Introduction: The Quiet Crisis Affecting Millions
In early 2025, one of America's largest government technology contractors suffered a ransomware attack that quietly spiraled into one of the most widespread data breaches in recent U.S. history. The scale of what happened at Conduent is staggering, yet most Americans have never heard the company's name.
Conduent handles the personal and health information of more than 100 million people across America. That's roughly one in three Americans. The company processes government benefits, manages health insurance records, handles child support enforcement, administers welfare programs, and operates behind the scenes in countless government agencies and healthcare systems. When Conduent gets hit, America's most vulnerable populations often suffer first.
The January 2025 ransomware attack that knocked out Conduent's systems for days revealed something troubling: the company didn't know the full scope of what attackers had stolen for months. What started as an estimate of 4 million affected people in Texas has since grown to 15.4 million. That's roughly half of Texas's entire population. Another 10.5 million people in Oregon were affected. Delaware, Massachusetts, New Hampshire, and dozens of other states have issued notifications. The final number could exceed 50 million Americans.
Here's what makes this particularly unsettling: Conduent wasn't fully transparent about the breach's scope. The company didn't immediately disclose how many people were affected. It took state attorneys general, not the company itself, to piece together the true scale. Even now, months after the initial attack, Conduent won't say if the breach extends to all 100 million people in its systems.
This article breaks down everything you need to understand about the Conduent breach: how it happened, who's affected, what data was stolen, why the company's response was inadequate, and what you should do to protect yourself.
TL; DR
- The breach affected 15.4 million in Texas alone: Initial estimates of 4 million grew to 15.4 million when Texas revealed the true scope
- Over 50 million Americans potentially impacted: Texas, Oregon, Delaware, Massachusetts, New Hampshire, and other states have issued notifications
- Stolen data includes Social Security numbers and health records: The attackers accessed names, SSNs, medical data, and health insurance information
- Conduent handles 100+ million Americans' data: The company processes government benefits, welfare, health insurance, and child support information nationwide
- Slow response and lack of transparency: Conduent took months to analyze the breach and didn't proactively disclose the full scope
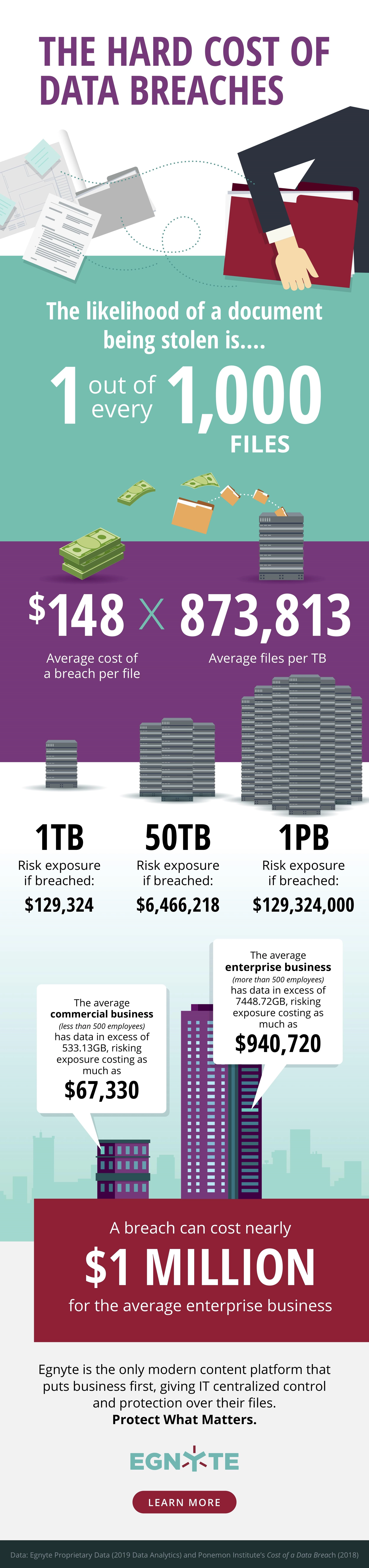
The Conduent data breach affected over 50 million people, with Texas and Oregon being the most impacted states. Estimated data for Delaware, Massachusetts, New Hampshire, and others.
What Is Conduent and Why Does It Matter?
Conduent sounds like a made-up word, which is probably why most Americans don't recognize the name. But understanding what Conduent does is crucial to grasping why this breach is so serious.
Conduent is a government technology and business process services company headquartered in New Jersey. It's one of the largest providers of what's called "back-office" services for government agencies and corporations. Think of it as the invisible infrastructure that keeps government functioning.
The company was spun off from Xerox in 2016 and went public. Today, it's a publicly traded company with revenues exceeding $4 billion annually. It serves federal, state, and local governments, as well as large corporations and healthcare organizations.
What does Conduent actually do? The list is long and touches nearly every American:
Government Benefits and Welfare: Conduent processes benefit claims for food assistance (SNAP), cash assistance programs, and other welfare services across multiple states. When you apply for benefits, there's a good chance a Conduent system is handling your application.
Child Support Enforcement: The company manages child support collection systems in multiple states. If you're paying or receiving child support, Conduent likely tracks those payments.
Medicaid and Healthcare: Conduent processes Medicaid claims, manages health insurance eligibility verification, and handles enrollment for state health programs. This means it touches the healthcare data of tens of millions of low-income and disabled Americans.
Unemployment Benefits: When you file for unemployment, Conduent's systems often process your claim. During the pandemic, as unemployment surged, Conduent's systems handled the surge in claims.
License and Tax Services: Conduent provides services to state motor vehicle departments and tax agencies.
Customer Service: The company operates call centers handling government services for multiple agencies.
In total, Conduent says it serves more than 100 million people across the United States through various government programs and services. This means the company doesn't just handle data for one agency or program—it's woven into the fabric of how American government operates at the state level.
When a company like Conduent gets breached, it's not just a corporate data security problem. It's a government services problem. It affects welfare recipients, unemployed workers, Medicaid beneficiaries, parents managing child support, and countless others who depend on government services.
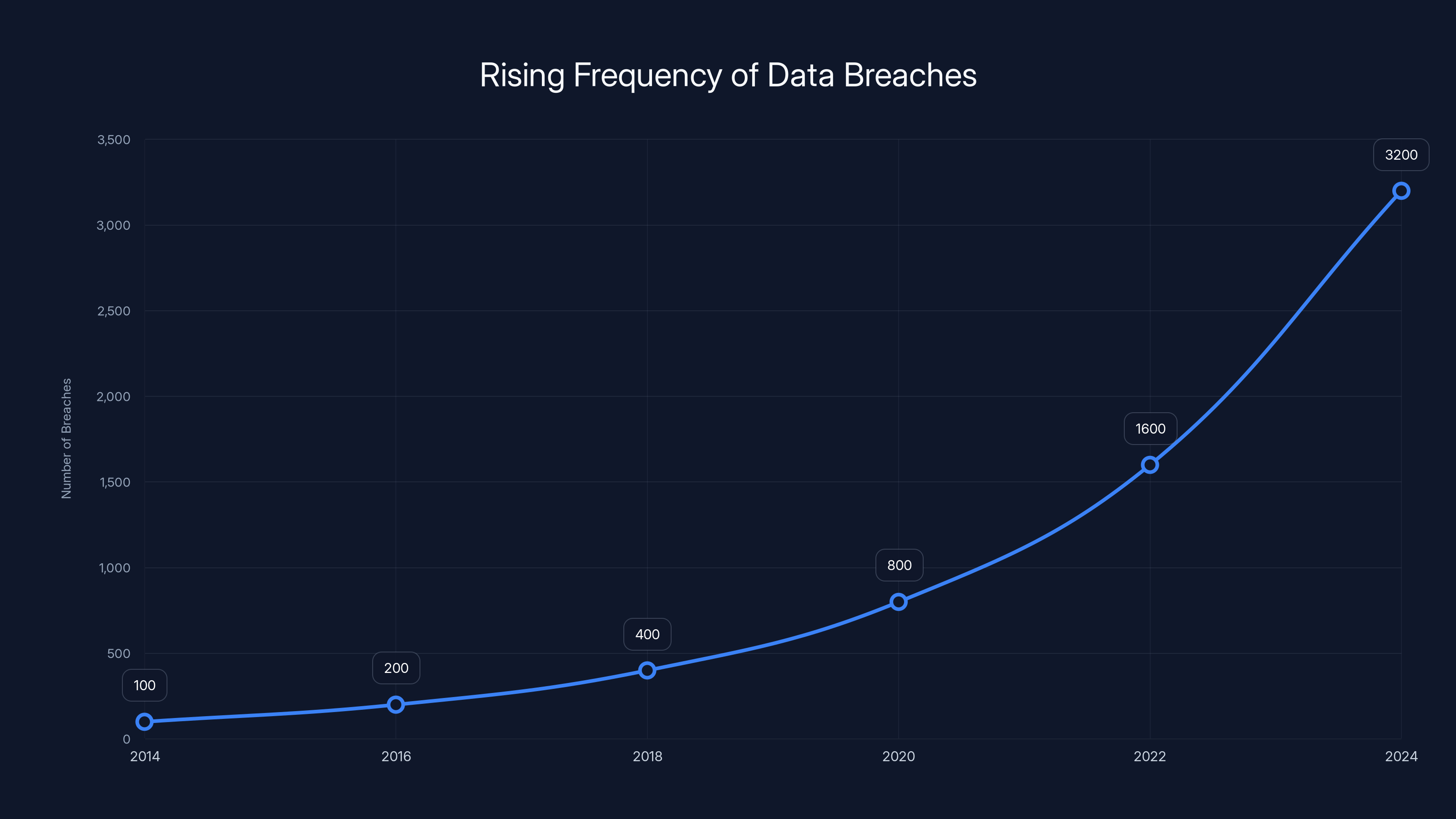
The frequency of data breaches has been increasing exponentially over the past decade, reflecting the growing sophistication and organization of ransomware attacks. (Estimated data)
Timeline: How the Breach Unfolded and What We Know
Understanding the timeline of the Conduent breach reveals a troubling pattern of delayed disclosure and inadequate transparency.
January 2025: The Attack Happens
In January 2025, the ransomware gang known as Safeway attacked Conduent's systems. The attackers encrypted critical systems, knocking Conduent's operations offline for several days. This wasn't a silent breach that went unnoticed—it was aggressive enough to disrupt services.
Government agencies relying on Conduent's systems experienced outages. Benefit processing slowed. Unemployment claims took longer. The company was hit and hit hard.
April 2025: Conduent Announces the Breach
Here's where things get murky. Conduent didn't announce the breach immediately. Instead, the company waited until April to disclose that a cyberattack had occurred. That's roughly three months after the initial attack. For three months, Conduent and affected government agencies said nothing to the public.
When Conduent finally disclosed the breach, the company claimed that the Safeway ransomware gang had stolen approximately 8 terabytes of data. That's a massive amount of information—roughly equivalent to 2 million high-quality photos or hundreds of thousands of documents.
October 2024 (Before April Announcement): First Disclosure
Wait, the timeline gets confusing here. According to available information, Conduent said in October that 4 million people in Texas were affected. But the breach was in January. This suggests there's a significant gap between when Conduent knew about the breach and when it informed the public.
Late 2025 and Early 2026: The Real Numbers Emerge
As state attorneys general investigated and demanded more information from Conduent, the true scope of the breach became clear. Texas revealed that 15.4 million people were affected—not 4 million. Oregon announced 10.5 million affected residents. Delaware, Massachusetts, New Hampshire, and other states issued notifications.
Conduent stated that it would conclude notifying affected individuals by early 2026. That notification process took a year. A year. For a company that was breached, that's an eternity.
Late 2025/Early 2026: Company Statement
When questioned about the breach, Conduent provided vague statements that didn't answer basic questions. The company wouldn't say how many total people were affected. It wouldn't confirm whether the breach touched all 100 million people in its systems. It said it was "conducting a detailed analysis of affected files" to identify stolen personal information—months after the breach occurred.
This timeline reveals a pattern: delayed disclosure, vague statements, and a slow response to understanding the breach's scope.
The Safeway Ransomware Gang: Who Attacked Conduent
The Safeway ransomware gang is responsible for the Conduent attack. Understanding who they are helps explain how serious this breach is.
Ransomware gangs operate like criminal enterprises with specialized roles and operations. Safeway is a moderately well-known group in the ransomware ecosystem. They're not the most notorious—that distinction belongs to groups like Lock Bit or Black Cat—but they're sophisticated enough to target large organizations and pull off significant attacks.
Here's how a typical ransomware attack works:
Initial Access: The attackers gain access to Conduent's network. This could happen through phishing emails to employees, exploitation of unpatched vulnerabilities, compromised credentials purchased on the dark web, or exposed remote access points.
Lateral Movement: Once inside, the attackers move through Conduent's network, escalating privileges and accessing more systems. This phase can take days, weeks, or even months as attackers quietly map out the network.
Data Exfiltration: Before deploying ransomware, attackers copy valuable data to their own servers. This ensures they have leverage even if the company has good backups.
Ransomware Deployment: The attackers then deploy ransomware across systems, encrypting critical files and making them inaccessible. This is when the attack becomes visible.
Extortion: The attackers contact the company and demand a ransom payment. Many modern ransomware gangs use double-extortion: they demand payment and threaten to sell or publish stolen data if the company refuses to pay.
In Conduent's case, Safeway claimed to have stolen over 8 terabytes of data and posted about the breach on their dark web site, confirming they had accessed Conduent's systems.
The fact that Safeway targeted Conduent specifically is telling. The gang doesn't target random companies—they target organizations that:
- Handle valuable data (personal information, health records, financial data)
- Have the ability to pay ransoms (large, well-funded organizations)
- Face pressure to restore services quickly (government contractors, healthcare providers)
Conduent fit all three criteria. A government contractor that handles millions of people's personal data and health information is an attractive target. When services go down, government agencies pressure the company to restore them. This creates urgency, and urgency leads to payment.
While it's unclear if Conduent paid a ransom, the company's resources would make it a target that could afford a substantial payment.
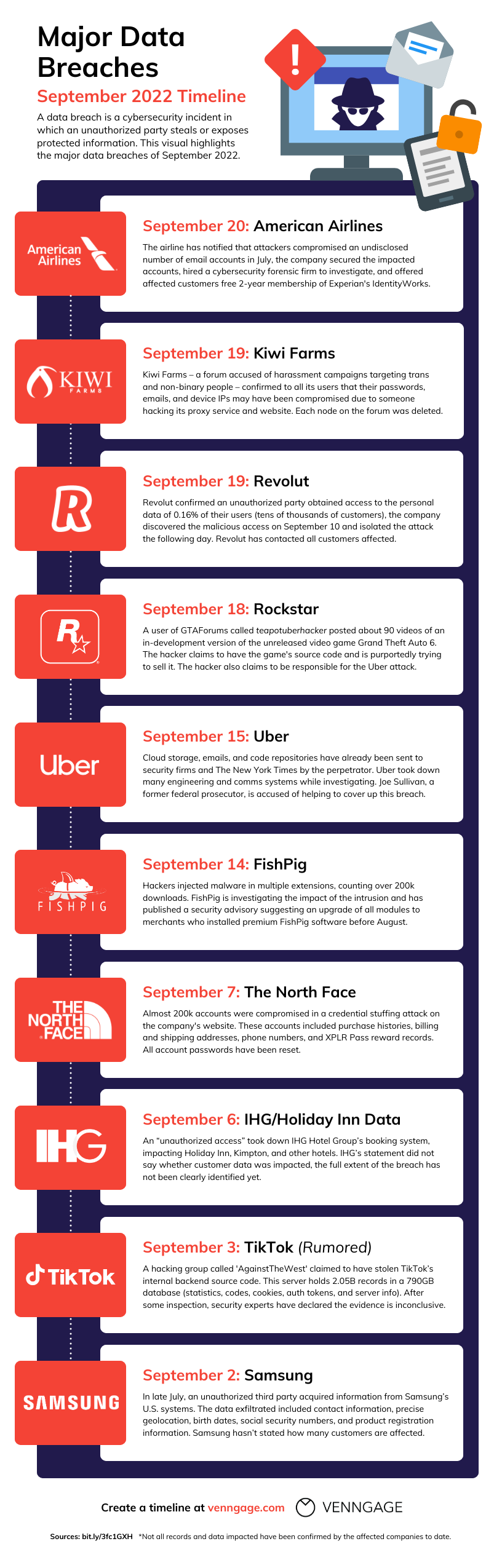
Estimated data distribution shows Health and Medical Information as the largest category, highlighting the potential for healthcare fraud and discrimination. Estimated data.
What Data Did Attackers Steal? A Breakdown
The data stolen from Conduent includes some of the most sensitive personal information that exists. Understanding what was compromised helps you understand your own risk.
Names and Identities
The attackers obtained people's full names. While this might seem basic, when combined with other data points, it enables identity theft and fraud. A criminal with your name and Social Security number can open accounts, apply for loans, or file fraudulent tax returns in your name.
Social Security Numbers
Social Security numbers are the keys to identity theft in America. With your SSN, an attacker can:
- Open credit card accounts in your name
- Take out loans
- File fraudulent tax returns and intercept refunds
- Open utility accounts
- Commit medical fraud
The theft of Social Security numbers is particularly serious because there's no way to change your SSN. Once it's compromised, it remains at risk for identity theft indefinitely.
Health and Medical Information
The breach exposed medical data and health insurance information. This includes:
- Medical diagnoses and treatments
- Prescription information
- Health insurance details
- Medicaid enrollment information
- Claims history
This information can be used for healthcare fraud, but it also exposes people to discrimination. Some people might face discrimination based on their medical conditions if the data becomes public or is used in targeted scams.
Government Benefit Information
Because Conduent processes government benefits, the stolen data includes:
- Welfare and food assistance enrollment
- Unemployment benefit information
- Child support payment information
- Benefit amounts and payment schedules
This data could be used for fraud or to target individuals for scams.
The Scope: 8 Terabytes of Data
When the Safeway gang claimed to have stolen 8 terabytes of data, that's not hyperbole. To put this in perspective:
- 1 terabyte = 1,000 gigabytes
- 8 terabytes = 8,000 gigabytes
- This could represent:
- Approximately 2 million high-quality photos
- About 1.6 million Word documents
- Roughly 40 million average emails
- Or a massive database with millions of complete individual records
Given that Conduent handles 100+ million people's data, 8 terabytes represents a significant but not complete extraction of their systems. However, the 50+ million people notified of the breach suggests the actual scope is enormous.
The Numbers: How Many Americans Are Actually Affected?
Figuring out exactly how many people were affected by the Conduent breach requires piecing together notifications from multiple states because Conduent itself hasn't provided a comprehensive total.
Texas: 15.4 Million
Texas is the largest breach notification to date. The Texas Attorney General revealed that 15.4 million Texas residents had their data exposed in the Conduent breach. This is approximately half of Texas's population.
What makes the Texas number significant is that it contradicts Conduent's earlier claim that 4 million Texans were affected. The initial estimate was off by a factor of nearly 4x. This suggests that Conduent's analysis of the breach was inadequate or that the company was being intentionally vague about the scope.
Oregon: 10.5 Million
Oregon's Attorney General announced that 10.5 million Oregon residents were affected by the Conduent breach. This is notable because Oregon's total population is only about 4.2 million. The discrepancy suggests that the breach includes:
- Current residents
- Former residents
- Records dating back several years
- Potentially people who applied for benefits but weren't ultimately enrolled
Other States
Notifications have been issued in:
- Delaware
- Massachusetts
- New Hampshire
- And other states
While complete numbers aren't available for all states, notifications suggest that every state with government benefit programs processed by Conduent has issued notifications to affected residents.
The Real Total: 50+ Million (Possibly More)
Based on available state notifications, the affected population appears to exceed 50 million Americans. However, the actual number could be significantly higher:
-
Incomplete Notifications: Not all states have issued public notifications or announced specific numbers. Some states may still be in the process of notifying residents.
-
Multiple States Per Person: Some individuals may have applied for benefits in multiple states or moved between states, resulting in their data appearing in multiple state breach notifications. However, even accounting for this, the total affected population is massive.
-
Conduent Won't Disclose Total: The company has refused to state the total number of affected individuals or confirm whether the breach extends to all 100 million people in its systems.
-
Historical Data: Conduent's systems contain years of historical records. People who applied for benefits years ago and are no longer enrolled may still have their data in the system.
To put 50 million in perspective: that's about 1 in 6.5 Americans. For context, the Equifax breach (2017) affected 147 million people, but Equifax is a credit reporting agency with broader scope. The Conduent breach's impact is more concentrated on government services users, but the number is still staggering.

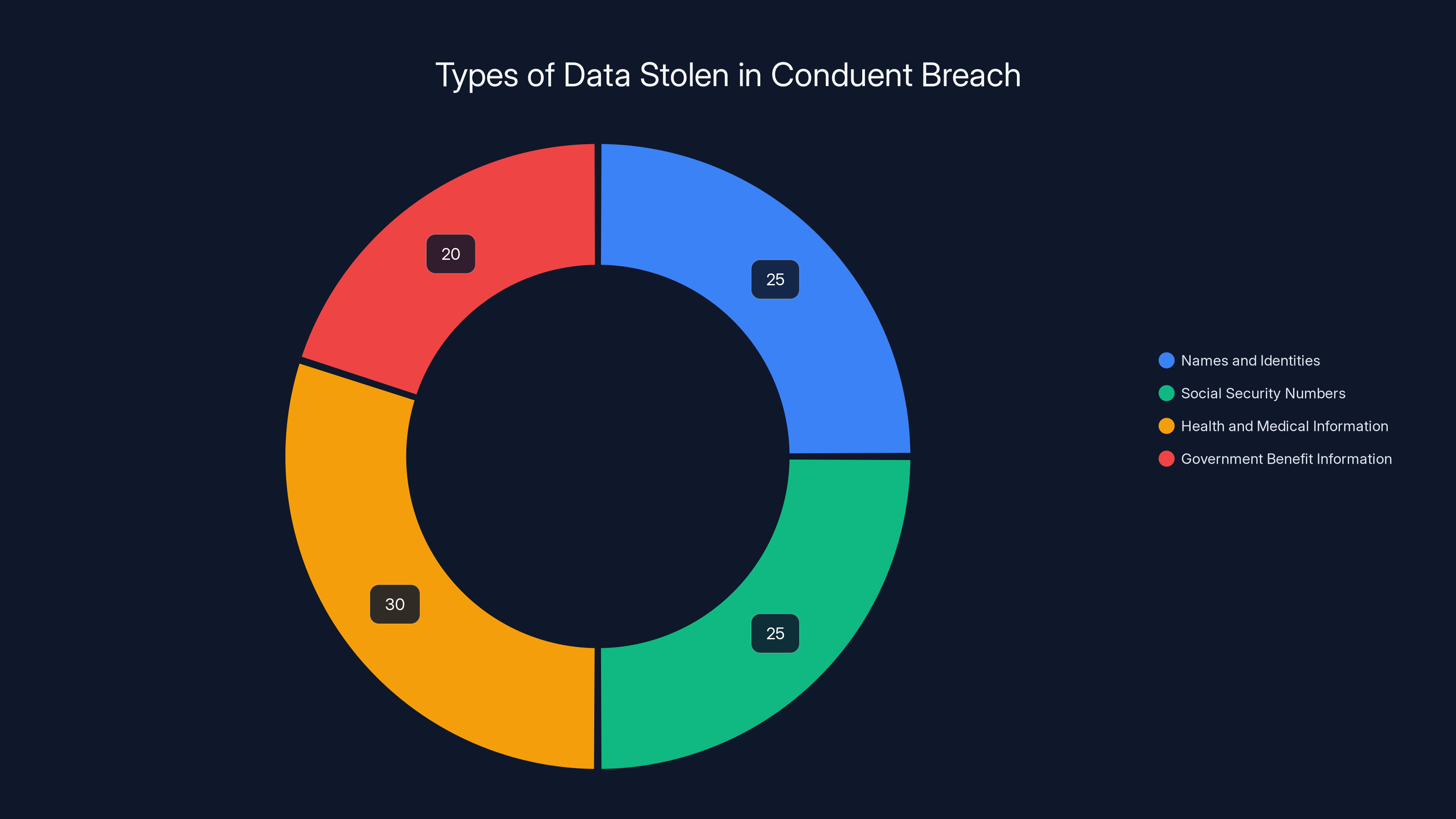
Conduent's response to the breach was inadequate across multiple aspects, with particularly low scores in transparency and estimate accuracy. (Estimated data)
Why Conduent's Response Was Inadequate
Conduent's response to the breach reveals institutional failures that put affected individuals at risk.
Slow Initial Disclosure
Conduent waited three months before publicly announcing the breach. While the company later claimed it was conducting analysis during that period, silence creates problems:
- People didn't know their data was compromised
- They couldn't take preventive measures
- Attackers had time to attempt fraud before victims even knew to monitor for it
Best practices in data breach response call for immediate notification. The longer a company waits, the longer attackers have to exploit the stolen data.
Inaccurate Initial Estimates
When Conduent finally disclosed the breach, it claimed 4 million Texans were affected. That number was wrong by a factor of nearly 4x. This suggests either:
- The company didn't adequately analyze the breach
- The company had incomplete visibility into its own systems
- The company was being deliberately vague
None of these options inspire confidence in the company's security posture or transparency.
Months to Complete Analysis
Conduent stated it was still analyzing the affected files months after the breach. In the modern era, companies have tools to quickly identify what data was accessed. The fact that Conduent took months to provide accurate numbers suggests inadequate security monitoring and forensics capabilities.
Vague Corporate Statements
When questioned about the breach, Conduent provided boilerplate responses that didn't answer direct questions:
- How many people in total are affected?
- Does the breach touch all 100 million people in your systems?
- What specific files were accessed?
- How did the attackers gain initial access?
- Were there security controls that failed?
Instead of answering, Conduent provided generic statements about "conducting detailed analysis." This lack of transparency undermined trust with affected individuals and regulators.
Slow Notification Timeline
Conduent planned to complete notifying affected individuals by early 2026—nearly a year after the breach. During this entire period, affected individuals were at risk without knowing it. Responsible companies prioritize notifying affected individuals quickly.

The Broader Context: Data Breaches Are Becoming Routine
The Conduent breach didn't happen in a vacuum. It reflects broader trends in cybersecurity where large organizations are increasingly vulnerable to ransomware attacks.
Ransomware as a Business Model
In the past decade, ransomware has evolved from opportunistic attacks to a sophisticated criminal business model. Organized gangs operate like corporations with:
- Specialized roles (initial access specialists, lateral movement experts, ransom negotiators)
- Customer service (they actually help victims understand what data was stolen)
- Liability (they guarantee the data is deleted after payment)
- Marketing (they advertise on dark web forums)
This professionalization has made ransomware attacks more effective and more damaging. The Safeway gang that attacked Conduent operates within this professional ecosystem.
Rising Attack Frequency
Data breaches affecting government contractors and healthcare providers are increasing in frequency. These organizations are targeted because they handle sensitive data and have resources to pay ransoms. A government contractor handling millions of people's data is an ideal target.
The Ransomware Ransom Economy
Ransomware gangs demand substantial payments. While we don't know if Conduent paid, comparable attacks have ranged from hundreds of thousands to tens of millions of dollars. The FBI estimates that in 2024 alone, ransomware generated over $1 billion in payments to attackers.
When organizations pay ransoms, they:
- Fund criminal organizations
- Create incentive for future attacks
- Reward the very actors harming their systems
However, organizations also face pressure to pay because restoring systems can be expensive, and downtime can be costly.
Inadequate Security at Many Organizations
Large organizations often have security gaps. Common vulnerabilities that lead to ransomware include:
- Unpatched systems running outdated software
- Weak or reused passwords
- Lack of multi-factor authentication
- Inadequate monitoring of network activity
- Poor security training for employees
- Excessive privileged access
While it's not known how Safeway initially accessed Conduent's systems, these common vulnerabilities likely played a role.

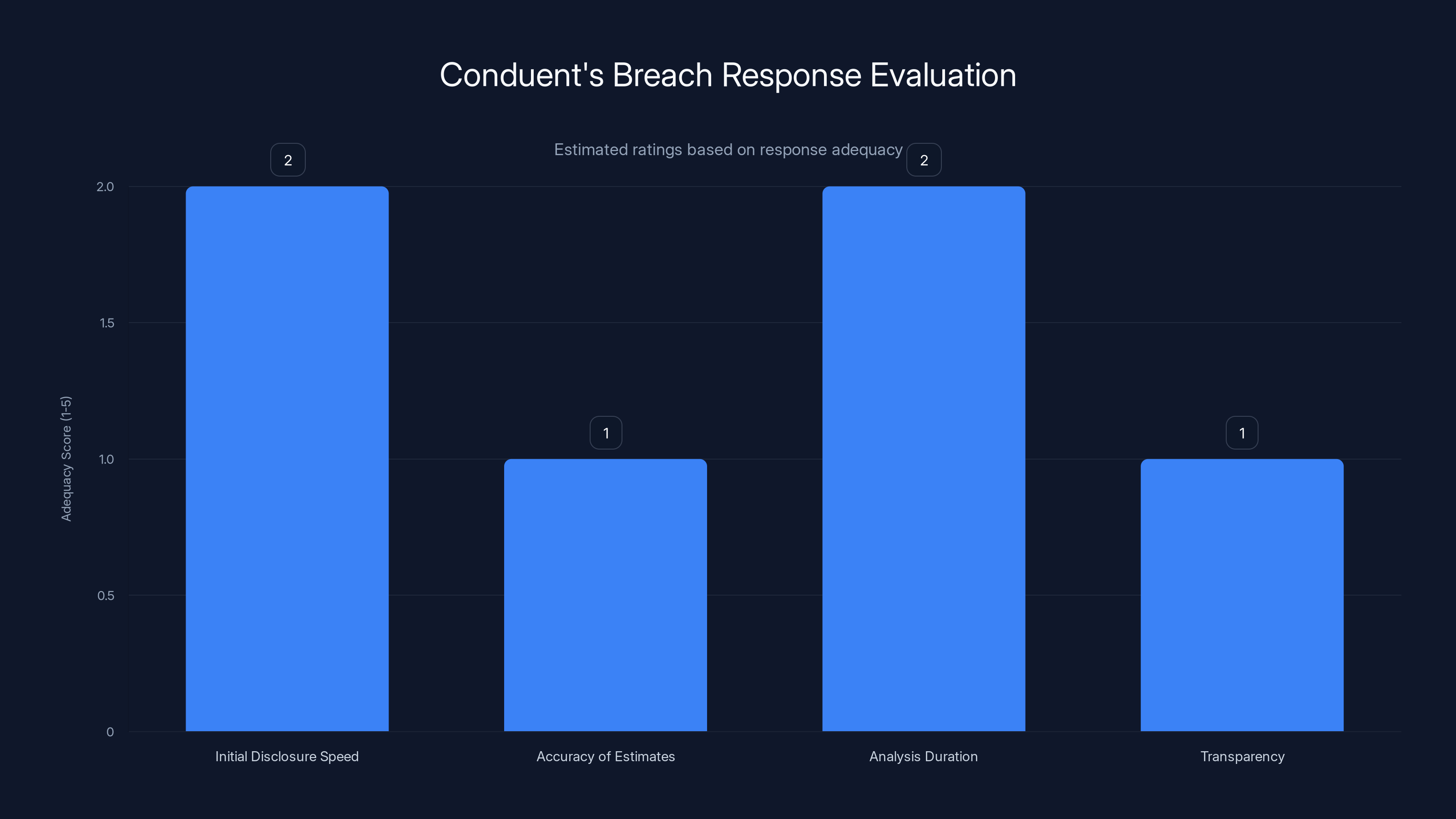
Estimated time required for each step to mitigate risks after a data breach. 'Get Credit Reports' is the most time-consuming step.
Who Is Most Vulnerable to the Consequences?
The Conduent breach doesn't affect all Americans equally. Some groups face heightened risk from the stolen data.
Low-Income and Vulnerable Populations
Conduent processes data for welfare, Medicaid, and unemployment benefits. These programs disproportionately serve:
- Low-income families
- Disabled individuals
- Elderly Americans
- Unemployed workers
These populations often have:
- Lower credit scores (making them less likely to detect fraudulent accounts)
- Less financial literacy about identity theft protection
- Fewer resources to recover from identity theft
- Dependence on government services (making them vulnerable to benefit fraud)
A person on Medicaid who falls victim to identity theft faces double harm: the fraud itself, plus potential disruption to their healthcare benefits if the attacker uses their identity to access services.
Parents in Child Support Systems
Parents with child support cases had their information exposed. This includes:
- Payment information
- Contact details
- Employment information
- Financial details
These individuals could be targeted for fraud or harassment.
People with Medical Conditions
The exposure of medical data puts people with chronic conditions, mental health conditions, or stigmatized medical conditions at risk of discrimination or targeted scams. A criminal knowing someone has diabetes or depression could target them with scams related to those conditions.
Unemployed Workers
People filing for unemployment were already vulnerable during the economic hardship of losing jobs. Having their personal information exposed compounds this vulnerability. They're at risk for:
- Unemployment fraud where attackers file claims in their name
- Identity theft leading to damaged credit
- Targeted scams

What the Stolen Data Enables: Fraud Scenarios
Understanding what criminals can do with stolen data helps you understand your risk.
Identity Theft and Credit Fraud
With a person's name, Social Security number, and date of birth, an attacker can:
- Open new credit card accounts
- Take out personal loans
- Open lines of credit
- Make fraudulent purchases
- Apply for cell phone contracts
The victim doesn't discover this fraud until:
- They check their credit report
- Credit agencies report the fraud
- Debt collectors contact them
- Banks flag unauthorized accounts
By then, significant damage is done.
Medical Identity Theft
With health insurance information and medical records, attackers can:
- File fraudulent medical claims
- Obtain prescription medications
- Access mental health or addiction treatment records
- Receive medical services in the victim's name
This is particularly dangerous because:
- The victim's medical records become corrupted with fraudulent information
- Insurance benefits can be depleted
- The victim might be denied coverage if fraudulent claims hit deductibles
- Medical records contamination can cause healthcare issues
Government Benefit Fraud
With welfare or unemployment information, attackers can:
- File additional benefit claims in the victim's name
- Change address or payment information
- Increase benefit amounts
- Redirect benefit payments to attacker accounts
This harms both the victim (who may face investigation for fraud) and government programs (which lose funding to fraudulent claims).
Tax Refund Fraud
With a Social Security number, attackers can file fraudulent tax returns claiming refunds. The IRS processes millions of returns and catches most fraud, but some slip through, with refunds being diverted to attacker accounts.
Targeted Phishing and Scams
Attackers with stolen personal information can conduct highly targeted phishing attacks:
- "Your [specific agency name] account was compromised, please verify your information"
- "Your [specific health insurance company] benefits need reauthorization"
- "We detected fraud on your [specific bank name] account"
These targeted attacks have much higher success rates than generic phishing because they include real details about the victim.

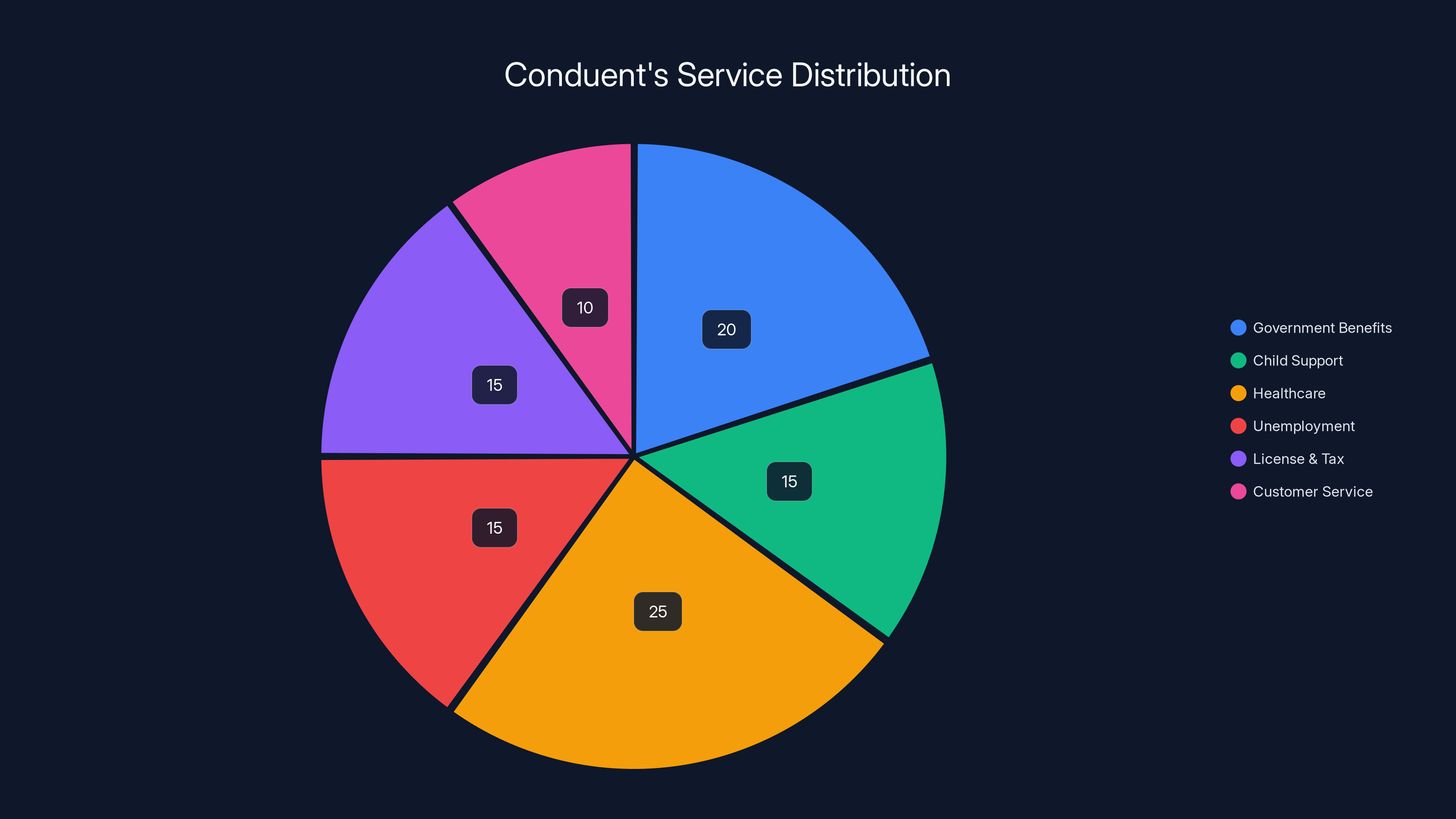
Conduent's services are broadly distributed across various sectors, with healthcare and government benefits being the largest areas. Estimated data.
What You Should Do If You're Affected
If you believe your data was exposed in the Conduent breach, here are concrete steps to take.
Step 1: Check If You're Affected
Determine if you're in one of the affected states. Check your state attorney general's website or the Conduent notification page for official confirmation. Don't rely on rumors or unsourced lists.
Step 2: Enroll in Credit Monitoring
When notification is issued, Conduent should offer free credit monitoring. If offered, enroll immediately. Credit monitoring services alert you if:
- New accounts are opened in your name
- Inquiries are made into your credit
- Your credit file is accessed
- Your credit score changes significantly
Step 3: Place a Fraud Alert
Contact the three major credit bureaus (Equifax, Experian, Trans Union) and place a fraud alert. A fraud alert requires creditors to verify your identity before opening new accounts. This is free and takes 5 minutes per bureau.
Step 4: Consider a Credit Freeze
A credit freeze prevents anyone (including you) from accessing your credit file without a unique PIN. This is the most aggressive identity theft protection. It's free in most states and can be placed online. Note that a freeze means you'll need to unfreeze your credit to open new accounts yourself, which takes a few days.
Step 5: Get Your Credit Reports
Visit annualcreditreport.com and get free copies of your credit reports from all three bureaus. Review them for:
- Accounts you don't recognize
- Inquiries from creditors you didn't contact
- Address changes you didn't make
- Incorrect payment history
If you find fraud, dispute it immediately with the bureau and the creditor.
Step 6: Monitor Your Health Insurance
If your health insurance information was exposed, monitor your accounts for:
- Unexpected claims
- Bills for services you didn't receive
- Denial of coverage due to overused benefits
- Changes to your coverage details
Contact your insurance provider immediately if something seems wrong.
Step 7: Monitor Government Benefits
If you receive government benefits:
- Log into your accounts regularly
- Check that payment amounts are correct
- Verify payment methods haven't changed
- Report any suspicious activity to the benefits agency
Step 8: Set Up Fraud Alerts on Financial Accounts
Call your bank and set up fraud alerts on your checking and savings accounts. Many banks offer free monitoring services. Opt into them.
Step 9: Be Suspicious of Unsolicited Contact
After a breach, you may receive:
- Phishing emails pretending to be from Conduent
- Fake credit monitoring offers
- Scams exploiting the breach
Be skeptical of unsolicited contact. Verify directly through official channels before clicking links or providing information.
Step 10: Document Everything
Keep records of:
- When you placed fraud alerts
- Credit monitoring enrollment details
- Any fraudulent accounts discovered
- Disputes filed with credit bureaus
- Communication with financial institutions
These records help if you need to dispute fraud claims.

Regulatory and Legal Implications
The Conduent breach has significant regulatory and legal consequences.
State Attorney General Investigations
State attorneys general have investigated Conduent's response to the breach. Key areas of focus likely include:
- Why notification took months
- Why initial numbers were so inaccurate
- Whether Conduent had adequate security controls
- Whether the company violated state data breach notification laws
Potential Regulatory Penalties
Conduent could face:
- Fines from state attorneys general for violations of data breach notification laws
- Requirements to implement additional security measures
- Mandatory security audits
- Restrictions on handling certain types of sensitive data
Class Action Lawsuits
Affected individuals or groups could file class action lawsuits against Conduent. These lawsuits might claim:
- Negligent security practices
- Failure to notify promptly
- Economic damages from fraud
- Emotional distress
- Cost of credit monitoring
Class action lawsuits against major corporations for data breaches typically result in settlements ranging from millions to tens of millions of dollars.
Government Contract Implications
Conduent's government contracts could be affected. Agencies may:
- Demand security improvements
- Reduce future contract awards
- Terminate contracts
- Impose penalties for the breach
For a company that depends on government contracts, this is a significant concern.
Lessons for Organizations: What Should Have Been Different
The Conduent breach reveals security and business practice failures. Here's what should have been different.
Robust Network Segmentation
Organizations should segment their networks so that compromised systems don't grant attackers access to all data. If Conduent had properly segmented its network by function (benefits processing separate from health data, for example), attackers couldn't have exfiltrated all data types simultaneously.
Continuous Security Monitoring
Conduent should have had continuous monitoring for:
- Unusual data access patterns
- Lateral movement through the network
- Large data transfers to unauthorized locations
- Unauthorized access to sensitive systems
Modern security tools can detect these activities. If Conduent had this monitoring, the breach might have been detected before 8 terabytes of data was exfiltrated.
Faster Incident Response
When ransomware is detected, organizations should:
- Immediately isolate affected systems
- Begin forensics investigation
- Notify relevant parties
- Communicate transparently
Conduent's three-month delay before announcing the breach is indefensible.
Comprehensive Backup Strategy
A good backup strategy allows organizations to restore systems without paying ransoms and without negotiating with attackers. Conduent's recovery process appears to have been slow, suggesting inadequate backups.
Multi-Factor Authentication
Multi-factor authentication (requiring passwords plus a second factor like a code from a phone) prevents attackers from using compromised credentials to access systems. Widespread MFA would have slowed the attackers' lateral movement.
Regular Security Audits
Third-party security audits identify vulnerabilities before attackers do. Conduent doesn't appear to have discovered and fixed the vulnerabilities that led to the breach, suggesting inadequate audits.
Transparent Communication
When breaches happen, transparent communication is essential. Conduent provided vague statements and inaccurate numbers. Transparency would have been:
- What we know was compromised
- What we're still analyzing
- When we'll have complete information
- What affected individuals should do

The Broader Government Technology Security Crisis
The Conduent breach highlights a systemic problem: government technology infrastructure is aging, underfunded, and insecure.
Legacy Systems
Many government agencies run on legacy systems from the 1990s and 2000s. These systems:
- Lack modern security features
- Run outdated software with known vulnerabilities
- Can't easily be patched
- Weren't designed for modern threats
Conduent likely manages some government systems that fall into this category.
Underfunded Cybersecurity
Government agencies often underfund cybersecurity. When budgets are tight, security is cut. This creates the vulnerabilities that attackers exploit.
Centralized Contractor Model
Government increasingly outsources critical functions to contractors like Conduent. This creates concentration of risk: when one contractor is breached, millions of people are affected. A better model would distribute systems across multiple providers or bring critical systems in-house.
Lack of Accountability
When government technology fails, accountability is often unclear. Is it the agency's fault? The contractor's fault? The vendor's fault? Without clear accountability, problems persist.
Looking Forward: Will Things Change?
After a major breach, people often ask: will this force change in how companies handle security?
Historically, the answer is disappointing. After major breaches like Equifax (2017) or Yahoo (2013), companies did implement some improvements. But systemic security remained inadequate. The pattern is:
- Breach occurs
- Lawsuits and regulatory fines follow
- Company pays settlements
- Security is modestly improved
- Companies revert to cutting security spending when attention fades
- Another breach occurs
The Conduent breach may force some change:
- Government agencies may audit their contracts with Conduent
- Agencies may diversify contractors to reduce concentration of risk
- Regulators may mandate specific security controls for government contractors
- Congress may pass legislation requiring government technology security standards
But these changes take time and require sustained political will.

Conclusion: The Vulnerable Meet the Inadequate
The Conduent breach represents a troubling convergence: vulnerable populations whose data is essential to government services meeting a contractor that failed to protect that data adequately.
What Happened
The Safeway ransomware gang breached Conduent's systems in January 2025, stealing approximately 8 terabytes of data including names, Social Security numbers, health information, and government benefit details. Initial disclosures claimed 4 million Texans were affected. Months later, the true number was revealed to be 15.4 million in Texas alone, plus 10.5 million in Oregon and millions more in other states. The total affected population likely exceeds 50 million Americans.
Why It Matters
Conduent handles personal and health data for over 100 million Americans through government benefit programs. When Conduent is breached, recipients of welfare, Medicaid, unemployment benefits, and child support services lose control of their most sensitive information. These populations are often the most vulnerable to identity theft and fraud.
What Went Wrong
Conduent's response was inadequate at every stage: slow initial disclosure, inaccurate initial numbers, vague corporate communications, months-long analysis period, and slow notification timeline. The breach suggests security vulnerabilities that should have been discovered and fixed. The company's handling of the breach may have made things worse by delaying victim notification and not being transparent about scope.
What You Should Do
If you're affected, place fraud alerts, get credit monitoring, monitor your accounts, and stay vigilant for fraud attempts. The stolen data will enable criminals for years. Your risk isn't limited to the first year after the breach—it persists indefinitely.
The Bigger Picture
The Conduent breach is not an isolated incident. It reflects systemic problems in how government technology is structured, how government contractors handle security, and how data breaches are regulated. After each major breach, we see modest improvements followed by reversion to inadequate security. Meaningful change requires sustained regulatory pressure and government investment in modern, secure technology infrastructure.
For now, the 50+ million affected by the Conduent breach must take personal responsibility for protecting themselves—not because they did anything wrong, but because the systems entrusted with their data failed them.
FAQ
What is the Conduent data breach?
The Conduent data breach occurred in January 2025 when the Safeway ransomware gang attacked the government technology contractor's systems, stealing approximately 8 terabytes of data including names, Social Security numbers, medical records, and government benefit information. The breach was announced months later and affected millions of Americans across multiple states, with current estimates suggesting over 50 million people were impacted.
How many people were affected by the Conduent breach?
The confirmed numbers show 15.4 million people in Texas and 10.5 million in Oregon, with additional millions affected in Delaware, Massachusetts, New Hampshire, and other states. The total affected population likely exceeds 50 million Americans. Conduent has declined to disclose the total number or confirm whether the breach extends to all 100 million people in its systems.
What data was stolen in the Conduent breach?
The stolen data includes names, Social Security numbers, health and medical information, health insurance details, and government benefit information including welfare, Medicaid, unemployment, and child support data. The Safeway gang claimed to have stolen over 8 terabytes of data from Conduent's systems, representing a massive extraction of sensitive personal information.
Why did Conduent's response take so long?
Conduent announced the breach three months after it occurred in January, and initially provided inaccurate numbers claiming only 4 million Texans were affected when the actual number was 15.4 million. The company said it was conducting analysis of affected files during this period, but the slow response meant victims didn't know their data was compromised and couldn't take protective measures. Conduent also took until early 2026 to complete notifying affected individuals.
What should I do if my data was exposed in the Conduent breach?
Immediate steps include placing a fraud alert with credit bureaus, enrolling in any offered credit monitoring, getting your free credit reports to check for fraud, considering a credit freeze, monitoring your health insurance and government benefit accounts, setting up fraud alerts on financial accounts, and remaining vigilant for phishing and fraud attempts. These steps should be taken even if you haven't yet received formal notification from Conduent or your state.
Who is most vulnerable to the consequences of the Conduent breach?
Vulnerable populations include recipients of government benefits (welfare, Medicaid, unemployment, child support), people with medical conditions or disabilities, low-income individuals with limited resources to recover from identity theft, and those with limited financial literacy about identity theft protection. These groups often have lower credit scores, making them less likely to detect fraudulent accounts, and face greater consequences from benefit or healthcare fraud.
What is Conduent and why does it handle so much personal data?
Conduent is a government technology and business process services company that provides back-office services for government agencies and large corporations. It processes data for welfare programs, Medicaid, unemployment benefits, child support enforcement, and other government services. The company was spun off from Xerox in 2016 and serves over 100 million Americans through various government programs and state agencies.
What is ransomware and how did the Safeway gang use it against Conduent?
Ransomware is malicious software that encrypts an organization's files, making them inaccessible until a ransom is paid. The Safeway ransomware gang used a double-extortion model: they encrypted Conduent's critical systems (disrupting services) while also exfiltrating data to use as leverage. They threatened to sell or publish the stolen data if Conduent didn't pay the ransom, combining operational pressure with financial threats.
Could the Conduent breach have been prevented?
Yes, several security practices could have prevented or limited the breach: network segmentation to isolate sensitive data, continuous monitoring to detect unauthorized data access, multi-factor authentication to prevent attackers from using compromised credentials, regular security audits to identify vulnerabilities before attackers do, faster incident response procedures, and comprehensive backup strategies that allow system restoration without paying ransoms.
What are the legal consequences for Conduent?
Conduent could face investigations by state attorneys general, fines for violations of state data breach notification laws, requirements to implement additional security measures, and potential class action lawsuits from affected individuals. These lawsuits might claim negligent security practices, failure to notify promptly, and damages from identity theft and fraud. Additionally, government agencies may audit Conduent's contracts or reduce future business awards.
How long will I be at risk from the Conduent breach?
Your risk persists indefinitely. While identity theft is most common in the months immediately following a breach, criminals use stolen Social Security numbers for years. Health information and government benefit data can also enable fraud for extended periods. This is why ongoing vigilance, credit monitoring, and fraud protection measures are essential for years following a breach like this.
Key Takeaways
- The Conduent breach affected 50+ million Americans, with 15.4 million in Texas and 10.5 million in Oregon confirmed
- Conduent's initial disclosure and numbers were significantly inaccurate, delaying victim protection by months
- Stolen data includes Social Security numbers, health records, and government benefit information enabling multiple fraud types
- Vulnerable populations dependent on government services face heightened identity theft risk from the breach
- Immediate steps like fraud alerts, credit monitoring, and account vigilance are essential for protecting yourself from exploited data
Related Articles
- Harvard and UPenn Data Breaches: What You Need to Know [2025]
- Password Security Guide: Why Strong Credentials Matter in 2025
- 8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]
- Apple Pay Unusual Activity Scam: How to Spot Fake Messages [2025]
- Substack Data Breach [2025]: What Happened & How to Protect Yourself
- ExpressKeys Password Manager: Complete Guide & Alternatives [2025]
![Conduent Data Breach 2025: What Millions of Americans Need to Know [2026]](https://tryrunable.com/blog/conduent-data-breach-2025-what-millions-of-americans-need-to/image-1-1770305984632.jpg)



