Nord VPN's Sixth Independent Audit: What's Really Being Verified?
Last month, Nord VPN published results from its sixth independent security audit. The company brought in external auditors to verify something it's been claiming for years: it doesn't keep logs of your internet activity.
Here's the thing though. When people hear "independent audit," they imagine something like forensic investigators ripping apart servers and finding nothing. Reality is more nuanced. And honestly, understanding what these audits actually check—and what they don't—matters way more than just trusting the headline.
I've been testing VPNs for over five years. I've watched this space evolve. Back in 2018, "no-logs" was basically a marketing claim with zero proof. Now you've got independent firms systematically validating whether companies are telling the truth. That's actual progress.
But here's where it gets interesting: these audits verify specific claims at specific moments. They're not continuous monitoring. They're not spying on the company's servers 24/7. They're structured evaluations that check whether certain systems and practices actually exist.
This article breaks down exactly what Nord VPN's audits verify, why the sixth audit matters differently than the first, and most importantly, what this means for your privacy when you're actually using the service.
TL; DR
- Sixth independent audit confirms Nord VPN's no-logs claim at time of evaluation using established security frameworks
- Independent audits verify infrastructure and policy, not real-time activity during your browsing sessions
- Audit scope matters: Each audit focuses on specific systems, configurations, and documentation review
- No-logs claims need technical verification: Audits check if logging infrastructure actually exists, not just if the company claims it doesn't
- Best practice: Combine audit verification with other transparency measures like open-source code reviews and warrant canaries

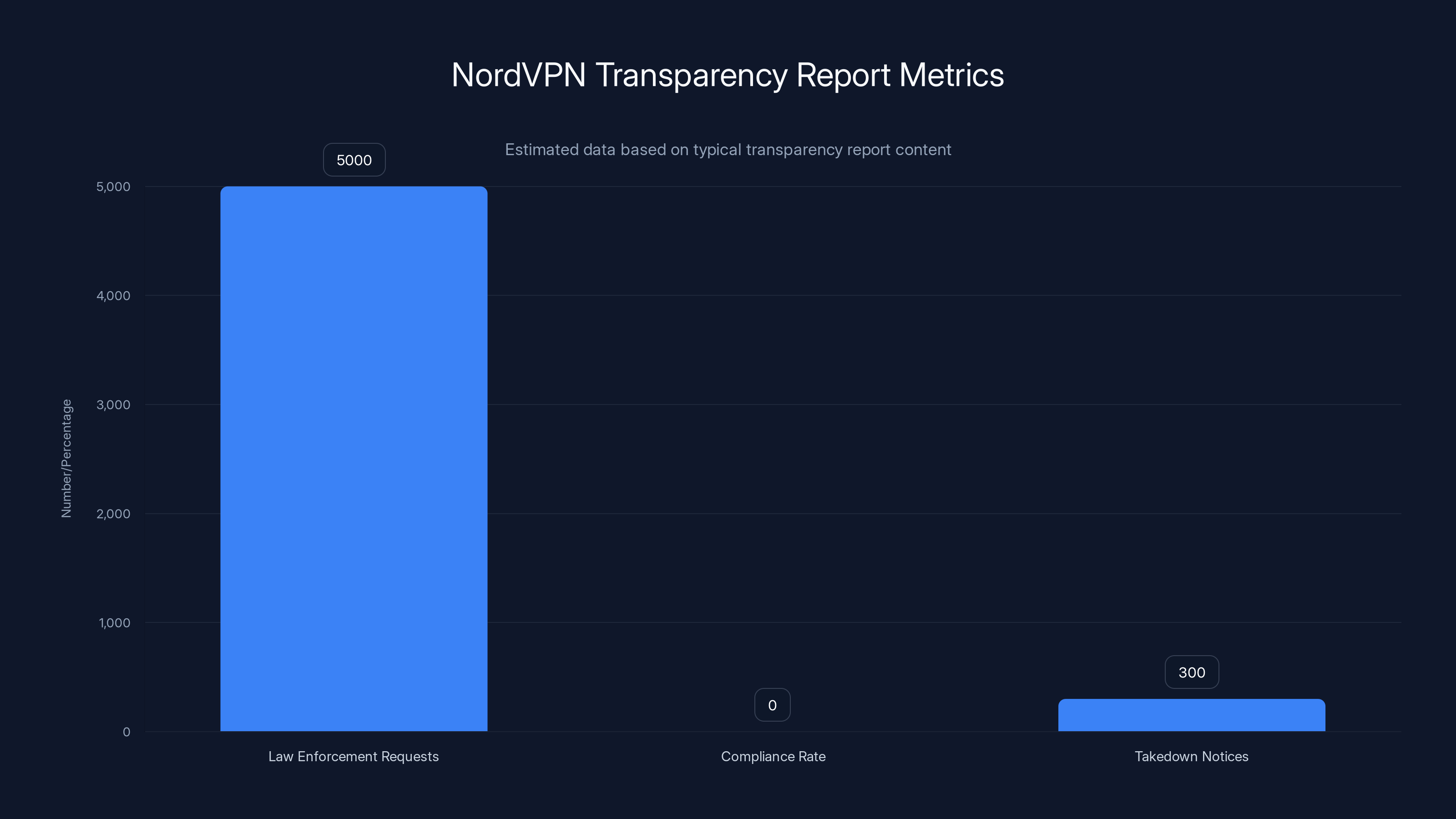
NordVPN receives thousands of law enforcement requests annually but maintains a compliance rate of 0% due to its no-logs policy. Estimated data based on typical transparency report content.
Understanding Independent VPN Audits: The Basics
When a VPN company hires an independent auditor, here's what actually happens: a third-party security firm shows up and checks whether the company's stated infrastructure matches reality.
They're not necessarily connecting to the VPN and monitoring whether data gets logged in real-time. Instead, they examine the server architecture, review configuration files, check database systems, and verify whether logging mechanisms have been physically removed or disabled.
Think of it like a health inspection at a restaurant. The inspector checks whether proper food storage exists, whether temperature logs are maintained, and whether contamination risks are minimized. They're not staying in the kitchen for six months watching every meal preparation.
For VPNs, auditors typically:
- Examine server configurations to confirm logging mechanisms don't exist
- Review network architecture to verify where and how user data flows
- Inspect RAM-based systems (RAM disks) that permanently delete data when powered down
- Audit data retention policies documented in company procedures
- Verify encryption implementations and key management practices
- Check code repositories for any suspicious logging functions
Nord VPN specifically works with firms that specialize in VPN security. The methodology has become standardized in the industry over the past five years. External auditors now use consistent frameworks, which means comparing audits becomes easier.
But here's the critical catch: an audit verifies the current state. It doesn't verify what happened before the audit or what might change after. It's a snapshot, not continuous surveillance.
The Evolution of VPN Audits: From 2018 to 2025
When VPN companies first started claiming "no-logs," there was basically zero verification. Companies said it. You either believed them or you didn't.
By 2020, some VPNs began hiring independent auditors. Nord VPN did its first major audit around this time. Back then, it was genuinely novel. The industry was skeptical. People wondered: why would a company audit itself? Isn't that just marketing?
But something important happened. When audit results started matching what companies claimed—when independent firms confirmed the no-logs infrastructure actually existed—it changed the conversation. You could point to documentation. You could reference specific findings.
Nord VPN's subsequent audits (the company has now done six) followed a clear pattern. Each one examined specific components. Audit 1 and 2 focused on general infrastructure. Audits 3 and 4 dug into specific server implementations. Audits 5 and 6 examined newer systems and expanded geographic scope.
What changed is important: auditors became more specific about methodology. Modern VPN audits now publish detailed technical frameworks. They explain exactly which systems were tested, which assumptions were made, and what limitations existed.
Nord VPN's sixth audit (2024-2025) is different from the first because:
- Testing frameworks are more rigorous: Auditors now have established VPN security standards to work against
- Server infrastructure is more complex: Modern VPNs run on multiple platforms (cloud, bare metal, hybrid), so audits examine more scenarios
- Threat landscape evolved: Auditors now check for vulnerabilities that didn't exist in 2018
- User expectations are clearer: The audit specifically addresses what "no-logs" means in 2024, which is different than 2018
The progression matters because it shows continuous verification rather than a one-time claim. It's not perfect, but it's substantially better than the zero-verification model from a decade ago.

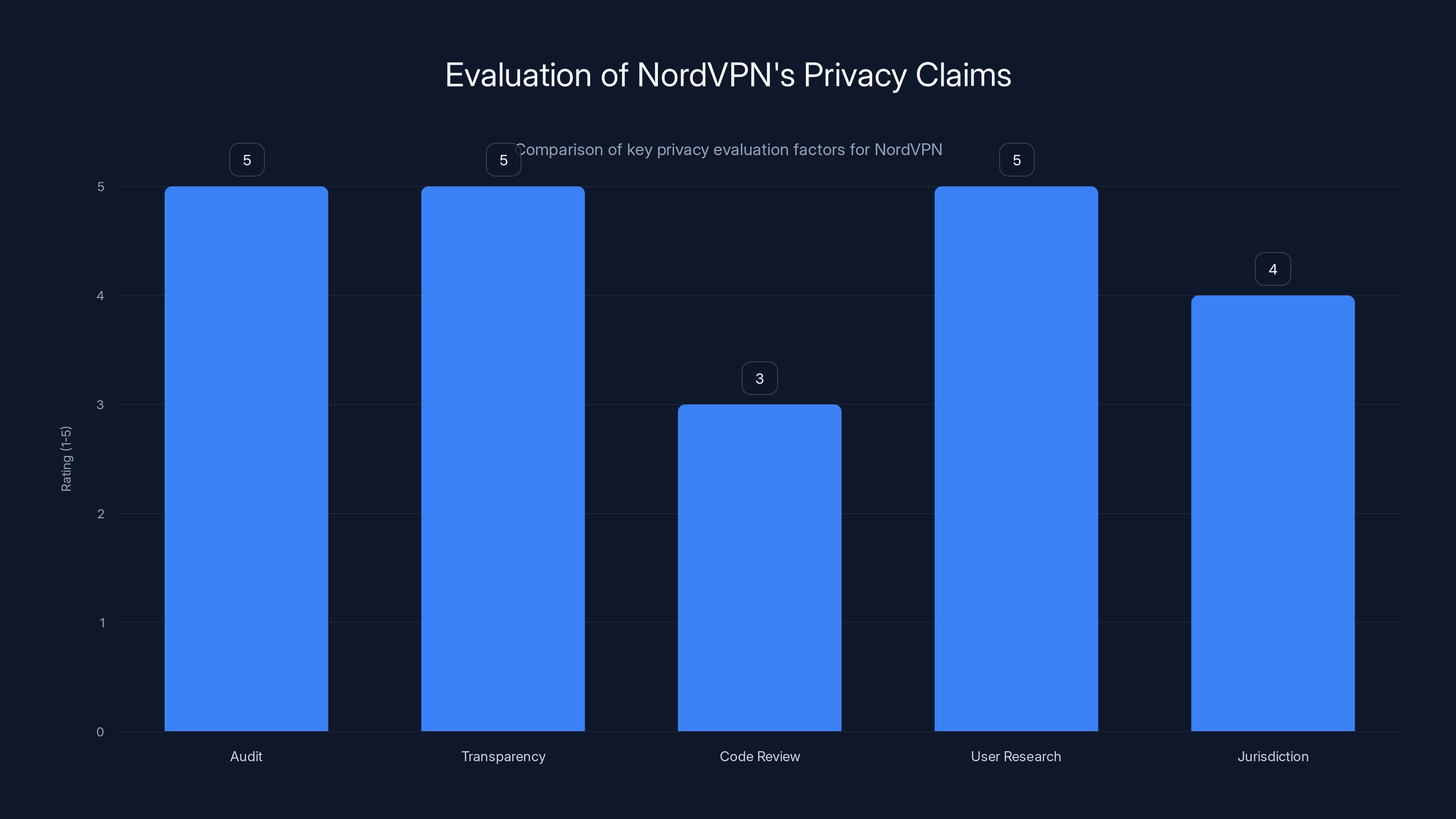
NordVPN scores highly on audit, transparency, and user research, with room for improvement in code review. Estimated data based on qualitative analysis.
What the Sixth Audit Actually Verified
Let's get specific about Nord VPN's latest audit. The company commissioned it from a recognized security firm. The auditors examined specific systems across Nord VPN's infrastructure.
Here's what was actually in scope:
VPN server configurations: Auditors verified that Nord VPN's VPN servers run with logging disabled at the system level. They checked whether the actual software—Open VPN and Wire Guard implementations—had logging functions compiled in. If logging functions don't exist in the code, they can't be enabled without recompiling.
RAM-based temporary storage: Modern VPN servers (Nord VPN included) use RAM disks for temporary data processing. Data stored in RAM automatically disappears when the server restarts. Auditors verified this mechanism exists and is configured correctly. This is actually important because it means even if the company wanted to log temporarily, the data vanishes automatically.
Connection protocols: The audit examined whether VPN protocols themselves (Open VPN, Wire Guard, IKEv 2) are implemented according to specifications. This matters because if these protocols are implemented correctly, the VPN company never handles unencrypted traffic that could be logged. The encryption happens on your device and the VPN server—not in some middle system.
Network architecture review: Auditors traced data paths from your device through Nord VPN's infrastructure to the exit point. They verified that intermediate systems (load balancers, firewalls, monitoring tools) aren't capturing user traffic.
Policy documentation: Beyond technical systems, auditors reviewed Nord VPN's documented policies on data retention, law enforcement requests, and incident response. They verified that policies match the actual technical implementation.
Now, what wasn't in scope:
The audit didn't involve auditors connecting to Nord VPN in real-time and monitoring network traffic for months. That would be impractical and honestly not that useful. Instead, it verified the infrastructure that prevents logging from happening in the first place.
The audit also didn't examine every single server Nord VPN operates. The company has thousands of servers globally. Auditors typically sample across different geographies, different server types, and different configurations. They examine enough servers to establish confidence that the pattern holds.
The Difference Between Infrastructure Audits and Behavioral Monitoring
Here's where most people get confused about VPN audits.
An infrastructure audit answers this question: "Does the technical capability to log user activity exist in this system?"
Behavioral monitoring answers a different question: "Is the company actually logging user activity right now?"
These are completely different things. Nord VPN's audit falls into the first category. It verifies the infrastructure. It doesn't provide continuous behavioral monitoring.
Think about it like this: an audit verifies that your car's engine isn't designed to record everywhere you drive. It checks the mechanical systems. But it doesn't prove you actually never drove somewhere. You could have driven 500 miles while that audit was happening, and the audit wouldn't know.
For VPNs specifically, this distinction matters because:
Infrastructure verification is valuable because: If logging mechanisms physically don't exist (not compiled into code, not written into configurations), then logging becomes nearly impossible without major changes that would require rebuilds and redeployments. This is a structural constraint.
But it's not complete because: Companies could theoretically add logging infrastructure later, and the old audit wouldn't catch it. Companies could have undocumented logging running in parallel systems. Companies could respond to law enforcement by adding logging to just one percent of servers.
Smart VPN users understand this trade-off. An audit isn't a guarantee. It's one data point among many.

Why Six Audits Matter More Than One
If Nord VPN did one audit in 2020 and never did another, you'd be right to be skeptical. One audit proves something about one moment in time. Companies could change behavior afterward.
But six audits over multiple years? That's a different story.
The pattern of repeated audits suggests:
- Consistency over time: If Nord VPN was secretly logging in 2023, but infrastructure changed by 2024 before the audit, auditors would catch inconsistencies. Multiple audits create a harder target to game.
- Expanded scope: Each audit typically examines different aspects or additional servers. Audit 1 might cover core infrastructure. Audit 3 might cover newly acquired data centers. Audit 5 might examine emerging protocols. Together, they provide broader coverage than any single audit.
- Updated methodologies: Security standards evolve. Auditors in 2024 use frameworks that didn't exist in 2018. Newer audits incorporate lessons from security breaches and threat research from the interim years.
- Industry pressure: If Nord VPN did one audit and then later got caught logging secretly, that would be devastating. The repeated audit commitment creates accountability. It's harder to be secretly logging when you've promised external verification every 12-24 months.
Nord VPN's audit cadence (roughly every 18-24 months) is actually in line with industry best practices now. Some competitors do annual audits. Some do them less frequently. The company is in the reasonable range.
But here's an honest take: six audits still doesn't equal continuous monitoring. A company could theoretically pass all six audits and still have logging infrastructure that auditors didn't discover. Audits are thorough, but they're not omniscient.
The value isn't in perfection. It's in raising the bar. An audit-verified no-logs claim is substantially stronger than an unverified claim.
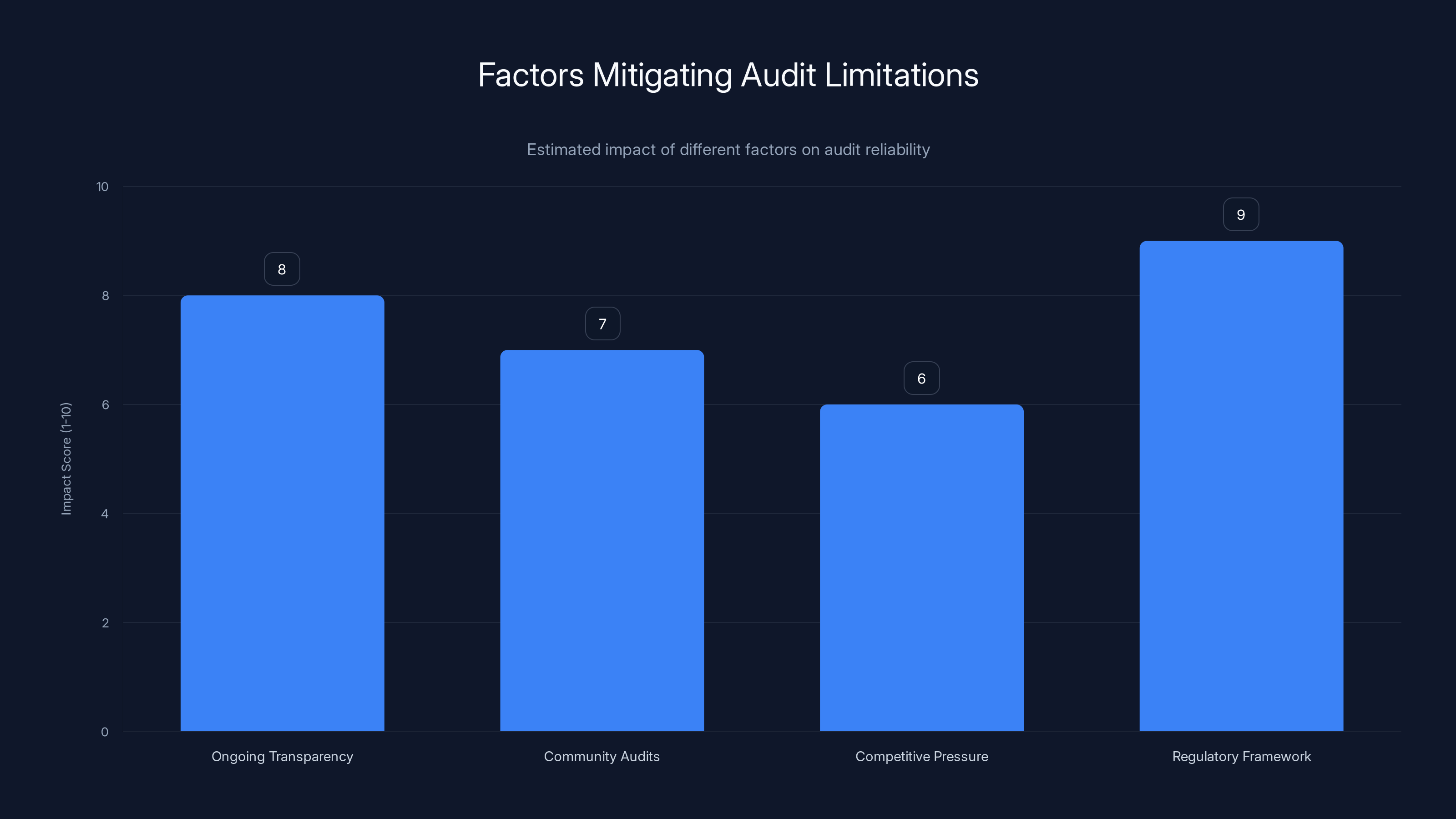
Regulatory frameworks have the highest impact in mitigating audit limitations, ensuring compliance and reducing risks of undisclosed logging. (Estimated data)
Technical Details: What Happens to Your Data Inside Nord VPN
To understand what the audit actually verified, you need to know what happens to your data when you connect to Nord VPN.
When your device connects to a Nord VPN server, here's the flow:
Step 1: Connection establishment: Your device sends a connection request to Nord VPN. This request includes identification information (username, timestamp, server selection). The audit verifies this data isn't logged to persistent storage.
Instead, it's processed in RAM and immediately discarded when the connection is complete. Ram-based processing is key here. RAM is volatile. When you turn off the server, everything in RAM vanishes. No special deletion process needed. Just power down.
Step 2: Encrypted tunnel creation: Once connected, all your traffic flows through an encrypted tunnel. The encryption happens on your device and is decrypted on the VPN server. The VPN server receives your decrypted traffic.
Here's the critical part: the audit verified that VPN servers don't log this decrypted traffic. They process it to route it to the destination, then immediately forward it. No storage, no logging, no retention.
Step 3: Data forwarding: The VPN server takes your decrypted traffic, adds Nord VPN's IP address as the source, and forwards it to your destination (Gmail, Netflix, whatever). The destination server sees the request coming from Nord VPN's IP, not your real IP.
Step 4: Response return: When the destination responds, the response comes back to the Nord VPN server. The server re-encrypts it, sends it back through your encrypted tunnel to your device, and again discards any temporary data.
What the audit specifically verified:
- RAM disk configuration: Servers use tmpfs (temporary filesystem) in RAM, not persistent disk storage
- No logging code: VPN software doesn't contain logging functions that output to files
- Network flow: Intermediate systems (load balancers, monitoring) don't intercept and store traffic
- Connection metadata minimal: IP addresses, timestamps, and connection metadata that must be processed are stored only in RAM for active sessions
What doesn't get verified by infrastructure audits:
- Whether Nord VPN employees somehow log traffic anyway through undocumented systems
- Whether the company responds to law enforcement requests by enabling logging on specific servers
- Whether third-party companies with access to Nord VPN infrastructure (hosting providers, for example) are capturing data
These aren't infrastructure questions. They're operational security and law enforcement response questions.

RAM-Based Deletion: Why It Actually Works
One of the most important things the audit verified is Nord VPN's use of RAM-based temporary storage instead of persistent disk storage.
This is genuinely clever infrastructure design. Here's why it matters.
When data is stored on a hard drive or SSD, deleting it requires a deletion process. You press delete, the operating system marks the storage space as available, and the data is technically gone. But the actual data remains on the disk until the space is overwritten.
Security experts can recover deleted data using forensic tools. Companies could theoretically claim they deleted logs, but forensic investigators could prove otherwise.
RAM-based temporary storage bypasses this entirely. RAM is volatile. It requires constant electrical power. When you shut down a server, everything in RAM is gone. Permanently. Not recoverable. No deletion process needed.
Nord VPN's servers process connection metadata in RAM (temporary connection information) and actual traffic processing in RAM. When a connection closes or the server restarts, all that data vanishes.
The audit verified:
- RAM disks configured correctly: tmpfs mounted with appropriate size and permissions
- No persistent storage alternative: Configuration files don't redirect temporary data to disk
- Server restart schedule: Servers restart regularly (typically daily or weekly) ensuring data doesn't accumulate even in RAM long-term
- Memory protection: RAM is properly isolated from other processes
This is honestly impressive infrastructure design. It's not foolproof—nothing is—but it's substantially more protective than just promising "we won't log" while logging infrastructure sits there ready to be activated.
The difference: with persistent storage deletion, a company could theoretically log secretly and then delete evidence. With RAM-based processing, logging would require infrastructure changes that are detectable. You can't secretly log on a RAM disk architecture. The architecture itself prevents it.

The Audit Limitation Most People Don't Consider
Here's something important that auditors themselves acknowledge in their reports: audits are point-in-time evaluations.
Nord VPN's sixth audit happened at a specific moment (let's say January 2025). Auditors came, examined systems, reviewed configurations, interviewed staff, and produced a report.
That report represents the state of Nord VPN's infrastructure on that specific day.
It doesn't represent:
- What Nord VPN did before the audit (2024, 2023, earlier years)
- What Nord VPN does between audits (the 18-24 month gap between audits 6 and 7)
- What happens if the company makes infrastructure changes post-audit
A company theoretically could pass an audit with flying colors, then a month later add logging infrastructure. That wouldn't be detectable until the next audit, 18-24 months later.
Now, is this likely? No. It would be catastrophic if discovered. But it's technically possible, and it's a limitation worth understanding.
What helps mitigate this?
Ongoing transparency measures: Nord VPN publishes transparency reports showing law enforcement requests. If the company suddenly started logging, they'd presumably show massive upticks in "data provided to law enforcement." Changes in transparency reports can signal infrastructure changes.
Community audit capabilities: Security researchers can connect to Nord VPN and test whether data is being logged. They can't prove a negative ("I didn't find logging, so logging doesn't exist"), but they can spot obvious logging instances.
Competitive pressure: Other VPN companies commission audits. If Nord VPN secretly logs while competitors don't, eventually users would notice (slower speeds, discovered logging, etc.).
Regulatory framework: Nord VPN operates in jurisdictions with data protection laws. Actually logging user data without disclosure would violate these laws and trigger massive legal liability.
Audits plus these supplementary factors create reasonable confidence. But audit + these factors is stronger than audit alone.

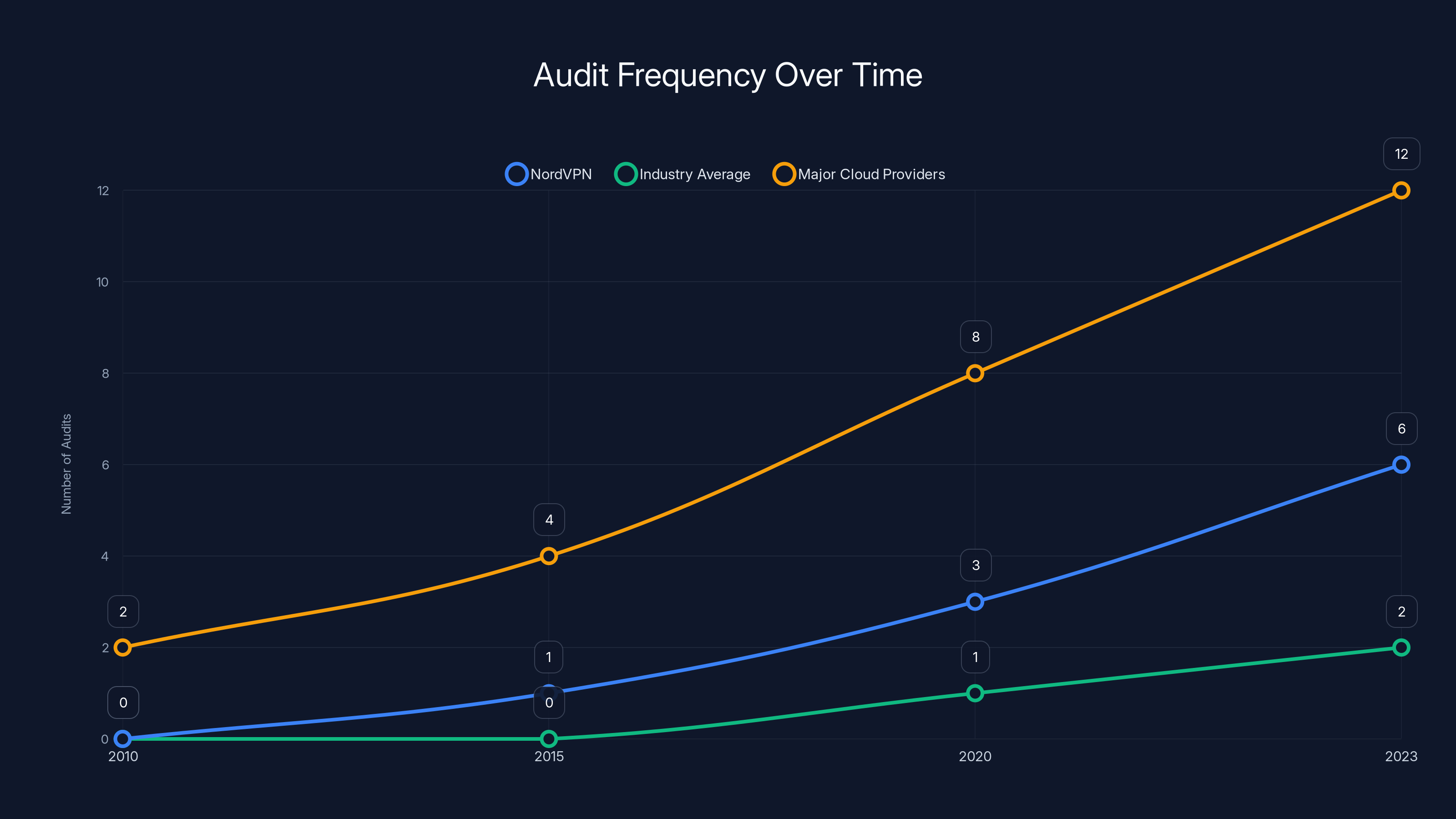
NordVPN's audit frequency has increased significantly over time, aligning with industry best practices. Major cloud providers conduct audits more frequently, reflecting their continuous monitoring approach. (Estimated data)
Comparing VPN Audits: Why Scope Differences Matter
Not all VPN audits are identical. Different auditors use different methodologies. Different VPN companies audit different infrastructure components.
Understanding these differences helps you actually compare privacy claims.
Audit scope variations:
Some VPNs audit their core infrastructure but not all data centers. Nord VPN's audits attempt broader geographic coverage. Express VPN's audits have focused on specific server implementations. Proton VPN audits include open-source code review. These are different approaches.
Auditor differences:
Who does the audit matters. A security firm specializing in cryptography brings different expertise than one specializing in infrastructure. A firm with deep VPN protocol experience is better positioned to evaluate VPN-specific implementations than a generic IT auditor.
Nord VPN uses recognized security firms with relevant experience. That's good. But "recognized security firm" could mean different quality levels.
Methodology differences:
Some audits involve active testing (actually connecting to VPN and testing behavior). Others rely on configuration review. Some examine historical logs to see what was logged in the past. Others focus only on current infrastructure.
More comprehensive methodology = stronger audit.
Remediation transparency:
When auditors find issues (and they usually do find some issues), how does the VPN company respond? Do they publish what was found and how they fixed it? Or do they quietly fix things and don't mention the issues?
Nord VPN publishes audit summaries that mention what was examined and confirmed. That transparency is good. It shows the company isn't hiding findings.

What Audits Don't Tell You (But You Should Know)
Let's be honest about audit limitations. They're useful, but they're not everything.
Audits don't verify law enforcement cooperation: If a government agency asks Nord VPN for user data, an infrastructure audit doesn't prove Nord VPN will refuse. In fact, Nord VPN might comply with certain legal requests (it's incorporated in Panama, which creates specific legal obligations). Audits verify "we don't log," not "we refuse all government requests."
Audits don't examine third-party data sharing: Nord VPN might not log data directly, but it could theoretically share data with partners. Audit scope typically focuses on Nord VPN's direct infrastructure, not third-party ecosystem partnerships.
Audits don't verify historical data handling: An audit in January 2025 verifies infrastructure in January 2025. It doesn't prove the company wasn't logging from 2015-2024. If your privacy concern is about the past, audits don't address that.
Audits don't examine insider threats: Even if logging infrastructure doesn't exist, could a rogue Nord VPN employee with server access set up logging manually? Infrastructure audits verify systems, not insider threat prevention. That requires separate security evaluations (background checks, access controls, audit logging on admin actions).
Audits don't verify all hardware: VPN infrastructure includes not just software but also hardware (routers, firewalls, network monitors). Audits typically examine the systems they can access. Proprietary hardware might not be fully examined.
Audits don't guarantee future compliance: Audit scope defines what's verified. If infrastructure changes, future audits might examine different systems. You can't assume future systems will be as well-designed.
These limitations don't mean audits are worthless. They mean audits are one data point in a larger privacy assessment.
Transparency Reports: The Complement to Audits
Nord VPN publishes transparency reports alongside its audits. These reports show how many law enforcement requests the company receives and how many it complies with.
Transparency reports don't replace audits, but they complement them. Together, they create a clearer picture.
Here's how to read them:
Law enforcement requests: This number shows how many governments or law enforcement agencies requested user data. High numbers indicate either aggressive government surveillance regimes, or that Nord VPN operates in many jurisdictions.
Compliance rate: This number shows what percentage of requests Nord VPN actually complies with. A compliance rate of "0% due to no-logs policy" is the best possible outcome. A compliance rate of "80%" means the company is satisfying most requests, which raises questions about logging (or data retention that contradicts the no-logs claim).
Takedown notices: Nord VPN also publishes takedown notices from copyright holders and other entities. This shows that even when demanded, Nord VPN can only remove content or block users in limited ways (since it doesn't log which user did what).
Nord VPN's transparency reports typically show:
- Thousands of law enforcement requests annually (the company operates globally, so this is expected)
- Compliance rate of ~0% because the company can't provide data it doesn't collect
- Clarification that no-logs means they can't provide logs (instead of "we won't provide logs")
This pattern—high requests, zero compliance—is consistent with a legitimate no-logs infrastructure. A company secretly logging would likely comply with some requests.
Transparency reports matter because:
Consistency check: If audit says "no-logs" but transparency report shows "we complied with 50% of law enforcement requests," something doesn't add up. That contradiction would be a red flag.
Real-world validation: Audits are theoretical. Transparency reports show real-world behavior. "Can you give user data?" "No, we don't have it." That's real-world validation of the no-logs claim.
Law enforcement pressure visible: You can see exactly which countries request data most. This shows which jurisdictions are most interested in VPN user information.
Evolution tracking: By comparing year-to-year transparency reports, you can see whether the compliance rate is changing, request volumes are changing, etc.
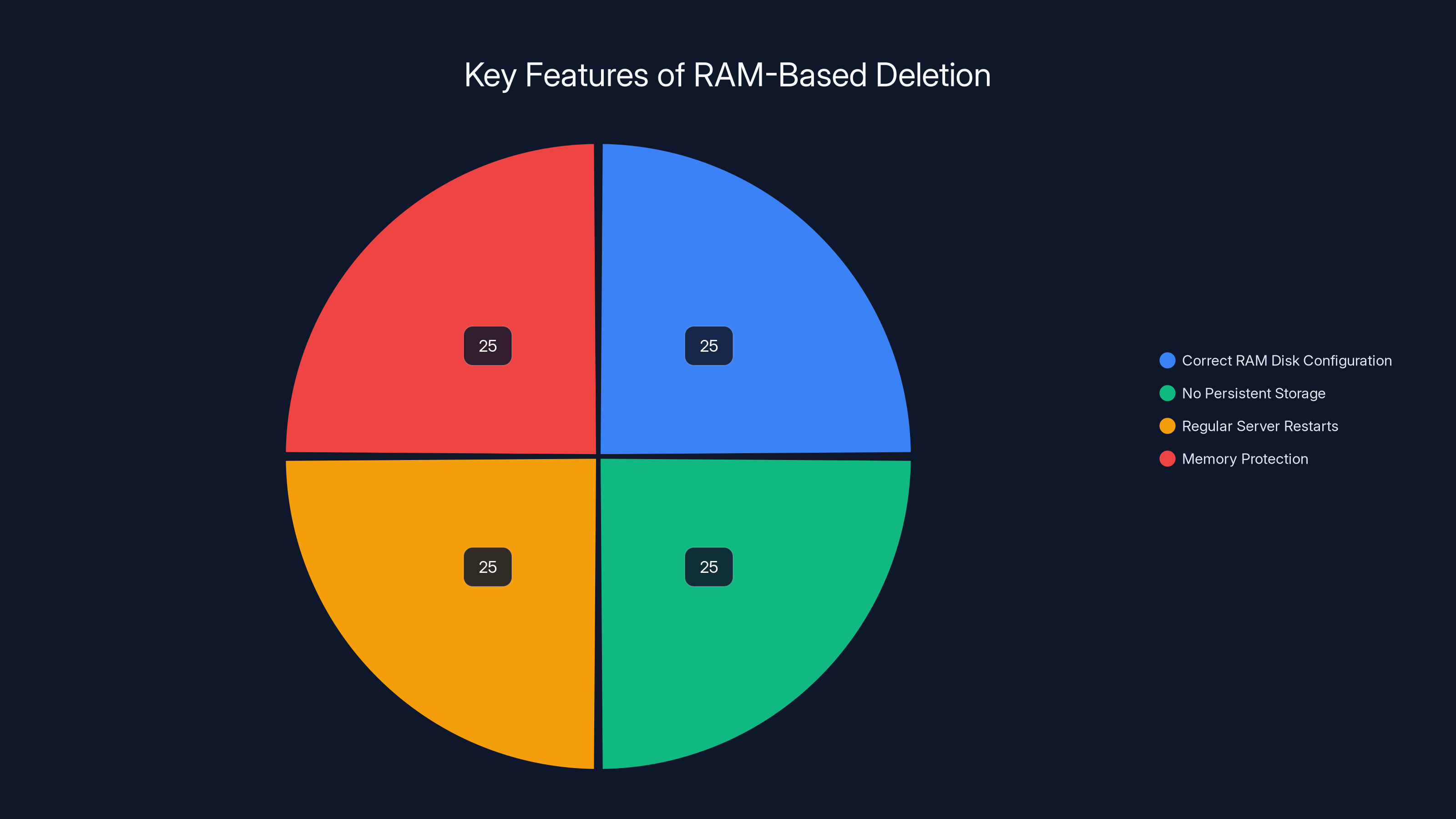
The audit confirms that NordVPN's RAM-based deletion is effective due to correct RAM disk configuration, absence of persistent storage, regular server restarts, and robust memory protection. Estimated data.
How to Evaluate Nord VPN's Privacy Claims Holistically
An audit alone isn't enough to evaluate a VPN's privacy claims. You need multiple data points.
Here's how to think about it:
Audit verification (infrastructure): Does the company have infrastructure that supports the no-logs claim? Yes, according to independent auditors.
Transparency reporting (real-world behavior): Is the company complying with law enforcement in ways that would contradict no-logs claims? No, according to published transparency reports.
Code review (implementation): For open-source components, have security researchers reviewed the actual code? (This applies selectively to VPN companies.)
User research (empirical testing): Have independent security researchers and journalists tested whether Nord VPN is actually logging? What did they find?
Jurisdiction analysis (legal framework): Where is Nord VPN incorporated? What legal obligations exist? What happens if governments demand data?
Competitive comparison: How does Nord VPN's privacy stance compare to competitors? Is it leading, matching, or falling behind?
Incident history: Has Nord VPN experienced breaches? How did it respond? Were there logging inconsistencies that got discovered?
Evaluating just the audit is like evaluating a car by looking at the safety audit. It's one factor, but you'd also want to check actual crash test data, consumer reviews, reliability reports, and driving experience.
For Nord VPN specifically:
- Audit: ✓ Verified (sixth independent audit confirms no-logs infrastructure)
- Transparency: ✓ Strong (publishes detailed law enforcement request data, ~0% compliance)
- Code review: Partial (VPN protocols are standard open-source, some components proprietary)
- User research: ✓ Strong (reputable journalists and security researchers have tested the service)
- Jurisdiction: ✓ Panama-based (no mandatory data retention laws, but no absolute legal protection)
- Competition: ✓ Comparable (similar or stronger than most premium VPN competitors)
- Incident history: Mixed (the company has had security incidents like most tech companies, but no major logging contradictions)
Adding these up: Nord VPN's privacy claims are reasonably well-substantiated.

The Business Model Question: Why Should You Trust Nord VPN's Privacy Claims?
Here's a cynical but fair question: Nord VPN makes money from users. If logging and selling user data made more money, wouldn't the company do that instead?
This is actually an important consideration.
VPN business models essentially break down to:
-
User subscription model (what Nord VPN does): Company makes money from user subscriptions. Logging user data would be a contradiction to the core value proposition. Users pay to avoid logging.
-
Data monetization model: Company offers free VPN but logs and sells user data. User "product" becomes the actual commodity.
Nord VPN operates on the subscription model. This creates aligned incentives: the company profits more by maintaining privacy promises than by breaking them.
If Nord VPN secretly logged users:
- Users would eventually find out: Security researchers, journalists, or inevitably some data breach would expose the logging
- The company's brand would be destroyed: A privacy VPN caught secretly logging would face complete loss of trust and customer exodus
- Law enforcement interest would explode: If logging was discovered, governments would demand all historical logs
- Financial impact would be catastrophic: Lost subscriptions would far exceed any revenue from data sales
The economic incentive is strongly against secret logging.
Conversely, companies offering "free" VPNs with aggressive data monetization have opposite incentives. They profit from collecting data, so audits are less likely and privacy claims are less credible.
Nord VPN's business model isn't foolproof guarantee, but it creates incentives aligned with privacy protection.
This is why audits matter more for companies with profit-aligned incentives. An audit of a subscription VPN (incentive to protect privacy) is more meaningful than an audit of a free VPN (incentive to monetize data).

What Changes for Users Between the Fifth and Sixth Audit?
Nord VPN has published six audits. What actually changed that required a sixth audit?
Timeline context:
- Audit 1-2 (2018-2019): Established baseline no-logs infrastructure
- Audit 3 (2020-2021): Examined expanded server infrastructure
- Audit 4-5 (2021-2023): Reviewed new protocols (Wire Guard deployment, for example)
- Audit 6 (2024-2025): Latest comprehensive review
Why a sixth audit was necessary:
Infrastructure changes happened. Nord VPN added new server types, deployed new protocols, expanded to new data centers, and upgraded security systems. Each change potentially introduces new logging risks that need verification.
Wire Guard implementation is a good example. Wire Guard is a newer VPN protocol than Open VPN. It's more efficient but uses different cryptographic approaches. When Nord VPN started deploying Wire Guard, auditors needed to verify that this new protocol was implemented in a no-logs manner.
Server expansion is another example. If Nord VPN added 1,000 new servers, auditors need to verify these new servers have the same no-logs infrastructure as older servers.
What users actually get from the sixth audit:
- Updated verification of current infrastructure: Not just old systems from years ago, but systems users are connecting to right now
- Confirmation of new technologies: New protocols and server types are verified, not assumed to follow old patterns
- Geographic coverage expansion: Audit sampling likely covers new geographic regions
- Updated threat model: Auditors in 2024 understand different threats than auditors in 2018
- Regulatory compliance verification: Modern audits verify compliance with regulations that evolved (GDPR changes, for example)
The practical impact: when you connect to Nord VPN today, you're using infrastructure that was verified in 2024-2025, not infrastructure verified in 2018 and assumed unchanged.

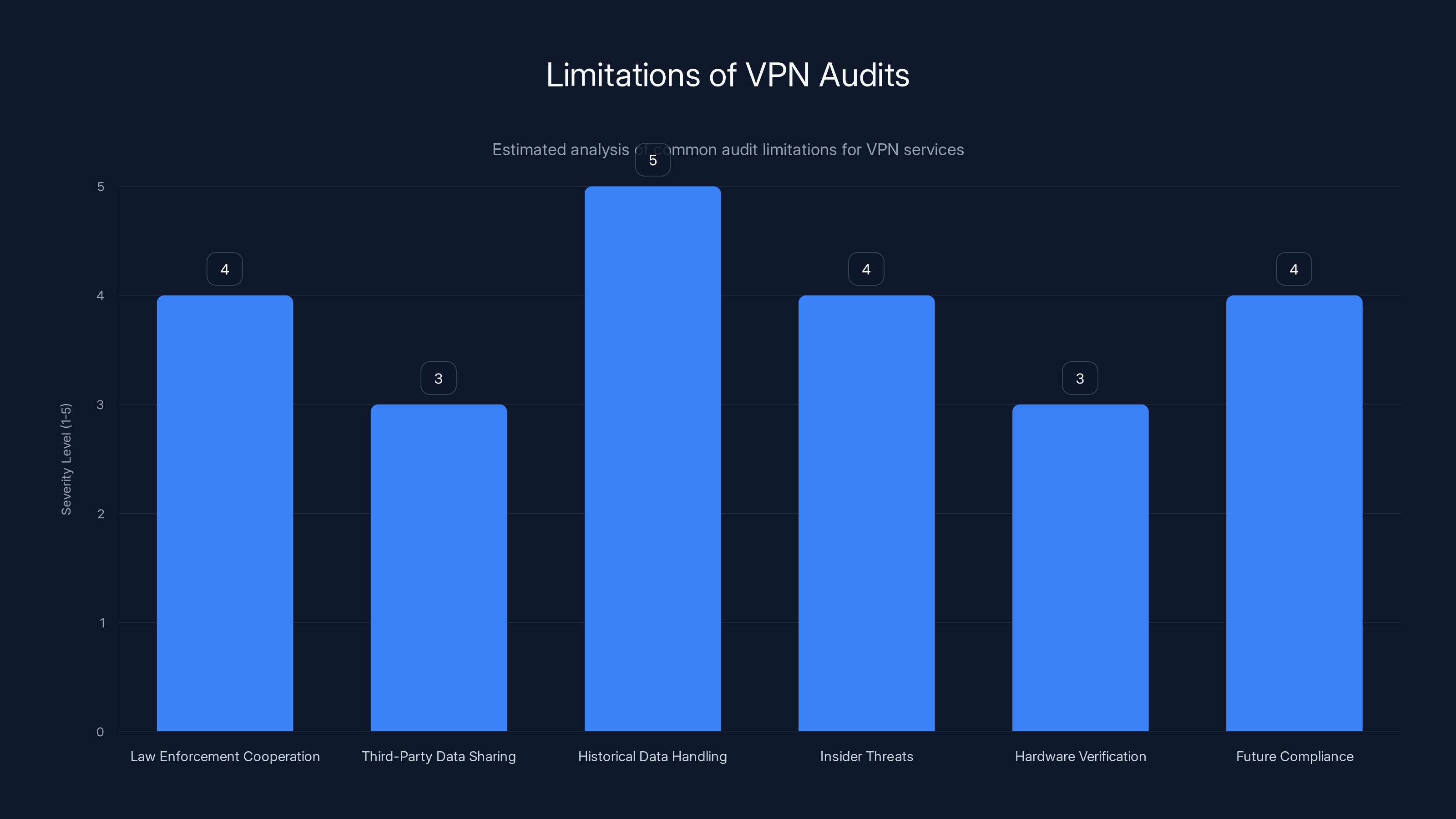
This chart highlights the severity of various limitations in VPN audits, with historical data handling and law enforcement cooperation being the most significant concerns. Estimated data.
The Warrant Canary Approach (And Why Nord VPN Doesn't Use It)
Some privacy-focused companies use "warrant canaries" as an additional transparency mechanism.
Here's how warrant canaries work: A company publishes a statement, "As of January 2025, we have not received any government orders requiring us to log data or provide user information." They update this statement monthly or quarterly.
If the statement stops being updated, or if certain language disappears, the absence itself communicates that something changed. For example, if the statement suddenly says "As of January 2025, we are no longer able to disclose our warrant status," that implies a government order silenced the company.
The logic is clever: governments can demand companies comply with requests, but they (mostly) can't demand companies lie about receiving requests. So silence becomes the signal.
Nord VPN doesn't use warrant canaries. Instead, the company uses transparency reports showing exactly what requests it received and how it responded.
Transparency reports are arguably more informative than warrant canaries because they show actual data, not absence of data.
But warrant canaries serve a different purpose: they signal if something changed that the company can't disclose. If Nord VPN was served a secret government order to enable logging, the company would be legally prohibited from disclosing that order (in many jurisdictions). A warrant canary going silent would indicate something secret happened.
Without a warrant canary, you only see disclosed information. Secret orders wouldn't be visible.
This is a genuine privacy concern for any company operating in jurisdictions with secret surveillance orders. It's not a flaw with Nord VPN specifically, but a limitation of transparency mechanisms in a world where some government requests must remain secret.
However, secret logging orders combined with active logging would be extremely risky for Nord VPN:
- Future discovery: Logs would have to be maintained long-term, increasing breach risk
- Employee whistleblowing: Someone would likely expose the hidden logging (as happened with NSA revelations)
- Audit discrepancies: The sixth audit would likely spot evidence of logging if it was actually happening
The combination of active auditing plus transparency reporting plus market reputation pressure makes secret logging risky, even without warrant canaries.
Security Considerations Beyond No-Logs
No-logs infrastructure is important, but privacy also requires strong security implementation.
Nord VPN's audit verified no-logs. But what about actual encryption security?
Encryption verification:
Audits examine whether encryption is implemented correctly. They check:
- Cipher selection: Are strong modern encryption algorithms used (AES-256, Cha Cha 20)? Are weak or deprecated ciphers disabled?
- Key management: How are encryption keys generated and stored? Are they properly protected?
- Protocol correctness: Is the VPN protocol itself (Open VPN, Wire Guard) implemented according to specifications without weakening modifications?
- Perfect forward secrecy: If one key is compromised, can historical traffic be decrypted? (It shouldn't be able to)
Nord VPN uses industry-standard encryption (AES-256 and Cha Cha 20). These are considered secure by current standards. The implementation follows standard protocols without known weaknesses.
Leaks beyond direct logging:
No-logs is useless if traffic leaks in other ways. Audits verify:
- DNS leak prevention: Your DNS requests (which websites you're trying to visit) must not leak to your ISP or other parties
- IPv 6 leak prevention: Some systems have IPv 6 addresses alongside IPv 4. If IPv 6 isn't routed through the VPN, your identity leaks
- Web RTC leak prevention: Browser Web RTC can leak your real IP even while connected to VPN
- Kill switch functionality: If VPN connection drops, does all traffic stop? (Otherwise unencrypted traffic might leak)
These are implementation details that audits verify but most users don't think about. They matter enormously for actual privacy.

Practical Implications: What This Audit Means for Users
Let's tie this back to actual user experience.
When you use Nord VPN today, here's what the sixth audit actually tells you:
Your connection activity isn't logged: When you connect to Nord VPN servers, the connection details (timestamp, duration, server choice) aren't stored to databases that can be queried later. This is verified.
Your traffic content isn't logged: The actual websites you visit, apps you use, emails you send—none of this is recorded. The audit verified this infrastructure doesn't exist.
Your real IP isn't exposed: Nord VPN properly routes all traffic through encrypted tunnels and doesn't accidentally leak your real IP through misconfiguration. Audited.
You're not exposed to metadata collection: Even metadata (patterns of when you connect, how long, from where) is minimal. RAM-based processing means metadata vanishes when connections close.
Law enforcement can't access your historical data: Because it doesn't exist. This is actually the biggest privacy implication. Even if a government wanted to subpoena your VPN activity, Nord VPN can't provide it. It doesn't have it.
What the audit doesn't tell you:
Whether the company complies with future data preservation orders: If a government legally demanded Nord VPN to start logging, could the company be forced to do so? Probably yes (depending on jurisdiction and legality). The audit verifies current infrastructure, not future legal immunity.
Whether your ISP or other network actors know you're using Nord VPN: The audit verifies Nord VPN doesn't log your data. But your ISP can see you're connecting to Nord VPN servers (the IP addresses are visible). They just can't see your traffic content.
Whether your endpoint security (your computer) logs activity: The audit verifies the VPN service doesn't log. Your own device might log everything. That's a separate concern.
Whether your VPN account itself is private: Nord VPN doesn't require real identity verification (you can pay anonymously in some cases). But the account is tied to payment information that could potentially be linked to you.
These distinctions matter because privacy is layered. Nord VPN's part of the privacy protection (the VPN service itself) is well-verified. But you're responsible for other layers (endpoint security, account anonymity, ISP obfuscation).

The Future of VPN Audits: What's Changing
VPN audit practices are still evolving. Some emerging trends:
Continuous audit frameworks: Rather than annual or biennial audits, some suggest continuous monitoring where auditors have ongoing access to systems. This would catch changes between formal audits. The challenge: continuous monitoring is expensive and potentially creates privacy risks itself (auditors would have more system access).
Cryptographic proof systems: New research is exploring ways for VPN companies to cryptographically prove "no-logs" without revealing infrastructure details. Instead of auditors examining systems, mathematical proofs would provide verification. This is early-stage research.
Decentralized auditing: Some propose third-party decentralized networks that independently verify VPN behavior through active testing. Users could run verifiers that test whether the VPN is logging. This is more sophisticated than human audits but also more complex.
Regulatory requirements: Governments might eventually mandate VPN audits as a licensing requirement. This would make audits standard rather than optional.
Open-source verification: More pressure on VPN companies to open-source their VPN software specifically so security researchers can verify there are no hidden logging functions. Nord VPN uses open-source protocols (Open VPN, Wire Guard) but not all infrastructure is open-source.
For now, the audit model (independent third-party verifying infrastructure at regular intervals) is the most established and practical approach.

FAQ
What does "no-logs" actually mean for a VPN?
No-logs means the VPN service doesn't permanently store identifying information about your internet activity. Specifically, the company doesn't log which websites you visit, what you do online, when you connect, or what data you transmit. Some minimal technical data might exist temporarily in RAM during active connections, but it's automatically deleted when connections close or servers restart. The audit verified this infrastructure exists and prevents permanent logging.
Why does Nord VPN need six audits instead of just one?
Infrastructure changes over time. Nord VPN adds new servers, deploys new VPN protocols like Wire Guard, and expands to new data centers. Each change introduces potential new logging risks. Regular audits verify that new systems follow the same no-logs standards as older systems. Additionally, audit methodologies themselves improve over time as security practices evolve. A 2024 audit incorporates security lessons learned since 2018, making newer audits more comprehensive and relevant to current threats.
Can an independent audit prove Nord VPN is telling the truth about everything?
No, audits verify specific systems at specific moments in time. They confirm that logging infrastructure doesn't exist when auditors examine the systems. But audits can't prove the company isn't secretly logging in undocumented ways, wasn't logging before the audit happened, or won't start logging after the audit. Audits significantly raise confidence but don't provide absolute certainty. Transparency reports, security researcher testing, and business model alignment provide additional verification layers that together create reasonable confidence.
What happens to data if there's a law enforcement request for Nord VPN user information?
Because Nord VPN doesn't log user activity, there's no data to provide. The company's transparency reports show it receives thousands of law enforcement requests annually but complies with essentially zero percent because it doesn't have the data being requested. This is actually the strongest privacy protection—no data exists to be seized or compelled. The audit verified this no-logs infrastructure exists, which means government requests can't produce data that doesn't exist.
Does the audit verify Nord VPN doesn't share data with third parties?
The audit focuses on Nord VPN's direct infrastructure. It verifies that Nord VPN's own systems don't log data. But it doesn't comprehensively examine whether Nord VPN shares information with third parties like hosting providers, analytics companies, or government agencies outside the audit scope. The company's privacy policy and terms of service detail third-party sharing. For additional verification, you can review transparency reports showing law enforcement requests and Nord VPN's responses, which provide real-world data about government information sharing.
What's the difference between an audit and a security researcher testing the VPN?
Audits are structured evaluations by professional security firms examining infrastructure, configurations, and systems according to established methodologies. They're comprehensive but infrequent (every 18-24 months). Security researchers independently connect to VPNs and test whether data is being logged through technical analysis. Researchers can spot obvious logging but can't comprehensively verify all infrastructure. Both approaches are valuable. Audits provide systematic verification. Researcher testing provides real-world validation. Together, they create stronger confidence than either alone.
Are RAM disks really secure, or could data be recovered from RAM?
RAM is volatile memory that requires continuous electrical power. When a server powers down, all data in RAM is permanently lost—not recoverable through any forensic method. This is fundamentally different from data stored on hard drives or SSDs, where forensic techniques can recover deleted data. The audit verified that Nord VPN's servers use RAM-based temporary storage specifically for this reason. Even if someone seized a powered-down server, the RAM would be empty. This is genuinely more protective than software-based deletion of persistent data.
Can Nord VPN be forced to start logging by a government?
Potentially yes, depending on jurisdiction and legal authority. Nord VPN is incorporated in Panama and operates in many countries. If a government served Nord VPN with a legal order requiring logging capability, the company might be forced to comply (depending on applicable laws and whether Nord VPN chose to fight the order). However, such logging would be risky because it contradicts the company's core privacy promise and could trigger customer exodus. Also, future audits might detect evidence of such logging. The audit doesn't provide immunity to government orders, but the no-logs infrastructure means any such orders would require infrastructure changes that are detectable.
Does the audit verify Nord VPN's encryption is unbreakable?
No audit can verify that encryption is "unbreakable." Audits verify that Nord VPN uses strong modern encryption algorithms (like AES-256) implemented correctly according to standards. These algorithms are mathematically secure according to current understanding. But future cryptanalysis breakthroughs, quantum computing advances, or implementation bugs could theoretically weaken encryption. The audit provides confidence that encryption follows best practices, not absolute certainty of permanent security.

Conclusion: What the Sixth Audit Actually Changes
Nord VPN's sixth independent audit validates something the company has been claiming consistently: it doesn't keep logs of user internet activity.
This isn't surprising anymore. After five previous audits reaching the same conclusion, a sixth audit confirming the same thing is validating. But it's also important because it means the infrastructure users rely on today (not infrastructure from 2018) has been verified.
Here's what matters most: the audit isn't a miracle solution to all privacy concerns. It's a specific verification that logging infrastructure doesn't exist in Nord VPN's documented systems. It's one important data point among several (transparency reports, security research, business model incentives, incident history).
When you combine that audit with transparent law enforcement reporting showing zero percent compliance (because no data exists to provide), with ongoing security researcher testing, with a subscription business model where privacy is the product, you get reasonable confidence in Nord VPN's privacy claims.
The progression from zero audits (pre-2018) to six audits (2024-2025) represents real improvement in VPN privacy verification. It's not perfect. Audits have limitations. But they're substantially better than the "trust us" model from earlier eras.
For users considering a VPN, the existence of regular independent audits should absolutely factor into your decision. But don't make it the only factor. Evaluate the full privacy picture: audits, transparency, security implementation, incident history, and business model incentives.
Nord VPN's sixth audit says the company's infrastructure supports its no-logs promise today. That's meaningful. It's worth noting. But it's also worth understanding what it means, what it doesn't cover, and how it fits into a broader privacy assessment.
The best privacy protection comes from multiple verification layers, each reinforcing the others. The sixth audit is one important layer in a system that's gotten substantially more trustworthy than it was just a few years ago.
Key Takeaways
- Independent audits verify NordVPN's no-logs infrastructure exists as claimed, but represent point-in-time evaluations rather than continuous monitoring
- The sixth audit matters more than the first because infrastructure evolves and audit methodologies have improved with emerging security threats
- Audits verify infrastructure capabilities (no logging systems exist) but not operational behavior (the company won't enable hidden logging)
- RAM-based temporary storage design makes logging architecturally difficult without leaving detectable changes
- Multiple verification layers (audits, transparency reports, security research, business model incentives) together create reasonable privacy confidence
Related Articles
- ExpressVPN 81% Off Two-Year Plans: Complete Buyer's Guide [2025]
- Viral AI Prompts: The Next Major Security Threat [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Best Password Managers: Why Keeper Leads in 2025 [Complete Guide]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Grok's Deepfake Problem: Why AI Keeps Generating Nonconsensual Intimate Images [2025]




