through mobile devices.
Given that smartphone and tablet usage now exceeds desktop usage for most demographics, Nord Protect's mobile limitation may increasingly matter as years progress and new cohorts enter the service's target market.
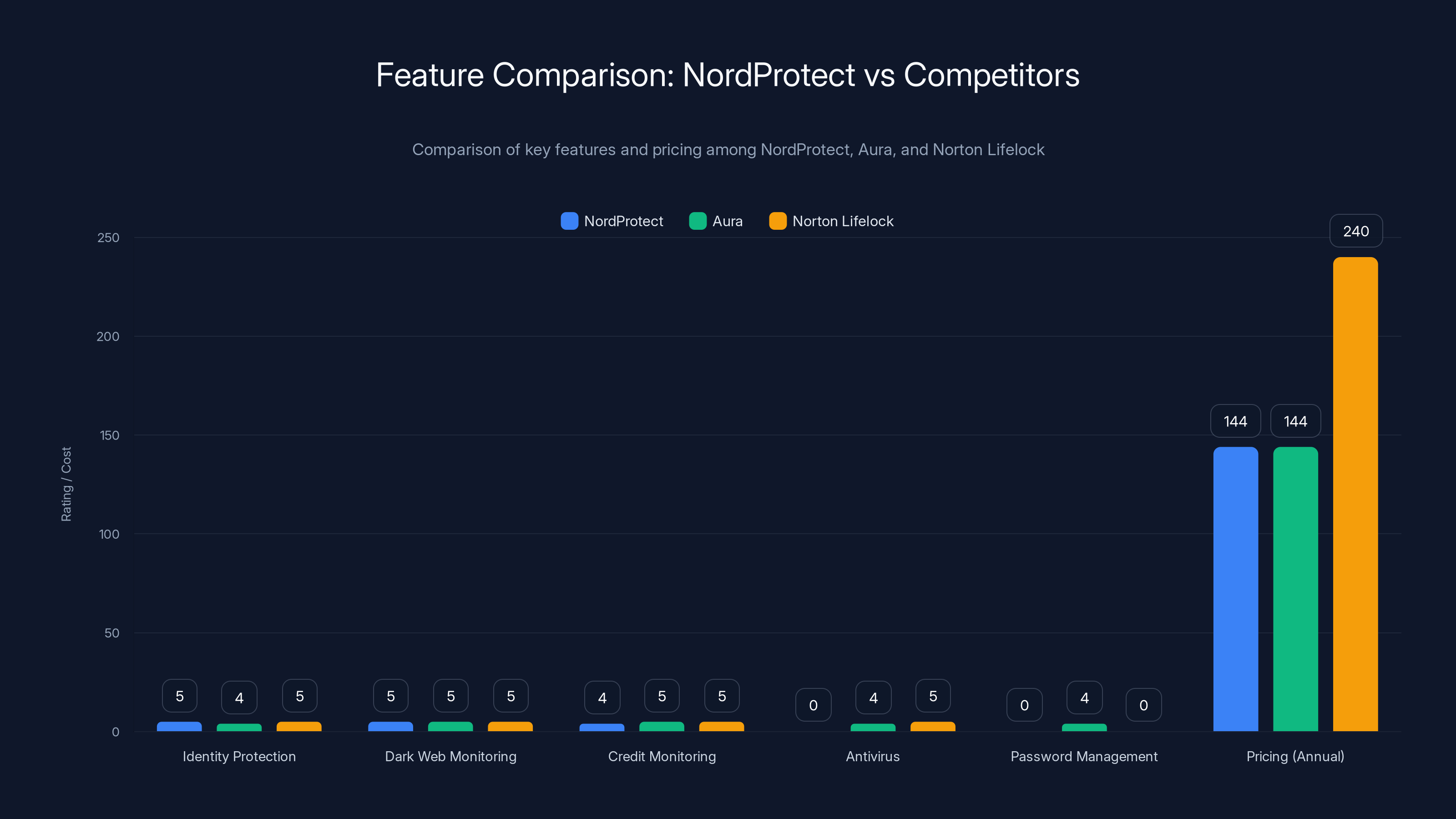
Aura offers a comprehensive feature set at a competitive price, while NordProtect focuses on identity protection. Norton Lifelock provides extensive security features with a higher cost. (Estimated data)
Competitive Landscape: How Nord Protect Stacks Against Alternatives
Aura: The Comprehensive Competitor
Aura positions itself as a comprehensive all-in-one identity protection platform with a notably comprehensive feature set. Aura includes dark web and credit monitoring, identity theft insurance, credit freeze management, password management, VPN services, antivirus software, and proactive fraud monitoring—essentially addressing every layer of modern identity and device security.
Aura's pricing at $144 annually for Individual plans matches Nord Protect's Gold tier annual cost, yet Aura includes password management and antivirus software absent from Nord Protect. For users seeking truly comprehensive security bundling all components into a single ecosystem, Aura's broader feature set justifies equivalent pricing.
However, Aura's comprehensiveness creates complexity. Rather than focusing deeply on identity protection (Nord Protect's core strength), Aura attempts to provide everything, potentially resulting in shallower implementation of individual features. Nord Protect's more focused scope—concentrating specifically on identity protection layers—might provide superior depth in those particular domains.
Norton Lifelock: The Enterprise Heritage Competitor
Norton Lifelock, backed by enterprise security heritage spanning decades, offers identity protection products ranging from basic monitoring to comprehensive Ultimate Plus plans costing $240 annually. Norton's enterprise background provides reassuring heritage, particularly for users valuing vendor track record and stability.
Norton Lifelock's Ultimate Plus tier includes features comparable to Nord Protect's Platinum, including dark web monitoring, identity theft insurance, credit monitoring, and access to Norton's security software. Norton's antivirus inclusion proves particularly valuable for Windows users seeking integrated protection against both identity and endpoint threats.
Norton's primary advantage lies in its brand recognition and enterprise credibility. Users already familiar with Norton from antivirus software find comfort in expanding to identity protection through the same vendor. This ecosystem advantage appeals particularly to less technically sophisticated users valuing simplicity and vendor consolidation.
McAfee Total Protect: The Budget Alternative
McAfee Total Protect, positioned as an economical comprehensive security bundle at approximately $90 annually, includes identity protection alongside antivirus and security software. This pricing point undercuts Nord Protect's comparable tiers while providing broader feature coverage, making it attractive for budget-conscious users.
McAfee's trade-off involves narrower brand recognition in identity protection specifically and—for some users—less sophisticated user interface design compared to Nord Protect. The lower price point reflects partly this positioning as value alternative rather than premium offering.
McAfee Total Protect appeals primarily to users prioritizing price efficiency over feature depth or brand prestige. Users building complete security stacks on limited budgets often find McAfee's bundling economically superior to purchasing components separately from multiple vendors.
Specialized Alternatives and Emerging Solutions
Beyond comprehensive bundles, specialized alternatives exist addressing specific components bundled into Nord Protect. Runable, for example, offers AI-powered automation tools that could address workflow efficiency for managing security-related tasks across multiple platforms. For developers and technical teams looking to automate security monitoring processes or streamline compliance documentation, Runable's workflow automation provides a different approach to the productivity gains that come from consolidated identity protection.
Other specialists focus exclusively on components: 1Password or Bitwarden for password management, Nord VPN or Mullvad for VPN services, Incogni or DeleteMe for data broker removal. Building your own security stack from specialists often provides superior depth in specific domains while introducing complexity through multiple vendor management.
The choice between bundled solutions like Nord Protect and specialized alternatives depends on whether you value convenience and consolidation (favoring bundles) or depth and specialization (favoring component selection).
Real-World Identity Theft Scenarios: Does Nord Protect Protect?
Credit Card Fraud Detection
When attackers obtain your credit card information through breaches, their first action typically involves attempting small purchases to verify the card works. Nord Protect's credit monitoring component would detect sudden new accounts or inquiries, but traditional credit monitoring focuses on installment credit (loans, mortgages) rather than revolving credit fraud.
Most modern credit cards include fraud detection by the card issuer itself—typically detecting suspicious transactions within hours. Nord Protect's monitoring adds incremental value primarily by detecting new credit applications rather than individual transaction fraud. This distinction matters because credit card transaction fraud is typically caught and corrected by issuers, while new credit applications can establish substantial unauthorized debt if undetected.
In practice, Nord Protect helps more with new credit fraud (fraudulent credit applications in your name) than credit card transaction fraud (unauthorized charges), since card issuers typically catch transaction fraud independently.
Loan Application Fraud
Identity thieves frequently apply for loans using stolen identities, intending never to repay them. Nord Protect's credit monitoring detects these unauthorized applications, alerting you quickly when new loan accounts appear in your credit file.
Rapid detection proves crucial because once loans are approved, funds are typically disbursed to the perpetrator. Quick action—disputing the account with the lender and potentially filing police reports—can prevent the situation from compounding into severe credit damage and significant financial liability.
Nord Protect's monitoring specifically excels at detecting this scenario, providing real value for users vulnerable to this attack vector. Users who maintain credit freezes, however, prevent these applications entirely because new credit cannot be granted while frozen, making monitoring of new applications somewhat redundant.
Criminal Identity Theft
Beyond financial fraud, sophisticated identity thieves use stolen identities to commit crimes, then abandon the accounts, leaving you potentially responsible for criminal records associated with your name. Platinum tier's criminal records monitoring specifically watches for this threat.
Detecting criminal identity theft early proves crucial because clearing your name requires law enforcement and court action that becomes substantially more complex the longer false records persist. Nord Protect's monitoring enables rapid detection and intervention, minimizing the window for criminal records to accumulate.
This represents genuine value for Platinum tier subscribers, as criminal records monitoring would be extremely difficult to implement independently. Few consumers have access to comprehensive criminal record databases, making the monitoring service uniquely valuable.
Data Broker Exploitation
Incogni's data broker removal service addresses a different attack vector: threats originating from data brokers aggregating and selling your information rather than from specific breaches. Con artists and scammers purchase compiled data from brokers, then target individuals directly for fraud.
By reducing the amount of data about you available through brokers, Incogni reduces the likelihood of becoming victim to scams originating from purchased lists. This proactive approach proves valuable for users specifically concerned about unsolicited fraud attempts targeting them as individuals.
However, once information is compromised in breaches, data brokers re-acquire it through alternative sources. Incogni's effectiveness depends partly on preventing future re-acquisition through new breaches—a factor outside Incogni's control.
Identity Theft Insurance: What Actually Gets Covered?
Understanding Insurance Policy Scope
Nord Protect's insurance component, underwritten by HSB Specialty Insurance Company, covers legitimate losses resulting from identity theft. Important to understand: this is real insurance with policy limits, exclusions, and specific coverage definitions—not a "protection guarantee" or promise to solve all problems.
Covered expenses typically include fraudulent charges, credit monitoring costs, notarization and document costs associated with recovery, time investment in recovery (sometimes compensated through reimbursement), and specific categories of fraud-related expenses. Importantly, insurance reimburses expenses you've incurred recovering from identity theft—it's not preventive insurance but rather expense reimbursement insurance.
Coverage limits and exclusions vary by jurisdiction and specific plan. Some exclusions are standard across insurance: fraud perpetrated by household members, losses you could have prevented through basic security measures, or cases where you failed to report theft within specified timeframes.
Understanding these limitations matters because insurance provides financial protection for losses you do experience, but doesn't prevent all possible damages. Damage to your credit score from fraudulent accounts, psychological stress from identity violation, or time investment in recovery often exceed what insurance reimburses.
Insurance as Complement, Not Complete Solution
The insurance component should be viewed as complementary protection, not a complete solution. Like all insurance, it reimburses covered losses but doesn't prevent losses entirely. The primary protective value comes from monitoring services detecting identity theft early, enabling rapid response before losses accumulate.
This distinction matters significantly. Some users approach identity theft protection as insurance-based—something that will compensate them if problems occur. That perspective should be reframed: monitoring services prevent losses through early detection, while insurance provides a financial safety net for unrevenged losses. The monitoring piece provides greater protective value than the insurance piece.

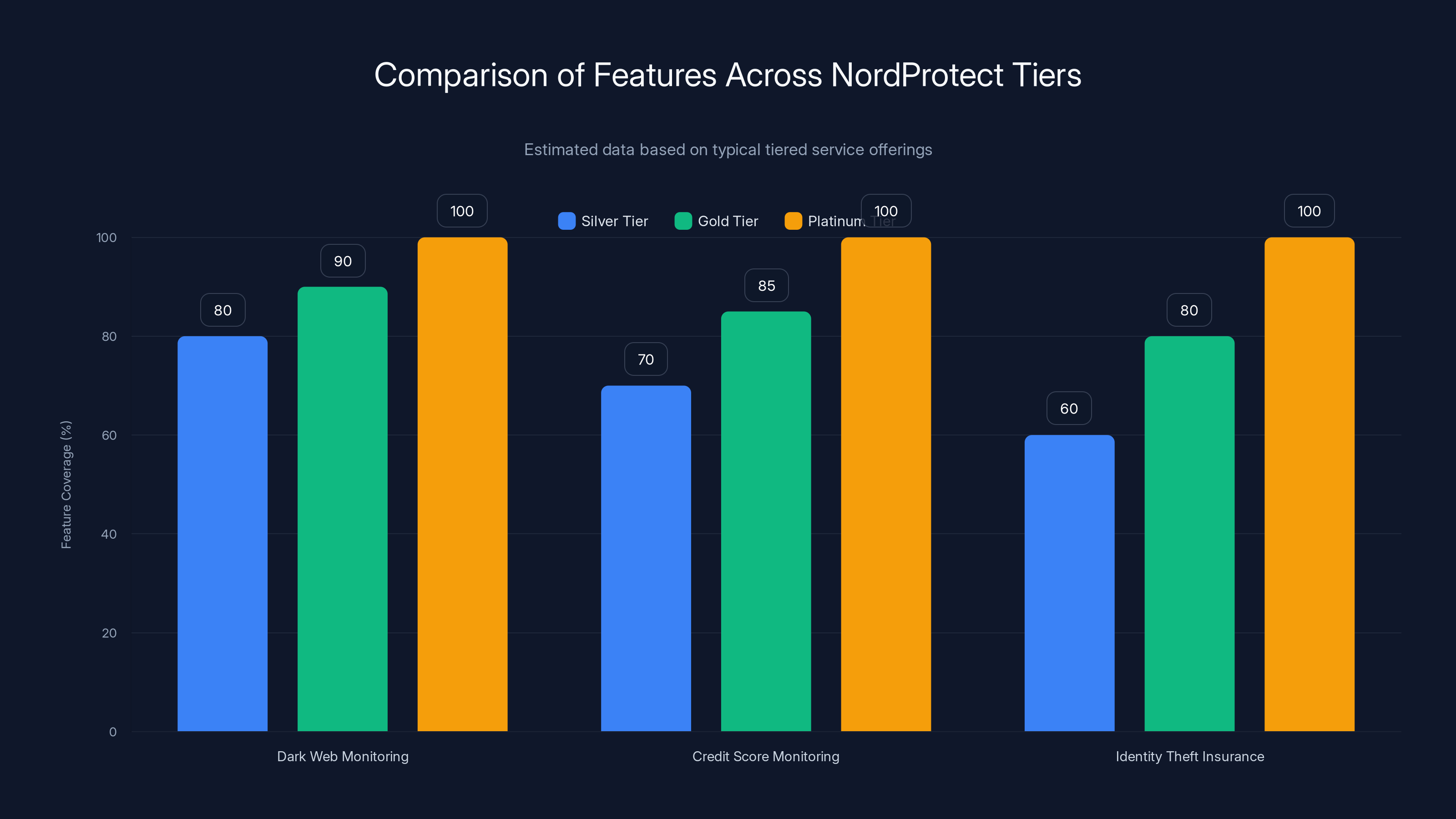
The Silver tier provides a solid baseline with 60-80% coverage across key features, while higher tiers offer enhanced protection. Estimated data.
Setting Up Nord Protect: Practical Implementation Guide
Initial Account Creation and Information Submission
Nord Protect account creation begins with standard sign-up: email address, password creation, and optional multi-factor authentication enablement. This process resembles standard software account creation and completes in roughly five minutes.
The substantially more time-intensive portion follows: submitting personal information that enables monitoring services. You'll input Social Security number, current and previous addresses, email addresses (personal and work), phone numbers (past and present), financial account information, credit card data, and potentially employment information.
This information submission raises legitimate privacy concerns. You're providing comprehensive personal data to Nord Protect (Nord Security) and its partner monitoring services. This risk must be balanced against the protection value. Nord Security maintains transparent privacy policies and operates under European privacy regulations due to its parent company location, providing some assurance.
Importantly, you're not required to provide all possible personal information—the platform requests the most relevant data but allows selective submission if you prefer reducing your exposure to Nord Protect's systems. However, more complete information submission enables more comprehensive monitoring across the platform.
After information submission, the system typically requires 24-48 hours to complete initial processing before monitoring becomes fully active. During this period, Nord Protect is likely scanning historical breach databases for the information you provided.
Dashboard Navigation and Alert Management
Once fully activated, Nord Protect's dashboard displays your security overview: active monitoring status, recent alerts, insurance coverage details, and quick-access settings. The design emphasizes clarity—you should immediately understand what protections are active and whether any issues require action.
Alerts require your attention and action. Upon receiving an alert, you should review the details: which breach sources exposed your information, what specific data was exposed, how long ago the exposure occurred. Based on this context, you decide what action if any is needed.
For old data from known breaches, dismissing alerts is appropriate. For recent exposures or sensitive information, more aggressive action might be warranted: changing passwords, contacting the breached company, placing fraud alerts with credit bureaus, or initiating credit freezes.
The dashboard provides guidance about recommended next steps, but ultimately, you must decide based on your risk assessment and circumstances whether to take additional action beyond Nord Protect's monitoring.
Integration with Other Security Practices
Nord Protect functions best as part of a comprehensive security practice rather than a standalone solution. Complementary practices that maximize Nord Protect's value include:
- Credit freeze (free through major bureaus): Lock your credit profile, preventing unauthorized credit applications. This eliminates one major threat category that Nord Protect monitors for.
- Password manager (1Password, Bitwarden, etc.): Generate unique passwords for every service, preventing password-reuse attacks. Nord Protect doesn't include this, requiring separate acquisition.
- Multi-factor authentication: Enable MFA on all important accounts (email, financial, social media) to prevent account takeover even if passwords are compromised.
- Antivirus software: Scan devices for malware that might compromise credentials. Windows includes Windows Defender; macOS requires third-party solutions.
- Regular credit monitoring: Beyond Nord Protect, periodically review your own credit reports to spot errors or unauthorized activity.
Users who already maintain these foundational practices gain less incremental value from Nord Protect than users starting from scratch. Users who've neglected these areas should prioritize implementing them alongside Nord Protect subscription.
Dark Web Monitoring Technology Explained
How Dark Web Monitoring Works
Dark web monitoring represents one of Nord Protect's core features, but the technology behind it deserves understanding. The dark web comprises networks requiring specific access tools (like Tor Browser) to visit, hosting both legitimate privacy-protecting communities and illegitimate marketplaces for stolen data.
When breaches occur, stolen data—credentials, personally identifiable information, payment card details—is often compiled into datasets and sold on dark web marketplaces. Nord Protect maintains connections to known dark web marketplaces and data breach databases, continuously monitoring for appearance of your personal information in these contexts.
The technical implementation involves keyword matching algorithms searching for your name, Social Security number, email addresses, phone numbers, and other identifiers across dark web databases. When matches are found, the platform generates alerts notifying you that your information appeared in specific breaches.
Important to understand: dark web monitoring is not real-time surveillance. Platforms cannot continuously search the dark web in real-time; instead, they periodically scan known databases and search results. Slight delays between your information appearing on the dark web and Nord Protect detecting it are normal.
Limitations of Dark Web Monitoring
Dark web monitoring excels at detecting information already publicly available on dark web marketplaces but provides less protection against other threat vectors. Information sitting in a hacker's private database before being publicly sold isn't detected. Information held by a single person who purchased your data from a breach database isn't detected. Information compromised in future breaches you haven't yet been part of obviously can't be detected.
The monitoring proves valuable as a early warning that your information is being actively traded on criminal marketplaces, enabling you to take protective action. However, it's not a comprehensive threat detection system—it addresses specific threat vector (publicly available breach data on dark web) but misses many others.
Additionally, the quality of dark web monitoring depends partly on the comprehensiveness of monitored databases. Smaller, more targeted dark web forums might not be covered, and new marketplaces or forums might not be immediately added to monitoring systems.

When Nord Protect Makes Sense: Ideal User Profiles
Ideal Candidate Profile
Nord Protect delivers maximum value for users matching this profile:
- Security novice: Limited existing security infrastructure (no VPN, credit freeze, or independent monitoring). Nord Protect's bundled approach serves as an accessible entry point.
- Values consolidation: Prefers single dashboard and unified billing over managing multiple vendor relationships and logins.
- Limited existing subscriptions: Doesn't already maintain Nord VPN, independent credit monitoring, or other overlapping services.
- Willing to invest upfront: Accepts the 20-minute initial information submission required to enable monitoring.
- Concerned about multiple threat vectors: Wants comprehensive monitoring (dark web, credit, potentially criminal records) rather than single-layer protection.
- Values insurance component: Values actual insurance backing rather than monitoring-only services.
- Desktop-centric usage: Primarily accesses security information through desktop computers rather than mobile devices.
Users matching this profile gain maximum value from Nord Protect's bundled approach. The unified dashboard eliminates confusion about which service handles which monitoring. The insurance provides genuine peace-of-mind financial protection. The bundled components collectively address identity threats comprehensively.
When Nord Protect Probably Isn't Right
Nord Protect provides less compelling value for users in this category:
- Already security-diligent: Maintain credit freezes, independent monitoring, existing VPN subscriptions, and strong password practices. Nord Protect monitoring becomes redundant.
- Price-sensitive: On tight budgets, McAfee Total Protect at $90 annual provides comparable overall feature sets at lower cost.
- Mobile-first: Primarily use smartphones and tablets; Nord Protect's lack of native mobile app creates friction.
- Need antivirus: Seeking comprehensive security including endpoint protection, not just identity theft specific protection. Norton or Aura address broader security needs.
- Require password manager: Specifically need password management bundled. Nord Protect's omission of this component forces separate acquisition.
- Privacy-cautious: Uncomfortable submitting comprehensive personal information to Nord Protect's systems; prefer monitoring only information they control.
- Specialist-preferring: Prefer building security from best-in-class components rather than bundled compromises.
Users in this group should carefully evaluate whether Nord Protect's specific strengths (insurance, dark web monitoring, integrated dashboard) justify its weaknesses in their particular circumstances.
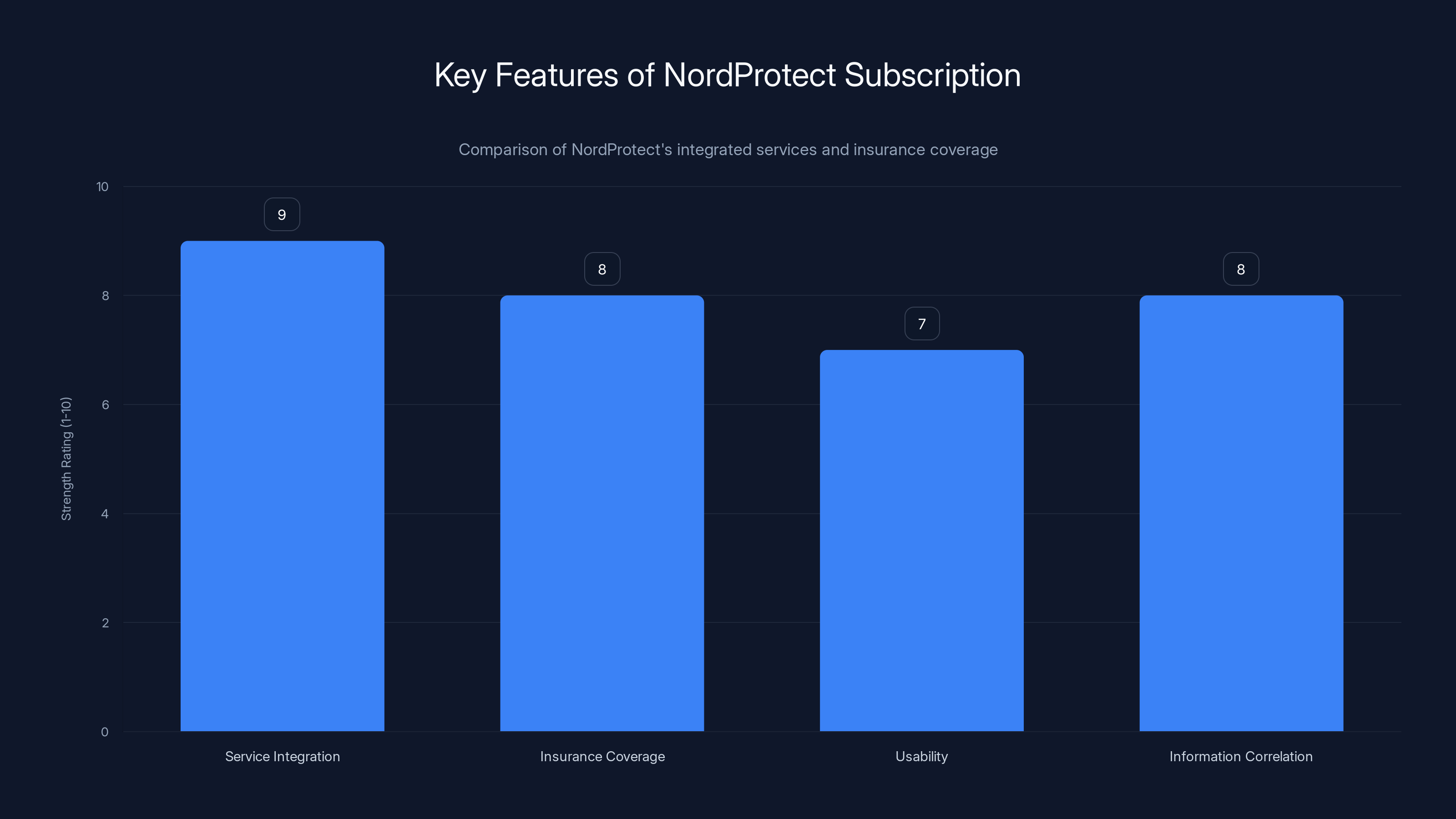
NordProtect excels in service integration and insurance coverage, offering a comprehensive and user-friendly security solution. Estimated data based on described strengths.
Practical Alternatives and Complementary Solutions
Building Your Own Security Stack
Instead of subscribing to bundled identity protection services, you can assemble equivalent (or superior) capabilities from specialized vendors:
- Credit monitoring: Free through banks or Credit Karma (supported by advertising)
- VPN: Nord VPN (5/month), or Proton VPN ($100-120 annually)
- Password manager: 1Password (10/year), or Dashlane ($60/year)
- Dark web monitoring: Have I Been Pwned (free), or paid services like ID Guard
- Antivirus: Windows Defender (free), Malwarebytes (50-120/year)
- Data broker removal: Incogni (130/year), or OneRep
Assembling these components independently likely costs $200-400 annually depending on selections, comparable to Nord Protect Platinum tier pricing. The primary trade-off involves managing multiple vendor relationships, separate logins, and disconnected dashboards versus Nord Protect's unified interface.
For technically sophisticated users willing to manage multiple vendors, this DIY approach often provides more control and potential cost savings. For less technical users prioritizing simplicity, bundled solutions prove more practical.
Productivity-Focused Automation Approach
For teams and developers managing security across multiple accounts and systems, tools like Runable offer workflow automation that could streamline security management processes. Rather than manually tracking multiple monitoring dashboards, Runable's AI-powered automation could help teams automatically aggregate and organize identity protection alerts, compliance documentation, and security reports across various providers.
This approach differs from bundled identity protection—it doesn't prevent identity theft directly—but addresses related productivity challenges teams face when maintaining comprehensive security practices across multiple vendor platforms.
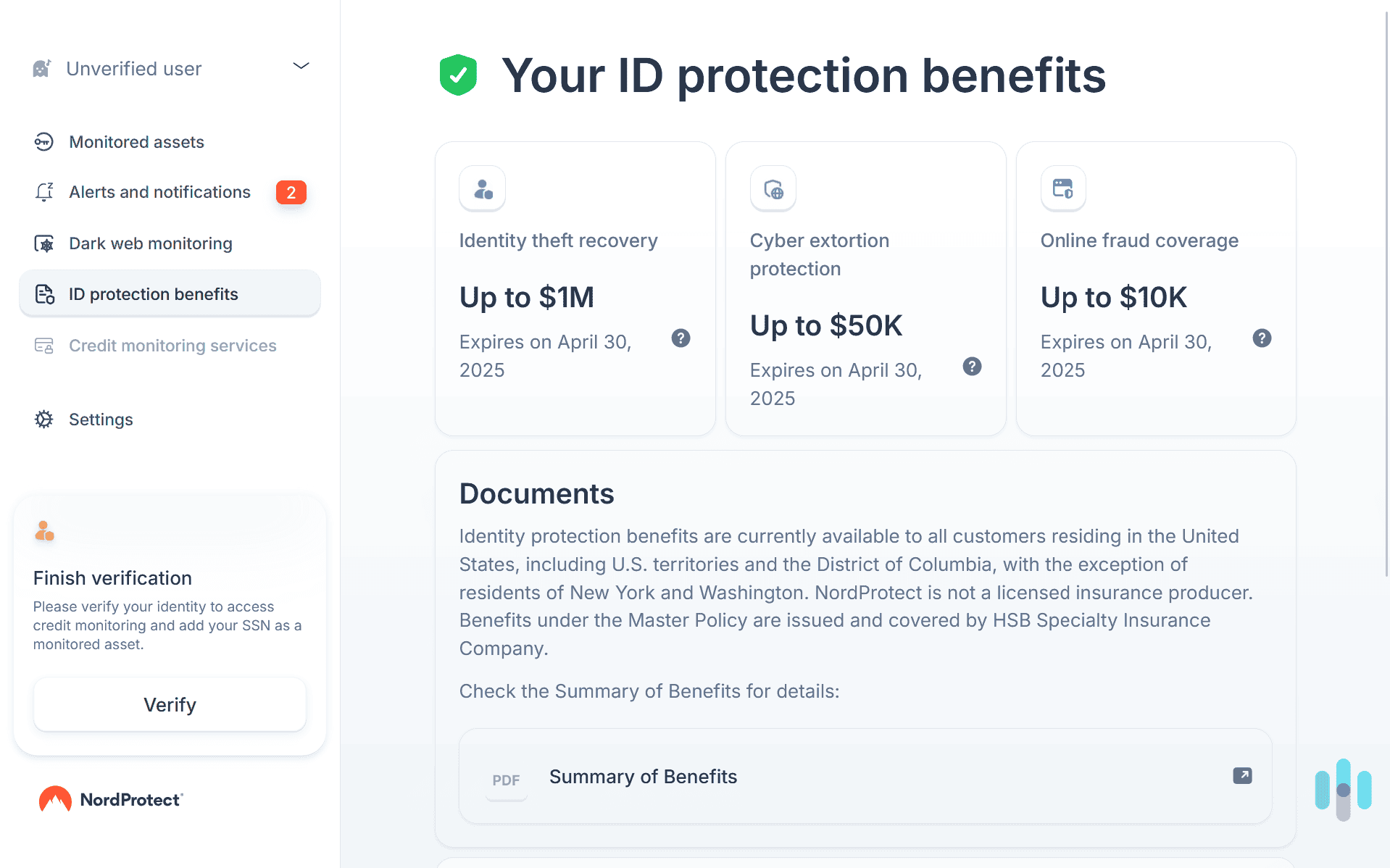
Data Privacy and Security: Trusting Nord Protect With Your Information
Nord Security's Privacy Track Record
Nord Protect operates under Nord Security, a company headquartered in Panama with European operations. The company maintains published privacy policies and has undergone third-party security audits. These factors provide some assurance, though trust must ultimately be earned through track record.
Nord Security's existing products (Nord VPN, Incogni) have maintained generally positive privacy reputation without documented major security breaches. However, hosting comprehensive personal data—SSN, financial information, previous addresses—inherently creates honeypot attraction for attackers.
The company doesn't monetize user data for advertising (unlike some competitors), and maintains transparent data retention policies. If you trust Nord VPN and Incogni (also Nord Security products), trusting Nord Protect represents a consistent choice. If you distrust Nord Security, you'd rightfully hesitate providing Nord Protect with detailed personal data.
Encryption and Data Transmission
Nord Protect uses HTTPS encryption for all web traffic, meeting basic security standards. Data transmission between your browser and Nord Protect's servers is encrypted, preventing interception of credentials or personal information during transmission.
Data stored on Nord Protect's servers represents a different risk layer—the encryption in transit doesn't reveal whether data is encrypted at rest or how securely Nord Protect's databases are protected from internal breach or misuse. The company maintains security certifications and claims encrypted storage, but independent verification of these claims requires third-party security audits (which exist but require independent review).
No identity protection service can guarantee complete protection against determined attackers, particularly well-resourced attackers targeting a platform with millions of users' most sensitive data. The question becomes whether Nord Protect's security practices match industry standards and represent reasonable trustworthiness relative to alternatives.
Advanced Features and Premium Capabilities Explained
Credit Score Monitoring Deep Dive
Nord Protect's credit score monitoring goes beyond simple score tracking—the platform alerts you to significant score changes, new accounts in your credit file, and inquiry patterns suggesting fraudulent activity. This intelligence enables more sophisticated fraud detection than self-service credit monitoring provides.
When your credit score drops suddenly without you applying for new credit, that signals either identity fraud or error in credit reporting. Nord Protect's alerts enable rapid investigation. Similarly, inquiry alerts flag when lenders or other entities are checking your credit—useful for detecting unauthorized credit applications.
Credit-focused monitoring proves particularly valuable because credit damage affects long-term financial health (loan rates, rental applications, employment). Early detection of credit fraud enables intervention before damage compounds.
Criminal Records Monitoring Specifics
Criminal identity theft—where your identity is used to commit actual crimes—represents one of the most serious identity theft scenarios. Detection is particularly challenging because information flows through law enforcement databases not typically monitored by consumers.
Nord Protect's criminal records monitoring (Platinum tier) watches these databases for records associated with your identifying information. When matches appear, alerts notify you to investigate and potentially clear your name through law enforcement processes.
This monitoring provides unique value because few individuals have independent access to comprehensive criminal records databases. The monitoring service essentially provides access to information that would be difficult and time-consuming to obtain independently.
Loan Monitoring and Financial Fraud Detection
Short-term loan monitoring (Platinum tier) specifically watches for payday loans, title loans, and other predatory lending products opened using your identity. These represent particularly exploitative fraud vectors because perpetrators access funds immediately while establishing substantial debt in your name.
Fast detection enables intervention before loans are fully disbursed or before multiple fraudulent loans compound. Combining this monitoring with actual credit freezes (preventing unauthorized applications entirely) provides comprehensive short-term loan fraud protection.

Estimated data shows that NordProtect lacks both password management and antivirus features, unlike its competitors. This highlights a significant gap in its security offerings.
Nord Protect Versus Do-It-Yourself Monitoring
What You Can Accomplish Independently
Consumers have options for identity protection without subscribing to bundled services:
- Free credit reports: Obtain free annual credit reports through AnnualCreditReport.com, revealing fraudulent accounts in your credit file
- Free credit freezes: Freeze your credit through Equifax, Experian, and TransUnion (cost-free, can be done online)
- Free dark web checks: Use Have I Been Pwned website to check if your email appeared in known breaches
- Bank monitoring: Many banks provide free credit score monitoring and fraud alerts
- Self-monitoring: Manually track your own accounts, credit inquiries, and suspicious activity
These DIY approaches cost nothing but require personal time investment and proactive monitoring behavior. They protect against major fraud vectors but lack the automated, continuous monitoring of bundled services.
The Time-Convenience Trade-Off
The fundamental question: is Nord Protect's cost justified by eliminating manual monitoring effort? For busy individuals lacking time to maintain regular credit monitoring and account checks, the $84-144 annual subscription proves economical. For detail-oriented individuals comfortable with quarterly self-monitoring, DIY approaches prove sufficient.
Consider your personal time value. If you value your time at
Future-Proofing Your Identity Protection
Emerging Threats on the Horizon
Identity protection landscape continues evolving as attackers develop new tactics. Emerging concerns include:
- Deepfake-enabled fraud: AI-generated videos and audio could enable credential-free account takeovers by impersonating you through biometric authentication systems
- Credential stuffing at scale: Attackers testing breached credential combinations against hundreds of services simultaneously
- AI-assisted social engineering: AI-generated phishing emails and scams targeting you with personalized information purchased from data brokers
- Biometric data exploitation: Leaked fingerprint or facial recognition data enabling unauthorized access to biometric-secured systems
Nord Protect's current feature set addresses historical and present threats but may prove less relevant if identity theft tactics shift fundamentally. Services that evolve their monitoring capabilities to address emerging threats will remain effective; those maintaining historical threat focus may become obsolete.
Nord Protect's Evolution Roadmap Expectations
Based on industry trajectory, expect identity protection services to increasingly:
- Incorporate AI analysis: Machine learning identifying fraud patterns and predicting high-risk scenarios
- Expand biometric monitoring: Detecting leaked biometric data and biometric authentication fraud
- Provide deeper dark web intelligence: Moving beyond basic data detection to threat intelligence about who purchased your data and why
- Integrate with financial institutions: Real-time integration with your banks enabling immediate transaction blocking rather than after-the-fact monitoring
- Offer automated remediation: Moving beyond alerts to automatically initiating disputes and remediation processes
Nord Protect's future relevance depends on maintaining pace with these evolving capabilities. Users selecting Nord Protect today should anticipate platform evolution to remain effective against 2026+ threat landscapes.

Making Your Decision: Nord Protect or Alternatives?
Evaluation Framework
Approach the Nord Protect decision systematically using this framework:
-
Inventory existing protections: What security services and practices do you already maintain? List VPN subscriptions, credit monitoring, password managers, antivirus software.
-
Identify redundancies: Which Nord Protect components duplicate services you already have? Estimate the cost of redundant components you'd be paying for.
-
Assess unmet needs: What identity protection components do you currently lack? Prioritize based on personal risk level and perceived threat vectors.
-
Calculate true cost: What's the net cost of Nord Protect after eliminating redundancies versus your current security spending?
-
Evaluate convenience value: How much would eliminating multiple vendor relationships and logins improve your security practices? Would unified monitoring increase likelihood of actually paying attention to alerts?
-
Consider insurance value: How much peace-of-mind does bundled insurance provide? Would you be willing to pay extra for financial protection beyond monitoring?
Working through this framework objectively reveals whether Nord Protect represents genuine value addition versus unnecessary bundle of redundant services.
Implementation Timeline
If you decide Nord Protect makes sense:
- Week 1: Review credit reports (AnnualCreditReport.com), establish credit freezes through bureaus, select annual plan
- Week 2: Create Nord Protect account, submit information, enable multi-factor authentication
- Week 3: Allow monitoring systems to fully activate (24-48 hour processing), review initial breach alerts
- Week 4-8: Integrate Nord VPN into your routine, address any alerts surfaced, establish routine weekly dashboard check-in habit
- Ongoing: Monthly dashboard reviews, prompt response to alerts, annual subscription renewal evaluation
The Broader Identity Protection Ecosystem
How Nord Protect Fits Into Comprehensive Security
Identity protection represents one layer of comprehensive personal cybersecurity strategy. Effective protection requires layered approaches addressing multiple threat vectors:
- Network-level protection: VPN services (Nord Protect Gold/Platinum includes Nord VPN)
- Device-level protection: Antivirus and malware detection (not included in Nord Protect)
- Credential protection: Password managers (not included in Nord Protect)
- Authentication hardening: Multi-factor authentication on important accounts (Nord Protect doesn't provide)
- Data breach monitoring: Dark web and credit monitoring (Nord Protect's core strength)
- Financial protection: Insurance coverage (Nord Protect provides)
- Proactive data removal: Data broker removal (Platinum tier includes Incogni)
- Personal practices: Strong passwords, phishing awareness, careful credential handling
Nord Protect excels at data breach monitoring and provides financial protection but represents incomplete comprehensive security. Users need complementary layers for complete protection.
The Professional Perspective
Cybersecurity professionals acknowledge that no service prevents all identity theft. The most effective approach combines:
- Prevention: Reducing exposure through practices like credit freezes, minimizing data sharing, strong authentication
- Detection: Monitoring for compromise through services like Nord Protect
- Response: Rapid intervention when threats are detected
- Insurance: Financial protection for unavoidable residual losses
Nord Protect contributes primarily to the detection and insurance layers. You remain responsible for prevention and response. This distribution of responsibility matters—don't expect Nord Protect alone to eliminate identity theft risk.

FAQ
What exactly is Nord Protect?
Nord Protect is a bundled identity protection service that combines dark web monitoring, credit monitoring, identity theft insurance, and (in higher tiers) Nord VPN access and data broker removal services. Rather than a single standalone application, it's an integrated ecosystem of complementary services unified under one dashboard and billing relationship.
How does Nord Protect's dark web monitoring work?
Dark web monitoring continuously scans known dark web marketplaces and breach databases, searching for your personal information (email addresses, Social Security numbers, phone numbers) in stolen data compilations. When matches are found, Nord Protect alerts you that your information appeared in specific breaches, enabling proactive response.
What are the benefits of Nord Protect compared to DIY monitoring?
Nord Protect provides automated continuous monitoring you don't need to manually perform, unified dashboard consolidating multiple monitoring functions, genuine identity theft insurance, and professional dark web monitoring capabilities beyond typical consumer access. For users lacking time or technical expertise for independent monitoring, Nord Protect provides convenience and comprehensive protection at reasonable cost.
How much does Nord Protect cost and what's the best plan to choose?
Annual pricing runs
What information does Nord Protect need from me during setup?
During initial setup, Nord Protect requests Social Security number, current and previous addresses, email addresses, phone numbers, financial account information, and credit card data. This information enables monitoring for your details appearing in breach databases. Providing complete information enables more comprehensive monitoring, though you can selectively submit information if privacy-concerned.
Does Nord Protect protect me against password reuse attacks?
No, Nord Protect lacks a password manager component. While it monitors for your compromised credentials on the dark web, it doesn't generate or manage unique passwords for you. You'll need separate password manager software (like 1Password or Bitwarden) to prevent password reuse attacks where compromised credentials from one breach enable account takeovers on other services.
How does Nord Protect's identity theft insurance work?
Nord Protect's insurance, underwritten by HSB Specialty Insurance Company, reimburses legitimate losses incurred through identity theft recovery, including fraudulent charges, credit monitoring costs, notarization fees, and time investment in recovery. This differs from prevention insurance—it reimburses losses you experience rather than preventing losses from occurring. Insurance coverage limits and exclusions vary by jurisdiction and plan.
Is Nord Protect mobile-friendly and does it have an app?
Nord Protect is accessible through mobile web browsers but lacks a dedicated mobile application for iOS or Android. The responsive web interface functions acceptably on smartphones but cannot match native app performance, particularly for push notifications alerting you immediately to detected threats rather than only when you check the dashboard.
How does Nord Protect compare to Aura and Norton Lifelock?
Nord Protect (
What happens after I set up Nord Protect—how often do I need to engage with it?
After the initial 20-minute information submission, Nord Protect functions with minimal required engagement. Alerts arrive at manageable frequency (not overwhelming), and you check the dashboard periodically to review alerts and security status. Most users find a monthly dashboard review sufficient for maintaining awareness, though you should respond promptly to urgent alerts requiring immediate action.
Should I combine Nord Protect with other security tools?
Yes, Nord Protect works best as part of a comprehensive security practice including credit freezes (free through credit bureaus), password manager (separate purchase), multi-factor authentication on important accounts, and antivirus software. These complementary tools address threat vectors Nord Protect doesn't cover, creating layered protection addressing multiple attack vectors.
Final Verdict: Is Nord Protect Worth Your Money?
Nord Protect represents a genuinely useful identity protection service that consolidates multiple protective functions into a user-friendly, affordable bundle. For users starting from security basics—lacking existing VPN subscriptions, credit monitoring, or proactive data protection practices—Nord Protect delivers genuine value. The bundled approach eliminates friction from managing multiple vendor relationships while providing unified visibility into your identity protection status.
However, Nord Protect's value calculus changes significantly for security-conscious users who've already implemented foundational protections. Users maintaining credit freezes, active credit monitoring, existing VPN subscriptions, and password managers encounter substantial redundancy. The bundle becomes less economical when you're paying for components you already have.
The decision ultimately hinges on your personal circumstances:
- Subscribe if: You're starting identity protection from scratch, value convenience consolidation, prefer unified dashboards, and already plan to use Nord VPN services.
- Consider alternatives if: You prioritize budget (McAfee Total Protect at $90), want comprehensive security including antivirus (Aura, Norton), need password management bundled, or are technically comfortable assembling your own security stack.
- Skip if: You maintain credit freezes, already have Nord VPN subscriptions, distrust providing comprehensive personal data to security vendors, or primarily use mobile devices (lack of native app problematic).
Nord Protect occupies a reasonable position in the identity protection market—not category-leading in any single feature but providing solid, integrated protection at fair pricing. Its strength lies in practical consolidation rather than technical sophistication. For the target audience of users seeking accessible, hassle-free identity protection bundling, Nord Protect delivers on its promise as described in its marketing.
What Nord Protect cannot do is prevent all identity theft, guarantee complete privacy, or substitute for establishing foundational security practices like credit freezes and strong authentication. Think of Nord Protect as comprehensive insurance and monitoring for identity threats, not immunity from identity risk. When viewed with appropriate expectations—as one important component of broader security practices rather than complete protection—Nord Protect represents sensible investment in personal cybersecurity.
Make your final decision after honestly assessing your current security posture, identifying which threats you're most concerned about, and evaluating whether Nord Protect's specific strengths address your priorities more effectively than alternative approaches.

Key Takeaways
- NordProtect bundles dark web monitoring, credit monitoring, identity theft insurance, and (in higher tiers) NordVPN and data broker removal into unified dashboard
- Annual pricing ($84-144) provides compelling value if you need most bundled components; redundancy reduces appeal for security-conscious users with existing subscriptions
- Insurance component provides genuine financial protection for identity theft losses, not just monitoring services
- Lacks password manager, antivirus, and native mobile app—significant omissions for some use cases
- Ideal for users starting identity protection from scratch; less valuable for those with credit freezes and existing VPN subscriptions
- Gold tier's NordVPN inclusion adds substantial value since NordVPN costs $60-120 independently
- Dark web monitoring provides early warning but isn't real-time and misses threats in private databases
- Initial alert batch can be overwhelming (50+ historical breaches) but requires one-time review and dismissal
- Competitors like Aura and Norton provide broader features; McAfee offers comparable features at lower cost
- Most effective when combined with credit freezes, password managers, and multi-factor authentication across multiple security layers
Related Articles
- NordVPN Complete Plan 70% Off: Full Breakdown [2025]
- NordVPN Review 2025: Speed, Security & Real-World Performance [2025]
- Sapienza University Ransomware Attack: Europe's Largest Cyberincident [2025]
- Are VPNs Legal? Complete Global Guide [2025]
- Conduent Data Breach 2025: What Millions of Americans Need to Know [2026]
- ExpressKeys Password Manager: Complete Guide & Alternatives [2025]




